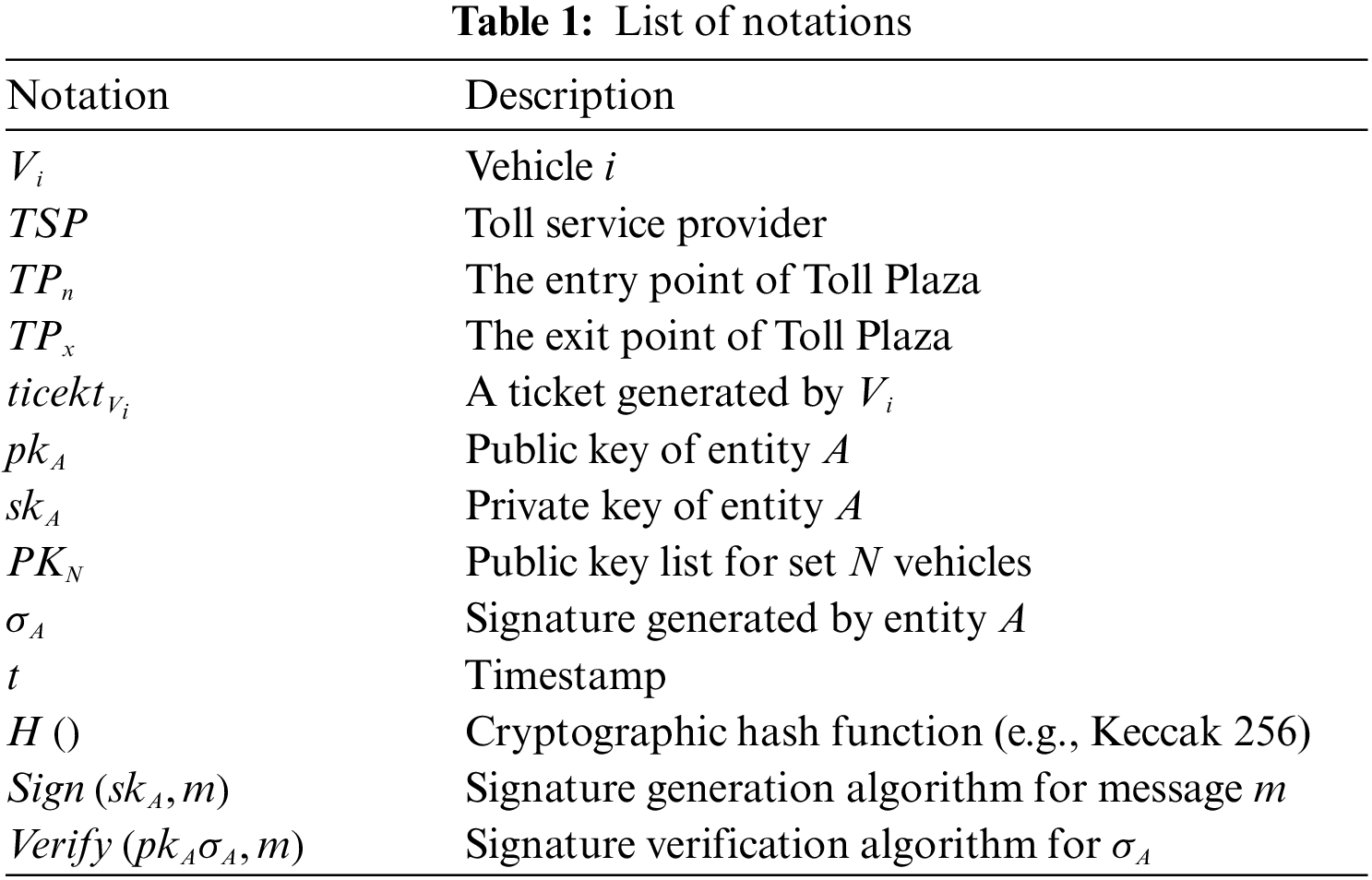
 Open Access
Open Access
ARTICLE
AnonymousTollPass: A Blockchain-Based Privacy-Preserving Electronic Toll Payment Model
1 Department of Electronic & Electrical Engineering, Graduate School, Hanyang University, Seoul, 04763, Korea
2 Department of Electrical Engineering and Computer Science, Khalifa University of Science and Technology, Abu Dhabi, 127788, United Arab Emirates
3 School of Electrical Engineering, Hanyang University, ERICA, Ansan, 15588, Korea
* Corresponding Author: Seung-Hyun Seo. Email:
(This article belongs to the Special Issue: Innovative Security for the Next Generation Mobile Communication and Internet Systems)
Computers, Materials & Continua 2024, 79(3), 3495-3518. https://doi.org/10.32604/cmc.2024.050461
Received 07 February 2024; Accepted 10 April 2024; Issue published 20 June 2024
Abstract
As big data, Artificial Intelligence, and Vehicle-to-Everything (V2X) communication have advanced, Intelligent Transportation Systems (ITS) are being developed to enable efficient and safe transportation systems. Electronic Toll Collection (ETC), which is one of the services included in ITS systems, is an automated system that allows vehicles to pass through toll plazas without stopping for manual payment. The ETC system is widely deployed on highways due to its contribution to stabilizing the overall traffic system flow. To ensure secure and efficient toll payments, designing a distributed model for sharing toll payment information among untrusted toll service providers is necessary. However, the current ETC system operates under a centralized model. Additionally, both toll service providers and toll plazas know the toll usage history of vehicles. It raises concerns about revealing the entire driving routes and patterns of vehicles. To address these issues, blockchain technology, suitable for secure data management and data sharing in distributed systems, is being applied to the ETC system. Blockchain enables efficient and transparent management of ETC information. Nevertheless, the public nature of blockchain poses a challenge where users’ usage records are exposed to all participants. To tackle this, we propose a blockchain-based toll ticket model named AnonymousTollPass that considers the privacy of vehicles. The proposed model utilizes traceable ring signatures to provide unlinkability between tickets used by a vehicle and prevent the identity of the vehicle using the ticket from being identified among the ring members for the ticket. Furthermore, malicious vehicles’ identities can be traced when they attempt to reuse tickets. By conducting simulations, we show the effectiveness of the proposed model and demonstrate that gas fees required for executing the proposed smart contracts are only 10% (when the ring size is 50) of the fees required in previous studies.Keywords
The rapid advancement of intelligent vehicle performance is accelerating the establishment of vehicular services and Intelligent Transport Systems (ITS) [1–4]. An Electronic Toll Collection (ETC) system, which is one of the main pivotal services of the ITS, is a wireless payment system that allows drivers to pass through toll facilities without stopping and paying toll fees [5]. The system facilitates smooth traffic flow and enables efficient traffic management. Due to these advantages, the implementation of ETC Systems is gradually increasing in developing countries such as India FASTag [6], and Pakistan NADRA [7], aimed at providing convenient payment options, improving efficiency, and complying with government regulations on carbon emissions. Accordingly, the market size of the ETC System is expected to increase from $9.2 Billion in 2020 to $17.7 Billion in 2027 [8].
The current ETC System faces two significant challenges. The first challenge is how
Secondly, the vehicle’s travel route is revealed during the electronic toll payment process. electronic toll payments using credit cards are flawed in protecting driver privacy. That is because credit card transaction data can lead to patterns of behavior that can reveal identifying information at any given time. In fact, ETC Systems (e.g., E-ZPass [9], hi-pass [10], and Vietnam Electronic Toll Collection (VETC) [11]) used in many countries make credit card-based payments in a similar way to the use of unique codes. However, this may expose personal information connected to the credit cards themselves. In these systems,
