 Open Access
Open Access
ARTICLE
A Text Image Watermarking Algorithm Based on Image Enhancement
1 School of Computer, Nanjing University of Information Science and Technology, Collaborative Innovation Center of Jiangsu Atmospheric Environment and Equipment Technology, Digital Forensics Engineering Research Center of Digital Forensics Ministry of Education, Nanjing, 210044, China
2 School of Software, Nanjing University of Information Science and Technology, Nanjing, 210044, China
* Corresponding Author: Baowei Wang. Email:
Computers, Materials & Continua 2023, 77(1), 1183-1207. https://doi.org/10.32604/cmc.2023.040307
Received 13 March 2023; Accepted 05 June 2023; Issue published 31 October 2023
Abstract
Digital watermarking technology is adequate for copyright protection and content authentication. There needs to be more research on the watermarking algorithm after printing and scanning. Aiming at the problem that existing anti-print scanning text image watermarking algorithms cannot take into account the invisibility and robustness of the watermark, an anti-print scanning watermarking algorithm suitable for text images is proposed. This algorithm first performs a series of image enhancement preprocessing operations on the printed scanned image to eliminate the interference of incorrect bit information on watermark embedding and then uses a combination of Discrete Wavelet Transform (DWT)-Singular Value Decomposition (SVD) to embed the watermark. Experiments show that the average Normalized Correlation (NC) of the watermark extracted by this algorithm against attacks such as Joint Photographic Experts Group (JPEG) compression, JPEG2000 compression, and print scanning is above 0.93. Especially, the average NC of the watermark extracted after print scanning attacks is greater than 0.964, and the average Bit Error Ratio (BER) is 5.15%. This indicates that this algorithm has strong resistance to various attacks and print scanning attacks and can better take into account the invisibility of the watermark.Keywords
Digital watermarking technology directly embeds copyright information into the data, achieving the invisibility and security of the data, thus completing the goal of protecting copyright. Digital watermarking technology can be divided into two categories: spatial domain and frequency domain. Spatial domain watermarking is a modification based on pixel position. Watermarking technology based on frequency domain embeds watermark information into corresponding the frequency coefficients through frequency domain transformation [1]. This technology has better concealment and robustness. With the development of e-commerce, the dissemination and development of text images are becoming faster and faster.
Printing and scanning are important ways to disseminate text images [2] and are common ways to leak and misappropriate text image information. Text image watermarking technology hides copyright information in text images. It provides an effective solution for text image copyright authentication [3] by extracting the watermark to verify the copyright when there is a copyright conflict. Digital watermarking text images resistant to printing and scanning [4] effectively solves text information security. The watermarking system should meet the requirements of both invisibility and robustness. Still, these two are contradictory and required to withstand printing and scanning operations [5], significantly challenging text image watermarking algorithms [6]. Images will encounter various attacks during the printing and scanning, and the pixel information of images will be lost to different degrees. The general digital watermarking algorithm is difficult to resist the print-scan attack well. It cannot guarantee that the watermark can be extracted successfully after the print scan. Therefore, designing a text image watermarking algorithm that can better resist print scanning attacks is necessary to achieve secure and reliable copyright protection for text images.
Researchers have proposed various text image watermarking methods. However, the robustness of the watermark against print scanning attacks still needs to be improved, which hinders the application of text image watermarking against print scanning attacks in practical scenarios. Text images have a single pixel value and few redundant data, making embedding watermarks in text images more difficult than in other carriers. The complexity of the print scanning process, which includes multiple attacks, poses a significant challenge to watermarking research against print scanning attacks. By studying existing text image watermarking techniques that resist print scanning attacks and aiming at the problems existing in existing processes, this paper proposes a new text image watermarking algorithm that improves the robustness of the watermark against print scanning attacks while ensuring that the watermark is visually invisible, enhancing the practical value of the technology.
In recent years, deep learning has developed very rapidly. Some researchers use the powerful feature processing and inductive bias capabilities of deep understanding to perform classification tasks [7,8]. Subsequently, deep learning was incorporated into watermarks, using neural networks instead of manual methods to embed secret information [9,10]. Keskinarkaus et al. [11] introduced a noise layer to achieve robustness in watermark images and used attack simulation for adversarial training, achieving good robustness and imperceptibility. Jia et al. [10] proposed a method of mixing simulated JPEG and real JPEG into the noise layer to attack JPEG noise so that the encoded image can achieve high robustness to JPEG compression. The current deep learning-based methods are adaptable and can train different specific codecs based on input noise. However, the learning-based watermarking method is not highly targeted and cannot provide high-precision feedback on certain types of noise. Therefore, manual algorithm design is more advantageous for anti-print scanning noise.
In this paper, we propose an image enhancement and DWT-SVD-based anti-print-scan watermarking algorithm, which has good anti-print-scan properties, invisibility, and robustness. The algorithm in this paper mainly solves the problem that existing algorithms cannot guarantee the invisibility of watermarks based on anti-print-scan. The innovative work in this paper is as follows.
1. For text images, firstly, pre-processing operations are performed for image segmentation, binarization, removal of some independent noise generated during printing and scanning, etc. The threshold segmentation operation and binarization operation reduce the computation of the subsequent pre-processing process, the removal of independent noise and interference line operation reduce the interference to the experiment by eliminating some invalid bit information, and enhance the visual effect of the watermark embedding to find The watermark embedding procedure minimizes the interference of the investigation by removing some weak bits of information.
2. The singular values of the watermark image and the original image are algebraically and arithmetically for the watermark embedding part. The embedding is performed with different embedding strengths for additional text images to have better embedding effects.
This article is divided into five sections in total, and the summary content of each section is as follows:
Section 1: This section discusses the background and significance of anti-print scanning text image watermarking research, summarizes the current research status and problems of text image watermarking technology, and proposes targeted solutions to these problems.
Section 2: Introduce the development status of transform domain text image watermarking algorithms at home and abroad.
Section 3: Introduce the specific steps of image enhancement processing and the watermark embedding and extraction scheme.
Section 4: Introduce evaluation indicators and conduct some common attack tests.
Section 5: Summary and Outlook. Summarize the full text of the work, pointing out the highlights and shortcomings of the research work and subsequent improvement plans.
This paper is about the transform domain anti-print-scan watermarking algorithm. The development status of the anti-print-scan watermarking algorithm is as follows.
Keskinarkaus et al. [11] proposed a blind method to embed multibit watermarks in images, robust to various geometry attacks and print-scan processes. A message sequence was mapped to a directional angle of a periodic pattern, which was then embedded into image blocks. But the watermark capacity was low, and the embedding strength needed to be continuously adjusted. Huang et al. [12] proposed a high-capacity text image watermarking technique against printing and scanning processes. Firstly, this method was based on the print-scan invariant. The Fourier descriptor flipped the trivial pixel points with high-frequency information on the character boundary. Next, a quadratic quantization function was proposed to embed watermark information of multiple bits for a single character. Finally, the Quick Response (QR) code, which had a significant information capacity, robust error correction ability, and high decoding reliability, was researched. By using the QR code as the watermark information, we can reduce the impact of the bit error rate during watermark extraction, and the robustness of the watermark information can be improved. But the Peak Signal to Noise Ratio (PSNR) was at most 30. Han et al. [13] proposed a digital watermarking algorithm that combines discrete wavelet transform and singular value decomposition. First, the low-frequency subgraphs of DWT were decomposed into SVDs, and then the watermark sequence was embedded into distinct values. Experiments showed that the algorithm was robust to printing scanning, could determine whether there was a second copy, and could meet the requirements of printing anti-counterfeiting. However, the watermark embedding strength of this method was meagre, which was 0.1 and 0.2. Tan et al. [6] proposed a new text image watermarking scheme based on contour features for printing and scanning processes. It adopted a mathematical multiplication transformation model to approximate geometric invariant features that could withstand various attacks during the printing scanning process, thus serving as reference points for watermark embedding and extraction. The experimental results showed that this method is more comprehensive than specific languages and had better robustness, watermark transparency, and hiding ability than existing methods. But the computational workload was large, and there was a significant computational cost. Wang et al. [14] proposed an algorithm based on the principle of colour space transformation. Firstly, the Neugebauer model separated the spot colour channels from the original image. Then the Integer Wavelet Transform (IWT) algorithm was used to transform the spot colour channels of the picture. The watermark was embedded in the singular values of the first level IWT decomposition subband. Using the Arnold algorithm and encryption technology to enhance the algorithm’s security, a series of experiments showed that the algorithm could effectively resist spot colour distortion attacks during the printing and scanning process and had good imperceptibility. However, the robustness of the algorithm needed to be improved, and it cannot balance imperceptibility and robustness well. Cu et al. [15] proposed a watermarking algorithm based on fully convolutional networks for handwritten documents. This algorithm first preprocessed handwritten documents by replacing the average value of document content with a high-intensity grayscale value. Then, the document was converted into a standard form to minimize geometric distortion. Next, the complete convolutional network (FCN) was used to detect the document watermark used to hide secret information. The FCN method used for document layout segmentation was adjusted to solve the problem of watermark area detection. Finally, the data-hiding process was performed by dividing the grey value of each connected object within the watermark area into two groups, To carry a watermark bit. This algorithm had been tested on various handwritten documents. It achieved high performance in imperceptibility and robustness to distortion caused by JPEG compression, geometric transformations, and printing and scanning processes. But this algorithm required many datasets to train the model and cannot resist complex attacks. Zhao et al. [16] proposed an elastic watermarking algorithm that combined stable local feature regions and DWT-SVD. The algorithm was mainly divided into two parts. The first part was constructing local feature regions, and the second was embedding watermark information repeatedly. The experimental results showed that the algorithm had achieved good results in resisting conventional attacks, printing, and scanning. Still, the watermark extracted by the algorithm had poor imperceptibility, and there was much noise and distortion. Ahmad et al. [17] proposed an algorithm for printed images based on perceptual image hashing, Wave Atomic Transform (WAT), and watermarking technology. The authenticity and copyright of printed images should be verified through image hashing and digital watermarking techniques, which were resilient to distortion during the printing and scanning process. This algorithm cannot balance robustness and differentiation strength well, and it was computationally cumbersome and had a significant time cost.
