 Open Access
Open Access
ARTICLE
A Wrapping Encryption Based on Double Randomness Mechanism
1 Department of Computer Science, Tunghai University, Taichung, 40764, Taiwan
2 Emergency Response Management Center, Ming Chung University, Taipei, 11103, Taiwan
3 General Education Center, Ming Chuan University, Taipei, 11103, Taiwan
* Corresponding Author: Fang-Yie Leu. Email:
Computers, Materials & Continua 2023, 77(1), 1143-1164. https://doi.org/10.32604/cmc.2023.037161
Received 26 October 2022; Accepted 19 July 2023; Issue published 31 October 2023
Abstract
Currently, data security mainly relies on password (PW) or system channel key (SKCH) to encrypt data before they are sent, no matter whether in broadband networks, the 5th generation (5G) mobile communications, satellite communications, and so on. In these environments, a fixed password or channel key (e.g., PW/SKCH) is often adopted to encrypt different data, resulting in security risks since this PW/SKCH may be solved after hackers collect a huge amount of encrypted data. Actually, the most popularly used security mechanism Advanced Encryption Standard (AES) has its own problems, e.g., several rounds have been solved. On the other hand, if data protected by the same PW/SKCH at different time points can derive different data encryption parameters, the system’s security level will be then greatly enhanced. Therefore, in this study, a security scheme, named Wrapping Encryption Based on Double Randomness Mechanism (WEBDR), is proposed by integrating a password key (or a system channel key) and an Initialization Vector (IV) to generate an Initial Encryption Key (IEK). Also, an Accumulated Shifting Substitution (ASS) function and a three-dimensional encryption method are adopted to produce a set of keys. Two randomness encryption mechanisms are developed. The first generates system sub-keys and calculates the length of the first pseudo-random numbers by employing IEK for providing subsequent encryption/decryption. The second produces a random encryption key and a sequence of internal feedback codes and computes the length of the second pseudo-random numbers for encrypting delivered messages. A wrapped mechanism is further utilized to pack a ciphertext file so that a wrapped ciphertext file, rather than the ciphertext, will be produced and then transmitted to its destination. The findings are as follows. Our theoretic analyses and simulations demonstrate that the security of the WEBDR in cloud communication has achieved its practical security. Also, AES requires 176 times exclusive OR (XOR) operations for both encryption and decryption, while the WEBDR consumes only 3 operations. That is why the WEBDR is 6.7~7.09 times faster than the AES, thus more suitable for replacing the AES to protect data transmitted between a cloud system and its users.Keywords
In recent years, owing to the fast advance of the 5th generation (5G) networks and Internet techniques and the popularity of mobile phones, a wide range of mobile applications were proposed to provide us with a colorful living environment and enrich our daily lives. Also, with the fast development of cloud computing, people frequently send data to a cloud for storage or processing. But data transmitted via wireless channels may be stolen by hackers, conducting severe security problems. This means we need a more secure data transmission environment before the delivered data can be safely protected.
In addition, in the age of big data, the sizes of files transferred between a cloud system and users are often huge, i.e., encryption/decryption speeds should be two of the key issues if we want to deliver them via a 5G network.
At present, Advanced Encryption Standard (AES) as a block cipher mechanism has been popularly employed to secure delivered data. The AES adopts the combinational logic encryption method [1], consequently attracting different kinds of brute-force attacks [2–4]. According to references [5,6], the AES will soon be insecure since it has been partially solved. Thus, a safer block ciphering method is required shortly. In 2016, Huang et al. [7] introduced a random method to encrypt/decrypt messages/files. However, it is not truly random, since Δh is derived from password (PW) only where Δh is the length of an additional character string utilized to hide the beginning point of the ciphertext. The weakness is that Δh may be solved by Brute-force attacks [7]. After that, the same PW will be employed to crack wrapped ciphertext files.
Thus, in this study, a more secure scheme, named “Wrapping Encryption Based on Double Randomness Mechanism (WEBDR for short) is proposed. The WEBDR enhances the security level of block ciphering by wrapping ciphertext with two dynamic data sequences of variable lengths to form a wrapped file, aiming to hide the ciphertext to protect it from being accessed by hackers. The WEBDR uses four types of keys to encrypt data. The first one is called the initial encryption key (IEK), which is generated by integrating a password key (or a channel key) and an initialization vector (IV). The second is a set of sub-keys (SK1~SK5), which is produced by using an accumulated shifting substitution (ASS) function and a Three-dimensional encryption method (3D Encryption). Following that, the WEBDR retrieves current time from its internal clock to produce a key, named the current time key (SKCT), as the third type of key. The fourth is a random encryption key (REK) generated randomly.
Owing to using these four types of keys, even encrypting the same plaintext with the same password, the WEBDR generates different corresponding ciphertext of different lengths and different wrapped ciphertext files. Therefore, it is not easy for hackers to access and then solve the ciphertext. Our previous research results can be seen in reference [7]. The main contributions of this study are listed below:
(1) We adopt the timing-random mechanism to randomly wrap ciphertext. This can effectively prevent hackers from solving the relationship between plaintext and ciphertext even when they have ever collected a huge number of (plaintext/ciphertext) pairs.
(2) Using the encryption method of sequential-logic style, due to adopting a feedback mechanism, the generated subsequent ciphertext blocks will vary according to the contents of previous plaintext blocks. This greatly increases the difficulty of illegal decryption.
(3) The WEBDR in its message encryption (decryption) stage only invokes three exclusive OR (XOR) operations, while the AES calls this operation a total of 176 times for each of its message encryption and decryption processes.
The rest of this article is structured as follows. In Section 2, we briefly describe the related studies of this paper. Section 3 introduces the WEBDR. In Section 4, we analyze the security level of the WEBDR. Simulations and performance of the WEBDR are demonstrated and evaluated in Section 5. Section 6 summarizes this study and overviews our future research.
2 Related Studies and Background
In this section, the AES is first described. Security challenges in cloud systems and their data delivery are also discussed.
AES as a standard block cipher technique may have different block/key sizes, i.e., 128, 192, or 256 bits [8]. The corresponding numbers of rounds on the data encryption are 10, 12, and 14, respectively, on a 4 × 4-byte matrix (also called state, denoted by M). The given plaintext block is the initial value.
