 Open Access
Open Access
ARTICLE
WiFi6 Dynamic Channel Optimization Method for Fault Tolerance in Power Communication Network
1 Nanjing Power Supply Branch, State Grid Jiangsu Electric Power Co., Nanjing, 210000, China
2 State Key Laboratory of Networking and Switching Technology, Beijing University of Posts and Telecommunications, Beijing, 100876, China
* Corresponding Author: Guangchang Yang. Email:
Computers, Materials & Continua 2023, 75(3), 5501-5519. https://doi.org/10.32604/cmc.2023.035759
Received 02 September 2022; Accepted 03 March 2023; Issue published 29 April 2023
Abstract
As the scale of power networks has expanded, the demand for multi-service transmission has gradually increased. The emergence of WiFi6 has improved the transmission efficiency and resource utilization of wireless networks. However, it still cannot cope with situations such as wireless access point (AP) failure. To solve this problem, this paper combines orthogonal frequency division multiple access (OFDMA) technology and dynamic channel optimization technology to design a fault-tolerant WiFi6 dynamic resource optimization method for achieving high quality wireless services in a wirelessly covered network even when an AP fails. First, under the premise of AP layout with strong coverage over the whole area, a faulty AP determination method based on beacon frames (BF) is designed. Then, the maximum signal-to-interference ratio (SINR) is used as the principle to select AP reconnection for the affected users. Finally, this paper designs a dynamic access selection model (DASM) for service frames of power Internet of Things (IoTs) and a scheduling access optimization model (SAO-MF) based on multi-frame transmission, which enables access optimization for differentiated services. For the above mechanisms, a heuristic resource allocation algorithm is proposed in SAO-MF. Simulation results show that the method can reduce the delay by 15% and improve the throughput by 55%, ensuring high-quality communication in power wireless networks.Keywords
With the development of the IoT, the requirements for communication quality in power business scenarios have gradually increased [1–3]. Especially in dense WIFI scenarios, where multiple users gather in a specific area, each with different service requirements, there is a need to guarantee the communication quality of each user [4,5]. Each AP is usually placed very close to each other [1,4]. To address the user transmission problem in dense WIFI scenarios [6], this paper will study the IEEE802.11ax standard [7] and combine the features and technical characteristics of IEEE802.11ax to study the service requirements in dense power service scenarios. It is guaranteed that the wireless network can provide continuous high-quality service even after the failure of one AP [8].
Compared with the previous generations of IEEE802.11 standards, 802.11ax firstly introduced the OFDMA technology, Basic Service Set (BSS) Coloring technology and Target Wakeup Time (TWT) technology [9], among which, OFDMA technology is one of the most representative technologies. How to achieve fault tolerance for multiple access points using OFDMA technology of WIFI6 requires a combination of factors [10]. In the future electric power scenario, the transmission of devices is bound to develop in the direction of multiple services and concurrency. Not only will the distribution of users become denser, but the resource allocation during transmission will also become more complex [11,12]. For multi-service transmission problems in dense scenarios, resource units (RUs) can be allocated to terminals according to the maximization of throughput, or according to delay requirements, or under Quality of Service (QoS) to ensure service transmission requirements. Ultimately, the realization of fault tolerance is the focus of DASM.
Combined with OFDMA technology of WiFi6, this paper designs a WiFi6 dynamic channel optimization method for fault tolerance, i.e., under the premise of satisfying the strong coverage of all devices in a specific scenario, beacon frames are sent periodically between neighboring APs to determine whether the AP is working properly. When an AP fails, stations (STAs) in its coverage area join a new AP. DASM dynamically allocates channels to meet service transmission requirements and improve resource utilization, taking into account service differences, resource utilization and maximum completion delay.
The main contributions to this work are summarized as follow:
• This paper proposed a beacon frame-based method for determining faulty APs. This method does not require the global scheduler to know the operating status of all APs. APs periodically send beacon frames to announce the presence of the network according to the 802.11 protocol and allow neighboring APs to detect the beacon frames at any time. Once the beacon is not received within a certain time, it can be determined that the AP is faulty.
• Develop a dynamic access selection model (DASM) for power IoT service frames. DASM dynamically differentiates data frame lengths, balancing data transfer rates and information interaction overheads, ultimately improving resource utilization.
• Develop a scheduling access optimization model based on multi-frame transmission (SAO-MF): For scheduling access, SAO-MF allows multi-frame transmission under one-time scheduling, and optimizes scheduling access by considering service priority and transmission delay. With the goal of maximizing the scheduling utility function, a low-complexity heuristic algorithm suitable for the scheduling model of SAO-MF is proposed. The rationality of the model and algorithm is verified by simulation.
The rest of this paper is organized as follows: the next section overviews the related works that have been conducted in the areas of the unique features of WIFI6 and WIFI fault tolerance. Section 3 introduces the related technologies of WIFI6. Section 4 describes fault AP determination and service set division model. Section 5 describes cross-slot scheduling access optimization method. Section 6 introduces the methodology proposed in this paper. Section 7 overviews the experiment and the analyzes results. Finally, the conclusion is in Section 8.
2.1 The Unique Features of WIFI6
802.11ax introduces OFDMA technology to provide parallel transmission with multiple users simultaneously. OFDMA divides the transmission bandwidth into multiple non-overlapping orthogonal subcarriers, and the user can select one or more subcarriers for parallel transmission. Since resource management and allocation have always been a key issue in wireless networks, many researchers have studied the OFDMA technology of WIFI6.
Specifically, in [13], the authors propose a distributed RU selection method for deep reinforcement learning (C-DRL) based on convolutional neural networks (CNNs), in which each STA is trained locally online based only on energy detection and confirmation packets. In [14], to improve the efficiency of uplink random access (OURA), a multi-busy tone arbitration mechanism (MBTA) was developed to reduce conflicts between sites competing for RU. In [15], the author considers the joint strategy design of resource unit allocation and power control of WIFI6 uplink, and splits the problem into minimized power problems and RU allocation problems under delay constraints to achieve the goal of reducing average latency. In [16], the authors combine WIFI6’s OFDMA technology and TWT technology to propose a scheduling channel access scheme to ensure that the STA is close to but smaller than RU at each TWT wake-up time, avoiding conflicts and improving throughput.
In [1], the authors designed a heuristic algorithm for multiple, dense user wireless scenarios to meet throughput while resisting AP failures. In [17], the authors mainly study the self-healing ability of wireless cellular networks, and compensate adjacent cells through antenna reconstruction and power compensation, thereby filling the coverage gap and improving users’ QoS.
However, the above work rarely combines the technology of WIFI6 with the fault recovery scenario. A fault determination and service set division model for AP failures in WIFI6 scenarios using the technical features of OFDMA is proposed. Then a WiFi6 dynamic channel optimization method for fault tolerance is proposed. To sum up, this paper studies the fault tolerance of wireless networks to ensure that the network after an AP of failure can still complete the system data transmission, and ultimately ensure the continuity of the network.
Table 1 lists the differences between this paper and the existing works.

3 Related Technologies of WIFI6
3.1 Physical (PHY) Layer Key Technology of WIFI6
WIFI6 introduces OFDMA technology to provide multi-user parallel transmission. OFDMA divides the transmission bandwidth into multiple non-overlapping orthogonal subcarriers, and users can select one or more subcarriers for parallel transmission. As shown in Fig. 1, the traditional WIFI protocol adopts the transmission mode of Orthogonal Frequency Division Multiplexing (OFDM), which allows only one user to transmit at any time; WIFI6 achieves multi-user parallel transmission by introducing OFDMA technology at the PHY layer, OFDMA has the following three advantages over OFDM technology: First, a more detailed channel allocation, WIFI6 can choose the best RU according to the channel quality for data transmission; The second is to provide better QoS, in OFDMA mode, since a sender only occupies part of the entire channel’s resources, it can send data from multiple users at the same time, thus reducing the latency of STA access; The third is more user concurrency and higher user bandwidth, as can be seen from the Fig. 1, OFDMA can satisfy multi-user transmission in the same time slot, providing more user concurrency.
