 Open Access
Open Access
ARTICLE
Elevating Image Steganography: A Fusion of MSB Matching and LSB Substitution for Enhanced Concealment Capabilities
1 Department of Information Technology, The Islamia University of Bahawalpur, Bahawalpur, 63100, Pakistan
2 Department of Computer Science, The Islamia University of Bahawalpur, Bahawalpur, 63100, Pakistan
3 School of Computer Science and Engineering, Yeungnam University, Gyeongbuk, 38541, Korea
* Corresponding Author: Gyu Sang Choi. Email:
(This article belongs to the Special Issue: Multimedia Encryption and Information Security)
Computers, Materials & Continua 2024, 79(2), 2923-2943. https://doi.org/10.32604/cmc.2024.049139
Received 28 December 2023; Accepted 03 April 2024; Issue published 15 May 2024
Abstract
In today’s rapidly evolving landscape of communication technologies, ensuring the secure delivery of sensitive data has become an essential priority. To overcome these difficulties, different steganography and data encryption methods have been proposed by researchers to secure communications. Most of the proposed steganography techniques achieve higher embedding capacities without compromising visual imperceptibility using LSB substitution. In this work, we have an approach that utilizes a combination of Most Significant Bit (MSB) matching and Least Significant Bit (LSB) substitution. The proposed algorithm divides confidential messages into pairs of bits and connects them with the MSBs of individual pixels using pair matching, enabling the storage of 6 bits in one pixel by modifying a maximum of three bits. The proposed technique is evaluated using embedding capacity and Peak Signal-to-Noise Ratio (PSNR) score, we compared our work with the Zakariya scheme the results showed a significant increase in data concealment capacity. The achieved results of our work show that our algorithm demonstrates an improvement in hiding capacity from 11% to 22% for different data samples while maintaining a minimum Peak Signal-to-Noise Ratio (PSNR) of 37 dB. These findings highlight the effectiveness and trustworthiness of the proposed algorithm in securing the communication process and maintaining visual integrity.Keywords
Nowadays, steganography stands as one of the most dynamic, private, and secure communication techniques [1], proving to be a prevalent and renowned method that offers enhanced security and serves as an alternative communication system. It is the procedure of concealing information within various mediums like images, audio, and videos, essential for secure communication [2]. The medium containing the hidden message is referred to as the stego-object. Among all media, images are the most utilized in steganography due to their popularity and availability [3]. In digital image steganography, methods are classified into spatial domain techniques [4] which manipulate pixel values directly, and frequency domain techniques [5], which alter the frequency components of the image. The application of steganography used worldwide in every field includes hiding the medical history of patients within their X-rays and scans [6–8], secure localization of nodes in sensor networks [9], smart tags on mobile devices [10], applied to the protection of biometric data, protection of IP and hiding individual information in smart identity card [11], employ for authentication purposes [12], sharing information between mobile devices and clouds [13]. This integration of steganography with cybersecurity measures underscores its importance in maintaining data integrity and confidentiality across various applications [14,15].
Despite its prevalence, steganography encounters a pressing challenge in safeguarding the confidentiality of transmitted data. Concealing the message within an image alters its statistics. Steganographic techniques must ensure that this alteration is minimal, thereby evading suspicion by unauthorized parties. With detection techniques evolving rapidly, traditional steganographic methods are increasingly vulnerable, posing a significant threat to secure communication channels. Furthermore, intruders often exploit vulnerabilities in steganographic systems through histogram analysis or by assessing the visual imperceptibility of the image. These factors greatly impact the effectiveness of steganographic methods; for instance, increasing the number of bits used to hide data alters the image’s statistics and affects its visual imperceptibility. As a result, researchers are continually striving to develop approaches that allow for the hiding of more data with minimal changes to the image, ensuring that the message remains secure from attackers. Payload capacity, imperceptibility, and robustness are three essential properties to test the effectiveness of any steganographic approach [16,17]: (1) Payload capacity refers to the amount of data hidden within a cover media (2) Imperceptibility refers to the human visual system identifying the changes in the cover images with the naked eye or using statistics. It is commonly assessed through metrics such as PSNR, where higher PSNR values indicate better imperceptibility. In essence, a higher PSNR signifies reduced distortion or alteration in the cover image due to the embedded information. (3) Robustness is measured as the ability of the hidden message to remain accurate even if the stego image undergoes various processing such as cropping, blurring, scaling, filtering, etc. The increase in these three parameters suggests the better security of the data communications algorithm. However, improving all three parameters at once is a challenging task.
The earlier approaches to steganography primarily relied on LSB (Least Significant Bit) substitution [18–22], where secret data is directly embedded into specific regions of the image by replacing the least significant bits. This method was popular due to its simplicity and minimal impact on the visual appearance of the cover image. However, it had its limitations. As the demand for hiding more data increased, it required changing more bits directly. Typically, these methods could utilize at most three LSBs to minimize the chances of detection, as changes in LSBs are less noticeable. Nonetheless, the direct alteration of more bits increased the risk of detection and compromised the security of the hidden message. Our work addresses the limitations of earlier steganographic approaches, particularly the direct changing of LSBs, by introducing a method. Instead of directly substituting message bits into the LSB, our approach involves comparing pairs of message bits with pairs of MSB (Most Significant Bit) bits. When a pair matches, we encode this matching information into the LSB. By doing so, we can store 2 bits of data with only one change in the LSB. We extend this concept by consecutively matching pairs in all MSBs, forming three pairs in total, to fully utilize the byte capacity and store more data efficiently.
The proposed approach offers several advantages over traditional LSB-based steganographic methods. Firstly, by utilizing pair-wise matching of message and MSB bits, we can hide more data with minimal changes to the LSB, thereby reducing the risk of detection. This not only enhances the security of the hidden message but also maintains the visual integrity of the cover image. However, traditional LSB-based methods often face limitations in achieving a balance between payload capacity and imperceptibility. Increasing the payload capacity by directly altering LSBs may lead to noticeable distortions in the cover image, compromising its visual quality and raising suspicion among potential adversaries. Secondly, while our method maximizes the utilization of the byte capacity by encoding information in three pairs of MSBs, allowing for efficient storage of additional data, traditional LSB-based techniques may struggle to maintain robustness against various image processing operations. These limitations can undermine the effectiveness of steganographic communication, particularly in scenarios where data integrity and covert communication are paramount. To evaluate the effectiveness of our approach, we conducted extensive experiments comparing it with existing LSB-based techniques. The results demonstrate that our method outperforms traditional approaches in terms of data hiding capacity and resistance to detection. This novel approach represents a significant advancement in steganographic techniques, offering improved security and efficiency in covert communication.