Giving its 10-round AES encryption as an example. A round has four operations, including SubBytes, ShiftRows, MixColumns, and AddRoundKey. But in the 0th round, i.e., the initial round, only AddRoundKey is executed. The last round performs SubBytes, ShiftRows, and AddRoundKey, skipping the MixColumns. Each of the remaining 9 rounds (rounds 1–9) invokes the mentioned four operations. The SubBytes operation substitutes each byte of the state M with the help of the S-Box; the ShiftRows rotates the last three rows, i.e., rotating the ith row a total of i times, i = 2,3,4; the MixColumns multiplies the columns of M with a polynomial function c(x); the AddRoundKey exclusive ORs (XORs) M with the round sub-key [8].
In 2002, the government of the United States (U.S.) adopted the AES as the security standard since it is the most secure encryption method at that time. However, Diehl [9] analyzed a cache attack on the AES, and [10] presented that a biclique attack has been successfully applied to attack AES [8,11] introduced different types of AES attacks, meaning that the AES will be solved soon, or at least, it is not really secure.
2.2 Data Security and Encryption
Today, cloud and Internet of Things (IoTs) systems are two popular applications in the world. Their data securities are essential before these applications can be successfully applied to the world. Reference [12] defined cloud security as the policies, services, controls, and technologies that prevent cloud data, infrastructure, and applications from threats. 7 challenges are also proposed. Among them, Granular Privilege and Key Management are concerned with privilege and cryptography keys. In reference [13], cloud security refers to a broad set of techniques and control methods used to protect data, applications, and cloud computing infrastructures. Because data archived in a cloud system can be accessed by using multiple client devices, when uploading data to the cloud, for security reasons, we need to consider who may access the data (e.g., the staff of the cloud system), and what applications and what methods will be, respectively, requested and utilized to access the data.
Bordak [14] mentioned that before cloud storage, plain-text data can be encrypted to differentiate the ability to save data from the ability to retrieve it. So, it would be better if the encryption key is securely protected to ensure that only authorized users can decrypt data.
Musa et al. [15] enforced their symmetric key encryption to protect a file locally on the client side before uploading it to the cloud system and the file is decrypted after it is downloaded on the client side using the key produced during encryption. Keys are generated by different algorithms, thus offering better security levels and enhanced system performance for large files.
Reis et al. [16] said that cryptography for cloud applications relies on both client-side and server-side cryptographies. The AES-256 in Cipher Block Chain (CBC) mode is employed to encrypt their healthcare data. Client-side cryptography encrypts data at the user’s device before sending data to the cloud storage, aiming to ensure user-data privacy and security. Server-side encrypts data before storage, i.e., inside the cloud system, for the reason that encrypts data, saves data, and manages keys at the same location. Of course, before these activities, the ciphertext sent by users should be decrypted first.
Banuelos [17] mentioned that users often utilize integers as keys by invoking a pseudo-random number generator or random-number generator. Sometimes, strings comprising numbers and letters are adopted. Also, a longer key is required, because longer keys consume a longer time to crack. The author also presented that SkyFlow, a data privacy vault company, uses a granular method to encryption keys that conveys a master key named a Key Encryption Key (KEK) and Data Encryption Keys (DEKs). Users may use Amazon Web Services Key Management Service (AWS KMS), Skyflow Key Management, or a bring-your-own-key (BYOK) technique to administrate KEK. But their data stored in the company’s vault is still encrypted by using DEKs.
Reference [18] described that an IoT security solution is required for business. Without security, businesses can be vulnerable to hacks and data breaches, making private information exploited and the public which will threaten the reputation and well-being of these corporations/companies.
Schacht et al. [19] evaluated 5 million Open Pretty-Good-Privacy (OpenPGP) keys with the algorithms utilized and internal parameters selected when establishing connections to third-party software. The authors analyzed the properties of keys and the trends of OpenPGP usage in the passing two decades, providing an internal look at OpenPGP and the adoption of public key cryptography. Looking at the details of the keys over time can make us recommend key features that affect real-world use. The analyses of OpenPGP keys give users a way to determine the time duration for changing the default settings of software packets.
Roundy [20] presented that IoT security risks were rising and stated the challenges listed in Verizon Mobile Security Index 2021 for mirroring mobile to the IoT environment. The author proposed a 6-step procedure to better IoT security. The last step is encrypting user and application data, aiming to protect the data from malicious actors. Without cryptography, an organization may face sensitive data leakage, reputational damage, and penalties.
Yang et al. [21] proposed an algorithm by exploiting encrypted packets and modeling network traffic to uncover stepping-stone statements/intrusions. The software tool used is OpenSSH which comprises n paths between Host 0 and Host 1. Each path has its cryptography key under the assumption that Host 0 acts as an intruder, and Host 1 plays the role of a victim. When a path is built, an encryption key is given. Authors claimed that the algorithm demonstrates better performance when detecting intruders’ both-side chaff attacks. However, it is better if the keys can be created with a secure approach.
Nowaczewski et al. [22] predicted that Customer Edge Switching (CES) would be used in 5G networks. They described the CES and explained how it works with Domain Name System (DNS). The possible attack models were also discussed. Currently, DNSs lack encryption/authentication. Hackers can exploit the system through man-in-the-middle attacks. They also extend CES’s implementation to fix this gap by adding DNSCrypt and DNSSEC functionalities. Their experimental results show that most attacks can be effectively detected by the proposed countermeasures. However, it would be better if the details of cryptography can be presented.
2.3 Three Working Models of Data Encryption
For those systems requesting high-security levels for their data transmission, three data transmission modes can be considered. Mode 1 is encrypting files transmitted between a user and a base station (BS) or a cloud with a channel key established to ensure their point-to-point security [23,24]. With mode 2, data is saved in client devices before its delivery, i.e., data is encrypted before transmission [25]. Therefore, a password given by the user is processed to generate a password key with which to encrypt/decrypt data files. Mode 3 adopts Proxy-based encryption methods to secure archived data. For some existing software or applications with no encryption functions, data can be encrypted by proxy servers [26] before transmission. Our opinion is that the WEBDR can enhance the security and performance of modes 1 and 2, particularly for those medium and large-size files.
Chakravarthy et al. [27] proposed a system named digital signature algorithm (DSA) which works together with deep packet inspection (DPI), known as the DSA-DPI model, to detect and prevent Distributed Denial of Service (DDoS) attacks. DDoS is an attack that overloads Central Process Units (CPUs) of the firewall and other network components and/or consumes their network bandwidths. The proposed system also provides preventive warnings on infrastructure before the malware attack. However, this system does not discuss how to protect, e.g., encrypt/decrypt, data itself. Digital signatures are one kind of anomaly-based detection scheme. Often a signature-based approach is required. DPI is often a function of firewalls. However, packet filtering often consumes a longer checking time.
