 Open Access
Open Access
ARTICLE
Coati Optimization-Based Energy Efficient Routing Protocol for Unmanned Aerial Vehicle Communication
1 Department of Information Systems, College of Computer and Information Sciences, Princess Nourah bint Abdulrahman University, P.O. Box 84428, Riyadh, 11671, Saudi Arabia
2 Department of Information Systems, College of Computer Science, Center of Artificial Intelligence and Unit of Cybersecurity, King Khalid University, Abha, 62529, Saudi Arabia
3 Department of Information Systems, College of Computer Science, King Khalid University, Abha, 62529, Saudi Arabia
4 Department of Computer Sciences, College of Computing and Information Systems, Umm Al-Qura University, Mecca, 24382, Saudi Arabia
5 Department of Computer Science, College of Computer, Qassim University, Buraydah, 52571, Saudi Arabia
6 Department of Computer Science, Faculty of Computers and Information Technology, Future University in Egypt, New Cairo, 11835, Egypt
7 Department of Computer Science, College of Sciences and Humanities-Aflaj, Prince Sattam bin Abdulaziz University, Al-Kharj, 16278, Saudi Arabia
* Corresponding Author: Mesfer Al Duhayyim. Email:
Computers, Materials & Continua 2023, 75(3), 4805-4820. https://doi.org/10.32604/cmc.2023.037810
Received 17 November 2022; Accepted 13 February 2023; Issue published 29 April 2023
Abstract
With the flexible deployment and high mobility of Unmanned Aerial Vehicles (UAVs) in an open environment, they have generated considerable attention in military and civil applications intending to enable ubiquitous connectivity and foster agile communications. The difficulty stems from features other than mobile ad-hoc network (MANET), namely aerial mobility in three-dimensional space and often changing topology. In the UAV network, a single node serves as a forwarding, transmitting, and receiving node at the same time. Typically, the communication path is multi-hop, and routing significantly affects the network’s performance. A lot of effort should be invested in performance analysis for selecting the optimum routing system. With this motivation, this study modelled a new Coati Optimization Algorithm-based Energy-Efficient Routing Process for Unmanned Aerial Vehicle Communication (COAER-UAVC) technique. The presented COAER-UAVC technique establishes effective routes for communication between the UAVs. It is primarily based on the coati characteristics in nature: if attacking and hunting iguanas and escaping from predators. Besides, the presented COAER-UAVC technique concentrates on the design of fitness functions to minimize energy utilization and communication delay. A varied group of simulations was performed to depict the optimum performance of the COAER-UAVC system. The experimental results verified that the COAER-UAVC technique had assured improved performance over other approaches.Keywords
Unmanned aerial vehicles (UAVs) have grabbed a lot of research interest over the past few decades because of several inherent features like their ability to establish a line of sight (LOS) links with the users, mobility, and their easy deployment [1]. Generally, UAVs, otherwise known as drones, are of two types: rotary-wing and fixed-wing. Each type of UAV can be adapted to a particular type of application. For instance, fixed-wing drones were very suitable for the type of mission stationarity was not required, e.g., Military applications like surveillance and attack [2]. But rotary-wing drones have complicated aerodynamics. It even can remain immobile at a specified location. However, it could not able to execute long-range missions [3]. The rotary-wing drones were better suited to offer impermanent wireless coverage to ground users. The participation of several industrial units in UAV production has facilitated minimizing their cost on markets; using a UAV network is no longer a futuristic idea or dream [4]. They were employed in several cases offering wireless connectivity, surveillance, weather forecasting, farming, disaster management, traffic control, and delivery.
A UAV-based transmission system is found to be better in between air and terrestrial medium [5]. But the existing routing path up-gradation of UAVs needs to be improved for completing the data transmission. The ideal path up-gradation was to govern the target area of a sink of network or UAV so that the drone may carry the sensing data to reach them out [6]. The drone sensing data relay transmission would encounter path selection problems, interruption, and distortion. The examination of relay network transmission influenced the transmission time delay and data quality [7]. The data is broadcasted through radio propagation in the routing path up-gradation. Depending on the topological data of the drone self-assembling network routing protocol model, drone self-assembling network transmission data peripheral forwarding, and greedy forwarding as per the communication among UAV swarm and UAV [8], the transmission data forwarding mode is modelled as per the situation, integrated with the spatial features of UAVs in the operation process; 2 forwarding modes were modeled from dual aspects like peripheral forwarding and greedy forwarding [9]. The greedy forwarding: in the UAVs self-organizing network, an adjacent communication node has a small spatial linear distance among the transmission target node, and a local neighbour table can be chosen from the communication node since the next data-delivering nodes, and nodes were considered as the main node in routing protocol [10].
This study introduces a new Coati Optimization Algorithm-based Energy-Efficient Routing Protocol for Unmanned Aerial Vehicle Communication (COAER-UAVC) technique. The presented COAER-UAVC technique establishes effective routes for communication between the UAVs. Besides, the presented COAER-UAVC technique concentrates on the design of fitness functions to minimize energy utilization and communication delay. A varied group of simulations was performed to depict the superior performance of the COAER-UAVC system. The experimental results verified that the COAER-UAVC model had assured better performance over other approaches.
The rest of the paper is organized as follows. Section 2 offers the related works, and Section 3 introduces the proposed model. Next, Section 4 provides experimental validation, and Section 5 concludes the work.
Francelin et al. [11] modelled a new method to initiate secured transmission in UAV networks. Initially, the UAV simulation is carried out. Then, using a routing path, the data communication can be executed among nodes; therefore, the best routing path can be constituted by utilizing the Tunicate Swarm Political Optimization (TSPO) technique. This modelled TSPO technique compiles the Political Optimizer and Tunicate Swarm Algorithm. Moreover, the data transmission can be performed through a monitoring agent and evaluation. Also, by utilizing the deep residual networks (DRNs), malicious recognition can be performed by a decision-making agent. Namdev et al. [12] devised a whale optimization algorithm (WOA)-related optimized link state routing (WOA-OLSR) on flying ad-hoc network (FANET) for offering the best routing for energy-efficient and secure FANET. Using WOA, the potentiality of OLSR can be improvised, and assessing results exhibits the superior performance of the WOA-OLSR technique. In [13], the authors developed the joint optimization of relay paths and drone locations in UAV-relayed Internet of Things (IoT) networks as graph issues and proposed a graph neural network (GNNs)-oriented method to solve it efficiently. The authors devised a reinforcement learning-based relay GNN (RGNN) in the training procedure for choosing an optimum relay path for users. Afterwards, the authors jointly use RGNN and location GNN (LGNN) to optimize every UAV’s places.
Khan et al. [14] devise a self-organization-oriented clustering scheme stimulated by the behavioural study of glowworm swarm optimization (GSO) for cluster management and formation. The cluster formation and cluster head (CH) selection were carried out based on connectivity with the ground control station and the drones' residual energy (RE) and luciferin values. The cluster management system employs behavioural analysis of GSO by upgrading luciferin values depending on the place of the UAV. Also, the authors devised a system for route selection related to the position, neighbour range, and RE of drones for effective transmission. In [15], modelled a Trust Based Clustering Scheme (TBCS) for FANETs. TBCS leverages a multi-criteria fuzzy technique for classifications relevant to the behavior of nodes in the complex and fuzzy environment. The devised method uses Takagi–Sugeno–Kang fuzzy inference approach. Moreover, a secure CH was chosen depending on computed trust values accountable for transmission with inter-cluster communication and a ground control station.