Wang et al. [18] proposed a fusion font-based anti-printing and scanning watermarking algorithm, mainly using a Generative Adversarial Network (GAN) to fuse multiple fonts to encode and replace the original fonts in the file to achieve the embedding of watermark information. In addition to resisting printing and scanning attacks, the watermark had a good capacity but could not balance robustness with invisibility of the watermark. Mu et al. [19] proposed an algorithm to determine the digital watermark embedding environment, using Discrete Cosine Transform (DCT) and SVD algorithms to embed the extracted image several times in different settings to determine the best embedding environment. The test results have a peak signal-to-noise ratio greater than 30 and a normalization factor greater than 0.8. Chen et al. [20] proposed an algorithm to embed a blind watermark into a print image that can be detected by a neural network, to achieve an anti-counterfeit watermark. Compared with other common watermarking, the algorithm had a good watermark display effect compared with other standard watermarking methods, but the algorithm’s robustness needed to be improved.
As can be seen from the above literature, the existing anti-print scanning watermarking algorithms can resist specific print scanning attacks. Still, they cannot consider the invisibility and anti-attack capabilities of the watermark. Moreover, some algorithms, such as the zero-watermark algorithm and the algorithm based on print scanning invariant, have a large amount of computation, high computational cost, a long training time of the algorithm model based on neural networks, poor timeliness, etc. So how to enhance the invisibility of watermarks while resisting print scanning attacks, further enhance watermark capacity, reduce computational costs, and improve timeliness has become an urgent problem to be solved.
The spatial domain watermarking algorithm modifies the image’s pixel value while embedding the watermark, quickly leading to image distortion and low robustness. Text images subjected to various attacks cause pixel values to change while the watermark changes. Therefore, this paper adopts a transform domain watermarking algorithm. The LL component after DWT transformation has good robustness, and the SVD algorithm [21] has structural stability and rotational invariance, making the algorithm better resistant to print scanning attacks while improving the invisibility of the watermark.
An image is a matrix (colour images are multiple matrices), with the number of rows and columns of the matrix representing the image size and the matrix elements representing the image pixel values. The image is transformed through DWT to obtain approximate and detailed matters of the original information. The image is decomposed into four parts: high-frequency subband HH1, intermediate subband LH1, intermediate subband HL1, and low-frequency subband LL1. The decomposed high frequency subbands represent the image’s details, edges, and texture features, and the human eye is not sensitive to this part. Embedding watermarks in this part can achieve sound-hiding effects, but high-frequency components are challenging to resist noise and image processing pollution and need to be more robust. Therefore, most of the feature information contained in the image is concentrated in the low frequency subband. Embedding a watermark in this section can resist the most common image noise interference and has good robustness. The DWT transformation diagram is shown in Fig. 1.
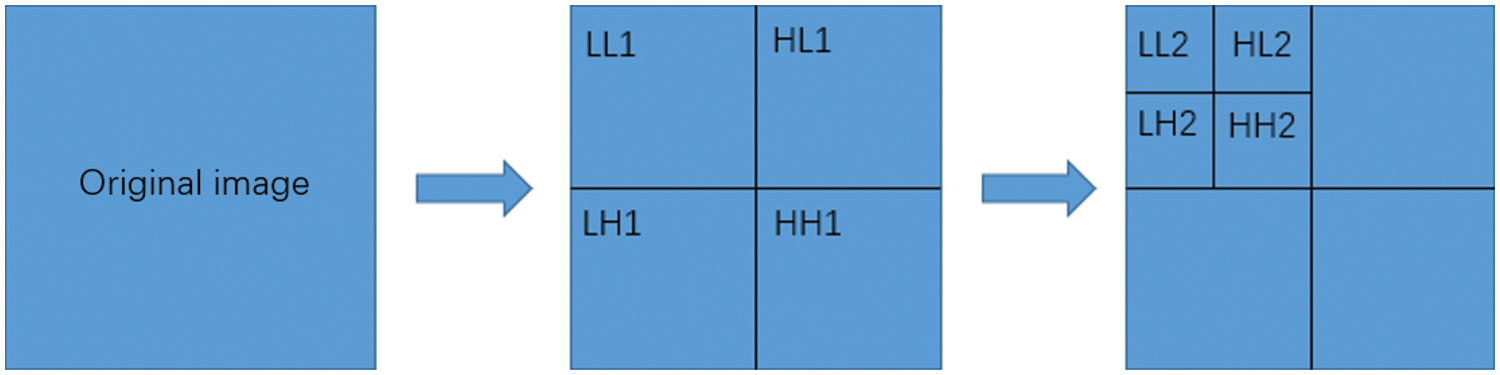
Figure 1: The DWT transformation diagram
Image quality in the printing and scanning process affects more factors, not only involves the printer scanner machine performance and parameters. At the same time, some human operations will also have a more significant impact on image quality. The printing and scanning process, including the image from continuous tone to halftone conversion process, also includes a series of non-digital transformation processes. The printing and scanning may lead to severe image distortion, and the watermark information can also cause damage. Although the image scanned by printing is visually similar to the original, its internal image quality and pixel values are severely damaged. The anti-print-scan digital watermark must further improve the robustness and stability of the print-scan process. By analyzing the transformation of the image before and after it is subjected to print scanning, the most suitable location for embedding the watermark is found to prevent severe damage to the watermark information [22].
Singular Value Decomposition (SVD) [21], a tool of linear algebra, is used to decompose orthogonal matrices. Assuming the matrix
where U is
SVD has been widely used in signal processing. From the perspective of image processing, on the one hand, the singular value matrix of the image has good stability. When little interference is applied to the image, the unique values generally do not change significantly; On the other hand, the singular value matrix represents the image’s intrinsic characteristics. The image’s visual effect does not change significantly when the distinct value changes. Therefore, embedding watermark information in the singular values of images can achieve strong robustness and solve the problem of wavelet transform being difficult to resist geometric attacks. Combining the two can meet the requirements of invisibility and improve the watermark’s robustness.
The image will be converted from a digital signal to an analogue signal in printing. In the conversion process, the loss of vision is inevitable; on the other hand, because the image is printed on paper, and the paper is through the ink dot to present the image information, the size of the ink dot can be used to replace the image of the hierarchy. Halftone images can cause drastic changes in the local details of the image, which is mainly reflected in the high-frequency information, and the change in the thickness of the ink dots will blur the performance of the complex areas of the texture, thus affecting the image’s visual quality and pixel values. Therefore, this article utilizes a series of image enhancement processing to eliminate the impact of print scanning on copyright verification of text images as much as possible. The specific implementation scheme is as follows.
3.1 Image Enhancement Processing
This paper carries out a series of preprocessing operations on the image, such as threshold segmentation, binary processing, removing independent noise points, and removing edge interference lines. The specific process is as follows:
(1) Threshold segmentation: find an appropriate grey level by calculating variance to divide the image’s foreground and background image. Because variance is a measure of the uniformity of grey distribution, the more significant the between-class variance between the background and foreground, the more influential the difference between the two parts of the image. In the images used in the experiment, the text and background occupy different grey levels, and a small number of images are disturbed by external light. Then we use variance calculation to obtain a dynamic threshold for segmentation. However, threshold segmentation can compress a large amount of data and put it first in the preprocessing process. After threshold segmentation, the amount of calculation can be reduced for the subsequent preprocessing process.
