 Open Access
Open Access
ARTICLE
Internet of Things Enabled DDoS Attack Detection Using Pigeon Inspired Optimization Algorithm with Deep Learning Approach
Department of Computer Science and Artificial Intelligence, College of Computing, Umm Al-Qura University, Makkah, 21955, Saudi Arabia
* Corresponding Author: Saud S. Alotaibi. Email:
Computers, Materials & Continua 2024, 80(3), 4047-4064. https://doi.org/10.32604/cmc.2024.052796
Received 15 April 2024; Accepted 11 July 2024; Issue published 12 September 2024
Abstract
Internet of Things (IoTs) provides better solutions in various fields, namely healthcare, smart transportation, home, etc. Recognizing Denial of Service (DoS) outbreaks in IoT platforms is significant in certifying the accessibility and integrity of IoT systems. Deep learning (DL) models outperform in detecting complex, non-linear relationships, allowing them to effectually severe slight deviations from normal IoT activities that may designate a DoS outbreak. The uninterrupted observation and real-time detection actions of DL participate in accurate and rapid detection, permitting proactive reduction events to be executed, hence securing the IoT network’s safety and functionality. Subsequently, this study presents pigeon-inspired optimization with a DL-based attack detection and classification (PIODL-ADC) approach in an IoT environment. The PIODL-ADC approach implements a hyperparameter-tuned DL method for Distributed Denial-of-Service (DDoS) attack detection in an IoT platform. Initially, the PIODL-ADC model utilizes Z-score normalization to scale input data into a uniform format. For handling the convolutional and adaptive behaviors of IoT, the PIODL-ADC model employs the pigeon-inspired optimization (PIO) method for feature selection to detect the related features, considerably enhancing the recognition’s accuracy. Also, the Elman Recurrent Neural Network (ERNN) model is utilized to recognize and classify DDoS attacks. Moreover, reptile search algorithm (RSA) based hyperparameter tuning is employed to improve the precision and robustness of the ERNN method. A series of investigational validations is made to ensure the accomplishment of the PIODL-ADC method. The experimental outcome exhibited that the PIODL-ADC method shows greater accomplishment when related to existing models, with a maximum accuracy of 99.81%.Keywords
Numerous IoT devices linked to the system promptly rise, so network attacks like DoS and flooding grow simultaneously [1]. These assaults cause system disruption and DoS to IoT systems. IoT safety is an intriguing and challenging subject requiring advanced measures to prevent numerous attacks [2]. Due to the significant heterogeneity of IoT, preserving even communication values through manifold systems is problematic. Developing many solutions for each device is a complex process. As an outcome, an intelligent system must adjust to numerous gadgets while professionally defending them from safety threats [3]. Distributed DDoS assaults are chief threats to the system, affecting users and gadgets based on them. DDoS assaults contain manifold plans besides one target, preventing genuine consumers from accessing services like websites and email [4]. They signify the most common and dangerous attack beside and from IoT networks, 5th generation (5G) communication systems, and Cloud Computing (CC).
DDoS attacks are classified into dual chief classes such as high- and low-rate attacks which afford to the dimension of traffic they create [5]. The low-rate attack behavior is really modest because they perform likewise to genuine traffic and account for nearly 10–20 percent of total usual network traffic. If regular traffic of low-rate assaults is small, they theoretically decrease the service quality of the target and stop the service completely [6]. However, many heterogeneous devices organized in an IoT environment make it complex to identify IoT attacks by employing customary rule-based safety solutions. It is a highly challenging task to improve optimum safety techniques for every kind of device [7]. Machine learning (ML) is a substitute method that permits one to improve optimum safety techniques depending on experimental data from every device. DL has a lot of achievements in numerous uses, such as face detection, image processing, and natural language translation [8].
DL can able to extract raw features from data without the need for human participation. It attains a higher performance rate by mechanically identifying associations in raw data [9]. As an outcome of DL-based techniques, the accuracy of classifying attacks has enlarged even more [10]. In addition, temporary network traffic connections frequently offer consecutive data and efficiently train DL techniques with successive traffic, leading to data loss [11]. Some methods related to enlarged cybersecurity include integrating ML models to recognize DDoS assaults over IoT gadgets [12]. ML or DL techniques are crucial for analyzing numerous datasets, mainly IoT, to improve the capability to identify cyberattacks [13]. The restricted resources, like the limited computational capability linked to IoT devices, pose many limitations, so other methodologies should be applied to tackle these limits frequently when needed [14].
This manuscript offers the design of pigeon-inspired pigeon-inspired optimization with DL-based attack detection and classification (PIODL-ADC) technique on an IoT platform. The PIODL-ADC system employs a hyperparameter-tuned DL model for DDoS attack recognition in the IoT atmosphere. Primarily, the PIODL-ADC technique employs Z-score normalization to scale input data into a uniform format. For the feature selection process, the PIODL-ADC technique uses the PIO algorithm. Meanwhile, the Elman Recurrent Neural Network (ERNN) model was applied to detect and identify DDoS attacks. Furthermore, Reptile Search Algorithm (RSA) based hyperparameter tuning is exploited for optimal hyperparameter selection of the ERNN model. A series of experimental analyses are made to ensure the performance of the PIODL-ADC technique.
In [15], the authors developed an exclusive technique for safeguarding IoT systems using an SDN (Software Defined Network)-enabled structure that integrates an active counter-based technique and DL methods. The main goal is to identify and moderate numerous safety vulnerabilities that attackers use to create DDoS attacks in IoT systems. A developed framework was verified by employing the CICDDoS2019 dataset for detecting exploitation and reflection attacks in User Datagram Protocol (UDP), Transmission Control Protocol (TCP), and Internet Control Message Protocol (ICMP). In [16], a new attack recognition technique was developed. Initially, input data pre-processed from the most applicable features are removed. The removed raw landscapes openly assumed long short-term memory (LSTM), and mined higher-order arithmetical features exposed to deep reinforcement learning (DRL) to detect. Next, the average of LSTM and DRL offers identified output in an actual way. The load of LSTM is enhanced by the self-improved battle royale optimization (SIBRO) technique.
