| Computers, Materials & Continua DOI:10.32604/cmc.2022.031490 |  |
| Article |
Active Authentication Protocol for IoV Environment with Distributed Servers
1Department of Computer Science and Information Engineering, Asia University, Taichung, Taiwan
2Bioinformatics and Medical Engineering, Asia University, Taichung, Taiwan
*Corresponding Author: Yu-Lin Song. Email: d87222007@ntu.edu.tw
Received: 19 April 2022; Accepted: 12 June 2022
Abstract: The Internet of Vehicles (IoV) has evolved as an advancement over the conventional Vehicular Ad-hoc Networks (VANETs) in pursuing a more optimal intelligent transportation system that can provide various intelligent solutions and enable a variety of applications for vehicular traffic. Massive volumes of data are produced and communicated wirelessly among the different relayed entities in these vehicular networks, which might entice adversaries and endanger the system with a wide range of security attacks. To ensure the security of such a sensitive network, we proposed a distributed authentication mechanism for IoV based on blockchain technology as a distributed ledger with an ouroboros algorithm. Using timestamp and challenge-response mechanisms, the proposed authentication model can withstand several security attacks such as Man-in-Middle (MiM) attacks, Distributed Denial of Service (DDoS) attacks, server spoofing attacks and more. The proposed method also provides a solution for single-point failure, forward secrecy, revocability, etc. We exhibit the security of our proposed model by using formal (mathematical) analysis and informal analysis. We used Random Oracle Model to perform the mathematical analysis. In addition, we compared the communication cost, computation cost, and security of the proposed model with the related existing studies. We have verified the security of the model by using AVISPA tool simulation. The security analysis and computation analysis show that the proposed protocol is viable.
Keywords: IoV; message authentication; random oracle model; blockchain; distributed server; revocability
In this decade, all the industries are influenced by high-tech innovations; the need for connected devices and automation devices is increasing day by day. The Internet of Things (IoT) is a crucial member of the invention that changes modern-day connected devices. The IoT facilitates a physical object to be intelligent by communicating with other devices. By 2025, forecasts suggest that more than 75 billion IoT-connected devices will be used. This count would be a nearly threefold increase from the IoT installed base in 2019 [1]. The cities are becoming smarter with the help of IoT like waste management, electricity supply, sanitization, efficient urban mobility, traffic management, etc. In the case of efficient urban mobility and traffic management, the IoV acts mail role. By using advanced networking technology like 5G and Cloud technologies, this system aims to achieve effective real-time communication among the Participant of the network. The IoV promises a system in which every vehicle on the street can communicate with each other, so it helps reduce accidents and increases the efficiency of fuel consumption and many more factors [2]. IoV Is a network of vehicles where the vehicle can communicate with each other and communicate with the Road-Side Units (RSU), pedestrian’s handheld devices, traffic signals, and public network using Vehicle to Vehicle (V2 V), Vehicle to the Road (V2R), as well as a Vehicle to Infrastructure (V2I) connectivity. In the IoV system, the vehicles are the core nodes of the network, which have the storage and computation power to process the environmental data. The vehicles are powered by n number of sensors that help them learn about the environment. The drivers, passengers, and pedestrians are considered users of the system. Recommendation-based systems can also benefit from the profile of the user. The sensors used in the vehicles generate a large amount of data given as input to the local compute unit to analyze the environmental factors. The local storage of the vehicle is used to store such input data and analyze results of the environment. Such information about the location, speed, traffic, road condition, local weather, and other required data is shared between the network participants [3].
However, despite several advantages that IoV offers, it has some significant challenges and difficulties also to be solved. In the IoV communication model, sensitive information is transmitted between vehicles and infrastructure in the insecure communication medium. Suppose the sensitive messages of the legal user are leaked. In that case, a malicious attacker can use it to perform network attacks and give wrong information to the other devices, and it can cause a fatal accident. Another critical issue in the IoV is transmitting data in real-time without delay. So, the IoV needs a lightweight transmission, computation, and processing protocol that helps to perform real-time communication effectively. Therefore, the IoV required a secure and effective message authentication protocol to ensure the road safety of the vehicular network user [4,5]. The following are the main security requirements that a specific message authentication protocol should follow,
• Confidentiality. The message transmitted between the different entities of the network should be kept secret or private, only the legal participants of the network should be able to validate the message.
• Untraceability and anonymity. The user’s real identity must be kept secret; it should not be revealed in any circumstance. Even if a small part of the transmission got leaked, the remaining should not be compromised.
• Mutual authentication. The protocol of the IoV should help a vehicle get mutually authenticated among the other entities of the network and obtain a meaningful message of communication.
• Withstand password guessing attack. The protocol for secure IoV should resist the password guessing attack where an intruder tries to think the driver password, even when the intruder got the transferred message or the smart card credentials.
• Withstand against insider attacks. The insider attack happens within the privileged account. The confidential or trusted user of the network who accesses sensitive information misuses this account access and acts as an adversary. A suitable design of IoV protocol should withstand this attack.
• Withstand against device theft attacks. An intruder can extract the credential from the stolen device or the vehicle. In a well-designed protocol, the information removed from the device should not be enough for the intruder to access that particular network.
• Revocability. If a vehicle’s smart card is stolen or the vehicle is dumped, the identity should be removed from the Distributed Authentication Server (DAS) database before the adversary uses it. The IoV protocol should give the option, and it should provide a re-registration option for the lost smart card.
Other than the above attacks, the IoV protocol should withstand some popular attacks like a man-in-the-middle-attack, impersonation attack, denial-of-service attack, SQL injections, dictionary attack, etc. [6] Most of the recent time IoV authentication servers are using the centralized registration server architecture. The problem with centralized architecture is a single-point failure. The central node failure can cause the entire system to fail. The centralized architecture only can be vertically scalable [7–9]. Horizontal scalability will contradict the single central unit characteristic of the system. The bottleneck can appear when the traffic spikes, as the server can only have a limited number of open ports to listen to vehicles’ connections. This server can suffer from a denial-of-service attack (DoS) or DDoS. The centralized server could attract hackers to perform DoS attacks; DDoS attacks commonly overpower their targets by sending a huge number of legal packets from multiple attack sites. Consequently, the target spends its key resources on processing the attack packets and cannot attend to its legitimate vehicles. DDoS traffic also creates heavy congestion in the Internet core during extensive attacks, disrupting communication between all Internet users whose packets cross congested the routers. It leads to system failure and causes a large-scale accident on the road. To avoid such a DDoS attack, the distributed architecture is one of the solutions [10,11]. The DAS has various advantages over the centralized server. In distributed servers, more nodes can be easily added, so scalability will be easy to handle. All the nodes in the distributed system are linked to each other. So, nodes can easily share data with other nodes. Failure of one node does not lead to the failure of the entire distributed system. Other nodes can still communicate with each other. Distributed server results in low latency. If a particular node is located closer to the user, the distributed system makes sure that the user system receives traffic from that nearby node. Blockchain technology has many advantages like trust, decentralized structure, improved security and privacy, reduced cost, visibility and traceability, speed, immutability, individual control of data, tokenization, etc. A lot of research is happening around the advantages of blockchain these days. In this proposed model, we used one of the advantages of the blockchain called decentralized structure and property of distributed ledger. The overall design of the authentication server is decentralized in the proposed model, so to hold the transactions of the DAS, we need a distributed ledger. The distributed ledger is used to store the request of the vehicles and keys of the transaction like session keys and security keys, as specified in Section 4. Compared to the customarily distributed ledgers, the blockchain ledger has the advantage of Proof-of-Work (PoW). In Blockchain, PoW is used to validate transactions. It is a system that requires some computationally heavy tasks to validate the Block and add it to the chain. This method ensures that the data added to a blockchain is not false or manipulated. So, the DAS becomes more secure and immutable [11]. To avoid such problems of centralized servers and to use the advantages of blockchain, the proposed model suggests a DAS for authentication in the IoV environment by using the blockchain as a distributed ledger for handling the transactions.
