 Open Access
Open Access
ARTICLE
An Efficient EMD-Based Reversible Data Hiding Technique Using Dual Stego Images
Princess Sumaya University for Technology, Amman, 11941, Jordan
* Corresponding Author: Ahmad A. Mohammad. Email:
Computers, Materials & Continua 2023, 75(1), 1139-1156. https://doi.org/10.32604/cmc.2023.035964
Received 12 September 2022; Accepted 08 December 2022; Issue published 06 February 2023
Abstract
Exploiting modification direction (EMD) based data hiding techniques (DHTs) provide moderate data hiding capacity and high-quality stego images. The overflow problem and the cyclic nature of the extraction function essentially hinder their application in several fields in which reversibility is necessary. Thus far, the few EMD reversible DHTs are complex and numerically demanding. This paper presents a novel EMD-based reversible DHT using dual-image. Two novel 2 × 4 modification lookup tables are introduced, replacing the reference matrix used in similar techniques and eliminating the numerically demanding search step in similar techniques. In the embedding step, one of the modification tables modifies a pixel in odd columns in the first cover image and keeps its image in the second cover image intact. The other modification table modifies a pixel in even columns in the second cover image and keeps its image in the first cover image intact. This embedding strategy enables direct reversibility at almost zero computational cost. This technique embeds one secret digit into each pixel in the first cover image and its image in the second cover image resulting in one bit per pixel (bpp) data embedding rate. The use of the numbering system enables direct and numerically efficient conversion of the binary secret message to the and vice versa. The advantages of the proposed algorithm are straightforward reversibility, simplicity, numerical efficiency, direct conversion of the binary secret message to and vice versa, and elimination of the need for the reference matrix by replacing it with two 2 × 4 lookup tables. Simulation results show that the embedding rate of the proposed technique is one bpp. It achieved more than 49 dB average Peak to Signal Noise Ratio (PSNR) over all test images.Keywords
In the era of the internet, the internet of things (IoT), and mobile communications, the interchange of vast amounts of digital data has become an easy task. Some of this information includes some secret data. Unintended recipients can easily access this data. Thus, there is a need for the development of means to protect the transmitted data. Thus far, researchers have developed two main methods to achieve data protection: Data encryption [1] and Data hiding [2–43]. Data encryption techniques share the data in a meaningless form and can be easily identified as confidential data, making it vulnerable to attacks [2]. DHTs conceal the secret data in meaningful digital media (usually a digital image called a cover image). Depending on the nature of the hidden message, one can classify DHTs into two main categories: Digital watermarking, when the message is concerned with the cover, and steganography, otherwise [2]. Steganographic techniques transparently conceal the secret message into a cover object such as a digital image. The main objective of these techniques is to hide the mere existence of the secret message in the cover object. However, the concealment of the secret message in the cover object produces a distorted stego object with reduced visual quality. Steganographic techniques should keep the distortion minimal and transparent so it cannot be detected. Another important objective in steganography is to increase the data hiding capacity, defined as the number of secret message bits embedded in the cover object. However, increasing data hiding capacity introduces more distortions in the cover image, reducing visual quality and destroying transparency. Thus, there is a need for a tradeoff between transparency and data-hiding capacity [3]. DHTs may also be classified as irreversible [3–23] and reversible [24–43]. In irreversible DHTs, the distortions to the cover object are permanent, and one can’t restore the original cover object after extracting the secret message. In reversible DHTs, the distortions to the cover image are not permanent, and one can restore the original cover image after extracting the secret message. The reversibility of DHTs is necessary for some applications, such as military, law enforcement, and medical applications. DHTs are numerous and may be carried out in the spatial or transform domains [3]. In the spatial domain, one can find several methods, such as Image interpolation, Difference expansion (D.E.), Histogram shifting (H.S.), Least significant bit substitution (LSB), and EMD-based methods [3].
The EMD-based methods have some attractive features: They provide high-quality stego images and can attain relatively high embedding rates. EMD-based techniques have witnessed extensive research efforts [4–36]. Reference [8] introduced the first EMD-based technique, partitioning the cover image into groups of
We summarize our findings by the following points:
• Due to the cyclic nature of the extraction function and the overflow problem, EMD-based DHTs are not directly reversible
• EMD-based DHTs can provide high embedding rates. However, increasing the embedding rate decreases the stego image quality
• In general, increasing embedding rates above two bpp results in significant distortions in the stego image, making it vulnerable to detection
• Researchers proposed the use of dual images to develop reversible EMD-based DHTs
• The use of dual images increases the security of the secret data via secret key sharing
• Thus far, existing dual image-based EMD-based reversible DHTs are numerically demanding, require complex search algorithms, and need to generate a
This paper presents an EMD-based reversible DHT using dual stego images. The contributions of our technique are:
• Simple and numerically efficient embedding and extraction algorithms
• Relatively high data-hiding capacity
• Direct and numerically efficient conversion of the binary secret message to
• Elimination of the need for the
• An embedding strategy that enables straightforward reversibility with almost zero computational cost
• Increased Security by using secret key sharing and the equal high-quality of the two stego images
The rest of this paper proceeds as follows. In Section 2, we give a summary of some related work. Section 3 outlines the proposed algorithm, the data-hiding step, and the data extraction and image recovery step. Section 4 gives experimental simulation results. Finally, Section 5 presents the discussion, conclusion, and future work.