Chiu et al. [28] proposed a network autonomous security system, named Detection and Defense of Denial of Service (DoS)/DDoS on 5G (DDD5G) which analyzes 5G network traffics and determines whether a protected system is under DoS/DDoS attack or not by using Shannon entropy (SE) and/or a mixed model. The latter mixes Shannon entropy and Cumulative Sum Algorithm (CUSUM) to further enhance a system’s security level. Shannon entropy adopts entropy derived from normal traffic at specific time intervals as the threshold and compares it with the entropies of other time intervals, denoted by T, to detect whether there are intrusions and attacks in T or not, while the CUSUM collects traffic and checks to see whether it exceeds the predefined thresholds or not to determine if this system is under attack. Authors claimed that a mixed-mode approach can effectively detect DDoS. However, with the two-stage detection approach, the detection time may be long, i.e., unable to detect attacks in a real-time manner.
Tsai et al. [29] proposed a Two-stage High-efficiency Long Range Wide Area Network (LoRaWAN) encryption key Update Scheme (THUS for short) for changing LoRaWAN’s session keys and root keys in an efficient and secure approach. The THUS comprises two stages, i.e., the Root Key Update (RKU) and the Session Key Update (SKU), and with different update periods, the security levels of RKU and SKU are higher than those of normal LoRaWAN specifications. A modified AES cryptography process is also adopted in the THUS to improve the THUS’s security level. According to the authors’ security analyses, the THUS can effectively protect important parameters in its key update stages, and satisfies the requirements of integrity mutual authentication, and confidentiality. Moreover, The THUS can further resist replay and eavesdropping attacks. However, THUS procedures can only be applied to LoRaWAN since the mechanism is limited to LoRaWAN, i.e., join-server, end-device, and network server. Also, when a sender generates a new D-box, it needs to deliver it (of course, encrypting it) to his/her target site. Otherwise, the target site does not know how to solve the receiving message, thus increasing the processing costs.
Khan et al. [30] stated that traditional authentication protocols are vulnerable in the quantum computing era. Therefore, they presented an authentication protocol according to the lattice technique for public cloud environments to prevent quantum attacks and avoid all known typical attacks. This protocol provably secures the protected systems with the Real-Or-Random (ROR) model. Their simulation results showed that this protocol is lightweight compared with some existing lattice-based authentication protocols. Their comparative analyses also demonstrated that this protocol is quite appropriate to be implemented in quantum-based environments. However, this scheme is developed for authentication, instead of encrypting/decrypting transmitted data.
Khalaf et al. [31] presented that hackers may send malicious inputs to confuse a web application. The purpose is to access or disable the application’s back end. The authors claimed that Cross-site scripting (XSS) and Structured Query Language (SQL) Injection Attacks (SQLIAs) are frequently launched. They then developed an input validation mechanism to check and evaluate for program codes and also developed a script whitelisting interception layer that is a part of the browser’s JavaScript engine. The SQLIA can be detected and the XSS attack is resolved with the approach of input verification and script whitelisting by using pushdown automatons. However, this system only focuses on SQLIA, XSS, and buffer overflow.
Yang et al. [32,33] described that Age-of-information (AoI) as an indicator reflects the freshness of data during the communication stage and Unmanned Aerial Vehicles (UAVs) play very important roles in Mobile Edge Computing Networks (MECN). They tried to solve the Channel Access Attack (CAA) problem of AoI-oriented channel access from game-theory viewpoints. A system model with active probability is first built to acquire a MECN-based AoI indicator under CAA attacks. Next, they proposed the AoI-based channel access optimization problem by using Ordinary Potential Game (OPG). At last, a learning algorithm named Distributed Channel Access Strategy Determination (DCASD) is presented to choose the channel access strategies. The experiments given different parameters to enhance the performance of the algorithm are conducted as compared with some state-of-the-art systems. But the proposed scheme is not applied to encrypt/decrypt data. Further, readers may like to know how attackers access the available channels to intrude on sensor nodes. How to implement the proposed approach with Carrier Sense Multiple Access (CSMA) families? How to work with IEEE 802.11 ax/be? It would be better if authors can deeply describe these.
The WEBDR dynamically hides ciphertext in a wrapped cipher file, aiming to hide the right position of ciphertext. Thus, it is not easy for hackers to collect a huge amount of effective (plaintext, ciphertext) pairs with which to break the system.
All parameters and operators adopted by the WEBDR are listed and defined below:
A. Parameters
Parameters used are as follows:
1.
2.
3.
4.
5.
6.
7.
8.
9.
10.
11.
12.
13.
14.
15.
16.
17.
18. Plaintext blocks:
19. Ciphertext blocks:
B. Operators
The operators employed and their functions are defined as follows:
1. XOR, denoted by
Encrypting plaintext p to ciphertext c with key k, i.e.,
Decrypting c to p with k, i.e.,
2. Binary adder [7]: +2
Encrypting plaintext p to ciphertext c with key k, i.e.,
Decrypting c to p with k, i.e.,
3. Rotate-Equivalence operator:
Encrypting plaintext pi to ciphertext ci with key k, i.e.,
Decrypting ci to pi with k, i.e.,
4. Three-dimensional operation: the operation encrypting a message by using encryption keys and three fundamental operators [1], i.e.,
5. Modulus operator: mod.
c = p mod n, where n is a positive integer.
6.
7.
8.