The contribution of the proposed model is summarized as follows.
• We have used the blockchain and distributed server architecture for authentication in IoV environment. Miners use the Ouroboros algorithm to assure the correctness of credentials of vehicles.
• We have formally analyzed the framework using the famous Random Oracle Model and performed the framework’s informal security analyses.
• The proposed model has solved the problem of revocability and single-point failure in the IoV environment.
• The proposed model has higher efficiency in communication cost over other related studies.
The paper is organized as follows: we have discussed the system’s background in Section 2. In Section 3, we have explained about the proposed system and its stages. Formal security analysis and Informal security analysis is discussed in the Section 4 and Section 5 respectively. In Section 6, we have discussed about the performance analysis of the proposed system. Finally, we have given the conclusion of the proposed system.
In this section, we discussed the various research that happened in IoV authentication protocol in recent times. Li et al. [12] proposed authentication with privacy preservation and nonrepudiation for IoV environment. However, Dua et al. [13] analyzed the framework of Li et al. [12] and pointed out that their research framework could not withstand the session key disclosure attack. At the same time, it does not provide user anonymity and untracebility. Recently, some researchers have concentrated on the lightweight framework to reduce the complexity of transmission in real-time. The authors Ying et al. [14] presented a scheme for a secure and lightweight authentication method for IoV, whereas Chen et al. [15] found that the Ying et al. [14] work has the disadvantage of location leakage, password guessing attacks, repeat attack, and same time consumes considerable authentication time. Then Chen et al. [15] introduced a secure framework for authentication for IoV to resolve the drawbacks of Ying et al. [14] however, the method presented by Chen et al. [15] has the drawback of high storage cost due to the vast amount of data stored in the memory. Vasudev et al. [16] proposed a secure and efficient message authentication protocol for IoV environment; they claimed that their proposed method could withstand various security issues in IoV. However, Yu et al. [17] demonstrate that Vasudev et al. [16] cannot withstand critical security attacks such as a middle-man attack, mutual authentication, and impersonation. Then they [17] introduce a secure authentication protocol in a smart city environment for IoV. However, they [17] do not address the problem of single-point failure, revocability Problem, or denial-of-service attack in the IoV environment. The scheme of them [17] has a high computational cost comparatively. Therefore, we proposed a distributed server architecture for the authentication model for IoV environment to resolve their observed security problems.
This section describes the system background and the building blocks of the proposed method,
3.1 Primitives for Cryptography
The prominent Elliptic Curve algorithm for digital signature is used in this proposed method [18]. There are three processes act a main role in the digital signature, those processes are discussed follow,
• Key Generation:
• Digital Signature Generation:
• Verification:
The Digital signature function must not be forgeable [19]. That’s mean legal signature
The following are the two main goals of adversary
• The
• The
Adversary
• The Adversary
• The Adversary
• The
To assess the proposed framework, we explained the attack statements including the well-known “Dolev-Yao threat model (DYTM)”. The abilities of a malicious adversary are as follows. Mentioning to the DYTM model, an adversary can modify, inject, reply, eavesdrop or delete the transmitted messages in a public network [10–12]. The adversary can rob the smart card of the legal driver and retrieve the confidential information saved in storage by using the power analysis attacks. After having the confidential information, the adversary may attempt potential attacks, including MiM attack, Repeat Attack, wrong credential access, impersonate attack, server spoofing attack, etc. The adversary has complete control over the network; the capability of the adversary are he knows all the public data of the protocol, he can start any number of parallel protocol sessions, he can encrypt/decrypt if he has the key, he can build and send messages, he can compose/decompose messages and so on.
Blockchain is a system that records information to make it difficult or impossible to modify, hack or cheat the system. It is necessarily a digital ledger to store duplicated transactions and distribute them across the whole network of a computer system on the blockchain. It contains an ordered chain of blocks [21]. These blocks have a specified number of transactions. Each block is connected to the previous block by referring to the previous block’s hash. We suggested using a blockchain similar to the bitcoin in our proposed model, as shown in Fig. 1. It contains several blocks, timestamp, previous block hash value, and Merkle tree root. In our proposed model, the distributed authentication server are miners of the blockchain network, the miner of the blockchain network; the miner will issue the next block. Generally, if the miner wants to create a new node, he must complete some PoW [22], but PoW has always consumed high computational power to check the transaction and add those transactions into a new block. This method is expensive because it costs a lot of energy and money. To overcome this drawback, a new approach was introduced by Scott Nadal, and Sunny King called Proof of Stack (PoS) or Delegated Proof of Stack (DPoS) [9]. These methods select one of the miners randomly to achieve a new block. The PoS and DPoS are more effective methods compared to PoW. In our proposed model, we used the ouroboros model, which is the model of PoS [22], which is provable and secure. It is used as a consensus system to enter a new block of transactions in the blockchain network. Blockchains are found to consume exorbitant amount of energy because of the algorithm used in PoW. The ouroboros can manage thousands of transactions in seconds and reduce energy consumption compared to PoW. When a vehicle requests registration to the authentication server, the DAS node must check the vehicle information specified in Fig. 2. Following the successful verification, the blockchain node will enter the transaction into the blockchain network, and the entire nodes will create a new block through the Ouroboros algorithm. Whenever a vehicle wants to access the authentication system to get authorized in the network, the DAS will cross-check the transactions in the blockchain ledger and update the new access in the blockchain network. The architecture of the proposed method is illustrated in Fig. 1; using the Road-Side Unit (RSU), Infrastructure, and different sensors vehicle can communicate with the distributed authentication server.
