| Computers, Materials & Continua DOI:10.32604/cmc.2022.030270 |  |
| Article |
Code-based Sequential Aggregate Signature Scheme
1School of Mathematics and Statistics, Nanjing University of Science and Technology, Nanjing, 210094, China
2College of Data Science, Taiyuan University of Technology, Taiyuan, 030000, China
3SCRIPTS, Nanyang Technological University, 639798, Singapore
*Corresponding Author: Bennian Dou. Email: benniandou@163.com
Received: 22 March 2022; Accepted: 29 May 2022
Abstract: This paper proposes the first code-based quantum immune sequential aggregate signature (SAS) scheme and proves the security of the proposed scheme in the random oracle model. Aggregate signature (AS) schemes and sequential aggregate signature schemes allow a group of potential signers to sign different messages respectively, and all the signatures of those users on those messages can be aggregated into a single signature such that the size of the aggregate signature is much smaller than the total size of all individual signatures. Because of the aggregation of many signatures into a single short signature, AS and SAS schemes can reduce bandwidth and save storage; moreover, when a SAS is verified, not only the valid but also the order in which each signer signed can be verified. AS and SAS schemes can be applied to traffic control, banking transaction and military applications. Most of the existing AS and SAS schemes are based either on pairing or Rivest–Shamir–Adleman (RSA), and hence, can be broken by Shor’s quantum algorithm for Integer Factoring Problem (IFP) and Discrete Logarithm Problem (DLP). There are no quantum algorithms to solve syndrome decoding problems. Hence, code-based cryptography is seen as one of the promising candidates for post-quantum cryptography. This paper shows how to construct quantum immune sequential aggregate signatures based on coding theory. Specifically, we construct our scheme with the first code based signature scheme proposed by Courtois, Finiasz and Sendrier (CFS). Compared to the CFS signature scheme without aggregation, the proposed sequential aggregate signature scheme can save about 90% storage when the number of signers is asymptotically large.
Keywords: Sequential aggregate signature; CFS signature; post-quantum cryptography
Security systems may often encounter the scenario which is to manage many different signatures on many different messages generated by many distinct users. For example, in a Public Key Infrastructure (PKI) of depth n, user signatures are accompanied by a chain of n certificates. The chain contains n signatures by n Certificate Authorities (CAs) on n distinct certificates. Another example is secure border gateway protocol (S-BGP) [1] in which each router receives a list of n signatures attesting to a certain path of length n in the network. A router signs its own segment in the path and passes the resulting list of n+1 signatures to the next router. Both systems would benefit from a method which can compress the different signatures on different messages issued by different users. The certificate chain would be shortened by compressing the n signatures in the chain into a short single signature.
Aggregate signatures (AS), proposed by Boneh et al. [2] in 2003, are digital signatures that address the problem of compressing signatures. AS allows n members of a given group of potential signers to sign n different messages
Because of the aggregation of many signatures into a single short signature, AS and SAS schemes can reduce bandwidth and save storage; moreover, when a SAS is verified, not only the valid but also the order in which each signer signed can be verified. AS and SAS schemes can be applied to traffic control, banking transaction and military applications. Particularly, AS and SAS schemes are suitable for the secure border gateway protocol (S-BGP) which is designed to improve the security of the global Internet routing system. In the scenario of S-BGP, each router receives a list of n signatures attesting to a certain path of length n in the network. A router signs its own segment in the path and passes the resulting list of n + 1 signatures to the next router. When an AS scheme or a SAS scheme is used in S-BGP, one can significantly reduce associated bandwidth overhead and memory space for signatures.
Since Boneh et al. introduced aggregate signature scheme, there are many AS schemes have been presented [2–8], most of them are constructed either from pairings [2,4–8] or from Rivest–Shamir–Adleman (RSA) [3]. The security of the above schemes except [7] is proved in the random oracle model, and the security of [7] is proved in the standard model.
