 Open Access
Open Access
ARTICLE
Attribute-Based Authentication Scheme from Partial Encryption for Lattice with Short Key
School of Information Engineering, Jingdezhen Ceramic University, Jingdezhen, 333403, China
* Corresponding Author: Shuhua Wang. Email:
Computers, Materials & Continua 2023, 75(1), 67-80. https://doi.org/10.32604/cmc.2023.035337
Received 17 August 2022; Accepted 13 October 2022; Issue published 06 February 2023
Abstract
Wireless network is the basis of the Internet of things and the intelligent vehicle Internet. Due to the complexity of the Internet of things and intelligent vehicle Internet environment, the nodes of the Internet of things and the intelligent vehicle Internet are more vulnerable to malicious destruction and attacks. Most of the proposed authentication and key agreement protocols for wireless networks are based on traditional cryptosystems such as large integer decomposition and elliptic curves. With the rapid development of quantum computing, these authentication protocols based on traditional cryptography will be more and more threatened, so it is necessary to design some authentication and key agreement protocols that can resist quantum attacks. In this paper, an anti-quantum authentication scheme for wireless networks based on lattice cryptosystem is constructed. In the attribute-based authentication scheme, the length of the authenticated public-private key pair depends on the maximum order and complexity of the formula in the algorithm. In the attribute-based authentication scheme, there is a certain correlation between the authenticated data and the attribute value of the user in the scheme. We show that the attribute-based authentication scheme gives an attribute-based with smaller public-private key pairs. The security of the attribute-based authentication scheme is based on the sub-exponential hard problem of the LWE (Learning With Errors). The Q-poly made by the adversary in the scheme, and our attribute-based authentication scheme guarantees that private data about user attributes and ciphertext cannot be obtained by malicious attackers.Keywords
There are many attributes-based authentication schemes proposed in protocols related to wireless networks and information security, such as references [1–4]. However, most of the proposed authentication and key agreement protocols for wireless networks are based on traditional cryptosystems such as large integer decomposition and elliptic curves. With the rapid development of quantum computing, these authentication protocols based on traditional cryptography will be more and more threatened. These attribute-based authentication schemes will not be secure in the post-quantum era. At present, the widely used anti-quantum cryptosystem is an anti-quantum algorithm based on lattice cryptosystem and coding-related problems. With the rapid development of quantum computer, the anti-quantum algorithm based on lattice cryptosystem will attract more researchers. For the related security protocols based on lattice cryptosystem [5–7], the anti-quantum performance of the protocols is based on the related difficult problems such as the shortest vector and learning with errors in a lattice-based cryptosystem. The authentication and key agreement protocol based on lattice cryptosystem can also resist various threats brought by quantum computers in the post-quantum era, and can ensure the security of wireless networks, which is a hot issue in anti-quantum algorithms [8–15]. The difficult problem of a lattice-based cryptosystem is that it plays a key role in information security in wireless networks in the future quantum era [16–18]. Based on the difficult problems of lattice-based cryptosystem, many fully homomorphic encryption schemes [19–24] and public-key encryption schemes [25–27] are presented.
