 Open Access
Open Access
ARTICLE
Modeling and Analysis of OFDMA-NOMA-RA Protocol Considering Imperfect SIC in Multi-User Uplink WLANs
1 School of Science, Lanzhou University of Technology, Lanzhou, 730050, China
2 School of Computer & Communication, Lanzhou University of Technology, Lanzhou, 730050, China
* Corresponding Author: Suoping Li. Email:
(This article belongs to the Special Issue: Innovative Security for the Next Generation Mobile Communication and Internet Systems)
Computers, Materials & Continua 2024, 79(3), 5273-5294. https://doi.org/10.32604/cmc.2024.050869
Received 20 February 2024; Accepted 09 May 2024; Issue published 20 June 2024
Abstract
To address the problems of network congestion and spectrum resources shortage in multi-user large-scale scenarios, this paper proposes a twice random access OFDMA-NOMA-RA protocol combining the advantages of orthogonal frequency division multiple access (OFDMA) and non-orthogonal multiple access (NOMA). The idea of this protocol is that OFMDA is used to divide the entire frequency field into multiple orthogonal resource units (RUs), and NOMA is used on each RU to enable more users to access the channel and improve spectrum efficiency. Based on the protocol designed in this paper, in the case of imperfect successive interference cancellation (SIC), the probability of successful competition subchannels and the outage probability are derived for two scenarios: Users occupy the subchannel individually and users share the subchannel. Moreover, when two users share the channel, the decoding order of the users and the corresponding probabilities are considered. Then, the system throughput is obtained. To achieve better outage performance in the system, the optimal power allocation algorithm is proposed in this paper, which enables the optimal power allocation strategy to be obtained. Numerical results show that the larger the imperfect SIC coefficient, the worse the outage performance of weak users. Compared with pure OFDMA and NOMA, OFDMA-NOMA-RA always maintains an advantage when the imperfect SIC coefficient is less than a specific value.Keywords
With the growth of the internet of things (IoT), many wireless devices access the network. Each device initializes the uplink through random access (RA) to establish communication with the base station, as in the work of Hasan et al. [1,2]. However, as the number of access users in the network continues to increase, a large number of devices try to access the base station in a relatively short time. This results in the probability of collision in the whole system becomes larger, and the probability of successfully accessing the channel decreases dramatically, ultimately leading to a decrease in spectrum utilization efficiency, as described by Zhen et al. [3]. Today, improving spectrum utilization efficiency and alleviating congestion are considered to be some of the most urgent requirements in large-scale 5G networks, as noted by Xu et al. [4]. Thus, it is necessary to break the traditional RA model and design a new large-scale RA scheme.
In large-scale communication scenarios, orthogonal frequency division multiple access (OFDMA) technology is currently widely used. By dividing the spectrum resources into multiple orthogonal and non-overlapping subcarrier blocks, these subcarrier blocks are then dynamically allocated to users, achieving multiple users to access and transmit data on the channel simultaneously. For example, Chen et al. [5] improve the throughput in density scenarios by using the characteristics of multi-user uplink OFDMA random access (UORA). Zhou et al. [6,7] propose a DRA-OFDMA protocol which allows users who failed to compete to re-access the unused free spectrum, thus the spectrum resources are utilized and the collision probability is reduced. Fan et al. [8] propose a new UORA access protocol based on IEEE 802.11ax. This protocol improves throughput and reduces packet delay by considering the number of retransmissions, the number of RUs, and the number of STAs to decide whether to double its OCW size. However, OFDMA technology also faces some challenges, as Anand et al. [9] described. For example, with the rapid development of mobile internet and wireless communication, the current communication environment is becoming increasingly complex, and the number of users needing to access the wireless communication network is increasing. However, the number of users cannot exceed the number of available orthogonal channels in the OFDMA scheme, which restricts the improvement of communication quality.
Unlike OFDMA, non-orthogonal multiple access (NOMA) can allocate the same resource to multiple users, like in the work of Li et al. [10,11]. The transmitter employs superposition coding and allocates different power to the users. The receiver then decodes the strong user signal using successive interference cancellation (SIC) technology (other user’s signals are considered interference), as noted by Anand et al. [12]. The decoded user’s signal is removed from the aliasing signal and the weak user’s signal is decoded, which enables more users to access the spectrum resources. Due to the possibility of decoding errors, Luo et al. [13] analyze the performance of the NOMA system in the case of imperfect SIC and evaluate the influence of imperfect SIC coefficients on outage probability and throughput. However, multiple users sharing the same spectrum resource in the system will increase decoding complexity at the receiving end. This is because when the receiver decodes the information of one user, it must first decode the information of the user who has a higher power than the user. In addition, with NOMA superposition coding, there is interference between the signals of different users, which will significantly degrade the outage performance of the system when the number of users is too high. The combination of NOMA and OFDMA technology provides the possibility to overcome the complexity of SIC decoding at the receiver and improve the interrupt performance, which is conducted by Bany Salameh et al. [14]. This is because the available transmission bandwidth provided by OFDMA is divided into multiple orthogonal subchannels to avoid co-channel interference in hybrid OFDMA-NOMA systems. Within the subchannels, more than one user can be served on each channel. This is achieved using the power domain multiplexing provided by NOMA. Therefore, the combination of OFDMA and NOMA enables the multiplexing of both the power domain and the frequency domain, which is expected to further improve the spectrum utilization efficiency and support large-scale transmission, as described by Tang et al. [15,16].
Recently, some literature has studied the potential capability of hybrid OFDMA-NOMA. For example, Rezvani et al. [17] propose a globally optimal power allocation strategy for downlink OFDMA-NOMA systems to maximize the sum rate of the users and the system’s energy efficiency. In this system, users are divided into NOMA clusters, and users within each cluster adopt superposition coding and SIC technology, while users between different clusters transmit on orthogonal subcarriers. A hybrid OFDMA/NOMA transmission scheme is proposed by Guo et al. [18]. The scheme multiplexes multiple subunits through OFDMA to avoid performance degradation due to cochannel interference in NOMA systems. In addition, NOMA significantly improves spectrum efficiency by allowing multiple users to share the spectrum within the same cell. In order to alleviate random access congestion for machine-based communication and to support massive connectivity with lower energy consumption in 5G cellular networks, a massive resource allocation scheme based on NOMA-OFDMA has been proposed by Wu et al. [19]. Tseng et al. [20] add NOMA to the downlink OFDMA video transmission system, and it is proposed to allocate the power to the users on each subcarrier to minimize the sum of the mean square errors, thus improving the peak signal-to-noise ratio and ultimately improve the video quality. A resource allocation scheme based on OFDMA-NOMA is proposed by Hadi et al. [21]. The resource allocation problem is formulated as a non-convex NP-hard optimization problem, which jointly designs subchannel allocation and power allocation to maximize the sum rate. Tutelian et al. [22] consider the joint use of OFDMA and NOMA for uplink transmission in Wi-Fi 6 networks, and the problem of optimal allocation of radio resources among users is posed to maximize some utility functions (such as geometric mean throughput). Promponas et al. [23] design three resource allocation schemes based on game theory principles using OFDMA and NOMA technologies to maximize individual user utility, maximize system utility, and guarantee minimum quality of service (QoS) for users, respectively.
