 Open Access
Open Access
ARTICLE
Detection of Copy-Move Forgery in Digital Images Using Singular Value Decomposition
1 Faculty of Engineering, School of Computing, University Technology of Malaysia, Johar Bahru, Malaysia
2 UTM-IRDA MaGICX, Institute of Human Centered Engineering, Universiti Teknologi Malaysia, Malaysia
3 Artificial Intelligence & Data Analytics Lab CCIS Prince Sultan University Riyadh, Saudi Arabia
4 Computer Techniques Engineering Department, Faculty of Information Technology, Imam Ja’afar Al-Sadiq University, Baghdad, Iraq
* Corresponding Author: Amjad Rehman. Email:
Computers, Materials & Continua 2023, 74(2), 4135-4147. https://doi.org/10.32604/cmc.2023.032315
Received 13 May 2022; Accepted 18 August 2022; Issue published 31 October 2022
Abstract
This paper presents an improved approach for detecting copy-move forgery based on singular value decomposition (SVD). It is a block-based method where the image is scanned from left to right and top to down by a sliding window with a determined size. At each step, the SVD is determined. First, the diagonal matrix’s maximum value (norm) is selected (representing the scaling factor for SVD and a fixed value for each set of matrix elements even when rotating the matrix or scaled). Then, the similar norms are grouped, and each leading group is separated into many subgroups (elements of each subgroup are neighbors) according to 8-adjacency (the subgroups for each leading group must be far from others by a specific distance). After that, a weight is assigned for each subgroup to classify the image as forgery or not. Finally, the F1 score of the proposed system is measured, reaching 99.1%. This approach is robust against rotation, scaling, noisy images, and illumination variation. It is compared with other similar methods and presents very promised results.Keywords
Nowadays, digital images have become part of daily life due to the high growth of technology and the development of the internet. This led to easy access to images and multimedia, processing them, transferring and quickly altering image details, and developing tampered images [1]. Digital images are almost used in every branch of our life and scientific fields. It is used in authentication, court, law, medical, industry, Remote sensing, forensics, machine vision, etc.
Editing and changing digital images become easier for anyone with the advancement of various low-cost hardware and software tools such as Adobe Photoshop, Corel draw, etc. As shown in Fig. 1 [2], many changes can be made to images.
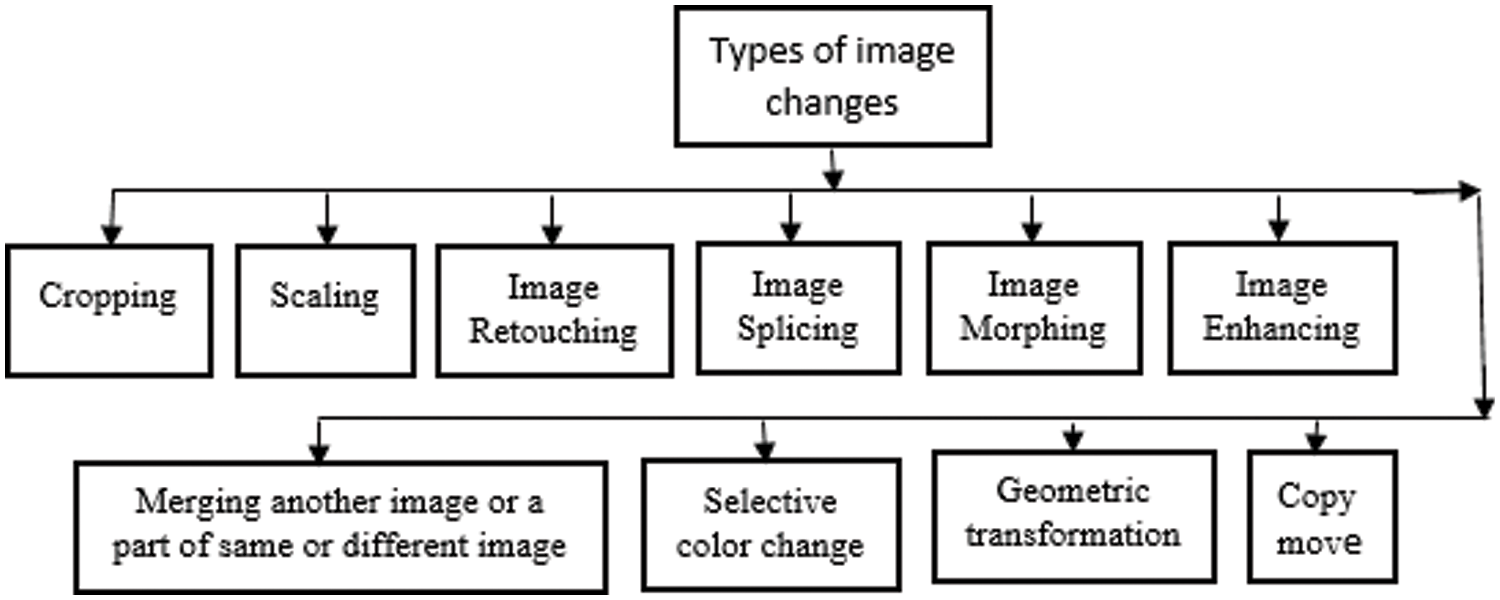
Figure 1: The possible changes that can be made to images
With the extensive use and transmission of digital images, authentication becomes very important to increase the trust in the images [3]. Image forensics is an alternative method of authenticating. One of these methods is forgery detection. Digital Image forgery can be generally classified into two main types, active and passive, as shown in Fig. 2 [4,5].
