 Open Access
Open Access
ARTICLE
Blockchain-Based Key Management Scheme Using Rational Secret Sharing
1 State Key Laboratory of Public Big Data, College of Computer Science and Technology, Guizhou University, Guiyang, 550025, China
2 Guizhou Big Data Academy, Guizhou University, Guiyang, 550025, China
* Corresponding Author: Changgen Peng. Email:
(This article belongs to the Special Issue: Security and Privacy for Blockchain-empowered Internet of Things)
Computers, Materials & Continua 2024, 79(1), 307-328. https://doi.org/10.32604/cmc.2024.047975
Received 23 November 2023; Accepted 23 January 2024; Issue published 25 April 2024
Abstract
Traditional blockchain key management schemes store private keys in the same location, which can easily lead to security issues such as a single point of failure. Therefore, decentralized threshold key management schemes have become a research focus for blockchain private key protection. The security of private keys for blockchain user wallet is highly related to user identity authentication and digital asset security. The threshold blockchain private key management schemes based on verifiable secret sharing have made some progress, but these schemes do not consider participants’ self-interested behavior, and require trusted nodes to keep private key fragments, resulting in a narrow application scope and low deployment efficiency, which cannot meet the needs of personal wallet private key escrow and recovery in public blockchains. We design a private key management scheme based on rational secret sharing that considers the self-interest of participants in secret sharing protocols, and constrains the behavior of rational participants through reasonable mechanism design, making it more suitable in distributed scenarios such as the public blockchain. The proposed scheme achieves the escrow and recovery of personal wallet private keys without the participation of trusted nodes, and simulate its implementation on smart contracts. Compared to other existing threshold wallet solutions and key management schemes based on password-protected secret sharing (PPSS), the proposed scheme has a wide range of applications, verifiable private key recovery, low communication overhead, higher computational efficiency when users perform one-time multi-key escrow, no need for trusted nodes, and personal rational constraints and anti-collusion attack capabilities.Keywords
Key Escrow [1] refers to the storage of decryption keys in a key escrow system (also known as a key recovery system), and in some cases, authorizes third parties to access these keys, which is a key management mechanism for statutory escrow agency. Government and law enforcement agencies’ needs to access encrypted data and recover commercial data have made key escrow a popular research topic in the 1990s [2]. Key Escrow faces two challenges: the trust level of the key escrow agent and the ability to protect the keys [3]. It is easy for a single key escrow party to collaborate with illegal organizations to obtain confidential data, facing widespread user doubts. A single key escrow node also faces the risk of a single point of failure. Therefore, split key escrow has gradually become a new direction for the development of key escrow [4]. In this stage, Shamir [5] proposed partial key escrow for DES keys, Lenstra et al. [6] proposed a time-constrained key escrow system, and Micali et al. [7] proposed shared random functions and key escrow schemes. However, based on Shamir [8] and Blakley [9], independently proposed the concept of key dispersed management, using threshold secret sharing as the representative threshold cryptography as the theoretical basis, comprehensively considering the security and implementation difficulty of the scheme, studying threshold key escrow schemes has become the main trend of key split escrow. Therefore, the key to designing a threshold key escrow scheme that meets actual needs lies in studying and developing corresponding threshold secret sharing technology.
Shamir’s threshold secret sharing and other early-stage secret sharing schemes assumed that the secret distributor and participants were honest without considering deceptive behavior. In response, Chor et al. [10] proposed the concept of verifiable secret sharing (VSS), which added a verification algorithm to the traditional secret sharing scheme. However, this scheme required an interactive process, resulting in low efficiency. Bai et al. [11] proposed a verifiable quantum secret sharing scheme based on d-dimensional Greenberger-Horne-Zeilinger (GHZ) state and analyzed its security against three main quantum attacks: interception retransmission attack, entanglement measurement attack, and honest participant attack. Gentry et al. [12] proposed a non-interactive public verifiable secret sharing (PVSS) scheme for large-scale distributed networks, which can be extended to have hundreds or even thousands of participants to support secure computing in large-scale distributed systems. However, these VSS schemes only consider honest participants and suspected fraudulent participants, without considering the motivations and benefits of each participant. For large-scale institutions like governments or enterprises, key escrow participants are usually bound by political orders, business contracts, and other forms of compulsion, which do not need to consider the self-interested behavior of each participant in the threshold key escrow scheme. Whereas, for online distributed systems like blockchain that target a large number of network users, the traditional threshold key escrow scheme does not have such constraints, resulting in participants who do not upload or upload false key shares still being able to obtain reconstructed keys.
Halpern et al. [13] considered the selfish behavior of participants and introduced Game theory to secret sharing and secure multi-party computation. They proposed a rational cryptographic protocol represented by rational secret sharing and rational secure multi-party computation for the first time. However, traditional rational secret sharing schemes rely on synchronous communication environments and cannot be applied to distributed systems such as blockchains with asynchronous communication. Kol et al. [14] used cryptographic techniques such as oblivious transfer and secure multi-party computation to construct the first rational secret sharing scheme suitable for asynchronous communication. In addition, Zhang et al. [15] introduced rational cryptography into quantum secret sharing research and proposed a rational quantum secret sharing scheme based on GHZ states, which was implemented on the IBM quantum computer [16].
The wide application of blockchain and smart contracts in the Internet of Things has enabled the fulfillment of resource sharing and automated transactions without trusted centers [17]. The public key cryptography technology widely used in blockchain is highly related to the security of user private keys, user asset security, data security, and identity certification security. As there is no trusted third party in the blockchain system, individuals need to locally store their private keys. Once the device where the private key is stored is lost, data is damaged, or even hacked by hackers, it will lead to the loss or leakage of user data and assets. In this context, blockchain private key escrow solutions based on threshold key management technology have become a research hotspot for blockchain private key protection. However, the currently proposed key management schemes for blockchain private key recovery still adopt traditional VSS technology, without considering the rational self-interest behavior of the escrow users [18]; the successfully implemented rational secret sharing schemes on blockchain require the secret sharing participants to deliver deposits in advance [19]. These schemes do not meet the individual rational constraint in mechanism design, limiting the application and promotion of corresponding blockchain threshold key escrow design. The main contributions of this paper are as follows:
We proposed a threshold multi-key escrow management scheme that satisfied individual rational constraints and incentive compatibility: We first designed a reputation mechanism for participants during the key reconstruction phase with the process of uploading and verifying private key fragments and reporting. Then, according to the ratio of contribution to promote the cooperation and behavioral norms of blockchain users, we also proposed a benefit distribution mechanism that relied on a fair process of cooperative gaming.
