 Open Access
Open Access
ARTICLE
Vector Dominance with Threshold Searchable Encryption (VDTSE) for the Internet of Things
1 College of Safety Science and Engineering, Xi’an University of Science and Technology, Xi’an, 710054, China
2 College of Computer Science and Technology, Xi’an University of Science and Technology, Xi’an, 710054, China
* Corresponding Author: Jingjing Nie. Email:
Computers, Materials & Continua 2024, 79(3), 4763-4779. https://doi.org/10.32604/cmc.2024.051181
Received 28 February 2024; Accepted 19 April 2024; Issue published 20 June 2024
Abstract
The Internet of Medical Things (IoMT) is an application of the Internet of Things (IoT) in the medical field. It is a cutting-edge technique that connects medical sensors and their applications to healthcare systems, which is essential in smart healthcare. However, Personal Health Records (PHRs) are normally kept in public cloud servers controlled by IoMT service providers, so privacy and security incidents may be frequent. Fortunately, Searchable Encryption (SE), which can be used to execute queries on encrypted data, can address the issue above. Nevertheless, most existing SE schemes cannot solve the vector dominance threshold problem. In response to this, we present a SE scheme called Vector Dominance with Threshold Searchable Encryption (VDTSE) in this study. We use a Lagrangian polynomial technique and convert the vector dominance threshold problem into a constraint that the number of two equal-length vectors’ corresponding bits excluding wildcards is not less than a threshold t. Then, we solve the problem using the proposed technique modified in Hidden Vector Encryption (HVE). This technique makes the trapdoor size linear to the number of attributes and thus much smaller than that of other similar SE schemes. A rigorous experimental analysis of a specific application for privacy-preserving diabetes demonstrates the feasibility of the proposed VDTSE scheme.Keywords
The Internet of Things (IoT) [1] provides safe and controllable real-time online monitoring, positioning, and other service functions. As an important IoT application in the medical field, the Internet of Medical Things (IoMT) can realize efficient and inexpensive healthcare and enhance patient comfort. However, the data involved in continuous monitoring can be massive, and the devices used to collect the data are resource-constrained. As a result, the data is often stored in the cloud, which may seriously violate patient privacy during data collection, storage, and computation. Suspecting the infringement of their healthcare privacy, patients may become reluctant to participate or encrypt their medical data before uploading it to service providers. This raises another question: how to perform a user search about this encrypted private data. In this context, Searchable Encryption (SE) is desirable as a prominent encryption tool for privacy-preserving IoMT [2,3].
Consider a specific example of privacy-preserving diabetes screening (see Fig. 1) in IoMT. In this example, a nurse tries to screen out diabetics from Personal Health Records (PHRs). However, PHRs contain private information, and the patient is unwilling to share them with anyone. Therefore, the patient in this example encrypts the medical record
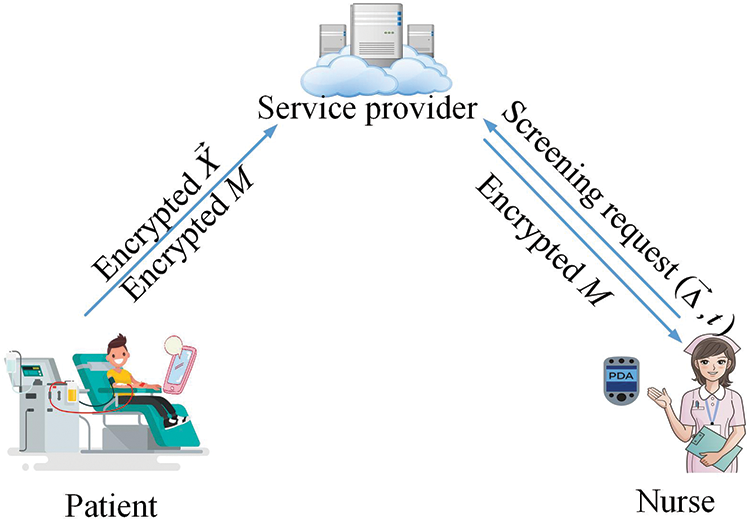
Figure 1: Privacy-preserving diabetes screening
For the application above, it is necessary to solve
Therefore, the proposed VDTSE scheme is favorable for threshold comparison queries in a public-key SE system. When number
The main contributions of this study are outlined below:
• We design a VDTSE scheme supporting comparable attributes that can function for the (t, n)-threshold policy. Although existing schemes [5–8] also support this feature, they are restricted to AND-gates (or (t, t)-threshold). We implement the threshold using a Lagrangian polynomial technique.
