DOI:10.32604/cmc.2022.028287

| Computers, Materials & Continua DOI:10.32604/cmc.2022.028287 |  |
| Article |
HDLIDP: A Hybrid Deep Learning Intrusion Detection and Prevention Framework
1Computer Engineering and Systems Department, Faculty of Engineering, Mansoura University, Mansoura, 35516, DK, Egypt
2Head of Communications and Computer Engineering Department, MISR Higher Institute for Engineering and Technology, Mansoura, 35111, DK, Egypt
3Mechatronics Department, Faculty of Engineering, Horus University in Egypt (HUE), New Damietta, 34517, DT, Egypt
*Corresponding Author: Magdy M. Fadel. Email: mfares@mans.edu.eg
Received: 07 February 2022; Accepted: 25 March 2022
Abstract: Distributed denial-of-service (DDoS) attacks are designed to interrupt network services such as email servers and webpages in traditional computer networks. Furthermore, the enormous number of connected devices makes it difficult to operate such a network effectively. Software defined networks (SDN) are networks that are managed through a centralized control system, according to researchers. This controller is the brain of any SDN, composing the forwarding table of all data plane network switches. Despite the advantages of SDN controllers, DDoS attacks are easier to perpetrate than on traditional networks. Because the controller is a single point of failure, if it fails, the entire network will fail. This paper offers a Hybrid Deep Learning Intrusion Detection and Prevention (HDLIDP) framework, which blends signature-based and deep learning neural networks to detect and prevent intrusions. This framework improves detection accuracy while addressing all of the aforementioned problems. To validate the framework, experiments are done on both traditional and SDN datasets; the findings demonstrate a significant improvement in classification accuracy.
Keywords: Software defined networks (SDN); distributed denial of service attack (DDoS); signature-based detection; whale optimization algorism (WOA); deep learning neural network classifier
Nowadays, the increasing use of Internet services like, data centers, electronic trade and cloud computing [1,2], causes computer network’s size increases drastically and becomes hardly managed. Software defined networks (SDN) with its centralized management [3,4], dynamic and programmable architecture becomes more suitable for huge networks rather than using traditional computer networks. The general working strategy of Distributed Denial of Service (DDoS) attacks depends on sending an enormous number of packets to network resources to hamper or even block the reachability of legitimate users [5,6]. However, by deeply studying the structure of both computer networks architecture (traditional and SDN), DDoS attacks specific to SDN characterized by some points. First, SDN attacks aim to exhaust only the network’s controller, while traditional networks have many points where attacks can be launched [7]. Second, the attacking packets usually pretend to have fake destination IP addresses, but in traditional networks, the destination IP addresses should be the IP of the targeted server to down [7].
Most of the detection and defense techniques used with SDN are literally a transplanting of traditional network techniques without taking in account the own characteristics of SDN environments. The processes of attack detection and defense are implemented on the SDN controller which increases computation overhead on the processor as well as the communication between SDN controller and switches (south bound) [7]. Several optimization techniques have been deployed to overcome these problems, as Genetic Algorithm (GA) [8], Firefly Algorithm (FF) [9], Particle Swarm Optimization (PSO) [10] and Whale Optimization Algorithm (WOA) [11]. Many of them have their limitations; such GA is more complex, depends on the initial population, and may fail to parameter convergence [8]. PSO has a poor control on discrete optimization problems and easy falls in local optima [10]. Due to these limitations, many hybridized and improved techniques have been applied to the original versions of Machine Learning (ML) to enhance their performance.
This paper deploys the detection of suspicious traffic at the data plane (switches) to alleviate both processing and communication overhead. The process of classifying suspicious packets executed at the controller plane is carried out by two techniques, signature-based [5,12] and deep learning-based to improve the accuracy and reduce the time of the classification process [13–15]. In signature-based technique every packet passes through the network have a unique pattern (signature) that is composed by intermediate routers while traversing through the network [16]. Signatures of malicious packets are stored in an attack signatures database, to be used later for identifying any attack packet that has a signature included in it. This technique has a high accuracy and a low false negative rate, but can’t detect new (day zero) attacking packets that are not involved in the attack signatures database [17].
