 Open Access
Open Access
ARTICLE
LSTDA: Link Stability and Transmission Delay Aware Routing Mechanism for Flying Ad-Hoc Network (FANET)
1 Department of Computer Science and Engineering, Sungkyunkwan University, Seoul, 03063, South Korea
2 Information Engineering School, Chang’an University, Xi’an, 710061, China
3 College of Technological Innovation, Zayed University, Dubai, 19282, United Arab Emirates
4 School of Computer Science and Technology, Zhejiang Gongshang University, Hangzhou, 310018, China
5 Institute of Computer Science and IT, The University of Agriculture Peshawar, Peshawer, 25120, Pakistan
6 Department of Computer Science and Technology, Kean University, Union, New Jersey, 07083, USA
* Corresponding Author: Daehan Kwak. Email:
(This article belongs to the Special Issue: AI-driven Cybersecurity in Cyber Physical Systems enabled Healthcare, Current Challenges, Requirements and Future research Foresights)
Computers, Materials & Continua 2023, 77(1), 963-981. https://doi.org/10.32604/cmc.2023.040628
Received 25 March 2023; Accepted 24 July 2023; Issue published 31 October 2023
Abstract
The paper presents a new protocol called Link Stability and Transmission Delay Aware (LSTDA) for Flying Ad-hoc Network (FANET) with a focus on network corridors (NC). FANET consists of Unmanned Aerial Vehicles (UAVs) that face challenges in avoiding transmission loss and delay while ensuring stable communication. The proposed protocol introduces a novel link stability with network corridors priority node selection to check and ensure fair communication in the entire network. The protocol uses a Red-Black (R-B) tree to achieve maximum channel utilization and an advanced relay approach. The paper evaluates LSTDA in terms of End-to-End Delay (E2ED), Packet Delivery Ratio (PDR), Network Lifetime (NLT), and Transmission Loss (TL), and compares it with existing methods such as Link Stability Estimation-based Routing (LEPR), Distributed Priority Tree-based Routing (DPTR), and Delay and Link Stability Aware (DLSA) using MATLAB simulations. The results show that LSTDA outperforms the other protocols, with lower average delay, higher average PDR, longer average NLT, and comparable average TL.Keywords
With the advancement and rapid development of technology, various types of communication networks have been introduced [1]. Among these networks, self-organizing networks play an important role due to their ability to be deployed in emergencies, ease of installation [2], and lack of centralized control required by traditional infrastructure [3]. Each device utilized in these innovative technologies can cover multiple aspects of a telecom organization. Mobile Ad-hoc Networks (MANETs) are dedicated networks where nodes establish an ad hoc network and move from one location to another without centralized leasing control. Flying Ad hoc Networks (FANETs) are a novel form of MANET and represent one such network [4]. FANETs consist of custom-built devices that enable the deployment of fifth-generation Unmanned Aerial Vehicles (UAVs) in three dimensions. Nodes within these networks can be positioned, extended, and transferred [5]. Terms such as drones, quadcopters, and airplanes are used to describe these nodes. The coupling approach allows these nodes to join other nodes to aggregate their test functions [6]. Drones can capture their surroundings using fixed cameras with two types of detection capabilities. One is active detection, where drones closely examine regions of interest [7]. The other is passive detection, where a UAV detector acquires the target and then compiles and processes the data for further analysis by the operator at the base station [8]. Ad-hoc networks, particularly FANETs, are well-suited for creating temporary networks, and their deployment is facilitated by their ability to handle both ground nodes and flying nodes. FANETs offer ease of deployment, as they require no human personnel, reducing risks and dangers. The primary reason for utilizing FANETs in this work is the market demand for ad hoc networks, with FANETs being particularly sought after.
Technology is constantly evolving, and right from the beginning, it has surpassed demand at the highest level and continues to grow. Significant efforts have been made to enhance FANET in terms of power, routing, security, and node scalability [9], as well as its geographic coverage. Various authors have published their work on improving FANET from different perspectives [10–12]. Numerous challenges in this network require appropriate solutions [13,14]. By envisioning an efficient algorithm, the network can reach its peak performance. The research on FANET is still in its early stages, and several approaches have already been proposed to enhance routing in FANET, such as Distributed Priority Tree-based Routing (DPTR), Link Stability Estimation-based Routing (LEPR), Delay and Link Stability Aware (DLSA) [15], and others. In a previous study, the authors proposed a routing algorithm for establishing reliable connections and designed routing trees as intermediaries for different operational units of FANET, including terrestrial, air, and relay connections. However, due to the limitations and shortcomings of the previous work, the current research focuses on improving link reliability and selecting network corridors that maximize channel utilization. The proposed approach has been evaluated in various scenarios, and the main motivation behind it is the effectiveness of the proposed protocol called Link Stability and Transmission Delay Aware (LSTDA) across all scenarios. This research is driven by multiple motivations, with the primary priority being the improvement of FANET routing protocols. Given the existing protocols in FANET, routing remains a major concern, and therefore, reliability and transmission losses are the main areas of research. Stability is measured using a defined metric, which generates three distinct values for stability that are also used for selecting network corridors while considering channel utilization.
FANET consists of flying nodes known as UAVs that can be operated remotely or through an alternative mechanism [16]. The high maneuverability and three-dimensional movement of UAVs pose a research challenge in terms of avoiding transmission loss (TL), minimizing delay, and stabilizing communication between nodes in this network. Existing routing methods in FANET, such as LEPR and DPTR, are specifically designed to ensure transmission loss, latency, and continuous communication among drones. LEPR takes a routing perspective by utilizing the Ad hoc On-Demand Distance Vector (AODV) routing protocol. It introduces stability metrics based on Global Positioning System (GPS) location information from airborne nodes to assess link stability. This approach enables the prediction of mobility, security, and connection quality. To establish stable connections, LEPR employs a flooding mechanism that determines suitable paths for data transmission among neighboring nodes. However, using the stability metric as a threshold for both Route Request (RREQ) and Route Reply (RREP) is unnecessary and leads to packet loss and delay. Moreover, this approach introduces overhead and suffers from packet loss due to high-threshold metrics, causing nodes to be unable to maintain a normal reception level for all packets [17].
The issues with the existing systems are highlighted in this section, specifically mentioning DPTR and LEPR. On the other hand, DPTR introduces the challenge of network segmentation, which utilizes the different operating units of FANETs to function in three ad hoc units: air (M), terrestrial (N), and neural interface (K). This approach incorporates a red-black (R-B) tree to prioritize node communication efficiently. The concept employed in this research is to leverage each node’s capabilities, addressing the main network issue of high latency. DPTR utilizes a distributed network of networks, with the neural interface serving as the central operational node due to the longer time required to establish higher priority connections between nodes, thus allowing other nodes to be preserved. Two current approaches to tackle these issues are barriers and barriers, both aiming to enhance the security and functionality of FANET. Both LEPR and DPTR possess their own advantages and disadvantages. In this context, a recent study revealed a correlation between the processes of LEPR and DPTR, leading to the development of LSTDA. The fusion of the current quality measures in our research significantly contributes to pollution prevention and stabilization (DPTR and LEPR).
The motivation and core contribution of this work encompasses various aspects of a novel approach. The approach revolves around link stability, relay strategy, and the selection of high-priority nodes in network corridors. The proposed work aims to enhance the network’s performance by modifying the Packet Delivery Ratio (PDR) and reducing network delay. The PDR is increased through the maximization of link stability, while the network delay is reduced by utilizing the R-B tree to optimize channel usage, thereby minimizing the distance between nodes. The uniqueness of the proposed work lies in its introduction of the link stability metric, prioritization of Network Corridor (NCs), and the maximum utilization of channels in FANET, with a specific emphasis on maintaining communication stability among flying nodes. Additionally, the work introduces a threshold measuring calculation for stability and prioritizes the reduction of delay among nodes, including the End-to-End Delay (E2ED) within the network. The main contributions of this work are outlined as follows:
• This paper proposes a new LSTDA routing protocol for FANET, which intelligently focuses on network corridor selection to ensure link stability and channel utilization. Furthermore, the proposed work establishes a strong association between link stability and network corridor selection.
• An efficient and novel routing system based on channel utilization and network corridor priority is developed and presented. Additionally, an advanced LSTDA network corridor with maximum channel utilization is introduced as a reliability metric threshold method.
• The functionality of the proposed LSTDA protocol is achieved through the implementation of a fair selection R-B tree, specifically designed to handle a large number of nodes, thus ensuring optimal and equitable communication. Moreover, the proposed protocol is designed to operate in high-mobility scenarios involving UAVs, while maintaining fair communication.
• This paper thoroughly investigates new issues and challenges related to routing in FANET.