The results of our experiments provide quantitative insights into the efficacy of our proposed steganographic approach. We measured the embedding capacity of our method, which quantifies the amount of data that can be hidden within the cover image. Additionally, we evaluated the Peak Signal-to-Noise Ratio (PSNR) value, which indicates the quality of the stego-image compared to the original cover image. Our findings indicate that our approach achieves a significant increase in embedding capacity while maintaining high PSNR values, indicating minimal distortion to the cover image. These results demonstrate the effectiveness of our method in efficiently hiding large amounts of data within cover images while preserving their visual quality.
The proposed study makes the following significant contributions:
1. Development of a steganography scheme focused on achieving high embedding capacity while maintaining visual imperceptibility by utilizing images as cover media to conceal data.
2. Developed a novel approach that involves mapping data into the LSB of cover pixels, with the mapping information stored within the LSB itself, differing from direct LSB substitution techniques.
3. Developed a method to conceal up to six bits per pixel/byte using only three LSBs, thereby addressing the identified research gap and advancing the field of steganography.
The rest of the paper is structured as follows. Section 2 describes the details of earlier studies. In Section 3, we present our proposed embedding and extracting scheme. Section 4 demonstrates experimental details and results. Finally, the conclusion is presented in Section 5.
This section will offer a comprehensive literature review of current steganography techniques, with a primary focus on the amalgamation of LSB and MSB methodologies. This emphasis is chosen as the proposed work centers on MSB matching and LSB substitution. Steganography techniques have been used for centuries. However, it gained more popularity during World War II when undetectable ink was utilized to compose data on paper so that no one could detect its hidden message [3] and since digital technologies. Although many highly protected and robust techniques have been presented so far [23–26], where these are progressing towards optimizing for better performance. Numerous steganographic algorithms have been proposed by the researchers based on LSB substitution [27–30], some key ones have been discussed in the following paragraphs.
Yang et al. [19] pioneered the adaptive LSB method of steganography, which exploits the cover object’s edges, brightness, and texture to compute the number of k LSBs for hiding information. His work shows that a pixel in the noise-non-sensitive area has a higher value of k than that in noise-sensitive regions. The edge area can tolerate fewer changes compared to a highly textured portion of an image but not more than a smooth area. Also, the LSBs are computed by the high-order bits instead of all bits of a pixel to achieve a more secure system. This method achieves the value of PSNR of 39 dB. Similarly, another adaptive LSB embedding technique is proposed by Khodaei et al. [23] which utilizes the pixel value differencing (PVD) characteristics. The cover images are divided into two consecutive pixel blocks. Further, the difference between the two pixels is computed to estimate the number of secret bits that can be embedded into the LSB of these neighboring pixels. This method also employs a readjustment process to keep the difference of stego-pixel with respective ranges before and after embedding. This method achieves a larger payload capacity by retaining the visual imperceptibility of 37 dB. In [20], an adaptive LSB substitution approach for data hiding is proposed based on edge detection. This method employs 4 LSBs during the embedding and shows an improvement in the payload capacity. However, it suffered from low imperceptibility and has a value of PSNR less than 35 dB.
Lee [30] applied the adaptive LSB method to color images of the smartphone, where various LSB replacements are made based on color channels (RGB), i.e., the method embedded 4 bits in the R channel, 2 bits in G, and 2 bits in B of the secret message. This method could hide 2.8 bits per channel and maintain the value of PSNR 43 dB. Lee’s technique employs only LSBs of every channel to hide the secret data. Similarly, in [24], another approach is presented by utilizing the RGB channels of color images. This study combines human visual properties with an adaptive LSB method to develop techniques for hiding data in an image. Two techniques are presented: One that takes into account the different sensitivities of the human eye to different color channels, allowing for different numbers of bits to be hidden in each channel, and another that utilizes the natural tendency for images to focus on their middle area, hiding data in a spiral pattern starting from the edges and moving towards the center. The amount of data hidden is determined by the length of the message, with any remaining bits hidden in the blue channel. The average PSNR for this method is 43.95 dB for various-sized secret messages. In [25], the LSB substitution approach is employed which works by dividing the cover image into two sections: The first section is used to hide data, and the other to store the embedding changes. The number of LSB substitutions is adaptive and varies from 1 to 5. This study shows an increase in the payload capacity; however, the visual quality of the stego image is affected due to extensive modifications of LSB values.
Sahoo et al. [6] proposed an LSB-based steganography method to protect the data of COVID-19 patients within their X-ray scans. Before hiding, the data is dually encrypted using DNA with a combination of a Baconian cipher. Firstly, the DNA encoding was applied to the binary-coded data, and then the resultant data was replaced with a 26-letter Baconian cipher. The X-ray scan is partitioned into n overlapping windows, and within each window, the specific region of interest is determined by analyzing the minimum mean intensity. This metric calculates the average brightness level within the window, allowing the identification of areas with the lowest average intensity, and aiding in the detection or analysis of targeted features or anomalies within the X-ray image. The data in each window is embedded with XOR operation between the window and cipher matrix. This algorithm is tested on various X-ray scans where the arbitrary information is hidden in each scan. However, the author does not provide any performance measures. Another study [31] introduces a novel Local Binary Pattern-based Reversible Data Hiding (LBP-RDH) technique, achieving a balance between perceptual transparency and hiding capacity by dividing the image into 3 × 3 blocks and utilizing LBP-based descriptors for embedding. Through XORing embedding bits with LBP codes and employing a pixel readjustment process, the method ensures minimal information loss during extraction, outperforming recent techniques in transparency measures and demonstrating robustness against various stego-attacks.
Several recent studies also utilize data compression techniques and LSB substitution to extend embedding capacity. Akhter et al. [21] proposed a combined LSB substitution and modulo-function method that compresses the message before embedding. The original message is divided into two sections, where each section of a message is stored into a different cover image using the 4-LSBs of a pixel. The result of the study shows that there is an improvement in payload capacity when using the modulo function by maintaining the value of PSNR from 34 to 40 dB. In [32], before hiding the secret message is compressed using the Huffman coding scheme. Also, the secret data is encoded with the Rivest-Shamir-Adleman (RSA) algorithm to increase security. Further, four sub-bands are obtained from the cover image using the discrete wavelet transform (DWT) technique. The compressed message is embedded in the LSB of the selected sub-band. The method has a value of PSNR 40 dB. Similarly, another image steganography was proposed with the concept of message compression before the embedding [26]. In this study, a compression algorithm known as GoldBach has been adopted to compress the secret message. GoldBach algorithm states that every even value or more significant than four can be represented as the sum of two odd primes. Then coded message is embedded in the LSBs of cover media. The algorithm is tested on various size messages, i.e., 16, 32, 48 KB, and obtains the value of PSNR 60, 57 dB, and 48 KB, respectively.