In 1997, Shor [9] discovered a remarkable quantum algorithm which can solve both the factoring problem and the discrete logarithm problem in finite fields and on elliptic curves in polynomial time. So in the age of quantum, Shor’s algorithm will break all digital signature schemes, including Full Domain Hash RSA (FDHRSA), the Digital Signature Algorithm (DSA) and the Elliptic Curve DSA (ECDSA), which are based on factoring problem and the discrete logarithm problem. Thus, Shor’s algorithm can also break all the aforementioned AS and SAS including Boneh et al.’s AS, Lysyanskaya et al.’s SAS. In response, the cryptographic community has been focusing on a coordinated effort to produce viable alternatives, based on hard problems which are not vulnerable to quantum cryptanalytic attacks. These include cryptosystems based on lattices, linear codes, multivariate equations, and others. Such an effort is led by NIST’s (National Institute of Standards and Technology) call for Post-Quantum Standardization [10], which is currently nearing its end.
In1978, McEliece [11] constructed a public key encryption (PKE) based on coding theory. In 1986, Niederreiter [12] proposed an equivalent code-based PKE. But the first practical code-based signature scheme was proposed by Courtois et al. until 2001 [13], their signature scheme is also known as the CFS signature. The CFS signature adapts the full domain hash (FDH) approach of Bellare et al. [14] to Niederreiter encryption scheme. The security of the CFS signature is based on two difficult problems of coding theory: The Goppa Bounded Decoding problem (GBD), and the Permuted Goppa Code Distinguishing problem (PGD) [13,15].
Our contribution. Up to date, there exists no quantum algorithm solving the GBD and PGD, so the CFS signature is seen as one of the promising candidates for post-quantum signatures [16,17]. After the publishing of the CFS scheme, there are just a few code-based signatures with special properties have been presented, namely blind, (threshold) ring signature, and identity-based signature, for details, refer to the survey paper [17]. To the best knowledge we know, there is no code-based aggregate signature or sequential aggregate signature in the literature.
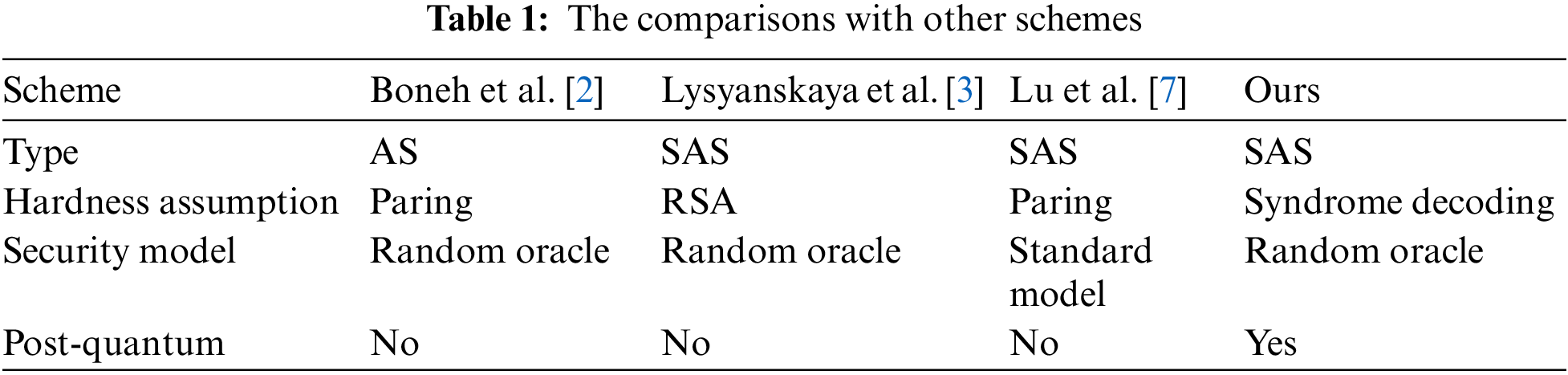
In this paper, we construct a code-based sequential aggregate signature from the CFS signature. We prove the proposed SAS secure in the random oracle under reasonable assumptions for permuted Goppa code. Due to the anti-quantum of the CFS signature schemes [16,17], to the best knowledge we know, our scheme is the first code-based quantum immune sequential aggregate signature (SAS) scheme. We compare our scheme with some other aggregate schemes in Tab. 1.
