 Open Access
Open Access
ARTICLE
AI-Driven Energy Optimization in UAV-Assisted Routing for Enhanced Wireless Sensor Networks Performance
1 College of Internet of Things (IoT) Engineering, Hohai University, Changzhou, 213001, China
2 Department of Electrical and Electronics Engineering, Beaconhouse International College, Islamabad, 44000, Pakistan
3 School of Computer Science and Engineering, Yeungnam University, Gyeongsan, 38428, Republic of Korea
* Corresponding Authors: Ali Nauman. Email: ; Sung Won Kim. Email:
(This article belongs to the Special Issue: AI-Assisted Energy Harvesting Techniques and its Applications in Wireless Sensor Networks)
Computers, Materials & Continua 2024, 80(3), 4085-4110. https://doi.org/10.32604/cmc.2024.052997
Received 22 April 2024; Accepted 19 July 2024; Issue published 12 September 2024
Abstract
In recent advancements within wireless sensor networks (WSN), the deployment of unmanned aerial vehicles (UAVs) has emerged as a groundbreaking strategy for enhancing routing efficiency and overall network functionality. This research introduces a sophisticated framework, driven by computational intelligence, that merges clustering techniques with UAV mobility to refine routing strategies in WSNs. The proposed approach divides the sensor field into distinct sectors and implements a novel weighting system for the selection of cluster heads (CHs). This system is primarily aimed at reducing energy consumption through meticulously planned routing and path determination. Employing a greedy algorithm for inter-cluster dialogue, our framework orchestrates CHs into an efficient communication chain. Through comparative analysis, the proposed model demonstrates a marked improvement over traditional methods such as the cluster chain mobile agent routing (CCMAR) and the energy-efficient cluster-based dynamic algorithms (ECCRA). Specifically, it showcases an impressive 15% increase in energy conservation and a 20% reduction in data transmission time, highlighting its advanced performance. Furthermore, this paper investigates the impact of various network parameters on the efficiency and robustness of the WSN, emphasizing the vital role of sophisticated computational strategies in optimizing network operations.Keywords
The first generation of wireless mobile communications focused on speech systems, while subsequent generations (G2, G3, G4, and G5) represented significant advancements building upon this foundation [1–3]. The field of cellular wireless technology has experienced exponential growth over the past two decades, marked by numerous successful technological advances. However, the rapid proliferation of radio frequencies poses a challenge to sustaining this technological revolution, despite the impressive achievements that have yet to be surpassed by any other technology. As a result, significant developments have occurred in physical layer technologies, frequency reuse in cellular networks, and digital modulation techniques [4–7]. Examples of these advancements include Wideband Code Division Multiple Access (WCDMA), Code Division Multiple Access (CDMA), Orthogonal Frequency Division Multiple Access (OFDMA), Multi Input Multi-Output (MIMO) schemes, and more. These modifications have collectively enhanced the overall performance of networks.
Mobile stations are powered up prior to the initial synchronization phase. This paper provides a concise overview of each generation of wireless technology, from 1 to 5 G. The rapid advancement of affordable, versatile, and compact sensors has been facilitated by wireless communication, computing, and microelectronic technologies [8,9]. These sensors are typically deployed randomly across an area to monitor physical conditions such as temperature, humidity, and pressure [10]. Cooperative methods, sometimes involving multiple hops, are employed to transmit observation data to a data collector (UAV), which then sends the data to a remote server for further analysis.
Fig. 1 depicts the Network Model Diagram for Wireless Sensor Networks (WSN). This diagram illustrates the overall architecture of the WSN, highlighting the deployment of sensor nodes, cluster heads, and the trajectory of the UAV within the network. The interaction among each component demonstrates the flow of data from sensor nodes through cluster heads to the UAV, which ultimately transmits collected data to a remote server for analysis. This figure provides a foundational overview of the network configuration supporting the proposed energy optimization framework discussed in this paper. Furthermore, network sensors can autonomously organize wireless sensor networks by collaborating within their immediate environments. Due to their inherent qualities, WSNs are ideally suited for deployment in hostile or extreme conditions, such as military operations or disaster monitoring [11–14], making them an excellent choice for such applications. Moreover, WSNs find extensive use across diverse domains, including monitoring industrial production lines, observing agricultural and wildlife phenomena, and healthcare applications. Advances in wireless communication and computing technology enable sensor deployments to cooperatively monitor their surroundings. Typically, this information is relayed to a remote server, though increasingly, data is transmitted via multi-hop methods like Wi-Fi to a data collector (UAV). The versatility of WSNs makes them valuable in challenging environments such as disaster zones, military operations, and industrial settings, including production lines. They are also increasingly employed in everyday applications like home automation, smart homes, and healthcare monitoring of agricultural or wildlife populations.
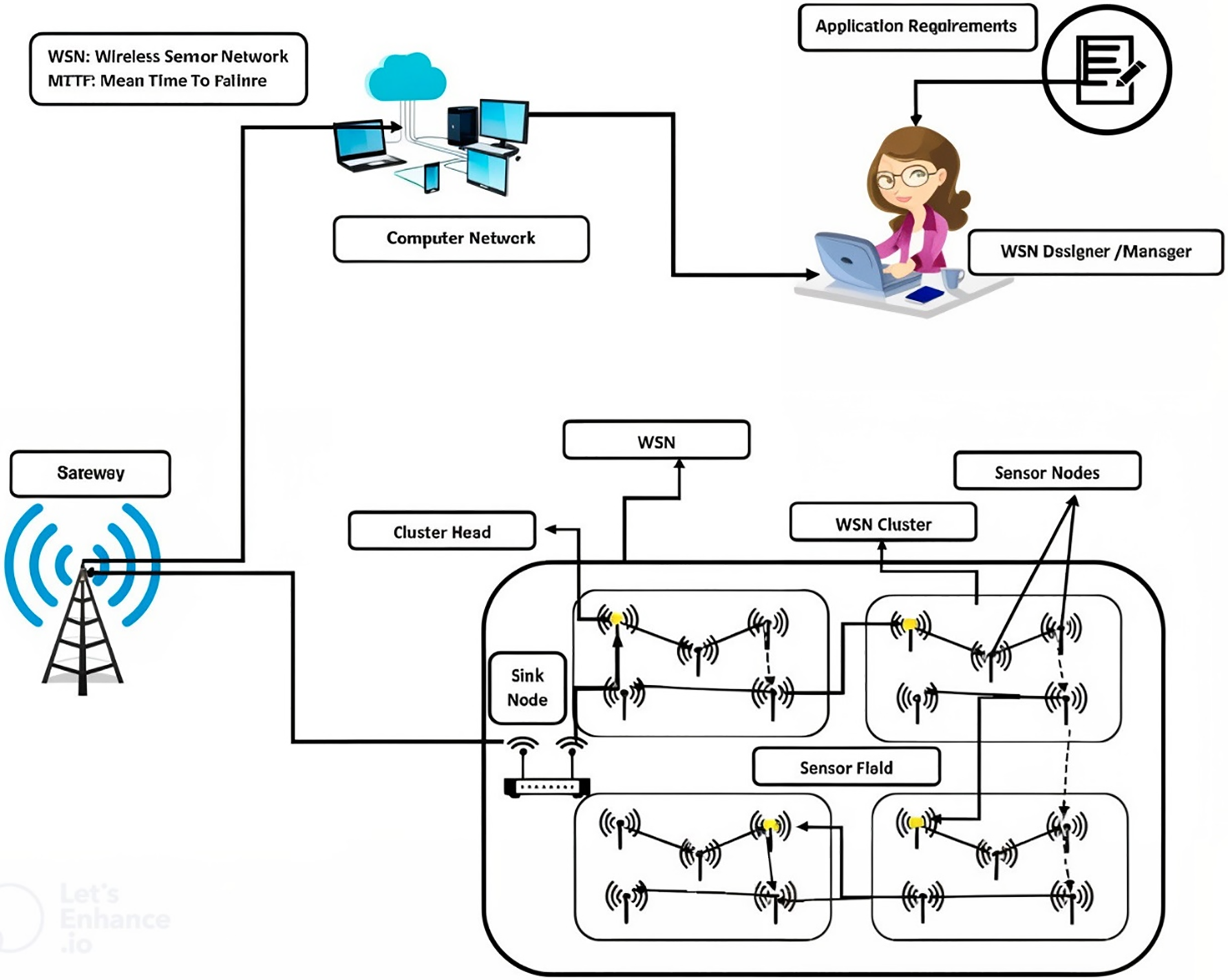
Figure 1: Network model diagram for wireless sensor network (WSN)
There has been a lot of research into the topic of energy efficiency and balance, and it has led to some important discoveries. Clustering technology, which groups sensors into clusters based on a set of criteria, has the ability to drastically reduce WSNs’ energy needs. To communicate with the UAV, one node in each cluster has been designated as a relay. By eliminating the need for direct communication between nodes, clustering also simplifies the topological structure of networks [15]. In addition, data fusion can be executed in relay nodes to reduce unnecessary work and filter redundant data. LEACH, a pioneering cluster-based routing technology, arbitrarily selects relay nodes. Currently, the LEACH framework is being used in more projects than ever before. UAV mobility technology helps reduce the wasteful consumption of power in wireless sensor network [16–20]. The UAV in a WSN supported by one or more UAVs is often transported by a smart vehicle or robot and has total freedom of movement. These benefits may result from allowing UAVs to move freely. First, as the UAV travels, “hot spot” regions where sensors use more energy than others are mitigated. Sensors take turns as “hot spots” to equally disperse energy consumption. Limiting the transmission distance between communication pairs reduces total energy consumption, assuming the UAV mobility pattern is well-designed [21]. Thirdly, a UAV may boost both the latency and throughput of a network (while still ensuring connection). Because adopting a UAV mobility option impacts an existing system in so many ways, there will definitely be obstacles.
For dealing with the problems of energy efficiency in routing, transmission, and data gathering, we present a schema that divides the sensors into sectors. Within each cluster, a CH is picked based on its weight (estimated based on the source node’s distance and residual energy). Within clusters, communications are either single- or multi-hop-determined by how much power remains [22]. Additionally, a CH is designated as the leader to communicate with the UAV by following an optimal path developed by a greedy algorithm [23]. After choosing the subsequent leader who optimizes performance, data collection continues along a predetermined trajectory. The suggested schema has been compared to various current schemas via extensive simulations. We additionally expand our framework by exploring the effects of a wide range of variables on performance.
The key research objectives can be summarized as follows:
• The proposed schema that categorizes the sensors into several sectors in order to address the issues of energy efficiency in routing, transmission, and data collection.
• The cluster head (CH) is nominated from each cluster based on its weight, which is calculated from the distance and remaining energy of the source node. Members of each cluster vote on the routing path that will take them to their respective CHs, which may include a single hop of communication or multiple hops, depending on the amount of power left.
• Additionally, CH is selected as the leader to interact with the UAV by adhering to an efficient path created by a greedy algorithm. Following the selection of the next leader who optimizes performance, data collecting follows a preset path.
• The simulations not only show that our innovative routing schemas are superior to CCMAR and ECDRA, However, we should also look into how various factors influence a network’s performance. The performance of the design was ultimately improved as a result of these simulations.
The rest of the paper is structured as follows: Section 2 reviews related literature, Section 3 details the system model, Section 4 outlines the proposed methodology, and Section 5 presents the simulation results.
Many individuals are commencing to look into energy-efficient routing methods. For instance, ECDRA, a dynamic routing system for unmanned aerial vehicles, can save power. This protocol differs from others in that sensor nodes are organized into clusters, and they’re tasked with rotating around a center point which holds the UAV. This dynamic network topology is changed according to the position of the UAV, which is situated on the outside perimeter of the circular arrangement of sensor nodes [24]. The most popular, widely recognized and prominent hierarchical routing protocols that has ever been invented is called LEACH, which stands for Lightweight Ethernet Access Protocol [25]. In LEACH, every sensor is placed into one of two categories: cluster heads (CHs) or normal nodes (ONs). An ON sends the data that it is monitoring to the CH that is most suited for it, and the CH in turn fuses and sends the data to a base station (BS). LEACH is more effective than traditional routing protocols because it lengthens the lifetime of networks by selecting CHs in a random fashion. This makes LEACH more efficient. CHs have a tendency to be dispersed in an erratic pattern, and the high energy loss that follows from their direct interaction with the BS.
The LEACH improvement, Power-Efficient Gathering in Sensor Information Systems, another hierarchical chain technique (PEGASIS) [26]. As long as the receiving node is closer to the base station than the sending node, the data packet only needs to be sent from the sending node. A greedy approach joins together communication chains between clusters. Sending data packets to the base station is the responsibility of the node nearest to the base, known as the chain leader [27]. The elimination of long-distance communication in the design results in significant energy savings. In the meanwhile, multi-hop transmission may result in severe network delay. Therefore, delay-sensitive applications should not use this protocol.
First node death time may have a significant impact on classic load-sharing clustering systems like LEACH. HEED (Hybrid Energy-Efficient Distributed Clustering) is able to get around this problem since it prioritizes nodes with the highest energy by giving them a better probability to be CHs when they are replaced. Using average minimum reachability power (AMRP) is a viable way for assessing intra-cluster communication costs and calculating how much each individual node will cost.
AMRP Calculation:
Average Minimum Reachability Power (AMRP) is a metric used to evaluate the communication cost within a cluster. It is defined as the average of the minimum power required for communication between nodes in a cluster. The formula for AMRP is given as:
We look at AMRP, the protocol where MinPwr refers to the minimum possible transmission power between two nodes, in this research. We will also investigate how wireless sensor networks may be used to deal with hotspots. A mobile UAV may go from a highly connected location to one with less service. This may be utilized in a wireless sensor network to give ongoing coverage. Below are several routing systems employing single hot spots. First node death time may have a significant impact on classic load-sharing clustering systems like LEACH. HEED (Hybrid Energy-Efficient Distributed Clustering) is able to get around this problem since it prioritizes nodes with the highest energy by giving them a better probability to be CHs when they are replaced. Using average minimum reachability power (AMRP) is a viable way for assessing intra-cluster communication costs and calculating how much each individual node will cost.