• A comprehensive analysis and evaluation of the routing protocols LEPR, DPTR, and DLSA are presented, considering parameters such as E2ED, PDR, Network Lifetime (NLT), and Transmission Loss (TS), in comparison with the LSTDA routing protocol for FANET.
The remaining sections of this article are organized as follows: Section 2 discusses related works, Section 3 presents the proposed methodology, Section 4 describes the simulation results, Section 5 provides conclusions and recommendations for future research, and the article concludes.
The LEPR routing protocol focuses on ensuring link stability by employing threshold metrics to calculate reliability in critical scenarios [9]. Additionally, LEPR utilizes preemptive mechanisms using the RREQ and RREP methods of the AODV routing protocol. The protocol takes into account factors such as quality of service, predicted mobility, and connection quality. Performance evaluations of the LEPR protocol, based on AODV and Dynamic Source Routing (DSR), demonstrate its effectiveness in terms of routing costs, delay, and packet rate. Another FANET routing protocol, known as the Adaptive Density-Based Routing Protocol (ADRP) [10], aims to enhance transport efficiency by adaptively determining transportability. ADRP incrementally compensates for a hub’s rebroadcast potential to dictate a demand bundle based on the number of neighboring hubs. The program has shown that ADRP outperforms AODV in terms of packet delivery percentage, start-end delay, routing load, Media Access Control (MAC) load, and throughput. ADRP adaptively calculates the transmission probability to determine the validity of the guiding heuristic. A comparison between the Destination Sequenced Distance Vector (DSDV) and AODV protocols for FANET is conducted, with a particular focus on energy values as it poses a significant challenge due to the flight characteristics of UAVs in this network [11]. Another study [12] addressed the issue of organizational boundaries between air and ground missions and proposes a guiding convention for transfers under a common scheme. This convention is governed by DPTR, which utilizes a red-black tree to form a demand network that determines the appropriate node and switching channel. The results showed significant improvements in various metrics such as packet delivery rates, channel utilization, start-to-end delays, overhead, uptime potential, and organizational throughput. To manage FANET scheduling, a variant of the Ant Colony Optimization (ACO) process called AntHocNet (AHN) is proposed [14], with a focus on minimizing energy usage for different organizations. Evaluation results demonstrate that AHN outperforms ACO. In the study [18], a clustering tool-based calculation was proposed to ensure sensitive coverage and rapid portability of UAV networks while extending tissue lifetime and ensuring reliable communications. The proposed approach isolates and selects the best assignments for clustered components, and evaluation is performed using two clustering schemes: Bio-Inspired Clustering Schemes for FANET (BICSF) and Energy-Attention Link-Based Clustering (EALC) based on Health, High PDR, Low Latency (EMASS) Guarantees Clustering. In [19], a boosting method for the Optimized Link State Routing Protocol (OLSR) called the Whale Optimization Algorithm (WOA) is presented to stabilize energy productivity in FANET. The proposed approach is compared to the existing work at a high level. Routing protocols and link stability are still in the early stages of development for FANET [20]. Routing is a primary concern in FANET due to the 3D motion of high-speed UAVs, with researchers focusing on ensuring link stability and conserving energy due to the limited battery capacity of these drones [21,22]. The study on FANET predominantly discusses routing protocols [23], with proposed approaches aimed at improving network reliability and connection stability between all nodes [24,25]. Some of these proposed protocols are hybrid [26,27], while others have been comparatively evaluated [28]. Additionally, a resource allocation protocol has been suggested for air slicing in multiple flexible UAV-assisted cellular communications [29], including Machine-to-Machine (M2M) [30] and Device-to-Device (D2D) communications [31–34]. A reliable and energy-efficient route selection protocol is proposed to efficiently reduce energy consumption and network latency [35]. Moreover, the same authors have proposed a novel routing protocol (RP) for heterogeneous environments, such as fault-tolerant aware (FTA) and workload resource management, to enhance energy efficiency [36,37].
Research on routing protocols for FANET is still in its early stages. The primary challenge in this network is routing, given the high-speed nodes that move in three dimensions. Researchers have focused on improving routing to ensure link stability and energy efficiency, considering that UAVs are equipped with small batteries and are remotely operated. The existing literature has proposed various approaches to enhance network performance. Our proposed protocol aims to tackle the issue of network partitioning and maintain link stability among all nodes by introducing a new stability metric based on threshold values. Previous studies have mainly focused on hybrid routing protocols and conducted comparative evaluations. However, our research distinguishes itself as we have developed a standalone routing protocol capable of addressing the network partitioning problem while simultaneously supporting three units and introducing a novel stability metric.
This section presents the research methodology, focusing on the simulation setup and the design of the system model depicted in Fig. 1 for the LSTDA protocol.
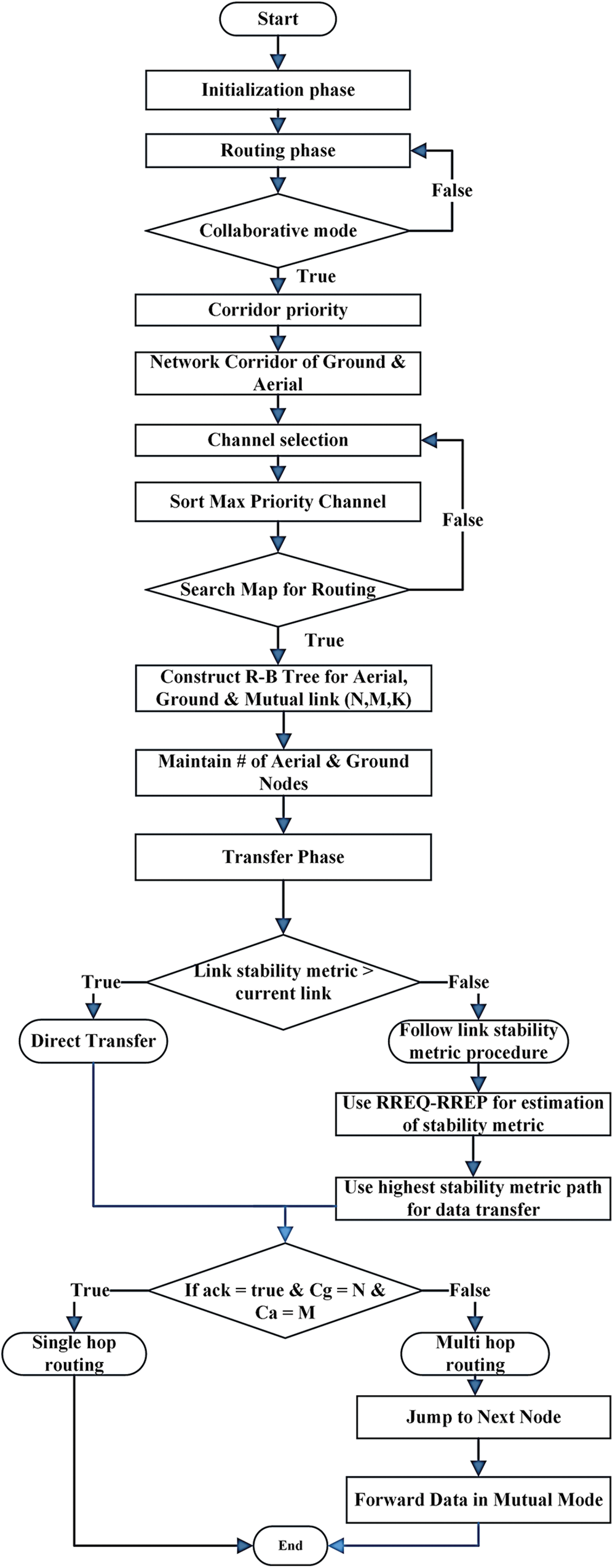
Figure 1: Working algorithm and flow of the routing protocol LSTDA
3.1 LSTDA: The Proposed Protocol
The proposed LSTDA protocol, as shown in Fig. 1, involves several steps. The first step is initialization, followed by the routing phase where the routing tree is examined to determine the need for cooperative mode communication. If the condition is met, the network switches to corridor priority. If the condition is not met, it reverts back to the previous routing step. Assuming the condition is accepted, the nodes are divided into two groups: external UAVs (acting as reset and shutdown nodes) and internal UAVs (acting as routing devices), which are combined into a self-organizing network corridor. Channel selection occurs next, with the highest priority channel being chosen for both the air and terrestrial ad hoc networks. The subsequent step is to determine the best route based on priority. If the selected ground node does not align with the network corridor, the protocol returns to the channel selection phase. If the conditions are met, a red-black tree is constructed for the three networks: ground (N), air (M), and intermediary neural networks (N). This process involves two phases, one for maintaining the number of antenna nodes and the other for combining them to obtain the number of ground nodes. The next step involves the roadmap and transmission phase, which is governed by two conditions related to the link stabilization procedure. This step is conditional and follows the preferred node selection path. It proceeds to the link stabilization process to establish link stability between nodes that will transmit data in case of a link failure or improper connection. If the link stability metric exceeds a certain threshold, data is transmitted using the link reliability process. Otherwise, the path with the best reliability metric value is chosen for communication by evaluating the reliability metric process. This scheme utilizes RREQ and RREP to determine the most reliable metric for the current connection.
