DOI:10.32604/cmc.2022.030229

| Computers, Materials & Continua DOI:10.32604/cmc.2022.030229 |  |
| Article |
Artificial Intelligence-Enabled Cooperative Cluster-Based Data Collection for Unmanned Aerial Vehicles
1Department of Computer Science Engineering, Lendi Institute of Engineering & Technology, Denkada, 535005, India
2Department of Electronics & Instrumentation Engineering, V. R. Siddhartha Engineering College, Vijayawada, 520007, India
3Department of Computer Science Engineering, Malla Reddy Engineering College, 500100, India
4Department of Computer Science and Engineering, Vignan’s Institute of Information Technology, Visakhapatnam, 530049, India
5Department of Applied Data Science, Noroff University College, Kristiansand, 4612, Norway
6Department of Computer Engineering, Sungkyul University, Anyang, 14097, Korea
*Corresponding Author: Sangsoon Lim. Email: lssgood80@gmail.com
Received: 21 March 2022; Accepted: 26 April 2022
Abstract: In recent times, sixth generation (6G) communication technologies have become a hot research topic because of maximum throughput and low delay services for mobile users. It encompasses several heterogeneous resource and communication standard in ensuring incessant availability of service. At the same time, the development of 6G enables the Unmanned Aerial Vehicles (UAVs) in offering cost and time-efficient solution to several applications like healthcare, surveillance, disaster management, etc. In UAV networks, energy efficiency and data collection are considered the major process for high quality network communication. But these procedures are found to be challenging because of maximum mobility, unstable links, dynamic topology, and energy restricted UAVs. These issues are solved by the use of artificial intelligence (AI) and energy efficient clustering techniques for UAVs in the 6G environment. With this inspiration, this work designs an artificial intelligence enabled cooperative cluster-based data collection technique for unmanned aerial vehicles (AECCDC-UAV) in 6G environment. The proposed AECCDC-UAV technique purposes for dividing the UAV network as to different clusters and allocate a cluster head (CH) to each cluster in such a way that the energy consumption (ECM) gets minimized. The presented AECCDC-UAV technique involves a quasi-oppositional shuffled shepherd optimization (QOSSO) algorithm for selecting the CHs and construct clusters. The QOSSO algorithm derives a fitness function involving three input parameters residual energy of UAVs, distance to neighboring UAVs, and degree of UAVs. The performance of the AECCDC-UAV technique is validated in many aspects and the obtained experimental values demonstration promising results over the recent state of art methods.
Keywords: 6G; unmanned aerial vehicles; resource allocation; energy efficiency; artificial intelligence; clustering; data collection
Sixth generation (6G) communication system is an advanced technology which provides high speed heterogeneous service access to clients. This technique aims to allow higher throughput and latency less service for various applications user ranges in cloud to small sensor device [1,2]. Also, the combination of artificial intelligence (AI), machine type communication (MTC), blockchain, and smart machine learning based resolution assists for enhancing the service consistency for diverse classes of users and applications from the 6G framework [3]. Communication and information relevant decisions, resource sharing, and allocation with access control are flexible from 6G platform. Particularly, the optical wireless, terahertz communication, network slicing [4], blockchain, massive multiple output, and input, are the most important enabling technology for 6G.
The 6G network requires advanced AI techniques to resolve several problems that exist in the 6G network. Indeed, in the perspective of various scientists, the 6G network must be an “AI-empowered” network, which means AI in both driver and important characteristics [5,6]. Unmanned aerial vehicles (UAVs) is generally recognized as drones, plays a significant role in an extensive scenario and use cases that could exceed 5G and 6G [7,8]. It is widely utilized in several applications when providing novel business chances in the following years.
The UAV is generally called a drone that is a classification of robotic vehicles which is either self-governed/remotely managed via remote control device using wireless transmission [9]. This guarantees wireless connection that is cost effective to device which aren’t establishing framework coverage. The UAV mostly consists of sensors to give data regarding the state of aerial vehicles and for detecting targets in an effective manner. It consists of computing devices like UAV software, transmission system, actuators, analog controls, and micro controllers. With respect to terrestrial transmission system, UAV wireless system is on demand and fly at lower altitude that is quicker to place [10]. It is designed flexibly and appears to have well-functioning transmission channel attributed to Line of Sight (LOS) relations which is short ranged. Primarily, the UAV was implemented in military applications, now, it can be accepted from a variation of civilian applications like precision agriculture, weather monitoring, urban planning, rescue, and search processes. The information gathered from applied UAV was significant in the implementation of emergency operations. A multi UAV system (several smaller UAV placed in analogous) conquers energy and coverage constraint and have the capacity of observing information from different viewpoints. The combined task of UAV enhances system efficiency and decreases operation cost. Because of the fault tolerance ability, the mission was accomplished in an efficient and quick manner. For productive and effective mission accomplishment, several UAVs are utilized as an outcome of their flight time, abilities, and limited payload [11]. To effectively arrange various UAVs, appropriate cooperation is needed by effective networking and communication.
Communication is the main proposal factor in Many UAV systems. But, it has a specific aspect of FANETs like limitation in the available battery resource, higher mobility of the UAV nodes, and sparse placement, which could obstruct the efficient and stable communications between UAVs [12]. The high mobile nature of UAV leads to recurrent modification in the topology. This would need recurrent transmission of the novel position between UAV nodes, results in consumption of energy based on overheads [13]. The sparse placement of UAV needs relatively high energy to communicate because of the significantly high distance between UAVs. The intelligent clustering method could perform a major part in improving the energy effectiveness of a network. Clustering is the procedure of separating the UAV nodes placed in a geographical position, have specific comparisons in attaining a specific objective for various groups. In cluster, all nodes are selected as cluster head (CH). The CH node is allowed with the task of relaying and coordinating the information of its cluster member (CM) to their end. The requirement and scalability of minimal overheads in clustering play an important part in enhancing the effectiveness of the ad-hoc network. In recent times, bio inspired techniques have been generally employed for solving the clustering problems in UAV networks. Due to their easiness, efficiency in resolving difficult optimization problems, and local minimum evasion. Major techniques are stimulated by evolutionary concepts, physical phenomena, and animal behavior. Because of their easiness, scientists have attempted to propose and develop novel bio inspired methods.
This paper designs an artificial intelligence enabled cooperative cluster-based data collection technique for unmanned aerial vehicles (AECCDC-UAV) in 6G environment. The proposed AECCDC-UAV technique purposes for dividing the UAV network as to different clusters and allocate a CH to each cluster which is responsible for effective cooperative data collection and data transmission. The presented AECCDC-UAV technique involves a quasi-oppositional shuffled shepherd optimization (QOSSO) algorithm to elect the CHs and construct clusters. The QOSSO algorithm is derived by the combined of quasi oppositional based learning (QOBL) with the SSO method to achieve better convergence rate. For validating the improved performance of the AECCDC-UAV approach, a series of simulations were implemented and the outcomes are investigated under varying measures.
The rest of the paper is organized as follows. Section 2 offers related works, Section 3 provides proposed model, Section 4 gives performance validation, and Section 5 draws conclusion.
Arafat et al. [14] developed bio inspired clustering (BIC) and localization (BIL) systems in UAV networks for detecting and observing wildfire. The authors proposed a grey wolf optimization (GWO) based compressive sensing (CSGWO) method for transmitting information from CH to the BS. Gul et al. [15] emphases on an energy-efficient data gathering issue via UAV In Kumar et al. [16], a Crow Search based clustering system is introduced for tackling above mentioned problems to enhance the entire performance and network lifespan of the flying adhoc network (FANET). The system considers the distance between residual energy, UAV nodes, and delay constraint for the creation of optimum cluster and its concurrent selection of CH. Noh et al. [17] proposed an ellipse clustering method to increase the client coverage probability of UAV and evades inter-cell interference with minimum transmission powers.