• The VDTSE scheme has a shorter trapdoor that makes it more suitable for data storage on mobile devices (such as PDAs). To achieve this, we solve it using our technique modified in Hidden Vector Encryption (HVE) [7], which makes the trapdoor size linear.
• We prove the security, flexibility, and effectiveness of the proposed scheme through theoretical comparison with other schemes. Finally, the experiment shows that the trapdoor size of our method is much smaller than that of other similar SE schemes.
The rest of this paper is structured as below. Section 2 describes the related work of VDTSE. Section 3 contains the preliminaries, while Section 4 presents the scheme construction. Section 5 discusses the security proof for our scheme, Section 6 describes the performance of the proposed scheme, and Section 7 concludes the article and suggests possible future work.
Song et al. popularized the SE scheme [9] that enabled a user to generate both ciphertexts and trapdoors under a symmetric system, so service providers could perform a match search on encrypted information. Under the symmetric system, SE was further improved in [10–12]. In 2004, Boneh et al. [13] considered the first asymmetric SE scheme, Public-key Encryption with Keyword Search (PEKS). The initial public-key SE schemes, however, were limited to test keyword equality. Among these developments, comparative searches received little attention.
To address the aforementioned issue, Boneh et al. [5] created a searchable public-key system called HVE in 2007, which allowed for conjunctive range queries over encrypted data. That same year, Shi et al. [6] proposed a multi-dimensional range SE scheme. However, the aforementioned methods were inefficient and disadvantageous from an operational standpoint. As a result, Park [7] proposed a novel HVE that was effective in prime-order groups significantly smaller than the composite-order groups on the identical level. Later, Park et al. [8] realized a more effective HVE scheme. Although the schemes above supported the AND gate of attribute comparison, they could not apply to arbitrary threshold gates. Fortunately, Sun et al. [14] extended the technique by combining HVE and predicate encryption (PE) for the inner product (called IPE) to achieve threshold comparison queries.
In addition to these references, other scholars addressed the threshold comparison. In 2007, Bethencourt et al. [15] presented a threshold comparison scheme to realize numeric ranges search. In 2018, Attrapadung et al. [16] developed a numeric comparison scheme under the Attribute-Based Encryption (ABE) system. In 2017, Xue et al. [17] constructed a comparable ABE scheme that was more efficient. Although these schemes [15–17] were under the public key system, they could not protect the privacy of
To the best of our knowledge, the only scheme that supported the threshold comparison was [14], but their ciphertext and private key size increased quadratically, posing potential challenges in resource-constrained IoT devices. Therefore, we need to design a more efficient SE scheme.
Assume
1. Bilinear. We have
2. Nondegenerate.
3. Computable.
Therefore, we state that
Decisional Bilinear Diffie-Hellman (DBDH) Assumption. The following describes the DBDH problem: Provided
Augmented Decision Linear (ADLIN) Assumption. Provided
Definition 1. The {DBDH, ADLIN} assumption holds in
Our scheme is characterized by a chosen plaintext security, and ciphertext CT offers no information about the vector
• Initialization (Init).
• Setup.
• Query Phase 1.
• Challenge.
• Query Phase 2.
• Guess.
We define
Definition 2. If the advantage
This section presents the techniques for solving
where
where
When the VDTSE scheme is used in multi-user scenarios, a trusted private service provider needs to be added to receive trapdoors from users and then send the trapdoors to an untrusted public service provider. Therefore, only single-user scenarios are considered in this paper.
Applying the example of privacy-preserving diabetes screening in the Introduction, set
For
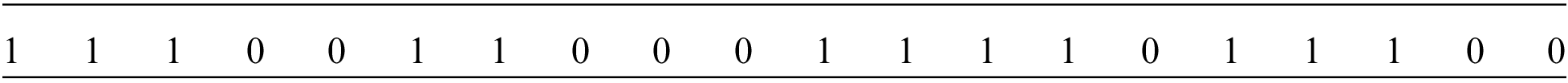
For

Since there are 3 (>t) equal corresponding bits of
•
•
This encryption algorithm ensures the confidentiality of
•
•
Step 1.
Step 2.
When
where
If the DBDH and ADLIN assumptions are met, the VDTSE scheme is selectively secure. The adversary chooses two vectors
When the adversary sends
In our model (the selective security), the adversary performs trapdoor queries for any vector
• Type 1.
• Type 2.