This section presents the fundamentals of EMD-based DHTs and gives details of some related techniques.
2.1 Fundamentals of EMD-Based DHTs
These schemes conceal an
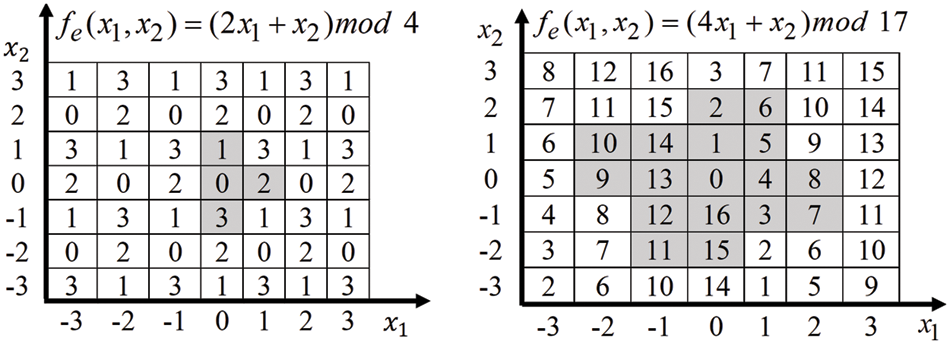
Figure 1: Neighborhood set for different extraction functions
This section presents two closely related DHTs proposed by [8,31].
2.2.1 EMD Algorithm [8]
This scheme is the basis of EMD-based DHTs. It embeds a
If
Set
ElseIf
Set
Else
Set
End.
At the receiver end, we extract the secret digit as
2.2.2 Reversibility Data Hiding [31]
Reference [31] proposed an EMD-based reversible DHT scheme using dual images. The extraction function is:
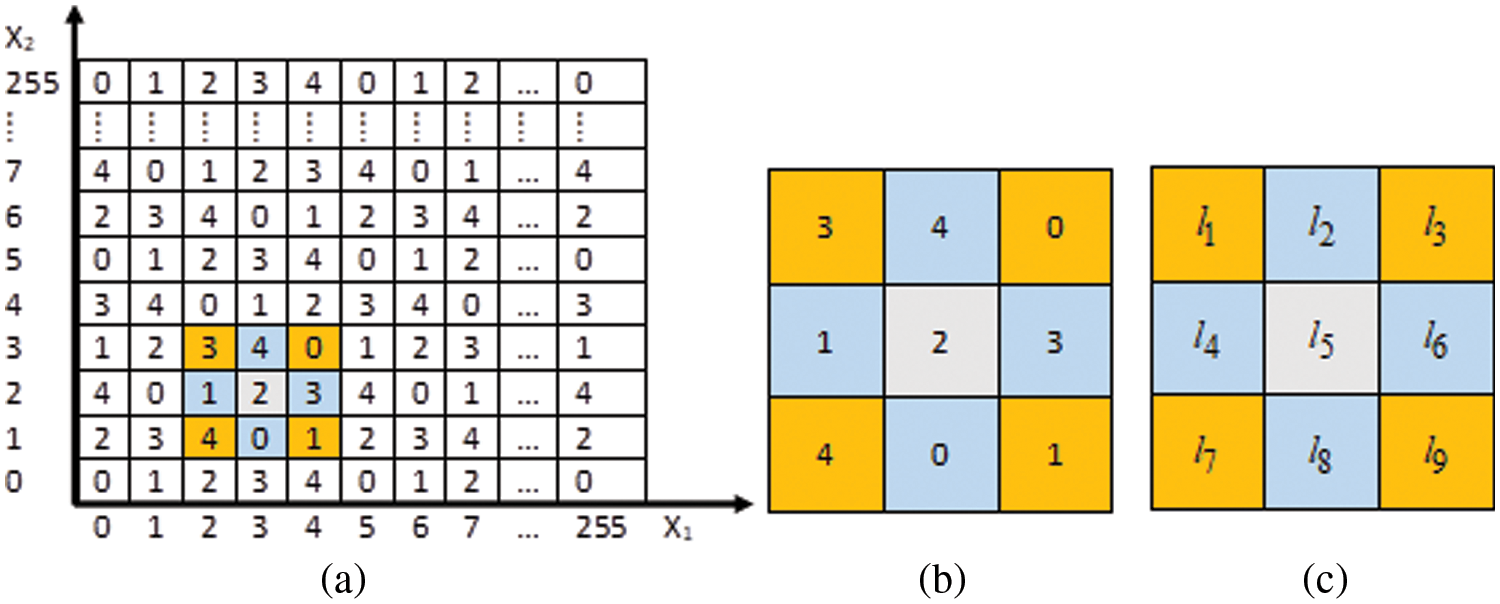
Figure 2: (a) Reference matrix (b) 3 × 3 block (c) 9 positions labeling
Embedding Algorithm [31]
If (
Do not embed the secret message. Set
ElseIf
Set
ElseIf
If
Set
ElseIf the line segment from
Set
Else
Set
End
End
Secret message extraction and original image recovery [31]
Given the two stego pixel pairs
Case 1:
If (
Set
Else
Set
End
Case 2
Set
Case 3
Set
Case 4
Set
If
Else
Set
Extract the two secret digits from the reference matrix M corresponding to
End
Case 5
Set
Case 6
Set
The proposed algorithm is a reversible EMD-based algorithm that uses the general extraction function:
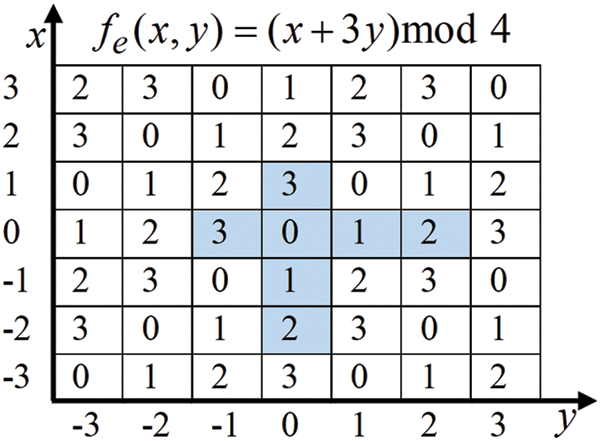
Figure 3: Neighborhood set
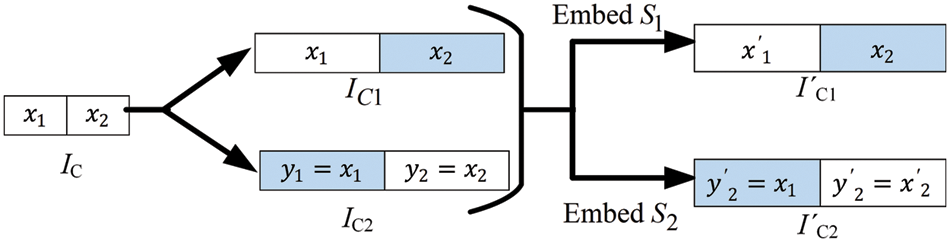
Figure 4: Flow of proposed dual images embedding
In the proposed algorithm, we facilitate the embedding process by defining two novel modification tables to eliminate the search step in the neighborhood set and modify the cover images systematically in a numerically efficient manner. In Fig. 4, the changes to pixels
Eq. (3) finds the stego pixels (
We calculate the stego pixels (
For extraction, we find the two secret digits
3.1 The Proposed Data Embedding Algorithm
Given the
Step 1: Obtain the dual cover images
Step 2: Classify the dual cover images’ pixels into two classes: embeddable pixels and non-embeddable pixels. Embeddable pixels in the first cover image
Step 3: Prevent overflow and underflow problems by modifying each embeddable pixel
where
Step 4: Sequentially scan the cover images from left to right and top to bottom and embed one
Step 5: Get two bits from the binary secret message and find its