Ortet Lopes et al. [17] developed CyDDoS, a combined Intrusion Detection Systems (IDS) structure integrating feature engineering techniques with Deep Neural Networks (DNNs). The ensemble Feature Selection (FS) depends on 5 ML classifiers employed to detect and remove the most relevant features utilized by the analytical method. In [18], a Low-Rate Denial of Service (LDDoS) attack recognition technique has been proposed depending on the DL model that contains an initiation purpose of LSTM by analyzing specific values of dissimilar LDDoS assaults and usual traffic. Ahmim et al. [19] developed a new DL-based IDS consisting of two stages. This hybrid technique integrates DL techniques such as Convolutional Neural Networks (CNNs), Deep Autoencoder, LSTM, and DNN. The primary stage has dissimilar parallel sub-neural systems trained by exact methods. The second stage employs the output of the frozen first stage joined by early data as input.
Sagu et al. [20] developed a hybrid technique for recognizing attacks in an IoT atmosphere with three levels. Primarily, higher-order arithmetical features are removed. Then, recognition takes place by employing Bidirectional Long Short-Term Memory (BLSTM) and Gated Recurrent Unit (GRU) to identify the presence of network assaults. To enhance classification accuracy, loads of BLSTM are optimally set over a self-upgraded Cat and Mouse Optimizer (SU-CMO) method. Ragab et al. [21] develop a Piecewise Harris Hawks Optimization (PHHO) with an Optimal DL Classifier (PHHO-ODLC) model. This method has a staged procedure. At an early stage, the PHHO technique is used to pick pertinent features and improve classification performance. Then, an attention-based bidirectional LSTM (ABiLSTM) system is used for the DDoS attack detection procedure. Lastly, the ABiLSTM network’s hyperparameter collection is executed using a grey wolf optimizer (GWO).
In [22], an SDN-enabled DL-driven structure has been developed for threat recognition in an IoT atmosphere. The advanced Cuda-DNN, GRU (Cu-DNNGRU), and Cuda-BLSTM (Cu-BLSTM) classification algorithms are approved for actual threat recognition. The offered model also executed ten-fold cross-validation to display the unbiasedness of outcomes. Aljebreen et al. [23] presented DDoS attack detection using a snake optimizer with ensemble learning (DDAD-SOEL) model. This approach incorporated a snake optimizer for the feature subset section and integration of LSTM, ABiLSTM, and deep belief network (DBN) methods. Also, an Adadelta optimizer is employed for the hyperparameter tuning process. Bella et al. [24] introduced a hybrid correlation-based feature selection-bat optimization algorithm (HCFS-BOA) technique and present a CNN method. This model utilized min-max normalization and CNN classification.
In the field of DDoS recognition in IoT platforms, present models mostly need help with the high heterogeneity and dimensionality of data, paving the way to inefficiency in detecting relevant factors that crucially affect the accuracy of the recognition. Conventional feature selection models may need to sufficiently address IoT data streams’ dynamic and convolutional behavior, so further advanced models are required. Metaheuristic techniques are prevalent because of their capacity to navigate substantial search spaces and maximize convolutional issues, improving feature selection outcomes in this background. Moreover, a research gap exists in effectually incorporating these models with hyperparameter tuning procedures to improve the precision and robustness of recognition methods. Present research considers feature selection and hyperparameter tuning separately, leaving out potential effects that may be attained by mutually maximizing both features. Addressing this gap via an overall model that utilizes metaheuristic techniques for feature selection and concurrent hyperparameter tuning may improve DDoS recognition, safeguarding more productive and dependable safety for IoT platforms. Therefore, the PIODL-ADC technique involves the development of PIO-based feature selection and Resident Space Object (RSO)-based hyperparameter tuning.
This manuscript proposes the design of the PIODL-ADC technique in an IoT environment. The technique employs a hyperparameter-tuned DL model for DDoS attack recognition in IoT platforms. Fig. 1 represents the entire flow of the PIODL-ADC methodology.
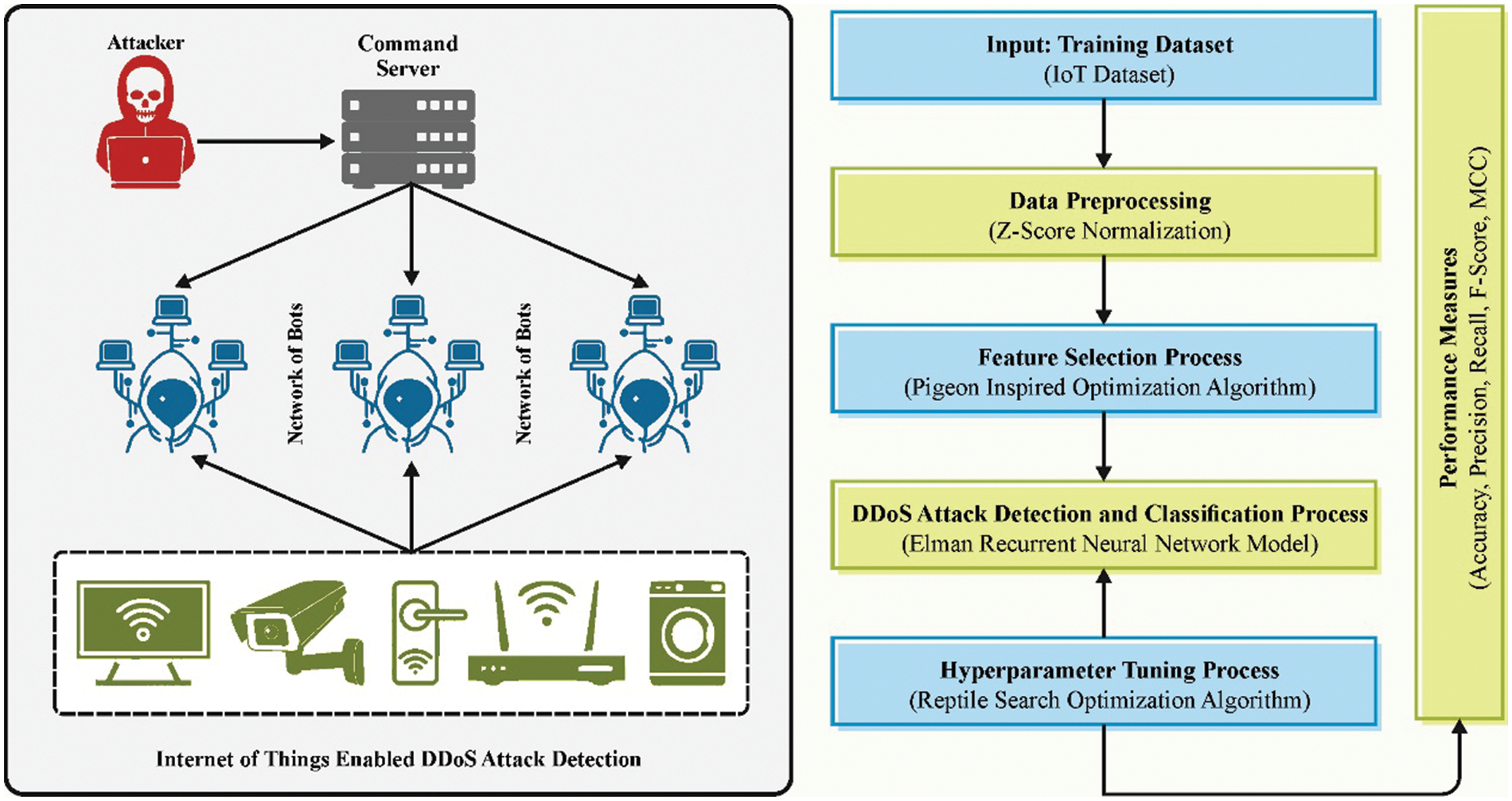
Figure 1: Overall flow of PIODL-ADC technique