Yu et al. [18] proposed new modularity based dynamic clustering based on modified Louvain technique for UAV supported mobile communication., they proposed 2 kinds of processes for modularity based dynamic clustering, such as differential and recurring operations. Arafat et al. [19] proposed swarm intelligence (SI) based localization and clustering systems in UAV network for emergency communication. Initially, they proposed a novel 3D SI based localization (SIL) method according to particle swarm optimization (PSO) algorithm.
Na et al. [20] presented a synergetic system for UAV trajectory planning and sub slot allocation. While the established problems suffer non-convexity and difficulty, an effectual iterative method is presented to tackle the situation. Poudel et al. [21] proposed an hybrid path planning (HPP) technique for effective data collection by guaranteeing the shorter collision free path to UAV in an emergency condition. In presented method, the Probabilistic Roadmap Method (PRM) method is utilized for designing the shorter trajectory map and the enhanced artificial bee colony (ABC) technique for improving various path constraints in a 3D platform. Yin et al. [22] employ nonorthogonal multiple access (NOMA) in UAV assisted wireless caching networks (WCN) for serving various clients on a similar spectrum consecutively and proposed cross layer Drone Reconfigurable Architecture (DRA) approach comprising allocation of power, scheduling of UAV, and grouping of users. Initially, the ρ–K means method was presented for assigning clients to several clusters and place UAVs based on distance from UAV to BS in the UAV placement layer. Later, the BS transmissions the common file for UAV through NOMA in the content deployment layer. Lin et al. [23] developed a 6G enabled massive IoT framework which assists DRA. Later, a dynamic nested NN was created to alter the nested learning module structure online for meeting trained needs of DRA.
The workflow involved in the presented AECCDC-UAV technique is depicted in Fig. 1. Primarily, the UAVs are placed arbitrarily from the interested region and the initialized procedure is carried out. Then, the AECCDC-UAV technique gets performed to define the optimum number of CHs for cooperative data collection and transmission in the network. Besides, the selection of CHs resulted in the sharing of neighboring UAVs to construct clusters. The detailed working of the AECCDC-UAV technique is given in the following subsections.
