 Open Access
Open Access
ARTICLE
Device Discovery in D2D Communication: Scenarios and Challenges
1 COMSATS University, Islamabad, 45550, Pakistan
2 Yeungnam University, Gyeongsan-si, 38541, Korea
* Corresponding Author: Sung Won Kim. Email:
Computers, Materials & Continua 2023, 75(1), 1735-1750. https://doi.org/10.32604/cmc.2023.034468
Received 18 July 2022; Accepted 28 September 2022; Issue published 06 February 2023
Abstract
Device to Device (D2D) communication is expected to be an essential part of 5G cellular networks. D2D communication enables close-proximity devices to establish a direct communication session. D2D communication offers many advantages, such as reduced latency, high data rates, range extension, and cellular offloading. The first step to establishing a D2D session is device discovery; an efficient device discovery will lead to efficient D2D communication. D2D device further needs to manage its mode of communication, perform resource allocation, manage its interference and most importantly control its power to improve the battery life of the device. This work has developed six distinct scenarios in which D2D communication can be initiated, considering their merits, demerits, limitations, and optimization parameters. D2D communication procedures for the considered scenarios have been formulated, based upon the signal flow, containing device discovery, resource allocation, and session teardown. Finally, latency for each scenario has been evaluated, based on propagation and processing delays.Keywords
Long-Term Evolution (LTE)-Advanced and Worldwide Interoperability for Microwave Access (WiMAX) are 4th Generation (4G) cellular systems with very good performance of Medium Access Control (MAC) and physical layers [1]. However, 4G telecom operators are still finding it hard to cope with exacting mobile users. Since new data-intensive applications, like proximity-aware services, video streaming and multimedia file sharing are increasing the load on the system day by day. The intended applications for the next decade are three-dimensional (3D) holography and telepresence with bandwidth requirements up to 1 Tbps. These bandwidth demands can’t be met with currently available communication systems like 4G LTE providing around 50 Mbps [2]. So, the trend of looking for more bandwidth and increased user data will continue in the 5th Generation (5G) cellular network and to meet these data demands, unconventional or out-of-box thinking is required. The Device to Device (D2D) communication system is one of the solutions that can enable 5G to support this high data rate [3–6]. In D2D communication, devices communicate with each other either with or without network control. The main advantage of D2D communication is that the data traffic is routed between devices directly, which offloads the base station (Evolved Node B (eNB) in LTE), reduces the latency, increases throughput and enables higher data rates. This ultimately results in improved system capacity and end-user satisfaction [7–9]. It has many applications, like proximity services, multicasting, content distribution, video dissemination, machine-to-machine (M2M) communication, video dissemination, gaming and so on [10,11].
To support D2D communication within a cellular communication system, further investigation is required on several D2D domains. If a device has to communicate with other devices through D2D communication, the first step would be to discover the nearby D2D devices, this is done through device discovery [12]. In the second step, devices choose the mode of communication. Whether the D2D-enabled users choose to communicate through a cellular network or opt for D2D communication, is the mode selection phase [13,14]. After the mode has been selected, the system allocates communication resources to the devices involved in D2D communication, i.e., the resource allocation phase [2,15]. Power management is another hot domain of research as power efficiency is always important for limited-power mobile nodes [2,16]. In D2D communication, the D2D users can use the resources of the cellular system if they are allowed to or they can opt for the Industrial Scientific and Medical (ISM) band as well [17,18]. To have a successful D2D communication scenario, the system will have to manage the interference among the D2D and cellular users [19,20], as resources are shared in the two domains, D2D and cellular. Determining the pricing model in this new paradigm [3], where D2D devices are bypassing the base station during communication, is an interesting domain to explore. Tempting a device to involve in the D2D communication, particularly when relaying, would be very challenging as various tradeoffs would be involved [2,21,22]. Other than these fundamental communication issues, achieving secure D2D communication is also an open research domain [23]. Likewise, ensuring the privacy of users is even more challenging as conflicting interests are generated in this new paradigm [24]. Fig. 1 summarizes the D2D communication domains that can be further explored and potential optimization parameters which can be used to improve the performance of each domain.

Figure 1: D2D communication domains and potential optimization parameters
If a device opts to establish a D2D communication session with its neighbouring device, first it needs to scan its surrounding for potential D2D enabled devices; i.e., device discovery. An efficient device discovery scheme can be achieved by optimizing energy consumption, reducing latency, minimizing unnecessary messages, yet ensuring accuracy privacy and security. The discovery process can be further divided into two steps. The first step is to discover the presence of potential D2D devices and the second step is to identify these devices [25,26].
Authors in [27] have studied the device discovery from the network perspective, according to their proposed method, the device discovery can be lightly or tightly controlled by a base station. In the case of lightly control signaling load decreases so as the control over the user but in the case of tightly control it provides better control over its users but increases the signaling load on the network. In [28], the authors have proposed a solution for Third Generation Partnership Project (3GPP) LTE-based system to share its spectrum resources with D2D users. The authors claim that they have increased the spectrum and energy efficiency of the traditional cellular system by allowing cellular devices and D2D pairs to share spectrum resources. In [29], the authors have proposed a beacon-based proximity device discovery scheme. The authors believed they have achieved energy efficiency by exploiting the spatial correlation of wireless channels. The results of the simulation indicate that D2D devices can be discovered by utilizing very low power but there is a tradeoff between energy efficiency and detection accuracy. According to [30], device discovery methods can follow the restricted device discovery or open device discovery. To maintain the privacy of the user, restricted device discovery mode is used, in this mode, the user’s device can’t be discovered without the explicit prior permission of the user. If the user chooses to be in open device discovery mode, his device can be discovered by all the devices available in close proximity at that time.
A simple device discovery algorithm has been proposed in [31], which uses power vectors to discover closed proximity devices. The authors believed that by considering the time-variant channel, they have achieved close to zero probability of false detection. As their proposed algorithm is network assisted, it will increase the load on the network and this solution is only for in-band D2D communication. The authors in [32] have proposed a social-aware device discovery scheme, which utilizes social information to improve the system performance by enhancing the data delivery ratio and peer discovery ratio. An effective device discovery technique, which works with the assistance of an LTE network in order to enable D2D communication in LTE has been presented in [33]. The results show that for a specific discovery interval, the protocol provides a very high probability of device discovery, but the evaluation performed by the authors is of a very preliminary level.
The vehicular network and Unmanned Aerial Networks (UAVs) are the important domains of D2D communication. The authors in [34] propose a new D2D discovery scheme that collaborates with vehicular users, which effectively reduces the utilization of valuable resources in the LTE-A network. The proposed scheme can offload some D2D discovery traffic and processing involving vehicular drivers and passengers to Vehicular Ad-hoc Networks. The sounding reference signal (SRS) channel is used in [35] to discover the nearby D2D devices for LTE users. The D2D devices are discovered with the help of uplink transmission of its neighbor cellular users with known channel statistics of neighboring devices. Statistical methods are used for simultaneous D2D device discovery and channel estimation. This estimated channel can later be utilized for D2D communication. Several device discovery methods are proposed and their performance is evaluated with practical LTE parameters. In [36] A comprehensive review of several device discovery schemes is presented. Wireless Fidelity (Wi-Fi) Ad-Hoc, Infrared Data Association (IrDA), Bluetooth, Request-based, Signature-based, Packet-based and network-assisted device discovery schemes are reviewed and classified in this work. They have compared packet-based and signature-based discovery schemes in terms of accuracy (missed and wrong detection), and the results suggest that the signature-based scheme outperforms the packet-based scheme.
In this paper, we aim to understand the impact of different D2D communication domains and their effect on successfully establishing a D2D communication session. The most of existing literature focuses on some single problem or tries to optimize two or three parameters. We aim to first understand the complete D2D in depth. We start by discussing in detail, the D2D device discovery scenarios, optimization parameters and challenges. D2D communication procedures for different scenarios are formulated mainly focusing on device discovery, resource allocation and session teardown.