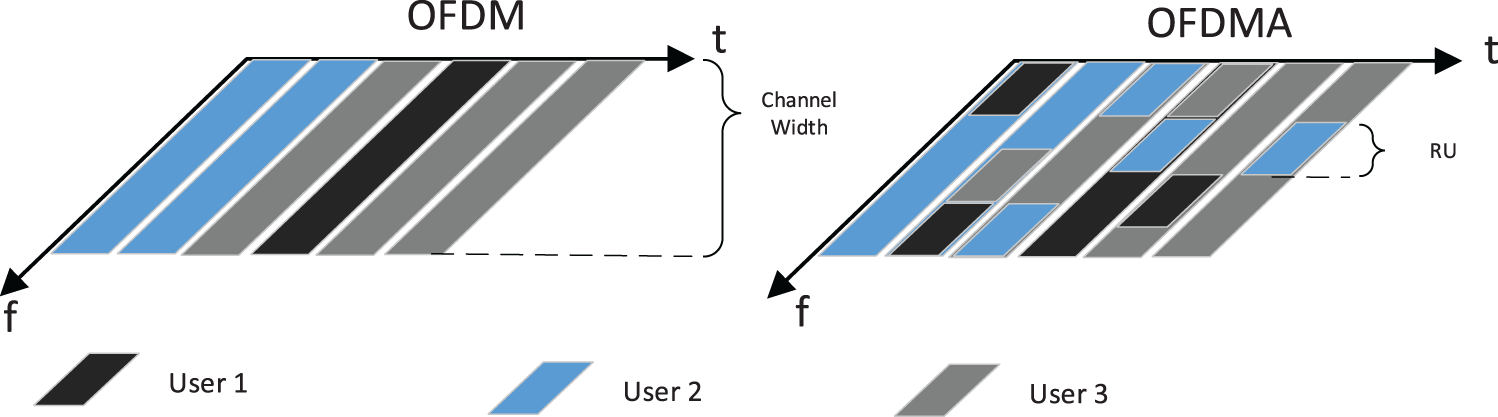
Figure 1: Comparison of OFDM and OFDMA principles
3.2 Media Access Control (MAC) Layer Key Technology of WIFI6
WiFi6 enhances the AP’s function, which supports two uplink transmission modes, random access and scheduled access [18]. Downlink transmission is simpler compared to uplink transmission, and this paper focuses on the more complex OFDMA uplink access problem:
WiFi6 supports two access modes for OFDMA uplink transmission, uplink OFDMA random access (UORA) and uplink OFDMA non-random access (UONRA). The former STA obtains RU resources by competing for access, while the latter requires STAs and AP to interact with each other in advance to complete the data transmission.
Fig. 2 shows the transmission process of UONRA. Through the information interaction process between the buffer status reports (BSR) frame and the Clear to Send (CTS) frame, the AP obtains the STA cache report information, and then the AP starts the uplink data transmission by sending a trigger frame (TF) frame, which contains the scheduling information (transmission time, power control information and RU allocation information). Then, the STAs receiving the TF frame upload the data in the physical protocol data unit (PPDU). Finally, the AP feeds back the MU-acknowledgement character (MU-ACK) to confirm the acceptance [19,20].
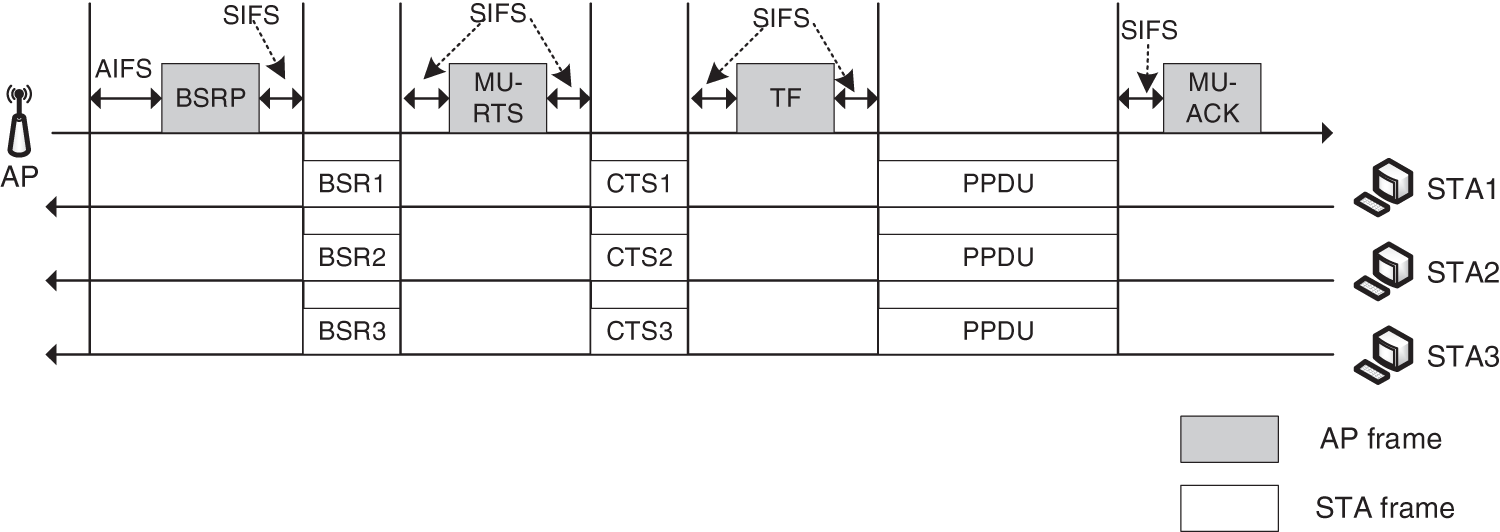
Figure 2: The procedure of UONRA transmission
4 Fault AP Determination and Service Set Division Model
The symbols used in this model are shown in Table 2.

4.1 Fault AP Determination Based on Beacon Frame
In view of the requirement of high reliable and high-quality communication in the wireless network of power, it is assumed that all STAs are covered by AP signals in a global strong coverage network, and each STA is guaranteed to be within the communication range of at least two APs. The neighbor AP listening method is used to determine whether the AP is faulty. In 802.11 communication protocol, data is encapsulated into a frame. A frame refers to a block of data in communication. According to 802.11 protocol, there are three types of frames, namely control frames, management frames and data frames.
The common control frames include Request to Send (RTS) frames, CTS frames and Acknowledge Character (ACK) frames, which are mainly used for handshake communication and forwarding acknowledgement at the end of the competitive and non-competitive periods. As the name implies, data frames are used to carry data.
Management frames are mainly used to control and negotiate the relationship between APs and STAs, such as association, authentication, synchronization, etc. This section focuses on management frames. Among them, the beacon frame is a very important frame, mainly used to announce the presence of an AP network. By sending beacons periodically, the AP can let the mobile users know the existence of the network and thus adjust the necessary parameters to join the network. In the basic network, the AP must be responsible for sending beacon frames, which range over the basic service area. In this paper, the principle of beacon frame is used. Each AP not only periodically sends beacon frame to the STAs under its jurisdiction, but also receives beacon frames from its neighboring APs.
AP will send beacon frames periodically to announce the existence of the 802.11 network. Neighboring APs always listens for the beacon frame. If the node fails and the neighboring node fails to receive the beacon frame within a certain period, the node loses the ability to communicate.
Fig. 3 is a beacon frame sending mode, the STAs passively listen to the beacon frame around the AP periodic broadcast (about 100 ms), the frame contains all the service parameters of the AP. Not only all STAs can receive the beacon frame, but also neighboring APs can listen to beacon frames to determine whether the network is functioning properly.