In the design of a secure data sharing model in a distributed environment, blockchain technology can be utilized to provide data traceability, integrity, and distributed ledger functionality. So far, several researchers [14–16] have been working on blockchain-based electronic toll payment systems. Ying et al. [14] proposed a blockchain-based highway electronic toll payment framework for efficient authentication using aggregate signature. Deng et al. [15] designed a smart contract-based electronic toll payment scheme for vehicle-to-RSU transactions. However, the blockchain models proposed in these papers still suffer from the issue of exposing users’ personal information to Roadside Units (RSUs), toll plazas, or other users, as the users’ toll usage records and payment details are directly stored and shared on the blockchain ledger. To preserve a vehicle’s privacy, Guo et al. [16] proposed a blockchain-based privacy-preserving electronic toll payment scheme using zero-knowledge Succinct Non-interactive ARgument of Knowledge (zk-SNARK) and group signature. Nevertheless, the group leader can still trace who generated a signature. Furthermore, the requirement for vehicles to execute smart contract operations for each toll payment is both financially and computationally inefficient.
To hide the user’s toll usage records from other entities such as
1. Blockchain-based ETC Model: We designed the AnonymousTollPass model, a blockchain-based ETC payment system. It eliminates the single point of failure and ensures reliable toll usage data sharing among the participants.
2. Anonymous Tickets: We introduced a method to hide users’ identities with AnonymousTollPass tickets, which is based on the traceable ring signature (TRS) algorithm. When a vehicle uses the ticket, no one, including the
3. Smart Contracts with Lower Costs: We designed two smart contracts, TicketSaleContract and TicketUsageContract, to handle ticket usage history. These smart contracts demonstrate cost efficiency that improves with ring size; as the ring size increases, the operational cost decreases. With a ring size of 50, the proposed smart contract requires only about 10% of the gas fees compared to those used in previous studies.
The rest of this paper is organized as follows: We discuss related works for ETC Systems in Section 2. We describe overall model including security requirements and AnonymousTollPass ticket in Section 3. We propose two smart contract systems and a basic protocol of our AnonymousTollPass model in Section 4. Then, we provide security analysis in Section 5. Also, we provide the performance evaluation of our model in Section 6. We discuss a case study of South Korea in Section 7. Finally, we conclude this paper in Section 8.
2.1 Text Layout Electronic Toll Collection for ITS
An ITS is an advanced transportation system that integrates communication, sensors, AI, and other intelligent technologies into legacy transportation systems to provide innovative applications. Accordingly, various studies [18–21] have been conducted to enhance user convenience through data management systems that collect and analyze transportation information. Borges et al. [18] proposed a privacy-preserving ETC scheme that utilizes a protocol called “Priced Oblivious Transfer” (POT) [19]. To use the POT protocol, the service provider needs to prepare tickets for all possible entrances when a vehicle exits the highway. It has a significant time overhead as all vehicles must use the system simultaneously. Randriamasy et al. [20] proposed an ETC model for vehicles equipped with C-ITS (Cooperative intelligent transport system) devices. They identified the vehicle’s geolocation at a toll plaza with a barrier environment and automatically opened the barrier for vehicles that successfully paid the toll. In this model, it requires an additional device. Aung et al. [21] proposed a system that reserves planned roads to alleviate congested traffic environments. Instead of collecting tolls, they used the T-coin (Traffic coin) they proposed to provide rewards for using alternative routes based on traffic congestion. References [20, 21] proposed an efficient ETC System, but they did not address the issue of user privacy exposure. Additionally, since the systems of [19–21] operate with a single central server, they have the issue of a single point of failure.
2.2 Blockchain-Based Electronic Toll Collection System
Blockchain means a distributed ledger technology in which multiple nodes that do not trust each other store a ledger without a trusted agency [22]. Using a cryptographic hash function and electronic signature, the recorded transactions’ order and contents in the ledger cannot be modified, providing data integrity. Blockchain technology plays a significant role in various fields that require safe data sharing and storage, such as vehicular networks [1], healthcare [23], and smart cities [24]. Also, researchers have conducted studies on integrating blockchain technology into the ETC System, which operates as a distributed system involving

