 Open Access
Open Access
ARTICLE
A Novel Approach for Security Enhancement of Data Encryption Standard
1 Department of Mathematics, Quaid-i-Azam University, Islamabad, Pakistan
2 Department of Mathematics, College of Science, King Khalid University, Abha, Saudi Arabia
3 College of Computing and Information Technology, University of Tabuk, Tabuk, 71491, Saudi Arabia
* Corresponding Author: Dawood Shah. Email:
Computers, Materials & Continua 2023, 75(3), 5073-5086. https://doi.org/10.32604/cmc.2023.020513
Received 27 May 2021; Accepted 14 January 2022; Issue published 29 April 2023
Abstract
Data Encryption Standard (DES) is a symmetric key cryptosystem that is applied in different cryptosystems of recent times. However, researchers found defects in the main assembling of the DES and declared it insecure against linear and differential cryptanalysis. In this paper, we have studied the faults and made improvements in their internal structure and get the new algorithm for Improved DES. The improvement is being made in the substitution step, which is the only nonlinear component of the algorithm. This alteration provided us with great outcomes and increase the strength of DES. Accordingly, a novel good quality S-box construction scheme has been hired in the substitution phase of the DES. The construction involves the Galois field method and generates robust S-boxes that are used to secure the scheme against linear and differential attacks. Then again, the key space of the improved DES has been enhanced against the brute force attack. The outcomes of different performance analyses depict the strength of our proposed substitution boxes which also guarantees the strength of the overall DES.Keywords
With rapid development in the field of information technology, it is observed that communication over electronics channels and broadcasting of digital data over the internet is increased. Accordingly, the security of sensitive information against prohibited copying and dissemination has become tremendously imperative. Cryptography is the study of secure communication which is contemplated as a recognized branch of science for the last 60 years. However, it is quite a new area of study comparable to other areas of sciences as each moment carries continual developments. Cryptography is divided into two sub-branches; asymmetric key cryptography, and symmetric key cryptography. This classification is based on the secret key that is used during encryption and decryption. In symmetric-key cryptography, the communicating parties share a secret key confidentially. The algorithms such as Lucifer, DES, Advanced encryption standard (AES), and the International data encryption algorithm (IDEA) are the prominent examples of symmetric key cryptography.
Data encryption standard (DES) is a symmetric key algorithm designed by IBM. It was adopted and published by the US National Institute of Standard Technology (NIST) in 1971, as a federal information processing scheme. The aim was to provide a secure cryptosystem for the security of sensitive data and information during transmission. This algorithm became a distinguished and broadly used algorithm [1]. In the same way, a considerable number of cryptanalytic papers on DES were published since its acceptance in 1971. In 1977, Diffie and Hellman proposed a parallel machine for the comprehensive search of the complete keyspace [2]. The author claimed was, that very-large-scale integration (VLSI) chips are constructed and each chip probably searches one key per microsecond. The construction of the search machine contains millions of such chips and all working in parallel mode. Each chip is credible to search 1012 keys per second. The order of the set of all keys of DES is
S-box is one of the most important components in block ciphers, which is used to confuse the relationship between the cipher data and the input key during the process of encryption. Since the confusion-creating capability of the cipher relies on the quality of the S-box. Therefore, the construction of good quality S-box has attracted the cryptographic research community. The S-box construction schemes based on all isomorphic Galois field
Keeping the above facts in view, this manuscript proposed a novel
The rest of this manuscript is organized as follows. In Section 2, we introduced some basic definitions. Section 3 is dedicated to the general principle of DES. The construction of the proposed S-box construction scheme is presented in Section 4. Section 5 is devoted to the performance analyses of the suggested S-boxes. The modified DES is examined using a specific ciphertext and compared the results with the DES in Section 6. Section 7 concluded the discussion.
We denote the direct product of n copies of the field
Let
where
Followed by [11], a function
For all
Followed by [11], let
The positive integer
DES is a symmetric key encryption scheme, which encrypts a 64-bits block of data. Thus, the input size of the algorithm is 64-bits and the output size is also 64-bits. The length of the key is 56-bits and it is mostly expressed as the block of 64-bits. The 56-bits are used as input key and the remaining eight least significant bits are utilizes for the parity check purpose. DES is consisting of two modules that are product cipher and Feistel cipher. The product cipher is used to combines two or more transformations because the combinations of ciphers are more secure than separated ciphers. A Feistel cipher is the iterated cipher that consists of the sequential repetition of the round functions. The formal definition of the FF is given as follows.