Step 6: Let the current decimal values of the pixels in the preprocessed cover images be:
Step 7: Use Eq. (7) to find the distance d as:
Step 8: Find
The result of this process is the two stego images
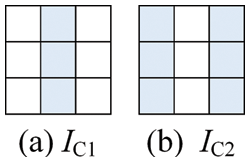
Figure 5: Embeddable pixels selection
3.2 The Proposed Data Extraction and Image Recovery Algorithm
Given the dual stego images
Step 1: Classify the stego images’ pixels into two classes: embeddable and non-embeddable pixels, in the same manner as in the embedding step. Fig. 6 shows this classification where the white pixels are the embeddable pixels while the shaded pixels are the non-embeddable pixels.
Step 2: Recover the original cover image
Step 3: Refer to Fig. 6 and let the current decimal values of the stego images’ pixels in
Step 4: Find the binary value of
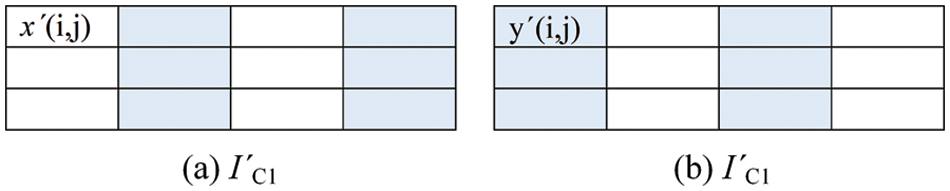
Figure 6: Embeddable pixels classification
We conclude this section by giving a numerical example to illustrate the operational steps of the proposed reversible DHT. Fig. 7 shows a 1 × 2 original cover image
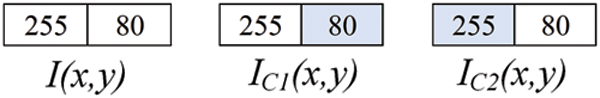
Figure 7: Original and dual cover images
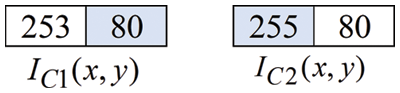
Figure 8: Preprocessed dual cover images
Given the binary secret message W = [1011], convert every two binary bits into its
Assign the value of the first pixel in
Assign the value of the next pixel in
Fig. 9 shows the resulting dual stego images.
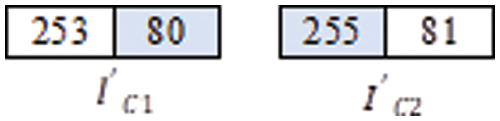
Figure 9: Dual stego images
For extraction, starting with dual stego images in Fig. 9, the original cover image is obtained by combining the shaded columns in
This section presents the simulation results of the proposed technique. To measure the quality of the stego images, we use the PSNR values of the stego images. The PSNR between an
We use the embedding rate as a measure of the data hiding capacity. The embedding rate R is given by Eq. (11).
where
We used the CPU time as a measure to evaluate the numerical efficiency. In our simulations, we used twelve

Figure 10: Test images
4.1 Performance Evaluation of the Proposed Technique
Fig. 11 shows the stego images at the maximum embedding rate. The high quality of the stego images is clear, and the human eye can detect no traces of any artifacts.

