 Open Access
Open Access
ARTICLE
DNBP-CCA: A Novel Approach to Enhancing Heterogeneous Data Traffic and Reliable Data Transmission for Body Area Network
1 InterNetWorks Research Laboratory, School of Computing, Universiti Utara Malaysia, Sintok, 06010, Malaysia
2 Faculty of Computer Science and Information Technology, Universiti Tun Hussein Onn Malaysia, Parit Raja, Johor, 86400, Malaysia
3 School of Games & Creative Technology, University for the Creative Arts, Farnham, GU9 7DS, UK
4 Computer Engineering Department, College of Computer and Information Sciences, King Saud University, Riyadh, 11543, Saudi Arabia
5 Software Engineering Department, College of Computer and Information Sciences, King Saud University, Riyadh, 11543, Saudi Arabia
* Corresponding Author: Abdulwadood Alawadhi. Email:
Computers, Materials & Continua 2024, 79(2), 2851-2878. https://doi.org/10.32604/cmc.2024.050154
Received 29 January 2024; Accepted 13 March 2024; Issue published 15 May 2024
Abstract
The increased adoption of Internet of Medical Things (IoMT) technologies has resulted in the widespread use of Body Area Networks (BANs) in medical and non-medical domains. However, the performance of IEEE 802.15.4-based BANs is impacted by challenges related to heterogeneous data traffic requirements among nodes, including contention during finite backoff periods, association delays, and traffic channel access through clear channel assessment (CCA) algorithms. These challenges lead to increased packet collisions, queuing delays, retransmissions, and the neglect of critical traffic, thereby hindering performance indicators such as throughput, packet delivery ratio, packet drop rate, and packet delay. Therefore, we propose Dynamic Next Backoff Period and Clear Channel Assessment (DNBP-CCA) schemes to address these issues. The DNBP-CCA schemes leverage a combination of the Dynamic Next Backoff Period (DNBP) scheme and the Dynamic Next Clear Channel Assessment (DNCCA) scheme. The DNBP scheme employs a fuzzy Takagi, Sugeno, and Kang (TSK) model’s inference system to quantitatively analyze backoff exponent, channel clearance, collision ratio, and data rate as input parameters. On the other hand, the DNCCA scheme dynamically adapts the CCA process based on requested data transmission to the coordinator, considering input parameters such as buffer status ratio and acknowledgement ratio. As a result, simulations demonstrate that our proposed schemes are better than some existing representative approaches and enhance data transmission, reduce node collisions, improve average throughput, and packet delivery ratio, and decrease average packet drop rate and packet delay.Keywords
In today’s context, the Internet of Medical Things (IoMT) has become a pivotal technology for managing patient health information, particularly in response to the global impact of the COVID-19 pandemic. The pandemic has compelled healthcare professionals to adopt remote patient monitoring through IoMT devices. IoMT, a fusion of medical devices and the Internet of Things (IoT) represents healthcare systems’ future [1–3]. In this paradigm, every medical device is interconnected and monitored by healthcare professionals via the Internet. This connectivity enables early detection of potential health issues, allowing proactive measures before they escalate. Moreover, IoMT contributes to cost reduction in healthcare by facilitating remote patient monitoring, where information is transmitted to healthcare experts and medical staff, and responses are relayed to patients, thereby minimizing the need for hospitalization. With the increasing deployment of IoMT devices in Body Area Networks (BAN) and open bands like the 2.4 GHz band, this field is rapidly becoming a significant area of research on a global scale [4–6].
There has been a surge in the utilization of BANs in recent years due to their adaptability and versatility. A BAN comprises Medical Sensor Nodes (MSNs) that are either affixed to or implanted within the body [7–9]. Through wireless connection, these MSNs may send biological data to a coordinator from anywhere in the human body. The BAN enables affordable and flexible health monitoring by using sensors to provide real-time updates of medical records via the Internet for people like patients, firefighters, and military personnel [10,11]. Signals for health monitoring can be captured from patients, transmitted wirelessly to receivers, and subsequently relayed to remote locations for analysis, allowing timely intervention when necessary. The signal transfer within the BAN encompasses three major domains. The communication architecture is organized into a three-tier structure [12–14].
1.1 Tier3: Beyond-BAN Communication
This means of communication is very suitable for urban contexts since it functions as a pivotal gateway. The Medical History Database Server (MHDS) is crucial in Tier 3 since it records the user’s medical history and individual profile [15]. The management of beyond-BAN utilizes queueing algorithms to simulate packet-level processes, enabling the efficient transmission of both emergent and non-urgent medical packets in Tier 3. These systems use first-come, first-serve (FCFS) and delay-dependent priority disciplines to retrieve important patient data efficiently [13,16,17]. In addition, the Coordinator in Tier1 can directly connect to the Tier 3 network via General Packet Radio Service (GPRS) /3G/4G/5G. Depending on the application, this connection could eliminate the need for an Access Point (AP) [18].
1.2 Tier2: Inter-BAN Communication
At this tier, the connection between the coordinator and the user is facilitated through Access Points (APs), integral network components strategically positioned to cater to emergency scenarios. The primary objective of communication at this level is to establish a link between the BAN and other systems or networks, enabling the seamless retrieval of information through mediums like the Internet [11,19].
1.3 Tier1: Intra-BAN Communication
In this stage, the interplay of MSNs revolves around the patient’s body. Compact and energy-efficient, an ideal MSN should be able to sense medical indications such as blood flow, pressure, temperature, pulse rates, electrocardiograms (ECGs), and electroencephalograms (EEGs). Data rates less than 10 kbps are usually required for blood flow, pressure, temperature, pulse rates, ECGs, and EEGs. On the other hand, electromyography (EMG) requires a maximum data rate of 100 kbps [17,20]. This investigation supports the 250 kbps appropriate data rate for a patient monitoring system, as defined by the Institute of Electrical and Electronics Engineers 802.15.4 (IEEE 802.15.4) BAN standard. The coordinator gathers data for diagnostic and therapeutic reasons and sends it to distant sites and earlier levels [13,14].
Establishing a wireless communication network in BANs involves utilizing diverse MSNs with varying computational power, storage capacity, energy consumption, and data generation rates. These heterogeneous MSNs generate various data packets with distinct delivery requirements, including tolerance for losses within specific time frames, intolerance to losses but with delivery deadlines, and the need for minimal losses without specific time constraints. Effectively managing the complexities of these heterogeneous MSNs in BAN operations is challenging [16,21]. BANs incorporate diverse wireless communication technologies, such as Bluetooth, Wireless Local Area Networks (WLANs), Wireless Personal Area Networks (WPANs), and ZigBee, with IEEE 802.15.4 and IEEE 802.15.6 commonly used at the Media Access Control (MAC) and physical (PHY) layers. IEEE 802.15.4, designed as a low-rate wireless personal area network (LR-WPAN), stands out for its attributes, including minimal energy consumption, lower data rates, small communication areas, and support for real-time traffic [9,10].
Its coordinator operates in two modes, and this discussion focuses on the beacon-enabled mode, particularly relevant to BAN applications, with a distinction between active and inactive periods within this mode being crucial [12]. The superframe structure in this mode incorporates adjustments for a duty cycle, facilitating effective node energy management by accommodating variable intervals among active and sleep periods [22]. During the active period, guaranteed time slots (GTS) assignment or a contention-based Carrier-sense multiple access with collision avoidance (CSMA/CA) channel access method are used. An essential CSMA/CA algorithm feature involves detecting channel congestion or autonomously sensing the channel before initiating transmission. During access to channel congestion in the contention access period (CAP), in slotted-CSMA/CA, every node awaits a random number of backoff periods selected from the backoff period range. Additionally, during each transmission attempt, a transmitting node must await MAC’s clear channel assessment (CCA) [12,23].
In an idle channel, as the CCA detects, an MSN is permitted to transmit its packets. While many earlier backoff techniques execute well in networks with low or medium traffic loads, they often assign the same range of backoff periods of all node types, leading to increased retransmissions, overlooking critical traffic, and causing a high collision rate during CCA for each node [21,24]. Because of this, the MAC protocol performs poorly, resulting in decreased throughput, increased packet drop rate (PDR), packet delay, and decreased packet delivery ratio (PDR), especially in networks with high traffic loads. Dynamically adjustable backoff times and CCA systems are required to address these problems. In order to manage the backoff time and maximize the CCA channel access of the dynamic IEEE 802.15.4 standers bases BAN at a star topology, this study suggests using a Takagi, Sugeno, and Kang (TSK) fuzzy logic controller. Since fuzzy logic provides a simple way to reach a definitive conclusion based on imprecise, ambiguous, or hazy input information, it is commonly used in the IEEE 802.15.4 protocol rather than mathematical models or traditional linear controllers [25–27]. This approach aims to provide a balanced solution where nodes neither wait excessively long for channel access nor gain access too quickly. It also tackles issues related to repeated data transmission and long acknowledgement wait periods experienced by nodes in the network [9].
This study introduces a novel approach called Dynamic Next Backoff Period and Clear Channel Assessment (DNBP-CCA) schemes to enhance backoff periods and channel clearance for improved utilization through CSMA/CA. These issues include neglected crucial traffic, increased collision rates, issues with buffer overflow common and raised retransmissions in low, medium, or high traffic loads; the DNBP-CCA scheme leverages TSK fuzzy models to enhance PDR. It decreases PDR in heterogeneous BANs. The critical contributions of DNBP-CCA include:
• Dynamic Next Backoff Period (DNBP), which adjusts the backoff process of the IEEE 802.15.4 standard for MSN access to the channel, adaptation aims to improve and decrease collision probabilities among MSNs. Utilizing input parameters like backoff exponent, channel clear, collision ratio, and data rate, the MSN calculates and determines the length of backoff periods to the network using the fuzzy rules and fuzzy TSK model.
• Dynamic Next Clear Channel Assessment (DNCCA) adjusts the channel process of the IEEE 802.15.4 standard based on data transmission to the coordinator and enhances data transmission reliability. Using an optimal model, the MSN uses input parameters like buffer status ratio and acknowledgement ratio to calculate and decide the length of CCA channel access to the network.
• The adaptive solution presented aims to enhance throughput, decrease packet delay, prevent packet drop, and ensure high reliability. The scheme’s performance is evaluated through simulations in Castalia-3.3.
The remaining sections of the document follow a similar format. Section 2 delves into the related literature, while Section 3 outlines the proposed schemes. Section 4 discusses the simulation process and its results. Lastly, Section 5 summarizes the entire research paper.
This section assesses prior research focused on improving the efficiency of the MAC protocol based on IEEE 802.15.4 through adjustments to the backoff period and CCA channel elements [28,29]. The existing body of literature exploring the optimization of MACs based on IEEE 802.15.4 encompasses various approaches [30,31]. This study specifically delves into the backoff-based and heterogeneous data rate approach, which we will incorporate into our proposed research. The optimization of the IEEE 802.15.4-based MAC protocol has been the subject of several recent research [32]. These studies have focused on backoff times and CCA techniques suited for low, medium, and high data rate needs.
Moreover, the Adaptive Backoff Mechanism (ABM) [33] developer proposed a strategy to implement a flexible contention window to enhance performance during periods of high load. This protocol utilizes collision history to assess connection status and wireless channel utilization. A substantial number of collisions indicate heightened competition in the wireless channel, prompting the use of a larger contention window. While the researchers claim an increased duration of access to alleviate competition, the exponential speed escalation may introduce undesired delays during heavy traffic. Consequently, this protocol can lead to elevated traffic loads and latency.
The author of the Efficient Backoff Scheme (EBS) [34] proposed a groundbreaking approach named efficient backoff (EB) to enhance both network performance and power efficiency within the IEEE 802.15.4 based on MAC protocol. EB achieves this by minimizing backoff redundancy by altering the backoff range. The adaptability of EB lies in its ability to dynamically determine the backoff range based on CCA findings, thereby reducing unnecessary sensing during ongoing transmissions. Additionally, the author develops a Markovian model that captures the essence of the proposed method, subjecting it to thorough performance evaluations through extensive experimental simulations.
Proposed for contention and channel access within an intra-Wireless Body Area Network (WBAN), Traffic Class Prioritization CSMA/CA (TCP-CSMA/CA) [35] allocates distinct, shortened, and prioritized backoff time ranges for each traffic class during contention and channel access. Based on categorizing current patient data, the traffic was classified into four distinct classes, and each was assigned a specific backoff time range. The objective is to diminish network latency, minimize packet loss, and enhance network lifespan and throughput.
In the study conducted by Onwuegbuzie et al. [36], an enhanced prioritized backoff MAC strategy is proposed for heterogeneous data wireless sensor networks, incorporating both non-real-time and real-time data. This approach, termed Class of Service Traffic Priority-based Medium Access Control (CSTP-MAC), determines backoff times utilizing priority-specific expressions for data, categorizing it into Low-Priority Data (LPD) and High-Priority Data (HPD). The aim is to minimize latency, lower power consumption, and improve PDR and throughput.
Zhu et al.’s work from 2022 [37] aims at improving Channel Contention Efficiency (CCE) by IEEE 802.15.4 standards based on the CSMA/CA framework by optimizing the MAC minimum Backoff Exponent, MAC maximum Backoff Exponent and MAC maximum CSMA Backoffs using Markov chain methodology. This reduces packet latency and increases throughput.
The presentation introduces the Adaptive Backoff Algorithm (ABA) [38], a probabilistic mechanism designed for adaptive control over the contention window (CW) size. ABA determines the CW size by factoring in the likelihood of collisions, which is calculated locally by each sensor node. This inclusion indirectly incorporates the numeral of nodes contending access to media in the CW update process. ABA is modelled using a Markov chain, and the model’s validity is confirmed through simulation utilizing a C-based simulator. The effectiveness of ABA is demonstrated in channel utilization, energy efficiency, reliability, and collision times within the channel.
The suggested Adaptive Backoff and Dynamic Clear Channel Assessment methods (RDTM) [39] aim to enhance PDR, end-to-end latency, residual energy and throughput in a dynamic environment. It is recommended to use specific ranges of backoff probabilities, known as Unique Backoff Probability Ranges (BPRs), for the first three backoffs to reduce the likelihood of collisions. An optimized channel access method, a customized CCA algorithm, is proposed to enhance the network’s power efficiency, packet delivery latency, and channel use. The suggested study uses a Markov chain model to evaluate the influence of hypothesized processes on network performance. The unique Backoff Packet Retransmissions (BPRs) for various backoff periods contribute to a certain degree of collision minimization. The revised CCA method sets the CW to zero when the channel is not in use and to a value of 1 when the channel is occupied. This leads to enhanced throughput, PDR, and decreased end-to-end delay. Nevertheless, the absence of specific Backoff Packet Retransmission (BPR) protocols for different types of traffic in each backoff results in the non-implementation of traffic prioritization.
The limitations of past studies, including ABM, EBS, TCP-CSMA/CA, CSTP-MAC, ABA, and RDTM, were evaluated for their effect on reliability, delay, energy consumption, throughput, and the overall performance of the network. However, these investigations highlighted node limitations, particularly under medium and high traffic loads. Challenges included notable packet and throughput losses when accessing the channel during the backoff period, resulting in a reduced buffer overflow and ratio of delivered packets. Further, issues surfaced whenever data was transmitted to the coordinator by MSNs during CCA utilizing CAP, leading to prolonged time for node acknowledgement, increased delay in the network, and diminished throughput, ultimately affecting network performance. Consequently, this study addresses existing literature gaps by suggesting the Dynamic Next Backoff Period and Clear Channel Assessment (DNBP-CCA) scheme, designed to alleviate packet loss, minimize delay, enhance reliability, and ensure improved throughput.
