 Open Access
Open Access
ARTICLE
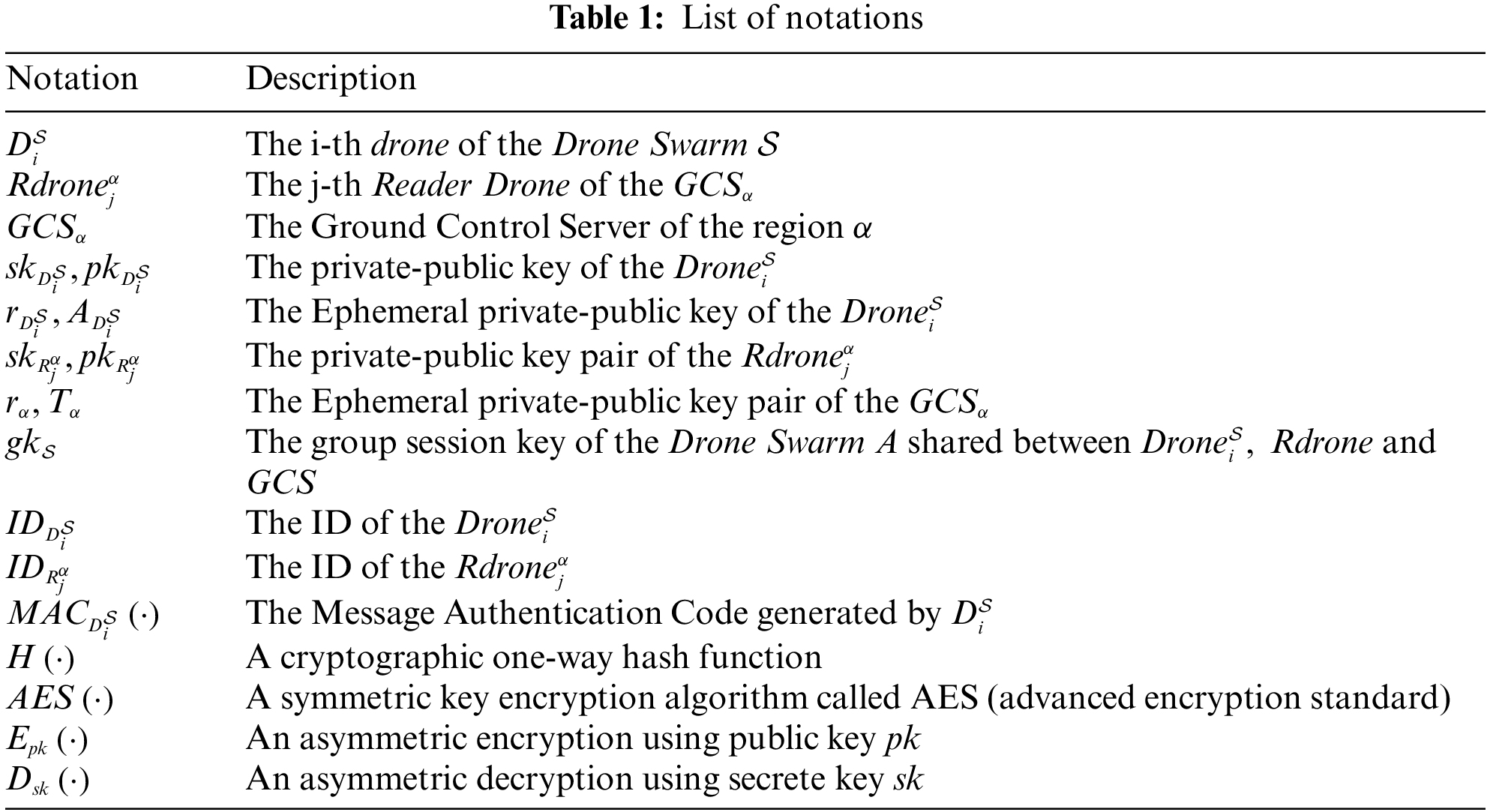
Efficient Remote Identification for Drone Swarms
1 The Department of Electronic & Electrical Engineering, Graduate School, Hanyang University, Ansan, Korea
2 School of Electrical Engineering, Hanyang University ERICA, Ansan, Korea
* Corresponding Author: Seung-Hyun Seo. Email:
(This article belongs to the Special Issue: Advances in Information Security Application)
Computers, Materials & Continua 2023, 76(3), 2937-2958. https://doi.org/10.32604/cmc.2023.039459
Received 31 January 2023; Accepted 17 April 2023; Issue published 08 October 2023
Abstract
With the advancement of unmanned aerial vehicle (UAV) technology, the market for drones and the cooperation of many drones are expanding. Drone swarms move together in multiple regions to perform their tasks. A Ground Control Server (GCS) located in each region identifies drone swarm members to prevent unauthorized drones from trespassing. Studies on drone identification have been actively conducted, but existing studies did not consider multiple drone identification environments. Thus, developing a secure and effective identification mechanism for drone swarms is necessary. We suggested a novel approach for the remote identification of drone swarms. For an efficient identification process between the drone swarm and the GCS, each Reader drone in the region collects the identification information of the drone swarm and submits it to the GCS for verification. The proposed identification protocol reduces the verification time for a drone swarm by utilizing batch verification to verify numerous drones in a drone swarm simultaneously. To prove the security and correctness of the proposed protocol, we conducted a formal security verification using ProVerif, an automatic cryptographic protocol verifier. We also implemented a non-flying drone swarm prototype using multiple Raspberry Pis to evaluate the proposed protocol’s computational overhead and effectiveness. We showed simulation results regarding various drone simulation scenarios.Keywords
Drone applications have recently expanded in fields such as agriculture, transportation, construction, and topographic exploration. As the number of studies in which Internet of Things (IoT) devices collaborate and perform tasks in groups increases [1–8], the development of drone swarms, in which multiple drones collaborate in large teams to accomplish a specific task or set of tasks, also has been actively pursued. The drone swarm can overcome the limitations of individual drones, which generally include constrained resources, such as battery life, flight time, and coverage area. In 2020, researchers at Imperial College London developed a new control system for drone swarms that allows drones to make decisions and adjust their behavior based on the behavior of other drones in the swarm [9]. The US Navy announced the successful test of a drone swarm that can protect ships and other vessels [10]. In 2021, Researchers at ETH Zurich developed a system that allows a drone swarm to work together to transport a heavy payload, such as a package or a piece of equipment, from one location to another [11]. These drone swarms are expected to be effectively used for a wide range of applications, such as search and rescue, mapping, military operations, and surveillance.
