 Open Access
Open Access
ARTICLE
Consortium Chain Consensus Vulnerability and Chain Generation Mechanism
School of Computer Science and Technology, Zhoukou Normal University, Zhoukou, 466001, China
* Corresponding Author: Shi Dong. Email:
(This article belongs to the Special Issue: Innovative Security for the Next Generation Mobile Communication and Internet Systems)
Computers, Materials & Continua 2023, 77(2), 2505-2527. https://doi.org/10.32604/cmc.2023.043476
Received 03 July 2023; Accepted 18 October 2023; Issue published 29 November 2023
Abstract
Effectively identifying and preventing the threat of Byzantine nodes to the security of distributed systems is a challenge in applying consortium chains. Therefore, this paper proposes a new consortium chain generation model, deeply analyzes the vulnerability of the consortium chain consensus based on the behavior of the nodes, and points out the effects of Byzantine node proportion and node state verification on the consensus process and system security. Furthermore, the normalized verification node aggregation index that represents the consensus ability of the consortium organization and the trust evaluation function of the verification node set is derived. When either of the two is lower than the threshold, the consortium institution or the verification node set members are dynamically adjusted. On this basis, an innovative consortium chain generation mechanism based on the Asynchronous Binary Byzantine Consensus Mechanism (ABBCM) is proposed. Based on the extended consortium chain consensus mechanism, a certain consensus value set can be combined into multiple proposals, which can realize crossdomain asynchronous message passing between multi-consortium chains without reducing the system’s security. In addition, experiments are carried out under four classical Byzantine Attack (BA) behaviors, BA1 to BA4. The results show that the proposed method can obtain better delay than the classical random Byzantine consensus algorithm Coin, effectively improving the consensus efficiency based on asynchronous message passing in the consortium chain and thus meeting the throughput of most Internet of Things (IoT) applications.Keywords
With the great success of the permissionless blockchain application in electronic cryptocurrency, blockchain networks based on decentralized identity authentication and group consensus attract increasing attention. However, limited by the scale, performance, and deployment cost of distributed application systems, permissionless blockchain technology is challenging to use widely. Consortium Blockchain (CBC) inherits the security characteristics of public chain to some extent with the openness that private chain does not provide, so more research focuses on CBCs [1–3]. The CBC limits the proposer set to a few known nodes and relies on a trusted service or consortium organization to authenticate the nodes. Based on proof of interest of chain or Byzantine Fault Tolerance (BFT), CBC proposes new blocks in the way of fault-tolerant consensus and verifies new transactions without needing confirmations, thus reducing the influence of potential Byzantine nodes on the system. Moreover, liquidity is achieved by deploying and running smart contracts on CBCs [4], of which the efficiency is significantly higher than that of the permissionless public chain driven by the proof-of-work mechanism. With the continuous expansion of the application scenarios of CBC in recent years, the diversity and durability of the services it can provide have been improved unprecedentedly. Therefore, CBC provides a new way for identity authentication and trust transfer among parties in the network [5–7].
The consensus mechanism of CBC ensures the consistency of contents stored by each node in the distributed ledger and protects data from unauthorized access, which is important for realizing the scalability, transaction speed, transaction certainty, and security of CBC [8,9]. The consensus mechanism of CBC is constantly improved to maintain compatibility of high efficiency and scalable applications such as side chain and sharding mechanisms [10–12]. Users of the CBC can create parallel and separate CBCs through the Application Program Interface (API) and set the initial consensus mechanism, allowing different parallel and separate CBCs belonging to the same consortium organization to adopt different consensus mechanisms. Meanwhile, the consensus mechanism of each parallel and separate CBC can be upgraded through voting at any time. The system can reach a consensus safely among several side chains or sharding chains by deploying smart contracts in CBC.
However, under the environment of a Byzantine partition consortium network, the information service entities of heterogeneous CBCs interact frequently and lack collaborative management, making it difficult for the data owner to control the access of other trusted domain entities to the data, resulting in the risk of data being stolen, tampered with and replayed when the data is shared across domains [13]. Chen et al. [14] proposed a blockchain-based cross-domain data-sharing method for the Internet of Things (IoT), which uses the threshold proxy re-encryption method to process the ciphertext to avoid collusion between malicious agents and visitors. Yu et al. [15] proposed an industrial IoT data-sharing scheme based on blockchain and proxy re-encryption, where cloud servers verify whether user attributes meet the access policy and generate decryption parameters to send to users when data users request cross-domain data. Existing consensus mechanisms can satisfy the scalability or security of distributed systems, but it is impossible to do both as long as the consensus mechanism of the final determination of block conflict is different and the impact of system scalability on security is also different. Thus, the consensus mechanism based on asynchronous communication still faces challenges. Therefore, it is of great academic significance and extensive application value to further research the consensus mechanism of CBC to improve the security and scalability of the partitioning network consensus mechanism in heterogeneous CBCs based on privacy protection and increase the efficiency of trust transfer and data sharing between different trust domains [16–19].
This paper established a new consortium chain generation model to solve the above problems. The rules of chain generation are extracted. The behaviors of nodes are analyzed and verified, based on which the consensus vulnerability of CBCs is deeply analyzed. Based on this, the paper proposes a novel generation mechanism for CBC based on the Asynchronous Binary Byzantine Consensus Mechanism (ABBCM). The main contributions of this work are as follows:
(1) A new generation model of CBC is established. The influence of logical and physical topology structure on the CBC performance is analyzed from the perspective of the chain generation process. The single-chain generation rule is given to avoid chain forking.
(2) The node behavior is analyzed and verified. Based on the node behavior, the consensus vulnerability of CBCs is deeply analyzed. The normalized verification node aggregation index is obtained to represent the consensus ability of consortium institutions.