In [16], blockchain (BC) can be used for investigating the secure transmission among drones to Wireless UAV base stations. Drones were more susceptible to security assaults. The devised BC-related architecture supported secure data transmission in the drone’s uncertain surroundings. This study develops a modified PSO technique for superior path selection to enhance network security. Zhen et al. [17] devise an intelligent self-organized algorithm (ISOA) to resolve a cooperative search-attack mission planning issue for multi-UAVs. In the initial stage, an enhanced distributed ant colony optimization (ACO) method was presented to execute the mission planning and produce waypoints. In the next stage, to smoothly join waypoints produced by ACO, the Dubins curve was used.
In this study, we have introduced a novel COAER-UAVC technique for effective UAV communication. The presented COAER-UAVC technique concentrated on identifying optimal routes for communication between the UAVs.
In this work, the UAV deployed are separated into two categories. A primary one is a drone with monitor and communication purposes, but another is a Radio Repeater drone. They utilize similar UAVs but have distinct functions and equipment [18]. Considering the requirement of communication and observation tasks, the coverage region of UAV must be maximized. Fig. 1 illustrates the UAV system model. UAV adopts the U-shaped route to monitor and patrol the fire, which could maximize the patrol region. UAV turns beside a semicircle with a radius of

Figure 1: System model
whereas
whereas
whereas
The COA is a population-based meta-heuristic approach where the coatis are population members of these algorithms. The location of every coati in the searching space defines the value for decision parameters [19]. Therefore, the location of the coatis characterizes a candidate’s solution to problems. At first, the location of coatis in the search space is initialized at random based on the following expression:
In Eq. (5),
The location of the candidate solution in the decision variable results in the assessment of distinct values for the objective function (OF).
The initial stage of upgrading the coati’s population from the searching space can be modeled according to the simulation of the strategy while attacking iguanas. In the presented method, the location of the best members of the population has considered the location of the iguana. Consequently, the location of coatis increasing in the tree can be simulated mathematically as follows.
Afterwards, the iguana falls to the ground; it can be positioned in an arbitrary location from the searching space. With that regard, coatis on the ground move from the searching space that is formulated by the subsequent expression.
For

Figure 2: Steps involved in COA
The novel location evaluated for every coati has satisfactory for the updating procedure if it enhances the value of OF, or else, the coati remains in the preceding location. This can be expressed by:
Now,
In the exploitation phase, the location updating of coatis from the searching space can be modeled mathematically according to the behaviors of coatis naturally while encountering predators and escaping from the predators. Coati’s move in these strategies results in it being in a safer location closer to the present location that, represents the exploitation capability of COA in local search. For stimulating these behaviors, a random location is produced nearby the location where every coati is positioned according to the following expression:
The recently estimated location is satisfactory when it increases the value of OFs that these conditions simulate as follows:
In Eq. (14),
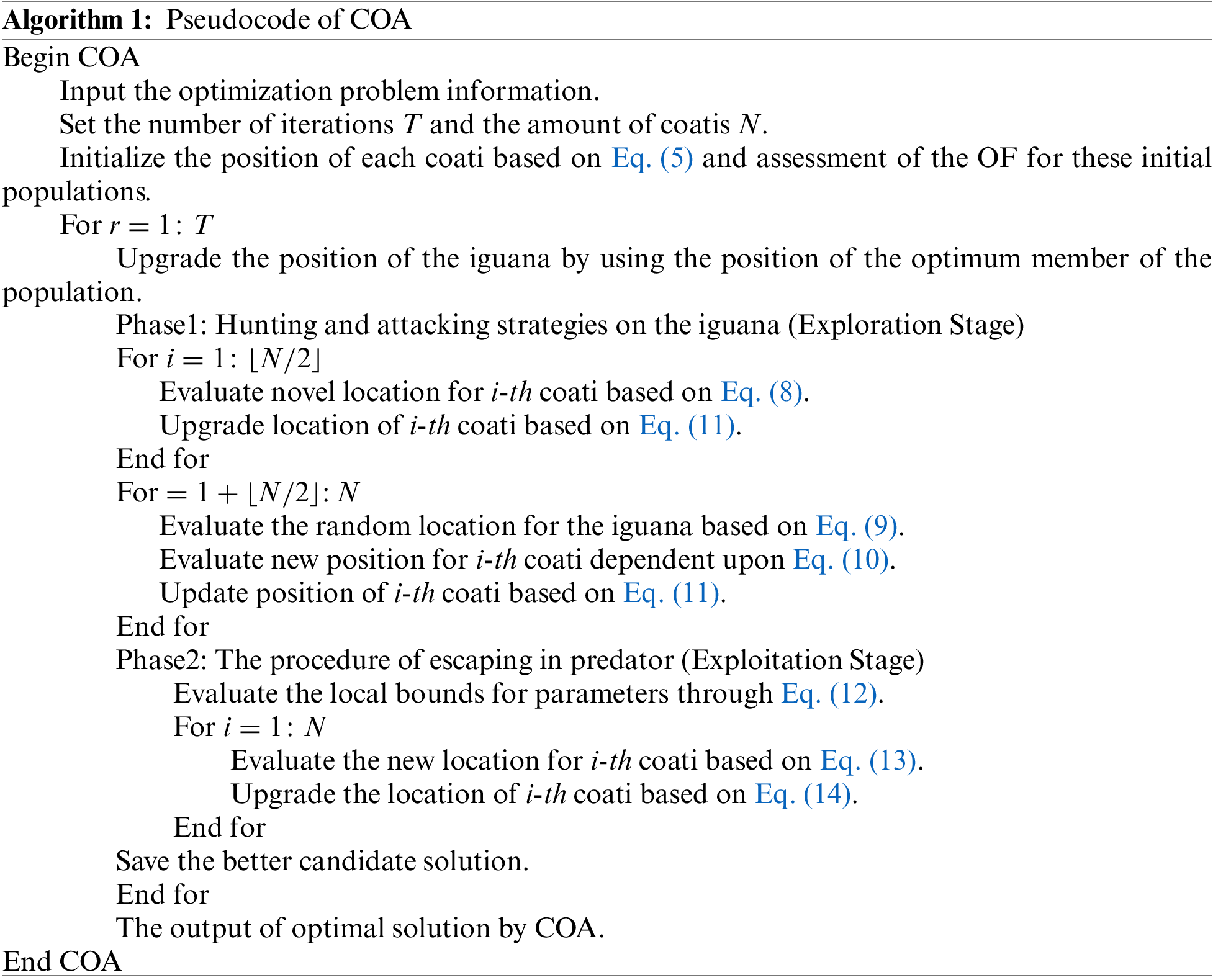
3.3 Process Involved in Routing Technique
The presented COAER-UAVC technique concentrates on the design of fitness functions to minimize energy utilization and communication delay. The latency and energy consumption of the method was determined in the subsequent. The potential of UAVs has included 3 portions.
whereas
In which
Also, the speed
whereas
In which
whereas
whereas
where
The main function of the MRP technique is for reducing delay and energy consumption. The delay or energy utilization has been chosen by frequent visits of UAVs. Thus, it could be determined as:
whereas
In this section, the routing performance of the COAER-UAVC approach was examined in detail. The proposed model is simulated using the MATLAB tool.