We constructed the whole multi-key escrow and reconstruction process based on verifiable random functions (VRF) and analyzed and demonstrated the collusion resistance, security verification ability, incentive compatibility and individual rational constraints of the threshold key escrow scheme through utility function analysis. We also compared it with existing blockchain recoverable key management schemes.
We used the smart contracts to complete a multi-wallet key escrow simulation, demonstrating the ability of the scheme to manage wallet keys in Ethereum. We analyzed the performance and costs of the scheme, providing possibilities for achieving a distributed rational key management system for blockchain.
2.1 Blockchain and Smart Contract
Nakamoto et al. [20] proposed Bitcoin, a virtual encrypted currency, and the blockchain transaction structure using Proof of Work and timestamp construction in 2008, which marked the birth of decentralized blockchain technology. Blockchain combines with cryptographic technology ensures traceability, immutability, non-repudiation, and non-counterfeiting of transactions, supporting data security sharing and large-scale collaborative computing, protecting user identity and confidential data privacy, and is suitable for high-privacy and secure distributed application scenarios. Traceability refers to the recording of transaction changes in a blockchain in chronological order, immutability and non-repudiation refer to the inability to modify and deny data written into a blockchain, and non-counterfeiting refers to the inability to forge transactions that can be verified by miners and the entire transaction change record. Blockchain uses hash functions, digital signatures, and distributed consensus fault tolerance to increase the difficulty and cost of attackers falsifying, forging, and denying data operations, enhancing data security.
Szabo proposed the smart contract, which is a computerized transaction protocol for executing contract terms [21]. In the context of blockchain, smart contracts serve as scripts on blockchain and are stored on the blockchain. As smart contracts are located on the blockchain, they have their unique addresses. We trigger their execution by sending transactions to their addresses. Subsequently, smart contracts will be executed independently and automatically on every node in the network according to the data contained in the triggered transaction. Smart contracts on blockchain possess uniqueness, transparency, predictability, and monitoring and tracking capabilities, and have fostered the concept of a decentralized autonomous organization, allowing blockchain to achieve general computing among users without a trusted central node’s supervision [17]. Raj et al. [22] proposed a blockchain smart contract scheme for supply chain management, which replaces the trust intermediary with smart contracts, shortens the payment process, reduces the communication cost, and improves the supply chain transaction efficiency.
2.2 Research on the Security of Blockchain Wallet and Threshold Key Escrow
Blockchain digital wallets provide users with a convenient way to manage private and public keys, while also enabling them to complete digital asset transfers and transactions, and record details of all transactions. The security of the wallet directly relates to the user’s asset security. The comparison of various blockchain key management schemes is shown in Table 1. The existing common wallet solution types include software wallets [23], hardware wallets [24], and custodial wallets [25], but they all have security risks in terms of centralized private key storage. To address these issues, decentralized secure threshold wallet schemes have emerged, which can split private keys into multiple parts and store them on different nodes, thereby achieving distributed storage and protection of private keys, while also allowing private keys to be restored. Therefore, this secure threshold wallet scheme is considered an effective protection plan.
A threshold secret sharing-based threshold signature wallet scheme such as [26] does not support the escrow and recovery of personal user wallet private keys, while a threshold wallet management scheme that meets the needs of personal key escrow and recovery, such as [18], is only applicable to consortium blockchain applications, which requires trusted central nodes and identity authentication mechanisms. In addition, the aforementioned threshold wallet schemes have not taken into account the rational self-interest behavior of participants, resulting in high costs and limited applicability, which cannot be satisfied to the safe escrow needs of public blockchain user wallet keys such as Ethereum. Therefore, designing a private key escrow smart contract based on rational secret sharing is beneficial for achieving the escrow and recovery of public blockchain user private keys in an environment without trusted nodes.
Definition 1: Let
1) Bilinearity: For any
2) Non-degeneracy:
3) Computability: There exists an efficient algorithm to compute
Definition 2: Elliptic Curve Discrete Logarithm Problem (DCELP): Given an elliptic curve
Definition 3: Computational Diffie-Hellman (CDH) Given
Definition 4: Bilinear Diffie-Hellman Problem Given
Definition 5: Decisional Bilinear Diffie-Hellman Inversion Assumption, also known as q-DBDHI problem. An adversary with polynomial time capability cannot distinguish between
3.2 Game Theory Related Knowledge
Incentive compatibility refers to the consistency between individual incentive mechanisms and overall benefits in a game. It includes Bayesian incentive compatibility and dominant strategy incentive compatibility. It should be noted that Bayesian incentive compatibility is a weak concept in games, while dominant strategy incentive compatibility is a strong concept. If a game is dominant strategy incentive compatible, then it must be Bayesian incentive compatible.
In mechanism design, Bayesian incentive compatibility is considered a sufficient and necessary condition for participants to speak the truth. A game is Bayesian incentive compatible if and only if, for any player
where
In a game, if each player adopts their dominant strategy regardless of the other players’ actions, the game is dominant strategy incentive compatible. Mathematically, a game is dominant strategy incentive compatible if and only if for any player
where
In game theory, individual rationality refers to each player choosing strategies that are beneficial to them in pursuit of their own maximum interests. This is also known as the assumption of rational participants. In mechanism design, individual rationality means designing a game mechanism to ensure that each participant has the motivation to participate and will not obtain a worse result due to participation.
Mathematically, individual rationality satisfies the following conditions:
For each participant
where
3.2.3 Fairness of Cooperative Game and Shapley Value Principle
Fairness is a concept to measure the justice of a game. In Game theory, fairness usually refers to whether a game satisfies some fair principles, such as the symmetry principle in a zero-sum game and the Shapley value principle in a cooperative game.
In a cooperative game, the Shapley value principle means that each player should get the corresponding reward for his contribution to the game. Specifically, the Shapley value refers to the average contribution of a player to all possible coalitions. If a player’s Shapley value is lower than other players, this situation is also unfair.
In Game Theory, rational fairness refers to the participants in a game mechanism pursuing their own interests (rationality) while also obtaining fair results. Rational fairness requires participants to consider not only their own interests but also the interests of other participants when choosing strategies, in order to achieve a fair balance.
Rational fairness should satisfy the following conditions:
For each participant, rational fairness requires that the chosen strategy is an optimal response, i.e.,
3.2.5 Resisting Collusion Attack
In Game Theory, a Collusion Attack refers to participants secretly collaborating or cooperating to devise strategies for their own benefits while disregarding the interests of other participants. This collusion may distort the results of the game, sacrificing fairness and balance. Resisting Collusion Attack refers to a feature of strategic or mechanism design that aims to prevent participants from forming collusion or cooperation that could harm the fairness or balance of the game.