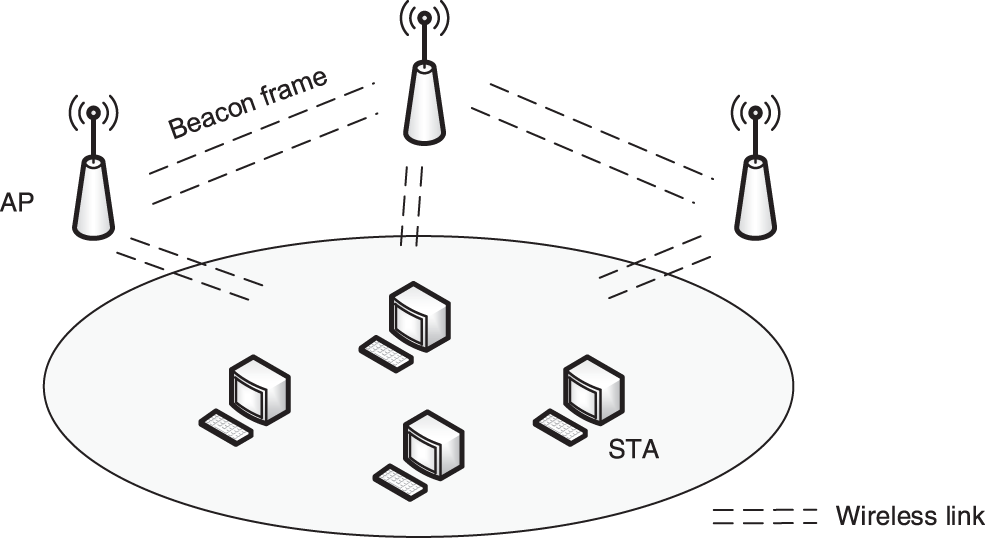
Figure 3: Beacon frame sending mode
If an AP fails to receive beacon frames from neighboring APs on time, the AP may be restarted due to abnormal power failure or common configuration delivery. The restart time of a WIFI6 device is about 3–5 min, but the processing delay of most real-time applications is in the millisecond type. If STAs wait for the device to restart and then transfer task, it will eventually cause most tasks to fail to meet the latency standard. This paper takes 5 min as the cycle. After dynamic channel allocation is started, beacon frames from the neighboring AP are received again every 5 min. If they are received, the restart is considered successful. After an AP is restarted, the terminal connects to the original AP after completing the current services to ensure full utilization of resources.
At the same time, if the STA cannot complete the data transmission after repeated retransmission, a new AP is selected for reconnection. Selecting connection for APs is described in the next section.
4.2 Service Set Division After AP Failure
Based on the above analysis, this paper determines whether the AP is in normal operation by receiving beacon frames sent periodically by the neighboring APs. This section describes that when an AP fails, the terminals covered by that failed AP will join the neighboring APs to continue receiving services under the condition that the service delay is satisfied. Fig. 4 shows an overlapping basic service set (OBSS), where each STA transmits data within the coverage of its own AP.
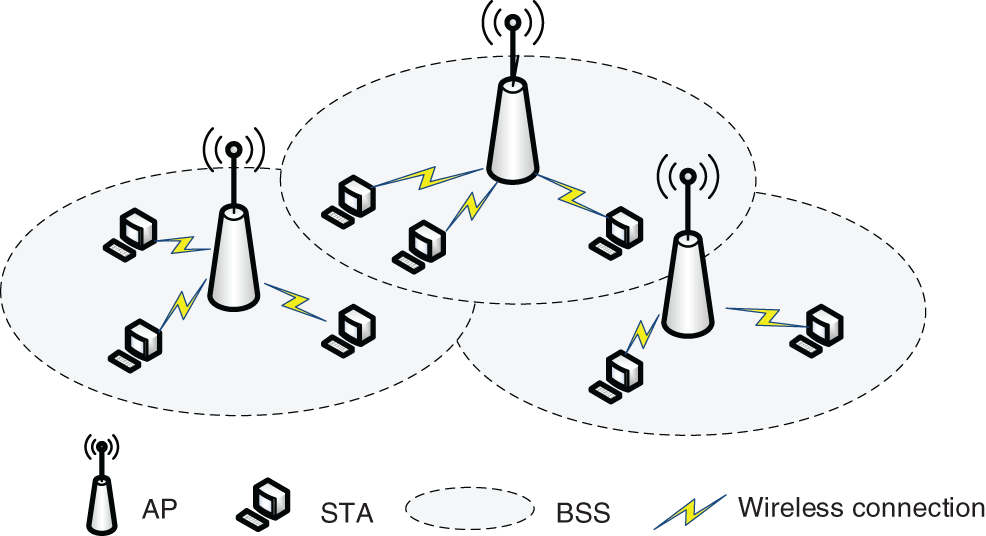
Figure 4: Overlap basic service sets
When an AP in the network fails, the STAs will select a neighboring AP to connect, as shown in Fig. 5. These users are set to
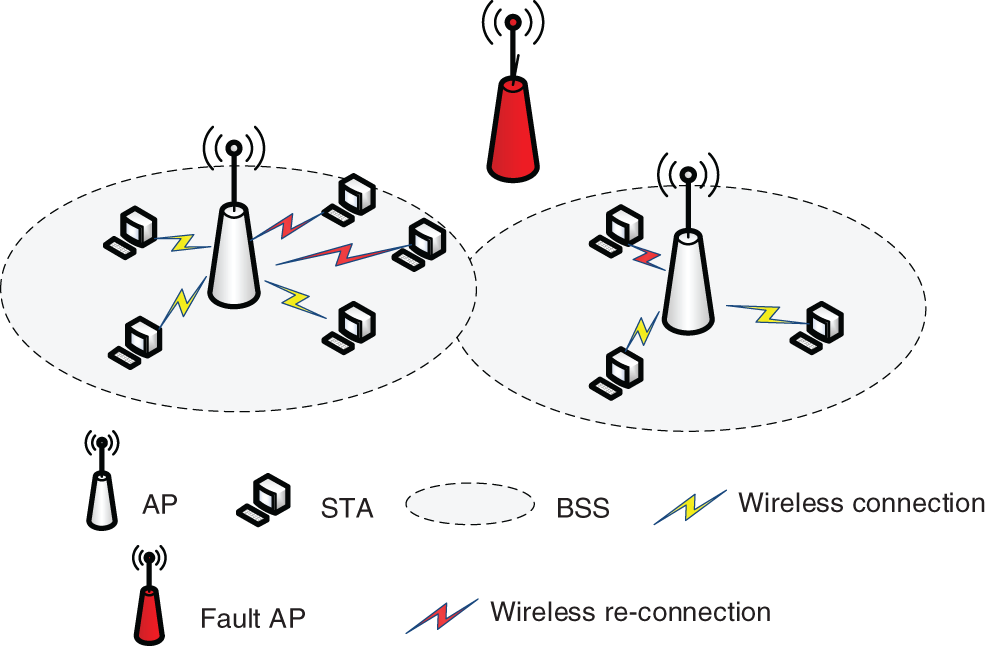
Figure 5: Overlapping basic service sets in the event of a failure

5 Cross-Slot Scheduling Access Optimization Method with Differentiated Service Priorities
After the STA of the faulty AP selects the new AP by reconnection algorithm, this paper proposes a differentiated WIFI6 access resource optimization method for power IoT services based on transmission time slot scheduling using OFDMA technology of WIFI6. Firstly, this paper establishes DASM based on power IoT service frames and SAO-MF based on service priorities from the perspective of resource transmission efficiency and service priorities. Then, clustering algorithm and heuristic algorithm are proposed. Finally, a reasonable and efficient channel allocation is achieved.
5.1 DASM Based on Service Frame of Power IoTs
After the affected STAs re-connect AP, this paper weighs the balance between the information interaction overhead and the data transmission rate, and designs a dynamic access selection model (DASM) for different data frames, specifically the long frame scheduling access (UONRA), and the short frame random competitive access (UORA), which improves the efficiency of data transmission and the utilization of resources. Fig. 2 is the transmission process of UONRA [21].
As can be seen from the Fig. 6, the UONRA mechanism requires two rounds of information interaction to be completed before data transmission, which is not friendly to the transmission of short data frames. Meanwhile, it has been demonstrated in the literature that UORA is more suitable for short frame transmission [14].