Fateh et al. [18] proposed a coding scheme to improve steganography capacity with the LSB revisiting approach. The secret message is divided into several blocks with a different n number of bits. To hide these secret bits,
Liao et al. [34] explore the use of cloud storage for steganography, focusing on embedding secret information into multiple images. It addresses the challenge of allocating embedding payload among a sequence of images to enhance security. The proposed adaptive payload distribution strategies leverage image texture features, offering improved security performance against modern steganalysis techniques. Furthermore, the article evaluates the detectability of multiple-image steganographic schemes compared to single-image steganalysis methods. Extensive experimental results highlight the effectiveness of the proposed payload distribution strategies in achieving better security performance. In [35], the authors address the issue of optimizing payload allocation in color image steganography to enhance security. Traditional schemes often allocate payloads equally across RGB channels, leaving room for improvement. The authors proposed a novel strategy that involves a channel-dependent payload partition approach based on amplifying channel modification probabilities. By simultaneously increasing modification probabilities across corresponding pixels in RGB channels, the embedding impacts can be clustered, enhancing steganographic security against channel co-occurrence detection. Experimental results demonstrate that the new schemes effectively concentrate embedding changes in textured regions, leading to improved resistance against modern color image steganalysis techniques.
In [22], a recursive approach to information hiding is presented through LSB, PVD shift, and modification of prediction error (MPE). This study image is divided into pixel blocks (2 × 1) classified into higher and lower texture areas. This pixel block is recursively utilized through MPE and PVD shifts to improve embedding capacity. The result of the study showed an improvement in embedding capacity by utilizing up to 4 LSB and maintaining visual quality to 38 dB. In [36], an enhanced LSB image steganography approach is presented, where the author proposes the embedding of a secret message specifically along the edges of an image. The proposed technique involves the categorization of image pixels into two and three categories. The first method distinguishes pixels in the smooth area and edge area, while the second method further divides pixels into the smooth area, intersection area, and edge area. Through this approach, the author demonstrates that the second method exhibits superior embedding capacity. In [4], authors focused on improving message capacity and security using the divide and modulus function in spatial domain steganography. The secret message is partitioned based on divide and modulus functions. Each byte in a message is divided by 16, the dividend is embedded into a cove. By keeping an image size of
Mohammad [37] presents a novel EMD-based reversible data hiding technique using dual-image modification lookup tables, replacing larger matrices. The method enables direct reversibility with minimal computational cost by modifying pixels in alternate columns of cover images. It achieves a one bit per pixel (bpp) embedding rate by embedding one 4-ary secret digit into each pixel. Simulation results exhibit a one bpp embedding rate and over 49 dB average Peak Signal Noise Ratio (PSNR) across test images. Singh et al. [38] introduce a DNA-based cryptographic scheme and access control model (DNACDS) to address security challenges in IoE-based cloud computing and big data. DNACDS utilizes Deoxyribonucleic Acid (DNA) computing to enhance security measures, incorporating the Station-to-Station Key Agreement Protocol (StS KAP) and Feistel cipher algorithms. Experimental results demonstrate DNACDS’s superior performance compared to other DNA-based security schemes, supported by theoretical security analysis highlighting its robust resistance capabilities. Similarly, Namasudra [39] proposes a novel cryptosystem employing DNA cryptography and steganography for securing cloud-based IoT infrastructures. The proposed system encrypts confidential data using a long secret key and hides it within an image, offering dual-layered security. Experimental evaluations demonstrate the effectiveness of the scheme in resisting security attacks and safeguarding data stored in the cloud-based IoT environment.
In [40], an edge detection-based steganography method is discussed. First, the image is divided into small blocks based on the histogram of the oriented gradient algorithm. Then, blocks of interest are selected based on the gradient magnitude and angle of the cover image. The Block of interest is further divided into
While various steganography techniques demonstrate commendable performance in concealing information within digital media, it is essential to acknowledge their inherent limitations. For instance, techniques [18] are susceptible to LSB detection and exhibit limited capacity for accommodating large datasets. The technique presented in [19] shows improved resistance to certain steganalysis methods, but it has a lower PSNR, indicating the possibility of visual artifacts. Furthermore, techniques [23] work well for grayscale images but have limited capacity for color images and are vulnerable to advanced steganalysis. Furthermore, the technique [20] reduces embedding capacity and displays sensitivity to image changes. Despite achieving high PSNR, the technique [26] is complex to implement and may be vulnerable to algorithm-specific attacks. Another technique [22] involves higher computational complexity and a limited capacity for high-quality images. The approach [32] has increased computational overhead and limited payload capacity. While offering high PSNR and good visual quality, reference [4] has limited embedding capacity and is vulnerable to spatial domain attacks. Finally, technique [40] shows improved resistance to specific steganalysis techniques but has limited robustness against advanced steganalysis methods.
The above literature review has provided a comprehensive overview of existing steganographic techniques and their applications. We have focused on studies that are directly comparable to our work or serve as the foundation for our proposed approach. It is important to note that while our methodology and results are based on these comparable studies, there are inherent differences that may affect direct comparison. For instance, many studies utilize color images with three channels per byte, allowing for the storage of three bytes of data per pixel. Additionally, variations in image sizes among different studies may impact the embedding capacity and overall performance of steganographic methods. Despite these differences, our review highlights the advancements and challenges in the field of steganography, paving the way for further research and development in secure communication techniques.
This paper proposes a steganographic algorithm based on MSB matching and LSB substitution to achieve higher embedding capacity with good invisibility of the stego-image. The proposed technique employs the mapping of secret message bits with the MSBs of cover media, where LSBs are utilized to store information on mapping bits. The embedding method requires input data from a cover image and a secret message to generate a stego image. On the other hand, the extraction process requires only a stego image and produces a hidden secret message. In the subsequent section, we presented our embedding and extracting algorithms. Fig. 1 depicts the proposed embedding scheme, it has three components which consist of a secrete message

Figure 1: Proposed embedding scheme
Case 1: In the embedding phase, a
Case 2: In case of unsuccessful comparison, the same message bits
Case 3: Again, in case of unsuccessful comparison, the same message bit
This process is repeated until complete
As one can observe from Fig. 1, the secret message bits pair are
The extraction process begins by examining each pixel or byte of the cover image. For the first pixel/byte, the algorithm checks the value of its least significant bit (LSB). If the LSB is set to 1, indicating that it contains hidden message data, the next two bits of the message are retrieved from the first and second most significant bits (MSB). This process continues for the second LSB, where if it is set to 1, the subsequent two bits of the message are retrieved from the second and third MSB. The same procedure applies to the third LSB. If any LSB is set to 0, it indicates that no message is hidden in the corresponding MSB pair. This systematic approach ensures the accurate extraction of the hidden message from the cover image.