The Feistel Function (FF) is an iterated cipher that maps plaintext of size
where
The FF is bijective and thus reversible. So, the same key is used for the encryption and decryption procedure. The Xor is used in the function to combine the output of the round function with the left half using the following equation.
Eq. (7), demonstrates that the DES algorithm is independent of the design of the FF. The invertibility of FF does not produce an impact on the invertibility of the DES algorithm. Accordingly, if the function FF is invertible or not, though the DES scheme is always invertible.
4 Construction of Galois Fields GF(26) and S-Boxes
The field of order p is a prime field that is denoted by
Thus, the quotient ring
4.1 Construction of Galois Fields
This main interest of this study is Galois field

4.2 Construction of 6 × 6 S-Boxes
The construction of the S-box required a nonlinear bijective map. In the proposed work, we have used the multiplicative inverse function module degree 6 primitive irreducible polynomial
The images

In [12], Let l be an affine transformation and
The Eq. (10) preserves the cryptographic properties of
A composition function of an affine function with a function g on the right-hand side or the left-hand side preserved the properties of linearity and differential uniformity of a function
An efficient cryptosystem should be secure against all kinds of attacks. Since the security of the block ciphers depends on the choice of the S-box, therefore this section we thoroughly analyzed the performance of the proposed
In Section 2, the definition of nonlinearity for the Boolean function has been already discussed. The general formula to calculate the upper bound of the nonlinearity of the function
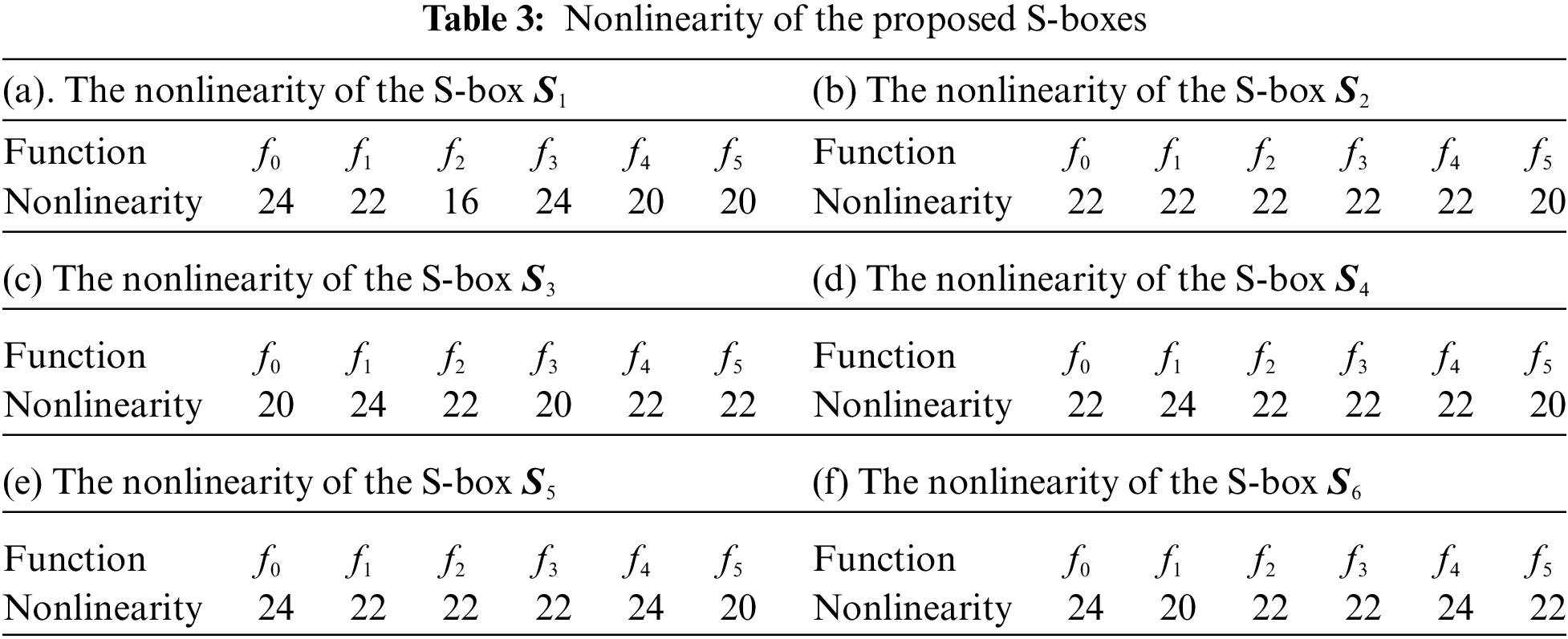
5.2 Differential Cryptanalysis
Differential approximation probability (DP) analysis is used to measure the differential uniformity of the S-box. The minimum possible value of differential uniformity for
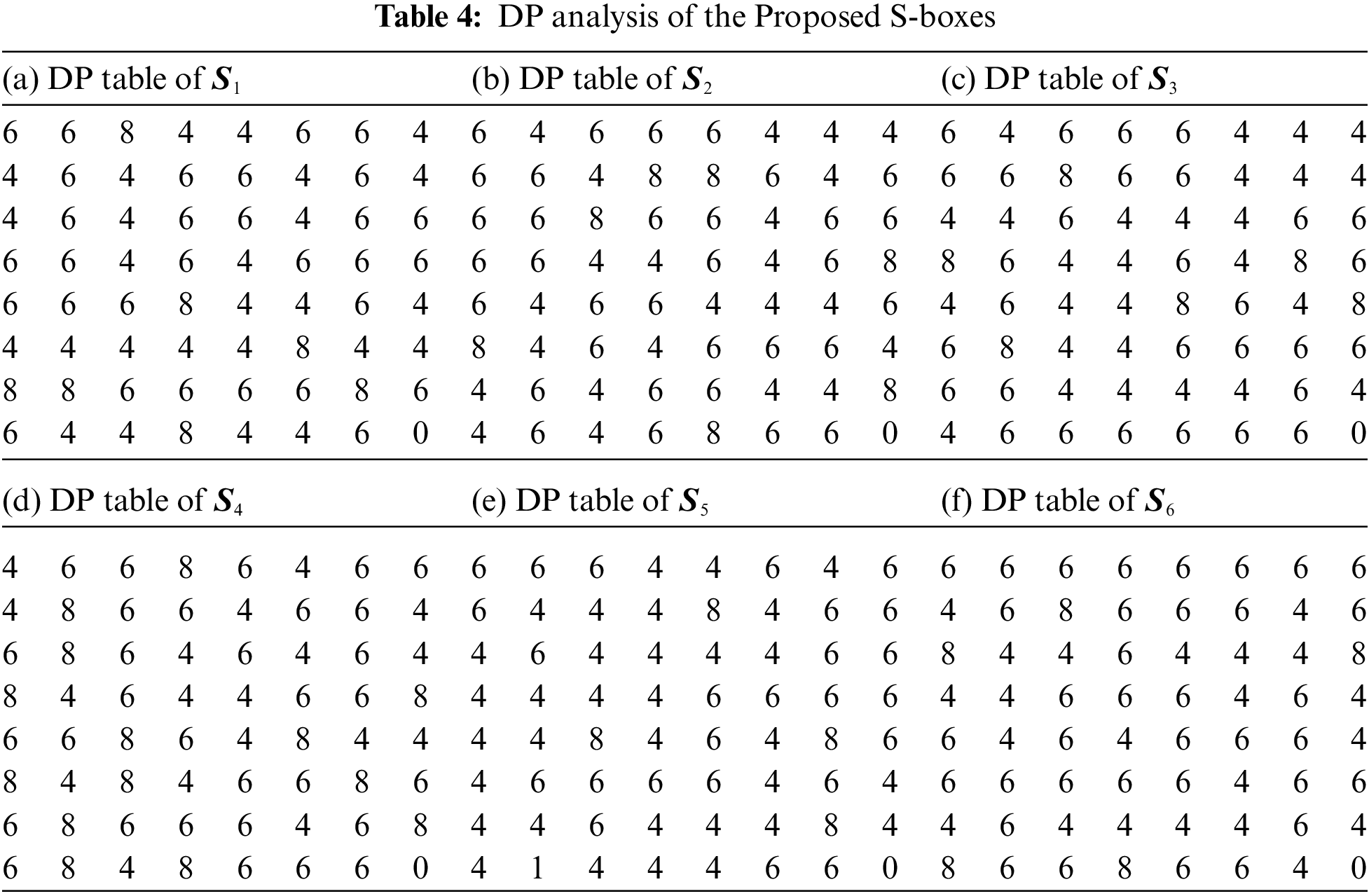
5.3 Strict Avalanche Criterion
In general, an S-box is considered a lookup table of Boolean functions from
For all
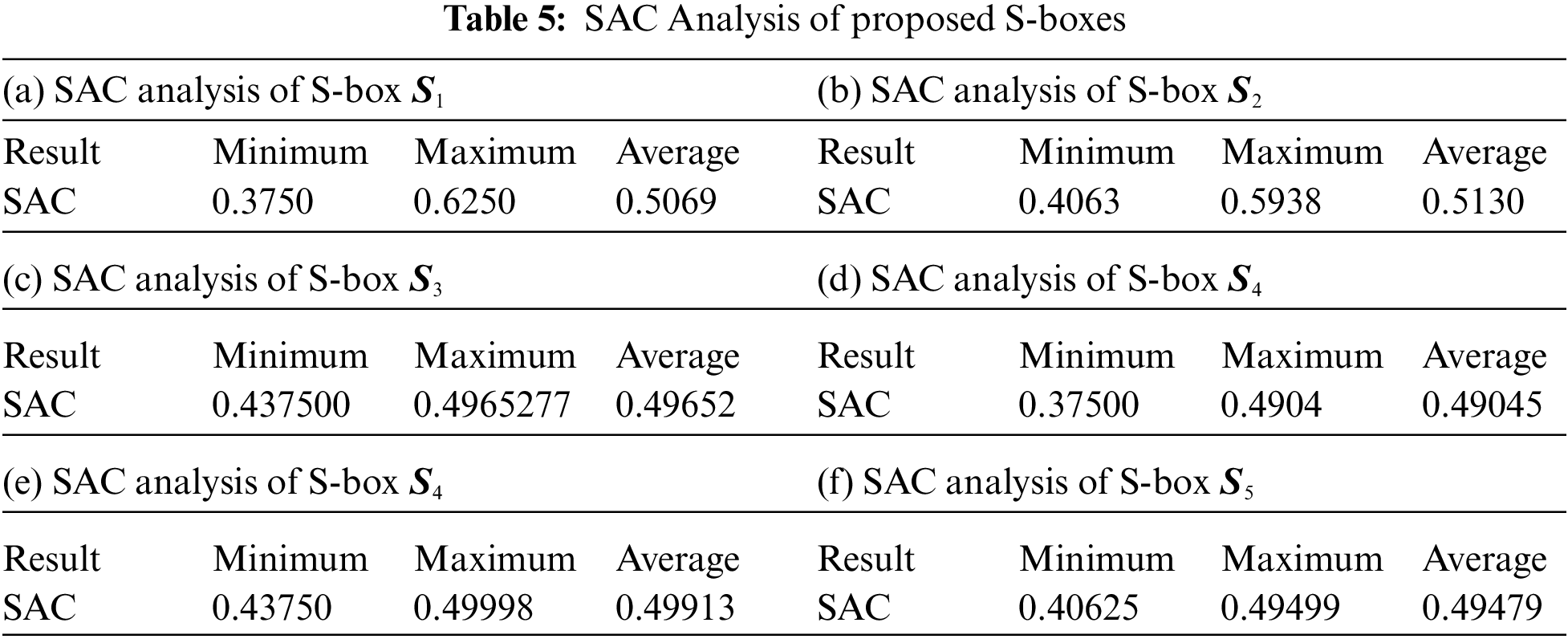
5.4 Linear Approximation Probability
Linear approximation probability (LP) analysis is used to investigate the maximum value of the imbalance of the scheme. Let
where the order of the set of in input value is
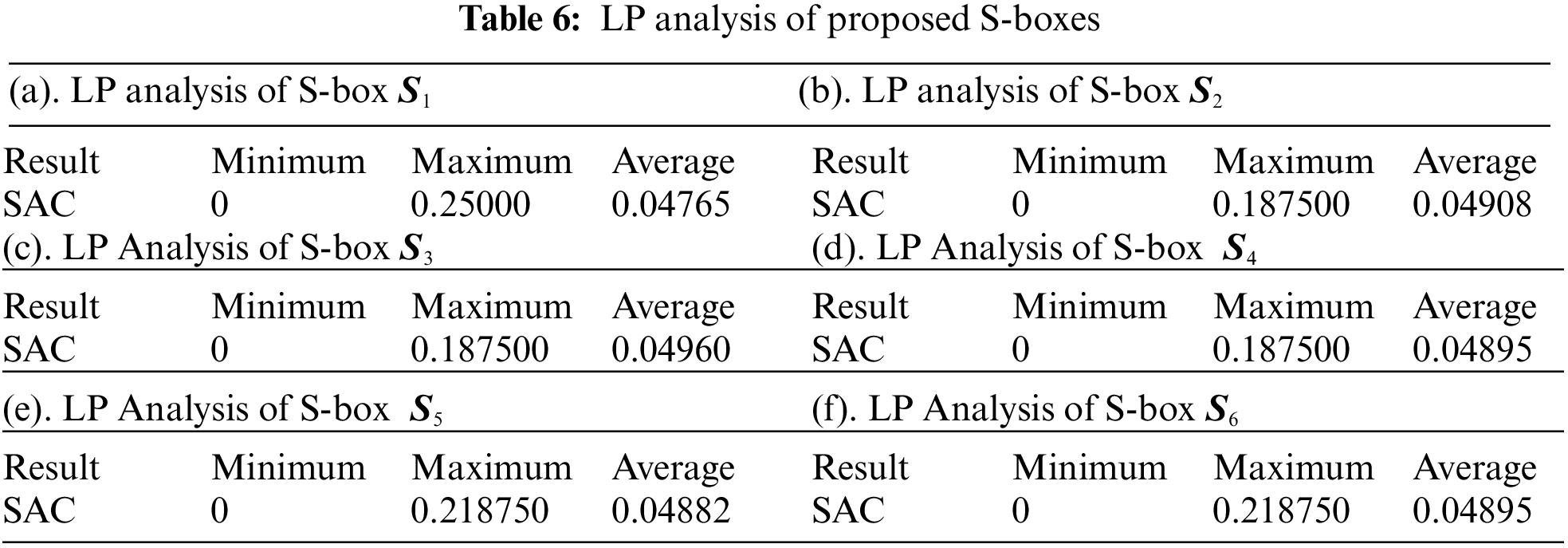