We have developed six different D2D communication scenarios in which D2D communication can be established. Starting from the simple D2D communication where the devices don’t have network coverage. The second scenario is where more than one D2D pair is establishing a D2D communication session without network support. The rest of the four scenarios summarizes the different possibilities of D2D communication with network support. To the best of our knowledge, it is the first time in literature that different D2D communication scenarios are developed and discussed based on different optimization parameters. Latencies of different scenarios are presented in this work. We start by anticipating the various scenarios in which D2D can be useful and discuss device discovery procedures for these considered cases. We have also evaluated the D2D delays in discovery, resource allocation and session termination, with due consideration for signal transmission and processing delays in the network.
4 Device Discovery Schemes Under Different Scenarios with their Applications
There are many scenarios in which a device can prefer a D2D communication mode. For each of the scenarios, there are different device discovery requirements and challenges. Some of the most imminent scenarios are shown in Fig. 2, each having diverse requirements, tradeoffs and challenges [2,36–38].
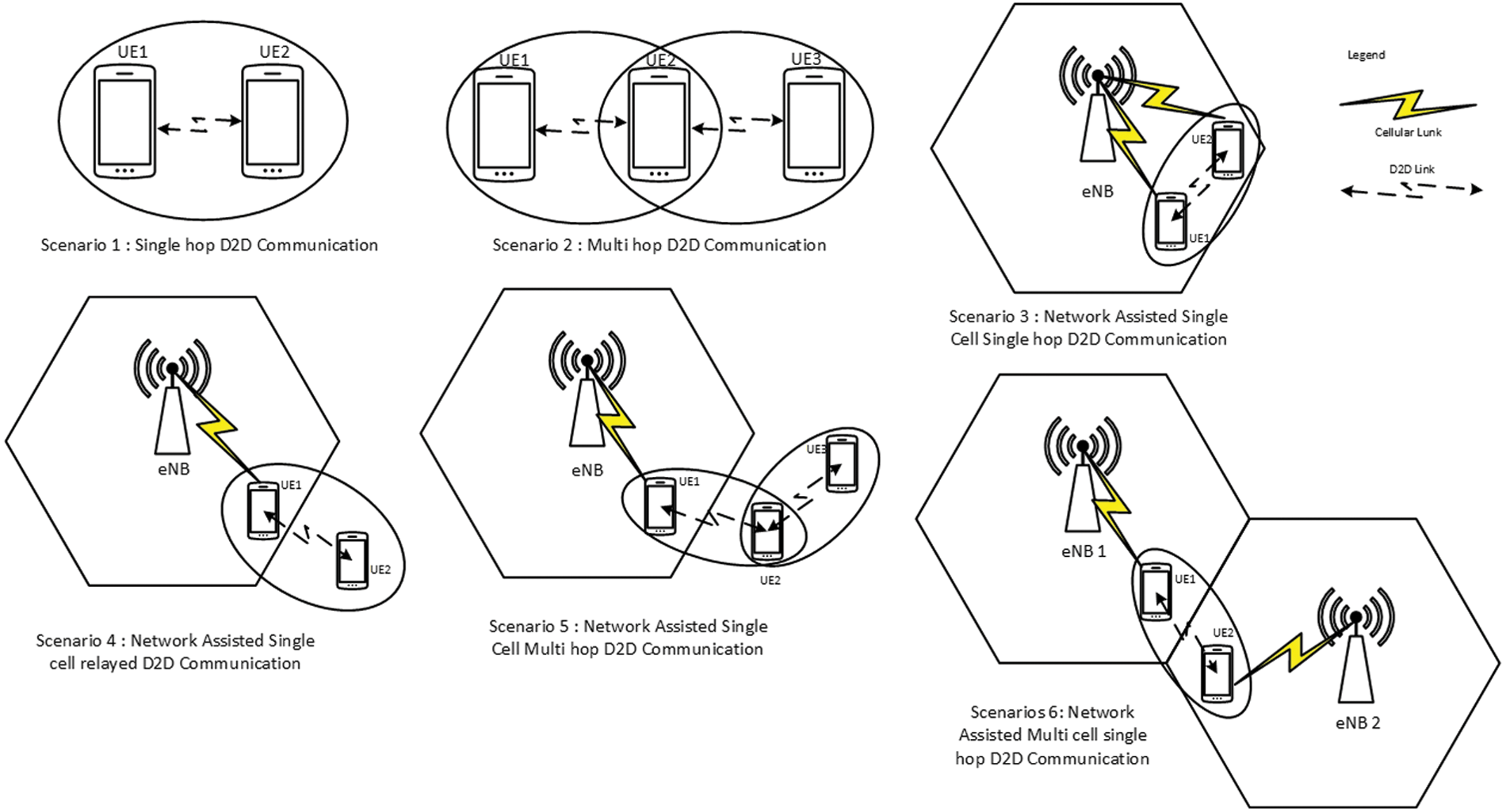
Figure 2: D2D communication scenarios
In Fig. 2 scenario 1, two out of cellular coverage devices are in close proximity and can establish a D2D session. The onus of device discovery, in this case, lies with the devices, as there is no network availability. The D2D devices can discover each other autonomously, using an ad-hoc network discovery scheme, such as beacon-based. The two devices communicating directly without any relay will achieve a high data rate with low latency. However, direct communication in this scenario puts an extra signaling burden of discovery and resource allocation on the devices, which have limited power. To make a communication session secure and ensure privacy there arises a need to add a layer of security and privacy, however, it should be light enough to have the minimum load on the battery consumption, as again the responsibility lies with the communicating devices. Natural disasters, battlefield, surveillance, social networking, gaming and low coverage areas are possible applications of this scenario [3,24]. Scenario 2 is an extended version of scenario 1, where the user equipment (UE) 2 acts as a relay device between UE1 and UE3, which are not in direct communication range. The relaying function comes with many advantages, like improved coverage and a higher probability of successful discovery. However, there are also tradeoffs involved, like extra signaling required for the discovery and resource allocation through relaying node, which increases latencies and increases battery power consumption [21]. The relay node can only be tempted to involve in the session by tempting it through some credit and ensuring minimum overhead and signaling load on it. Also, a node can work as a relay only when its transceiver is free and not engaged in its communication session. So, it may necessitate the handover or session termination whenever the relaying device initiates its communication session or when it moves to a new position where it is unable to relay between the two communicating nodes. A specially designed multi-transceiver handset can handle more than one communication session at a time. The addition of multiple transceivers in handsets requires hardware level changes in cellular handsets, this will affect the cost, size, and battery consumption of cellular handsets.
Fig. 2 scenario 3, is an example of network-assisted D2D communication. It shows two devices in the cellular coverage area, they are also in close proximity to each other and intend to establish a D2D session. In this case, the base station will assist the users in establishing a D2D connection i.e., device discovery, resource allocation and session teardown. The involvement of the base station offers many advantages, like robustness, security, better discovery and low battery consumption as the base station will be performing most of the signaling. The discovery latency of network-assisted systems is higher compared to pure D2D communication systems. As D2D communication is so lucrative for mobile users there can be many cellular users preferring the D2D mode of communication, which can burden the base station with the extra signaling, associated with the D2D communication. So, in this scenario, the D2D algorithm should be scalable and must not undermine the gain achieved through cellular offloading. Close proximity users, especially machines such as surveillance cameras and smart homes could be the possible use cases of this scenario where there are many devices and sensors which need to communicate to each other after periodic time intervals for reporting to the base station.
Fig. 2 scenarios 4 & 5 are the hybrid of both cellular and ad-hoc networks, out of coverage area UE is trying to reach the base station for communication. The link between UE and the base station can contain more than one relay nodes, which acts as mediators or range extenders. This is a special case where the relay node is connected to the network from one side and the D2D node on the other side, in the one hand this increases the range of the network but on the other hand, it also adds complexity and introduces delays. Single and multi-hop relaying is an essential part of 4G [21,39], The mobile relay node is an unreliable entity due to its limited resources, so the D2D communication algorithm should be optimized to save resources, like energy and time. On each hop, the inefficiency of the algorithm will increase energy consumption and delay. The base station can make sure security and privacy on its end but on the D2D side, it will be solely on the users to handle security and privacy. The use cases can be low coverage areas of the network like a basement of a building or a tunnel, remote areas like camping sites in mountains, rivers and high-speed vehicles like busses or trains can be possible examples where a specially designed relay node can be installed on a vehicle to provide uninterrupted communication service to passengers on board. There can be one big implementation on stadiums, shopping malls, parks, or playgrounds, where there is a big gathering of communication users in close proximity for a specific time. The organizers can share the time schedule of events, the layout of the place, special events and even video highlights or live streaming of events to users. Imagine sitting in a soccer stadium and you will not miss a single goal because you will get a video of each goal scored from multiple camera views on your handset. The base station will only send that video to a few users in close proximity and it will be relayed to each user from its close proximity user and that specific content will be distributed without even causing a burden on the base station.