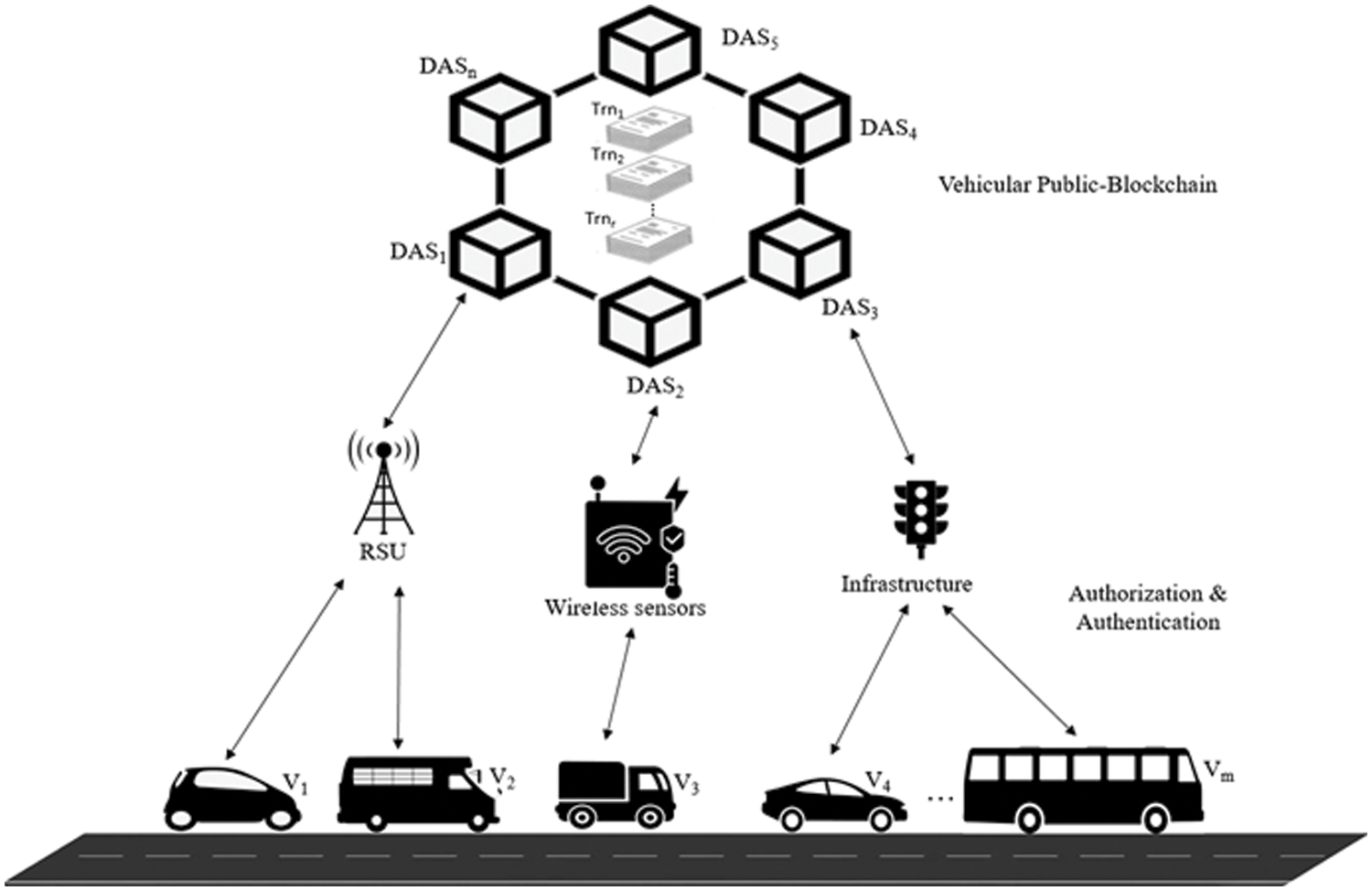
Figure 1: Blockchain based distributed authentication server architecture
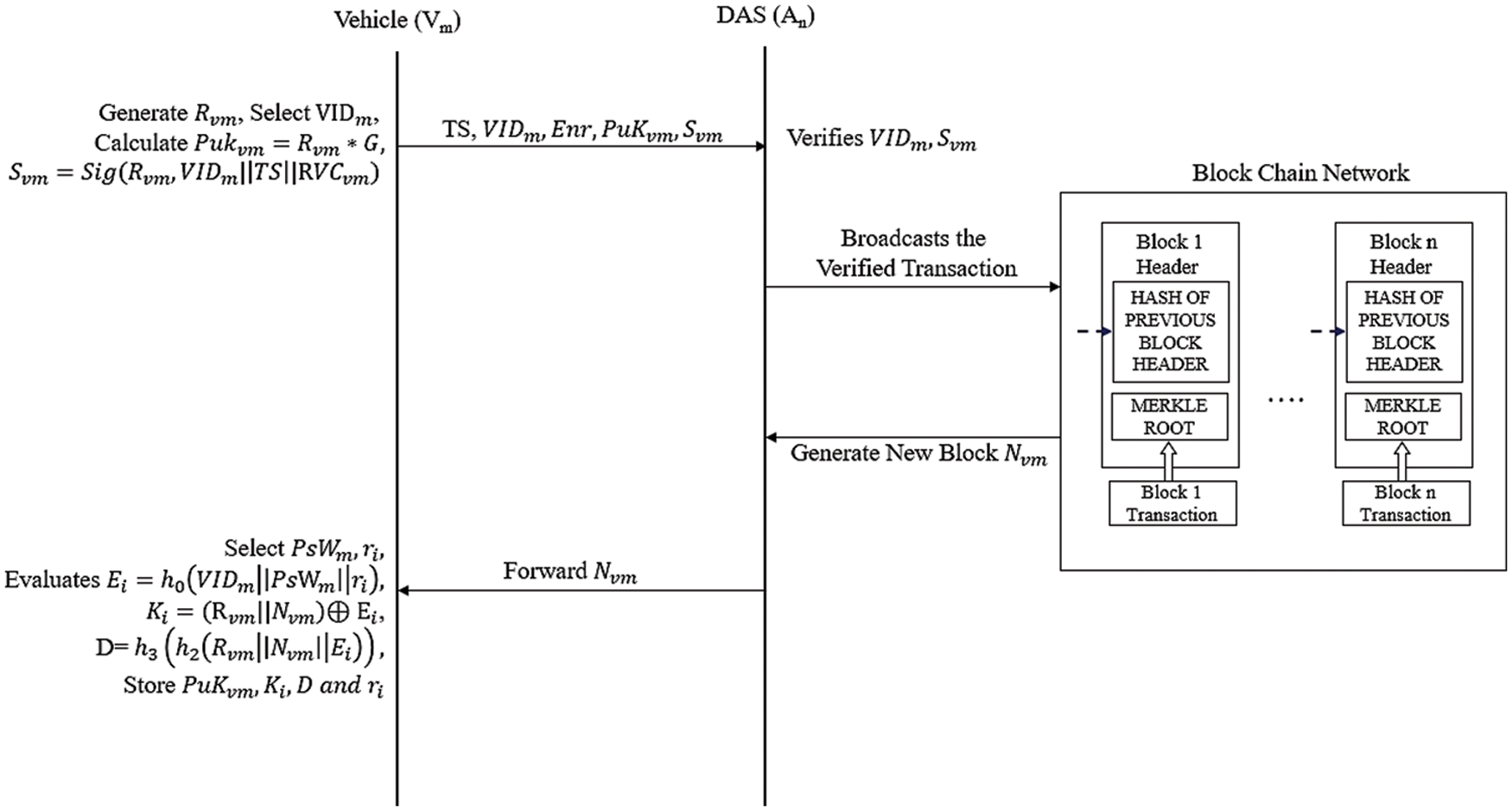
Figure 2: Sequence diagram of vehicle enrollment phase
The architecture of the proposed model is shown in Fig. 1. The
1. Low level formatting
2. Vehicle Enrollment
3. Two-way Authentication
4. Revocability
In the proposed system there are
When a vehicle
Step 1: A Vehicle
Step 2: After getting the message,
Step 3: Once the message is received by the vehicle
If the vehicle wants to authenticate in the network, the vehicle needs to succuss the two-way authentication with the nodes. As shown in Fig. 3, the process of two-way authentication is explained as follows.