Primarily, the PIODL-ADC technique employs a Z-score normalized to scale the input data into a uniform format. Z-score normalized is a serious pre-processing method in DDoS recognition in IoT environments, allowing standardized representation of different sensor data [25]. This model converts raw sensor values by deducting the mean and dividing by the standard deviation resulting in a distribution with a standard deviation of 1 and a mean of 0. Using Z-score normalization, differences in sensor readings are efficiently normalized, permitting reliable comparison and recognition of unusual patterns indicative of DDoS attacks. In IoT settings, where various devices with dissimilar sensing abilities donate to the data stream, Z-score normalization is essential in safeguarding the features employed for DDoS detection are reliably signified, allowing ML techniques to distinguish abnormal network behavior linked with potential attacks efficiently.
For the feature selection process, the PIODL-ADC technique uses the Pigeon-Inspired Optimization (PIO) algorithm. The PIO is a biologically inspired Swarm Intelligence (SI) optimization algorithm based on the behaviors of pigeons’ flocks [26]. Various amendments are introduced to improve the convergence rate by changing the implementation procedure or the tuning parameters. The study presents a predator-prey PIO (PPPIO) for combined controller design and mission planning. Moreover, Bloch quantum-behaved PIO (BQPIO) is a hybrid model that integrates PIO with a quantum model. Also, PIO is employed to find air robot path planning optimization problems and is adapted by incorporating control parameterization and time discretization (CPTD) methods to deal with the issue of Unmanned Aerial Vehicle (UAV) formation.
PIO is prolonged in its applicability to other uses such as control of landing systems, gliding trajectory, and Direct Current (DC) motors control spacecraft. The map and compass operator method entirely depends on the earth’s and sun’s magnetic field, whereby pigeons are used to discover a flock in long travel. For pigeon
In Eq. (1), the map and compass factor is
The landmark operator model is based on landmarks whereby pigeons use learned landmarks to discover their trajectory and fly toward their nest. This operator signifies that the pigeon is still far from its destination and assumes they are unaware of the landmark. This decreases the pigeon number in every new population by half. Consider
The location upgrading rule for pigeon
Fitness
For every individual, the optimum location of

Figure 2: Flowchart of PIO technique
The fitness function (FF) employed in the developed technique is specially designed to balance the number of designated features in every solution (minimum) and classification accuracy (maximum) achieved by utilizing these particular features. Eq. (7) signifies FF to assess solutions.
whereas
3.3 DDoS Attack Detection Model
At this stage, the ERNN model is applied to recognize and identify to recognize and identify DDoS attacks. ERNNs networks with hidden layer (HL) without innovative devices. ERNN is formally described below:
whereas
The parameters of networks enhanced with esteem to mean squared error loss function are mentioned as follows:
3.4 RSA-Based Hyperparameter Tuning
Eventually, the RSA-based hyperparameter tuning is exploited for optimal hyperparameter selection of the ERNN model. Abualigah et al. first developed RSA in 2021, a special kind of natural-inspired optimization technique. It is a gradient-free technique that can cope with complicated challenges subjected to certain constraints.
The initial phase of the algorithm involves selecting a potential solution randomly using Eq. (13):
Now, the overall population with
Crocodile moves within search space via two different strategies: high walking and belly walking. When
where the hunting operator is
The reduced function is
where
In Eq. (19),
The hunting or exploitation stage specifies that crocodiles apply cooperative and coordinated hunting strategies during prey attacks. In the optimization algorithm, this strategy is used to perform a local search and find the potential solution. The coordination hunting is performed according to
The termination condition is met once
The RSA model originates an FF to reach an upgraded classifier solution. It defines a positive integer to signify a better solution for candidate outcomes. In this research, the minimization of the classifier error rate is measured as FF, as assumed in Eq. (21).
This The experimental outcome of the PIODL-ADC technique has been tested using the attack database [27], which comprises 2056 instances and five class labels, as represented in Table 1.

Fig. 3 illustrates the confusion matrices attained by the PIODL-ADC technique under 80:20 and 70:30 of TRPH/TSPH. The results indicate the effectual detection and classification of all four classes.