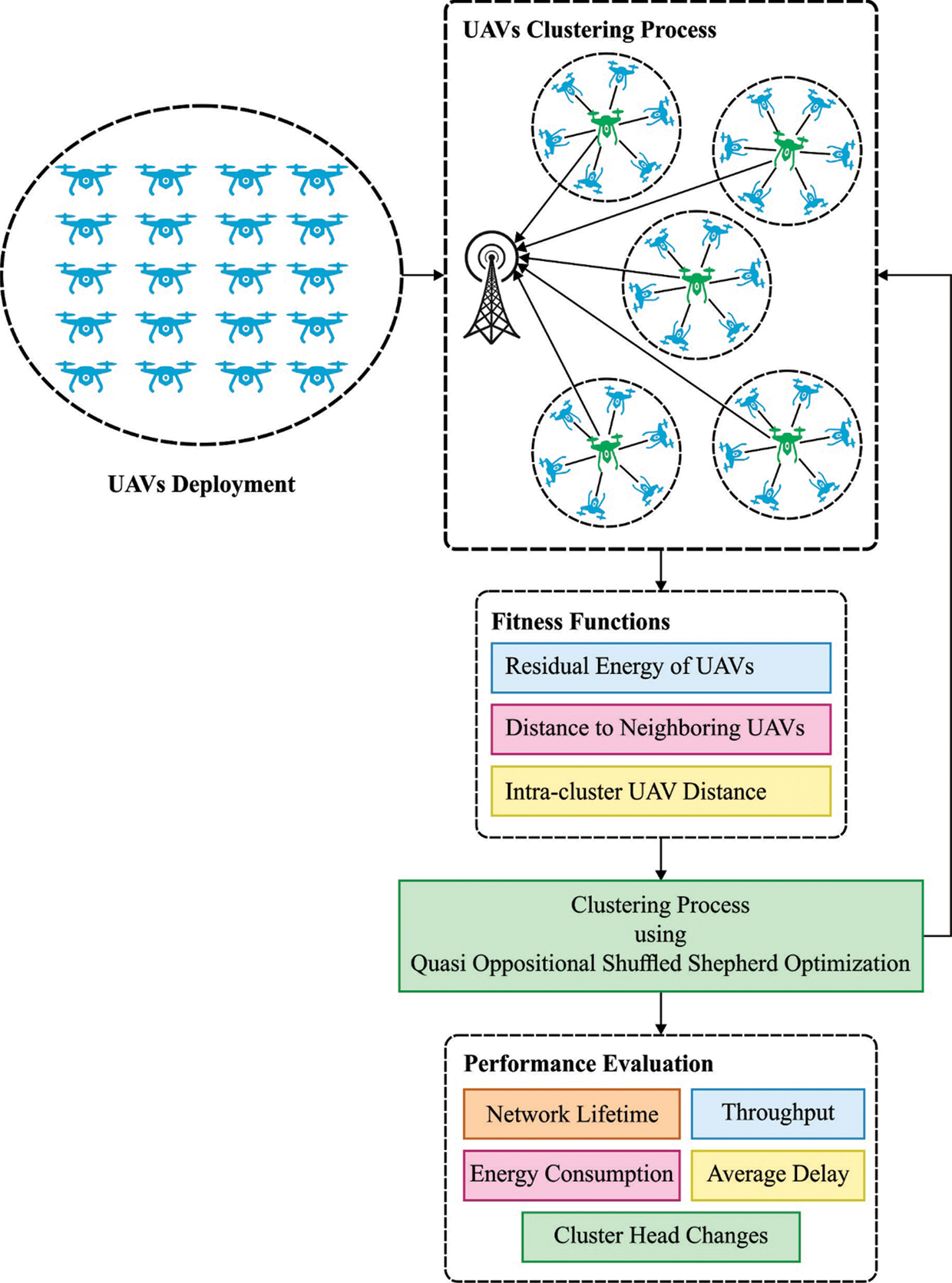
Figure 1: Working process of AECCDC-UAV model
Consider a UAV network, consisting of multiple UAVs. The UAVs employed are small to medium sized drones. Besides, a simpler collision approach is employed to avoid collision where the altitude of the UAVs gets changed. Besides, the UAVs move at a speed of 30 m/s. Every UAV is based on certain location aware elements and the characteristics of location aware model enable effective and accurate clustering process. In general, the location data is generally attained from external systems such as GPS. Every UAV knows about its location, location of the neighboring UAV, and location of the ground station. In addition, in UAV based mobile communication, it can be practical to purpose at an explicit data rate
3.2 Algorithmic Design of QOSSO Technique
In this section, the QOSSO algorithm is designed and the processes involved in it are explained clearly. The SSO algorithm is based on the behavior of shepherds [24]. Fig. 2 illustrates the flowchart of SSO method. Primarily, the SSO technique initiates with the arbitrarily make primary member of community (MOC) from the searching space by the succeeding equation:
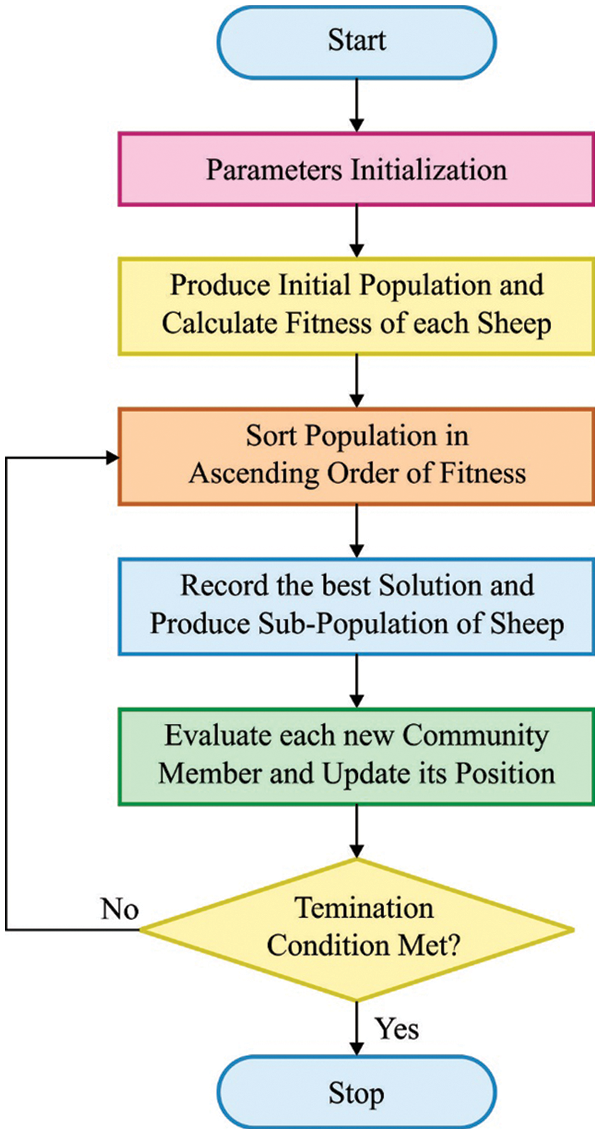
Figure 2: Flowchart of SSO
The shuffling procedure is executed in n time autonomously till MC matrix is created by:
The scientific equation of the step size is demonstrated by:
where
where
According to prior step, the novel place of
In this study, the QOBL concept is included in the SSO algorithm for improving the candidate solutions by the consideration of present and quasi-opposite populations concurrently. This procedure can be enhanced by the initialization of a nearer solution by concurrently inspecting the quasi-opposite solution. Using this process, the fittest solution (guess or quasi-opposite guess) can be elected as the initial solution. This procedure begins with the two closer guesses. It is applied to initial solution and also to every solution that exists in the present solution. It is guaranteed that the quasi-opposite number is generally nearer to the arbitrary number to the solution. Besides, the quasi-opposite number is generally nearer to the opposite number to the solution [25]. The concept of QOBL technique is utilized for population initialization and generation jumping.
