 Open Access
Open Access
ARTICLE
Blockchain-Enabled Secure and Privacy-Preserving Data Aggregation for Fog-Based ITS
1 Jiangsu Key Lab of Broadband Wireless Communication and Internet of Things, Nanjing University of Posts and Telecommunications, Nanjing, 210003, China
2 School of Internet of Things, Nanjing University of Posts and Telecommunications, Nanjing, 210003, China
* Corresponding Author: Siguang Chen. Email:
Computers, Materials & Continua 2023, 75(2), 3781-3796. https://doi.org/10.32604/cmc.2023.036437
Received 30 September 2022; Accepted 08 February 2023; Issue published 31 March 2023
Abstract
As an essential component of intelligent transportation systems (ITS), electric vehicles (EVs) can store massive amounts of electric power in their batteries and send power back to a charging station (CS) at peak hours to balance the power supply and generate profits. However, when the system collects the corresponding power data, several severe security and privacy issues are encountered. The identity and private injection data may be maliciously intercepted by network attackers and be tampered with to damage the services of ITS and smart grids. Existing approaches requiring high computational overhead render them unsuitable for the resource-constrained Internet of Things (IoT) environment. To address above problems, this paper proposes a blockchain-enabled secure and privacy-preserving data aggregation scheme for fog-based ITS. First, a fog computing and blockchain co-aware aggregation framework of power injection data is designed, which provides strong support for ITS to achieve secure and efficient power injection. Second, Paillier homomorphic encryption, the batch aggregation signature mechanism and a Bloom filter are effectively integrated with efficient aggregation of power injection data with security and privacy guarantees. In addition, the fine-grained homomorphic aggregation is designed for power injection data generated by all EVs, which provides solid data support for accurate power dispatching and supply management in ITS. Experiments show that the total computational cost is significantly reduced in the proposed scheme while providing security and privacy guarantees. The proposed scheme is more suitable for ITS with latency-sensitive applications and is also adapted to deploying devices with limited resources.Keywords
Electric vehicles (EVs) are highly favored by governments worldwide and can significantly reduce the air pollution generated by fuel-driven vehicles (account for 17% of global CO2 emissions). Research indicates that using EVs instead of traditional fuel-powered vehicles can reduce CO2 emissions by 70% [1]. With popularity of energy-saving and environmentally friendly EVs, they become an essential component of intelligent transportation systems (ITS). Due to the rapid development of ITS, vehicle-to-grid (V2G) is emerging as a promising service in ITS [2–4]. V2G provides mobile and distributed power for ITS and smart grid systems and reduces their dependence on nonrenewable energy. Furthermore, in V2G networks, as distributed energy storage elements, EVs can purchase power at valley hours and send power back to the smart grid at peak hours to achieve ‘peak shaving and valley filling’ to stabilize the power supply of ITS [5–7]. EVs can also generate profits by buying at a low price and selling at a high price [8]. This bidirectional power transmission produces many records, which can be analyzed by the control center to provide valuable services, such as charging/discharging scheduling, dynamic pricing, and optimal power dispatching [9–11].
However, these records can also cause a series of security and privacy issues, for example, the identities and locations of EVs and the amounts of charging and discharging [12,13]. These security and privacy issues are significant obstacles to the development of V2G in ITS. Especially when power is injected into the grid, information about power injection is highly sensitive. For example, network attackers may maliciously intercept relevant information, and power injection data may be tampered with to damage the ITS and smart grid services. In addition, each link from EVs to the control center is likely to be threatened by attacks. Measures should be taken to ensure the availability, integrity, confidentiality, and immutability of information in V2G networks.
Related studies have been conducted on the privacy and security issues of V2G networks. For example, from the perspective of identity authentication, Saxena et al. [14] presented a mutual authentication scheme for protecting the privacy of EV information by employing bilinear pairing technology. Still, its bilinear pairing implementation is costly. Abdallah et al. [15] constructed a secure authentication and privacy-preserving V2G connection scheme that leverages symmetric and public-private keys to authenticate identity. Tao et al. [16] investigated a lightweight protocol and developed capacity-based secure access authentication for the IoT that can efficiently satisfy security and privacy preservation requirements. Elliptic curve cryptography (ECC)-based schemes were also used in V2G networks. For example, Liang et al. [17] proposed a group authentication protocol by employing elliptic curve Diffie-Hellman and bilinear pairing, which effectively realizes security authentication in a V2G network. Fan et al. [18] developed a three-factor user authentication scheme, which significantly improves the robustness of the network by integrating one-way hash functions, bitwise exclusive OR (XOR) operations and ECC. Work [19] studied an anonymous key distribution scheme based on ECC, but its high computational overhead is unadaptable for the resource-constrained IoT environment.