(2) Binarization can convert grey ideas into binary images. Set the grey pixel level more significant than a particular critical grey value as the maximum grey level and set the grey pixel level less than this value as the minimum grey level to realize binarization. Binarization converts the grey image into a binary image, simplifies the image data, reduces the amount of data, and further reduces the computational complexity of the picture.
(3) Remove independent noise: Removing some independent noise generated during printing and scanning determines whether more than 2 pixels are white at a pixel’s top, bottom, left and right positions. If so, set its pixel value to 0.
(4) Remove edge interference lines: Some interference lines will be removed after printing and scanning the text image’s edge. The images used were analyzed before the experiment. Most examples show that there are still many invalid pixel points in the space of the image in general. Therefore, we add the noise reduction operation in the preprocessing process, judge whether the centre pixel point is an invalid pixel point through the edge pixel, and then eliminate the invalid bit information in the image to reduce the interference to the experiment. At the same time, it improves the visual effect after watermark embedding.
The whole flow chart of pretreatment is shown in Fig. 2.
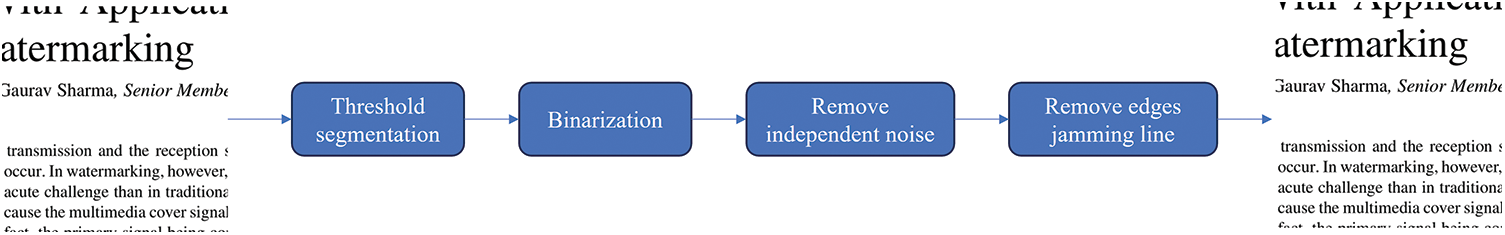
Figure 2: Pretreatment flow chart
The enhanced text image after text image preprocessing is shown in Figs. 3 to 6.

Figure 3: Print scanned announcements

Figure 4: Preprocessed announcement
Figure 5: Print scanned electronic invoice
Figure 6: Preprocessed electronic invoice
3.2 Watermark Embedding Process
The watermark embedding process is shown in Fig. 7, and the specific description is as follows:
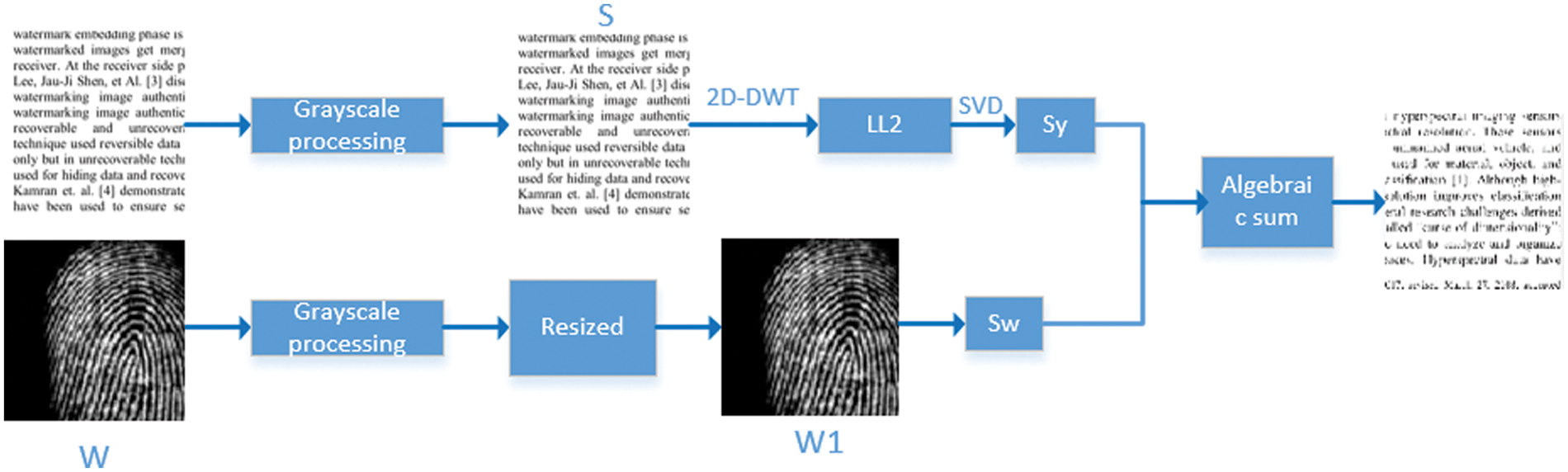
Figure 7: Watermark embedding flow chart
Step 1: Grayscale the text image, or select one of the R, G, and B channels as the original text image S.
Step 2: Grayscale the watermark image W, and the watermark image is resized to obtain a preprocessed watermark image W1. After reshaping, the watermark image W1 is 1/16 of the size of the original text image S (equal to the size of the LL subband after two DWT transformations).
Step 3: Perform the first-order DWT transformation on the original text image to obtain the LL1 component, and then perform the second-order DWT transformation on the LL1 element to get the LL2 detail.
Step 4: The singular value Sw of the watermark image is obtained by SVD transformation of the LL2 component of the original text image [23]. The transformed U and V matrices are saved to restore the extracted watermark’s image.
Step 5: Set the embedding strength to A. The singular value Sy obtained from the singular value decomposition of the reconstructed watermark image W1 is saved for verification during extraction. The algebraic sum operation is performed with the particular value Sw of the watermark image, according to the mean by Eq. (3).
Step 6: Get changed
The watermark extraction process is shown in Fig. 8, and the specific description is as follows:
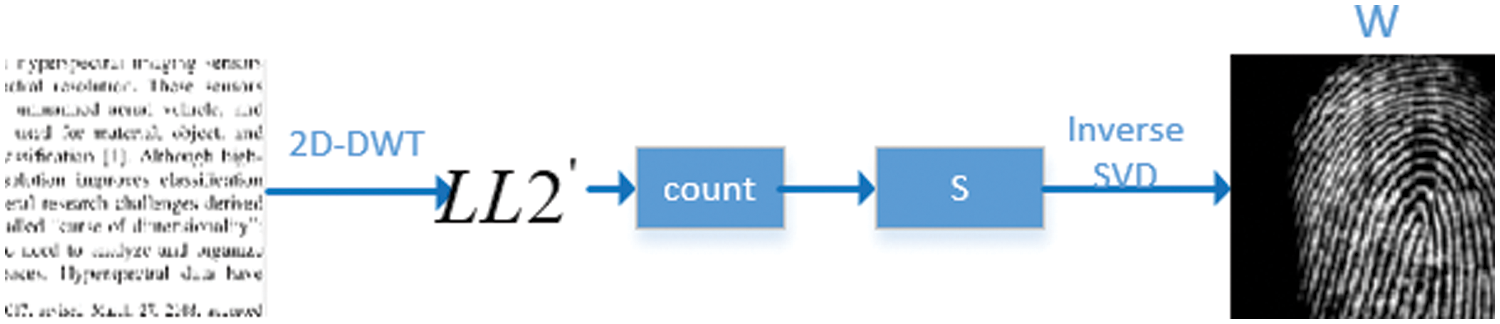
Figure 8: Watermark extraction flow chart
Step 1: DWT transform the text image containing watermark twice [24] to obtain the component
Step 2: SVD transformation of
Step 3: After obtaining the S component of the watermark, combine the U and V components of the watermark image saved during the embedding process to multiply the singular matrix by
Watermarking algorithms are usually measured in terms of invisibility and robustness, which are mutually constrained. A good watermarking algorithm should balance robustness and invisibility and improve watermark robustness while ensuring watermark invisibility.
4.1 Introduction to Experimental Environment
With multimedia development, documents that use electronic forms as information carriers have become mainstream, such as invoice vouchers, important announcements from government agencies, and papers with personal copyright. Most of them are printed, published, or disseminated in electronic form. However, existing technologies are prone to copying and forging such important image files through scanning, and if the tampered information is spread, it will cause incalculable losses. Therefore, embedding watermarks in these essential files can effectively protect the copyright of the files and prevent them from being maliciously modified by attackers. When electronic files containing watermarks are printed, even if scanned and altered by an attacker, the watermark information can be fully extracted during verification, protecting copyright content such as invoices, announcements, and papers.