When x denotes a real number among
and
Besides, consider
The quasi-opposite point
Using the quasi-opposite point, the QOSSO algorithm can be defined in the following. Assume
3.3 Application of QOSSO Technique for CH Selection and Cluster Construction
The proposed AECCDC-UAV based clustering mainly depends upon the QOSSO algorithm. The goal of the AECCDC-UAV technique is to divide the
where
where E implies the present energy level of UAVs and
where
Besides, the ADTN represents the average value of the distance of adjacent UAVs in its 1-hop transmission range [26]. It can be defined using Eq. (17):
where
At a time t, the DEG represents the UAV degree signifying the number of nearby nodes present for the UAV, which can be equated as follows
where
The proposed AECCDC-UAV approach has been simulated and the results are investigated under varying numbers of UAVs. Tab. 1 shows the parameter setting.
Tab. 2 and Fig. 3 examines the energy consumption (ECM) analysis of the AECCDC-UAV approach with state-of-art methods. From the table values, it is evident that the AECCDC-UAV approach has exhibited the compared methods by offering minimum ECM. At the same time, the PSO based clustering (PSO-C) algorithm has depicted ineffective outcomes by accomplishing maximum ECM. For sample, under 10 UAVs, the AECCDC-UAV approach has achieved a lower ECM of 31 mJ while the type 2 fuzzy logic based clustering (T2FL-C), krill herd algorithm based clustering (KHA-C), MPSO-C, and PSO-C approaches have gained a higher ECM of 40, 44, 46, and 55 mJ respectively. In addition, under 40 UAVs, the AECCDC-UAV approach has achieved a lower ECM of 75 mJ while the T2FL-C, KHA-C, MPSO-C, and PSO-C approaches have gained a higher ECM of 99, 108, 111, and 140 mJ correspondingly. Moreover, under 80 UAVs, the AECCDC-UAV system has obtained a reduced ECM of 133 mJ while the T2FL-C, KHA-C, MPSO-C, and PSO-C approaches have gained a higher ECM of 161, 178, 192, and 197 mJ respectively. Furthermore, under 100 UAVs, the AECCDC-UAV approach has achieved a lower ECM of 154 mJ while the T2FL-C, KHA-C, MPSO-C, and PSO-C algorithms have gained a higher ECM of 174, 196, 213, and 222 mJ correspondingly.