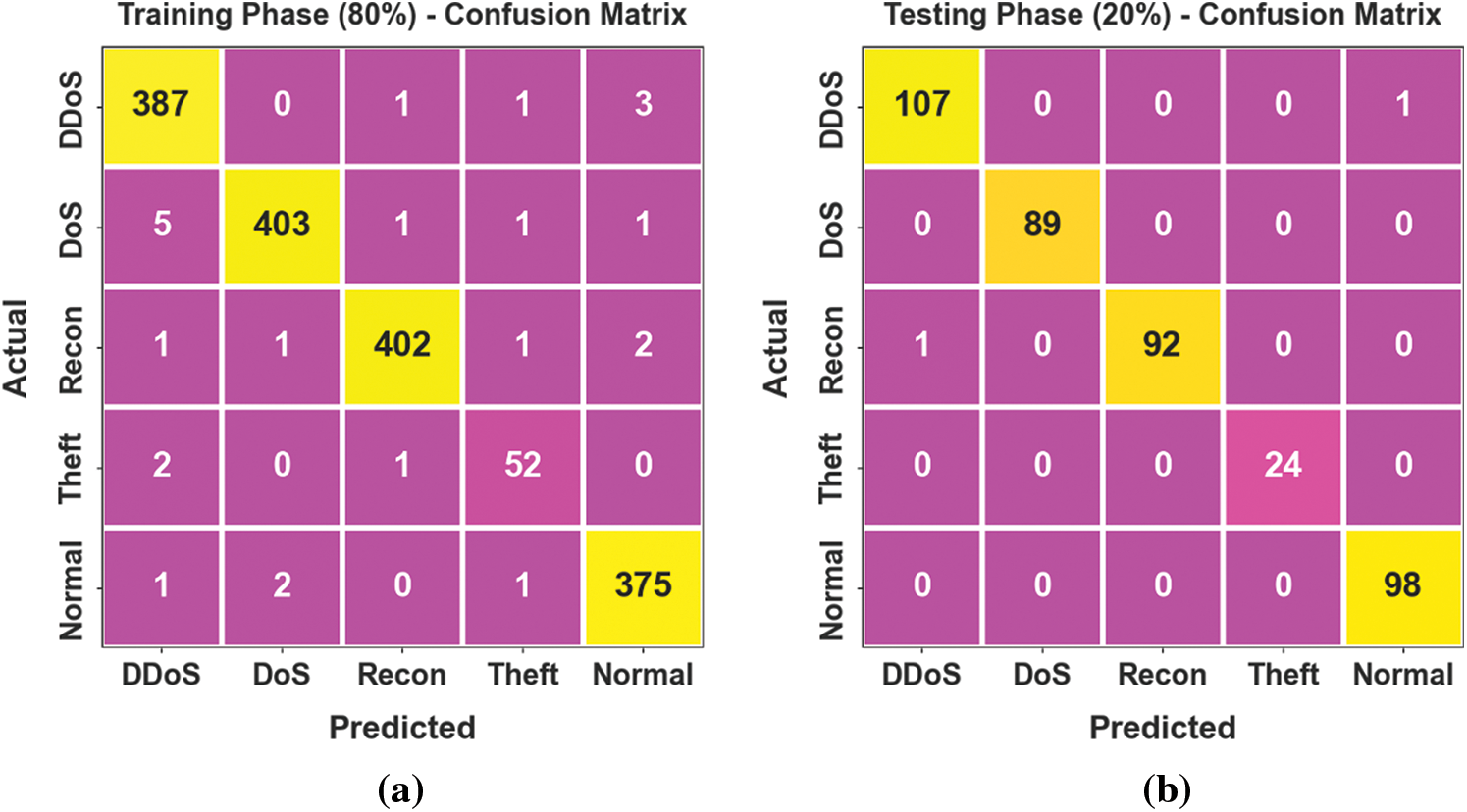
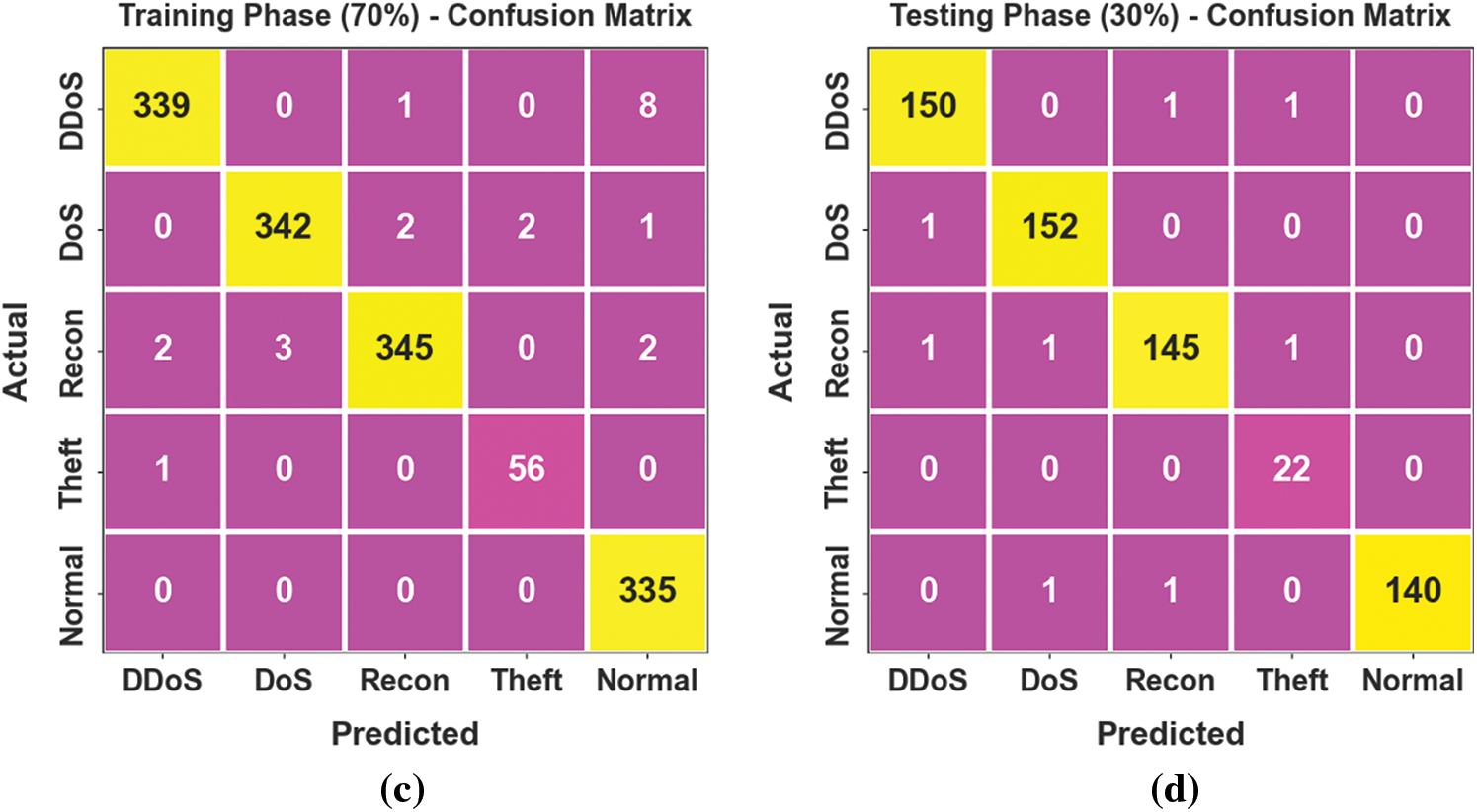
Figure 3: Confusion matrices of (a–c) TRPH of 80% and 70% and (b–d) TSPH of 20% and 30%
The DDoS attack recognition results of the PIODL-ADC approach are reported on 80:20 of TRPH/TSPH, presented in Table 2 and Fig. 4. The attained performances demonstrate that the PIODL-ADC system offers effectual recognition outcomes. On 80% of TRPH, the PIODL-ADC technique offers an average


Figure 4: Average of PIODL-ADC technique on 80:20 of TRPH/TSPH
The DDoS attack recognition outcome of the PIODL-ADC methodology is defined on 70:30 of TRPH/TSPH and is presented in Table 3 and Fig. 5. The archived outcomes demonstrate that the PIODL-ADC method offers an effectual recognition solution.
