 Open Access
Open Access
ARTICLE
An Efficient Three-Party Authenticated Key Exchange Procedure Using Chebyshev Chaotic Maps with Client Anonymity
1 Department of Applied Mathematics, Yeshwantrao Chavan College of Engineering, Nagpur, 441110, Maharashtra, India
2 Department of Statistics, Rashtrasant Tukadoji Maharaj Nagpur University, Nagpur, 440033, Maharashtra, India
3 Department of Computer Science, College of Computer Science, King Khalid University, Abha, Saudi Arabia
4 Department of Post Graduate Studies and Research in Mathematics, Jaywanti Haksar Government Post-Graduate College, College of Chhindwara University, Betul, 460001, Madhya Pradesh, India
* Corresponding Author: Chandrashekhar Meshram. Email:
Computers, Materials & Continua 2023, 75(3), 5337-5353. https://doi.org/10.32604/cmc.2023.037324
Received 30 October 2022; Accepted 22 February 2023; Issue published 29 April 2023
Abstract
Internet of Things (IoT) applications can be found in various industry areas, including critical infrastructure and healthcare, and IoT is one of several technological developments. As a result, tens of billions or possibly hundreds of billions of devices will be linked together. These smart devices will be able to gather data, process it, and even come to decisions on their own. Security is the most essential thing in these situations. In IoT infrastructure, authenticated key exchange systems are crucial for preserving client and data privacy and guaranteeing the security of data-in-transit (e.g., via client identification and provision of secure communication). It is still challenging to create secure, authenticated key exchange techniques. The majority of the early authenticated key agreement procedure depended on computationally expensive and resource-intensive pairing, hashing, or modular exponentiation processes. The focus of this paper is to propose an efficient three-party authenticated key exchange procedure (AKEP) using Chebyshev chaotic maps with client anonymity that solves all the problems mentioned above. The proposed three-party AKEP is protected from several attacks. The proposed three-party AKEP can be used in practice for mobile communications and pervasive computing applications, according to statistical experiments and low processing costs. To protect client identification when transferring data over an insecure public network, our three-party AKEP may also offer client anonymity. Finally, the presented procedure offers better security features than the procedures currently available in the literature.Keywords
The term “Internet of Things (IoT),” which is widely described as “a global network of networked devices uniquely reachable, based on standard communication protocols,” may have been coined by Kevin Ashton from Procter & Gamble in 1998 [1]. Since then, usage of IoT has sharply increased in part because of the digital revolution (such as widespread connectivity even in developing nations and the ongoing improvement of information and communication technologies). Mobile users may make payments for goods online, pay bills, and conduct other electronic transactions by subscribing to various remote services thanks to the rapid development of low-power and highly efficient networks. Despite being very portable, mobile computing devices are typically insecure and superficial to steal or lose. Without security measures, an unauthorized person might access the data kept on them. For instance, if the data is “sniffed out of the air” during wireless connections or any malware is introduced, intruders may obtain access illegally. Even more severe consequences, such as disabled devices, the loss of personal data, the revelation of non-public data, or charges of misused usage against the device owner, may occur from a lack of authentication and privacy. In addition to the data they hold, mobile computing devices pose a serious security risk since they may give clients access to other services that store or show non-public data. Before distant servers offer clients services for nearly all of these transactions, mutual authentication and client privacy is necessary for the key exchange. Applications for industrial networks [2], wireless sensor networks [3,4], dispersed networks [5–7], as well as Radio Frequency Identification (RFID) systems [8–10] in particular, place a high priority on authentication and privacy.
Many analogous procedures [11–14] have been proposed by researchers to ensure the security of secret keys that are exchanged over an insecure public network, including the Authenticated Key Exchange Procedure (AKEP) based on passwords. The AKEP based on password enables two parties to agree on a standard session key across an insecure public network while maintaining a single memorable password [15–17]. Generally speaking, provided clients use strong passwords that offer adequate entropy, password-based authentication can withstand brute force and dictionary assaults. However, one inherent issue with password-based authentication exists: consumers struggle to memorize long text sequences. Therefore, even though they are aware that the passwords might not be secure, most clients choose memorable passwords, making it difficult to defend against numerous attacks.