The performance analyses demonstrate that the results of all analyses of the proposed S-boxes are quite better. According to Theorem 2, the APA transformations preserve the cryptographic properties of the S-box, so we used the APA transformation to increase the number of good quality S-boxes and robust their algebraic complexity. In the next section, we deployed the APA transformation in the Feistel network to enhanced the security of the DES algorithm.
DES is a sixteen-round cryptosystem, each round is the combination of bits permutation, expansion of bits, substitution step and XOR operation. The practice of the bit permutation step is to rearrange the order of the data to aim to produce diffusion in the ciphered data. The usage of an exclusive XOR operation is to mix the round key with the plain data. The S-box is used to produce confusion in the ciphered data. In these operations the S-box is the only nonlinear component in the DES, thus the modification in any other operation of the algorithm would not make them less successful. Thus, in this study, we modified the DES algorithm by fitting a good quality 6-bit S-box in the FF and keep the other operation unchanged. The modified DES attains the following obligatory criteria.
i. Enhance the key space.
ii. Highly nonlinear output functions; the maximum distance from the linear functions.
iii. Successfully resist the linear and differential cryptanalysis.
iv. High nonlinearity is attained; degrees of the output bit functions are increased.
v. Efficient construction is easily implemented in hardware and software.
6.1 Generation of Key Dependent 6-Bits S-Boxes
The Key size of the modified DES is increased up to
where
6.2 Modified DES Feistel Network
The Feistel network was introduced by Horst Feistel. In general, it is a transformation of a function into a permutation, which is called F function. The FF is the nonlinear, reversible and key-dependent mapping, that maps an input string of data into the output string of data. The Feistel network has been widely used in many block ciphers such as in DES, GOST [13], Khufu and Khafre [14], RC5 [15], FEAL [17], Blowfish [18] and LOKI [19]. In this study, the Feistel network used in the DES is of our specific interest. The Feistel network plays a vital role in the security of DES. The input string of F-function in a round i is the right half output

Figure 1: Flow Chart of the Modified F-function
Example: Let
The order of the key space of the DES algorithm is equal to
This property of the DES cipher makes the brute force attack simpler. The attacker has to check half possible keys to break the DES through a brute force attack. However, the S-boxes deployed in the modified DES are key-dependent, which does satisfy the following property.