Figure 1: General blockchain-based ETC Systems
Ying et al. [14] suggested a blockchain-based efficient highway toll paradigm considering vehicle platoons. In the model, a vehicle platoon leader pays the toll fee for all platoon members simultaneously by applying an aggregate signature algorithm, enabling efficient vehicle toll payment. Deng et al. [15] proposed two electronic payment schemes, including a vehicle-to-RSU (V-R) transaction and a vehicle-to-RSUs (V-Rs) transaction. Vehicles conduct toll payments through a smart contract and RSUs. Chiu et al. [25] proposed a blockchain-based electronic toll collection system using a practical byzantine fault tolerance (PBFT) algorithm as a consensus algorithm for fast transaction processing. Xiao et al. [26] suggested a blockchain-based toll collection system for public sharing using edge nodes. In order to reduce the overhead of an edge node when there are a large number of toll payment requests, the authors applied a proxy server and greedy algorithm for efficiently matching the edge node and vehicle. Shukla et al. [27] proposed a deep learning-based dynamic toll pricing scheme. The proposed model predicts vehicle traffic and determines the toll payment amount according to lane type and vehicle class. References [14, 15, 25–27] proposed a blockchain-based electronic toll payment model. However, the vehicle’s public key, vehicle ID, and location of the toll plaza are stored in the blockchain so attackers can track a driver’s private information and driving routes. To overcome the limitation, some studies concern blockchain-based electronic toll systems, considering vehicle privacy. Wang et al. [28] designed a credit electronic toll collection system, including an evidence chain framework. Vehicle information is stored in a trusted storage center, and the evidence is recorded in the blockchain. However, RSUs and toll stations still know the driver’s personal information and payment history. Guo et al. [16] proposed a blockchain-based privacy-preserving payment scheme. The proposed scheme protects the vehicle’s location privacy by hiding the toll station information the vehicle has passed through by using zk-SNARK (zero-knowledge succinct non-interactive argument of knowledge) proof and a group signature algorithm. Nevertheless, a group leader can know who generates a signature according to the characteristics of the group signature. Therefore, the vehicle’s driving route may be revealed regardless of the vehicle’s will. In addition, vehicles should participate as a blockchain node and execute a payment smart contract whenever they start or end the toll service. So, vehicles must update and store the blockchain ledger in real-time, which burdens them due to their limited memory, low computing power, and mobility.
To effectively protect the privacy of vehicles from other vehicles, RSUs, and toll plazas, we propose a blockchain-based toll payment model utilizing a traceable ring signature that can safely hide the vehicle’s toll plaza usage information. Also, vehicles with relatively low computational power and memory capacity do not participate as blockchain nodes in our proposed model. So, the smart contract only stores ticket information to lower the execution costs of the smart contract.
In this section, we define the entities and threat models in the proposed model. We also present the security requirements and describe how we design AnonymousTollPass model.
The proposed model is based on a private blockchain in which
• Registration Authority
• Vehicle
• Toll Service Provider
• Toll Plaza
In the proposed model, a
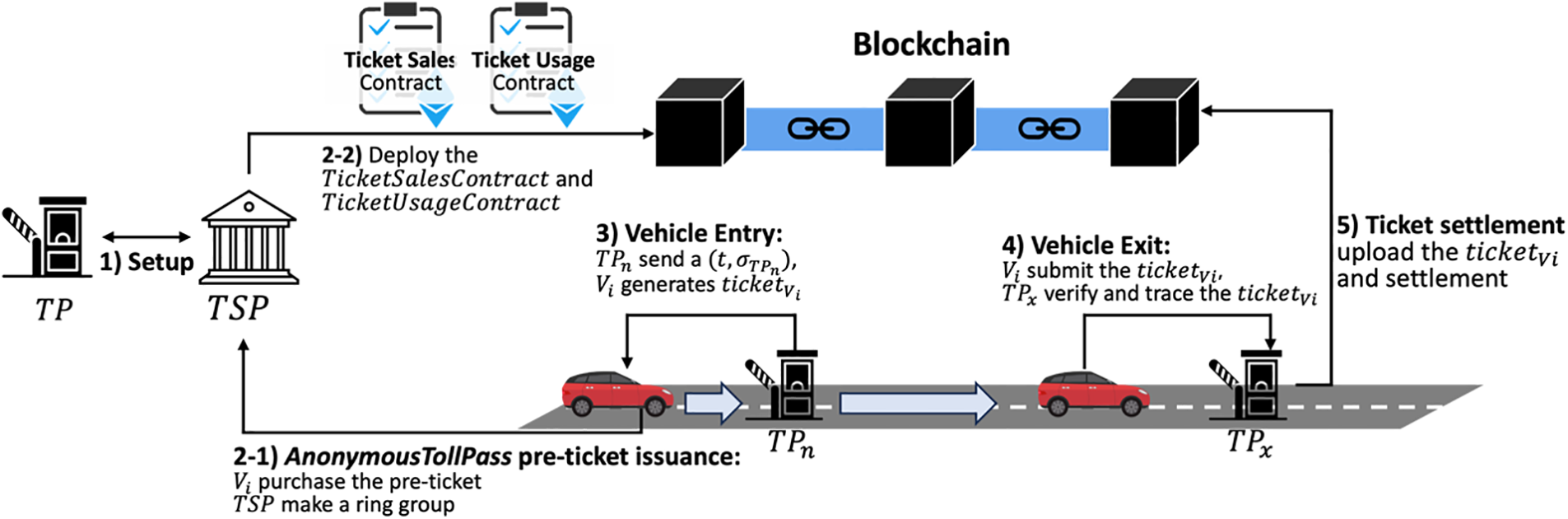
Figure 2: Overall model
3.2 Threat Model & Security Requirements
In the proposed model, we classified the threat models into three categories: A malicious
1. Identity Privacy: When a
2. Ticket Unlinkability: An attacker may attempt to infer the
3. Resistance to distance forgery: The AnonymousTollPass ticket price is proportional to the distance traveled by the
4. Abuse of tickets: A malicious
In this paper, we propose an AnonymousTollPass ticket to preserve vehicles’ privacy in the blockchain-based electronic toll payment model. The AnonymousTollPass ticket is a one-time toll ticket generated based on the traceable ring signature (TRS) algorithm [17]. The identity of each
•
•