C. Accumulated shifting substitution
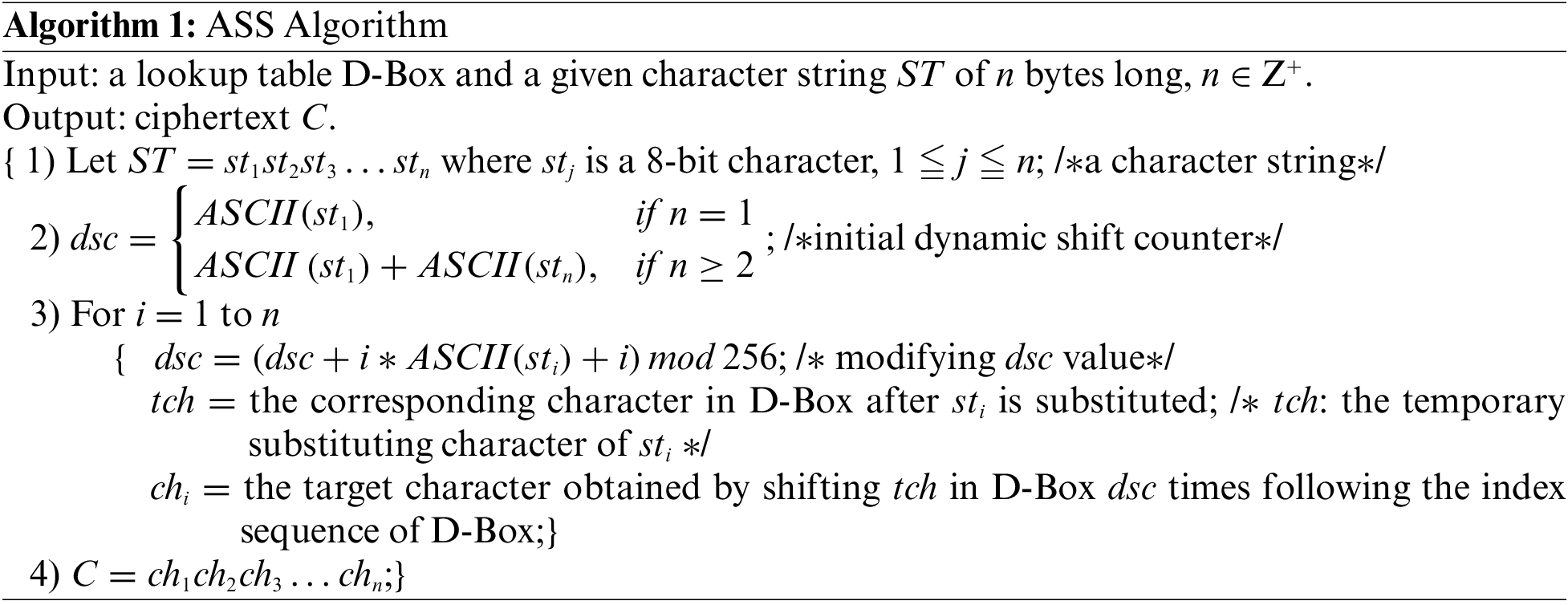
In the AES, the SubBytes is a mapping/substitution operation following the content of a given lookup table, i.e., a substitution box (S-Box). Basically, this mapping is a combinatorial-logic style encryption. The substring X in bytes appears at different locations in the plaintext will produce the same cipher substring S(X), consequently decreasing its security level since the mapping from X to S(X) is fixed, rather than a one-to-many mapping.
Next, the Accumulated Shifting Substitution algorithm (ASS), i.e., Algorithm 1, defined below is a sequential-logic style encryption mechanism which encrypts a plaintext into an irreversible ciphertext. The same substring Xs at different locations of the plaintext will be mapped to different cipher substrings. In other words, this is a one-to-many relationship, aiming to significantly enhance the security level of ciphertext.
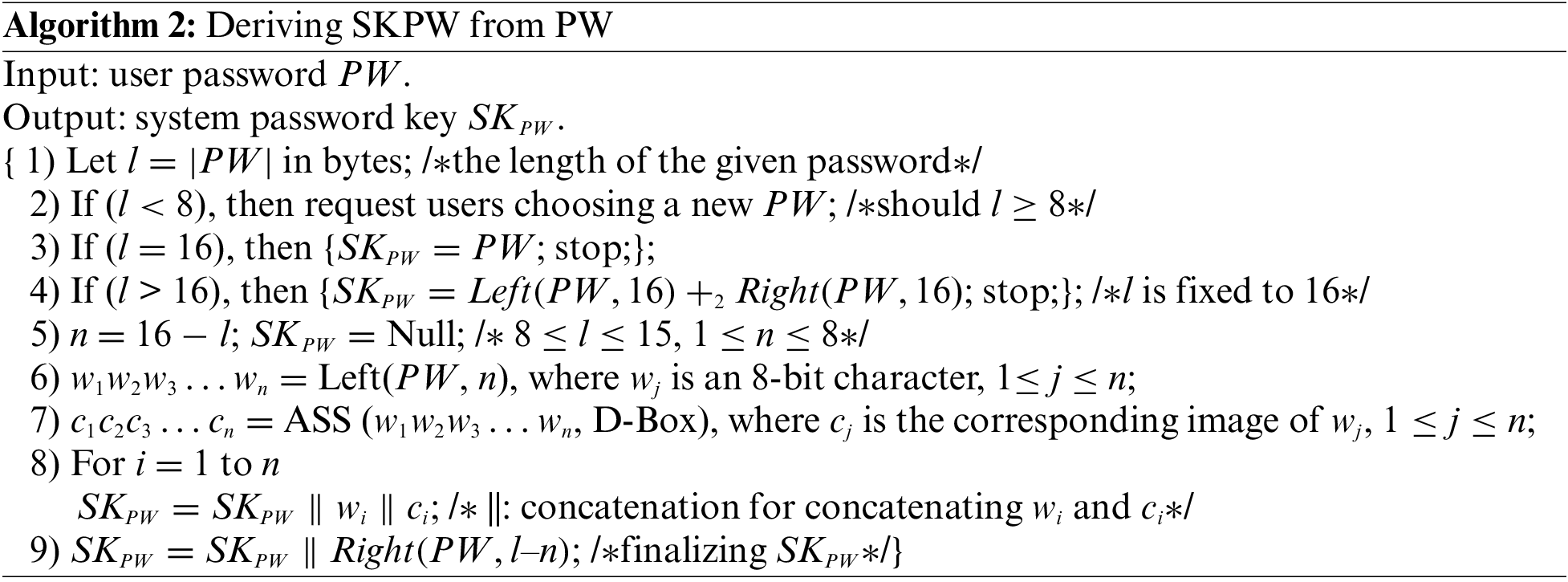
In the WEBDR, SKPW is the initial key. Its content significantly affects the security level of the WEBDR. To generate SKPW, we expand PW following three rules:
(1) The original content of PW is preserved;
(2) The code expanded is generated based on the original content of PW;
(3) When the same character repeatedly appears in PW, the expanded codes varies. The algorithm deriving SKPW from PW is shown in Algorithm 2.
In the WEBDR, before data encryption, there is an initial process used to generate system sub-keys
A. Initial process
The initial process of the WEBDR is shown below:
1. A string I, inputted by user, may be PW or SKCH;
2. If |I|
then {derive SK0 from I by invoking Algorithm 2;}
else SK0 = I;
3. Producing a random number RN and let IV= RN;
4.
5. Deriving
6.
7. Deriving SK3 from SK2 by invoking Algorithm 1, i.e., SK3 = ASS(SK2, D-Box);
8.
9.