Table 1 and Fig. 3 provide a comparative analysis of the COAER-UAVC model with other approaches concerning throughput (THRO). The simulation values inferred that the COAER-UAVC model has gotten higher THRO values. For instance, on 10 UAVs, the COAER-UAVC model has provided an improved THRO of 0.9765 Mbps while the energy efficient neuro fuzzy based clustering with multi-hop routing protocol (EENFNC-MRP), krill herd optimization algorithm (KHOA), grey wolf optimizer (GWO), ACO algorithm (ACOA), and particle swarm optimization algorithm (PSOA) models have reached lower THRO values of 0.9513, 0.9380, 0.9262, 0.9143, and 0.8877 Mbps respectively. In addition, on 60 UAVs, the COAER-UAVC approach has provided enhanced THRO of 0.8581 Mbps while the EENFNC-MRP, KHOA, GWO, ACOA, and PSOA models have attained lesser THRO values of 0.7783, 0.6762, 0.5845, 0.5313, and 0.4455 Mbps correspondingly.
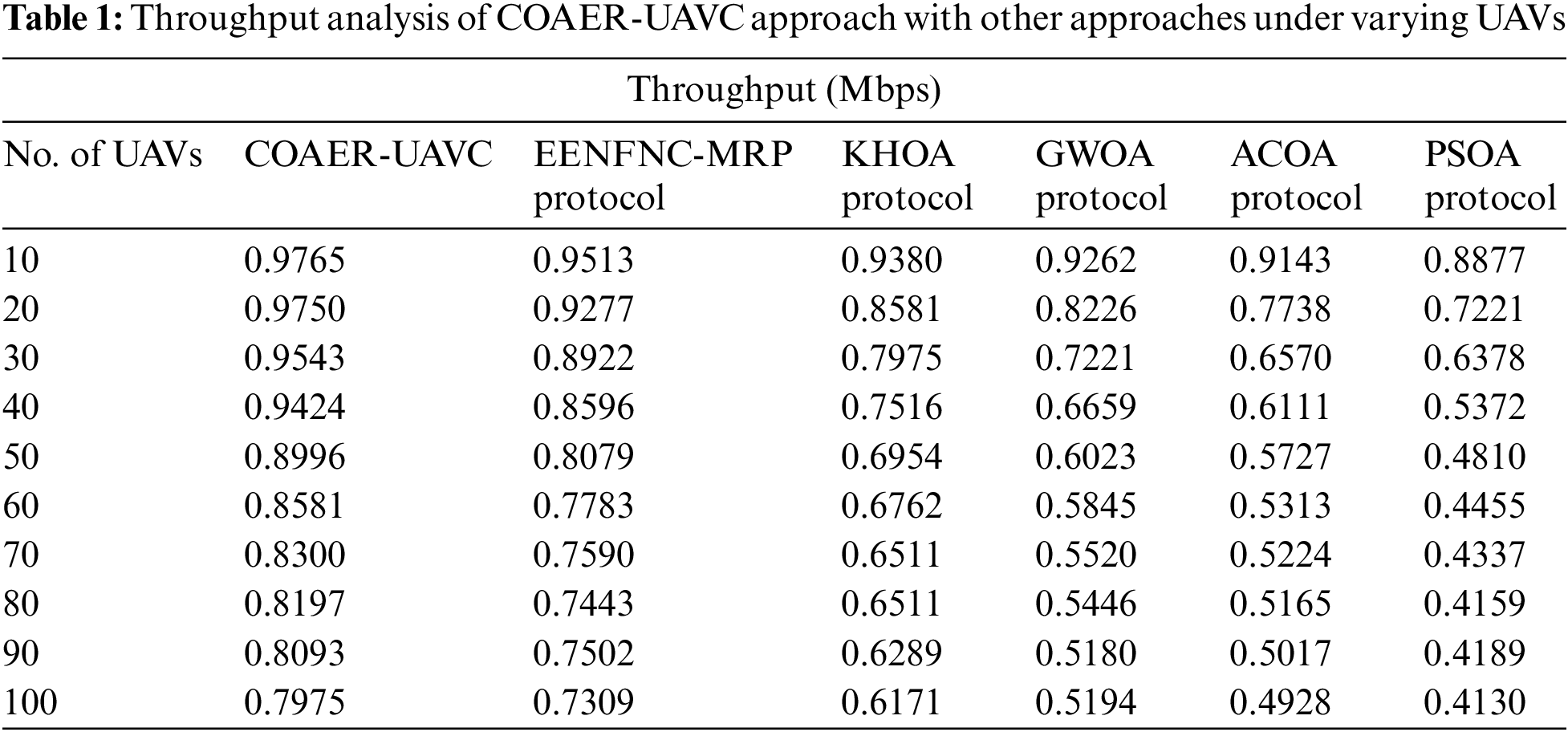

Figure 3: Throughput analysis of COAER-UAVC approach under varying UAVs
A comparative energy consumption (ECON) inspection of the COAER-UAVC model is made under various UAVs in Table 2 and Fig. 4. The outcomes revealed that the COAER-UAVC algorithm has attained the least values of ECON. For sample, on 10 UAVs, the COAER-UAVC model has resulted in a minimum ECON of 31 mJ while the EENFNC-MRP, KHOA, GWO, ACOA, and PSOA models have provided a maximum ECON of 32, 38, 39, 48, and 60 mJ respectively. Meanwhile, on 60 UAVs, the COAER-UAVC approach has resulted in a lesser ECON of 110 mJ while the EENFNC-MRP, KHOA, GWO, ACOA, and PSOA methodologies have provided a maximum ECON of 123, 147, 159, 173, 188 mJ correspondingly.