The extraction phase works by reading the values of


The extraction process operates on each pixel of the source image S in the following order:
1. For each pixel in
2. If
3. If
4. If
This process is applied for all pixels in the source image S, where n is the total number of pixels in S.
For conducting the experiments, the following experimental environment was utilized: Python served as the primary programming language for implementation. The machine specifications included an Intel Core i5, 7th Generation processor with 16 GB of RAM, running on the Windows 10 operating system. Python (version 3.6.12) was specifically used for development. The dataset employed for experimentation was sourced from the USC-SIPI image database [41]. Visual Studio Code (VS Code) was utilized as the Integrated Development Environment (IDE) for coding and experimentation purposes.
A set of experiments are conducted on a standard image dataset taken from USC-SIPI [41] to prove the efficacy of the proposed algorithm The experimental setup includes many grayscale images of different textures (i.e., aerial, persons, vehicles, and other features) that are categorized into three identical sets referred to as volume 1, volume 2, and volume 3 based on image resolutions (L × W). Volume 1 has eight images of size 256 × 256, volume 2 has 51 images of size 512 × 512, and volume 3 comprises 29 images of size 1024 × 1024. To ensure the consistency of the algorithm, multiple iterations were performed to obtain results from each image. A few samples of cover images used for experiments are shown in Fig. 2.


Figure 2: Cover image dataset samples from USC-SIPI for experiments
For confidential message data, we employ a random number function that generates a set of values in a range of
Embedding capacity is another parameter to measure the performance of any steganography scheme. It represents the amount of data embedded in a cover image. To fairly evaluate the embedding capacity of the proposed scheme, we used various
For a comprehensive analysis, we categorized the evaluation of the proposed scheme in multiple sections. Section 4.4.1 presents the maximum and average embedding capacity with the respective psnr of all three volumes. In Section 4.4.2, a comparison of the proposed method with the earlier approach [29] is provided.
4.4.1 Embedding Capacity & PSNR