Implies that
where
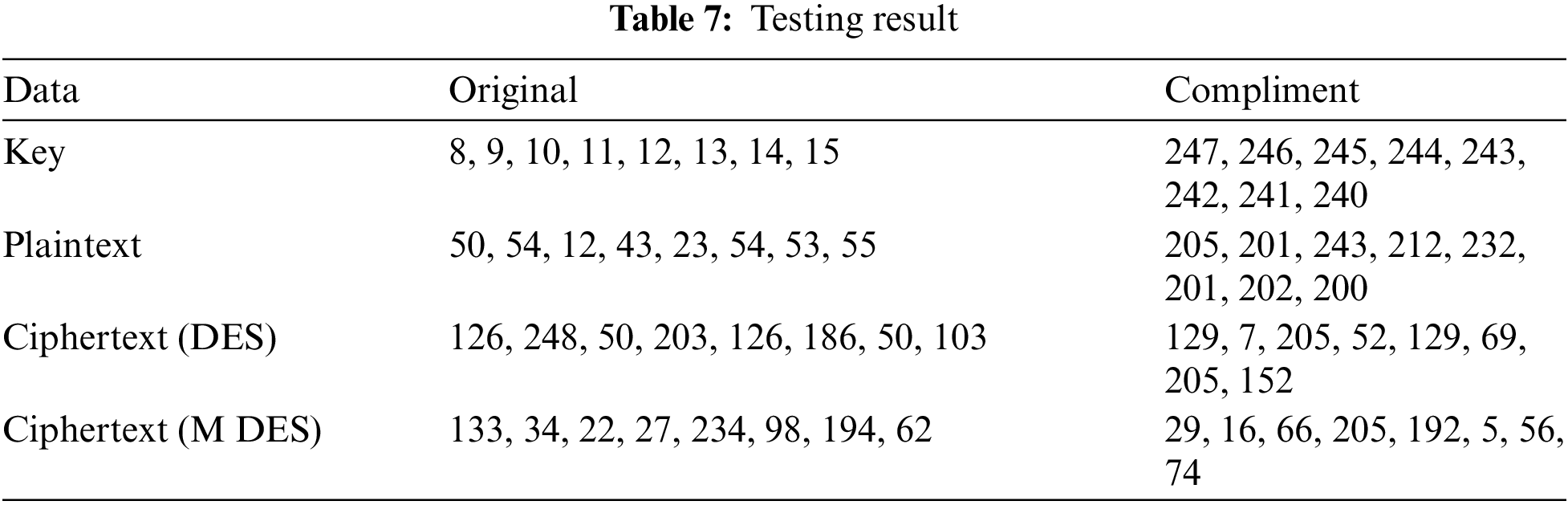
A brute force attack is a classical attack, that is used to check all the possible keys until the correct key is found. In this era, symmetric ciphers with 100-bits key or less are susceptible to brute force attack. The DES algorithm uses 56-bit keys and therefore, it was proved to be insecure against brute force attacks. The modified DES algorithm uses
The DES algorithm was proved to be insecure against brute force attack, differential and linear cryptanalysis. The reason for breaking the algorithm was the small key space and weak S-box used in the substitution part of the algorithm. In this latter, we proposed an algorithm for the construction of
Funding Statement: The authors extend their gratitude to the Deanship of Scientific Research at King Khalid University for funding this work through the research groups program under grant number R. G. P. 2/150/42.
Conflicts of Interest: The authors declare that they have no conflicts of interest to report regarding the present study.
