 Open Access
Open Access
ARTICLE
Securing the Internet of Health Things with Certificateless Anonymous Authentication Scheme
Department of Computer Science and Information Systems, College of Applied Sciences, AlMaarefa University, Riyadh, 13713, Saudi Arabia
* Corresponding Author: Nisreen Innab. Email:
Computers, Materials & Continua 2024, 80(2), 2237-2258. https://doi.org/10.32604/cmc.2024.049608
Received 12 January 2024; Accepted 06 June 2024; Issue published 15 August 2024
Abstract
Internet of Health Things (IoHT) is a subset of Internet of Things (IoT) technology that includes interconnected medical devices and sensors used in medical and healthcare information systems. However, IoHT is susceptible to cybersecurity threats due to its reliance on low-power biomedical devices and the use of open wireless channels for communication. In this article, we intend to address this shortcoming, and as a result, we propose a new scheme called, the certificateless anonymous authentication (CAA) scheme. The proposed scheme is based on hyperelliptic curve cryptography (HECC), an enhanced variant of elliptic curve cryptography (ECC) that employs a smaller key size of 80 bits as compared to 160 bits. The proposed scheme is secure against various attacks in both formal and informal security analyses. The formal study makes use of the Real-or-Random (ROR) model. A thorough comparative study of the proposed scheme is conducted for the security and efficiency of the proposed scheme with the relevant existing schemes. The results demonstrate that the proposed scheme not only ensures high security for health-related data but also increases efficiency. The proposed scheme’s computation cost is 2.88 ms, and the communication cost is 1440 bits, which shows its better efficiency compared to its counterpart schemes.Keywords
The Internet of Health Things (IoHT) is a networked system that incorporates various biomedical devices, including smart wearables, implants, and ingestible electronics. These devices are integrated with appropriate software applications to facilitate the collection, analysis, and dissemination of physiological data through the internet [1,2]. Physiological data often encompasses many health-related indications such as blood pressure, chest sounds, body temperature, respiration rate, electrocardiogram (ECG), patient posture, breathing rate, and other vital parameters [3–7]. In addition, IoHT systems could be used to update environmental factors such as patient care settings, room conditions, laboratory shift timings, treatment durations, and staff-to-patient ratios. The health information system maintains computerized records of patients’ environmental conditions and health-related information, accessible to medical professionals anytime the patient enters the hospital.
Privacy and security issues often occur in IoHT systems because biomedical sensors and user-customized devices are frequently involved in internet-based communication. The typical IoHT system architecture is shown in Fig. 1 [8]. To provide secure connectivity in an IoHT system, the primary security challenge is validating the integrity of data transmitted across an unsecured wireless link. The second security concern is ensuring receiver anonymity, which means that only the sender is aware of the identities of the receivers. An intruder can, for instance, intercept communication between biomedical devices and sensors to steal or forge health-related data. This system may also be susceptible to the “greedy behavior attack,” one of the most aggressive DoS attacks. It attempts to prevent authorized nodes from accessing the communication channel [9]. Unfortunately, most IoHT devices have low processing and storage capabilities, making it impossible for them to execute complex cryptographic computations to protect against such attacks. The majority of public key cryptosystems mentioned in the literature require a lot of computation, making them unsuitable for IoHT systems.

Figure 1: A typical architecture of IoHT system
To secure IoHT systems, authentication mechanisms based on the digital signature system can be implemented [10]. This mechanism uses a shared key to provide not just authentication and privacy but also the other three primary requirements of confidentiality, integrity, and non-repudiation [11]. Two of the most common authentication mechanisms used in public-key cryptosystems are Identity-Based Cryptography (IBC) and Public Key Infrastructure (PKI). It is essential in the PKI setting to have a reliable unforgeable connection between a user’s identity and their public keys. Because of this, a Certificate Authority (CA) that gives each link its signature is required. With certificates, the CA limits the public key to serve as the identification of a participant [12]. Problems with certificates expiring, being distributed, and being stored are only a few of the drawbacks of PKI systems. As an alternative, IBC is promoted as a means of cutting down on the cost of managing public keys [13]. The trustworthy Private Key Generator (PKG) has direct knowledge of the private keys of the participants, which is at the cost of private key escrow problems [14,15]. The issue of key escrow in authentication methods can be solved by using a certificateless cryptosystem with a signature strategy. Additionally, there is the problem of receiver anonymity, which means that only the sender knows who the receivers are. Fortunately, this obstacle can be circumvented by using anonymous authentication.
Motivation and Contributions
Authentication schemes are usually built using computing-based cryptographic operations like bilinear pairing, Rivest-Shamir-Adleman (RSA), and ECC, and then evaluated to see how well the proposed scheme works. These operations, on the other hand, have high computation and communication costs. As a result, HECC, an enhanced variant of ECC that employs 80-bit keys, identities, and certificate sizes to give the same level of security as ECC, bilinear pairing, and RSA [16], can be employed. As a result, for resource-constrained devices in IoHT systems, HECC would be a preferable alternative. This work provides a one-of-a-kind IoHT solution called the certificateless anonymous authentication scheme. The scheme is based on the HECC concept and has a small key size. The following are some of the key contributions of the undertaken research work:
1. We propose an efficient anonymous authentication scheme in certificateless settings for IoHT systems.
2. To overcome constraints such as low processing capabilities associated with biomedical devices and sensors, the proposed scheme uses a public-key cryptography method based on the HECC concept.