Moreover, this study presents a fuzzy logic-based controller, opting for it over traditional linear controllers or mathematical models. The preference for fuzzy logic stems from its ability to provide a straightforward approach for arriving at clear conclusions based on input information that is vague, imprecise, or ambiguous [25]. Fuzzy systems prove advantageous in handling very complicated systems with poorly comprehended behaviours, especially when there is a need for an approximate but swift solution [26].
The three main parts of a fuzzy system—fuzzification, rule-based engines of inference, and defuzzification—that operate input language factors to produce output variables of linguistics are shown in Fig. 1. A fuzzy logic system (FLS) converts precise inputs into exact outputs via its rules. The outcome of defuzzification is the acquisition of definite numerical values. While this number may indicate a forecast or a financial estimate in signal processing, it may also represent a particular control action in the context of a control system [27].
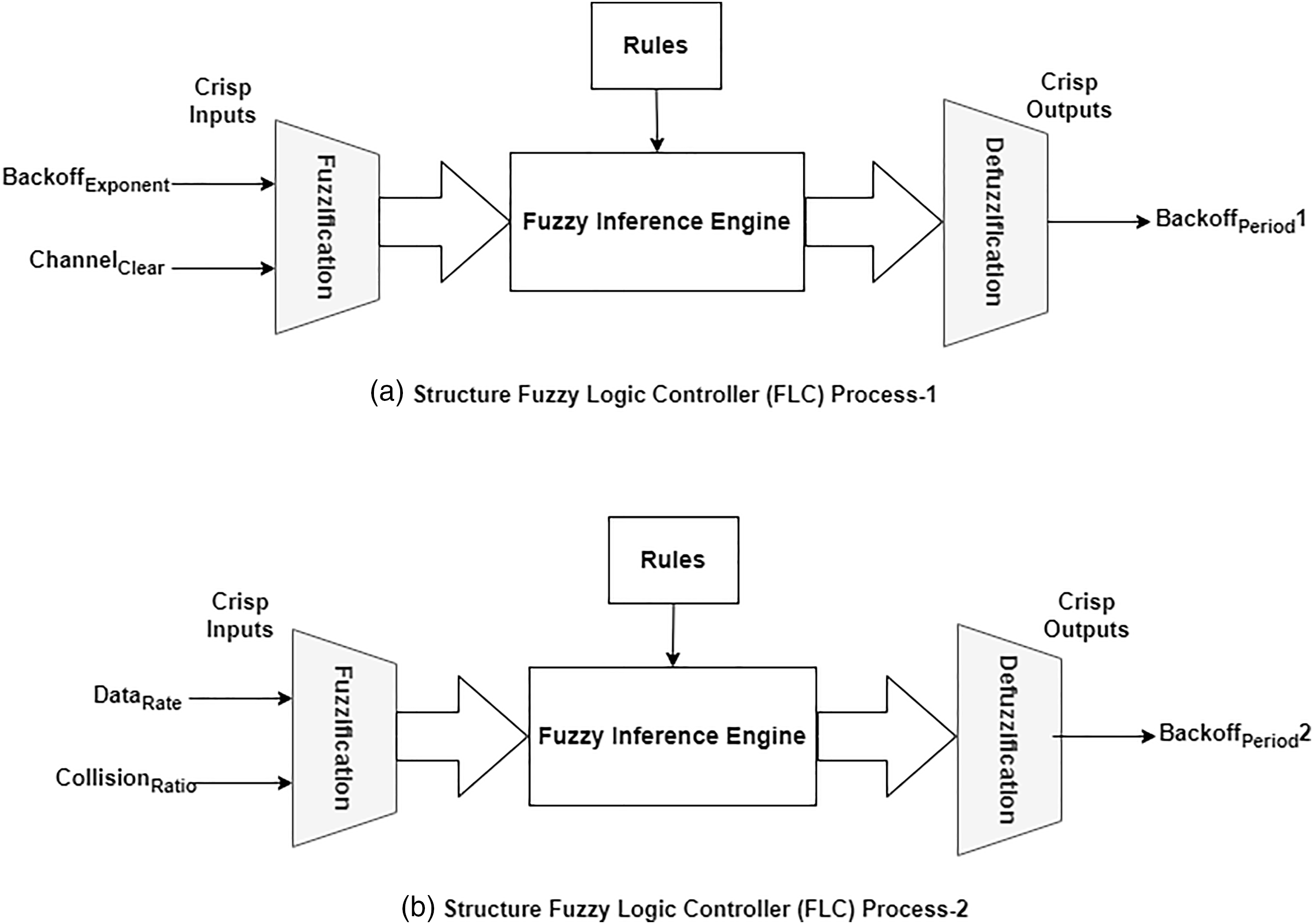
Figure 1: Fuzzy logic control structure for suggested (Backoff-Period1 and Backoff-Period2)
• Fuzzification: Fuzzification converts the system’s previously crisp input space into a fuzzy set within a particular universe. Each system input is assigned a membership function:
• Base Rule: A fuzzy rule may be characterized as a conditional statement of “If x is A, then y is B,” in which linguistic x and y variables are specified. Linguistic A and B values are defined as sets of fuzzy within the universes X and Y. Comprising various components, a fuzzy rule allows for the use of “and” or “or” operators to combine its elements [42,43].
• Inference Engine: The engine for inference employs reasoning to derive findings from knowledge and fuzzy inputs. The fuzzy rules become active and combine simultaneously.
• Defuzzification: The procedure entails translating the inference mechanism’s fuzzy output values into exact, crisp values [27,41].
The inference approach developed by Mamdani [42], widely adopted by many fuzzy systems, is characterized by its use of fuzzy sets to define both premise and derived parameters. This method, which is recognized for giving fuzzy logic its theoretical underpinnings, describes fuzzy rules as given by Eq. (1):
The output variable transforms the outcome parameter of the if-then rule into a fuzzy set, where mnj and σnj denote the Gaussian membership function for deviation and means, respectively, related to the jth rule and the nth dimension [26]. Additionally, TSK unveiled a modified inference method called the TSK fuzzy model. Fuzzifying the inputs and establishing a fuzzy inference process are the first two stages, similar to those in the original Mamdani method. Nevertheless, the TSK fuzzy model uses linear sets for crisp inputs and fuzzy sets for the following parameters. Eq. (2) displays the fuzzy rule standard for the TSK fuzzy model.
In the TSK inference system, where pnj signifies the degree of impact of each system input parameter, the need for the defuzzification stage is eliminated, as the outcome of a rule is precise [44]. Instead, the model output is generated by computing the average weighted outputs for the crisp rules, a process shorter than the defuzzification in the original centroid methodology. Regarding a comprehensive analysis of the quantitative of the entire method, the fuzzy TSK technique demonstrates superior performance compared to the Mamdani technique [40,44].
Past algorithms such as ABM, EBS, TCP-CSMA/CA, CSTP-MAC, ABA, and RDTM were based on conventional mathematics, making them less adaptable to unpredictable shifts in heterogeneous backoff periods within BAN. As a solution, this research endorses DNBP, utilizing the fuzzy TSK technique for its resilience in managing differences and unforeseen variations at heterogeneous backoff period conditions, making it suitable for decision-making in real time.
This division outlines the suggested solutions named the Dynamic Next Backoff Period and Clear Channel Assessment (DNBP-CCA) schemes to ensure fairness and optimal reliability in channel access among diverse MSNs and improve data transmission. Through the Dynamic Next Backoff Period (DNBP) scheme, which adjusts backoff periods based on CSMA/CA, MSNs experience reduced waiting times for channel access. Simultaneously, the Dynamic Next Clear Channel Assessment (DNCCA) scheme optimizes channel access using CSMA/CA, facilitating swift access for the MSNs. First, we define the network assumptions and then explain the methodology for estimating variables characterizing channel statuses. Subsequently, the enhancement criteria for DNBP and DNCCA are detailed.
Additionally, let us establish certain assumptions regarding the network method of running and configuration. At first designed for the 802.15.4 network utilizing a star topology between the Coordinator and MSNs, the proposed scheme leverages MSNs to create backoff periods and handle channel access during MSN entry in the CAP segment and CSMA/CA-based synchronization. By mimicking human decision-making, fuzzy logic proves adept at addressing evaluation challenges involving intricate factors and conditions related to the flow of information-carrying packets. This approach offers a practical means to conclude using descriptive language akin to human operators, making it well-suited for implementation by the MSNs.
The DNBP-CCA schemes are depicted in Fig. 2. First, within each MSN at CAP, relevant variables are declared and initialized, such as the number of backoff attempts (NB) = 0, CW = 2, and the backoff exponent (BE), which utilizes two constants, macMinBE = 1 and macMaxBE = 5, representing the minimum and maximum number of backoffs. If Battery Life Extension (BLE) is true, BE is assigned a value of one; otherwise, it takes on the value of macMinBE = 2. The coordinator, in turn, announces the next superframe and guides nodes on where to find the boundary for the next backoff period. The DNBP scheme calculates lower and upper backoff values throughout the CAP period and is designed and implemented. This involves delaying a random number of backoff periods using the fuzzy logic system explained in the subsequent section.
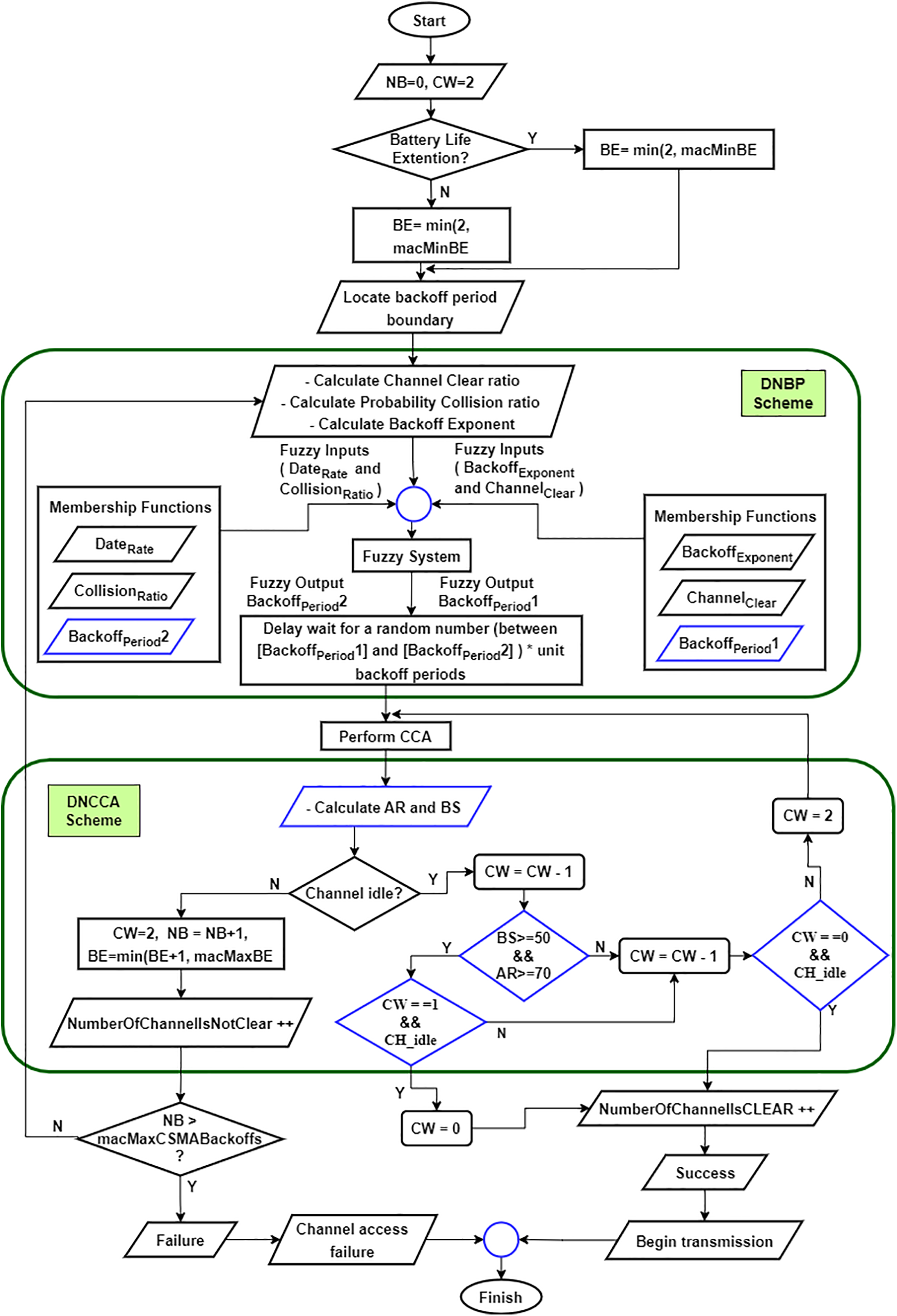
Figure 2: DNBP-CCA schemes flow diagram for IEEE 802.15.4
Through repeating human decision-making, fuzzy logic effectively addresses the challenge of determining the tallness of the backoff periods assigned to each node carrying information packets. The fuzzy logic provides a pragmatic method for nodes to make decisions based on descriptive language, akin to human operators’ input data handling. The pseudocode algorithm for the DNBP scheme is illustrated in Algorithm 1.

The proposed DNBP scheme for BAN is implemented to address changes in channel statuses, requiring dynamic adjustments of backoff periods for two value ranges using a fuzzy logic controller for the node. Four input parameters are utilized in two fuzzy processes to calculate and estimate delay lengths, determining a random number of backoff periods for each MSN seeking channel access. The first fuzzy process, Minimum Limit Backoff-Period1, relies on two input parameters: Backoff index and channel clear ratio. Meanwhile, the second fuzzy process, Maximum Limit Backoff-Period2, considers collision ratio and data rate. Ultimately, each node determines the values for the minimum limit Backoff-Period1 and maximum limit Backoff-Period2, introducing a random delay for the number of backoff periods. The central concept of our scheme is illustrated in Fig. 3, defined as follows:
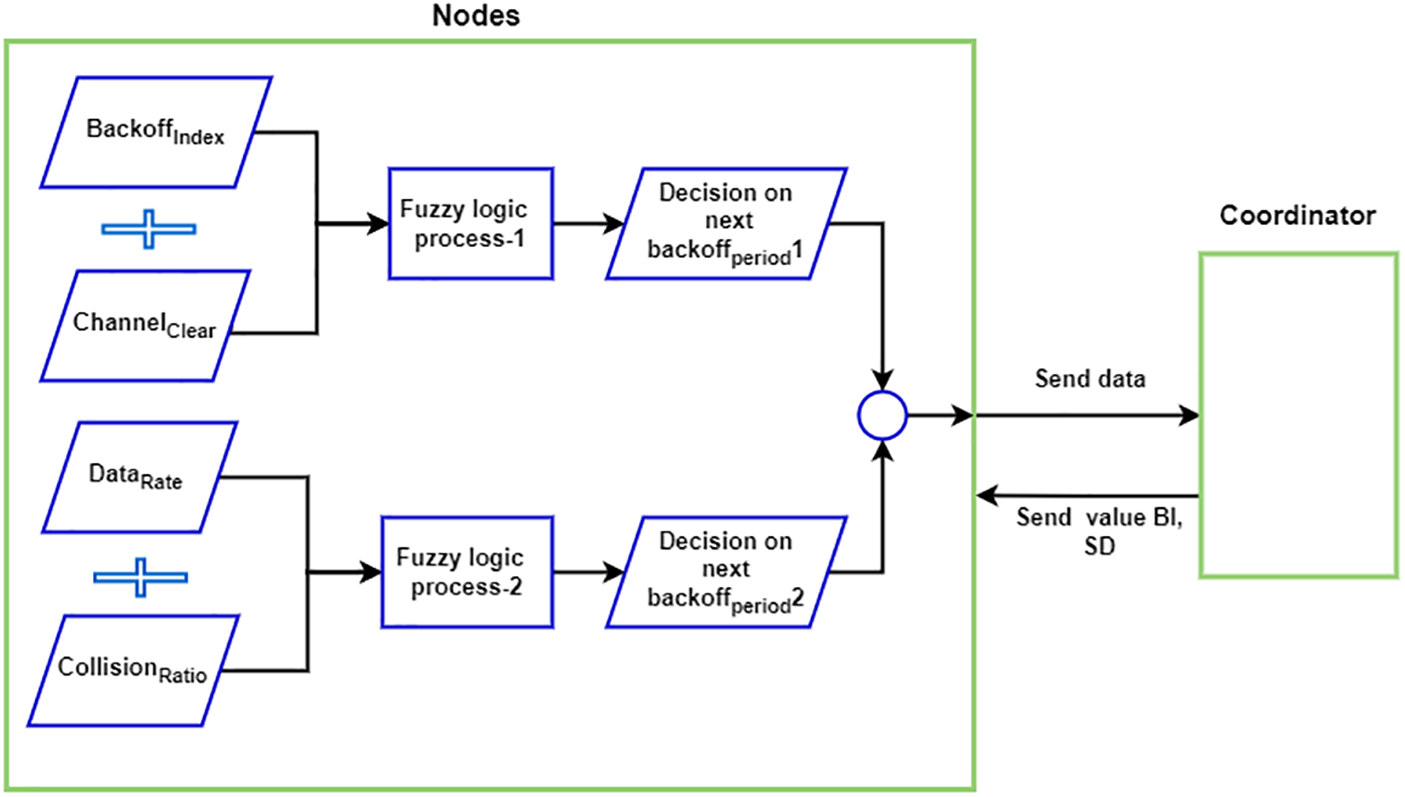
Figure 3: Design DNBP scheme
The first fuzzy process Backoff-Period1:
a) Backoff Index (BI): The backoff index variable represents the exponent value for the backoff (BE), ranging between the minimum and maximum numbers of backoffs denoted as macMinBE and macMaxBE, respectively. The specified values for the backoff minimum and maximum are established as macMinBE = 1 and macMaxBE = 5, as shown in Eq. (3).