Fig. 2 scenario 6 is network-assisted multi-cell single-hop D2D communication. Both users are in close proximity but are in the coverage area of two different base stations. This case can occur on the edge of a base station because normally coverage areas of base stations overlap each other. In this case, the base stations can direct the devices to start a D2D session instead of traditional communication and create room in the network for other cellular users. From the user’s perspective, it does not increase the coverage but improves the quality of communication for the user. As both devices have the assistance of a base station, they can discover each other with minimum signaling which will increase the energy efficiency of users and offload the base station.
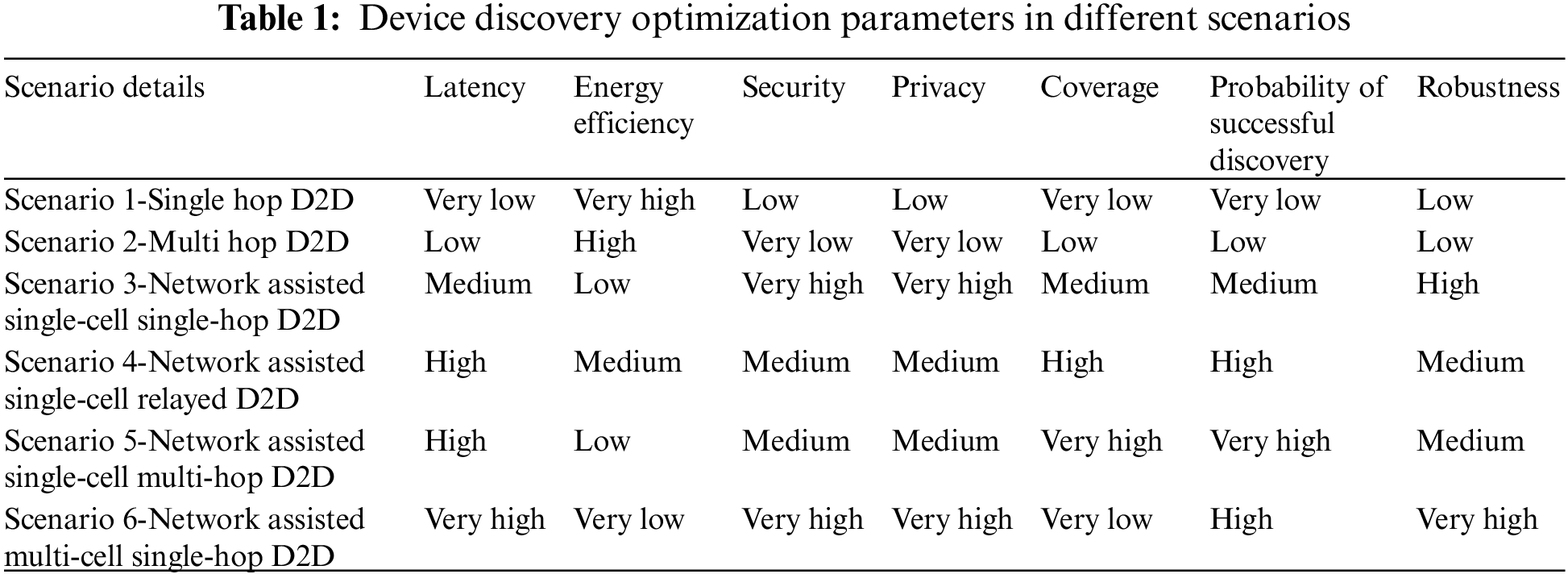
From Table 1 it can be concluded that there is a tradeoff between utilizing network-assisted device discovery and adhoc-based device discovery. Network-assisted device discovery schemes has the support of network which means they can provide better latency, security, privacy, robustness and probability of successful discovery. Adhoc-based schemes can be used for covering the area where there is either low or no coverage with high energy efficiency. The combination of both network assisted and adhoc based device discovery scheme will provide superior performance as they reap off the benefits of both schemes. To make D2D communication more robust and advantageous it must include both network-assisted and adhoc-based device discovery schemes.
5 D2D Communication Procedures
The signal flow routines are developed in this section, there are six D2D communication scenarios as shown in Fig. 2. For simplicity, the wireless channel characteristics are considered ideal and it is assumed that each time the device tries to communicate with another device it is successful in doing so. The whole process is divided into three phases: i) device discovery, ii) resource allocation and iii) session teardown.
In Fig. 3 scenario 1 is the simplest case of D2D communication where two users are in close proximity and intends to start a direct communication session. The UE1 will scan possible D2D candidates and discover UE2 by sending a discovery request message to UE2. The UE2 will calculate the distance based on the received signal strength and check if D2D communication is possible. The UE2 reply with a discovery response message in which it will approve the UE1 for D2D communication. Authentication is an optional function that can also be performed in this stage based on the quality of service (QoS) requirements of UE. In Fig. 3 scenario 2 is the representation of multi-hop D2D communication, there is an addition of one relay node, which can be further extended to multiple relay nodes. The relay node forwards the discovery message to the intended user. This will cause some processing and propagation delay in the signal, but it will enable UE1 to communicate to UE3, which was not in the D2D communication range otherwise. The range of D2D communication systems which is working autonomously without the support of a base station is extended by implementing a multi-hop D2D communication system.

Figure 3: Signal flow diagram scenario 1 and scenario 2
In Fig. 4 scenario 3 is simplest network assisted D2D communication scenario, the D2D devices will discover the neighbouring devices with the help of the base station. The network support can ease off a lot of battery and computational burden from D2D devices. The D2D devices will send the neighbour discovery request to the base station and the base station will probe UE2. The base station also calculates the distance between UE1 and UE2. After successful completion of distance calculation and also checking the availability of UE2, the base station will inform the UE1 about successful neighbour discovery. The application server (AS) will help the base station to assign resources requested by UE. The base station will keep track of the session and inform AS in case of session termination.