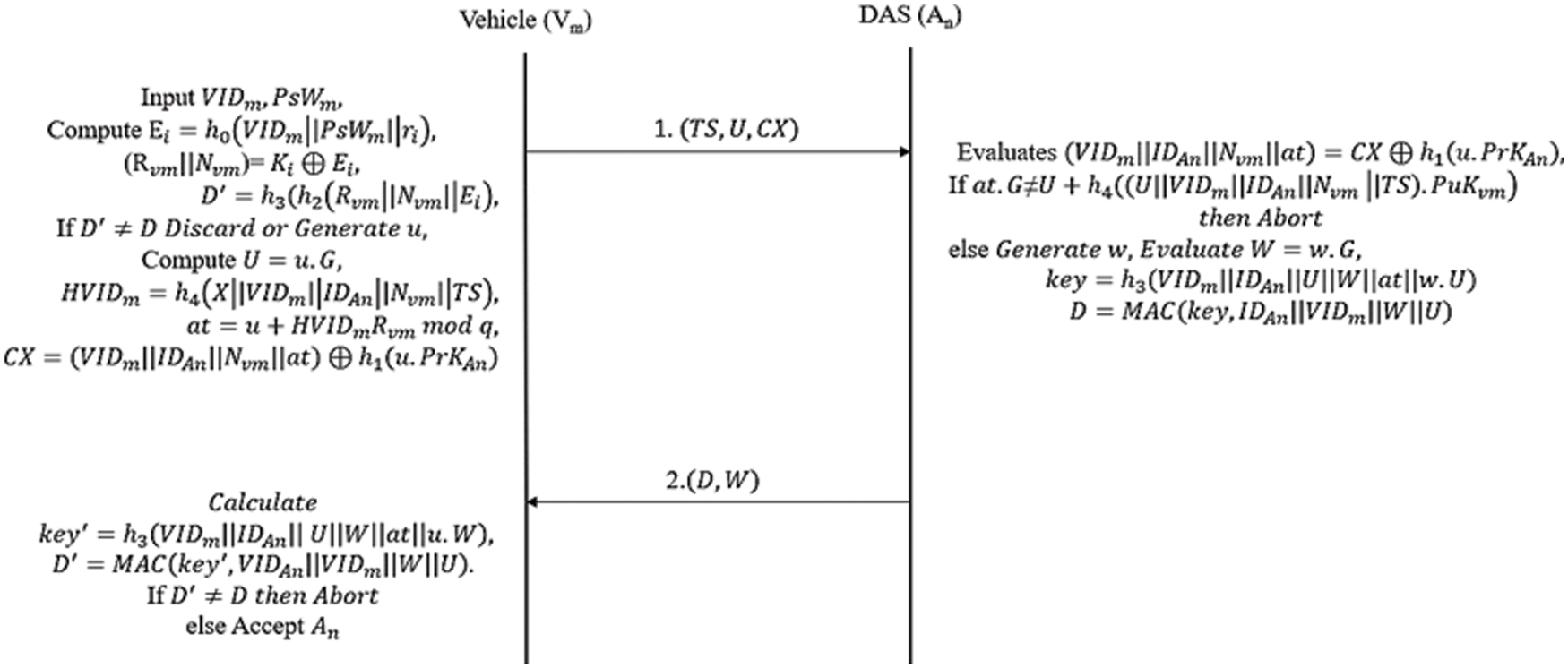
Figure 3: Sequence diagram of two-way authentication phase
Step 1: The vehicle
Step 2: Once
Condition 1:
Condition 2: Revocation status of the
Condition 3: The blocks
Step 3: After getting the message
The procedure of the revocability phase is explained in this section. When the vehicle’s smartcard is lost, stolen the system should have to remove the account and re-register it to the authentication server. The process of revocability is explained as follows,
Step1: The vehicle
Step 2: Based on the acknowledgement of the message, the authentication node
This section explains the security analysis of the proposed method and how it meets the security requirements. The Low-level formatting phase, the Vehicle Enrollment phase, will be performed in the protected channel. The proposed system may endure security threads in the two-way authentication stage. Hence, we explain the security of the two-way authentication phase in this section. We proposed a security mechanism based on the work of Yu et al. [23] and Goldwasser et al. [23–26]. The security model of our system is designed by an adversary
1.
2.
3.
4.
There are 2 corrupt queries,
1.
2.
Definition 1: Similar sessions: The session of the instance vehicle
Definition 2: Authentication protocol: The following properties should be held to say authentication protocol is secure,
The probability of
The probability of
Initially, we discuss two mathematical challenges to analyze our proposed protocol as follows,
Definition 3: Discrete logarithmic problem (DLP): Say
Theorem 1: Secure authentication of Vehicle: In our system, if hash function
Proof: Let assume that
1.
2.
A) If
B) If
3.
4.
5.
6.
7.
8.
As per the queries, if
The turing machine γ evaluates
where
Theorem 2: Secure Authentication of
Proof: Let assume, the legal
A challenger and a MAC server
1. The challenger can send two messages
2. The
3. The challenger can win the game by guessing the value of
The γ imitate the atmosphere of the method which is identical from the actual proposed method to the
1.
2.
A) If
B) If
3.
4.
5.
6.
Based on above queries, if the
According to the above equation, the
Theorem 3: The proposed method will be a secure protocol, if it follows the below condition,
1.
2. Hash
3. The Discrete probability problem is hard.
Proof: According to theorem 1 and 2, we understand the legal
6 Formal Security Verification Using AVISPA
We analyze the security of the proposed framework by using AVISPA tool simulation against the reply attack and MIM attack. The AVISPA toolset uses the “High-Language Protocol Specification Language” (HLPSL) language for specifying cryptographic protocols [28]. HLPSL specifications are translated into equivalent IF specifications by the HLPSL2IF translator. The current version of the tool integrates the four back-ends as follows, On-the-fly Model-Checker (OFMC), Constraint-Logic-based Attack Searcher (CL-AtSe), SAT-based Model-Checker (SATMC), Tree Automata based on Automatic Approximations (TA4SP). To analyze the security of our proposed system, we used the rule-oriented HLPSL. More details about HLPSL and AVISPA toolset specifications are explained in [28,29]. Various roles for the vehicle