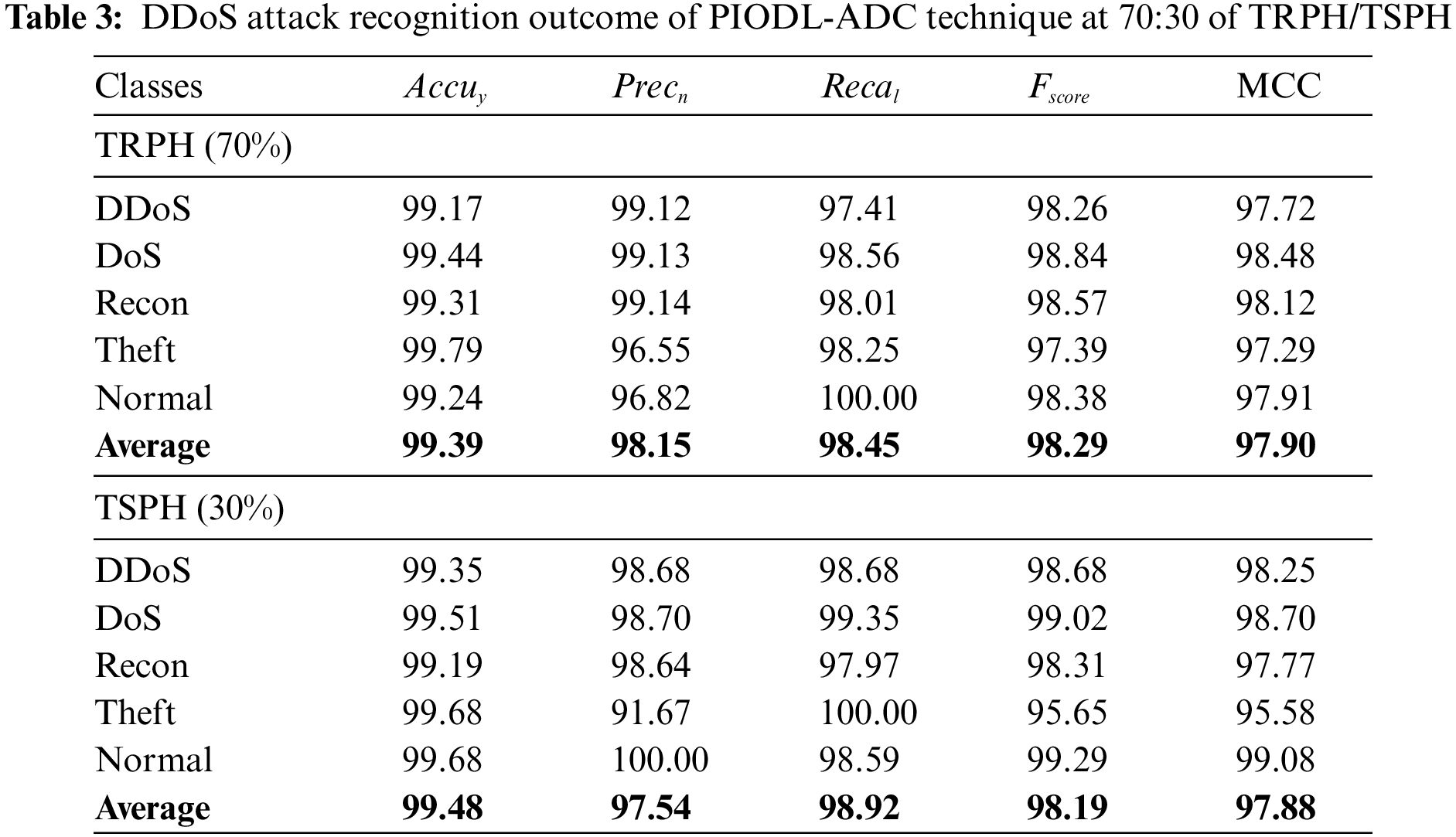
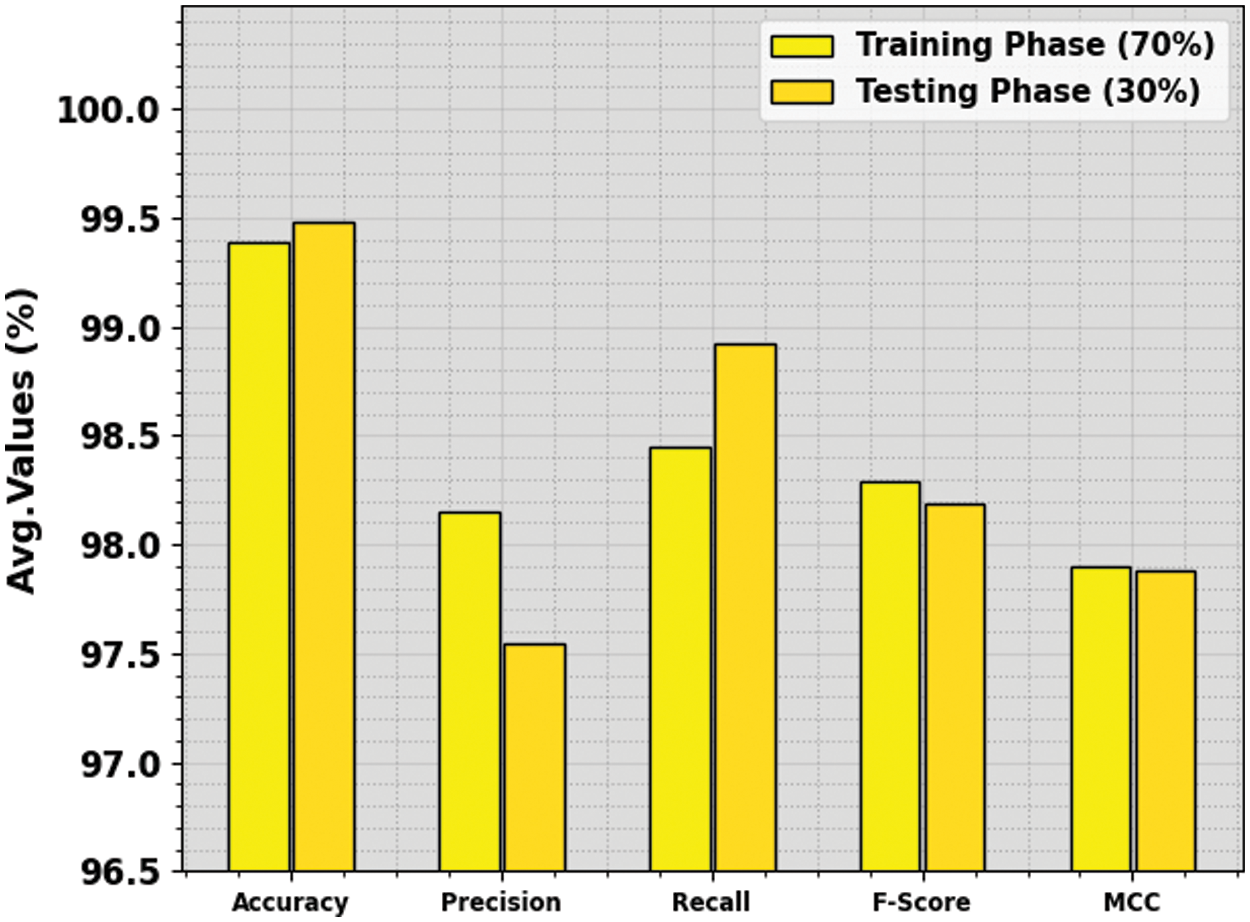
Figure 5: Average of PIODL-ADC technique on 70:30 of TRPH/TSPH
On 70% of TRPH, the PIODL-ADC approach gains an average
The

Figure 6:
Fig. 7 provides a widespread overview of the TR and TS loss outcomes for the PIODL-ADC approach on 80:20 of TRPH/TSPH under distinct epochs. The TR loss consistently decreases as the model refines its weight to minimize classifier errors on both data. The loss curves exemplify the model’s arrangement with the TR data, emphasizing its ability to capture patterns effectively in both datasets. Noteworthy is the continuous refinement of parameters in the PIODL-ADC algorithm, aimed at decreasing differences between forecasts and actual TR labels.

Figure 7: Loss curve of PIODL-ADC system at 80:20 of TRPH/TSPH
