| Computers, Materials & Continua DOI:10.32604/cmc.2022.031417 |  |
| Article |
Generalization of Advanced Encryption Standard Based on Field of Any Characteristic
1Department of Mathematical Sciences, College of Science, Princess Nourah Bint Abdulrahman University, P.O.Box 84428, Riyadh 11671, Saudi Arabia
2Department of Applied Mathematics & Statistics, Institute of Space Technology, Islamabad, Pakistan
3King Abdulaziz City for Science and Technology, Riyadh, Saudi Arabia
4Mathematics Program, Department of Mathematics, Statistics and Physics, College of Arts and Sciences, Qatar University, 2713, Doha, Qatar
5Statistical Consulting Unit, College of Arts and Science, Qatar University, Doha, Qatar
*Corresponding Author: Majid Khan. Email: mk.cfd1@gmail.com
Received: 17 April 2022; Accepted: 15 June 2022
Abstract: Nowadays most communications are done by utilizing digital transmission mechanisms. The security of this digital information transmitted through different communication systems is quite important. The secrecy of digital data is one of the burning topics of the digitally developed world. There exist many traditional algorithms in the literature to provide methods for robust communication. The most important and recent modern block cipher named the advanced encryption standard (AES) is one of the extensively utilized encryption schemes with binary based. AES is a succession of four fundamental steps: round key, sub-byte, shift row, and mix column. In this work, we will provide an innovative methodology for extending the AES in a Galois field with any characteristic p. All four steps in the fundamental process with binary characteristics will be adjusted because of the new enhancement. By applying double affine transformations, we have enhanced the number of options in our suggested substitution boxes. The reconstruction of the nonlinear confusion component and encryption structure provides robustness in the generalized AES. The increase in the keyspace due to the Galois field generalization implies that we have improved additional confusion abilities and broadened the current notions. The implementation of the proposed structure of AES for image, audio, and video encryption will provide high security for secure communication.
Keywords: AES; generalized AES; binary field; ternary function
It is critical to keep secret multimedia material out of the hands of unauthorized parties. Content, music, still images, liveliness, and video are all examples of the interactive media material. Multimedia security is used to protect these compounds. This is done using cryptographic techniques. These plans foster communication security, robbery, and refugee protection. Encryption is made more difficult by image size [1]. Typically, a typical photograph is of a large scale. Encryption of large amounts of mixed media data will be difficult if a standard encryption technique is used [2]. Due to the large amount of data that must be encrypted, we need to use techniques that demand a minimal amount of computation [3]. Privacy of data is also concerned with the authentication of the source [4,5]. Authentication is provided by some hashing and signature schemes [6,7]. Many encryption structures are protected by digital signature schemes [8]. Numerous studies show the importance of digital signature implementation [9–11]. Digital signatures work on the structure of the asymmetric encryption phenomenon [12]. In comparison to asymmetric key algorithms, private key methods are computationally less genuine. Asymmetric key algorithms are often thousands of times quicker than public-key algorithms [13]. Symmetric key encryption methods provide a more acceptable approach to scrambling interactive media content [14]. It is because of this that the AES symmetric key encryption approach is so fast [15]. In the literature, several novel AES enhancements have been presented [16–19]. In the symmetric block cipher family, the AES is one of the most important, with a key of 128 bits. Typically, the total round in AES is determined by one of three sizes of the secret key utilized in several variations: 128 bits, 192 bits, and 256 bits (10, 12 & 14). A new extension of current AES structures on any characteristic Galois field is our major goal here. Brute-force assaults on encrypted data have been bolstered by the removal of the field of generic prime features [20]. We have added two examples for ternary and quinary finite fields [21,22].
There are four sections in this research article. The basic notions are discussed in segment 2. The suggested scheme along with examples is now discussed in Section 3. Lastly, we have concluded the section.