1.1 Motivation and Contribution
Most of the above studies of hybrid OFDMA-NOMA systems were analyzed in the case of perfect SIC. However, hardware damage and decoding errors exist in the communication environment. It motivates the necessity to analyze the performance of OFDMA-NOMA in imperfect SIC. In addition, the research on hybrid OFDMA-NOMA systems mainly focus on the theoretical analysis of resource allocation schemes and power allocation strategies during data transmission, and few studies consider the problems of network congestion and low utilization of spectrum resources. Inspired by Zhou et al. [6], this paper proposes a random access (OFDMA-NOMA-RA) protocol combining OFDMA and NOMA to alleviate access congestion and low spectrum utilization. Different from Zhou et al. [6], we not only let the collision users compete again for the remaining subchannels but also combine OFDMA and NOMA, which breaks the limitation that a subchannel can serve only one user in the work of Zhou et al. [6]. The key idea of the protocol in this paper is: OFDMA divides the entire bandwidth into multiple subchannels, and multiple users can access and transmit data on the same subchannels through the NOMA scheme. In addition, the users who fail to compete can compete again for the remaining subchannels to get a transmission opportunity. Thereby, this paper achieves the research objectives of reducing network congestion and improving spectrum resource utilization under imperfect SIC cases in multi-user networks. The main contributions of this paper are as follows:
• A new OFDMA-NOMA-RA protocol is proposed for multi-user uplink WLAN. The protocol alleviates access congestion and wastage of spectrum resources by allowing users to compete for the remaining subchannels. In addition, the subchannels are orthogonal to avoid cochannel interference, and the NOMA principle is used to superimpose the signals within the subchannels, which enables multiple users to share the same spectrum resource and improves spectrum efficiency.
• Based on the proposed protocol and system, the probability of successfully competing subchannels is derived in the cases of users occupying the subchannel individually and users sharing the subchannel, and the outage probability and throughput are derived in the case of imperfect SIC. In addition, an optimal power allocation algorithm is proposed based on a closed expression for the outage probability, which provides a power allocation scheme to minimize the outage probability.
• To illustrate the superiority of OFDMA-NOMA-RA, this paper derives the probability of successfully competing subchannels and the outage probability of pure OFDMA and NOMA systems respectively. Thus, the system throughput expressions for pure OFDMA and NOMA are obtained.
• We verify the performance of OFDMA-NOMA-RA by numerical analysis. The influence of transmission power on the outage probability and the optimal power for the different users are shown. The effect of imperfect SIC coefficients on interrupt performance is revealed, and numerical results show that OFDMA-NOMA-RA consistently outperforms ODFMA and NOMA when the imperfect SIC coefficients are less than a specific value.
The rest of this paper is organized as follows: Section 2 introduces the system model and describes the details of the designed protocol. Section 3 derives the probability of successfully competing subchannels, outage probability, and system throughput based on the designed protocol and system. Furthermore, the optimal power allocation algorithm is provided. The system throughput expressions of pure OFDMA and NOMA are given in Section 4. In Section 5, we present numerical results to verify the performance analysis. Finally, we conclude the work of this paper in Section 6.
2 System Model and Protocol Design
To overcome the shortcomings of OFDMA and NOMA, this paper combines OFDMA and NOMA, using OFDMA between subchannels and NOMA within subchannels. This allows multiple users to share the same subchannel and avoids outage performance degradation due to cochannel interference and SIC complexity, as shown in Fig. 1. In addition, the combination of OFDMA and NOMA not only increases the number of users who access subchannel, but also alleviates the scarcity of spectrum resources.