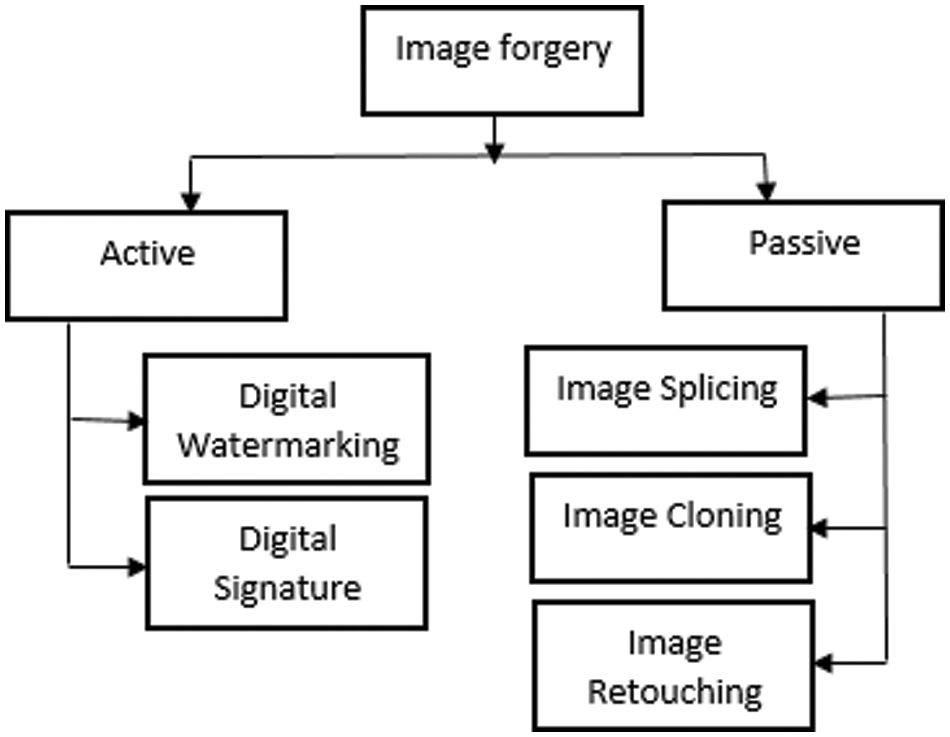
Figure 2: Types of image forgery
Three types of passive image forgery can be made for digital images.
1.1 Image retouching focuses on reducing or enhancing some of the digital image features that make it a less harmful type of image forgery.
1.2 Splicing is implemented by combining two or more images, which hides some critical information from the original image [6].
1.3 Copy-move forgery (CMF) is the most popular type. It includes copying part of the image and then pasting this part into another region of the image. Of course, image editing can be made along with this operation, such as scaling, rotation, adding noise, etc. Unfortunately, it is not easy to detect this type of image forgery. In general, passive forgery detection can be categorized into block-based and keypoint-based methods [3]. Usually, the keypoint approach is based on one or more feature extraction techniques, such as Scale-Invariant Feature Transform (SIFT), Speeded Up Robust Features, or others [5,7,8].
In this paper, we look to suggest a robust algorithm to detect copy-move forgery (also known as region duplication attack). Fig. 3 shows an example of this type of attack.

Figure 3: Effect of copy move forgery
The primary approach to detecting the same regions is block-based [9,10], which means they look for block pixels similar to the other block(s) in an image, where a gap is separate between them. Such methods help detect copy-move forgery, which occurs when an image region is replicated without being altered. However, approaches that entail region changes such as scaling, rotation, and image lighting variation are not as efficient for region duplication.
We will use a CASIA [11] and CoMoFoD dataset [12] that includes a set of color forgery images in the currently proposed method.
The rest of the paper is organized as follows: Section two presents the related works, while Section three focuses on the definition of singular value decomposition. In Section four, the proposed method methodology will be introduced. Then Section five specified results and discussion. Finally, the conclusion will be summarized in Section six.
(Amerini et al., 2013) suggested a method for the detection of image forgery based on SIFT. Features extracted from images of the dataset MICC-F220 and MICC-F2000. This method deal with the rotation and scaling of the forged object. The False Positive Rate (FPR) and True Positive Rate (TPR) achieved are 8% and 100%, respectively [11].
(Uliyan et al., 2016) introduced a forgery detection method based on combined features of Hessian points and a centrosymmetric local binary pattern (CSLBP). The advantage of this method is invariant to scale, translation, and illumination, but on the other side, it is not invariant when the image is degraded by blur. The false-positive and true-positive rates are 8% and 92%, respectively [12].
(Alkawaz et al., 2018) proposed image forgery detection approach based on discrete cosine transform (DCT). This method works with gray images. The input image is divided into several overlapping blocks. For each block, the 2D DCT coefficient is determined. A feature vector is generated using zig-zag scanning in every block and sorted by lexicographic. Finally, the Euclidean distance is used to locate duplicate blocks [13].