Due to the widespread use of mobile phones, routing protocols that use UAVs have become a hot topic. There are many different examples, including AMRP and Mobile Ad-Hoc Networks (MANETs). Where
According to [28], a novel approach titled Load Balanced Clustering with Dual Data Uploading (LBC-DDU) was presented. This approach partitions the network into three layers: Sencar, cluster head and sensor. At the outset of each cycle, sensors are able to compute an optimal route in advance and then walk it to collect data via single-hop broadcasts. After reaching each designated location, sensors would return to a home base to prepare for the subsequent round. Sensors have two antennas for exchanging information with two CHs so that they can utilize multi-user MIMO technology to reduce delay and improve efficiency.
As [29] introduced a data-gathering technique that organizes the data in clusters of trees, the data are arranged in trees (TCBDGA). Each node’s importance is calculated using a number of conditions, one of which is the amount of energy it has left over, the number of its neighbors, and its distance from the base station (BS). Thus, nodes choose their closet with the highest weights as their parents. This results in the growth of trees, which are then decomposed into smaller trees depending on their depth and traffic load to improve performance. As [30] designed UAVs with barriers for WSNs, using the suggested graph-based scheduling mechanism, they then offer a heuristic route planning method for avoiding obstacles. The UAV is programmed to walk along this route and gather data through direct transmission from CHs. After finishing its data collection, it goes back to where it was. Results from computer simulations show that the approach effectively extends the life of the network, with the scheduling mechanism playing a crucial role in reducing network complexity when obstacles are present.
According to [31], authors introduced the VELCT (velocity energy-efficient and link-aware cluster tree) system. Cluster Heads (CHs) are chosen at setup time based on their threshold values, and then performance-optimized clusters are formed through inter-CH communication. Then, in order to build a data collection tree (DCT), it is decided which nodes would be data collection nodes (DCNs). During the steady-state phase, where Cluster Heads (CHs) gather monitored data from their members and transmit aggregated data to DCNs, there is no degradation in throughput, energy consumption, or delay performance. Cluster-chain mobile agent routing, which is illustrated in [32], is an approach CCMAR. It employs the cluster head selection value to determine the most effective CHs. Members of the cluster construct data transmission networks. Using residual energy level, signal intensity, and path loss, a routing route for an MA is determined. There are several expenses associated with networks, but the longevity of a network is an essential issue that must be considered continuously. Combining the particle swarm optimization approach, the immune algorithm, and a biomimetic ant colony optimization algorithm yields improved outcomes. Several studies have shown that integrating a large number of UAVs into WSNs may greatly improve their performance. Since references [33–37] introduced a multi-UAV event-driven algorithm. Each node in this strategy may be in either the monitoring or broadcasting state. Whenever an event is detected, a node transitions from its monitoring state to its transmitting state and begins sending packets to the UAV. In large-scale WSNs, the movement of a UAV is unrestricted, thus it is divided into sections with separate UAVs on each section to minimize the energy consumption of the whole network. Also like [38–40], we use a multi-UAV distance-aware routing algorithm to decrease WSN energy consumption by delivering packages only when they are physically close to their ultimate destination. Multiple mobile CHs are constructed to gather data from various sensor field locations. The base station collaborated with mobile CHs to improve communication and decrease “multi-hop” communication. There were presented strategies for extending the lifespan of the network. Large number of mobile CHs are developed to collect data from various positions over the sensor field. The base station worked collaboratively with the mobile CHs to communicate more effectively and reduce “multi hop” communication. Methods were proposed to extend the network’s useful life.
We take into consideration that the detecting field is a spherical area. Each point of the node possesses a distinctive identification that varies from others’ points. We do some fundamental hypotheses as follows:
• All sensor devices are erratically implemented by moving objects, such as an airplane, and stay static after implementation.
• All sensors’ devices have information on the locality of the other connections through the data interchange.
• All sensors’ devices have even preliminary energy/power, and their batteries could not be replaced. One time a sensor consumes its power, it will be worthless.
• The communication energy of sensors can be configured and set based on the transmission interval.
• The varying route of the UAV is well-arranged, and it holds limitless energy or power also communication variety.
We deploy N sensor devices within a circular area of radius R. The sensors are denoted as
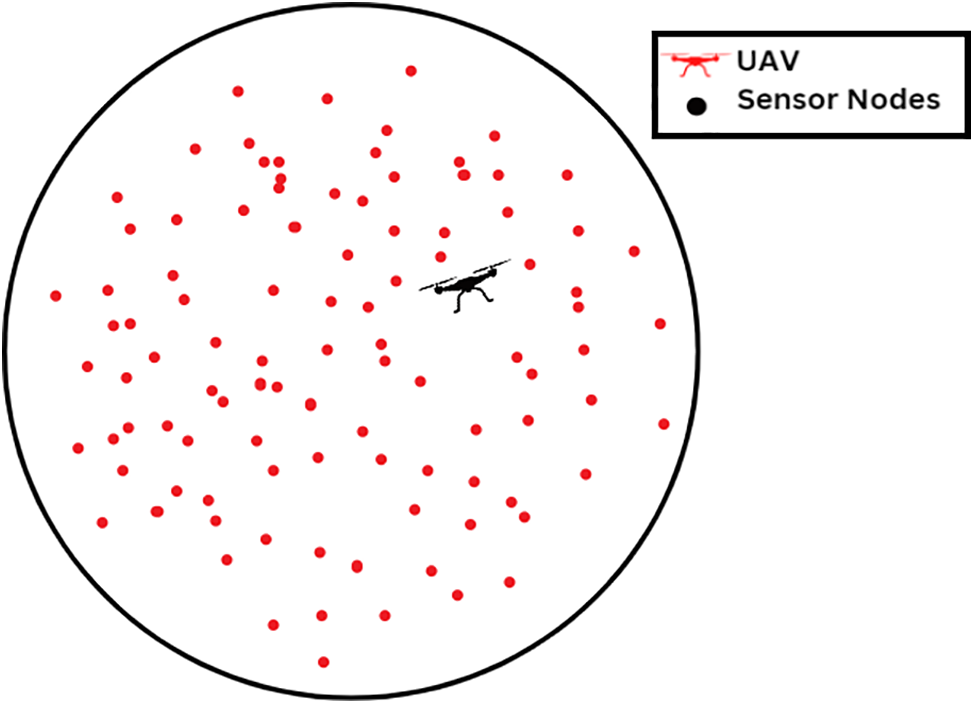
Figure 2: Randomly distribution of sensor nodes among the region-network model
Here, we develop a simulation model for energy that has been used before [40]. Fig. 3 illustrates that energy consumption is largely separated into two categories: transmission side utilization and reception side use. In the transmission phase, signals are generated and propagated. Once the signal has been created, the amplifier will amplify it. To boost the signal in line with its transmission gap, the amplifier employs two separate capabilities. This means that the transmission energy model is further divided into a free storage approach for short-distance communications and a multipath decreasing approach for long-distance communications. Transmission utilization refers to the energy used by the transmission route and amplifier, while reception use refers to the energy used by the reception route. As demonstrated in Equation, all sensors will need send out a packet of data with L bits of information over a distance of dis:
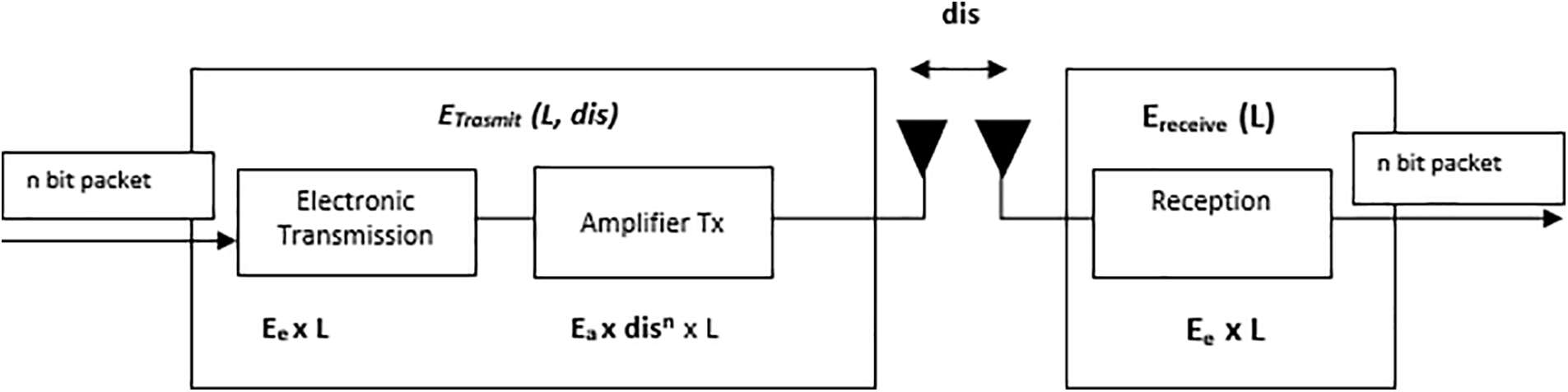
Figure 3: Energy consumption model
where
The energy consumed to receive an L-Bit data packet is given by:
where
The number of CHs determines the number of segments for the entire sensor node region. Based on its location data, each sensor node is placed into one of many groups. The equation for each sector’s angle is:
where
y ≥ 0 and x < 0 where y represents the position of the sensor node along the y-coordinate axis and x represents its position along the x-coordinate axis. After clustering, we establish the center of the sensor node region as the basis for the coordinate axis and the network according to Fig. 4.
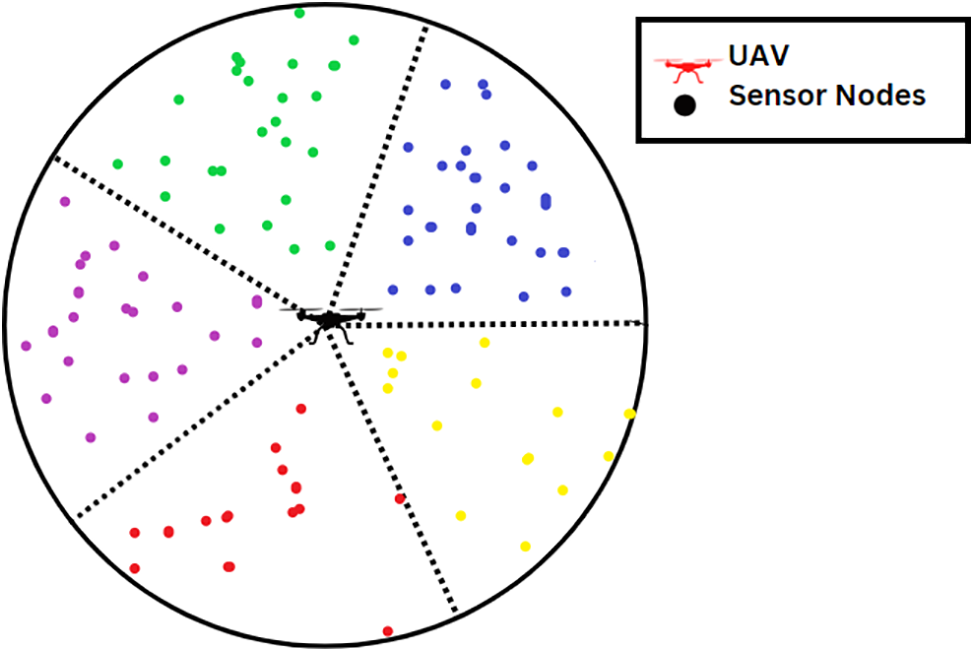
Figure 4: Distribution of sensor nodes into clusters-clustering formation
In optimizing the efficiency of our sensor network, our focus lies in the strategic selection of nodes abundant in energy resources. A pivotal criterion for CH determination is the residual energy of these sensor nodes, ensuring the vitality of the network. Simultaneously, we underscore the significance of the distance between UAVs, and CHs to enhance the diversity of CH distribution. With CHs tasked to relay data to the UAV, a process consuming substantial energy, proximity becomes imperative, compelling us to position sensor nodes in close vicinity to the UAV. The nuanced estimation of sensor node weights is achieved through the application of three distinct methods, and the ensuing simulation delves into the outcomes. Utilizing Eqs. (7)–(9), we systematically calculate the weights of sensor nodes, ensuring a comprehensive understanding of their impact on network dynamics and energy efficiency.
Assuming this is a precautionary CH situation, the UAV’s closest sensor node will predominantly communicate its mass to the other cluster members. Only sensor nodes that have attained the developed weight and been turned into a new CH applicant will broadcast their weight. As the final CH, the most substantial protuberance within each cluster will be chosen. After a CH is picked, the sensor node appears like Fig. 5. Numerous further research has examined the various CHs present in each cycle of CCMAR, LEACH, and TTDD. Even though a lot of power is being wasted, regulatory and control communications will expand considerably due to repeated CH selection. In our easily readable schema, the CHS distribution will never take place until none of the CHS fulfil the state that has the most significant weight. Throughout the whole of each cycle, each participant sensor node will send a data packet containing its weight to its associated CH for the purpose of collecting. Once the CHs in a given cluster become aware that the sensor nodes linked with them have grown more mass than they have, the CHS will broadcast a Re-clustering notice in such clusters once the CHs realize that their associated sensor nodes have gained more mass than themselves.