Reference [27] proposed a definition of a computable anti-collusion equilibrium: in a game
3.3 Verifiable Random Function
Verifiable Random Function (VRF) [28] is a random function with verification capabilities. It can generate an output and allow a verifier to verify that the output was generated from a specific input and key while maintaining the randomness and unpredictability of the output. Reference [29] proposed an efficient verifiable random function based on bilinear pairs. The scheme includes the following components:
a) Public-private key generation module
b) Encryption module
c) Evidence module
d) Verification module
4 Multi-Key Management Scheme Based on Rational Secret Sharing
Based on the anti-collusion rational secret sharing [27], and taking into account the practical situation of blockchain key escrow, the current and long-term benefits of secret-sharing participants, and the advantages of blockchain smart contracts, a multi-private key management scheme based on rational secret sharing is proposed as follows.
The parameters involved in the proposed scheme are shown in Table 2.

This algorithm is executed by the system administrator to generate public key and private key of
4.3 Key Escrow Negotiation Phase
As shown in Fig. 1, the key escrow user sets a threshold value
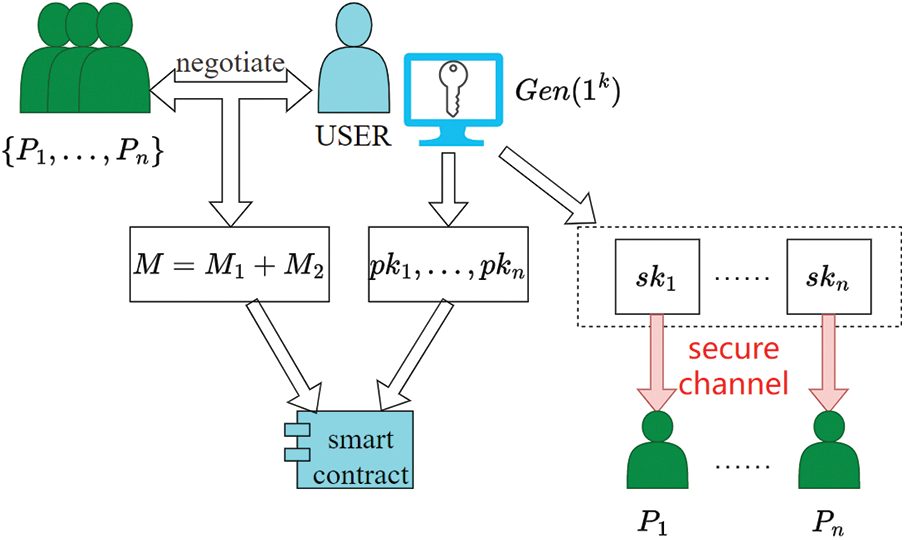
Figure 1: Key escrow negotiation process
Step 1: Key Escrow User uses the two-dimensional coordinate points
Let
Step 2: To avoid duplicate numerical pairs causing failure during the key reconstruction phase, the key escrow user selects
Step 3: Upload public data to the smart contract: a)
Step 4: The key escrow user deletes
The process of key sharing phase is shown in Fig. 2.
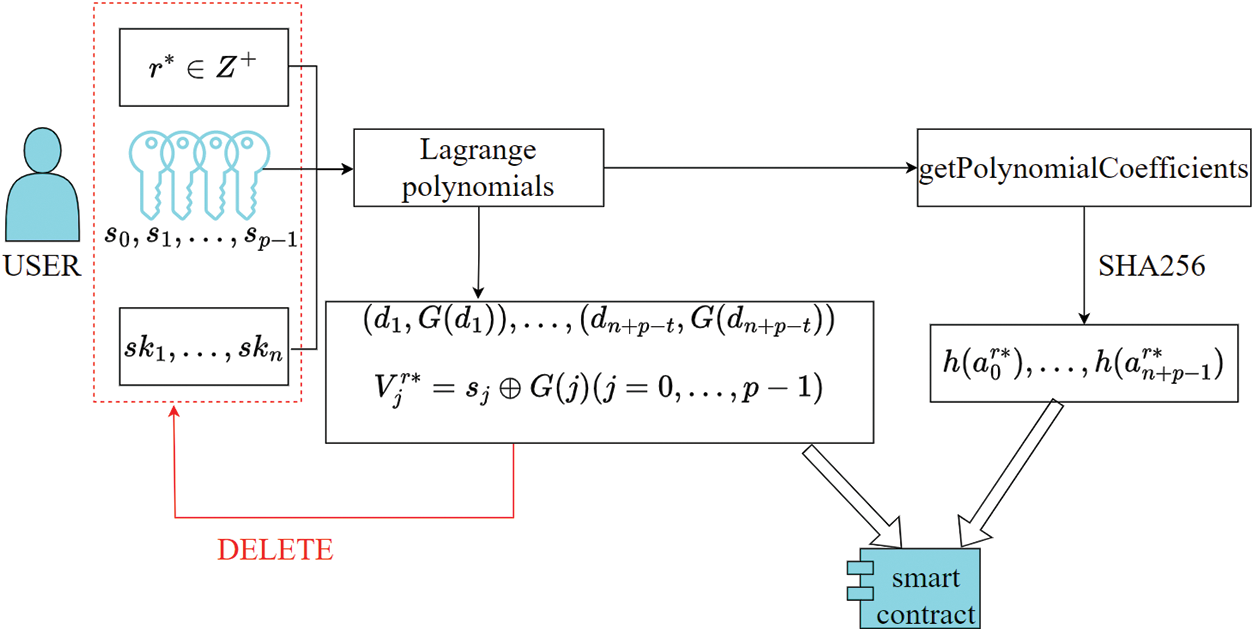
Figure 2: Key sharing process
Step 1: The contract indicates that round
Step 2: During the verification time
Step 3: Performs automatic contract verification of the reported account in order of submission. If the verification result is 0, the reputation value of the reported account will be
Step 4: Within
Step 5: The key escrow user and participants use
Then judge whether
Step 6: The contract automatically calculates and determines whether
Step 7: Check if
Step 8: The contract executes
The process of the key reconstruction phase is shown in Fig. 3. The algorithm pseudocode mainly executed by the smart contract is shown in Fig. 4.