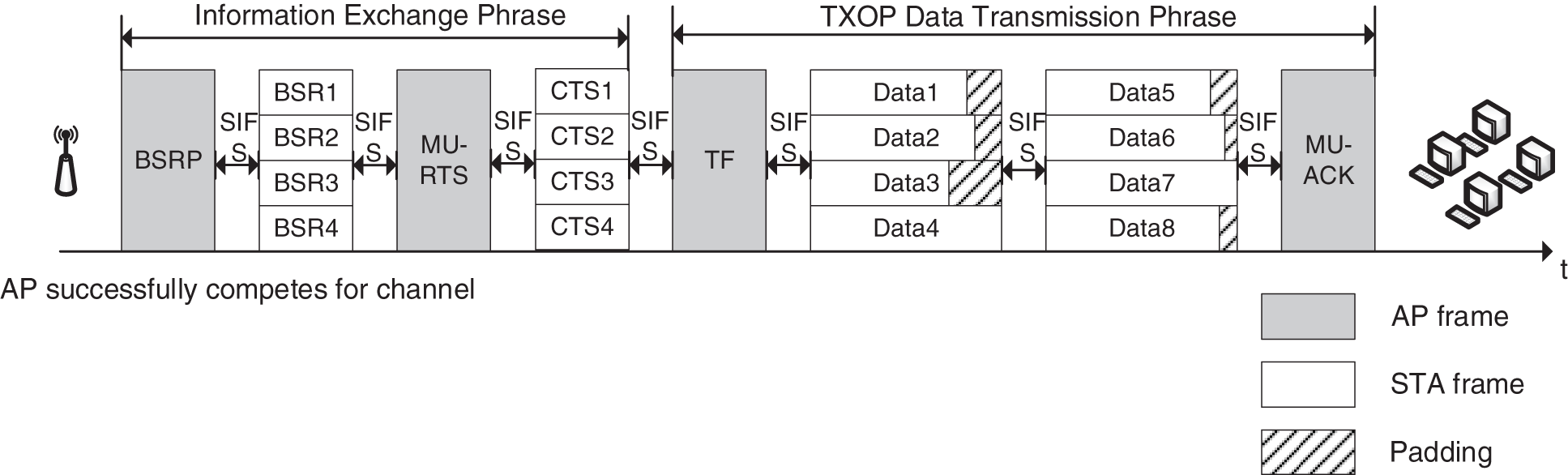
Figure 6: OFDMA uplink multi-frame transmission mode
However, it is impossible to distinguish whether a data frame is long or short with a definite value. In addition, whether from the perspective of resource awesome or scheduling allocation, it is desirable to reduce blank fields to improve resource utilization. 802.11ax stipulates that the AP can appropriately adjust the duration of each Transmission Opportunity (TXOP) [22]. Therefore, the transmission of multi-frame data can be performed within one TXOP. For synchronous transmission, this paper sets the length of each frame as the maximum length of the group of data frames, and padding is performed on other terminals. Minimize the length difference of each group of data frames to achieve the goal of improving resource utilization.
The AP allocates the ratio of short and long frames to the number of requested users to obtain the boundary of short and long frames. Subsequently, the STA is informed of the boundary based on the information interaction phase and selects the appropriate transmission mode.
The AP differentiates RU resources by following the principle of minimizing the internal variance between UORA and UONRA scheduling data while satisfying the resource reservation variance
where
5.2 SAO-MF Based on Service Priority
After the DASM, random access for short frames is not discussed in this paper, while for scheduling access, SAO-MF introduces a scheduling utility function and considers both delay and priority factors.
The SINR determines the MCS level of the RU assigned to the STA. In SAO-MF, the SINR is defined by formula (7):
where
The STA feeds CSI information to the AP through BSR frames, In SAO-MF, the statistical modeling of the channel is referenced to [23] as follows.
where
Each STA feeds
SAO-MF specifies five levels of task types, and STA feeds this information to the AP during the BSR interaction. Referring to [24], SAO-MF sets the following five services to classify the priority, where a lager number indicates a lower priority. As shown in Table 4.

Finally, the SAO-MF mechanism to maximize the scheduling utility function is formulated as follows.
where
In SAO-MF, the utility function is equal to SINR transmitted by each STA.
where
Defining the emergency factor
To sum up, the overall methodology is shown in Fig. 7. The Fault AP determination and service set division module has been described in detail in the previous section. Therefore, this section will focus on introducing the algorithm of the DASM and the SAO-MF.
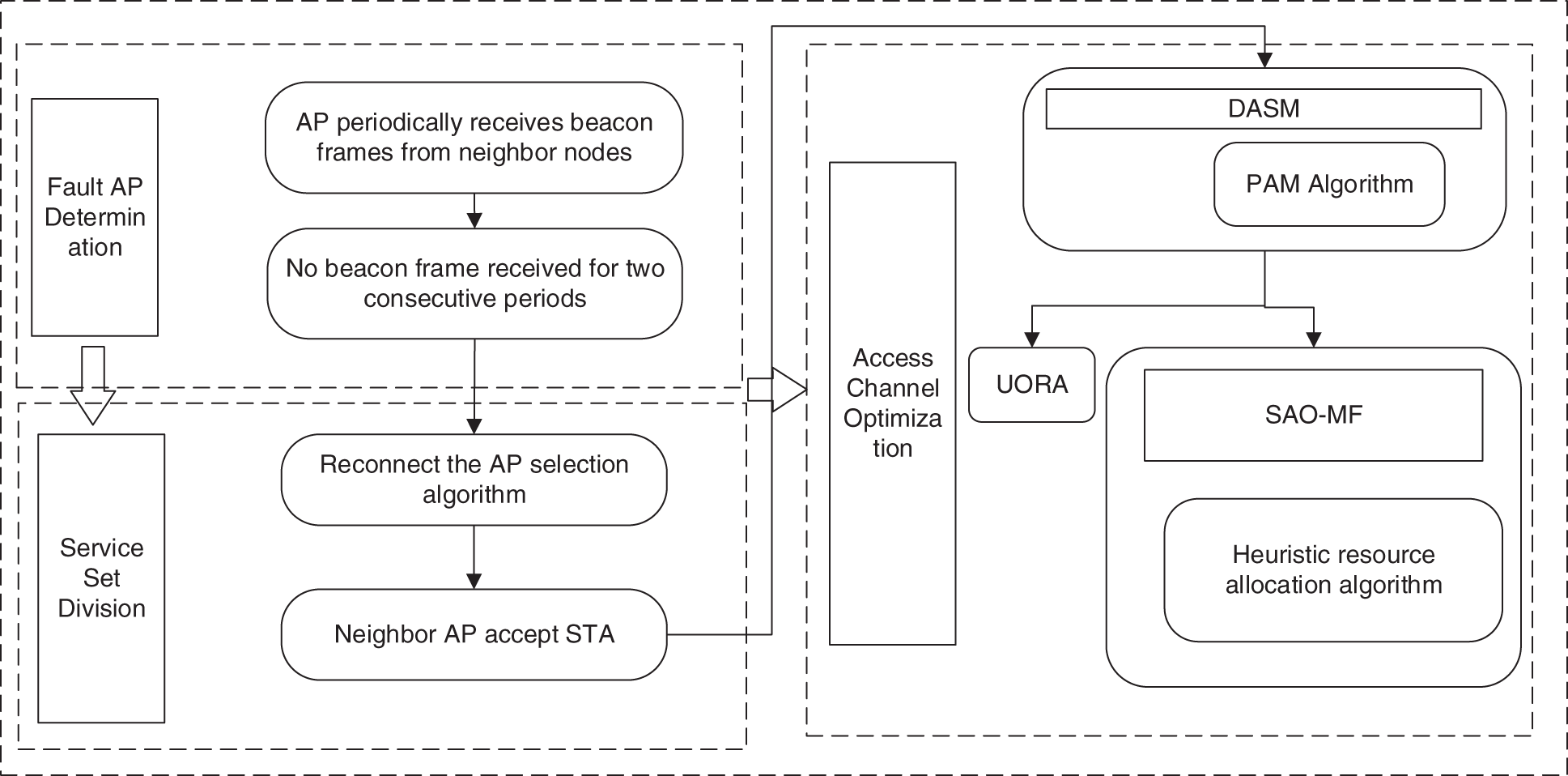
Figure 7: Framework of dynamic channel optimization method for fault tolerance
DASM uses the Partitioning Around Medoids (PAM) algorithm to distinguish between short and long frames. The PAM algorithm is introduced with reference to [19], and will not be repeated in this paper. In addition, the number of STA in a BSS range is mostly a few dozens, which is a small range of values and meets the requirements of the PAM algorithm.