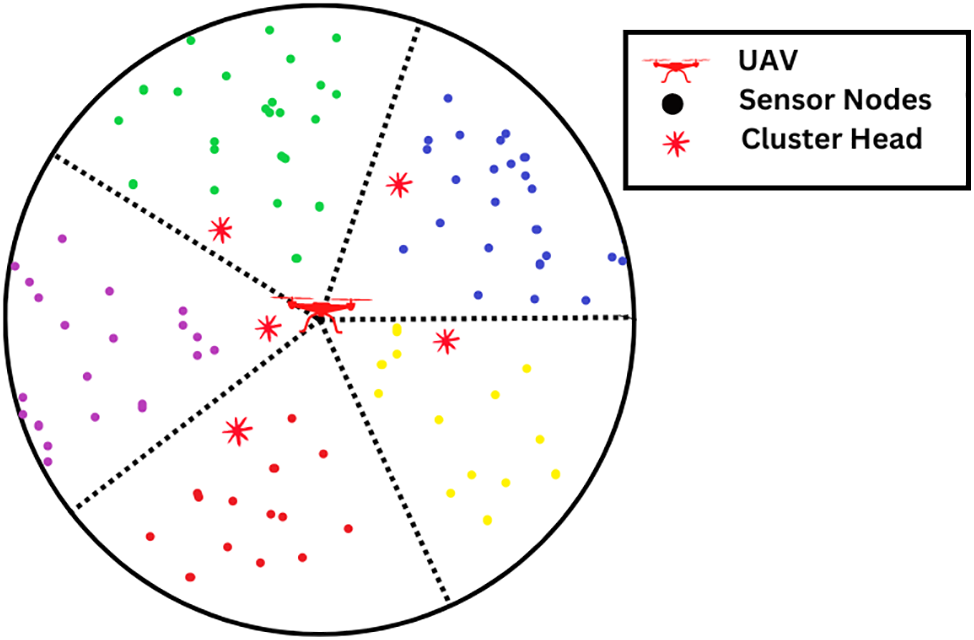
Figure 5: Selection of CHS
Frequently, long-distance communication uses a considerable quantity of energy and reduces the network’s durability. Therefore, intra-cluster transmission must prevent long-distance communication. Nodes in our architecture are capable of calculating the energy costs of alternate routing methods in order to choose the optimal relay node or transmit data directly. According to [41,42], transmission energy usage is almost one thousand times higher than expected. Therefore, it is important for representatives to calculate an optimal routing path. Calculating the energy consumption on the travel path when direct transmission is used is as follows:
where
The intra-cluster transmission energy consumption is evaluated using:
where
4.4 Inter-Cluster Communication
In this part, the optimistic technique is utilized to establish a chain for inter-cluster communication in order to prevent prolonged communication gaps. The strategy for the chain’s future growth may be broken down into the following steps:
Step 1: The UAV notifies all CHS of their identification and location by sending out a chain formation message that is broadcast throughout the whole of the network.
Step 2: When the UAV obtains input about CHS, it will choose the CH that is geographically nearest to it as the leading candidate. The leader is responsible for providing immediate communication of the information to the UAV.
Step 3: Each CH only sends data to a relay CH closer to the UAV using the inefficient way. Chain creation results in Fig. 6.
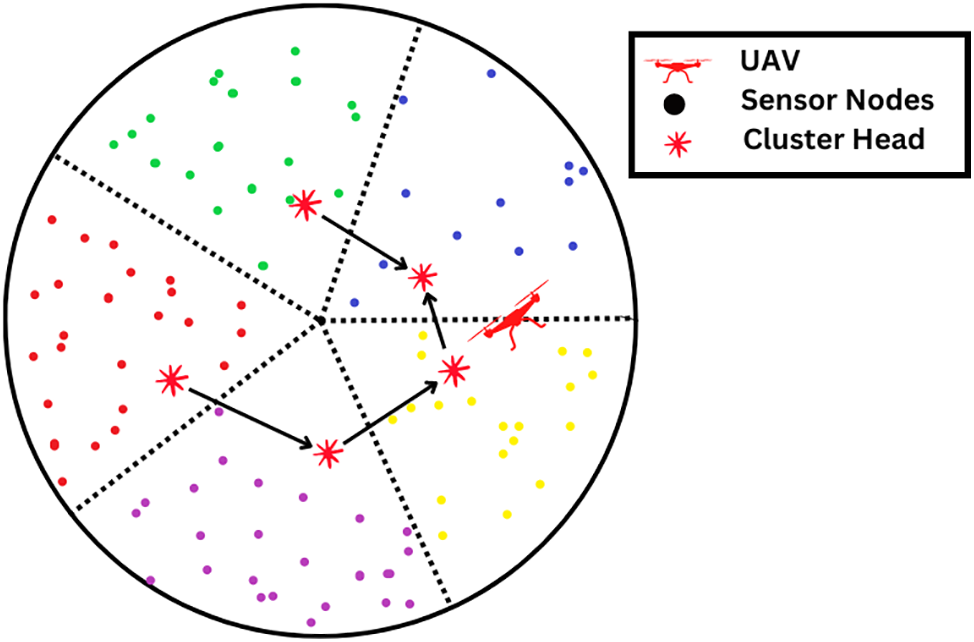
Figure 6: CHs generation chain
As can be seen in Fig. 7, the travel path that our proposed design for the UAV would take would be in the shape of a spherical. It is feasible to compute the current location of the UAV by using both its starting position and the amount of time it has moved. Because of this, all the unmanned aerial vehicle (UAV) has to do to limit the amount of broadcast message sent by the network is simply announce its beginning location and rotational velocity. Let’s say the UAV’s initial location is
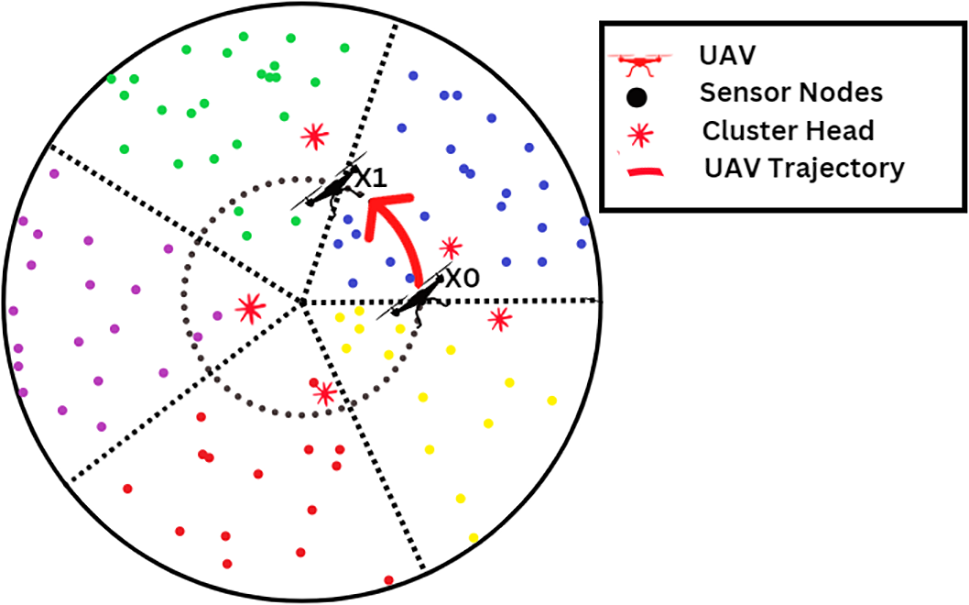
Figure 7: UAV flight path trajectory
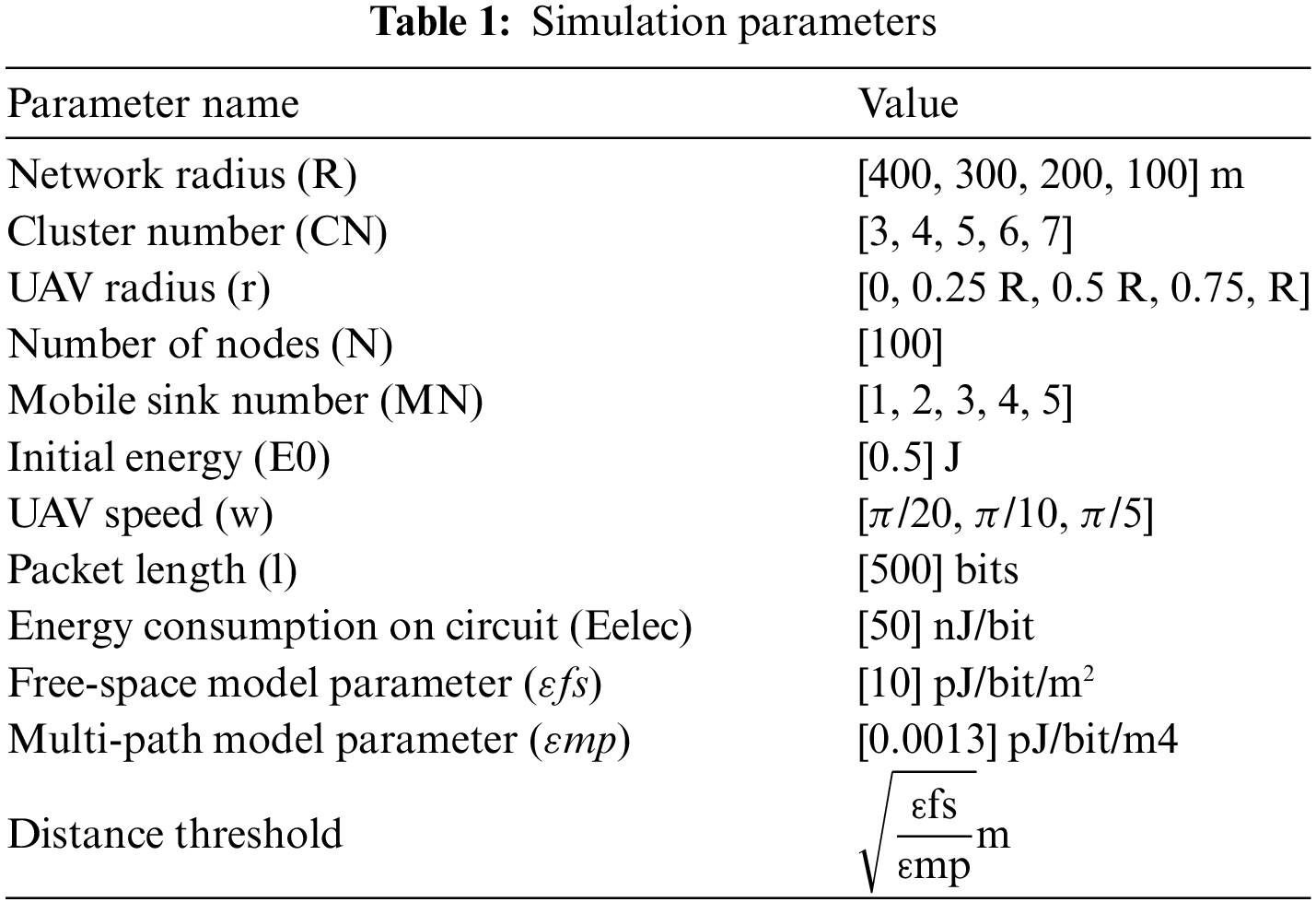
We used the MATLAB R2016a simulation environment to test our proposed schema. Table 1 summarizes some of the few key parameters.
Node use significantly affects WSN performance by decreasing energy consumption, increasing network longevity, and increasing the overall coverage of the system. In addition, the widespread usage of sensors might be able to aid in the eradication of the repercussions indicated above. We provided a framework for assessing the Cluster Chain Mobile Agent Routing Algorithm and the Energy Cluster-based Dynamic Routing Algorithm. To fairly evaluate the relative merits of the various methods, we ran them all on the same network model. In most situations, the lifespan of a network is defined as the moment in time when the network encounters its first occurrence of a dead node. Fig. 8 depicts the simulation result of comparing the network longevity of multiple strategies. From Fig. 8, our proposed schema demonstrates superior network lifetime compared to CCMAR and ECDRA. CCMAR incurs high forwarding costs due to its chain topology for intra-cluster communication. Moreover, CCMAR’s inter-cluster communication utilizes direct links between CHs and UAVs, significantly elevating the energy consumption of C. ECDRA also used a rotating UAV inside the sensor field, but only considered the UAV’s movement on the sensor field’s perimeter. As a result, border sensors waste more energy, hastening their demise. Our proposed schema obtained the highest performance since it calculated the energy for several routing paths and picked the optimal one. Fig. 8 shows the results of an analysis of the amount of energy used by a variety of distinct algorithms. The facts shown in Fig. 8 indicates without a reasonable doubt that the design we provided was the most effective. Due to its excessive data forwarding, CCMAR wasted unnecessary energy, resulting in a greater total energy consumption than the other two algorithms. Due to the fact that ECDRA’s average communication distance was much greater than that of the suggested approach, ECDRA consumed more energy than the proposed method.