Producing Δ1l, 3 ≤ Δ1l ≤ 1024 where
B. Message encryption
Message encryption has four steps:
Step 1: Producing
1. Producing the 0th random encryption key
2. Fetching CPU time with which to produce current time key
3. Yielding the random encryption key
4. Encrypting
Step 2: Producing ciphertext and
1. Let
2.
3. For plaintext block
4.
Step 3: Yielding
1. Yielding a random encryption key
2. Fetching CPU time with which to produce a system current time key
3.
t(0) = REK1;
4. For i = 1 to n1+ n2
{
5.
Step 4: Concatenating IV, PRS1, CREK, Ciphertext and PRS2 sequentially to produce the wrapped ciphertext file, the layout of which is illustrated in Fig. 1.
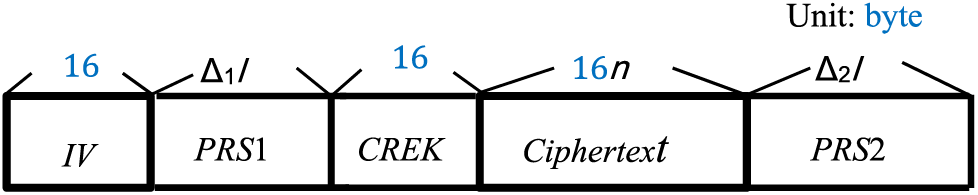
Figure 1: The layout of a wrapped ciphertext file
C. Message decryption
The decryption process is shown below:
1. Identifying the exact position of IV from the very beginning of the wrapped ciphertext file, and deleting it from the file;
2. Invoking the initial process to generate
3. Deleting
4. Identifying the exact position of
5.
Decrypting
6.
7. According to
n = |Ciphertext|/
8. For i = 1 to n
9. Output the plaintext P1P2…Pn.
We analyze security of the WEBDR’s working environment on operation mode 1 and mode 2 stated above, containing the securities of system sub-keys
In the WEBDR, the system sub-keys
Claimed 1:
When the WEBDR worked on operation mode 1 or mode 2, the generated system sub-keys
Proof: In operation mode 1 or mode 2, SK0 is defined as
About the first approach, in Eq. (3),
For the second approach,
For the third approach, hackers may break Eqs. (6) to (9) and the wrapped ciphertext file construction by employing brute-force attacks. In mode 1 or mode 2, without knowing plaintext, hackers cannot launch chosen-plaintext attacks and known-plaintext attacks. They can only collect and analyze wrapped ciphertext files. Even though hackers have collected a huge amount of wrapped ciphertext files encrypted by
Furthermore, the WEBDR generates a random key REK for each plaintext P. Each time when the plaintext encryption process is executed, different
Next, even hackers correctly guesses the exact location of the ciphertext and obtain
From the analyses above, we dare to say that in operation mode 1 or mode 2, the generated system sub-keys
The key point for solving the wrapped ciphertext files is acquiring
Claimed 2:
In operation mode 1 or 2,
Proof: Besides a blind guess, there are only two approaches for hackers to solve the value of
With the first approach, in operation mode 1, data transmitted between a user and a base station (or the cloud) is encrypted, i.e.,
According to Claimed 1,
By using the second approach, hackers may try to analyze the wrapped ciphertext file format with brute-force attacks. But, in operation mode 1 or mode 2, they cannot solve the file by employing chosen-plaintext attacks or known-plaintext attacks because they are unable to solve
In addition, the ciphertext is placed between
4.3 Security on Random Encryption Key REK
Since the dynamic random key REK is used to encrypt a plaintext file, it requires a relatively high level of security. In Eq. (5), i.e.,
Theorem 1:
In operation mode 1 or 2, if the dynamic random encryption key
Proof: To break
Firstly, in operation mode 1 or 2, from previous analyses, we know that
Secondly, in operation mode 1 or mode 2, hackers are unable to successfully crack the WEBDR by submitting chosen-plaintext attacks and known-plaintext attacks. They can only crack the system by analyzing the wrapped ciphertext files collected. But without the values of
On the other hand, hackers may somehow accurately guess where the ciphertext block
Therefore, the variables
Thirdly, without knowing the values of
4.4 Security on a Wrapped Ciphertext File
The ciphertext shown in Fig. 1 is wrapped by
Assume that hackers, by some method, correctly retrieve the ciphertext from the wrapped ciphertext file. Theorem 2 proves that the plaintext is secure.
Theorem 2:
Let
Proof: Eq. (11), i.e.,
4.6 Security on the WEBDR against Eavesdropping Attacks
In operation mode 1 or 2, active brute-force attacks, like the chosen-plaintext attack and known-plaintext attack, cannot successfully crack a system protected by the WEBDR. Therefore, passive eavesdropping attacks will be the main method used to break the WEBDR by hackers. Now we would like to prove that the WEBDR can effectively defend against eavesdropping attacks.
In operation mode 1, before data files are transmitted between UE and a base station (or a cloud system), both sides of the connection have already owned their channel key, i.e.,
In operation mode 2, even if a wrapped ciphertext file is stolen. As mentioned above, hackers cannot figure out the right position of the ciphertext, and then crack the wrapped ciphertext file. Nevertheless, even though many wrapped ciphertext files are encrypted by using the same
5 Performance Analyses and Improvements
The performance of encrypting and decrypting data blocks mainly depends upon the number of operating instructions. Table 1 lists the number of operations required by the WEBDR and AES when they encrypt/decrypt data blocks that are 128 bits long.