The delay threshold of each terminal is used as the clustering sample, namely
SAO-MF proposes the maximum SINR scheduling algorithm that integrates delay and priority. The procedure is as follows: Eqs. (7) and (8) calculate the SINR, then the utility function value is obtained by Eq. (13). Finally, the RU is allocated to the STA with the highest
The data transmission rate obtained for each STA is obtained from the MCS, and the MCS levels and transmission rates (Mb/s) at GI = 3.2us in the 802.11ax standard are tabulated below [25].
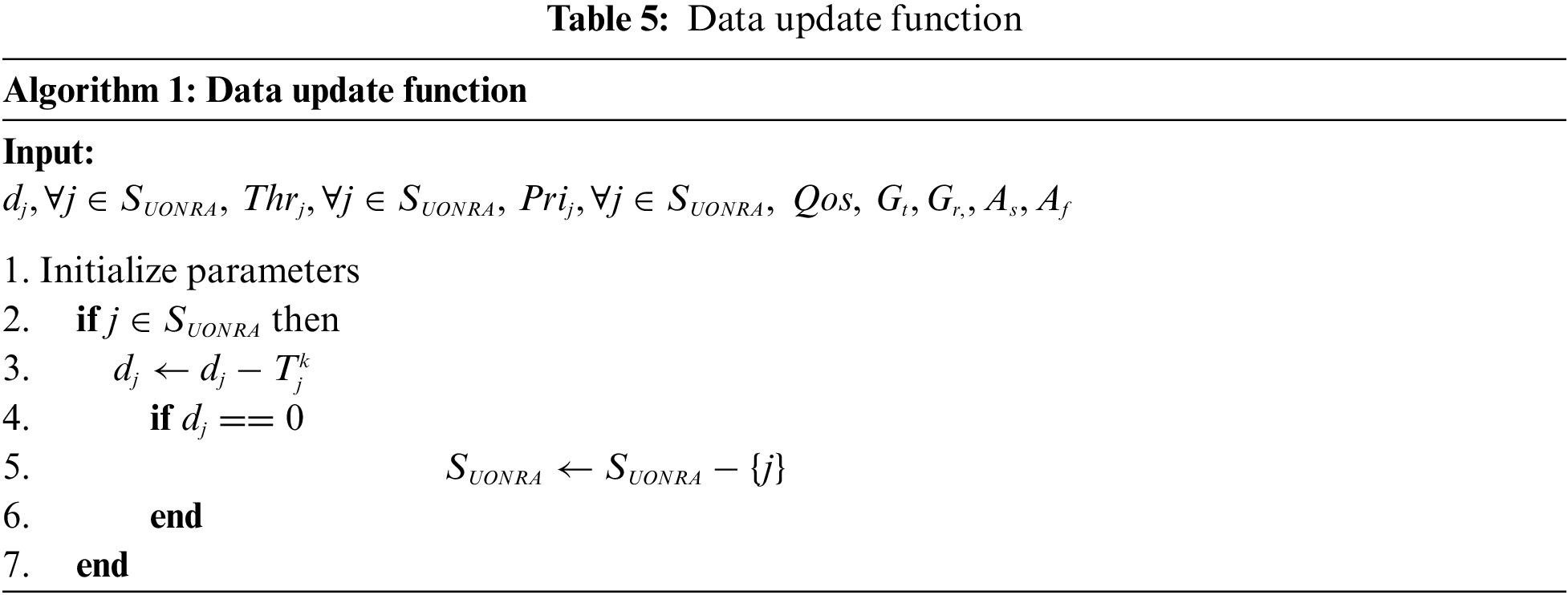
In SAO-MF, AP updates the data to be uploaded by STA and the data after uploading before each scheduling. Then, the AP selects the STA with the largest utility function for resource allocation. Tables 5 and 6 are the data update function and the heuristic resource allocation algorithm, respectively.

In this paper, the proposed fault tolerant WIFI6 dynamic channel optimization allocation method is simulated by matrix laboratory (MATLAB). The problem of optimal resource allocation under BSS after a fault occurs is considered. The feasibility of the model is verified from three aspects. First, this paper verifies the heuristic channel allocation algorithm and proves that it can approach optimal performance. Secondly, the QoS-distinguishing scheduling algorithm, the SINR-based scheduling algorithm and the Round Robin algorithm are compared to verify the superiority of the QoS-distinguishing scheduling algorithm. Finally, the enhancement of system throughput by the fault tolerance mechanism is verified.
The parameter settings are shown in Table 7.

To verify the heuristic resource allocation algorithm, this paper compares the heuristic algorithm with the optimal algorithm, and MATLAB Software for Disciplined Convex Programming (CVX) is used to solve the optimal problem. The average running time of the two algorithms under each iteration is shown in Table 8:

As can be seen from Table 8, the running time of the heuristic algorithm is shorter. This paper simulates the ratio of the throughput box plot of the two algorithms. As shown in Fig. 8, the comparison can be seen that the box plot of the two algorithms is very similar, and the average throughput obtained by both algorithms is about 180 bps/s. Moreover, the other four parameters are also very close, which shows that the throughput calculated using the heuristic algorithm is almost the same as the optimal algorithm performance. Although the average throughput of the terminal is improved by moving the box plot upward with the optimal algorithm, it increases the running time by almost three times. Fig. 9 shows a comparison of the two sets of data after excluding the outliers, the similarity is as high as 96.2%. Meanwhile, Fig. 10 shows a comparison of the two sets of delay after excluding the outliers, the similarity is as high as 99.2%. therefore, the algorithm proposed in this paper can achieve near-optimal results while minimizing complexity.