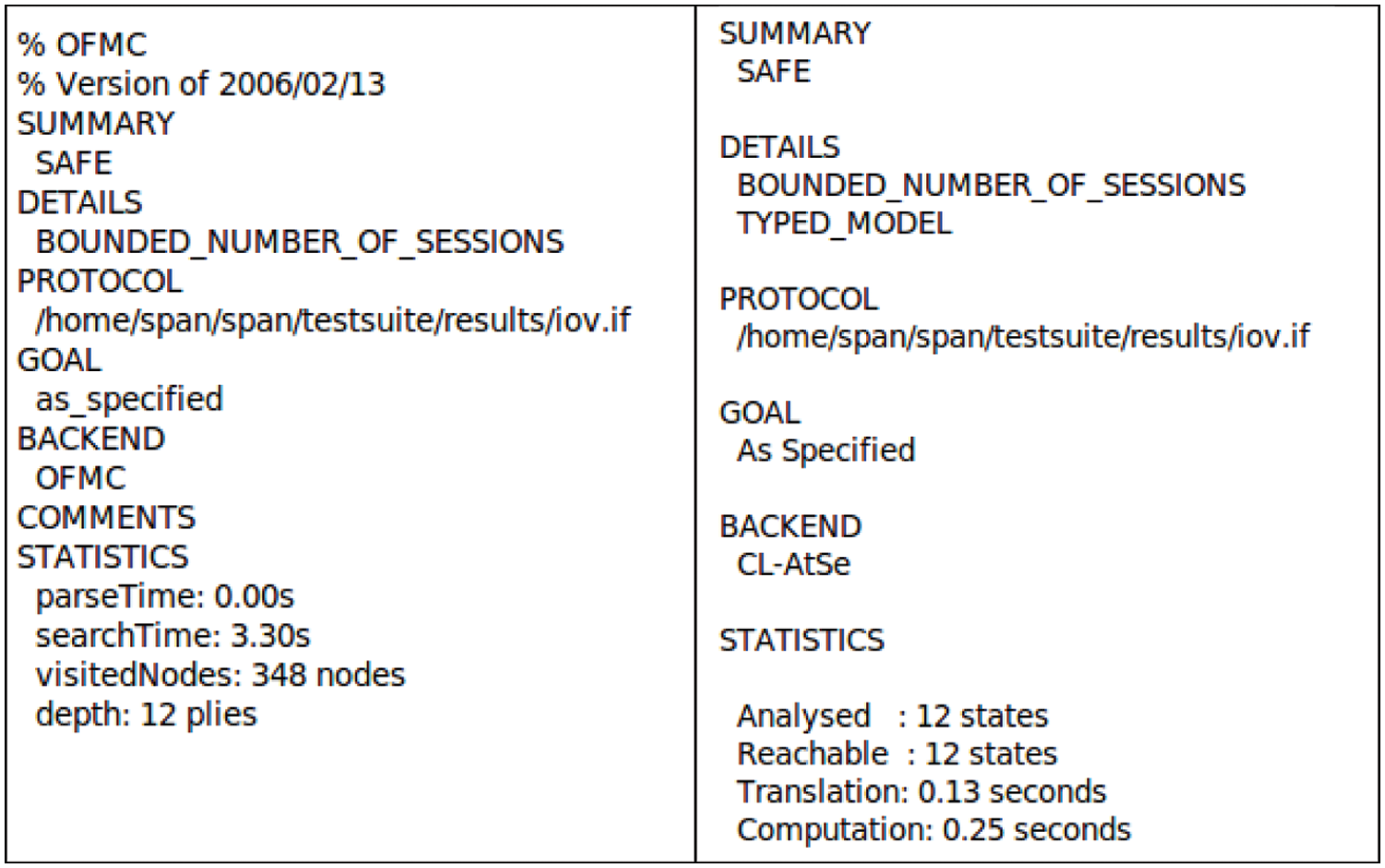
Figure 4: Simulation results of AVISPA
• Mutual Authentication. Based On theorem 1, if DLP problem is hard and MAC is an ideally random function, then we can determine that there will be no polynomial adversary that can be able to cast a legitimate
• Impersonate Attack. An impersonation attack is an attack in which an adversary successfully assumes the identity of one of the legal nodes in a system or a communication protocol [30] . In our proposed method, if the adversary
• Man-in-Middle Attack. In this attack, the Intruder secretly communicates and probably alters the communications among two nodes who believe that they are directly communicating with each other, as the Intruder has injected themselves between the two nodes [31]. In our proposed method, the message transferred between legitimate
• Server Spoofing Attack. Spoofing is the act of disguising a communication from an unknown source as being from a known, trusted source [32–35]. According to theorem 1, without the private key of the legitimate user or authentication node, no polynomial adversary can cast the message. In our proposed method, the
• Repeat Attack. A repeat attack is when the intruder records a communication session and replays the entire session, or some portion of the session, at a later on [36]. We prevent the repeat attack by using the challenge and response method in our proposed way. We are using two random numbers u and
• Untraceable and Anonymity. The vehicle’s identity
• Poison block attack. A poison block attack, sometimes referred to as a ‘big block attack’ is where a malicious miner will create a huge block that takes smaller miners with less hash power a long time to validate. In the proposed system the blockchain ledger only can be accessed by the DAS. So, there are no worries about the malicious miner in the blockchain network.
• Wrong credential access. In our proposed method, we used a password verification model
8 Performance and Comparison Analysis
In this section to calculate the Comparison analysis of “security characteristics” and “communication cost” of the proposed method we have utilized the related studies [12,13], [16,17].
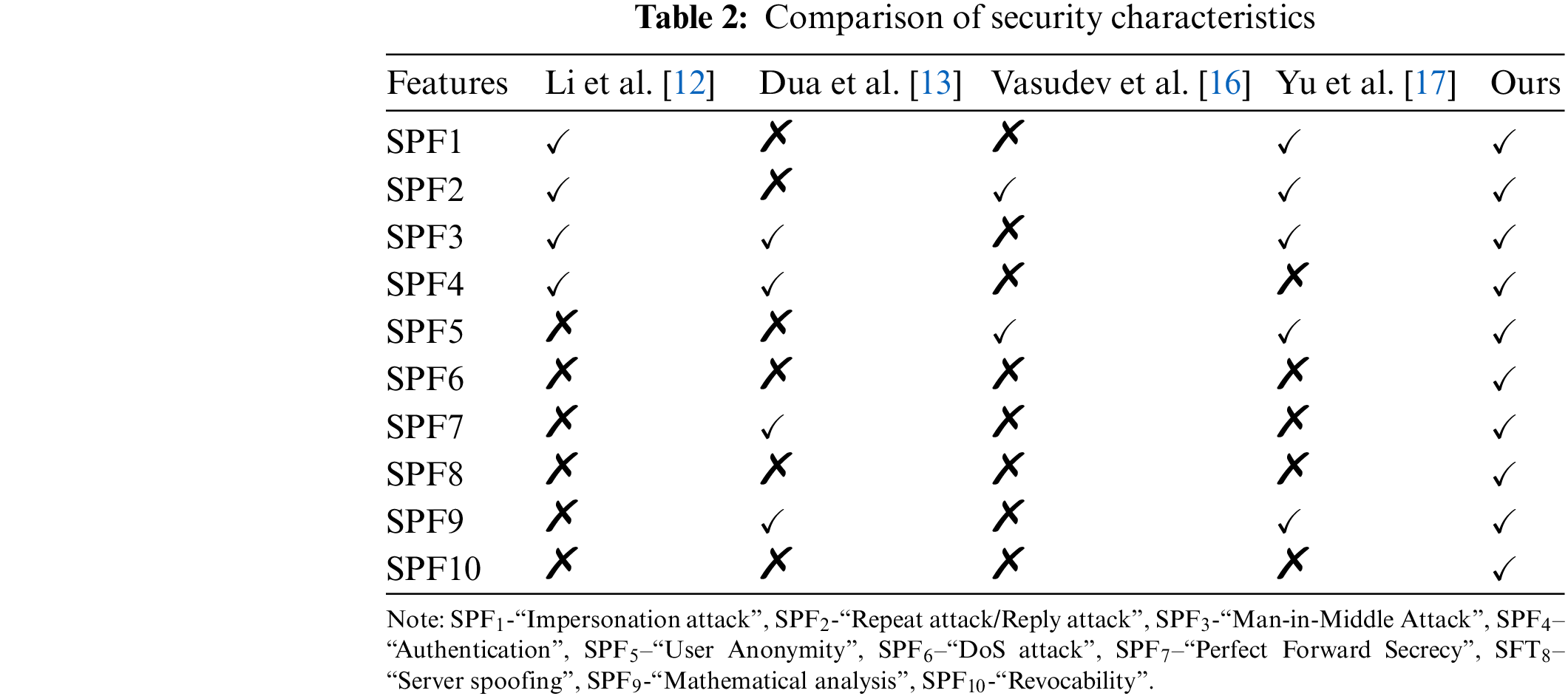
In Tab. 2, we presented the security characteristics comparison of our proposed model with the related studies [12,13], [16,17]. By referring to Tab. 2, the existing schemes [12,13], [16,17] are endured various security attacks. Same time the related methods cannot provide authentication and anonymity in various cases. The proposed model for distributed authentication method prevents various security attacks and provides a revocability feature for lost vehicles.