Bellovin et al. [18] first introduced the AKEP based on the password procedure in 1992. After ten years, other related procedures have been presented, including the two-party AKEP [11,12] and the three-party AKEP [19,20]. Two-party AKEPs, on the other hand, are not appropriate in the significant peer-to-peer architecture, according to Hassan et al. [21]. Some of the three-party AKEPs are also insufficiently efficient or secure for usage in real-world applications. Recently, in 2005 and 2007, respectively, Abdalla et al. [22], Lu et al. [23], and Algubili et al. [24] introduced three effective three-party AKEPs. Sadly, both methods were still susceptible to offline or online dictionary attacks that were undetectable.
Three-party AKEP based on the password was suggested by Deng et al. [25] in 2009, and it was deemed secure by the universal compostable framework. Deng et al. AKEP, however, is vulnerable to an offline dictionary attack by any other client, according to Yuan et al. [26]. Huang’s [27] procedure could not withstand undetectable online dictionary attacks and key-compromise impersonation attacks, according to Yoon et al. [28], who presented a protocol in 2011. Later, Yoon et al. [29] introduced a different procedure and demonstrated how Lou et al. [30] procedure was susceptible to an attacker’s off-line password guessing attempts. The security flaws in Huang’s [27] procedure were later discovered by Wu et al. [31], who also suggested a three-party AKEP based on the password to fix the issues with Huang’s procedure. The procedure developed by Wu et al. required the most difficult computations due to its numerous exponential computations. Also, their procedure was unable to guarantee client anonymity. Table 1 provides a brief comparison of related research with our proposed AKEP.
It is challenging to create a three-party AKEP that is both lightweight and secure. Numerous three-party-AKEP have been put forth and afterward shown to be insecure. For instance, Zhang et al. [32] suggested a three-party-AKEP based on the standard model’s verification feature in 2019. It employs anonymous authentication for server and client authentication to strengthen procedure security, which raises computation costs. A three-party-AKEP based on the verification element on the ideal lattice was proposed by Shu et al. [33] in 2021. It reduces space complexity but requires six rounds of communication to negotiate a session key, increasing communication overhead. Peikert’s [34] error reconciliation mechanism was adopted by Shu et al. [33].
This paper introduced a three-party-AKEP with user anonymity using Chebyshev chaotic maps to increase security and efficiency.
• The presented three-party AKEP encrypts and decrypts the data sent by the user or the server using Chebyshev chaotic maps.
• The presented three-party AKEP can also offer client and server mutual authentication and client anonymity to ensure that clients’ identities, which are conveyed via an insecure public network, are guaranteed.
• The presented three-party AKEP has low computing and communication costs and can fend off various attacks, according to the security, statistical experiment and performance analysis.
The rest of this paper is structured as follows. The definitions of Chebyshev chaotic maps are introduced briefly in Section 2. Section 3 presents the proposed AKEP. In Section 4, we analyze the projected AKEP and demonstrate that it can withstand several attacks. Section 5 will examine the performance of our AKEP using the former protocols and statistical experiments. Finally, in Section 6, we present our conclusion.
The section provides a brief overview of the trigonometry in Galois fields, Chebyshev polynomials over Galois fields that are used in the proposed procedure, and the necessary security notations.
2.1 Trigonometry in Galois Fields (
Here we assume that calculations over
Definition 1. The set
Definition 2. Let
In this case, we modify the notational scheme established in [35]. Properties like the unit circle and the addition of arcs [35] are naturally shared by the
The description of the
Lemma 1. For
Definition 3. The unimodular set of
Proposition 1.
Proposition 2. The structure
Lemma 2. If
Example 1. Consider

Even if
Theorem 1. Let
Example 2. Let

2.2 Chebyshev Polynomials (CP) over Galois Fields
In this section, we will look at the properties of CP over Galois fields. There is a definition in [37] that uses the
Definition 4. The CP over
It can be seen that Eq. (3) is analogous to the arc
where
Proposition 3. Let
Proof: From Definition 4, we have
After using the formula for the extension of arcs, we can reformulate the preceding statement as
Since
If we need to estimate
The semigroup possessions and the chaotic possessions are two significant characteristics that the Chebyshev polynomials display [39,40].