In this paper, simulation experiments are done on the Matlab platform. The original images used in this experiment are not only standard grayscale images and colour images but also some screenshots of electronic invoices and screenshots of the thesis. The watermarked images are 64 × 64 and 128 × 128, 256 × 256 grayscale images, and the original images and watermarked images used in this experiment are shown in Figs. 9 and 10.

Figure 9: Original images used in the experiment ((a) Lena; (b) Paper screenshot; (c) Announcement with handwritten signature; (d) Screenshot of electronic invoice; (e) Screenshot of announcement;(f) Lake)

Figure 10: Watermark image used in the experiment ((a) cman; (b) fingerprint; (c) loco)
Figs. 9a, 9e are color images, 9b, 9c, 9e, 9f are grayscale images, 9c has handwritten content, and 9d is an electronic invoice with a seal.
Figs. 10a–10c are the cman diagrams, fingerprint diagram and loco diagram in the standard grayscale image.
4.2 Algorithm Performance Test
The performance test mainly includes the watermark extraction effect test for printing and scanning. This paper adopts the Peak Signal-to-Noise Ratio (PSNR) [25], Structural Similarity (SSIM), and Normalized Correlation coefficient (NC) [25] as the experimental result metric criteria. The invisibility of the watermark is proportional to the quality of the image, and the higher the quality of the image, the stronger the invisibility of the watermark. The quality of the recovered image determines the recovery quality of the fragile watermarking scheme with recovery capability. If the recovered image quality is good, the recovery capability of the delicate watermarking scheme is good. Image quality metrics are generally measured by the peak signal-to-noise ratio (PSNR), normalized correlation coefficient (NC) [26], and structural similarity (SSIM). The three metrics peak signal-to-noise ratio、structural similarity and NC are described below.
Assume the original image size is M × N. Then PSNR can be defined as Eq. (5).
where,
SSIM is a measure of the similarity between two images. SSIM can be defined by Eq. (6).
Among them,
NC is a measure of the similarity between two signals. NC can be defined by Eq. (7).
where,
Robustness refers to the ability to extract relatively complete watermark information from an embedded image after various attacks.
Generally, Bit Error Ratio (BER) [27] is used to evaluate the robustness of the watermark. The ability of the watermark algorithm to resist various attacks is judged by calculating the proportion of error bits in the extracted watermark. BER is inversely proportional to the robustness of the watermark, and its calculation formula is shown in Eq. (8).
4.2.1 Watermark Embedding and Extraction Effect Test Without Attack
The algorithm experiment without any attack and processing is carried out in this paper to verify the visual invisibility of the algorithm. The original image is shown in Fig. 11. The experiment results in the watermark image and the extracted watermark image, as shown in Figs. 12 and 13.

Figure 11: Original images

Figure 12: Watermaked image

Figure 13: Extracted image
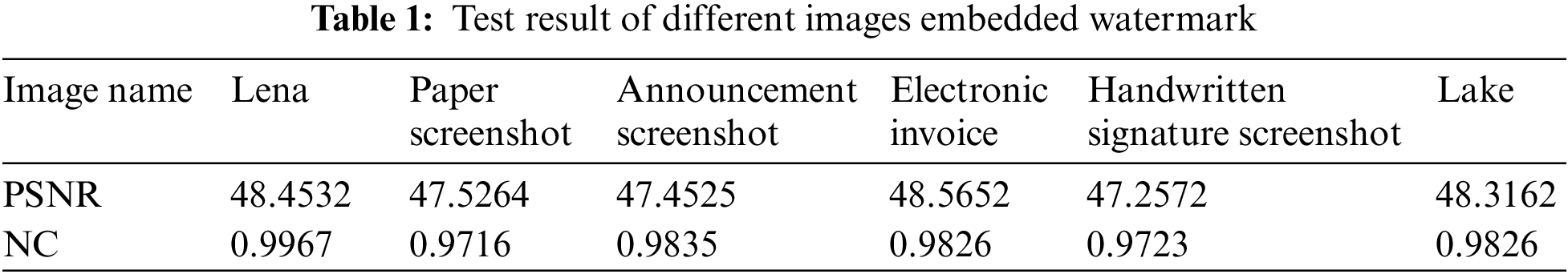
The embedding strength A of the watermark in the experiment is 0.75, and the level of embedding strength will affect human eye vision and the calculation of image feature values [28]. From the effect of the image with the watermark in Fig. 12.
As shown in Table 1, the average PSNR of the embedded watermarked image is 47.9285 dB, and the lowest PSNR is 47.2572 dB with high image invisibility. The average NC of the extracted watermark is 0.9815, and the lowest NC is 0.9716 with high accuracy.
4.2.2 Watermark Embedding Effect Test under Different Embedding Intensities
The watermark embedding strength selected in this experiment is 0.1, 0.5 and 0.75, respectively, and the embedding effect is shown in Fig. 14.

Figure 14: ((a)–(c) Announcement screenshot; (d)–(f) Paper screenshot; (g)–(i) Lake; (j)–(l) Handwritten signature)
The image quality under different embedding intensities in Fig. 13 is reflected by the PSNR, as shown in Table 2.
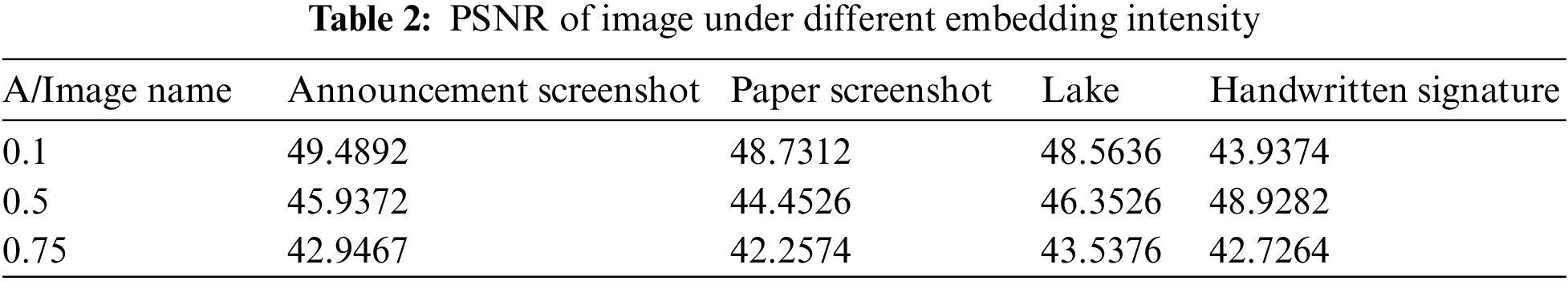
Generally speaking, if the PSNR of the watermarked image is greater than 36 dB, the visual system of human eyes cannot distinguish the traces of the watermark. As shown in Table 2, the PSNR of the watermarked image is greater than 36 dB for all embedding intensities in the table, indicating that the watermark’s invisibility is better. It can be seen from Table 2 that for the handwritten signature,the image quality is highest when the embedding intensity is 0.5, and for other experimental images, the quality is highest when the embedding intensity is 0.1. The algorithm can flexibly adjust the embedding intensity for different images to achieve the best embedding effect.
4.2.3 Anti-Print Scanning Test
For the embedded image, the watermark quality extracted after printing and scanning is reflected by the NC. The watermark is extracted from the embedded image in Fig. 14, and its NC is calculated as shown in Table 3.
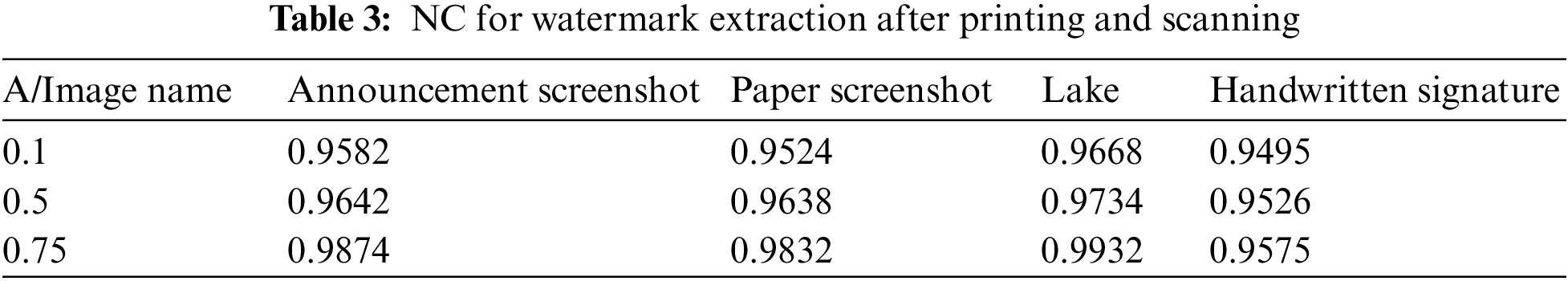
As shown in Table 3, the average NC of the watermark extracted after the printing and scanning attack is 0.9669, and the watermark algorithm has high invisibility. The minimum NC is 0.9495, and the size of the NC is proportional to the embedding strength. The NC change diagram of watermark extraction after printing and scanning is shown in Fig. 15.