(3) A novel CBC generation mechanism, ABBCM, based on asynchronous binary Byzantine consensus, is proposed, which extends the general definition of Byzantine consensus and allows a definite set of consensus values to combine multiple proposals. The experimental results show that under the four classical Byzantine node attack behaviors, BA1 to BA4, the ABBCM obtains better time delay than the Coin, a classical random Byzantine consensus mechanism, and can meet the throughput of most IoT applications.
This paper is structured as follows. Section 2 describes the related work of CBCs and consensus algorithms. Section 3 analyzes the effect of logical and physical topology on the CBC performance from the perspective of chain generation and gives the single chain generation rule avoiding chain forking. Section 4 analyzes the consensus vulnerability of CBCs based on node behavior. Section 5 introduces a novel consortium chain generation mechanism based on asynchronous binary Byzantine consensus. In Section 6, the proposed mechanism is simulated, and the results are discussed. Section 7 concludes with lessons learned and a plan for future work.
Decentralized applications based on CBC have been involved in data governance [20], cloud storage [21], IoT [22], supply chain [23], and other fields to establish a trusted environment for stakeholders, achieving trusted and durable services. However, its low scalability and throughput limit the performance of the hosted decentralized applications. The section enfolds works to improve the performance of CBCs in recent years: mainstream platforms and consensus mechanisms. Various works related to the cross-domain consensus of CBCs are also compared based on research description, techniques, and limitations.
The mainstream CBC platforms include HyperLedger, Corda, and Quorum. In 2015, led by the Linux Foundation, International Business Machines Corporation (IBM), Intel, Cisco, and others announced the establishment of the HyperLedger project, which provides open-source reference and implementation for transparent, public, and decentralized enterprise-level distributed ledger technology. It also introduces blockchain into the application of distributed consortium ledger for the first time, which is grounds for building an efficient business network based on blockchain in the future [24–27]. Like Hyperledger, Corda uses a distributed notary mechanism to meet growing business demands [28,29]. However, the distributed consensus mechanism’s performance between nodes significantly impacts ledger synchronization between nodes and system performance. This project provides consensus mechanism selection strategies for different businesses. For example, in applications with high trust between nodes, Raft, Paxos, and other Crash Fault Tolerance (CFT) algorithms are selected to achieve high system performance.
On the contrary, the BFT class algorithm is applied to obtain higher system security and reliability. Subsequently, JPMorgan launched a distributed ledger protocol, Quorum, based on the Raft consensus mechanism based on Ethereum. It greatly improved the system performance by introducing the Enclave module with transaction isolation and specific encryption functions to realize parallel operation [30,31]. Although the implementation schemes of the above CBC platforms are different, they pursue usability and scalability to ensure performance and adapt to different industries’ requirements.
2.2 Consensus Mechanism Based on CBCs
Based on the existing CBC platform, much research has been done to improve its performance [32]. Some performance-driven consensus protocols of CBCs ensure ledger consistency and partition fault tolerance through the delegation mechanism [33–37] but reduce the number of core nodes participating in the consensus and the security brought by system decentralization. Sun et al. [38] proposed a blockchain-based on-board social network data-sharing system. This scheme can realize one-to-many data sharing, but the identity of the shared entity needs to be determined in advance, making it difficult to realize large-scale and fine-grained data sharing. Su et al. [39] proposed an authorization Byzantine fault-tolerant algorithm based on node reputation, which can reach consensus among the various authorization partitions in CBCs. Yang et al. [40] built a new blockchain-based energy management architecture for IoT-assisted smart homes, enabling smart homes to interact with the grid and other users in an energy Internet system. Based on [40], Abishu et al. [41] proposed a new consensus mechanism, which takes advantage of practical Byzantine fault tolerance and proof of reputation to ensure the high reliability of energy transactions. Zhang et al. [42] proposed a consensus mechanism based on credit risk assessment to realize credit management of counterparties in distributed energy transactions. However, the above consensus research based on CBC still cannot meet high concurrency, low delay, and strong security in Byzantine cross-domain applications.
There are also researches such as Tezos [43], which proposed an on-chain governance model to generate blocks dynamically and realized the autonomous management of chain ecology by establishing a digital federation, thus simplifying the verification process of transactions and smart contracts, which has a broad application prospect in IoT where the computing power of node is limited. A time segmentation solution of CBC based on the Tezos blockchain was proposed by [44], which allows computing devices with low storage capacity to keep only the latest segmentation ledger instead of the whole consortium ledger. It supports the construction of mobile self-organizing CBC and inter-chain transactions under a 5G network of heterogeneous vehicle networking and conducts the built-in form verification of some transactions and smart contracts. Qasse et al. [45] tried to solve the cross-domain authentication and trust transfer between independent Inter-blockchain Communication (IBC) systems based on CBC to ensure the security of multi-domain consensus consistency of user identity. Practical Byzantine Fault Tolerance (PBFT) and other BFT consensus protocols do not require verification nodes to solve encryption problems or provide proof of stake to determine the ownership of accounting rights [46,47]. Generally, only a subset of participating nodes need to run the BFT protocol. The consensus can be reached by exchanging rounds of messages so that nodes can reach the consensus of the current round before the next round starts. Therefore, it has good anti-fork and potential application prospects in CBCs [48].
BFT protocol usually can be verified mathematically as long as 2/3 of the participants follow the protocol. Then, the BFT protocol can ensure no block conflicts regardless of whether there is an upper limit of network delay [46]. Some studies further explored solutions to improve the performance of the BFT consensus mechanism [49]. They proposed that cloud computing and programmable hardware can be used to improve the efficiency of the BFT consensus, allowing the consortium chain to deliver higher throughput, lower latency, and the ability to scale with better network bandwidth and hardware environments. However, BFT-like consensus protocols still face challenges, such as the communication systems’ high complexity and weak scalability.