In the past decade, many schemes of anti-quantum authentication and security protocols based on the difficult problems of lattice cryptosystem have been proposed [28–34]. In 2016, Bansarkhani et al. [5]. Based on lattice cryptosystem, a new anti-quantum authentication signature protocol is proposed, and the authentication protocol is applied to block chain security. In 2018, Behina et al. [35]. From the difficult problem of lattice-based cryptosystem, an effective key searchable security authentication scheme is proposed, the key searchable security authentication scheme uses a new strategy to search keywords such as keys. In 2019, Fukumitsu et al. [7]. Based on the difficulty of lattice cryptosystem, a secure and efficient authentication signature protocol is proposed, which is proved to be secure in the random model, which is a three-round scheme with the public key aggregation with the security proof, A group signatures scheme without NIZK (Non-Interactive Zero Knowledge) base on lattice was designed [36], but this group signatures scheme requires a combination of attribute-based encryption and signatures. Ma et al. [10]. Based on lattice cipher, an effective anti-quantum authentication signature protocol for blockchains is proposed, which is a four-round scheme with the key aggregation and Tso et al. [12]. An effective anti-quantum blind signature protocol based on attributes from lattices is proposed, which is the attribute-based signature. In 2020, Kansal et al. [9]. Based on the difficulty of lattice cryptosystem, an effective anti-quantum authentication signature scheme is proposed, which is a round optimal secure authentication scheme. In 2020, Sun et al. [37]. Proposed an effective anti-quantum lattice cipher group signature authentication protocol based on zero knowledge proofs. Canard et al. [38]. Proposed an anti-quantum group signature authentication protocol with secure data fixed length based on lattice cryptosystem. The protocol is proved to be secure under the standard model. In 2020, Doss et al. [39]. Proposed a secure and effective meme optimization method based on lattice public key cryptosystem, which is used to transmit important medical privacy information in block chain and the internet of things that can resist the key exchange. The application of the attribute-based authentication scheme also includes hierarchical electronic voting for multiple regions, robust reversible audio watermarking for telemedicine and privacy protection, and much more [40]. At present, many scholars are studying anti-quantum secure signature and authentication protocols based on lattice cryptosystem, such as the quantum-resistant batch verifiable data privacy security authentication protocol of VANETs (Vehicular Ad Hoc Networks) using lattice [8].
Hence, it is of great significance to construct a secure authentication protocol based on the difficult problem of lattice cryptosystem. In this paper, an effective attribute-based authentication protocol is proposed, which supports full homomorphic encryption of information. The length of the public-private key pair in this protocol is short, and the corresponding computational overhead is reduced.
The general definition in these lattices can be expressed as: randomly select a prime number
Definition 1 (
where
Connection with lattices. Suppose
There is a C-bounded Gaussian distribution
Lemma 1 ([31])
Randomly select the matrixes C in
Suppose
Lemma 2 ([31])
Randomly select the matrixes C in
Suppose
Lemma 3 [29]
1.
2.
3 Attribute-Based Authentication Scheme
Based on the partial hidden predicate encryption protocol based on the difficult problem of lattice cryptosystem, a new attribute-based anti-quantum authentication protocol (
In the section, it is proposed that the public key, common parameter, and master key of all users are generated by the algorithm
1. Randomly select some important parameters
2. Choose some important random matrices:
3. Sampling matrix with algorithm
4. The algorithm outputs some parameters and the most important core key of the scheme:
The private key of the scheme for the user is generated using those public parameters generated above, where
1. Compute the parameter
2. Sample a random subset
3. Sampling the key with algorithm
4. Let
Take Alice and Bob as an example, Alice and Bob are necessary to authenticate each other before finally generating a symmetric key for communication, which is jointly generated by the Alice private attributes
1. Sample a Gaussian parameter
2. Choose a security hash function
3. Compute the message
4. Select a parameter b, and set
5. Random sampling t matrices
6. Random sampling l matrices
7. Finally, out the encrypted ciphertext
1. Based on these parameters
2. Compute:
3. If
Then set
4. Compute the partial communication key associated with Alice:
The partial communication key associated with the Bob negotiation process is as follows: Alice uses the hash function
1. Sample a Gaussian parameter
2. Compute the message
3. Select a parameter
4. Random sampling t matrices
5. Random sampling l matrices
6. Choose a hash algorithm
7. Compute the symmetric communication key with Bob:
8. Out the ciphertext
1. Using
2. Compute
3. Round computes each datum of
Then set
4. Compute the partial communication key associated with Bob:
5. Compute the symmetric communication key with Bob:
Finally, the whole attribute-based authentication Scheme is over, and Alice and Bob can communicate securely with the authentication symmetric key
The correctness of Alice to Bob’s partial authentication in the
If
Compute
If the first
Otherwise, if
Therefore, with overwhelming probability from the No.1 to No.