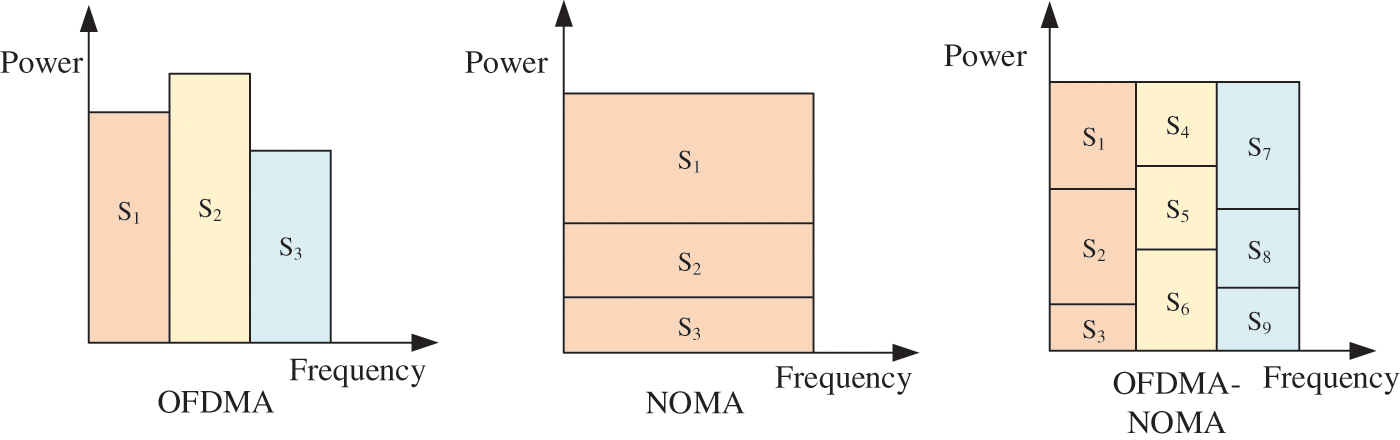
Figure 1: Comparison of the spectrum utilization of OFDMA, NOMA, OFDMA-NOMA
This paper considers the uplink OFDMA-NOMA system in a Basic Service Set (BSS) to analyze and optimize system performance. As shown in Fig. 2, the system consists of a receiver AP and
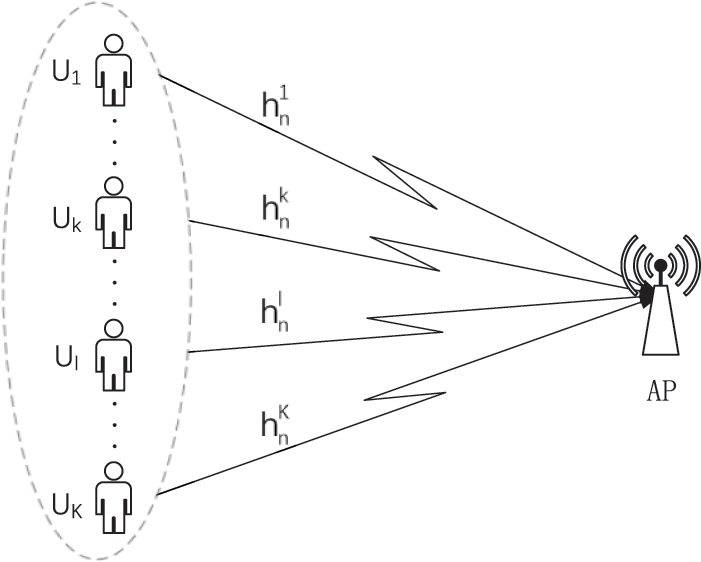
Figure 2: System model for multi-user uplink transmission
Assuming that all subchannels have additive Gaussian white noise (AWGN) with mean 0 and variance
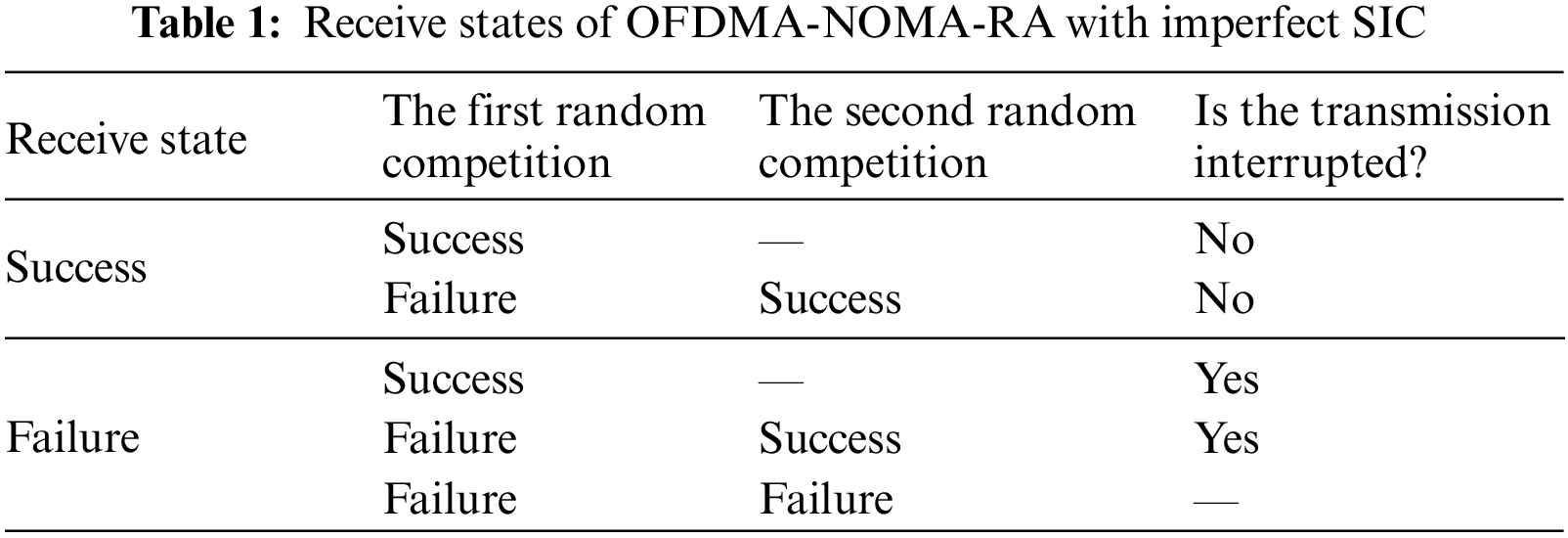
Based on the ideas of Zhou et al. [6], this paper proposes an OFDMA-NOMA-RA protocol in the uplink for the considering system. The protocol adopts two random accesses to compete for the subchannels. The first random access is a fair competition for the subchannels to get the transmission opportunity. Due to the combination of NOMA and OFDMA, a subchannel can be used by two users simultaneously. If the number of users competing for the same subchannel is less than or equal to two, the users compete successfully. Then, the users transmit according to the power and subchannel indicated by the controlling information. When the number of users exceeds 2, the users fail to compete in the subchannel. Therefore, some subchannels may not be used. To fully utilize these remaining subchannels, we allow the users who failed in completion to compete again for these remaining subchannels. Similarly, these remaining subchannels can serve two users at the same time. In addition, users who have successfully competed may be unable to transmit data due to factors such as damaged hardware or decoding errors. Table 1 shows the possible cases of the whole transmission process. If at least one of the two random contentions succeeds and the transmission is not interrupted, the receiver can receive the user’s message correctly.
3 Performance Modeling Analysis
Since the competition is random and the subchannel may be used by one user or shared by two users, this section derives the probability of successfully competing and the outage probability in two random competitions under two conditions of
3.1 The First Random Competition
Since the backoff period is required before random competition, and the backoff mechanism is not the focus of this paper, the OBF backoff mechanism is adopted directly, and the specific details are obtained from Xie et al. [24]. We can obtain the probability of data transmission by Eq. (7) from Xie et al. [24].
where
We can find that
The probability that a subchannel is selected by at least one of users is as follows:
The probability that a subchannel is selected by only one user is
The probability that the user succeeds in competing for the subchannel in the first access, but the user shares the subchannel with another user is:
3.2 The Second Random Competition
The number of users who failed in the first competition is
The probability that a remaining subchannel is selected by only one user is
The probability that the second competition is successful but the user shares the subchannel with another user is:
Combining the results of the two competitions, we can get the probability that the user competes for subchannel
The probability that the user competes successfully for subchannel
Let
where
When
where
When
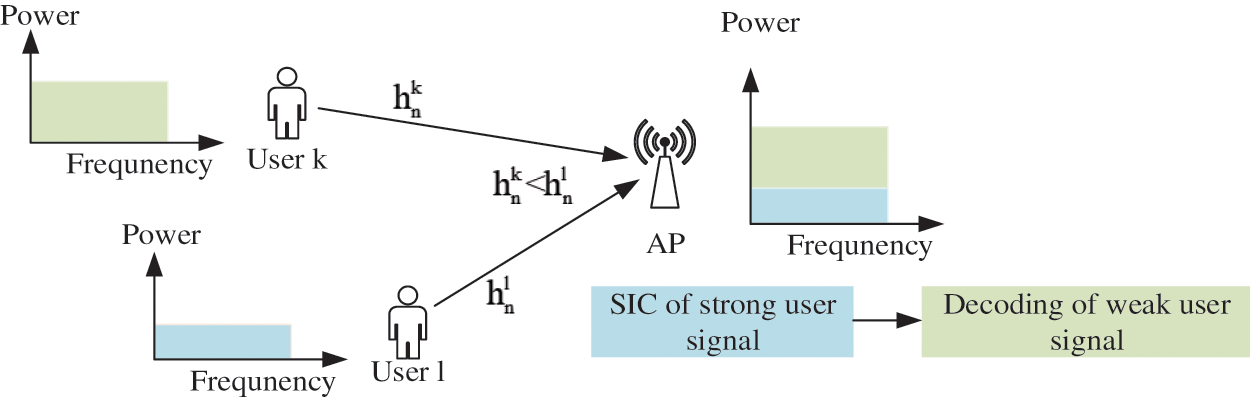
Figure 3: Base station side decoding order in NOMA uplink scenario
Assuming that the signal with higher power at the receiver is the signal of
Imperfect SIC is considered in realistic scenarios due to decoding errors and hardware damage. We model the imperfect SIC errors using Gaussian distribution, inspired by Luo et al. [13], i.e.,
We derive the outage probability due to the channel noise and user’s interference. The probability density functions of
To keep the formula brief,
Similarly, let
When
where
When
The power of user at AP is the product of transmission power and channel gain, i.e.,
Derivation of
The probability of
The probability of
Theorem 1: When
The proof of Theorem 1 is given in Appendix A.