Case 1. Type 1 does not match. Additionally, there is an index
Case 2. Type 1 and Case 1 fail to hold, and there exist
Lemma 1. Suppose that the DBDH assumption holds. In other words, the distinct difference in the advantage of
Proof. Suppose
• Init. At the start of the game,
• Setup.
• Query Phase 1.
Type 1.
Type 2. These two scenarios imply that there exists at least one index
If
If
• Challenge.
where
• Query Phase 2.
• Guess. For the challenge ciphertext,
Lemma 2. Suppose that the ADLIN assumption is true. In other words, the difference in the advantage of
Proof. Consider
• Init. At the start of the game,
• Setup.
• Query Phase 1.
Type 1. This describes the situation with
Type 2. Case 1. Assume
Case 2. Assume
We verify that it is a well-formed trapdoor via random exponents
• Challenge.
where
If
• Query Phase 2.
• Guess.
If
To analyze the vector dominance threshold problem in a public key system, we compare the proposed scheme with the schemes in [5–8] and [14–17] and show the results in Table 1. In [5–8], the authors create searchable public-key systems that support comparison. Unfortunately, these schemes cannot conduct threshold comparisons, which means some of their search results are not flexible. Although the schemes in [14–17] can perform it, the schemes in [15–17] are not attribute-hiding. Besides, the scheme in [14] is not efficient. Our scheme requires a ciphertext size of
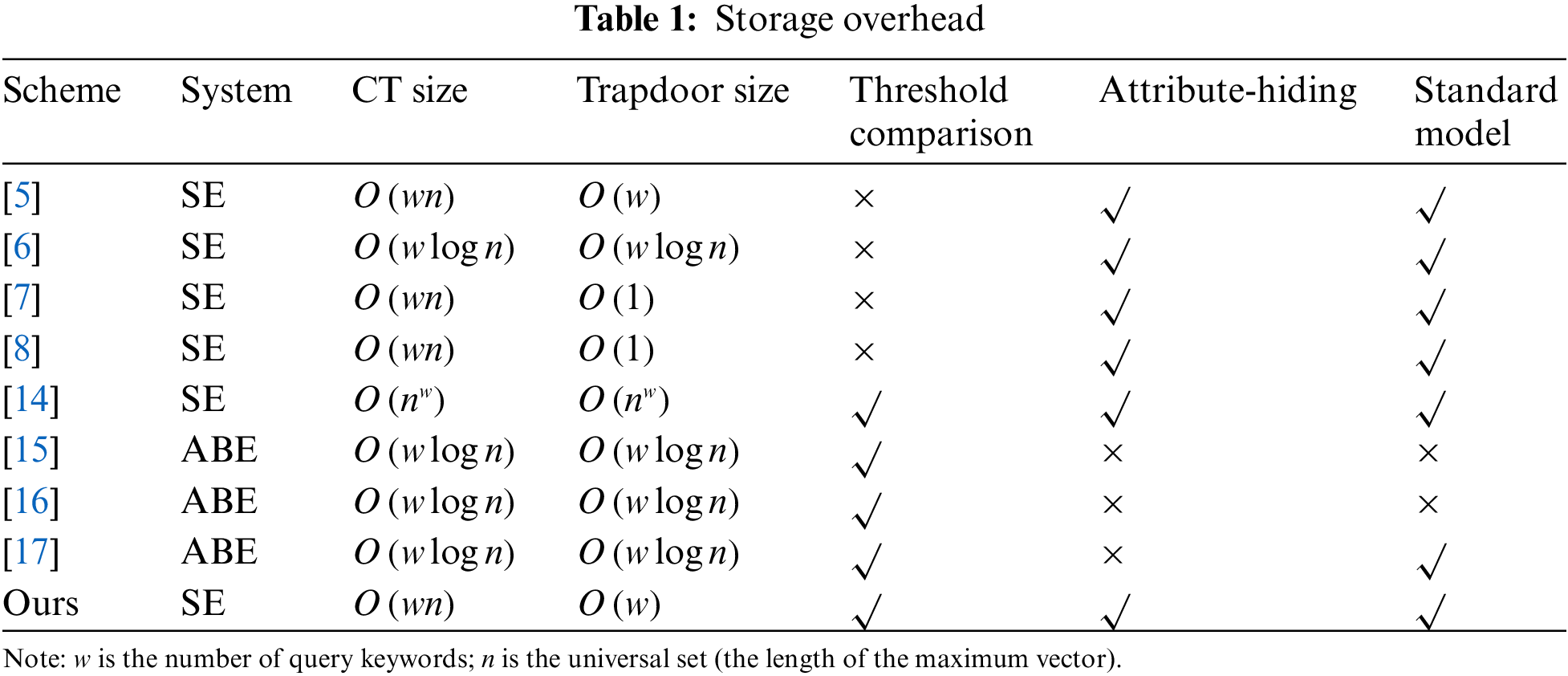
Since the scheme in [14] deals with the same problem and system as our scheme, we make a further comparison between the two in Table 2. The computation tasks involve pairing and exponentiation operations where pairing operations cost the most time.