Once the reliability of the link with the highest metric is confirmed, the priority node is selected. If the check verifies that the terrestrial corridor (Cg) matches the terrestrial network and the antenna corridor (Ca) corresponds to the air network, the process proceeds to the single-hop routing step, which leads to the final step if the current state is true. However, if the condition is false, it moves to the multi-hop routing stage and connects to the subsequent stage. At this point, communication transitions to the next stage, which is the one-hop routing step, and then returns to the previous exit step. If the check in the exit step is true, the process advances to the subsequent step where the terrestrial and air ad hoc networks are interconnected through neural interfaces or mutual mode. Finally, the process proceeds to the next end state.
Algorithm 1 employs a link stability approach that incorporates threshold values. The provided metric ensures the maintenance of a stable link between nodes, which is dependent on link stability. The summation value results in 1, indicating the presence of stable links. If the value drops below 1, it signifies the absence of stable links. Conversely, if the value exceeds 1, the velocity of the UAVs increases, resulting in unstable links and posing challenges to maintaining reliable communication. Algorithm 1 serves as the central component of the proposed work, outlining the convergence and evaluation of the LSTDA routing protocol. It presents the overall link stability of LSTDA and establishes initial and maximum threshold metric values, each corresponding to a specific routing method for link stability. The algorithm prioritizes link stability and maximum network corridor when deploying and selecting nodes, favoring nodes with high-stability links and shorter distances. Fair node selection is achieved through the use of an R-B tree, and the threshold values range from 0 to 1, with 0 indicating no link stability and 1 indicating a stable link that allows direct communication or communication through a neighboring node. In this algorithm, N, M, and K represent the ground, aerial, and relay layers, respectively. Additionally, the algorithm utilizes three input values, specifically 0.33, 0.34, and 0.33, to ensure highly stable link connectivity with a summation of 1. The term NC refers to the network corridor in the algorithm, and Eq. (2) provides an additional implementation of Algorithm 1. Table 1 presents several parameters proposed for LSTDA.
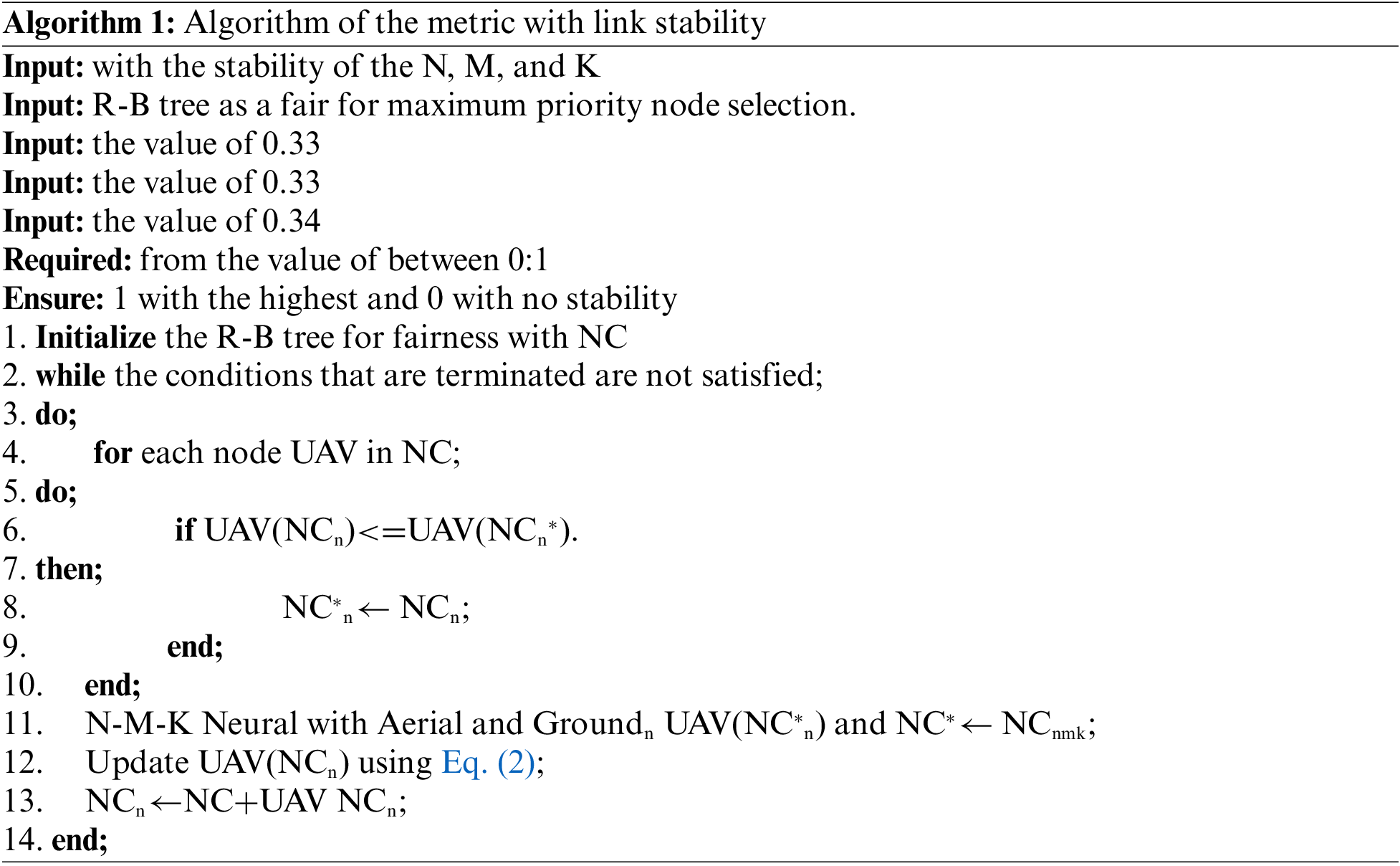
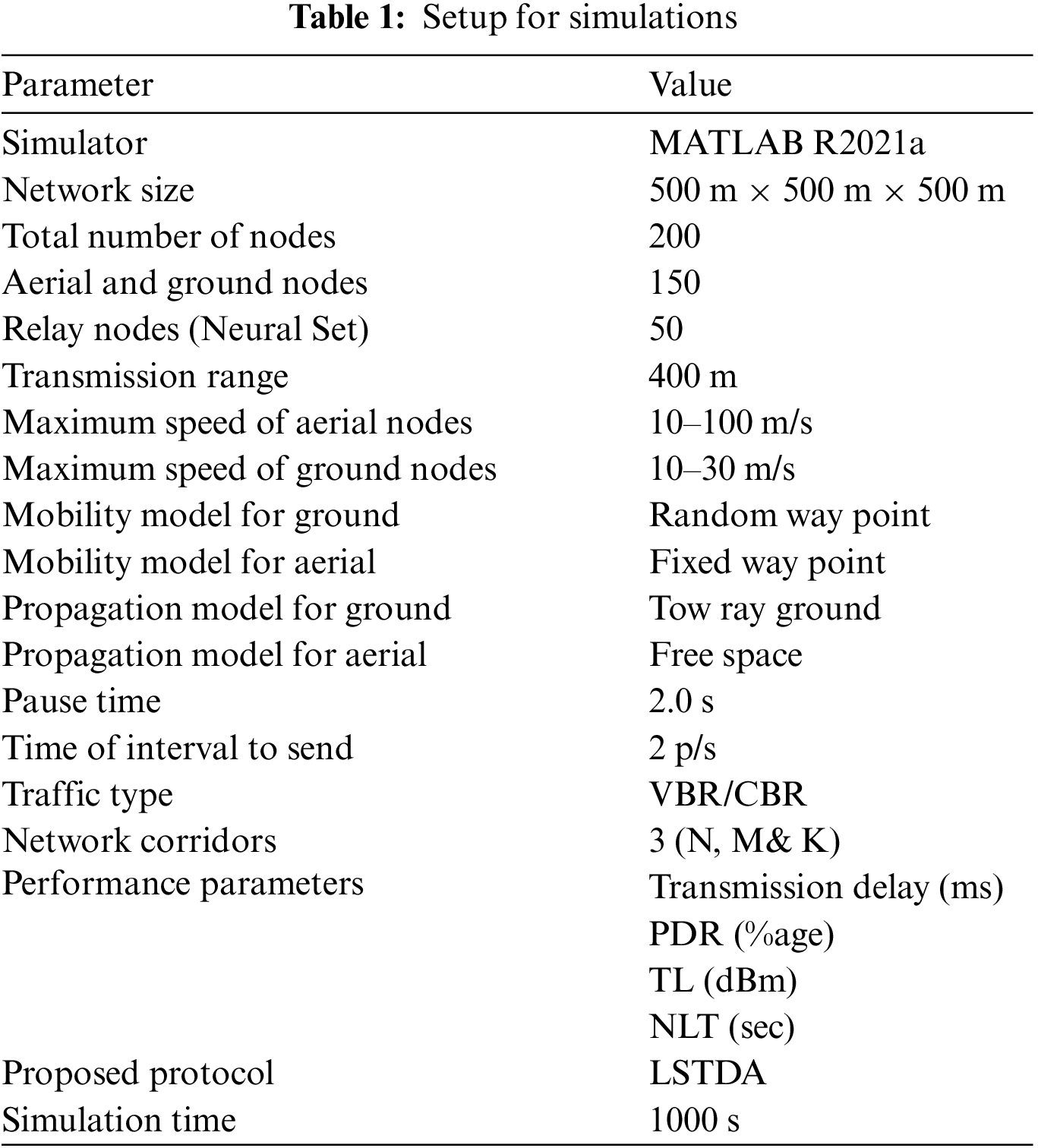
The design strategy of the proposed LSTDA is illustrated in Fig. 2, which includes a mathematical model consisting of multiple numerical illustrations and equations. These equations demonstrate the network corridor with maximum channel utilization. The simulation was carried out in MATLAB.