The security of Bob to Alice’s other partial authentication in the
So, the symmetric communication key of Bob and Alice is:
The specific process of the security of Alice to Bob’s partial authentication in the
Proof. First, we describe the auxiliary evaluation algorithms of the proof.
1. Sampling matrix with algorithm
2. Random sample l parameters
3. Random sample t parameters
4. Random choose some subsets
5. Sample some random matrices
6. Sample the private key
7. Output necessary public key of our scheme as
And the most important core key of our scheme as
1. Sample a Gaussian parameter
2. Select a parameter
3. Compute the
4. Random sampling t matrices
5. Final output the encrypted ciphertext
1. Compute the key corresponding to
2. We know that
1) A
Let
Therefore that:
Return
2) The
Now, we describe a sim algorithm, which claims that the result of the real algorithm is indistinguishable from game simulation through the following hybrids.
(1). The first case that satisfies indistinguishable situation is the following two simulation algorithm:
Algorithm 0: The realistic simulation.
Algorithm 1: The simulation
(2). The second case that satisfies indistinguishable situation is the following two simulation algorithm:
Algorithm 1: This algorithm is the same as algorithm 1 in the first case.
Algorithm 2: The game simulation
(3). The third case that satisfies indistinguishable situation is the following two simulation algorithm:
Algorithm 2: This algorithm is the same as algorithm 2 in the second case.
Algorithm 3: The game simulation
(4). The fourth case that satisfies indistinguishable situation is the following two simulation algorithm:
Algorithm 3: This algorithm is the same as algorithm 3 in the third case.
Algorithm 4: The algorithm
(5). The fifth case that satisfy indistinguishable situation is the following two simulation algorithm:
Algorithm 4: This algorithm is the same as algorithm 4 in the fourth case.
Algorithm 5: The game simulation
(6). The sixth case that satisfy indistinguishable situation is the following two ism algorithm:
Algorithm 5: This algorithm is the same as algorithm 5 in the fifth case.
Algorithm 6: The game simulation
(7). The seventh case that satisfy indistinguishable situation is the following two ism algorithm:
Algorithm 6: This algorithm is the same as algorithm 6 in the sixth case.
Algorithm 7: The game simulation
A detailed proof of indistinguishability (1) –(7) is provided in the references [23,29]. The security of Bob with Alice's other partial authentication in the
Next, we compare our attribute-based authentication scheme with other related secret key schemes [6,13,14,22]. We mainly focus on the computational costs, storage overhead, and several security properties.
As depicted in Table 1, we compare the storage overhead and other related secret key schemes. The public key parameter' size is
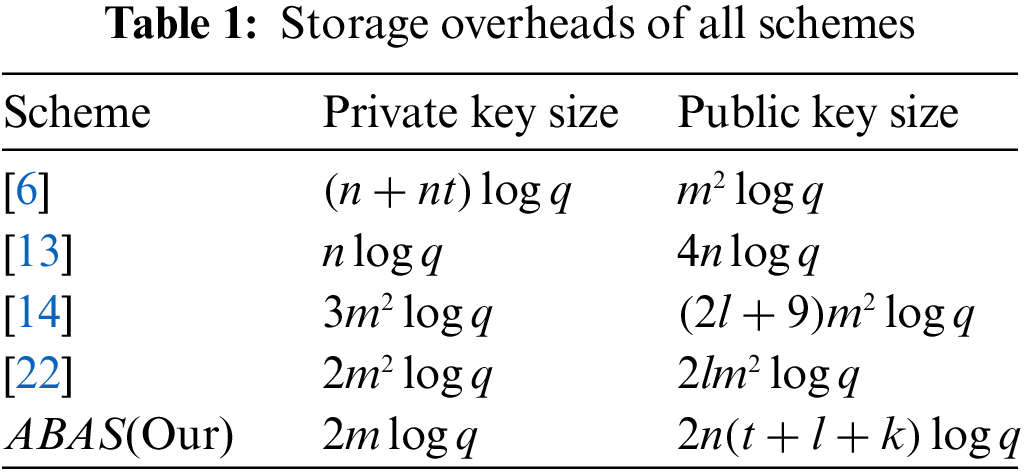
In Table 2, the SM represents the standard model, and the SCPA represents the selective chosen plaintext attack, the NTRU represents the number theory research unit, and the CVP represents the closest vector problem. We compare the security properties and other related secret key schemes, according to the Table 1, Li et al. [13] is more effectivie than our attribute-based authentication scheme over lattice in terms of computational storage, which is based on NTRU lattice, so it lacks provable security. Gentry et al. [22], Wang et al. [14] and Brakerski et al. [6] Schemes are slightly weaker than our attribute-based authentication scheme over lattice in terms of computational complexity and storage. Moreover, our scheme is based on partially hiding predicate encryption, so the key size is also efficient, and our scheme is provably security of
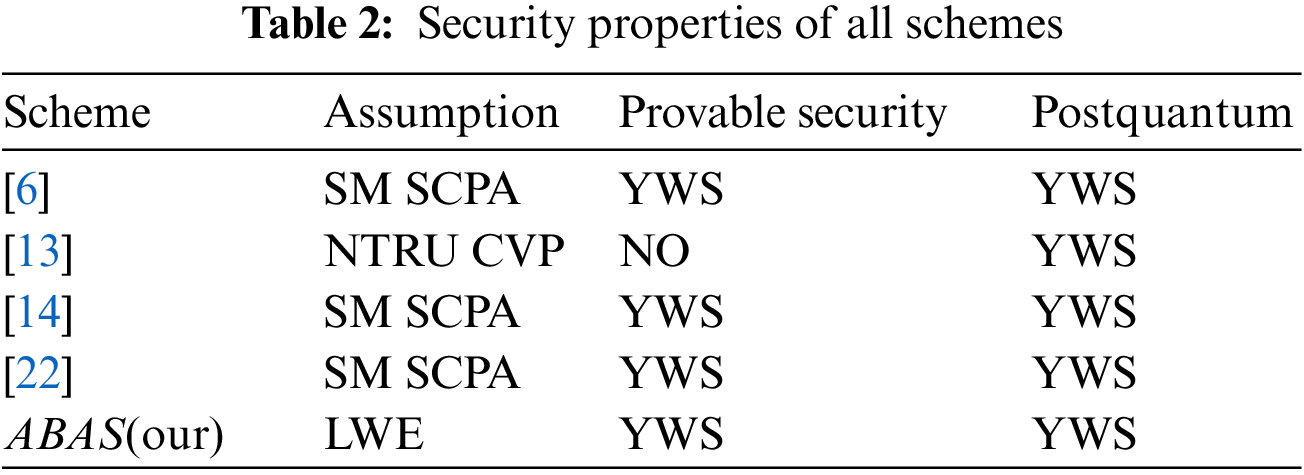
Based on the
Funding Statement: This work was supported by the Special Project for Scientific and Technological Cooperation of Jiangxi Province [no. 20212BDH80021].
Conflicts of Interest: The authors declare that they have no conflicts of interest to report regarding the present study.