Related works. Recently, [18–20] used the Schnorr-Lyubashevsky framework to construct code based signatures without trapdoors. The Schnorr-Lyubashevsky framework has been shown able to produce secure and efficient signature schemes without trapdoors in the lattice-based setting. There are some works [21] analyzed such Schnorr-Lyubashevsky framework code based signatures. Some lattice based aggregate signatures have been proposed in [22,23]. Xu et al. proposed a post-quantum blind signature in [24]. Quantum spin states can be used to construct hybrid cryptosystems and other schemes [25–27].
Organizations. The rest of the paper is organized as follows: In Section 2, we give the formal definitions and security model of sequential aggregate signature schemes. Section 3 reviews coding theory and the CFS signature. A concrete code-based sequential aggregate signature scheme is proposed in Section 4.We compare the efficiency between aggregate and non-aggregate for the CFS signature in Section 5. Finally, we end with concluding remarks in Section 6.
2 Sequential Aggregate Signature Scheme
In this section, we give the formal definitions and security model of sequential aggregate signature (SAS) schemes. We adopt the main notions in [3].
Definition 1. A sequential aggregate signature (SAS) scheme SAS = (KeyGen, AggSign, AggVerify) consists of three algorithms:
KeyGen(
AggSign: AggSign takes as inputs a secret key
AggVerify: AggVerify takes as inputs a sequential aggregate signature
Fig. 1 shows how a sequential aggregate signature scheme works. SAS schemes can reduce bandwidth and save storage; moreover, when a SAS is verified, not only the valid but also the order in which each signer signed can be verified.

Figure 1: Workflow of a sequential aggregate signature scheme
2.2 Security Model of SAS Schemes
Let SAS = (KeyGen; AggSign; AggVerify) be a sequential aggregate signature scheme. To give the security model of SAS schemes, we consider the following game associated to a challenger C and a forger A. A’s advantage, AdvAggSigA, is defined to be his probability to win in the game.
Setup. The aggregate forger A is provided with a public key PK, generated at random.
Queries. Proceeding adaptively, A requests sequential aggregate signatures with PK on messages of his choice. For each query, he supplies a sequential aggregate signature
Response. Finally, A outputs i distinct public keys
The forger wins if the sequential aggregate signature
Definition 2. We say a sequential aggregate forger A
3 Coding Theory and CFS Signature
A binary [n, k]-code C is a linear subspace of dimension k of the linear space
Goppa codes are subfield subcodes of particular alternant codes with efficient decoding algorithm. Goppa codes are widely used in coding-based cryptography. For given integers m and t, Goppa codes are of length
In order to establish the security of the CFS signature and the pro-posed SAS, we introduce some problems on coding theory.
Definition 3. Goppa Bouned Decoding Problem (GBD): Given a random
The associated decision problem of GBD is NP-complete [28].
Definition 4. Multiple Goppa Bounded Decoding (MGBD): Given a random
The associated decision problem of MGBD is conjectured to be NP-complete, too [29].
Definition 5. We say an algorithm A is
Lemma 1. There is no algorithm A which is
Let
The basic idea of code-based cryptography is using a certain code which has efficient decoding algorithm with trapdoor information as private key and publishing the random look like variant of this code as public key.
The first code-based signature is the CFS signature which was introduced by Courtois, Finiasz and Sendrier at Asiacrypt 2001 [13]. The CFS signature is obtained by applying full hash domain approach to the Niederreiter public key cryptosystem. The CFS signature we will describe below is a minor modification of the original CFS signature, and this modified CFS signature enables us to prove its security more reasonable in random oracle [15,30]. The CFS signature consists of three algorithms which are described as follows:
SystemParameters: Two integers
CFSKeyGen (
Sign: Let
1. choose
2.
3. if no
Let
Verification: Let
Security of the CFS Signature: The security of the CFS signature is based on two assumptions: One is the intractability of GBD as stated in Lemma1; the other is the intractability of the Permuted Goppa Code Distinguish (PGD) which we will describe below.