Figure 2: Design of LSTDA based on DPTR and LEPR existing routing protocols
The mathematical model is the core methodology of the proposed LSTDA routing protocol, which implements stability metrics and network corridor selection using an R-B tree.
3.3.1 Stability with Threshold Metrics
The threshold calculation for stability is provided by Eq. (1).
Eq. (1) introduces the stability threshold metric, where (
Eq. (2) expands the implementation of Algorithm 1 by specifying threshold values for the stability metric. Each value corresponds to 0.33, 0.34, and 0.33 for each lambda. The weighting coefficients for these three values are 0.34, 0.33, and 0.33.
3.3.2 Network Corridor (NC) Selection
The value of NC will be greater than 1 due to the adoption of a multiple sending and receiving strategy. The calculation of NC is performed using the collaborative mode, as shown in Eqs. (3) and (4).
Eq. (3) describes the collaboration mode in LSTDA. In Eq. (4), Gs and NC represent the ground session and network corridor, respectively. Collaboration mode is achieved when the sender and receiver are within communication range. In collaborative mode, two or more nodes in LSTDA can form network corridors with multiple routing paths for communication.
Maximum channel utilization and the sorting of channels based on priority are calculated using Eq. (5).
Eq. (5) represents channel selection and sorting with the highest priority. In LSTDA, multiple channels are utilized by each UAV for different routing approaches. The division of the two network corridors is denoted as s/2, with the initial network corridor represented as NC1 [4].
3.3.4 Channel Utilization (CU)
The objective is to maximize channel utilization while maintaining a priority order. Eqs. (6) and (7) were utilized to calculate the process and transmission time, which are important factors in determining channel utilization.
The variables tt and tp represent the transmit time and process time, respectively. The LSTDA routing protocol aims to establish connections between UAVs for potential communication and utilize each node based on link stability. A fairness concept was introduced to accomplish this goal. Eqs. (8) and (9) describe Eq. (7), incorporating the processing, queuing, and probability time (f) of the LSTDA protocol.
They can be used to transmit data along a path with active link stability. Eq. (9) illustrates that the overall time (r) for the propagation and transmission of data can be represented by a value of 100. The equation also indicates the time it takes for data to travel from the sender to the receiver within a finite amount of time.
3.3.5 Selection of Relay UAV as an Access with NCs
Eqs. (10)–(12) are employed to calculate the NCs in LSTDA, where each NC represents a different transmission angle. These NCs are assigned to network corridors, which have been previously established for stable links. By multiplying each corridor with newly connected links, they can be extended further. Each corridor is denoted by the channel (C) and divided by s/2 to represent the concatenation of two links. Eq. (13) assumes that the designated NC is complete.
3.3.6 Prediction of Network Leaving (L) and Joining (J) Rate
Eqs. (14) and (15) are utilized to compute leaving and joining predictions for a network with multiple operating units. The leaving and joining rates are illustrated and calculated. Additionally, network probability factors are determined in Eqs. (16) and (17).
where
The PLJ will be described as a probability of L and J as follows:
The possibilities of leaving (L) and joining (J) in the network are given as follows with the change of time (∆t):
The leaving (L) and joining (J) rates in the network are predicted using Eqs. (14)–(17), and their corresponding probabilities are introduced. The time interval for node variation is represented by ∆t, and the link stability is characterized by the L and J rates of the network under the conditions of 0 and 1.
This section presents the simulation results for the LEPR, DPTR, DLSA, and LSTDA methodologies. The findings presented here are based on a limited number of simulations, with each measurement requiring data collection. Although E2ED, PDR, NLT, and TL were not directly compared or scaled, they serve as valuable indicators for exploring alternative process planning strategies. A plot was generated in MATLAB, with the simulation duration set to 1000 s, and the x and y axes representing the assessment indicators. The assessed indicators include:
• E2ED: The time it takes for a packet to travel from the sender to the receiver. This includes the time it takes for the packet to be transmitted and received. A shorter delay is preferable, and it is measured in seconds or milliseconds (ms).
• PDR: The percentage of data packets sent by the sender that are received by the destination, or the total number of sent and received packets.
• NL: The total duration of uninterrupted network operation despite unstable links or disconnected nodes. This can be measured by counting the number of disconnected nodes.
• TL: The decrease in signal strength as it propagates from one node to another. It is measured in decibels mill watt (dBm).
The evaluation criteria for the four routing mechanisms are presented below in both tabular and graphical formats.
4.1 Evaluation of End-to-End Delay (E2ED) (ms)
Fig. 3 shows the calculated LSTDA results at 1000 s for E2ED. The results were 2.533 for DLSA, 3.8 for DPTR, and 4.18 for LEPR. In comparison to the guaranteed LSTDA, the E2ED value was 1.384, which outperforms other routing approaches. As simulation time increased, the value of each protocol decreased in E2ED scenarios. However, the proposed protocol demonstrated a decrease in delay compared to others in all 1000 s. The primary reason for LSTDA’s superior performance over other protocols is its connection stability and the maximum channel utilization mechanism that utilizes all active nodes. This delay is indirectly related to the increased PDR in LSTDA, as the delay decreases.