(1) The semigroup possessions:
(2) The chaotic possessions:
The Chebyshev polynomial map
It is challenging to solve in polynomial time the following two CP problems [36,38,39]:
(a) The discrete logarithm problem (DLP) is defined as the task of determining the number
(b) The Diffie-Hellman problem (DHP) is defined as the task of computing the value
3 The AKEP Based on Chebyshev Chaotic Maps
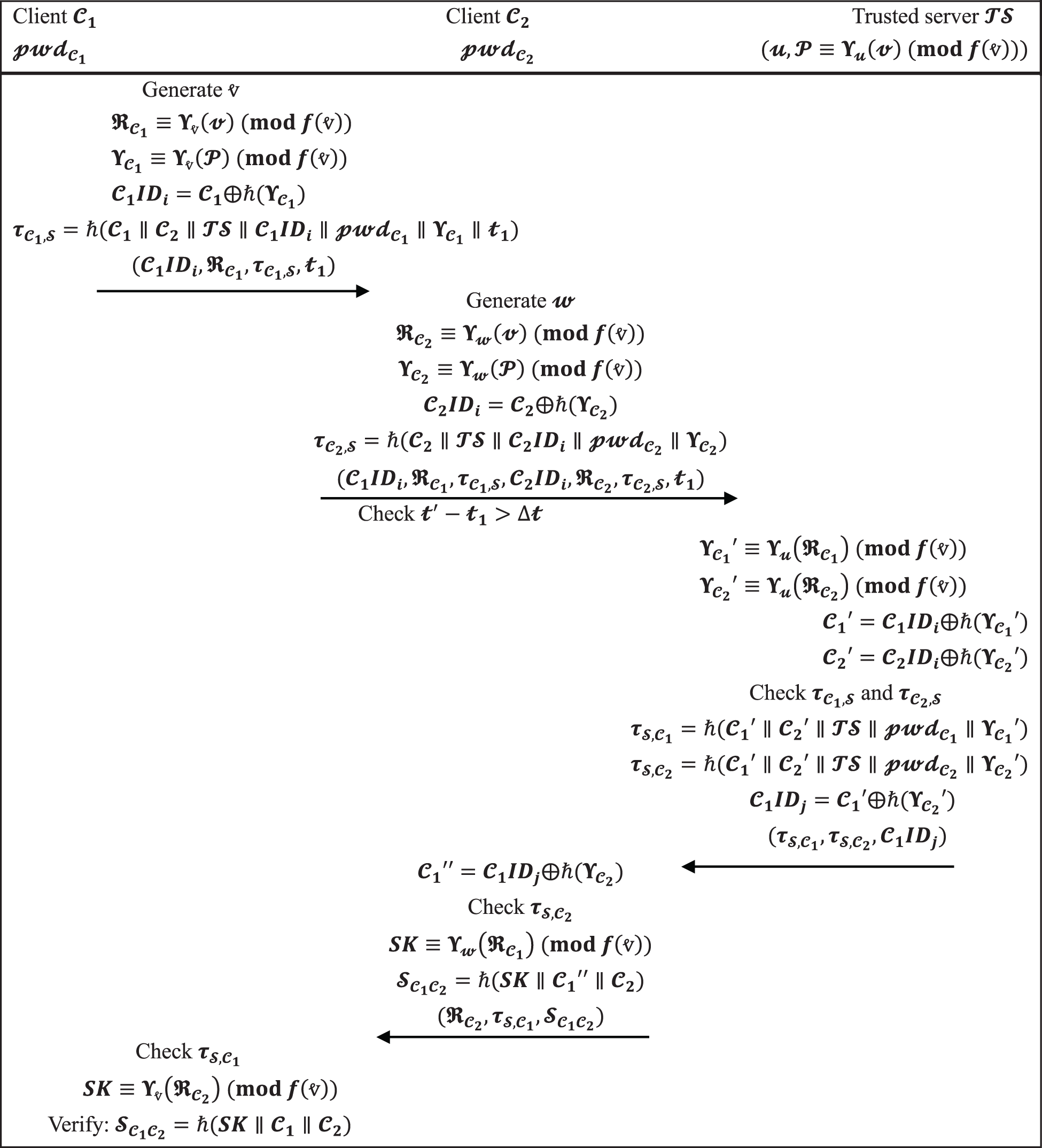
The projected procedure with user anonymity using extended chaotic maps is detailed in depth in this section. Table 4 summarizes the notations utilized in our protocol.