A Galois field is a finite field with finite order. The Galois field has an order of prime or an exponent of prime,
Now we describe the structure of
As in
The elements of
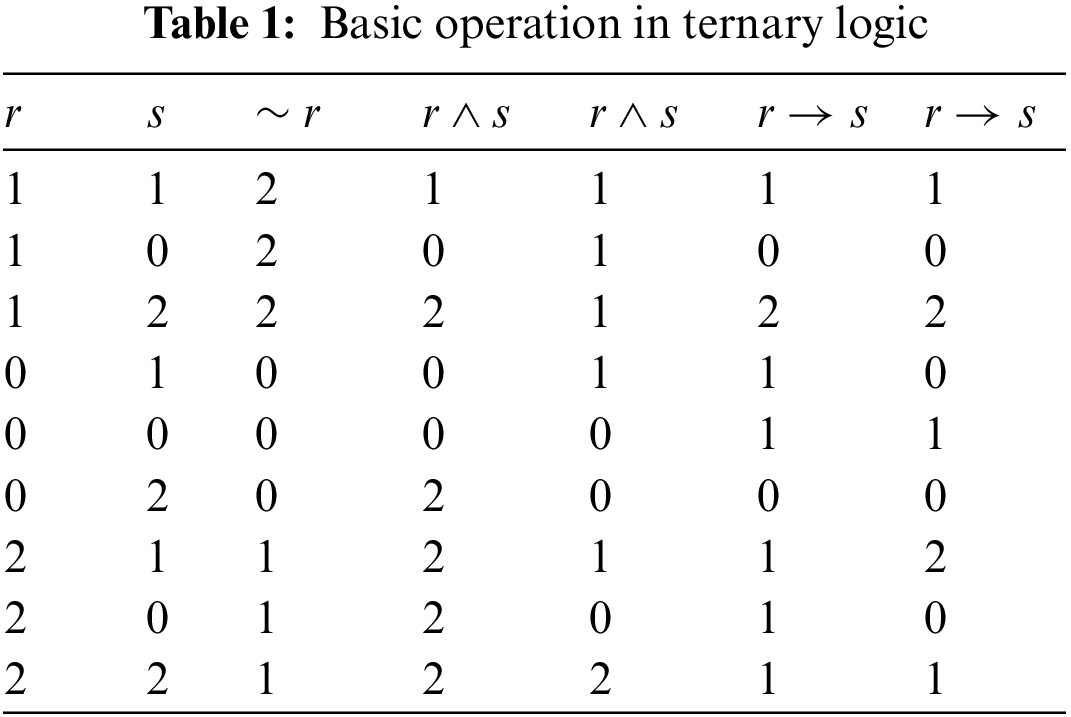
There are three sets of assertions or propositions that we will refer to as ternary logic
Consider, if
• Implication
• Negation
• Conjunction
• Disjunction
The system
The outcomes in Tab. 1 are
Unary functions are defined as those in which there is only one solution, and this is the case when n is equal to one. There are
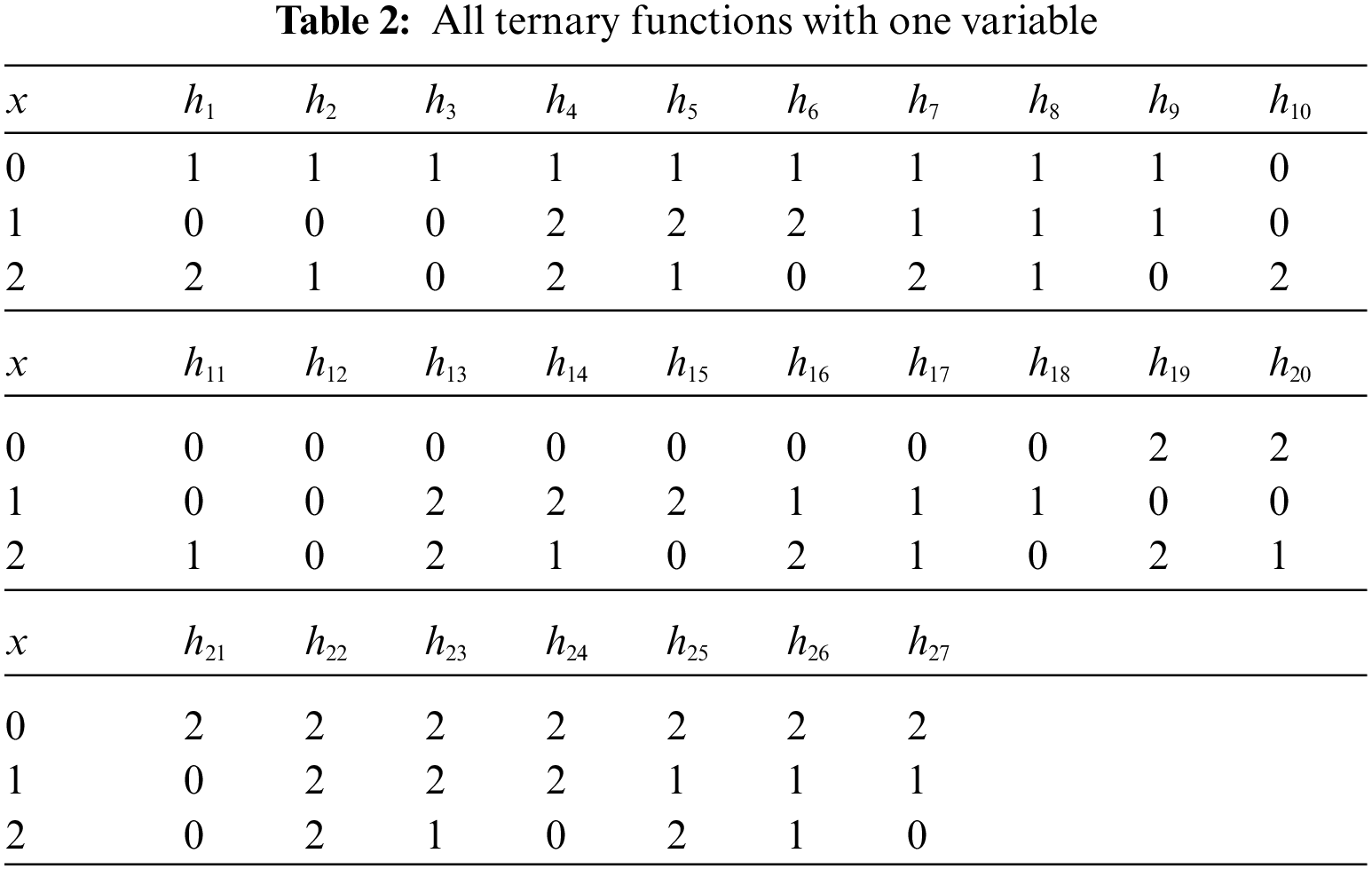
By utilizing this process, we can calculate
An affine transformation
where L is the linear transformation, M is the inverse transformation, and G is the affine transformation, which can be stated mathematically as follows:
As a result, S-box structure is described as
This is the required structure for the S-Box design created on
S-box is the main non-linear component of the block cipher, which increase the confusion in the algorithm, therefore it must be strong and highly resistant to cryptanalytic attacks. Here we define a new approach to constructing a strong Substitution box. We define a map
where
2.5 Advanced Encryption Standard
In the context of symmetric algorithms, AES is referred to as a “block cipher.” Commercial systems, such as Microsoft’s Windows, use it regularly (IPsec, the internet Skype, the IEEE 802.11i, and TLS). AES is referred to as AES-128, AES-192, or AES-256 depending on the size of the key employed in the encryption of the information being protected. Depending on the size of the key, the data matrix has 10, 12, or 14 rounds.
3 Generalization of AES on Ternary Logic Function and Double Affine Transformation
Other than binary qualities, we’ve mostly made use of the extension field in this section. To begin, we must expand the block cipher’s nonlinear S-box component to include features 3 and 5, as well as shift row, mix column, and round key. Here we define AES on the plaintext and key of 8-rits with two rounds of encryption, but in general, we can use the desired length of key and plaintext. The round of encryption can also be increased. The working strides of the proposed generalized AES are shown in Fig. 1.