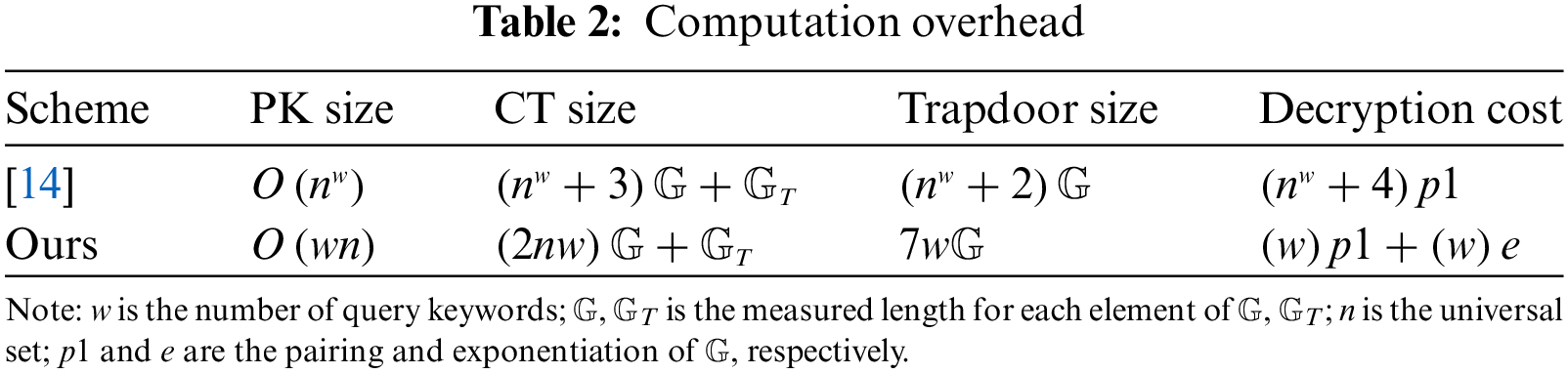
For [14], its PK size expands exponentially with w, while the PK size of our scheme only increases linearly. The ciphertext size (CT size) of [14] requires
To compute the storage overhead, we set
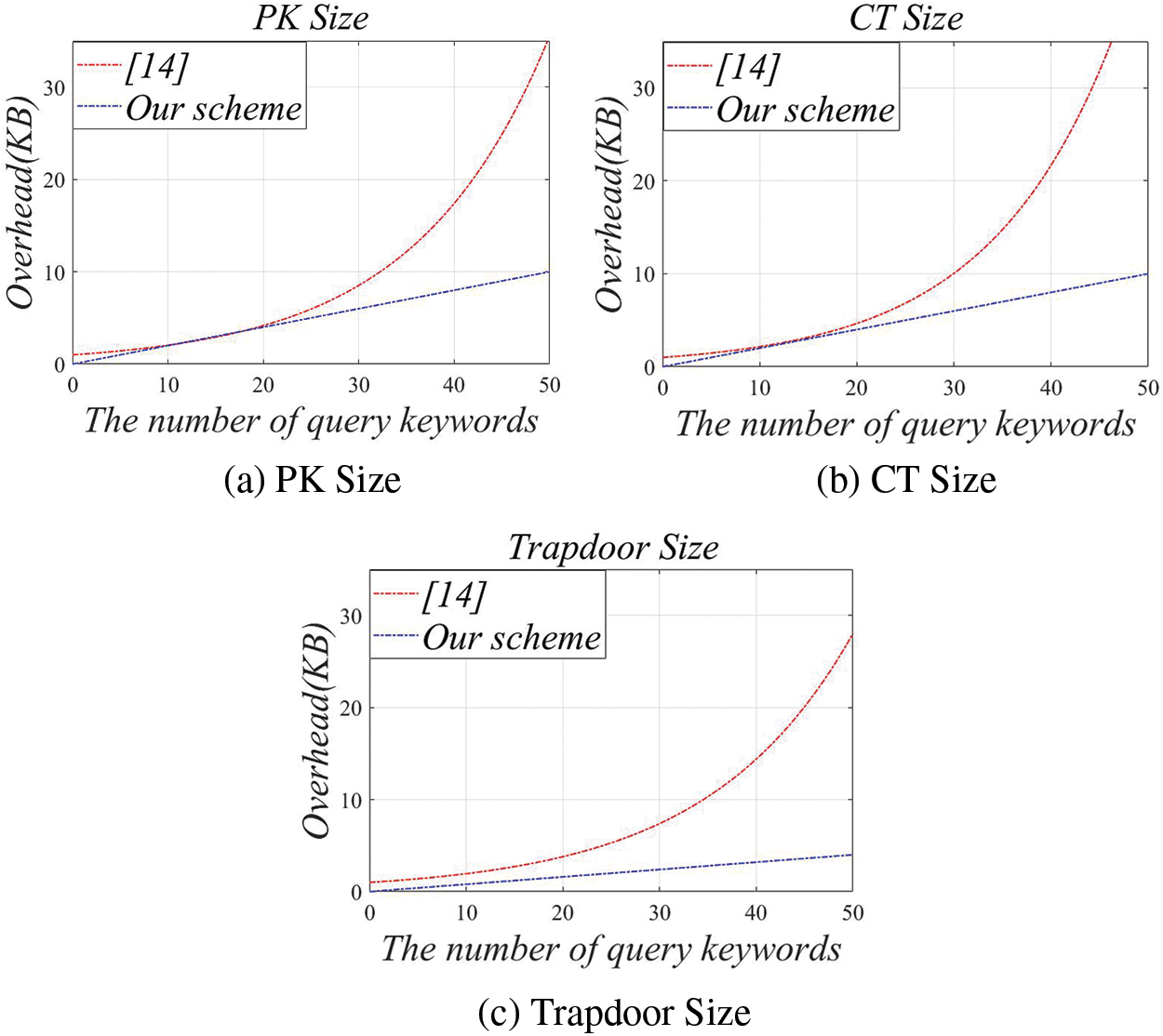
Figure 2: Storage overhead of each parameter as a function of the number of query keywords
We implement the algorithm with C language employing the GNU Multiple Precision Arithmetic (GMP) and Pairing-Based Cryptographic (PBC) libraries. Furthermore, this experiment makes use of the Pima Indians Diabetes Dataset at https://www.kaggle.com/uciml/pima-indians-diabetes-database.
The execution time of the scheme of [14] and our scheme for the KeyGen, PEKS, Trapdoor, and Test algorithms is displayed in Figs. 3a–3d, respectively. The universal set is set to 100. According to [14], as the number of query keywords grows from 0 to 100, the cost time required for KeyGen creation rises from 0.024 to 50 s and the cost time for PEKS generation increases from 0.37 to 300 s. Considering that the generation time of the Trapdoor and Test algorithms is excessive, we change the number of query keywords to 0–50. In [14], the cost time required for trapdoor generation climbs from 0.24 to 500 ms, while the test generation time rises from 0.37 to 600 ms. Our algorithm, however, takes almost no time. The execution time for KeyGen represents the time for PK and SK to be generated, and the PEKS time indicates the ciphertext generation time. The Trapdoor and Test algorithms involve the time of trapdoor generation and the time of cloud server search, respectively.