At first, the distant server

Figure 1: Chebyshev-based Decisional Diffie-Hellman problem
(1) Client
Client
(2) The client then sends back the response
The second client,
(3) When receiving
(4) After receiving
(5) Client
4 Security Investigation and Discussion
In this segment, we examine the security and performance of our presented procedure and demonstrate its ability to withstand various attacks. Here, we explain several security analyses in our proposed process.
Proposition 4.1: The presented AKEP can accomplish off-line dictionary attacks.
Proof: The attacker might deduce the password from the element
Proposition 4.2: The presented AKEP can accomplish undetectable online dictionary attacks.
Proof: The attacker may attempt to impersonate a legitimate client by intercepting the messages
Proposition 4.3: The presented AKEP can accomplish detectable online dictionary attacks.
Proof: The attacker may attempt to impersonate a legitimate client by intercepting the messages
Proposition 4.4: The presented AKEP can counterattack replay and impersonation attacks.
Proof: A client’s messages may be intercepted by the attacker, who may then replay them to the server in the subsequent run. However, by verifying the accuracy of the timestamp
Proposition 4.5: The presented AKEP can achieve user anonymity.
Proof: The attacker may listen in on the client’s conversation with the trusted server and attempt to identify the client’s true identity to gather some of the client’s security-sensitive data. The real identities of clients
Proposition 4.6: The presented AKEP can accomplish mutual authentication.
Proof: Mutual authentication between the client and the server is possible with our presented procedure. Step 3 of our procedure requires the server
Proposition 4.7: The presented AKEP can prevent denial-of-service (DoS) attacks.
Proof: When
Proposition 4.8: The presented AKEP can accomplish Bergamo et al.’s attack [41].
Proof: This attack is conceivable in two scenarios. First, an attacker must have the relevant parameters
Statistical experiments will be used to demonstrate the Chebyshev-based Decisional Diffie-Hellman (CDDH) assumption. A fast graphical tool for comparing two probability distributions in statistics is the quantile-quantile plot
The vertical axis shows estimated quintiles from the
Fig. 1 depicts a comparison of the distributions of
In addition, we provide the Chebyshev polynomial’s function image for random

Figure 2: Chebyshev polynomials image map
5.2 Efficiency and Performance Analysis
To illustrate the security performance and effectiveness of our new design, we will compare the security properties of our given AKEP with four previous AKEPs introduced by Wu et al. [31], Yanrong et al. [44], Guo et al. [45], and Lee [46] in Table 5. In Table 5, we can see that our AKEP is more secure than other AKEPs. To express the execution time necessary for modular multiplication, one-way hash function, chaotic map operation, group modular exponentiation, and symmetric encryption/decryption operation, notations such as


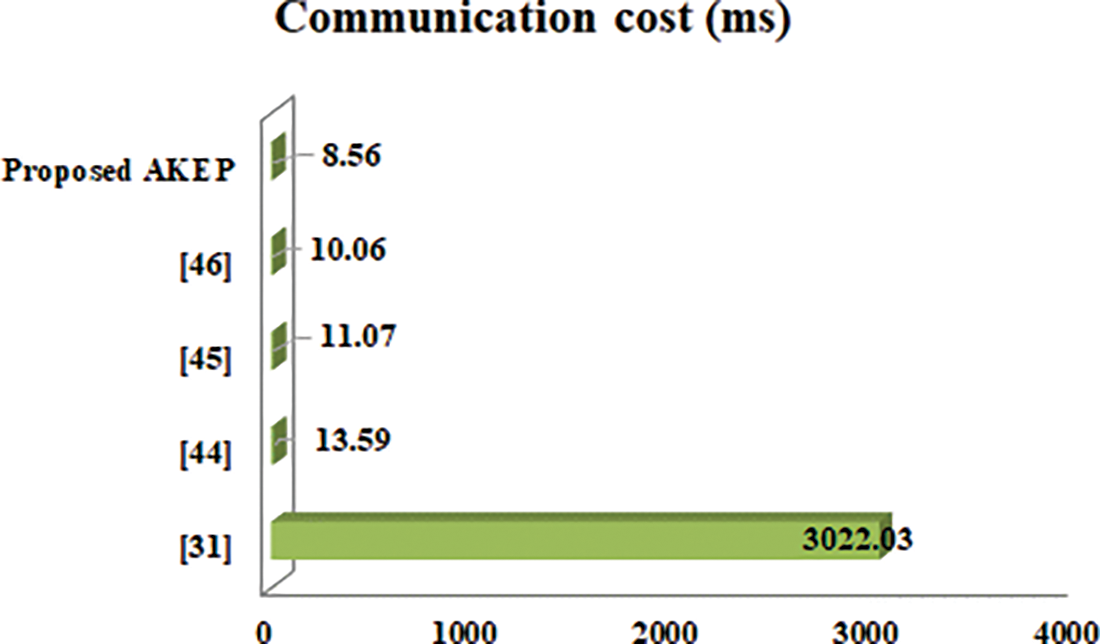
Figure 3: The total communication costs