However, drone flight-related accidents such as invasion of personal privacy, access to no-fly zones, and drone crashes have also become frequent. In 2018, two unidentified drones appeared at Gatwick Airport in the UK, so the runway was shut down [12]. In 2019, two oil production facilities in Saudi Arabia were also bombed using drones [13]. As drone accident cases and illegal use increase, the need to accurately identify the source of drones has been raised. Currently, the authorities of each country, including the Federal Aviation Administration (FAA) [14] and the European Union Aviation Safety Agency (EASA) [15], and the Ministry of Land, Infrastructure, Transport and Tourism (MLIT) of Japan [16] are working to come up with rules on drone remote identification. “Digital License Plates” for drones are being considered a possible drone remote identification method.
Remote identification of drones would mean the drone’s functionality could provide information such as identification and location of the drones in flight to people on the ground or other airspace users. Identifying a drone and a drone swarm is essential for many reasons. One of the main reasons is safety. Suppose a drone swarm is operating in an area where there are other aircraft or people. In that case, it is crucial to identify the drones and track their movements to prevent collisions or other accidents. Another reason is to maintain security. Drones can potentially be used for malicious purposes such as espionage or smuggling. Identifying the drones in a swarm can help authorities to track and intercept them if they are being used for illegal activities. Remote identification makes it easier to distinguish between licensed users who comply with drone flight rules and potentially malicious users who pose security risks.
Furthermore, drones are not capable of long-distance flights with limited capacity batteries, so it is necessary to route to intermediate landing spots for long distances. The ground control server that monitors each landing spot base must quickly identify the drone that comes to the base station and verify its authenticity. In the case of drones that have passed unauthorized places, such as no-fly zones, tracking the travel path of the drones is necessary [17]. Identifying a drone swarm can also be helpful for managing and coordinating the drones. For example, suppose a swarm is being used for search and rescue operations. In that case, it is crucial to be able to identify each drone in order to direct them to specific areas or to retrieve data from them.
These reasons make it necessary to develop a remote identification system for drones, including drone swarms. There have been numerous works on drone identification and authentication methods [18–25], but only a few on authentication methods for drone swarms [26–30]. Also, there is still no effective method of identification for drone swarms. Unfortunately, it is challenging for the ground control server to recognize a drone swarm effectively. Developing a method to identify drone swarms before they perform tasks effectively should be ongoing. In this paper, we propose a remote identification protocol for efficiently identifying drone swarms and verifying their access authorization. Our protocol utilizes a Reader drone (
The gathered message is a grouping proof that is evidence to the ground control server (verifier) that the identities (IDs) of the authorized swarm drones were simultaneously in a range of the
In this section, we explain a remote identification rule and related works of drone swarm authentication protocol.
2.1 Remote Identification Rule
In December 2019, the US Federal Aviation Administration (FAA) issued guidelines for solving safety/security problems for unmanned aerial vehicles [14]. After that, from April 2021, the final rules for remote drone identification took effect and were implemented. The user must use the Standard Remote ID Drone or attach the Remote ID broadcast module to the drone. The FAA made it possible to identify and locate the ID of a drone in flight using the Remote ID. Some FAA-approved areas allow drones to operate without a Remote ID, but most areas require Remote IDs containing information about drones and control stations to comply with Remote ID rules.
According to the FAA, whether using a Standard Remote ID Drone or a remote ID broadcast module, the message elements must be broadcast from take-off to shut down. A Standard Remote ID Drone or a drone with a remote ID broadcast module must transmit the following message elements [14].
• A unique identifier for the drone
• The drone’s latitude, longitude, geometric altitude, and velocity
• An indication of the latitude, longitude, and geometric altitude of the control station (standard) of the take-off location (broadcast module)
• A time mark
• Emergency status (Standard Remote ID Drone only)
The European Union Aviation Safety Agency (EASA) announced operational procedures and rules according to specifications to identify drones in May 2019 and is making efforts to respond to the standardization of illegal drones [15]. The EASA is considering Direct Remote ID, a broadcast-type remote identification method, as a drone remote identification method. The EASA plans to use Direct Remote ID for the purpose of drone security. Related content is contained in UAS Regulation (EU) 2019/945 and 947, which addresses design and manufacturing requirements for drone systems in Europe and rules on drone operations. According to this rule, in the case of drones corresponding to Classes 5 and 6, it is mandatory to install Direct Remote ID. Before the operation of the system, the pilot is required to ensure that the Direct Remote ID system is active and up to date. Information that must be transmitted from Direct Remote ID includes operator registration information, drone-specific serial number, topographic drone location, flight guard, and pilot location or take-off location information.