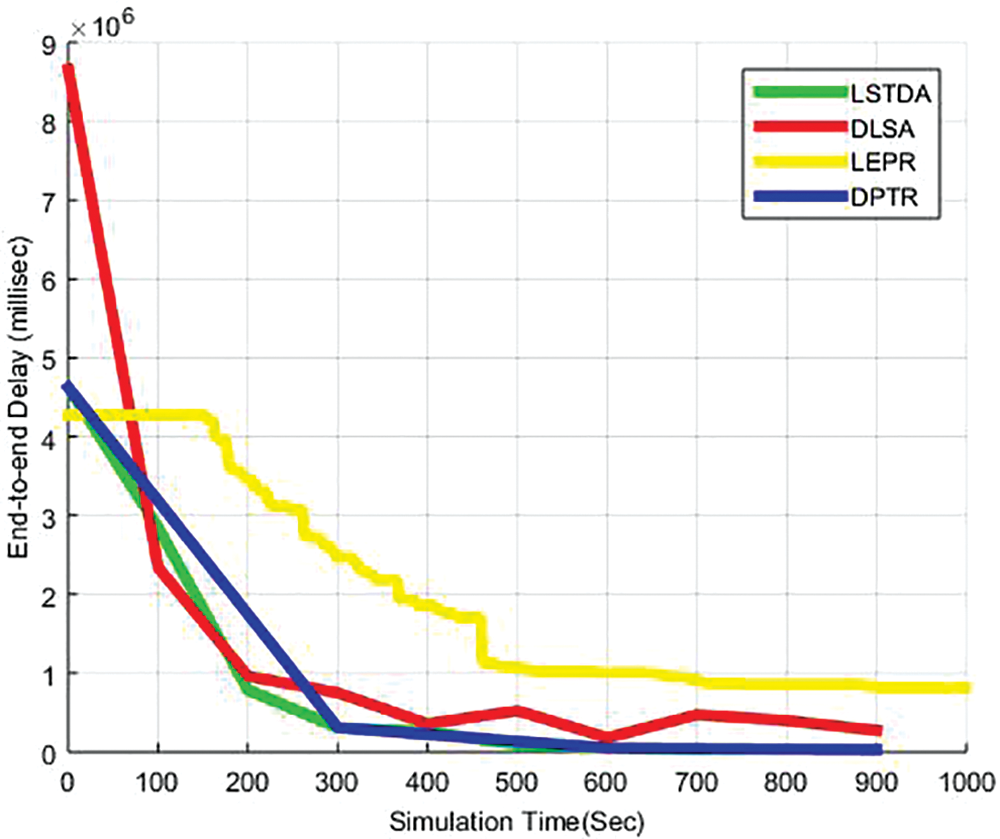
Figure 3: E2ED of LSTDA, DLSA, LEPR, and DPTR vs. simulation time
4.2 Evaluation of Packet Delivery Ratio (PDR) (%age)
In Fig. 4, the PDR values for LSTDA, DLSA, DPTR, and LEPR were determined. The estimated value for DLSA after 100 s was 2.66, while DPTR’s estimated value increased to 36.25 as the simulation progressed. The value for LEPR was 2.66, the same as LSTDA. Throughout all simulation scenarios, LSTDA consistently achieved the highest PDR value. Initially, DPTR had the best PDR performance, but over time, LSTDA gradually outperformed other protocols in terms of PDR. The key factor enabling LSTDA to achieve the best PDR was its optimal latency and PDR, as discussed in the previous section. This value had an influence on the PDR, which increased as the simulation time advanced. The PDR calculation for all protocols was based on the NC, which also considered channel utilization as an important factor. The NC determined the optimal path by prioritizing nodes with high priority and selecting nodes with shorter distances to efficiently transmit data. Various NCs, such as NC1, NC2, NC3, and NC/2, were introduced to calculate broken routing paths and transfer data through the best available routing path. When two nodes were connected, two NCs were required, with the sending node acting as NC1 and the receiving node as NC2. This task involved a large number of nodes, totaling 200, and NCs up to s/2 were introduced for session management. LSTDA consistently achieved the highest PDR value across all simulation runtimes. One crucial factor in achieving this result was the shorter delay in LSTDA compared to the previous section, which contributed to the increased PDR value. The utilization of NCs allowed for the calculation of optimal paths by prioritizing nodes and finding the best nodes with shorter distances for efficient data transmission. The decrease in protocol delay and the increase in PDR were indirectly related. Multiple NCs were introduced to calculate broken routing paths and transfer data through the best available routing path from NC1 to NC/2. When two UAVs were connected, two NCs were required, with the sending UAV acting as NC1 and the receiving UAV as NC2. This task involved a large number of nodes (200 nodes in total) with NCs up to s/2 for session management. The proposed protocol demonstrated higher PDR values due to its effective channel utilization and the use of NC priorities.
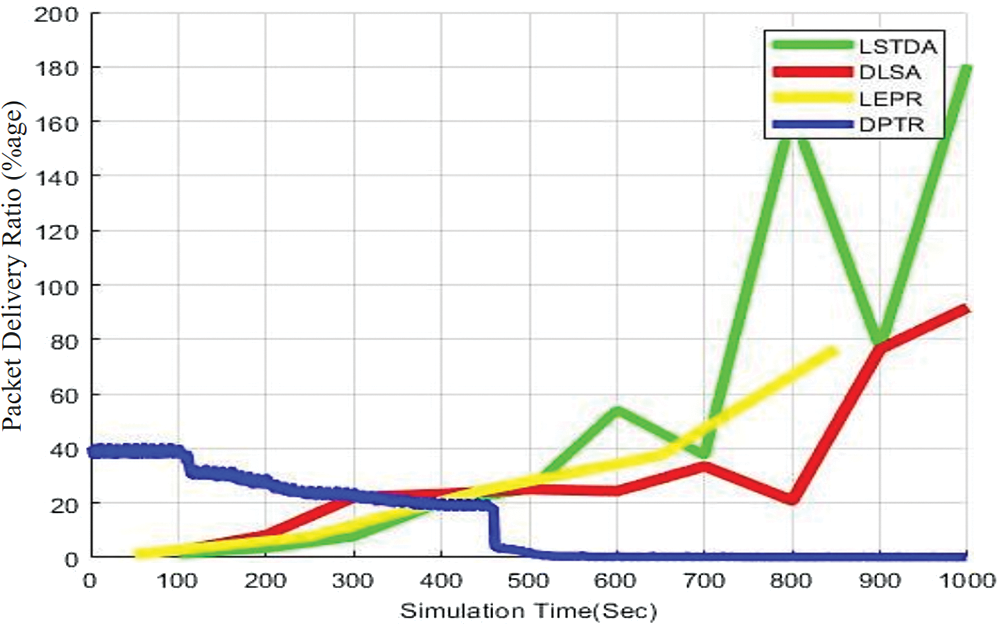
Figure 4: PDR of LSTDA, DLSA, LEPR, and DPTR vs. simulation time
4.3 Evaluation of Network Lifetime (NLT) (Sec)
Fig. 5 presents the NLT for various protocols, including LSTDA, DLSA, DPTR, and LEPR. The estimated values for DLSA, DPTR, and LEPR increased as the simulation time progressed. For instance, at 100 s, the estimated values for DLSA, DPTR, and LEPR were 2.68, 2.45, and 2.15, respectively. LSTDA achieved the highest NLT value of 4.09, surpassing all other simulation scenarios. During the simulation, DPTR, LEPR, and DLSA achieved NLT values of 1.84, 1.7, and 1.97, respectively, at 200 s. The proposed LSTDA achieved an NLT of 3.09 throughout the simulation. Furthermore, at 300 s, LSTDA achieved the highest NLT value of 2.39, indicating its superiority among all models. The NLT values for each protocol increased with simulation time, demonstrating that the proposed protocol achieved a higher NLT percentage throughout the entire 1000-s duration. The lower NLT values indicate that the network experienced minimal discontinuity and that all nodes had active transmission periods.
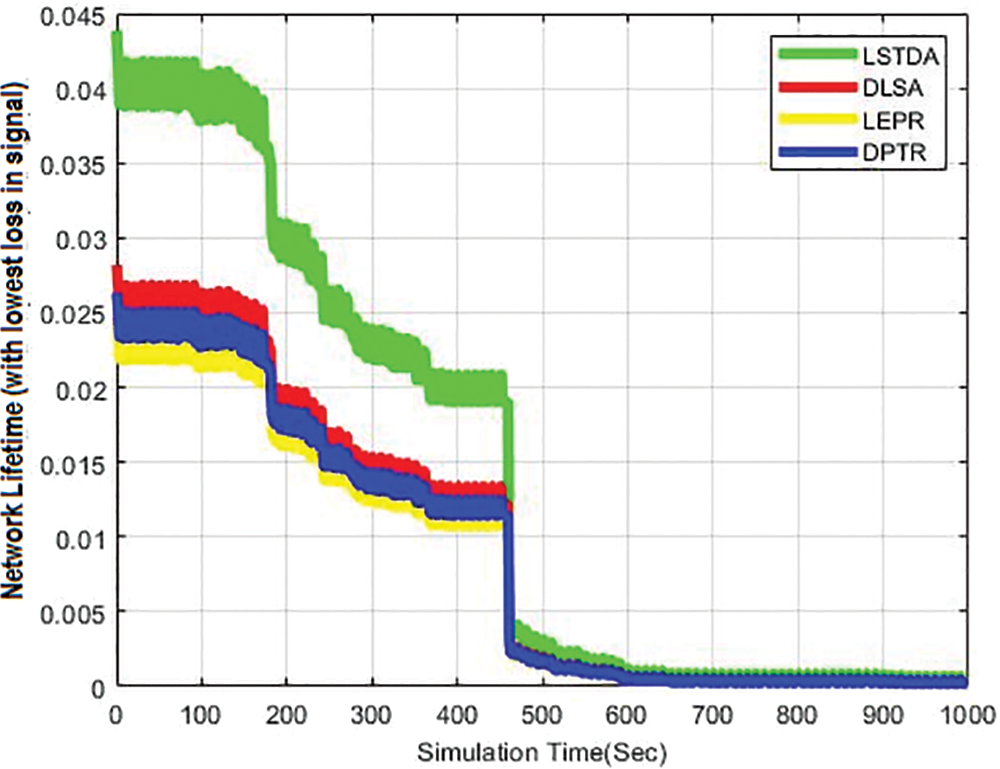
Figure 5: NLT of LSTDA, DLSA, LEPR, and DPTR vs. simulation time
4.4 Evaluation of Transmission Loss (TLs) (dBm)
Fig. 6 illustrates the TLs of LSTDA, DLSA, DPTR, and LEPR. The estimated TLs for DLSA, DPTR, and LEPR after 100 s were 1.494, 1.8, and 1.243, respectively, with an increase in simulation duration. LSTDA demonstrated the best dBm value among all scenarios. The TL of interest consisted of 10 slots over 1000 s, each divided into 100-s intervals. LSTDA exhibited the lowest TL value, indicating superior performance. The utilization of the R.B tree in LSTDA contributed to the reduction in TL by leveraging NC to identify nodes with the shortest distance within the communication range. LSTDA achieved the best TL, and the minimization of delay resulted in increased PDR and NLT. The TL for each protocol was estimated using NC, R.B tree, and CU, which calculated the optimal path and identified the best nodes with shorter distances for efficient data transmission. Multiple NCs, including NC1, NC2, NC3, and NC/2, were introduced to compute broken routing paths and transfer data through the most optimal routing path. When two UAVs were connected, two NCs were required. This task involved 200 nodes with NCs up to s/2, where sessions were presented.