References
1. M. Azees, P. Vijayakumar and L. J. Deboarh, “EAAP: Efficient anonymous authentication with conditional privacy-preserving scheme for vehicular ad hoc networks,” IEEE Transactions on Intelligent Transportation Systems, vol. 18, no. 9, pp. 2467–2476, 2017. [Google Scholar]
2. J. Zhang, J. Cui, H. Zhong, Z. Chen and L. Liu, “PA-CRT: Chinese remainder theorem based conditional privacy-preserving authentication scheme in vehicular ad-hoc networks,” IEEE Transactions on Dependable and Secure Computing, vol. 18, no. 2, pp. 722–735, 2021. [Google Scholar]
3. H. Li, F. Guo, L. Wang, J. Wang, B. Wang et al., “A blockchain-based public auditing protocol with self-certified public keys for cloud data,” Security and Communication Networks, vol. 2021, no. 1, pp. 6623639–6623649, 2021. [Google Scholar]
4. A. Yang, X. Tan, J. Baek and D. S. Wong, “A new ADS-B authentication framework based on efficient hierarchical identity-based signature with batch verification,” IEEE Transactions on Services Computing, vol. 10, no. 2, pp. 165–175, 2017. [Google Scholar]
5. R. El Bansarkhani and J. Sturm, “An efficient lattice-based multi signature scheme with applications to bitcoins,” in Proc. of the Int. Conf. on Cryptology and Network Security (CANS 2016), vol. 10052 of LNCS, Milan, Italy, pp. 140–155, 2016. [Google Scholar]
6. Z. Brakerski, D. Cash D, R. Tsabary and H. wee, “Targeted homomorphic attribute-based encryption,” in Proc. of Theory of Cryptography (TCC 2016), Beijing, China, pp. 330–360, 2016. [Google Scholar]
7. M. Fukumitsu and S. Hasegawa, “A lattice-based provably secure multi signature scheme in quantum random oracle model,” in Proc. of the 14th Int. Conf. on Provable and Practical Security (ProvSec 2020), Singapore, Singapore, pp. 45–64, 2020. [Google Scholar]
8. S. Mukherjee, D. S. Gupta and G. Biswas, “An efficient and batch verifiable conditional privacy-preserving authentication scheme for VANETs using lattice,” Computing, vol. 101, no. 12, pp. 1763–1788, 2019. [Google Scholar]
9. M. Kansal and R. Dutta, “Round optimal secure multi signature schemes from lattice with public key aggregation and signature compression,” in Proc. of the 12th Int. Conf. on Cryptology in Africa (AFRICACRYPT 2020), Cairo, Egypt, pp. 281–300, 2020. [Google Scholar]
10. C. Ma and M. Jiang, “Practical lattice-based multi signature schemes for blockchains,” IEEE Access, vol. 7, pp. 179765–179778, 2019. [Google Scholar]
11. P. Dupont, J. Hesse, D. Pointcheval, L. Reyzin and S. Yakoubov, “Fuzzy password-authenticated key exchange,” in Proc. of the 37th Annual Int. Conf. on the Theory & Applications of Cryptographic Techniques (EUROCRYPT 2018), Tel Aviv, Israel, pp. 393–424, 2018. [Google Scholar]
12. R. Tso, Z. Liu and Y. Tseng, “Identity-based blind multi signature from lattices,” IEEE Access, vol. 7, pp. 182916–182923, 2019. [Google Scholar]
13. D. Li, H. Chen, C. Zhong, T. Li and F. Wang, “A new self-certified signature scheme based on ntrusing for smart mobile communications,” Wireless Personal Communications, vol. 96, no. 3, pp. 4263–4278, 2017. [Google Scholar]
14. G. Wang, Z. Liu Z and D. Gu, “Ciphertext policy attribute-based encryption for circuits from LWE assumption,” in Proc. of the 21st Int. Conf. on Information and Communications Security (ICICS 2019), Beijing, China, pp. 278–396, 2019. [Google Scholar]