•

•

In this section, we first propose our smart contract system for managing AnonymousTollPass tickets. Then we present a basic protocol for our AnonymousTollPass model in detail.
The smart contract system for AnonymousTollPass model consists of TicketSaleContract and TicketUsageContract. A
The
• ring_size: It is the number of
• pk_list: It is the public key list of the ring members.
• ticket_price: It is the price of the AnonymousTollPass ticket.
These ticket-related data are stored in the blockchain through the Register_ticket_information() function and can be checked through the Read_ticket_information() function.
• Register_ticket_information(): This is a function to record AnonymousTollPass ticket information on the TicketSaleContract. Since only the
• Read_ticket_information(): This is a function to check the information of the AnonymousTollPass ticket. The

The
• timestamp: It is the timestamp of when a
• signature: It is the signature of the AnonymousTollPass ticket that the
• verification_result: If the ticket verification is successful, ‘True’ is stored. Otherwise, ‘False’ is stored.
The variables used in the TicketUsageContract are as follows:
• address[] TP_address: This is an array that stores the addresses of
• ticket_state[] request_ticket: This is an array that stores the ticket_state of the tickets that have been requested for exchange from the
• ticket_state[] used_ticket: This is an array that stores the ticket_state of the used tickets.
• mapping(address
• string[] trace_pubkey: This is an array that stores the public key of
The description of the five functions of the TicketUsageContract is as follows:
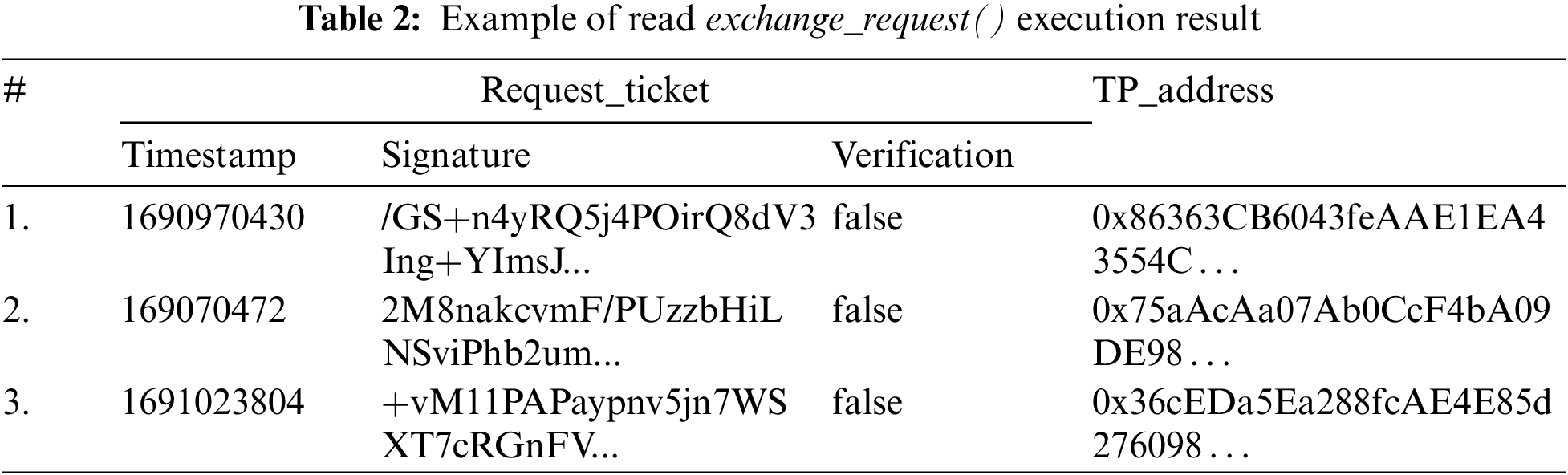
• Exchange_request(): The
• Verify_ticket(): The
• Read_request_ticket(): This is the function to check the request_ticket list. The
• Read_used_ticket(): This function checks already used ticket sets. The
• withdraw(): This function allows

The basic protocol for AnonymousTollPass model consists of five steps: (1) Registration, (2) AnonymousTollPass pre-ticket issuance, (3) Vehicle Entry, (4) Vehicle Exit, (5) Ticket settlement. The list of notations is shown in Table 1. We assume that all participants, such as a toll service provider
The Toll Service Provider
4.2.2 AnonymousTollPass Pre-Ticket Issuance
The
Each
The
In this phase,
Then,
In the Vehicle Exit phase,
Also,
Then,
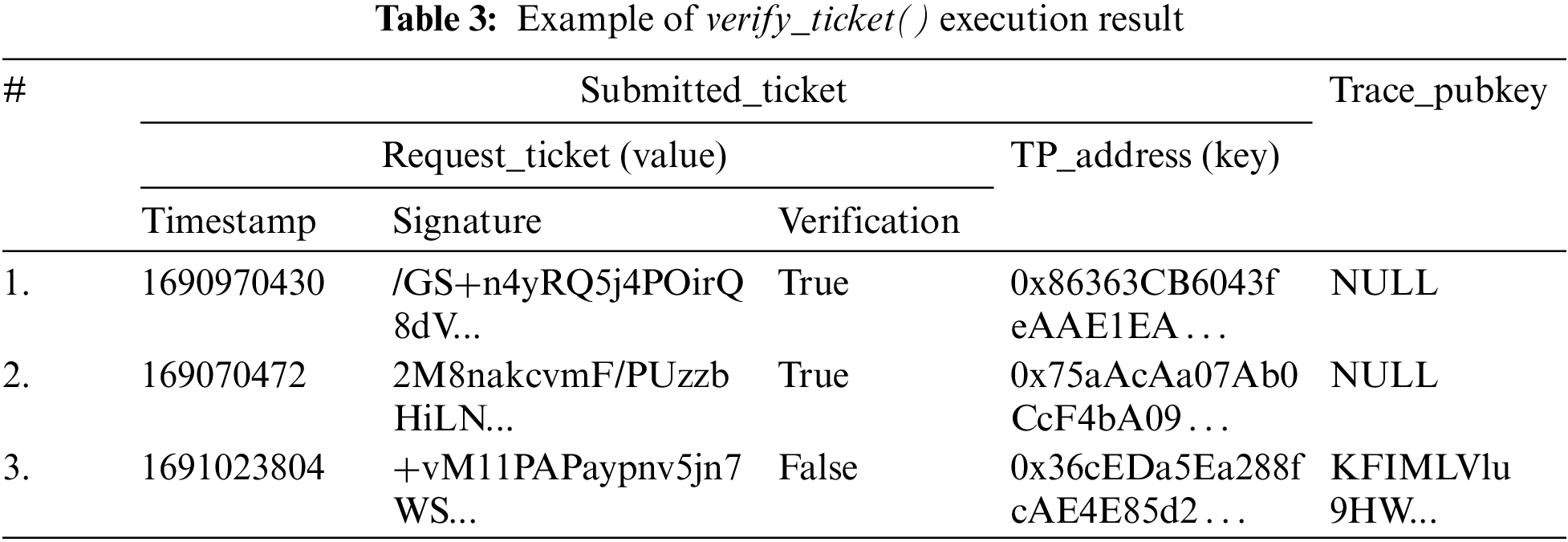
All results must be ‘indep’ to pass the verification. After verification,

Figure 3: The transaction of exchange_request() on remix IDE
The size of
In the Ticket Settlement phase, the
For tickets that pass the verification, the