(Huang et al., 2019) suggested a method to detect copy-move forgery based on superpixel segmentation and Helmert transformation. The first step of this method used the SIFT algorithm to extract the key points and their descriptors. Matching pairs is achieved by determining the similarity of key points based on the descriptor. These pairs are grouped based on the spatial distance by Helmert transformation to get coarse forgery regions. The isolated area will be removed. The advantage of this method is the robustness for rotation, scaling, and compression. The best recall and precision were 80% and 82%, respectively [14].
(Ali et al., 2022) Proposed a system based on deep learning to detect forgery images in the context of double image compression. Training the proposed model based on the difference between the original and recompressed images. The performance of this model was 92.23% as a validation accuracy [15].
3 Singular Value Decomposition (SVD)
In linear algebra, SVD is a critical topic by many famous mathematicians, which is a factoring of a true matrix and is utilized to elicit geometric and algebraic features of the image. SVD is a stable transformation for scaling and rotation invariance, it is a vigorous and trustworthy orthogonal matrix decomposition method, so it has become popular in many practical applications in signal and image processing and statistics [16]. A unique feature of SVD is its application on real (m, n) matrix, as Eq. (1). For any given matrix A∈Rm × n, there exists a decomposition
such that
• U is an m × n matrix with orthonormal columns.
• S is an n × n diagonal matrix with nonnegative entries.
• VT is an n × n orthonormal matrix.
We can visualize this decomposition in Fig. 4.

Figure 4: Decompose a matrix using SVD
This proposal suggested a robust algorithm for detecting copy-move forger images based on the SVD transformation. The primary step to solving the problem of detecting copy-move forger is listed in Algorithm 1.

The input image for this system is a color image. First, preprocessing for the input image is implemented, which includes (converting the RGB image into a gray image, image denoising by using a deep neural network (CNN), and resizing the image (most of the images in the dataset have a size of 256 × 384, so every image with a size larger or less than this size will be normalized to (256 × 384)).
A sliding window with size 11 × 11 will be scanned on the entire image from left to right and top to bottom. At each step, the SVD transformation will be calculated. The result of the SVD process will be three matrices. We are concerned with the diagonal matrix. The largest value of the diagonal matrix at each step is selected, called (the norm value), and stored in a matrix (has norm values and locations of a norm).
After scanning the entire image, the norm vector will be sorted in ascending order. This vector is divided into many groups (each group has a similar norm value), and groups with less than four pixels will be ignored.
We try to find the connected norms for each group according to the 8-adjacency. This process divides the group into several sub-groups (there is no connection between each sub-group with other sub-groups of the same norm). Each subgroup with less than three norms will be ignored. A weight for a group will be created according to the sub-group size (weight increase by one for every two subgroups has the same size or different by one).
Finally, two arrays will be created. The first includes the norm value and the corresponding weights, while the second consists of the norm value with the corresponding number of subgroups (left in the group). The two arrays are sorted in ascending order according to the weight and number of the subgroup. We select the first (highest) six norms of the first array (weight array) and the first ten norms of the second array (subgroup array).
Image classified as a forgery image if achieved the following condition:
“If the subgroup number in the selected norm is more than seven, and selected weights are greater than fifteen or less than nine.”
Else it is classified as a non-forgery image. Fig. 5 shows the block diagram of the suggested algorithm.

Figure 5: The block diagram for the suggested algorithm
Several tested experiments are conducted to assess the proposed schemes in this section. MATLAB 2018b is used to carry out the experiments. First, the approach was tested on 500 color stander images from the CASIA and CoMoFoD datasets. Animals, plants, structures, and some types of meals are among the original authentic images from two databases, Fig. 6 shows a sample of dataset images used in the current proposal. Second, Adobe Photoshop CS6 was used to create the altered images from the originals (scaling and rotation objects).

Figure 6: Samples of the dataset’s images used in the current proposal from CASIA and CoMoFoD datasets
Precision as Eq. (2), recall as Eq. (3), and F1 score as Eq. (4) are used as performance assessments to measure the accuracy of the tampered images detection of the proposed algorithm [17,18].
where TP is the true positive, FP is a false positive, and FN is a false negative.
The first test focuses on evaluating the performance of the suggested system when using different sliding window sizes. Forgery and non-forgery images are fed from the datasets into the system one by one, and the system’s performance is assessed. The best performance is achieved when the block size of the sliding window equals 11 × 11, as shown in Table 1. This test is also regarded as a test for determining the best sliding window size that can be used in this proposal. The results are summarized in Fig. 7 in addition to Table 1.