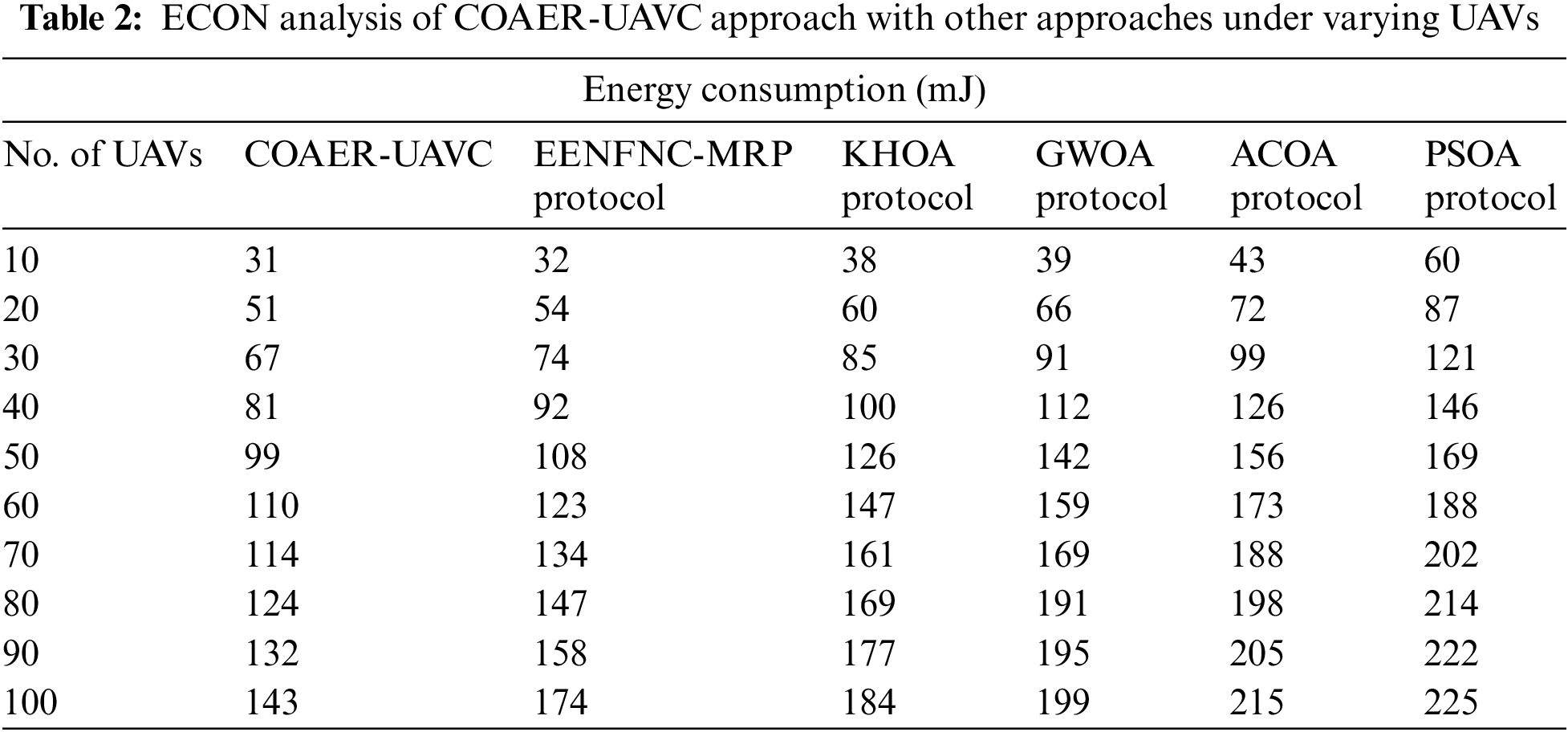
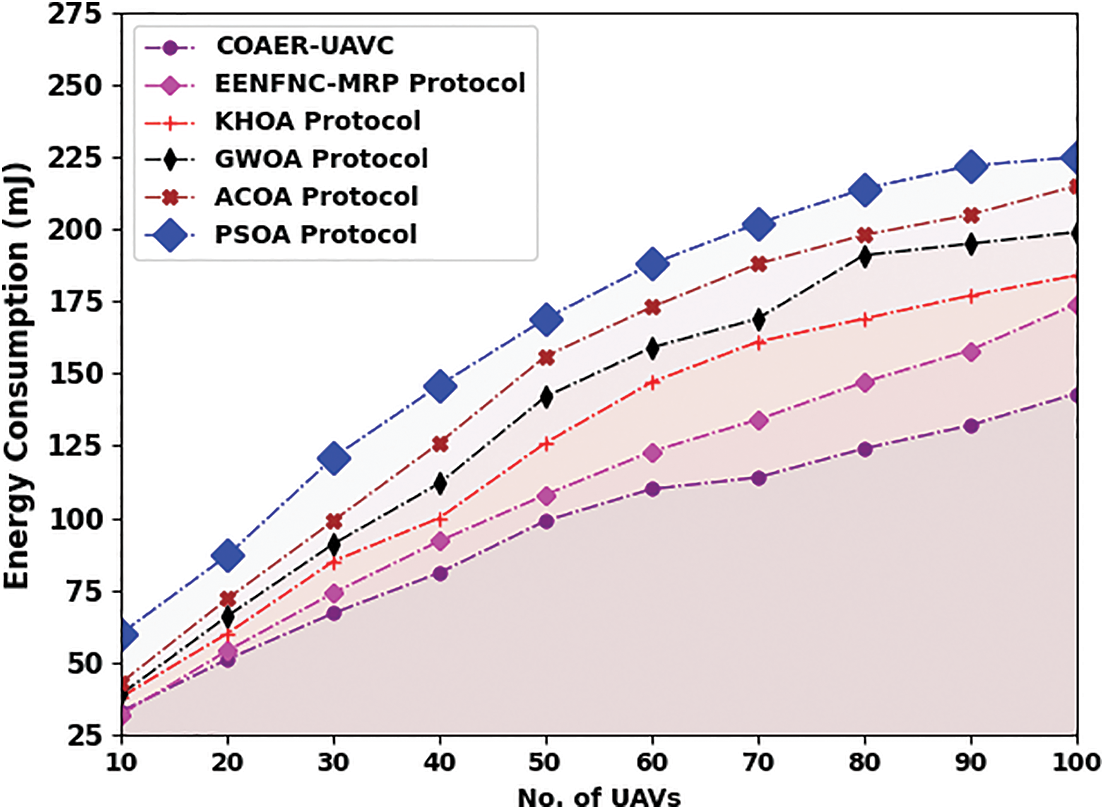
Figure 4: ECON analysis of COAER-UAVC approach under varying UAVs
In Table 3 and Fig. 5, a comparative analysis of the COAER-UAVC methodology with other methods concerning network lifetime (NLT) is provided. The simulation values stated that the COAER-UAVC model has gotten superior NLT values. For instance, on 10 UAVs, the COAER-UAVC algorithm has provided an improved NLT of 5760 rounds while the EENFNC-MRP, KHOA, GWO, ACOA, and PSOA approaches have reached lower NLT of 5638, 5270, 5169, 4881 and 4419 rounds correspondingly. Besides, on 60 UAVs, the COAER-UAVC approach has provided a greater NLT of 4974 rounds, while the EENFNC-MRP, KHOA, GWO, ACOA, and PSOA methodologies have achieved lower NLT of 4599, 4477, 4160, 3871 and 3641 rounds correspondingly.