Regarding the precision-recall (PR) curve obtainable in Fig. 8, the findings unequivocally support that the PIODL-ADC system on 80:20 of TRPH/TSPH consistently accomplishes improved PR values across all the classes. These outcomes underscore the model’s effectual capacity for discriminating among different classes, underscoring its efficacy in accurately identifying class labels.
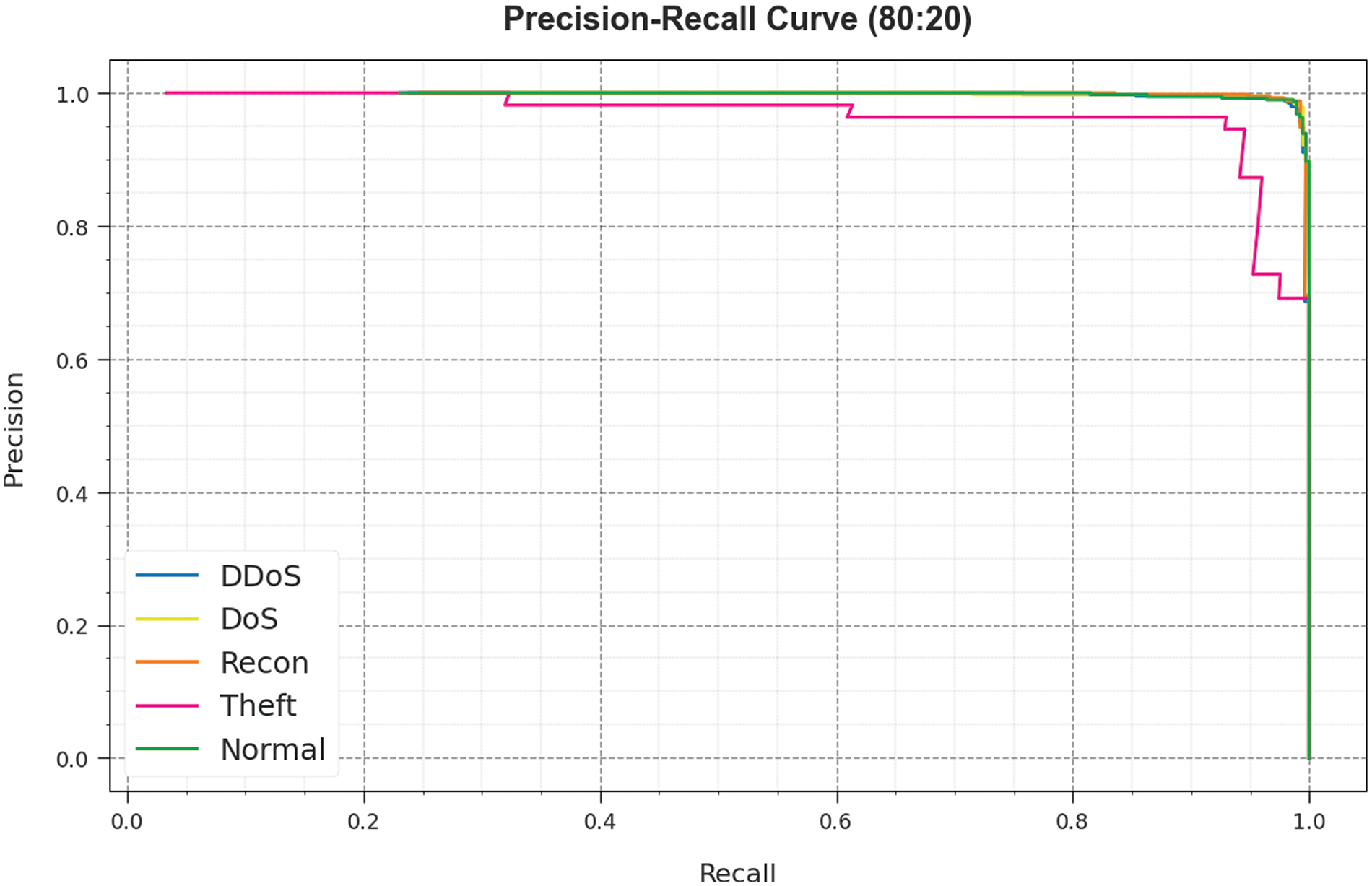
Figure 8: PR curve of PIODL-ADC system at 80:20 of TRPH/TSPH
Furthermore, in Fig. 9, the PIODL-ADC algorithm creates Receiver Operating Characteristic (ROC) outcomes on 80:20 of TRPH/TSPH, demonstrating its proficiency in distinguishing among classes. These curves provide appreciated insights into how the trade-off between True Negative Rate (TPR) and False Positive Rate (FPR) varies under various classifier epochs and thresholds. The results underscore the model’s correct classifier performance under various class labels, emphasizing its effectiveness in addressing diverse classification challenges.