Figure 11: Stego images
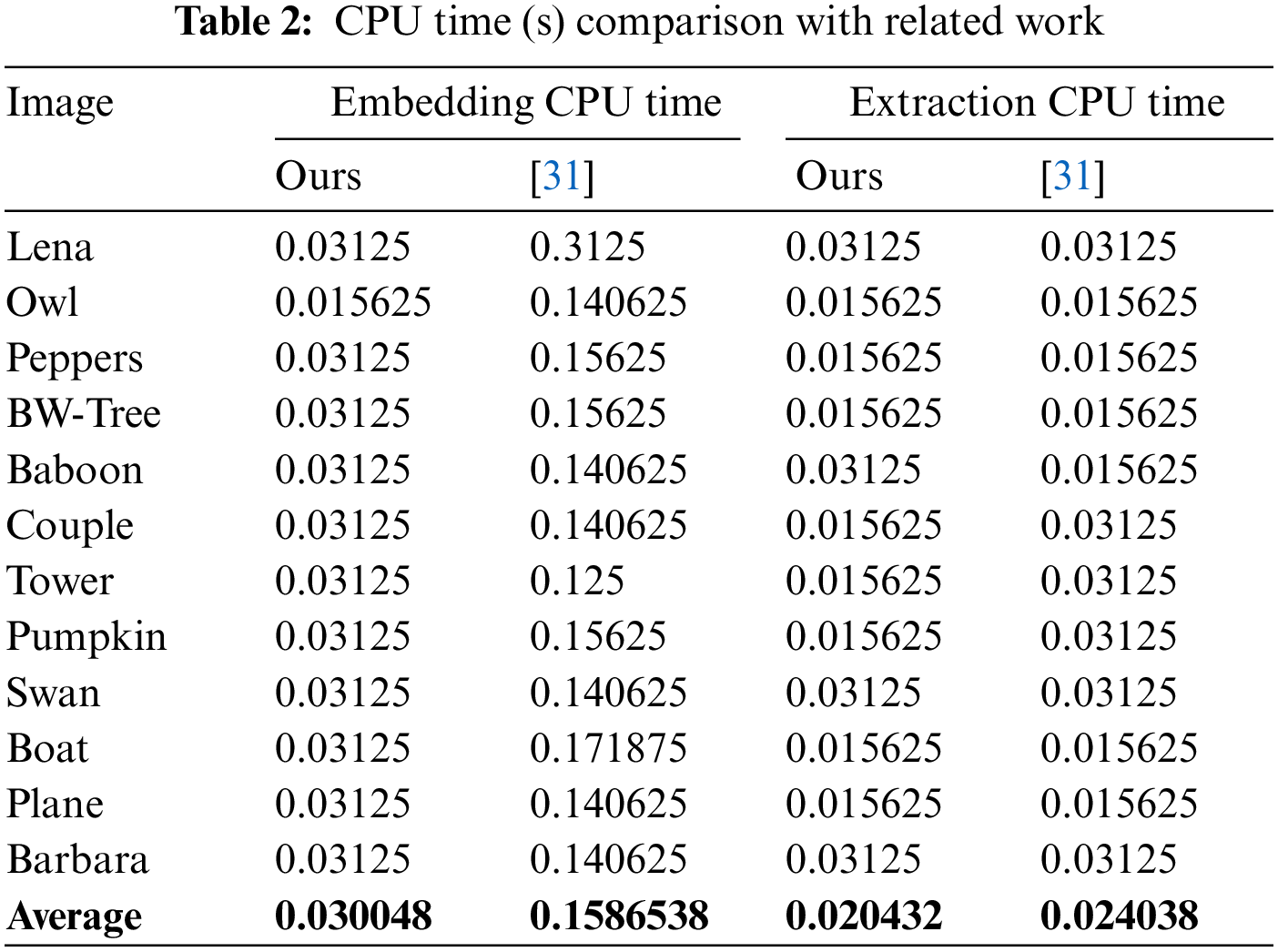
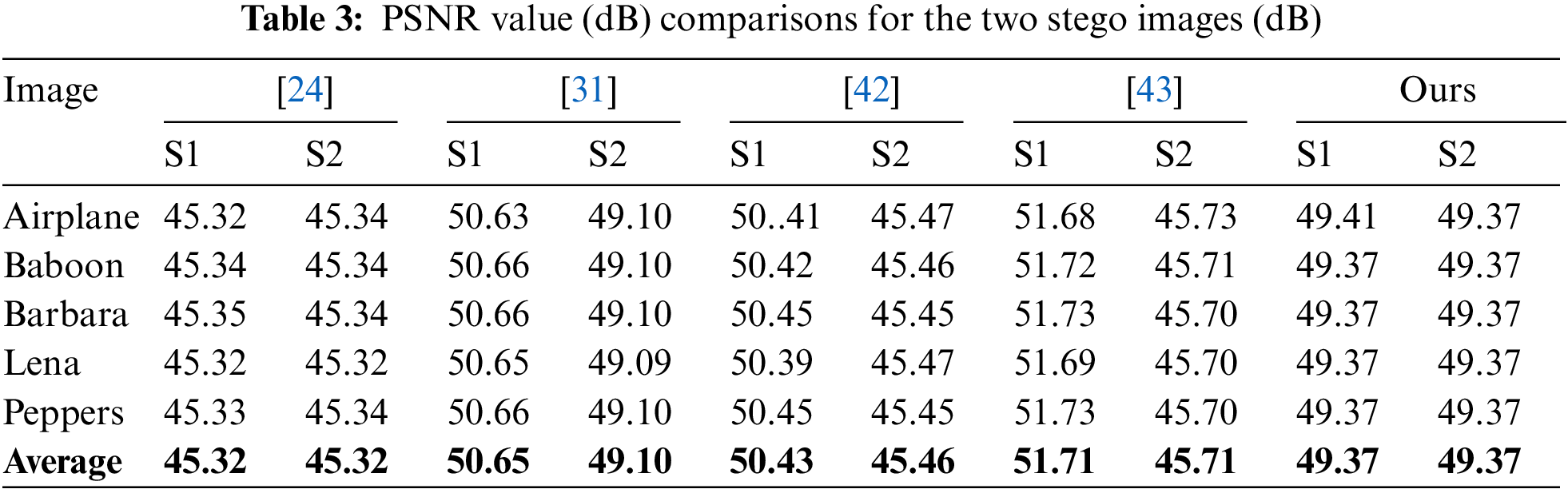
Table 1 gives the main features of our technique. The high quality of the stego images is evident via an average PSNR value of more than 49 dB. In addition, Table 1 also shows that the average absolute distortion in the pixels is about 0.5/pixel. Moreover, Table 1 also shows that, at the maximum embedding rate, our algorithm achieved a high average PSNR value of 49 dB. We conducted another experiment to investigate the PSNR values of the stego images against different embedding rates. Fig. 12 shows the results for the Lena image, where the PSNR values for both stego