Table 1 compares the existing research with the proposed work based on the research description, techniques, and limitations. However, these existing solutions usually require some nodes to be coordinators. If the coordinators are non-Byzantine nodes and messages are delivered timely in the asynchronous round, they broadcast their proposals to all nodes in the consortium network. If not, exploiting its power within the consensus round can significantly hinder the performance. This paper proposed a new consortium chain generation mechanism, which can realize cross-domain asynchronous message passing between multi-consortium chains without reducing the system’s security.
CBC is usually endorsed by institutions to determine the set of verification nodes and the block generation mechanism. In CBC, child blocks are voted from existing blocks to build a growing tree of blocks, the root of which is called a “creation block”. Normally, blocks form a single chain under the block generation mechanism, meaning a parent block has only one child block. However, due to network delays or malicious attacks, one parent block inevitably generates more than one child block to be confirmed. The consensus of CBC is to select only one child block from several unconfirmed child blocks of each parent block when asynchronous nodes are executed asynchronously and sequentially, that is, to select the most authoritative chain from the block tree.
The following is an Asynchronous node-based CBC Generation Model (ACCGM), of which the practicability and effectiveness are illustrated by experiments. From the perspective of chain generation, the influence of the logical and physical topology structure of the CBC network on its performance is analyzed. Then, a single chain generation rule is given to prevent CBC from forking.
Definition 1: Asynchronous Node Set (ANS). ANS refers to a set of asynchronous sequential execution nodes and their public keys in CBC, denoted as
ANS communicates by exchanging data through an asynchronous and reliable point-to-point consortium network. Any pair of nodes can be connected through a two-way communication channel. The transaction will not be lost, copied, or tampered with in the network transmission process, but there is a transaction transmission delay.
The ACCGM chain generation model satisfies the following properties:
Property 1: Recursion. Each new block
Eqs. (1) and (2) are recursive representations of blockchains. In Eq. (3),
Property 2: Locality. Due to network delay, eclipse attack, and other reasons, different CBC nodes are allowed to perceive different block sets in the chain generation model, namely:
Property 3: Inheritance. In the process of CBC generation, blockchain consensus has inheritance, namely:
If
It is assumed that a maximum of
Definition 2: Upper limit time
In Definition 2, the local time deviation of each node on CBC is incorporated into
Definition 3:
It can be seen that the correctness of node voting depends on the chain in which the node votes. Typically, the verifier
Definition 4: If block
As a basis for the recursive definition, it is generally assumed that Genesis Block
Definition 5: Absolute majority link. An absolute majority link means that for ordered block
Definition 6: Block conflict. Block conflict is considered to occur between blocks
From Definitions 2 to 6, it can be seen that if neither block
(1) The tail block
(2) There is an absolute majority link
(3) Blocks
(4) Block height
Thus, the single chain generation rule avoiding chain forking and ensuring at most one reasonable block height
Rule 1: Unequal height rule. If
Rule 2: Exclude rule. If
Rule 3: Nonoverlapping rule. For any height
The existing access mechanism of CBC helps improve the ability of the ACCGM-based CBC system to resist external attacks. Still, it cannot identify and prevent the threats of Byzantine nodes to the system. The impact of the behavior of Byzantine nodes in the ACCGM consensus on the system is analyzed as follows.
4.1 Behavior of Verification Node
In the ACCGM consensus process, Byzantine nodes can initiate abnormal voting without violating the rules to obtain a final result or retain the intermediate data in the calculation process to infer and snoop the data of other participants. On the one hand, when the verification node initiates non-voting behavior, the correct voting proportion of the verifier will be lower than the consensus threshold, and a consensus block will not be generated. On the other hand, if two or more conflicting validation blocks are generated in the same round due to malicious voting or incorrect behavior of the verifier, either the chain forks or the off-chain governance mechanism is used to support one branch at the expense of the other. Therefore, the analysis of verification node behavior matters in constructing the system incentive mechanism and ensuring the correct formation of CBC.
The voting behavior of the verification node will be written into the block as a transaction, which can be divided into correct voting, malicious voting, incorrect voting, and no voting.
A. Correct voting
If only a single block meets Definition 3 and has verification nodes exceeding the threshold and voting correctly in a certain round, the block will be written into CBC, and each node synchronizes the ledger.
B. Malicious voting
Malicious voting means that the verifier votes for two new blocks in the same round simultaneously, which meets Definition 6, thus causing a conflict.
C. Incorrect voting
Incorrect voting refers to the situation in which the verifier cannot vote correctly in the same consensus round due to some incorrect behavior. Typical cases of incorrect voting are as follows:
(1) The verifier sends the vote later, resulting in the vote not reaching CBC within the consensus round.
(2) Some nodes do not propagate the vote of a verification node, resulting in the vote not reaching CBC within the consensus round.
(3) The vote does not reach CBC within the consensus round due to network delay.
(4) The signature of the verifier’s vote is invalid.
(5) The voting block is not generated in the current highest block.
D. No voting
No voting includes no voting of the verification node and voting loss.
Non-byzantine nodes may produce votes A and C, and Byzantine nodes may produce votes B, C, and D. When dealing with voting transactions, CBC based on ABBCM only processes the correct voting A and malicious voting B defined above; the incorrect voting and no voting are invalid votes and will be ignored. If only correct votes exist, the system will select a single legal block within a specified time cycle and record it in CBC. Otherwise, the system may fail to obtain consensus due to the failure to obtain more than the threshold number of verification signatures in a specific time round, called active failure, or the system forks due to two conflicting blocks being finalized simultaneously, called a security failure.
The consortium institutions will use the punishment mechanism for cases B, C, and D. The mechanism is affected by the following aspects:
(1) The larger the proportion of malicious voting nodes, incorrect voting nodes, or non-voting nodes, the more serious the penalty will be.
(2) Failure to consensus or chain forks will increase punishment. The following is a formal analysis.