3. The proposed scheme is secure against various attacks in both formal and informal security analyses. The formal study makes use of the Real-or-Random (ROR) model.
4. Lastly, we show that the proposed scheme has lower costs for both computation and communication than relevant existing schemes.
The following section outlines the organizational structure of the remaining portions of the article. The literature review is further discussed in Section 2. In Section 3, we provide the preliminary information. The CAA plan under consideration is included in Section 4. Section 5 of the document encompasses the security analysis. Section 6 of the document encompasses a comprehensive performance assessment analysis, while Section 7 presents conclusions and future work.
This section focuses on the security and privacy concerns of the IoHT system while using an authentication scheme. Also, we have given the limitations of the scheme, which appear in this section’s literature review in Table 1. Chen et al. [17] proposed a telemedicine information system authentication scheme based on dynamic identity. According to the authors, their scheme overcomes the problem of user anonymity. Jiang et al. [18] pointed out that the Chen et al.’s scheme did not ensure user anonymity or untraceability, which could lead to identity guessing and tracking attacks. They presented an updated strategy for maintaining user anonymity, saying their scheme could survive any attack. On the other hand, Kumari et al. [19] revealed that Jiang et al.’s scheme is vulnerable to several attacks, including password guessing, impersonation, DoS attacks, and even improper login request verification.
Chen et al. [20] proposed an authentication scheme for medical data interchange in the cloud environment to prevent security issues and safeguard patients’ health data. Neither patient privacy nor message authentication were ensured by the proposed scheme, as shown by the work proposed by Chiou et al. [21]. Therefore, they improved the cloud-based healthcare system’s privacy authentication process. Patients’ privacy was not protected in Mohit et al.’s [22] analysis of the method reported in Chiou et al.’s scheme, which they found could be compromised by attacks from stolen mobile devices. To strengthen healthcare security and reduce its burdensome complexity, they designed a lightweight two-factor authentication solution using cloud computing. It was pointed out by Li et al. [23] that the scheme proposed by Mohit et al. is susceptible to the forged inspection report and cannot guarantee patient anonymity or data confidentiality.
Saeed et al. [24] proposed an online/offline certificateless signature approach in wireless body area networks based on the internet of things to build a heterogeneous remote anonymous authentication mechanism. However, Liao et al. [25] demonstrated that the approach of Saeed et al. is vulnerable to a forgery attack in which no information other than public system parameters is required. He et al. [26] proposed anonymous authentication for WBAN and shown that their scheme is both secure and efficient when compared to its counterpart schemes. Kasyoka et al. [27] proposed an ECC-based authentication scheme for WBANs. The proposed scheme was both certificateless and pairing-free. The authors of the presented scheme of Kasyoka et al. claimed that their scheme is efficient in terms of communication cost and running time. Liu et al. [28] introduced a novel and efficient anonymous authentication scheme for WBANs that ensures that doctors and patients are legal in a secure manner.
All of the above-mentioned solutions involve the use of cryptographic techniques; these schemes are mostly based on ECC and bilinear pairing, both of which have prohibitively expensive communication and computation costs. However, the proposed scheme is based on the concept of HECC, a more sophisticated form of ECC. HECC uses an 80-bit key size, which is half as large as ECC’s key size, but it still offers the same level of security as ECC and bilinear pairing.
This section explains some of the key concepts and materials that will be used in constructing the proposed scheme.
In 1989, Koblitz introduced a group law for the Jacobian of a Hyperelliptic curve (HE). It is defined by the Jacobian of genus
It typically has
(HE):
3.2 Hyperelliptic Curve Deffie-Hellman (HEDH) Problem
Suppose the random triple
3.3 Hyperelliptic Curve Discrete Logarithm (HEDL) Problem
Suppose the random tuple
In this section, the network model is provided first, followed by the construction and correctness of the proposed scheme.
Depending on the requirements, the network model of IoHT systems can be implemented in several topologies; one such networking architecture is shown in Fig. 2. Wearable Biomedical Devices (WBD), Network Manager (NMGR)/Service Provider, Application Provider (APDR), and IoT gateway are all included in this network model. Each entity’s function is described as follows:

Figure 2: Proposed network model
1. APDR: The APDR will assess a patient’s health and generate health-related information. Following this, it sends its encrypted identity along with a public number send (
2. WBD: To register WBD, the user compute and send (
1. NMGR/Service Provider: When NMGR/Service Provider receives identity from both WBD and APDR, this entity will act as a key generation canter in certificateless cryptography and will be responsible for creating the partial private key for both WBD and APDR.
2. IoT Gateway: The IoT gateway router can be used to connect any things that communicate using wireless technologies.
4.2 Construction of the Proposed Scheme
The proposed scheme has been constructed on the basis of the following phases and all the symbols used in the construction is included in Table 2.