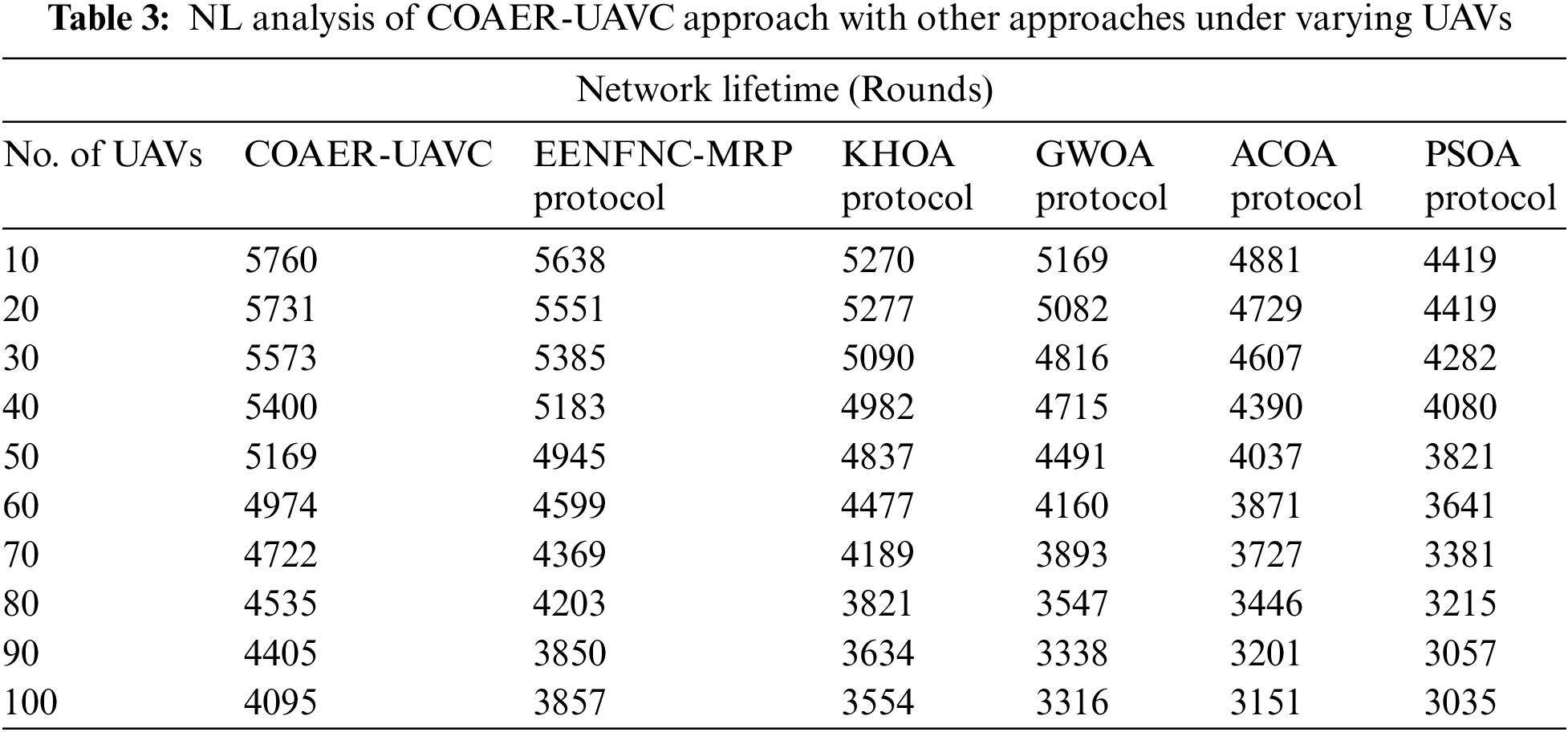
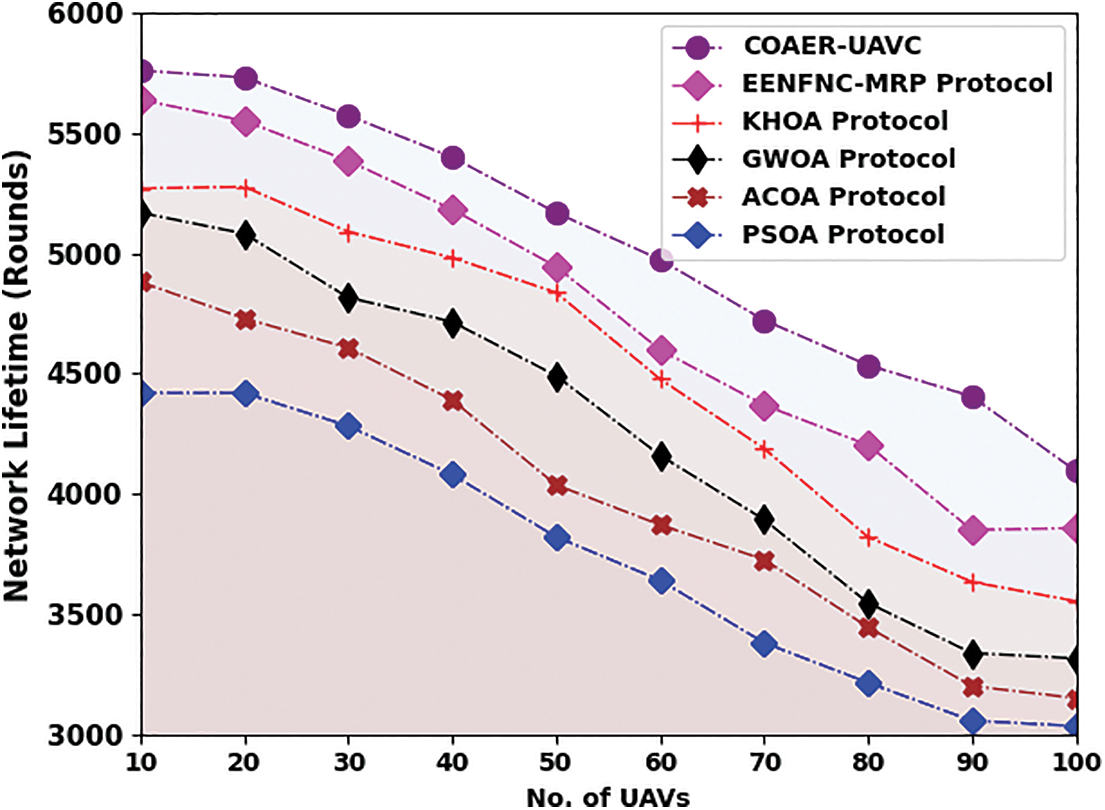
Figure 5: NLT analysis of COAER-UAVC approach under varying UAVs
In Table 4 and Fig. 6, a comparative investigation of the COAER-UAVC algorithm with existing systems in terms of packet delivery ratio (PDR) is provided. The resultant values pointed out that the COAER-UAVC approach has gotten superior PDR values. For sample, on 10 UAVs, the COAER-UAVC model has provided an improved PDR value of 97.78%, while the EENFNC-MRP, KHOA, GWO, ACOA, and PSOA methodologies have obtained lesser PDR values of 89.95%, 85.91%, 82.63%, 91.97%, and 72.78% respectively. Followed by 60 UAVs, the COAER-UAVC approach has provided an enhanced PDR of 82.88%, while the EENFNC-MRP, KHOA, GWO, ACOA, and PSOA models have gained minimum PDR values of 64.45%, 52.33%, 46.27%, 37.94% and 31.12 correspondingly.