b) Channel Clear Ratio (CHr): The channel clear ratio variable is defined as the Total Numeral of Clear Channels (TNCC) divided by the sum of the Total Numeral of Clear Channels (TNCC) and the Total Numeral of Not-Clear Channels (TNNCC), as shown in Eq. (4).
The second fuzzy process Backoff-Period2:
a) Data Rate (DR): The data rate is significance in the CFP and the CAP. Specifically, MSNs with high data rates attempt to access the channel more frequently, necessitating higher priority from the coordinator. Prioritizing high-data-rate nodes is crucial to mitigate collisions and minimize packet loss.
b) Collision Ratio (ColR): The collision ratio (ColR) variable is defined as the Total Numeral of Collisions for each node (TNC) divided by the sum of each MSN’s total numeral of collisions and the Total Numeral of Received Packets from the Coordinator (TNRP), as shown in Eqs. (5) and (6).
To conduct two fuzzification analyses for Backoff-Period1 and Backoff-Period2 during the CAP-based CSMA/CA, each node employs the first fuzzification process to handle Backoff-Period1 in the first step. Input parameters for BI and CHr are transformed into fuzzy linguistic variables, as shown in Eqs. (7) and (8), illustrating their respective fuzzy sets.
As observed, the fuzzy linguistic variable for the BI is categorized into membership degrees: ‘BE1,’ ‘BE2,’ ‘BE3,’ ‘BE4,’ and ‘BE5.’ Similarly, the fuzzy linguistic variable for CHC is divided into ‘SLOW,’ ‘MEDIUM,’ and ‘FAST.’ The second step involves converting fuzzification to process Backoff-Period2, utilizing input parameters for DR and ColR as fuzzy linguistic variables, as shown in Eqs. (9) and (10).
Observing the fuzzy linguistic variable for Data Rate (DR), it is categorized into membership degrees: ‘LOW,’ ‘NLOW’ (near-low), ‘MED’ (medium), ‘NHIGH’ (near-high), and ‘HIGH.’ Similarly, the fuzzy linguistic variable for Collision Ratio (ColR) is divided into ‘LO’ (low), ‘ME’ (medium), and ‘HI’ (high).
The triangle membership function, denoted as TRI and defined by Eq. (11), and the trapezoidal membership function, denoted as TRA and defined by Eq. (12), are commonly used in fuzzy inference systems. TRI(x) and TRA(x) represent the degree of membership inside their respective functions, which dynamically determine variations in the associated fuzzy linguistic variable. The triangle’s vertices are mapped to the X-axis using the values a1, b1, and c1, while the trapezoid’s vertices are mapped using the values a2, b2, c2, and d2. The triangle membership function is commonly used for variables representing boundaries, but the trapezoidal membership function is more suitable for intermediate values. The function of membership of all the linguistic variables in the fuzzy set of the subordinate parameter is combined to get the overall function of membership for the relevant parameter. Figs. 4–7 show the membership functions for fuzzy input parameters generated from our empirical findings.
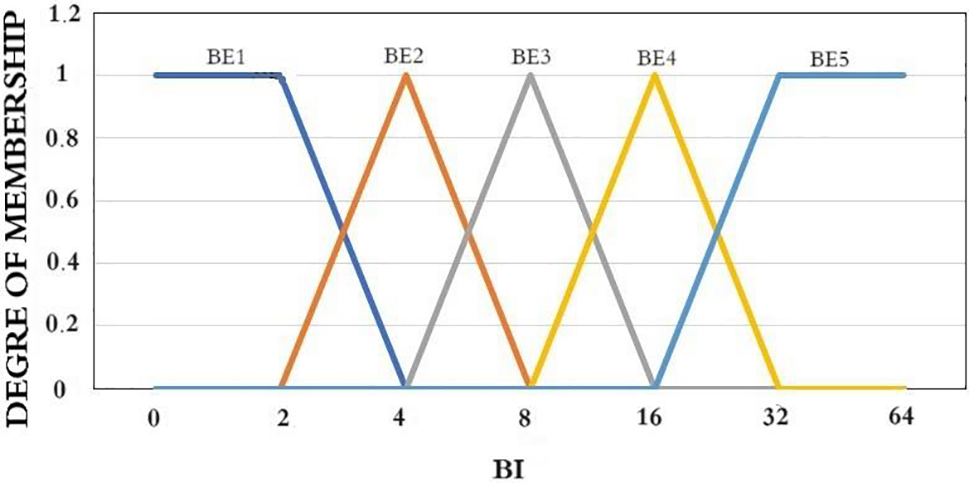
Figure 4: The function of membership for backoff index
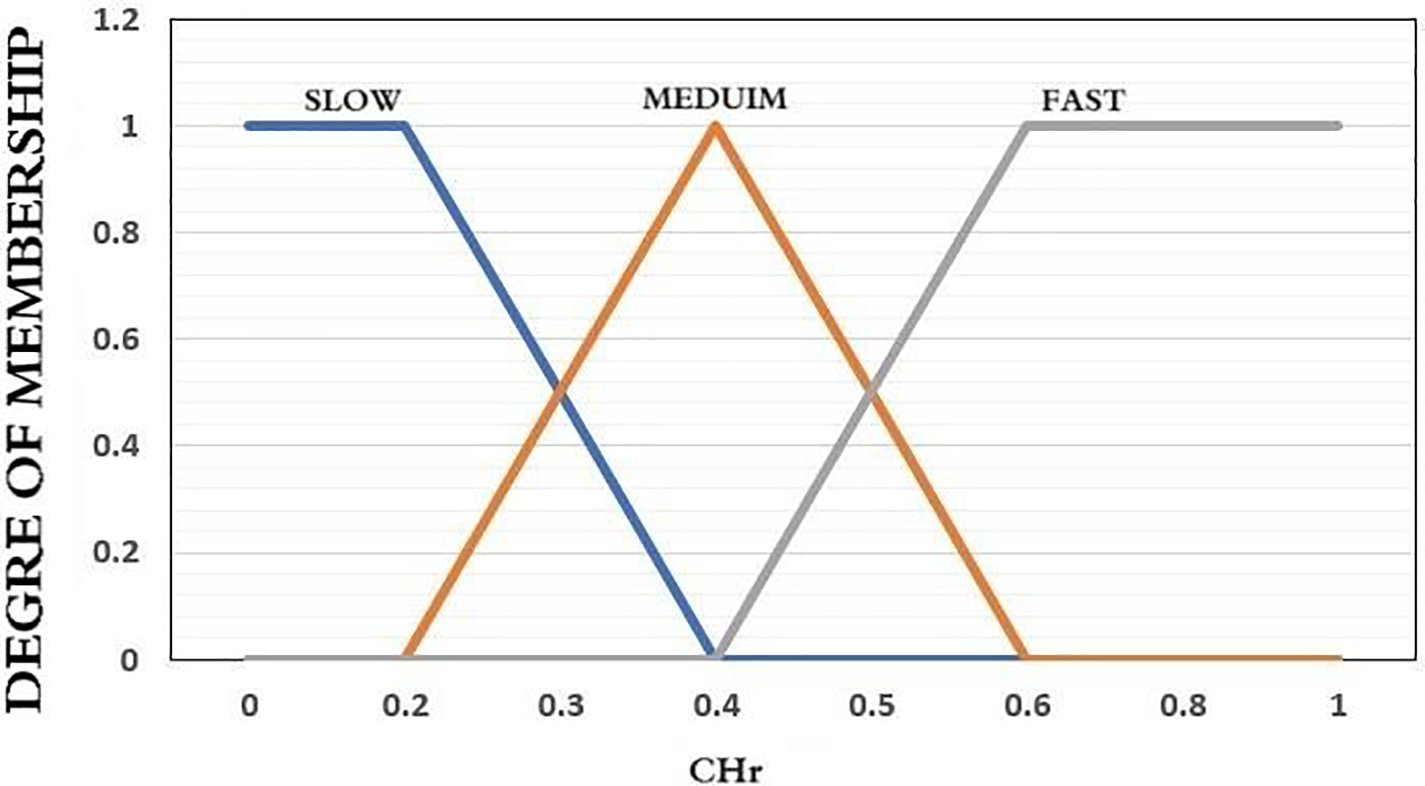
Figure 5: The function of membership for channel clear ratio
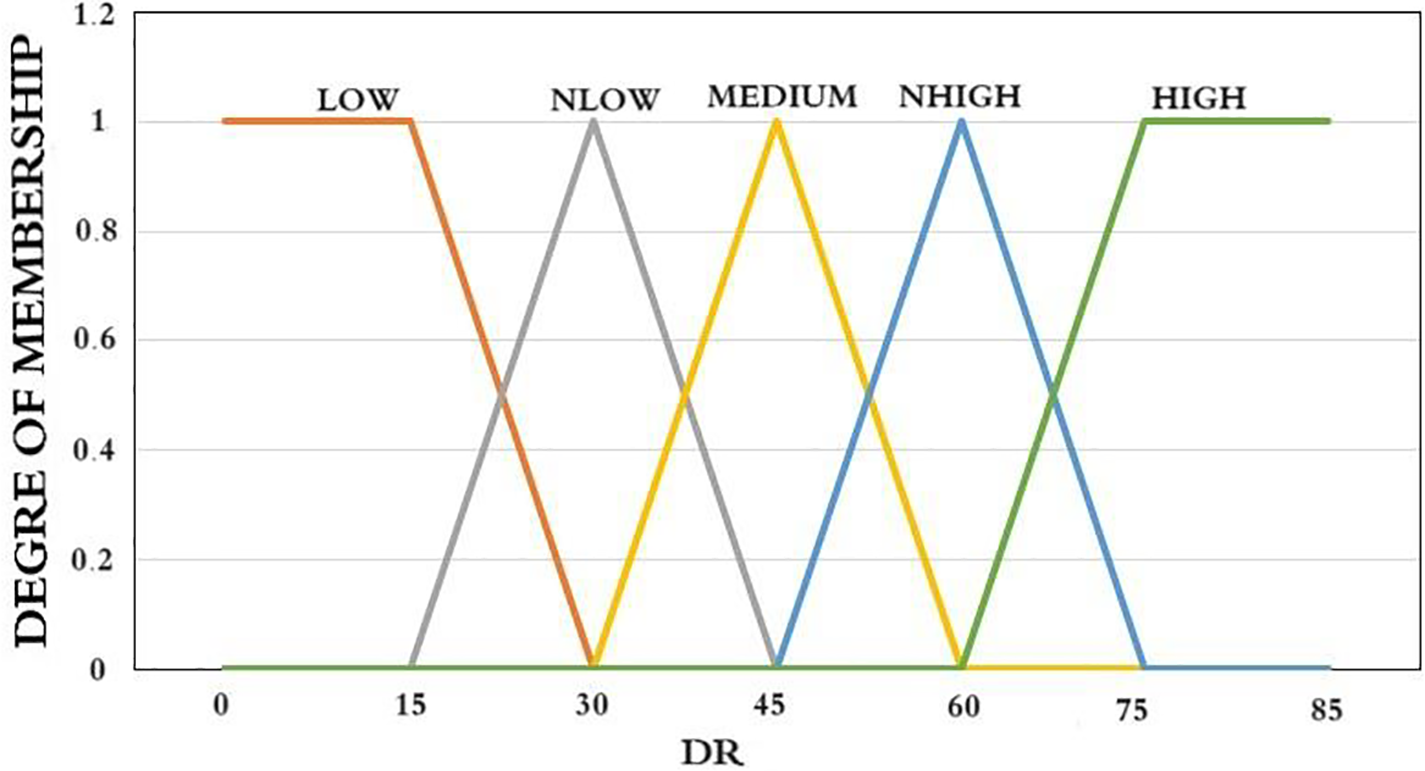
Figure 6: The function of membership for data rate
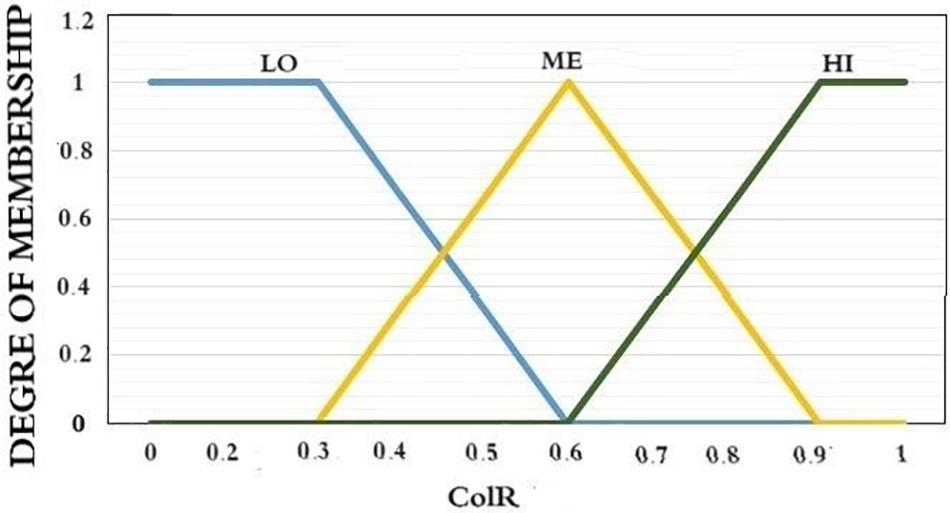
Figure 7: The function of membership for collision ratio
Figs. 4 and 5 illustrate the membership functions for processing Backoff-Period1. Fig. 4 presents the membership function for the backoff exponent degree utilized in the initial fuzzification process. Five membership functions, namely ‘BE1,’ ‘BE2,’ ‘BE3,’ ‘BE4,’ and ‘BE5,’ correspond to the fuzzy elements within the BE fuzzy set. These functions convert the current crisp Backoff Index (BI) into corresponding membership degrees, forming the fuzzy variable. For instance, if BI is 3, corresponding to ‘BE1,’ the membership degree is 5; for ‘BE2,’ it is 9; for ‘BE3,’ it is 15; for ‘BE4,’ it is 31; and for ‘BE5,’ it is obtained accordingly. This results in the BI membership set (3, 5, 9, 15, 31), serving as the BI fuzzy variable for subsequent fuzzy logic analysis. The same principle applies to Fig. 5, which illustrates the function of membership for the channel clear degree. Three functions of membership, ‘SLOW,’ ‘MEDIUM,’ and ‘FAST,’ are equal to the fuzzy components within the CHr degree set of fuzzy. They convert the existing crisp Channel Clear Ratio (CHr) degree to the corresponding membership degree set as the fuzzy variable.