We analyzed the storage costs of the proposed system with existing schemes [12,13], [16,17] According to [11], we estimate that the bit-lengths of the timestamp (
We compared the computation cost of our proposed framework with the related works [12,13], [16,17] during the authentication. We estimated the following parameter values based on the Vasudev et al. [16] analysis method.
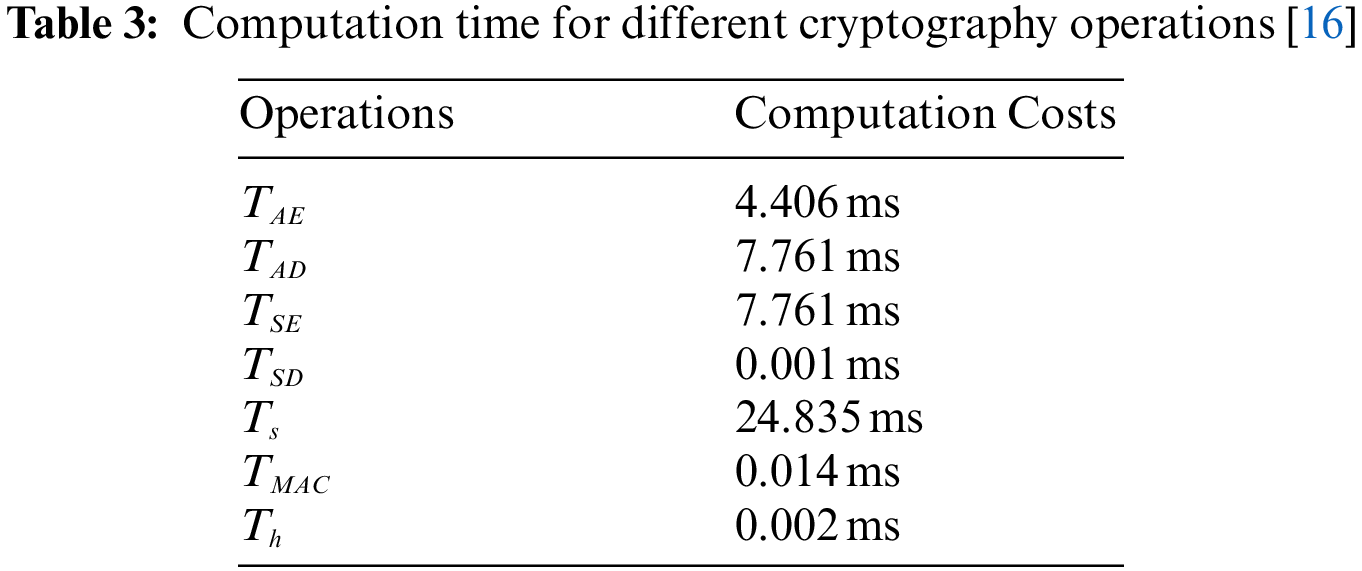
The computation time of the various cryptography operation in Tab. 3 is calculated based on the following desktop configuration, “Windows 10. Professional with an Intel (R) Core (TM) CPU i5–7200U, 8.1GB memory, @2.50 GHz” [16].
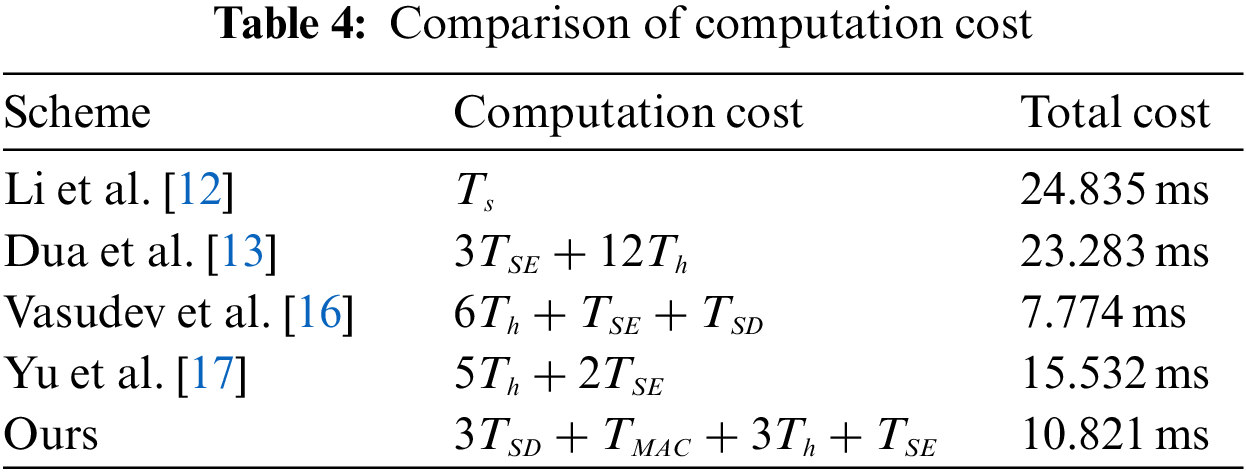
The total computation cost of the related works and our proposed model are compared in Tab. 4. The total computation costs of the proposed framework and Vasudev et al.’s scheme [16] are 10.821 ms and 7.774 ms. Even though Vasudev et al.’s scheme has a minimum computation cost, many attacks still affect it, as demonstrated by Yu et al. [17] So, compared to that method, our proposed model has a better computation cost with strong security.
We have calculated the communication cost of the proposed framework with the related studies [12,13], [16,17]. To calculate a convincing comparison, we assumed that the bit length of timestamp, the block size of symmetric encryption, the block size of symmetric decryption, hash output, identity, the number of blocks, random number, and signature are 32 bits, 128 bits, 128 bits, 32 bits, 180 bits, 32 bits, 320 bits respectively. The bit length of the elliptic curve for digital signature is 160 bits, and the exponentiation is 1024 bits. The communication efficiency comparison is discussed in Tab. 5. [43,44].