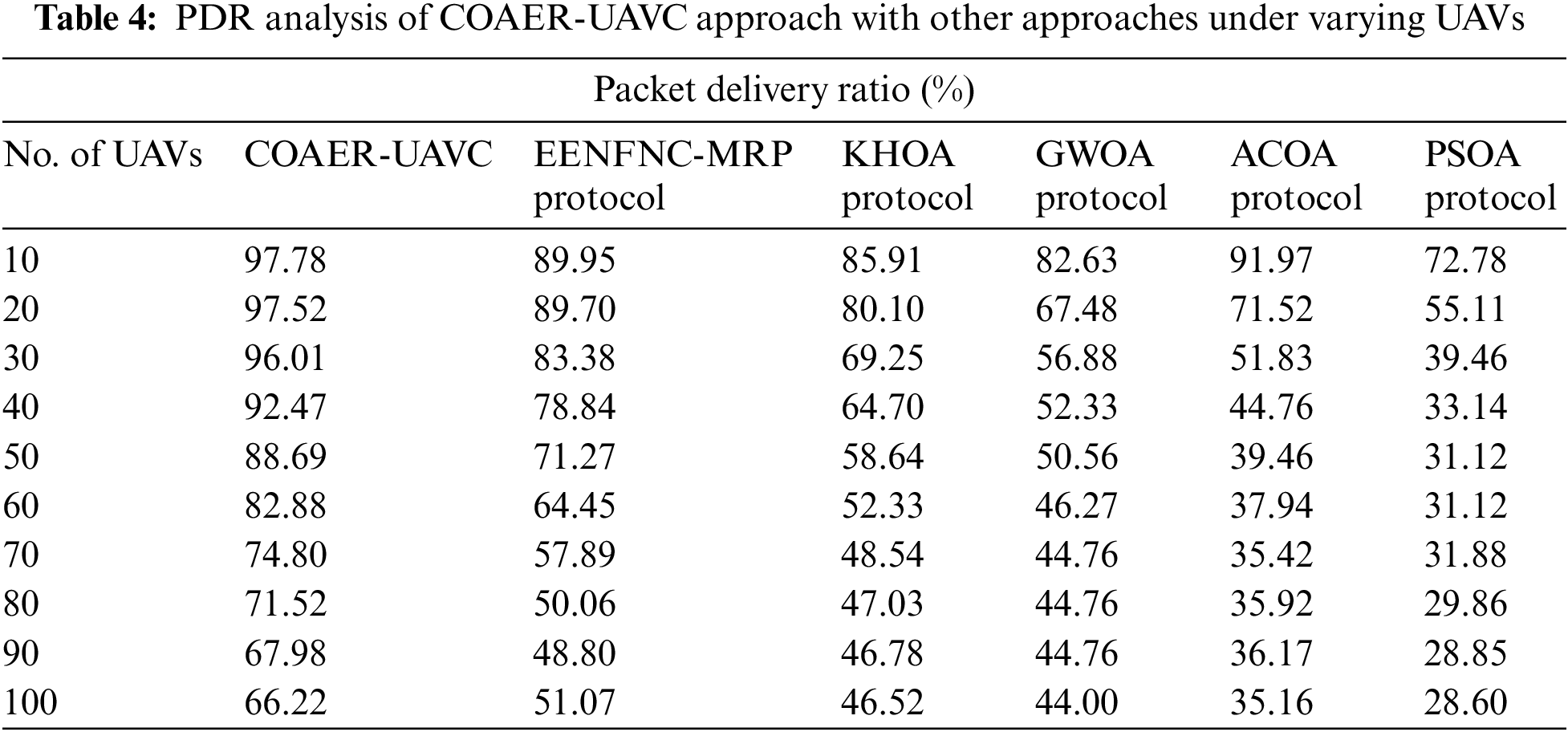
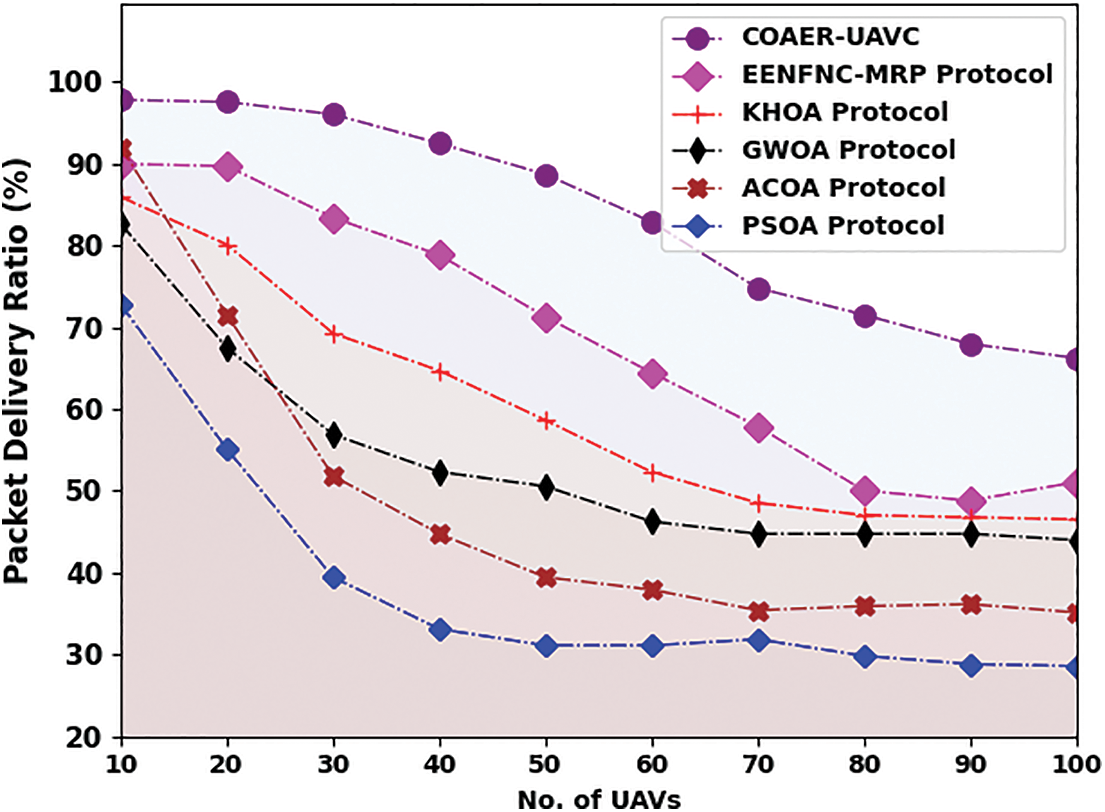
Figure 6: PDR analysis of COAER-UAVC approach under varying UAVs
A comparative packet loss rate (PLR) examination of the COAER-UAVC algorithm is made under various UAVs in Table 5 and Fig. 7. The outcome exposed that the COAER-UAVC system has reached the least values of PLR. For the sample, on 10 UAVs, the COAER-UAVC approach has resulted in lesser PLR of 2.22% while the EENFNC-MRP, KHOA, GWO, ACOA, and PSOA methodologies have provided superior PLR of 10.05%, 14.09%, 17.37%, 8.03% and 27.22% correspondingly. In the meantime, on 60 UAVs, the COAER-UAVC approach has resulted in a minimum PLR of 17.12% while the EENFNC-MRP, KHOA, GWO, ACOA, and PSOA algorithms have provided higher PLR of 35.55%, 47.67%, 53.73%, 62.06% and 68.88% correspondingly.
