 Open Access
Open Access
ARTICLE
EduASAC: A Blockchain-Based Education Archive Sharing and Access Control System
1 Department of Electronics and Communication Engineering, Beijing Electronic Science and Technology Institute, Beijing, 100070, China
2 Department of Cyberspace Security, Beijing Electronic Science and Technology Institute, Beijing, 100070, China
* Corresponding Author: Wenbin Gao. Email:
Computers, Materials & Continua 2023, 77(3), 3387-3422. https://doi.org/10.32604/cmc.2023.042000
Received 14 May 2023; Accepted 03 November 2023; Issue published 26 December 2023
Abstract
In the education archive sharing system, when performing homomorphic ciphertext retrieval on the storage server, there are problems such as low security of shared data, confusing parameter management, and weak access control. This paper proposes an Education Archives Sharing and Access Control (EduASAC) system to solve these problems. The system research goal is to realize the sharing of security parameters, the execution of access control, and the recording of system behaviors based on the blockchain network, ensuring the legitimacy of shared membership and the security of education archives. At the same time, the system can be combined with most homomorphic ciphertext retrieval schemes running on the storage server, making the homomorphic ciphertext retrieval mechanism controllable. This paper focuses on the blockchain access control framework and specifically designs smart contracts that conform to the business logic of the EduASAC system. The former adopts a dual-mode access control mechanism combining Discretionary Access Control (DAC) and Mandatory Access Control (MAC) and improves the tagging mode after user permission verification based on the Authentication and Authorization for Constrained Environments (ACE) authorization framework of Open Authorization (OAuth) 2.0; the latter is used in the system to vote on nodes to join requests, define access control policies, execute permission verification processes, store, and share system parameters, and standardize the behavior of member nodes. Finally, the EduASAC system realizes the encryption, storage, retrieval, sharing, and access control processes of education archives. To verify the performance of the system, simulation experiments were conducted. The results show that the EduASAC system can meet the high security needs of education archive sharing and ensure the system’s high throughput, low latency, fast decision-making, and fine-grained access control ability.Keywords
With the rapid improvement of social education, many multidisciplinary and multi-form education archives have been generated involving students, educational institutions, enterprises, government departments, and other stakeholders. At the same time, data breaches occur frequently in the education field, and attack methods are increasing day by day. In January 2022, Illuminate Education, an online scoring and attendance system, was attacked, and hackers gained access to the personal database of approximately 820,000 New York City public school students. In May of the same year, a large-scale data breach occurred in Chicago Public Schools in the United States, and the data of nearly 500,000 students and 60,000 employees were leaked. Therefore, the needs of organizations and institutions for the authority, security, and comprehensiveness of education archives have increased, and the confidentiality, completeness, authenticity, and availability of educational archive-sharing systems have been improved [1]. In particular, new privacy regulations (such as the California Privacy Rights Act (CPRA) implemented in California, USA on July 01, 2023) impose stricter privacy protection obligations on organizations. The high-requirement education archive-sharing system is designed to store education archives in the ciphertext state in the storage server and control the access of users who request data. After the user access permission is approved, the storage server runs the ciphertext retrieval mechanism, thus completing the process of searching and sharing the target data in the database.
In the research work, this storage server used for data storage, ciphertext retrieval, and access control is generally designed as a third-party storage service provider. It has the advantages of large storage capacity, low cost, multi-functionality, and easy sharing. Still, as a third party of interest, it may raise problems such as low user trust, high user privacy risk, and less user control over data. The homomorphic ciphertext retrieval mechanism running on the storage server has a high algorithm, key, encrypted data security, and retrieval efficiency. Still, it has problems such as extensive computation, complex parameter sharing, and retrieval access control. The centralized access control mechanism running on storage servers can deny unauthorized access requests from illegal users and overstepped access requests from legitimate users to ensure controlled and legitimate use of system resources. Still, it has problems such as centralized power, single point of failure, high operating costs, third-party service trust, low scalability, etc. It cannot be used in application scenarios with decentralized equipment, multi-party management, and multiple power assignments [2,3].
This paper adopts a blockchain network with distributed, non-tamperable, public, and traceable features to run the access control mechanism to solve the abovementioned problems and challenges. It can provide a retrieval permission verification service for the homomorphic ciphertext retrieval mechanism on the storage server. It finally realizes a blockchain-based education archive sharing and access control system, EduASAC. The system scheme includes access control policies and an education archive-sharing framework and realizes data encryption, storage, retrieval, sharing, and access control processes in modules. The blockchain can realize voting node joining requests, algorithm parameter sharing, access policy storage, access permission verification, and record system behavior, which is a verifiable and unchangeable ledger. The storage server is responsible for storing big data education archives and running homomorphic ciphertext retrieval mechanisms. The smart contract on the chain automatically executes the behaviors, functions, and strategies that have reached consensus, responds to member nodes’ join requests or access data requests, and ensures the consistency of network-wide behavior under non-manual intervention.
The significance and value of this paper are that the designed system framework can be combined with most of the proposed retrieval schemes in the homomorphic cryptographic retrieval research field and has universal applicability. We adopt blockchain technology to realize distributed access control, including the fusion of multiple access control models and the innovation of an access authorization framework. We use smart contracts to modularize and automate the system workflow, reducing errors’ impact, improving operational efficiency, and reducing system costs. The system is applied to the field of education to ensure confidentiality, integrity, controllability, availability, and non-repudiation in the process of sharing education archives, which provides new solutions and ideas for various problems faced by the research work of educational systems. The main contributions of the article can be summarized as follows:
1) The EduASAC system adopts a dual-mode access control mechanism combining DAC and MAC models. It improves the access authorization framework based on the ACE authorization framework of OAuth 2.0. The system can be combined with most homomorphic ciphertext retrieval schemes to provide retrieval permission verification, retrieval parameter sharing, retrieval process records, and other services for homomorphic ciphertext retrieval mechanisms. This article details the architecture, parameters, workflow, access control, and homomorphic ciphertext retrieval modules of the EduASAC. It can encrypt, store, retrieve, share, and access education archives among educational institutions and record system parameters and user behavior in a way that prevents tampering.
2) Four smart contracts, Vote Contract, Mapping Contract, Control List Contract, and Access Control Contract are designed to automate the process of secure sharing and access control of education archives. In the scheme, joining new member nodes requires the whole network to call Vote Contract to vote, and then the vote count, result return, and record on the chain are completed through contract automation. The management of system security parameters is executed through Mapping Contract, and a variety of parameter mappings are formed and stored on the chain. Users call Control List Contract to dynamically set up Access Control List (ACL) for education archives, including adding, deleting, updating, and querying table items. The access control scheme is written into the Access Control Contract to verify permission when users request data, and the system behavior logs are recorded on the chain.
3) The theoretical analysis and experiments tested the EduASAC system. The specific work includes analyzing and comparing the system’s security and performance, testing the efficiency of four smart contracts on the chain, and simulating the system’s data sharing and user access control process to test the system’s operational efficiency. The experimental results show that the EduASAC system has a short running time, low cost, and high application value.
The rest of this paper is organized as follows. In Section 2, we introduce the relevant work of this paper. In Section 3, we present the system architecture, system parameters, and workflow of EduASAC, and we detail the access control module and homomorphic ciphertext retrieval module. Section 4 introduces the design of four smart contracts in detail. In Section 5, we theoretically analyze the system’s security and performance, test the EduASAC system’s operation efficiency in the sharing and access control process of education archives, and analyze the experimental results. Section 6 concludes the paper and looks forward to future research work.
This section outlines the research on blockchain application in education, focusing on innovative research on access control schemes running on different blockchain system frameworks. The advantages of blockchain technology in education are becoming increasingly prominent [4–6]. These applications include (1) ensuring the integrity and traceability of educational information on the chain [7], (2) student degree management and summative assessment of learning outcomes [8], (3) management, dissemination, and documentation of learning resources [9], (4) peer-to-peer, secure interaction and sharing of relevant people [10], (6) and decentralized control of a distributed digital ledger [11]. These advantages motivate the following summary of related research.
Literature [7] proposed an education record storage and sharing scheme EduRSS on the blockchain architecture, in which the storage server ciphertext stores the original education records and the blockchain records Hash to ensure the security and reliability of the education record storage and sharing process. The scheme design smart contract standardizes the storage and sharing behavior between nodes, and introduces cryptographic technology to encrypt and sign data. In the literature [10], a practical architecture for student certificate sharing was proposed on the underlying technology of the blockchain, using an off-chain storage mechanism and a novel privacy protection mechanism to ensure shared data security, user identity privacy, and system scalability. Finally, develop a Decentralized Application (DApp) based on Ethereum for testing. In the literature [12], a system CredenceLedger that uses blockchain to store certificate Hash was designed, which can be used to protect, share and verify student certificates. Literature [13] designed a lifelong learning log for students that can be recorded on the blockchain. That is, verifiable proof of all learning activities is recorded on the chain, which can verify the authenticity of the log and evaluate student achievement, employment options, and intelligence. In the literature [14], a blockchain-based academic degree traceability authentication system was designed, and smart contracts were used to realize the functions of data collaborative storage, user access control, and degree determination to ensure the safe and efficient operation of the system.
The above summarizes some system research work that uses the blockchain as the underlying technical architecture to serve the upper education platform. Among these works, the research on implementing access control to educational information is one of the key points which can allow or restrict users’ access to education archives and improve the security of shared data. Unfortunately, the results of the survey show that there is little research work on educational systems based on blockchain networks operating access control mechanisms, and this model is mainly applied in healthcare [15], the Internet of Things [16], the Internet of Vehicles [17], and other fields.
The literature [18] was specifically designed for Internet of Things (IoT) data traffic, using blockchain technology for distributed access control, sensor data management, and auditable logging to support secure sharing and fine-grained access control of data-by-data owners. The literature [19] designs a distributed trusted access control system for IoT, which is centered on three smart contracts, namely Access Control Contract (ACC), Judgment Contract (JC), and Registration Contract (RC), and finally implemented based on the Ethernet smart contract platform. In the literature [20], IoTChain, designed based on the Object Security Architecture for the Internet of Things (OSCAR) object security model and the ACE authorization framework [21], was proposed to provide an End to End (E2E) solution for secure authorized access to IoT resources. In the literature [22], a medical application framework based on blockchain, and a cloud database solved the problem of storing and sharing big medical data in a trustless environment. The literature [23] used encryption and signature techniques to control user access to shared data pools. It used permission blockchain to ensure the security of electronic medical records, user identity legality, and traceability of behavior logs. The literature [24] proposed a cloud storage framework with fine-grained access control capability by combining Ethernet with Ciphertext-Policy Attribute-Based Encryption (CP-ABE). The data owner can set properties and access validity periods for users and invoke smart contracts to realize on-chain data storage and tracking. In the literature [25], based on the Hyperledger Fabric framework and smart contract, Attribute Based Access Control (ABAC) and decentralized, fine-grained, and dynamic access control management were implemented that can be applied to large-scale IoT environments.
The above research shows that blockchain-based access control research focuses on different system frameworks, can meet business needs in various fields, and has different research characteristics, application advantages, and realization value. The core of the research work in this paper is the framework design of a blockchain-based access control system, which is the first to serve a homomorphic ciphertext retrieval mechanism and provide retrieval permission verification service for storage servers running a homomorphic ciphertext retrieval mechanism. Therefore, the designed access control scheme is antecedence, innovation, and universality. Meanwhile, the data sharing scheme designed can solve the problems of third-party service distrust, data source uncertainty, data legitimacy, data access control, user identity privacy, as well as log integrity recording, and illegal behavior pursuit when running homomorphic ciphertext retrieval mechanisms on storage servers. In addition, the system application fully considers the user needs in the field of education, the data characteristics, and security features of education archives, so that the blockchain system has both data security sharing and access control capabilities.
In this section, the architecture, threat model, parameters, workflow, and core functional modules of the EduASAC system are outlined in detail, which can ensure the security of educational archives and the privacy of user identities and perform efficient access control management on data.
The EduASAC system architecture is shown in Fig. 1, which mainly includes four major entities: government, educational institutions, storage servers, and blockchain.