The traditional centralized mechanism relies on a trusted third party to manage every energy transaction. Each transaction is vulnerable to a series of security threats in this scenario, such as single-point failure, denial of service attacks, and privacy leakage. Therefore, some schemes, such as [20–22], introduced blockchain technology for energy transactions because blockchains have the properties of decentralization, anonymity and immutability to provide an effective solution for V2G networks. Liu et al. [23] proposed a cross-domain identity authentication scheme based on a blockchain, which utilizes the encryption algorithm SM9 to guarantee the security and privacy required by V2G networks. Similarly, Kang et al. [24] addressed security and privacy issues in peer-to-peer (P2P) energy transactions by employing a consortium blockchain. Garg et al. [25] studied a combination mechanism of an ECC encryption algorithm and blockchain technology, which provides secure and anonymous energy transactions in V2G.
Although a secure identity authentication protocol can provide privacy preservation for users, fine-grained power consumption data are also sensitive due to their correlation with users’ activities when EVs inject power into the grid. From the perspective of power consumption data, Tonyali et al. [26] developed a meter data confusion scheme for protecting consumer privacy by concealing meter data. However, it does not involve specified V2G networks. Mahmoud et al. [27] presented a power injection scheme for smart grid system that utilizes homomorphic encryption to aggregate power injection bids from the storage unit at the local gateway. Unfortunately, this scheme cannot ensure the privacy of power injection data. Accordingly, Zhang et al. [28] constructed a privacy-aware sensing data aggregation scheme for protecting the power injection information, but it involves many expensive bilinear pairing operations. Next, Zhang et al. [29] proposed a 5G-based communication and power injection scheme for privacy protection in V2G networks, which adopts the novel aggregation technology named ‘hash-then-homomorphic’ to further aggregate blinded bids in various time slots. The above schemes focus on the bidding prices of users but fail to consider the amounts of power that users can inject into the grid. Although they protect users’ power injection and consumption data, security remains the major challenge of V2G networks.
In contrast to the previously established solutions, from the perspective of security and privacy preservations of identity and private injection data, this paper proposes a blockchain-enabled secure and privacy-preserving data aggregation scheme for fog-based ITS by combining blockchain technology and fog computing. The significant contributions are summarized as follows:
• A fog computing and blockchain co-aware three-tier aggregation framework for power injection data is constructed, which provides firm support for the V2G network to realize secure, reliable and efficient power injection.
• A secure and privacy-preserving data aggregation mechanism is designed by jointly integrating Paillier homomorphic encryption, the batch aggregation signature mechanism and a Bloom filter, which can effectively ensure the security of power injection data and the identity privacy of V2G users.
• Fine-grained homomorphic aggregation of the power injection data generated by all EVs is realized, which provides accurate data support for flexible power dispatching and effectively stabilizes the power supply of the ITS.
Finally, extensive simulation results show that the proposed scheme has lower computational costs than the previously established schemes while providing security and privacy protections. It is more suitable for ITS with latency-sensitive applications and limited resources.
The remainder of this paper is structured as follows. Section 2 describes the fog computing and blockchain co-aware three-tier aggregation network model for ITS. Section 3 presents a blockchain-enabled secure and privacy-preserving data aggregation scheme. Then, a simple security analysis and detailed performance evaluation of the experimental results are conducted in Section 4. Finally, Section 5 presents the conclusions of this study.