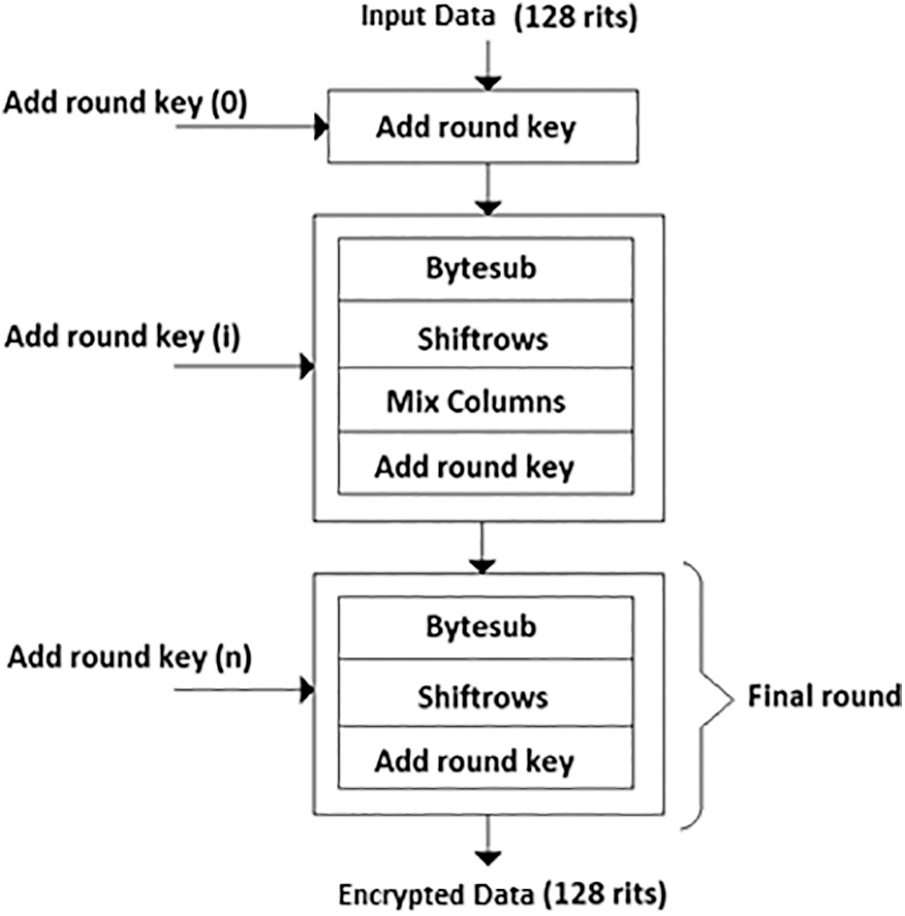
Figure 1: Working strides of proposed generalized AES
3.1 Structure of S-box Created on
A substitution box can be constructed by using the map
where I represents the inverse transformation and the symbol
The S-box changes to the following value when input values are inserted into the expression (see Tab. 3):
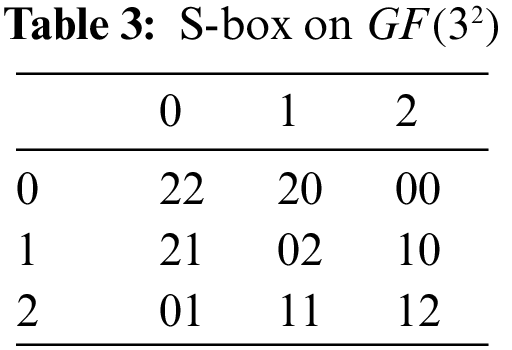
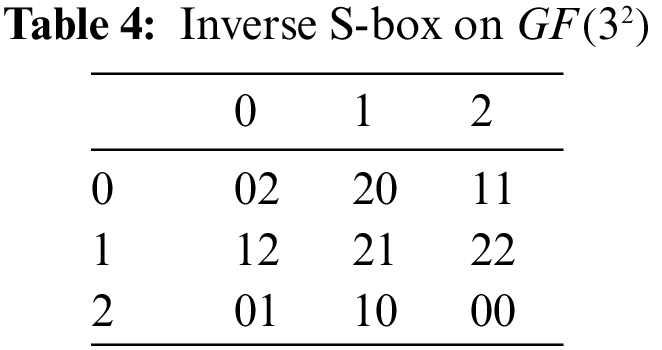
The inverse S-box, as shown in the Tab. 4, can be obtained by applying the inverse transformation.