The Ministry of Land, Infrastructure, Transport and Tourism (MLIT) [16] of Japan is planning to implement a drone registration rule on June 20, 2022. Drone users are required to attach a ‘Remote ID’ that transmits information such as registration number during drone flights. After June 2022, drones will be produced with a Remote ID attached.
2.2 ECC-Based IoT Edge Device Authentication Protocol
Several studies have recently been conducted on authentication protocols between IoT edge devices, such as drones, robots, and authentication servers in IoT environments [6–8]. The previous works utilized ECC (Elliptic Curve Cryptography)-based authentication for resource-constraint devices [7]. Rostampour et al. [6] proposed a new ECC-based authentication protocol for ensuring secure communication between cluster servers and IoT edge devices. The authors masked the embedded device’s unique identifier and used a random value to prevent a traceability attack. Kwon et al. [8] proposed mutual authentication and handover authentication for an unmanned aerial vehicle (UAV). A zone service provider in each region supports a handover process. Jain et al. [7] suggested a robot access control protocol by designing ECC-based mutual authentication between robots and cloud servers. The authors reduced the robot’s computation power and proved that their protocol is resistant to several attacks, such as a Man-in-the-middle attack and a forgery attack. However, existing authentication protocols are inefficient in terms of computational cost when verifying multiple devices’ identities, as they only consider the authentication of a single device.
2.3 Drone Swarm Authentication Protocol
Recently, as the need for drone swarms has increased, studies on drone swarms, such as drone swarm formation [33], drone swarm allocation [34], and drone swarm application [35–37], have been conducted. Since a drone swarm is a very recent development (within the last two to three years), there are few studies on drone swarm authentication or key distribution. Moreover, there have yet to be considered drone swarm identification. In this section, we introduce some examples of recent drone swarm authentication protocols. Ardin et al. [26,27] proposed a group authentication and handover solution for drone swarms in 2021. Their protocol allows a new drone to join an existing drone swarm by using a guard drone, but it does not take into account drones leaving the drone swarm. However, if drones inevitably leave the drone swarm, such as when drones fail or battery power is lost, the drone leaving process, such as establishing a new group key, must be considered.
Abdel-Malek et al. [28] proposed a distributed delegation-based authentication mechanism for overcoming drone resource limitations and scalability. The proposed method can reduce traffic overhead from the 5G core network. Moreover, when a failure or compromise to the leader drone occurs, a new leader drone can be assigned without interrupting the drone swarm communication. However, the PKI (Public Key Infrastructure)-based proxy signature solution requires significant computational overhead when authenticating many drones in the swarm. Han et al. [29] proposed an authentication protocol that enables mutual authentication between fog and edge without a ground station. The proposed method is effective against MITM (Man in the Middle Attack) attacks and replay attacks. Moreover, since it utilizes security functions with various hardware, it is more computationally efficient than the PKI-based approaches. However, it does not cover the compromised drone issue, and it requires special hardware. Han et al. [30] proposed a blockchain-based UAV swarm identity management model (B-UIM-M). The proposed method has advantages in UAV identity management, UAV identity authentication, scalability, and secure transmission of communication data. However, the blockchain operation causes a communication bottleneck between drones which are consensus nodes.
In this section, we describe the overall and adversary models of our proposed remote identification protocol for drone swarms.
The proposed model consists of five components: UAV Traffic Management (UTM), Base stations, Ground Control Servers (GCSs), Reader drones (

Figure 1: Overall system model
• UAV Traffic Management (UTM): The UTM is a system that manages the traffic of a drone swarm. The UTM is responsible for the management of drones throughout each region using base stations and GCSs. Before flying, the drone swarm should inform the flight route, including the list of the drone swarm ID, regions to visit, and flight time slots to the UTM. The UTM shares registered flight information with servers on the flight route.
• Base Station: The base station is a communication infrastructure to facilitate communication between entities in each region. The base station connects the wireless communication network and the entities such as
• Ground Control Server (GCS): The GCS in each region has the role of verifying the identification of drone swarms joining its region for access control. It receives flight-related information from the UTM before flying. For drone swarm verification, the server gets the collected drones’ authentication information from the
• Reader Drone (Rdrone): A
• Drone Swarm: A drone swarm is a group of drones that move and work together for a particular purpose, such as data collection and reconnaissance. It is assumed that each drone in the drone swarm has enough processing power to compute cryptographic operations such as symmetric and asymmetric encryption.
We assume that the drones used in the proposed protocol meet the FAA’s remote identification requirements. The drone controller creates several drones as a swarm and pre-registers the swarm’s movement path in the UTM. Following that, when the registered drone swarm moves along the registered route, a GCS is present in each region and performs remote identification of drones passing through the region. Through the group session key and remote ID, the GCS verifies that each drone in the drone swarm is a part of the drone swarm registered to fly in advance. The
The adversarial attackers in the proposed protocol can be classified as a malicious drone or a malicious drone swarm. A malicious drone may try to disguise itself as a member of a drone swarm attempting to access the area to gain access to the area he wishes to enter. A malicious drone swarm may attempt to access a location that has not previously registered with the UTM. Alternatively, a drone not previously registered may attempt to join the drone swarm. We assume that an attacker can listen in on the communication channel between the drone and the
• Impersonation attack: Malicious drones may attempt to impersonate members of a specific drone swarm. They may attempt to participate in the authentication process by generating fake IDs or keys while the
• Replay attack: A malicious drone or drone swarm can reuse information used to authenticate in the past without prior permission. A malicious drone can also attempt to access a location other than a UTM-registered route by using expired information.