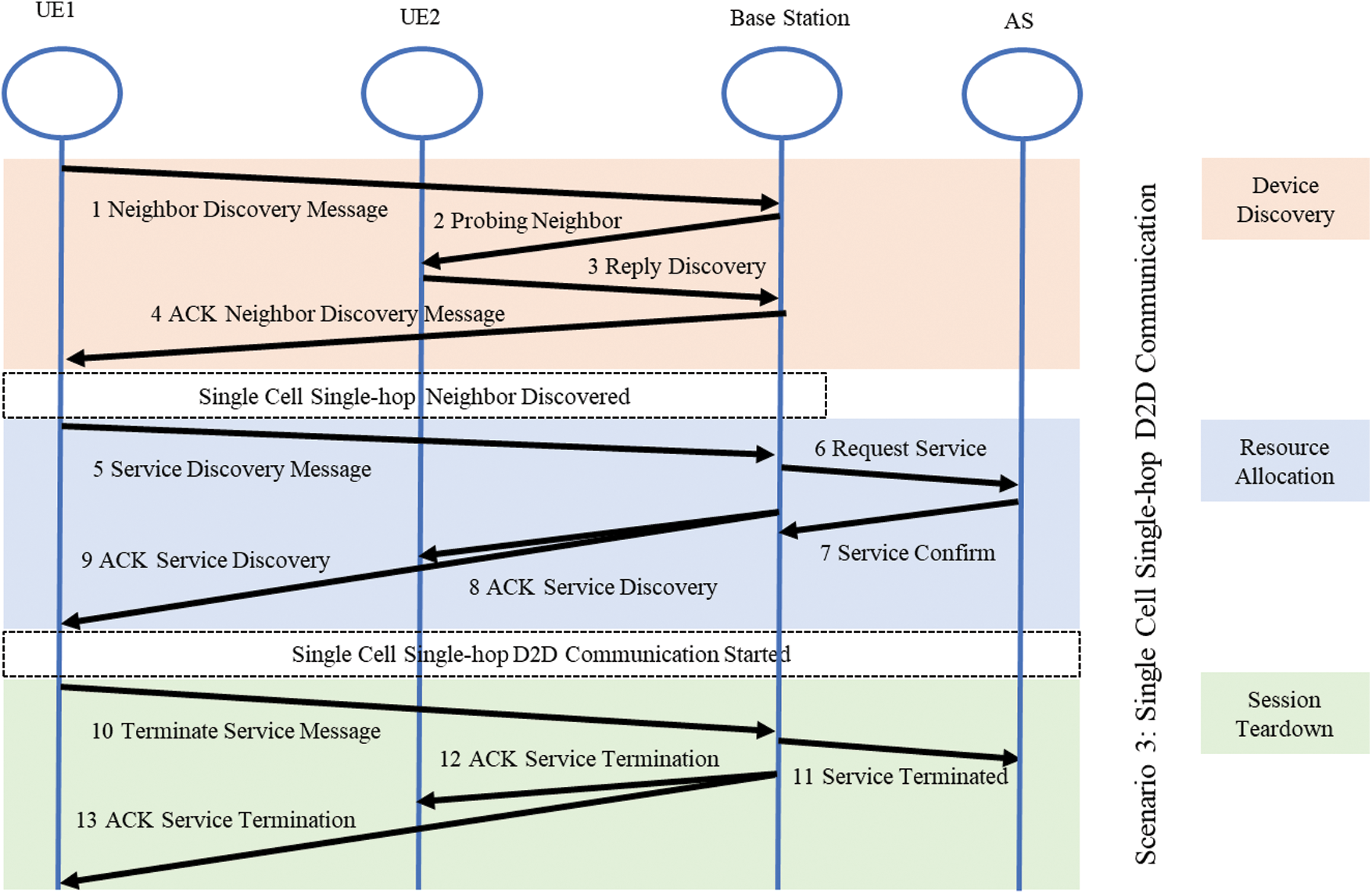
Figure 4: Signal flow diagram scenario 3
In Fig. 5 scenario 4 the relay assisted D2D communication session is established, there is a relay device UE2 between UE1 and the base station. UE1 intends to start a communication session with a device that is somewhere in the network but not in its close proximity. So UE2 is assisting UE1 to establish a session with the base station. The UE1 will send the discovery request message to UE2 and UE2 will calculate its distance from UE1 and forward this information to the base station. The base station will find the receiver device and reply to UE2 about the successful discovery of the device. UE2 will forward that information to UE1 and neighbour discovery will complete here. The base station in this case will increase its coverage with the help of D2D communication. The UE1 can be a user out of the coverage area, or inside a coverage area with a signal strength below a threshold. These below-threshold areas are called blind spots and they can be inside a tunnel or basement of a building [11,40].
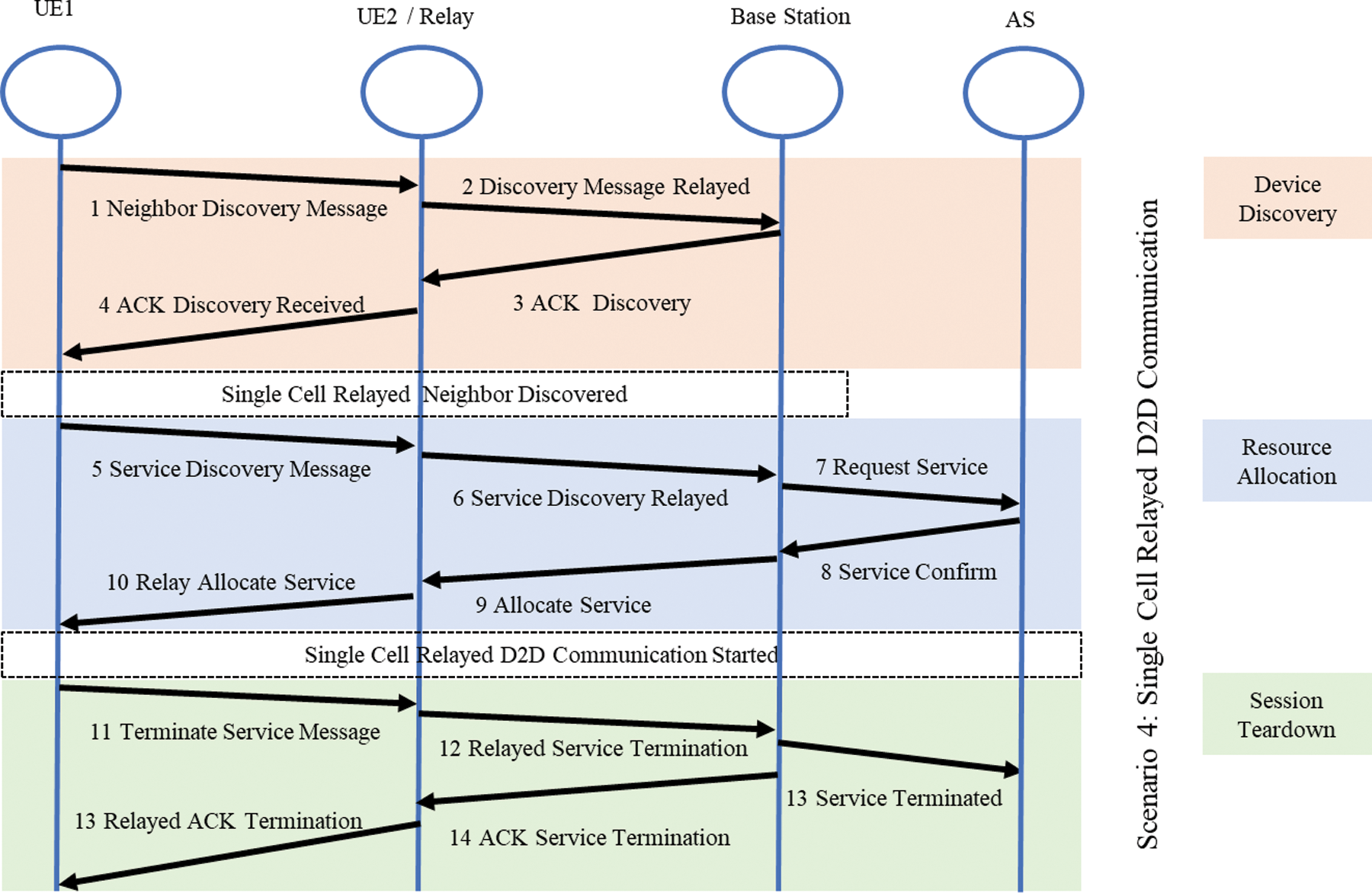
Figure 5: Signal flow diagram scenario 4
The blind spots inside the coverage area can also occur due to the mobility of the users [41]. The channel characteristics also have a major role in developing blind spots. The 5G/beyond 5G research is moving towards the utilization of higher frequency bands. Millimetre-wave communication has a great potential to increase the capacity of 5G [42,43]. Similarly, a lot of effort is put to achieve communication in the tera-hertz band which has ample potential to improve the performance of D2D and beyond 5G communication systems [44,45]. The higher frequencies are more prone to propagation losses like reflection, absorption and scattering [46]. This will seriously damage the performance of the systems operating on those frequencies. D2D communication can realize the proximity communication as developed in scenario 4 and help mitigate blind spots inside the coverage area.
In Fig. 6 scenario 5, multi-hop relaying is introduced which incorporates two relays instead of one. The coverage of the system is further increased. There is a trade-off of increased signalling load and higher latency, in order to achieve successful relaying. Scenario 5 is used for vehicular and IoT nodes as well as for the limited number of data packets. In the situation where the relaying data is too high or the devices require QoS for real-time services, the multi-hop relaying is not going to be a feasible solution due to its increased overhead.