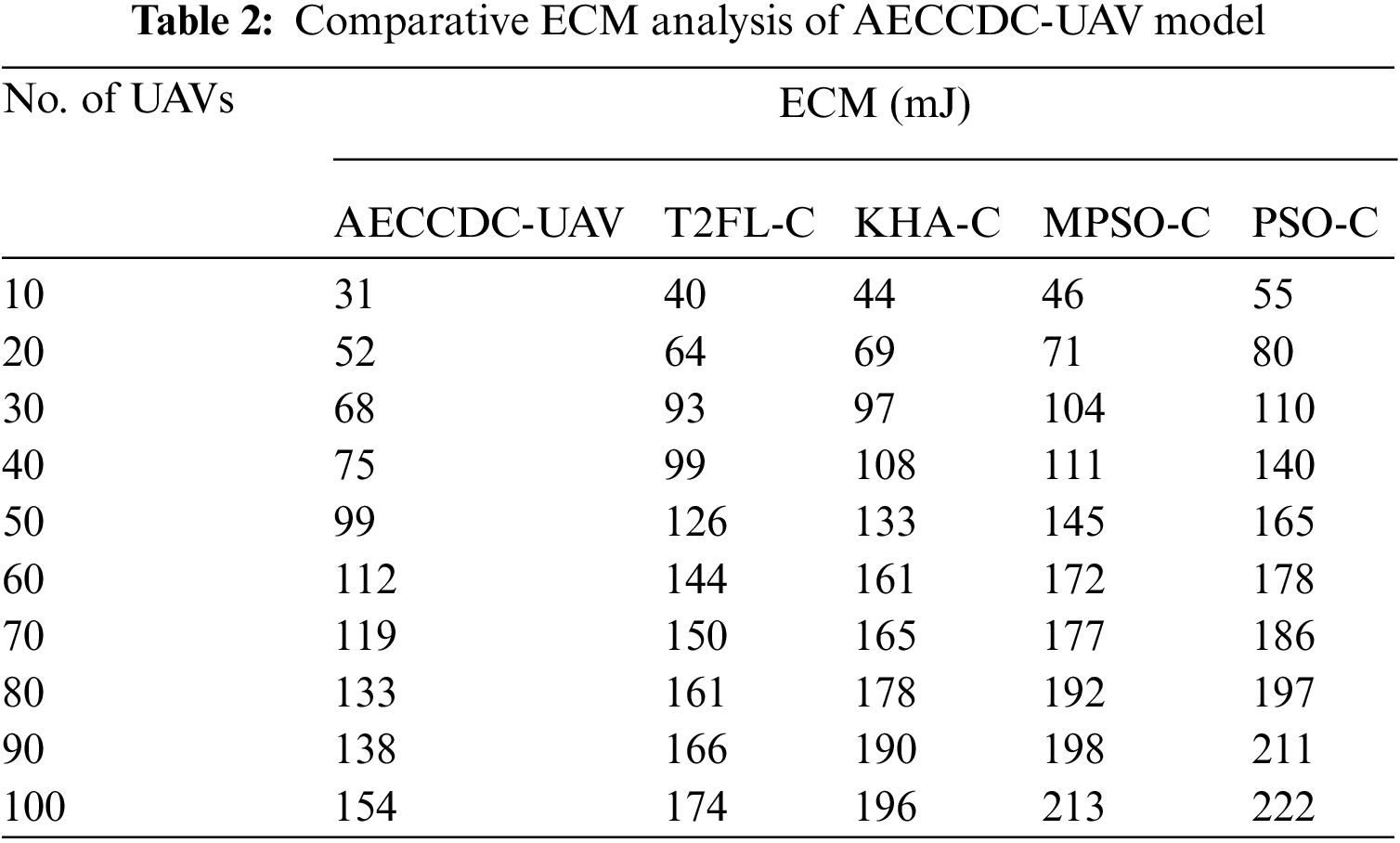
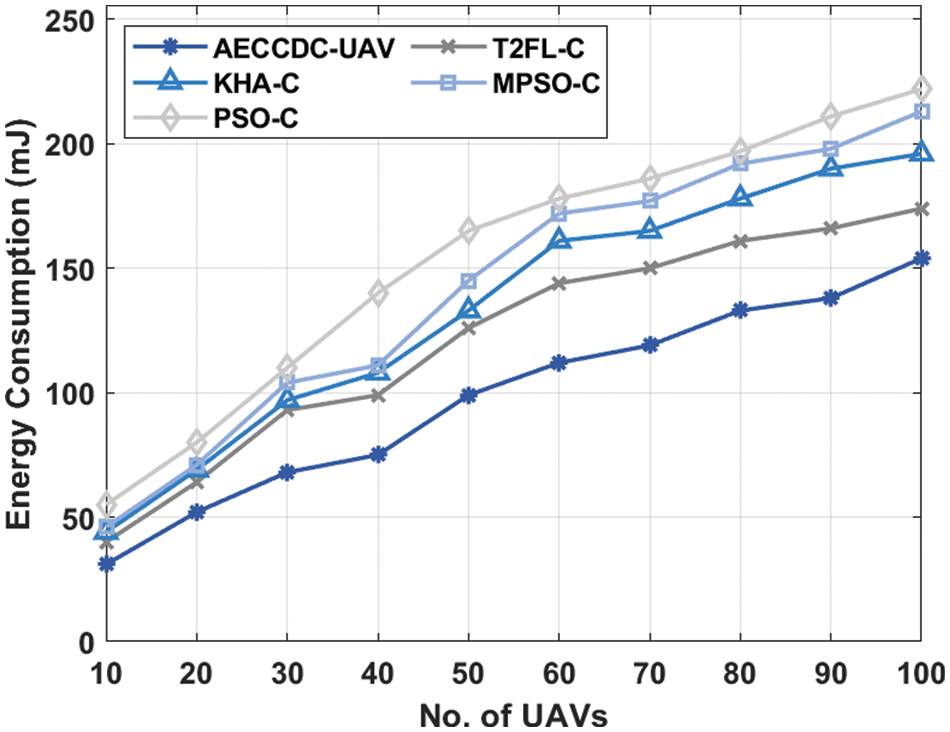
Figure 3: ECM analysis of AECCDC-UAV model
An analysis of network lifetime (NLT) of the AECCDC-UAV approach with existing approaches shown in Tab. 3 and Fig. 4. From the gained outcomes, it could be evident that the PSO-C algorithm has accomplished poor results with the worse network lifetime while the AECCDC-UAV approach has reached effectual outcome with the maximum network lifetime. For sample, under 10 UAVs, the AECCDC-UAV approach has led to in an improved network lifetime of 5750 rounds while the T2FL-C, KHA-C, MPSO-C, and PSO-C approaches have demonstrated a reduced network lifetime of 5400, 5350, 5160, and 4600 rounds respectively. Besides, under 40 UAVs, the AECCDC-UAV system has caused in a higher network lifetime of 5240 rounds while the T2FL-C, KHA-C, MPSO-C, and PSO-C approaches have demonstrated a reduced network lifetime of 5080, 4780, 4430, and 4010 rounds correspondingly. Additionally, under 80 UAVs, the AECCDC-UAV methodology has resulted in enhanced network lifetime of 4260 rounds while the T2FL-C, KHA-C, MPSO-C, and PSO-C approaches have demonstrated a reduced network lifetime of 3910, 3670, 3590, and 3420 rounds respectively. At last, under 100 UAVs, the AECCDC-UAV system has led to a superior network lifetime of 3990 rounds while the T2FL-C, KHA-C, MPSO-C, and PSO-C approaches have demonstrated a reduced network lifetime of 3380, 3210, 3110, and 3040 rounds correspondingly.
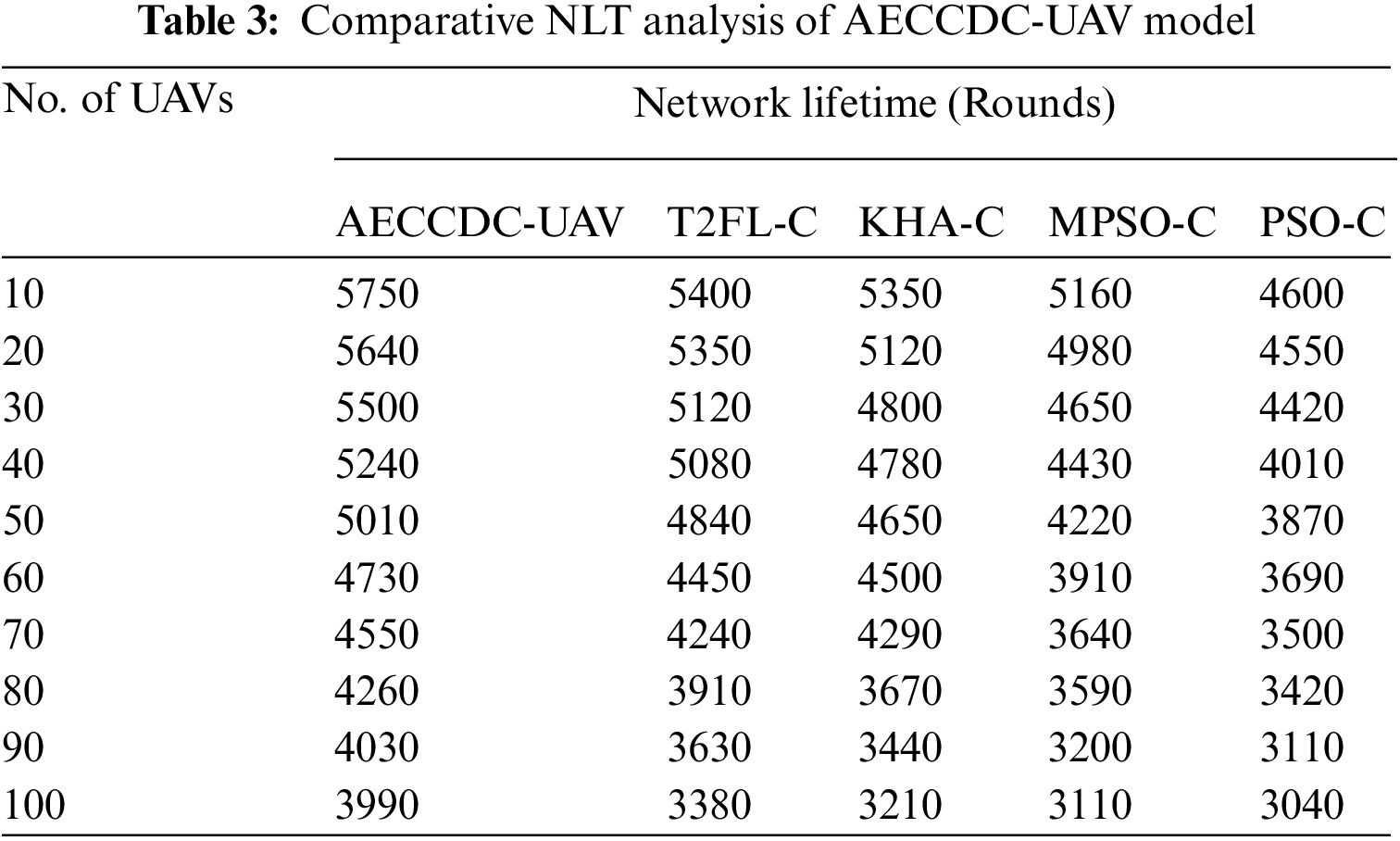
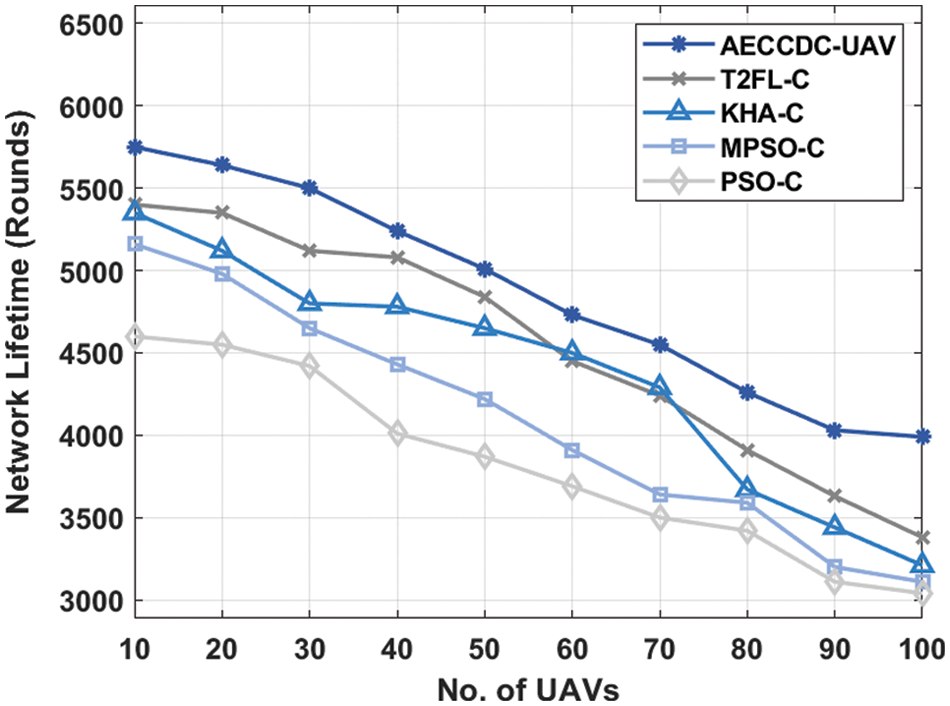
Figure 4: Network lifetime analysis of AECCDC-UAV model
An analysis of throughput (THPT) of the AECCDC-UAV approach with existing approaches occurs in Tab. 4 and Fig. 5. From the reaches outcomes, it could be evident that the PSO-C algorithm has accomplished poor results with the worse THPT while the AECCDC-UAV approach has achieved effectual outcome with the maximum THPT. For sample, under 10 UAVs, the AECCDC-UAV approach