Figure 4: The transaction of verify_ticket() on Remix IDE
5 Security and Privacy Analysis
The proposed protocol provides privacy-preserving authentication through AnonymousTollPass ticket. A curious
When a vehicle uses multiple AnonymousTollPass tickets, if the tickets used by the vehicle are linked, the vehicle’s route could be exposed. Therefore, the tickets used by a single vehicle must be unlinkable to each other. A curious participant can try to infer if a
5.3 Resistance to Distance Forgery
A malicious
The used AnonymousTollPass tickets cannot be reused, and it should be possible to reveal the identity of a vehicle that maliciously reused a ticket. Malicious
Previous blockchain-based ETC Systems [14–16,25–28] exposed vehicles’ toll usage information directly on the blockchain. In [16], they proposed the first ETC System that provides privacy for vehicles. Related studies of blockchain-based ETC Systems are outlined in Table 4. In this section, we demonstrate that our proposed smart contract systems for the AnonymousTollPass model have more efficient performance compared to [16].
We implemented our smart contract systems by using Remix v0.8.7 [39], and then deployed the smart contract using Ganache v2.5.4 [40] and a virtual Ethereum test blockchain. The deployed smart contract was executed using Python v3.9.1 [41]. We utilized a laptop equipped with Mac OS Monterey v12.5.1, an Intel Core i7 1.2 GHz CPU and 16 GB of RAM for the experiments. Our experimental scenario refers to the actual ETC System in South Korea called Hipass to realistically set the maximum allowable time parameters for AnonymousTollPass ticket generation and verification. In South Korea’s ETC System, there is a speed limit of 30 km/h near the tollgate and DSRC (Dedicated Short Range Communication) based on IEEE 802.11 standard with a communication range of up to 90 m. So, we assume that the vehicle communicates with the
Fig. 5 shows the execution time of the ticketTRACE phase according to the number of used tickets when the ring size is 50. As the number of used tickets increases, the time also increases because more tickets must be checked for reuse. The time it took to check the reusability of the last ticket when there were 49 used tickets was approximately 2.5 s.

Figure 5: The ticket verification time according to the number of used tickets
Fig. 6 shows the execution time of each phase according to the ring size. As the ring size increases, the key size used in the ticketGEN and ticketVER phases increases, resulting in increased computation time. When the ring size is 50, the ticketGEN phase takes 81 ms, the ticketVER phase takes 79 ms, and the ticketTRACE phase takes 1737 ms. The total time required is approximately 3.3 s, which is less than the previously assumed 3.5 s requirement. Therefore, our AnonymousTollPass system can be applied effectively in a real-world situation.
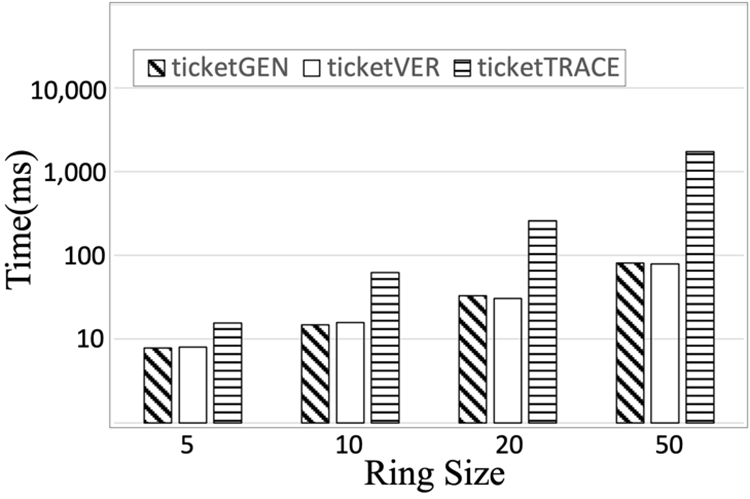
Figure 6: The performance of each AnonymousTollPass algorithm according to the ring size
We also measured the key size for each phase of the AnonymousTollPass model. The result is shown in Fig. 7. The key size increases linearly as the ring size increases. When the ring size is 50, the key size in the ticketGEN phase is about 8.6 MB, and in the ticketVER phase, it is about 13 MB, which is a reasonable size.