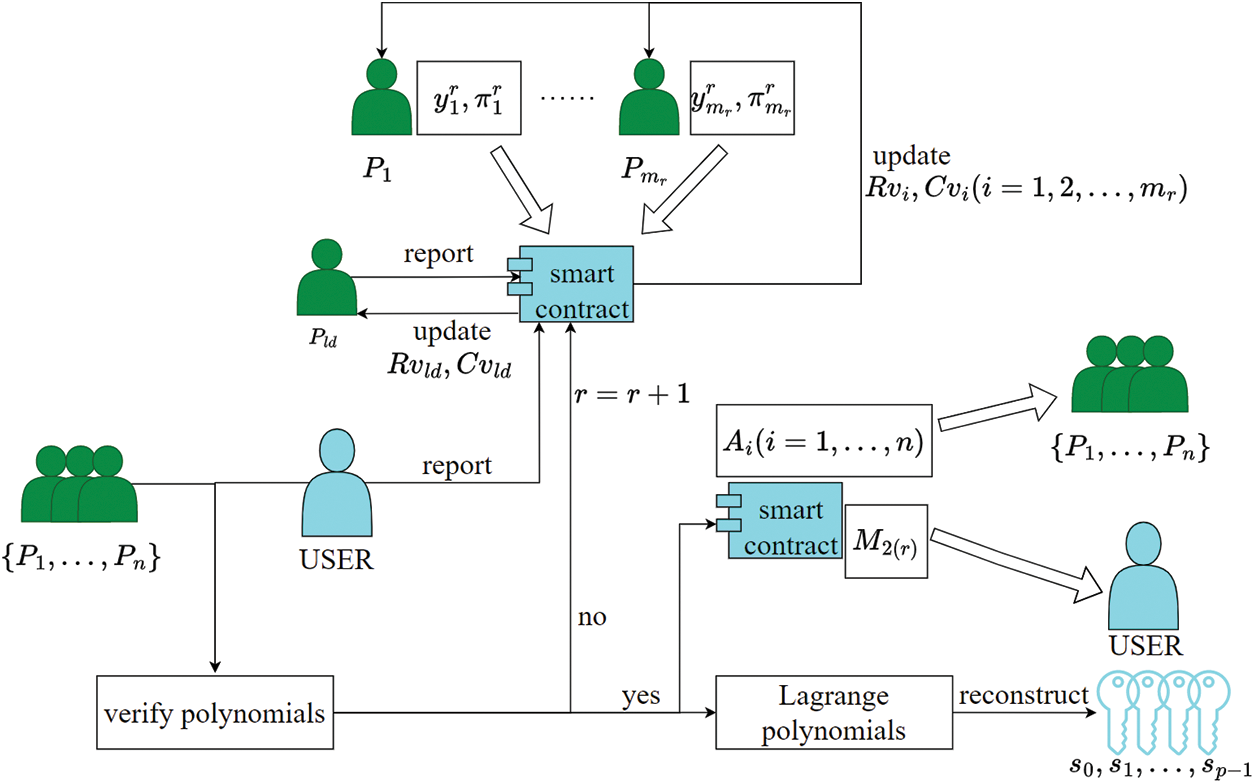
Figure 3: Key reconstruction process
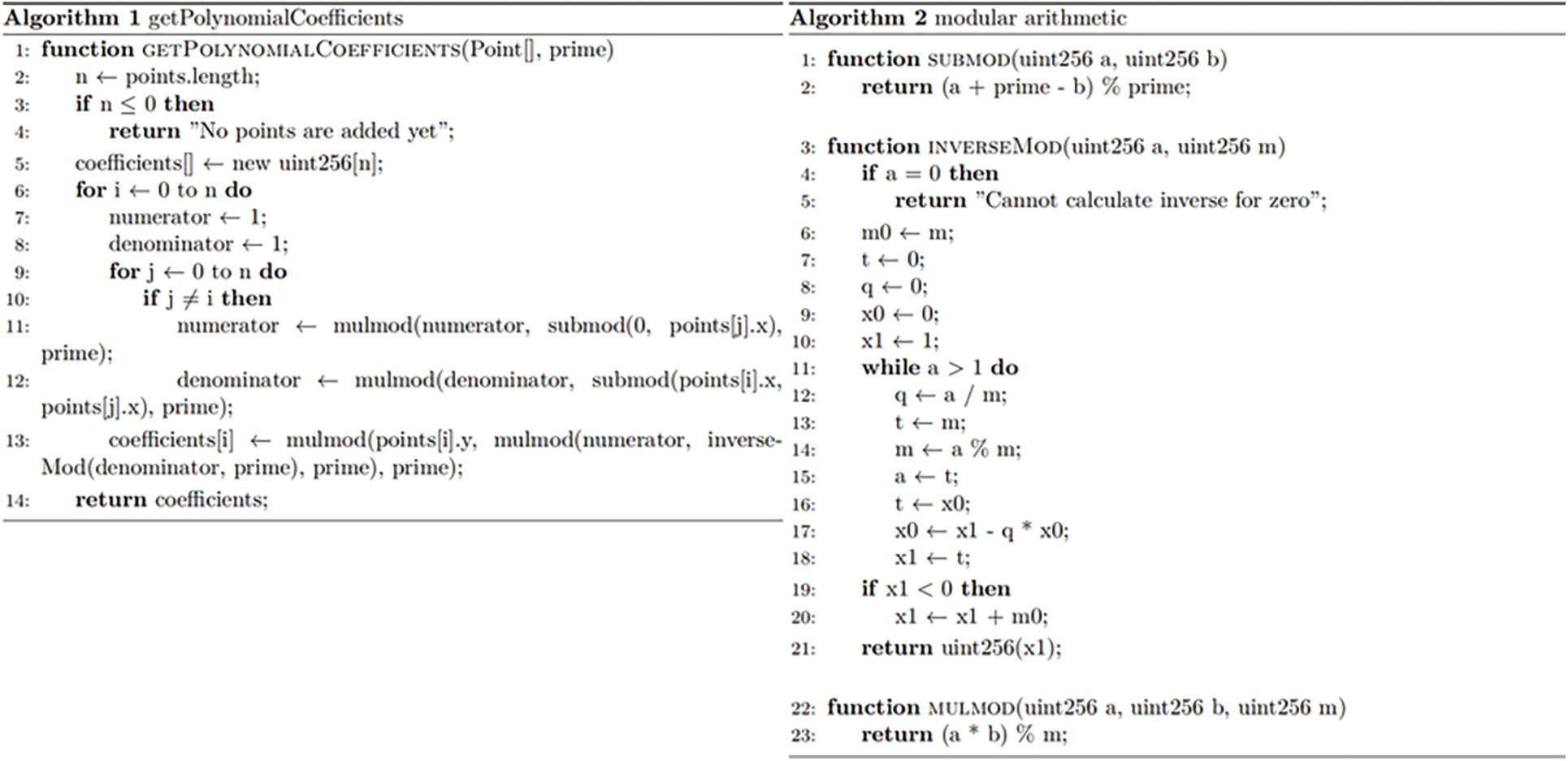
Figure 4: Pseudocode for the main algorithms in the smart contract
Participants and smart contracts can verify the accuracy of the input
Proof:
5.2 Smart Contract Participant Utility Analysis
For Step 1, the contract setting does not allow participants to upload duplicate data to avoid “free-riding” behavior in a round of polynomial reconstruction, which would improperly increase the contribution value
For Step 2 to Step 4, participants
Participant set
The game tree for two players is shown in Fig. 5 (
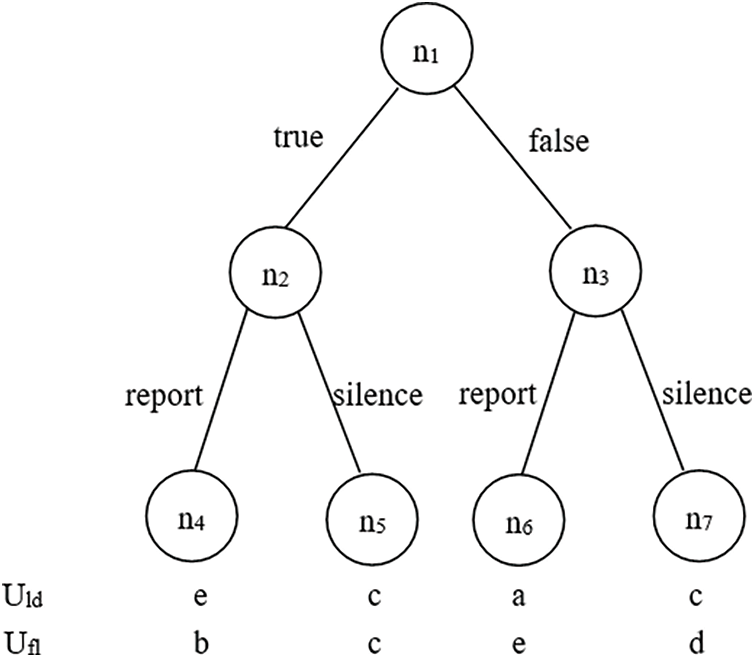
Figure 5: Participants’ game in key reconstruction phase
It is easy to find that the game has two optimal choices (true, silence) and (false, report) for participant
For Step 5 to Step 8, there is actually no effective contribution value gain among participants, but only a reputation value reward is given to honest declaration behavior when the key escrow user declares deception to the contract. In principle, the key escrow user has no motivation to deceive, because the key escrow user needs to pay the contract verification overhead, and declaring success only increases the contract polynomial reconstruction overhead by 1 time when the polynomial is not reconstructed successfully. If the key escrow user does not declare reconstruction success in
For the entire key escrow protocol, the actual benefits for each participant are
5.3 Analysis of Smart Contract Fairness
5.3.1 Fairness Analysis of Cooperative Game
In this key escrow contract scheme, the Shapley value of the participant
5.3.2 Rational Fairness Analysis
In this scheme, everyone’s choice strategy
5.4.1 Fairness Analysis of Cooperative Game
In the key escrow contract scheme,
5.4.2 Personal Rational Analysis
In the key escrow contract scheme, it was found in the utility analysis in Section 5.2 that
Proof: Assume there exists an algorithm