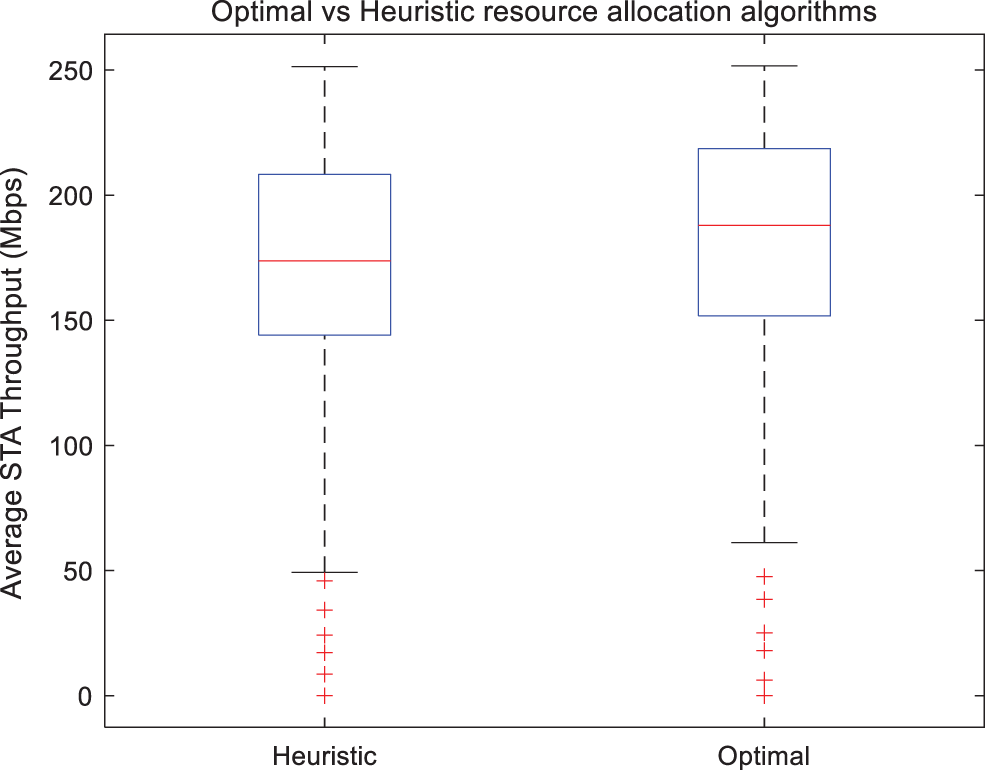
Figure 8: Heuristic vs. optimal: box plot of throughout
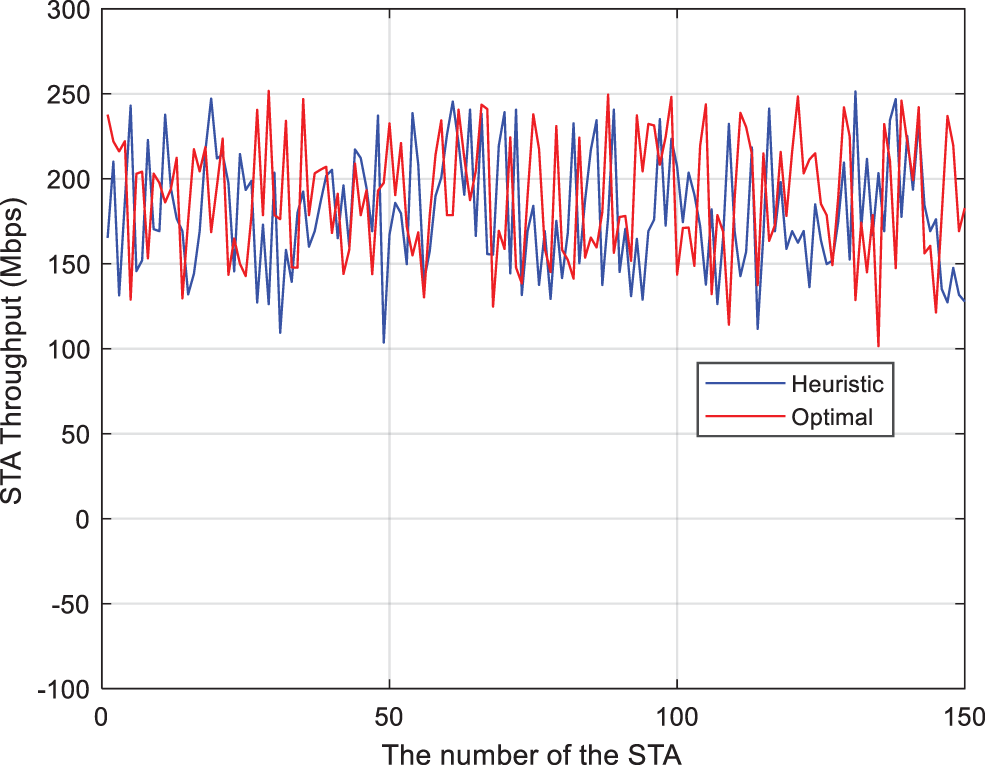
Figure 9: Heuristic vs. optimal: average throughout
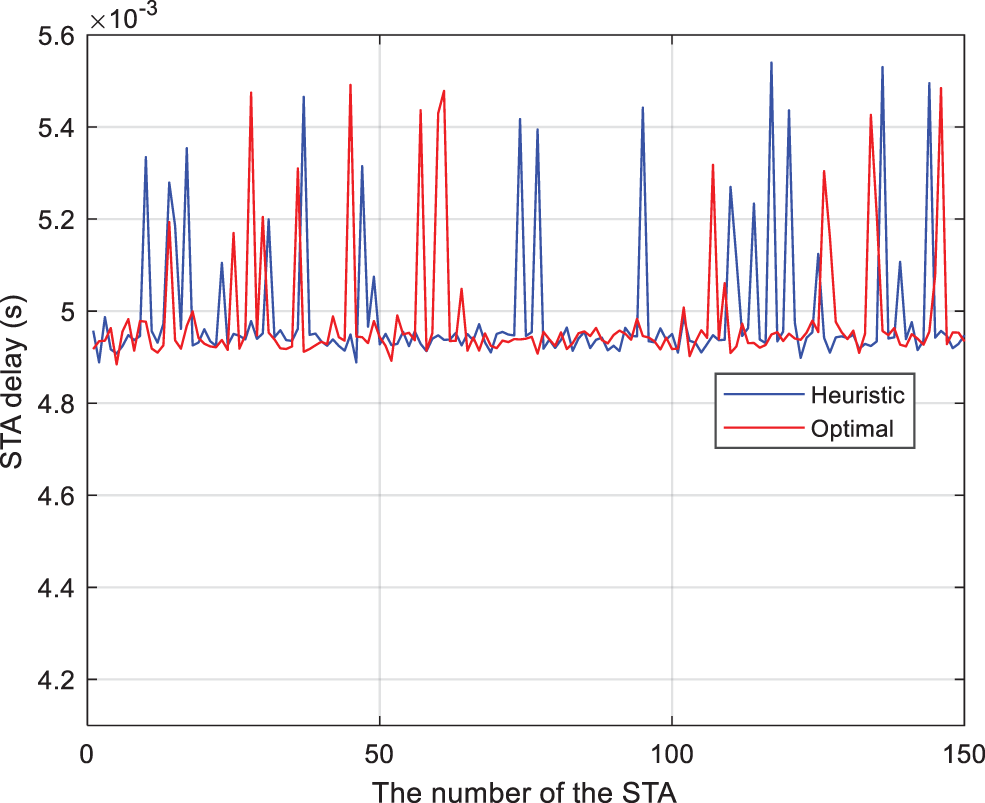
Figure 10: Heuristic vs. optimal: Delay
Fig. 11 compares the average throughput vs. the number of terminals under three algorithms, namely, the QoS differentiated scheduling algorithm (QoS = 0.5), the SINR-based scheduling algorithm (QoS = 1), and the Round Robin (RR) algorithm. With the increase of the number of STAs, the average throughput of all the above three algorithms tends to decrease, which is because with the increase of the number of terminals, some STAs cannot transmit data properly due to conflicts. Under the RR algorithm, the average throughput of the system varies little with the increase of the number of terminals, and the overall stability is at a relatively low level. This is because when the AP uses the RR algorithm for scheduling, the channel conditions of each channel and the QoS between different services are not considered, resulting in low system performance. The scheduling algorithm that distinguishes QoS and the scheduling algorithm based on SINR is very close in performance when there are fewer terminals, but with the increase of the number of terminals, the average throughput of the QoS scheduling algorithm decreases more slowly. Finally, in the saturation state, the QoS-distinguishing scheduling algorithm also has about 55% higher throughput.
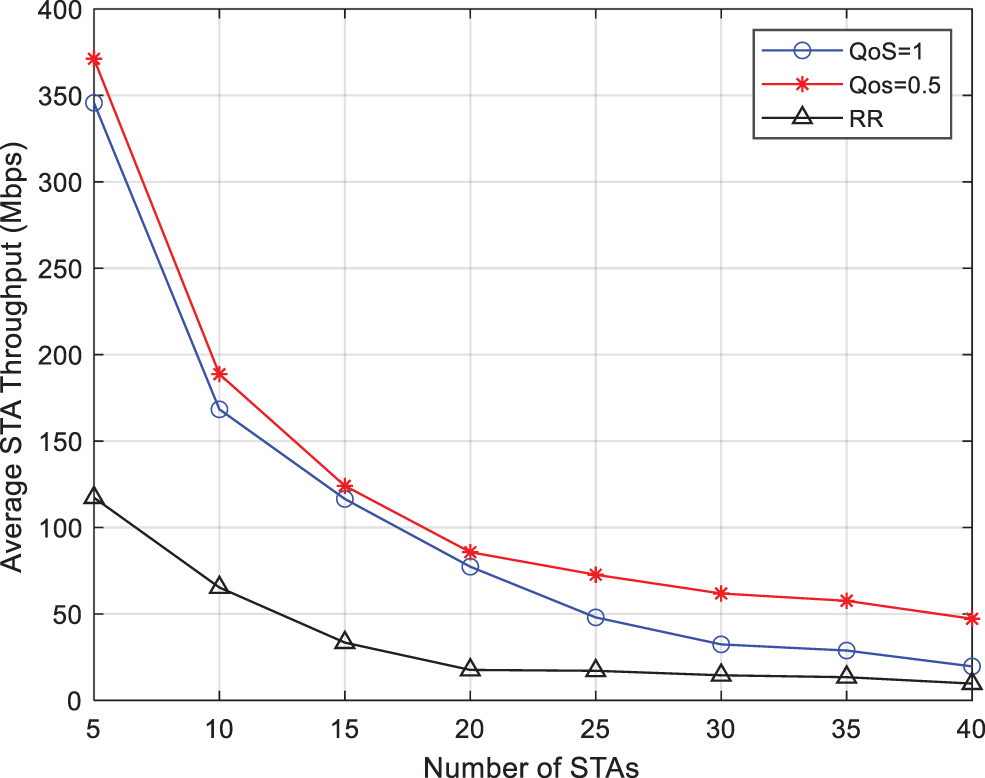
Figure 11: Comparison of average throughout
Fig. 12 shows the result of the average delay with the change of the number of terminals. As can be seen from Fig. 12, the average latency of the SINR scheduling algorithm of the QoS-distinguished scheduling algorithm increases with the increase of the number of STAs. When the number of terminals is small, it can be seen that the average delay of all three algorithms is low, which is because the current AP can meet the transmission demand. However, with the increasing number of terminals, the advantages of the algorithms proposed in this paper gradually come out. When the number of terminals is greater than 20, the proposed algorithm distinguishes between service delay and priority, which enables the system to schedule at a higher rate and ensures that the generated packets can be scheduled faster, so it has a lower average delay. The final average delay is 15% lower than the SINR algorithm, which can guarantee the high quality and low delay requirements for power services. For the RR algorithm, the average delay first increases with the number of terminals, then slowly decreases and eventually stabilizes, but the average delay is much higher than the other two algorithms.