This section constructs a fog computing and blockchain co-aware three-tier aggregation network model for ITS, consisting of five types of entities: EVs, charging stations (CSs), fog nodes, a data center and a trusted authority (TA). Consider a city as an example. The city is divided into m subareas, and each subarea usually has w EVs. For simplicity, this paper uses symbol
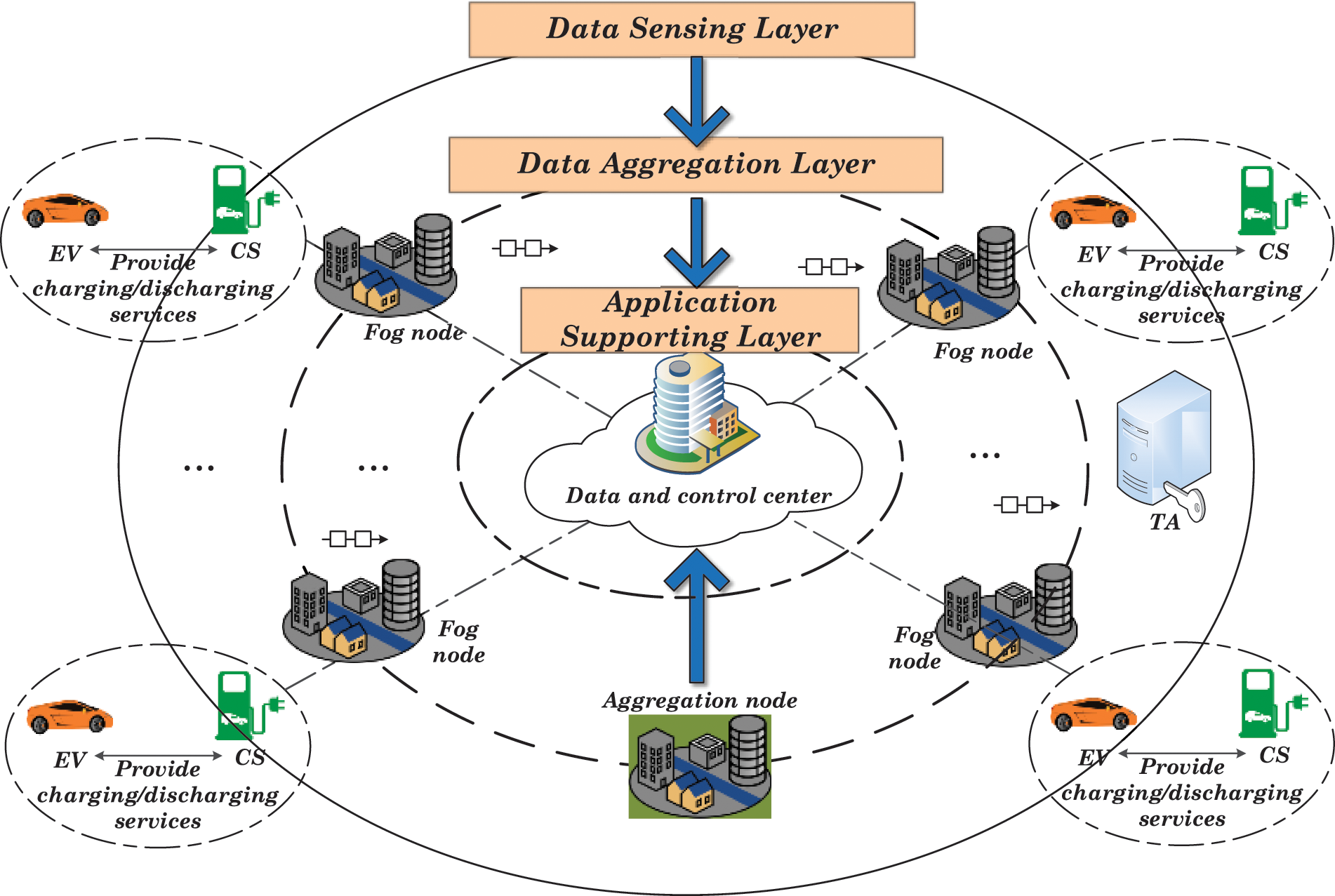
Figure 1: Three-tier aggregation framework for the ITS
Data Sensing Layer: The data sensing layer is located on the user side and includes EVs and CSs. EVs mainly refer to automobiles, motorcycles, ships, aircraft and other vehicles powered by batteries. CSs can provide charging or discharging services for vehicle batteries equipped with smart meters to record the corresponding data. In this layer, EVs can buy energy from the grid at a low price and inject the remaining power into the grid at a higher price to earn profits.
Data Aggregation Layer: The data aggregation layer is located on the edge side of the ITS. It is mainly composed of many fog nodes in all subareas. This layer selects an aggregation node in each time slot according to the remaining energy, and the remaining nodes are regarded as ordinary fog nodes. When the CS uploads the power injection data of an EV, the corresponding ordinary fog node is responsible for aggregating these data, generating a block, adding it to the blockchain through the consensus mechanism, and subsequently transmitting it to an aggregation node. The aggregation node is responsible for aggregating the received data from ordinary fog nodes (namely, for executing secondary aggregation of the power injection data) in this layer and encapsulating the data into a block with other relevant information. Then, the newly generated block is appended to the blockchain through a consensus mechanism and uploaded to the application supporting layer, where it awaits the decryption and analysis operations on the data center.
Application Supporting Layer: The application supporting layer refers to the data and control center, which contains a cloud server and is mainly responsible for decrypting and analyzing the data uploaded from the lower layer.
TA: TA is mainly used to generate and allocate public parameters and keys for entities. At the same time, it generates a Bloom filter by collecting the pseudonyms of EVs and fog nodes and sends the Bloom filter to the corresponding entities.