The proposed scheme is tested on the images of all three volumes as described in Subsection 4.2. To generate secret messages, we utilize a randomized function, generating messages of varying sizes to match the different capacities of the images for data concealment. We initialize the first message, m, with a size of n = 1024 bytes and increment it until reaching the saturation point of the embedding capacity. Thus, the value of
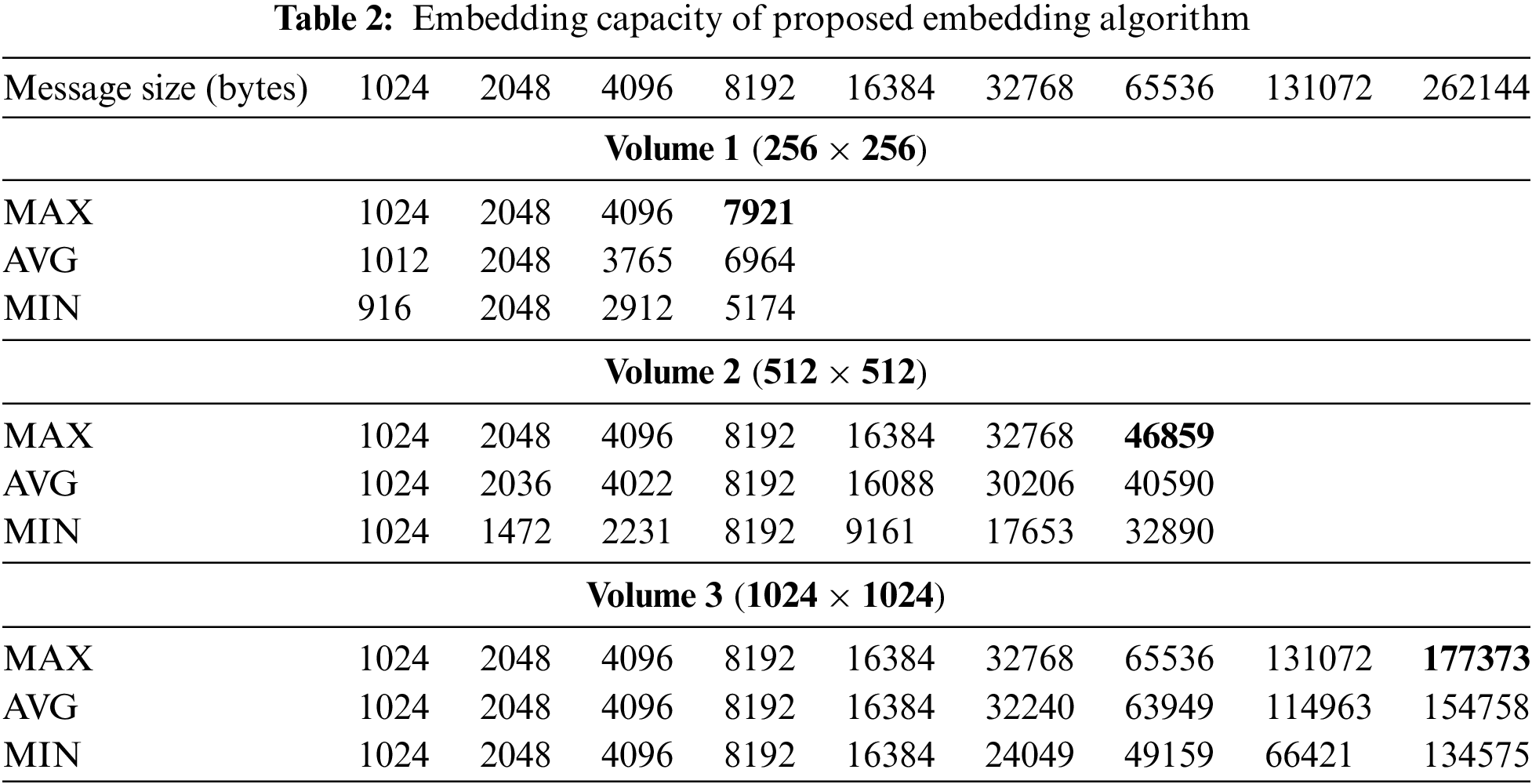
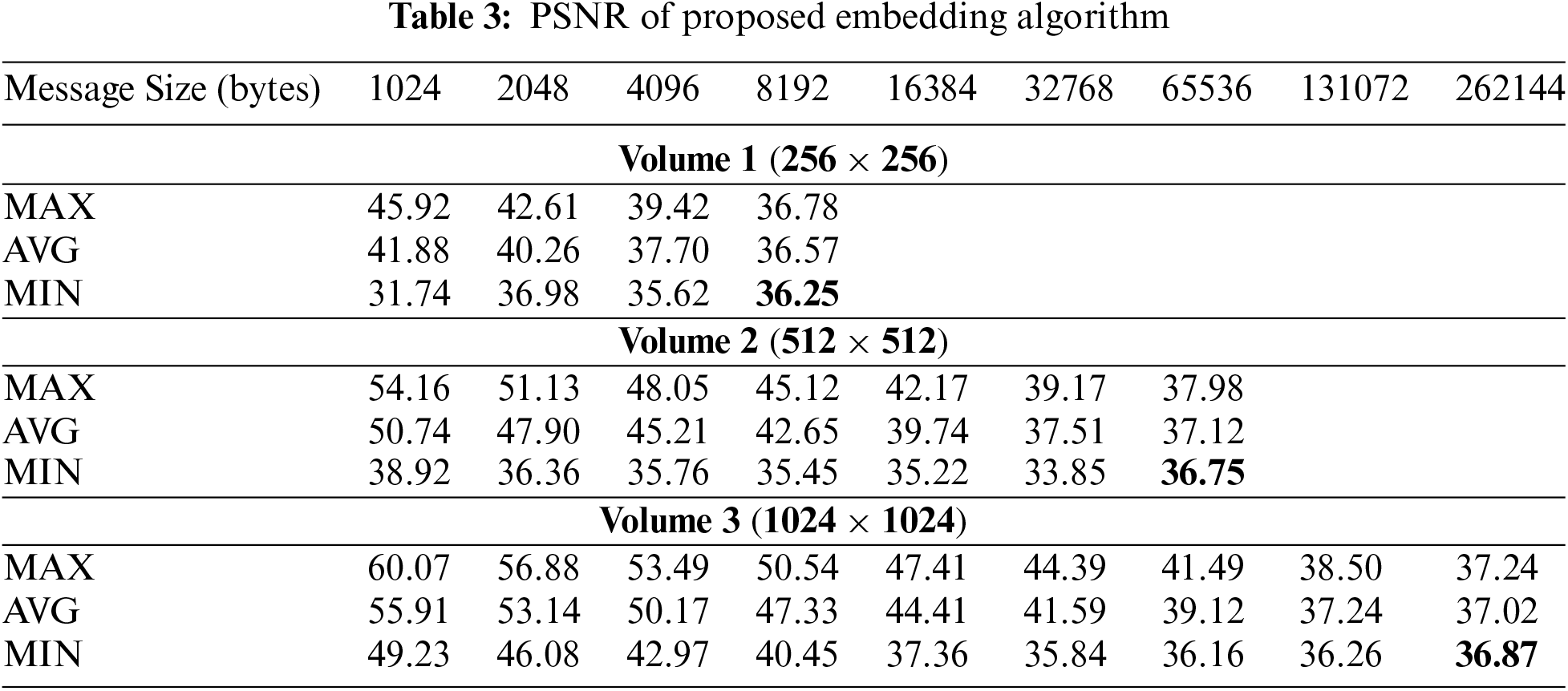
Similarly, volumes 2 and 3 uphold the value of psnr is 36 dB. Because all three volumes have different resolutions e, the maximum embedding capacity achieved on the smallest value of

Figure 3: The average embedding capacity & PSNR of all three volumes
4.4.2 Comparison of the Proposed Algorithm with Zakariya [29] Scheme
We compare our approach’s psnr, embedding capacity, and histogram with another recent approach by Zakariya [29] to evaluate its effectiveness. The proposed and Zakariya methods are based on LSB substitution and MSB mapping. Furthermore, Zakariya compared their method with earlier studies, where Zakariya claims the best embedding capacity. For a fair comparison of our approach against Zakariya, we need a synchronization phase. Thus, we implemented the Zakariya algorithm to reproduce their result on the dataset with the same messages. The embedding capacity comparison of both algorithms is represented using Table 4, Figs. 4 and 5.
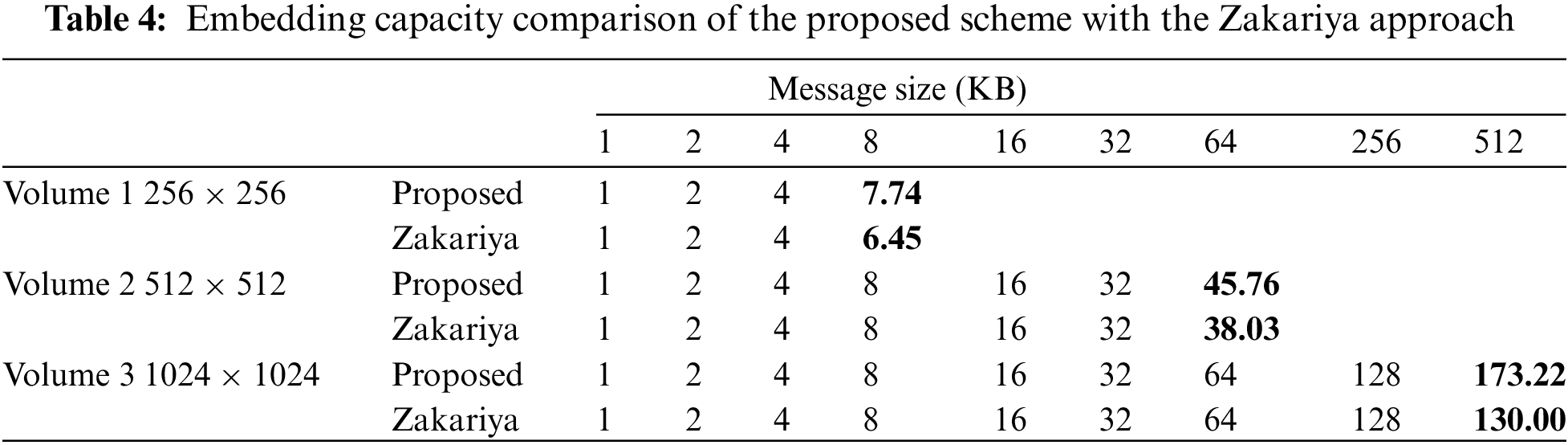

Figure 4: Embedding capacity comparison of proposed and Zakariya algorithms

Figure 5: Bit per-pixel comparison of the proposed and Zakariya algorithm
The projected result demonstrates that the proposed algorithm outperforms other schemes for embedding capacity in all three volumes. The experiment shows that both approaches have been saturated using the same message size for each volume, i.e., volume 1, volume 2, and volume 3 were saturated at 8, 64, and 256 KB, respectively. However, the proposed scheme can hide 1,315 more bits than the Zakariya approach in volume 1. Similarly, in volume 2, our approach can hide 7,913 more bits than the Zakariya approach, whereas, in volume 3, the embedding capacity difference between the proposed and Zakariya approaches is 44,254 bits. Furthermore, by considering image resolutions and maximum embedding capacities, we find that the proposed scheme averagely mapped 1 byte of secret messages utilizing 6 bytes of the cover image. In contrast, the Zakariya approach required 8 bytes of a cover image against 1 byte of secret data. Also, a bpp comparison is provided in Fig. 5 of both algorithms. The proposed algorithm maintains the bpp value of 0.97, 1.43, and 1.35, whereas the Zakariya achieves 0.81, 1.19, and 1.02.