• Eavesdropping attack: A malicious attacker may collect communication information between a drone swarm and a
4 Remote Identification Protocol for Drone Swarms
In this section, we propose a protocol for remote identification via a

Figure 2: Proposed protocol
In the Setup Phase, each drone of the drone swarm and the
• A controller establishes a drone swarm
• Each
• The
Drone swarms register their flight route with the UTM. Then, each drone in the drone swarm generates an ephemeral private-public pair for each region it will visit. The UTM shares drone swarm flight information with the GCS in each region, as well as generates and distributes the drone swarm’s group session keys. The detailed process is as follows.
- The
- A
- The UTM generates a random number which is used as a group session key
4.3 Remote ID Identification Phase
When a drone swarm enters the region, the
• A drone
• where H is the hash function,
• The
• If the
To the
• The
The
The

In the case of drones, sudden battery shortages or discharge can result in a falling situation. Furthermore, unexpected sensor failures can result in situations where the mission is not normally carried out, or environmental factors can cause deviations from the drone swarm. Because the drone that left at this time is no longer a member of the drone swarm, the group session key for the newly changed member of the drone swarm must be updated. The GCS updates the group session key and shares it with the drone swarm once it confirms that the members of the drone swarm have been changed through the batch verification step. The following are the detailed group session key update steps.
• A
• The
• The
• Each
5 Security Analysis and Formal Verification
In this section, we provide a security analysis of the proposed scheme. We also demonstrate the security of the proposed scheme through formal verification using ProVerif.
Resistance against impersonation attack: A malicious drone might pretend to be a member of one of the drone swarms. However, the malicious drone does not know the shared secret key
Resistance against replay attack: A malicious drone that left the drone swarm might attempt to enter the area
Resistance against eavesdropping attack: A malicious drone might attempt to capture a B or messages of other drones. Each drone refreshes the
5.2 Formal Security Verification Using ProVerif
We demonstrated the proposed protocol’s mutual authentication between the drone and the
(1) The secrecy of the group session key
(2) The authenticity of the message sent by the drone swarm
(3) The authenticity of the message st by the
As shown in Fig. 3, we generated four events and three queries to verify the above security requirements through the ProVerif tool.

Figure 3: Declaration of events and queries
ProVerif checks (1) by the first query whether the attacker will be aware of the secret value

Fig. 4 shows the verification results for the above queries. The experiments are carried out in Mac OS and Intel Core i7 with 1.2 GHz and 16 GB RAM. We published detailed protocol code and result on the GitHub repository1. The first result means the

Figure 4: Output provided by the ProVerif tool
In this section, we implemented the proposed protocol and evaluated the performance of the drone swarm identification scheme. We also analyzed the computation overhead of the proposed drone swarm identification scheme by comparing existing schemes that have similar authentication steps.
We built a non-flying drone swarm prototype on a MacBook and multiple Raspberry Pis to evaluate the computational performance of the proposed protocol. We used Raspberry Pi 3 Model Bs to simulate a drone swarm and the
Fig. 5 shows an experimental environment with a drone swarm consisting of 5 drones and one

Figure 5: Experimental prototype of the proposed protocol
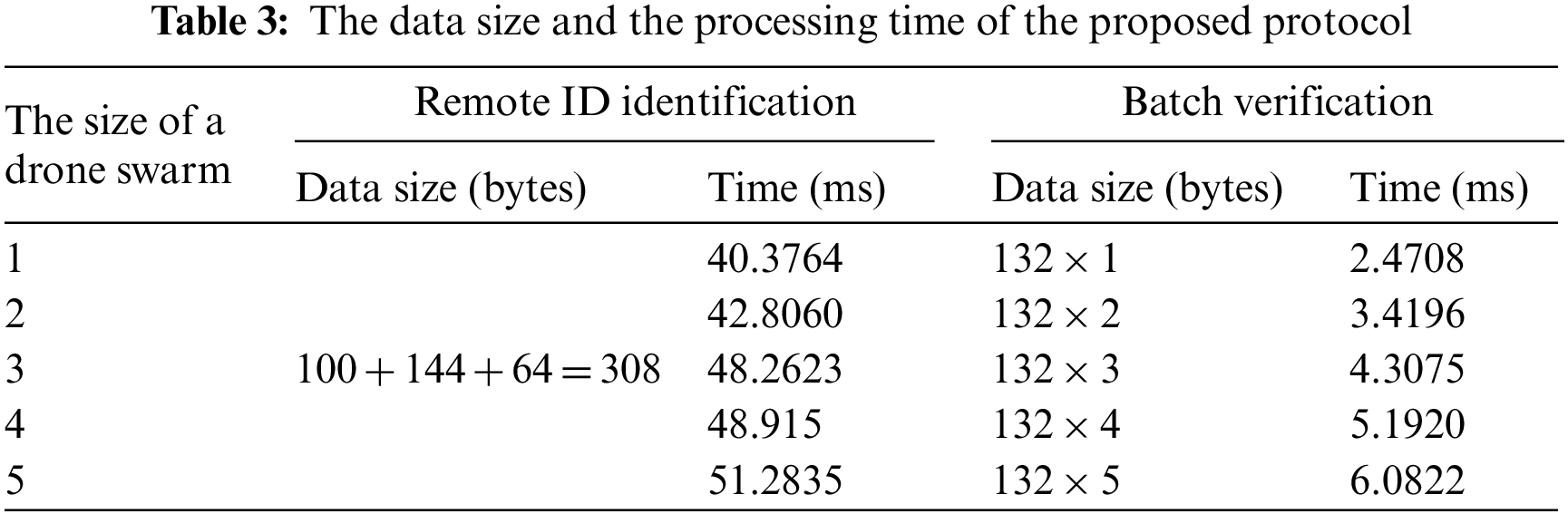
We analyzed the computation overhead for our protocol and the existing schemes [6–8]. We chose related schemes that provide authentication between IoT devices and a server, which is similar to our proposed protocol. For the computational comparison, we measured the average computational time of the cryptographic primitives on a drone and a GCS that we explained in 6.1. We utilized the PyCryptodome [39], which is a Python library that has been widely accepted as a way to measure each operation. Table 4 shows the execution time for computing cryptographic primitives, including hash function, ECC point multiplication, ECC point addition, and so on. Table 5 shows the result of the computational overhead comparison in terms of an IoT device, a reader node, and a server.