The network model mainly considers the following three types of network threats: (1) threats on fog nodes and the data center: fog nodes and the cloud server are considered honest but curious. Namely, they strictly abide by the service protocol, but at the same time, they will attempt to learn all detailed information from received data. In addition, fog nodes and the cloud server are easy to capture; (2) threats on the communication link: there is a potential hazard that an attacker may obtain private user data through eavesdropping on communication links; (3) threats of active attacks: an attacker may damage the authenticity and integrity of transmission data by launching active attacks (such as tampering, forgery, or replay).
3 Blockchain-Enabled Secure and Privacy-Preserving Data Aggregation
This section presents a blockchain-enabled secure and privacy-preserving data aggregation scheme for fog-based ITS. This scheme includes five parts: system initialization, power injection request, EV-chain generation, fog-chain generation and application support.
The TA is used to perform system initialization, including two procedures: the generation and distribution of parameters and the registration of devices.
3.1.1 The Generation and Distribution of Parameters
In the generation phase, the TA selects security parameter k and generates
Each EV chooses a random secure key
Finally, after the generation of system parameters
The EVs need to be registered, and the registration process is illustrated in Fig. 2.
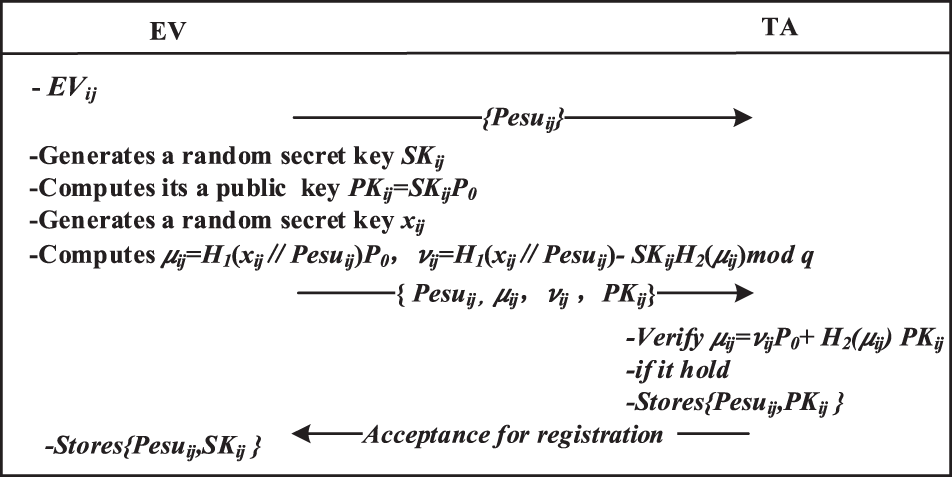
Figure 2: Registration process of EVs
Step-1: First, in a certain subarea, every new EV will generate information
Step-2: Then, in the such subarea,
Step-3: Subsequently,
Step-4: Next, the EV sends the parameters
Step-5: Finally, the TA creates a Bloom filter based on the stored parameter
Similarly, the fog node also needs to be registered, and the process is the same as that for the EV. Specifically, the fog node generates parameters
During peak hours of power consumption, the cloud server in the data and control center will perform the following operations.
Step-1: First, the cloud server will select a random element
Then, it obtains the power injection request packet
Step-2: After the fog node
According to the equation
Step-3: To protect the identity information of the fog node
Then, it obtains the packet
Step-4: After receiving the data packet
If the above equation holds, the packet’s source is legal, and the EV prepares for a power injection operation. Next, the generation processes of EV chains and fog chains are illustrated in Fig. 3.

Figure 3: Generation processes of an EV chain and a fog chain
The electric vehicle
3.3.1 Generation of a Transaction
Step-1: Generation of injection power ciphertext. The uploaded injection data of
Step-2: Generation of ciphertext signature. This signature is mainly used to verify the integrity and authenticity of the ciphertext.
Step-3: Verification of EV’s pseudonym and timestamp. After the
Step-4: Verification of the ciphertext signature. If
Step-5: Generation of fine-grained aggregated ciphertext. The fog node
Step-6: Generation of aggregated ciphertext signature.
Step-7: Transaction generation. After the above operations are completed, it generates the transaction information
The fog node records the generated transaction
After the fog node creates a new EV block, this new block will be broadcast to all EVs in this subarea. These EVs will verify the records in the new block, and each EV only verifies the data with which it is associated to save computing resources. If the new block passes the verification, it will broadcast the verification result to other EVs in the same subarea. It is assumed that the number of malicious EVs is less than
3.4 Generation of the Fog-chain
When the system generates the EV chain, the fog node transmits the EV chain to the aggregation node for secondary aggregation at the data aggregation layer. Subsequently, the aggregation node generates a new block based on the result of the secondary aggregation and adds it to the fog chain. The specific process is similar to the generation of the EV chain.