For the psnr comparison, we selected three images (5.1.10, 1.2.06, 1.3.05) from each volume that hid the maximum secret message for the Zakariya algorithm. The reason for doing this is that we did not compare psnr simply in the range from maximum to minimum by considering that our approach can hide more data, where there is always a trade-off between embedding capacity and psnr. For example, the Zakariya approach can hide a maximum of 6500 bytes in image 5.1.10, 38000 bytes in image 1.2.06, and 133000 bytes in image 1.3.05. Hence, we created three constant size messages of
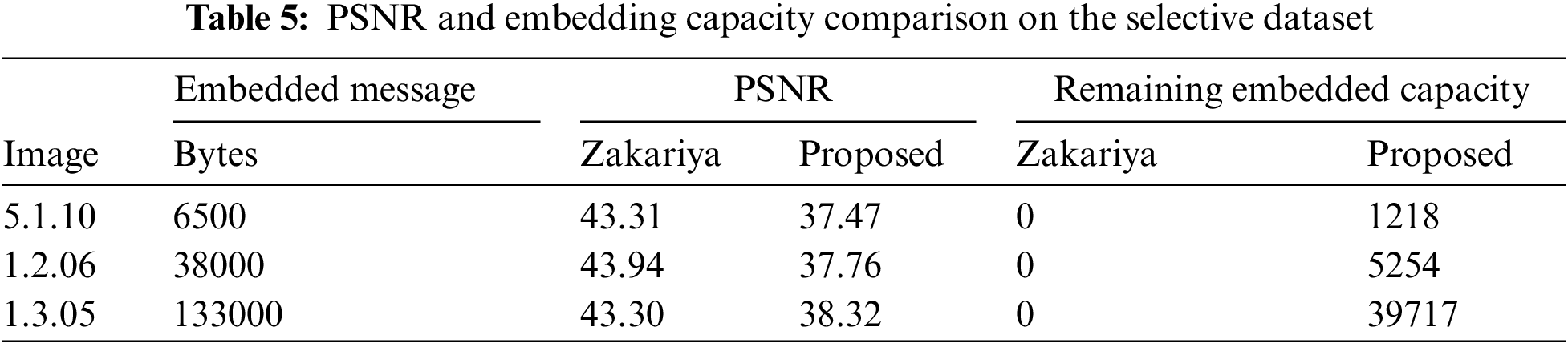

Figure 6: PSNR comparison of proposed with Zakariya approach using constant messages and images
Zakariya’s approach maintained psnr of 43 dB by hiding maximum data in all three images, while the proposed algorithm upholds the value of psnr 37 to 38 dB for the same message. Furthermore, the message sizes were set according to the Zakariya approach to maximum capacity. The results show that our approach can hide the exact data sizes by consuming fewer bytes in any image. At the same time, 5 dB psnr was compromised when compared to the Zakariya method best scenario. Also, the visual comparison between the original and resultant stego objects of these three images is represented in Fig. 7. We can see no significant change in the visual quality of the resulting stego-object of the three images. However, the stego-image generated with the Zakariya approach has a blurrier effect than the cover image. Fig. 7 indicates that the bit changes with our approach do not cause a visual modification detectable by human sight.

Figure 7: Visual comparison of original, Zakariya and proposed algorithm
Today the secure transmission of confidential data is an essential requirement of any communication network. Steganography is considered one of the best techniques to hide data from an intruder. Researchers from information security are continuously working to propose new algorithms or enhance existing steganography algorithms to achieve more reliable systems to hide data as much as possible and maintain the quality of cover media. This study presented a high embedding capacity steganography algorithm based on MSB matching and LSB substitution. The proposed solution offers high embedding capacity while guaranteeing the visual quality of stego images. This system covers the secret communication in the image, where each pixel of the cover image has been utilized to map a maximum of 6 bits of a secret message within each pixel’s 4 MSBs. This mapping process has been performed so that every message bit pair is matched with the consecutive MSB pair of the cover image in increasing form. A flag has been maintained to store the result of the comparison
The proposed algorithm was tested on a standard dataset, including grayscale images of multiple dimensions. We have used embedding capacity, psnr, and bpp to measure the effectiveness of this study. The proposed algorithm’s highest embedding capacity for
As for future research directions, there are opportunities to further enhance the hiding capacity of steganography algorithms while simultaneously preserving PSNR values, particularly in the context of grayscale and color images. Expanding the scope of investigation to include other types of cover media, such as audio signals and video frames, presents an intriguing avenue for exploration. By extending the application of steganography to these domains, researchers can unlock new possibilities for secure data transmission and communication across diverse multimedia platforms. Additionally, continued advancements in steganography methodologies and techniques will contribute to the ongoing evolution of secure data concealment strategies in the digital age.
Acknowledgement: We express our gratitude to our families and colleagues for offering us moral support.
Funding Statement: This work was supported in part by the Basic Science Research Program through the National Research Foundation of Korea (NRF) funded by the Ministry of Education (NRF-2021R1A6A1A03039493) and by the 2024 Yeungnam University Research Grant.