Figure 7: The key size of each AnonymousTollPass algorithm according to the ring size
Table 5 shows the gas fees consumed by the three main functions of the TicketSalesContract and TicketUsageContract in our smart contract system. For register_ticket_information(), the gas fee increases as the ring size increases, with 387,824 for a ring size of 5 and 2,056,796 for a ring size of 50, as more information is registered with larger ring sizes. For exchange_request(), the gas fee is the same for each ticket, with 17,260 gas consumed when the function is executed. For verify_ticket(), the gas fee increases slightly as the ring size increases, with 5,467,598 gas consumed for a ring size of 5 and 5,524,174 for a ring size of 50.
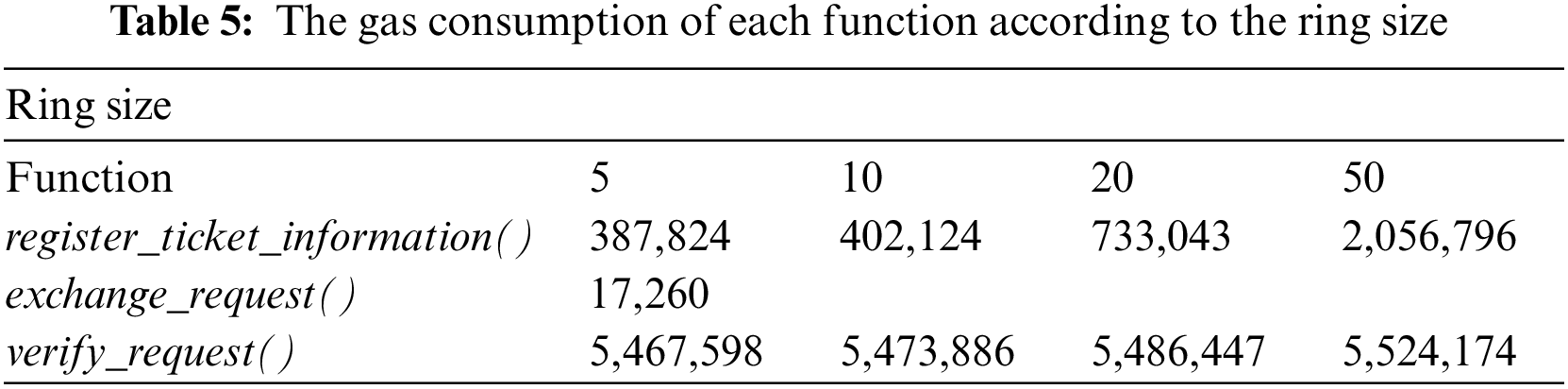
Table 6 compares the total gas fees and ether costs consumed by the functions for each number of vehicles with Vehiclock [16]. The gas fees consumed in the proposed smart contract system were calculated based on the average gas fee consumed when executing functions of the TicketSalesContract and TicketUsageContract, with ether cost calculated by converting 1 gas to 1 gwei. The total gas fee is calculated through register_ticket_information() + (exchange_request() * ring size) + verify_ticket(). As the ring size increases, more information about the ring members is stored in the blockchain and the number of used tickets increases, so the total gas fee increases as well. However, setting the ring size to 50 rather than 10 for creating 5 rings can reduce the total gas fee. In [16], all signature generation and verification processes are performed on the smart contract and recorded in the blockchain.
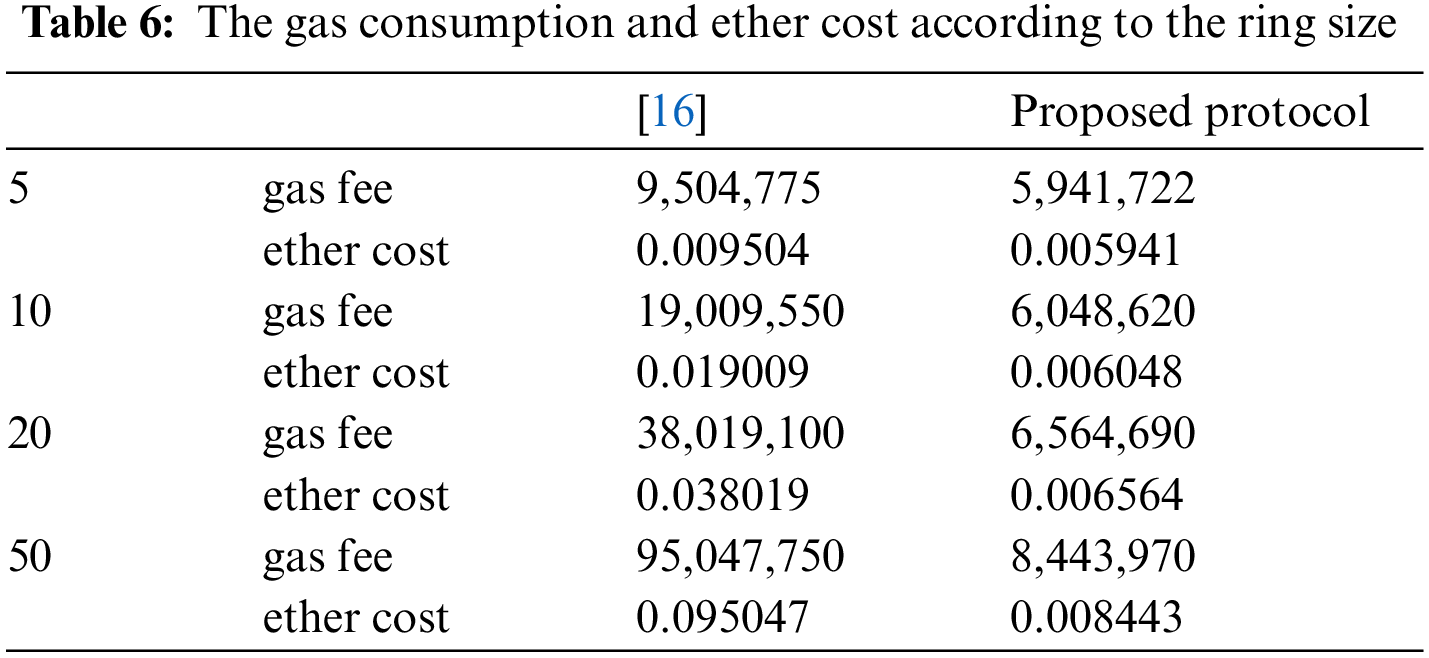
However, in our proposed system, only the hash value of the ticket signature and the verification result are recorded on the blockchain, and the ticket generation and verification are performed in the local environment, reducing the computational load of running the smart contract. As a result, when the ring size is 50, our AnonymousTollPass smart contract system consumes approximately 10% of the gas required in [16]. This result demonstrates the efficiency of our smart contract system.
In this section, we discuss the security and privacy levels by analyzing a case study in South Korea utilizing our AnonymousTollPass model.
When a V uses a ticket, the probability that the curious participant can correctly identify the route of a

For instance, if a user commute using a vehicle five days a week, he uses 10 tickets per week and 40 tickets per month. For a ring size of 50, this satisfies 192-bit security, which is the highest security level. Thus, when considering real-world driving scenarios for regularly using the ETC System, it is difficult for the participants to determine a single vehicle’s route through the used ticket list recorded in the blockchain.
There is no restriction on applying the proposed AnonymousTollPass model when launching a new ETC System for toll plazas where none currently exist. However, for countries that already provide ETC Systems, to determine whether different routes taken by the
To verify this, we used the ETC toll data of South Korea as a test case. We represented the toll fees for each vehicle type based on the weekday toll data provided by Korea Expressway Corporation in 2022 [10] in Fig. 8. When counting all toll routes for each vehicle type within the same price range, we found that the number of routes varied. In the price range of

Figure 8: The number of routes by toll fee range
Additionally, we compared popular routes that start in Seoul, and travel to nearby cities. Fig. 9 represents the routes marked as D1