3.4.1 Generation of the Transaction
Step-1: Verification of information. The aggregation node queries the transaction information
Step-2: Generation of coarse-grained aggregated ciphertext. After the aggregation node completes the above verifications, it will perform a secondary aggregation to collect the injection power from m subareas.
Step-3: Generation of the ciphertext signature. After the coarse-grained aggregated ciphertext is generated, the aggregation node signs the aggregated ciphertext C, as expressed below.
Step-4: Transaction generation. After the above operations are completed, the aggregation node will generate the transaction
3.4.2 Addition to the Fog-chain
The aggregation node at the data aggregation layer records the transaction in a new block and broadcasts this new block to other fog nodes for information authentication. Similar to the creation of the EV chain, a new fog block at the aggregation node mainly includes transactions, timestamps, pseudonyms, Merkle roots, and the hash values of the previous block and the current block. After the execution of the consensus mechanism, the verified block is added to the fog chain, and the aggregation node sends the newly generated fog chain to the data center at the application supporting layer for further processing.
At the application supporting layer, the cloud server reads the transaction information T of the received fog chain and verifies the identity of the aggregation node. If the node’s identity is correct, it further checks the signature of the ciphertext. If it also passes the signature verification, the Paillier decryption algorithm is used to decrypt the aggregated ciphertext, and the steps are as follows.
Step-1: Verification of information. After the cloud server queries the transaction information
Step-2: Decryption of the aggregated ciphertext. If all the verifications are passed, the decryption operation of the Paillier algorithm is applied to decrypt the aggregated ciphertext using the private key, and it can obtain the total amount of plaintext injection power of the whole area. Meanwhile, the amount of injection power of each subarea can be derived by employing Horner’s rule; namely, the fine-grained aggregation result can be recovered. Based on these coarse-grained and fine-grained results, the ITS can flexibly regulate the power supply during peak hours to maintain the supply-demand balance. It can also realize peak shaving and valley filling by a historical data-based time-of-use pricing mechanism. Thus, these data can provide strong support for various application services in ITS.
The focus of this section is to analyze the security and privacy of the developed scheme and evaluate its performance while guaranteeing the security and privacy of collected data.
As described in Section 2, there are three main types of network threats: honest-but-curious processing nodes, link eavesdropping and active attacks. To resist first two types of threats, Paillier homomorphic encryption is utilized to encrypt the power injection data to counteract eavesdropping attacks and prevent information from leaking to honest-but-curious fog and cloud nodes. Although the cloud server can derive the aggregation result of each subarea, it cannot recover the power injection data of each EV. Consequently, the proposed scheme can guarantee confidentiality for EV power injection data. Intending to resist active attacks from attackers, the signature mechanism with a timestamp in the proposed scheme guarantees the integrity and validity of private data. Furthermore, the Bloom filter can ensure the identity anonymity and authenticity of valid nodes. As a result, the developed scheme guarantees the integrity and validity of private data and provides identity protection for EVs and fog nodes.
To analyze the performance of the proposed scheme, this paper compares the computational costs of this scheme with two previously established schemes: privacy-aware data aggregation (PADA) [28] and efficient privacy-preserving communication and power injection (ePPCP) [29]. To facilitate the explanation, with the same definitions in reference [30], it represents

In the PADA scheme, the generation of a power request packet
In the ePPCP scheme, to generate power requests, a computational cost of
To generate the power request

Through the above analysis, the developed solution has advantages over computational costs, but these advantages are not unconditional. For example, to achieve secure and reliable power injection, this paper adopts blockchain technology which usually associates with specific memory and bandwidth consumptions, but this trade-off is acceptable and well worth for the security and privacy preservation improvements. To show the above results more intuitively, the following figures are shown.
As shown in Fig. 4, the computational cost at the UC is directly proportional to the number of EVs. Compared with PADA and ePPCP, the computational cost at the UC of the proposed scheme is lower, and as the number of EVs increases, this advantage is enhanced. This is mainly because PADA uses expensive bilinear pairing calculations to generate packets, and ePPCP uses many exponential operations. Compared to PADA and ePPCP, the proposed scheme effectively avoids these operations, thereby reducing computational costs.