Figs. 6 and 7 illustrate the membership functions for processing Backoff-Period2. Fig. 6 presents the membership function for the degree of data rate employed in the initial fuzzification process. Five membership functions, namely ‘LOW,’ ‘NLOW’ (near-low), ‘MED’ (medium), ‘NHIGH’ (near-high), and ‘HIGH,’ correspond to the fuzzy elements within the Data Rate (DR) fuzzy set. These functions convert the current crisp DR into corresponding membership degrees, forming the fuzzy variable. For instance, if DR is 16, corresponding to ‘LOW,’ the membership degree is 28; for ‘NLOW,’ it is 40; for ‘MED,’ it is 55; for ‘NHIGH,’ it is 73; and for ‘HIGH,’ it is obtained accordingly. This results in the DR membership set as (16, 28, 40, 55, 73), serving as the DR fuzzy variable for subsequent fuzzy logic analysis. The same principle applies to Fig. 7, which illustrates the function of membership for the collision ratio degree. Three functions of membership, ‘LO’ (low), ‘ME’ (medium), and ‘HI’ (high), are equal to the fuzzy components within the Collision Ratio (ColR) degree fuzzy set. They convert the existing crisp ColR degree to the corresponding degree of membership set as the fuzzy variable.
Figs. 4–7 present the segmented membership functions for all input linguistic of fuzzy variables. The fuzzy method’s two-process inference transforms the crisp’s initial values into two-process linguistic of fuzzy variables. Eqs. (13) and (14) illustrate that we can formulate two-process IF-THEN rules using the TSK deductive system’s mechanism. Tables 1 and 2 showcase the IF-THEN rules for the DNBP scheme.
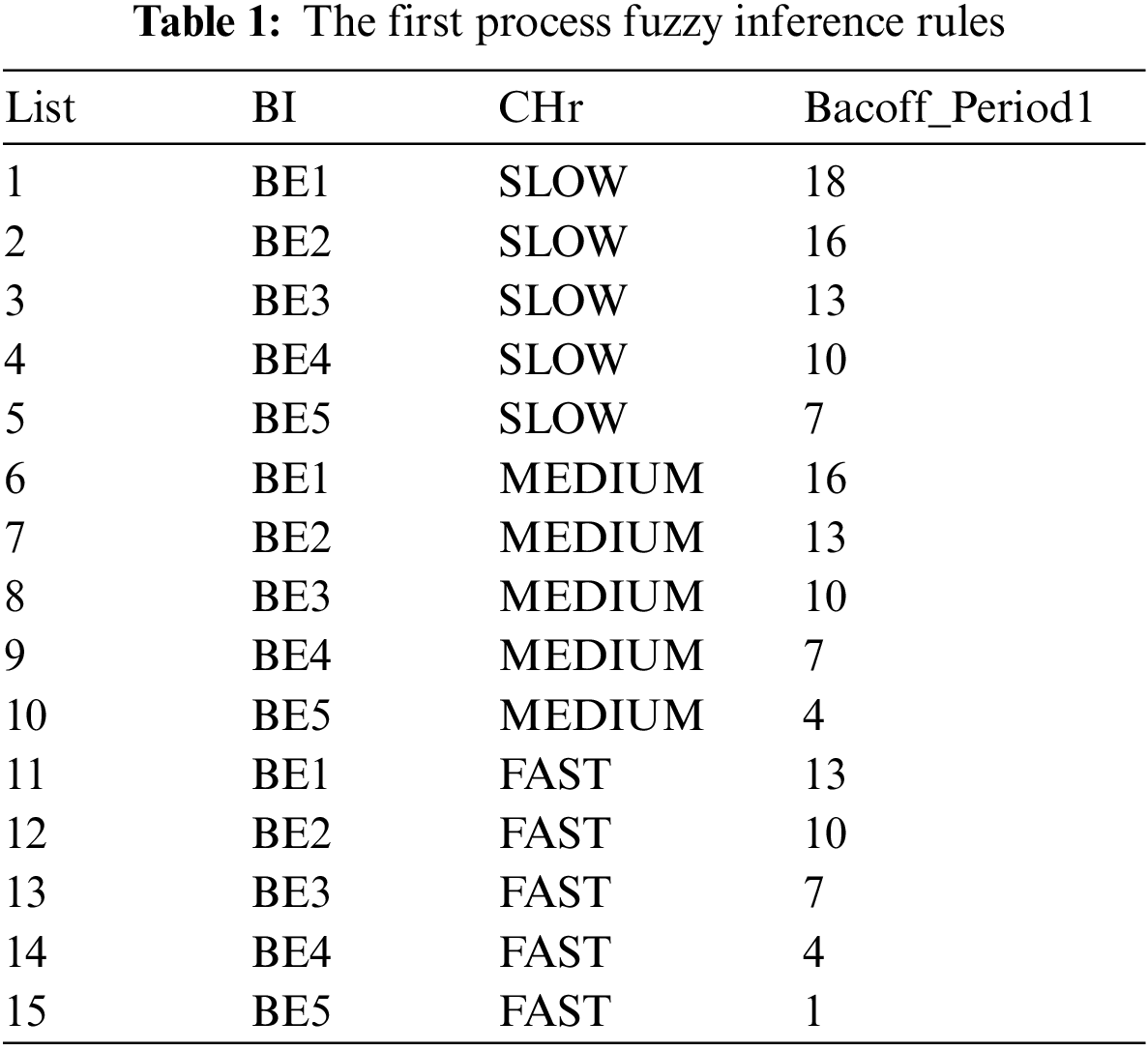
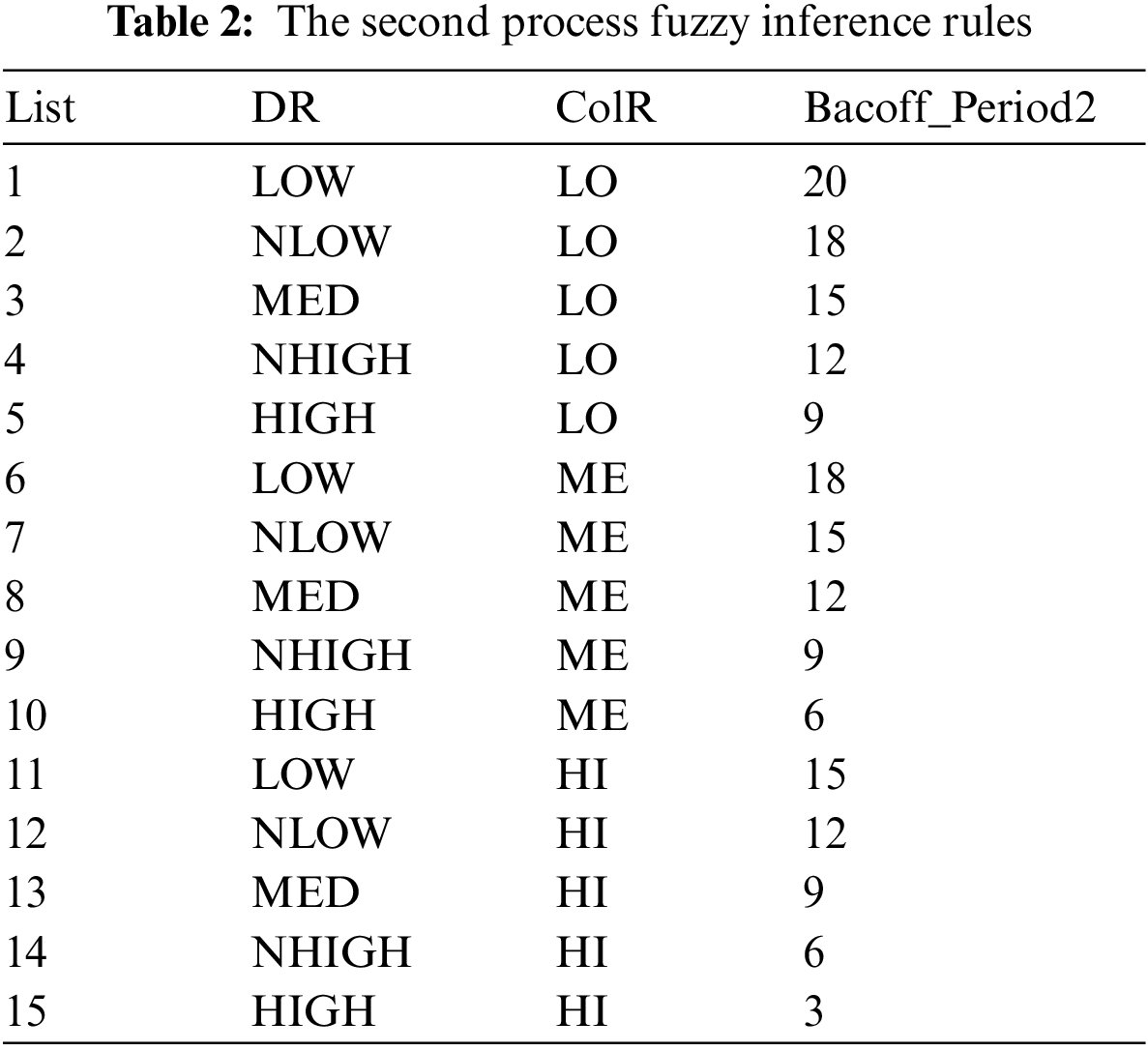
The fuzzy inference system (FIS) modifies the original crisp input variables to conform to fuzzy variables’ linguistic properties by using the previously mentioned methods for input function membership. In fuzzy logic, creating linguistic formulations that adhere to the IF premise, THEN conclusion structure is a standard method of simulating human thought. As information derived from natural language descriptions and models, the premise serves as a decision condition expressed via linguistic fuzzy variables within the set of fuzzy input parameters in the IF-THEN rule-based representation. However, the conclusion also shows the result of the fuzzy variable. This indicates that the fuzzy engine encapsulates information from an expert assessment system to calculate the values of output variables. Tables 1 and 2 illustrate the two processes of fuzzy rules, incorporating empirical data from previous experiments. Nevertheless, the TSK method is employed for the inference of a fuzzy system built on a Sugeno one-order method. Due to the two backoff processes, the first process uses two input parameters. The first parameter contains five levels, and the second parameter contains three levels for the first Backoff-Period1 output parameter. Conversely, the second process uses two input parameters. The first parameter contains five levels, and the second parameter contains three levels for the second Backoff-Period2 output parameter. The outcome (consequent) of the method for the two processes is described in the form of constant equations, as shown in Eqs. (15) and (16).
Here, j represents the number of fuzzy rules for the two processes, and the numerical values of p and q are constants. Eqs. (17) and (18) show the last outputs of both processes for all rules, which establish the weighted average method.
Here, r denotes the number of fuzzy rules for the two processes, and wj1 and wj2 represent the membership function weights for the two processes. The linguistic variable of the fuzzy input parameter in the jth rule’s firing strength is expressed as Eqs. (19) and (20).
We introduce Kj1 and Kj2 to simplify the calculations, as expressed in Eqs. (21) and (22). Subsequently, we formulate Eqs. (23) and (24) to represent the outputs
The generation of random backoff time by IEEE 802.15.4 is described and shown as Eq. (25). The prescribed range for the DNBP scheme is presented and shown in Eq. (26).
Furthermore, the MAC sublayer of the MSN initiates the calculation of the DNCCA scheme, where the PHY sublayer conducts two CCAs at the boundary of the backoff period to confirm the absence of channel activities, as elaborated in the following section.
The proposed DNCCA scheme for MSN addresses variations in the waiting period by dynamically adjusting the clear channel assessment (CCA) value ranges. This adjustment is based on the MSN’s Acknowledgement Ratio (AR) and Buffer Status (BS) calculations. The process involves two phases: First, through the initial phase, CCA whenever CW = 1 and the channel is unoccupied; second, through the subsequent phases, CCA whenever CW = 0 and the channel remains idle. The pseudocode algorithm for the DNCCA scheme, as shown in Algorithm 2.

a) Acknowledgement Rate (AR): The acknowledgement ratio variable is calculated by dividing the Total Numeral of Sender Acknowledgments from the coordinator (TNRA) by the Total Numeral of Transmitter Packets from a node (TNSP), as illustrated in Eq. (27).
b) Buffer Status (BS): The buffer status rate variable is calculated by dividing the Numeral of Packets Waiting in the Queue (NPWQ) by the Total Buffer Size (TBS) of each node, as illustrated in Eq. (28).
Assuming the transmission channel is vacant during the initial CCA, the DNCCA scheme reduces CW by one. It then checks the first stage to verify if BS is equal to or greater than 50 and AR is equal to or greater than 70. If these conditions are met, and CW is equal to one with an idle channel, CW is set to zero. With CW now at zero, the node can access the channel for send patient data to a coordinator, incrementing the count of clear channels. Conversely, if CW is one, the channel is not idle, and also, BS is not greater than or equal to 50, or AR is not greater than or equal to 70, CW decreases by one, and the second stage begins. If CW is zero with an idle channel, the node transfers data to the coordinator, increasing the count of clear channels. If CW is not zero and the channel is not idle, CW is set to 2, and the MAC sublayer requests the PHY sublayer to perform CCA again at the backoff period boundary. If either CCA1 or CCA2 detects a busy channel, the node resets, sets CW to 2, and increments the values of BE, NB, and the count of unclear channels by one. This process ensures that BE does not surpass macMaxBE, set at 5. If NB exceeds macMaxCSMABackoffs = 4, the node discards the packet, concluding the DNBP scheme. If NB is lower than or equal to macMaxCSMABackoffs, the DNBP scheme initiates the next backoff.