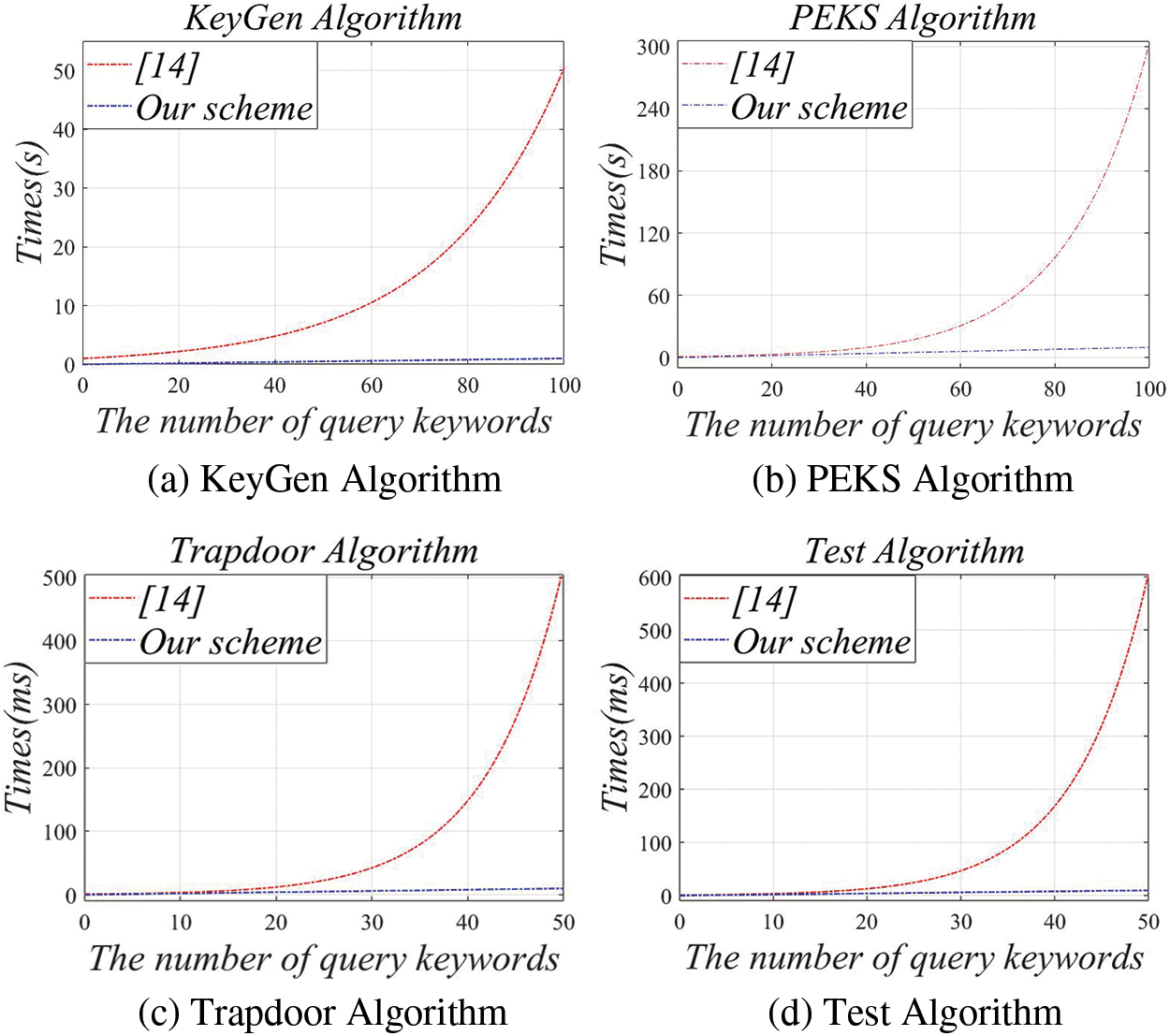
Figure 3: Time cost of each algorithm as a function of the number of query keywords
It can be seen from Fig. 3 that the runtime of our algorithm increases slowly with the increase of query keywords, while the runtime of [14] increases exponentially. The experiment shows that our scheme is more efficient. In addition, our scheme uses real data sets and is carried out on a cloud outsourcing platform, therefore it will be feasible and effective in real-world scenarios.
In addition to the number of query keywords, the varying size of encrypted diabetes data also has a great effect on algorithm performance. As the encrypted data increases, the service provider will continuously run the VDTSE scheme to search until it finds all matched ciphertexts. Therefore, the performance of VDTSE degrades linearly with the increase of encrypted data. Note that although the threshold t has a range, it takes a fixed value every time the algorithm runs so it has no impact on the performance of the scheme.
In theoretical comparison to existing schemes, the proposed VDTSE scheme obtains a shorter trapdoor that makes it more suitable for storage on mobile devices. It supports comparable attributes that can work for the (t, n)-threshold policy. Then, its security, flexibility, and effectiveness are proved through comparison with other SE schemes.
However, there are also some limitations in this research. Although our scheme is more efficient than other existing SE schemes, it does not work well on large real-world datasets. The larger data is transformed into a longer vector, lowering the efficiency. Besides, when dealing with floating data, the scheme converts the floating data to integer data through multiple expansions. For example, 0.1 is expanded 10 times and converted to 1. In addition, the Lagrangian polynomial technique is not efficient in dealing with the vector dominance threshold problem, but it is currently the most suitable technique. We will look for a better technique to solve these issues.