Figure 9: ROC curve of PIODL-ADC technique on 80:20 of TRPH/TSPH
Finally, a detailed comparative analysis of the PIODL-ADC approach with recent systems is provided in Table 4 and Fig. 10 [23]. The results implied a higher solution for the PIODL-ADC method regarding different metrics. Based on


Figure 10: Comparative outcome of PIODL-ADC technique with other approaches
These results guaranteed the superior performance of the PIODL-ADC technique on the DDoS attack recognition process.
In this manuscript, the PIODL-ADC technique is proposed in an IoT environment. The PIODL-ADC technique employs a hyperparameter-tuned DL model for DDoS attack recognition in an IoT environment. Primarily, the PIODL-ADC technique employs Z-score normalization to scale the input data into a uniform format. For the feature selection process, the PIODL-ADC technique uses the PIO algorithm. Meanwhile, the ERNN model is applied to identify and detect DDoS attacks. Furthermore, RSA-based hyperparameter tuning is exploited to optimize the hyperparameter selection of the ERNN model. A series of experimental analyses are made to ensure the performance of the PIODL-ADC model. The experimental values stated that PIODL-ADC methodology exhibits better performance when compared to other techniques in different measures.
Acknowledgement: None.
Funding Statement: None.
Author Contributions: The authors confirm contribution to the paper as follows: study conception and design: Turki Ali Alghamdi, Saud S. Alotaibi; data collection: Turki Ali Alghamdi, Saud S. Alotaibi; analysis and interpretation of results: Turki Ali Alghamdi, Saud S. Alotaibi, draft manuscript preparation: Turki Ali Alghamdi, Saud S. Alotaibi. All authors reviewed the results and approved the final version of the manuscript.
Availability of Data and Materials: Data sharing does not apply to this article as no datasets were generated during the current study.
Ethics Approval: This study not included human or animal subjects.
Conflict of Interest: The authors declare that they have no conflict of interest to report regarding the present study.
References
1. A. Alomiri, S. Mishra, and M. AlShehri, “Machine learningbased security mechanism to detect and prevent cyber-attacks in IoT networks,” Int. J. Comput. Digit. Syst., vol. 14, no. 1, pp. 645–659, 2023. [Google Scholar]
2. K. Sritharan, R. Elagumeeharan, S. Nakkeeran, A. Mohamed, B. Ganegoda and K. Yapa, “Machine learning based distributed denial-of-services attacks detection and mitigation testbed for SDN-enabled IoT devices,” in 2022 13th Int. Conf. on Comput. Commun. and Netw. Technol. (ICCCNT), Kharagpur, India, IEEE, 2022, pp. 1–6. [Google Scholar]
3. R. Zagrouba and R. Alhajri, “Machine learning-based attacks detection and countermeasures in IoT,” Int. J. Commun. Netw. Inform. Secur., vol. 13, no. 2, pp. 158– 167, 2021. [Google Scholar]
4. A. Seifousadati, S. Ghasemshirazi, and M. Fathian, “A Machine Learning approach for DDoS detection on IoT devices,” arXiv preprint arXiv:2110.14911, 2021. [Google Scholar]
5. H. Chen, C. Meng, and J. Chen, “DDoS attack simulation and machine learning-based detection approach in the Internet of Things experimental environment,” Int. J. Inf. Secur. Priv., vol. 15, no. 3, pp. 1–18, 2021. doi: 10.4018/IJISP.2021070101. [Google Scholar] [CrossRef]
6. H. Cheng, J. Liu, T. Xu, B. Ren, J. Mao and W. Zhang, “Machine learning-based low-rate DDoS attack detection for SDNenabled IoT networks,” Int. J. Sens. Netw., vol. 34, no. 1, pp. 56–69, 2020. doi: 10.1504/IJSNET.2020.109720 [Google Scholar] [CrossRef]
7. J. G. Almaraz-Rivera, J. A. Perez-Diaz, and J. A. Cantoral-Ceballos, “Transport and application layer DDoS attack detection to IoT devices by using machine learning and deep learning models,” Sensors, vol. 22, no. 9, pp. 3367, 2022. doi: 10.3390/s22093367. [Google Scholar] [PubMed] [CrossRef]
8. M. ElKashlan, H. Aslan, and M. A. Azer, “DDoS attack detection in iot using machine learning based intrusion detection system (IDS),” in 2022 18th Int. Comput. Eng. Conf. (ICENCO), IEEE, 2022, vol. 1, pp. 19–24. doi: 10.1109/ICENCO55801.2022.10032515. [Google Scholar] [CrossRef]
9. M. Anwer, S. M. Khan, and M. U. Farooq, “Attack detection in IoT using machine learning,” Eng. Technol. Appl. Sci. Res., vol. 11, no. 3, pp. 7273–7278, 2021. doi: 10.48084/etasr.4202. [Google Scholar] [CrossRef]
10. K. Wehbi, “Machine learning based practical and efficient DDoS attacks detection system for IoT,” Doctoral dissertation, Tennessee State Univ., USA, 2022. [Google Scholar]
11. A. Prashanthi and R. R. Reddy, “Enhancing cyber security frameworks: Integrating pigeon-inspired optimization and dense neural networks for advanced intrusion detection using the CIC-IDS-2017 dataset,” Int. J. Intell. Syst. Appl. Eng., vol. 12, no. 11, pp. 220–233, 2024. [Google Scholar]