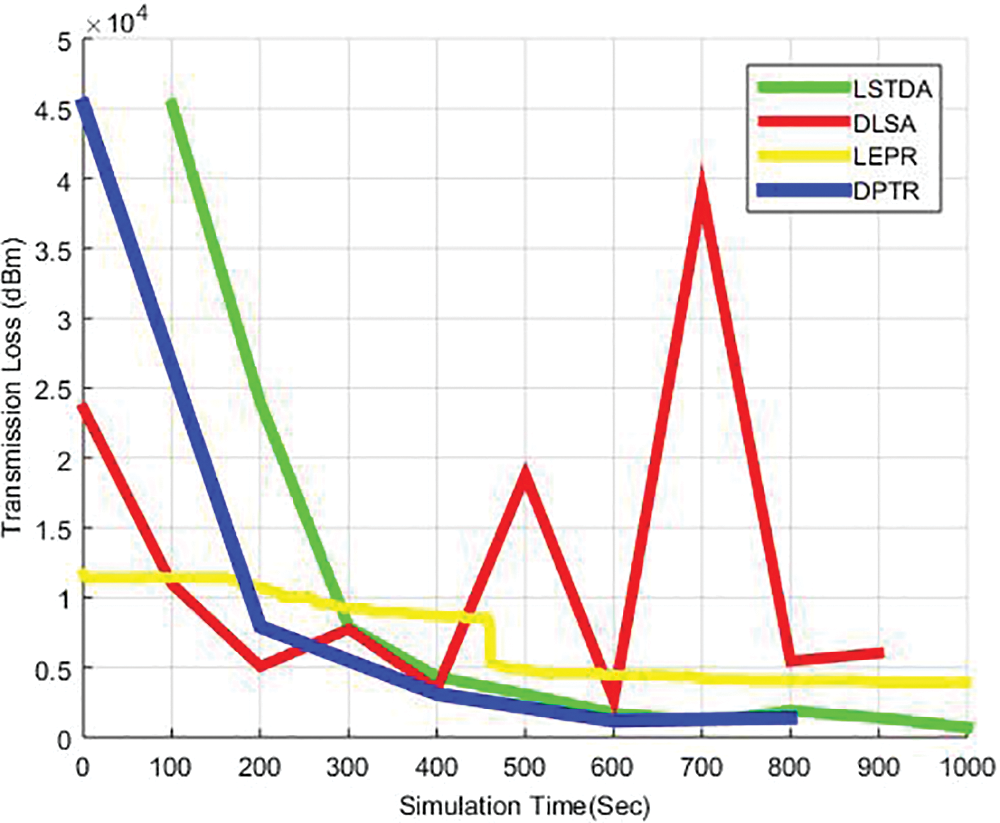
Figure 6: TL of LSTDA, DLSA, LEPR, and DPTR vs. simulation time
4.5 Results of LSTDA, DLSA, LEPR, and DPTR
This section presents the average values of four parameters (DPTR, LEPR, DLSA, and LSTDA) derived from Figs. 3–6. The performance of the LSTDA routing protocol is evaluated and compared to DPTR, LEPR, and DLSA protocols in FANET using E2ED, PDR, network lifetime, and transmission losses as evaluation parameters. The results are summarized in Table 2. The average latency for DPTR, LEPR, DLSA, and LSTDA is 0.6581, 1.3961, 0.7468, and 0.3393, respectively. Similarly, the mean PDR for DPTR, LEPR, DLSA, and LSTDA is 0.743, 0.65, 0.802, and 1.243, respectively. The mean NLT for DPTR, LEPR, DLSA, and LSTDA is 10.822, 24.252, 27.117, and 44.736, respectively. Lastly, the average TL for DPTR, LEPR, DLSA, and LSTDA is 0.4336, 0.6977, 0.9632, and 0.6719, respectively, based on the simulation results. Table 2 presents the mean values of PDR, E2E delay, network lifetime, and transmission losses for the four routing protocols: DPTR, LEPR, DLSA, and LSTDA. The table provides the evaluation parameters for each protocol along with their corresponding values. In Fig. 7a, individual charts display the average E2E delay values for each protocol, which are also compared to the overall average. Fig. 7b presents the average PDR values for each protocol, while Fig. 7c displays the average NLT values for DPTR, LEPR, DLSA, and LSTDA. Finally, Fig. 7d shows the average TL for each of the four protocols. Following the MATLAB simulation, the results of all scenarios were evaluated in relation to the proposed task. The assessment parameters were discussed and justified, leading to the conclusion that the mobility of drones significantly impacts routing in FANET due to variations in speed and distance. Mean values were compared between the proposed work and existing methods, including LEPR, DPTR, and DLSA. The proposed work prioritizes link stability, proper channel utilization, and network corridor priority. However, the protocol does not prioritize QoS or energy efficiency, which are limitations. Additionally, it does not fully address energy, QoS, localization, network partitioning, and node geographic scaling, among other factors.