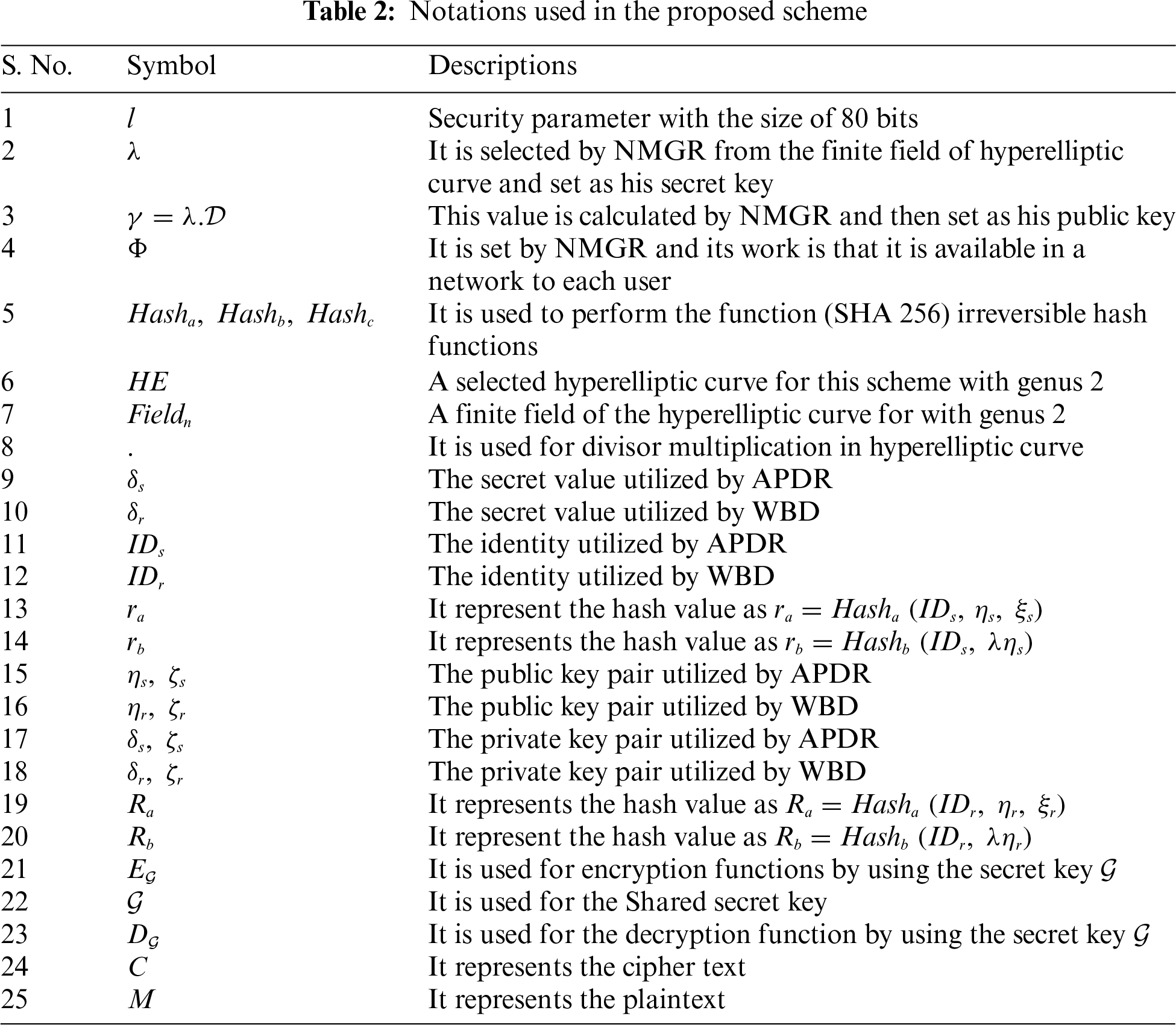
i. Initialization
Given an 80-bit hyper elliptic curve parameter
ii. Registration Phase
In this phase, APDR and WBD will be registered using the following steps:
1. Fig. 3 shows the registration process of APDR, in which the user selects
2. Fig. 4 shows the registration process of WBD, in which the user selects

Figure 3: Application provider registration

Figure 4: Wearable biomedical devices registration
iii. Authentication and Key Management
Fig. 5 represents the flow of proposed scheme, in which the application provider generates the signature for mutual authentication with WBD by using the following steps:

Figure 5: Mutual authentication phase of proposed scheme
• The APDR can compute
• Compute
• Calculate
• Upon reception (
• Also, compute
• The WBD set the secret key as
• After reception of (
As a receiver of (
Also, WBD can process its secret key as followed:
In this section, we provide the provable security based on Random Oracle Model (ROM) and informal security analysis, which are as follows.
5.1 Provable Security Analysis
Here, we are going to prove the confidentiality and unforgeability of our proposed scheme against the following two types of attackers by using the ROM.