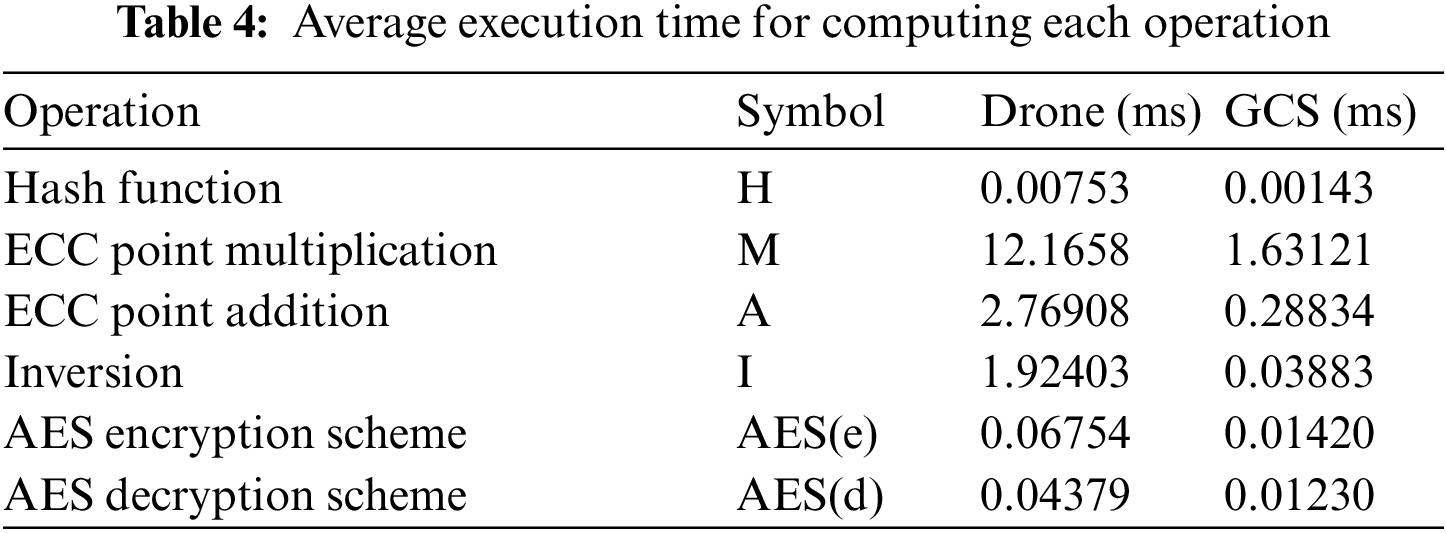
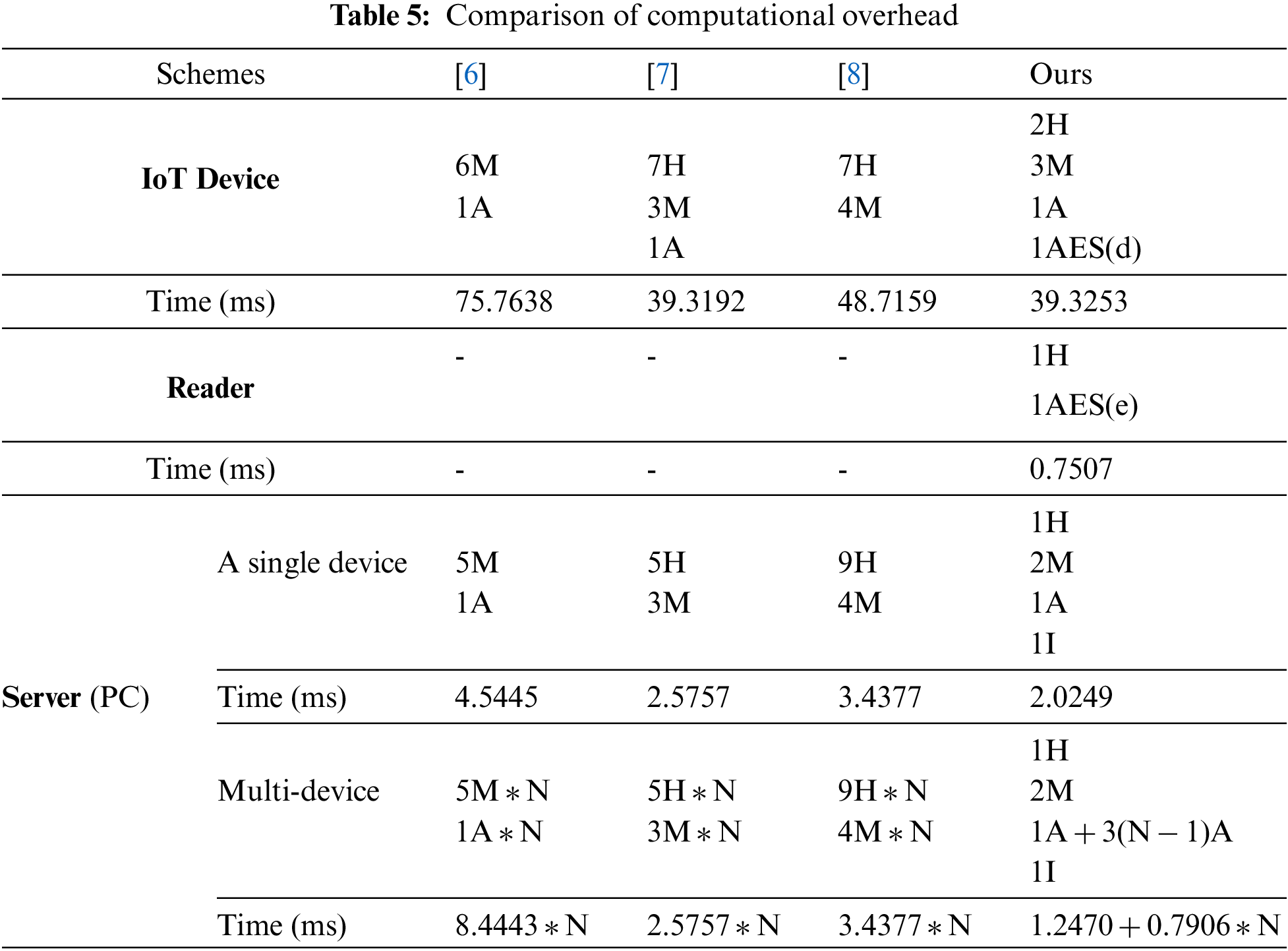
For an accurate comparison, we only compared the authentication phase except for other processes such as key agreement and registration phase. The computational overhead on the device side in the proposed protocol is 2H + 3M + 1A + 1AES(d) ≈ 39.3253 ms, while existing schemes [6–8] require 6M + 1A
Fig. 6 shows the computational overhead according to the size of a drone swarm. When the size of a drone swarm increases, a gap in the computational overhead between the related schemes and our protocol gradually gets larger. For example, if the size of a drone swarm is 50, the proposed protocol requires only 40.7477 ms, while the highest computational overhead of compared schemes is 227.223 ms, which is 5.6 times larger. This result implies that the proposed protocol is more efficient and suitable than existing protocols in the authentication of multiple IoT devices.

Figure 6: Computational overhead according to the size of a drone swarm
We simulated the proposed protocol assuming multiple drone swarms and multiple
We assumed that there is no mobility when the drone swarm communicates with the

Figure 7: Simulation models for drone swarms
7.2 Performance Analysis for Drone Swarm Identification
To check the verification time based on the size of the drone swarm, we compared the total verification time based on the size of the drone swarm and the number of

Figure 8: Comparison of identification time according to the size of a drone swarm
Using more
We compared the time required for the

Figure 9: Comparison of identification time according to the number of drone swarms
7.3 Performance Analysis for Drone Swarm Scheduling
To analyze drone swarm scheduling, we simulated the cluster average waiting time according to the cluster arrival plan using the Matlab.