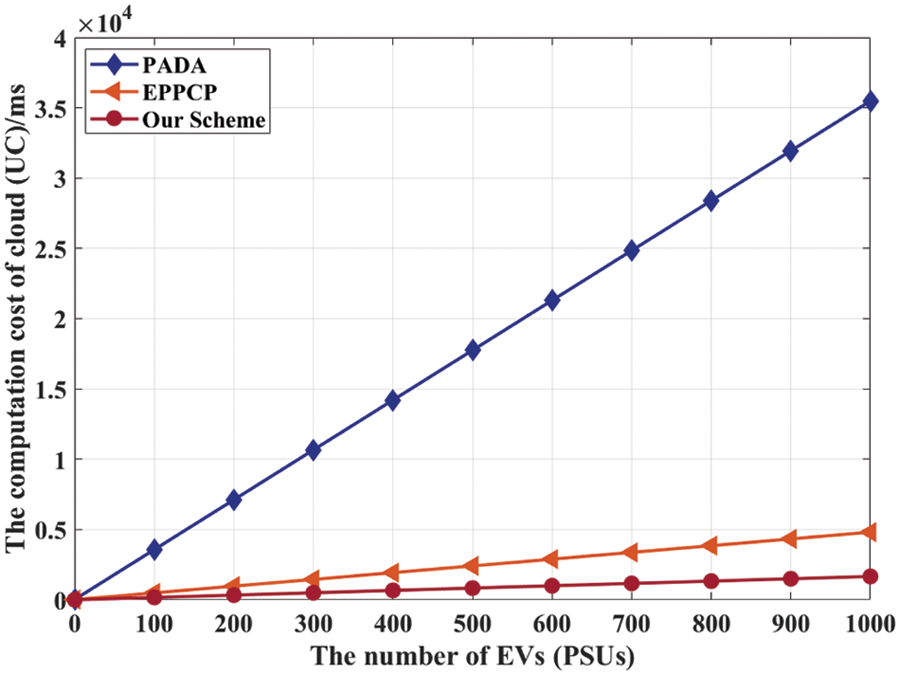
Figure 4: Comparison of computational costs of the cloud (UC)
As shown in Fig. 5, the computational cost at the fog (GW) is also proportional to the number of EVs. Meanwhile, compared with those of schemes PADA and ePPCP, the computational cost of the proposed scheme is lower, and this advantage is strengthened with the increase in the number of EVs. This is mainly because PADA uses pairing calculations to verify the data packets generated by the UC in the privacy aggregation phase, the PADA scheme also uses pairing operations and many multiplication operations. At the same time, ePPCP uses many exponential operations to verify data packets and aggregate private data. Compared to PADA and ePPCP, the proposed scheme effectively avoids pairing operations and simplifies the operations as much as possible; thus, it can reduce the computational costs significantly.

Figure 5: Comparison of computational costs of the fog (GW)
Results similar to those in the above two figures are presented in Fig. 6, which shows the computational cost of the proposed scheme is lower than those of the other two schemes at the EV. PADA utilizes many bilinear pairing operations to protect private data and verify the integrity and authenticity of packets broadcasted by the gateway. Meanwhile, in ePPCP, many exponential operations are used, which consume a substantial amount of time.

Figure 6: Comparison of computational costs of the EV (PSU)
As depicted in Fig. 7, the total computational cost is significantly reduced in our proposed scheme while providing security and privacy protections. The proposed scheme is more suitable for ITS with latency-sensitive applications and is also adapted to deploying devices with limited resources.

Figure 7: Total computational costs comparison
Existing privacy protection schemes tend to focus on the security of identity, while ignoring that fine-grained power consumption data are also sensitive. And many privacy protection schemes of power consumption data require high computational costs. To achieve the efficient aggregation of EV injection data with security and privacy guarantees, this paper proposes a blockchain-enabled secure and privacy-preserving data aggregation scheme for fog-based ITS. The proposed scheme constructs a secure and efficient aggregation framework by combining fog computing and blockchain technology. Then, it uses the Bloom filter and lightweight signature mechanism to build a secure and anonymous registration and authentication mechanism for preventing forgery attacks from malicious nodes. Furthermore, Paillier homomorphic encryption is implemented to encrypt the power injection data to ensure the confidentiality of the data. Finally, the performance evaluation shows that the proposed scheme has a lower computational cost with security and privacy guarantees. It is assumed that all EVs are benign and do not consider the impact of malicious EVs uploading fake private data on system performance. In the future, this paper will combine blockchain and smart contract technology to defend against malicious poisoning attacks.