First, the challenger sets
Initial phase: Simulate the algorithm
Phase 1:
Challenge phase:
Let
Phase 2: Repeat the process of Phase 1.
Guessing phase:
6.2 Threshold Security: No More Than
Public information
6.3 Resisting Collusion Attacks
Based on the threshold security analysis, any colluding party of the colluding group
For this private key management protocol, the probability of guessing the plaintext of the private key of the blockchain private wallet is negligible, i.e.,
During key escrow agreement, the user uploads all public key data (
7.2 User Communication Overhead
As shown in Table 3, during the key distribution phase, whether it is Ogata’s scheme [30], Ra’s scheme [31], or the proposed scheme in this paper, it is necessary to transmit the corresponding key shares to

As shown in Table 4, the current password-protected secret sharing (PPSS)-based key recovery management schemes for blockchain can meet the key recovery needs of blockchain with semi-honest nodes, such as the consortium blockchain [30,31]. However, these schemes require interactive verification between users and servers and often require synchronous communication. At the same time, they do not consider the rational self-interested behavior of blockchain, and cannot realize key recovery in more blockchain application scenarios such as the public blockchain. Our scheme uses rational secret sharing and the non-interactive verification method Elliptic Curve VRF (ECVRF) to meet all the requirements in the table, thus realizing the key recovery needs of blockchain users in the asynchronous communication environment of the public blockchain.

7.4 Computational Efficiency Analysis
Based on the calculation efficiency analysis in Ra et al. [31] and the key distribution and reconstruction process proposed in the proposed scheme, we compare the computational complexity of Ogata’s scheme [30], Ra’s scheme [31], and the proposed scheme, as shown in Table 5.