Outsider Attacker (
Insider Attacker (
So, keeping in view the capabilities of the above attackers (
Theorem 1-Confidentiality: Suppose the outsider attacker (
Proof: Suppose the random triple
Setup: Given an 80 bit hyper elliptic curve parameter
• If
• If
Public Key Queries:
1. If
2. If
Partial Private Key Queries:
1. If
2. If
Private Key Queries:
1. If
2. If
Replace Public Key Queries:
Sender Query: As a response of this query,
• If
• If
Receiver Query:
• If
• If
• If
Challenge:
• If
• If
Guess: After performing the same number of queries as performed above,
• In the event that any steps of the simulation are avoided,
• Otherwise, if
Note that,
Probability Analysis: In the above game, let
On the other hand, if each of the independent events listed below occurs,
So, the probability of
Finally, we can get:
Theorem 2-Confidentiality: Suppose the insider attacker (
Proof: Suppose the random triple
Setup: Given an 80-bit hyper elliptic curve parameter
Public Key Queries:
• If
• If
Private Key Queries:
1. If
2. If
Sender Query: As a response of this query,
• If
• If
Receiver Query:
• If
• If
• If
Challenge:
• If
• If
Guess: After performing the same number of queries as performed above,
• In the event that any steps of the simulation are avoided,
• Otherwise, if
Note that,
Probability Analysis: In the above game, let
On the other hand, if each of the independent events listed below occurs,
So, the probability of
Finally, we can get:
Theorem 3-Unforgeability: Suppose the outsider attacker (
Proof: Suppose the random triple
Setup: Given an 80 bit hyper elliptic curve parameter
Queries: The queries which can ask by
Output: After performing all the queries that are done in Theorem 1,
So, in the above equations,
Probability Analysis: In the above game, let
On the other hand, if each of the independent events listed below occurs,
So, the probability of
Finally, we can get:
Theorem 4-Unforgeability: Suppose the insider attacker (
Proof: Suppose the random triple
Setup: Given an 80-bit hyper elliptic curve parameter
Queries: The queries which can ask by
Output: After performing all the queries that are done in Theorem 2,
So, in the above equations,
Probability Analysis: In the above game, let
On the other hand, if each of the independent events listed below occurs,
So, the probability of
Finally, we can get:
5.2 Informal Security Analysis