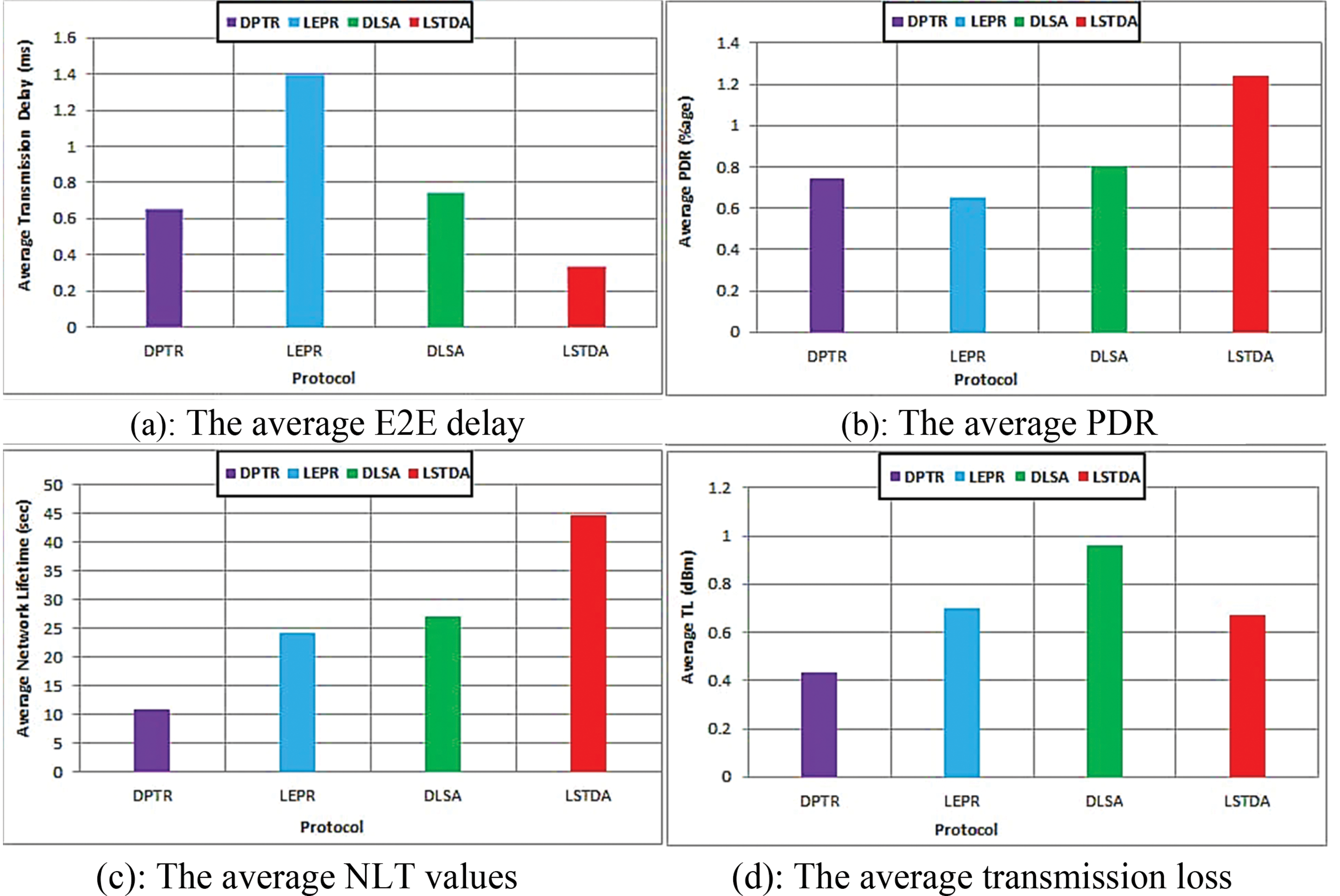
Figure 7: Average results evaluations of LSTDA vs. DLSA, LEPR, and DPTR
The study revealed that FANET is in its infancy and still requires routing approaches. Additionally, the proposed LSTDA routing protocol was introduced as a novel routing protocol for FANET. After conducting experimental analysis and discussions, it was suggested that the proposed protocol be performed efficiently. The core contributions and novelty of the proposed protocol lie in the network corridor and high-priority node selection. The advanced relay mechanism was introduced as a fair approach with the help of the R-B routing priority tree. This paper presents a novel routing mechanism called LSTDA for FANET, which is a hybrid protocol combining the existing LEPR, DPTR, and DLSA protocols. The focus of the proposed protocol is on link stability and maximum channel utilization in terms of NCs selection. The proposed protocol was evaluated based on transmission loss, network latency, packet forwarding speed, and network endurance. The results indicate that the proposed LSTDA achieved significantly better performance compared to other routing protocols in FANET. The average delay of DPTR, LEPR, and DLSA was calculated as 0.6581, 1.3961, and 0.7468, respectively, while LSTDA had an average delay of 0.3393. Similarly, the average PDR of DPTR, LEPR, and DLSA was calculated as 0.743, 0.65, and 0.802, respectively, whereas LSTDA had an average PDR of 1.243. The average network lifetime was evaluated as 10.822, 24.252, and 27.117 for DPTR, LEPR, and DLSA, respectively, while LSTDA had a network lifetime of 44.736. Lastly, the average transmission loss of DPTR, LEPR, and DLSA was calculated as 0.4336, 0.6977, and 0.9632, respectively, whereas LSTDA had an average transmission loss of 0.6719. These results demonstrate the improved performance of the proposed protocol compared to existing state-of-the-art protocols. The key factors contributing to this improvement are the priority given to NCs, maximum channel utilization, and threshold factors for link stability, which are not present in existing works.
The future of FANET is still in its infancy but holds promising potential for communication, especially between ground and aerial nodes. Various challenges have emerged in FANET, such as scalability, mobility, and energy concerns due to the reliance on battery power for the flying nodes. In the future, it would be beneficial to evaluate the LEPR, DPTR, DLSA, and LSTDA protocols across different evaluation boundaries and portability models of FANET, including arbitrary waypoints. Other factors like jitter, road dissatisfaction, network duration, and power consumption should also be considered. FANET faces numerous challenges, including QoS, security, suitable platforms for drones, adaptability, and drone mobility. These challenges require robust mechanisms and solutions. This research work specifically focuses on link stability, NCs, channel utilization, and priority-based selection, rather than incorporating 5G or 6G implementations. Additionally, the study introduces metric threshold values, while other factors like energy, localization, and QoS are not addressed in this work.
This study investigated the current state of FANET and its need for efficient routing approaches. The proposed LSTDA routing protocol was introduced as a novel solution to address this need. Through experimental analysis and discussion, it was found that the proposed protocol performs efficiently, with core contributions and novelty achieved through network corridor and high-priority node selection. Additionally, an advanced relay mechanism was introduced using the R-B routing priority tree. The proposed hybrid protocol combines the existing LEPR, DPTR, and DLSA protocols and focuses on link stability and maximum channel utilization when selecting network corridors. The results of the study demonstrated that the proposed LSTDA protocol outperformed other state-of-the-art routing protocols in FANET, achieving a TL of 0.6719, a network latency of 0.3393, a packet forwarding speed of 1.243, and a network endurance of 44.736. These findings highlight the potential of the proposed LSTDA routing protocol as a more efficient and effective solution for routing in FANET. Further research and development in this area can enhance the performance and reliability of FANET, enabling its application in various fields.
The future development of FANET is confronted with several challenges, including scalability, mobility, and energy concerns arising from the reliance on batteries. Protocols such as LEPR, DPTR, DLSA, and LSTDA can be evaluated across different boundaries and portability models to address these issues, considering factors like jitter, road dissatisfaction, network strength duration, and absolute power consumption. Moreover, challenges related to QoS, security, adaptability, drone mobility, and finding suitable platforms for drones need to be addressed with robust mechanisms.
Acknowledgement: We thank all the authors for their research contributions.
Funding Statement: This work was supported in part by the Office of Research and Sponsored Programs, Kean University, the RIF Activity Code 23009 of Zayed University, UAE, and the National Natural Science Foundation of China under Grant 62172366.
Author Contributions: Conceptualization, methodology, and draft manuscript preparation: F. A, K. Z, D. K; data collection, visualization, and analysis: B. S, T. H, H. U, and A. H. All authors reviewed the results and approved the final version of the manuscript.
Availability of Data and Materials: This study used an open-source dataset.
Conflicts of Interest: The authors declare that they have no conflicts of interest to report regarding the present study.
References
1. J. Shen, H. W. Tan, J. Wang, J. W. Wang and S. Y. Lee, “A novel routing protocol providing good transmission reliability in underwater sensor networks,” Journal of Internet Technology, vol. 16, no. 1, pp. 171–178, 2015. [Google Scholar]
2. R. W. Coutinho, A. Boukerche, L. F. Vieira and A. A. Loureiro, “Design guidelines for opportunistic routing in underwater networks,” IEEE Communications Magazine, vol. 54, no. 2, pp. 40–48, 2016. https://doi.org/10.1109/MCOM.2016.7402259 [Google Scholar] [CrossRef]
3. K. Wang, Y. Z. Tian and Y. H. Shi, “Energy balanced pressure routing protocol for underwater sensor networks,” in 2016 Int. Computer Symp. (ICS), Chiayi, Taiwan, pp. 216–220, 2016. [Google Scholar]
4. T. Hussain, B. Yang, H. U. Rahman, A. Iqbal, F. Ali et al., “Improving Source location privacy in social Internet of Things using a hybrid phantom routing technique,” Computers & Security, vol. 123, pp. 102917, 2022. [Google Scholar]
5. G. Tuna and V. C. Gungor, “A survey on deployment techniques, localization algorithms, and research challenges for underwater acoustic sensor networks,” International Journal of Communication Systems, vol. 30, no. 17, pp. 3350, 2017. [Google Scholar]
6. A. Khan, I. Ali, A. U. Rahman, M. Imran and H. Mahmood, “Co-EEORS: Cooperative energy efficient optimal relay selection protocol for underwater wireless sensor networks,” IEEE Access, vol. 6, pp. 28777–28789, 2018. [Google Scholar]
7. M. Khalid, Z. Ullah, N. Ahmad, H. Khan, H. S. Cruickshank et al., “A comparative simulation based analysis of location based routing protocols in underwater wireless sensor networks,” in 2017 2nd Workshop on Recent Trends in Telecommunications Research (RTTR), Palmerstone North, New Zealand, pp. 1–5, 2017. [Google Scholar]
8. M. Khalid, Z. Ullah, N. Ahmad, A. Adnan, W. Khalid et al., “Comparison of localization free routing protocols in underwater wireless sensor networks,” International Journal of Advanced Computer Science and Applications, vol. 8, no. 3, pp. 408–414, 2017. [Google Scholar]