Author Contributions: The authors’ contribution to this work are as follows: Study conceptualization and design: Muhammad Zaman Ali; implementation: Muhammad Zaman Ali, Omer Riaz, Hafiz Muhammad Hasnain, Waqas Sharif; analysis and interpretation of results: Muhammad Zaman Ali, Omer Riaz, Waqas Sharif; validation: Tenvir Ali, Gyu Sang Choi; draft manuscript preparation: Muhammad Zaman Ali, Omer Riaz, Hafiz Muhammad Hasnain, Waqas Sharif; review and editing: Waqas Sharif, Tenvi Ali, Gyu Sang Choi; funding: Gyu Sang Choi. All authors reviewed the results and approved the final version of the manuscript.
Availability of Data and Materials: The authors verify that the data backing the findings of this study can be found in the paper. No additional data or materials were used or generated for this study.
Conflicts of Interest: The authors declare that they have no conflicts of interest to report regarding the present study.
References
1. M. Kumar, S. Kumar, and H. Nagar, “Comparative analysis of different steganography technique for image or data security,” Int. J. Adv. Sci. Technol. (IJAST), vol. 29, no. 4, pp. 11246–11253, 2020. [Google Scholar]
2. A. Yahya, “ Introduction to steganography”. in Steganography Techniques for Digital Image. Cham, Switzerland: Springer International Publishing AG, 2018, pp. 1–7. [Google Scholar]
3. I. J. Kadhim, P. Premaratne, P. J. Vial, and B. Halloran, “Comprehensive survey of image steganography: Techniques, evaluations, and trends in future research,” Neurocomputing, vol. 335, pp. 299–326, 2019. doi: 10.1016/j.neucom.2018.06.075. [Google Scholar] [CrossRef]
4. H. A. Santoso, E. H. Rachmawanto, and C. A. Sari, “An improved message capacity and security using divide and modulus function in spatial domain steganography,” in 2018 Int. Conf. Inform. Commun. Technol. (ICOIACT), 2018, pp. 186–190. [Google Scholar]
5. N. Ayub and A. Selwal, “An improved image steganography technique using edge based data hiding in DCT domain,” J. Interdiscipl. Math., vol. 23, no. 2, pp. 357–366, 2020. doi: 10.1080/09720502.2020.1731949. [Google Scholar] [CrossRef]
6. S. Sahoo and S. S. Sahoo, “A new COVID-19 medical image steganography based on dual encrypted data insertion into minimum mean intensity window of LSB of X-ray scans,” in 2020 IEEE 17th India Council Int. Conf. (INDICON), New Delhi, India, 2020, pp. 1–6. [Google Scholar]
7. S. Karakus, “A new image steganography method with optimum pixel similarity for data hiding in medical images,” Med. Hypotheses., vol. 139, no. 3, pp. 109621, 2020. doi: 10.1016/j.mehy.2020.109691. [Google Scholar] [PubMed] [CrossRef]
8. R. Karakis, “MI-STEG: A medical image steganalysis framework based on ensemble deep learning,” Comput. Mater. Contin., vol. 74, no. 3, pp. 4649–4666, 2023. doi: 10.32604/cmc.2023.035881. [Google Scholar] [CrossRef]
9. A. Tondwalkar and P. Vinayakray-Jani, “Secure localisation of wireless devices with application to sensor networks using steganography,” Procedia Comput. Sci., vol. 78, pp. 610–616, 2016. doi: 10.1016/j.procs.2016.02.107. [Google Scholar] [CrossRef]
10. D. Bucerzan and C. Raţiu, “Testing methods for the efficiency of modern steganography solutions for mobile platforms,” in 2016 6th Int. Conf. Comput. Commun. Control (ICCCC), 2016, pp. 30–36. [Google Scholar]
11. N. Lofgren, S. K. Decker, H. L. Brunk, and J. S. Carr, Digitally Watermaking Holograms for Use with Smart Cards. U.S Patent, Washington DC, no. 6,608,911, 2003. [Google Scholar]
12. Y. Liu, Q. Zhong, M. Xie, and Z. Chen, “A novel multiple-level secret image sharing scheme,” Multimed. Tools Appl., vol. 77, no. 5, pp. 6017–6031, 2018. doi: 10.1007/s11042-017-4512-5. [Google Scholar] [CrossRef]
13. T. Xiang, J. Hu, and J. Sun, “Outsourcing chaotic selective image encryption to the cloud with steganography,” Digit. Signal Process., vol. 43, no. 6, pp. 28–37, 2015. doi: 10.1016/j.dsp.2015.05.006. [Google Scholar] [CrossRef]
14. M. K. Hooshmand and D. Hosahalli, “Network anomaly detection using deep learning techniques,” CAAI Trans. Intell. Technol., vol. 7, no. 2, pp. 228–243, 2022. doi: 10.1049/cit2.12078. [Google Scholar] [CrossRef]
15. D. Nashat and L. Mamdouh, “An efficient steganographic technique for hiding data,” J. Egypt. Math. Soc., vol. 27, no. 1, pp. 1–14, 2019. doi: 10.1186/s42787-019-0061-6. [Google Scholar] [CrossRef]
16. B. Li, J. He, J. Huang, and Y. Q. Shi, “A survey on image steganography and steganalysis,” J. Inform. Hid. Multimed. Signal Process., vol. 2, no. 2, pp. 142–172, 2011. [Google Scholar]
17. M. S. Subhedar and V. H. Mankar, “Current status and key issues in image steganography: A survey,” Comput. Sci. Rev., vol. 13, pp. 95–113, 2014. doi: 10.1016/j.cosrev.2014.09.001. [Google Scholar] [CrossRef]
18. M. Fateh, M. Rezvani, and Y. Irani, “A new method of coding for steganography based on LSB matching revisited,” Secur. Commun. Netw., vol. 2021, no. 5, pp. 1–15, 2021. doi: 10.1155/2021/6610678. [Google Scholar] [CrossRef]
19. H. Yang, X. Sun, and G. Sun, “A high-capacity image data hiding scheme using adaptive LSB substitution,” Radioengineering, vol. 18, no. 4, pp. 509–516, 2009. [Google Scholar]
20. H. W. Tseng and H. S. Leng, “High-payload block-based data hiding scheme using hybrid edge detector with minimal distortion,” IET Image Process., vol. 8, no. 11, pp. 647–654, 2014. doi: 10.1049/iet-ipr.2013.0584. [Google Scholar] [CrossRef]