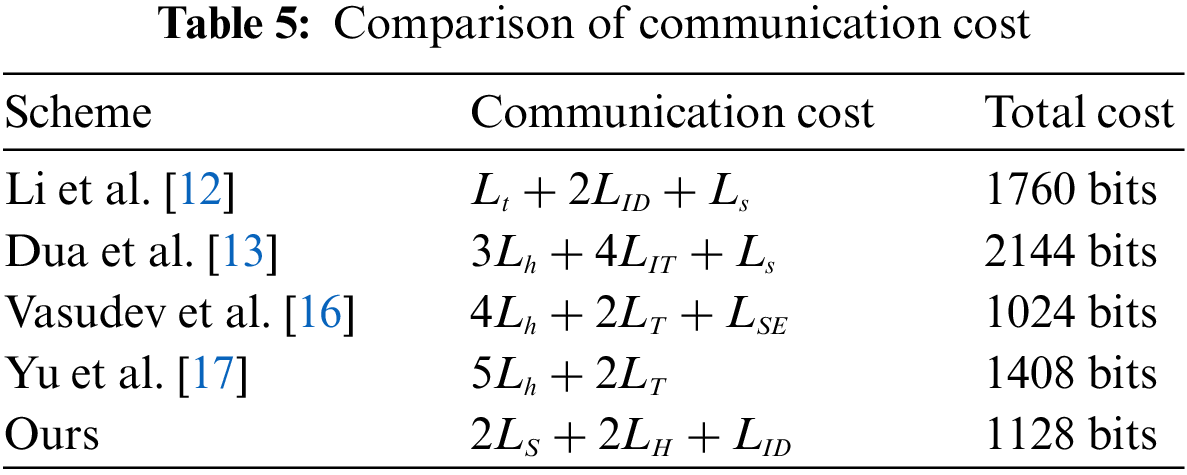
In the proposed method, the initial message
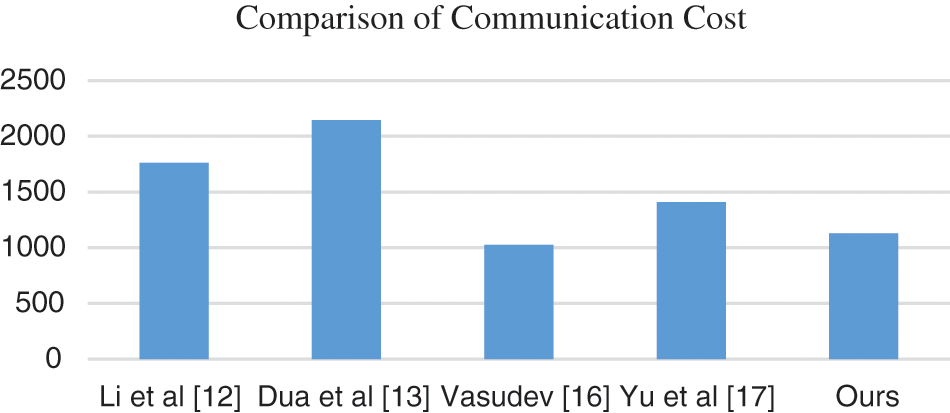
Figure 5: Graph for comparison of communication cost
Vasudev et al. [16] has the lowest communication cost, but it is affected by many attacks as demonstrated by Yu et al. [17]. In the security and communication cost wise the proposed model has efficient results, and it has the potential to implement in real time.
In this research, we proposed a distributed authentication mechanism for IoV environment based on blockchain technology with an ouroboros algorithm that protects the system from various security attacks such as man-in-middle attack, DDoS attack, server spoofing attack and provide a solution for single-point failure, forward secrecy, revocability, etc. The formal and informal security analysis proves that our proposed method is secure the random oracle model. The performance analysis demonstrates that the proposed model has high communication efficiency, which will be suitable for real time IoV environment.
Acknowledgement: This work was supported in part by the Ministry of Science and Technology, Taiwan, through grant MOST 110–2622-E-468–002 and 110–2218-E-468–001-MBK. The authors also gratefully acknowledge the helpful comments and suggestions of the Editor and anonymous reviewers, which have improved the presentation of this paper.
Funding Statement: This work was supported by the Ministry of Science and Technology of Taiwan, R.O.C., under Grant MOST 110–2622-E-468–002 and 110–2218-E-468–001-MBK.
Conflicts of Interest: The authors declare that they have no conflicts of interest to report regarding the present study.
References
1. H. Stipp, “Number of IoT devices 2015–2025,” Statista, https://www.statista.com/statistics/471264/iot-number-of-connected-devices-worldwide/ (accessed Apr. 08, 2022). [Google Scholar]
2. A. Hbaieb, S. Ayed and L. Chaari, “A survey of trust management is the internet of vehicles,” Computer Networks: The International Journal of Computer and Telecommunications Networking, vol. 203, no. C, pp. 108558, 2022. [Google Scholar]
3. H. Chiroma, S. M. Abdulhamid, I. A. T. Hashem, K. S. Adewole, A. E. Ezugwu et al., “Deep learning-based big data analytics for internet of vehicles: Taxonomy, challenges, and research directions,” Mathematical Problems in Engineering, vol. 202, no. 12, pp. 20, 2021. [Google Scholar]
4. J. Wang, K. Zhu and E. Hossain, “Green internet of vehicles (IOV) in the 6 G era: Toward sustainable vehicular communications and networking,” IEEE Transactions on Green Communications and Networking, vol. 6, no. 1, pp. 391–423, 2022. [Google Scholar]
5. S. Abbas, M. A. Talib, A. Ahmed, F. Khan, S. Ahmad et al., “Blockchain-based authentication in internet of vehicles: A survey,” Sensors, vol. 21, no. 23, pp. 23, 2021. [Google Scholar]
6. Y. Sun, L. Wu, S. Wu, S. Li, T. Zhang et al., “Security and privacy in the internet of vehicles,” in Int. Conf. on Identification, Information, and Knowledge in the Internet of Things (IIKI), Beijing, China, vol.21, no.5, pp. 116–121, 2015. [Google Scholar]
7. M. K. Priyan and G. U. Devi, “A survey on internet of vehicles: Applications, technologies, challenges and opportunities,” International Journal of Advanced Intelligence Paradigms, vol. 12, no. 1/2, pp. 98, 2019. [Google Scholar]
8. J. Lauinger, “Identity management in internet of vehicles based on distributed ledger technology,” NIoVe, 2021. [Online]. Available: https://www.niove.eu/index.php/blogs/identity-management-in-internet-of-vehicles-based-on-distributed-ledger-technology (accessed Mar. 19, 2022). [Google Scholar]
9. A. Monrat, K. Andersson and O. Schelén, “A survey of blockchain from the perspectives of applications, challenges, and opportunities,” IEEE Access, vol. 1, no. 1, pp. 99, 2019. [Google Scholar]
10. L. Mendiboure, M. A. Chalouf and F. Krief, “Survey on blockchain-based applications in internet of vehicles,” Computers & Electrical Engineering, vol. 84, no. 1, pp. 106646, 2020. [Google Scholar]
11. N. Sharma, N. Chauhan, N. Chand and L. K. Awasthi, “Secure authentication and session key management scheme for internet of vehicles,” Transactions on Emerging Telecommunications Technologies, vol. 6, no. 1, pp. 4451, 2022. [Google Scholar]
12. J. Li, H. Lu and M. Guizani, “ACPN: A novel authentication framework with conditional privacy-preservation and non-repudiation for vanets,” IEEE Transactions on Parallel and Distributed Systems, vol. 26, no. 4, pp. 938–948, 2015. [Google Scholar]
13. A. Dua, N. Kumar, A. K. Das and W. Susilo, “Secure message communication protocol among vehicles in smart city,” IEEE Transactions on Vehicular Technology, vol. 67, no. 5, pp. 4359–4373, 2018. [Google Scholar]
14. B. Ying and A. Nayak, “Anonymous and lightweight authentication for secure vehicular networks,” IEEE Transactions on Vehicular Technology, vol. 66, no. 12, pp. 10626–10636, 2017. [Google Scholar]
15. C. -M. Chen, B. Xiang, Y. Liu and K. -H. Wang, “A secure authentication protocol for internet of vehicles,” IEEE Access: Security and Privacy for Cloud and IOT, vol. 7, no. 1, pp. 12047–12057, 2019. [Google Scholar]
16. H. Vasudev, D. Das and A. V. Vasilakos, “Secure message propagation protocols for IoVs communication components,” Computers and Electrical Engineering, vol. 82, no. 1, pp. 106555, 2020. [Google Scholar]
17. S. Yu, J. Lee, K. Park, A. K. Das and Y. Park, “IoV-SMAP: Secure and efficient message authentication protocol for IOV in smart city environment,” IEEE Access: Towards Smart Cities with IOT Based on Crowdsensing, vol. 8, no. 1, pp. 167875–167886, 2020. [Google Scholar]
18. D. Johnson, A. Menezes and S. Vanstone, “The elliptic curve digital signature algorithm (ECDSA),” International Journal of Information Security, vol. 1, no. 1, pp. 36–63, 2001. [Google Scholar]