It is assumed that
where
By analyzing the behavior of validation nodes, the polymerization index of validation nodes was obtained to represent the consensus ability of consortium institutions. The node polymerization index
According to the Byzantine node proportion
4.2 Vulnerability of CBC Consensus
In the chain generation model ACCGM, the CBC network is partially synchronous, and the transaction transfer between nodes has an upper bound finite delay. Although the verification node can independently choose the time for issuing the voting transaction within each consensus round, it cannot ensure that the voting transaction of each verification node in each round will be synchronized among the CBC nodes before the end of the round. If the voting transaction is issued too early, the verification node will fail to vote on other more competitive blocks within the consensus round. Late issuance of voting transactions may result in activity consensus failure. In addition, the authentication node update transaction is allowed to be sent after only consensus blocks are generated in each consensus round, and the authentication node set is dynamically managed. Therefore, in a single consensus round, it is necessary to consider the impact of network partition, network delay, Byzantine node proportion, verification node state, and other factors on the consensus. Network partition and delay have been explained in the previous section. The following focuses on analyzing the influence of Byzantine node proportion and verification node state on the consensus.
4.2.1 Consensus Vulnerability Based on Byzantine Node Proportion
Consortium nodes are divided into ordinary nodes, which sort transactions and package blocks in the underlying chain, and verification nodes, which vote for new blocks; however, they are somewhat interdependent. Ordinary nodes collect and classify transactions, determine the order of transactions in CBC, and write global computer state information (contract variables, etc.) and related data into the block as part of the transaction. The voting transaction sent by the verification node is the same as the ordinary transaction, which needs to be packaged and recorded by the ordinary node. Byzantine ordinary nodes can refuse to include the voting transactions of some verification nodes in their proposed blocks. It can also improve the probability of successful execution of the above attacks by increasing the proportion of Byzantine nodes in a working state, sending out voting transactions in advance in consensus rounds, or even forcing other nodes to perform the same operation by network attacks.
When enough non-Byzantine nodes are offline in a certain period, the proportion of Byzantine nodes will increase, greatly improving the possibility of chain forking in the system. It is assumed that the proportion of Byzantine nodes in ACCGM-based CBC is

Figure 1: The relationship between Byzantine node proportion and system security
It can be seen that when
4.2.2 Consensus Vulnerability Based on Node Reputation
In the ACCGM-based CBC distributed network environment, the initial reputation of the node is provided by the endorsement of the institutions, which is a static trust management mechanism based on authentication and authorization. However, when each node participates in the calculation autonomously, using the initial reputation to evaluate the node often presents a lag to some extent. For example, nodes in the CBC network have the capability of routing and forwarding transactions or blocks. Nodes with high initial reputations hijacked by malicious forces can independently change the forwarding route or discard part of transactions or blocks. If nodes with high initial reputations provide fraudulent services or do not provide services, the system consensus will be seriously threatened. This paper established a node trust model of CBC based on consensus rotation information feedback and proposed a dynamic maintenance mechanism of node reputation relying on weighted trust feedback from nodes to improve the accuracy and dynamic adaptability of node reputation evaluation. The above model is quantitatively evaluated to further analyze the relationship between node reputation and CBC consensus.
Definition 7: Node reliability evaluation function. The reliability evaluation of node
where
Definition 8: Node set trust evaluation function. It is assumed that the number of CBC nodes in each consensus round is
In Eq. (15),
Before the system reaches a consensus at the beginning of each round, when the value of the trust evaluation function
(1) keeping the credit value of the verification node whose value of credibility evaluation function is higher than the preset value in each round unchanged;
(2) reducing the credibility value of verification nodes whose credibility evaluation function value is lower than the preset value or does not vote;
(3) removing the verification nodes whose reputation value is lower than the reputation threshold from the set of verification nodes, which will increase the influence of normally working verification nodes in the consortium institutions, significantly reducing the risk of system consensus.
5 Asynchronous Binary Byzantine Consensus-Based Chain Generation Mechanism
The above analysis of the influence of network partition, network delay, Byzantine node proportion, verification node state, and other factors on the consensus found that in CBC with
The ABBCM-based CBC generation mechanism relies on many-to-many communication of binary values of nodes, extending the common definition of Byzantine consensus and allowing a definite set of consensus values to combine multiple proposals. On the one hand, it is assumed that values proposed only by Byzantine nodes cannot be agreed upon, and non-Byzantine nodes can quickly achieve consensus without the help of coordinating nodes. On the other hand, if the consensus values proposed by non-Byzantine nodes are not consistent, the round of consensus will be terminated early. Let
• Certainty. Each non-Byzantine node will eventually propose a value for consensus.
• Consistency. No two non-Byzantine nodes determine different values.
• Validity. If all non-Byzantine nodes propose the same value for the consensus, the final consensus value will not be something else.
ABBCM relies on many-to-many communication (binary value broadcast) of node binary values, expressed as BiVa-B. In the BiVa-B instance, each non-Byzantine node
The following rules define BiVa-B:
Rule 1: Incremental rule. If at least (
Rule 2: Reverse rule. If
Rule 3: Diffusion rule. If a non-Byzantine node
Rule 4: Balancing rule. Finally, the local read-only variable set
Based on the above rules, the set of local read-only variables
System model


Stage 1: Consensus value cleaning to filter out the consensus value proposed by the Byzantine node. Node
Stage 2: Consensus value estimate exchange to reach a consensus. At this stage, node
• The values of
•
Thus, in any round of
Stage 3: Consensus values converge, a local calculation stage, to determine the candidate of consensus value of node
• If
• If
In the above ABBCM-based CBC generation mechanism, node
To test the performance of the asynchronous binary Byzantine consensus-based chain generation mechanism proposed in this paper, we built the Ethereum simulation test environment consisting of 100 virtual verification nodes on five servers and compared its performance with “Coin,” the recent randomized algorithm from Mostéfaoui et al. [52] used in the HoneyBadger blockchain. Experiments show that under all our workloads, our mechanism outperforms “Coin,” which is known to terminate in O (1) round in expectation. This is due to the overhead of the Coin implementation that slows down every round and the risks of being unlucky at tossing the coin by increasing the number of rounds needed to decide. Even with Byzantine behaviors, our method is always superior to the latter.