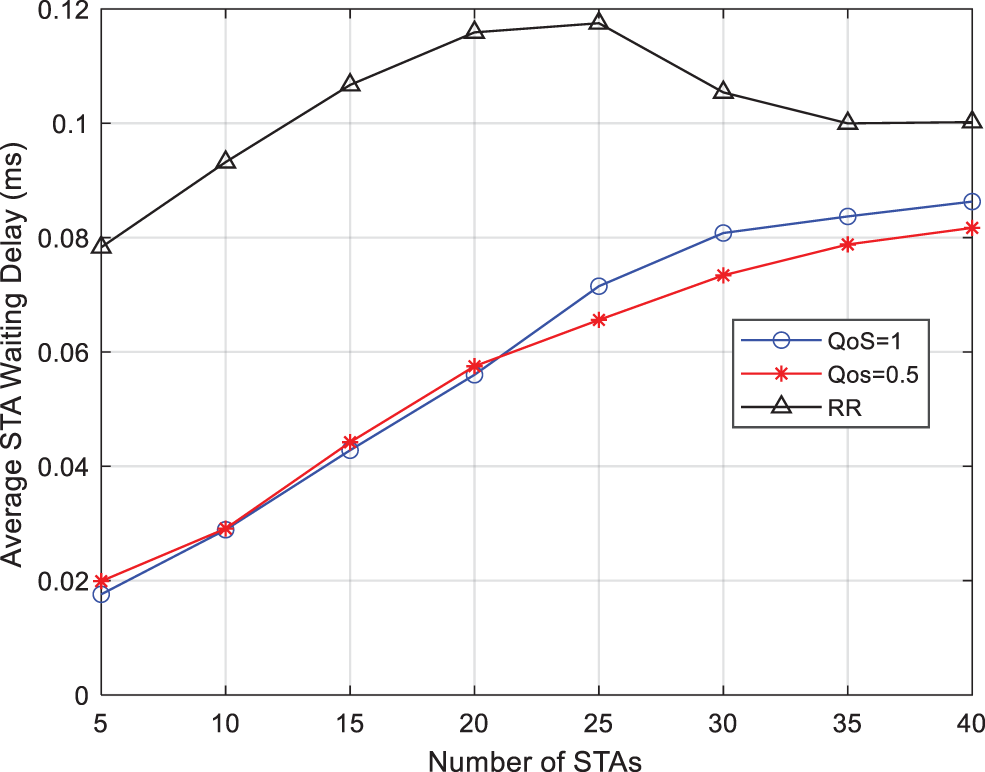
Figure 12: Comparison of average delay
Fig. 13 compares the variation of the overall system throughput with the number of terminals for the three algorithms with no failure occurrence, a single AP failure but no failure tolerance mechanism, and the proposed fault tolerance mechanism. As can be seen from the Fig. 13, the system throughput is maximum when no failure occurs. When a single AP fails, the throughput of the other two mechanisms decreases, but the fault-tolerant mechanism still maintains a high throughput, and these results can be attributed to the following reasons: 1) the periodic detection of beacon frames enhances the robustness of the network; 2) SINR-based neighbor AP reconnection algorithm ensures that affected users select the best AP to access; 3) the scheduling access optimization model enables a reasonable allocation of resources to the network.
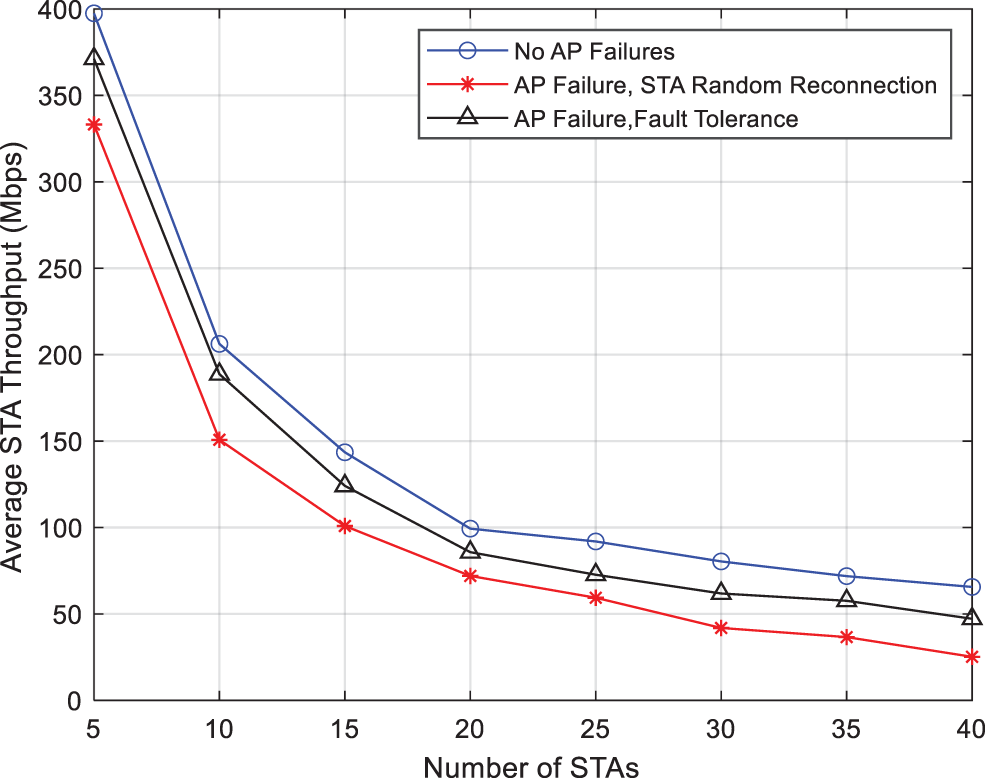
Figure 13: Impact of fault tolerance on network throughput
This paper proposes a WIFI6 dynamic channel optimization method for fault tolerance, which uses the method of neighboring APs listening to beacon frames to determine the faulty AP. In addition, a reconnection AP selection algorithm is designed to re-select the AP for the STAs under the faulty AP. According to the OFDMA characteristics, this paper designs a WIFI6 access resource optimization method based on transmission time slot scheduling for differentiated WIFI6 access of power IoT services. First, in order to maximize UL transmission efficiency and minimize overhead, this paper designs DASM, which distinguishes the length of data frames. Then, considering the two factors of delay threshold and service priority, SAO-MF is designed to realize the multi-frame transmission in one TXOP. Then, a heuristic-based resource allocation algorithm is designed based on the access resource optimization method of WIFI6. Finally, the simulation results show that the method can improve the throughput of the system and ensure the requirements of high quality and low latency of power services.
Even though the feasibility of DASM and SAO-MF has been verified by simulation, there are still some shortcomings:
1) The experimental data is generated by software and there is a lack of real data. Although it has passed the verification in theory, whether it can pass the practice in the future needs further research and analysis.
2) Considering the complexity of the model, only studies the failure of one AP in the network (although the model can also solve the simultaneous failure of multiple non-adjacent APs), and does not analyze the failure of two adjacent APs at the same time. Further analysis will follow.