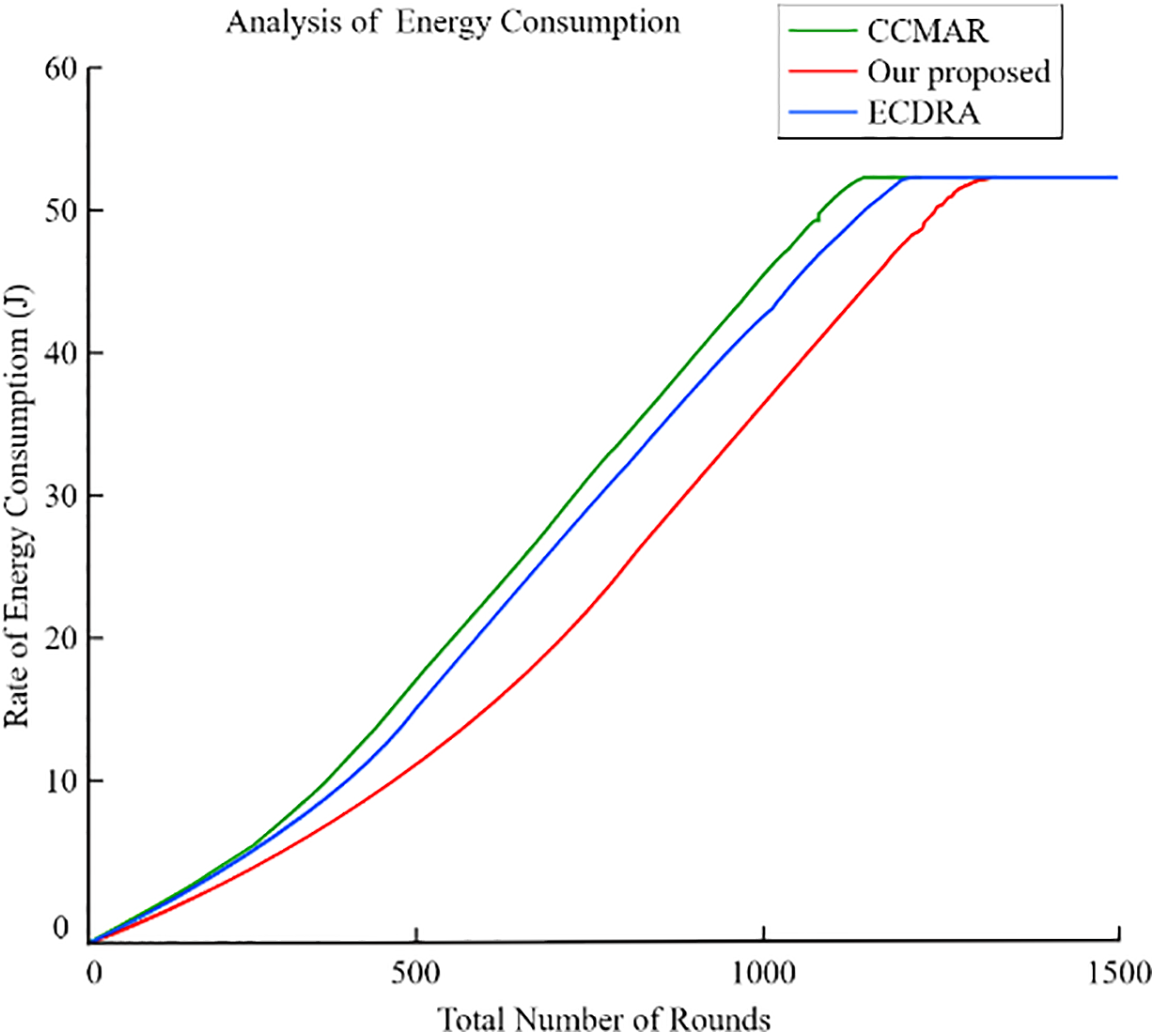
Figure 8: Analysis of the amount of energy
5.1 Analysis on UAV Different Radius for Different Network Size
We propose a design where the UAV moves in a circular path with a small radius. By varying the trajectory’s radius while keeping all other variables constant, we achieved our desired outcome. Fig. 9 illustrates the network lifetime under different radius settings: 0, 0.25 R, 0.5 R, 0.75 R, and R. The results from Fig. 9 show that the network had the longest lifetime when the UAV traveled with a radius of 0.25 R. Conversely, network performance was weakest when the UAV operated outside this circular path. The proposed method investigated the amount of energy required by UAVs with a variety of radii. Fig. 10 displays simulation results. When the UAV’s radius reached somewhere around 0.25 R, the energy consumption obviously rose at a far slower rate than normal. In addition to this, the network’s consumption of energy skyrocketed as the UAV’s radius got closer and closer to R. It is probable that we compensated for each node’s residual energy, which led to inefficient network-wide energy utilization, and that this was the cause of the discrepancy.
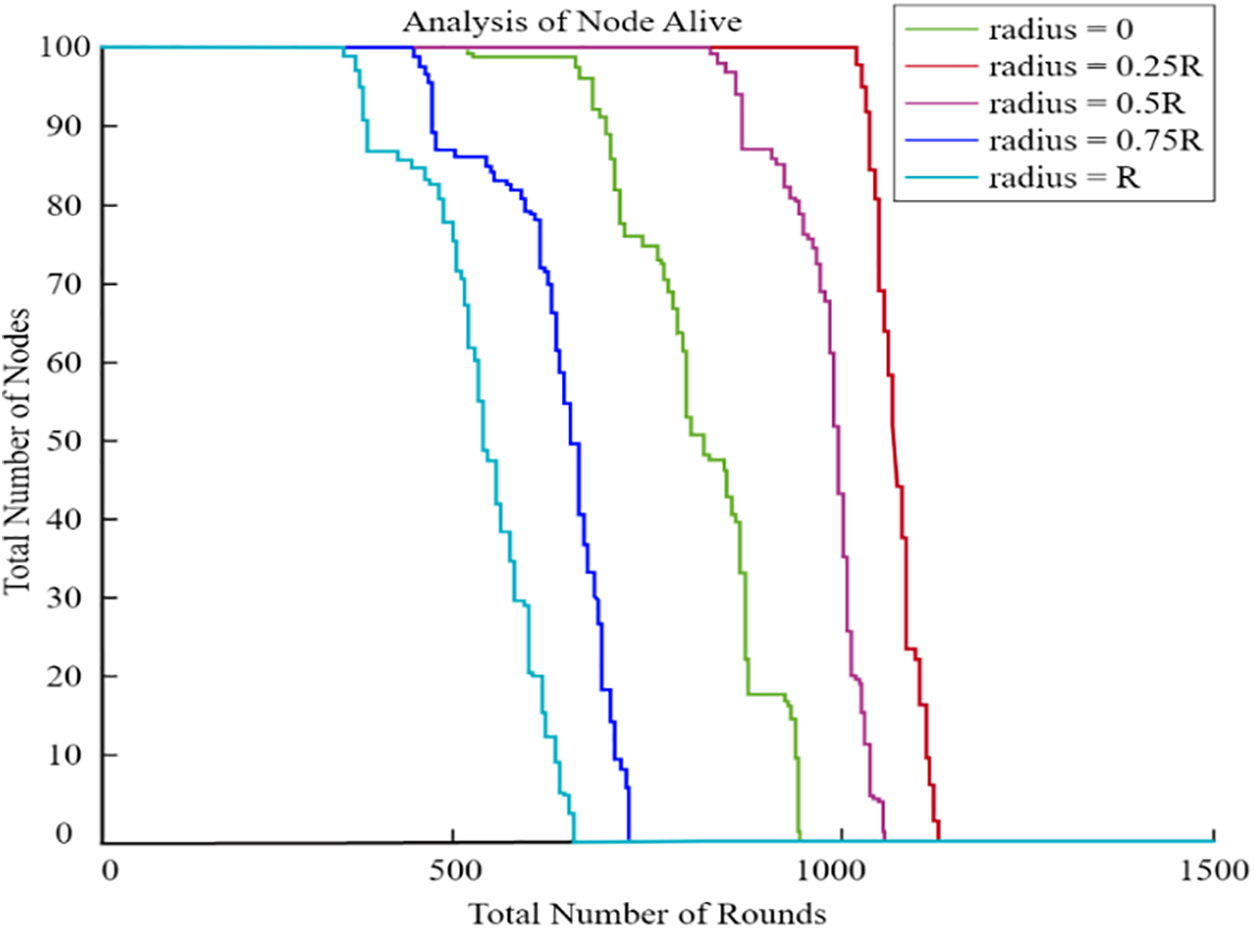
Figure 9: Network lifetime
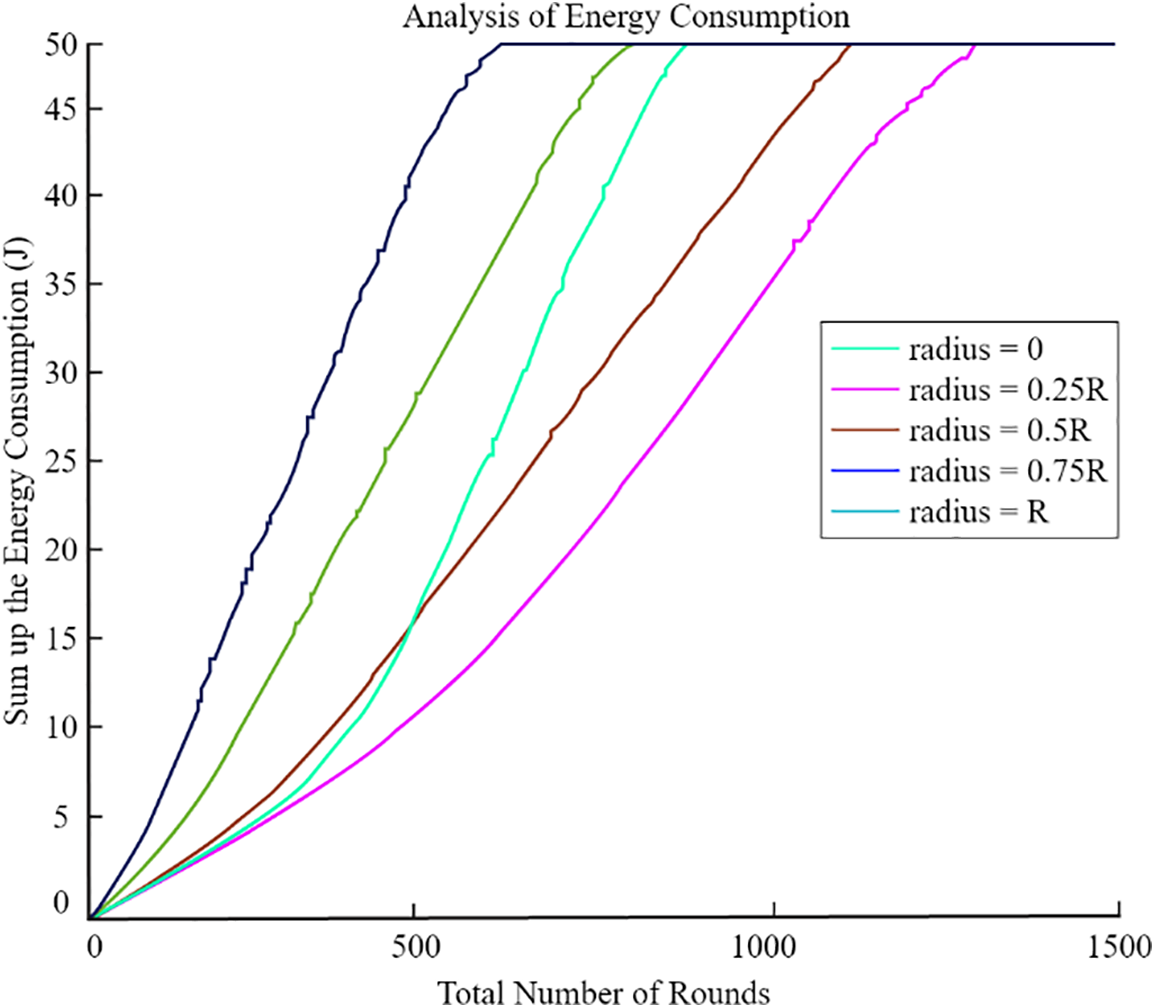
Figure 10: Energy consumption (radius based)
Furthermore, Fig. 9 illustrates the network lifetime comparison between CCMAR, ECDRA, and the proposed algorithm. The x-axis represents the number of rounds, while the y-axis shows the remaining energy. The proposed algorithm demonstrates a longer network lifetime compared to CCMAR and ECDRA, indicating its efficiency in energy management.
This figure compares the residual energy levels of the sensor nodes for CCMAR, ECDRA, and the proposed algorithm. The x-axis represents the number of sensor nodes, and the y-axis shows the residual energy. The proposed algorithm maintains higher residual energy levels, demonstrating its effectiveness in minimizing energy consumption. Clearly, the energy consumption rose far less rapidly as the UAV’s radius approached 0.25 R. Furthermore, we analyzed the optimal radius of the UAV’s circular trajectory at distances of 100, 200, 300, and 400 m, tailored to various network sizes. As the network size R increased, both total energy consumption and network lifespan also increased. Fig. 10 clearly demonstrates that a radius of 0.25 R consistently proved to be optimal for the UAV across all network sizes. So, in the further graphs from Figs. 11–14, we have analysed the number of nodes alive with variation of radius.