Figure 1: System architecture
1) Educational Institution: Educational institutions refer to schools, training institutions, educational enterprises, and other organizational units involved in student education. As the largest subject in the EduASAC system, each educational institution has a lifetime-bound account on the blockchain, where keys and identity information are stored. The identity information of the new educational institution is verified by the member nodes of the whole network and then joins the network after voting. Educational institutions can carry out the process of uploading, retrieving, and downloading education archives; set access rights to education archives to define the scope of data sharing; and request access tokens for target education archives.
2) Storage Server: As another main body in the EduASAC system, the storage server can provide educational institutions with services such as cryptographic storage of education archives, homomorphic cryptographic retrieval, and source data download. It can verify the identity legality of the data requestor and the authenticity of the access token on the chain and run the homomorphic ciphertext retrieval mechanism in the database after verification is passed.
3) Government: The only authoritative entity in the field of education, with the force of law and administrative capacity. The government can be divided into three major departments: management, secrecy, and supervision. Different departments have different identities, different participation links, and different roles in the system. The following describes separately:
• Management Department: responsible for the off-chain verification of the identity information of the nodes requesting to join; able to assign the static access permission level of the system based on the identity information; publish the verified identity information and level on the chain, and initiate Vote Contract to count the opinions of the whole network on the new nodes joining the network; record all registration behaviors and voting results on the chain.
• Secrecy Department: responsible for re-encryption work of ciphertext data to ensure the security of the key.
• Supervision Department: for illegal member nodes, illegal system behavior, and illegal data sharing. Review, determine responsibility and punish illegal targets, and maintain the security and stability of the system.
4) Blockchain: blockchain is the underlying technical architecture of the system and is responsible for promoting the network-wide voting process, verifying entity identity information, sharing system security parameters, enforcing data access control, and recording system behavior and data. The on-chain nodes are responsible for constructing new transactions from the uploaded, shared data, packaging them into blocks after verification, and recording all behaviors and data of the system as evidence of future review and accountability by the Supervision Department.
In addition to the system architecture briefly described above, to simplify the description of the scheme, this paper divides the system participants into two identity entities, i.e., Data Owners (DO) and Data Users (DU):
• DO: It has the authority to manage, control, and share education records, is the owner of interests related to the data, and can set data access permission to control the scope of sharing.
• DU: It requests targeted education archives from multiple parties according to individual needs and uses the data in various application scenarios.
The threat model of the EduASAC system is divided into three levels:
• Data threat level: The data threat level defines that the attacker performs some illegal operations on the data without the data owner’s knowledge or against the data owner’s will, thereby endangering the privacy of the user’s identity and the value of the data.
• Entity identity threat level: The entity identity threat level defines that attackers join the network with illegal identities or pretend to be legal identities and bring security threats to other legitimate users.
• System behavior threat level: The system behavior threat level defines the system or system entity, due to its own economic interests or software and hardware failures, does not operate following pre-consensus rules and terms, which affects the stability of the system operation.
This paper aims to achieve the following threat model goals:
• The public key encryption algorithm is used to encrypt the data, and the private key is stored confidentially to ensure the security of the encrypted data; some sensitive data are stored on the chain, relying on the anti-tampering feature of the blockchain to ensure the integrity of the data.
• The authoritative entity verifies the identity information off-chain, and allows new users to join by voting to ensure the fairness and openness of entity identity information; the smart contract automatically executes the process of storing entity identity information on the chain, ensuring that there is no manual intervention so that the entire network can query that identity information.
• Record all system behaviors through smart contracts to ensure that system behaviors are auditable and traceable; the authoritative entity determines the system behavior threat level based on high-reliability records on the chain.
As a core module of the system architecture, access control is based on improving the ACE authorization framework, DAC, and MAC model, with enhanced security and availability as research objectives.
Internet Engineering Task Force (IETF) ACE [21] proposes a generic framework for authentication and authorization in restricted environments-an ACE based on OAuth 2.0 [26]. DO do not have the ability to control access by themselves and need to issue tokens through third-party authorization servers to control access to sensitive, protected resources. To securely distribute Tokens with access control capabilities must establish a secure channel between users and authorization servers to encrypt data and verify the identity or use technologies such as certificates and secret sharing. At the same time, the third-party authorization server that performs access control according to the user’s wishes must be honest and trustworthy to ensure the authority and authenticity of the Token. These problems make the application of the ACE framework subject to multiple environmental constraints, with low security and availability. The research work in this paper uses blockchain instead of a third-party authorization server in the ACE framework, and smart contracts are responsible for generating access Tokens and storing them securely on the chain for other users to query and verify.
DAC means that the data owner can autonomously grant or withdraw access permissions for the object requesting access to the data. The research work in this paper uses an ACL to add, change, and delete user access permissions dynamically. It combines with MAC to improve access control management’s flexibility, reduce access control mechanisms’ operating costs, and make the system scheme more robust and available.
MAC is a mandatory security attribute setting rules for all subjects, where the system decides whether the user can access according to the user’s fixed security attributes. The research work in this paper adopts static permission levels as the fixed security attributes. They are collectively referred to as Static Access Control (SAC) below for ease of description. It can make up for the decentralized permission control ability of ACL. Because the system forcibly sets the static authority level, it has unchangeable and strong control characteristics and improves user permissions’ security.
In this subsection, we define the designed system security parameters. The parameters include four Identity Documents (ID) of Data Owner