images ranged from 80 dB when the embedding rate is 1/16 bpp to 49 dB when the embedding rate is one bpp. An essential feature of our algorithm is that the PSNR values are practically identical for both stego images. This feature improves security. In addition, the PSNR values are almost identical for all test images. This shows that the performance of our technique does not depend on the cover image. Our technique embeds one
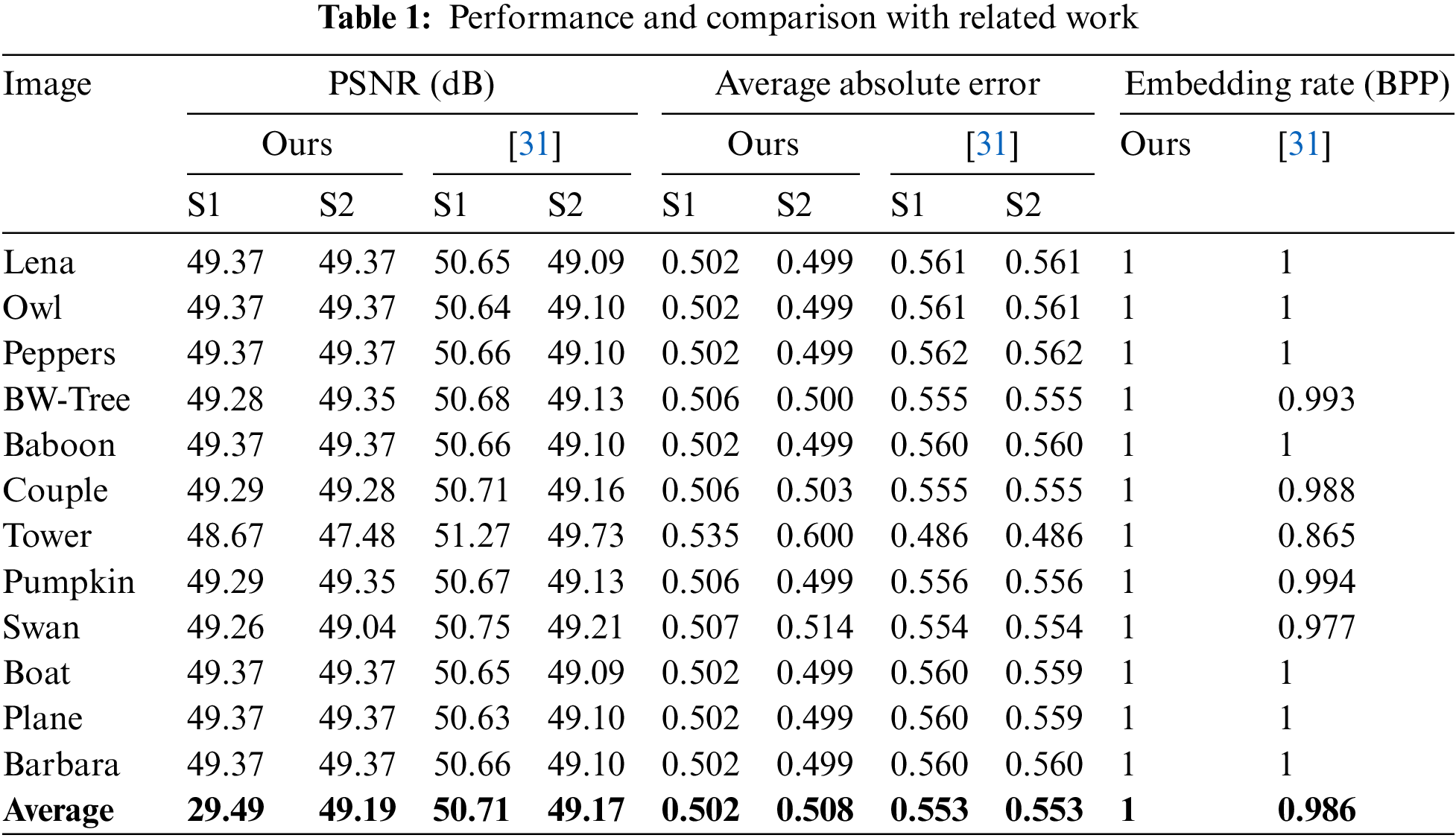
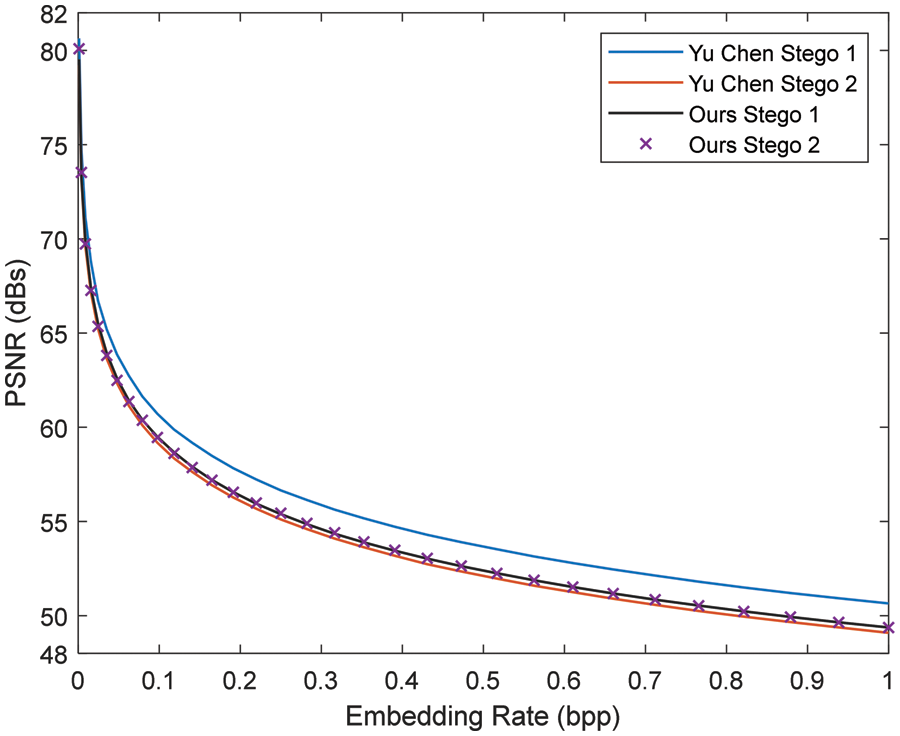
Figure 12: PSNR vs. embedding rate performance lena image
4.2 Performance Comparisons with Related Work
Table 1 also compares our technique with [31] in terms of PSNR values, average absolute error, and embedding rates. The average embedding rate of our technique is one bpp, while that of [31] is 0.9859 bpp. In obtaining these results, we converted each byte of the binary message to its
This paper presented a new reversible RDHT based on EMD. The proposed technique is simple and numerically efficient. It limits image distortions and increases stego image quality and transparency. Each pixel pair of the two stego images (one pixel from each stego image) hides one
Funding Statement: The author received no funding for this study.
Conflicts of Interest: The author declares that he has no conflicts of interest to report regarding the present study.