When
When user
where
Theorem 2: The expression of
The expression of
The proof of Theorem 2 is given in Appendix B.
The user’s signal can be successfully received when the user successfully competes for the subchannel and the AP decodes the user’s signal successfully. Thus, the probability of successful reception of the user’s signal can be obtained.
The first term indicates the probability that the user has exclusive access to the subchannel and the transmission is successful. The second term indicates the probability that a strong power user shares a subchannel with another user and the transmission is successful. The third term is the probability of successful transmission when a weak power user shares a subchannel with another user.
In this model, each user transmits signals at a fixed rate, and the throughput depends on the probability of successful competition and the outage probability. Based on the results of the previous analysis, the expression for the system throughput is as follows:
3.5 Optimal Power Allocation Scheme
This section provides an optimization problem that is solved to find the optimal power allocation strategy that minimizes the probability of interruption in order to optimize the system’s performance. Due to the combination of OFDMA and NOMA, users may exclusively access the subchannels or share the subchannels with other users. Therefore, the optimal power allocation strategy is discussed separately in both cases.
3.5.1 User Access to Subchannel Individually
This section presents the power allocation optimization problem in the case of the user exclusive access to the subchannel. The objective is to minimize the outage probability for user
where
3.5.2 Two Users Sharing a Subchannel
This section presents the power allocation optimization problem in the case of users sharing subchannels, assuming
where
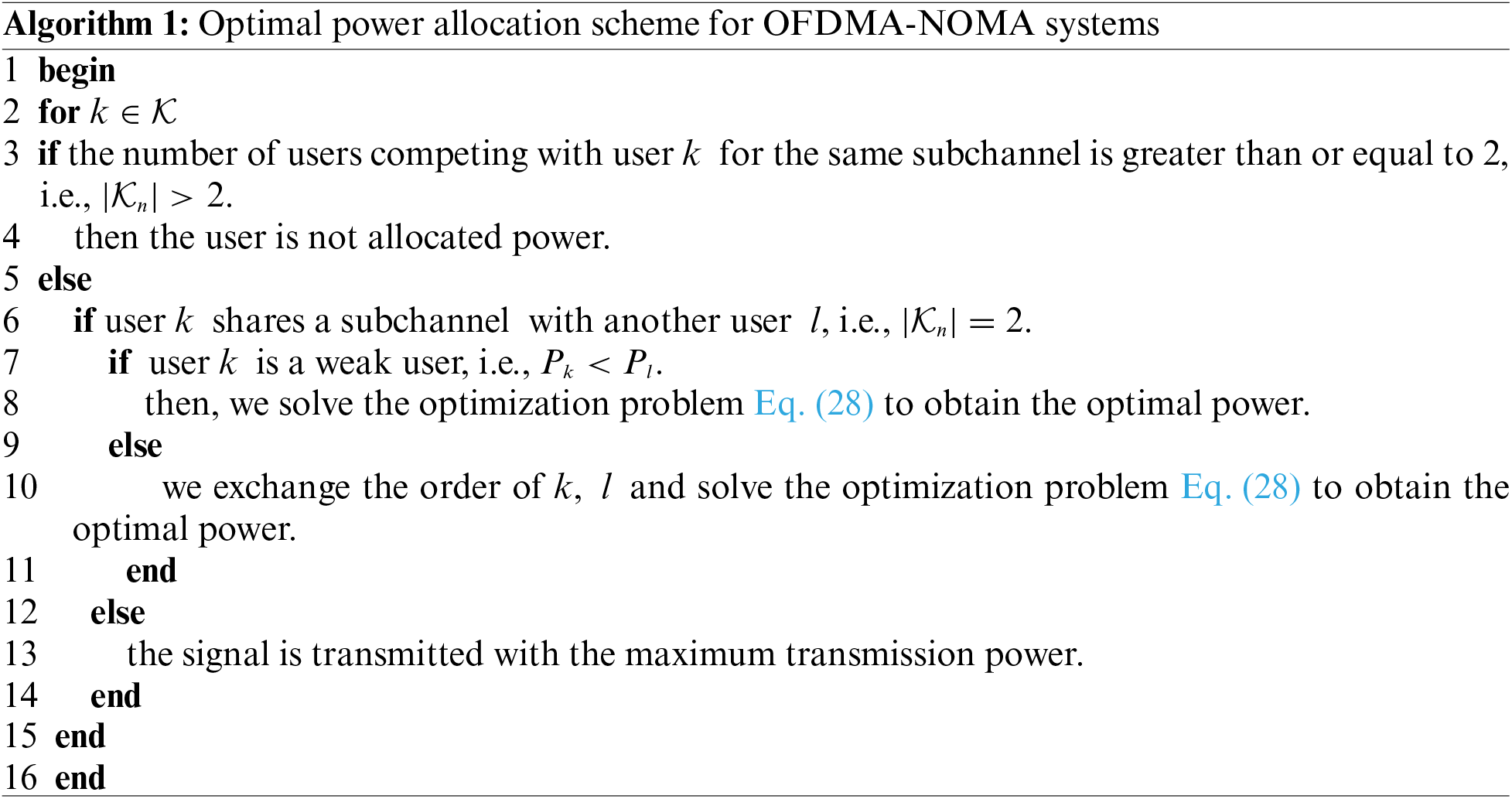
In summary, Algorithm 1 demonstrates the power allocation scheme for multiuser OFDMA-NOMA-RA systems. This algorithm rationally allocates power to users based on the number of users competing for the subchannel. If the number of users exceeds 2, the user cannot access the channel and no power is allocated. When the number of users is 2, the power is allocated to the users according to Eq. (28). When only one user accesses the channel, the maximum power within the allowed range is allocated to the user to ensure successful data transmission.
To demonstrate the superiority of OFDMA-NOMA-RA, the throughput of pure OFDMA and pure NOMA are analyzed in this section.
Different from OFDMA-NOMA-RA system, at most one user is allowed to access the subchannel in OFDMA mode, so the collision probability changes in OFDMA mode. Notably, the transmission probability also varies from the collision probability.