The proposed scheme is based on hash function and hyper elliptic curve discrete logarithm problem. The two main properties of the hash function are irreversibility and collision resistance. Suppose
Mutual Authentication: The APDR generates the digital signature for mutual authentication with WBD as
For authentication, and if the equality of
Signature Unforgeability: In the proposed scheme, the signature generated by the application provider is computed using the formula,
Sender Anonymity: To register APDR, the user selects
Receiver Anonymity: To register WBD, the user selects
Integrity: The WBD set the secret key as
This section compares the proposed scheme to other relevant schemes in terms of computation cost, communication cost, memory overhead and security functionalities.
In this section, we compare the proposed approach with the methods presented by Liao et al. [25–28]. The comparison is conducted based on the computational costs. Table 2 provides a summary of the important conclusions obtained from the comparison of computing costs. The computational time for Elliptic Curve Point Multiplication (EMUL) is 0.97 milliseconds, while bilinear pairing (P) takes 14.90 ms. Pairing-based point multiplications (BPM) need 4.31 ms, while exponentials on bilinear pairing (EXP) take 1.25 ms [29–32]. To evaluate the computational cost of the suggested approach, we used the Multi-precision Integer and Rational Arithmetic C Library (MIRACL) [33]. The library does a substantial quantity of tests, potentially reaching up to 1000, on fundamental cryptographic procedures. The simulations are executed on a computing device equipped with an Intel Core i7-4510U CPU operating at a frequency of 2.0 GHz, 8 GB of random-access memory (RAM), and the Windows 7 operating system [34]. The HEMUL is expected to have a processing time of 0.48 milliseconds due to its key size of 80 bits. The analysis of Tables 3 and 4, and Fig. 6 demonstrates that the suggested design exhibits much higher cost-effectiveness in terms of computing.
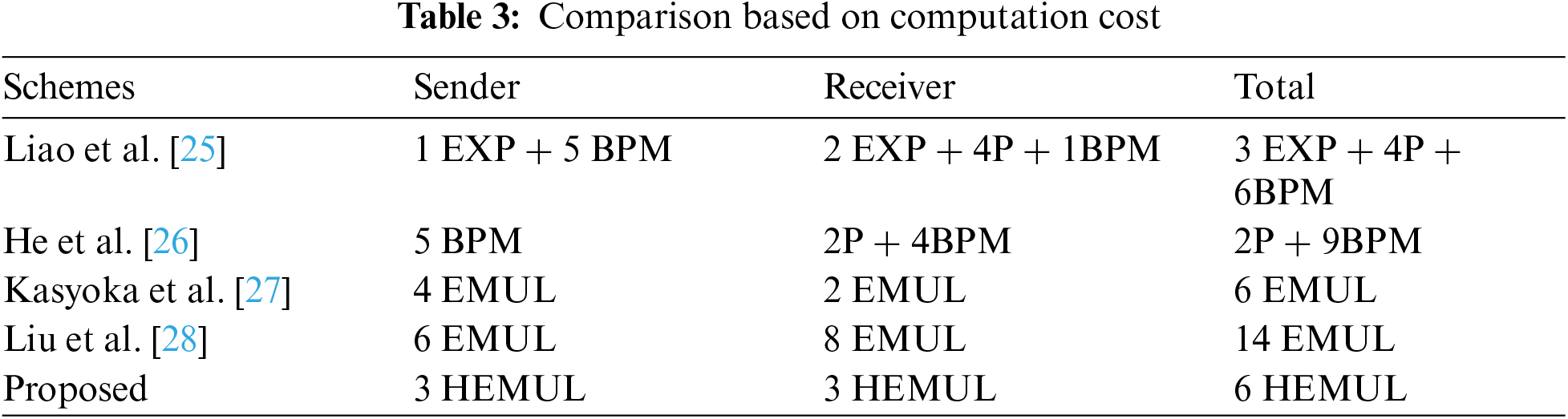
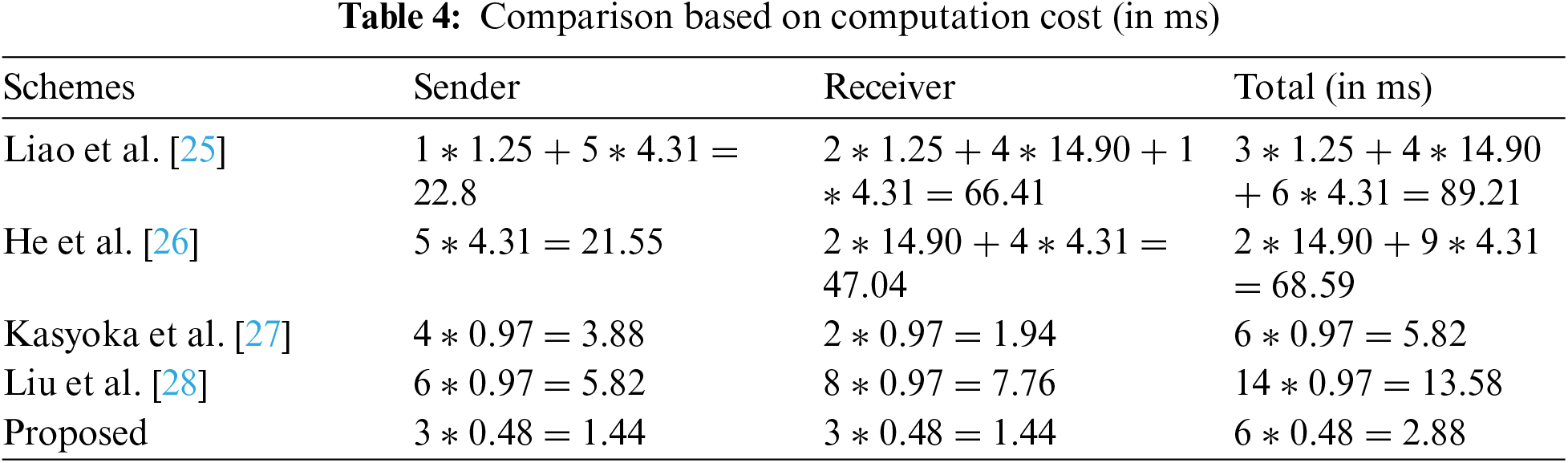

Figure 6: Comparative analysis based on communication cost (in bits) (Liao et al. [25], He et al. [26], Kasyoka et al. [27], Liu et al. [28])