In this paper, we propose a three-party password-based AKEP with client anonymity that uses Chebyshev chaotic maps and is more efficient and secure than previous procedures. Chebyshev chaotic maps are used to encrypt and decrypt data transmitted by either the client or the server to increase security and efficiency. Because it solely employs hash and XOR operations, we were able to show through security and performance studies that our AKEP is more effective and secure than others. To protect client identification when transferring data over an insecure public network, our AKEP may also offer client anonymity. In the future, we plan to provide efficient, lightweight, provably secure authentication protocols for the Internet of Things based on authenticated key exchange procedures using Chebyshev chaotic maps.
Acknowledgement: The authors would like to thank anonymous reviewers of Computers, Materials & Continua Journal for their careful and helpful comments. Prof. Monia Hadj Alouane-Turki extends her appreciation to the Deanship of Scientific Research at King Khalid University for funding this work through Small Groups. Project under grant number (RGP.1/257/43).
Funding Statement: The authors received no specific funding for this study.
Conflicts of Interest: The authors declare that they have no conflicts of interest to report regarding the present study.
References
1. L. Atzori, A. Iera and G. Morabito, “The internet of things: A survey,” Computer Networks, vol. 54, no. 15, pp. 2787–2805, 2010. [Google Scholar]
2. A. Valenzano, L. Durante and M. Cheminod, “Review of security issues in industrial networks,” IEEE Transactions on Industrial Informatics, vol. 9, no. 1, pp. 277–293, 2013. [Google Scholar]
3. V. C. Gungor and G. P. Hancke, “Industrial wireless sensor networks: Challenges, design principles and technical approaches,” IEEE Transactions on Industrial Electronics, vol. 56, no. 10, pp. 4258–4265, 2009. [Google Scholar]
4. D. Liu, M. C. Lee and D. Wu, “A node-to-node location verification method,” IEEE Transactions on Industrial Electronics, vol. 57, no. 5, pp. 1526–1537, 2010. [Google Scholar]
5. C. Chang and C. Lee, “A secure single sign-on mechanism for distributed computer networks,” IEEE Transactions on Industrial Electronics, vol. 59, no. 1, pp. 629–637, 2012. [Google Scholar]
6. G. Wang, J. Yu and Q. Xie, “Security analysis of a single sign-on mechanism for distributed computer networks,” IEEE Transactions on Industrial Informatics, vol. 9, no. 1, pp. 294–302, 2013. [Google Scholar]
7. L. Barolli and F. Xhafa, “JXTA-Overlay: A P2P platform for distributed, collaborative and ubiquitous computing,” IEEE Transactions on Industrial Electronics, vol. 58, no. 6, pp. 2163–2172, 2010. [Google Scholar]
8. Y. Huang, W. Lin and H. Li, “Efficient implementation of RFID mutual authentication protocol,” IEEE Transactions on Industrial Electronics, vol. 59, no. 12, pp. 4784– 4791, 2012. [Google Scholar]
9. B. Wang and M. Ma, “A server independent authentication scheme for RFID systems,” IEEE Transactions on Industrial Informatics, vol. 8, no. 3, pp. 689–696, 2012. [Google Scholar]
10. B. Fabian, T. Ermakova and C. Muller, “SHARDIS: A privacy enhanced discovery service for RFID-based product information,” IEEE Transactions on Industrial Informatics, vol. 8, no. 3, pp. 707–718, 2012. [Google Scholar]