Figure 9: Routes from Seoul to surrounding cities

In this paper, we proposed a privacy-preserving blockchain-based toll payment model for ETC Systems, called AnonymousTollPass model. Vehicles use disposable AnonymousTollPass tickets generated based on TRS, which provide anonymity to the vehicles but can reveal the identities of malicious vehicles. Moreover, the usage history of AnonymousTollPass tickets and information about malicious vehicles are shared between the ETC service provider and toll plazas through smart contracts to ensure the integrity of the ticket usage history. To demonstrate the effectiveness of the proposed model, we calculated the gas fee the cost of executing the smart contract and checked that it consumes less gas compared to previous work. Also, we utilized the ETC System in South Korea as a test case and demonstrated the practicality of the proposed model in real-world situations. Additionally, AnonymousTollPass model can be utilized in ETC Systems and various payment systems that require anonymity in the future.
Acknowledgement: We are grateful to the editors and reviewers for their insightful feedback on this work. We would also like to thank the National Research Foundation of Korea (NRF) and the Korea government (MSIT) for their support.
Funding Statement: This work was supported by the National Research Foundation of Korea (NRF) grant funded by the Korea government (MSIT) (No. 2021R1A2C1095591).
Author Contributions: Authors confirm contribution to the paper as follows: Study conception and design: Jane Kim, Seung-Hyun Seo; data collection: Jane Kim, Soojin Lee; analysis and interpretation of results: Jane Kim, Soojin Lee; draft manuscript preparation: Jane Kim, Chan Yeob Yeun, Seung-Hyun Seo. All authors reviewed the results and approved the final version of the manuscript.
Availability of Data and Materials: The datasets used in the experiments should be clearly cited in the article.
Conflicts of Interest: The authors declare that they have no conflicts of interest to report regarding the present study.
References
1. S. Lee and S. H. Seo, “Design of a two layered blockchain-based reputation system in vehicular networks,” IEEE Trans. Vehicular Technol., vol. 71, no. 2, pp. 1209–1223, Nov. 2021. doi: 10.1109/TVT.2021.3131388. [Google Scholar] [CrossRef]
2. N. Zhao, X. Zhao, M. Chen, G. Zong, and H. Zhang, “Resilient distributed event-triggered platooning control of connected vehicles under denial-of-service attacks,” IEEE Trans. Intell. Transp. Syst., vol. 24, no. 6, pp. 6191–6202, Jun. 2023. doi: 10.1109/TITS.2023.3250402. [Google Scholar] [CrossRef]
3. D. Das, S. Banerjee, P. Chatterjee, U. Ghosh, and U. Biswas, “A secure blockchain enabled v2v communication system using smart contracts,” IEEE Trans. Intell. Transp. Syst., vol. 24, no. 4, pp. 4651–4660, Dec. 2023. doi: 10.1109/TITS.2022.3226626. [Google Scholar] [CrossRef]
4. A. Badshah et al., “AAKE-BIVT: Anonymous authenticated key exchange scheme for blockchain-enabled internet of vehicles in smart transportation,” IEEE Trans. Intell. Transp. Syst., vol. 24, no. 2, pp. 1739–1755, Feb. 2023. doi: 10.1109/TITS.2022.3220624. [Google Scholar] [CrossRef]
5. F. Don, “Electronic toll collection: An introduction and brief look at potential vulnerabilities,” Rockville, MD, USA: SANS Institute, 2004. Accessed: Apr. 04, 2024. [Online]. Available: https://www.giac.org/paper/gsec/3854/electronic-toll-collection-introduction-potential-vulnerabilities/106183 [Google Scholar]
6. National Electronic Toll Collection (NETC) Fastag. Accessed: Jun. 29, 2023. [Online]. Available: https://www.npci.org.in/what-we-do/netc-fastag/product-overview [Google Scholar]
7. E-toll Collection System. Accessed: Jun. 29, 2023. [Online]. Available: https://www.nadra.gov.pk/e-toll-collection-system/ [Google Scholar]
8. ReportLinker. Accessed: Apr. 01, 2024. [Online]. Available: https://www.reportlinker.com/p05069898/Global-Electronic-Toll-Collection-ETC-Systems-Industry.html?utm+source=GNW [Google Scholar]
9. E-ZPass GROUP. Accessed: Mar. 19, 2023. [Online]. Available: https://www.e-zpassiag.com/ [Google Scholar]
10. Korea Expressway Corporation. Accessed: Jul. 11, 2023. [Online]. Available: https://www.hipass.co.kr/main.do#FamilySite [Google Scholar]
11. VETC: Vietnam Electronic Toll Collection. Accessed: Mar. 19, 2023. [Online]. Available: https://vetc.com.vn/ [Google Scholar]
12. C. Hu, X. Cheng, Z. Tian, J. Yu, and W. Lv, “Achieving privacy preservation and billing via delayed information release,” IEEE/ACM Trans. Netw., vol. 29, no. 3, pp. 1376–1390, Mar. 2021. doi: 10.1109/TNET.2021.3063102. [Google Scholar] [CrossRef]
13. THE DRIVE. Accessed: Jul. 18, 2023. [Online]. Available: https://www.thedrive.com/news/ai-traffic-surveillance-can-link-your-driving-patterns-to-criminal-behavior/ [Google Scholar]
14. Z. Ying, L. Yi, and M. Ma, “BEHT: Blockchain-based efficient highway toll paradigm for opportunistic autonomous vehicle platoon,” Wirel. Commun. Mob. Comput., vol. 2020, pp. 1–13, Sept. 2020. doi: 10.1155/2020/8868656. [Google Scholar] [CrossRef]
15. X. Deng and T. Gao, “Electronic payment schemes based on blockchain in VANETs,” IEEE Access, vol. 8, pp. 38296–38303, Feb. 2020. doi: 10.1109/ACCESS.2020.2974964. [Google Scholar] [CrossRef]
16. Y. Guo, Z. Wan, H. Cui, X. Cheng, and F. Dressler, “Vehicloak: A blockchain-enabled privacy-preserving payment scheme for location-based vehicular services,” IEEE Trans. Mob. Comput., Nov. 2022. doi: 10.1109/TMC.2022.3193165. [Google Scholar] [CrossRef]
17. E. Fujisaki and K. Suzuki, “Traceable ring signature,” in Public Key Cryptography–PKC 2007: 10th Int. Conf. on Practice and Theory, Beijing, China, Springer, 2007, pp. 181–200. [Google Scholar]