Definition 6. Permuted Goppa Code Distinguish Problem (PGD): Given H generated by CFSKeyGen (
Definition 7. We say an algorithm A is
Lemma 2 ( [13,15]). There is no algorithm A which is
Because of Lemma 2, we can apply Lemma 1 to permuted Goppa code. In fact, we have
Definition 8. Permuted Goppa Code Bounded Decoding (PGBD): Given H generated by CFSKeyGen (
Lemma 3 ( [13]). There is no algorithm A which is
In this section, we propose a sequential aggregate signature based on CFS signature, and also prove the security of the proposed SAS.
We firstly introduce some notations for vectors. We write a vector as
The proposed SAS consists of three algorithms which are described below:
SystemParameters: Two integers
KeyGen (
AggSign: The inputs are a secret key
1. choose
2.
3. if no
Let
AggVerify: The input is a sequential aggregate signature
Correctness of the proposed scheme. From the process of AggVerify, we know that
On the other hand, if the sequential signature is computed correctly, from the process AggSign we have,
which implies
4.2 Security of the Proposed SAS
In this section, we prove the security of the proposed SAS in the random oracle model, we will prove the security of our scheme based on the assumption in lemma 3.
To make the proof easier, we firstly prove the following lemma.
Lemma 4. There is a forger A
Proof: The lemma can be immediately obtained by the observation that during the AggVerify phase of our scheme, supposing
Henceforward, we suppose that matrix-vector multiplication, exclusive or of vectors and the computation of
Theorem 1. If there is a
where
Proof: If A is
Below we will show that if there is an algorithm A is
B is given a parity check matrix H of a random [n, k, d]-binary permuted Goppa code (
Hash queries: The random hash function h has two properties: i.e., the property that the outputs of h are random and the property that one output from
B maintains a list of tuples
1. If the query
2. Otherwise set
2.1
2.2
3. Finally, B adds
In all cases, B’s response,
Aggregate signature queries: A supplies a sequential aggregate signature
B’s output:At last, algorithm A halts and produces a correct forgery sequential aggregate signature
This completes the description of algorithm B.
Claim 1. If A makes a valid sequential aggregate signature query on(
Proof: Firstly, we introduce some notations. For each j,
The last equation shows that
Claim 2: If A outputs a valid nontrivial forgery sequential aggregate signature
Proof: We use the same notations introduced in Claim 1. If B does not abortion, then
Thus,
And hence, we can obtain that if we set
It remains to show that the success probability
Then B succeeds in giving the correct solution if all of the above events happen, i.e.,
On the other hand, we have the following three claims.
Claim 3.
Proof: If B does not abort during each aggregate signature query, then all
Claim 4.
Proof: Trivially.
Claim 5.
Proof: If B does not abort during the output phase, then all
Combine the results of the above claims, we obtain immediately that
The running ting
We now compare the efficiency between our scheme and the original CFS scheme without aggregate in N users setting. To achieve security, for the CFS signature, [31] suggests the parameters:

6 Conclusions and Open Problems
In this paper, we propose the first code based sequential aggregate signature, and prove the security of the scheme in the random oracle model. We note that the length of the aggregate signature in our scheme is not constant. It is an open problem to construct code based sequential aggregate signatures with constant length. It is also an interesting problem to construct code based aggregate signatures using the Schnorr-Lyubashevsky Framework [18,20].
Funding Statement: This work was supported in part by the National Natural Science Foundation of China under Grant 62072240, by the Natural Science Foundation of Jiangsu Province under Grant BK20210330 and by the National Key Research and Development Program of China under Grant 2020YFB1804604.
Conflicts of Interest: The authors declare that they have no conflicts of interest to report regarding the present study.