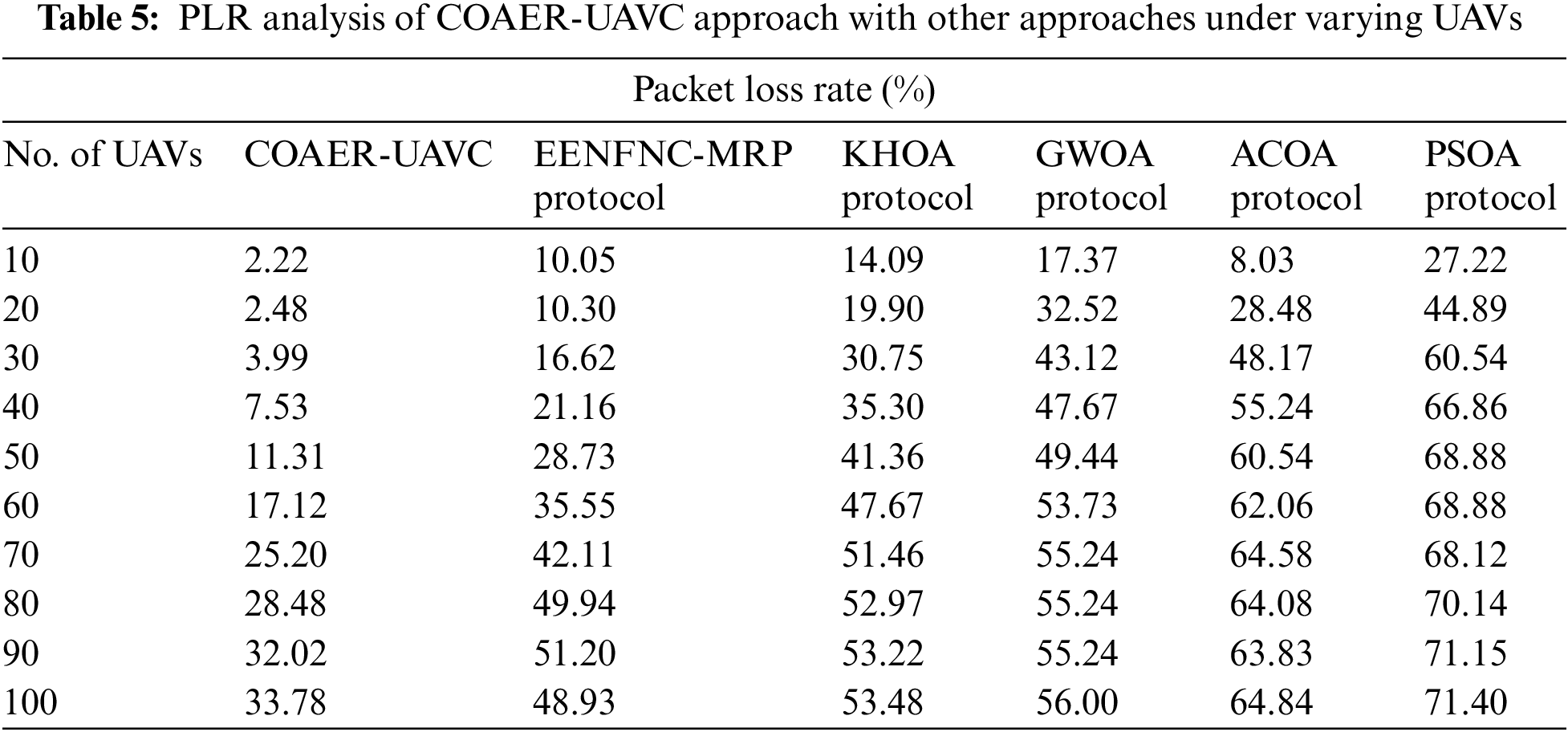
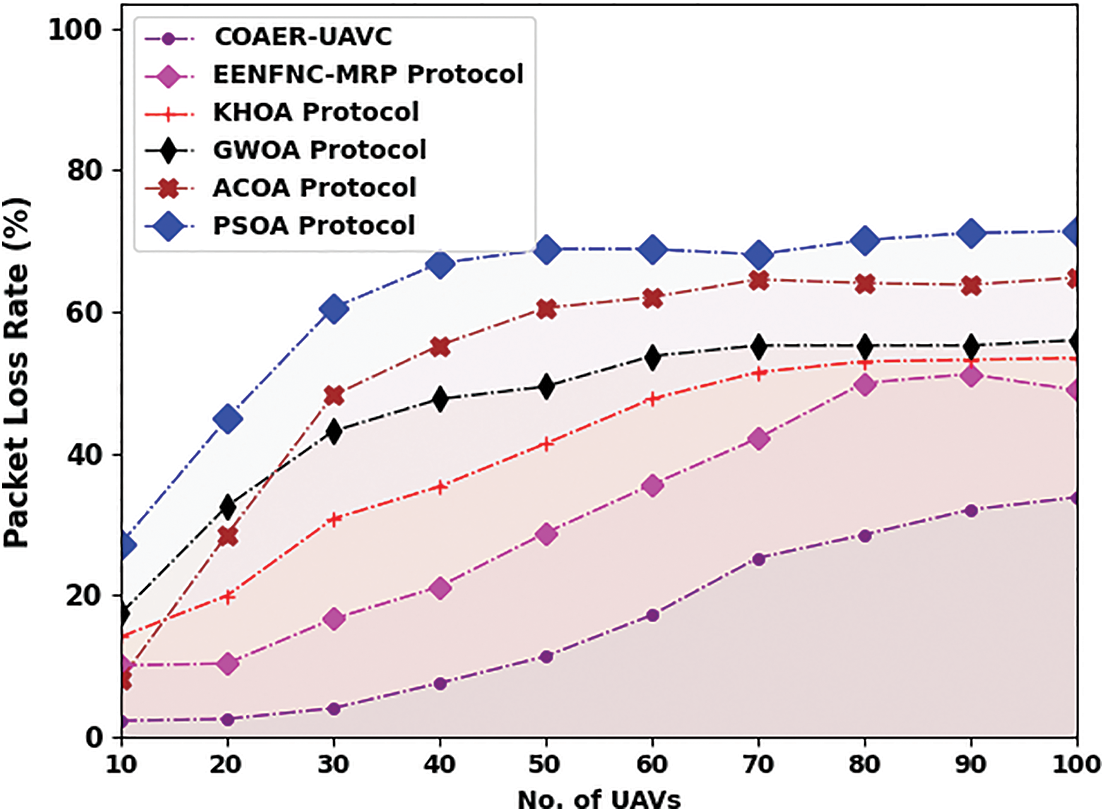
Figure 7: PLR analysis of COAER-UAVC approach under varying UAVs
A comparative average delay (AD) study of the COAER-UAVC technique is made under various UAVs in Table 6 and Fig. 8. The outcomes pointed out that the COAER-UAVC approach has gained the least values of AD. For the sample, on 10 UAVs, the COAER-UAVC algorithm has resulted in minimum AD of 0.15 s while the EENFNC-MRP, KHOA, GWO, ACOA, and PSOA systems have provided maximum AD of 0.11, 0.27, 0.30, 0.84 and 1.90 s correspondingly. Moreover, on 60 UAVs, the COAER-UAVC system has resulted in minimum AD of 3.16 s while the EENFNC-MRP, KHOA, GWO, ACOA, and PSOA approaches have provided maximum AD of 5.37, 6.70, 7.46, 9.33 and 10.66 s correspondingly.