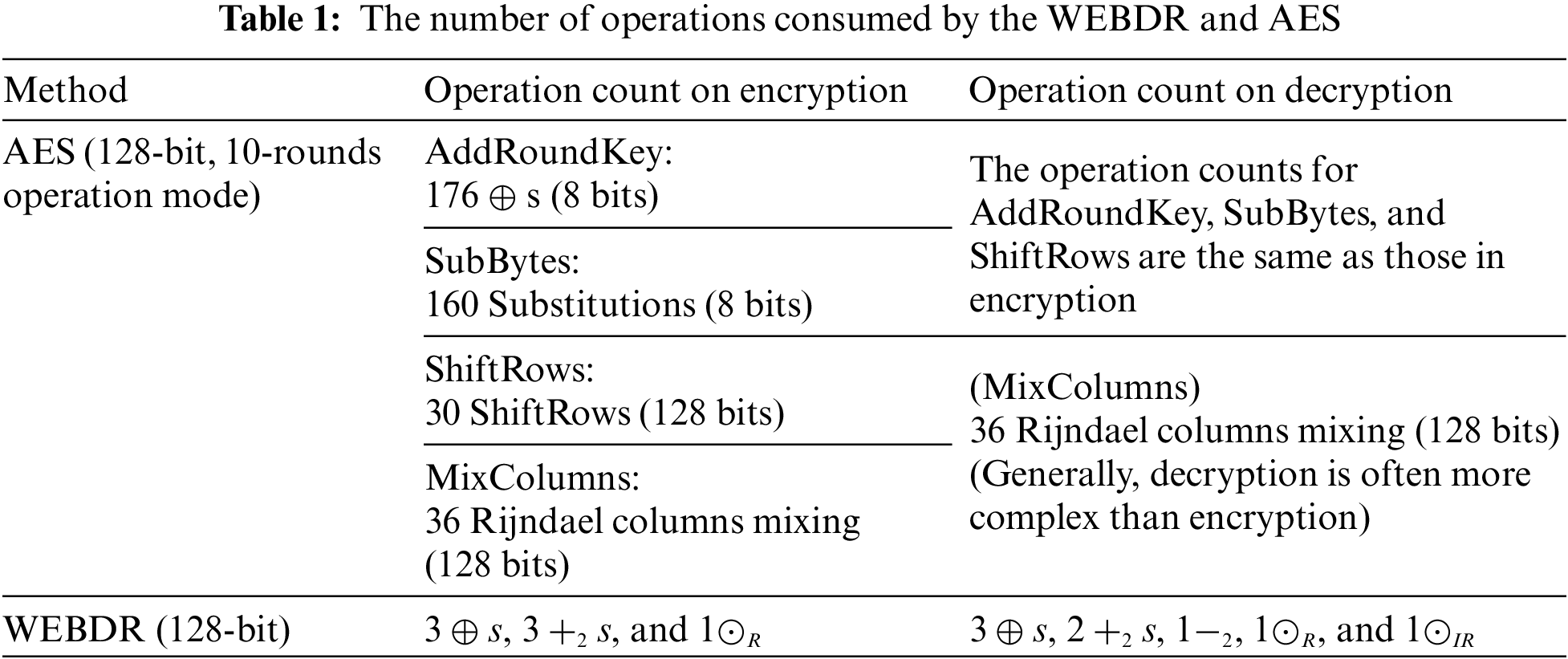
Due to the natural-randomness property, it is difficult for most cryptographic algorithms to theoretically compare time complexity. To demonstrate the better performance of the WEBDR than the AES, we conduct several experiments with test scenarios that encrypt/decrypt data blocks of different sizes from 1 KBs to billion KBs. In each test case, we calculate the average time consumed by each step of pre-processing procedures and the encryption/decryption step by million times of executions.
The experimental results by employing devices of different specifications are shown in Table 2 which shows that the cost of encrypting (decrypting) a plaintext (ciphertext) block by the AES is 6–8 times higher than that of encrypting (decrypting) a plaintext (ciphertext) block by the WEBDR in average. Since before encryption, the AES needs to execute Key-Expansion, i.e., generating round-keys by manipulating its cipher-key. Similarly, before encryption, the WEBDR has to perform preprocessing, including initial process, Step 1 of the encryption process and the generation of
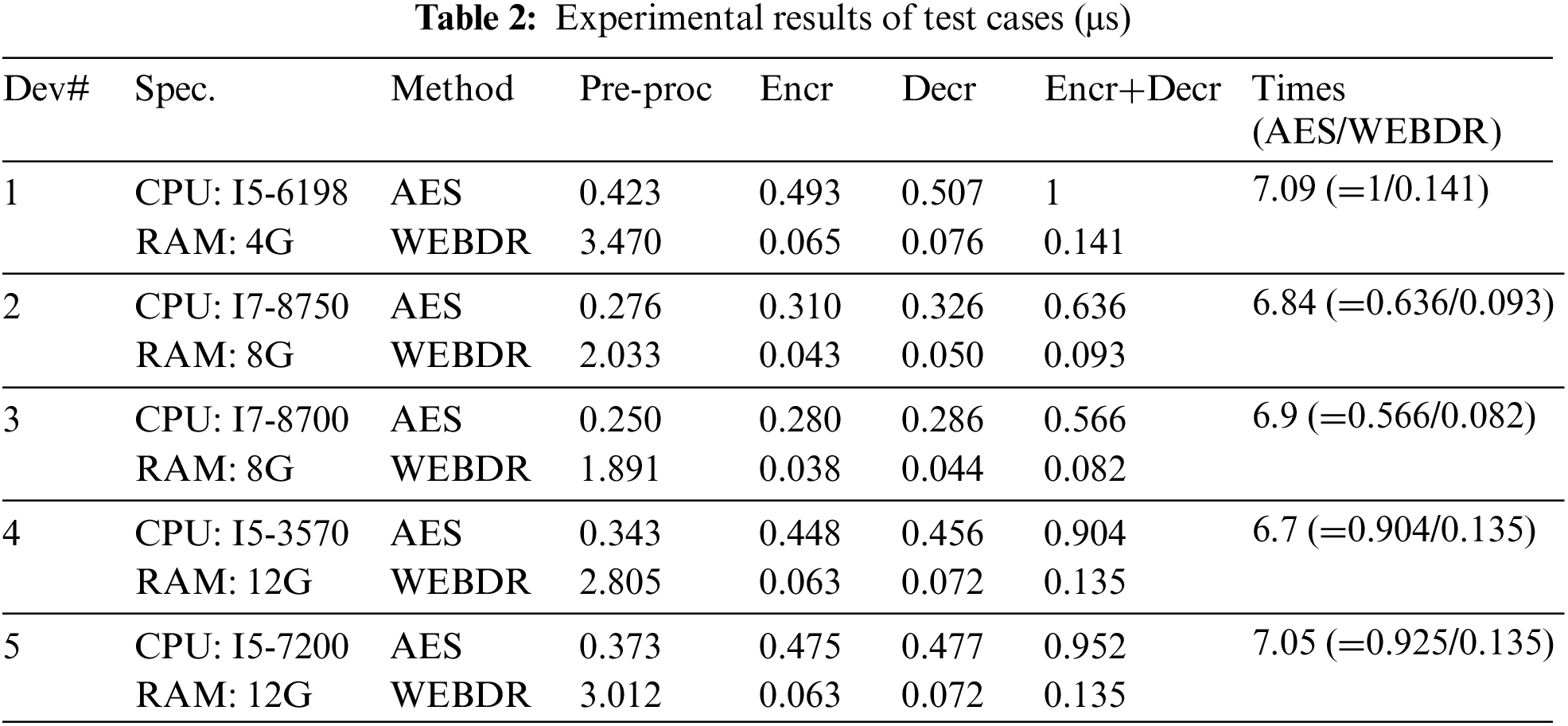
To produce a wrapped ciphertext file, the WEBDR should execute post-processing procedures, i.e., the generation of PRS1 and PRS2, in Step 3 of the encryption process. The costs of extra sub-operations required by the AES and WEBDR are also listed in Table 2. The costs for pre/post-processing in the decryption process of the WEBDR are lower than that in its encryption process since the decryption does not need to generate PRS1 and PRS2, only identifying their lengths. If a plaintext file has n plaintext blocks, each of which is 16 bytes long, the theoretical encryption/decryption costs of the WEBDR and AES can be derived from Table 2.