As shown in Fig. 2, the entire workflow of the system is divided into four parts. This section will detail the specific steps of each part, and the symbols are shown in Table 1.
1) Register
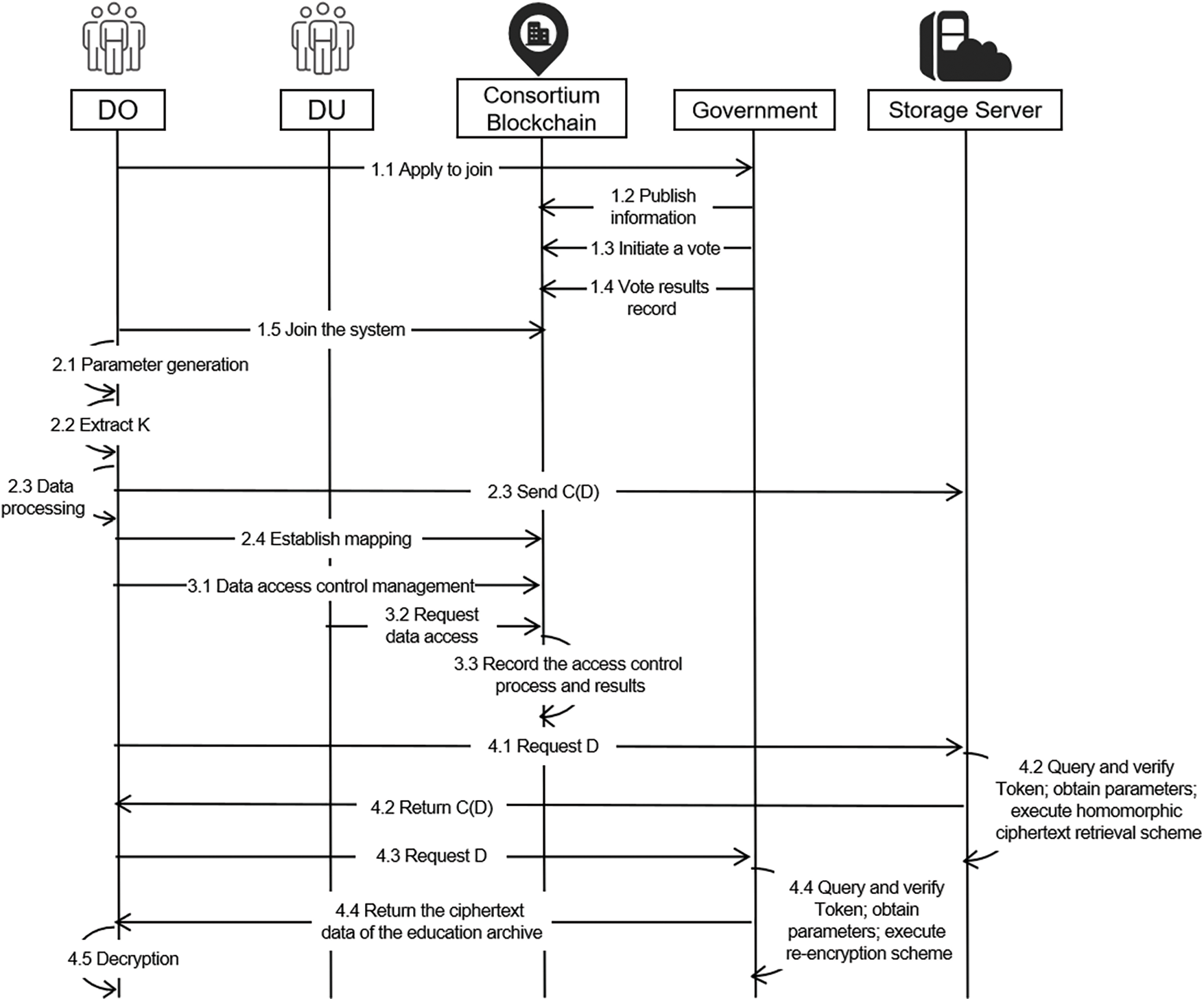
Figure 2: Workflow of EduASAC system
When an educational institution joins the network, it sends a registration application to the government. As the guide node, the Government Management Department verifies the identity information of the node off-chain and publishes it on the chain, and then initiates a Vote Contract to vote for the joining request of the new node by the nodes of the whole network.
Step 1 When an educational institution applies to enter the EduASAC system, it will send
Step 2 After the Government Management Department approves, the static node access level
Step 3 The Government Management Department calls Vote Contract to initiate an on-chain vote. The nodes of the entire network participate in the voting within the voting period, and the contract automatically counts the number of votes. If the consent vote exceeds 90% of the total votes, the contract returns the Yes result and allows the new node to join; otherwise, it returns the Refuse result and rejects the new node.
Step 4 Vote Contract will record the results on the chain after the voting is completed, providing valid evidence for the follow-up work such as review and accountability. Details are shown in Table 2.