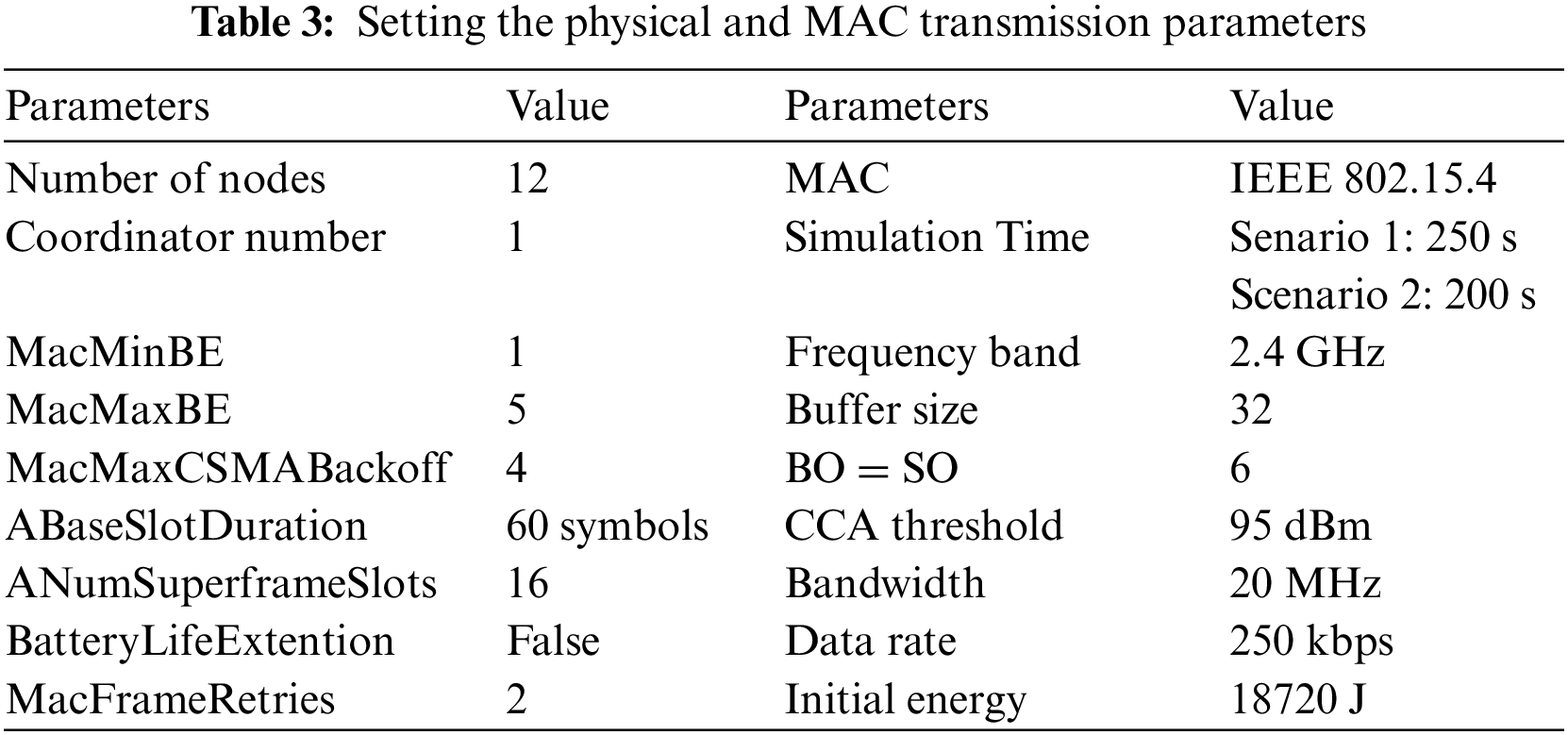
To simulate the proposed approach, we leverage the advantages of the CASTALIA 3.3 simulation built on the Omnet++ podium [21,45,46]. Crafted in C++, this simulator is an objective testbed for modular networks to be the most pragmatic Body Area Network (BAN) simulator. CASTALIA 3.3 is a versatile and multidisciplinary tool with manipulable features for diverse purposes, operating as a framework for object-oriented modular and discrete-event network simulation [47,48]. Refer to Table 3 for a comprehensive list of simulation parameters.
Our network comprises 12 MSNs and one central coordinator arranged in a star topology. The coordinator occupies the central position, with nodes distributed randomly around it. The simulation commences as the coordinator initiates beacon messages at the beginning to the superframe. Subsequently, the slotted CSMA/CA-based CAP was activated, and nodes contend for the channel using the proposed DNBP-CCA schemes during the active period. Whenever a node intends of transmit a packet, the coordinator receives and acknowledges it. MSNs enter a sleep mode during the inactive period to conserve power. To address beaconing conflicts and minimize delays, various SO and BO values have been incorporated to evaluate the impact of the beaconing technique on the BAN connection. Our network model performs much better when BO = SO = 6 since this indicates that the CAP spans the whole active period while the CFP value becomes zero. Undoubtedly, the simulation outcomes are more pragmatic due to the consideration of reliability and throughput values.
BAN tackles chronic diseases such as hypertension and diabetes via implanted or wearable monitoring devices. Through continuous monitoring of physiological indicators and forecasting unfavorable scenarios, BAN has the potential to save lives. Implantable sensors encounter constraints while measuring vital signals, as they necessitate prolonged viability without external assistance, typically lasting for months or even years. Conversely, wearable sensors are highly adaptable. They can accurately measure essential factors, including blood pressure (BP), EEG, heart rate, oxygen saturation (SpO2), pulse oximeter, ECG, gyroscope, EMG, accelerometer, barometer and temperature [13,14]. The simulation scenario revolves around utilizing wearable medical applications to monitor patients. It involves explicitly a restricted quantity of MSNs that are assigned to patients.
Following the completion of eight iterations for each scenario, we gathered data. Afterwards, we computed and recorded the mean reading and a 95% confidence interval. We will analyze the results in two separate scenarios: The first scenario involved a predetermined group of 12 MSNs, a coordinator, and a simulation duration of 250 s for each procedure. Each operation generated data from sensors at consistent rates, with packet generation ranging from 5 to 85 packets per second (PPS). In the second scenario, MSNs were generated in each process, ranging from 2 to 12, respectively, over a predetermined period of 200 s. Four groups were assigned categorized data rates, with distinct rates allocated to each process production for MSNs. More precisely, the nodes numbered 1, 6, and 12 have a rate of 5 PPS; nodes 2, 5, and 11 have a rate of 18 PPS; nodes 3, 8, and 10 have a rate of 35 PPS; and nodes 4, 7, and 9 have a rate of 50 PPS.
We evaluate the efficacy of the IEEE 802.15.4 default scheme in conjunction with the proposed DNBP-CCA schemes in the initial scenario. The second scenario compares the suggested DNBP-CCA schemes and existing schemes, namely RDTM [39], CSTP-MAC [36], and TCP-CSMA/CA [35]. The evaluation includes essential measurements like packet drop rate (PDR), average throughput, packet delay and packet delivery ratio (PDR).
Fig. 8 shows the average PDR values between the default IEEE 802.15.4 methods and the suggested DNBP-CCA scheme. DNBP-CCA exhibits a 57.72% increase in PDR when producing varying data rates for each phase. The improvement can be credited to carefully selecting MAC parameters in the DNBP and DNCCA schemes, reducing conflicts among MSNs for channel access and enhancing reliability. When creating data rates for each process, ranging from 5 to 25, the PDR refinement ratio among DNBP-CCA and IEEE 802.15.4 is 69%. The variation in data rates is a significant contributing component to this improvement. Furthermore, when the data rates rise from 48 to 85, the enhancement ratio between DNBP-CCA and IEEE 802.15.4 amounts to 46.6%. The enhancement is due to the dynamic modifications made to the backoff period and waiting period for channel access in DNBP-CCA schemes, in contrast with the IEEE 802.15.4, which uses the static scheme with fixed backoff and waiting period durations. As a result, the static scheme leads to reduced reliability and higher collision rates.
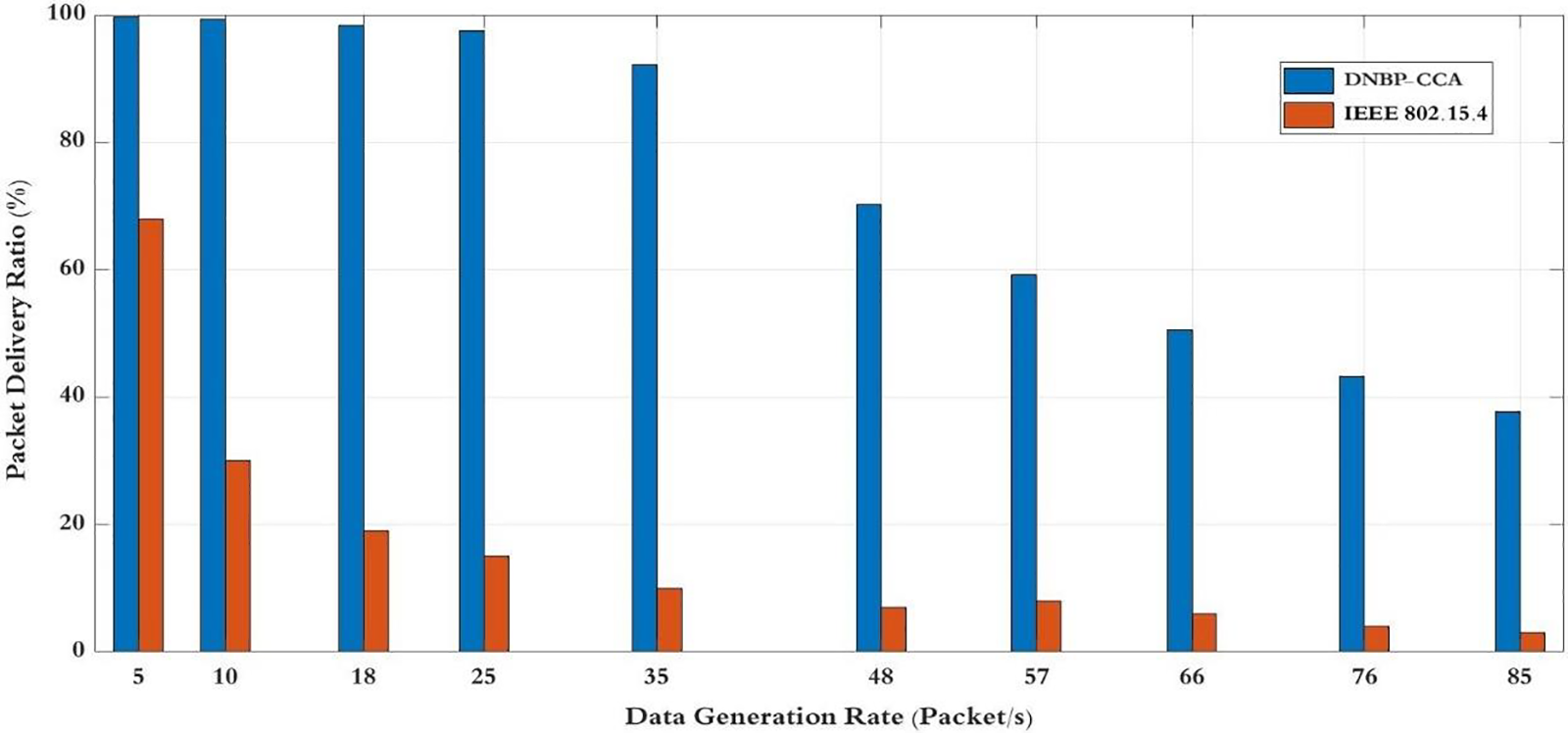
Figure 8: Packet delivery ratio for data generation rate
Fig. 9 depicts the mean packet delay, the time a data packet travels from the source to the destination. Packet delays can occur when collisions happen in the transmission channel, especially when different data rates are generated for each operation due to the backoff and CCA algorithms. The simulation findings indicate that the DNBP-CCA schemes proposed have an average delay of 40.8% less than the packet delay of the IEEE 802.15.4 network. The enhancement can be credited to the DNBP system, which utilizes fuzzy rules that consider inputs such as backoff index, channel clear, collision ratio, and data rate to anticipate optimal values for the subsequent random backoff period. In addition, the DNCCA system improves channel accessibility by considering factors such as acknowledgement ratio and buffer status. On the other hand, IEEE 802.15.4 networks encounter elevated collision probabilities among nodes, leading to amplified delays.
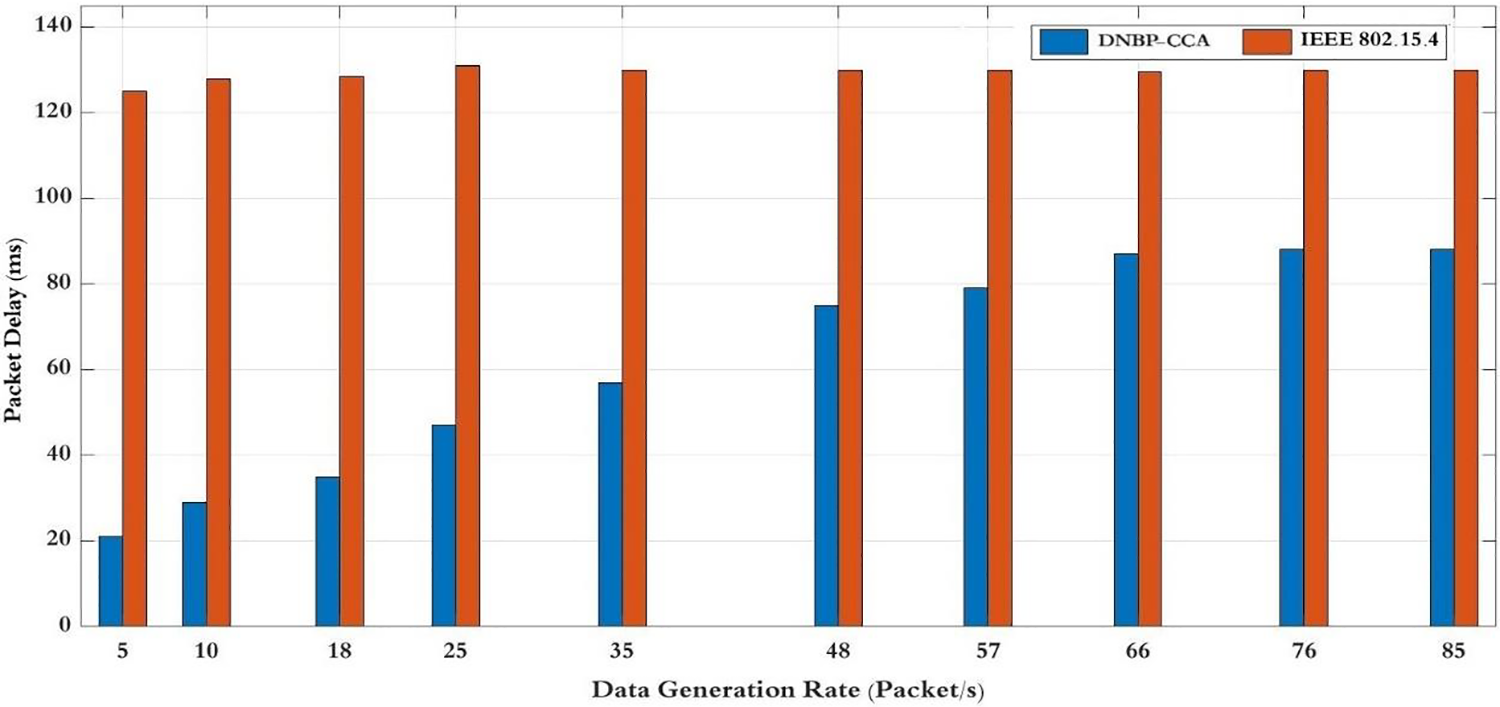
Figure 9: Packet delay for data generation rate
Fig. 10 illustrates the influence of sensor nodes on both channel access and the total throughput of the network. Average throughput refers to the number of data packets the coordinator receives during a defined period. The results of our study demonstrate that the DNBP-CCA schemes exhibit superior performance compared to the IEEE 802.15.4 protocol, especially when there is an increase in the generation of diverse data rates for each process. The performance improvement is credited to our DNBP solution, which utilizes fuzzy rules that consider the backoff index, channel clear, collision ratio, and data rate to forecast optimal values for the subsequent random backoff period. In addition, the DNCCA scheme utilizes inputs such as acknowledgement ratio and buffer status to extract CCA values, hence improving network performance and throughput for DNBP-CCA schemes. In contrast, the fixed waiting periods for access to the channel at IEEE 802.15.4 are significantly shorter than those in DNBP-CCA, leading to longer waiting times in DNBP-CCA. This discrepancy promotes heightened collisions of data packets in IEEE 802.15.4, resulting in reduced throughput measures.