Fig. 10 shows the average waiting time of a drone swarm according to the arrival time interval of a drone swarm in the same region when the number of

Figure 10: Average latency of drone swarms according to the arrival time interval of drone swarms
In this paper, we proposed an efficient remote identification for drone swarms. To efficiently perform drone swarm identification between the GCS and the drone swarm, the
Acknowledgement: The abstract version of this work was presented in WISA2022 poster session.
Funding Statement: This work was partly supported by Institute of Information & Communications Technology Planning & Evaluation (IITP) grant funded by the Korea government (MSIT) (No. RS-2023-00225201, Development of Control Rights Protection Technology to Prevent Reverse Use of Military Unmanned Vehicles, 50) and by MSIT under the ITRC (Information Technology Research Center) Supported Program (IITP-2023-2018-0-01417, Industrial 5G Bigdata Based Deep Learning Models Development and Human Resource Cultivation, 50) supervised by the IITP.
Authorship Contributions: Kang-Moon Seo and Jane Kim contributed equally to this work as co-first authors. The authors confirm contribution to the paper as follows: study conception and design: Kang-Moon Seo, Jane Kim, Seung-Hyun Seo; data collection: Kang-Moon Seo, Soojin Lee, Jun-Woo Kwon; analysis and interpretation of results: Jane Kim, Soojin Lee; draft manuscript preparation: Kang-Moon Seo, Jane Kim, Seung-Hyun Seo. All authors reviewed the results and approved the final version of the manuscript.
Availability of Data and Materials: Data sharing is not applicable to this article as no new data were created or analyzed in this study.
Conflicts of Interest: The authors declare that they have no conflicts of interest to report regarding the present study.