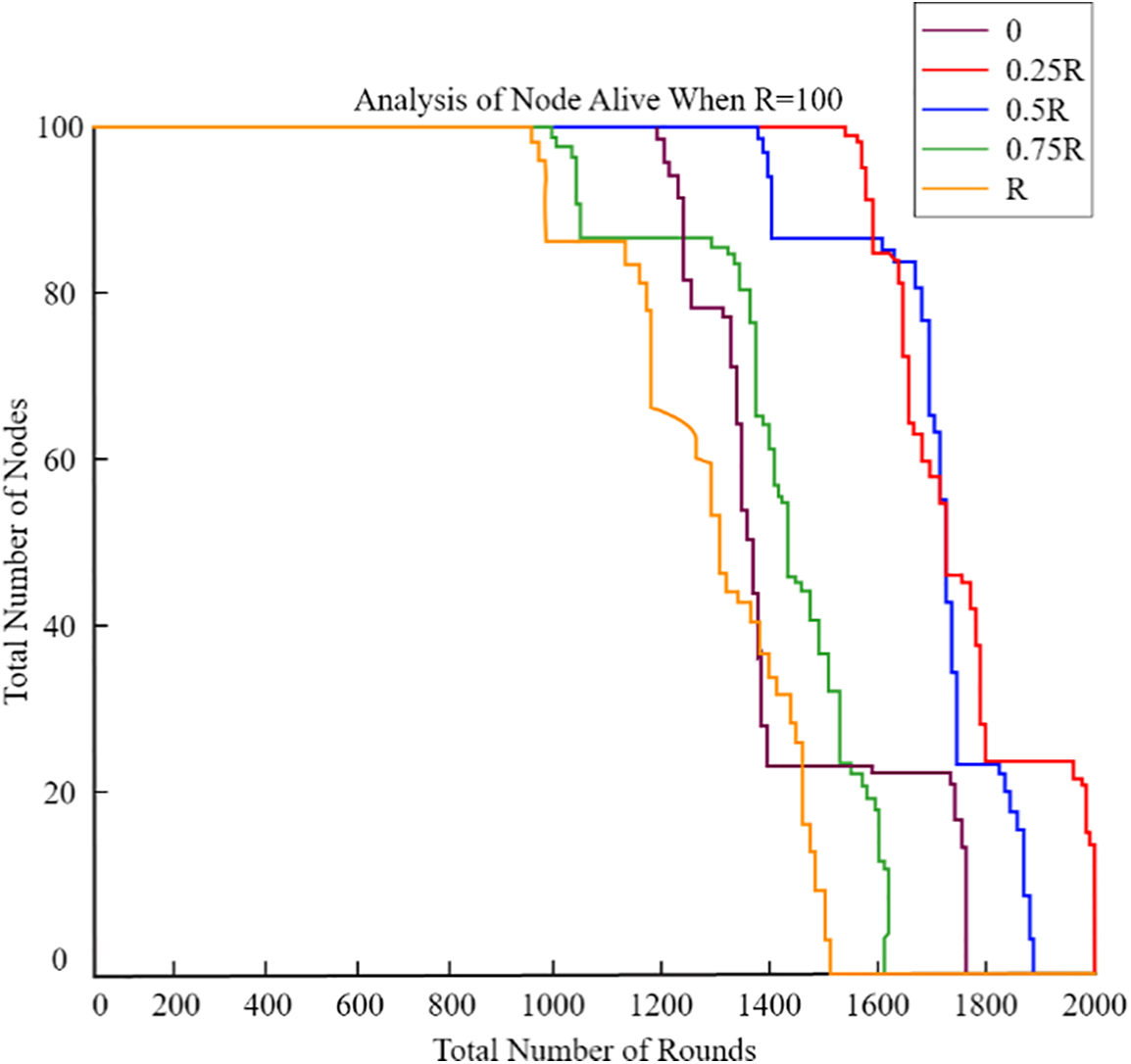
Figure 11: Analysis of nodes alive when R = 100
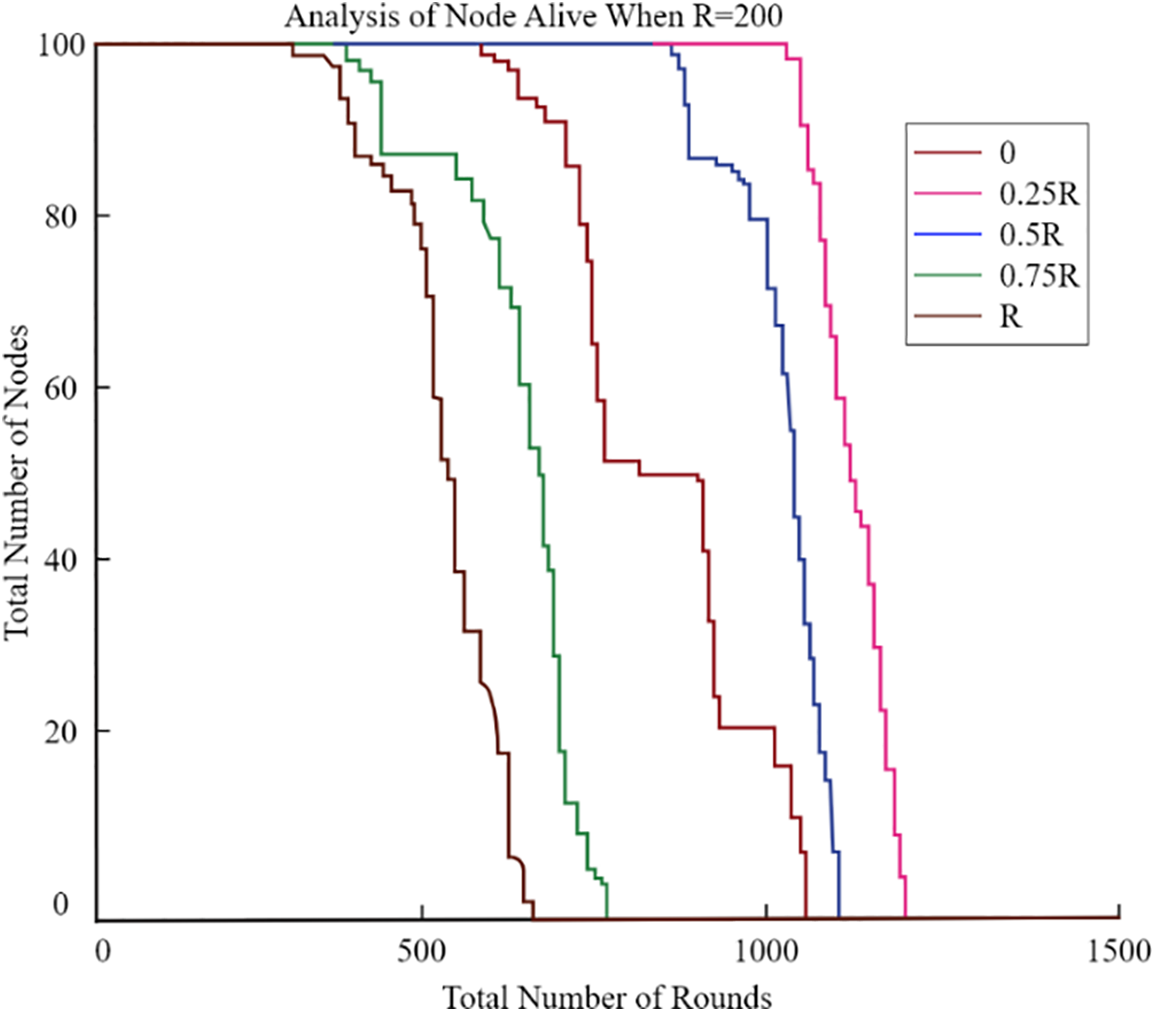
Figure 12: Analysis of nodes alive when R = 200
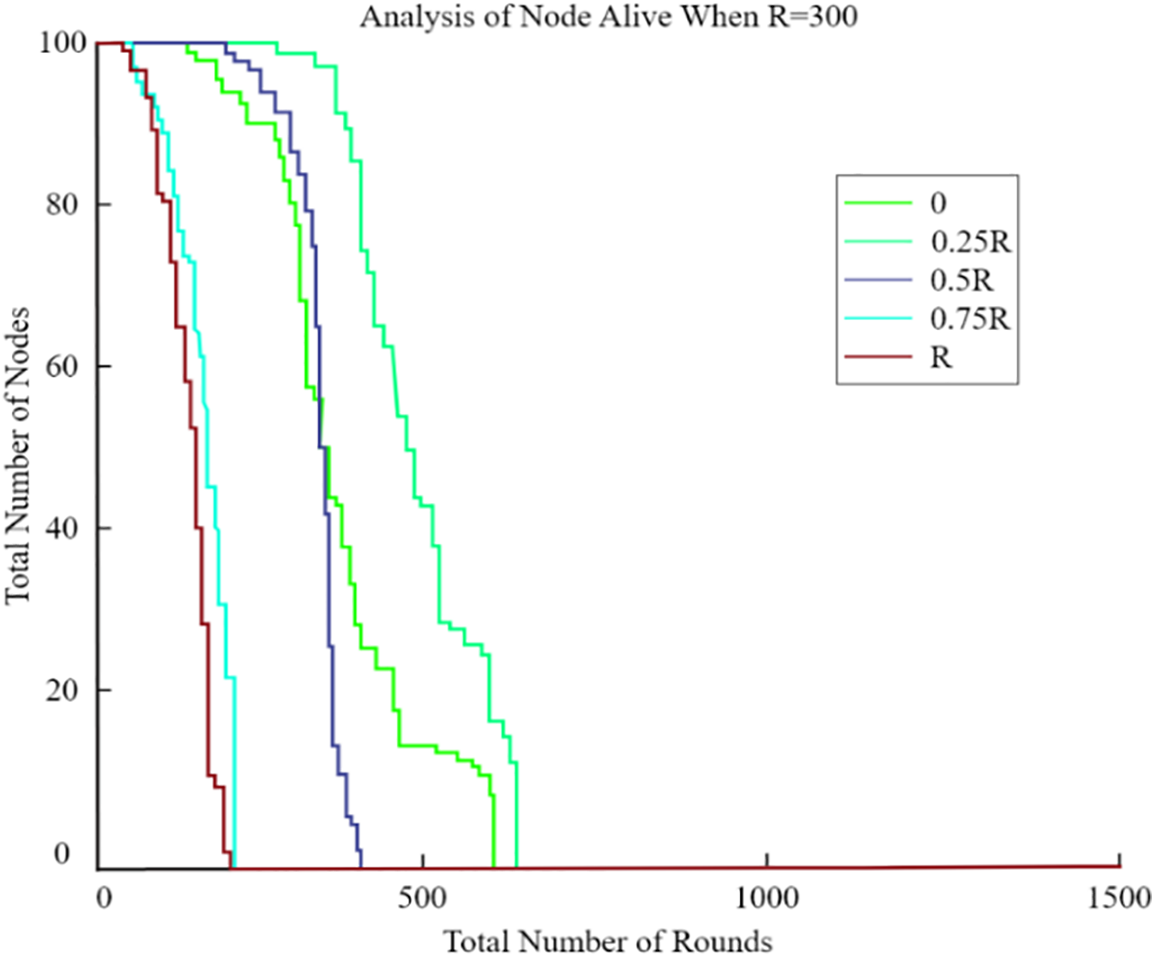
Figure 13: Analysis of nodes alive when R = 300
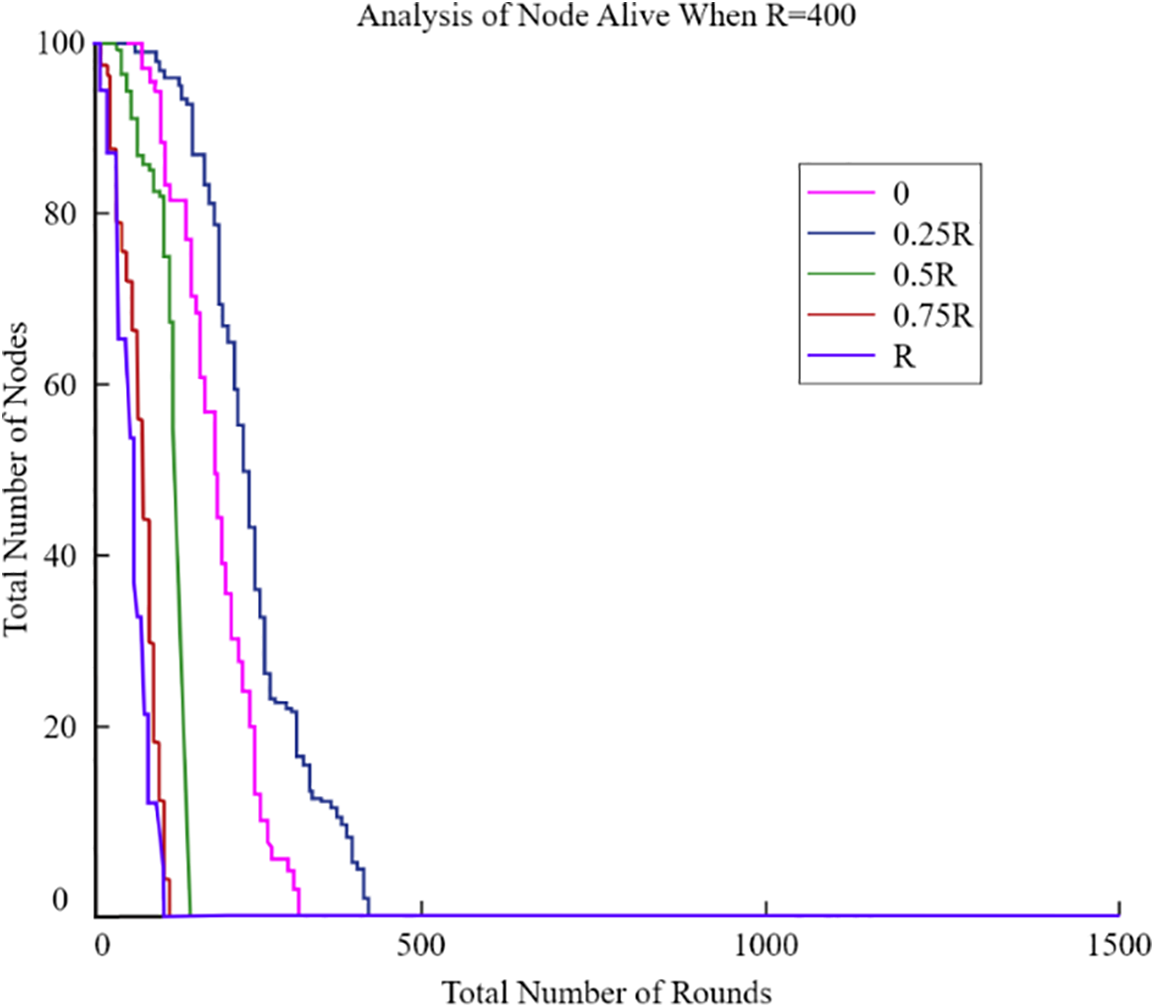
Figure 14: Analysis of nodes alive when R = 400
Utilizing sensors that have a large amount of remaining energy is a wise choice for CHs. On the other hand, high-residual-energy nodes often exist at a great distance from the UAV. Therefore, The CHs and UAV would be in constant contact over a wide area, if we merely checked the amount of energy that was still present in the nodes. In order to extend the system’s lifespan, it was important to find a balance between how much energy was left and how far away the CHs were from the UAV. Before calculating the weight of each node, we first set the UAV’s radius to 0.25 R. Then, we utilize Eqs. (7)–(9). Fig. 15 shows simulation results that demonstrate the practicality of determining node weights using Eq. (9). Research suggests that defining the network lifespan can be based on the time of the first node’s failure. However, using Eq. (6) may accelerate node failure due to its strong dependence on distance in weight calculation. Given that each node initially had less than 1 J of energy, we chose to compute weights using Eq. (7) to highlight the significance of residual energy. It was thought that each node’s energy at the start was less than 1 J. The results of the simulation show that it worked better in terms of how long it took for the first node to die.