15. N. Tahat, A. K. Alomari, O. M. Al-Hazaimeh and M. F. Al-Jamal, “An efficient self-certified multi-proxy signature scheme based on elliptic curve discrete logarithm problem,” Journal of Discrete Mathematical Sciences and Cryptography, vol. 23, no. 4, pp. 935–948, 2020. [Google Scholar]
16. O. Regev, “On lattices, learning with errors, random linear codes, and cryptography,” in Proc. of the 37th Annual ACM Symp. on Theory of Computing, Association for Computing Machinery (STOC 2005), New York, NY, USA, pp. 84–93, 2005. [Google Scholar]
17. O. Regev, “On lattices, learning with errors, random linear codes, and cryptography,” Journal of the ACM, vol. 56, no. 6, pp. 1–122, 2009. [Google Scholar]
18. C. Peikert, “Public-key cryptosystems from the worst-case shortest vector problem,” in Proc. of the 41th Annual ACM Symp. on Theory of Computing, Association for Computing Machinery (STOC 2009), Bethesda, MD, USA, pp. 333–342, 2009. [Google Scholar]
19. Z. Brakerski, A. Langlois, C. Peikert, O. Regev and D. Stehlé, “Classical hardness of learning with errors,” in Proc. of the 45th Annual ACM Symp. on Theory of Computing, Association for Computing Machinery (STOC 2013), New York, NY, USA, pp. 575–584, 2013. [Google Scholar]
20. Z. Brakerski, C. Gentry and V. Vaikuntanathan, “(Leveled) fully homomorphic encryption without bootstrapping,” in Proc. of the 3rd Innovations in Theoretical Computer Science Conf. (ITCS 2012), Cambridge, MA, USA, pp. 309–325, 2012. [Google Scholar]
21. L. Ducas and D. M. Fhew, “Bootstrapping homomorphic encryption in less than a second,” in Proc. of the 34th Annual Int. Conf. on the Theory & Applications of Cryptographic Techniques (EUROCRYPT 2015), Sofia, Bulgaria, pp. 617–640, 2015. [Google Scholar]
22. C. Gentry, A. Sahai and B. Waters, “Homomorphic encryption from learning with errors: Conceptually-simpler, asymptotically-faster, attribute-based,” in Proc. of the 33th Annual Int. Conf. on Cryptology (CRYPTO 2013), Santa Barbara, California, USA, pp. 75–92, 2013. [Google Scholar]
23. S. Agrawal, “Stronger security for reusable garbled circuits, general definitions and attacks,” in Proc. of the 37th Annual Int. Conf. on Cryptology (CRYPTO 2017), Santa Barbara, CA, USA, pp. 3–35, 2017. [Google Scholar]
24. R. Steinfeld, A. Sakzad and R. K. Zhao, “Practical MP-LWE-based encryption balancing security-risk versus efficiency,” Designs Codes and Cryptography, vol. 87, pp. 2847–2884, 2019. [Google Scholar]
25. A. Lombardi, V. Vaikuntanathan and T. D. Vuong, “Lattice trapdoors and IBE from middle-product LWE,” in Proc. of the Theory of Cryptography Conf. (TCC 2019), Nuremberg, Germany, pp. 24–54, 2019. [Google Scholar]
26. A. Pellet-Mary, G. Hanrot and D. Stehlé, “Approx-SVP in ideal lattices with pre-processing,” in Proc. of the 38th Annual Int. Conf. on the Theory & Applications of Cryptographic Techniques (EUROCRYPT 2019), Darmstadt, Germany, pp. 685–716, 2019. [Google Scholar]
27. S. Gorbunov, V. Vaikuntanathan and H. Wee, “Functional encryption with bounded collusions via multi-party computation,” in Proc. of the 32nd Annual Int. Conf. on Cryptology (CRYPTO 2012), Santa Barbara, CA, USA, pp. 162–179, 2012. [Google Scholar]
28. Y. Ishai and H. Wee, “Partial garbling schemes and their applications,” in Proc. of the Int. Colloquium on Automata, Languages, and Programming (ICALP 2014), Copenhagen, Denmark, pp. 650–662, 2014. [Google Scholar]