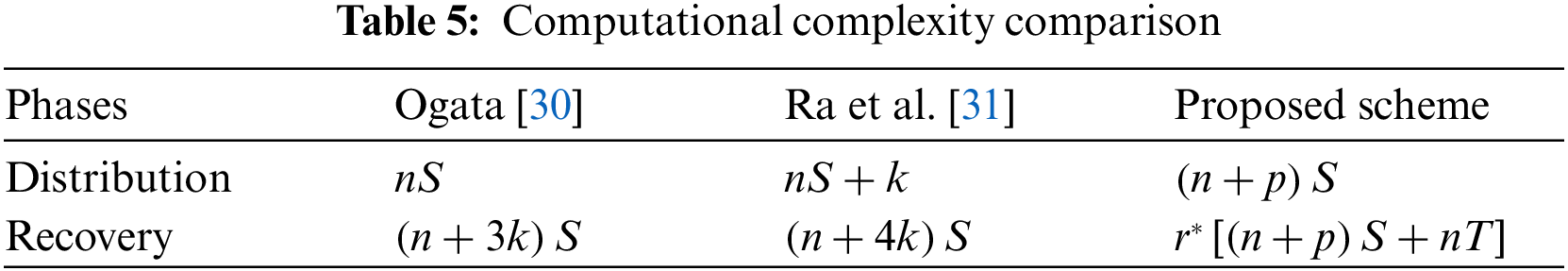
The computational complexity of Shamir’s secret sharing is denoted as
Typically, from the perspective of Byzantine fault tolerance,
As shown in Fig. 6, in the key distribution process, when the user only hosts one key, the computational time overhead of the proposed scheme is higher than Ogata’s scheme [30] and Ra’s scheme [31]. When the user hosts two keys at once, only in the case of
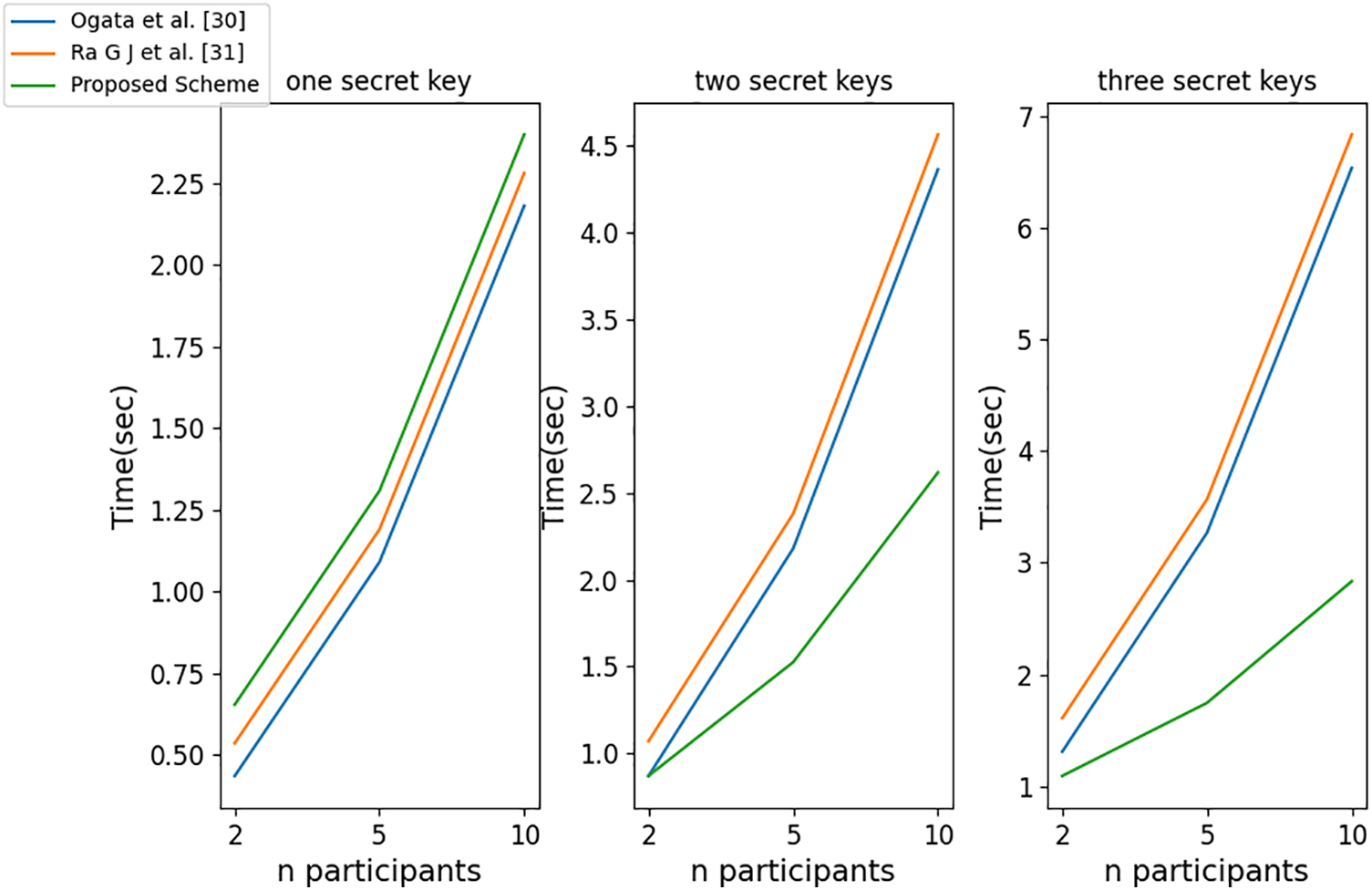
Figure 6: Computational efficiency comparison during distribution
As shown in Fig. 7, when the user only hosts one key in the key recovery process, the computational time overhead of the proposed scheme is higher than Ogata’s scheme [30] and Ra’s scheme [31]. When the user hosts five keys at once, in the case of
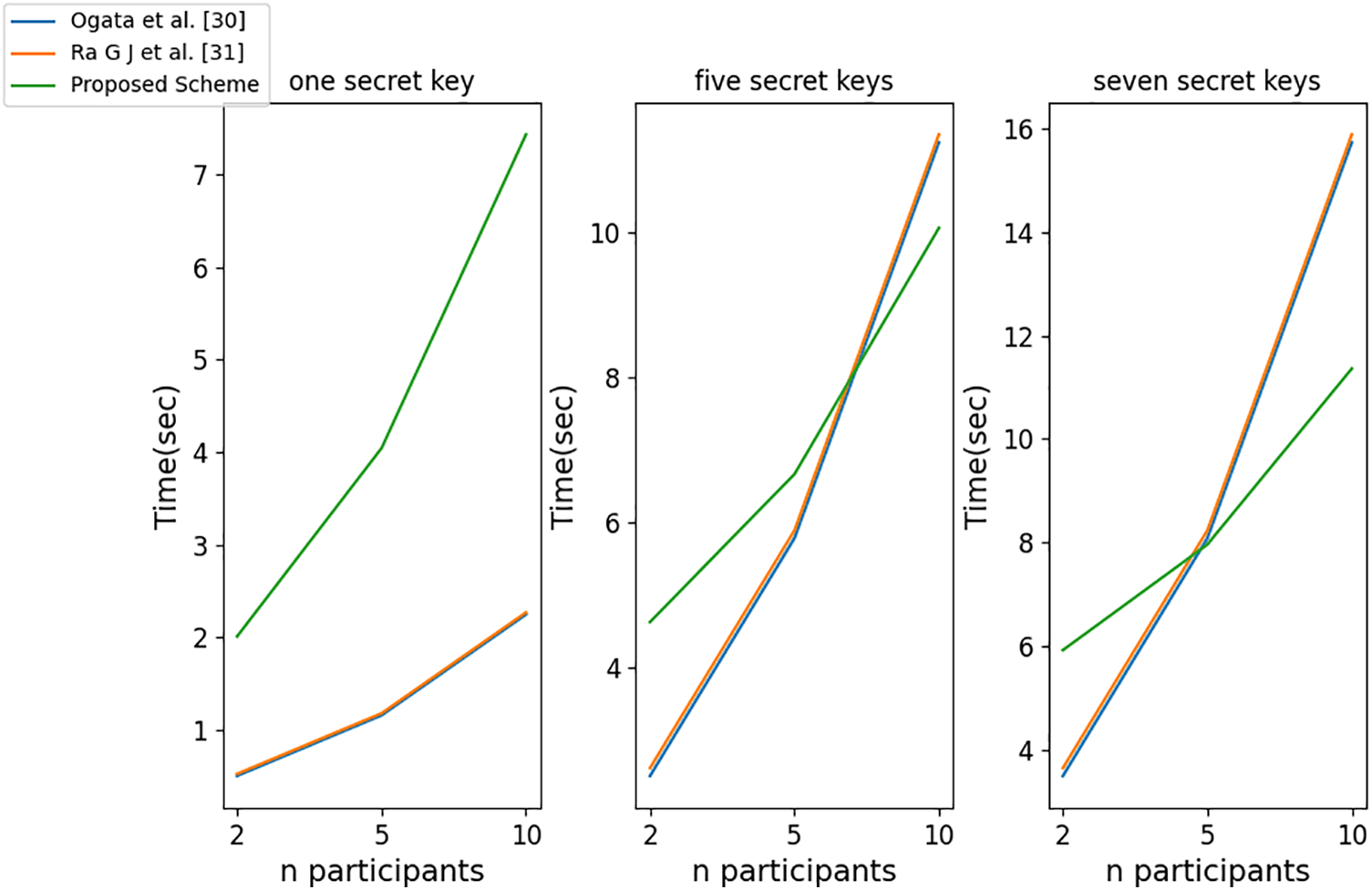
Figure 7: Computational efficiency comparison during recovery
We conducted computational cost simulations on a personal computer with a 12th Gen Intel (R) Core (TM) i7-12700H 2.70 GHz CPU and 16.0 GB RAM, using JavaScript language. The number of participants in the proposed scheme is set to be
Table 6 shows the functions and corresponding Ether costs involved in the smart contract during the refactoring phase of the proposed scheme. However, according to the utility analysis in Section 5.2, participants will comply with the protocol and upload real data without false reporting. In principle, the contract will only execute a polynomial refactoring and hash value verification once, and will not execute the relevant functions of ECVRF (i.e., serial 2 and 3).