References
1. S. Kent, C. Lynn and K. Seo, “Secure border gateway protocol (secure-BGP),” IEEE J. Selected Areas in Comm, vol. 18, no. 4, pp. 582–92, 2000. [Google Scholar]
2. D. Boneh, C. Gentry, B. Lynn and H. Shacham, “Aggregate and verifiably encrypted signatures from bilinear maps,” in Advances in Cryptology, EUROCRYPT 2003. Proc.: Lecture Notes in Computer Science (LNCS 2656), Warsaw, Poland, pp. 416–432, 2003. [Google Scholar]
3. A. Lysyanskaya, S. Micali, L. Reyzin and H. Shacham, “Sequential aggregate signatures from trapdoor permutations,” in Advances in Cryptology, EUROCRYPT 2004. Proc.: Lecture Notes in Computer Science (LNCS 3027), Interlaken, Switzerland, pp. 74–90, 2004. [Google Scholar]
4. A. Boldyreva, C. Gentry, A. O’Neill and D. Yum, “Ordered multisignatures and identity-based aggregate signatures with applications to secure routing,” in Proc. of the 14th ACM Conf. on Computer and Communications Security, CCS 2007, Alexandria, Virginia, USA, pp. 276–285, 2007. [Google Scholar]
5. X. Cheng, J. Liu and X. Wang, “Identity-based aggregate and verifiably encrypted signatures from bilinear pairing,” in Int. Conf. on Computational Science and Its Applications, ICCSA 2005. Proc.: Lecture Notes in Computer Science (LNCS 3483), Singapore, pp. 1046–1054, 2005. [Google Scholar]
6. C. Gentry and Z. Ramzan, “Identity-based aggregate signatures,” in Public Key Cryptography, PKC 2006. Proc.: Lecture Notes in Computer Science (LNCS 3958), New York City, NY, USA, pp. 257–273, 2006. [Google Scholar]
7. S. Lu, R. Ostrovsky, A. Sahai, H. Shacham and B. Waters, “Sequential aggregate signatures and multisignatures without random oracles,” in Advances in Cryptology, EUROCRYPT 2006. Proc.: Lecture Notes in Computer Science (LNCS 4004), St. Petersburg, Russia, pp. 465–485, 2006. [Google Scholar]
8. J. Xu, Z. Zhang and D. Feng, “ID-Based aggregate signatures from bilinear pairings,” in Cryptology and Network Security, 4th Int. Conf., CANS 2005. Proc.: Lecture Notes in Computer Science (LNCS 3810), Xiamen, China, pp. 110–119, 2005. [Google Scholar]
9. P. W. Shor, “Polynomial-tme algorithms for prime factorization and discrete logarithms on a quantum computer,” SIAM J. Computing, vol. 26, pp. 1484–1509, 1997. [Google Scholar]
10. National Institute of Standards and Technology, “NIST post quantum standardization process,” 2017. [Online]. Available: https://csrc.nist.gov/Projects/Post-Quantum-Cryptography. [Google Scholar]
11. R. J. McEliece, “A Public-key cryptosystem based on algebraic coding theory,” Jet propulsion Laboratory DSN Progress Report, vol. 42-44, pp. 114–116, 1978. [Google Scholar]
12. H. Niederreiter, “Knapsack-type crytosystems and algebraic coding theory,” Prob. Contr. Inform. Theory, vol. 15, no. 2, pp. 157–166, 1986. [Google Scholar]
13. N. Courtois, M. Finiasz and N. Sendrier, “How to achieve a McEliece-based digital signature scheme,” in Advances in Cryptology, ASIACRYPT 2001. Proc.: Lecture Notes in Computer Science (LNCS 2248), Gold Coast, Australia, pp. 157–174, 2001. [Google Scholar]
14. M. Bellare and P. Rogaway, “Random oracles are practical: A paradigm for designing efficient protocols,” in Proc. of the 1st ACM Conf. on Computer and Communications Security, CCS 1993, Fairfax, Virginia, USA, pp. 62–73, 1993. [Google Scholar]
15. L. Dallot, “Towards a concrete security proof of courtois, finiasz and sendrier signature scheme,” in Research in Cryptology, Second Western European Workshop, WEWoRC 2007. Proc.: Lecture Notes in Computer Science (LNCS 4945), Bochum, Germany, pp. 65–77, 2008. [Google Scholar]