11. T. Y. Chang, M. S. Hwang and W. P. Yang, “A communication-efficient three-party password authenticated key exchange protocol,” Information Sciences, vol. 181, no. 1, pp. 217–226, 2011. [Google Scholar]
12. T. Y. Chang, W. P. Yang and M. S. Hwang, “Simple authenticated key agreement and protected password change protocol,” Computers & Mathematics with Applications, vol. 49, no. 5–6, pp. 703–714, 2005. [Google Scholar]
13. T. F. Lee, T. Hwang and C. L. Lin, “Enhanced three-party encrypted key exchange without server public keys,” Computers & Security, vol. 23, no. 7, pp. 571–577, 2004. [Google Scholar]
14. S. W. Lee, H. S. Kim and K. Y. Yoo, “Efficient verifier-based key agreement protocol for three parties without server’s public key,” Applied Mathematics and Computation, vol. 167, no. 2, pp. 996–1003, 2005. [Google Scholar]
15. D. He, Y. Chen and J. Chen, “Cryptanalysis and improvement of an extended chaotic maps-based key agreement protocol,” Nonlinear Dynamics, vol. 69, no. 3, pp. 1149–1157, 2012. [Google Scholar]
16. J. W. Lo, J. Z. Lee, M. S. Hwang and Y. P. Chu, “An advanced password authenticated key exchange protocol for imbalanced wireless networks,” Journal of Internet Technology, vol. 11, no. 7, pp. 997–1004, 2010. [Google Scholar]
17. J. W. Lo, S. C. Lin and M. S. Hwang, “A parallel password-authenticated key exchange protocol for wireless environments,” Information Technology and Control, vol. 39, no. 2, pp. 146–151, 2010. [Google Scholar]
18. S. M. Bellovin and M. Merritt, “Encrypted key exchange: Password-based protocols secure against dictionary attacks,” in Proc. of IEEE Computer Society Symp. on Security and Privacy, Oakland, CA, USA, pp. 72–84, 1992. [Google Scholar]
19. C. C. Lee, R. X. Chang and H. J. Ko, “Improving two novel three-party encrypted key exchange protocols with perfect forward secrecy,” International Journal of Foundations of Computer Science, vol. 21, no. 6, pp. 979–991, 2010. [Google Scholar]
20. C. C. Lee and Y. F. Chang, “On security of a practical three-party key exchange protocol with round efficiency,” Information Technology and Control, vol. 37, no. 4, pp. 333–335, 2008. [Google Scholar]
21. M. I. Hassan and A. Abdullah, “A new grid resource discovery framework,” The International Arab Journal of Information Technology, vol. 8, no. 1, pp. 99–107, 2011. [Google Scholar]
22. M. Abdalla and D. Pointcheval, “Interactive Diffie-Hellman assumptions with applications to password-based authentication,” Lecture Notes in Computer Science, vol. 3570, pp. 341–356, 2005. [Google Scholar]
23. R. Lu and Z. Cao, “Simple three-party key exchange protocol,” Computers & Security, vol. 26, no. 1, pp. 94–97, 2007. [Google Scholar]
24. B. H. T. Algubili, N. Kumar, H. Lu, A. A. Yassin, R. Boussada et al., “EPSAPI: An efficient and provably secure authentication protocol for an IoT application environment,” Peer-to-Peer Networking and Applications, vol. 15, pp. 2179–2198, 2022. [Google Scholar]
25. M. Deng, J. Ma and F. Le, “Universally composable three party password-based key exchange protocol,” China Communications, vol. 6, no. 3, pp. 150–154, 2009. [Google Scholar]