In this part, the proposed scheme is compared to existing schemes proposed by Liao et al. [25–28] in terms of communication cost. Tables 5 and 6 show the primary conclusions drawn from the comparison. According to the data shown in Fig. 7, choosing the proposed scheme results in a significant reduction in communication costs.
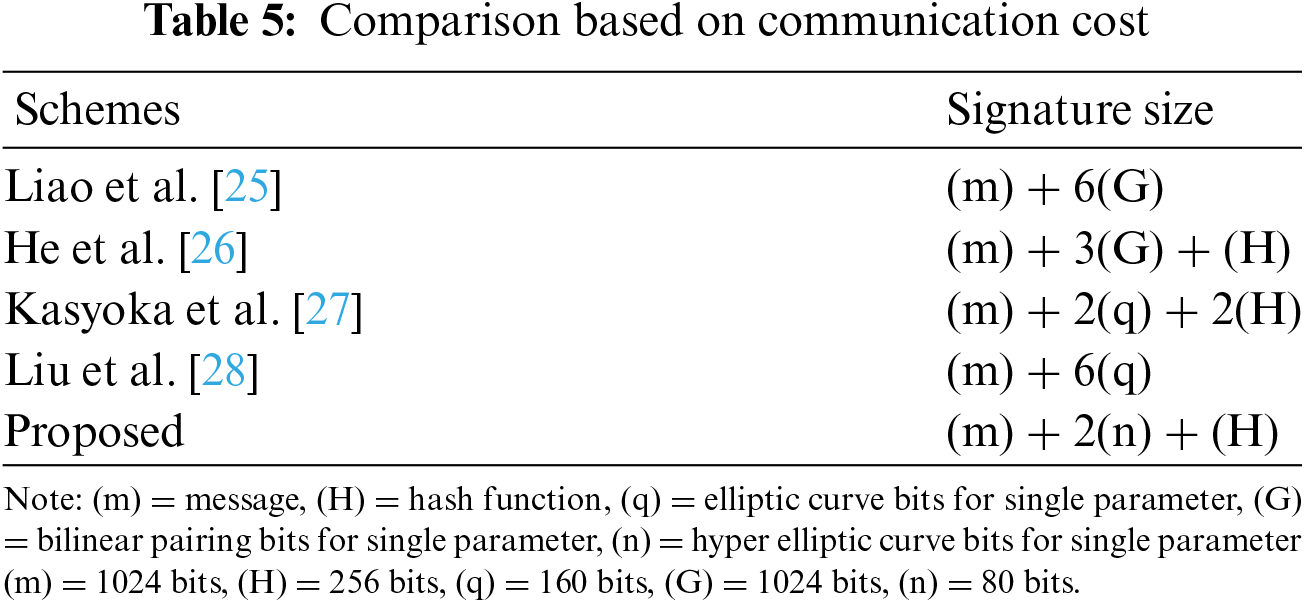
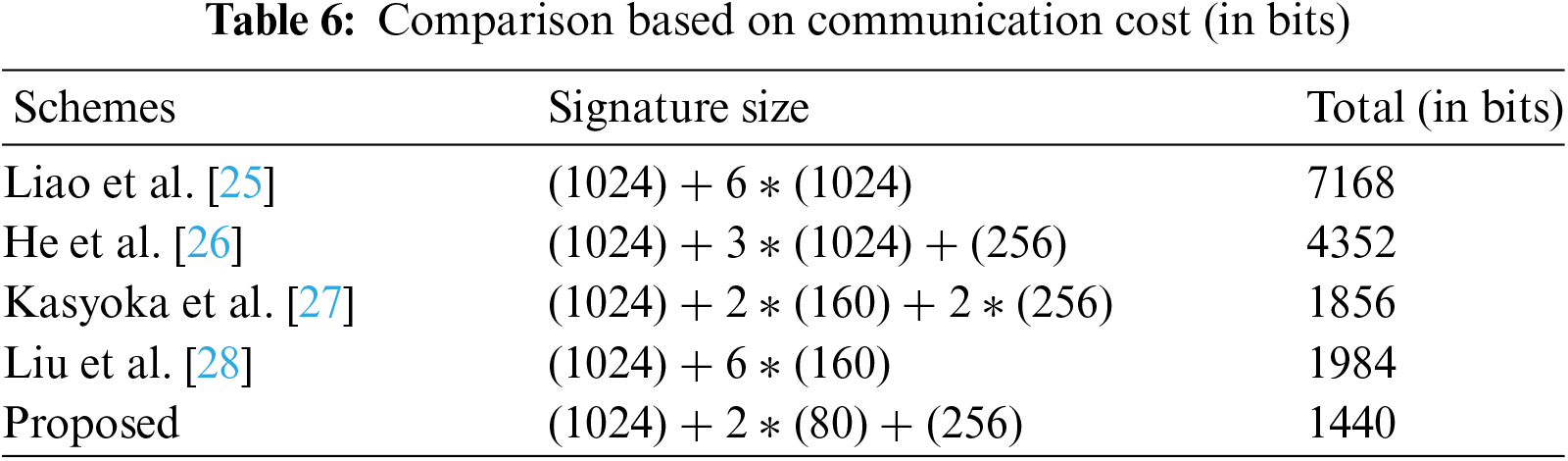

Figure 7: Comparative analysis based on communication cost (in bits) [25–28]
7 Conclusions and Future Works
IoHT systems are used to exchange remote data for a variety of physical activities, including patient monitoring, treatment development, observation and counseling. In IoHT, communication, computing, and interoperability are provided through multiple sensors, actuators, and controllers, resulting in a seamless connection and efficient resource management. Traditional cryptographic techniques, on the other hand, are not practicable for the vast majority of IoHT deployments due to the restrictions of low-power embedded devices. As a result, we proposed the CAA scheme, a security method based on the HECC in this article. The HECC method is effective with small key sizes and can be used in IoHT systems. The security analysis demonstrates the proposed scheme’s efficacy in preventing several cyber-attacks. Second, comparing the proposed scheme with existing schemes is carried out in terms of computation and communication costs. The proposed scheme takes 2.88 ms to compute, compared to 89.21, 68.59, 5.82, and 13.58 ms for Liao et al. [25–28], respectively. Similarly, the proposed scheme’s communication cost is 1440 bits, compared to 7168, 4352, 1856, and 1984 bits for Liao et al. [25–28], respectively. This comparison reveals that the proposed scheme is more efficient than the existing methods in computation and communication costs. In the future, we are intended to consider Genus 3 hyperelliptic curve, which will further improve the proposed scheme efficiency.
Acknowledgement: Nisreen Innab would like to express sincere gratitude to AlMaarefa University, Riyadh, Saudi Arabia, for supporting this research.
Funding Statement: The author received no specific funding for this study.
Availability of Data and Materials: The data supporting the conclusions of this article are included within the article.
Conflicts of Interest: The author declares that he has no conflicts of interest to report regarding the present study.