16. J. Buchmann, C. Coronado, M. Doring, D. Engelbert, C. Ludwig et al., “Post-quantum signatures,” 2004. [Online]. Available: https://eprint.iacr.org/2004/297.pdf. [Google Scholar]
17. P. Cayrel and M. Meziani, “Post-quantum cryptography: Code-based signatures,” in Advances in Computer Science and Information Technology, AST/UCMA/ISA/ACN 2010. Proc.: Lecture Notes in Computer Science (LNCS 6059), Miyazaki, Japan, pp. 82–89, 2010. [Google Scholar]
18. Y. Song, X. Huang, Y. Mu, W. Wu and H. Wang, “A Code-based signature scheme from the lyubashevsky framework,” Theoretical Computer Science, vol. 835, pp. 15–30, 2020. [Google Scholar]
19. Z. Li, C. Xing and S. L. Yeo, “A new code based signature scheme without trapdoors,” Cryptology ePrint Archive, Report 2020/1250, 2020. [Google Scholar]
20. M. Baldi, F. Chiaraluce and P. Santini, “Code-based signatures without trapdoors through restricted vectors,” Cryptology ePrint Archive, Report 2021/294, 2021. [Google Scholar]
21. M. Baldi, J. C. Deneuville, E. Persichetti and P. Santini, “Cryptanalysis of a code-based signature scheme based on the schnorr-lyubashevsky framework,” IEEE Communications Letters, vol. 25, no. 9, pp. 2829–2833, 2021. [Google Scholar]
22. R. Bansarkhani and J. Buchmann, “Towards lattice based aggregate signatures,” in“ Progress in Cryptology, AFRICACRYPT 2014. Proc.: Lecture Notes in Computer Science (LNCS 8469), Marrakesh, Morocco, pp. 336–355, 2014. [Google Scholar]
23. Y. Zhang, Y. Hu and M. Jiang, “Lattice- based sequential aggregate signatures with lazy verification,” the Journal of China Universities of Posts and Telecommunications, vol. 22, no. 6, pp. 36–44, 2015. [Google Scholar]
24. G. Xu, Y. Cao, S. Xu, K. Xiao, X. Liu et al., “A novel post-quantum blind signature for log system in blockchain,” Computer Systems Science and Engineering, vol. 41, no. 3, pp. 945–958, 2022. [Google Scholar]
25. A. Alghafis, H. M. Waseem, M. Khan and S. S. Jamal, “A hybrid cryptosystem for digital contents confidentiality based on rotation of quantum spin states,’’ Physica A: Statistical Mechanics and its Applications, vol. 554(C), pp. 123908, 2020. [Google Scholar]
26. H. M. Waseem, A. Alghafis and M. Khan, “An efficient public Key cryptosystem based on dihedral group and quantum spin states,” IEEE Access, vol. 8, pp. 71821–71832, 2020. [Google Scholar]
27. A. Alghafis, H. M. Waseem, M. Khan, S. S. Jamal, M. Amin et al., “A novel digital contents privacy scheme based on quantum harmonic oscillator and schrodinger paradox,” Wireless Networks, 2020. https://doi.org/10.1007/s11276-020-02363-7. [Google Scholar]
28. M. Finiasz, “Nouvelles constructions utilisant des codes correcteurs derreurs en cryptographie ‘a clef publique,” Ph.D dissertation, INRIA C Ecole Polytechnique, France, 2004. [Google Scholar]
29. N. Sendrier, “Code-based one way functions,” 2007. [Online]. Available: http://ecrypt-ss07.rhul.ac.uk/Slides/Thursday/sendrier-samos07.pdf. [Google Scholar]
30. R. Overbeck and N. Sendrier, “Code based cryptography,” in D. J. Bernstein, J. Buchmann, E. Dahmen, (Eds.Post-Quantum Cryptography, Berlin, Heidelberg, Germany: Springer, pp. 95–145, 2009. [Google Scholar]
31. M. Finiasz and N. Sendrier, “Security bounds for the design of code-based cryptosystems,” in Advances in Cryptology, ASIACRYPT 2009. Proc.: Lecture Notes in Computer Science (LNCS 5912), Tokyo, Japan, pp. 88–105, 2009. [Google Scholar]
 | This work is licensed under a Creative Commons Attribution 4.0 International License, which permits unrestricted use, distribution, and reproduction in any medium, provided the original work is properly cited. |