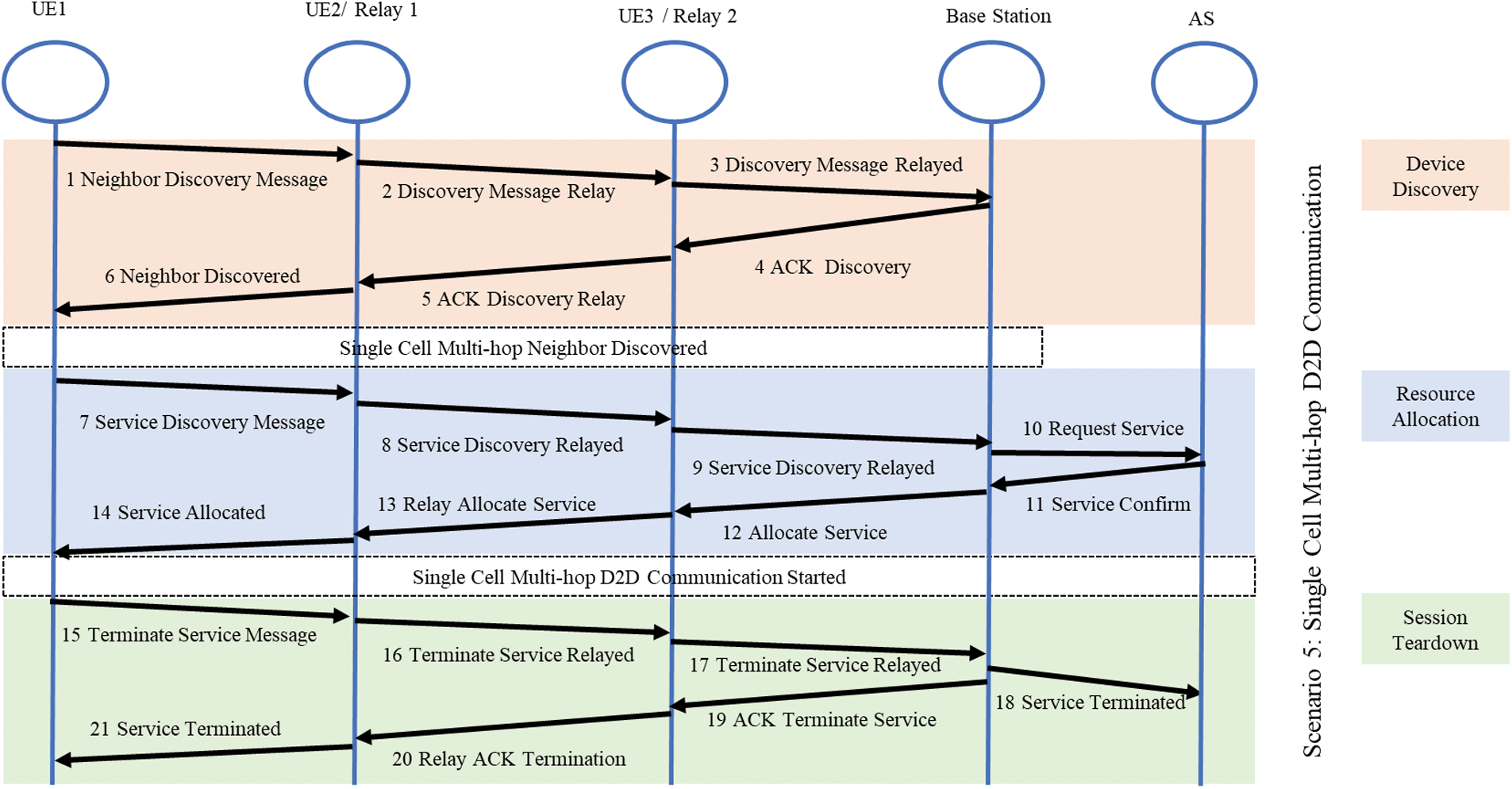
Figure 6: Signal flow diagram scenario 5
Fig. 7 shows the multi-cell single-hop D2D signalling which is scenario 6. It is the situation where the two users are connected to two different base stations. These D2D users are also in close proximity and initiating a D2D session. For the currently deployed 4G-LTE or 3G systems with large coverage areas such a scenario is highly unlikely, but for the 5G and beyond 5G systems with small cells the probability is such scenarios is very high [47–49]. UE1 will send a discovery request to base station 1 and base station 1 will calculate its distance from UE1 and forward that information to base station 2. Base station 2 will probe UE2 and calculate its distance from UE2. The distance between UE1 and UE2 is also calculated to ensure both are in close proximity. The confirmation reply message is sent to base station 1. Base station 1 informs the UE1 about the confirmation of device discovery. Furthermore, the resources are allocated to both the UEs with the consent of base station 1 and base station 2. The AS will assist the base stations in resource allocation for the D2D users. The resources are assigned to UEs based on their requirements to ensure their QoS.
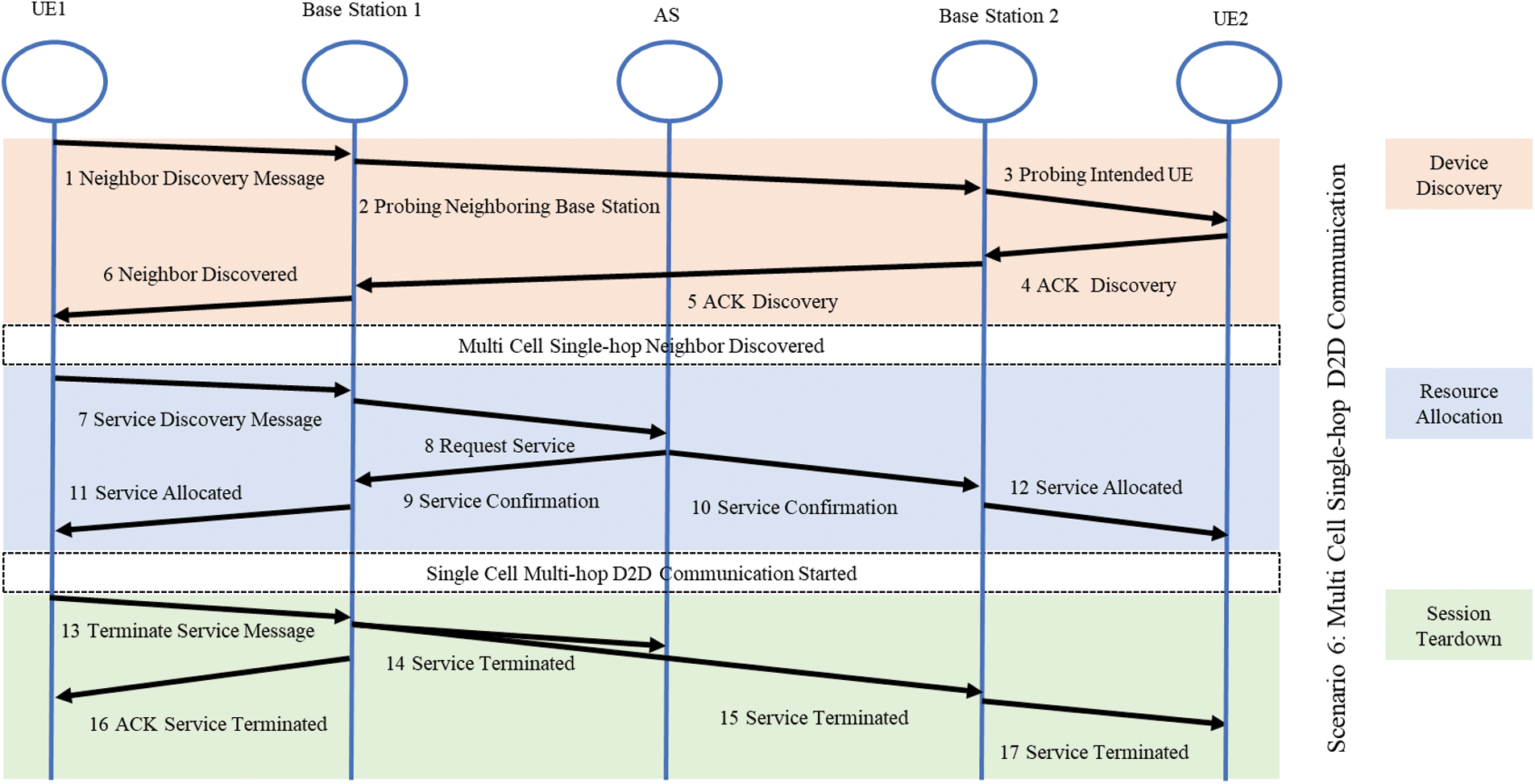
Figure 7: Signal flow diagram scenario 6
The final phase of all the developed scenarios is session teardown, where the devices inform the network or other devices about the completion of the communication session and abrogation of assigned resources. The session teardown can be initiated by any of the UEs. The base station is informed about the terminate service message. The base station informs the AS and any other base station involved in the communication session. In the case of scenario 1 and scenario 2, where only D2D users are involved in the communication devices directly inform each other about session teardown.