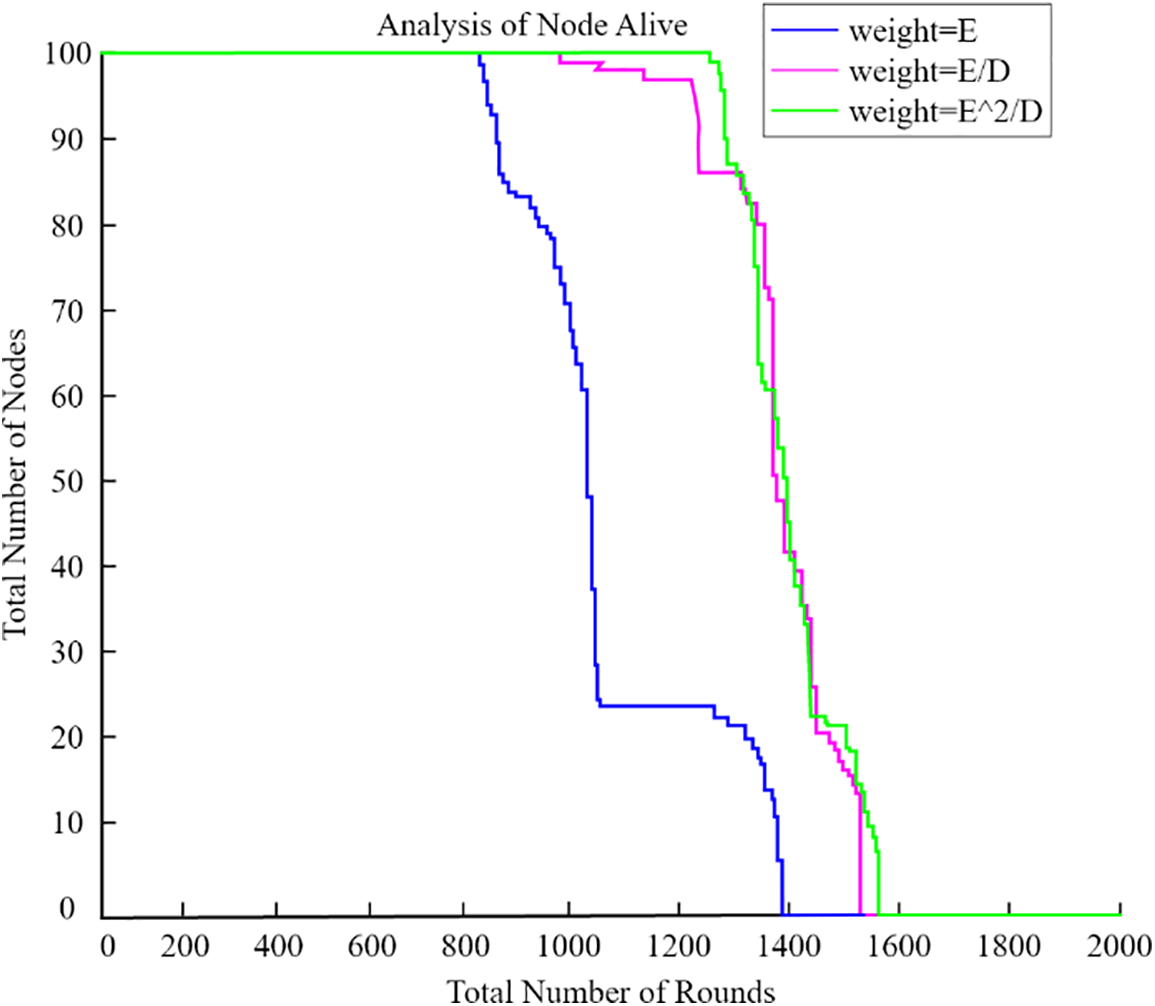
Figure 15: Weight evaluation
Another important network factor was the total number of clusters. Too few CHs may result in communication across significant distances between cluster members and CHs. During intra-cluster communication, though, too many CHs led to chains that were too big. The forwarding of data packets will waste a huge quantity of energy, and network latency will dramatically rise. Fig. 16 shows simulation results for a UAV with a radius of 0.25 R, for which we used a variety of cluster counts in our model. When cluster size was 5, the network worked better, notably in terms of the period when the first node died.
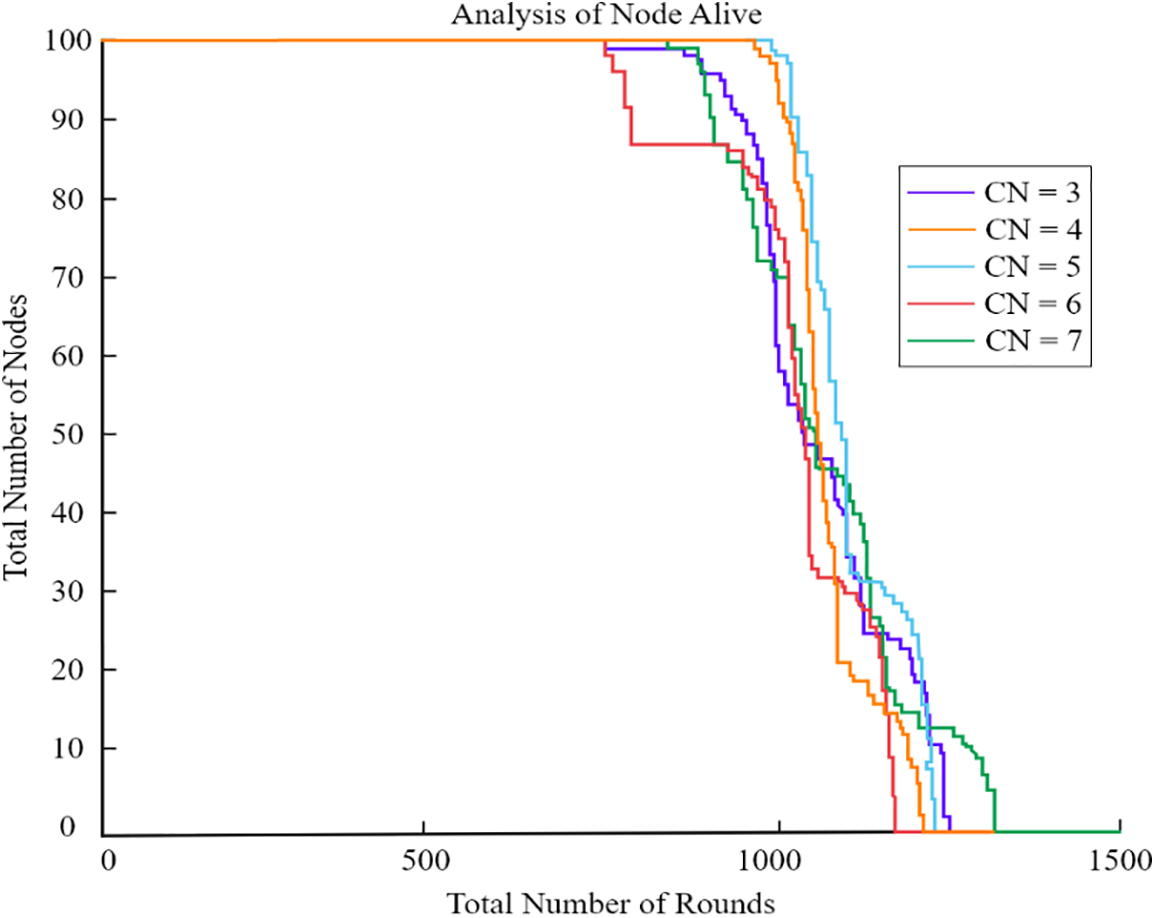
Figure 16: Different cluster evaluation
We conducted multiple tests to determine the maximum speed of the UAV. Adjustments to the UAV’s speed were made possible by vehicles such as the intelligent automobile during its transport. Therefore, we set the UAV’s angular velocities to −20, −10, and −5, while maintaining a radius of 0.25 R. The simulation results are depicted in previous graphs. Despite potential increases in UAV speed, the network’s lifetime showed minimal improvement, as evidenced in Fig. 17. Consequently, we conclude that the UAV’s speed has a negligible impact on network longevity; it should therefore be neither excessively fast nor overly slow.
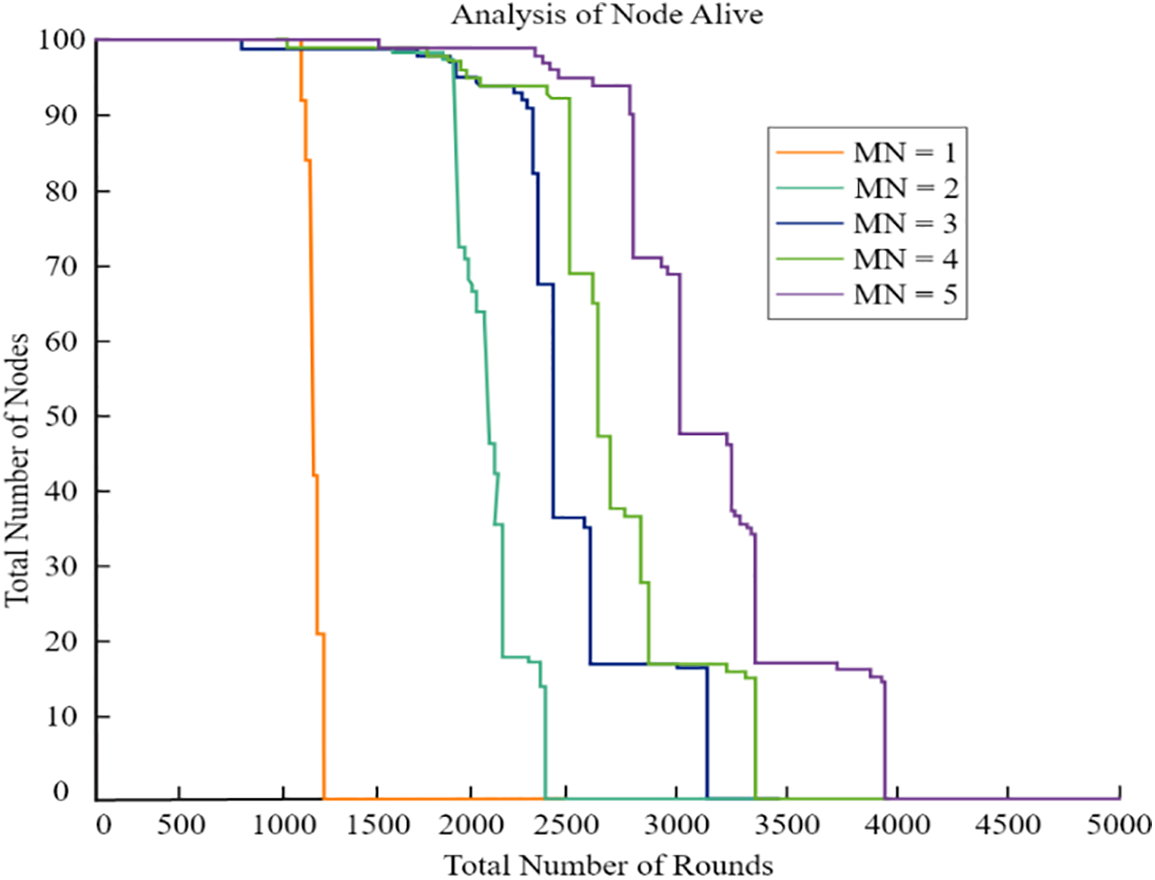
Figure 17: Speed analysis of UAV
We also analyzed how different UAVs will affect the longevity of the network. Each UAV’s range of motion was limited to 0.25 R. As shown in Fig. 18, simulation findings showed that network lifespan rose as the number of UAVs grew. We have also discovered that when the quantity of unmanned aerial vehicles (UAVs) grows, the improvement in their lifetime drops. Since UAVs are more costly than conventional sensors, three UAVs are suggested as the most cost-effective option.
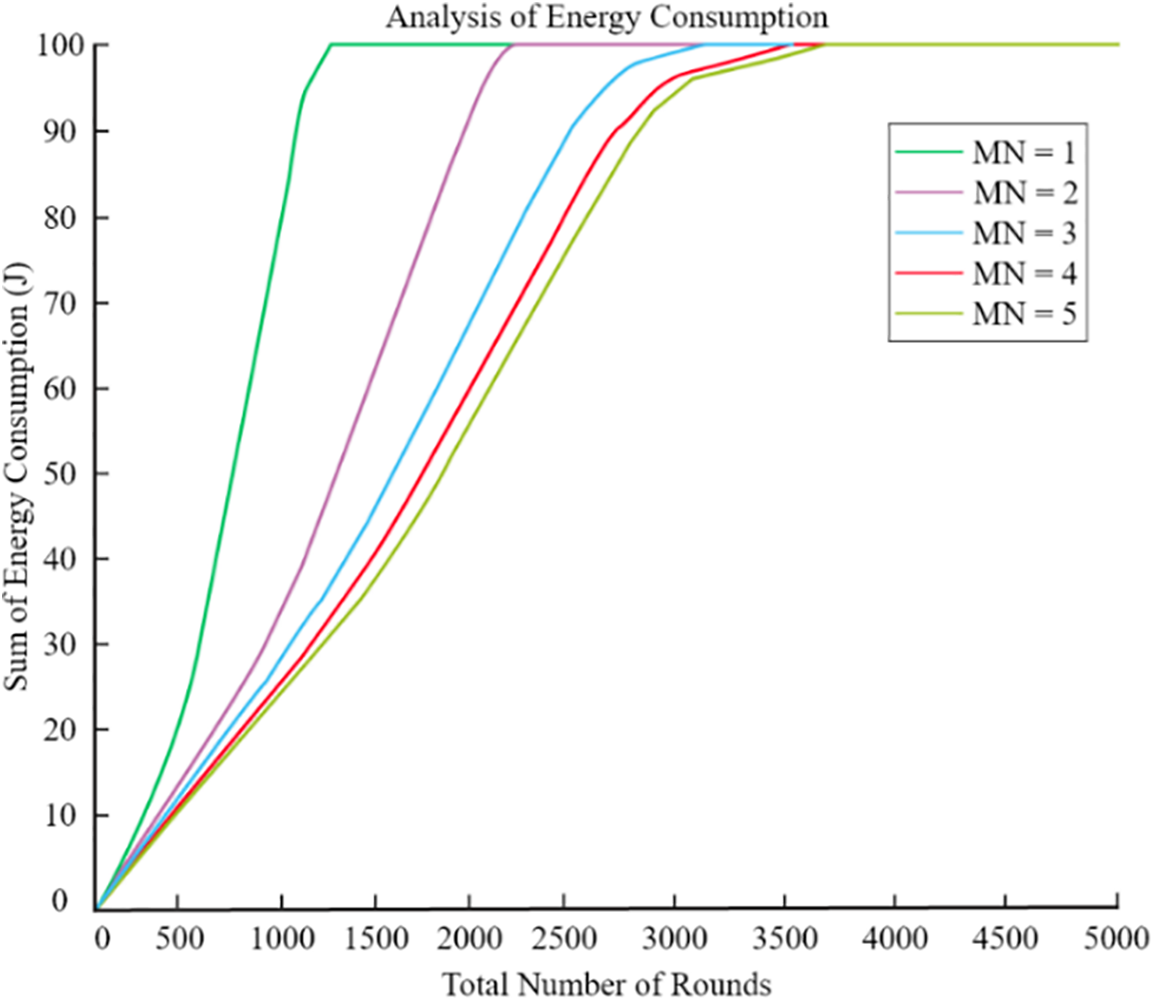
Figure 18: Various UAV nodes
At a distance of 0.25 R, we analyse the power needs of a variety of UAVs. As seen in Fig. 19, the network’s overall energy usage reduced as the number of UAVs rose. When the number of unmanned aerial vehicles (UAVs) approached three, there was no noticeable change in the network’s overall performance.