The OFDMA mode is similar to the OFDMA-NOMA-RA mode with
The outage probability of the user in OFDMA mode is the same as the outage probability in the case of OFDMA-NOMA-RA mode with
Compared to OFDMA-NOMA-RA scheme, NOMA allows multiple users to access the entire spectrum simultaneously, so OFDMA-NOMA-RA is synonymous with NOMA when
Similarly, we assume that the maximum number of user accesses is 2. The probability that a user successfully competes for the channel and
Similarly, the probability that a user successfully competes for the channel with
Since the user utilizes the entire spectrum in NOMA mode, the data rate becomes
In this section, numerical results of outage probability and throughput are given by Matlab to validate the performance analysis. Without loss of generality, this section assumes that the number of users
Fig. 4 shows the relationship between the transmission SNR
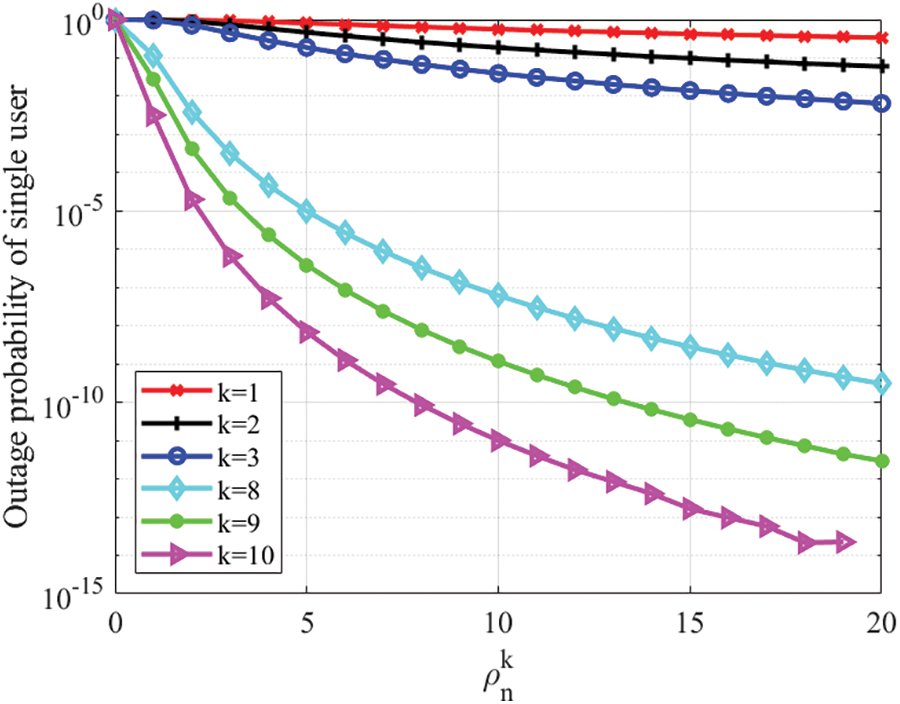
Figure 4: Outage probability vs.
Fig. 5 reveals the relationship between
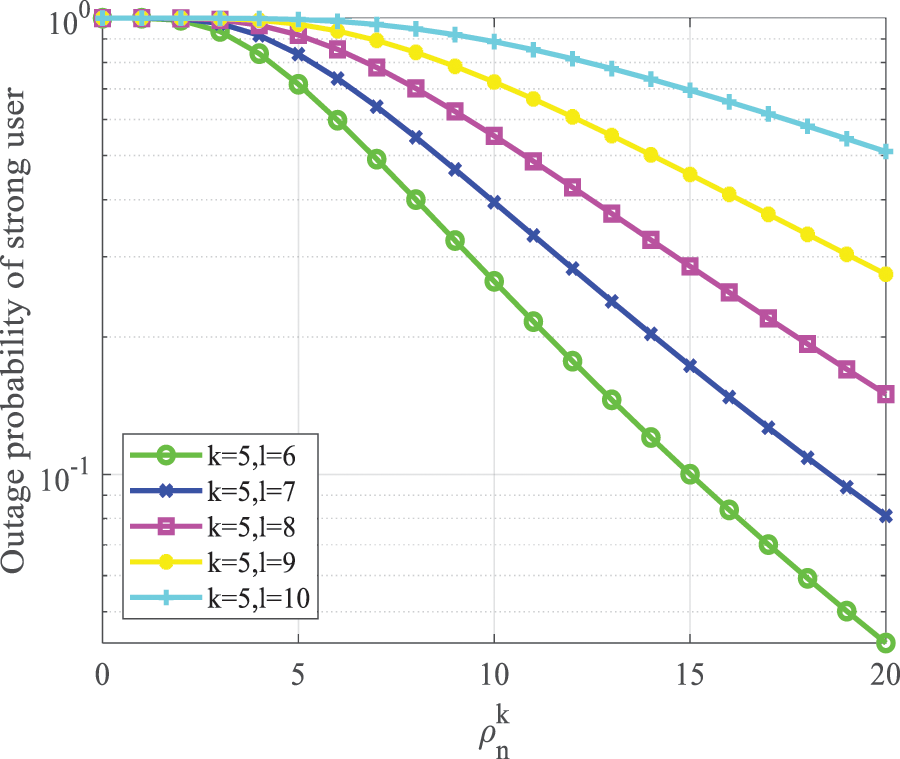
Figure 5: Strong user outage probability vs.
In Fig. 6, the relationship between the interruption probability of weak users and
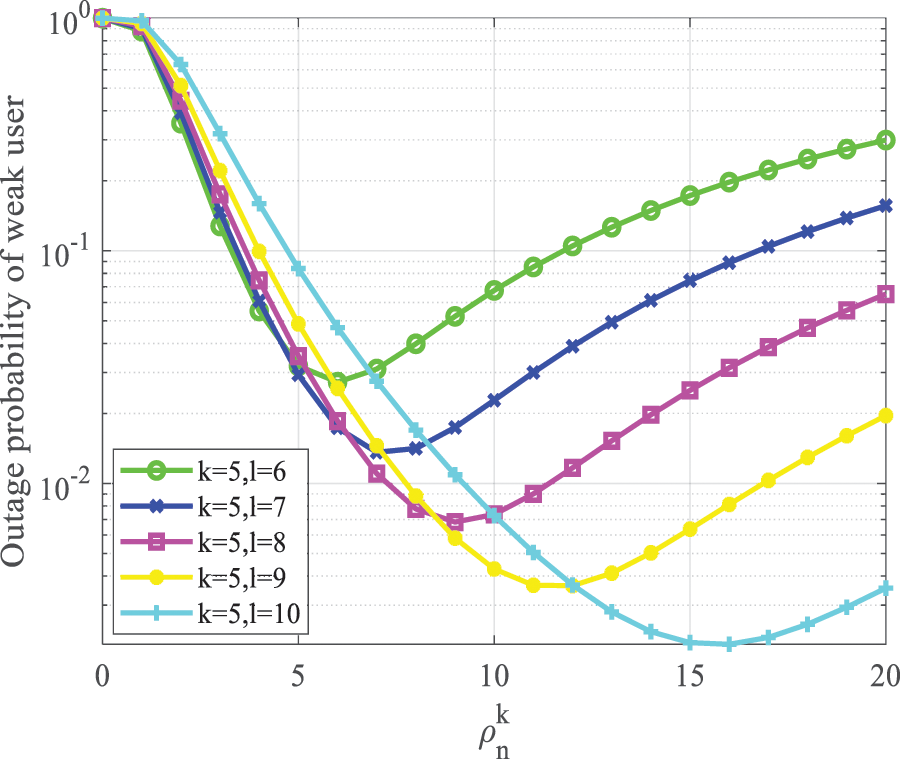
Figure 6: Weak user outage probability vs.