More fascinating, this work inspires some excellent open problems. Firstly, our research does not address video encryption [18,19], which is an engaging research direction. In the future, we will apply SE algorithms to more scenarios, such as images [20] and other situations [21–23]. Secondly, it will be an intriguing path to demonstrate how to reduce the ciphertext size, which appears difficult to achieve at the moment.
Acknowledgement: Not applicable.
Funding Statement: This work was supported in part by the National Natural Science Foundation of China under Grant Nos. 61872289 and 62172266, and in part by the Henan Key Laboratory of Network Cryptography Technology LNCT2020-A07 and the Guangxi Key Laboratory of Trusted Software under Grant No. KX202308.
Author Contributions: The authors confirm that the contributions to the paper are as follows: Study conception and design: Jingjing Nie, Zhenhua Chen; draft manuscript preparation: Jingjing Nie. All authors reviewed the results and approved the final version of the manuscript.
Availability of Data and Materials: The data that support the findings of this study are openly available at https://www.kaggle.com/uciml/pima-indians-diabetes-database.
Conflicts of Interest: The authors declare that they have no conflicts of interest to report regarding the present study.
References
1. Z. Zhou et al., “Blockchain-based secure and efficient secret image sharing with outsourcing computation in wireless networks,” IEEE Trans. Wirel. Commun., vol. 23, no. 1, pp. 423–435, Jan. 2024. doi: 10.1109/TWC.2023.3278108. [Google Scholar] [CrossRef]
2. Z. Shen, F. Ding, Y. Yao, A. Bhardwaj, Z. Guo and K. Yu, “A privacy-preserving social computing framework for health management using federated learning,” IEEE Trans. Comput. Soc. Syst., vol. 10, no. 4, pp. 1666–1678, Aug. 2023. doi: 10.1109/TCSS.2022.3222682. [Google Scholar] [CrossRef]
3. Z. Shen, F. Ding, A. Jolfaei, K. Yadav, S. Vashisht and K. Yu, “DeformableGAN: Generating medical images with improved integrity for healthcare cyber physical systems,” IEEE Trans. Netw. Sci. Eng., vol. 10, no. 5, pp. 2584–2596, Jul. 2022. doi: 10.1109/TNSE.2022.3190765. [Google Scholar] [CrossRef]
4. M. J. Atallah and W. Du, “Secure multi-party computational geometry,” in Proc. 7th Int. Workshop Algorithms Data Struct. (WADS), Providence, RI, USA, Aug. 2001, pp. 165–179. [Google Scholar]
5. D. Boneh and B. Waters, “Conjunctive, subset, and range queries on encrypted data,” in Proc. 4th Theory Cryptogr. Conf. (TCC), Amsterdam, The Netherlands, Feb. 2007, pp. 535–554. [Google Scholar]
6. E. Shi, J. Bethencourt, T. H. Chan, D. Song, and A. Perrig, “Multi-dimensional range query over encrypted data,” in Proc. IEEE Symp. Secur. Priv. (SSP), Berkeley, CA, USA, May 2007, pp. 350–364. [Google Scholar]
7. H. Park, “Efficient hidden vector encryption for conjunctive queries on encrypted data,” IEEE Trans. Knowl. Data Eng., vol. 23, no. 10, pp. 1483–1497, Oct. 2011. doi: 10.1109/TKDE.2010.206. [Google Scholar] [CrossRef]
8. J. H. Park, K. Lee, W. Susilo, and D. H. Lee, “Fully secure hidden vector encryption under standard assumptions,” Inf. Sci., vol. 232, pp. 188–207, May 2013. doi: 10.1016/j.ins.2012.12.034. [Google Scholar] [CrossRef]
9. D. X. Song, D. Wagner, and A. Perrig, “Practical techniques for searches on encrypted data,” in Proc. IEEE Symp. Secur. Priv. (SSP), Berkeley, CA, USA, May 2000, pp. 44–55. [Google Scholar]
10. Y. Zheng, R. Lu, J. Shao, F. Yin, and H. Zhu, “Achieving practical symmetric searchable encryption with search pattern privacy over cloud,” IEEE Trans. Serv. Comput., vol. 15, no. 3, pp. 1358–1370, May 2020. doi: 10.1109/TSC.2020.2992303. [Google Scholar] [CrossRef]