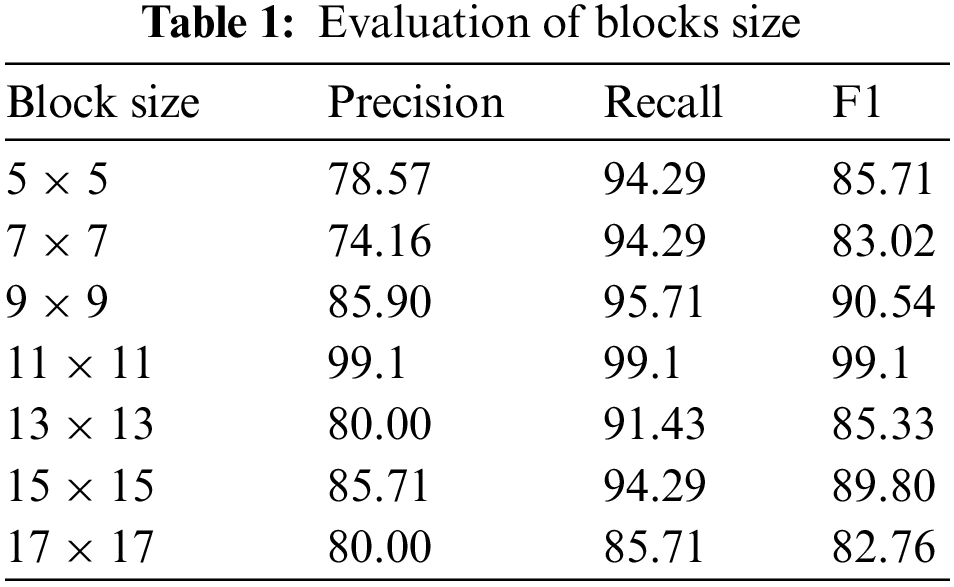
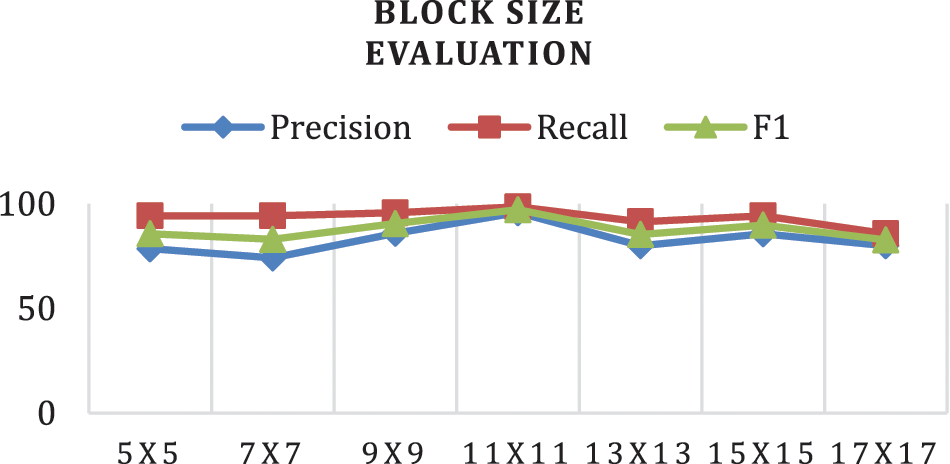
Figure 7: Block size evaluation of sliding window
The input image size has high effects on the performance of the proposed algorithm, so we test how the image size affects the results in the proposed algorithm and what is the best image size that can be used to get optimum accuracy. Fig. 8 shows the result of this test. We can conclude from this figure that the image size (256 × 384) is the best choice to get better accuracy.
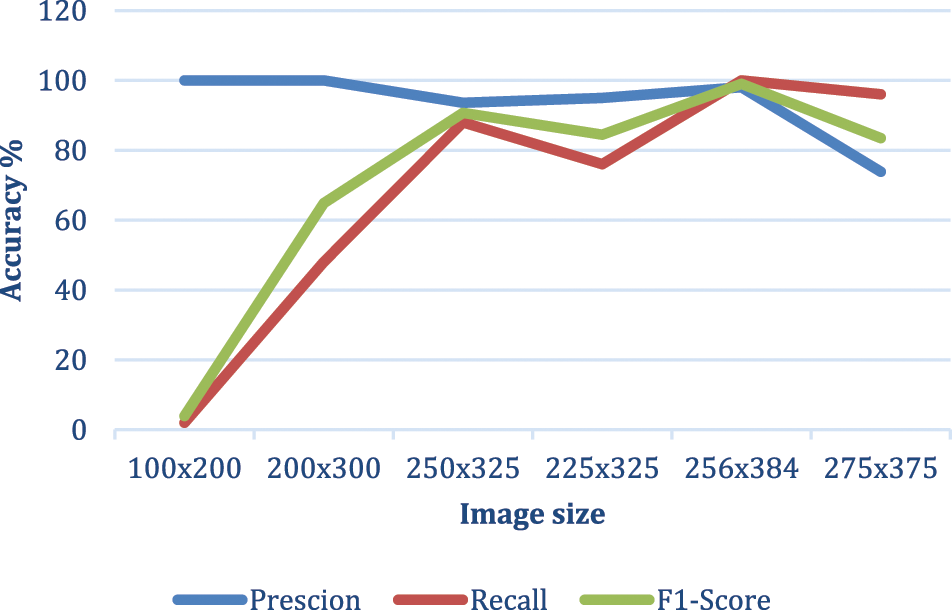
Figure 8: Effect of image size on accuracy
Also, the current proposal is tested when the duplicated object is rotated with different angles ranging from 20 degrees to 180 degrees. The testing results are tabulated in Table 2. As shown in Table 3, the suggested technique successfully detects all duplicated regions under rotation attacks from various angles. Fig. 9 shows a sample of rotated object images tested by the proposed scheme.