Figure 8: AD analysis of COAER-UAVC approach under varying UAVs
These extensive result analyses showcased the enhanced performance of the COAER-UAVC model on UAV communication.
In this study, we have introduced a new COAER-UAVC technique for effective UAV communication. The presented COAER-UAVC technique concentrated on the identification of optimal routes for communication between the UAVs. It is primarily based on the coati characteristics in nature: if attack and hunt iguanas and escaping from the predators. Besides, the presented COAER-UAVC technique concentrates on the design of fitness functions to minimize energy utilization and communication delay. To depict the optimum performance of the COAER-UAVC system, a varied group of simulations was performed. The experimental outcomes verified that the COAER-UAVC model has assured enhanced performance over other approaches. In the future, data aggregation techniques can be applied to improve UAV communication results.
Funding Statement: The authors extend their appreciation to the Deanship of Scientific Research at King Khalid University for funding this work through Large Groups Project under grant number (235/44). Princess Nourah bint Abdulrahman University Researchers Supporting Project number (PNURSP2023R114), Princess Nourah bint Abdulrahman University, Riyadh, Saudi Arabia. The authors would like to thank the Deanship of Scientific Research at Umm Al-Qura University for supporting this work by Grant Code: (22UQU4310373DSR71). This study is supported via funding from Prince Sattam bin Abdulaziz University project number (PSAU/2023/R/1444).
Conflicts of Interest: The authors declare that they have no conflicts of interest to report regarding the present study.
References
1. M. Faraji-Biregani and R. Fotohi, “Secure communication between UAVs using a method based on smart agents in unmanned aerial vehicles,” The Journal of Supercomputing, vol. 77, no. 5, pp. 5076–5103, 2021. [Google Scholar]
2. A. Sharma, P. Vanjani, N. Paliwal, C. M. W. Basnayaka, D. N. K. Jayakody et al., “Communication and networking technologies for UAVs: A survey,” Journal of Network and Computer Applications, vol. 168, no. 2, pp. 102739, 2020. [Google Scholar]
3. H. Fatemidokht, M. K. Rafsanjani, B. B. Gupta and C. H. Hsu, “Efficient and secure routing protocol based on artificial intelligence algorithms with UAV-assisted for vehicular ad hoc networks in intelligent transportation systems,” IEEE Transactions on Intelligent Transportation Systems, vol. 22, no. 7, pp. 4757–4769, 2021. [Google Scholar]
4. X. Tan, Z. Zuo, S. Su, X. Guo and X. Sun, “Research of security routing protocol for UAV communication network based on AODV,” Electronics, vol. 9, no. 8, pp. 1185, 2020. [Google Scholar]
5. J. Xue, H. Zhang and Q. Hu, “A low-cost communication security scheme of UAV based on multi-round reverse auction model,” Pervasive and Mobile Computing, vol. 85, no. 3, pp. 101652, 2022. [Google Scholar]
6. Y. Cai, Z. Wei, R. Li, D. W. K. Ng and J. Yuan, “Joint trajectory and resource allocation design for energy-efficient secure UAV communication systems,” IEEE Transactions on Communications, vol. 68, no. 7, pp. 4536–4553, 2020. [Google Scholar]
7. V. Hassija, V. Chamola, A. Agrawal, A. Goyal, N. C. Luong et al., “Fast, reliable, and secure drone communication: A comprehensive survey,” IEEE Communications Surveys & Tutorials, vol. 23, no. 4, pp. 2802– 2832, 2021. [Google Scholar]
8. R. Zhuo, S. Song and Y. Xu, “UAV communication network modeling and energy consumption optimization based on routing algorithm,” Computational and Mathematical Methods in Medicine, vol. 2022, pp. 1–10, 2022. [Google Scholar]
9. J. Li and F. Shang, “Research on performance optimization method of uav communication link in emergency communication environment,” Security and Communication Networks, vol. 2022, no. 7, pp. 1–7, 2022. [Google Scholar]
10. H. S. Mansour, M. H. Mutar, I. A. Aziz, S. A. Mostafa, H. Mahdin et al., “Cross-layer and energy-aware aodv routing protocol for flying ad-hoc networks,” Sustainability, vol. 14, no. 15, pp. 8980, 2022. [Google Scholar]
11. V. F. S. Francelin, J. Daniel and S. Velliangiri, “Intelligent agent and optimization-based deep residual network to secure communication in UAV network,” International Journal of Intelligent Systems, vol. 37, no. 9, pp. 5508–5529, 2022. [Google Scholar]
12. M. Namdev, S. Goyal and R. Agarwal, “An optimized communication scheme for energy efficient and secure flying ad-hoc network (FANET),” Wireless Personal Communications, vol. 120, no. 2, pp. 1291–1312, 2021. [Google Scholar]
13. X. Wang, L. Fu, N. Cheng, R. Sun, T. Luan et al., “Joint flying relay location and routing optimization for 6g uav-iot networks: A graph neural network-based approach,” Remote Sensing, vol. 14, no. 17, pp. 4377, 2022. [Google Scholar]
14. A. Khan, F. Aftab and Z. Zhang, “Self-organization based clustering scheme for FANETs using glowworm swarm optimization,” Physical Communication, vol. 36, no. 5, pp. 100769, 2019. [Google Scholar]
15. K. Singh and A. K. Verma, “TBCS: A trust based clustering scheme for secure communication in flying ad-hoc networks,” Wireless Personal Communications, vol. 114, no. 4, pp. 3173–3196, 2020. [Google Scholar]
16. M. Kayalvizhi and S. Ramamoorthy, “Blockchain-based secure data transmission for uav swarm using modified particle swarm optimization path planning algorithm,” International Journal of Advanced Computer Science and Applications, vol. 12, no. 11, pp. 554–563, 2021. [Google Scholar]
17. Z. Zhen, D. Xing and C. Gao, “Cooperative search-attack mission planning for multi-UAV based on intelligent self-organized algorithm,” Aerospace Science and Technology, vol. 76, no. 4, pp. 402–411, 2018. [Google Scholar]
18. D. Meng, Y. Xiao, Z. Guo, A. Jolfaei, L. Qin et al., “A data-driven intelligent planning model for UAVs routing networks in mobile internet of things,” Computer Communications, vol. 179, no. 7, pp. 231–241, 2021. [Google Scholar]
19. M. Dehghani, Z. Montazeri, E. Trojovská and P. Trojovský, “Coati optimization algorithm: A new bio-inspired metaheuristic algorithm for solving optimization problems,” Knowledge-Based Systems, vol. 259, no. 1, pp. 110011, 2022. [Google Scholar]
Cite This Article
 Copyright © 2023 The Author(s). Published by Tech Science Press.
Copyright © 2023 The Author(s). Published by Tech Science Press.This work is licensed under a Creative Commons Attribution 4.0 International License , which permits unrestricted use, distribution, and reproduction in any medium, provided the original work is properly cited.


 Submit a Paper
Submit a Paper Propose a Special lssue
Propose a Special lssue View Full Text
View Full Text Download PDF
Download PDF Downloads
Downloads
 Citation Tools
Citation Tools