We proposed a blockchain private key management scheme based on rational secret sharing, which can achieve one-time escrow and recovery of multiple wallet private keys for blockchain private user. This scheme can be applied to the secure backup scenario of digital assets such as blockchain user wallets and encrypted data. The proposed scheme takes into account the self-interested behavior of participants and satisfies individual rational constraints and incentive compatibility. It promotes the cooperation and behavioral norms of blockchain users by designing a reputation mechanism and a revenue distribution mechanism based on contribution value proportion. In addition, the scheme also designed the whole process of multi-key escrow and reconstruction based on verifiable random functions and demonstrated the collusion resistance, security verification ability, communication overhead, computational overhead, incentive compatibility and individual rational constraints through participants’ utility function analysis. Finally, the scheme was simulated on Ethereum smart contracts to prove its feasibility on the public blockchain.
In the future work, in order to make the proposed scheme a long-term blockchain key management protocol, we will consider the evolutionary game of blockchain users, adjust the reputation incentive design in this scheme and improve the efficiency of blockchain private key escrow and recovery. In addition, we will consider extending the management of the blockchain user’s private key from the wallet to more application scenarios of blockchain key management.
Acknowledgement: I would like to express my deepest gratitude to all those who have supported and guided me throughout the course of this research.
Funding Statement: This work was supported in part by the State’s Key Project of Research and Development Plan under Grant 2022YFB2701400, in part by the National Natural Science Foundation of China under Grants 62272124 and 62361010, in part by the Science and Technology Planning Project of Guizhou Province under Grant [2020]5017, in part by the Research Project of Guizhou University for Talent Introduction under Grant [2020]61, in part by the Cultivation Project of Guizhou University under Grant [2019]56, in part by the Open Fund of Key Laboratory of Advanced Manufacturing Technology, Ministry of Education under Grant GZUAMT2021KF[01], the Science and Technology Program of Guizhou Province (No. [2023]371).
Author Contributions: The authors confirm contribution to the paper as follows: study conception and design: Xingfan Zhao and Changgen Peng; supervision: Changgen Peng; data collection: Kun Niu; analysis and interpretation of results: Weijie Tan; draft manuscript preparation: Xingfan Zhao. All authors reviewed the results and approved the final version of the manuscript.
Availability of Data and Materials: There is no available data and materials.
Conflicts of Interest: The authors declare that they have no conflicts of interest to report regarding the present study.
References
1. D. E. Denning and D. K. Branstad, “A taxonomy for key escrow encryption systems,” Commun. ACM, vol. 39, no. 3, pp. 34–40, 1996. doi: 10.1145/227234.227239. [Google Scholar] [CrossRef]
2. H. Abelson et al., “The risks of key recovery, key escrow, and trusted third-party encryption,” World Wide Web J., vol. 2, no. 3, pp. 241–257, 1997. [Google Scholar]
3. C. Boyd, X. Boyen, C. Carr, and T. Haines, “Key recovery: Inert and public,” in Paradigms in Cryptology—Mycrypt 2016. Malicious and Exploratory Cryptology. Cham: Springer International Publishing, 2017, pp. 111–126. [Google Scholar]
4. M. Bellare and S. Goldwasser, “Verifiable partial key escrow,” in Proc. 4th ACM Conf. Comput. Commun. Secur., 1997, pp. 78–91. [Google Scholar]
5. A. Shamir, “Partial key escrow: A new approach to software key escrow,” in Key Escrow Conf., 1995. [Google Scholar]
6. A. K. Lenstra, P. Winkler, and Y. Yacobi, “A key escrow system with warrant bounds,” in Annual Int. Cryptol. Conf., Berlin, Heidelberg: Springer Berlin Heidelberg, 1995, pp. 197–207. [Google Scholar]
7. S. Micali and R. Sidney, “A simple method for generating and sharing pseudo-random functions, with applications to clipper-like key escrow systems,” in Annual Int. Cryptol. Conf., Berlin, Heidelberg: Springer Berlin Heidelberg, 1995, pp. 185–196. [Google Scholar]
8. A. Shamir, “How to share a secret,” Commun. ACM, vol. 22, no. 11, pp. 612–613, 1979. doi: 10.1145/359168.359176. [Google Scholar] [CrossRef]
9. G. R. Blakley, “Safeguarding cryptographic keys,” in Managing Requirements Knowl., Int. Workshop on, IEEE Comput. Soc., 1979, pp. 313. [Google Scholar]
10. B. Chor, S. Goldwasser, S. Micali, and B. Awerbuch, “Verifiable secret sharing and achieving simultaneity in the presence of faults,” in 26th Annual Symp. Foundations of Comput. Sci., Portland, OR, USA, 1985, pp. 383–395. [Google Scholar]
11. C. M. Bai, S. Zhang, and L. Liu, “Verifiable quantum secret sharing scheme using d-dimensional GHZ state,” Int. J. Theor. Phys., vol. 60, no. 10, pp. 3993–4005, 2021. doi: 10.1007/s10773-021-04955-1. [Google Scholar] [CrossRef]