Figure 19: Energy utilization by different UAV
To verify the effect of multiple parameters on the performance of the proposed algorithm, we conducted additional experiments where we varied key parameters simultaneously. Table 2 lists the parameters and their respective ranges used in the experiments.
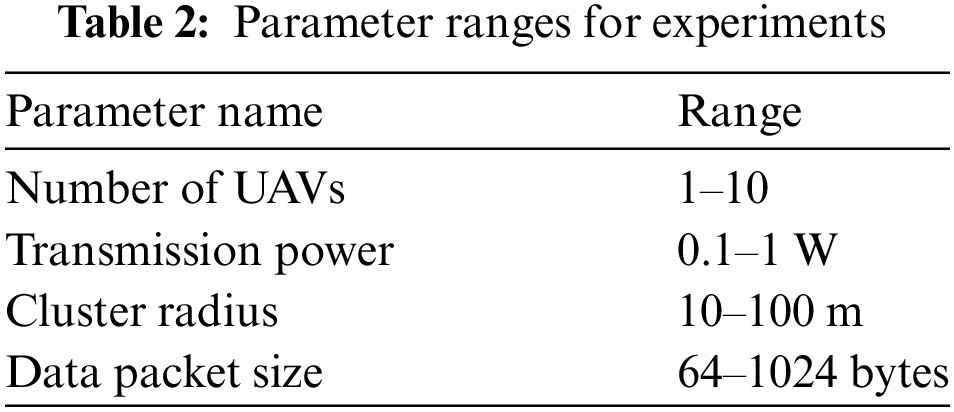
Figs. 18 and 19 illustrate the combined effect of varying the number of UAVs, transmission power, cluster radius, and data packet size on the network performance. Our analysis shows that; Increasing the number of UAVs and optimizing transmission power significantly improves network lifetime and reduces energy consumption. Adjusting the cluster radius and data packet size also plays a crucial role in balancing the network load and enhancing packet delivery ratio.
The task of finding the best path for a sink as it moves is known to be NP-hard. The routing methods also have a direct impact on the sink mobility issue. For this reason, one of the most pressing concerns in the field is how to improve mobile sink approaches and routing algorithms in tandem. Each application must thoroughly define its routing strategy, cluster head selection, sink placement, speed, movement pattern, and resting positions, along with selecting appropriate routing techniques. Security remains a critical and challenging aspect in WSNs, exacerbated by resource constraints and deployment limitations [42]. Risks such as data tampering and malicious attacks pose substantial threats to network security and can escalate energy consumption during data transmission between source and destination nodes. The mobility of sinks and selective forwarding further complicates matters, potentially resulting in data loss or alteration during transmission in WSNs employing sink mobility technology. As a result, more study is required to fully appreciate the significance of data transmission security in the ever-changing context of sensor networks. There is a good chance that store and forward security will come in handy here. Many location-based applications might benefit from using data obfuscation techniques to protect user privacy and stop damage from a hacked location. As a result of the accuracy loss induced by data obfuscation technology, many data information places might have a fuzzy appearance. However, further investigation is required to confirm the efficacy of this technique. For example, in [42], two main components are suggested: one for managing a mobile sink node and another for establishing pairwise keys between sensor nodes, creating a three-tier security architecture. In sensor networks, this technique may thwart attacks in which replicas of access nodes are placed in fixed positions. It has been shown that NP-hard issues may be researched in order to get a deeper comprehension of the characteristics and boundaries of these problems. Not only is this valid for the dynamic mobility of UAVs, but it also applies to routing methods. It is significant to emphasize that the simultaneous optimization of these two aspects is one of the most pressing concerns in research. In addition to a valid moving trajectory, the number of UAVS deployed and the number of cluster heads chosen, different mobile positioning applications need the selection of various routing methods.
Regarding wireless sensor networks, security is always a challenging topic. The difficulty lies in the fact that limited resources and a deployment environment make it challenging to develop solid security techniques. In addition, potential threats such as data modification and malicious attacks have serious implications for network security, hence increasing the energy needed for data transmission. When connectivity between source and destination nodes is disrupted or lost due to the UAV’s movement, the use of UAV mobility technology in WSNs exposes a range of data types. This implies that security in dynamic sensor networks requires more investigation, and store-forwarding may be the solution. Frequently, location-based applications utilize data obfuscation to safeguard location privacy. These programs conceal the locations of multiple data points and reduce their precision, thereby reducing the user’s risk of exposure. However, the safety of this sort of technology has not yet been thoroughly investigated. For instance, a general three-tier security framework utilizing two distinct key pools has been proposed to ensure that a UAV node and pairwise keys between sensor nodes cannot be utilized to replicate stationary access node attacks on sensor networks.
However, we did find a common occurrence in which the energy distribution among clusters was uneven, despite the fact that our proposed technique and algorithm both had high lifetime performance. As seen in Fig. 20, some clusters had no live nodes, whereas other clusters had living nodes. The following factors may contribute to a problem:
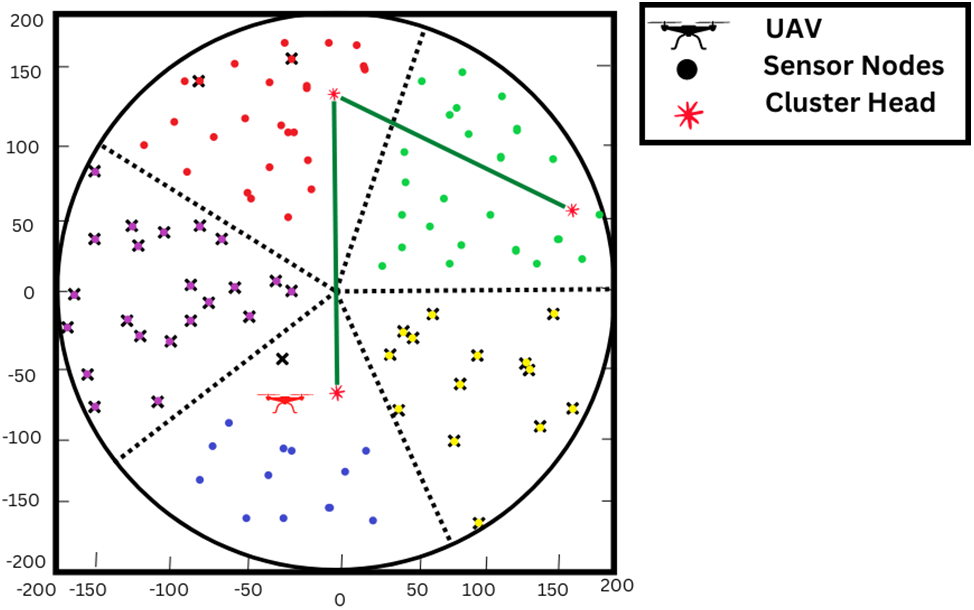
Figure 20: Un-even energy consumption among cluster
• There was no uniformity in the distribution of sensors, and the number of nodes in any given cluster could be different from that in any other.
• In some clusters, the average distance between nodes and the regional center may be larger than in others.
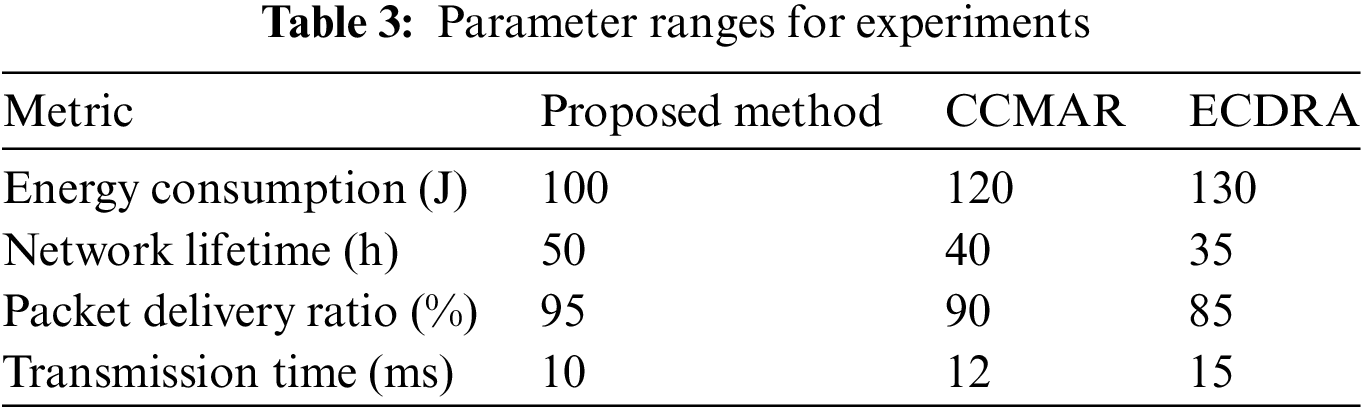
6.1 Comparative Performance Analysis
To present our experimental results clearly, we have summarized the performance metrics of the proposed method compared to other conventional methods such as CCMAR and ECDRA in the following Table 3 and figures.
Using UAVs, we offer an efficient CH selection technique for WSNs. According to early analytic investigation, the suggested method efficiently increases the WSN’s lifespan. In addition, the suggested technique randomly chooses the CH depending on the location of the UAV. We anticipate evaluating the suggested approach in the future using comprehensive simulations and experimental data. In recent years, research has focused a significant amount of effort on technologies that make clustering easier and receiver mobility more flexible. Clustering and the mobility provided by UAVs have proven to be helpful in achieving this objective. In this investigation, upon division the whole of the sensor field into sections of the same size. Following that, we assign a cluster head (CH) to each section based on the weights that are associated with it. Members of each cluster vote on the routing path that will take them to their respective CHs, which may include a single hop of communication or multiple hops. After then, the CH uses a greedy strategy to construct a chain of clusters by communicating with one another across clusters. Through the use of simulation, we compare our innovative routing strategies, such as CCMAR and ECDRA, to our proposed algorithm in terms of the amount of energy they use and the amount of time they last. The simulations not only show that our innovative routing schemas are superior to CCMAR and ECDRA, However, we should also look into how various factors influence a network’s performance. The performance of the design was ultimately improved as a result of these simulations.
Investigating the potential for this field of study requires concentrating on solving the complex problems related to UAV trajectory optimization. In order to increase the effectiveness and efficiency of aerial systems in dynamic sensor networks, it will be essential to prioritize the simultaneous optimization of UAV mobility and routing algorithms. Furthermore, there is much room for investigation regarding the evolution of security measures, particularly in relation to UAV mobility, which calls for creative solutions to strengthen data integrity and communication confidentiality. Prospective directions for additional research also encompass the use of sophisticated methods, like data obfuscation, to protect location privacy in dynamic sensor network settings. The development of the next generation of UAV-enabled systems and the enhancement of their capabilities in diverse applications depend heavily on these research directions.
While our study demonstrates significant improvements in energy efficiency and network performance, several limitations should be noted:
Dataset Biases: The simulations were conducted using synthetic datasets, which may not fully capture the variability and complexity of real-world sensor networks. The synthetic data might not represent all possible environmental conditions and node behaviors that could occur in practical deployments. Potential biases in the dataset could arise from the assumptions made during data generation, such as uniform node distribution and consistent communication patterns. These assumptions might not hold true in all real-world scenarios, leading to different performance outcomes.
Scalability: Although our algorithm shows promising results for networks of a certain size, its scalability to very large-scale networks need further investigation. The computational complexity and communication overhead in much larger networks could affect the algorithm’s efficiency.
Real-World Validation: The proposed algorithm has been validated through simulations. However, real-world implementation and testing are essential to confirm its practical applicability and robustness. Factors such as hardware limitations, environmental interference, and dynamic network conditions could impact performance.
Field experiments are necessary to evaluate the algorithm under various real-world conditions, such as urban environments with high interference or remote areas with limited connectivity.
Energy Model Assumptions: The energy consumption model used in our simulations is based on certain assumptions about the hardware and energy usage patterns. Real sensor nodes might exhibit different energy characteristics, and the model may need adjustments to accurately reflect actual energy consumption.
Future Work
To address these limitations, future research will focus on:
• Dataset Expansion: Utilizing real-world datasets from diverse environments to validate the algorithm’s performance across different scenarios.
• Scalability Testing: Conducting experiments on larger networks to evaluate the algorithm’s scalability and identify potential bottlenecks.
• Field Trials: Implementing the algorithm in real-world sensor networks to test its robustness and adaptability to various conditions.
• Energy Model Refinement: Refining the energy consumption model to better match the characteristics of real sensor nodes and incorporating more sophisticated energy management strategies.
Acknowledgement: We gratefully acknowledge all the individuals for their valuable contributions to this research.
Funding Statement: This research was supported in part by Basic Science Research Program through the National Research Foundation of Korea (NRF) funded by the Ministry of Education (NRF-2021R1A6A1A03039493) and in part by the NRF Grant funded by the Korea government (MSIT) (NRF-2022R1A2C1004401).
Author Contributions: Syed Kamran Haider wrote the original manuscript and did all the simulations solely. Syed Kamran Haider and Nauman Mujeeb Khan revised the manuscript in several meetings and refined the manuscript. Ali Nauman and Sung Won Kim have supervised this research work. Whereas, Abbas Ahmed and Ali Nauman have reviewed the manuscript and helped in improving the paper quality. All authors reviewed the results and approved the final version of the manuscript.