(1) The AES (for Device# = 5)
The encryption cost = (cost for generating sub-keys) + (cost for encrypting a plaintext block) * n
(2) The WEBDR (for Device# = 5)
The encryption cost = (cost of pre/post-processing) + (cost of encrypting a plaintext block) * n
Basically, most of the 5th-generation (5G) applications are data intensive and at least 100 kb of data size. As shown in Table 2, the performance of the WEBDR is around 6.7–7.09 times faster than that of the AES.
The cost of wrapping n-block ciphertext, denoted by CC, in a wrapped file is
where 130 =
6 Conclusions and Future Works
In this study, the WEBDR is developed by using a randomly wrapped feedback approach based on user passwords or channel keys, which together with IV construct high security wrapped ciphertext files with high performance. When receiving a plaintext at different time points, the dynamic random encryption approach, which adopts current time keys and random keys, will produce different wrapped ciphertext files of different cipher texts and lengths, consequently highly improving the security level of transmitted ciphertext. Our theoretical analyses demonstrate that the WEBDR has achieved practical security in transmitting wireless data and encrypting personal files.
Theorems 1 and 2 prove the security level that the proposed scheme can achieve, i.e., the probability with which to obtain REK from an intercepted wrapped ciphertext file is
According to reference [34], the download speed of a 5G system is about 10 times that of a 4th generation (4G) network, and high-speed communication has been widely requested by users, high-performance transmission is always desired, while keeping the practical security.
In the future, we will continue developing a faster encryption and decryption approach and then apply it to image cryptography [35]. Also, users may forget their passwords. Then they have trouble decrypting their ciphertexts to plaintexts. Therefore, we need a forgotten-password-recovery mechanism following which users can recover their original passwords, and then decrypt the wrapped ciphertext files. These constitute our future studies.
Acknowledgement: We would like to thank reviewers who gave us many valuable comments and suggestions with which we can then significantly improve the quality of our manuscript.
Funding Statement: This work is financially supported in part by Ministry of Science and Technology (MOST), Taiwan under the Grant MOST 109-2221-E-029-017-MY2.
Author Contributions: Study concepts and system design: Yi-Li Huang and Fang-Yie Leu; Data collection and preparation: Ruey-Kai Sheu and Chi-Jan Huang; Draft manuscript preparation: Yi-Li Huang and Fang-Yie Leu; Analysis and interpretation of results: Ruey-Kai Sheu and Jung-Chun Liu; Theorem derivation and proofs: Yi-Li Huang and Jung-Chun Liu.
Availability of Data and Materials: A part of the data adopted in this study is articles randomly collected from the Internet. The remaining part is a company’s personnel data. For privacy consideration, the personnel data cannot be accessed without this company’s permission.
Conflicts of Interest: The authors declare that they have no conflicts of interest to report regarding the present study.
References
1. Y. L. Huang, C. R. Dai, F. Y. Leu and I. You, “A secure data encryption method employing a sequential-logic style mechanism for a cloud system,” International Journal of Web and Grid Services, vol. 11, no. 1, pp. 102–124, 2015. [Google Scholar]
2. Kasperski, “Brute force attack: Definition and examples,” 2023. [Online]. Available: https://www.kaspersky.com/resource-center/definitions/brute-force-attack [Google Scholar]
3. Fortinet, “What is a brute force attack?,” 2023. [Online]. Available: https://www.fortinet.com/resources/cyberglossary/brute-force-attack [Google Scholar]
4. M. Al-Mhiqani, R. Ahmad, Z. Z. Abidin, K. H. Abdulkareem, M. A. Mohammed et al., “A new intelligent multilayer framework for insider threat detection,” Computers & Electrical Engineering, vol. 97, no. 1, pp. 107597, 2022. [Google Scholar]
5. Wikipedia, “The EFF DES cracker,” 2023. [Online]. Available: http://en.wikipedia.org/wiki/EFF_DES_cracker [Google Scholar]
6. M. Kirschenbaum, “A practical guide for cracking AES-128 encrypted firmware updates,” Hypoxic Extreme Electronics, 2020. https://gethypoxic.com/blogs/technical/a-practical-guide-for-cracking-aes-128-encrypted-firmware-updates [Google Scholar]
7. Y. L. Huang, F. Y. Leu, I. You, H. C. Chen, C. S. Liaw et al., “Random cladding with feedback mechanism for encrypting mobile messages,” in Proc. INFOCOM WKSHPS, San Francisco, CA, USA, pp. 970–975, 2016. [Google Scholar]
8. Wikipedia, “Advanced encryption standard,” 2023. [Online]. Available: https://en.wikipedia.org/wiki/Advanced_Encryption_Standard [Google Scholar]
9. W. Diehl, “Attack on AES implementation exploiting publicly-visible partial result,” Cryptology ePrint Archive, 2017. [Google Scholar]
10. Wikipedia, “Biclique attack,” 2023. [Online]. Available: https://en.wikipedia.org/wiki/Biclique_attack [Google Scholar]
11. Tutorialspoint, “What are the types of Cryptanalysis Attacks on AES in information security?,” 2023. [Online]. Available: https://www.tutorialspoint.com/what-are-the-types-of-cryptanalysis-attacks-on-aes-in-information-security [Google Scholar]
12. Checkpoint, “What is cloud security?,” 2022. [Online]. Available: https://www.checkpoint.com/cyber-hub/cloud-security/what-is-cloud-security/ [Google Scholar]
13. Wikipedia, “Cloud security,” 2023. [Online]. Available: http://en.wikipedia.org/wiki/Cloud_computing_security [Google Scholar]