18. R. Borges, F. Sebé, M. Valls, “An anonymous and unlinkable electronic toll collection system,” Int. J. Inf. Secur., vol. 21, no. 5, pp. 1151–1162, Aug. 2022. doi: 10.1007/s10207-022-00604-8. [Google Scholar] [CrossRef]
19. B. Aiello, Y. Ishai, and O. Reingold, “Priced oblivious transfer: How to sell digital goods,” in Advances in Cryptology—EUROCRYPT 2001: Int. Conf. on the Theory and Application of Cryptographic Techniques, Innsbruck, Austria, Springer, 2001, pp. 119–135. [Google Scholar]
20. M. Randriamasy, A. Cabani, H. Chafouk, and G. Fremont, “Geolocation process to perform the electronic toll collection using the ITS-G5 technology,” IEEE Trans. Vehicular Technol., vol. 68, no. 9, pp. 8570–8582, Jul. 2019. doi: 10.1109/TVT.2019.2931883. [Google Scholar] [CrossRef]
21. N. Aung, W. Zhang, S. Dhelim, and Y. Ai, “T-coin: Dynamic traffic congestion pricing system for the internet of vehicles in smart cities,” Information, vol. 11, no. 3, pp. 149, Mar. 2020. doi: 10.3390/info11030149. [Google Scholar] [CrossRef]
22. R. Böhme, N. Christin, B. Edelman, and T. Moore, “Bitcoin: Economics, technology, and governance,” J. Econ. Perspect., vol. 29, no. 2, pp. 213–238, 2015. doi: 10.1257/jep.29.2.213. [Google Scholar] [CrossRef]
23. T. McGhin, K. R. Choo, C. Z. Liu, and D. He, “Blockchain in healthcare applications: Research challenges and opportunities,” J. Netw. Comput. Appl., vol. 135, pp. 62–75, Jun. 2019. doi: 10.1016/j.jnca.2019.02.027. [Google Scholar] [CrossRef]
24. Y. Bai, Q. Hu, S. H. Seo, K. Kang, and J. J. Lee, “Public participation consortium blockchain for smart city governance,” IEEE Internet Things J., vol. 9, no. 2, pp. 2094–2108, Jun. 2021. doi: 10.1109/JIOT.2021.3091151. [Google Scholar] [CrossRef]
25. W. Y. Chiu and W. Meng, “EdgeTC–A PBFT blockchain-based ETC scheme for smart cities,” Peer-to-Peer Netw. Appl., vol. 14, pp. 2874–2886, Mar. 2021. doi: 10.1007/s12083-021-01119-0. [Google Scholar] [CrossRef]
26. B. Xiao, X. Fan, S. Gao, and W. Cai, “EdgeToll: A blockchain-based toll collection system for public sharing of heterogeneous edges,” presented in Conf. IEEE INFOCOM WKSHPS., Paris, France, Apr. 29–May 02, 2019, pp. 1–6. [Google Scholar]
27. A. Shukla, P. Bhattacharya, S. Tanwar, N. Kumar, and M. Guizani, “DwaRa: A deep learning-based dynamic toll pricing scheme for intelligent transportation systems,” IEEE Trans. Vehicular Technol., vol. 69, no. 11, pp. 12510–12520, Sep. 2020. doi: 10.1109/TVT.2020.3022168. [Google Scholar] [CrossRef]
28. J. Wang, R. Zhu, T. Li, F. Gao, Q. Wang, and Q. Xiao, “ETC-oriented efficient and secure blockchain: Credit-based mechanism and evidence framework for vehicle management,” IEEE Trans. Vehicular Technol., vol. 70, no. 11, pp. 11324–11337, Sep. 2021. doi: 10.1109/TVT.2021.3116237. [Google Scholar] [CrossRef]
29. Patch. Accessed: Nov. 16, 2023. [Online]. Available: https://patch.com/virginia/oldtownalexandria/here-s-when-expect-most-thanksgiving-traffic-northern-va-dc [Google Scholar]
30. Public Data Portal DATA.GO.KR. Accessed: Aug. 02, 2023. [Online]. Available: https://www.data.go.kr/en/%20data/15043728/fileData.do [Google Scholar]
31. D. Johnson, A. Menezes, and S. Vanstone, “The elliptic curve digital signature algorithm (ECDSA),” Int. J. Inf. Secur., vol. 1, pp. 36–63, Jan. 2001. doi: 10.1007/s102070100002. [Google Scholar] [CrossRef]
32. L. Cheng, Q. Wen, Z. Jin, H. Zhang, and L. Zhou, “Cryptanalysis and improvement of a certificateless aggregate signature scheme,” Inf. Sci., vol. 295, pp. 337–346, Feb. 2015. doi: 10.1016/j.ins.2014.09.065. [Google Scholar] [CrossRef]
33. E. Androulaki et al., “Hyperledger fabric: A distributed operating system for permissioned blockchains,” in Proc. Thirteenth EuroSys Conf., Porto, Portugal, 2018, pp. 1–15. [Google Scholar]
34. J. Edmonds, “Matroids and the greedy algorithm,” Math. Program., vol. 1, pp. 127–136, Dec. 1971. doi: 10.1007/BF01584082. [Google Scholar] [CrossRef]
35. J. F. Shortle, J. M. Thompson, D. Gross, and C. M. Harris, “General models and theoretical topics,” in Fundamentals of Queueing Theory, 5th ed. Hoboken, NJ, USA: John Wiley & Sons, pp. 313–361, 2018, vol. 399, pp. 313–361. [Google Scholar]
36. Z. Guan, Z. Wan, Y. Yang, Y. Zhou, and B. Huang, “BlockMaze: An efficient privacy-preserving account-model blockchain based on zk-SNARKs,” IEEE Trans. Dependable Secure Comput., vol. 19, no. 3, pp. 1446–1463, Sep. 2020. doi: 10.1109/TDSC.2020.3025129. [Google Scholar] [CrossRef]
37. B. Parno, J. Howell, C. Gentry, and M. Raykova, “Pinocchio: Nearly practical verifiable computation,” Commun. ACM, vol. 59, no. 2, pp. 103–112, Jan. 2016. doi: 10.1145/2856449. [Google Scholar] [CrossRef]
38. D. Chaum and E. Van Heyst, “Group signatures,” in EUROCRYPT’91. Brighton, UK, Apr. 8–11, 1991, pp. 257–265. [Google Scholar]
39. Remix. Accessed: Jun. 12, 2023. [Online]. Available: https://remix.ethereum.org/ [Google Scholar]
40. Trufflesuite. Accessed: Jun. 12, 2023. [Online]. Available: https://trufflesuite.com/ganache/ [Google Scholar]
41. G. V. Rossum and F. L. Drake, Top-level components. in Python Reference Manual, 1st ed. Amsterdam, Netherlands: Centrum voor Wiskunde en Informatica, 1995, vol. 111, pp. 1–52. [Google Scholar]
Cite This Article
 Copyright © 2024 The Author(s). Published by Tech Science Press.
Copyright © 2024 The Author(s). Published by Tech Science Press.This work is licensed under a Creative Commons Attribution 4.0 International License , which permits unrestricted use, distribution, and reproduction in any medium, provided the original work is properly cited.


 Submit a Paper
Submit a Paper Propose a Special lssue
Propose a Special lssue View Full Text
View Full Text Download PDF
Download PDF
 Downloads
Downloads
 Citation Tools
Citation Tools