Availability of Data and Materials: Not applicable.
Ethics Approval: Not applicable.
Conflicts of Interest: The authors declare that they have no conflicts of interest to report regarding the present study.
References
1. M. Nabati, M. Maadani, and M. A. Pourmina, “AGEN-AODV: An intelligent energy-aware routing protocol for heterogeneous mobile ad-hoc networks,” Mob. Netw. Appl., vol. 27, no. 2, pp. 576–587, 2022. doi: 10.1007/s11036-021-01821-6. [Google Scholar] [CrossRef]
2. M. Samir, S. Sharafeddine, C. M. Assi, T. M. Nguyen, and A. Ghrayeb, “UAV trajectory planning for data collection from time-constrained IoT devices,” IEEE Trans. Wirel. Commun., vol. 32, no. 1, pp. 34–46, 2024. [Google Scholar]
3. R. Dogra, S. Rani, H. Babbar, and D. Krah, “Energy-efficient routing protocol for next-generation application in the Internet of Things and wireless sensor networks,” Wirel. Commun. Mob. Comput., vol. 2022, no. 1, pp. 1–10, 2022. doi: 10.1155/2022/8006751. [Google Scholar] [CrossRef]
4. M. A. Jamshed, K. Ali, Q. H. Abbasi, M. A. Imran, and M. Ur-Rehman, “Challenges, applications, and future of wireless sensors in Internet of Things: A review,” IEEE Sens. J., vol. 22, no. 6, pp. 5482–5494, 2022. doi: 10.1109/JSEN.2022.3148128. [Google Scholar] [CrossRef]
5. T. Rault, A. Bouabdallah, and Y. Challal, “Energy efficiency in wireless sensor networks: A top-down survey,” Comput. Netw., vol. 67, no. 1, pp. 104–122, 2014. doi: 10.1016/j.comnet.2014.03.027. [Google Scholar] [CrossRef]
6. J. Wang, Y. Gao, W. Liu, A. K. Sangaiah, and H. -J. Kim, “Energy efficient routing algorithm with mobile sink support for wireless sensor networks,” Sensors, vol. 19, no. 7, pp. 1494, 2019. doi: 10.3390/s19071494. [Google Scholar] [PubMed] [CrossRef]
7. S. Poudel and S. Moh, “Medium access control protocols for unmanned aerial vehicle-aided wireless sensor networks: A survey,” IEEE Access, vol. 7, no. 7, pp. 65728–65744, 2019. doi: 10.1109/ACCESS.2019.2917948. [Google Scholar] [CrossRef]
8. A. Ranjha and G. Kaddoum, “URLLC facilitated by mobile UAV relay and RIS: A joint design of passive beamforming, block length, and UAV positioning,” IEEE Internet Things J., vol. 8, no. 6, pp. 4618–4627, 2020. [Google Scholar]
9. S. Kumar, P. R. Gautam, T. Rashid, A. Verma, and A. Kumar, “Division algorithm-based energy-efficient routing in wireless sensor networks,” Wireless Pers. Commun., vol. 122, no. 3, pp. 2335–2354, 2022. [Google Scholar]
10. L. Gupta, R. Jain, and G. Vaszkun, “Survey of important issues in UAV communication networks,” IEEE Commun. Surv. Tutorials, vol. 18, no. 2, pp. 1123–1152, 2016. doi: 10.1109/COMST.2015.2495297. [Google Scholar] [CrossRef]
11. S. K. Haider, M. A. Jamshed, A. Jiang, and H. Pervaiz, “An energy efficient cluster-heads re-usability mechanism for wireless sensor networks,” in 2019 IEEE Int. Conf. Commun. Workshops (ICC Workshops), Shanghai, China, 2019, pp. 1–6. [Google Scholar]
12. P. A. Neves and J. J. P. C. Rodrigues, “Internet protocol over wireless sensor networks, from myth to reality,” J. Commun., vol. 5, pp. 189–196, 2010. doi: 10.4304/jcm.5.3.189-196. [Google Scholar] [CrossRef]
13. A. Razaque, M. Abdulgader, C. Joshi, F. Amsaad, and M. Chauhan, “P-LEACH: Energy efficient routing protocol for Wireless Sensor Networks,” in Proc. 2016 IEEE Long Island Syst., Appl. Technol. Conf. (LISAT), Farmingdale, NY, USA, 2016, pp. 1–5. [Google Scholar]
14. M. A. Jamshed, F. Héliot, and T. W. C. Brown, “A survey on electromagnetic risk assessment and evaluation mechanism for future wireless communication systems,” IEEE J. Electromagn., RF Microw. Med. Biol., vol. 4, no. 1, pp. 24–36, 2020. doi: 10.1109/JERM.2019.2917766. [Google Scholar] [CrossRef]
15. S. K. Haider, M. A. Jamshed, A. Jiang, H. Pervaiz, and Q. Ni, “UAV-assisted cluster-head selection mechanism for wireless sensor network applications,” in 2019 UK/China Emerg. Technol. (UCET), Glasgow, UK, 2019, pp. 1–2. [Google Scholar]
16. T. Pal, R. Saha, and S. Biswas, “Sink mobility-based energy efficient routing algorithm variants in WSN,” Int. J. Wirel. Inf. Netw., vol. 29, no. 3, pp. 373–392, 2022. doi: 10.1007/s10776-022-00557-8. [Google Scholar] [CrossRef]
17. C. Zhu, S. Wu, G. Han, L. Shu, and H. Wu, “A tree-cluster-based data-gathering algorithm for industrial WSNs with a mobile sink,” IEEE Access, vol. 3, no. 1, pp. 381–396, 2015. doi: 10.1109/ACCESS.2015.2424452. [Google Scholar] [CrossRef]
18. D. Popescu, C. Dragana, F. Stoican, L. Ichim, and G. Stamatescu, “A collaborative UAV-WSN network for monitoring large areas,” Sensors, vol. 18, no. 12, pp. 4202, 2018. doi: 10.3390/s18124202. [Google Scholar] [PubMed] [CrossRef]
19. R. Velmani and B. Kaarthick, “An efficient cluster-tree based data collection scheme for large mobile wireless sensor networks,” IEEE Sens. J., vol. 15, no. 4, pp. 2377–2390, 2015. doi: 10.1109/JSEN.2014.2377200. [Google Scholar] [CrossRef]
20. S. Sasirekha and S. Swamynathan, “Cluster-chain mobile agent routing algorithm for efficient data aggregation in wireless sensor network,” J. Commun. Netw., vol. 19, no. 4, pp. 392–401, 2017. doi: 10.1109/JCN.2017.000063. [Google Scholar] [CrossRef]
21. Z. Wang, R. Liu, Q. Liu, J. S. Thompson, and M. Kadoch, “Energy-efficient data collection and device positioning in UAV-assisted IoT,” IEEE Internet Things J., vol. 11, no. 2, pp. 1122–1139, 2024. [Google Scholar]
22. R. Ramya and T. Brindha, “A comprehensive review on optimal cluster head selection in WSN-IoT,” Adv. Eng. Softw., vol. 171, no. 1, pp. 103170, 2022. doi: 10.1016/j.advengsoft.2022.103170. [Google Scholar] [CrossRef]
23. D. Ebrahimi, S. Sharafeddine, P. -H. Ho, and C. Assi, “UAV-aided projection-based compressive data gathering in wireless sensor networks,” IEEE Internet Things J., vol. 6, no. 2, pp. 1893–1905, 2019. doi: 10.1109/JIOT.2018.2878834. [Google Scholar] [CrossRef]
24. M. A. Jamshed, W. U. Khan, H. Pervaiz, M. A. Imran, and M. Ur-Rehman, “Emission-aware resource optimization framework for backscatter-enabled uplink NOMA networks,” in 2022 IEEE 95th Veh. Technol. Conf. (VTC2022-Spring), Helsinki, Finland, 2022, pp. 1–5. [Google Scholar]
25. M. C. M. Thein and T. Thein, “An energy efficient cluster-head selection for wireless sensor networks,” in Proc. 2010 Int. Conf. Intell. Syst., Modell. Simul., Liverpool, UK, 2010, pp. 287–291. [Google Scholar]
26. W. Zhou, “Energy efficient clustering algorithm based on neighbors for wireless sensor networks,” (in Chinese), J. Shanghai Univ., vol. 15, no. 2, pp. 150–153. 2011. doi: 10.1007/s11741-011-0712-1. [Google Scholar] [CrossRef]
27. H. M. Abdulsalam and L. K. Kamel, “W-LEACH: Weighted low energy adaptive clustering hierarchy aggregation algorithm for data streams in wireless sensor networks,” in IEEE Int. Conf. Data Min. Workshops, Sydney, NSW, Australia, 2010, pp. 1–8. [Google Scholar]
28. J. Baek, S. I. Han, and Y. Han, “Energy-efficient UAV routing for wireless sensor networks,” IEEE Trans. Veh. Technol., vol. 69, no. 2, pp. 1741–1750, 2019. doi: 10.1109/TVT.2019.2959808. [Google Scholar] [CrossRef]
29. T. Kim and D. Qiao, “Energy-efficient data collection for IoT networks via cooperative multi-hop UAV networks,” IEEE Trans. Vehicular Technol., vol. 69, no. 11, pp. 13796–13811, 2020. doi: 10.1109/TVT.2020.3027920. [Google Scholar] [CrossRef]
30. Z. Ullah, F. Al-Turjman, and L. Mostarda, “Cognition in UAV-Aided 5G and beyond communications: A survey,” IEEE Trans. Cogn. Commun. Netw., vol. 6, no. 3, pp. 872–891, 2020. doi: 10.1109/TCCN.2020.2968311. [Google Scholar] [CrossRef]
31. J. Gu, T. Su, Q. Wang, X. Du, and M. Guizani, “Multiple moving targets surveillance based on a cooperative network for multi-UAV,” IEEE Commun. Mag., vol. 62, no. 4, pp. 82–89, 2024. [Google Scholar]
32. Z. Ding, L. Shen, H. Chen, F. Yan, and N. Ansari, “Energy-efficient relay-selection-based dynamic routing algorithm for IoT-oriented software-defined WSNs,” IEEE Internet Things J., vol. 7, no. 9, pp. 9050–9065, 2020. doi: 10.1109/JIOT.2020.3002233. [Google Scholar] [CrossRef]
33. Z. Liu, Y. Cao, P. Gao, X. Hua, D. Zhang and T. Jiang, “Multi-UAV network assisted intelligent edge computing: Challenges and opportunities,” China Commun., vol. 31, no. 3, pp. 258–278, 2024. [Google Scholar]
34. B. Zhu, E. Bedeer, H. H. Nguyen, R. Barton, and J. Henry, “Joint cluster head selection and trajectory planning in UAV-aided IoT networks by reinforcement learning with sequential model,” IEEE Internet Things J., vol. 12, no. 14, pp. 12071–12084, 2024. [Google Scholar]
35. M. M. Azari, F. Rosas, and S. Pollin, “Cellular connectivity for UAVs: Network modeling, performance analysis, and design guidelines,” IEEE Trans. Wirel. Commun., vol. 18, no. 7, pp. 3366–3381, 2019. doi: 10.1109/TWC.2019.2910112. [Google Scholar] [CrossRef]
36. P. Chithaluru, S. Kumar, A. Singh, A. Benslimane, and S. K. Jangir, “An energy-efficient routing scheduling based on fuzzy ranking scheme for Internet of Things,” IEEE Internet Things J., vol. 9, no. 10, pp. 7251–7260, 2022. doi: 10.1109/JIOT.2021.3098430. [Google Scholar] [CrossRef]
37. S. Sotheara, I. Hikari, L. Jiang, and S. Shimamoto, “Priority-based data gathering framework in UAV-assisted wireless sensor networks,” IEEE Sens. J., vol. 16, no. 14, pp. 5785–5794, 2016. doi: 10.1109/JSEN.2016.2568260. [Google Scholar] [CrossRef]
38. G. Arya, A. Bagwari, and D. S. Chauhan, “Performance analysis of deep learning-based routing protocol for an efficient data transmission in 5G WSN communication,” IEEE Access, vol. 10, no. 1, pp. 9340–9356, 2022. doi: 10.1109/ACCESS.2022.3142082. [Google Scholar] [CrossRef]
39. M. Mir, M. Yaghoobi, and M. Khairabad, “A new approach to energy-aware routing in the Internet of Things using improved grasshopper metaheuristic algorithm with Chaos theory and fuzzy logic,” Multimed. Tools Appl., vol. 82, no. 4, pp. 5133–5159, 2023. doi: 10.1007/s11042-021-11841-9. [Google Scholar] [CrossRef]
40. S. Verma and N. S. Mitra, “An efficient routing approach to improve the performance of IoT node for 5G communication applications,” Int. J. Innov. Res. Sci., Eng. Technol. (IJIRSET), vol. 11, no. 4, pp. 3746–3750, 2022. [Google Scholar]
41. S. K. Haider et al., “Energy efficient UAV flight path model for cluster head selection in next-generation wireless sensor networks,” Sensors, vol. 21, no. 24, pp. 1424–1436, 2021. doi: 10.3390/s21248445. [Google Scholar] [PubMed] [CrossRef]
42. S. K. Haider, A. Nauman, M. A. Jamshed, A. Jiang, S. Batool and S. W. Kim, “Internet of drones: Routing algorithms, techniques and challenges,” Mathematics, vol. 10, no. 9, pp. 1488–1510, 2022. doi: 10.3390/math10091488. [Google Scholar] [CrossRef]
Cite This Article
 Copyright © 2024 The Author(s). Published by Tech Science Press.
Copyright © 2024 The Author(s). Published by Tech Science Press.This work is licensed under a Creative Commons Attribution 4.0 International License , which permits unrestricted use, distribution, and reproduction in any medium, provided the original work is properly cited.


 Submit a Paper
Submit a Paper Propose a Special lssue
Propose a Special lssue View Full Text
View Full Text Download PDF
Download PDF Downloads
Downloads
 Citation Tools
Citation Tools