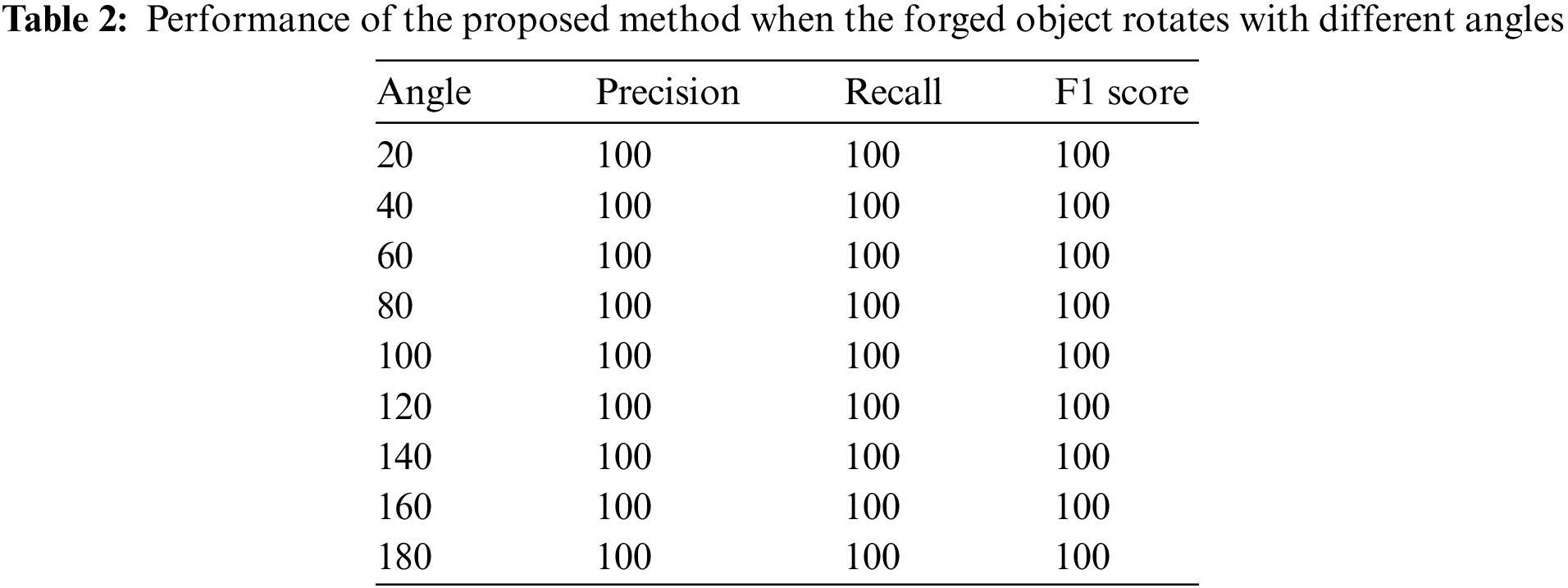
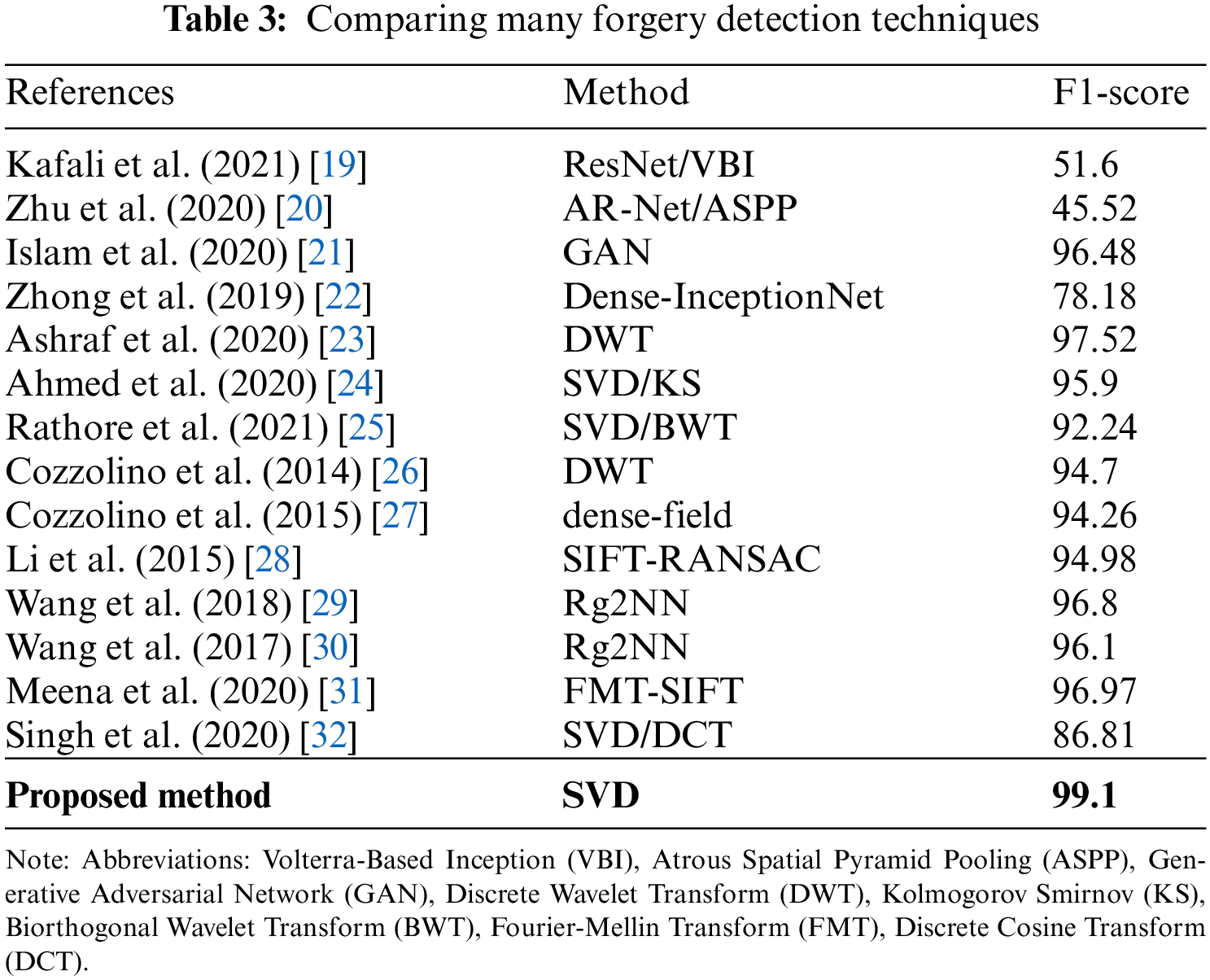

Figure 9: Sample of forgery images with rotating forged objects from CASIA and CoMoFoD datasets
The other performance testing of the proposed method is when the duplicated object is scaled. A sample of images when scaling forged objects is shown in Fig. 10. The proposed method successfully detected all the forgery and non-forgery images with scaled objects.

Figure 10: Sample of forgery images with a scaled object from CASIA and CoMoFoD datasets
For further analysis of the robustness of the proposed algorithm, we implemented various experiments on the forgery images where it is contaminated with noise. First, Gaussian noise is inserted in the tested images. Then, gaussian noises were added randomly, with zero mean and standard deviations of 0.2, 0.4, 0.6, and 0.8. In this test, 300 images were used. The F1-score accuracies are shown in Fig. 11. Although the proposed algorithm shows a robust behavior against the noise, the method performance did not affect when using noisy images.
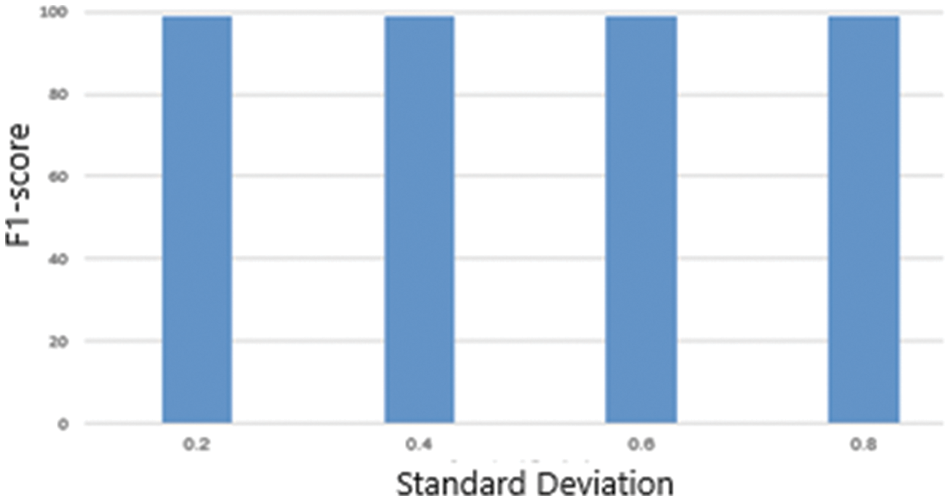
Figure 11: The F1-measure chart under attacks of additive white Gaussian noise
The result of detecting forgery images contaminated with noise is compared with other works, as shown in Fig. 12.

Figure 12: Comparing F1-score for different works under attacks of additive white Gaussian noise
Also, the proposed method was tested with various image illumination, and we found that the F1-score for detecting forgery images was up to 99.1%. A sample of the image used in this test is shown in Fig. 13.

Figure 13: Sample of image with various illumination from CASIA and CoMoFoD datasets
The elapsed time of the CPU for the detection of the forgery image was 18.5 s.
Finally, the suggested method results are compared with several similar methods, as illustrated in Table 3.
This paper proposed a new enhancement of the SVD for digital image forgery detection. First, we used CASIA and CoMoFoD datasets to evaluate the proposed method. Then, a preprocessing technique was applied to convert the input images from RGB to grayscale, and the images were resized into 256 × 384. Next, the image was divided into 11 × 11 overlapped blocks. After that, we used the SVD (diagonal array) to extract features from each block.
The norm’s value was also calculated for each block, finding similar norms. Finally, for each similar norms subgroups, the weight was calculated, and this led to deciding if the image was copy-move or not. The suggested method gives excellent results, and we proved it robust against rotation, scaling, noisy images, and illumination variation. Furthermore, when the introduced method is compared with other methods, it shows high performance, giving better results than most copy-move detection methods. For future work, we suggest using generalized singular value decomposition (GSVD) to detect the copy-move forgery, which has many features that need to be discovered.