9. X. Du, M. Li and K. Li, “Reliable transmission protocol for underwater acoustic networks,” In: K. Daimi (Ed.Computer and Network Security Essentials. Cham: Springer, pp. 173–187, 2018. [Google Scholar]
10. N. Javaid, Z. Ahmad, A. Sher, Z. Wadud, Z. A. Khan et al., “Fair energy management with void hole avoidance in intelligent heterogeneous underwater WSNs,” Journal of Ambient Intelligence and Humanized Computing, vol. 10, pp. 4225–4241, 2019. [Google Scholar]
11. F. Ahmed, Z. Wadud, N. Javaid, N. Alrajeh, M. S. Alabed et al., “Mobile sinks assisted geographic and opportunistic routing based interference avoidance for underwater wireless sensor network,” Sensors, vol. 18, no. 4, pp. 1062, 2018. [Google Scholar] [PubMed]
12. Y. H. Xu, X. Liu, W. Zhou and G. Yu, “Generative adversarial LSTM networks learning for resource allocation in UAV-served M2M communications,” IEEE Wireless Communications Letters, vol. 10, no. 7, pp. 1601–1605, 2021. [Google Scholar]
13. S. Jabbar, M. Asif Habib, A. A. Minhas, M. Ahmad, R. Ashraf et al., “Analysis of factors affecting energy aware routing in wireless sensor network,” Wireless Communications and Mobile Computing, vol. 2018, pp. 1–21, 2018. [Google Scholar]
14. Q. Liu, X. Chen, X. Liu and N. Linge, “CACA-UAN: A context-aware communication approach to efficient and reliable underwater acoustic sensor networks,” International Journal of Sensor Networks, vol. 26, no. 1, pp. 1–11, 2018. [Google Scholar]
15. A. Hussain, T. Hussain, F. Faisal, I. Ali, I. Khalil et al., “DLSA: Delay and link stability aware routing protocol for flying Ad-hoc Networks (FANETs),” Wireless Personal Communications, vol. 121, no. 4, pp. 2609–2634, 2021. [Google Scholar]
16. Z. Kaleem, A. Ahmad, O. Chughtai and J. J. P. C. Rodrigues, “Enhanced max-min rate of users in UAV-assisted emergency networks using reinforcement learning,” IEEE Networking Letters, vol. 4, no. 3, pp. 104–107, 2022. [Google Scholar]
17. Z. Kaleem, W. Khalid, A. Muqaibel, A. A. Nasir, C. Yuen et al., “Learning-aided UAV 3D placement and power allocation for sum-capacity enhancement under varying altitudes,” IEEE Communications Letters, vol. 26, no. 7, pp. 1633–1637, 2022. [Google Scholar]
18. A. Nayyar, “Flying adhoc network (FANETsSimulation based performance comparison of routing protocols: AODV, DSDV, DSR, OLSR, AOMDV and HWMP,” in 2018 Int. Conf. on Advances in Big Data, Computing and Data Communication Systems (icABCD), Durban, South Africa, IEEE, pp. 1–9, 2018. [Google Scholar]
19. A. M. Morshed and S. Moh, “Survey on Q-learning-based position-aware routing protocols in flying Ad-hoc networks,” Electronics, vol. 11, no. 7, pp. 1099, 2022. [Google Scholar]
20. M. Atul and S. Kaur, “A comprehensive review on recent advancements in routing protocols for flying ad hoc networks,” Transactions on Emerging Telecommunications Technologies, vol. 33, no. 3, pp. 3688, 2022. [Google Scholar]
21. J. V. Ananthi and P. S. H. Jose, “A review on various routing protocol designing features for flying Ad-hoc networks,” In: S. Shakya, R. Bestak, R. Palanisamy, K. A. Kamel (Eds.Mobile Computing and Sustainable Informatics. Lecture Notes on Data Engineering and Communications Technologies, vol. 68. pp. 23, Singapore: Springer, 2022. [Google Scholar]
22. A. M. Rahmani, S. Ali, E. Yousefpoor, M. S. Yousefpoor, D. Javaheri et al., “OLSR+: A new routing method based on fuzzy logic in flying Ad-hoc Networks (FANETs),” Vehicular Communications, vol. 36, pp. 100489, 2022. [Google Scholar]
23. K. Y. Tsao, T. Girdler and V. G. Vassilakis, “A survey of cyber security threats and solutions for UAV communications and flying ad-hoc networks,” Ad Hoc Networks, vol. 133, no. 3, pp. 102894, 2022. [Google Scholar]
24. S. K. Maakar, M. Khurana, C. Chakraborty, D. Sinwar and D. Srivastava, “Performance evaluation of AODV and DSR routing protocols for flying ad hoc network using highway mobility model,” Journal of Circuits, Systems and Computers, vol. 31, no. 1, pp. 2250008, 2022. [Google Scholar]
25. M. F. Khan, A. Y. Kok-Lim, M. H. Ling, M. A. Imran and Y. W. Chong, “An intelligent cluster-based routing scheme in 5G flying ad hoc networks,” Applied Sciences, vol. 12, pp. 3665, 2022. [Google Scholar]
26. V. Gupta and S. Dambarudhar, “Design issues for developing routing protocols for flying ad hoc network,” in Multimedia Technologies in the Internet of Things Environment, 1st ed., vol. 3. Singapore: Springer, pp. 135–145, 2022. [Google Scholar]
27. A. H. Wheeb, “Flying Ad hoc networks (FANETPerformance evaluation of topology based routing protocols,” International Journal of Interactive and Mobile Technologies, vol. 16, no. 4, pp. 137–149, 2022. [Google Scholar]
28. A. Hussain, B. Shah, T. Hussain, F. Ali and D. Kwak, “Co-DLSA: Cooperative delay and link stability aware with relay strategy routing protocol for flying ad-hoc network,” Human-Centric Computing and Information Sciences, vol. 12, pp. 1– 20, 2022. [Google Scholar]
29. Y. H. Xu, Q. M. Sun, W. Zhou and G. Yu, “Resource allocation for UAV-aided energy harvesting-powered D2D communications: A reinforcement learning-based scheme,” Ad Hoc Networks, vol. 136, pp. 102973, 2022. [Google Scholar]
30. Y. H. Xu, W. Zhou, Y. G. Zhang and G. Yu, “Stochastic game for resource management in cellular zero-touch deterministic industrial M2M networks,” IEEE Wireless Communications Letters, vol. 11, pp. 2635–2639, 2022. [Google Scholar]
31. Y. H. Xu, Y. B. Tian, P. K. Searyoh, G. Yu and Y. T. Yong, “Deep reinforcement learning-based resource allocation strategy for energy harvesting-powered cognitive machine-to-machine networks,” Computer Communications, vol. 160, pp. 706–717, 2020. [Google Scholar]
32. Y. H. Xu, J. H. Li, W. Zhou and C. Chen, “Learning-empowered resource allocation for air slicing in UAV-assisted cellular V2X communications,” IEEE Systems Journal, vol. 17, no. 1, pp. 1008–1011, 2023. [Google Scholar]
33. V. Sharma, R. Kumar and N. Kumar, “DPTR: Distributed priority tree-based routing protocol for FANETs,” Computer Communications, vol. 122, pp. 129–151, 2018. [Google Scholar]
34. X. Li and J. Yan, “LEPR: Link stability estimation-based preemptive routing protocol for flying Ad hoc networks,” in 2017 IEEE Symp. on Computers and Communications (ISCC), Heraklion, Greece, pp. 1079–1084, 2017. [Google Scholar]
35. K. Anish Pon Yamini, K. Suthendran, T. Arivoli and V. Ravi, “New approach for advanced energy efficiency in MANET (AEE-M) by improving optimized link state routing protocol version 2 (OLSRv2),” Wireless Personal Communications, vol. 125, pp. 2369–2392, 2022. [Google Scholar]
36. D. S. Nayagi, G. Sivasankari, V. Ravi, K. Venugopal and S. Sankar, “Fault tolerance aware workload resource management technique for real-time workload in heterogeneous computing environment,” Transactions on Emerging Telecommunications Technologies, vol. 34, no. 3, pp. e4703, 2023. [Google Scholar]
37. D. S. Nayagi, G. G. Sivasankari, V. Ravi, K. R. Venugopal and S. Sennan, “REERS: Reliable and energy-efficient route selection algorithm for heterogeneous Internet of Things applications,” International Journal of Communication Systems, vol. 34, pp. e4900, 2021. [Google Scholar]
Cite This Article
 Copyright © 2023 The Author(s). Published by Tech Science Press.
Copyright © 2023 The Author(s). Published by Tech Science Press.This work is licensed under a Creative Commons Attribution 4.0 International License , which permits unrestricted use, distribution, and reproduction in any medium, provided the original work is properly cited.


 Submit a Paper
Submit a Paper Propose a Special lssue
Propose a Special lssue View Full Text
View Full Text Download PDF
Download PDF
 Downloads
Downloads
 Citation Tools
Citation Tools