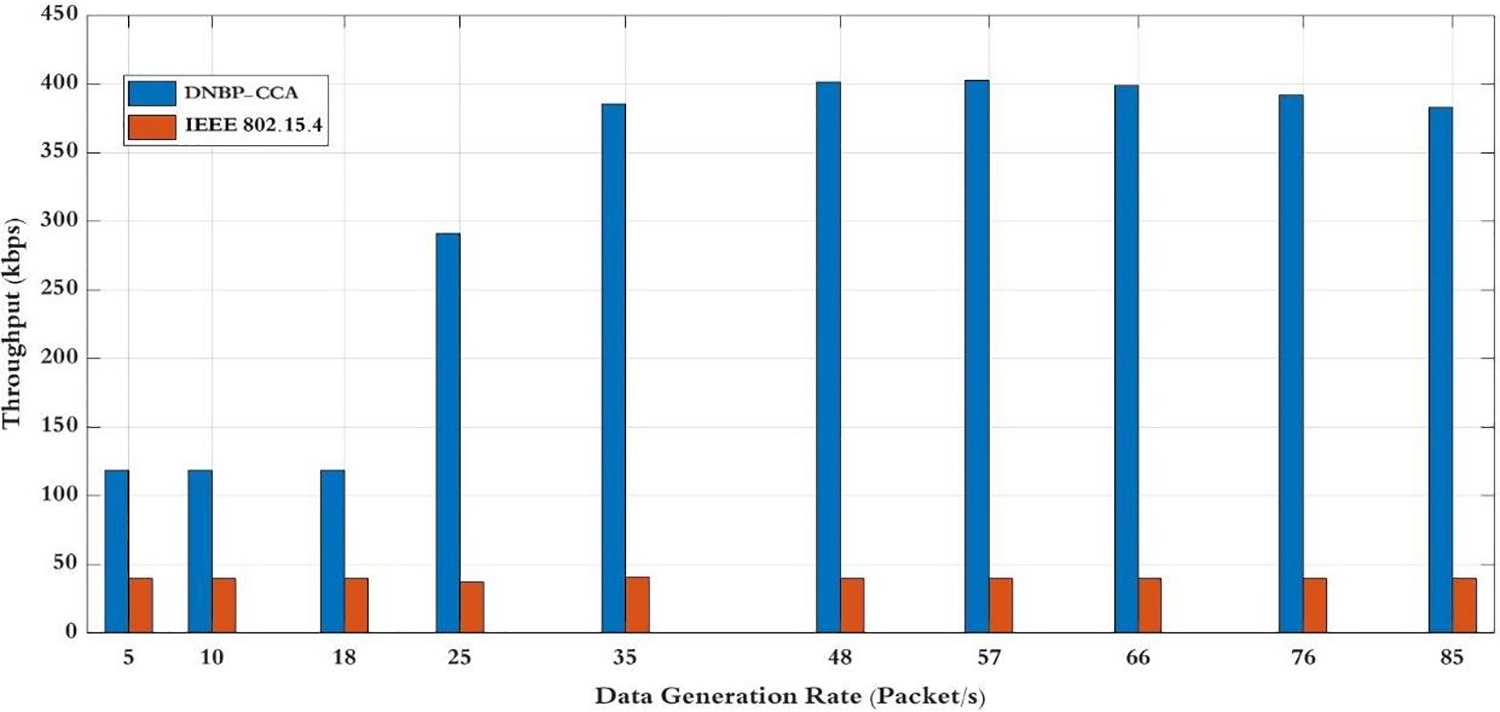
Figure 10: Throughput for data generation rate
The packet drop rates of two backoff and channel access control techniques, including the suggested scheme, are shown in Fig. 11. The diagram demonstrates a direct correlation between the number of packet dropouts and the generation of varied data rates for each activity. As the data rates for each process increase, the packets also increase, resulting in a longer waiting time between MSNs to access the channel. The exponential growth of the waiting interval leads to ambiguity in the rates at which packets are dropped. By implementing a varied range of data rates, from 5 to 25, for each process, the proposed DNBP-CCA technique achieves a significant 66% decrease in packet drop as opposed to IEEE 802.15.4. The utilization to multiple data rates is crucial in achieving this improvement. Furthermore, when the data rates rise from 48 to 85 in each process, the suggested technique exhibits a decrease ratio of 46.6% for packet drop compared to DNBP-CCA and IEEE 802.15.4. The decrease in performance can be due to the dynamic modifications in the lengths of the backoff periods and the dynamic changes in the waiting period for channel access between sensor nodes in DNBP-CCA schemes, compared to the static technique used at IEEE 802.15.4. The latter incorporates predetermined backoff and waiting interval durations, reducing missed packets and collisions among MSNs.
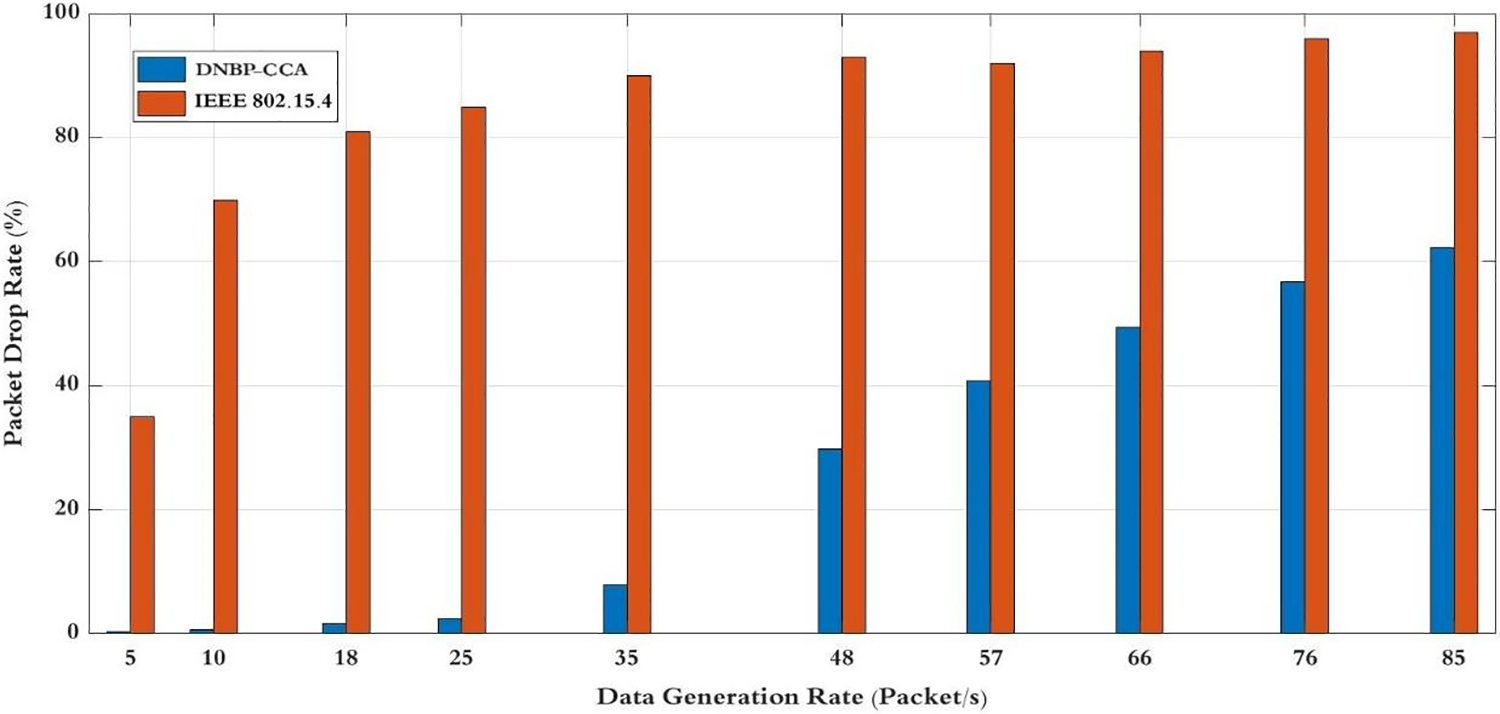
Figure 11: Packet drop rate for data generation rate
The second set of trials involved varying processes of MSNs, ranging from 2 to 12, with different data rates set at 5, 18, 35, and 50 pps to simulate a fixed time of 200 s. Figs. 12 to 15 present comparative results for PDR, packet delay, average throughput, and PLR for RDTM, CSTP-MAC, TCP-CSMA/CA, and the proposed DNBP-CCA schemes.
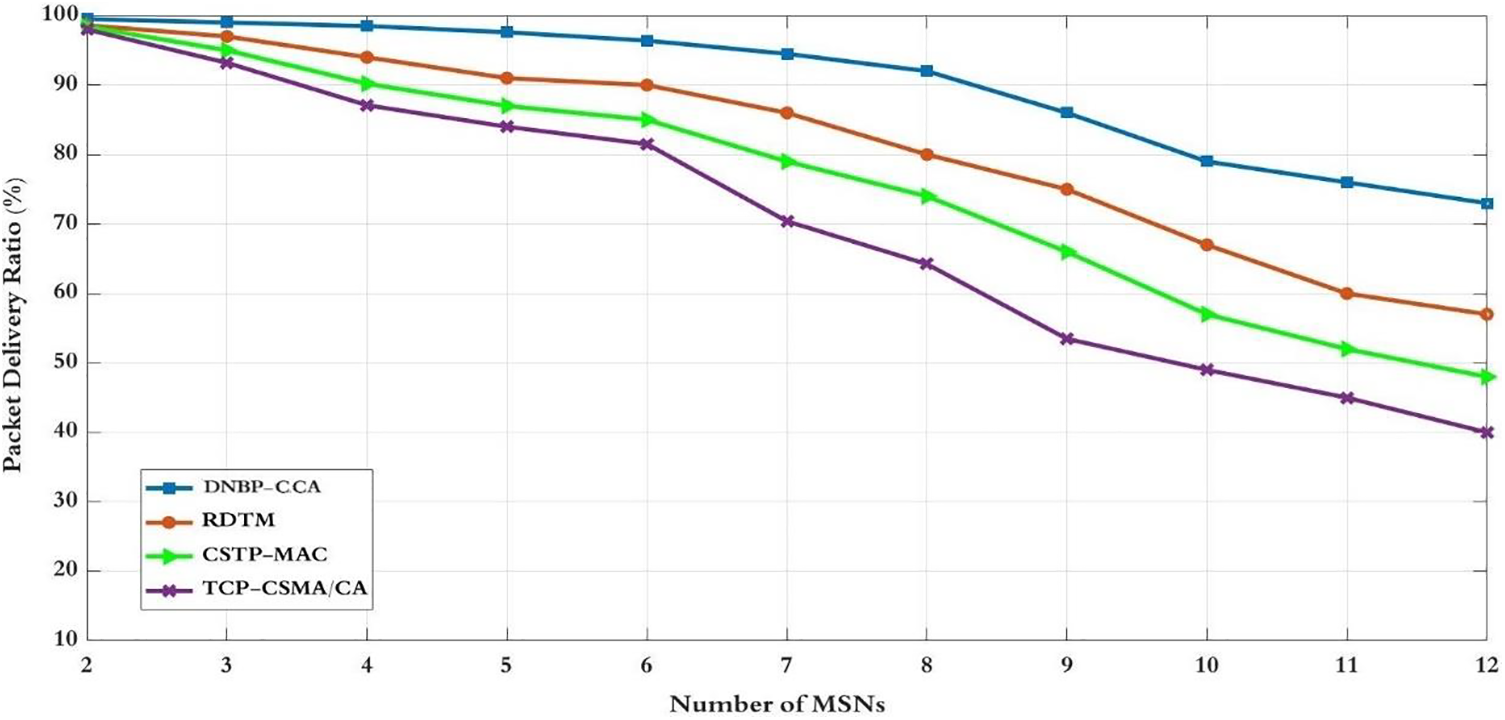
Figure 12: Packet delivery ratio for the number of MSNs
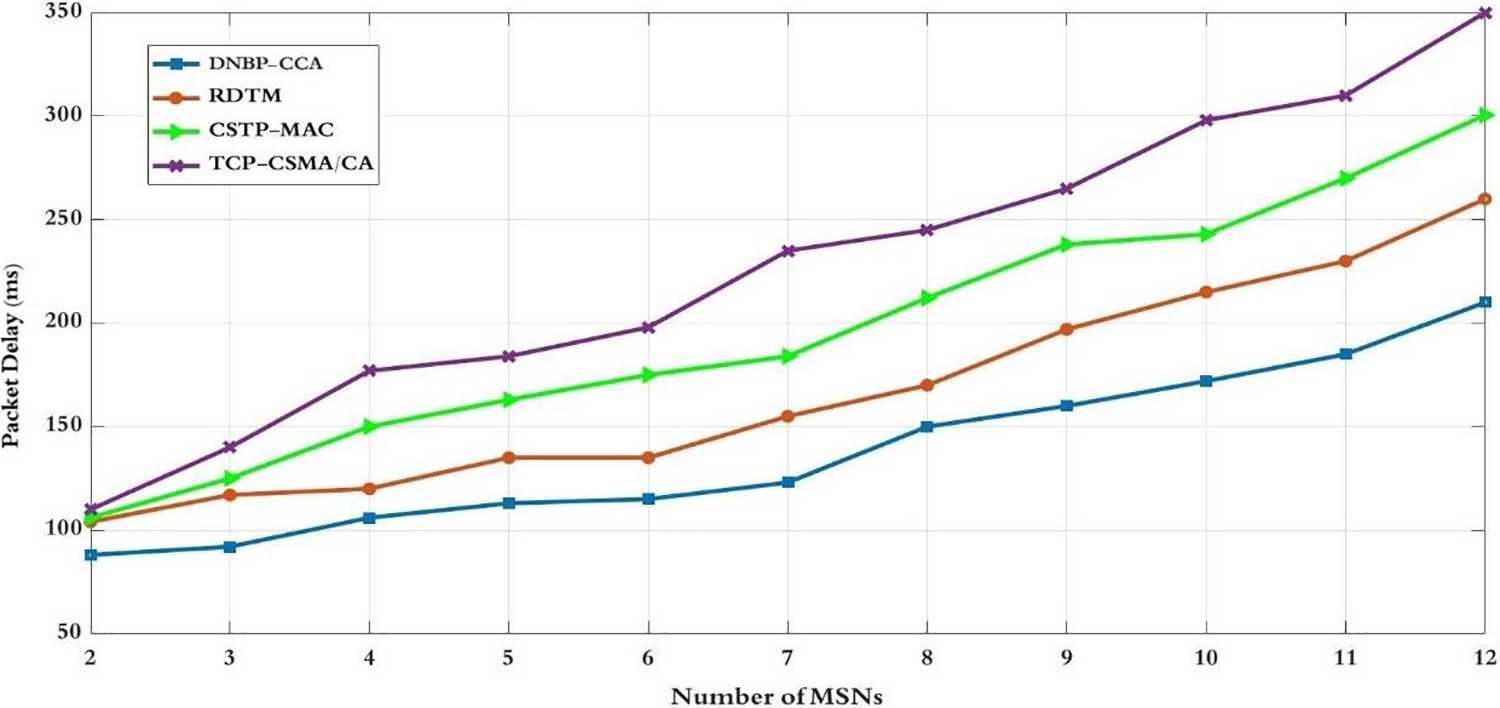
Figure 13: Packet delay for the number of MSNs
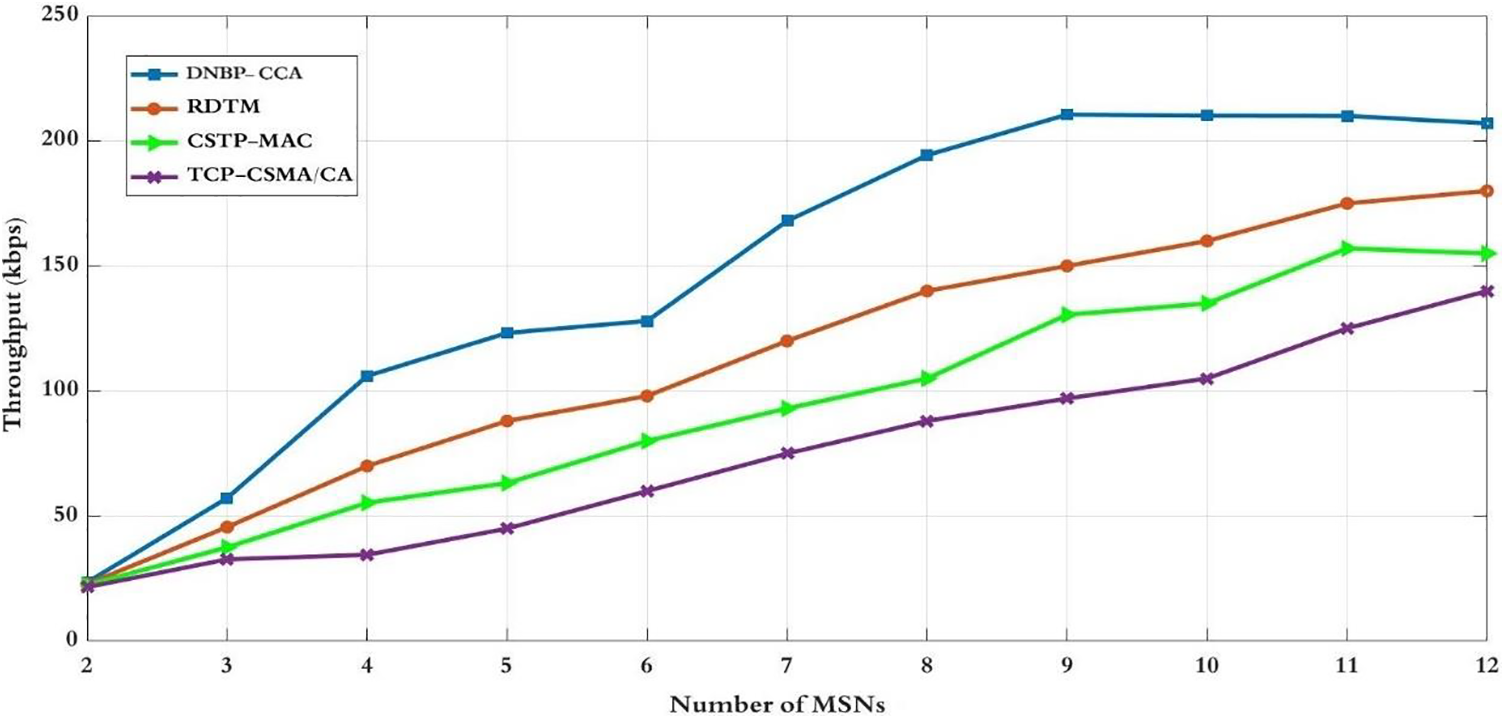
Figure 14: Throughput for the number of MSNs
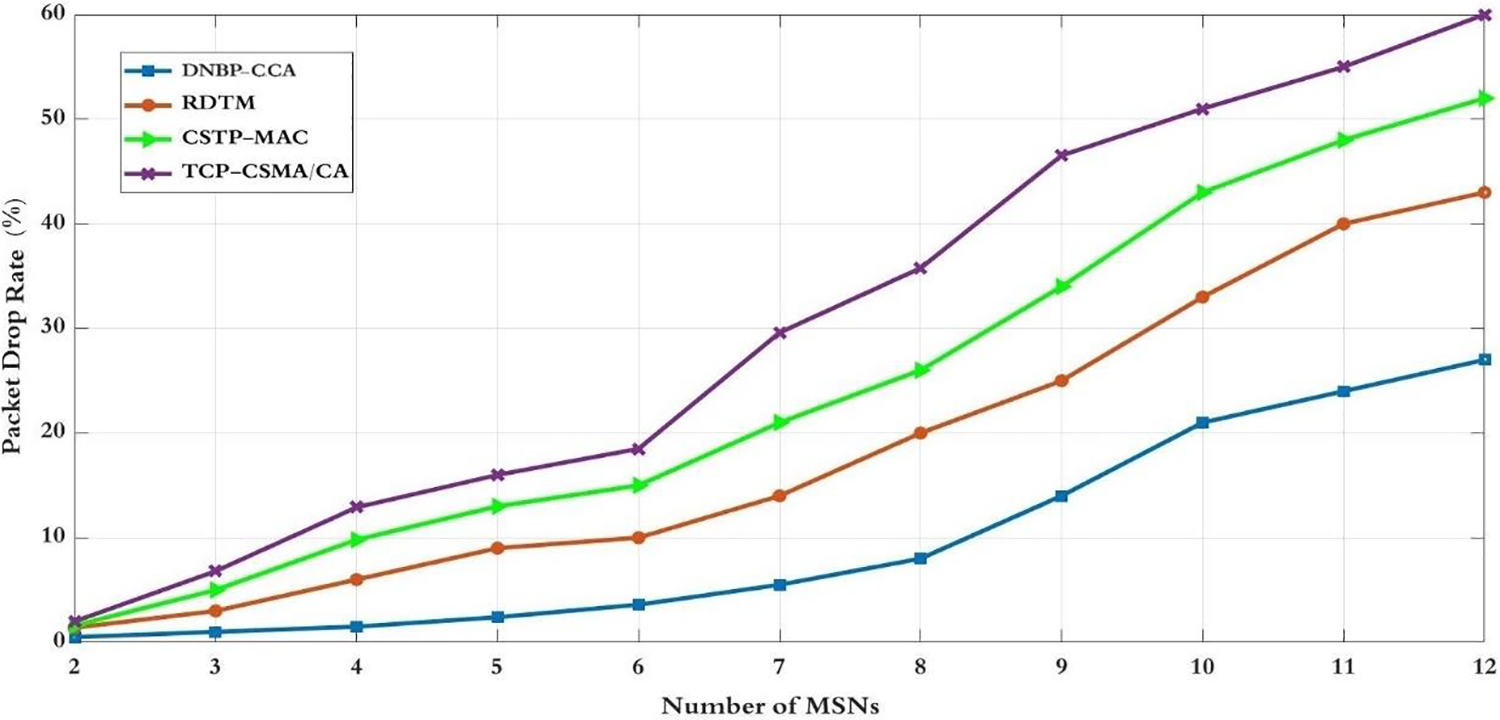
Figure 15: Packet drop rate for number of MSNs
Fig. 12 portrays the PDR across various backoff and channel access control schemes, illustrating distinct levels of network reliability. The PDR network effectiveness might gradually diminish as the number of nodes with diverse data rates increases unless the backoff period and channel access control are carefully regulated. Some schemes, such as CSTP-MAC, employ two traffic classes: High-priority data with the class of service = 0 and low-priority data with the class of service = 1. TCP-CSMA/CA allows various classes of service traffic, providing each scheme with a unique range of backoff slots to choose from. Nevertheless, the intricate backoff period algorithm introduces substantial computational overhead on MSNs and lacks CCA adaptation and packet retransmission algorithms, impacting PDR performance. In contrast, RDTM relies on backoff and CCA adaptation mechanisms. However, with more than six MSNs in the network with different data rates, it experiences a higher collision rate, leading to reduced PDR performance. Consequently, DNBP-CCA attains approximately 8.7% to 20.6% higher dependability than comparable schemes by utilizing a fuzzy logic-based backoff period and calculating channel access control to ensure fairness between nodes, ultimately enhancing PDR performance.
Fig. 13 depicts the average packet delay experienced by the MSNs network across various schemes, including DNBP-CCA, RDTM, CSTP-MAC, and TCP-CSMA/CA. Delay increases with more MSNs and different data rates as nodes spend more time in the backoff period. DNBP-CCA schemes dynamically adjust the backoff period using fuzzy logic, calculate channel access control appropriately, and reduce delay to foster fairness between MSNs. In contrast, CSTP-MAC calculates the backoff period based on two traffic classes (high and low priority data), and TCP-CSMA/CA calculates the backoff period based on different classes of service traffic (critical, reliability, delay, and non-constrained). However, both schemes lack CCA adaptation and packet retransmission algorithms, impacting delay performance. On the other hand, the RDTM scheme incorporates backoff and CCA adaptation mechanisms, but an increased number of MSNs with different data rates affects delay performance. Consequently, DNBP-CCA schemes exhibit the lowest average delay between nodes for channel access.
Fig. 14 showcases the consistently fairly throughput observed in the proposed DNBP-CCA scheme as MSN numbers and heterogeneous data rates increase in the simulation networks. In contrast, systems lacking controlled channel access and regulated backoff periods, such as CSTP-MAC and TCP-CSMA/CA, exhibit increased packet collisions between nodes, negatively impacting network throughput. The DNBP-CCA system adeptly anticipates the uptick in data rates between nodes. Unlike CSTP-MAC, which employs two traffic classes, and TCP-CSMA/CA, allowing various classes of service traffic without CCA adaptation, these schemes experience limitations in access channel control and packet retransmission efficiency, resulting in inferior performance compared to the proposed solution. The DNBP-CCA system optimally triggers throughput based on parameters like backoff index, channel clear ratio, data rate, collision ratio for the backoff period, acknowledgement ratio, buffer status ratio for CCA, and the quantity of correctly received data. This ensures fairness in slotted CSMA/CA between MSNs. Additionally, while RDTM relies on backoff and CCA adaptation mechanisms, its performance diminishes with an increasing number of MSNs with different data rates, falling short of the proposed productivity. Consequently, DNBP-CCA establishes a superior throughput, offering 13% to 30% greater efficiency than comparable systems.