Funding Statement: This research is supported by Artificial Intelligence & Data Analytics Lab (AIDA) CCIS Prince Sultan University, Riyadh, Saudi Arabia. The authors also would like to acknowledge the support of Prince Sultan University for paying the APC of this publication.
Conflicts of Interest: The authors declare that they have no conflicts of interest to report regarding the present study.
References
1. M. H. Alkawaz, G. Sulong, T. Saba and A. Rehman, “Detection of copy-move image forgery based on discrete cosine transform,” Neural Computing and Applications, vol. 30, no. 1, pp. 183–192, 2016. [Google Scholar]
2. K. Rathi and P. Singh, “Copy move forgery detection by using integration of SLIC and SIFT,” in Proceeding of Expert Clouds and Applications, vol. 209. Bangalore, India: Springer, pp. 531–544, 2022. DOI: https://doi.org/10.1007/978-981-16-2126-0_43. [Google Scholar]
3. M. Bilal, H. A. Habib, Z. Mehmood, R. M. Yousaf, T. Saba et al., “A robust technique for copy-move forgery detection from small and extremely smooth tampered regions based on the DHE-SURF features and mDBSCAN clustering,” Australian Journal of Forensic Sciences, vol. 53, no. 4, pp. 459–482, 2021. [Google Scholar]
4. S. Walia and K. Kumar, “Digital image forgery detection: A systematic scrutiny,” Australian Journal of Forensic Sciences, vol. 51, no. 5, pp. 488–526, 2019. [Google Scholar]
5. T. Mahmood, Z. Mehmood, M. Shah and T. Saba, “A robust technique for copy-move forgery detection and localization in digital images via stationary wavelet and discrete cosine transform,” Journal of Visual Communication and Image Representation, vol. 53, pp. 202–214, 2018. [Google Scholar]
6. T. Saba, A. Rehman, T. Sadad and Z. Mehmood, “Copy-move image forged information detection and localisation in digital images using deep convolutional network,” Journal of Information Science, vol. 52, no. 2, pp. 016555152110500, 2021. [Google Scholar]
7. W. Sun, X. Chen, X. Zhang, G. Dai, P. Chang et al., “A multi-feature learning model with enhanced local attention for vehicle re-identification,” CMC-Computers, Materials & Continua, vol. 69, no. 3, pp. 3549–3561, 2021. [Google Scholar]
8. F. H. Najjar, H. M. Al-Jawahry, M. S. Al-Khaffaf and A. T. Al-Hasani, “A novel hybrid feature extraction method using LTP, TFCM, and GLCM,” Proceeding of Journal of Physics: Conference Series, vol. 1892, no. 1, pp. 012018, 2021. [Google Scholar]
9. X. Kang and S. Wei, “Identifying tampered regions using singular value decomposition in digital image forensics,” in Proc. of 2008 Int. Conf. on Computer Science and Software Engineering, IEEE, Wuhan, China, vol. 3, pp. 926–930, 2008. DOI: https://doi.org/10.1109/CSSE.2008.876. [Google Scholar]
10. Z. N. Khudhair, F. Mohamed and K. A. Kadhim, “A review on copy-move image forgery detection techniques,” Proceeding of Journal of Physics: Conference Series, vol. 1892, no. 1, pp. 012010, 2021. [Google Scholar]
11. I. Amerini, L. Ballan, R. Caldelli, A. Del Bimbo, L. Del Tongo et al., “Copy-move forgery detection and localization by means of robust clustering with J-Linkage,” Signal Processing: Image Communication, vol. 28, no. 6, pp. 659–669, 2013. [Google Scholar]
12. D. M. Uliyan, H. A. Jalab and A. W. Wahab, “Copy move image forgery detection using Hessian and center symmetric local binary pattern,” in Proc. of 2015 IEEE Conf. on Open Systems (ICOS), IEEE, Melaka, Malaysia, pp. 7–11, 2015. DOI: https://doi.org/10.1109/ICOS.2015.7377269. [Google Scholar]
13. M. H. Alkawaz, G. Sulong, T. Saba and A. Rehman, “Detection of copy-move image forgery based on discrete cosine transform,” Neural Computing and Applications, vol. 30, no. 1, pp. 183–192, 2018. [Google Scholar]
14. H. Y. Huang and A. J. Ciou, “Copy-move forgery detection for image forensics using the superpixel segmentation and the Helmert transformation,” EURASIP Journal on Image and Video Processing, vol. 2019, no. 1, pp. 1–16, 2019. [Google Scholar]
15. S. S. Ali, I. I. Ganapathi, N. S. Vu, S. D. Ali, N. Saxena et al., “Image forgery detection using deep learning by recompressing images,” Electronics, vol. 11, no. 3, pp. 403, 2022. [Google Scholar]
16. N. K. El Abbadi, A. Al Rammahi, D. S. Redha and M. AbdulHameed, “Image compression based on SVD and MPQ-BTC,” Journal of Computer Science, vol. 10, no. 10, pp. 2095–2104, 2014. [Google Scholar]