The experimental platform was CPU Xeon-E5 with memory size 64 G and operating system Ubuntu-64bit. Consortium chain
Considering that the behavior of Byzantine node can greatly affect chain generation based on binary Byzantine consensus, the following four typical Byzantine attack behaviors are constructed for performance testing:
BA1: Byzantine nodes send bit flip value; when the protocol specification expects to send bit
BA2: Byzantine nodes send the combination of the random value and the flipped value of the bit.
BA3: Byzantine nodes do not respond to any transactions.
BA4: Byzantine nodes form consortiums to block the consensus of non-Byzantine nodes in each round by sending messages.
To eliminate the influence of the time interval of constructing transactions on the delay, referring to the previous work [53] and take

Figure 2: Delay comparison between ABBCM and Coin
As shown in Fig. 2, when the Byzantine node proportion
(1) The consensus round time
Consensus round time

Figure 3: Throughput test under unrestricted conditions
As can be seen from Fig. 3, when consensus round time
(2) The consensus round time
Consensus round time
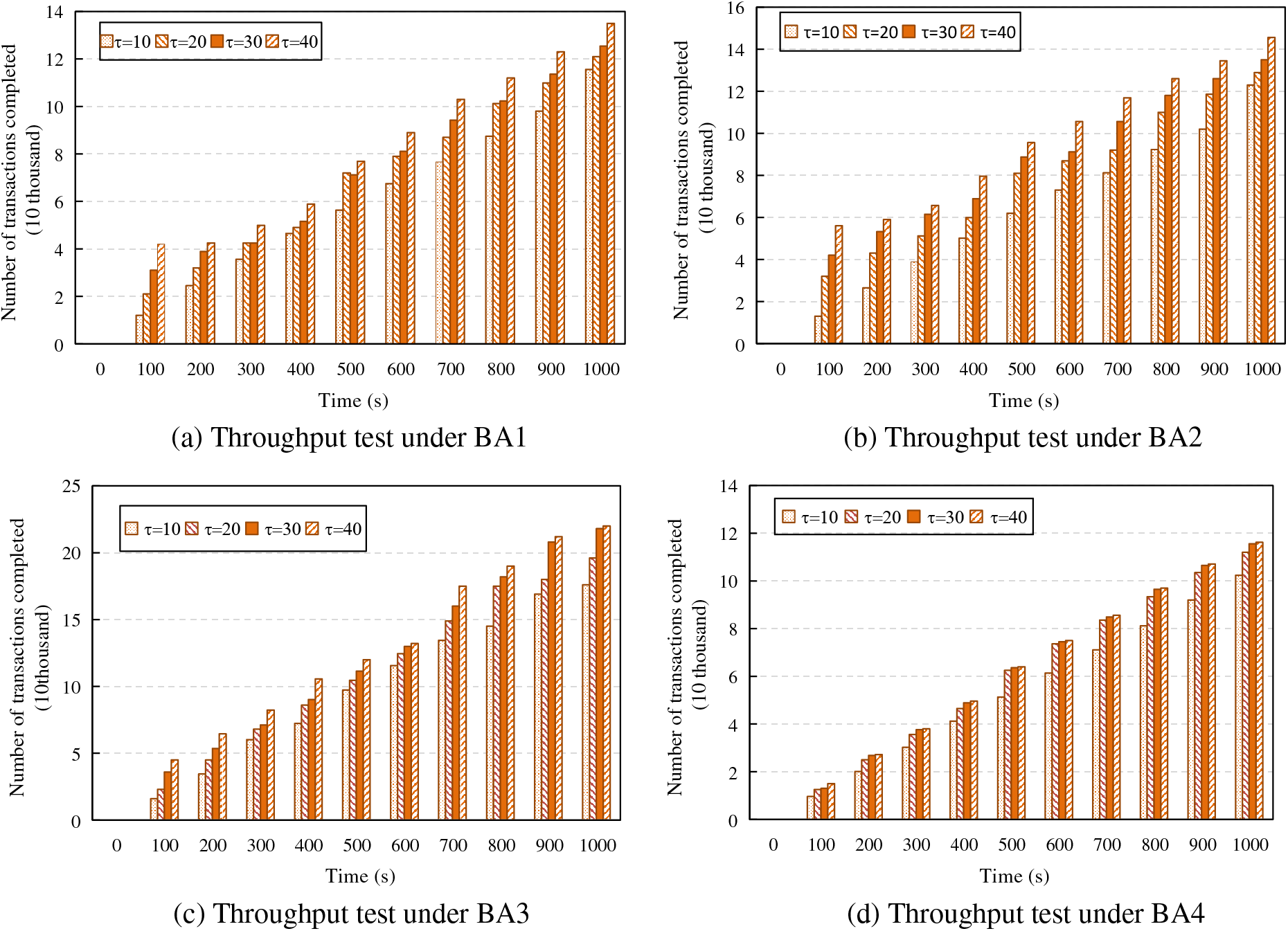
Figure 4: Throughput test under restricted conditions
Compared with the throughput test under unrestricted conditions, the system throughput decreases under the four attack modes when the consensus round time is set to 500 ms in Fig. 4. Under the same conditions, the average value of the highest throughput decreases by 9.2%, and the average value of the lowest throughput decreases by about 50%. In Fig. 4c, under attack BA3, system throughput declines slightly because Byzantine nodes do not respond to anything, which increases the influence of non-Byzantine nodes to some extent and thus weakens the influence of the reduction of consensus round time on consensus efficiency. In Figs. 4a and 4d, under attacks BA1 and BA4, the system throughput decreases greatly because the influence of Byzantine nodes reduces the consensus efficiency, failing part of the consensus to be completed within a consensus round time, especially when the number of consensus transactions in a single round is large. In addition, under attack BA4, after Byzantine nodes form a consortium, they cannot control the speed or order of messages from non-Byzantine nodes. However, they can observe and decide the time to send messages according to the time when non-Byzantine nodes receive or forward messages. Thus, they can significantly hinder the consensus progress within the round.