Scenarios 1 and 2 are the basic representation of adhoc-based device discovery schemes. Scenarios 3 and 6 are network-assisted. Scenarios 4 and 5 are the hybrid solution of both network-assisted and adhoc-based schemes. We have tried to minimize the signalling to make the procedure simple and energy efficient. Whenever the UE tries to contact the other UE or base station, we have assumed that the other side is ready to receive the signal and will successfully receive the signal. In the next section, we have calculated the delays of these different scenarios.
The overall D2D communication latency from idle UE to session teardown of six scenarios is calculated in this section using MATLAB. The file size consider in this work is 5 Kb and the Maximum Transmission Unit (MTU) is considered 1500 bytes based on LTE MTU size. Table 2 summarizes different types of delays, their symbols and values. The propagation delay and processing delay at UE, base station (BS) and application server (AS) are calculated based on values given in [50–53]. D2D UEs are considered a maximum distance of 1000 m apart with a propagation delay of 4.003 ms. the channel characteristics in propagation delay are considered ideal.
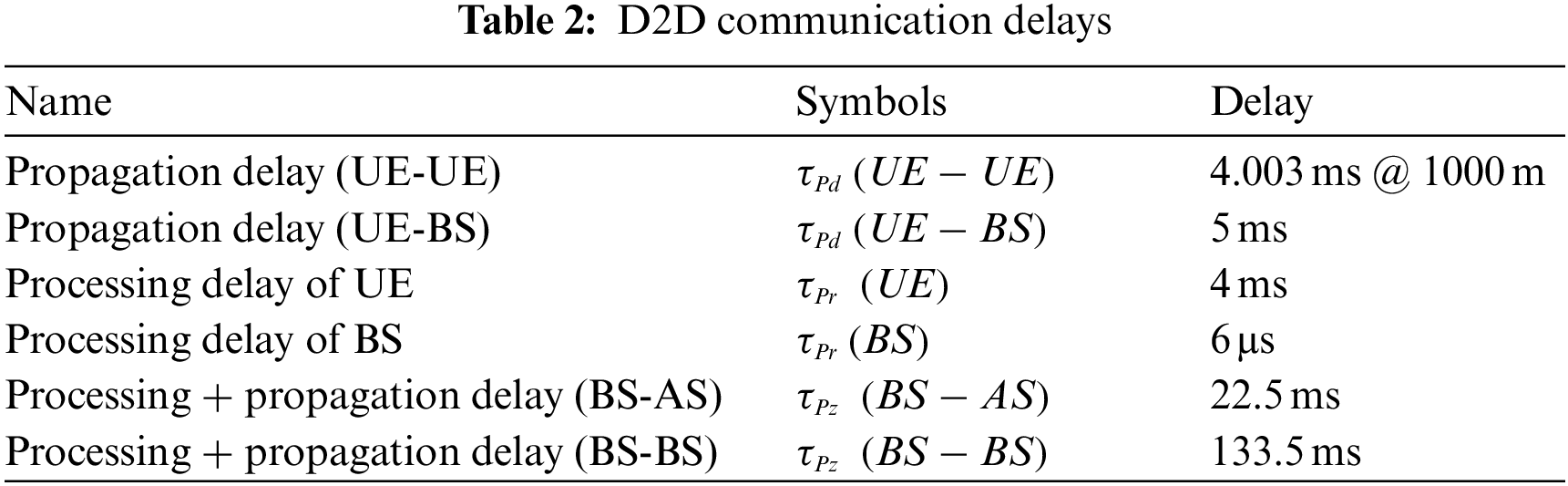
LTE supports cell sizes ranging from tens of metres for femtocells to picocells to 100 km for macrocells. In the lower frequency bands that will be used in rural areas, 5 km cell size is optimal, 30 km has reasonable performance, and cell sizes up to 100 km are supported with acceptable performance. Higher frequency bands, such as 2.6 GHz in the EU, are used in cities and urban areas to support high-speed mobile broadband. In this case, cell sizes could be as small as 1 km. We used a 5 km cell size for the delay calculation. The total delay offered in each scenario can be mathematically expressed with the help of the following expression.
The values of n depend on the number of messages. If a message is not used in some specific scenario, the value is zero. Delay analysis of different scenarios is shown in Fig. 8. The values of delay are calculated on the bases of device discovery time, resource allocation time and session teardown time.
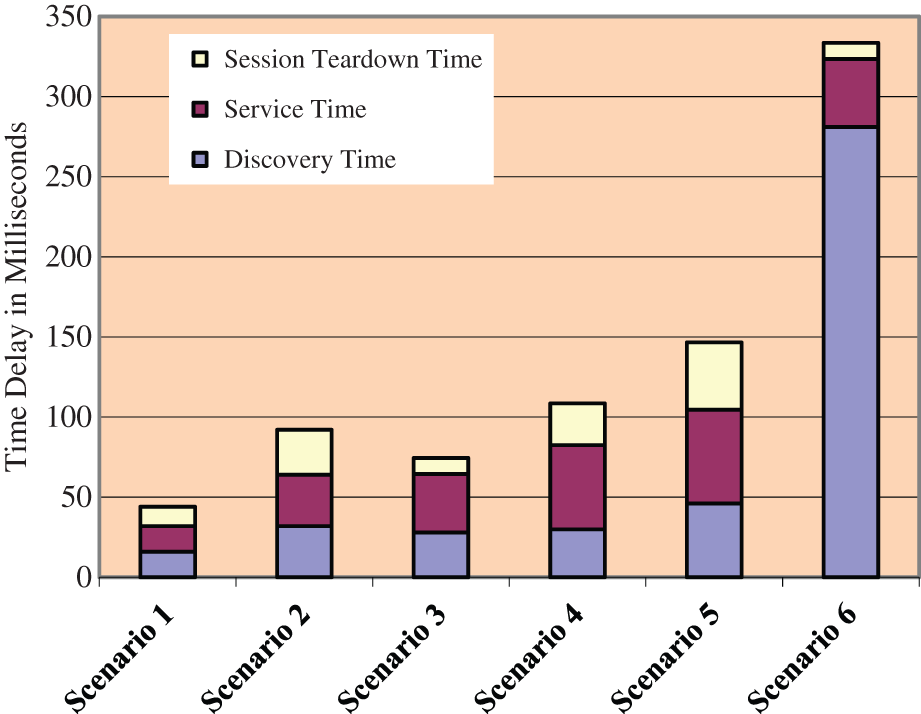
Figure 8: Latency of D2D communication scenarios
Scenario 1 takes the least time because two devices are in close proximity, scenario 2 takes a little more time because a relay station is introduced between two devices. Scenario 3 is network-assisted so its response time is better than scenario 2 but not better than scenario 1. Scenarios 3 and 4 merge adhoc and cellular networks so their delay increases but they can increase network coverage. The delay of scenario 6 is at maximum because two base stations are involved. The most delay-causing factor is device discovery and in that discovery network assistance for two devices connected to different base stations requires the consent of both base stations which is causing this delay. This delay can be reduced significantly by allowing the devices to discover each other independently and if they can discover each other, they can request BS for the assignment of resources.
In this work, we have developed various D2D communication scenarios and summarized their behavior according to several optimization parameters. The D2D communication life cycle, divided into device discovery, resource allocation and session teardown are elaborated with the help of a signal flow diagram. The latency of each phase has been evaluated for the considered scenarios. D2D devices can either directly discover and establish the communication session or with the assistance of a cellular network. The direct method is fast but as the number of relay stations increases, it consumes more energy and compromises security and privacy. Network assisted method offers better security, privacy and energy efficiency but has larger delays. The relay devices in D2D communication are used to provide multi-hop D2D communication, they offer an advantage of range extension, but at the cost of increased delays and further compromised privacy and security. These relays could be static or mobile and in the case of mobile relays handoff, energy efficiency and dynamic resource allocation are open research challenges.