Step 5 When a new educational institution joins the EduASAC system, it will act as a blockchain member node. Certificate Authority (CA) creates a certificate for it, generates a public key
2) Data Management
DO first processes the data with various algorithmic mechanisms for the education archives that must be uploaded to the storage server, generating parameters that participate in the sharing and access control process. Then DO invokes the Mapping Contract to establish three parameter mappings and store them securely on the chain for easy calling by other system entities when performing arithmetic operations on the data.
Step 1 DO generate parameters or keys

Step 2 DO extract
Step 3 DO homomorphically encrypts the education archive with
Step 4 DO invokes Mapping Contract to establish
3) Access Control
The access control process of the EduASAC contains SAC, ACL, or other access control mechanisms to realize DO fine-grained access control education archives.
Step 1 DO calls Control List Contract as needed to set data access permissions on the chain. The process will be matched to the
• SAC: the
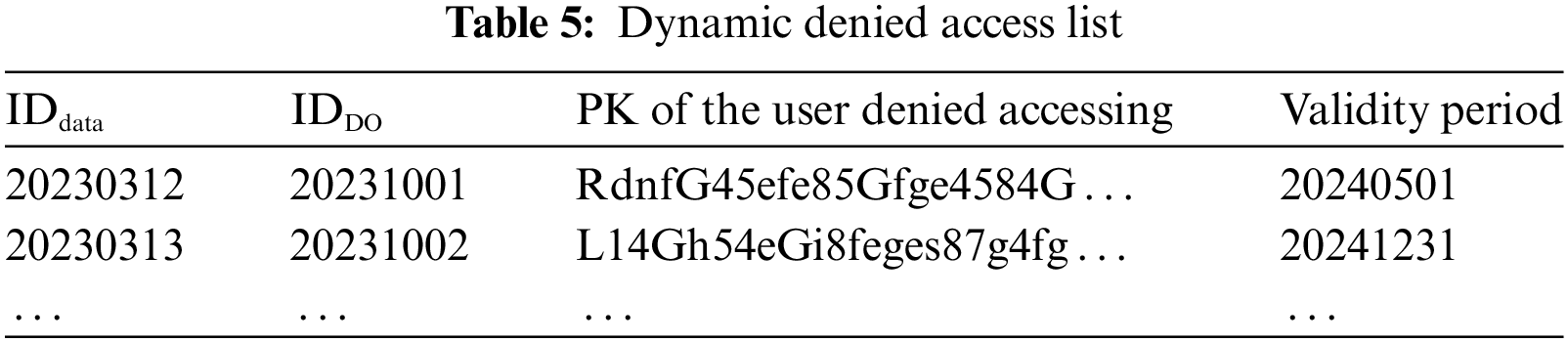
• ACL: realize adding, updating, deleting, and querying dynamic access list. The dynamic access list is divided into Dynamic Allowed Access List (DAAL), Dynamic Denied Access List (DDAL):
DAAL: can be used in the separate ACL process, allowing only the allowed objects set by DO in the list to share data; can be used in the ACL and SAC co-working process, which is for users with low static access permission level, and DO adds their information to DAAL to give them additional access permissions. See Table 4.

b. DDAL: serves SAC and will allow DO to deny access to users with high static access permission levels. See Table 5.
Step 2 DU calls the Access Control Contract to request access to the target data. The contract validates DU access permissions according to DO’s access control management of the data. When the access permissions are verified, the contract generates Tokens and forms blockchain transactions stored on the chain.
Step 3 Access Control Contract will record the access control process and results for review and accountability by the Government Supervision Department. The access control information records are shown in Table 6.
4) Data Sharing

Step 1 DU sends
Step 2 The storage server queries the Token and verifies the validity according to the correspondence of
Step 3 DU sends
Step 4 According to the correspondence of
Step 5 DU uses
3.6 Homomorphic Ciphertext Retrieval Module
The ciphertext retrieval scheme [27] based on a homomorphic encryption algorithm was first proposed by BONEH [28], and it is based on Difficulties in cryptography. The strategy is to obtain retrieval results by comparing homomorphic ciphertext and ciphertext keywords with high data security and retrieval efficiency. The EduASAC system proposed in this paper can be used with most homomorphic ciphertext retrieval schemes running on storage servers to achieve decentralized fine-grained access control and efficient data sharing.
Homomorphic encryption schemes generally consist of four Probabilistic Polynomial Time (PPT) algorithms [29]. The specific content is as follows:
1) Key generation algorithm (KeyGen). Input security parameters and public parameters that meet other actual needs and can output the encryption key (public key), the decryption key (private key), and the public key used for homomorphic ciphertext calculation.
2) Encryption algorithm (Encrypt). Input the plaintext and encryption key and output the ciphertext result of the encryption operation. Among them is a one-to-one correspondence between plaintext and ciphertext, and the ciphertext results obtained by encrypting the same plaintext are different.
3) Decryption algorithm (Decrypt). Input the ciphertext and decryption key and output the plaintext result of the decryption operation.
4) Homomorphic computing algorithm (Evaluate). It is a homomorphic correctness verification algorithm, which does not involve any system modules in this paper, and the specific process is omitted.
In the workflow shown in Fig. 2, Mark 2.1 corresponds to KeyGen (). DO generates keys and security parameters of the homomorphic encryption algorithm. Mark 2.2 is DO extracts keywords from archives. Mark 2.3 corresponds to Encrypt (), DO encrypts education archives and keywords and uploads them to the storage server and blockchain. Mark 4.4 corresponds to Decrypt (), the government department decrypts education archives, performs re-encryption operations, and then shares them with DU. Mark 4.2 corresponds to the homomorphic ciphertext retrieval algorithm Retrieval (), which is run independently by the storage server. The above steps are all run off-chain. It can effectively reduce the amount of computation on the chain, improve the system’s scalability, enable the system framework to be used in conjunction with most homomorphic ciphertext retrieval schemes, and meet the different needs of different retrieval schemes for access control.
The EduASAC system provides the following services for the homomorphic ciphertext retrieval mechanism:
1) For the key and security parameter
2) For the ciphertext keywords after homomorphic encryption, they are packaged together with the retrieval security parameter
3) For the educational archives stored on the storage server, the access control management of SAC and ACL is carried out based on the blockchain network, and the retrieval permission can be verified before running the homomorphic ciphertext retrieval mechanism.
4) Blockchain implements access control on the DU that requests the retrieval data service, calls the contract to verify the DU’s retrieval permission, and automatically generates a Token and stores it on the chain. Token indicates the access permission of DU and provides corresponding parameters for the subsequent retrieval and decryption process.
The above content can be set according to user needs and the homomorphic ciphertext retrieval scheme. For example, the generation algorithm of the key and security parameter
The EduASAC system uses smart contract technology to control the system’s workflow, that is, the process of education archive sharing and access control. This section details four kinds of smart contracts: Vote Contract, Mapping Contract, Control List Contract, and Access Control Contract, and their associated algorithms and logic interfaces.
The Government Management Department invokes the Contract and can initiate the voting of the entire network nodes on the educational institutions applying to join the network. After the voting, the Contract will automatically count the votes, return the information of allowing or rejecting the joining request, and record the voting results in a table on the chain, see Table 2 in the previous section. The specific content of the Contract is as follows:
VoteInstitution(): As shown in Algorithm 1, member nodes vote before the voting deadline. Info is the identity information of the voting node. Nodes vote for the Info included in the AccessmemberMap mapping and against the Info in the RefusememberMap mapping. Both mapping records will be uploaded to the chain. The two-mapping records deadline is the voting period, a fixed value stipulated and released by the Government Management Department on the chain.