There is not yet an effective consensus algorithm ensuring safety and liveness in fully asynchronous message-passing systems, and even a single process may cause a consortium chain system to crash. However, the crash failure model is less severe than the Byzantine failure model because if the process commits Byzantine failure, the system cannot reach a consensus. To ensure consensus is reached, a consortium chain generation model based on ANS in the Byzantine environment is established to further analyze the influence of chain structure on its performance, obtaining single chain generation rules to avoid chain forking. On this basis, the influence of network partition, network delay, Byzantine node proportion, and verification node state on the consensus process is further analyzed, and a novel consortium chain generation mechanism based on asynchronous binary Byzantine consensus is proposed. The mechanism neither uses a classical (strong) coordinator nor relies on randomization or signatures, meaning it does not wait for a specific message. The above mechanism shows better consensus efficiency under the four classical Byzantine aggression behaviors and asynchronous environment. In the future, based on the study of the asynchronous binary Byzantine consensus mechanism, the relationship between the effectiveness of multiple Byzantine consensus mechanisms and the behavior of nodes in the chain generation process will be studied to meet the needs of more practical application scenarios.
Acknowledgement: The authors gratefully acknowledge the helpful comments and suggestions of the reviewers, which have improved the presentation.
Funding Statement: This work is supported by Henan University Science and Technology Innovation Talent Support Program (23HASTIT029), the National Natural Science Foundation of China (61902447), Tianjin Natural Science Foundation Key Project (22JCZDJC00600), Research Project of Humanities and Social Sciences in Universities of Henan Province (2024-ZDJH-061), Key Scientific Research Projects of Colleges and Universities in Henan Province (23A520054) and Henan Science and Technology Research Project (232102210124).
Author Contributions: Study conception and design: Rui Qiao; data collection: Shi Dong; analysis and interpretation of results: Rui Qiao, Shi Dong; draft manuscript preparation: Rui Qiao, Shi Dong. All authors reviewed the results and approved the final version of the manuscript.
Availability of Data and Materials: The authors confirm that the data supporting the findings of this study are available within the paper.
Conflicts of Interest: The authors declare that they have no conflicts of interest to report regarding the present study.
References
1. M. Dabbagh, K. Choo, A. Beheshti, M. Tahir and N. S. Safa, “A survey of empirical performance evaluation of permissioned blockchain platforms: Challenges and opportunities,” Computers & Security, vol. 100, no. 1, pp. 1–18, 2021. [Google Scholar]
2. W. Liang, Y. Yang, C. Yang, Y. Hu, S. Xie et al., “PDPChain: A consortium blockchain-based privacy protection scheme for personal data,” IEEE Transactions on Reliability, vol. 8, no. 5, pp. 586–598, 2022. [Google Scholar]
3. L. Vishwakarma and D. Das, “SmartCoin: A novel incentive mechanism for vehicles in intelligent transportation system based on consortium blockchain,” Vehicular Communications, vol. 33, no. 6, pp. 1–11, 2022. [Google Scholar]
4. M. Firdaus, S. Rahmadika and K. Rhee, “Decentralized trusted data sharing management on Internet of Vehicle Edge Computing (IoVEC) networks using consortium blockchain,” Sensors, vol. 21, no. 7, pp. 2410–2421, 2021. [Google Scholar] [PubMed]
5. K. Huang, X. Zhang, Y. Mu, X. Wang, G. Yang et al., “Building redactable consortium blockchain for industrial Internet-of-Things,” IEEE Transactions on Industrial Informatics, vol. 15, no. 6, pp. 3670–3679, 2019. [Google Scholar]
6. P. Li, G. Wang, X. Chen, F. Long and W. Xu, “Gosig: A scalable and high-performance byzantine consensus for consortium blockchains,” in SoCC’20: ACM Symp. on Cloud Computing, New York, NY, USA, pp. 223–237, 2020. [Google Scholar]
7. H. Huang, X. Chen and J. Wang, “Blockchain-based multiple groups data sharing with anonymity and traceability,” Science China Information Sciences, vol. 63, no. 3, pp. 1–13, 2020. [Google Scholar]
8. P. Zheng, Q. Xu, Z. Zheng, Z. Zhou, Y. Yan et al., “Meepo: Sharded consortium blockchain,” in 2021 IEEE 37th Int. Conf. on Data Engineering (ICDE), Chania, Greece, pp. 1847–1852, 2021. [Google Scholar]
9. C. Wang, C. Jiang, J. Wang, S. Shen, S. Guo et al., “Blockchain-aided network resource orchestration in intelligent Internet of Things,” IEEE Internet of Things Journal, vol. 10, no. 7, pp. 6151–6163, 2023. [Google Scholar]
10. S. Aggarwal and N. Kumar, “A consortium blockchain-based energy trading for demand response management in vehicle-to-grid,” IEEE Transactions on Vehicular Technology, vol. 70, no. 9, pp. 9480–9494, 2021. [Google Scholar]
11. T. Meng, Y. Zhao and K. Wolter, “On consortium blockchain consistency: A queueing network model approach,” IEEE Transactions on Parallel and Distributed Systems, vol. 32, no. 6, pp. 1369–1382, 2021. [Google Scholar]