26. W. Yuan, L. Hu, H. Li and J. Chu, “Offline dictionary attack on a universally composable three-party password-based key exchange protocol,” Procedia Engineering, vol. 15, no. 11, pp. 1691–1694, 2011. [Google Scholar]
27. H. F. Huang, “A simple three-party password-based key exchange protocol,” International Journal of Communication Systems, vol. 22, no. 7, pp. 857–862, 2009. [Google Scholar]
28. E. J. Yoon and K. Y. Yoo, “Cryptanalysis of a simple three-party password-based key exchange protocol,” International Journal of Communication Systems, vol. 24, no. 4, pp. 532–542, 2011. [Google Scholar]
29. E. J. Yoon and K. Y. Yoo, “Cryptanalysis of an efficient three-party password-based key exchange scheme,” Procedia Engineering, vol. 29, no. 5, pp. 3972–3979, 2012. [Google Scholar]
30. D. C. Lou and H. F. Huang, “Efficient three-party password-based key exchange scheme,” International Journal of Communication Systems, vol. 24, no. 4, pp. 504–512, 2011. [Google Scholar]
31. S. Wu, K. Chen and Y. Zhu, “Enhancements of a three-party password-based authenticated key exchange protocol,” International Arab Journal of Information Technology, vol. 10, no. 3, pp. 215–221, 2013. [Google Scholar]
32. Q. Zhang, P. Chaudhary, S. Kumari, Z. Kong and W. Liu, “Verifier-based anonymous password-authenticated key exchange protocol in the standard model,” Mathematical Biosciences and Engineering, vol. 16, no. 5, pp. 3623–3640, 2019. [Google Scholar] [PubMed]
33. Q. Shu, S. B. Wang, B. Hu and L. D. Han, “Verifier-based three-party password-authenticated key exchange protocol from ideal lattices,” Journal of Cryptologic Research, vol. 8, no. 2, pp. 294–306, 2021. [Google Scholar]
34. C. Peikert, “Lattice cryptography for the internet,” in Proc. of the Int. Workshop on Post-quantum Cryptography, Waterloo, ON, Canada, pp. 197–219, 2014. [Google Scholar]
35. R. M. Campello de Souza, H. M. A. de Oliveira Kauffman, A. N. Kauffman and A. J. A. Paschoal, “Trigonometry in finite fields and a new Hartley transform,” in Proc. of IEEE Int. Symp. Information Theory (ISIT’98), Cambridge, MA, USA, pp. 293, 1998. [Google Scholar]
36. J. B. Lima, D. Panariob and R. M. Campello de Souza, “Public-key encryption based on Chebyshev polynomials over GF(q),” Information Processing Letters, vol. 111, pp. 51–56, 2010. [Google Scholar]
37. J. B. Lima, R. M. Campello de Souza and D. Panariob, “Security of publickey cryptosystems based on Chebyshev polynomials over prime finite fields,” in Proc. IEEE Int. Symp. Information Theory (ISIT 2008), Toronto, ON, Canada, pp. 1843–1847, 2008. [Google Scholar]
38. J. C. Mason and D. C. Handscomb, Chebyshev polynomials. Boca Raton, Florida: Chapman & Hall/CRC, 2003. [Google Scholar]
39. C. Meshram, C. C. Lee, S. G. Meshram and A. Meshram, “OOS-SSS: An efficient online/offline subtree-based short signature scheme using chebyshev chaotic maps for wireless sensor network,” IEEE Access, vol. 8, no. 1, pp. 80063–80073, 2020. [Google Scholar]
40. C. Meshram, C. C. Lee, A. S. Ranadive, C. T. Li, S. G. Meshram et al., “A subtree-based transformation model for cryptosystem using chaotic maps under cloud computing environment for fuzzy user data sharing,” International Journal of Communication Systems, vol. 33, no. 7, pp. e4307, 2020. [Google Scholar]