typedefine <Struct>
VoteCounting(): As shown in Algorithm 2, after the voting deadline, the votes are counted. When the approval votes account for more than 90% of the total votes, new nodes are allowed to join. Otherwise, the joining request is rejected. The percentage of votes allowed to join can be changed according to actual needs.
institutionMap(): As shown in Algorithm 3, this function describes the process of establishing a mapping between
isExitInstitution(): This function checks whether the educational institution applying to join already exists in the network to prevent the internal nodes from sending many requests to affect the system’s proper operation.
addVoteCase()/queryVoteCase(): Upload or query events that require member nodes to vote, including the id, name, content, time limit, and the number of votes in favor and against. In the initial state, the number of votes in favor and against is 0; after the voting, this value is the final result provided to VoteCounting() for calculation.
This Contract is invoked by DO, who uploads education archives and hopes to share them with other users, to establish three parameter mapping:



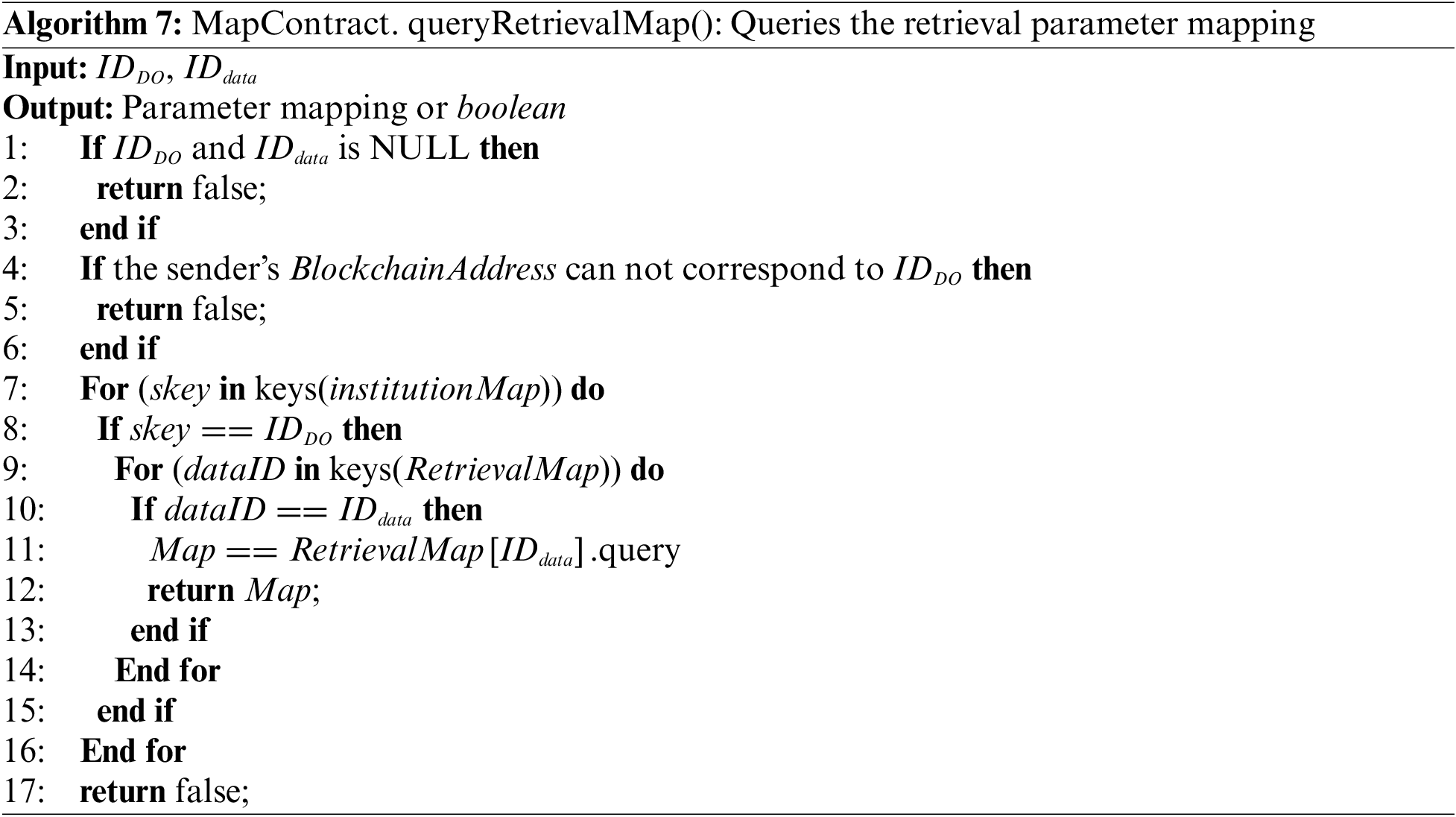
initVerifyMap()/initRetrievalMap()/initEncryptMap(): Establish validation parameter mapping, retrieval parameter mapping and encryption parameter mapping process, as shown in Algorithm 4. The same input parameters of the three functions are the IDs of DO and data, and the different input parameters are
typedefine <Struct>
typedefine <Struct>
typedefine <Struct>
updateVerifyMap()/updateRetrievalMap()/updateEncryptMap(): It is the same as the input of establishing the mapping function, and the old mapping is overwritten with
deleteVerifyMap()/deleteRetrievalMap()/deleteEncryptMap(): Need to input the IDs of DO and data to delete the corresponding parameter mapping, as shown in Algorithm 6.
queryVerifyMap()/queryRetrievalMap()/queryEncryptMap(): Query validation parameter mapping, retrieval parameter mapping and encryption parameter mapping procedures, as shown in Algorithm 7. Need to input the IDs of DO and data to query the parameter mapping and return the corresponding parameter or error reminder information.
The role of this Contract is for the DO to perform access control management on shared education archives and call the Contract to manage and maintain two types of lists on the chain, namely the DAAL and the DDAL. As the contract initiator, DO’s blockchain address needs to match the input
addAllowList()/updateAllowList()/deleteAllowList ()/queryAllowList (): This function is to add, delete, modify, and query table items in the DAAL.
addDenyList()/updateDenyList()/deleteDenyList()/queryDenyList(): This function is to add, delete, modify, and query table items in the DDAL.
This Contract is the core of the system access control process and is used to verify the access permissions of the person who initiated the Contract. The Contract is designed according to the EduASAC system scheme, and the verification parameter mapping corresponding to the target data is queried on the chain. According to
checkAccess(): Check DU access permissions, as shown in Algorithm 8. The input is the IDs of DU, data, and DO. A Token is generated if the verification is successful; otherwise, empty data returns to indicate that the verification failed. The access control mechanism adopted by the system will be based on the
• If
• If
• If
• If
• If