21. N. Akhtar, V. Ahamad, and H. Javed, “A compressed LSB steganography method,” in 3rd Int. Conf. Comput. Intell. Commun. Technol. (CICT), 2017, pp. 1–7. [Google Scholar]
22. M. Hussain, A. W. A. Wahab, N. Javed, and K. Jung, “Recursive information hiding scheme through LSB, PVD shift, and MPE,” IETE Tech. Rev., vol. 35, no. 1, pp. 53–63, 2018. doi: 10.1080/02564602.2016.1244496. [Google Scholar] [CrossRef]
23. M. Khodaei, B. S. Bigham, and K. Faez, “Adaptive data hiding, using pixel-value-differencing and LSB substitution,” Cybernet. Syst., vol. 47, no. 8, pp. 617–628, 2016. doi: 10.1080/01969722.2016.1214459. [Google Scholar] [CrossRef]
24. A. AbdelRaouf, “A new data hiding approach for image steganography based on visual color sensitivity,” Multimed. Tools Appl., vol. 80, no. 15, pp. 23393–23417, 2021. doi: 10.1007/s11042-020-10224-w. [Google Scholar] [CrossRef]
25. M. H. Mohamed and L. M. Mohamed, “High capacity image steganography technique based on LSB substitution method,” Appl. Math. Inf. Sci., vol. 10, no. 1, pp. 259–266, 2016. doi: 10.18576/amis/100126. [Google Scholar] [CrossRef]
26. J. Arroyo and A. J. P. Delima, “LSB image steganography with data compression technique using goldbach G0 code algorithm,” Int. J., vol. 8, no. 7, pp. 3259–3264, 2020. [Google Scholar]
27. N. M. Zamri, S. M. H. Asraf, and S. Z. S. Idrus, “Two level security in delivering message using encryption and steganography techniques,” J. Phys.: Conf. Ser., vol. 1529, no. 3, pp. 032079, 2020. doi: 10.1088/1742-6596/1529/3/032079. [Google Scholar] [CrossRef]
28. G. Swain, “A steganographic method combining LSB substitution and PVD in a block,” Procedia Comput. Sci., vol. 85, no. 2, pp. 39–44, 2016. doi: 10.1016/j.procs.2016.05.174. [Google Scholar] [CrossRef]
29. A. Zakaria, M. Hussain, A. Wahab, M. Idris, N. Abdullah and K. Jung, “High-capacity image steganography with minimum modified bits based on data mapping and LSB substitution,” Appl. Sci., vol. 8, no. 11, pp. 2199, 2018. doi: 10.3390/app8112199. [Google Scholar] [CrossRef]
30. H. Lee, “Data hiding in spatial color images on smartphones by adaptive RGB LSB replacement,” IEICE Trans. Inf. Syst., vol. 101, no. 8, pp. 2163–2167, 2018. [Google Scholar]
31. M. Sahu, N. Padhy, S. S. Gantayat, and A. K. Sahu, “Local binary pattern-based reversible data hiding,” CAAI Trans. Intell. Technol., vol. 7, no. 4, pp. 695–709, 2022. doi: 10.1049/cit2.12130. [Google Scholar] [CrossRef]
32. O. F. A. Wahab, A. A. M. Khalaf, A. I. Hussein, and H. F. A. Hamed, “Hiding data using efficient combination of RSA cryptography, and compression steganography techniques,” IEEE Access, vol. 9, pp. 31805–31815, 2021. doi: 10.1109/ACCESS.2021.3060317. [Google Scholar] [CrossRef]
33. A. A. Eshmawi, S. A. Alsuhibany, S. Abdel-Khalek, and R. F. Mansour, “Competitive swarm optimization with encryption based steganography for digital image security,” Comput. Mater. Contin., vol. 72, no. 2, pp. 4173–4184, 2022. doi: 10.32604/cmc.2022.028008. [Google Scholar] [CrossRef]
34. X. Liao, J. Yin, M. Chen, and Z. Qin, “Adaptive payload distribution in multiple images steganography based on image texture features,” IEEE Trans. Dependable Secure Comput., vol. 19, no. 2, pp. 897–911, 2020. [Google Scholar]
35. X. Liao, Y. Yu, B. Li, Z. Li, and Z. Qin, “A new payload partition strategy in color image steganography,” IEEE Trans. Circuits Syst. Video Technol., vol. 30, no. 3, pp. 685–696, 2019. doi: 10.1109/TCSVT.2019.2896270. [Google Scholar] [CrossRef]
36. J. Jumanto, “An enhanced LSB-image steganography using the hybrid canny-Sobel edge detection,” Cybern. Inf. Technol., vol. 18, no. 2, pp. 74–88, 2018. [Google Scholar]
37. A. A. Mohammad, “An efficient EMD-based reversible data hiding technique using dual stego images,” Comput. Mater. Contin., vol. 75, no. 1, pp. 1139–1156, 2023. doi: 10.32604/cmc.2023.035964. [Google Scholar] [CrossRef]
38. A. Singh, A. Kumar, and S. Namasudra, “DNACDS: Cloud IoE big data security and accessing scheme based on DNA cryptography,” Front. Comput. Sci., vol. 18, no. 1, pp. 5937, 2024. doi: 10.1007/s11704-022-2193-3. [Google Scholar] [CrossRef]
39. S. Namasudra, “A secure cryptosystem using DNA cryptography and DNA steganography for the cloud-based IoT infrastructure,” Comput. Electr. Eng., vol. 104, pp. 108426, 2022. doi: 10.1016/j.compeleceng.2022.108426. [Google Scholar] [CrossRef]
40. M. A. Hameed, M. Hassaballah, S. Aly, and A. I. Awad, “An adaptive image steganography method based on histogram of oriented gradient and PVD-LSB techniques,” IEEE Access, vol. 7, pp. 185189–185204, 2019. doi: 10.1109/ACCESS.2019.2960254. [Google Scholar] [CrossRef]
41. “The USC-SIPI Image Database,” Signal and Image Processing Institute (SIPIUniversity of Southern California (USC). Accessed: Dec. 24, 2020. [Online]. Available: http://sipi.usc.edu/database/ [Google Scholar]
Cite This Article
 Copyright © 2024 The Author(s). Published by Tech Science Press.
Copyright © 2024 The Author(s). Published by Tech Science Press.This work is licensed under a Creative Commons Attribution 4.0 International License , which permits unrestricted use, distribution, and reproduction in any medium, provided the original work is properly cited.


 Submit a Paper
Submit a Paper Propose a Special lssue
Propose a Special lssue View Full Text
View Full Text Download PDF
Download PDF Downloads
Downloads
 Citation Tools
Citation Tools