29. S. Gorbunov, V. Vaikuntanathan and H. Wee, “Predicate encryption for circuits from lwe,” in Proc. of the 35th Annual Int. Conf. on Cryptology (CRYPTO 2015), Santa Barbara, CA, USA, pp. 503–523, 2015. [Google Scholar]
30. C. Gentry, C. Peikert and V. Vaikuntanathan, “Trapdoors for hard lattices and new cryptographic constructions,” in Proc. of the 40th Annual ACM Symp. on Theory of Computing, Association for Computing Machinery (STOC 2008), Victoria (BCCanada, pp. 197–206, 2008. [Google Scholar]
31. S. Agrawal, D. Boneh and X. Boyen, “Efficient lattice (H)IBE in the standard model,” in Proc. of the 29th Annual Int. Conf. on the Theory & Applications of Cryptographic Techniques (EUROCRYPT 2010), French Riviera, pp. 553–572, 2010. [Google Scholar]
32. D. Cash, D. Hofheinz, E. Kiltz and C. Peikert, “Bonsai trees, or how to delegate a lattice basis,” Journal of Cryptology, vol. 25, no. 4, pp. 601–639, 2012. [Google Scholar]
33. C. Baum, I. Damgård, V. Lyubashevsky, S. Oechsner and C. Peikert, “More efficient commitments from structured lattice assumptions,” in Proc. of the 11th Conf. on Security and Cryptography for Networks (SCN 2018), Amalfi, Italy, pp. 614–629, 2018. [Google Scholar]
34. V. Lyubashevsky and G. Neven, “One-shot verifiable encryption from lattices,” in Proc. of the 36th Annual Int. Conf. on the Theory & Applications of Cryptographic Techniques (EUROCRYPT 2017), Paris, France, pp. 293–323, 2017. [Google Scholar]
35. R. Behnia, M. O. Ozmen and A. A. Yavuz, “Lattice-based public key searchable encryption from experimental perspectives,” IEEE Transactions on Dependable Secure Compute, vol. 17, no. 6, pp. 1269–1282, 2018. [Google Scholar]
36. S. Katsumata and S. Y amada, “Group signatures without NIZK: From lattices,” in Proc. of the 38th Annual Int. Conf. on the Theory & Applications of Cryptographic Techniques (EUROCRYPT 2019), Darmstadt, Germany, pp. 312–344, 2019. [Google Scholar]
37. Y. Sun and Y. Liu, “A lattice-based fully dynamic group signature scheme without NIZK,” in Proc. of the Information Security and Cryptology (INSCYPT 2020), Guangzhou, China, pp. 359–367, 2020. [Google Scholar]
38. S. Canard, A. Georgescu, G. Kaim, A. R. Langlois and J. Traoré, “Constant-size lattice-based group signature with forward security in the standard model,” in Proc. of the 14th Int. Conf. on Provable and Practical Security (ProvSec 2020), Singapore, Singapore, pp. 24–44, 2020. [Google Scholar]
39. S. Doss, J. Paranthaman, S. Gopalakrishnan, A. Duraisamy, S. Pal et al., “Memetic optimization with cryptographic encryption for secure medical data transmission in IoT-based distributed systems,” Computers, Materials & Continua, vol. 64, no. 2, pp. 1577–1594, 2021. [Google Scholar]
40. X. Zhang, X. Sun, X. Sun, W. Sun and S. K. Jha, “Robust reversible audio watermarking scheme for telemedicine and privacy protection,” Computers, Materials & Continua, vol. 71, no. 2, pp. 3035–3050, 2022. [Google Scholar]
Cite This Article
 Copyright © 2023 The Author(s). Published by Tech Science Press.
Copyright © 2023 The Author(s). Published by Tech Science Press.This work is licensed under a Creative Commons Attribution 4.0 International License , which permits unrestricted use, distribution, and reproduction in any medium, provided the original work is properly cited.


 Submit a Paper
Submit a Paper Propose a Special lssue
Propose a Special lssue View Full Text
View Full Text Download PDF
Download PDF Downloads
Downloads
 Citation Tools
Citation Tools