12. F. Xiao, T. Lai, Y. Guan, J. Hong, H. Zhang et al., “Application of blockchain sharding technology in Chinese medicine traceability system,” Computers, Materials & Continua, vol. 76, no. 1, pp. 35–48, 2023. [Google Scholar]
13. J. Grover, “Security of vehicular ad hoc networks using blockchain: A comprehensive review,” Vehicular Communications, vol. 34, no. 1, pp. 100458–100477, 2022. [Google Scholar]
14. Y. Chen, B. Hu, H. Yu, Z. Duan and J. Huang, “A threshold proxy re-encryption scheme for secure IoT data sharing based on blockchain,” Electronics, vol. 10, no. 19, pp. 2359–2377, 2021. [Google Scholar]
15. K. Yu, L. Tan, M. Aloqaily, H. Yang and Y. Jararweh, “Blockchain-enhanced data sharing with traceable and direct revocation in IIoT,” IEEE Transactions on Industrial Informatics, vol. 17, no. 11, pp. 7669–7678, 2021. [Google Scholar]
16. P. Sun, S. Shen, Z. Wu, H. Zhou and X. Gao, “Stimulating trust cooperation in edge services: An evolutionary tripartite game,” Engineering Applications of Artificial Intelligence, vol. 116, no. 11, pp. 1–6, 2022. [Google Scholar]
17. S. Yu, Z. Jie, G. Wu, H. Zhang and S. Shen, “FedNRM: A federal personalized news recommendation model achieving user privacy protection,” Intelligent Automation & Soft Computing, vol. 37, no. 2, pp. 1729–1751, 2023. [Google Scholar]
18. G. Wu, L. Xie, H. Zhang, J. Wang, S. Shen et al., “STSIR: An individual-group game-based model for disclosing virus spread in social Internet of Things,” Journal of Network and Computer Applications, vol. 214, no. 1, pp. 1–7, 2023. [Google Scholar]
19. S. Shen, X. Wu, P. Sun, H. Zhou, Z. Wu et al., “Optimal privacy preservation strategies with signaling Q-learning for edge-computing-based IoT resource grant systems,” Expert Systems with Applications, vol. 225, no. 1, pp. 1–6, 2023. [Google Scholar]
20. R. Garcia, G. Ramachandran, R. Jurdak and J. Ueyama, “Blockchain-aided and privacy-preserving data governance in multi-stakeholder applications,” IEEE Transactions on Network and Service Management, vol. 19, no. 4, pp. 3781–3793, 2022. [Google Scholar]
21. Y. Ren, Y. Leng, J. Qi, P. Sharma, J. Wang et al., “Multiple cloud storage mechanism based on blockchain in smart homes,” Future Generation Computer Systems, vol. 115, no. 1, pp. 304–313, 2021. [Google Scholar]
22. T. Cai, H. Lin, W. Chen, Z. Zheng and Y. Yu, “Efficient blockchain empowered data sharing incentive scheme for Internet of Things,” Journal of Software, vol. 32, no. 4, pp. 953–972, 2021. [Google Scholar]
23. Z. Liu and Z. Li, “A blockchain-based framework of cross-border e-commerce supply chain,” International Journal of Information Management, vol. 52, no. 6, pp. 1–9, 2020. [Google Scholar]
24. C. Cachin, “Architecture of the hyperledger blockchain fabric,” in Workshop on Distributed Cryptocurrencies and Consensus Ledgers, Chicago, USA, pp. 1–4, 2016. [Google Scholar]
25. H. Sukhwani, N. Wang, K. Trivedi and A. Rindos, “Performance modeling of hyperledger fabric (permissioned blockchain network),” in 2018 IEEE 17th Int. Symp. on Network Computing and Applications (NCA), Cambridge, MA, USA, pp. 1–8, 2018. [Google Scholar]
26. D. Agrawal, S. Minocha and S. Namasudra, “A robust drug recall supply chain management system using hyperledger blockchain ecosystem,” Computers in Biology and Medicine, vol. 140, no. 1, pp. 1–15, 2022. [Google Scholar]
27. N. Sammeta and L. Parthiban, “Hyperledger blockchain enabled secure medical record management with deep learning-based diagnosis model,” Complex & Intelligent Systems, vol. 8, no. 1, pp. 625–640, 2022. [Google Scholar]
28. J. Minango, M. Zambrano and W. Parada, “Proof of concepts of corda blockchain technology applied on the supply chain area,” in Trends in Artificial Intelligence and Computer Engineering, Riobamba, Ecuador, pp. 619–631, 2023. [Google Scholar]
29. S. Panda, S. Daliyet and S. Lokre, “Distributed ledger technology in the construction industry using corda,” The New Advanced Society: Artificial Intelligence and Industrial Internet of Things Paradigm, vol. 1, no. 1, pp. 15–41, 2022. [Google Scholar]
30. M. Mazzoni, A. Corradi and V. Di Nicola, “Performance evaluation of permissioned blockchains for financial applications: The consensys quorum case study,” Blockchain: Research and Applications, vol. 3, no. 1, pp. 1–12, 2022. [Google Scholar]
31. T. Kuo and A. Pham, “Quorum-based model learning on a blockchain hierarchical clinical research network using smart contracts,” International Journal of Medical Informatics, vol. 169, no. 1, pp. 1–9, 2023. [Google Scholar]
32. S. Saad and R. Radzi, “Comparative review of the blockchain consensus algorithm between Proof of Stake (PoS) and Delegated Proof of Stake (DPoS),” International Journal of Innovative Computing, vol. 10, no. 2, pp. 1–6, 2020. [Google Scholar]
33. C. Akcora, Y. Gel and M. Kantarcioglu, “Blockchain networks: Data structures of Bitcoin, Monero, Zcash, Ethereum, Ripple, and Iota,” Wiley Interdisciplinary Reviews: Data Mining and Knowledge Discovery, vol. 12, no. 1, pp. 1–35, 2022. [Google Scholar]