5 Implementation and Evaluation of EduASAC
According to the threat model mentioned in Section 3.2, this section theoretically analyzes the specific solutions proposed by the EduASAC system for data threat, entity identity threat, and system behavior threat.
1) Data security on the chain
The EduASAC system uses the blockchain network to store and share the data used or generated during the system’s work. It deploys the smart contract that regulates the system’s behavior on the chain to record the data operation process and ensure the data’s integrity, correctness, and validity. Table 7 below is the security data stored on the chain.

One data item is not listed in the above list, i.e., all system workflow records stored on the chain. These records will serve as evidence of dishonest behavior by system entities and reduce the impact of malicious tampering of execution results or changes to the execution process by system entities. It can also provide extremely reliable data records for authorities’ subsequent review and accountability process.
2) Parameter security
The generation, storage, and sharing of security parameters in the EduASAC system are all done by DO alone without third-party participation. Each workflow of the system is modularized, and different system working mechanisms require different security parameters, which can meet the security requirements of different mechanisms. The security parameters required by a system entity to run a certain mechanism have been encrypted by the asymmetric key of the system entity and stored on the chain in a ciphertext state.
a) The access control mechanism needs
b) The homomorphic ciphertext retrieval mechanism requires
c) The re-encryption mechanism requires
3) Security of system entity identity
a) At the time of registration, the system entity’s identity information must be verified off-chain by the Government Management Department. After verification, the identity information will be published on the chain and voted on by the whole network. The opinions will be counted before deciding whether to allow them to join the EduASAC system.
b) The identity information, public key, voting process, and results of newly joined nodes are recorded on the chain for network-wide nodes to verify node identity, obtain
c) The blockchain address of the contract initiator needs to match the input ID to ensure the authenticity and legitimacy of the participant’s identity in the process of parameter mapping setting, data access permission setting, and request permission verification.
d) When DU requests retrieval and re-encryption of education archives from storage servers and the Government Secrecy Department, respectively, they need to verify the entity’s identity information in the chain based on its ID.
5.2 Performance Comparison and Testing
This section explains the research characteristics, application advantages, and realization value of the EduASAC system by comparing the performance of related research schemes and conducting simulation tests.
1) Test environment
The performance test environment is shown in Table 8.
2) Performance analysis

Table 9 below will use the designed EduASAC system as the base point to compare the data characteristics of the shared system under different storage modes.

The system solution in this paper uses a combination of storage server and blockchain to store different data based on two different storage models, centralized and decentralized ledger, to jointly complete the work of sharing the data. As shown in the above table, the blockchain is a distributed structure, an open platform, without third-party participation and user access control. At the same time, because the authenticity of pre-chain data cannot be verified, there is a security threat of legitimate users uploading illegal data. There are third-party government departments with the force of law and administrative capacity in the EduASAC system, which can guarantee data security, verify data authenticity, and protect user identity privacy. Therefore, the advantages of system data characteristics are significant, and the social application value is greater. Table 10 below compares the research schemes of other blockchain education systems, highlighting the uniqueness of the scheme in this paper.

By comparing the system’s characteristics, it can be concluded that there is originality in the research of EduASAC system. It can be combined with most homomorphic ciphertext retrieval schemes. It adopts on-chain authorization and off-chain storage, integrates multiple access control modes, and realizes sharing and access control of educational archives based on smart contracts. Table 11 compares other system research schemes that run access control policies on the blockchain.

As can be seen from the Table 11, compared with the centralized trusted institutions used in the literature [18] to manage access permissions, this paper uses a distributed network of blockchain without trust relationship to manage access permissions, which solves the problems of single point failure and third-party service trust; compared with the literature [19] based on static access permissions verification, this paper adopts a combination of static and dynamic access permissions verification mode, which has higher system flexibility and usability; compared with the literature [22,23], which use encryption or signature technology to control access to sensitive data, the security encryption technology used in this paper does not play a role in access control, but ensures the security of data sharing on the chain and reduce security threats from members of the system; compared with the public platform of the Ethernet blockchain used in literature [24], the newly registered system entities in this paper need to be joined after a whole network voting vote; literature [25] is similar to the research scheme of this paper, but the access control mechanism and specific application scenarios adopted by both are different, and this paper also combines homomorphic ciphertext retrieval mechanism and improves the access authorization framework. By comparing various research works, the safety, efficiency, and functional advantages of the scheme in this paper are outstanding, and it has high research significance and application value.
3) Test results
a)Test contract efficiency
On the Hyperledger Fabric, test the running time of installing and instantiating four EduASAC system smart contracts, and test the impact of the average memory of the contract Docker container and the number of APIs in the contract on the contract initialization efficiency, as shown in Fig. 3.

Figure 3: Comparison chart of various factors affecting contract efficiency
Smart contract code written in the Go language generally cannot run directly on the blockchain but needs to be run in a specific sandbox environment Docker container. The installation process is that the smart contract is uploaded to the chain, and the running time is short. The instantiation process needs to call the Docker container and initialize the smart contract, which takes a long time. As can be seen from the figure above, the on-chain efficiency of different smart contracts is related to the amount of memory in the Docker container, the number of APIs, and the complexity of the system behavior controlled by the contract. Tested the average latency and Central Processing Unit (CPU) of the three contracts when writing and querying ledger data, as shown in Fig. 4; tested the average latency and throughput of AccessControlContract under different transaction numbers, as shown in Fig. 5.