References
1. FIPS 46, “Data Encryption Standard,” in Federal Information Processing Standard, Washington D. C., USA: National Bureauof Standards, U.S. Department of Commerce, 1977. [Google Scholar]
2. W. Diffie and M. E. Hellman, “Special feature exhaustive cryptanalysis of the NBS data encryption standard,” Computer, vol. 10, no. 6, pp. 74–84, 1977. [Google Scholar]
3. M. E. Hellman, “A cryptanalytic time-memory trade-off,” IEEE Transactions on Information Theory, vol. 26, no. 4, pp. 401–406, 1980. [Google Scholar]
4. D. Chaum and J. H. Evertse, “Cryptanalysis of DES with a reduced number of rounds,” in Conf. on the Theory and Application of Cryptographic Techniques, Berlin, Heidelberg, Springer, 1985. [Google Scholar]
5. E. Biham and A. Shamir, “Differential cryptanalysis of DES-like cryptosystems,” Journal of CRYPTOLOGY, vol. 4, no. 1, pp. 3–72, 1991. [Google Scholar]
6. T. Shah and D. Shah, “Construction of highly nonlinear S-boxes for degree 8 primitive irreducible polynomials over ℤ 2,” Multimedia Tools and Applications, vol. 78, no. 2, pp. 1219–1234, 2019. [Google Scholar]
7. F. A. Khan, J.Ahmed, J. S. Khan, J. Ahmad,M. A. Khan et al., “A new technique for designing 8× 8 substitution box for image encryption applications,” in 2017 9th Computer Science and Electronic Engineering (CEEC), Colchester, UK: IEEE, pp. 7–12, 2017. [Google Scholar]
8. M. A. Khan, J. Ahmad, Q. Javaid and N. A. Saqib, “An efficient and secure partial image encryption for wireless multimedia sensor networks using discrete wavelet transform, chaotic maps and substitution box,” Journal of Modern Optics, vol. 64, no. 5, pp. 531–540, 2017. [Google Scholar]
9. A. Qayyum, J. Ahmad, W. Boulila, S. Rubaiee, A. Arshad et al., “Chaos-based confusion and diffusion of image pixels using dynamic substitution,” IEEE Access, vol. 8, pp. 140876–140895, 2020. [Google Scholar]
10. A. Arshad, S. Shaukat, A. Arshid, A. Eleyan, S. A. Shah et al., “Chaos theory and its application: An essential framework for image encryption,” Chaos Theory and Applications, vol. 2, no. 1, pp. 17–22, 2020. [Google Scholar]
11. K. Nyberg, “Differentially uniform mappings for cryptography,” in Workshop on the Theory and Application of Cryptographic Techniques, Springer, Berlin, Heidelberg, pp. 55–64, 1993. [Google Scholar]
12. L. Cui and Y. Cao, “A new S-box structure named affine-power-affine,” International Journal of Innovative Computing, Information and Control, vol. 3, no. 6, pp. 751–759, 2007. [Google Scholar]
13. I. A. Zabotin, G. P. Glazkov and V. B. Isaeva, “Cryptographic protection for information processing systems: Cryptographic transformation algorithm.” Government Standard of the USSR, Government Committee of the USSR for Standards, pp. 28147–28189, 1989. [Google Scholar]
14. R. C. Merkle, “A fast software one-way hash function,” Journal of Cryptology, vol. 3, no. 1, pp. 43–58, 1990. [Google Scholar]
15. R. L. Rivest, “The RC5 encryption algorithm,” in Int. Workshop on Fast Software Encryption, Springer, Berlin, Heidelberg, pp. 86–96, 1994. [Google Scholar]
16. P. P. Mar and K. M. Latt, “New analysis methods on strict avalanche criterion of S-boxes,” World Academy of Science, Engineering and Technology, vol. 2, no. 2, pp. 150–154, 2008. [Google Scholar]
17. A. Shimizu and S. Miyaguchi, “Fast data encipherment algorithm FEAL,” in Workshop on the Theory and Application of Cryptographic Techniques, Springer, Berlin, Heidelberg, pp. 267–278, 1988. [Google Scholar]
18. B. Schneier, “Other block ciphers,” in Applied Cryptography, Second Edition, New York, USA: John Wiley and Sons, pp. 319–325, 1996. [Google Scholar]
19. L. P. Brown, M. Kwan, J. Pieprzyk and J. Seberry, “Improving resistance to differential cryptanalysis and the redesign of LOKI,” in Int. Conf. on the Theory and Application of Cryptology, Springer, Berlin, Heidelberg, pp. 36–50, 1991. [Google Scholar]
Cite This Article
 Copyright © 2023 The Author(s). Published by Tech Science Press.
Copyright © 2023 The Author(s). Published by Tech Science Press.This work is licensed under a Creative Commons Attribution 4.0 International License , which permits unrestricted use, distribution, and reproduction in any medium, provided the original work is properly cited.


 Submit a Paper
Submit a Paper Propose a Special lssue
Propose a Special lssue View Full Text
View Full Text Download PDF
Download PDF Downloads
Downloads
 Citation Tools
Citation Tools