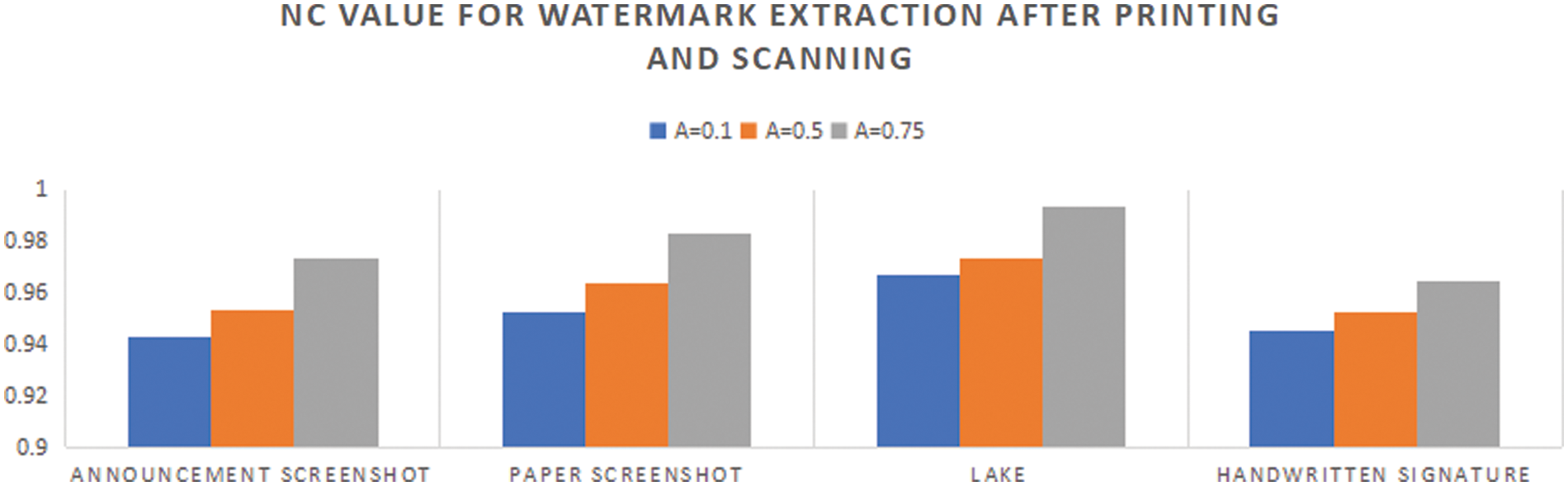
Figure 15: NC change diagram for watermark extraction after printing and scanning
Digital information will be subject to various attacks during transmission, and the embedded watermark information will be damaged to a certain extent after being attacked [29]. The following attack experiments are conducted on the image with a watermark. The attack types include speckle noise, Joint Photographic Experts Group JPEG compression, sharpening attack, salt and pepper noise, and JPEG2000 compression. The embedded strength in the test is 0.75.
Speckle noise is a significant feature of the Synthetic Aperture Radar (SAR) imaging system. It originates from the random scattering in the basic resolution unit. It is shown as small spots related to the image’s signal, which reduces the image quality and seriously affects image segmentation, classification, and target detection information extraction. As shown in Fig. 16, the watermark image and watermark extraction result are after the speckle noise attack.

Figure 16: Watermarked image and watermark extraction results after speckle noise attack
The watermarked image after being attacked by speckle noise is shown in Fig. 16a, with PSNR of 35.4092 and SSIM of 0.87631; The NC of the watermark extracted after the speckle noise attack is 0.99371.
JPEG is lossy compression, this process for images containing watermarks will lose a lot of important information, and there will be some impact on the extraction of watermarks. Still, this lost part is part of human vision is not easily perceived [30,31]. It takes full advantage of the human eye not being sensitive to the high-frequency information part of the computer colour to save significantly the data that needs processing [32–35]. Fig. 17 shows the JPEG compression attack after containing the watermarked image and the watermark extraction results.

Figure 17: Watermarked image and watermark extraction result after JPEG compression attack
The watermarked image after the JPEG compression attack is shown in Fig. 17a, with PSNR of 35.5959 and SSIM of 0.91854; The watermark NC extracted after the JPEG compression attack is 0.99437.
Pepper noise, also known as impulse noise, is a type of noise often seen in images. It is a random appearance of white or black dots, either as black pixels in bright areas or white pixels in dark places (or both). Pepper noise can be caused by sudden and intense interference with the image signal, analogous digital converters, or bit transfer errors. As shown in Fig. 18, the watermark-containing image and watermark extraction results after the pretzel noise attack are shown.

Figure 18: Watermarked image and watermark extraction results after salt and pepper noise attack ((a) Watermarked image after salt and pepper noise attack; (b) Watermarks extracted after salt and pepper noise attack)
The watermarked image after being attacked by salt and pepper noise is shown in Fig. 18a, with PSNR of 35.0048 and SSIM of 0.97112; The NC of the watermark extracted after salt and pepper noise attack is 0.99539.
JPEG2000 is an image compression standard based on wavelet transform. It is often considered the next-generation image compression standard to replace JPEG (based on discrete cosine transform) in the future. JPEG2000 has a higher compression ratio and does not produce the blocky blurring imperfections created by the original JPEG standard based on discrete cosine transform. JPEG2000 supports both lossy and lossless compression. Fig. 19 shows the result of the JPEG compression attack with watermarked images and watermark extraction.

Figure 19: Watermarked image and watermark extraction results after JPEG2000 compression attack ((a) Watermarked image after JPEG2000 attack; (b) Watermarks extracted after JPEG2000 attacks)
The watermarked image after being attacked by JPEG2000 noise is shown in Fig. 19a, with a PSNR of 37.9741 and SSIM of 0.93591; The NC of the watermark extracted after the JPEG2000 noise attack is 0.99598.
From the above four attack tests, it can be seen that the average PSNR of the watermark image after the attack is 35.996, and the average SSIM is 0.92547; The average NC of the extracted watermark image is 0.9948. The experimental results show that the algorithm has good robustness under different attacks and has the most vital ability to resist JPEG2000 compression attacks.
NC of Image Embedded with Different Size Watermarks under Various Attacks
In this experiment, the screenshot of the paper is selected as the original image, and the embedding strength is 0.75. The watermark images of different sizes are embedded, and the dimensions are respectively 64 × 64, 128 × 128 and 256 × 256. And we perform various attack tests on the original image containing the watermark image, such as JPEG compression, JPEG2000 compression, Gaussian low-pass filtering, and median filtering attacks. Calculate the NC of the watermark extracted after the attack, as shown in Fig. 20.