In Fig. 7, the effect of
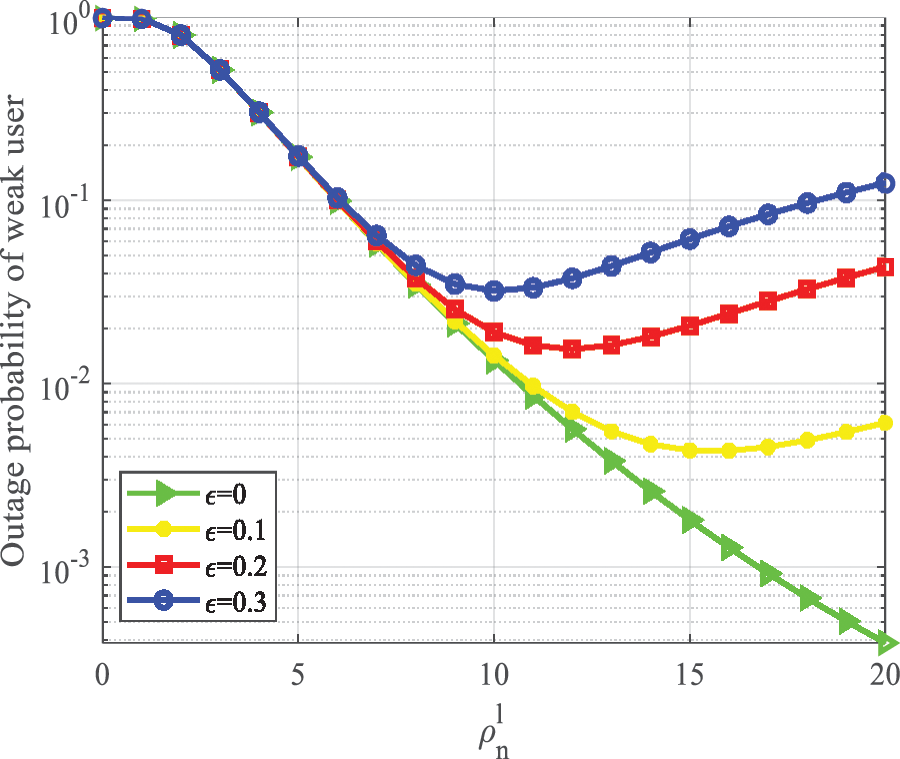
Figure 7: Weak user outage probability vs.
To reveal the optimal power allocation scheme, Fig. 8 shows the effect of
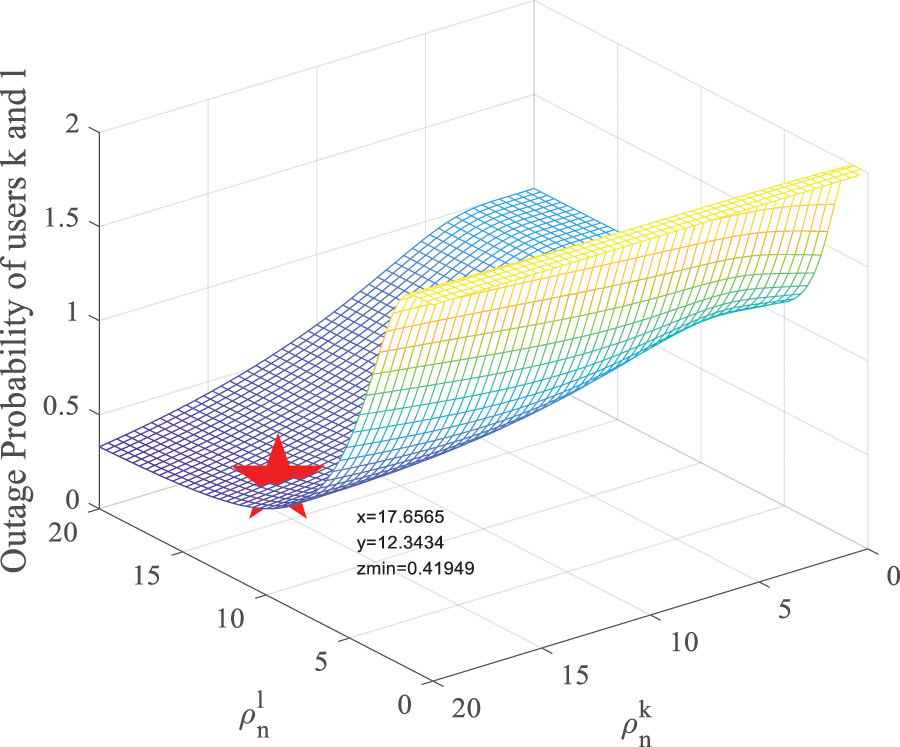
Figure 8: Outage probability vs.
Fig. 9 illustrates the relationship between system throughput and
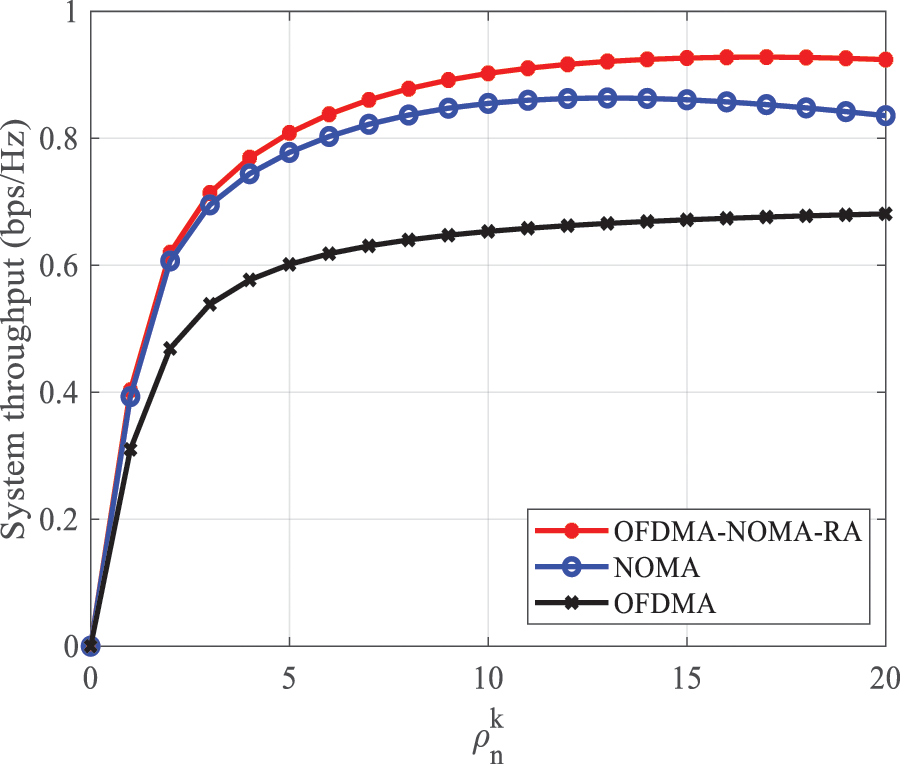
Figure 9: System throughput vs.