To the best of our knowledge, this is the first work to accommodate all possible scenarios in a single discovery procedure. D2D communication can be applied to IoT and Vehicular networks as part of 5G/6G networks. The proximity communication has a great potential to enable 5G/6G communication networks to high low latency for the Ultra Reliable Low Latency Communication (URLLC) applications. The future cellular networks are expected to be robust and highly intelligent so machine learning-based D2D solutions can also be further explored. The architecture proposed in this work can further be extended to formulate SIP based scheme for D2D, Vehicular, and IoT devices.
Acknowledgement: Dr. Adeel Iqbal and Dr. Ali Nauman has equal contribution. Dr. Adeel Iqbal has wrote the original manuscript. Dr. Latif Hussain and Dr. Ali Nauman has revised the manuscript in several meetings and refined the manuscript. Dr. Riaz Hussain and Dr. Sung Won Kim has supervised this research work. Whereas, Dr. Sana Shuja, and Dr. Ali Khaqan have reviewed the manuscript and helped in improving the paper quality.
Funding Statement: This research was supported in part by Basic Science Research Program through the National Research Foundation of Korea (NRF) funded by the Ministry of Education (NRF-2021R1A6A1A03039493) and in part by the NRF grant funded by the Korea government (MSIT) (NRF-2022R1A2C1004401).
Conflicts of Interest: The authors declare that they have no conflicts of interest to report regarding the present study.
References
1. A. Murkaz, R. Hussain, J. Ahmed, M. Adil, B. Omoniwa et al., “An intra–inter-cell device-to-device communication scheme to enhance 5G network throughput with delay modeling,” Telecommunication Systems, vol. 69, pp. 1–15, 2018. [Google Scholar]
2. L. Wei, R. Q. Hu, Y. Qian and G. Wu, “Enable device-to-device communications underlaying cellular networks: Challenges and research aspects,” IEEE Communications Magazine, vol. 52, no. 6, pp. 90–96, 2014. [Google Scholar]
3. A. Asadi, Q. Wang and V. Mancuso, “A survey on device-to-device communication in cellular networks,” IEEE Communications Surveys & Tutorials, vol. 16, no. 4, pp. 1801–1819, 2014. [Google Scholar]
4. P. Gandotra and R. K. Jha, “Device-to-device communication in cellular networks: A survey,” Journal of Network and Computer Applications, vol. 71, pp. 99–117, 2016. [Google Scholar]
5. A. Nauman, T. N. Nguyen, Y. A. Qadri, Z. Nain, K. Cengiz et al., “Artificial intelligence in beyond 5G and 6G reliable communications,” IEEE Internet of Things Magazine, vol. 5, no. 1, pp. 73–78, 2022. [Google Scholar]
6. A. Nauman, M. A. Jamshed, Y. A. Qadri, R. Ali and S. W. Kim, “Reliability optimization in narrowband device-to-device communication for 5G and beyond-5G networks,” IEEE Access, vol. 9, pp. 157584–157596, 2021. [Google Scholar]
7. A. Iqbal, R. Hussain, A. Shakeel, I. L. Khan, M. A. Javed et al., “Enhanced spectrum access for QoS provisioning in multi-class cognitive D2D communication system,” IEEE Access, vol. 9, pp. 33608–33624, 2021. [Google Scholar]
8. A. Nauman, M. A. Jamshed, Y. Ahmad, R. Ali, Y. B. Zikria et al., “An intelligent deterministic D2D communication in narrow-band internet of things,” in 15th Int. Wireless Communications & Mobile Computing Conf. (IWCMC), Tangier, Morocco, IEEE, pp. 2111–2115, 2019. [Google Scholar]
9. A. Nauman, M. A. Jamshed, R. Ali, K. Cengiz and S. W. Kim, “Reinforcement learning-enabled intelligent device-to-device (I-D2D) communication in narrowband internet of things (NB-IoT),” Computer Communications, vol. 176, pp. 13–22, 2021. [Google Scholar]
10. L. Chen and K. Bian, “Neighbor discovery in mobile sensing applications: A comprehensive survey,” Ad Hoc Networks, vol. 48, pp. 38–52, 2016. [Google Scholar]
11. A. Iqbal, M. Rahim, R. Hussain, A. Noorwali, M. Z. Khan et al., “cDERSA: Cognitive D2D enabled relay selection algorithm to mitigate blind-spots in 5G cellular networks,” IEEE Access, vol. 9, pp. 89972–89988, 2021. [Google Scholar]
12. K. Doppler, C. B. Ribeiro and J. Kneckt, “Advances in D2D communications: Energy efficient service and device discovery radio,” in Wireless Communication, Vehicular Technology, Information Theory and Aerospace & Electronic Systems Technology (Wireless VITAE2011 2nd Int. Conf. on, Chennai, India, IEEE, pp. 1–6, 2011. [Google Scholar]
13. C. N. Ververidis and G. C. Polyzos, “Service discovery for mobile Ad Hoc networks: A survey of issues and techniques,” IEEE Communications Surveys & Tutorials, vol. 10, no. 3, pp. 30–45, 2008. [Google Scholar]
14. S. Hakola, T. Chen, J. Lehtomaki and T. Koskela, “Device-to-device (D2D) communication in cellular network-performance analysis of optimum and practical communication mode selection,” in Wireless Communications and Networking Conf. (WCNC2010 IEEE, Sydney, Australia, IEEE, pp. 1–6, 2010. [Google Scholar]
15. L. Lei, Y. Kuang, X. Shen, C. Lin and Z. Zhong, “Resource control in network assisted device-to-device communications: Solutions and challenges,” IEEE Communications Magazine, vol. 52, no. 6, pp. 108–117, 2014. [Google Scholar]
16. Y. V. L. d. Melo, R. L. Batista, T. F. Maciel, C. F. M. e. Silva, J. M. B. d. Silva et al., “Power control with variable target SINR for D2D communications underlying cellular networks,” in European Wireless 2014; 20th European Wireless Conf., Barcelona, Spain, pp. 1–6, 2014. [Google Scholar]
17. B. Zhou, S. Ma, J. Xu and Z. Li, “Group-wise channel sensing and resource pre-allocation for LTE D2D on ISM band,” in IEEE Wireless Communications and Networking Conf. (WCNC), Shanghai, China, IEEE, pp. 118–122, 2013. [Google Scholar]
18. H. H. Hussein, H. A. Elsayed, A. El-kader and M. Sherine, “Intensive benchmarking of D2D communication over 5G cellular networks: Prototype, integrated features, challenges, and main applications,” Wireless Networks, vol. 26, no. 5, pp. 3183–3202, 2020. [Google Scholar]
19. S. Wang, R. Hou, K. S. Lui, H. Li and J. Li, “A novel interference management scheme in underlay D2D communication,” in Vehicular Technology Conf. (VTC Fall2015 IEEE 82nd, Boston, USA, pp. 1–5, 2015. [Google Scholar]
20. S. A. Gbadamosi, G. P. Hancke and A. M. Abu-Mahfouz, “Interference avoidance resource-allocation for D2D-enabled 5G narrowband internet of things,” IEEE Internet of Things Journal, 2022. https://doi.org/10.1109/JIOT.2022.3184959. [Google Scholar]
21. C. Hoymann, W. Chen, J. Montojo, A. Golitschek, C. Koutsimanis et al., “Relaying operation in 3GPP LTE: Challenges and solutions,” IEEE Communications Magazine, vol. 50, no. 2, pp. 156–162, 2012. [Google Scholar]
22. K. W. Yang, M. Wang, K. J. Zou, M. Hua, J. J. Hu et al., “Device discovery for multihop cellular networks with its application in LTE,” IEEE Wireless Communications, vol. 21, no. 5, pp. 24–34, 2014. [Google Scholar]
23. Y. Liu, L. Wang, S. A. R. Zaidi, M. Elkashlan and T. Q. Duong, “Secure D2D communication in large-scale cognitive cellular networks: A wireless power transfer model,” IEEE Transactions on Communications, vol. 64, no. 1, pp. 329–342, 2016. [Google Scholar]