12. M. Abd Elaziz, M. A. Al-qaness, A. Dahou, R. A. Ibrahim, and A. A. Abd El-Latif, “Intrusion detection approach for cloud and IoT environments using deep learning and Capuchin Search Algorithm,” Adv. Eng. Softw., vol. 176, no. 5, pp. 103402, 2023. doi: 10.1016/j.advengsoft.2022.103402. [Google Scholar] [CrossRef]
13. C. Kumar and M. S. A. Ansari, “An explainable nature-inspired cyber attack detection system in Software-Defined IoT applications,” Expert. Syst. Appl., vol. 250, no. 4, pp. 123853, 2024. doi: 10.1016/j.eswa.2024.123853. [Google Scholar] [CrossRef]
14. H. Asgharzadeh, A. Ghaffari, M. Masdari, and F. S. Gharehchopogh, “Anomaly-based intrusion detection system in the Internet of Things using a convolutional neural network and multi-objective enhanced Capuchin Search Algorithm,” J. Parallel Distr. Comput., vol. 175, no. 5, pp. 1–21, 2023. doi: 10.1016/j.jpdc.2022.12.009. [Google Scholar] [CrossRef]
15. M. Cherian and S. L. Varma, “Secure SDN-IoT framework for DDoS attack detection using deep learning and counter based approach,” J. Netw. Syst. Manage., vol. 31, no. 3, pp. 54, 2023. doi: 10.1007/s10922-023-09749-w. [Google Scholar] [CrossRef]
16. H. Rekha and M. Siddappa, “Hybrid deep learning model for attack detection in internet of things,” Serv. Oriented Comput. Appl., vol. 16, no. 4, pp. 293–312, 2022. doi: 10.1007/s11761-022-00342-8. [Google Scholar] [CrossRef]
17. L. Ortet Lopes, D. Zou, F. A. Ruambo, S. Akbar, and B. Yuan, “Towards effective detection of recent DDoS attacks: A deep learning approach,” Secur. Commun. Netw., vol. 2021, pp. 1–14, 2021. [Google Scholar]
18. A. A. Alashhab, M. S. M. Zahid, A. Muneer, and M. Abdullahi, “Low-rate DDoS attack detection using deep learning for SDN-enabled IoT Networks,” Int. J. Adv. Comput. Sci. Appl., vol. 13, no. 11, pp. 371–377, 2022. doi: 10.14569/issn.2156-5570. [Google Scholar] [CrossRef]
19. A. Ahmim, F. Maazouzi, M. Ahmim, S. Namane, and I. B. Dhaou, “Distributed denial of service attack detection for the Internet of Things using hybrid deep learning model,” IEEE Access, vol. 11, pp. 119862–119875, 2023. doi: 10.1109/ACCESS.2023.3327620. [Google Scholar] [CrossRef]
20. A. Sagu, N. S. Gill, P. Gulia, J. M. Chatterjee, and I. Priyadarshini, “A hybrid deep learning model with self-improved optimization algorithm for detection of security attacks in IoT environment,” Future Internet, vol. 14, no. 10, pp. 301, 2022. doi: 10.3390/fi14100301. [Google Scholar] [CrossRef]
21. M. Ragab, S. Alshammari, L. A. Maghrabi, D. Alsalman, T. Althaqafi and A. A. M. AL-Ghamdi, “Robust DDoS attack detection using piecewise Harris Hawks optimizer with deep learning for a secure internet of things environment,” Mathematics, vol. 11, no. 21, pp. 4448, 2023. doi: 10.3390/math11214448. [Google Scholar] [CrossRef]
22. D. Javeed, T. Gao, M. T. Khan, and I. Ahmad, “A hybrid deep learning-driven SDN enabled mechanism for secure communication in Internet of Things (IoT),” Sensors, vol. 21, no. 14, pp. 4884, 2021. doi: 10.3390/s21144884. [Google Scholar] [PubMed] [CrossRef]
23. M. Aljebreen, H. A. Mengash, M. A. Arasi, S. S. Aljameel, A. Salama and M. A. Hamza, “Enhancing DDoS attack detection using snake optimizer with ensemble learning on internet of things environment,” IEEE Access, vol. 11, pp. 104745, 2023. doi: 10.1109/ACCESS.2023.3318316. [Google Scholar] [CrossRef]
24. H. K. Bella and S. Vasundra, “Healthcare intrusion detection using hybrid correlation-based feature selection-bat optimization algorithm with convolutional neural network: A hybrid correlation-based feature selection for intrusion detection systems,” Int. J. Adv. Comput. Sci. & Appl., vol. 15, no. 1, pp. 671–697, 2024 [Google Scholar]
25. T. Rathod et al., “AI and blockchain-based secure data dissemination architecture for iot-enabled critical infrastructure,” Sensors, vol. 23, no. 21, pp. 8928, 2023. doi: 10.3390/s23218928. [Google Scholar] [PubMed] [CrossRef]
26. M. Saad and M. A. H. Abozied, “Nonlinear system control analysis and optimization using advanced Pigeon-Inspired optimization algorithm,” J. King Saud Univ.-Eng. Sci., vol. 36, no. 1, pp. 45–56, 2022. doi: 10.1016/j.jksues.2022.11.001. [Google Scholar] [CrossRef]
27. N. Koroniotis, N. Moustafa, E. Sitnikova, and B. Turnbull, “Towards the development of realistic botnet dataset in the internet of things for network forensic analytics: Bot-IoT dataset,” Future Gener. Comput. Syst., vol. 100, no. 7, pp. 779–796, 2019. doi: 10.1016/j.future.2019.05.041. [Google Scholar] [CrossRef]
Cite This Article
 Copyright © 2024 The Author(s). Published by Tech Science Press.
Copyright © 2024 The Author(s). Published by Tech Science Press.This work is licensed under a Creative Commons Attribution 4.0 International License , which permits unrestricted use, distribution, and reproduction in any medium, provided the original work is properly cited.


 Submit a Paper
Submit a Paper Propose a Special lssue
Propose a Special lssue View Full Text
View Full Text Download PDF
Download PDF Downloads
Downloads
 Citation Tools
Citation Tools