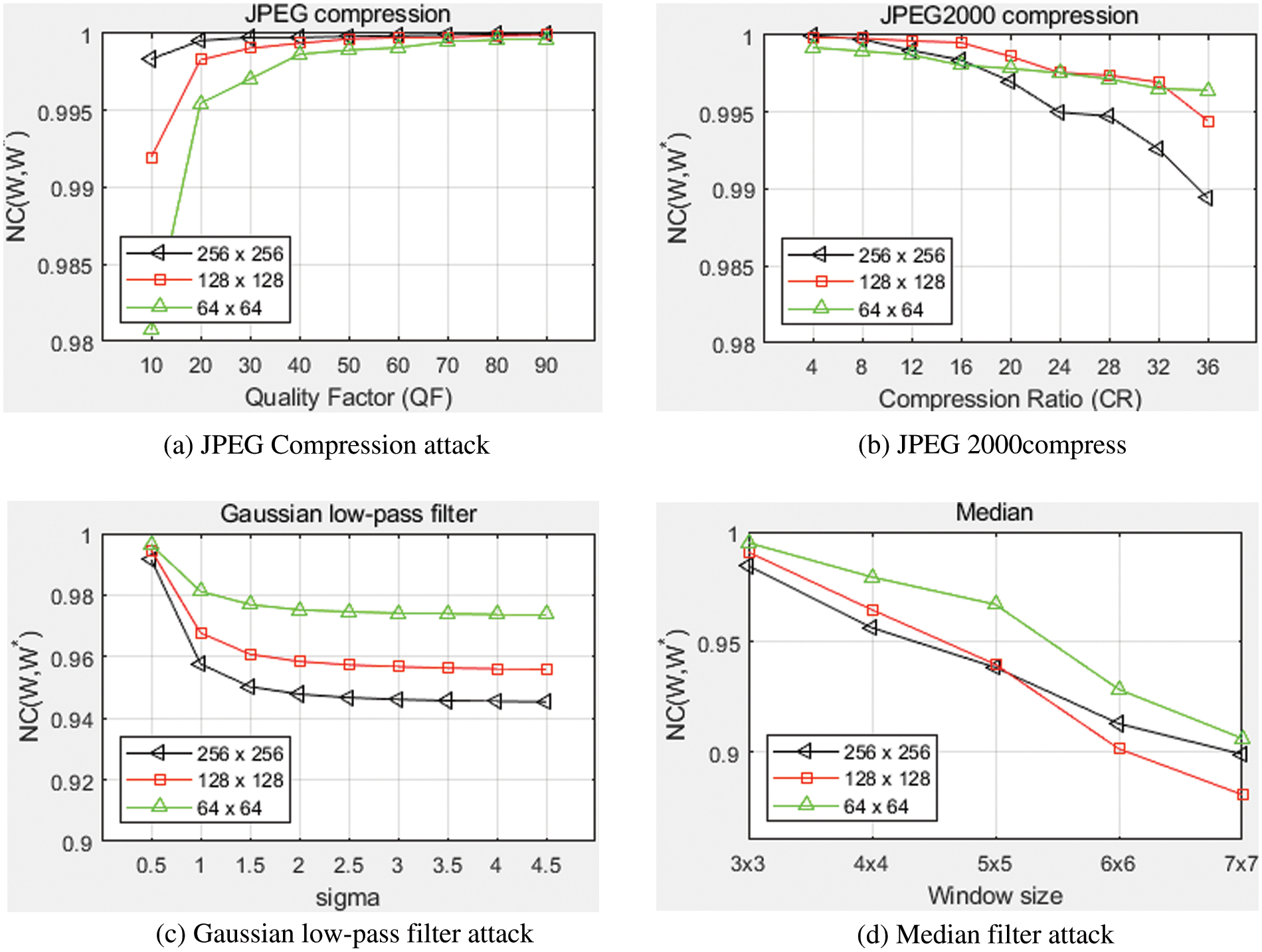
Figure 20: Extract the NC result of the watermark image after being attacked ((a) JPEG compression attack; (b) JPEG2000 compression; (c) Gaussian low-pass filtering attack; (d) Median filter attack)
Generally speaking, if the PSNR of the watermarked image is greater than 36 dB, the visual system of human eyes cannot distinguish the traces of the watermark. As shown in Table 2, the PSNR of the watermarked image is greater than 36 dB for all embedding intensities in the table, indicating that the watermark’s invisibility is better. It can be seen from Table 2 that for the handwritten signature,the image quality is highest when the embedding intensity is 0.5, and for other experimental images, the quality is highest when the embedding intensity is 0.1. The algorithm can flexibly adjust the embedding intensity for different images to achieve the best embedding effect.
The article [20] is to find a way to embed a blind watermark into images for printing which is against print-and-scan but can be detected by the neural network to realize a kind of anti-counterfeit watermark. During the screening, two different types of dithering were used to fuse each pixel of the binary watermark with the host images into halftone ones. Based on the set of sample pairs of the printed-and-scanned image with the watermark and the watermark data, a back propagation (BP) neural network was trained to embed watermark information. Our proposed method showed the best watermark display effect compared to standard watermarking techniques, such as pixel embedding and local gird-adding. It offers a print-and-scan (PS) resilient watermarking scheme based on the mean of DCT coefficients (MDC) for a fixed AC frequency of image in the article [31] and a zero-watermarking algorithm based on visual cryptography and matrix norm in the paper [32]. Conduct Gaussian noise attack, salt, pepper noise attack, JPEG attack, and print scan attack on these four algorithms, respectively. The original image is 512 × 512 Lena images, and the watermark images in articles [20,31,35] are 32 × 32 sizes. The watermark image in this paper is 128 × 128. The embedded intensity of 256 images is 0.75. The comparative data of these algorithms are shown in Table 4.
In Table 4, the anti-Gaussian noise is represented by the PSNR of the image before and after the attack, and the anti-salt and pepper noise, anti-JPEG attack, and anti-print scanning attack are described by the NC of the extracted watermark. It can be seen from Table 4 that the algorithm in this paper has good resistance to Gaussian noise, salt and pepper noise, JPEG attack, and print scan attack, and the watermark image size of [11,31] algorithm was 32 × 32, the watermark image size of this algorithm was 128 × 128, which improved the embedding capacity of the watermark while ensuring the strong robustness and anti-attack ability of the algorithm, and solved the problem that the existing anti-print scanning watermarking algorithm cannot take into account the robustness and high watermark embedding capacity. For the algorithm [20], the watermark image size was 64 × 64, the algorithm used a neural network and deep learning tools to improve the detection ability of the watermark, but the embedded watermark was 64 × 64. This algorithm can better balance the contradiction between robustness and watermark embedding capacity. The more significant the amount of embedded information, the more traceable information can be embedded. At the same time, improving watermark capacity also improved the algorithm’s robustness. In reference [35], it used a QR code to hide critical information into a credential, then embed it into the credential photo and combined the wavelet transform and matrix norm to extract the image characteristics and configure invariance of the print-scanning. Next, it combined visual cryptography and digital watermark. And it used one share of the visual cryptography to be saved as a zero-watermark. This algorithm strongly resisted print scanning attacks, but this generated zero watermarks to protect copyright, increasing the cost of preserving watermarked images.
In literature [18], the algorithm proposed by Wang et al. takes an average of 14 s to embed watermark information, while the algorithm only toke less than 1 s to embed the watermark. The watermark embedding and extraction efficiency were high, and the time cost was saved. Moreover, preparing the watermarking algorithm based on deep learning was relatively complex and time-consuming. For example, in literature [18], a certain number of new fonts need to be generated and deleted, and font classifiers need to be trained. Moreover, the accuracy of the classifier cannot reach 100%, and the watermark information will fail to be embedded.
The BER of the watermark extracted after various attacks are calculated to verify the algorithm’s robustness. Robustness verification attacks can be divided into other common attacks and print scanning attacks. The BER experimental values of watermark images extracted under six different attacks by the algorithm in this chapter are shown in Table 5. The robustness comparison of the six attacks is shown in Fig. 20.
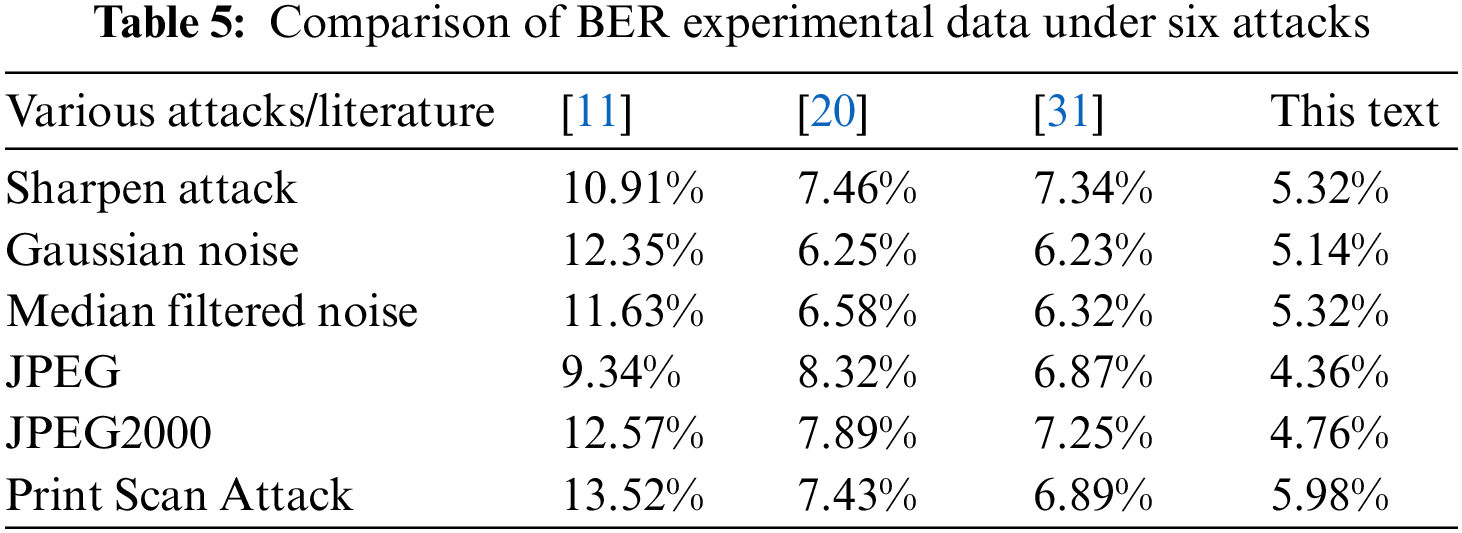
As can be seen from Table 5, the mean BER of the algorithm in this chapter is 5.15%, while the mean BER of the literature [11,20,31] are 11.72%, 7.32%, and 6.82%, respectively. The BER mean value of the algorithm in this chapter has decreased by 56.1%, 29.6%, and 24.5%, respectively, based on the literature [11,20,31], indicating that the algorithm in this chapter has better resistance to the six attacks as a whole, and its robustness has been dramatically improved.