Suppose the plaintext of 8-rits be
Now we divide this 8-rits plaintext into 4 parts, each consisting of 2-rits
The following matrix can be used to represent the simple text:
Assume the key be of equal length as plaintext i.e., 8-rits
The following is a matrix representation of the key:
First, we add a key matrix in the plaintext matrix
Round 1
Sub-byte Transformation
The first step is to do the sub-byte conversion to each element of the matrix
Shift Row
After shifting the components in the matrix
Mix Column
Consider a matrix for the mix column’s operation.
By successively multiplying the X matrix by the
In the end, when we combine these two columns into a single matrix, we obtain
Key Generation
By using the recent key
Therefore, the key becomes
Key Addition
By adding the key
Round 2
Sub-byte transformation
We obtain the following as the matrix
Shift Row
Shift row is applied to the matrix
Mix Column
There is no mix column in the last round
Key Generation
The following procedure can be used to produce the key:
Therefore, the key becomes
Key Addition
The encrypted message is
Decryption
The encrypted data can be decrypted by utilizing the reverse process of encryption.
Round 1
Key subtraction
For decryption, the key matrix
Inverse Shift Row
After key subtraction inverse shift row is applied to the matrix
Inverse Sub-byte Transformation
After applying inverse shift row, inverse sub-byte transformation is applied by using inverse S-box
Round 2
Key Subtraction
Now we subtract the key of round 2 i.e.,
Inverse Mix Column
In the inverse mix column, we take the inverse of the matrix
After multiplying the columns of the matrix
After putting these columns together in a matrix,
Inverse Shift Row
After utilizing the inverse shift row on the matrix, which is obtained after the inverse mix column,
Inverse Sub-byte Transformation
After utilizing inverse Sub-byte transformation by using inverse S-box, we get
Key Subtraction
Finally, we subtract the initial key from the matrix
Finally, the recovered message is
3.3 Construction of S-box
A substitution box can be constructed by using the map
where I represents the inverse transformation and the symbol
Now consider the matrices for this expression be
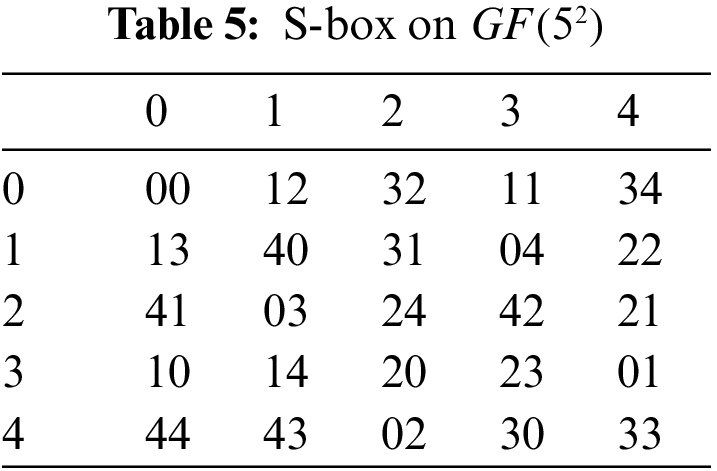
As a result, we acquire output values by adding input values into the above formula, the required S-box is given in Tab. 5.
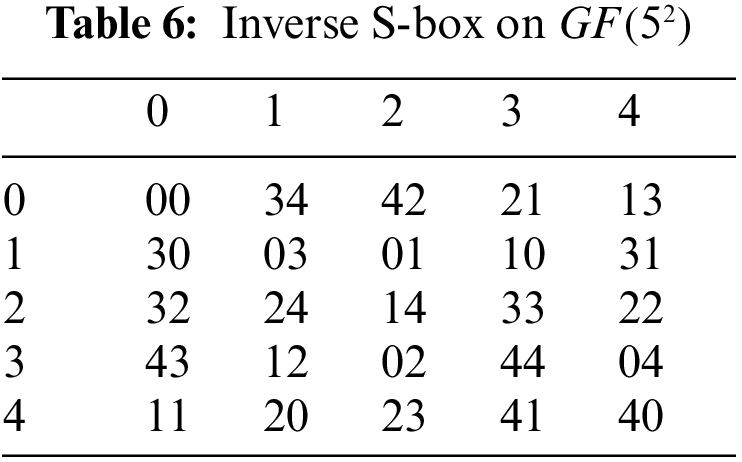
The inverse S-box is shown below in Tab. 6.