17. H. Abdi, “Singular value decomposition (SVD) and generalized singular value decomposition,” In: N. J. Salkind (Ed.Encyclopedia of Measurement and Statistics, Thousand Oaks, CA: Sage, pp. 907–912, 2007. [Google Scholar]
18. S. Satonkar Suhas, B. Kurhe Ajay and B. Khanale Prakash, “Face recognition using singular value decomposition of facial color image database,” International Journal of Science and Research, vol. 4, no. 1, pp. 249–254, 2015. [Google Scholar]
19. E. Kafali, N. Vretos, T. Semertzidis and P. Daras, “RobusterNet: Improving copy-move forgery detection with volterra-based convolutions,” in Proc. of 2020 25th Int. Conf. on Pattern Recognition (ICPR), IEEE, Milan, Italy, pp. 1160–1165, 2021. DOI: https://doi.org/10.1109/ICPR48806.2021.9412587. [Google Scholar]
20. Y. Zhu, C. Chen, G. Yan, Y. Guo and Y. Dong, “AR-Net: Adaptive attention and residual refinement network for copy-move forgery detection,” IEEE Transactions on Industrial Informatics, vol. 16, no. 10, pp. 6714–6723, 2020. [Google Scholar]
21. A. Islam, C. Long, A. Basharat and A. Hoogs, “DOA-GAN: Dual-order attentive generative adversarial network for image copy-move forgery detection and localization,” in Proc. of the IEEE/CVF Conf. on Computer Vision and Pattern Recognition, Seattle, WA, USA, pp. 4676–4685, 2020. DOI: https://doi.org/10.1109/CVPR42600.2020.00473. [Google Scholar]
22. J. L. Zhong and C. M. Pun, “An end-to-end dense-inceptionnet for image copy-move forgery detection,” IEEE Transactions on Information Forensics and Security, vol. 15, pp. 2134–2146, 2019. [Google Scholar]
23. R. Ashraf, M. S. Mehmood, T. Mahmood, J. Rashid, M. W. Nisar et al., “An efficient forensic approach for copy-move forgery detection via discrete wavelet transform,” in Proc. of 2020 Int. Conf. on Cyber Warfare and Security (ICCWS), Islamabad, Pakistan, IEEE, pp. 1–6, 2020. DOI: https://doi.org/10.1109/ICCWS48432.2020.9292372. [Google Scholar]
24. B. Ahmed, T. A. Gulliver and S. al-Zahir, “Blind copy-move forgery detection using SVD and KS test,” SN Applied Sciences, vol. 2, no. 8, pp. 1–12, 2020. [Google Scholar]
25. N. K. Rathore, N. K. Jain, P. K. Shukla, U. Rawat and R. Dubey, “Image forgery detection using singular value decomposition with some attacks,” National Academy Science Letters, vol. 44, no. 4, pp. 331–338, 2021. [Google Scholar]
26. D. Cozzolino, G. Poggi and L. Verdoliva, “Copy-move forgery detection based on patchmatch,” in Proc. of 2014 IEEE Int. Conf. on Image Processing (ICIP), Paris, France, IEEE, pp. 5312–5316, 2014. DOI: https://doi.org/10.1109/ICIP.2014.7026075. [Google Scholar]
27. D. Cozzolino, G. Poggi and L. Verdoliva, “Efficient dense-field copy-move forgery detection,” IEEE Transactions on Information Forensics and Security, vol. 10, no. 11, pp. 2284–2297, 2015. [Google Scholar]
28. J. Li, X. Li, B. Yang and X. Sun, “Segmentation-based image copy-move forgery detection scheme,” IEEE Transactions on Information Forensics and Security, vol. 10, no. 3, pp. 507–518, 2014. [Google Scholar]
29. X. Y. Wang, L. X. Jiao, X. B. Wang, H. Y. Yang and P. P. Niu, “A new keypoint-based copy-move forgery detection for color image,” Applied Intelligence, vol. 48, no. 10, pp. 3630–3652, 2018. [Google Scholar]
30. X. Y. Wang, S. Li, Y. N. Liu, Y. Niu, H. Y. Yang et al., “A new keypoint-based copy-move forgery detection for small smooth regions,” Multimedia Tools and Applications, vol. 76, no. 22, pp. 23353–23382, 2017. [Google Scholar]
31. K. B. Meena and V. Tyagi, “A hybrid copy-move image forgery detection technique based on Fourier-Mellin and scale invariant feature transforms,” Multimedia Tools and Applications, vol. 79, no. 11, pp. 8197–8212, 2020. [Google Scholar]
32. G. Singh and K. Singh, “An improved block based copy-move forgery detection technique,” Multimedia Tools and Applications, vol. 79, no. 19, pp. 13011–13035, 2020. [Google Scholar]
Cite This Article
 Copyright © 2023 The Author(s). Published by Tech Science Press.
Copyright © 2023 The Author(s). Published by Tech Science Press.This work is licensed under a Creative Commons Attribution 4.0 International License , which permits unrestricted use, distribution, and reproduction in any medium, provided the original work is properly cited.


 Submit a Paper
Submit a Paper Propose a Special lssue
Propose a Special lssue View Full Text
View Full Text Download PDF
Download PDF Downloads
Downloads
 Citation Tools
Citation Tools