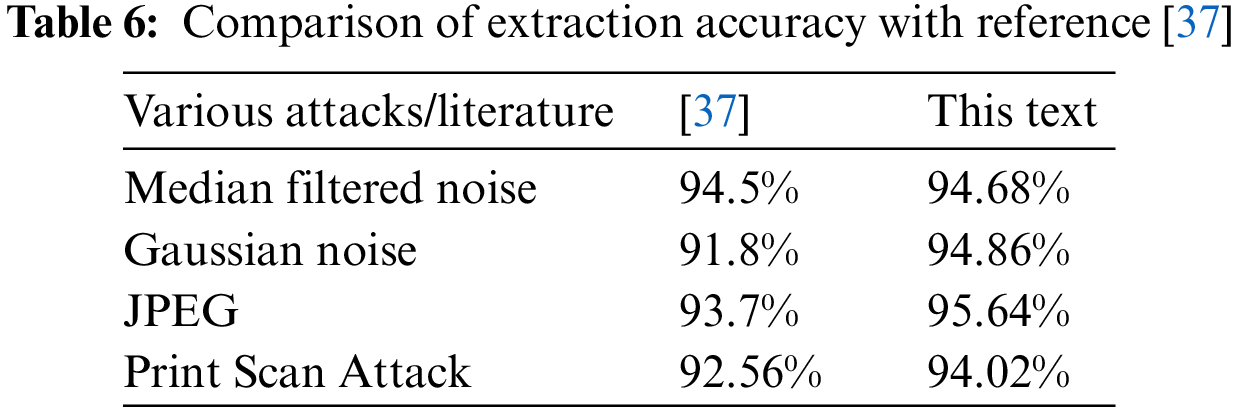
From Table 6, it can be seen that the performance of this article is similar to that of reference 38 when subjected to median filtering noise. However, the performance of other attacks, such as Gaussian noise attacks, JPEG attacks, and print scan attacks, is significantly higher than that of the algorithm in reference 38 in extracting watermarks. It can be seen that the performance of deep learning methods is far inferior to our method after targeted training, and the training time of deep learning methods is longer and the computational cost is higher. The watermark capacity of deep learning methods is mostly 64 × 1. The capacity of our method is much greater than that of deep learning methods. Even in unfair comparisons, our method is superior.
This paper combines image enhancement to embed a watermark in the transform domain and combines the DWT algorithm with the SVD algorithm to propose a digital watermarking algorithm suitable for text images to resist print scanning. This algorithm embeds a watermark by combining DWT-SVD so that the image with the watermark can still be extracted completely after printing and scanning and has good watermark capacity. The algorithm in this paper embeds watermarks of different sizes. The results show that the algorithm has good imperceptibility while embedding watermark information with a large capacity. For attacks such as JPEG compression, JPEG2000 compression, Gaussian low-pass filtering, median filtering, and print scanning, the average NC of the watermark extracted by the algorithm in this paper is above 0.93, which shows that the algorithm has high robustness and anti-attack ability and improves the capacity of watermark embedding under the premise of ensuring robustness and invisibility. The next step is to further improve the NC of the watermark image and make the algorithm effectively process all kinds of data except the image.
Acknowledgement: The author of this article is very grateful for the help of the following experts and people: Weishen Wang for his supplementary comments on the paper, and Guoqing Xu for his valuable comments on the structure and logic of the paper.
Funding Statement: This work was sponsored by the National Natural Science Foundation of China under Grants 61972207, U1836208, U1836110, 61672290, and the Project was through the Priority Academic Program Development (PAPD) of Jiangsu Higher Education Institution.
Author Contributions: The authors confirm contribution to the paper as follows: study conception and design: Baowei Wang, Luyao Shen; data collection: Luyao Shen, Junhao Zhang; analysis and interpretation of results: Luyao Shen, Zenghui Xu; draft manuscript preparation: Luyao Shen, Neng Wang. All authors reviewed the results and approved the final version of the manuscript.
Availability of Data and Materials: If readers need data, they can contact my email: 1139901607@qq.com.
Conflicts of Interest: The authors declare that they have no conflicts of interest to report regarding the present study.
References
1. U. A. Bhatti, Z. Y. Yu, J. B. Li, S. A. Nawaz, A. Mehmood et al., “Hybrid watermarking algorithm using clifford algebra with arnold scrambling and chaotic encryption,” IEEE Access, vol. 8, pp. 2169–3536, 2020. [Google Scholar]
2. G. Xie, Y. Liu, G. Xin and P. Yang, “Review on text watermarking resistant to print-scan, screen-shooting,” in 5th Int. Conf. on Artificial Intelligence and Security, New York, NY, USA, pp. 140–149, 2019. [Google Scholar]
3. U. Khadam, M. M. Iqbal, M. A. Azam, S. Khalid, S. Rho et al., “Digital watermarking technique for text document protection using data mining analysis,” IEEE Access, vol. 7, pp. 64955–64965, 2019. [Google Scholar]
4. K. Thongkor and T. Amornraksa, “Digital image watermarking for printed and scanned documents,” in Ninth Int. Conf. on Digital Image Processing, Hong Kong, China, pp. 782–786, 2017. [Google Scholar]
5. S. A. Nawaz, J. Li, U. A. Bhatti, A. Mehmood, M. U. Shoukat et al., “Advance hybrid medical watermarking algorithm using speeded up robust features and discrete cosine transform,” PLoS One, vol. 15, no. 6, pp. 1–21, 2020. [Google Scholar]
6. L. Tan, K. Hu, X. Zhou, R. Chen and W. Jiang, “Print-scan invariant text image watermarking for hardcopy document authentication,” Multimedia Tools and Applications, vol. 78, pp. 13189–13211, 2019. [Google Scholar]
7. U. A. Bhatti, Z. Yu, J. Chanussot, Z. Zeeshan and L. Yuan, “Local similarity-based spatial–spectral fusion hyperspectral image classification with deep CNN and gabor filtering,” IEEE Transactions on Geoscience and Remote Sensing, vol. 60, pp. 1–15, 2021. [Google Scholar]
8. U. A. Bhatti, H. Tang, G. Wu, S. Marjan and A. Hussain, “Deep learning with graph convolutional networks: An overview and latest applications in computational intelligence,” International Journal of Intelligent Systems, vol. 2023, pp. 1–28, 2023. [Google Scholar]
9. J. Zhu, R. Kaplan, J. Johnson and F. L. Fei, “Hidden: Hiding data with deep networks,” in Proc. of the European Conf. on Computer Vision (ECCV), Amsterdam, The Netherlands, pp. 657–672, 2018. [Google Scholar]
10. Z. Jia, H. Fang and W. Zhang, “MBRS: Enhancing robustness of DNN-based watermarking by mini-batch of real and simulated JPEG compression,” in Proc. of the 29th ACM Int. Conf. on Multimedia, Chengdu, China, pp. 41–49, 2021. [Google Scholar]
11. A. Keskinarkaus, A. Pramila and T. Seppänen, “Image watermarking with a directed periodic pattern to embed multibit messages resilient to print-scan and compound attacks,” Journal of Systems and Software, vol. 83, pp. 1715–1725, 2010. [Google Scholar]
12. K. Huang, X. Tian, H. Yu, M. Yu, A. Yin et al., “A high-capacity watermarking technique for the printed document,” Electronics, vol. 8, pp. 1403–1416, 2019. [Google Scholar]
13. S. Han and W. L. Zhang, “SVD based digital watermarking algorithm for print-and-scan process,” in 2020 IEEE 20th Int. Conf. on Communication Technology (ICCT), Nanning, China, IEEE, pp. 1427–1431, 2020. [Google Scholar]