Fig. 10 reveals the relationship between the imperfect factor
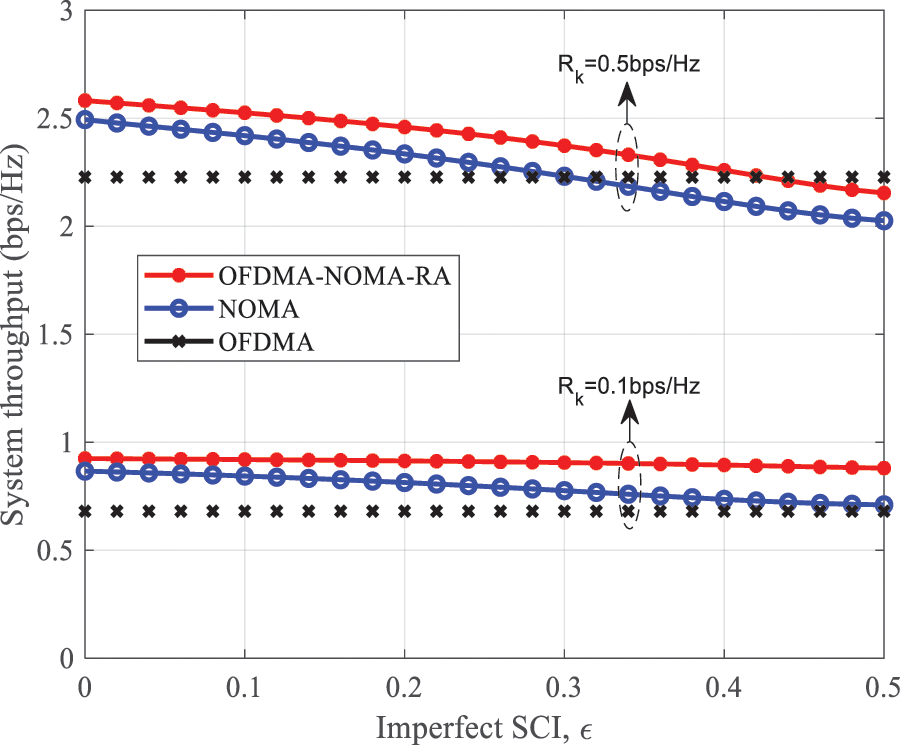
Figure 10: System throughput vs. imperfect SIC factor
To address the issues of network congestion and spectrum wastage in large-scale multi-user scenarios, this paper proposes a new OFDMA-NOMA-RA protocol with two random accesses that combines the advantages of OFDMA and NOMA. The protocol utilizes OFDMA to divide the frequency band into multiple orthogonal subchannels, and NOMA superposition coding is adopted in the subchannels, which realizes multiple users accessing the channel simultaneously and overcomes the SIC decoding complexity in the NOMA multi-user scenario. Based on the proposed protocol, in the case of imperfect SIC, we derive the probability of successfully competing subchannels and the outage probability considering both the user dominates subchannel and the users share subchannel. The decoding order of the users is not fixed when two users share the subchannel. Thus, we consider the decoding order of the users and the corresponding probabilities. Then, the expression of system throughput is derived based on the probability of successful contention for subchannels and the outage probability. In addition, we propose an optimization problem, the optimal power allocation scheme can be obtained by solving the problem to minimize the outage probability. The numerical results demonstrate the superiority of OFDMA-NOMA-RA proposed in this paper compared to pure OFDMA and NOMA when the imperfect SIC factor
Acknowledgement: The authors are thankful to the National Natural Science Foundation of China and Lanzhou University of Technology for funding this work.
Funding Statement: This study was funded in part by the National Natural Science Foundation of China under Grant 61663024 and in part by the Hongliu First Class Discipline Development Project of Lanzhou University of Technology (25-225305).
Author Contributions: The authors confirm contribution to the paper as follows: Study conception and design: Suoping Li, Hailing Yang; data collection: Hailing Yang, Suoping Li, Duo Peng; analysis and interpretation of results: Hailing Yang, Suoping Li; draft manuscript preparation: Hailing Yang, Suoping Li. All authors reviewed the results and approved the final version of the manuscript.
Availability of Data and Materials: The data supporting this article are from previously reported studies and datasets, which have been cited.
Conflicts of Interest: The authors declare that they have no conflicts of interest to report regarding the present study.
References
1. M. Hasan, E. Hossain, and D. Niyato, “Random access for machine-to-machine communication in LTE-advanced networks: Issues and approaches,” IEEE Commun. Mag., vol. 56, no. 6, pp. 86–93, Jun. 2013. doi: 10.1109/MCOM.2013.6525600. [Google Scholar] [CrossRef]
2. L. Zhen, H. Qin, B. Song, R. Ding, and X. Du, “Random access preamble design and detection for mobile satellite communication systems,” IEEE J. Sel. Areas. Commun., vol. 36, no. 2, pp. 280–291, Feb. 2018. doi: 10.1109/JSAC.2018.2804138. [Google Scholar] [CrossRef]
3. L. Zhen, Y. Zhang, K. Yu, N. Kumar, and A. Barnawi, “Early collision detection for massive random access in satellite-based internet of things,” IEEE Trans. Veh. Technol., vol. 70, no. 5, pp. 5184–5189, May 2021. doi: 10.1109/TVT.2021.3076015. [Google Scholar] [CrossRef]
4. Y. Xu, G. Gui, H. Gacanin, and F. Adachi, “A survey on resource allocation for 5G heterogeneous networks: Current research, future trends, and challenges,” IEEE Commun. Surv. Tutor., vol. 523, no. 2, pp. 668–695, Feb. 2021. doi: 10.1109/COMST.2021.3059896. [Google Scholar] [CrossRef]
5. Q. Chen, Z. Weng, X. Xu, and G. Chen, “A target wake time scheduling scheme for uplink multiuser transmission in IEEE 802.11ax-based next generation WLANs,” IEEE Access, vol. 7, pp. 158207–158222, Oct. 2019. doi: 10.1109/ACCESS.2019.2950464. [Google Scholar] [CrossRef]
6. R. Zhou, B. Li, M. Yang, Z. Yan, and A. Yang, “DRA-OFDMA: Double random access based QoS oriented OFDMA MAC protocol for the next generation WLAN,” Mobile Netw. Appl., vol. 24, no. 5, pp. 1425–1436, May 2019. doi: 10.1007/s11036-019-01268-w. [Google Scholar] [CrossRef]
7. S. P. Li, H. L. Yang, R. M. Gao, T. T. Jia, and H. L. Li, “Performance analysis of QoS-oriented OFDMA protocol based on IEEE 802.11 ax for cognitive radio network,” Appl. Sci., vol. 513, no. 12, pp. 7163, May. 2023. doi: 10.3390/app13127163. [Google Scholar] [CrossRef]
8. P. Z. Fan, L. Li, H. Chen, G. Cheng, and L. Yang, “Random access for massive internet of things: Current status, challenges and opportunities,” J. Commun., vol. 42, no. 4, pp. 1–21, Jul. 2021. doi: 10.11959/j.issn.1000-436x.2021098. [Google Scholar] [CrossRef]
9. S. Anand, S. Sabud, A. K. Singh, and P. Kumar, “A use-case efficient DFrFT-based index modulated-OFDM system in the presence of CFO,” Int. J. Electron. Commun., vol. 170, no. 4, pp. 154756, Oct. 2023. doi: 10.1016/j.aeue.2023.154756. [Google Scholar] [CrossRef]