Figure 4: Average latency and CPU when contracts write and query ledger data

Figure 5: The average latency and throughput of AccessControlContract under different transaction numbers
The experimental results in the above figure show that the EduASAC system can maintain high throughput in a large-scale transaction environment with high efficiency and low latency. It enables all network parties to reach a low-cost consensus to ensure data consistency.
b) Test contract API
To illustrate the system performance of EduASAC, four contracts of the EduASAC system are called, and the running time of each contract API was recorded in detail. The specific test results are shown in Figs. 6–9.

Figure 6: API runtime of Vote Contract

Figure 7: API runtime of Map Contract
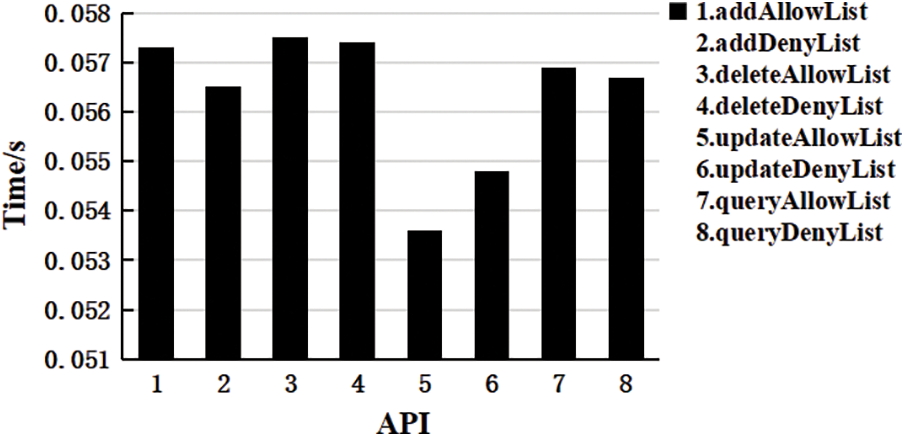
Figure 8: API runtime of Control List Contract
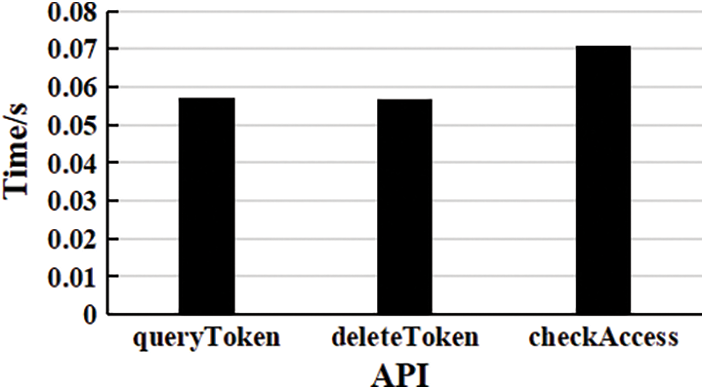
Figure 9: API runtime of Access Control Contract
Note: checkAccess() in the Access Control Contract is when VP is set to 0, the API running time without access control.
API is the behavior code for smart contracts to perform specific operations on data on the chain, including adding, deleting, updating, and querying data. As can be seen from the figure above, the operating efficiency of codes of the same behavior is roughly the same, and the subtle difference is the amount of data stored on the chain and the amount of data of the operation object. The scheme in this paper stores and shares the parameters relating to the homomorphic ciphertext retrieval scheme and access control strategy on the chain. Asymmetric algorithms encrypt all of them. Mechanisms with a large amount of calculation are all run off-chain, and education archives with a large amount of data are stored in the storage server. The data operated by smart contracts on the chain has high security, a small amount of data, and simple operation, improving the EduASAC system’s operating efficiency to a certain extent.
c) Test access verification
When DO sets different

In the simulation test, if DU’s access request to the data is allowed, the test content will include the generation of the Token and the storage process on the chain; otherwise, the contract will end directly after the verification permissions fail. Fig. 10 below shows the running time results of checkAccess() in the Access Control Contract under different conditions.