1https://github.com/jelliyjane/DroneSwarmIDentification_ProVerif
References
1. S. H. Alsamhi, B. Lee, M. Guizani, N. Kumar, Y. Qiao et al., “Blockchain for decentralized multi-drone to combat COVID-19 and future pandemics: Framework and proposed solutions,” Transaction on Emerging Telecommunications Technologies, vol. 32, no. 9, pp. e4255, 2021. [Google Scholar]
2. S. H. Alsamhi and B. Lee, “Blockchain-empowered multi-robot collaboration to fight COVID-19 and future pandemics,” IEEE Access, vol. 9, pp. 44173–44197, 2020. [Google Scholar] [PubMed]
3. A. Saif, K. Dimyati, K. A. Noordin, S. H. Alsamhi and A. Hawbani, “Multi-UAV and SAR collaboration model for disaster management in B5G networks,” Internet Technology Letters, pp. e310, 2021. [Google Scholar]
4. S. H. Alsamhi, F. A. Almalki, H. AL-Dois, A. V. Shvetsov, M. S. Ansari et al., “Multi-drone edge intelligence and SAR smart wearable devices for emergency communication,” Wireless Communications and Mobile Computing, vol. 2021, pp. 1–12, 2021. [Google Scholar]
5. S. H. Alsamhi, A. V. Shvetsov, S. V. Shvetsova, A. Hawbani and M. Guizani, “Blockchain-empowered security and energy efficiency of drone swarm consensus for environment exploration,” IEEE Transactions on Green Communications and Networking, vol. 7, pp. 328–338, 2023. [Google Scholar]
6. S. Rostampour, M. Safkhani, Y. Bendavid and N. Bagheri, “ECCbAP: A secure ECC-based authentication protocol for IoT edge devices,” Pervasive and Mobile Computing, vol. 67, pp. 101194, 2020. [Google Scholar]
7. S. Jain, C. Nandhini and R. Doriya, “ECC-based authentication scheme for cloud-based robots,” Wireless Personal Communications, vol. 117, pp. 1557–1576, 2021. [Google Scholar]
8. D. Kwon, S. Son, Y. Park, H. Kim, Y. Park et al., “Design of secure handover authentication scheme for urban air mobility environments,” IEEE Access, vol. 10, pp. 42529–42541, 2022. [Google Scholar]
9. S. Charuchandra, A Swarm of Flying 3D Printers Inspired by Bees. Advanced Science News, 2022. [Online]. Available: https://www.advancedsciencenews.com/a-swarm-of-flying-3d-printers-inspired-by-bees/ [Google Scholar]
10. D. Hambling, U.S. Navy Destroys Target with Drone Swarm—And Sends a Message to China. Forbes, 2021. [Online]. Available: https://www.forbes.com/sites/davidhambling/2021/04/30/us-navy-destroys-target-with-drone-swarm---and-sends-a-message-to-china/?sh=45aedfe02df1 [Google Scholar]
11. D. Hambling, Indian Army Shows Off Drone Swarm of Mass Destruction. Forbes, 2021. [Online]. Available: https://www.forbes.com/sites/davidhambling/2021/01/19/indian-army-shows-off-drone-swarm-of-mass-destruction/?sh=9cae55a23840 [Google Scholar]
12. The BBC News, Gatwick: New Technology’ could Prevent Airport Drone Chaos’. The BBC News, 2021. [Online]. Available: https://www.bbc.com/news/uk-england-sussex-58572762 [Google Scholar]
13. Michael Dempsey, Shooting Drones out of the sky with Phasers. The BBC News, 2019. [Online]. Available: https://www.bbc.com/news/business-49984415 [Google Scholar]
14. FAA, Uas Remote Identification Overview. Federal aviation administration, 2023. [Online]. Available: https://www.faa.gov/uas/getting_started/remote_id/ [Google Scholar]
15. EASA, Easy Access Rules for Unmanned Aircraft Systems, European union aviation safety agency, 2019. [Online]. Available: https://www.easa.europa.eu/document-library/easy-access-rules/online-publications/easy-access-rules-unmanned-aircraft-systems?page=4#-Toc256000009 [Google Scholar]
16. MLIT, The Mandatory Registration of Unmanned Aircraft Became Effective. Unmanned Aircraft Registration Web Porta, 2022. [Online]. Available: https://www.mlit.go.jp/koku/drone/en/ [Google Scholar]
17. P. Tedeschi, S. Sciancalepore and R. D. Pietro, “A RID: Anonymous remote IDentification of unmanned aerial vehicles,” in ACSAC ’21: Annual Computer Security Applications Conf., New York City, NY, USA, pp. 207–218, 2021. [Google Scholar]
18. D. He, N. Kumar, N. Chilamkurti and J. H. Lee, “Lightweight ECC based RFID authentication integrated with an ID verifier transfer protocol,” Journal of Medical Systems, vol. 38, no. 10, pp. 1–6, 2014. [Google Scholar]
19. S. Kumar, H. Banka, B. Kaushik and S. Sharma, “A review and analysis of secure and lightweight ECC-based RFID authentication protocol for internet of vehicles,” Transactions on Emerging Telecommunications Technologies, vol. 32, pp. e4354, 2021. [Google Scholar]
20. C. I. Lee and H. Y. Chien, “An elliptic curve cryptography-based RFID authentication securing e-health system,” International Journal of Distributed Sensor Networks, vol. 11, no. 12, pp. 642425, 2015. [Google Scholar]
21. Y. P. Liao and C. M. Hsiao, “A secure ECC-based RFID authentication scheme integrated with ID-verifier transfer protocol,” Ad Hoc Networks, vol. 18, pp. 133–146, 2014. [Google Scholar]