has led to in maximal THPT of 0.98 Mbps while the T2FL-C, KHA-C, MPSO-C, and PSO-C systems have demonstrated a reduced THPT of 0.92, 0.91, 0.89, and 0.85 Mbps correspondingly. Also, under 40 UAVs, the AECCDC-UAV method has led to in higher THPT of 0.86 Mbps while the T2FL-C, KHA-C, MPSO-C, and PSO-C algorithms have demonstrated a reduced THPT of 0.71, 0.65, 0.59, and 0.52 Mbps respectively. In addition, under 80 UAVs, the AECCDC-UAV approach has caused in a superior THPT of 0.77 Mbps while the T2FL-C, KHA-C, MPSO-C, and PSO-C methods have demonstrated a reduced THPT of 0.60, 0.52, 0.51, and 0.41 Mbps correspondingly. Followed by, under 100 UAVs, the AECCDC-UAV technique has led to in higher THPT of 0.73 Mbps while the T2FL-C, KHA-C, MPSO-C, and PSO-C methodologies have demonstrated a reduced THPT of 0.56, 0.48, 0.47, and 0.38 Mbps respectively.
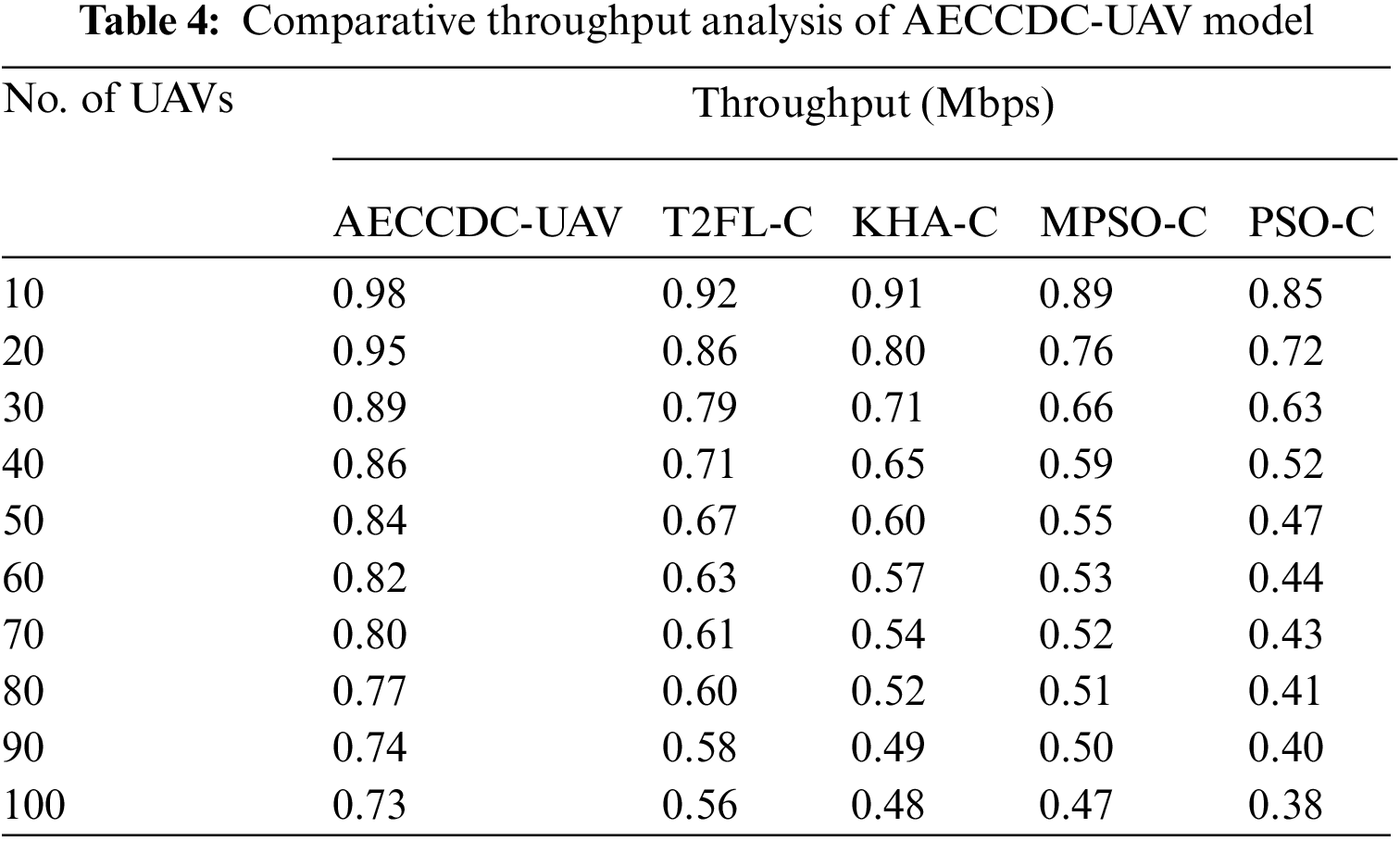
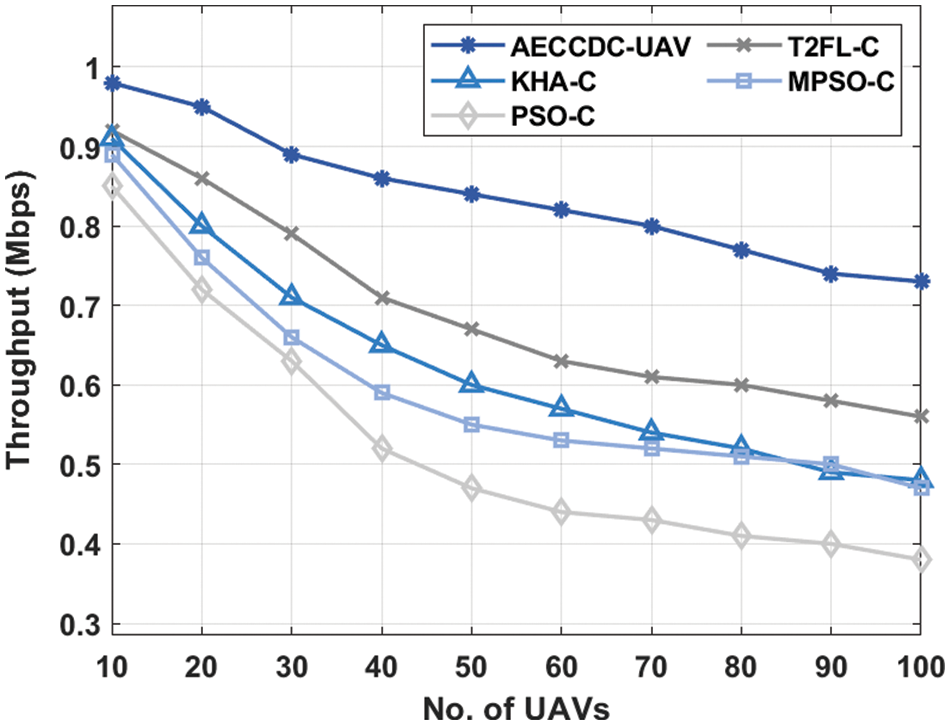
Figure 5: Throughput analysis of AECCDC-UAV model
Tab. 5 and Fig. 6 examines the average delay (ADEL) analysis of the AECCDC-UAV approach with existing methods. From the table values, it is evident that the AECCDC-UAV approach has demonstrated the compared methods by offering minimum ADEL. Also, the PSO-C approach has depicted ineffective outcomes by accomplishing maximum ADEL. For sample, under 10 UAVs, the AECCDC-UAV approach has achieved a lower ADEL of 2.04 s while the T2FL-C, KHA-C, MPSO-C, and PSO-C approaches have gained a maximal ADEL of 2.17, 2.20, 2.27, and 2.86 s respectively. In addition, under 40 UAVs, the AECCDC-UAV approach has achieved a lower ADEL of 2.54 s while the T2FL-C, KHA-C, MPSO-C, and PSO-C approaches have achieved an enhanced ADEL of 4.27, 4.85, 5.67, and 7.86 s respectively. Moreover, under 80 UAVs, the AECCDC-UAV system has reached a reduced ADEL of 6.43 s while the T2FL-C, KHA-C, MPSO-C, and PSO-C approaches have gained a higher ADEL of 7.17, 7.82, 8.36, and 10.39 s respectively. Eventually, under 100 UAVs, the AECCDC-UAV approach has achieved a minimal ADEL of 6.98 s while the T2FL-C, KHA-C, MPSO-C, and PSO-C systems have reaches a superior ADEL of 8.16, 8.92, 9.19, and 11.89 s correspondingly.
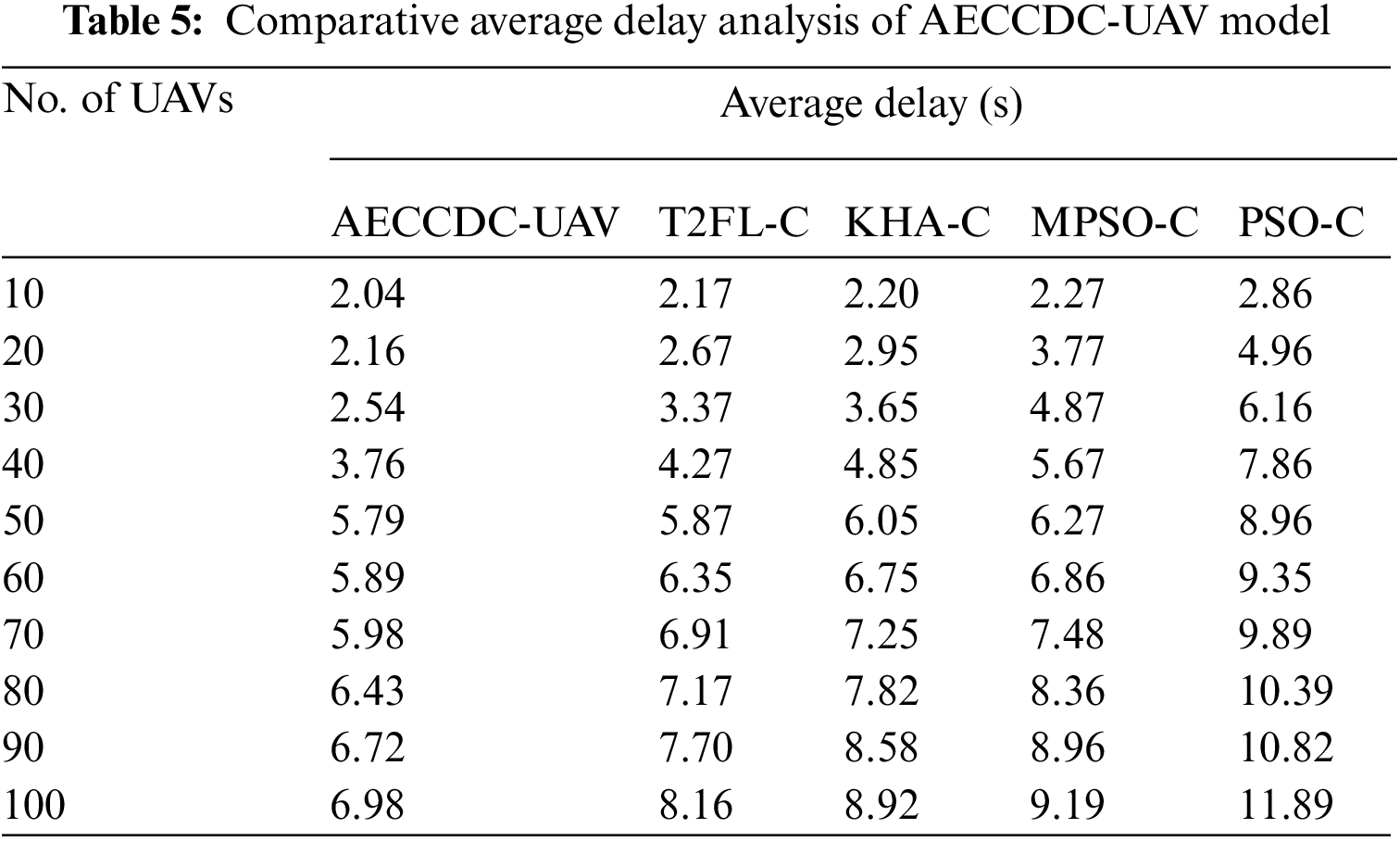
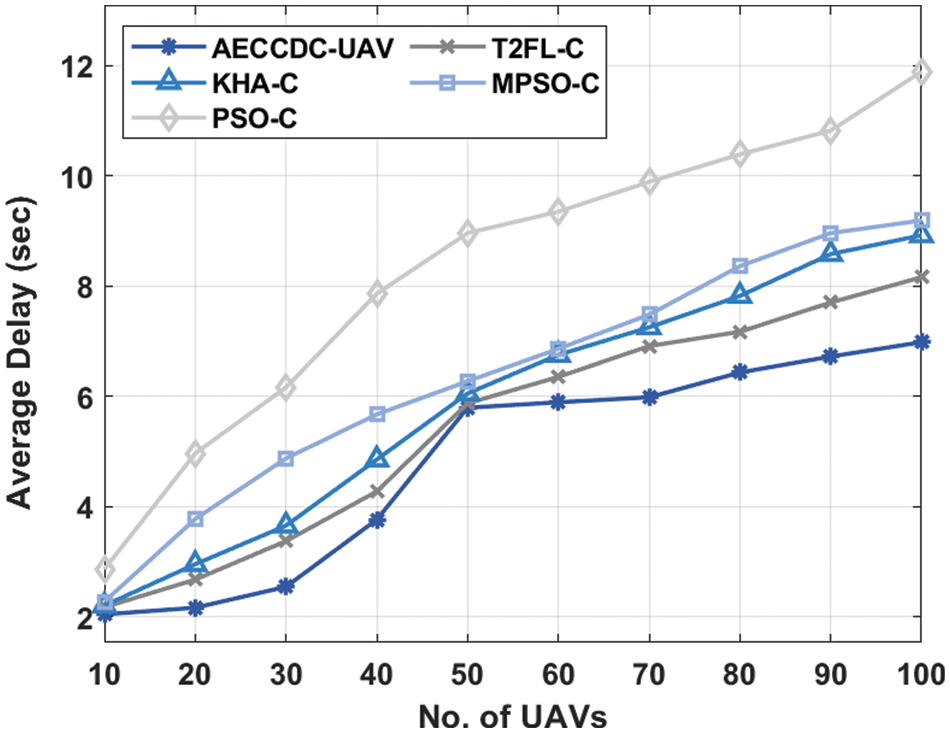