Consider the plaintext of 8-rits be
Now we divide this 8-rits plaintext into 4 parts, each consisting of 2-rits
The following is a matrix representation of the plain text
Assume the key be of equal length as plaintext i.e., 8-rits
Using the matrix form, the key may be expressed as follows:
First, we add a key matrix in the plaintext matrix
Round 1
Sub-byte Transformation
Initially, we utilize the S-box transformation to all components of the matrix
Shift Row
After employing the shift row to the components of the matrix
Mix Column
Consider a matrix for the mix column’s operation.
This is the result of multiplying each column of the matrix
Combining these two columns into one matrix yields the following result:
Key Generation
By using the recent key
Therefore, the key becomes
Key Addition
By adding the key
Round 2
Sub-byte transformation
We obtain the following as the matrix
Shift Row
By implementing shift row on the matrix
Mix Column
In the last round, there is no mix column.
Key Generation
Keys can be produced in the following way:
Therefore, the key becomes
Key Addition
The encrypted message is
Decryption
The encrypted text can be decrypted by utilizing the reverse process of encryption.
Round 1
Key Subtraction
For decryption, the key matrix
Inverse Shift Row
After key subtraction inverse shift row is applied to the matrix
Inverse Sub-byte Transformation
After applying inverse shift row, inverse sub-byte transformation is applied by using inverse S-box
Round 2
Key subtraction
Now we subtract the key of round 2 i.e.,
Inverse Mix Column
In the inverse mix column, we take the inverse of the matrix
After multiplying the columns of the matrix
After combining these columns in one matrix
Inverse Shift Row
After utilizing the inverse shift row on the matrix, which is obtained after the inverse mix column,
Inverse Sub-byte Transformation
After employing inverse Sub-byte transformation by using inverse S-box, we get
Key Subtraction
Finally, we subtract the initial key from the matrix
Finally, the recovered message is
In this paper, we have defined a generalization of AES which gives better results to increase the security of the algorithm. This modifies AES as a complex mathematical structure which is utilizing the composition of two affine nonlinear functions instead of one affine Boolean function as in the case of standard AES. Moreover, the use of different characteristics other than the binary is one of the thought-provoking problems of cryptography. As a result, brute force attacks fail on the modified AES due to increasing the number of possibilities to find the key. The use of ternary and quinary characteristic finite field is yet not used in the development of AES structure. We have utilized ternary and quinary characteristic fields to design a new mathematical foundation for modified AES. The implementation of the generalized AES on hardware is one of the challenging problems for future interests. The designed structure can be utilized for audio and video encryption as well.
Acknowledgement: This research was funded by Princess Nourah bint Abdulrahman University Researchers Supporting Project Number (PNURSP2022R87), Princess Nourah bint Abdulrahman University, Riyadh, Saudi Arabia.
Funding Statement: This research was funded by Princess Nourah bint Abdulrahman University Researchers Supporting Project Number (PNURSP2022R87), Princess Nourah bint Abdulrahman University, Riyadh, Saudi Arabia.
Conflicts of Interest: The authors declare that they have no conflicts of interest to report regarding the present study.