34. A. Kiayias, A. Russell, B. David and R. Oliynykov, “Ouroboros: A provably secure proof-of-stake blockchain protocol,” in Advances in Cryptology-CRYPTO 2017, Cham, Switzerland: Springer, pp. 357–388, 2017. [Google Scholar]
35. H. Sukhwani, J. M. Martínez, X. Chang, K. S. Trivedi and A. Rindos, “Performance modeling of PBFT consensus process for permissioned blockchain network (Hyperledger Fabric),” in 2017 IEEE 36th Symp. on Reliable Distributed Systems (SRDS), Hong Kong, China, pp. 253–255, 2017. [Google Scholar]
36. M. Conti, A. Gangwal and M. Todero, “Blockchain trilemma solver algorand has dilemma over undecidable messages,” in Proc. of the 14th Int. Conf. on Availability, Reliability and Security, Canterbury, UK, pp. 1–8, 2019. [Google Scholar]
37. M. Yin, D. Malkhi, M. K. Reiter, G. G. Gueta and I. Abraham, “Hotstuff: BFT consensus with linearity and responsiveness,” in Proc. of the 2019 ACM Symp. on Principles of Distributed Computing (PODC ‘19), New York, NY, USA, pp. 347–356, 2019. [Google Scholar]
38. J. Sun, H. Xiong, S. Zhang, X. Liu, J. Yuan et al., “A secure flexible and tampering-resistant data sharing system for vehicular social networks,” IEEE Transactions on Vehicular Technology, vol. 69, no. 11, pp. 12938–12950, 2020. [Google Scholar]
39. Z. Su, Y. Wang, Q. Xu, M. Fei, Y. Tian et al., “A secure charging scheme for electric vehicles with smart communities in energy blockchain,” IEEE Internet of Things Journal, vol. 6, no. 3, pp. 4601–4613, 2018. [Google Scholar]
40. Q. Yang and H. Wang, “Privacy-preserving transactive energy management for IoT-aided smart homes via blockchain,” IEEE Internet of Things Journal, vol. 8, no. 14, pp. 11463–11475, 2021. [Google Scholar]
41. H. Abishu, A. Seid, Y. Yacob, T. Ayall, G. Sun et al., “Consensus mechanism for blockchain-enabled vehicle-to-vehicle energy trading in the Internet of Electric Vehicles,” IEEE Transactions on Vehicular Technology, vol. 71, no. 1, pp. 946–960, 2021. [Google Scholar]
42. Y. Zhang, “Distributed energy intelligent transaction model and credit risk management based on energy blockchain,” Journal of Information Science & Engineering, vol. 37, no. 1, pp. 55–66, 2021. [Google Scholar]
43. V. Allombert, M. Bourgoin and J. Tesson, “Introduction to the tezos blockchain,” in 2019 Int. Conf. on High Performance Computing & Simulation (HPCS), Dublin, Ireland, pp. 1–10, 2019. [Google Scholar]
44. M. Allouche, T. Frikha and M. Mitrea, “Lightweight blockchain processing case study: Scanned document tracking on tezos blockchain,” Applied Sciences, vol. 11, no. 15, pp. 1–17, 2021. [Google Scholar]
45. I. Qasse, M. Talib and Q. Nasir, “Toward inter-blockchain communication between hyperledger fabric platforms,” Trust Models for Next-Generation Blockchain Ecosystems, vol. 4, no. 1, pp. 251–272, 2021. [Google Scholar]
46. S. Gupta, J. Hellings, S. Rahnama and M. Sadoghi, “An in-depth look of BFT consensus in blockchain: Challenges and opportunities,” in Proc. of the 20th Int. Middleware Conf. Tutorials, New York, NY, USA, pp. 6–10, 2019. [Google Scholar]
47. R. Saltini, “BigFooT: A robust optimal-latency BFT blockchain consensus protocol with dynamic validator membership,” Computer Networks, vol. 204, no. 1, pp. 1–33, 2022. [Google Scholar]
48. Y. Li, L. Qiao and Z. Lv, “An optimized Byzantine fault tolerance algorithm for consortium blockchain,” Peer-to-Peer Networking and Applications, vol. 14, no. 1, pp. 2826–2839, 2021. [Google Scholar]
49. K. Sit, M. Bravo and Z. István, “An experimental framework for improving the performance of BFT consensus for future permissioned blockchains,” in Proc. of the 15th ACM Int. Conf. on Distributed and Event-Based Systems, Virtual Event, Italy, pp. 55–65, 2021. [Google Scholar]
50. R. Anu and S. Prakash, “A privacy-preserving authentic healthcare monitoring system using blockchain,” International Journal of Software Science and Computational Intelligence, vol. 14, no. 1, pp. 1–23, 2022. [Google Scholar]
51. C. Esposito, M. Ficco and B. Gupta, “Blockchain-based authentication and authorization for smart city applications,” Information Processing & Management, vol. 58, no. 2, pp. 1–16, 2021. [Google Scholar]
52. A. Mostéfaoui, H. Moumen and M. Raynal, “Signature-free asynchronous Byzantine consensus with t < n/3 and O(n2) messages,” in Proc. of the 2014 ACM Symp. on Principles of Distributed Computing, Paris, France, pp. 2–9, 2014. [Google Scholar]
53. R. Qiao, X. Luo, S. Zhu, X. Yan and Q. Wang, “Dynamic autonomous cross consortium chain mechanism in e-healthcare,” IEEE Journal of Biomedical and Health Informatics, vol. 24, no. 8, pp. 2157–2168, 2020. [Google Scholar] [PubMed]
Cite This Article
 Copyright © 2023 The Author(s). Published by Tech Science Press.
Copyright © 2023 The Author(s). Published by Tech Science Press.This work is licensed under a Creative Commons Attribution 4.0 International License , which permits unrestricted use, distribution, and reproduction in any medium, provided the original work is properly cited.


 Submit a Paper
Submit a Paper Propose a Special lssue
Propose a Special lssue View Full Text
View Full Text Download PDF
Download PDF
 Downloads
Downloads
 Citation Tools
Citation Tools