Funding Statement: The authors received Funding for this study from the National Natural Science Foundation of China (No. 61971235), the China Postdoctoral Science Foundation (No. 2018M630590), the Jiangsu Planned Projects for Postdoctoral Research Funds (No. 2021K501C), the 333 High-level Talents Training Project of Jiangsu Province, and the 1311 Talents Plan of NJUPT.
Conflicts of Interest: The authors declare that they have no conflicts of interest to report regarding the present study.
References
1. J. Dixon, W. Bukhsh, C. Edmunds and K. Bell, “Scheduling electric vehicle charging to minimise carbon emissions and wind curtailment,” Renewable Energy, vol. 161, no. 4, pp. 1072–1091, 2020. [Google Scholar]
2. L. Calearo, M. Marinelli and C. Ziras, “A review of data sources for electric vehicle integration studies,” Renewable and Sustainable Energy Reviews, vol. 151, no. 3, pp. 1–18, 2021. [Google Scholar]
3. J. Van Mierlo, M. Berecibar, M. El Baghdadi, C. De Cauwer, M. Messagie et al., “Beyond the state of the art of electric vehicles: A fact-based paper of the current and prospective electric vehicle technologies,” World Electric Vehicle Journal, vol. 12, no. 1, pp. 1–26, 2021. [Google Scholar]
4. M. R. Patel, A. P. Shah, K. J. Chudasama and G. J. Jadhav, “A review of EV converters performance during V2G /G2V mode of operation,” in Proc. INCET, Belgaum, India, pp. 1–7, 2022. [Google Scholar]
5. M. Boni, T. Ch, S. Alamanda, B. V. S. G. Arasada and A. Maria, “An efficient and secure anonymous authentication scheme for V2G networks,” in Proc. ICDCS, Coimbatore, India, pp. 432–436, 2022. [Google Scholar]
6. G. Sharma, A. M. Joshi and S. P. Mohanty, “An efficient physically unclonable function based authentication scheme for V2G network,” in Proc. ISES, Jaipur, India, pp. 421–425, 2021. [Google Scholar]
7. S. Ahmed, S. Shamshad, Z. Ghaffar, K. Mahmood, N. Kumar et al., “Signcryption based authenticated and key exchange protocol for EI-based V2G environment,” IEEE Transactions on Smart Grid, vol. 12, no. 6, pp. 5290–5298, 2021. [Google Scholar]
8. F. Wang, L. Jiao, K. Zhu, K. Zhu and L. Zhang, “Online edge computing demand response via deadline-aware V2G discharging auctions,” IEEE Transactions on Mobile Computing, pp. 1–14, 2022. https://doi.org/10.1109/TMC.2022.3208420 [Google Scholar] [CrossRef]
9. B. Bibak and H. Tekiner-Moğulkoç, “A comprehensive analysis of vehicle to grid (V2G) systems and scholarly literature on the application of such systems,” Renewable Energy Focus, vol. 36, no. February (2016), pp. 1–20, 2021. [Google Scholar]
10. S. Goyal, S. Bhushan, Y. Kumar, A. H. S. Rana, M. R. Bhutta et al., “An optimized framework for energy-resource allocation in a cloud environment based on the whale optimization algorithm,” Sensors, vol. 21, no. 5, pp. 1–24, 2021. [Google Scholar]
11. S. Rani, D. Koundal, Kavita, M. F. Ijaz, M. Elhoseny et al., “An optimized framework for WSN routing in the context of industry 4. 0,” Sensors, vol. 21, no. 19, pp. 1–15, 2021. [Google Scholar]
12. F. Gao, L. Zhu, M. Shen, K. Sharif, Z. Wan et al., “A blockchain-based privacy-preserving payment mechanism for vehicle-to-grid networks,” IEEE Network, vol. 32, no. 6, pp. 184–192, 2018. [Google Scholar]
13. W. Han and Y. Xiao, “Privacy preservation for V2G networks in smart grid: A survey,” Computer Communications, vol. 91, no. 1, pp. 17–28, 2016. [Google Scholar]
14. N. Saxena and B. J. Choi, “Authentication scheme for flexible charging and discharging of mobile vehicles in the V2G networks,” IEEE Transactions on Information Forensics and Security, vol. 11, no. 7, pp. 1438–1452, 2016. [Google Scholar]
15. A. Abdallah and X. S. Shen, “Lightweight authentication and privacy preserving scheme for V2G connections,” IEEE Transactions on Vehicular Technology, vol. 66, no. 3, pp. 2615–2629, 2017. [Google Scholar]
16. M. Tao, K. Ota, M. Dong and Z. Qian, “AccessAuth: Capacity-aware security access authentication in federated-IoT-enabled V2G networks,” Journal of Parallel and Distributed Computing, vol. 118, no. 4, pp. 107–117, 2018. [Google Scholar]