Figure 10: Runtime of checkAccess()
It can be seen from the figure that compared with the running time of checkAccess() without access control when
The EduASAC system studied in this article takes advantage of the decentralization, tamper-proof, and traceability of blockchain technology, and applies blockchain smart contract technology to implement a dual-mode access control mechanism and a new access authorization framework. At the same time, the system can be combined with most homomorphic ciphertext retrieval schemes running on storage servers to solve the problem of low data security in the storage and sharing of education archives. The paper designs the system workflow of educational archive sharing and access control in detail, including the core modules of the system—access control and homomorphic ciphertext retrieval; introduces the algorithm input, operating logic, and data output of four smart contracts running on the blockchain, emphasizing the role of each smart contract in the system; tests the operating efficiency and memory of the smart contract, as well as the running time of the smart contract API and access control process to prove the availability of the system.
In summary, the design and implementation of the EduASAC system provide a practical reference for other researchers to carry out relevant research. In future work, we can improve in the following areas:
1) The experiments in this paper were conducted on the test network of Hyperledger Fabric. In the future, we will consider deploying a Blockchain as a Service (BaaS) platform closer to the actual blockchain application and further verify the system’s performance.
2) This scheme involves the design and implementation of multiple smart contracts. In the future, we will consider using a more professional platform to deploy, schedule and manage smart contracts.
3) Sharing homomorphic ciphertext data involves the security of sharing encryption keys. This paper uses a re-encryption process that allows education archives in a ciphertext state to be shared among education institutions without revealing the encryption key to third-party service providers. In the future, we can try to combine the homomorphic ciphertext retrieval mechanism with proxy re-encryption to jointly complete the secure retrieval and sharing process of data.
Acknowledgement: Not applicable.
Funding Statement: This work was supported by the Fundamental Research Funds for the Central Universities. Nos. 3282023017, 328202251. RL H received the grant.
Author Contributions: Study conception and design: Ronglei Hu, Chuce He; Data collection: Yaping Chi, Xiaohong Fan; Analysis and interpretation of results: Xiaoyi Duan, Ping Xu; Draft manuscript preparation: Chuce He, Wenbin Gao. All authors reviewed the results and approved the final version of the manuscript.
Availability of Data and Materials: The scheme design, flow, smart contract pseudo-code and related data of this paper have been provided in the paper, readers can reproduce the scheme according to the content of the article. If you need the smart contract code and simulation data, please contact the corresponding author.
Conflicts of Interest: The authors declare that they have no conflicts of interest to report regarding the present study.
References
1. D. Schaffnauser, Blockchain: Letting Student Own Their Credentials, Campus Technology, 2017. [Online]. Available: https://campustechnology.com/articles/2017/03/23/blockchain-letting-students-own-their-credentials.aspx (accessed on 30/10/2023) [Google Scholar]
2. M. U. Bokhari, Q. Makki and Y. K. Tamandani, “A survey on cloud computing,” Big Data Analytics, Advances in Intelligent Systems and Computing, vol. 654, pp. 149–164, 2018. [Google Scholar]
3. C. Cachin, I. Keidar and A. Shraer, “Trusting the cloud,” ACM Sigact News, vol. 40, no. 2, pp. 81, 2009. [Google Scholar]
4. X. Chen, D. Zou, G. Cheng, H. Xie and M. Jone, “Blockchain in smart education: Contributors, collaborations, applications and research topics,” Education and Information Technologies, vol. 28, pp. 4597–4627, 2023. [Google Scholar]
5. A. O. J. Kwok and H. Treiblmaier, “No one left behind in education: Blockchain-based transformation and its potential for social inclusion,” Asia Pacific Education Review, vol. 23, no. 3, pp. 445–455, 2022. [Google Scholar]
6. R. J. Maestre, J. B. Higuera, N. G. Gómez, J. R. B. Higuera and J. A. S. Montalvo, “The application of blockchain algorithms to the management of education certificates,” Evolutionary Intelligence, vol. 16, pp. 1967–1984, 2023. [Google Scholar]
7. H. Li and D. Han, “EduRSS: A blockchain-based educational records secure storage and sharing scheme,” IEEE Access, vol. 7, pp. 179273–179289, 2019. [Google Scholar]
8. M. Sharples and J. Domingue, “The blockchain and kudos: A distributed system for educational record,” Adaptive and Adaptable Learning, EC-TEL 2016: Adaptive and Adaptable Learning, pp. 490–496, 2016. [Google Scholar]
9. D. Tapscott and A. Tapscott, “The blockchain revolution and higher education,” Educause Review, vol. 52, no. 2, pp. 11–24, 2017. [Google Scholar]
10. R. A. Mishra, A. Anshuman, A. Braeken and M. Liyanage, “Privacy protected blockchain based architecture and implementation for sharing of students’ credentials,” Information Processing and Management, vol. 58, no. 3, pp. 102512, 2021. [Google Scholar]
11. T. Hewa, M. Ylianttila and M. Liyanage, “Survey on blockchain based smart contracts: Applications, opportunities and challenges,” Journal of Network and Computer Applications, vol. 177, pp. 102857, 2021. [Google Scholar]
12. R. Arenas and P. Fernandez, “CredenceLedger: A permissioned blockchain for verifiable academic credentials,” in 2018 IEEE Int. Conf. on Engineering, Technology and Innovation (ICE/ITMC), Stuttgart, Germany, pp. 1–6, 2018. [Google Scholar]
13. P. Ocheja, B. Flanagan, H. Ueda and H. Ogata, “Managing lifelong learning records through blockchain,” Research and Practice in Technology Enhanced Learning, vol. 14, pp. 1–19, 2019. [Google Scholar]
14. F. Hua, Y. Ding, J. Sun, J. Li and W. Shen, “A blockchain-based trusted education and degree certification system,” Cyberspace Security, vol. 11, no. 9, pp. 9–18, 2020. [Google Scholar]
15. W. Yuan, B. Yan, W. Li, L. Hao and H. Yang, “Blockchain-based medical health record access control scheme with efficient protection mechanism and patient control,” Multimedia Tools and Applications, vol. 82, pp. 16279–16300, 2022. [Google Scholar] [PubMed]
16. P. Bagga, A. K. Das, V. Chamola and M. Guizani, “Blockchain-envisioned access control for Internet of Things applications: A comprehensive survey and future directions,” Telecommunication Systems, vol. 81, pp. 125–173, 2022. [Google Scholar] [PubMed]
17. L. Zhang, Y. Zhang, Q. Wu, Y. Mu and F. Rezaeibagha, “A secure and efficient decentralized access control scheme based on blockchain for vehicular social networks,” IEEE Internet of Things Journal, vol. 9, no. 18, pp. 17938–17952, 2022. [Google Scholar]
18. H. Shafagh, L. Burkhalter, A. Hithnawi and S. Duquennoy, “Towards blockchain-based auditable storage and sharing of IoT data,” in Proc. of the 2017 on Cloud Computing Security Workshop, Dallas, USA, pp. 45–50, 2017. [Google Scholar]
19. Y. Zhang, S. Kasahara, Y. Shen, X. Jiang and J. Wan, “Smart contract-based access control for the Internet of Things,” IEEE Internet of Things Journal, vol. 6, no. 2, pp. 1594–1605, 2019. [Google Scholar]
20. O. Alphand, M. Amoretti, T. Claeys, S. D. Asta, A. Duda et al., “IoTChain: A blockchain security architecture for the Internet of Things,” in 2018 IEEE Wireless Communications and Networking Conf. (WCNC), Barcelona, Spain, pp. 1–6, 2018. [Google Scholar]
21. S. Erdtman, L. Seitz, E. Wahlstroem, G. Selander and H. Tschofenig, Authentication and Authorization for Constrained Environments (ACE), 2017. [Online]. Available: https://datatracker.ietf.org/doc/html/draft-ietf-ace-oauth-authz-07 (accessed on 30/10/2023) [Google Scholar]
22. Q. Xia, E. B. Sifah, K. O. Asamoah, J. Gao, X. Du et al., “MeDShare: Trust-less medical data sharing among cloud service providers via blockchain,” IEEE Access, vol. 5, pp. 14757–14767, 2017. [Google Scholar]
23. Q. Xia, E. B. Sifah, A. Smahi, S. Amofa and X. Zhang, “BBDS: Blockchain-based data sharing for electronic medical records in cloud environments,” Information, vol. 8, pp. 44, 2017. [Google Scholar]
24. S. Wang, X. Wang and Y. Zhang, “A secure cloud storage framework with access control based on blockchain,” IEEE Access, vol. 7, pp. 112713–112725, 2019. [Google Scholar]
25. H. Liu, D. Han and D. Li, “Fabric-IoT: A blockchain-based access control system in IoT,” IEEE Access, vol. 8, pp. 18207–18218, 2020. [Google Scholar]
26. D. Hardt, “The OAuth 2.0 authorization framework,” Internet Requests for Comments, vol. 6749, pp. 1–76, 2012. [Google Scholar]
27. R. L. Rivest, L. M. Adleman and M. L. Dertouzos, “On data banks and privacy homomorphisms,” Foundations of Secure Computation, vol. 4, pp. 169–179, 1978. [Google Scholar]
28. D. Boneh, G. D. Crescenzo, R. M. Ostrovsky and G. Persiano, “Public key encryption with keyword search,” in Int. Conf. on the Theory and Application of Cryptographic Techniques, Interlaken, Switzerland, vol. 3027, pp. 506–522, 2004. [Google Scholar]
29. Y. Yang, Y. Zhao, J. Zhang, J. Huang and Y. Gao, “Recent development of theory and application on homomorphic encryption,” Journal of Electronics and Information Technology, vol. 43, no. 2, pp. 475–487, 2020. [Google Scholar]
Cite This Article
 Copyright © 2023 The Author(s). Published by Tech Science Press.
Copyright © 2023 The Author(s). Published by Tech Science Press.This work is licensed under a Creative Commons Attribution 4.0 International License , which permits unrestricted use, distribution, and reproduction in any medium, provided the original work is properly cited.


 Submit a Paper
Submit a Paper Propose a Special lssue
Propose a Special lssue View Full Text
View Full Text Download PDF
Download PDF Downloads
Downloads
 Citation Tools
Citation Tools