24. S. Andreev, J. Hosek, T. Olsson, K. Johnsson, A. Pyattaev et al., “A unifying perspective on proximity-based cellular-assisted mobile social networking,” IEEE Communications Magazine, vol. 54, no. 4, pp. 108–116, 2016. [Google Scholar]
25. I. Corporation, Meeting No 73, (2013, May 24“Discussion on design options for D2D discovery,” [Online]. Available: 3GPP TDocs: Meeting: R1-77. [Google Scholar]
26. S. Jung and S. Chang, “A discovery scheme for device-to-device communications in synchronous distributed networks,” in Advanced Communication Technology (ICACT2014 16th Int. Conf. on, Pyeong Chang, South Korea, IEEE, pp. 815–819, 2014. [Google Scholar]
27. L. Lei, Z. Zhong, C. Lin and X. Shen, “Operator controlled device-to-device communications in LTE-advanced networks,” IEEE Wireless Communications, vol. 19, no. 3, pp. 96, 2012. [Google Scholar]
28. G. Fodor, E. Dahlman, G. Mildh, S. Parkvall, N. Reider et al., “Design aspects of network assisted device-to-device communications,” IEEE Communications Magazine, vol. 50, no. 3, pp. 170–177, 2012. [Google Scholar]
29. W. Lee, J. Kim and S. -W. Choi, “New D2D peer discovery scheme based on spatial correlation of wireless channel,” IEEE Transactions on Vehicular Technology, vol. 65, 12, pp. 10120–10125, 2016. [Google Scholar]
30. D. Feng, L. Lu, Y. Yuan-Wu, G. Y. Li, S. Li et al., “Device-to-device communications in cellular networks,” IEEE Communications Magazine, vol. 52, no. 4, pp. 49–55, 2014. [Google Scholar]
31. C. F. e Silva, T. F. Maciel, R. L. Batista, L. Elias, A. Robson et al., “Network-assisted neighbor discovery based on power vectors for D2D communications,” in IEEE 81st Vehicular Technology Conf. (VTC Spring), Glasgow, Scotland, IEEE, pp. 1–5, 2015. [Google Scholar]
32. B. Zhang, Y. Li, D. Jin, P. Hui and Z. Han, “Social-aware peer discovery for D2D communications underlaying cellular networks,” IEEE Transactions on Wireless Communications, vol. 14, no. 5, pp. 2426–2439, 2015. [Google Scholar]
33. P. Nguyen, P. Wijesinghe, R. Palipana, K. Lin and D. Vasic, “Network-assisted device discovery for LTE-based D2D communication systems,” in IEEE Int. Conf. on Communications (ICC), Sydney, Australia, IEEE, pp. 3160–3165, 2014. [Google Scholar]
34. H. Chour, Y. Nasser, H. Artail, A. Kachouh and A. Al-Dubai, “VANET aided D2D discovery: Delay analysis and performance,” IEEE Transactions on Vehicular Technology, vol. 66, no. 9, pp. 8059–8071, 2017. [Google Scholar]
35. H. Tang, Z. Ding and B. C. Levy, “Enabling D2D communications through neighbor discovery in LTE cellular networks,” IEEE Transactions on Signal Processing, vol. 62, no. 19, pp. 5157–5170, 2014. [Google Scholar]
36. K. J. Zou, M. Wang, K. W. Yang, J. Zhang, W. Sheng et al., “Proximity discovery for device-to-device communications over a cellular network,” IEEE Communications Magazine, vol. 52, no. 6, pp. 98–107, 2014. [Google Scholar]
37. M. N. Tehrani, M. Uysal and H. Yanikomeroglu, “Device-to-device communication in 5G cellular networks: Challenges, solutions, and future directions,” IEEE Communications Magazine, vol. 52, no. 5, pp. 86–92, 2014. [Google Scholar]
38. X. Lin, J. G. Andrews, A. Ghosh and R. Ratasuk, “An overview of 3GPP device-to-device proximity services,” IEEE Communications Magazine, vol. 52, no. 4, pp. 40–48, 2014. [Google Scholar]
39. K. Loa, C. -C. Wu, S. -T. Sheu, Y. Yuan, M. Chion et al., “IMT-advanced relay standards [WiMAX/LTE update],” IEEE Communications Magazine, vol. 48, no. 8, pp. 40–48, 2010. [Google Scholar]
40. J. Yao, T. Wang, X. Wu, L. Wang and B. Zheng, “Blind spot coverage strategy based on D2D communications for electric LTE network,” in 8th Int. Conf. on Wireless Communications & Signal Processing (WCSP), Jiangsu, China, IEEE, pp. 1–4, 2016. [Google Scholar]
41. M. Waqas, Y. Niu, Y. Li, M. Ahmed, D. Jin et al., “A comprehensive survey on mobility-aware D2D communications: Principles, practice and challenges,” IEEE Communications Surveys & Tutorials, vol. 22, no. 3, pp. 1863–1886, 2019. [Google Scholar]
42. W. Yi, Y. Liu and A. Nallanathan, “Modeling and analysis of D2D millimeter-wave networks with poisson cluster processes,” IEEE Transactions on Communications, vol. 65, no. 12, pp. 5574–5588, 2017. [Google Scholar]
43. G. H. Sim, A. Loch, A. Asadi, V. Mancuso and J. Widmer, “5G millimeter-wave and D2D symbiosis: 60 GHz for proximity-based services,” IEEE Wireless Communications, vol. 24, no. 4, pp. 140–145, 2017. [Google Scholar]
44. N. A. Tultul, S. Farha, S. S. Hossain, M. A. Hossain and S. R. Sabuj, “Device-to-device communication in terahertz frequency band: Enhancement of energy efficiency,” in IEEE Region 10 Conf. (TENCON), Osaka, Japan, IEEE, pp. 117–122, 2020. [Google Scholar]
45. C. -X. Wang, J. Huang, H. Wang, X. Gao, X. You et al., “6G wireless channel measurements and models: Trends and challenges,” IEEE Vehicular Technology Magazine, vol. 15, no. 4, pp. 22–32, 2020. [Google Scholar]
46. W. Guan and K. R. Liu, “Mitigating error propagation for wireless network coding,” IEEE Transactions on Wireless Communications, vol. 11, no. 10, pp. 3632–3643, 2012. [Google Scholar]
47. Y. Liu, Y. Wang, R. Sun and Z. Miao, “Distributed resource allocation for D2D-assisted small cell networks with heterogeneous spectrum,” IEEE Access, vol. 7, pp. 83900–83914, 2019. [Google Scholar]
48. V. Sathya, “Evolution of small cell from 4G to 6G: Past, present, and future,” arXiv preprint arXiv:2101.10451, 2020. [Google Scholar]
49. S. Zhang, J. Liu, H. Guo, M. Qi and N. Kato, “Envisioning device-to-device communications in 6G,” IEEE Network, vol. 34, no. 3, pp. 86–91, 2020. [Google Scholar]
50. S. Mohan, R. Kapoor and B. Mohanty (2011, February 10Rev 896146821, “Latency in HSPA data networks,” [Online]. Available: White Paper: Qualcomm. [Google Scholar]
51. Z. Savic (2011, December 1“LTE design and deployment strategies,” [Online]. Available: CISCO VNI: Report. [Google Scholar]
52. Z. Xiao and H. Perros, “Response time of the S1 and X2 handover procedures between (H) eNBs in a virtualized environment,” in The Future Network and Innovation, Nanjing, China: Chinese Engineering Academy, pp. 1–8, 2015. [Google Scholar]
53. A. Murkaz, R. Hussain, S. F. Hasan, M. Y. Chung, B. C. Seet et al., “Architecture and protocols for inter-cell device-to-device communication in 5G networks,” in IEEE 14th Intl Conf on Dependable, Autonomic and Secure Computing, Auckland, New Zealand, pp. 489–492, 2016. [Google Scholar]
Cite This Article
 Copyright © 2023 The Author(s). Published by Tech Science Press.
Copyright © 2023 The Author(s). Published by Tech Science Press.This work is licensed under a Creative Commons Attribution 4.0 International License , which permits unrestricted use, distribution, and reproduction in any medium, provided the original work is properly cited.


 Submit a Paper
Submit a Paper Propose a Special lssue
Propose a Special lssue View Full Text
View Full Text Download PDF
Download PDF Downloads
Downloads
 Citation Tools
Citation Tools