17. G. Liang, S. R. Weller, F. Luo, J. Zhao and Z. Dong, “Distributed blockchain-based data protection framework for modern power systems against cyber attacks,” IEEE Transactions on Smart Grid, vol. 10, no. 3, pp. 3162–3173, 2019. [Google Scholar]
18. M. Fan and X. Zhang, “Consortium blockchain based data aggregation and regulation mechanism for smart grid,” IEEE Access, vol. 7, pp. 35929–35940, 2019. [Google Scholar]
19. Z. Guan, G. Si, X. Zhang, L. Wu, N. Guizani et al., “Privacy-preserving and efficient aggregation based on blockchain for power grid communications in smart communities,” IEEE Communications Magazine, vol. 56, no. 7, pp. 82–88, 2018. [Google Scholar]
20. L. F. A. Roman, P. R. L. Gondim and J. Lloret, “Pairing-based authentication protocol for V2G networks in smart grid,” Ad Hoc Networks, vol. 90, no. 3, pp. 1–16, 2019. [Google Scholar]
21. M. Wazid, A. K. Das, N. Kumar and J. J. P. C. Rodrigues, “Secure three factor user authentication scheme for renewable energy based smart grid environment,” IEEE Transactions on Industrial Informatics, vol. 13, no. 6, pp. 3144–3153, 2017. [Google Scholar]
22. D. Abbasinezhad-Mood and M. Nikooghadam, “An anonymous ECC-based self-certified key distribution scheme for the smart grid,” IEEE Transactions on Industrial Electronics, vol. 65, no. 10, pp. 7996–8004, 2018. [Google Scholar]
23. D. Liu, D. Li, X. Liu, L. Ma, H. Yu et al., “Research on a cross-domain authentication scheme based on consortium blockchain in V2G networks of smart grid,” in Proc. EI2, Beijing, China, pp. 1–5, 2018. [Google Scholar]
24. J. Kang, R. Yu, X. Huang, S. Maharjan, Y. Zhang et al., “Enabling localized peer-to-peer electricity trading among plug-in hybrid electric vehicles using consortium blockchains,” IEEE Transactions on Industrial Informatics, vol. 13, no. 6, pp. 3154–3164, 2017. [Google Scholar]
25. S. Garg, K. Kaur, G. Kaddoum, F. Gagnon, J. J. P. C. Rodrigues et al., “An efficient blockchain-based hierarchical authentication mechanism for energy trading in V2G environment,” in Proc. ICC Workshops, Shanghai, China, pp. 1–6, 2019. [Google Scholar]
26. S. Tonyali, O. Cakmak, K. Akkaya, M. M. E. A. Mahmoud, I. Guvenc et al., “Secure data obfuscation scheme to enable privacy-preserving state estimation in smart grid AMI networks,” IEEE Internet of Things Journal, vol. 3, no. 5, pp. 709–719, 2016. [Google Scholar]
27. M. M. E. A. Mahmoud, N. Saputro, P. K. Akula and K. Akkaya, “Privacy-preserving power injection over a hybrid AMI/LTE smart grid network,” IEEE Internet of Things Journal, vol. 4, no. 4, pp. 870–880, 2017. [Google Scholar]
28. Y. Zhang, D. Zheng, Q. Zhao, C. Lai and F. Ren, “PADA: Privacy-aware data aggregation with efficient communication for power injection in 5G smart grid slice,” in Proc. NaNA, Kathmandu, Nepal, pp. 11–16, 2017. [Google Scholar]
29. Y. Zhang, J. Li, D. Zheng, P. Li and Y. Tian, “Privacy-preserving communication and power injection over vehicle networks and 5G smart grid slice,” Journal of Network and Computer Applications, vol. 122, no. 6, pp. 50–60, 2018. [Google Scholar]
30. S. Chen, L. Yang, C. Zhao, V. Varadarajan and K. Wang, “Double-blockchain assisted secure and anonymous data aggregation for fog-enabled smart grid,” Engineering, vol. 8, no. 1, pp. 159–169, 2022. [Google Scholar]
Cite This Article
 Copyright © 2023 The Author(s). Published by Tech Science Press.
Copyright © 2023 The Author(s). Published by Tech Science Press.This work is licensed under a Creative Commons Attribution 4.0 International License , which permits unrestricted use, distribution, and reproduction in any medium, provided the original work is properly cited.


 Submit a Paper
Submit a Paper Propose a Special lssue
Propose a Special lssue View Full Text
View Full Text Download PDF
Download PDF Downloads
Downloads
 Citation Tools
Citation Tools