12. C. Gentry, S. Halevi, and V. Lyubashevsky, “Practical non-interactive publicly verifiable secret sharing with thousands of parties,” in Annual Int. Conf. Theory Appl. Cryptographic Tech., 2022, pp. 458–487. [Google Scholar]
13. J. Halpern and V. Teague, “Rational secret sharing and multiparty computation,” in Proc. Thirty-Sixth Annual ACM Symp. Theory Comput., 2004, pp. 623–632. [Google Scholar]
14. G. Kol and M. Naor, “Cryptography and game theory: Designing protocols for exchanging information,” in Theory Cryptography Conf., Berlin, Heidelberg: Springer, 2008, pp. 320–339. [Google Scholar]
15. X. Zhang, L. Wang, S. Lin, N. Wang, and L. Hong, “Rational quantum secret sharing scheme based on GHZ state,” Quantum Inf. Process., vol. 22, no. 2, pp. 91, 2023. doi: 10.1007/s11128-022-03739-8. [Google Scholar] [CrossRef]
16. D. Joy, M. Sabir, B. K. Behera, and P. K. Panigrahi, “Implementation of quantum secret sharing and quantum binary voting protocol in the IBM quantum computer,” Quantum Inf. Process., vol. 19, no. 1, pp. 1–20, 2020. doi: 10.1007/s11128-019-2531-z. [Google Scholar] [CrossRef]
17. K. Christidis and M. Devetsikiotis, “Blockchains and smart contracts for the internet of things,” IEEE Access., vol. 4, pp. 2292–2303, 2016. doi: 10.1109/ACCESS.2016.2566339. [Google Scholar] [CrossRef]
18. G. Li, L. You, G. Hu, and L. Hu, “Recoverable private key scheme for consortium blockchain based on verifiable secret sharing,” KSII. Trans. Internet Inf. Syst. (TIIS), vol. 15, no. 8, pp. 2865–2878, 2021. [Google Scholar]
19. Z. Chen, Y. Tian, and C. Peng, “An incentive-compatible rational secret sharing scheme using blockchain and smart contract,” Sci. China Inf. Sci., vol. 64, no. 10, pp. 1–21, 2021. doi: 10.1007/s11432-019-2858-8. [Google Scholar] [CrossRef]
20. S. Nakamoto, “Bitcoin: A peer-to-peer electronic cash system,” White Paper, 2008. Accessed: Sep. 17, 2019. [Online]. Available: https://bitcoin.org/bitcoin.pdf [Google Scholar]
21. N. Szabo, “Smart contracts,” 1994. Accessed: Dec. 20, 2018. [Online]. Available: https://www.fon.hum.uva.nl/rob/Courses/InformationInSpeech/CDROM/Literature/LOTwinterschool2006/szabo.best.vwh.net/smart.contracts.html [Google Scholar]
22. P. V. R. P. Raj, S. K. Jauhar, M. Ramkumar, and S. Pratap, “Procurement, traceability and advance cash credit payment transactions in supply chain using blockchain smart contracts,” Comput. Ind. Eng., vol. 167, no. 8, pp. 108038, 2022. doi: 10.1016/j.cie.2022.108038. [Google Scholar] [CrossRef]
23. A. R. Thota, P. Upadhyay, S. Kulkarni, P. Selvam, and B. Viswanathan, “Software wallet based secure participation in Hyperledger Fabric networks,” in 2020 Int. Conf. Commun. Syst. Netw. (COMSNETS), 2020, pp. 1–6. [Google Scholar]
24. D. Park, M. Choi, G. Kim, D. Bae, H. Kim and S. Hong, “Stealing keys from hardware wallets: A single trace side-channel attack on elliptic curve scalar multiplication without profiling,” IEEE Access, vol. 11, pp. 44578–44589, 2023. [Google Scholar]
25. K. Chalkias, P. Chatzigiannis, and Y. Ji, “Broken proofs of solvency in blockchain custodial wallets and exchanges,” in Lecture Notes in Computer Science, Cham: Springer, vol. 13412, 2023. [Google Scholar]
26. R. Gennaro, S. Goldfeder, and A. Narayanan, “Threshold-optimal DSA/ECDSA signatures and an application to bitcoin wallet security,” in Appl. Cryptography Netw. Secur.: 14th Int. Conf.,Guildford, UK, Springer International Publishing, Jun. 2016, pp. 156–174. [Google Scholar]
27. E. Zhang, Q. Sun, and Y. Liu, “Collusion-free rational multi-secret sharing scheme,” Comput. Sci., vol. 42, no. 10, pp. 164–169, 2015. [Google Scholar]
28. S. Micali, M. Rabin, and S. Vadhan, “Verifiable random functions,” in 40th Annual Symp. Foundations Comput. Sci. (Cat. No. 99CB37039), New York, NY, USA, 1999, pp. 120–130. [Google Scholar]
29. Y. Dodis and A. Yampolskiy, “A verifiable random function with short proofs and keys,” in Int. Workshop Public Key Cryptography, Berlin, Heidelberg: Springer Berlin Heidelberg, 2005, pp. 416–431. [Google Scholar]
30. W. Ogata, “Improvement of IT-secure password-protected secret sharing,” in 30th Symp. Cryptography Inf. Secur. (SCIS 2013), 2013. [Google Scholar]
31. G. J. Ra, C. H. Roh, and I. Y. Lee, “A key recovery system based on password-protected secret sharing in a permissioned blockchain,” Comput.Mater. Conti., vol. 65, no. 1, pp. 153–170, 2020. doi: 10.32604/cmc.2020.011293. [Google Scholar] [CrossRef]
32. S. Sugianto, S. Suharjito, and N. Surantha, “Comparison of secret splitting, secret sharing and recursive threshold visual cryptography for security of handwritten images,” TELKOMNIKA. (Telecommun. Comput. Electron. Cont.), vol. 16, no. 1, pp. 323–333, 2018. doi: 10.12928/telkomnika.v16i1.6632. [Google Scholar] [CrossRef]
Cite This Article
 Copyright © 2024 The Author(s). Published by Tech Science Press.
Copyright © 2024 The Author(s). Published by Tech Science Press.This work is licensed under a Creative Commons Attribution 4.0 International License , which permits unrestricted use, distribution, and reproduction in any medium, provided the original work is properly cited.


 Submit a Paper
Submit a Paper Propose a Special lssue
Propose a Special lssue View Full Text
View Full Text Download PDF
Download PDF
 Downloads
Downloads
 Citation Tools
Citation Tools