References
1. Z. Yin, Y. Peng and Y. Xiang, “Reversible data hiding in encrypted images based on pixel prediction and bit-plane compression,” IEEE Transactions on Dependable and Secure Computing, vol. 19, no. 2, pp. 992–1002, 2022. [Google Scholar]
2. I. J. Cox, M. L. Miller, J. A. Bloom, J. Fridrich and T. Kalker, “Chapter 1-Introduction,” in The Morgan Kaufmann Series in Multimedia Information and Systems, 2nd edition, Morgan Kaufmann, Amsterdam, Netherlands: Elsevier Publishing company, pp. 1–13, 2008. [Google Scholar]
3. A. A. Mohammad, A. Al-Haj and M. Farfoura, “An improved capacity data hiding technique based on image interpolation,” Multimedia Tools and Applications, vol. 78, no. 6, pp. 7181–7205, 2018. [Google Scholar]
4. Z. S. Younus and M. K. Hussain, “Image steganography using exploiting modification direction for compressed encrypted data,” Journal of King Saud University-Computer and Information Sciences, vol. 34, no. 6, pp. 2951–2963, 2022. [Google Scholar]
5. C. -M. Wang, N. -I. Wu, C. -S. Tsai and M. -S. Hwang, “A high quality steganographic method with pixel-value differencing and modulus function,” Journal of Systems and Software, vol. 81, no. 1, pp. 150–158, 2008. [Google Scholar]
6. K. -H. Jung and K. -Y. Yoo, “Improved exploiting modification direction method by modulus operation,” International Journal of Signal Processing Image Processing and Pattern Recognition, vol. 2, no. 3, pp. 79–87, 2009. [Google Scholar]
7. W. Kou, “Image hiding by square fully exploiting modification directions,” Journal of Information Hiding and Multimedia Signal Processing, vol. 4, no. 1, pp. 128–137, 2013. [Google Scholar]
8. X. Zhang and S. Wang, “Efficient steganographic embedding by exploiting modification direction,” IEEE Communications Letters, vol. 10, no. 11, pp. 781–783, 2006. [Google Scholar]
9. C. -F. Lee, Y. -R. Wang and C. -C. Chang, “A steganographic method with high embedding capacity by improving exploiting modification direction,” in Third Int. Conf. on Intelligent Information Hiding and Multimedia Signal Processing (IIH-MSP 2007), Kaohsiung, Taiwan, pp. 497–500, 2007. [Google Scholar]
10. R. -M. Chao, H. -C. Wu, C. -C. Lee and Y. -P. Chu, “A novel image data hiding scheme with diamond encoding,” EURASIP Journal on Information Security, vol. 2009, pp. 1–9, 2009. [Google Scholar]
11. R. Rasiyath, “Data embedding and extracting using pixel pair matching with potential masking,” Indian Journal of Applied Research, vol. 3, no. 7, pp. 272–276, 2011. [Google Scholar]
12. T. D. Kieu and C. -C. Chang, “A steganographic scheme by fully exploiting modification directions,” Expert Systems with Applications, vol. 38, no. 8, pp. 10648–10657, 2011. [Google Scholar]
13. W. -C. Kuo and M. -C. Kao, “A steganographic scheme based on formula fully exploiting modification directions,” IEICE Transactions on Fundamentals of Electronics, Communications and Computer Sciences, vol. E96.A, no. 11, pp. 2235–2243, 2013. [Google Scholar]
14. S. -Y. Shen and L. -H. Huang, “A data hiding scheme using pixel value differencing and improving exploiting modification directions,” Computers & Security, vol. 48, pp. 131–141, 2015. [Google Scholar]
15. T. D. Sairam and K. Boopathybagan, “An improved high capacity data hiding scheme using pixel value adjustment and modulus operation,” Multimedia Tools and Applications, vol. 79, no. 23–24, pp. 17003–17013, 2019. [Google Scholar]
16. S. Atawneh, A. Almomani, H. Al Bazar, P. Sumari and B. Gupta, “Secure and imperceptible digital image steganographic algorithm based on diamond encoding in DWT domain,” Multimedia Tools and Applications, vol. 76, no. 18, pp. 18451–18472, 2016. [Google Scholar]
17. Z. Li and Y. He, “Steganography with pixel-value differencing and modulus function based on PSO,” Journal of Information Security and Applications, vol. 43, pp. 47–52, 2018. [Google Scholar]
18. S. Saha, A. Chakraborty, A. Chatterjee, S. Dhargupta, S. K. Ghosal et al., “Extended exploiting modification direction based steganography using hashed-weightage array,” Multimedia Tools and Applications, vol. 79, no. 29–30, pp. 20973–20993, 2020. [Google Scholar]
19. J. -H. Horng, S. Xu, C. -C. Chang and C. -C. Chang, “An efficient data-hiding scheme based on multidimensional mini-sudoku,” Sensors, vol. 20, no. 9, pp. 2739, 2020. [Google Scholar]
20. H. -H. Liu, P. -C. Su and M. -H. Hsu, “An improved steganography method based on least-significant-bit substitution and pixel-value differencing,” KSII Transactions on Internet and Information Systems, vol. 14, no. 11, pp. 4537–4556, 2020. [Google Scholar]
21. C. -F. Lee, J. -J. Shen, S. Agrawal, Y. -X. Wang and Y. -H. Lee, “Data hiding method based on 3D magic cube,” IEEE Access, vol. 8, pp. 39445–39453, 2020. [Google Scholar]
22. R. Atta, M. Ghanbari and I. Elnahry, “Advanced image steganography based on exploiting modification direction and neutrosophic set,” Multimedia Tools and Applications, vol. 80, no. 14, pp. 21751–21769, 2021. [Google Scholar]
23. J. J. Ranjani and F. Zaid, “Pseudo magic cubes: A multidimensional data hiding scheme exploiting modification directions for large payloads,” Computers & Electrical Engineering, vol. 89, pp. 106928, 2021. [Google Scholar]
24. C. -C. Chang, T. Kieu and Y. -C. Chou, “Reversible data hiding scheme using two steganographic images,” in Proc. of TENCON 2007-2007 IEEE Region 10 Conf., Taipei, Taiwan, pp. 1–4, 2007. [Google Scholar]