An optimized Neural Network (NN) with a set of optimal extracted features is used to classify and detect new offensive packets as part of the proposed deep learning technique. Combining both techniques allows the network to learn new attack patterns and append them to the attack signature database automatically for future use [13]. The contribution of this paper is as follows:
• Developing DDoS attack detection system that uses both signature-based and deep learning techniques to enhance the detection accuracy in SDN networks.
• Using the Neural Network to select the effective traffic feature set and to tune it (number of hidden layers and number of neurons in each layer), for decreasing the detection time and increasing the accuracy of the detection process.
• Validating the proposed framework using both traditional and SDN datasets to ensure it can handle both environments.
The remainder of this paper is organized as follow: the next section gives an overview of the related work, Section 3 describes the proposed framework in detail, Section 4 presents the experimental results and performance evaluation and finally Section 5 concludes the paper.
Different detection and defense approaches are implemented by research community of defense since the first reported DDoS attacks in 1999 [18]. This section discusses two integrated categories of anomaly-based detection techniques, statistical approaches and artificial intelligence approaches.
2.1 Statistical Detection Approaches
Also called entropy-based approaches, entropy is the measure of the randomness in a dataset. Since every feature of normal network traffic has a special distribution pattern, for example a balance between the count of source and destination IP addresses in normal flow. This entropy pattern will deviate in attack flows since the number of destination IP addresses greatly increases than the number of source IP addresses. Despite this approach is characterized by a fast response and a low computation overhead of processing a large traffic volume. Its detection accuracy is greatly affected by the proper selection of the threshold value for a certain traffic feature to reduce the ratios of false positive and false negative.
In [19] authors proposed a hybrid system for attack detection that merges both entropy and traffic volume characteristics, which offers good results than using each technique alone. Kalkan et al. [20] introduced a joint entropy-based scoring system (JESS) to defend attacks in SDN environments, by utilizing Joint entropy they can defend even unfamiliar attacks efficiently. Lima et al. [21] suggested a system based on statistical analysis of traffic entropy in SDN environments.
Wang et al. [22] proposed a flow statistics process in SDN switches, then performed lightweight entropy-based detection model executed in the edge switches to reduce the communication overhead between the data plane and controller plane. Ahmed et al. [23] introduced a new structure called application fingerprints to express packet attributes and traffic flow level statistics to differentiate legitimate packets from attack packets. However, this approach is not proper for online systems, since some flow attributes such total bytes, number of packets between source and destination and flow duration cannot compute their statistics while gathering them. In [24] authors introduced new hybrid approaches where flow level statistics or entropy based are combined with some techniques of Machine Learning (ML) or Artificial Neural Networks (ANN) to overcome some limitations of flow statistics approaches. The ML and ANN mechanisms will be introduced in detail in the next subsection.
2.2 Artificial Intelligence (AI) Detection Approaches
Buczak et al. [25] introduced summaries for different methods of Machine Learning (ML) and Data Mining (DM) used for attack detection, such Support Vector Machine (SVM), k-Nearest Neighbor (k-NN), Random Forest (RF), etc. over recent years, with the abundance of real network traffic datasets. These methods perform better results in traffic classification field.
He et al. [26] suggested a new source side (active defense) machine learning technique instead of defending attacks at destination side (passive defense) preventing malicious network flows from being sent outside the attacking network. This showed a high accuracy and low false positive rates. Hoon et al. [27] introduced the concept of dataset feature selection which reduces the feature engineering processes and increasing classification accuracy. Few papers addressed the implementation of Deep Learning (DL) approaches in attack detection; authors in [28] combined the entropy-based techniques with DL methods to easily control the problem of setting accurate threshold. Conducted experiments showed a high accuracy. Yin et al. [29] proposed a deep learning attack detection model deploying a Recurrent Neural Network (RNN) to perform binary and multiclass classification. They compared its performance with a set of known Machine Learning (ML) models such SVM, Random Forest (RF) and Artificial Neural Networks (ANN). Their proposed model showed a higher performance from point of accurate classification. Wu et al. [30] introduced a multiclass Convolutional Neural Network (CNN) intrusion detection system, deploying CNN to select highly related features from the massive data gathered to improve the classification accuracy and reduce computation overload. Over traditional ML algorithms, CNN showed better performance. Kwon et al. [31] studied the performance of three different models of CNN (shallow, moderate and deep) to check the effect of depth of the CNN to the detection performance. The models are verified using two datasets NSL-KDD [32] and MAWILab [33] showing that shallow CNN model with a single convolutional layer and single maximum pooling layer performed best.