14. C. Wang and C. Li, “Spot color watermarking: The use of the IWT-SVD and tone correction model,” Multimedia Tools and Applications, vol. 79, pp. 21627–21652, 2020. [Google Scholar]
15. V. L. Cu, J. C. Burie and J. M. Ogier, “Watermarking for security issue of handwritten documents with fully convolutional networks,” in 2018 16th Int. Conf. on Frontiers in Handwriting Recognition (ICFHR), NY, USA, IEEE, pp. 303–308, 2018. [Google Scholar]
16. X. Zhao, H. Lin and X. Xu, “Resilient watermarking algorithm to printing and scanning combining local feature regions and DWT-SVD,” in Proc. of the 2022 4th Int. Conf. on Robotics, Intelligent Control and Artificial Intelligence (RICAI 2022), Dongguan, China, pp. 1191–1195, 2022. [Google Scholar]
17. F. Ahmad and L. M. Cheng, “Authenticity and copyright verification of printed images,” Signal Processing, vol. 148, pp. 322–335, 2018. [Google Scholar]
18. H. Wang, Q. Zuo, X. Cao, S. Zhao and H. Li, “An anti-printing scanning watermarking algorithm based on fusion fonts,” in Advances in Artificial Intelligence and Security: 8th Int. Conf. on Artificial Intelligence and Security, Qinghai, China, pp. 450–463, 2022. [Google Scholar]
19. M. Mu, L. Guo, N. Li, C. Ma, J. Xu et al., “Research on embedding environment of digital watermark resistant to print-scan and print-camera (PSPC),” in Advances in Graphic Communication, Printing and Packaging Technology and Materials: Proc. of 2020 11th China Academic Conf. on Printing and Packaging, Guangzhou, China, pp. 199–203, 2022. [Google Scholar]
20. Y. Chen, Q. Wang, Y. Luo and C. Wu, “A halftone blind watermark to resist print-and-scan and be detected by BP neural network,” in Interdisciplinary Research for Printing and Packaging (CACPP 2021), Beijing, China, pp. 137–142, 2022. [Google Scholar]
21. K. A. Al-Afandy, O. S. Faragallah, E. S. M. EL-Rabaie, F. E. A. El-Samie and A. ELmhalawy, “Efficient color image watermarking using homomorphic based SVD in DWT domain,” 2016 Fourth Int. Japan-Egypt Conf. on Electronics, Cairo, Egypt, pp. 43–47, 2016. [Google Scholar]
22. M. Hamidi, M. E. Haziti, H. Cherifi and M. E. Hassouni, “Hybrid blind robust image watermarking technique based on DFT-DCT and Arnold transform,” Multimedia Tools and Applications, vol. 77, pp. 27181–27214, 2018. [Google Scholar]
23. J. Liu, J. Huang, Y. Luo, L. Cao, S. Yang et al., “An optimized image watermarking method based on HD and SVD in DWT domain,” IEEE Access, vol. 7, pp. 80849–80860, 2019. [Google Scholar]
24. B. Ahmaderaghi, F. Kurugollu, J. M. D. Rincon and A. Bouridane, “Blind image watermark detection algorithm based on discrete shearlet transform using statistical decision theory,” IEEE Transactions on Computational Imaging, vol. 4, no. 1, pp. 46–59, 2018. [Google Scholar]
25. A. Hore and Z. Djemel, “Image quality metrics: PSNR vs. SSIM,” in 2010 20th Int. Conf. on Pattern Recognition, Istanbul, Turkey, pp. 2366–2369, 2010. [Google Scholar]
26. L. Wu and L. Zhao, “ISAR Image Registration Based on Normalized Correlation Coefficient,” in The 2023 IEEE 3rd International Conference on Power, Electronics and Computer Applications (ICPECA), China, Guangzhou, pp. 354–359, 2023. [Google Scholar]
27. G. Breed, “Bit error rate: Fundamental concepts and measurement issues,” High Frequency Electronics, vol. 2, no. 1, pp. 46–47, 2003. [Google Scholar]
28. R. A. Alotaibi and L. A. Elrefaei, “Text-image watermarking based on integer wavelet transform (IWT) and discrete cosine transform (DCT),” Applied Computing and Informatics, vol. 15, no. 2, pp. 191–202, 2019. [Google Scholar]
29. Z. Yuan, Q. Su, D. Liu and X. Zhang, “A blind image watermarking scheme combining spatial domain and frequency domain,” Visual Computer, vol. 37, no. 7, pp. 1867–1881, 2021. [Google Scholar]
30. Q. Su, H. Wang, D. Liu, Z. Yuan and X. Zhang, “A combined domain watermarking algorithm of color image,” Multimedia Tools and Applications, vol. 79, no. 39–40, pp. 30023–30043, 2020. [Google Scholar]
31. D. Cheng, X. Li, W. Qi and B. Yang, “A statistics-based watermarking scheme robust to print-and-scan,” in 2008 Int. Symp. on Electronic Commerce and Security, Guangzhou, China, pp. 894–898, 2008. [Google Scholar]
32. W. Guo and W. F. Qi, “An improved print-scan resistant watermarking scheme,” Applied Mechanics and Materials, vol. 731, pp. 153–158, 2015. [Google Scholar]
33. D. C. Su, Z. H. Liu, G. Yuan and X. F. Wang, “New rapid and robust color image watermarking technique in spatial domain,” IEEE Access, vol. 7, pp. 30398–30409, 2019. [Google Scholar]
34. B. Tian, “Research on anti-printing scanning digital watermarking for complex layout documents,” M.S. dissertation, Zhejiang University, China, 2020. [Google Scholar]
35. D. Li, X. Dai, L. Chen and L. Cui, “A zero-watermarking algorithm based on visual cryptography and matrix norm in order to withstand printing and scanning,” in Advanced Multimedia and Ubiquitous Engineering, vol. 518. Singapore: Springer, pp. 557–563, 2018. [Google Scholar]
36. C. C. Chang, Y. S. Hu and C. C. Lin, “A digital watermarking scheme based on singular value decomposition,” in Int. Symp. on Combinatorics, Hangzhou, China, Springer Berlin Heidelberg, pp. 82–93, 2007. [Google Scholar]
37. H. Fang, Z. Y. Jia, H. Zhou, Z. H. Ma and W. M. Zhang, “Encoded feature enhancement in watermarking network for distortion in real scenes,” IEEE Transactions on Multimedia, pp. 1–13, 2022. [Google Scholar]
Cite This Article
 Copyright © 2023 The Author(s). Published by Tech Science Press.
Copyright © 2023 The Author(s). Published by Tech Science Press.This work is licensed under a Creative Commons Attribution 4.0 International License , which permits unrestricted use, distribution, and reproduction in any medium, provided the original work is properly cited.


 Submit a Paper
Submit a Paper Propose a Special lssue
Propose a Special lssue View Full Text
View Full Text Download PDF
Download PDF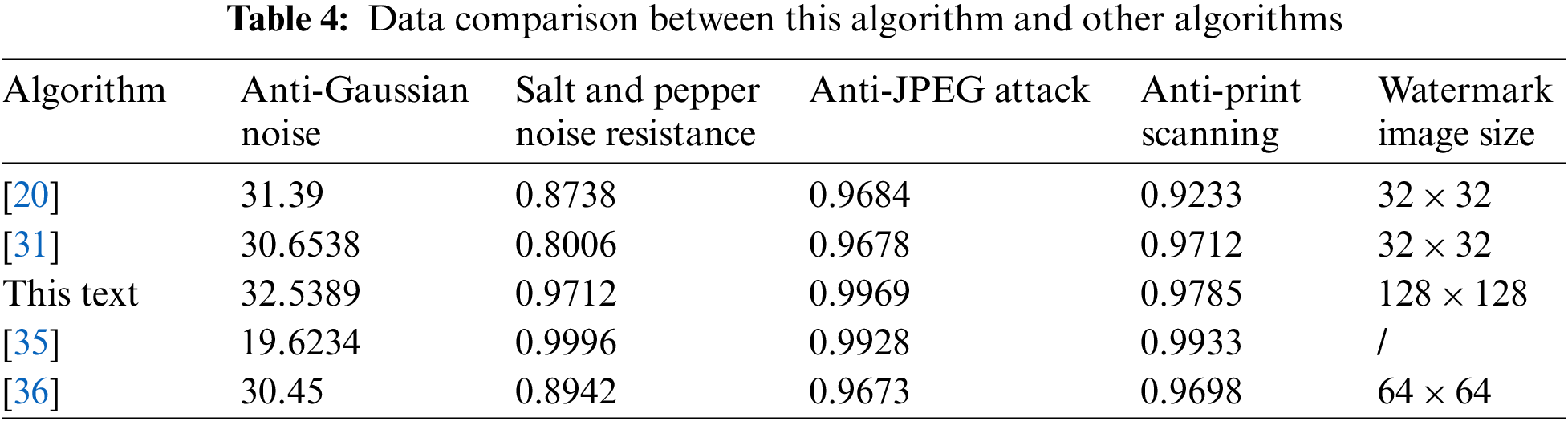
 Downloads
Downloads
 Citation Tools
Citation Tools