Figure 6: ADEL analysis of AECCDC-UAV model
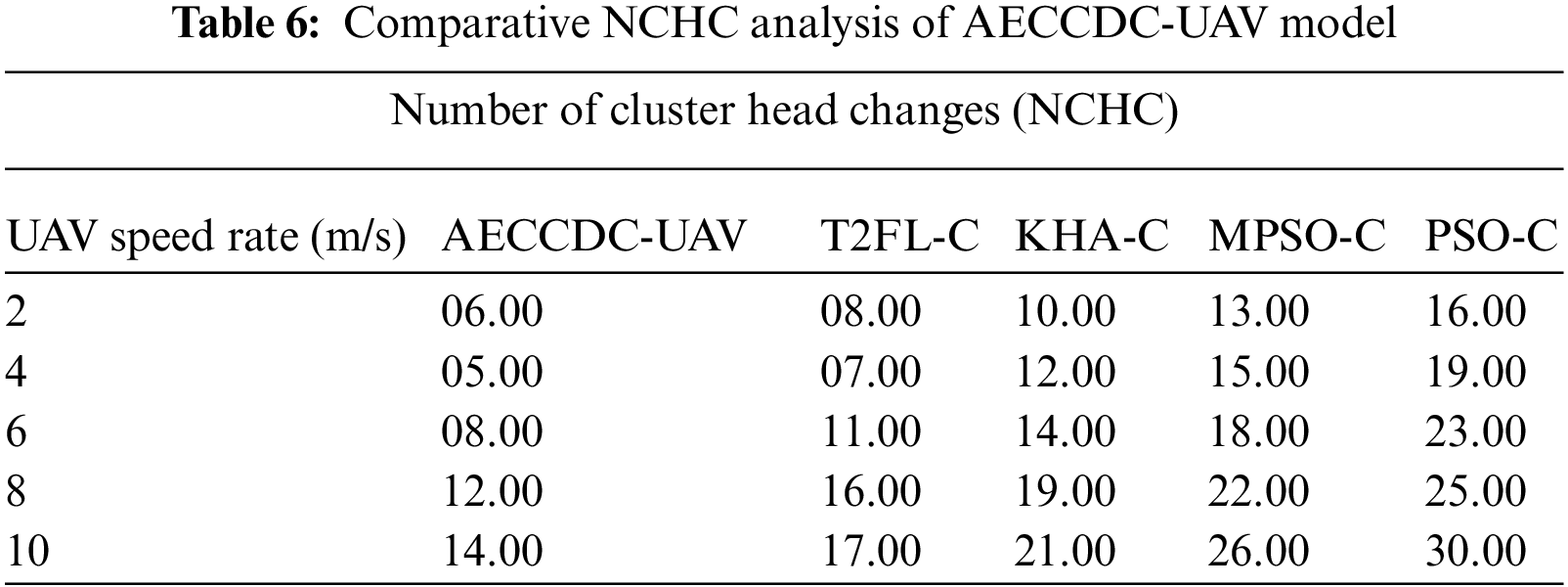
A detailed comparison results analysis of the AECCDC-UAV approach with other methodologies under distinct speed of mobile nodes in Tab. 6. From the achieved outcomes, it can be demonstrated that the AECCDC-UAV approach has exhibited higher outcomes with the minimal NCHC. For sample, with the UAV speed of 2 m/s, the AECCDC-UAV approach has offered a minimum NCHC of 6 while the T2FL-C, KHA-C, MPSO-C, and PSO-C approaches have demonstrated a maximum NCHC of 9, 10, 13, and 16 respectively. Eventually, with the UAV speed of 6 m/s, the AECCDC-UAV approach has offered a minimum NCHC of 8 while the T2FL-C, KHA-C, MPSO-C, and PSO-C approaches have demonstrated a maximum NCHC of 11, 14, 18, and 23 respectively. Meanwhile, with the UAV speed of 10 m/s, the AECCDC-UAV approach has offered a minimum NCHC of 14 while the T2FL-C, KHA-C, MPSO-C, and PSO-C approaches have demonstrated a maximum NCHC of 17, 21, 26, and 30 respectively. From the aforementioned results analysis, it could be stated that the proposed approach is found that an effectual data collection and clustering tool for UAV networks in 6G environment. It allows to effectively collect the data from the deployed environment and cooperatively transmit it to the ground station via intercluster communication.
This paper has established a new AECCDC-UAV approach to achieve energy efficient data collection for UAVs in 6G environment. The proposed AECCDC-UAV approach aims for selecting an optimum group of CHs and construct clusters in such a way that the total ECM of the UAV networks gets reduced. Besides, the integration of QOBL concept to the SSO algorithm supports for considerably enhance the performance of the SSO technique. For validating the improved performance of the AECCDC-UAV approach, a series of simulations are executed and the outcomes are examined under distinct measures. The resultant experimental values make sure the betterment of the AECCDC-UAV approach on the existing techniques under different dimensions. As a part of future scope, the performance of the AECCDC-UAV approach can be improved by the design of optimal route planning process and data compression approaches.