41. P. Bergamo, P. D’Arco, A. De Santis and L. Ko Carev, “Security of public-key cryptosystems based on Chebyshev polynomials,” IEEE Transactions on Circuits and Systems, vol. 52, no. 7, pp. 1382–1393, 2005. [Google Scholar]
42. J. Li, L. Wang, L. Wang, X. Wang, Z. Huang et al., “Verifiable chebyshev maps-based chaotic encryption schemes with outsourcing computations in the cloud/fog scenarios,” Concurrency and Computation: Practice and Experience, vol. 31, no. 5, pp. e4523, 2018. [Google Scholar]
43. D. Kahrobaei, C. Koupparis and V. Shpilrain, “Public key exchange using matrices over group rings,” Groups, Complexity, Cryptology, vol. 5, no. 1, pp. 11–97, 2013. [Google Scholar]
44. L. Yanrong and Z. Dawei, “A chaotic-map-based password-authenticated key exchange protocol for telecare medicine information systems,” Security and Communication Networks, vol. 2021, pp. 1–8, 2021. https://doi.org/10.1155/2021/7568538 [Google Scholar] [CrossRef]
45. X. Guo and J. Zhang, “Secure group key agreement protocol based on chaotic hash,” Information Sciences, vol. 180, no. 20, pp. 4069–4074, 2010. [Google Scholar]
46. T. -F. Lee, “Enhancing the security of password authenticated key agreement protocols based on chaotic maps,” Information Sciences, vol. 290, pp. 63–71, 2015. [Google Scholar]
47. C. Meshram, S. G. Meshram, R. W. Ibrahim, H. A. Jalab, S. S. Jamal et al., “Conformal chebyshev chaotic maps based remote user password authentication protocol using smart card,” Complex & Intelligent Systems, vol. 8, pp. 973–987, 2022. [Google Scholar]
48. M. B. Algehawi and A. Samsudin, “A new identity-based encryption (IBE) scheme using extended Chebyshev polynomial over finite fields Zp,” Physics Letters A, vol. 374, pp. 4670–4674, 2010. [Google Scholar]
49. M. H. Ibrahim, S. Kumari, A. K. Das, M. Wazid and V. Odelu, “Secure anonymous mutual authentication for star two-tier wireless body area networks,” Computer Methods and Programs in Biomedicine, vol. 135, no. 1, pp. 37–50, 2016. [Google Scholar] [PubMed]
50. C. Meshram, A. L. Imoize, S. S. Jamal, P. Tambare, A. R. Alharbi et al., “An efficient three-factor authenticated key agreement technique using FCM under HC-IoT architectures,” Computers, Materials & Continua, vol. 72, no. 1, pp. 1373–1389, 2022. [Google Scholar]
51. C. Meshram, A. L. Imoize, S. S. Jamal, A. Aljaedi and A. R. Alharbi, “SBOOSP for massive devices in 5G WSNs using conformable chaotic maps,” Computers, Materials & Continua, vol. 71, no. 3, pp. 4591–4608, 2022. [Google Scholar]
Cite This Article
 Copyright © 2023 The Author(s). Published by Tech Science Press.
Copyright © 2023 The Author(s). Published by Tech Science Press.This work is licensed under a Creative Commons Attribution 4.0 International License , which permits unrestricted use, distribution, and reproduction in any medium, provided the original work is properly cited.


 Submit a Paper
Submit a Paper Propose a Special lssue
Propose a Special lssue View Full Text
View Full Text Download PDF
Download PDF
 Downloads
Downloads
 Citation Tools
Citation Tools