22. I. Nemer, T. Sheltami, I. Ahmad, A. U. Yasar and M. A. R. Abdeen, “RF-based UAV detection and identification using hierarchical learning approach,” Sensors, vol. 21, no. 6, pp. 1947, 2021. [Google Scholar]
23. A. Gumaei, M. Al-Rakhami, M. M. Hassan, P. Pace, G. Alai et al., “Deep learning and blockchain with edge computing for 5G-enabled drone identification and flight mode detection,” IEEE Network, vol. 35, no. 1, pp. 94–100, 2021. [Google Scholar]
24. M. Nikooghadam, H. Amintoosi, S. K. H. Iskam and M. F. Moghadam, “A provably secure and lightweight authentication scheme for Internet of Drones for smart city surveillance,” Journal of Systems Architecture, vol. 115, pp. 101955, 2021. [Google Scholar]
25. M. A. Khan, I. Ullah, S. Nisar, F. Noor, I. M. Qureshi et al., “An efficient and provably secure certificateless key-encapsulated signcryption scheme for flying ad-hoc network,” IEEE Access, vol. 8, pp. 36807–36828, 2020. [Google Scholar]
26. Y. Ardin, G. K. Kurt, E. Ozdemir and H. Yanikomeroglu, “Group authentication for drone swarms,” in IEEE Int. Conf. on Wireless for Space and Extreme Environments (WiSEE), Cleveland, Ohio, USA, pp. 72–77, 2021. [Google Scholar]
27. Y. Ardin, G. K. Kurt, E. Ozdemir and H. Yanikomeroglu, “Authentication and handover challenges and methods for drone swarms,” IEEE Journal of Radio Frequency Identification, vol. 6, pp. 220–228, 2022. [Google Scholar]
28. M. Abdel-Malek, K. Akkaya, A. Bhuyan and A. S. Ibrahim, “A proxy signature-based swarm drone authentication with leader selection in 5G networks,” IEEE Access, vol. 10, pp. 57485–57498, 2022. [Google Scholar]
29. K. Han, E. A. Nuaimi, S. A. Blooshi, R. Psiakis and C. Y. Yeun, “A new scalable mutual authentication in fog-edge drone swarm environment,” in Information Security Practice and Experience. Switzerland AG, Taipei, Taiwan: Springer, pp. 179–196, 2022. [Google Scholar]
30. P. Han, A. Sui and J. Wu, “Identity management and authentication of a UAV swarm based on a blockchain,” Applied Sciences, vol. 12, pp. 179–196, 2022. [Google Scholar]
31. B. Bruno, “Automatic verification of correspondences for security protocols,” Journal of Computer Security, vol. 17, no. 4, pp. 363–434, 2009. [Google Scholar]
32. A. Varga and R. Hornig, “An overview of the OMNeT++ simulation environment,” 1st Int. ICST Conf. on Simulation Tools and Techniques for Communications, Networks and Systems, Marseille, France, pp. 1–10, 2008. [Google Scholar]
33. H. Gao, W. Li and H. Cai, “Fully distributed robust formation flying control of drones swarm based on minimal virtual leader information,” Drones, vol. 6, no. 10, pp. 266, 2022. [Google Scholar]
34. B. Alkouz and B. Athman, “Provider-centric allocation of drone swarm services,” in 2021 IEEE Int. Conf. on Web Services (ICWS), Chicago, IL, USA, pp. 230–239, 2021. [Google Scholar]
35. B. Alkouz, B. Athman and M. Sajib, “Swarm-based drone-as-a-service (sdaas) for delivery,” in 2020 IEEE Int. Conf. on Web Services (ICWS), Beijing, China, pp. 441–448, 2020. [Google Scholar]
36. C. Conte, S. Verini Supplizi, G. de Alteriis, A. Mele, G. Rufino et al., “Using drone swarms as a countermeasure of radar detection,” Journal of Aerospace Information Systems, vol. 20, no. 2, pp. 70–80, 2023. [Google Scholar]
37. F. Saffre, H. Hildmann, H. Karvonen and T. Lind, “Monitoring and cordoning wildfires with an autonomous swarm of unmanned aerial vehicles,” Drones, vol. 6, no. 10, pp. 301, 2022. [Google Scholar]
38. D. Dolev and A. Yao, “On the security of public key protocols,” IEEE Transactions on Information Theory, vol. 29, no. 2, pp. 198–208, 1983. [Google Scholar]
39. PyCryptodome, 2023. [Online]. Available: https://www.pycryptodome.org/en/latest/index.html [Google Scholar]
40. D. J. Higham and N. J. Higham, “MATLAB guide,” in Matrices, 3rd ed. Philadelphia, PA, USA: Society for Industrial and Applied Mathematics, pp. 47–66, 2016. [Google Scholar]
41. O. Bouachir, M. Aloqaily, F. Garcia, N. Larrieu and T. Gayraud, “Testbed of QoS ad-hoc network designed for cooperative multi-drone tasks,” in Proc. of the 17th ACM Int. Symp. on Mobility Management and Wireless Access, New York City, NY, USA, pp. 89–95, 2019. [Google Scholar]
Cite This Article
 Copyright © 2023 The Author(s). Published by Tech Science Press.
Copyright © 2023 The Author(s). Published by Tech Science Press.This work is licensed under a Creative Commons Attribution 4.0 International License , which permits unrestricted use, distribution, and reproduction in any medium, provided the original work is properly cited.


 Submit a Paper
Submit a Paper Propose a Special lssue
Propose a Special lssue View Full Text
View Full Text Download PDF
Download PDF Downloads
Downloads
 Citation Tools
Citation Tools