14. L. Bordak, “Cloud computing security,” in Proc. of ICETA, Startfytf Smokovec, Slovakia, pp. 87–92, 2019. [Google Scholar]
15. A. Musa and A. Mahmood, “Client-side cryptography based security for cloud computing system,” in Proc. of ICAIS, Tamil Nadu, India, pp. 594–600, 2021. [Google Scholar]
16. L. H. A. Reis, M. T. de Oliveira, J. Bowden, D. Krefting, S. D. Olabarriaga et al., “Cryptography on untrustworthy cloud storage for healthcare applications: A performance analysis,” in Proc. of SBESC, Online, pp. 1–8, 2021. [Google Scholar]
17. O. Banuelos, “Encryption key management and its role in modern data privacy,” SkyFlow, 2022. [Online]. Available: https://www.skyflow.com/post/encryption-key-management-and-its-role-in-modern-data-privacy?utm_source=google&utm_medium=ppc&utm_campaign=blog&utm_term=encryption%20key&utm_campaign=All+Tiers:+%27How+To%27+Campaign&utm_source=adwords&utm_medium=ppc&hsa_acc=6575335991&hsa_cam=13968847646&hsa_grp=141732157609&hsa_ad=610758177074&hsa_src=s&hsa_tgt=kwd-297166611545&hsa_kw=encryption%20key&hsa_mt=b&hsa_net=adwords&hsa_ver=3&gclid=CjwKCAjwg5uZBhATEiwAhhRLHodD_Y57v3jHwkTHdCbasltaSHnAl5y5g_GVnzwmQYxp6uMUvrKUkxoCDJYQAvD_BwE [Google Scholar]
18. Software AG, “What is an IoT security solution?,” 2023. [Online]. Available: https://www.softwareag.com/en_corporate/resources/what-is/iot-security-solution.html [Google Scholar]
19. B. Schacht and P. Kieseberg, “An analysis of 5 million OpenPGP keys,” Journal of Wireless Mobile Networks, Ubiquitous Computing, and Dependable Applications (JoWUA), vol. 11, no. 3, pp. 107–140, 2020. [Google Scholar]
20. J. Roundy, “IoT security: IoT device security challenges and solutions,” 2023. [Online]. Available: https://www.verizon.com/business/resources/articles/iot-device-security-challenges-and-solutions/ [Google Scholar]
21. J. Yang, L. Wang and S. Shakya, “Modelling network traffic and exploiting encrypted packets to detect stepping-stone intrusions,” Journal of Internet Services and Information Security (JISIS), vol. 12, no. 1, pp. 2–25, 2022. [Google Scholar]
22. S. Nowaczewski and W. Mazurczyk, “Searching future Internet and 5G using customer edge switching using DNSCrypt and DNSSec,” Journal of Wireless Mobile Networks, Ubiquitous Computing, and Dependable Applications (JoWUA), vol. 11, no. 3, pp. 87–106, 2020. [Google Scholar]
23. Cloud Security Alliance (CSA“Cloud security alliance, top threats to cloud computing,” 2023. [Online]. Available: http://www.cloudsecurityalliance.org [Google Scholar]
24. F. Chen, K. Wu, W. Chen and Q. Zhang, “The research and implementation of the VPN gateway based on SSL,” in Proc. of ICCIS, Shiyang, China, pp. 1376–1379, 2013. [Google Scholar]
25. D. Clinton, “How website encryption works,” ENCRYPTION, 2023. [Online]. Available: https://www.freecodecamp.org/news/understanding-website-encryption/ [Google Scholar]
26. Wikipedia, “Proxy server,” 2023. [Online]. Available: http://zh.wikipedia.org/wiki/%E4%BB%A3%E7%90%86%E6%9C%8D%E5%8A%A1%E5%99%A8 [Google Scholar]
27. V. D. Chakravarthy, K. L. N. C. Prakash, K. Ramana and T. R. Gadekallu, “A novel DDOS attack detection and prevention using DSA-DPI method,” in Proc. of ICICC, Delhi, India, pp. 733–744, 2022. [Google Scholar]
28. S. Daneshgadeh, T. Ahmed, T. Kemmerich and N. Baykal, “Detection of DDoS attacks and flash events using shannon entropy, KOAD and mahalanobis distance,” in Proc. of ICIB, Thessaloniki, Greece, pp. 222–229, 2019. [Google Scholar]
29. K. L. Tsai, L. W. Chen, F. Y. Leu and C. T. Wu, “Two-stage high-efficiency encryption key update scheme for LoRaWAN based IoT environment,” Computers, Materials & Continua, vol. 73, no. 1, pp. 547–562, 2022. [Google Scholar]
30. N. Khan, J. Zhang, U. Intikhab, S. M. S. Pathan and H. Lim, “Lattice-based authentication scheme to prevent quantum attack in public cloud environment,” Computers, Materials & Continua, vol. 75, no. 1, pp. 35–49, 2023. [Google Scholar]
31. O. I. Khalaf, M. Sokiyna, Y. Alotaibi, A. Alsufyani and S. Alghamdi, “Web attack detection using the input validation method: DPDA theory,” Computers, Materials & Continua, vol. 68, no. 3, pp. 3167–3184, 2021. [Google Scholar]
32. Y. Yang, W. Wang, R. Xu, G. Srivastava, M. Alazab et al., “AoI optimization for UAV-aided MEC networks under channel access attacks: A game theoretic viewpoint,” in Proc. of ICC, Seoul, South Korea, pp. 1–6, 2022. [Google Scholar]
33. W. Wang, G. Srivastava, J. C. W. Lin, Y. Yang, M. Alazab et al., “Data freshness optimization under CAA in the UAV-Aided MECN: A potential game perspective,” IEEE Transactions on Intelligent Transportation Systems, pp. 1–10, 2022. https://doi.org/10.1109/TITS.2022.3167485 [Google Scholar] [CrossRef]
34. M. V. Nichita, P. Ciotîrnae, R. L. Luca and V. N. Petrescu, “5G propagation: Current solutions and future proposals,” in Proc. of ISETC, Timisoara, Romania, pp. 47–50, 2016. [Google Scholar]
35. E. Bashier and T. Ben Jabeur, “An efficient secure image encryption algorithm based on total shuffling, integer chaotic maps and median filter,” Journal of Internet Services and Information Security (JISIS), vol. 11, no. 2, pp. 64–79, 2021. [Google Scholar]
Cite This Article
 Copyright © 2023 The Author(s). Published by Tech Science Press.
Copyright © 2023 The Author(s). Published by Tech Science Press.This work is licensed under a Creative Commons Attribution 4.0 International License , which permits unrestricted use, distribution, and reproduction in any medium, provided the original work is properly cited.


 Submit a Paper
Submit a Paper Propose a Special lssue
Propose a Special lssue View Full Text
View Full Text Download PDF
Download PDF Downloads
Downloads
 Citation Tools
Citation Tools