References
1. A. M. Shtewi, “An efficient modified advanced encryption standard (MAES) adapted for image cryptosystems,” International Journal of Computer Science and Network Security, vol. 10, pp. 226–2232, 2010. [Google Scholar]
2. S. Lian, “Quasi-commutative watermarking and encryption for secure media content distribution,” Multimedia Tools and Applications, vol. 43, pp. 91–107, 2009. [Google Scholar]
3. K. Gu, W. J. Jia and J. M. Zhang, “Identity-based multi-proxy signature scheme in the standard model,” Fundamenta Informaticae, vol. 150, no. 2, pp. 179–210, 2017. [Google Scholar]
4. K. Gu, W. J. Jia, G. J. Wang and S. Wen, “Efficient and secure attribute-based signature for monotone predicates,” Acta Informatica, vol. 54, no. 5, pp. 521–541, 2017. [Google Scholar]
5. K. Gu, K. M. Wang and L. L. Yang, “Traceable attribute-based signature,” Journal of Information Security and Applications, vol. 49, pp. 102400, 2019. [Google Scholar]
6. K. Gu, W. J. Jia and C. L. Jiang, “Efficient identity-based proxy signature in the standard model,” the Computer Journal, vol. 58, no. 4, pp. 792–807, 2015. [Google Scholar]
7. K. Gu, L. H. Yang, Y. Wang and S. Wen, “Traceable identity-based group signature,” RAIRO-Theoretical Informatics and Applications, vol. 50, no. 3, pp. 193–226, 2016. [Google Scholar]
8. K. Gu, Y. Wang and S. Wen, “Traceable threshold proxy signature,” Journal of Information Science & Engineering, vol. 33, no. 1, pp. 63–79, 2017. [Google Scholar]
9. Z. Xu, C. Xu, J. Xu and X. Meng, “A computationally efficient authentication and key agreement scheme for multi-server switching in WBAN,” International Journal of Sensor Networks, vol. 35, no. 3, pp. 143–160, 2021. [Google Scholar]
10. L. Y. Xiang, X. B. Shen, J. H. Qin and W. Hao, “Discrete multi-graph hashing for large-scale visual search,” Neural Processing Letters, vol. 49, no. 3, pp. 1055–1069, 2019. [Google Scholar]
11. M. A. R. Khan and M. K. Jain, “Feature point detection for repacked android apps,” Intelligent Automation & Soft Computing, vol. 26, no. 6, pp. 1359–1373, 2020. [Google Scholar]
12. N. B. A. Ghani Binti, M. Ahmad, Z. Mahmoud and R. M. Mehmood, “A pursuit of sustainable privacy protection in big data environment by an optimized clustered-purpose based algorithm,” Intelligent Automation & Soft Computing, vol. 26, no. 6, pp. 1217–1231, 2020. [Google Scholar]
13. S. Heron, “Advanced encryption standard (AES),” Network Security, vol. 2009, no. 12, pp. 8–12, 2009. [Google Scholar]
14. F. B. Muhaya, “Modified AES using chaotic key generator for satellite imagery encryption,” Emerging Intelligent Computing Technology and Applications, vol. 5754, pp. 1014–1024, 2009. [Google Scholar]
15. G. N. Krishnamurthy and V. Ramaswamy, “Making AES stronger: AES with key dependent S-box,” International Journal of Computer Science and Network Security, vol. 8, pp. 388–398, 2008. [Google Scholar]
16. P. Kawle, A. Hiwase, G. Bagde, E. Tekam and R. Kalbande, “Modified advanced encryption standard,” International Journal of Soft Computing and Engineering, vol. 4, pp. 21–23, 2014. [Google Scholar]
17. M. Khan, T. Shah and S. I. Batool, “A new approach for image encryption and watermarking based on substitution box over the classes of chain rings,” Multimedia Tools and Applications, vol. 76, pp. 24027–24062, 2017. [Google Scholar]
18. M. Khan and T. Shah, “Construction and applications of chaotic S-boxes in image encryption,” Neural Comput & Applic, vol. 27, pp. 677–685, 2016. [Google Scholar]
19. M. Khan, T. Shah and S. I. Batool, “A new implementations of chaotic S-boxes in CAPTCHA,” Signal, Image and Video Processing, vol. 10, pp. 293–300, 2016. [Google Scholar]
20. A. Belazi, M. Khan, A. A. Abd El-Latif and S. Belghith, “Efficient cryptosystem approaches: S-boxes and permutation substitution-based encryption,” Nonlinear Dynamics, vol. 87, pp. 337–361, 2017. [Google Scholar]
21. K. N. Vijeyakumar, V. Sumathy, M. G. Devi, S. Tamilselvan and R. R. Nair, “Design of hardware efficient high speed multiplier using modified ternary logic,” Procedia Engineering, vol. 38, pp. 2186–219, 2012. [Google Scholar]
22. M. Mukaidono, “Regular ternary logic functions; ternary logic functions suitable for treating ambiguity,” IEEE Transactions on Computers, vol. 35, pp. 179–183, 1986. [Google Scholar]
 | This work is licensed under a Creative Commons Attribution 4.0 International License, which permits unrestricted use, distribution, and reproduction in any medium, provided the original work is properly cited. |