25. C. -C. Chang, T. -C. Lu, G. Horng, Y. -H. Huang and Y. -M. Hsu, “A high payload data embedding scheme using dual stego-images with reversibility,” in Proc. of 2013 9th Int. Conf. on Information, Communications & Signal Processing, Tainan, Taiwan, pp. 1–5, 2013. [Google Scholar]
26. C. Qin, C. -C. Chang and T. -J. Hsu, “Reversible data hiding scheme based on exploiting modification direction with two steganographic images,” Multimedia Tools and Applications, vol. 74, no. 15, pp. 5861–5872, 2014. [Google Scholar]
27. J. -Y. Hsiao, A. -C. Pan and P. -Y. Chen, “An adaptive reversible data hiding scheme using dual stego-image,” International Journal of Computers and Applications, vol. 43, no. 3, pp. 282–291, 2018. [Google Scholar]
28. C. -F. Lee, C. -Y. Weng and K. -C. Chen, “An efficient reversible data hiding with reduplicated exploiting modification direction using image interpolation and edge detection,” Multimedia Tools and Applications, vol. 76, no. 7, pp. 9993–10016, 2016. [Google Scholar]
29. J. -Y. Lin, Y. Chen, C. -C. Chang and Y. -C. Hu, “Dual-image-based reversible data hiding scheme with integrity verification using exploiting modification direction,” Multimedia Tools and Applications, vol. 78, no. 18, pp. 25855–25872, 2019. [Google Scholar]
30. X. Chen and W. Guo, “Reversible data hiding scheme based on fully exploiting the orientation combinations of dual stego-images,” International Journal of Network Security, vol. 22, no. 1, pp. 126–135, 2020. [Google Scholar]
31. Y. Chen, J. Lin, C. C. Chang and Y. C. Hu, “Reversibly hiding data using dual images scheme based on EMD data hiding method,” International Journal of Computational Science and Engineering, vol. 21, no. 4, pp. 583, 2020. [Google Scholar]
32. J. -Y. Lin, J. -H. Horng, C. -C. Chang and Y. -H. Li, “Asymmetric orientation combination for reversible and authenticable data hiding of dual stego-images,” Symmetry, vol. 14, no. 4, pp. 819, 2022. [Google Scholar]
33. S. Subburam, S. Selvakumar and S. Geetha, “High performance reversible data hiding scheme through multilevel histogram modification in lifting integer wavelet transform,” Multimedia Tools and Applications, vol. 77, no. 6, pp. 7071–7095, 2017. [Google Scholar]
34. S. Kim, X. Qu, V. Sachnev and H. J. Kim, “Skewed histogram shifting for reversible data hiding using a pair of extreme predictions,” IEEE Transactions on Circuits and Systems for Video Technology, vol. 29, no. 11, pp. 3236–3246, 2019. [Google Scholar]
35. L. -C. Huang, S. -F. Chiou and M. -S. Hwang, “A reversible data hiding based on histogram shifting of prediction errors for two-tier medical images,” Informatica, vol. 32, no. 1, pp. 69–84, 2021. [Google Scholar]
36. J. -Y. Lin, Y. Liu and C. -C. Chang, “A real-time dual-image-based reversible data hiding scheme using turtle shells,” Journal of Real-Time Image Processing, vol. 16, no. 3, pp. 673–684, 2019. [Google Scholar]
37. H. Yu, R. Wang, L. Dong, D. Yan, Y. Gong et al., “A high-capacity reversible data hiding scheme using dual-channel audio,” IEEE Access, vol. 8, pp. 162271–162278, 2020. [Google Scholar]
38. X. Chen and C. Hong, “An efficient dual-image reversible data hiding scheme based on exploiting modification direction,” Journal of Information Security and Applications, vol. 58, pp. 102702, 2021. [Google Scholar]
39. X. -Z. Xie and C. -C. Chang, “Hiding data in dual images based on turtle shell matrix with high embedding capacity and reversibility,” Multimedia Tools and Applications, vol. 80, no. 30, pp. 36567–36584, 2021. [Google Scholar]
40. S. Chen and C. -C. Chang, “Reversible data hiding based on three shadow images using rhombus magic matrix,” Journal of Visual Communication and Image Representation, vol. 76, pp. 103064, 2021. [Google Scholar]
41. J. -Y. Lin, J. -H. Horng and C. -C. Chang, “A reversible and authenticable secret sharing scheme using dual images,” Multimedia Tools and Applications, vol. 81, no. 13, pp. 17527–17545, 2022. [Google Scholar]
42. C. -C. Chang, G. -D. Su, C. -C. Lin and Y. -H. Li, “Position-aware guided hiding data scheme with reversibility and adaptivity for dual images,” Symmetry, vol. 14, no. 3, pp. 509, 2022. [Google Scholar]
43. Y. Liu and C. C. Chang, “A turtle shell-based visual secret sharing scheme with reversibility and authentication,” Multimedia Tools and Applications, vol. 19, no. 3, pp. 25295–25310, 2018. [Google Scholar]
44. A. Shamir and M. -S. Hwang, “How to share a secret,” Communications of the ACM, vol. 22, no. 11, pp. 612–613, 1979. [Google Scholar]
45. D. R. Setiadi, “PSNR vs. SSIM: Imperceptibility quality assessment for image steganography,” Multimedia Tools and Applications, vol. 80, no. 6, pp. 8423–8444, 2020. [Google Scholar]
Cite This Article
 Copyright © 2023 The Author(s). Published by Tech Science Press.
Copyright © 2023 The Author(s). Published by Tech Science Press.This work is licensed under a Creative Commons Attribution 4.0 International License , which permits unrestricted use, distribution, and reproduction in any medium, provided the original work is properly cited.


 Submit a Paper
Submit a Paper Propose a Special lssue
Propose a Special lssue View Full Text
View Full Text Download PDF
Download PDF Downloads
Downloads
 Citation Tools
Citation Tools