Acknowledgement: This work was supported by the National Research Foundation of Korea(NRF) grant funded by the Korea government(MSIT) (No. 2021R1F1A1063319).
Funding Statement: The authors received no specific funding for this study.
Conflicts of Interest: The authors declare that they have no conflicts of interest to report regarding the present study.
1. G. Manogaran, B. S. Rawal, V. Saravanan, P. M. Kumar, O. S. Martínez et al., “Blockchain based integrated security measure for reliable service delegation in 6G communication environment,” Computer Communications, vol. 161, pp. 248–256, 2020. [Google Scholar]
2. B. Duan, “Evolution and innovation of antenna systems for beyond 5G and 6G,” Frontiers of Information Technology & Electronic Engineering, vol. 21, no. 1, pp. 1–3, 2020. [Google Scholar]
3. E. Madhan, S. Neelakandan and R. Annamalai, “A novel approach for vehicle type classification and speed prediction using deep learning,” Journal of Computational and Theoretical Nanoscience, vol. 17, no. 5, pp. 2237–2242, 2020. [Google Scholar]
4. O. I. Khalaf, G. M. Abdulsahib, H. D. Kasmaei and K. A. Ogudo, “A new algorithm on application of blockchain technology in live stream video transmissions and telecommunications,” International Journal of e-Collaboration, vol. 16, no. 1, pp. 16–32, 2020. [Google Scholar]
5. M. Wang, T. Zhu, T. Zhang, J. Zhang, S. Yu et al., “Security and privacy in 6G networks: New areas and new challenges,” Digital Communications and Networks, vol. 6, no. 3, pp. 281–291, 2020. [Google Scholar]
6. S. K. Lakshmanaprabu, K. Shankar, S. S. Rani, E. Abdulhay, N. Arunkumar et al., “An effect of big data technology with ant colony optimization based routing in vehicular ad hoc networks: Towards smart cities,” Journal of Cleaner Production, vol. 217, pp. 584–593, 2019. [Google Scholar]
7. M. Mozaffari, X. Lin and S. Hayes, “Toward 6G with connected sky: UAVs and beyond,” IEEE Communications Magazine, vol. 59, no. 12, pp. 74–80, 2021. [Google Scholar]
8. S. Neelakandan and S. Muthukumaran, “Transformation-based optimizations framework (ToF) for workflows and its security issues in the cloud computing,” International Journal of Engineering and Computer Science, vol. 4, no. 8, pp. 13746–13753, 2015. [Google Scholar]
9. R. Gupta, A. Nair, S. Tanwar and N. Kumar, “Blockchain-assisted secure UAV communication in 6G environment: Architecture, opportunities, and challenges,” IET Communications, vol. 15, no. 10, pp. 1352–1367, 2021. [Google Scholar]
10. S. Neelakandan, “An efficient cache consistency scheme in mobile networks,” CiiT International Journal of Wireless Communication, vol. 3, no. 9, pp. 604–609, 2011. [Google Scholar]
11. M. Buvanesvari, J. Uthayakumar and J. Amudhavel, “Fuzzy based clustering to maximize network lifetime in wireless mobile sensor networks,” Journal of Advanced Research in Dynamical and Control Systems, vol. 2017, no. 12, pp. 2156–2167, 2017. [Google Scholar]
12. M. A. Khan, A. Safi, I. M. Qureshi and I. U. Khan, “Flying ad-hoc networks (FANETsA review of communication architectures, and routing protocols,” in 2017 First Int. Conf. on Latest Trends in Electrical Engineering and Computing Technologies (INTELLECT), Karachi, Pakistan, pp. 1–9, 2017. [Google Scholar]
13. A. Khan, F. Aftab and Z. Zhang, “BICSF: Bio-inspired clustering scheme for FANETs,” IEEE Access, vol. 7, pp. 31446–31456, 2019. [Google Scholar]
14. M. Y. Arafat and S. Moh, “Bio-inspired approaches for energy-efficient localization and clustering in UAV networks for monitoring wildfires in remote areas,” IEEE Access, vol. 9, pp. 18649–18669, 2021. [Google Scholar]
15. O. M. Gul and A. M. Erkmen, “Energy-efficient cluster-based data collection by a uav with a limited-capacity battery in robotic wireless sensor networks,” Sensors, vol. 20, no. 20, pp. 5865, 2020. [Google Scholar]
16. K. Kumar, M. Goswami and R. Arya, “Energy-efficient clustering of uavs with crow search interaction,” in 2nd Int. Conf. on Communication & Information Processing (ICCIP), The Nutan College of Engineering and Research (NCERTalegaon-Dabhade, Pune, India, 2020, https://doi.org/10.2139/ssrn.3658897. [Google Scholar]
17. S. C. Noh, H. B. Jeon and C. B. Chae, “Energy-efficient deployment of multiple uavs using ellipse clustering to establish base stations,” IEEE Wireless Communications Letters, vol. 9, no. 8, pp. 1155–1159, 2020. [Google Scholar]
18. J. Yu, R. Zhang, Y. Gao and L. L. Yang, “Modularity-based dynamic clustering for energy efficient uavs-aided communications,” IEEE Wireless Communications Letters, vol. 7, no. 5, pp. 728–731, 2018. [Google Scholar]
19. M. Y. Arafat and S. Moh, “Localization and clustering based on swarm intelligence in uav networks for emergency communications,” IEEE Internet of Things Journal, vol. 6, no. 5, pp. 8958–8976, 2019. [Google Scholar]
20. Z. Na, Y. Liu, J. Shi, C. Liu and Z. Gao, “UAV-Supported clustered noma for 6G-enabled internet of things: Trajectory planning and resource allocation,” IEEE Internet of Things Journal, vol. 8, no. 20, pp. 15041–15048, 2021. [Google Scholar]
21. S. Poudel and S. Moh, “Hybrid path planning for efficient data collection in uav-aided wsns for emergency applications,” Sensors, vol. 21, no. 8, pp. 2839, 2021. [Google Scholar]
22. Y. Yin, M. Liu, G. Gui, H. Gacanin, H. Sari et al., “Cross-layer resource allocation for uav-assisted wireless caching networks with NOMA,” IEEE Transactions on Vehicular Technology, vol. 70, no. 4, pp. 3428–3438, 2021. [Google Scholar]
23. K. Lin, Y. Li, Q. Zhang and G. Fortino, “AI-driven collaborative resource allocation for task execution in 6G-enabled massive IoT,” IEEE Internet of Things Journal, vol. 8, no. 7, pp. 5264–5273, 2021. [Google Scholar]
24. A. Kaveh, A. Zaerreza and S. M. Hosseini, “Shuffled shepherd optimization method simplified for reducing the parameter dependency,” Iranian Journal of Science and Technology, Transactions of Civil Engineering, vol. 45, no. 3, pp. 1397–1411, 2021. [Google Scholar]
25. M. Basu, “Quasi-oppositional differential evolution for optimal reactive power dispatch,” International Journal of Electrical Power & Energy Systems, vol. 78, pp. 29–40, 2016. [Google Scholar]
26. Y. Sun, Z. Mi, H. Wang, F. Lu and N. Zhao, “Adaptive enhanced weighted clustering algorithm for uav swarm,” in 2020 IEEE 20th Int. Conf. on Communication Technology (ICCT), Nanning, China, pp. 709–714, 2020. [Google Scholar]
 | This work is licensed under a Creative Commons Attribution 4.0 International License, which permits unrestricted use, distribution, and reproduction in any medium, provided the original work is properly cited. |