10. S. P. Li, W. W. Liang, V. Pla, N. N. Yang, and S. Yang, “Two-stage adaptive relay selection and power allocation strategy for cooperative CR-NOMA networks in underlay spectrum sharing,” Appl. Sci., vol. 11, no. 21, pp. 10433, Nov. 2021. doi: 10.3390/app112110433. [Google Scholar] [CrossRef]
11. Y. Tian, “A non-orthogonal multiple access and interference mitigation combined strategy in multi-user networks,” Wirel. Pers. Commun., vol. 104, no. 1, pp. 111–128, Oct. 2018. doi: 10.1007/s11277-018-6011-z. [Google Scholar] [CrossRef]
12. S. Anand and P. Kumar, “Low complexity successive interference cancellation receiver for DCT-NOMA-OFDM system with CFO,” Phys. Commun., vol. 58, no. 4, pp. 102053, Jun. 2023. doi: 10.1016/j.phycom.2023.102053. [Google Scholar] [CrossRef]
13. L. P. Luo, Q. Z. Li, and J. L. Cheng, “Performance analysis of overlay cognitive NOMA systems with imperfect successive interference cancellation,” IEEE Trans. Commun., vol. 68, no. 8, pp. 4709–4722, Aug. 2020. doi: 10.1109/TCOMM.2020.2992471. [Google Scholar] [CrossRef]
14. H. Bany Salameh, R. Tashtoush, H. Al-Obiedollah, A. Alajlouni, and Y. Jararweh, “Power allocation technique with soft performance guarantees in hybrid OFDMA-NOMA cognitive radio systems: Modeling and simulation,” Simul. Model. Pract. Theory, vol. 112, no. 4, pp. 102370, Nov. 2021. doi: 10.1016/j.simpat.2021.102370. [Google Scholar] [CrossRef]
15. T. Tang, Y. L. Mao, and G. M. Hu, “A fair power allocation approach to OFDM-based NOMA with consideration of clipping,” Electronics, vol. 9, no. 10, pp. 1743, Oct. 2020. doi: 10.3390/electronics9101743. [Google Scholar] [CrossRef]
16. A. R. Sharief, A. O. Haitham, and B. S. Haythem, “Efficient user-channel pairing with power-domain sum-rate maximization in opportunistic hybrid OFDMA-NOMA IoT systems,” Cluster Comput., vol. 25, no. 4, pp. 2501–2514, Jul. 2021. doi: 10.1007/s10586-021-03365-6. [Google Scholar] [CrossRef]
17. S. Rezvani, E. A. Jorswieck, R. Joda, and H. Yanikomeroglu, “Optimal power allocation in downlink multicarrier NOMA systems: Theory and fast algorithms,” IEEE J. Sel. Areas. Commun., vol. 40, no. 4, pp. 1162–1189, Apr. 2022. doi: 10.1109/JSAC.2022.3143237. [Google Scholar] [CrossRef]
18. X. Y. Guo and Y. Luo, “Hybrid NOMA/OFDMA visible light communication system with coordinated multiple point transmission,” Opt. Express, vol. 30, no. 26, pp. 47404–47420, Dec. 2022. doi: 10.1364/OE.477769. [Google Scholar] [PubMed] [CrossRef]
19. Y. L. Wu, S. Zhang, Z. X. Liu, X. S. Liu, and J. F. Li, “An efficient resource allocation for massive MTC in NOMA-OFDMA based cellular networks,” Electronics, vol. 9, no. 5, pp. 705, Apr. 2020. doi: 10.3390/electronics9050705. [Google Scholar] [CrossRef]
20. S. M. Tseng, W. D. Tsai, and H. S. Suo, “Cross-layer 1 and 5 user grouping/power allocation/subcarrier allocations for downlink OFDMA/NOMA video communications,” Int. J. Commun. Syst., vol. 32, no. 14, pp. e4084, Jul. 2019. doi: 10.1002/dac.4084. [Google Scholar] [CrossRef]
21. M. Hadi and R. Ghazizadeh, “Sub-channel assignment and power allocation in OFDMA-NOMA based heterogeneous cellular networks,” Int. J. Electron. Commun., vol. 120, no. 3, pp. 153195, Jun. 2020. doi: 10.1016/j.aeue.2020.153195. [Google Scholar] [CrossRef]
22. S. A. Tutelian and E. M. Khorov, “Joint usage of OFDMA and NOMA for uplink transmissions in Wi-Fi networks,” J. Commun. Technol. Electron., vol. 67, no. 2, pp. S222–S232, Mar. 2023. doi: 10.1134/S1064226922140108. [Google Scholar] [CrossRef]
23. P. Promponas, C. Pelekis, E. E. Tsiropoulou, and S. Papavassiliou, “Games in normal and satisfaction form for efficient transmission power allocation under dual 5G wireless multiple access paradigm,” IEEE ACM Trans. Netw., vol. 29, no. 6, pp. 2574–2587, Dec. 2021. doi: 10.1109/TNET.2021.3095351. [Google Scholar] [CrossRef]
24. D. H. Xie, J. W. Zhang, A. M. Tang, and X. D. Wang, “Multi-dimensional busy-tone arbitration for OFDMA random access in IEEE 802.11ax,” IEEE Trans. Wirel. Commun., vol. 19, no. 6, pp. 4080–4094, Jun. 2020. doi: 10.1109/TWC.2020.2979852. [Google Scholar] [CrossRef]
25. J. J. Men and J. H. Ge, “Performance analysis of non-orthogonal multiple access in downlink cooperative network,” IET Commun., vol. 9, no. 18, pp. 2267–2273, Dec. 2015. doi: 10.1049/iet-com.2015.0203 [Google Scholar] [CrossRef]
where
where
Cite This Article
 Copyright © 2024 The Author(s). Published by Tech Science Press.
Copyright © 2024 The Author(s). Published by Tech Science Press.This work is licensed under a Creative Commons Attribution 4.0 International License , which permits unrestricted use, distribution, and reproduction in any medium, provided the original work is properly cited.


 Submit a Paper
Submit a Paper Propose a Special lssue
Propose a Special lssue View Full Text
View Full Text Download PDF
Download PDF Downloads
Downloads
 Citation Tools
Citation Tools