19. O. Mir, M. Roland and R. Mayrhofer, “Decentralized, privacy-preserving, single sign-on,” Security and Communication Networks, vol. 2022, no. 8, pp. 983–995, 2022. [Google Scholar]
20. A. Tewari and B. B. Gupta, “Secure timestamp-based mutual authentication protocol for IOT devices using RFID tags,” International Journal on Semantic Web and Information Systems, vol. 16, no. 3, pp. 20–34, 2020. [Google Scholar]
21. J. Wang, W. Chen, Y. Ren, O. Alfarraj and L. Wang, “Blockchain based data storage mechanism in cyber physical system,” Journal of Internet Technology, vol. 21, no. 6, pp. 1681–1689, 2020. [Google Scholar]
22. A. Kiayias, A. Russell, B. David and R. Oliynykov, “Ouroboros: A provably secure proof-of-stake blockchain protocol,” Advances in Cryptology-CRYPTO, vol. 1, no. 2, pp. 357–388, 2017. [Google Scholar]
23. J. Yu, G. Wang, Y. Mu and W. Gao, “An efficient generic framework for three-factor authentication with provably secure instantiation,” IEEE Transactions on Information Forensics and Security, vol. 9, no. 12, pp. 2302–2313, 2014. [Google Scholar]
24. S. Goldwasser, S. Micali and R. L. Rivest, “A digital signature scheme secure against adaptive chosen-message attacks,” SIAM Journal on Computing, vol. 17, no. 2, pp. 281–308, 1988. [Google Scholar]
25. C. L. Stergiou, K. E. Psannis and B. B. Gupta, “IoT-Based big data secure management in the fog over a 6 g wireless network,”. IEEE Internet of Things Journal, vol. 8, no. 7, pp. 5164–5171, 2020. [Google Scholar]
26. M. H. Lim, B. M. Goi and S. Lee, “An analysis of group key agreement schemes based on the bellare-rogaway model in multi-party setting,” KSII Transactions on Internet and Information Systems, vol. 5, no. 1, pp. 822–839, Apr. 2011. [Google Scholar]
27. D. Pointcheval and J. Stern, “Security arguments for digital signatures and blind signatures,” Journal of Cryptology, vol. 13, no. 3, pp. 361–396, 2000. [Google Scholar]
28. A. Armando, D. Basin, Y. Boichut and Y. Chevalier, “The AVISPA tool for the automated validation of internet security protocols and applications,” Lecture Notes in Computer Science, vol. 3576, no. 1, pp. 135–165, 2005. [Google Scholar]
29. G. Thomas, “SPAN: A security protocol animator for AVISPA,” [Online]. Available: http://www.avispa-project.org. (Accessed May. 15, 2022). [Google Scholar]
30. C. Adams and V. Tilborg, “Impersonation Attack,” in Encyclopedia of Cryptography and Security, vol. 1. Boston, MA: Springer US, pp. 286–286, 2005. [Google Scholar]
31. E. D. Knapp and J. T. Langill, “Chapter 7-Hacking industrial control systems,” in Industrial Network Security, 2nd ed., vol. 1,. Boston: Syngress, pp. 171–207, 2015. [Google Scholar]
32. M. Gregg, “Chapter 4-Layer 3: The network layer,” in Hack the Stack, vol. 1. Burlington: Syngress, pp. 103–150, 2006. [Google Scholar]
33. C. Adams, “Replay attack,” in Encyclopedia of Cryptography and Security, vol. 4, Boston, MA: Springer US, pp. 1042–1042, 2011. [Google Scholar]
34. J. Wang, B. Wei, J. Zhang, X. Yu and P. K. Sharma, “An optimized transaction verification method for trustworthy blockchain-enabled IIoT,” Ad Hoc Networks, vol. 119, no. 1, pp. 102526, 2021. [Google Scholar]
35. J. Y. Zhang, S. Q. Zhong, T. Wang, H. C. Chao and J. Wang, “Blockchain-based systems and applications: A survey,” Journal of Internet Technology, vol. 21, no. 1, pp. 1–14, 2020. [Google Scholar]
36. J. Zhang, S. Zhong, J. Wang, X. Yu and O. Alfarraj, “A storage optimization scheme for blockchain transaction databases,” Computer Systems Science and Engineering, vol. 36, no. 3, pp. 521–535, 2021. [Google Scholar]
37. Z. Xu, W. Liang, K. C. Li, J. Xu and H. Jin, “A Blockchain-based roadside unit-assisted authentication and key agreement protocol for internet of vehicles,” Journal of Parallel and Distributed Computing, vol. 149, pp. 29–39, 2021. [Google Scholar]
38. W. Sun, G. C. Zhang, X. R. Zhang, X. Zhang and N. N. Ge, “Fine-grained vehicle type classification using lightweight convolutional neural network with feature optimization and joint learning strategy,” Multimedia Tools and Applications, vol. 80, no. 20, pp. 30803–30816, 2021. [Google Scholar]
39. W. Sun, X. Chen, X. R. Zhang, G. Z. Dai, P. S. Chang et al., “A multi-feature learning model with enhanced local attention for vehicle re-identification,” Computers, Materials & Continua, vol. 69, no. 3, pp. 3549–3561, 2021. [Google Scholar]
40. K. Alieyan, A. Almomani, M. Anbar, M. Alauthman, R. Abdullah et al., “DNS Rule-based schema to botnet detection,” Enterprise Information Systems, vol. 15, no. 4, pp. 545–564, 2021. [Google Scholar]
41. I. Cvitić, D. Perakovic, B. B. Gupta and K. R. Choo, “Boosting-based DDOS detection in internet of things systems,” IEEE Internet of Things Journal, vol. 1, no. 1, pp. 1–1. 2021. [Google Scholar]
42. A. Dahiya and B. B. Gupta, “A reputation score policy and Bayesian game theory based incentivized mechanism for DDoS attacks mitigation and cyber defense,” Future Generation Computer Systems, vol. 117, no. 1, pp. 193–204, 2021. [Google Scholar]
43. A. Tewari and B. B. Gupta, “Security, privacy and trust of different layers in internet-of-things (IoTs) framework,” Future Generation Computer Systems, vol. 108, no. 2, pp. 909–920, 2020. [Google Scholar]
44. Z. Zhou and A. Gaurav, “A fine-grained access control and security approach for intelligent vehicular transport in 6 G communication system,” IEEE Transactions on Intelligent Transportation Systems, vol. 1, no. 3, pp. 23 2021. [Google Scholar]
 | This work is licensed under a Creative Commons Attribution 4.0 International License, which permits unrestricted use, distribution, and reproduction in any medium, provided the original work is properly cited. |