11. Z. Gui, K. G. Paterson, and S. Patranabis, “Rethinking searchable symmetric encryption,” in Proc. IEEE Symp. Secur. Priv. (SSP), San Francisco, CA, USA, May 2023, pp. 1401–1418. [Google Scholar]
12. E. Molla, P. Rizomiliotis, and S. Gritzalis, “Efficient searchable symmetric encryption supporting range queries,” Int. J. Inf. Secur., vol. 22, no. 4, pp. 785–798, Feb. 2023. doi: 10.1007/s10207-023-00667-1. [Google Scholar] [CrossRef]
13. D. Boneh, D. G. Crescenzo, R. Ostrovsky, and G. Persiano, “Public key encryption with keyword search,” in Proc. Int. Conf. Theory Appl. Cryptogr. Tech., Interlaken, Switzerland, May 2004, pp. 506–522. [Google Scholar]
14. D. Sun, C. Boyd, and J. M. G. Nieto, “Predicate encryption for multi-inner-products,” Secur. Commun. Netw., vol. 6, no. 3, pp. 325–339, Mar. 2013. doi: 10.1002/sec.566. [Google Scholar] [CrossRef]
15. J. Bethencourt, A. Sahai, and B. Waters, “Ciphertext–policy attribute-based encryption,” in Proc. IEEE Symp. Secur. Priv. (SSP), Berkeley, CA, USA, May 2007, pp. 321–334. [Google Scholar]
16. N. Attrapadung, G. Hanaoka, K. Ogawa, G. Ohtake, H. Watanabe and S. Yamada, “Attribute based encryption for range attributes,” IEICE Trans. Fundam. Electron., Commun. Comput., vol. 101, no. 9, pp. 1440–1455, Sep. 2018. doi: 10.1587/transfun.E101.A.1440 [Google Scholar] [CrossRef]
17. K. Xue, J. Hong, Y. Xue, D. S. Wei, N. Yu and P. Hong, “CABE: A new comparable attribute-based encryption construction with 0-encoding and 1-encoding,” IEEE Trans. Comput., vol. 66, no. 9, pp. 1491–1503, Sep. 2017. doi: 10.1109/TC.2017.2693265. [Google Scholar] [CrossRef]
18. H. Li, Z. Gu, L. Deng, Y. Han, C. Yang and Z. Tian, “A fine-grained video encryption service based on the cloud-fog-local architecture for public and private videos,” Sensors, vol. 19, no. 24, pp. 5366, Dec. 2019. doi: 10.3390/s19245366. [Google Scholar] [PubMed] [CrossRef]
19. K. M. Hosny, M. A. Zaki, N. A. Lashin, and H. M. Hamza, “Fast colored video encryption using block scrambling and multi-key generation,” Vis. Comput., vol. 39, no. 12, pp. 6041–6072, Dec. 2023. doi: 10.1007/s00371-022-02711-y. [Google Scholar] [CrossRef]
20. M. Liu, J. Fan, and Q. Liu, “Biomedical image segmentation algorithm based on dense atrous convolution,” Math. Biosci. Eng., vol. 21, no. 3, pp. 4351–4369, Feb. 2024. doi: 10.3934/mbe.2024192. [Google Scholar] [PubMed] [CrossRef]
21. H. A. Li, L. Wang, and J. Liu, “Application of multi-level adaptive neural network based on optimization algorithm in image style transfer,” Multimed. Tools Appl., vol. 23, pp. 1–23, Feb. 2024. doi: 10.1007/s11042-024-18451-1. [Google Scholar] [CrossRef]
22. Y. Ju et al., “Reliability-security tradeoff analysis in mmWave ad hoc-based CPS,” ACM Trans. Sens. Netw., vol. 20, no. 2, pp. 1–23, Jan. 2024. doi: 10.1145/3582556. [Google Scholar] [CrossRef]
23. Z. Zhou et al., “Generative steganography via auto-generation of semantic object contours,” IEEE Trans. Inf. Forensics Secur., vol. 18, pp. 2751–2765, Apr. 2023. doi: 10.1109/TIFS.2023.3268843. [Google Scholar] [CrossRef]
Cite This Article
 Copyright © 2024 The Author(s). Published by Tech Science Press.
Copyright © 2024 The Author(s). Published by Tech Science Press.This work is licensed under a Creative Commons Attribution 4.0 International License , which permits unrestricted use, distribution, and reproduction in any medium, provided the original work is properly cited.


 Submit a Paper
Submit a Paper Propose a Special lssue
Propose a Special lssue View Full Text
View Full Text Download PDF
Download PDF Downloads
Downloads
 Citation Tools
Citation Tools