References
1. J. J. P. C. Rodrigues et al., “Enabling technologies for the internet of health things,” IEEE Access, vol. 6, no. 1, pp. 13129–13141, 2018. doi: 10.1109/ACCESS.2017.2789329. [Google Scholar] [CrossRef]
2. S. M. R. Islam, D. Kwak, M. H. Kabir, M. Hossain, and K. S. Kwak, “The internet of things for health care: A comprehensive survey,” IEEE Access, vol. 3, no. 1, pp. 678–708, 2015. doi: 10.1109/ACCESS.2015.2437951. [Google Scholar] [CrossRef]
3. L. Catarinucci et al., “An IoT-aware architecture for smart healthcare systems,” IEEE Internet Things J., vol. 2, no. 6, pp. 515–526, Dec. 2015. doi: 10.1109/JIOT.2015.2417684. [Google Scholar] [CrossRef]
4. Y. Yin, Y. Zeng, X. Chen, and Y. Fan, “The internet of things in healthcare: An overview,” J. Ind. Inf. Integr., vol. 1, no. 1, pp. 3–13, Mar. 2016. doi: 10.1016/j.jii.2016.03.004. [Google Scholar] [CrossRef]
5. C. Dong, Y. Sun, M. Shafiq, N. Hu, Y. Liu and Z. Tian, “Optimizing mobility-aware task offloading in smart healthcare for internet of medical things through multi-agent reinforcement learning,” IEEE Internet Things J., vol. 11, no. 8, pp. 13677–13691, 15 Apr. 2024. doi: 10.1109/JIOT.2023.3338718. [Google Scholar] [CrossRef]
6. B. Farahani, F. Firouzi, V. Chang, M. Badaroglu, N. Constant and K. Ankodiya, “Towards fog-driven IoT eHealth: Promises and challenges of IoT in medicine and healthcare,” Future Gener. Comput. Syst., vol. 78, pp. 659–676, Jan. 2018. doi: 10.1016/j.future.2017.04.036. [Google Scholar] [CrossRef]
7. F. Firouzi et al., “Internet-of-things and big data for smarter healthcare: From device to architecture, applications and analytics,” Future Gener. Comput. Syst., vol. 78, no. 1, pp. 583–586, 2018. doi: 10.1016/j.future.2017.09.016. [Google Scholar] [CrossRef]
8. X. Lin, R. Lu, X. Shen, Y. Nemoto, and N. Kato, “Sage: A strong privacy preserving scheme against global eavesdropping for eHealth systems,” IEEE J. Sel. Areas Commun., vol. 27, no. 4, pp. 365–378, 2009. doi: 10.1109/JSAC.2009.090502. [Google Scholar] [CrossRef]
9. F. S. Sadek, K. Belkadi, A. Abouaissa, and P. Lorenz, “Identifying misbehaving greedy nodes in IoT networks,” Sensors, vol. 21, no. 15, pp. 5127, 2021. doi: 10.3390/s21155127. [Google Scholar] [PubMed] [CrossRef]
10. C. M. Chen, Z. Li, S. A. Chaudhry, and L. Li, “Attacks and solutions for a two-factor authentication protocol for wireless body area networks,” Secur. Commun. Netw., vol. 2021, no. 2021, pp. 1–12. doi: 10.1155/2021/3116593. [Google Scholar] [CrossRef]
11. S. A. Chaudhry, A. Irshad, K. Yahya, N. Kumar, M. Alazab and Y. B. Zekeria, “Rotating behind privacy: An improved lightweight authentication scheme for cloud-based IoT environment,” ACM Trans. Internet Technol., vol. 21, no. 3, pp. 1–19, 2021. [Google Scholar]
12. K. Kim, J. Ryu, Y. Lee, and D. Won, “An improved lightweight user authentication scheme for the internet of medical things,” Sensors, vol. 23, no. 3, pp. 1122, 2023. doi: 10.3390/s23031122. [Google Scholar] [PubMed] [CrossRef]
13. S. Hussain, I. Ullah, H. Khattak, M. A. Khan, C. -M. Chen and S. Kumari, “A lightweight and provable secure identity-based generalized proxy signcryption (IBGPS) scheme for industrial internet of things (IIoT),” J. Inf. Secur. Appl., vol. 58, no. 1, pp. 102625, 2021. doi: 10.1016/j.jisa.2020.102625. [Google Scholar] [CrossRef]
14. C. M. Chen, Z. Chen, S. Kumari, and M. C. Lin, “LAP-IoHT: A lightweight authentication protocol for the Internet of Health Things,” Sensors, vol. 22, no. 14, pp. 5401, Jul. 2022. doi: 10.3390/s22145401. [Google Scholar] [PubMed] [CrossRef]
15. P. Kumar, S. Kumari, V. Sharma, X. Li, A. K. Sangaiah and S. H. Islam, “Secure CLS and CL-AS schemes designed for vanets,” J. Supercomput., vol. 75, no. 6, pp. 3076–3098, 2018. doi: 10.1007/s11227-018-2312-y. [Google Scholar] [CrossRef]
16. I. Ullah, N. U. Amin, M. A. Khan, H. Khattak, and S. Kumari, “An efficient and provable secure certificate-based combined signature, encryption and signcryption scheme for internet of things (IoT) in mobile health (m-health) system,” J. Med. Syst., vol. 45, no. 1, pp. 1–20, 2020. [Google Scholar]
17. H. M. Chen, J. W. Lo, and C. K. Yeh, “An efficient and secure dynamic id-based authentication scheme for telecare medical information systems,” J. Med. Syst., vol. 36, no. 6, pp. 3907–3915, 2012. doi: 10.1007/s10916-012-9862-y. [Google Scholar] [PubMed] [CrossRef]
18. Q. Jiang, J. Ma, Z. Ma, and G. Li, “A privacy enhanced authentication scheme for telecare medical information systems,” J. Med. Syst., vol. 37, no. 1, pp. 9897–9898, 2013. doi: 10.1007/s10916-012-9897-0. [Google Scholar] [PubMed] [CrossRef]