Fig. 15 shows the PDR for various backoff and access channel control schemes, illustrating different dropped packet levels. The network’s PDR may gradually increase with a growing number of MSNs having heterogeneous data rates if the backoff period and access channel control are not properly regulated. This complexity in channel access can lead to an elevated drop packet rate. While schemes like CSTP-MAC and TCP-CSMA/CA employ two traffic classes and permit various classes of service traffic, each scheme has a distinct range of backoff slots. Nevertheless, CSTP-MAC and TCP-CSMA/CA lack CCA adaptation, packet retransmission algorithms, and consideration of heterogeneous data rates, which limits their PDR performance. In contrast, RDTM relies on both backoff and CCA adaptation mechanisms. Nevertheless, a higher collision rate occurs with more than six MSNs in the network operating at different data rates, resulting in increased PDR performance. DNBP-CCA schemes employ fuzzy logic for backoff period determination and channel access control calculation to achieve lower data loss than similar schemes, promote fairness between nodes and reduce PDR performance.
The simulation outcomes demonstrate that the suggested DNBP-CCA system surpasses current approaches regarding packet delivery ratio at both high and low data rates. This improvement is reflected in lower data-dropping ratios and delays, contributing to a total rise in average throughput. The key to this success lies in applying dynamic TSK fuzzy logic, which dynamically controls the optimal output for the next backoff period. Input parameters like the backoff index, channel clear ratio, data rate, and collision ratio are based on this decision. Additionally, the DNBP-CCA schemes optimize the next channel access control by taking input parameters such as buffer status ratio and acknowledgement ratio. As a result, these schemes significantly reduce packet drop rates and average delays, showcasing their effectiveness. The proposed DNBP-CCA schemes demonstrate a practical reduction in packet-dropping, leading to increased throughput in healthcare patient monitoring. This improvement could decrease reliance on costly facilities. Doctors can access patient information anytime and anywhere within the hospital setting.
This work introduces the Dynamic Next Backoff Period and Clear Channel Assessment (DNBP-CCA) schemes to enhance the dependability of data transmission, reduce collisions and attain fairness between sensor nodes based on the CAP in IEEE 802.15.4 Body Area Networks (BAN). Schemes in the control strategy offer the main benefit of enabling nodes to create DNBP and DNCCA schemes. When dealing with varying data rates, these schemes help regulate channel access and data transmission to the coordinator. The TSK fuzzy model controller assesses the backoff index, channel clear ratio, data rate, and collision ratio to adjust the next backoff period. Conversely, the dynamic CCA analyzes the acknowledgement ratio and buffer status to modify the next clear channel assessment. Simulation outcomes of two scenarios demonstrate that the proposed system decreased the packet drop rate, decreased the average delay among nodes and improved the average throughput and packet delivery ratio compared to IEEE 802.15.4, whether the data rate was low, medium, or high in the first scenario. In the second scenario, the suggested scheme outperforms RDTM, CSTP-MAC, and TCP-CSMA/CA, demonstrating a significantly improved average throughput and packet delivery ratio with a lower packet drop rate and average delay between nodes. With the use of the suggested DNBP-CCA schemes, patient throughput can be increased, and hospital facility utilization can be reduced by providing more helpful monitoring data. Information on patients is always available to doctors. Future work would involve executing DNBP-CCA on advanced testbed configurations in genuine work scenarios. Additionally, there is a plan to examine dynamic access to channel and packet transportation in the presence of exterior interference, aligning with a current sending plan to MAC conducts based on IEEE 802.15.4e. A fog-assisted network with different data rates to monitor patients’ health has also been established.
Acknowledgement: None.
Funding Statement: This work was supported by Research Supporting Project Number (RSP2024R421), King Saud University, Riyadh, Saudi Arabia.
Author Contributions: The authors confirm their contribution to the paper as follows: Study conception and design: Abdulwadood Alawadhi, Abdullah Almogahed and Noradila Nordin; data collection: Abdulwadood Alawadhi and Abdullah Almogahed; analysis and interpretation of results: Abdulwadood Alawadhi, Abdullah Almogahed, Mohd. Hasbullah Omar, Noradila Nordin, Salman A. Alqahtani and Atif M. Alamri; draft manuscript preparation: Abdulwadood Alawadhi and Abdullah Almogahed. All authors reviewed the results and approved the final version of the manuscript.
Availability of Data and Materials: Data and material are included and referenced in the article.
Conflicts of Interest: The authors declare that they have no conflicts of interest to report regarding the present study.