Acknowledgement: This work is supported by State Grid Jiangsu Electric Power Co., Ltd. Science and Technology Project “Research on Low-Cost Wireless Coverage and Trusted Access Technologies for Underground Pipe Gallery Digital Network” (J2021081).
Funding Statement: The authors received no specific funding for this study.
Conflicts of Interest: The authors declare that they have no conflicts of interest to report regarding the present study.
References
1. S. Qiu, X. Chu, Y. -W. Leung and J. K. Yin Ng, “Joint access point placement and power-channel-resource-unit assignment for 802.11ax-based dense WiFi with QoS requirements,” in IEEE INFOCOM 2020-IEEE Conf. on Computer Communications, Toronto, ON, Canada, pp. 2569–2578, 2020. [Google Scholar]
2. S. Y. Guo, K. Q. Zhang, B. Gong, L. D. Chen, Y. L. Ren et al., “Sandbox computing: A data privacy trusted sharing paradigm via blockchain and federated learning,” IEEE Transactions on Computers, vol. 72, no. 3, pp. 800–810, 2023. [Google Scholar]
3. S. Y. Guo, X. Hu, S. Guo, X. S. Qiu and F. Qi, “Blockchain meets edge computing: A distributed and trusted authentication system,” IEEE Transactions on Industrial Informatics, vol. 16, no. 3, pp. 1972–1983, 2020. [Google Scholar]
4. O. Said, “A Dynamic Management scheme for Internet of Things (IoT) environments: simulation and performance evaluation,” CMES-Computer Modeling in Engineering & Sciences, vol. 133, no. 3, pp. 673–695, 2022. [Google Scholar]
5. S. Joshi, S. Manimurugan, A. Aljuhani, U. Albalawi and A. Aljaedi, “Energy-efficient and secure wireless communication for telemedicine in IoT,” Computer Systems Science and Engineering, vol. 43, no. 3, pp. 1111–1130, 2022. [Google Scholar]
6. S. Barrachina-Muñoz, B. Bellalta and E. W. Knightly, “Wi-Fi channel bonding: An all-channel system and experimental study from urban hotspots to a sold-out stadium,” IEEE/ACM Transactions on Networking, vol. 29, no. 5, pp. 2101–2114, 2021. [Google Scholar]
7. M. S. Afaqui, E. Garcia-Villegas and E. Lopez-Aguilera, “IEEE 802.11ax: Challenges and requirements for future high efficiency WiFi,” IEEE Wireless Communications, vol. 24, no. 3, pp. 130–137, 2017. [Google Scholar]
8. K. Zhou, X. Jia, L. Xie and Y. Chang, “Fault tolerant AP placement with QoS constraint in wireless local area networks,” IEEE Global Telecommunications Conf.-GLOBECOM, 2011, Houston, TX, USA, pp. 1–5, 2011. [Google Scholar]
9. B. Bellalta, “IEEE 802.11ax: High-efficiency WLANS,” IEEE Wireless Communications, vol. 23, no. 1, pp. 38–46, 2016. [Google Scholar]
10. I. Selinis, K. Katsaros, S. Vahid and R. Tafazolli, “Control OBSS/PD sensitivity threshold for IEEE 802.11ax BSS color,” in 2018 IEEE 29th Annual Int. Symp. on Personal, in Indoor and Mobile Radio Communications (PIMRC), Bologna, Italy, pp. 1–7, 2018. [Google Scholar]
11. X. Ling and K. L. Yeung, “Joint access point placement and channel assignment for 802.11 wireless LANs,” IEEE Transactions on Wireless Communications, vol. 5, no. 10, pp. 2705–2711, 2006. [Google Scholar]
12. X. Qin, X. Yuan, Z. Zhang, F. Tian, Y. T. Hou et al., “On AP assignment and transmission scheduling for Multi-AP 60 GHz WLAN,” in 2017 IEEE 14th Int. Conf. on Mobile Ad Hoc and Sensor Systems (MASS), Orlando, FL, USA, pp. 189–197, 2017. [Google Scholar]
13. D. Kotagiri, K. Nihei and T. Li, “Multi-user distributed spectrum access method for 802.11ax stations,” in 2020 29th Int. Conf. on Computer Communications and Networks (ICCCN), Honolulu, HI, USA, pp. 1–2, 2020. [Google Scholar]
14. D. Xie, J. Zhang, A. Tang and X. Wang, “Multi-dimensional busy-tone arbitration for OFDMA random access in IEEE 802.11ax,” IEEE Transactions on Wireless Communications, vol. 19, no. 6, pp. 4080–4094, 2020. [Google Scholar]
15. B. Binoy and B. S. Vineeth, “Minimum delay scheduling under average power constraint for 802.11ax uplink,” in 2019 IEEE Int. Conf. on Advanced Networks and Telecommunications Systems (ANTS), Goa, India, pp. 1–5, 2019. [Google Scholar]
16. Q. Chen and Y. H. Zhu, “Scheduling channel access based on target wake time mechanism in 802.11ax WLANs,” IEEE Transactions on Wireless Communications, vol. 20, no. 3, pp. 1529–1543, 2021. [Google Scholar]
17. A. Saeed, O. G. Aliu and M. A. Imran, “Controlling self healing cellular networks using fuzzy logic,” in 2012 IEEE Wireless Communications and Networking Conf. (WCNC), Paris, France, pp. 3080–3084, 2012. [Google Scholar]
18. J. Li, Q. Y. Lu, J. Liu, K. Yuan, W. Tian et al., “Communication service priority in smart substation and its queue scheduling method,” Journal on Communications, vol. 42, no. 7, pp. 25–40, 2021. [Google Scholar]
19. S. J. Liu, J. W. Li, G. C. Yang, S. J. Shao and S. Y. Guo, “A differentiated WiFi6 access resource optimization method for power internet of things services based on transmission time slot scheduling,” in Proc. of the 12th Int. Conf. on Computer Engineering and Networks. (CENet 2022), Haikou, China, vol. 961, pp. 84–94, 2022. [Google Scholar]
20. M. S. Kuran, A. Dilmac, Ö. Topal, B. Yamansavascilar, S. Avallone et al., “Throughput-maximizing OFDMA scheduler for IEEE 802.11ax networks,” in 2020 IEEE 31st Annual Int. Symp. on Personal, Indoor and Mobile Radio Communications, London, UK, pp. 1–7, 2020. [Google Scholar]
21. D. Bankov, A. Didenko, E. Khorov and A. Lyakhov, “OFDMA uplink scheduling in IEEE 802.11ax networks,” in 2018 IEEE Int. Conf. on Communications (ICC), Kansas City, MO, USA, pp. 1–6, 2018. [Google Scholar]
22. Z. M. Zhu, F. M. Cao and Z. Fan, “WLAN throughput management: A game theoretic TXOP scheduling approach,” in 2015 IEEE 20th Int. Workshop on Computer Aided Modelling and Design of Communication Links and Networks (CAMAD), Guildford, UK, pp. 161–164, 2015. [Google Scholar]
23. H. Fawaz, M. E. Helou, S. Lahoud and K. Khawam, “A reinforcement learning approach to queue-aware scheduling in full-duplex wireless networks,” Computer Networks, vol. 189, pp. 107893, 2021. [Google Scholar]
24. S. Wan, J. Hu, C. Chen, A. Jolfaei, S. Mumtaz et al., “Fair-hierarchical scheduling for diversified services in space, air and ground for 6G-dense internet of things,” IEEE Transactions on Network Science and Engineering, vol. 8, no. 4, pp. 2837–2848, 2021. [Google Scholar]
25. B. Boris and K. -S. Katarzyna, “AP-Initiated multi-user transmissions in IEEE 802.11ax WLANs,” Ad Hoc Networks, vol. 85, pp. 145–159, 2019. [Google Scholar]
Cite This Article
 Copyright © 2023 The Author(s). Published by Tech Science Press.
Copyright © 2023 The Author(s). Published by Tech Science Press.This work is licensed under a Creative Commons Attribution 4.0 International License , which permits unrestricted use, distribution, and reproduction in any medium, provided the original work is properly cited.


 Submit a Paper
Submit a Paper Propose a Special lssue
Propose a Special lssue View Full Text
View Full Text Download PDF
Download PDF Downloads
Downloads
 Citation Tools
Citation Tools