19. S. Kumari, M. K. Khan, and R. Kumar, “Cryptanalysis and improvement of ‘a privacy enhanced scheme for telecare medical information systems’,” J. Med. Syst., vol. 37, no. 4, pp. 1–11, 2013. doi: 10.1007/s10916-013-9952-5. [Google Scholar] [PubMed] [CrossRef]
20. C. L. Chen, T. T. Yang, M. L. Chiang, and T. F. Shih, “A privacy authentication scheme based on cloud for medical environment,” J. Med. Syst., vol. 38, no. 11, pp. 143–216, 2014. doi: 10.1007/s10916-014-0143-9. [Google Scholar] [PubMed] [CrossRef]
21. S. Y. Chiou, Z. Ying, and J. Liu, “Improvement of a privacy authentication scheme based on cloud for medical environment,” J. Med. Syst., vol. 40, no. 4, pp. 101, 2016. doi: 10.1007/s10916-016-0453-1. [Google Scholar] [PubMed] [CrossRef]
22. P. Mohit, R. Amin, A. Karati, G. P. Biswas, and M. K. Khan, “A standard mutual authentication protocol for cloud computing based health care system,” J. Med. Syst., vol. 41, no. 4, pp. 35–50, 2017. doi: 10.1007/s10916-017-0699-2. [Google Scholar] [PubMed] [CrossRef]
23. C. T. Li, D. H. Shih, and C. C. Wang, “Cloud-assisted mutual authentication and privacy preservation protocol for telecare medical information systems,” Comput. Methods Programs Biomed., vol. 157, no. 1, pp. 191–203, 2018. doi: 10.1016/j.cmpb.2018.02.002. [Google Scholar] [PubMed] [CrossRef]
24. M. E. S. Saeed, Q. Liu, G. Tian, B. Gao, and F. Li, “Remote authentication schemes for wireless body area networks based on the internet of things,” IEEE Internet Things J., vol. 5, no. 6, pp. 4926–4944, 2018. doi: 10.1109/JIOT.2018.2876133. [Google Scholar] [CrossRef]
25. Y. Liao, Y. Liu, Y. Liang, Y. Wu, and X. Nie, “Revisit of certificateless signature scheme used to remote authentication schemes for wireless body area networks,” IEEE Internet Things J., vol. 7, no. 3, pp. 2160–2168, 2020. doi: 10.1109/JIOT.2019.2959602. [Google Scholar] [CrossRef]
26. D. He, S. Zeadally, N. Kumar, and J. H. Lee, “Anonymous authentication for wireless body area networks with provable security,” IEEE Syst. J., vol. 11, no. 4, pp. 2590–2601, 2017. doi: 10.1109/JSYST.2016.2544805. [Google Scholar] [CrossRef]
27. P. Kasyoka, M. Kimwele, and S. M. Angolo, “Certificateless pairing-free authentication scheme for wireless body area network in healthcare management system,” J. Med. Eng. Technol., vol. 44, no. 1, pp. 12–19, 2020. doi: 10.1080/03091902.2019.1707890. [Google Scholar] [PubMed] [CrossRef]
28. Y. Liu, Y. Wang, and Z. Peng, “A novel and efficient anonymous authentication for wbans,” Internet Technol. Lett., vol. 1, no. 1, pp. 12–19, 2021. [Google Scholar]
29. M. A. Khan et al., “An online-offline certificateless signature scheme for internet of health things,” J. Healthc. Eng., vol. 2020, pp. 1–10, 2020. doi: 10.1155/2020/6654063. [Google Scholar] [PubMed] [CrossRef]
30. I. Ullah, S. Zeadally, N. U. Amin, M. Asghar Khan, and H. Khattak, “Lightweight and provable secure cross-domain access control scheme for internet of things (IoT) based wireless body area networks (WBAN),” Microprocess. Microsyst., vol. 81, no. 1, pp. 103477, 2021. doi: 10.1016/j.micpro.2020.103477. [Google Scholar] [CrossRef]
31. M. A. Khan et al., “A provable and privacy-preserving authentication scheme for uav-enabled intelligent transportation systems,” IEEE Trans. Ind. Inform., vol. 18, no. 5, pp. 3416–3425, 2022. doi: 10.1109/TII.2021.3101651. [Google Scholar] [CrossRef]
32. M. A. Khan, B. A. Alzahrani, A. Barnawi, A. Al-Barakati, A. Irshad and S. A. Chaudhry, “A resource friendly authentication scheme for space-air–ground-sea integrated maritime communication network,” Ocean Eng., vol. 250, no. 110894, Apr. 2022. doi: 10.1016/j.oceaneng.2022.110894. [Google Scholar] [CrossRef]
33. P. Rastegari, M. Khalili, and A. Sakhaei, “Security analysis and improvement of an access control protocol for wbans,” Int. J. Netw. Security, vol. 25, no. 2, pp. 285–296, 2023. [Google Scholar]
34. S. Yu, A. K. Das, Y. Park, and P. Lorenz, “SLAP-IoD: Secure and lightweight authentication protocol using physical unclonable functions for internet of drones in smart city environments,” IEEE Trans. Vehicular Technol., vol. 71, no. 10, pp. 10374–10388, 2022. doi: 10.1109/TVT.2022.3188769. [Google Scholar] [CrossRef]
Cite This Article
 Copyright © 2024 The Author(s). Published by Tech Science Press.
Copyright © 2024 The Author(s). Published by Tech Science Press.This work is licensed under a Creative Commons Attribution 4.0 International License , which permits unrestricted use, distribution, and reproduction in any medium, provided the original work is properly cited.


 Submit a Paper
Submit a Paper Propose a Special lssue
Propose a Special lssue View Full Text
View Full Text Download PDF
Download PDF
 Downloads
Downloads
 Citation Tools
Citation Tools