References
1. A. Si-Ahmed, M. A. Al-Garadi, and N. Boustia, “Survey of machine learning based intrusion detection methods for internet of medical things,” Appl. Soft Comput., vol. 140, pp. 110227, 2023. doi: 10.1016/j.asoc.2023.110227. [Google Scholar] [CrossRef]
2. A. Alawadhi, R. B. Ahmad, A. Almogahed, and A. Abrar, “Deep learning techniques in mobile edge computing for internet of medical things,” in 2023 3rd Int. Conf. Emerg. Smart Technol. Appl. (eSmarTA), IEEE, 2023, pp. 1–6. doi: 10.1109/eSmarTA59349.2023.10293737. [Google Scholar] [CrossRef]
3. A. Ghubaish, T. Salman, M. Zolanvari, D. Unal, A. Al-Ali and R. Jain, “Recent advances in the internet-of-medical-things (IoMT) systems security,” IEEE Internet Things J., vol. 8, no. 11, pp. 8707–8718, 2020. doi: 10.1109/JIOT.2020.3045653. [Google Scholar] [CrossRef]
4. J. Shahid, R. Ahmad, A. K. Kiani, T. Ahmad, S. Saeed and A. M. Almuhaideb, “Data protection and privacy of the internet of healthcare things (IoHTs),” Appl. Sci., vol. 12, no. 4, pp. 1927, 2022. doi: 10.3390/app12041927. [Google Scholar] [CrossRef]
5. U. Pandey, P. Singh, R. Singh, N. P. Gupta, S. K. Arora and E. Nizeyimana, “Miniaturized ultrawideband microstrip antenna for IoT-based wireless body area network applications,” Wirel. Commun. Mob. Comput., vol. 2023, pp. 1–19, 2023. doi: 10.1155/2023/3950769. [Google Scholar] [CrossRef]
6. P. N. Srinivasu, G. JayaLakshmi, R. H. Jhaveri, and S. P. Praveen, “Ambient assistive living for monitoring the physical activity of diabetic adults through body area networks,” Mob. Inf. Syst., vol. 2022, no. 6, pp. 1–18, 2022. doi: 10.1155/2022/3169927. [Google Scholar] [CrossRef]
7. A. K. Sagar, S. Singh, and A. Kumar, “Energy-aware WBAN for health monitoring using critical data routing (CDR),” Wirel. Pers. Commun., vol. 112, no. 1, pp. 273–302, 2020. doi: 10.1007/s11277-020-07026-6. [Google Scholar] [CrossRef]
8. S. Javaid, S. Zeadally, H. Fahim, and B. He, “Medical sensors and their integration in wireless body area networks for pervasive healthcare delivery: A review,” IEEE Sens. J., vol. 22, no. 5, pp. 3860–3877, 2022. doi: 10.1109/JSEN.2022.3141064. [Google Scholar] [CrossRef]
9. A. M. O. Alawadhi, M. H. Omar, and N. Nordin, “IEEE 802.15.4 MAC protocol optimization in body sensor networks: A survey, outlook and open issues,” Int. J. Commun. Netw. Distrib. Syst., vol. 29, no. 3, pp. 315–340, 2023. doi: 10.1504/IJCNDS.2023.130568. [Google Scholar] [CrossRef]
10. M. S. Hajar, M. O. Al-Kadri, and H. K. Kalutarage, “A survey on wireless body area networks: Architecture, security challenges and research opportunities,” Comput. Secur., vol. 104, no. 1, pp. 102211, 2021. doi: 10.1016/j.cose.2021.102211. [Google Scholar] [CrossRef]
11. H. Su, M. -S. Pan, H. Chen, and X. Liu, “MDP-based MAC protocol for WBANs in edge-enabled ehealth systems,” Electron., vol. 12, no. 4, pp. 947, 2023. doi: 10.3390/electronics12040947. [Google Scholar] [CrossRef]
12. S. S. Bamber, N. Dogra, and M. Angurala, “Modified adaptive mechanism for optimizing IEEE 802.15.4 wpans for wireless sensor networks,” Wirel. Pers. Commun., vol. 128, no. 2, pp. 1391–1415, 2023. doi: 10.1007/s11277-022-10005-8. [Google Scholar] [CrossRef]
13. C. Yi and J. Cai, “Transmission management of delay-sensitive medical packets in beyond wireless body area networks: A queueing game approach,” IEEE Trans. Mob. Comput., vol. 17, no. 9, pp. 2209–2222, 2018. doi: 10.1109/TMC.2018.2793198. [Google Scholar] [CrossRef]
14. N. Alimorad, M. Maadani, and M. Mahdavi, “REO: A reliable and energy efficient optimization algorithm for Beacon-enabled 802.15.4-based wireless body area networks,” IEEE Sens. J., vol. 21, no. 17, pp. 19 623–19 630, 2021. doi: 10.1109/JSEN.2021.3091768. [Google Scholar] [CrossRef]
15. M. Morales-Sandoval, R. De-La-Parra-Aguirre, H. Galeana-Zapién, and A. Galaviz-Mosqueda, “A three-tier approach for lightweight data security of body area networks in e-health applications,” IEEE Access, vol. 9, pp. 146350–146365, 2021. doi: 10.1109/ACCESS.2021.3123456. [Google Scholar] [CrossRef]
16. J. Wang, H. Han, H. Li, S. He, P. Kumar Sharma and L. Chen, “Multiple strategies differential privacy on sparse tensor factorization for network traffic analysis in 5G,” IEEE Trans. Ind. Inform., vol. 18, no. 3, pp. 1939–1948, 2022. doi: 10.1109/TII.2021.3082576. [Google Scholar] [CrossRef]
17. A. Alawadhi, M. H. Omar, and N. Nordin, “A survey on IEEE 802.15.4 MAC protocols for body sensor networks,” in 6th Int. Conf. Internet Appl., Protoc. Serv., 2021, pp. 109–114. [Google Scholar]
18. J. Chen et al., “A revolution of personalized healthcare: Enabling human digital twin with mobile AIGC,” 2023. doi: 10.48550/arXiv.2307.12115. [Google Scholar] [CrossRef]
19. M. Abdulkarem, K. Samsudin, M. F. A. Rasid, and F. Z. Rokhani, “Contiki IEEE 802.15.4 MAC layer protocols: Implementation and evaluation of node’s throughput and power consumption,” Wirel. Pers. Commun., vol. 124, no. 3, pp. 2367–2390, 2022. doi: 10.1007/s11277-022-09468-6. [Google Scholar] [CrossRef]
20. A. Gallegos Ramonet and T. Noguchi, “Performance analysis of IEEE 802.15.4 bootstrap process,” Electron., vol. 11, no. 24, pp. 4090, 2022. doi: 10.3390/electronics11244090. [Google Scholar] [CrossRef]
21. A. Alawadhi, A. Almogahed, F. Mohammed, B. Ba-Quttayyan, and A. Hussein, “Improving performance metrics in WBANs with a dynamic next beacon interval and superframe duration scheme,” Heliyon, vol. 10, no. 5, pp. e26468, 2024. doi: 10.1016/j.heliyon.2024.e26468. [Google Scholar] [CrossRef]
22. S. Sarwar, R. Sirhindi, L. Aslam, G. Mustafa, M. M. Yousaf and S. W. U. Q. Jaffry, “Reinforcement learning based adaptive duty cycling in lrwpans,” IEEE Access, vol. 8, pp. 161157–161174, 2020. doi: 10.1109/ACCESS.2020.3021016. [Google Scholar] [CrossRef]
23. L. Alkama and L. Bouallouche-Medjkoune, “IEEE 802.15.4 historical revolution versions: A survey,” Comput., vol. 103, no. 1, pp. 99–131, 2021. doi: 10.1007/s00607-020-00844-3. [Google Scholar] [CrossRef]
24. M. G. Asuti and P. I. Basarkod, “An optimal clear channel assessment in IEEE 802.15.4 medium access control protocol for recurrent data transmission and long acknowledgement wait period,” Trans. Emerg. Telecomm. Technol., vol. 32, no. 2, pp. e4167, 2021. doi: 10.1002/ett.4167. [Google Scholar] [CrossRef]
25. S. Sharif, S. A. H. Seno, and A. Rowhanimanesh, “A fuzzy-logic-based fault detection system for medical internet of nano things,” Nano Commun. Netw., vol. 30, no. 12, pp. 100366, 2021. doi: 10.1016/j.nancom.2021.100366. [Google Scholar] [CrossRef]
26. S. Lata, S. Mehfuz, S. Urooj, and F. Alrowais, “Fuzzy clustering algorithm for enhancing reliability and network lifetime of wireless sensor networks,” IEEE Access, vol. 8, pp. 66013–66024, 2020. doi: 10.1109/ACCESS.2020.2985495. [Google Scholar] [CrossRef]
27. A. K. Das, B. Pratihar, and D. K. Pratihar, “Evolving fuzzy reasoning approach using a novel nature-inspired optimization tool,” Expert Syst. Appl., vol. 170, no. 6, pp. 114577, 2021. doi: 10.1016/j.eswa.2021.114577. [Google Scholar] [CrossRef]
28. J. Chen, C. Yi, S. D. Okegbile, J. Cai, and X. S. Shen, “Networking architecture and key supporting technologies for human digital twin in personalized healthcare: A comprehensive survey,” IEEE Commun. Surv. Tutorials, pp. 1, 2023. doi: 10.1109/COMST.2023.3308717. [Google Scholar] [CrossRef]
29. M. Gamal, N. Sadek, M. R. Rizk, and M. A. E. Ahmed, “Optimization and modeling of modified unslotted CSMA/CA for wireless sensor networks,” Alex. Eng. J., vol. 59, no. 2, pp. 681–691, 2020. doi: 10.1016/j.aej.2020.01.035. [Google Scholar] [CrossRef]
30. A. Alawadhi, A. Almogahed, and A. Abrar, “Recent advances in edge computing for 6G,” in 2022 Int. Conf. Intell. Technol., Syst. Serv. Internet Everything (ITSS-IoE), IEEE, 2022, pp. 1–6. doi: 10.1109/ITSS-IoE56359.2022.9990957. [Google Scholar] [CrossRef]
31. A. Alawadhi, A. Almogahed, and E. Azrag, “Towards edge computing for 6G internet of everything: Challenges and opportunities,” in 2023 1st Int. Conf. Adv. Innov. Smart Cities (ICAISC), IEEE, 2023, pp. 1–6. doi: 10.1109/ICAISC56366.2023.10085007. [Google Scholar] [CrossRef]
32. S. Moulik and K. Ray, “d-CARE: Context-aware regulation of backoff delay in wireless personal area networks,” in TENCON 2019–2019 IEEE Region 10 Conf. (TENCON), IEEE, 2019, pp. 135–140. doi: 10.1109/TENCON.2019.8929352. [Google Scholar] [CrossRef]
33. P. Sun, G. Li, and F. Wang, “An adaptive backoff mechanism for wireless sensor networks,” Future Internet, vol. 9, no. 2, pp. 19, 2017. doi: 10.3390/fi9020019. [Google Scholar] [CrossRef]
34. B. Khandish, E. Lee, H. Park, and J. B. Suk, “An efficient backoff scheme in wireless sensor networks,” in 2018 10th Int. Conf. Ubiquit. Future Netw. (ICUFN), IEEE, 2018, pp. 332–337. doi: 10.1109/ICUFN.2018.8437013. [Google Scholar] [CrossRef]
35. F. Masud, A. H. Abdullah, A. Altameem, G. Abdul-Salaam, and F. Muchtar, “Traffic class prioritization-based slotted-csma/ca for IEEE 802.15.4 mac in intra-WBANs,” Sens., vol. 19, no. 3, pp. 466, 2019. doi: 10.3390/s19030466. [Google Scholar] [PubMed] [CrossRef]
36. I. U. Onwuegbuzie, S. Abd Razak, I. Fauzi Isnin, T. S. Darwish, and A. Al-Dhaqm, “Optimized backoff scheme for prioritized data in wireless sensor networks: A class of service approach,” PLoS One, vol. 15, no. 8, pp. e0237154, 2020. doi: 10.1371/journal.pone.0237154. [Google Scholar] [PubMed] [CrossRef]
37. Y. H. Zhu, L. Jia, and Y. Zhang, “Enhancing channel contention efficiency in IEEE 802.15.4 wireless networks,” Sens., vol. 22, no. 4, pp. 1600, 2022. doi: 10.3390/s22041600. [Google Scholar] [PubMed] [CrossRef]
38. H. Hajaje, M. Khanafer, Z. E. A. Guennoun, J. Israr, and M. Guennoun, “A collision-aware MAC protocol for efficient performance in wireless sensor networks,” Int. J. Adv. Comput. Sci. Appl., vol. 12, no. 3, 2021. doi: 10.14569/issn.2156-5570. [Google Scholar] [CrossRef]
39. K. G. Mkongwa, C. Zhang, and Q. Liu, “A reliable data transmission mechanism in coexisting ieee 802.15.4-beacon enabled wireless body area networks,” Wirel. Pers. Commun., vol. 128, no. 2, pp. 1019–1040, 2023. doi: 10.1007/s11277-022-09987-2. [Google Scholar] [CrossRef]
40. K. Ray, V. Pal, G. Singal, and S. Moulik, “Fuzzy-MAC: An fis based mac protocol for a multi-constrained traffic in wireless body area networks,” Comput. Commun., vol. 195, no. 3, pp. 451–462, 2022. doi: 10.1016/j.comcom.2022.09.013. [Google Scholar] [CrossRef]
41. J. Santos, C. Torres-Machi, S. Morillas, and V. Cerezo, “A fuzzy logic expert system for selecting optimal and sustainable life cycle maintenance and rehabilitation strategies for road pavements,” Int. J. Pavement Eng., vol. 23, no. 2, pp. 425–437, 2022. doi: 10.1080/10298436.2020.1751161. [Google Scholar] [CrossRef]
42. D. V. Petrović, M. Tanasijević, S. Stojadinović, J. Ivaz, and P. Stojković, “Fuzzy model for risk assessment of machinery failures,” Symmetry, vol. 12, no. 4, pp. 525, 2020. doi: 10.3390/sym12040525. [Google Scholar] [CrossRef]
43. S. Gupta, I. Snigdh, and S. K. Sahana, “A fuzzy logic approach for predicting efficient lora communication,” Int. J. Fuzzy Syst., vol. 24, no. 5, pp. 1–9, 2022. doi: 10.1007/s40815-021-01233-4. [Google Scholar] [CrossRef]
44. J. Zhang, X. Wang, and X. Shao, “Design and real-time implementation of takagi-sugeno fuzzy controller for magnetic levitation ball system,” IEEE Access, vol. 8, pp. 38221–38228, 2020. doi: 10.1109/ACCESS.2020.2971631. [Google Scholar] [CrossRef]
45. M. Sharif and A. Sadeghi-Niaraki, “Ubiquitous sensor network simulation and emulation environments: A survey,” J. Netw. Comput. Appl., vol. 93, no. 2, pp. 150–181, 2017. doi: 10.1016/j.jnca.2017.05.009. [Google Scholar] [CrossRef]
46. V. C. Ferreira, C. Albuquerque, and D. C. Muchaluat-Saade, “Channelaware gait-cycle-based transmission in wireless body area networks,” IEEE Sens. J., vol. 22, no. 10, pp. 10009–10017, 2022. doi: 10.1109/JSEN.2022.3166695. [Google Scholar] [CrossRef]
47. M. Kumar and S. Hussain, “Simulation model for wireless body area network using castalia,” in 2022 1st Int. Conf. Inform. (ICI), IEEE, 2022, pp. 204–207. doi: 10.1109/ICI53355.2022.9786924. [Google Scholar] [CrossRef]
48. N. Z. Cedeño, O. P. Asqui, and E. E. Chaw, “Analysis of the performance of wireless sensor networks with mobile nodes under the AODV protocol,” in Inf. Technol. Syst.: Proc. ICITS 2020, Springer, 2020, pp. 255–264. doi: 10.1007/978-3-030-40690-5_25. [Google Scholar] [CrossRef]
Cite This Article
 Copyright © 2024 The Author(s). Published by Tech Science Press.
Copyright © 2024 The Author(s). Published by Tech Science Press.This work is licensed under a Creative Commons Attribution 4.0 International License , which permits unrestricted use, distribution, and reproduction in any medium, provided the original work is properly cited.


 Submit a Paper
Submit a Paper Propose a Special lssue
Propose a Special lssue View Full Text
View Full Text Download PDF
Download PDF Downloads
Downloads
 Citation Tools
Citation Tools