Authors in [34] converted the suspicious traffic traces into arrays that contain flow features by combining both CNNs and RNNs, testing their model on ISCX2012 dataset [35] showing good results from point of reducing classification error from 7.517% to 2.103% relative to conventional machine learning algorithms. Despite the efficiency of deep learning algorithms for detecting DDoS attacks, they are time-consuming, resource-intensive, and require large numbers of model parameters to be trained.
3 The Proposed Hybrid Deep Learning Intrusion Detection and Prevention (HDLIDP) Framework
Traditional networks’ routers are assigned many customary duties like determining packets routes, assigning priorities, carrying out policies specified by the network administrator and many others, so they cannot detect and respond to DDoS attacks automatically. By leveraging SDN architecture, these attacks can be processed automatically and yield a fast and accurate response. Fig. 1 illustrates that.

Figure 1: Traditional vs. SDN network architectures
Three layers SDN architecture is show in Fig. 2, the switching task is split between a data layer and a control layer that are implemented on separate devices. The data plane is mainly responsible for forwarding network packets, while the brain or control plane performs all intelligent tasks in the network. In standard SDN, the control layer performs both the attack detection and defense tasks this may increase the controller’s CPU utilization and communication workload through southbound interface, observe hourly the traffic flowing through switches to detect the DDoS attack.

Figure 2: SDN three layers architecture
The proposed framework (HDLIDP) may help to overcome this defect. It is made up of two layers, Data Layer Detection (DLD) and Control Layer Defense (CLD) as depicted in Fig. 3.

Figure 3: The proposed (HDLIDP) framework
3.1 Data Layer Detection (DLD)
This layer detects any suspicious flows and raises an alarm to the control layer for accurately classifying whether it is an actual DDoS attack or legitimate burst traffic then carrying out proper response. This way the load on CPU Controller and the traffic overload through southbound interface may decrease drastically, it is designed as two modules:
3.1.1 Legitimate Traffic Module
Packets in SDN arrive first at the data plane devices, these packets may be classified into four categories: Known traffic that is already found in the switch’s forwarding table; hence it is forwarded to its proper destination. The second type is a new legitimate traffic, when the switch does not find matching entries in its forwarding table, and after sending a pktIN message to the controller it will get a reply with a suitable forwarding route to be registered in its forwarding table for future use. The other two categories occur when the switch receives a suspicious packet. Such a packet does not have a matching entry in the forwarding table, and the controller does not able to determine its forwarding route, due to tampering in the source and/or destination IP addresses of it. All DDoS detection systems are concerned about the arrival rate of the last two categories of received packets (suspicious).
3.1.2 Suspicious Traffic Module
The maximum packets counter method is utilized at the data plane to calculate the suspicious packet’s arrival rate within a predefined time window. In the framework, when a switch classifies the received packet as a suspicious flow, the suspicious flow counter is incremented (Susp++) and its features appended in both current interval and training datasets. Then, the value of the Susp variable is compared with the value of predefined adaptive maximum attacking packets (Val). The detection is in safe condition if Susp value is less than Val, so dropping this packet and processing any new incoming one.
Otherwise, if Susp equals or exceeds the predefined value (Val), the detection system calculates the time window, packets’ arrival rate (PR) and initializes all counters. If the packets’ arrival rate (PR) exceeds the predefined value, a suspicious alarm is raised to the control layer.
3.2 Control Layer Defense (CLD):
This layer is composed of two modules, Signature Based Detection and Deep Learning Classification.
3.2.1 Signature Based Detection Module
Traceback enabled routers utilize one of two techniques to insert their identification ID numbers in the packet’s header, Deterministic Packet Marking (DPM) [36] or Probabilistic Packet Marking (PPM) [37]. The accumulation of all IDs along the packet’s path forms what is called path’s signature. It is used to characterize the exact route of received packet regardless of its source IP address that could be easily forged. After isolating attacking traffic, its signature is stored in attack signature database for future use.
3.2.2 Deep Learning Classification Module
Is the conclusive classification stage that identifies the fourth category of suspicious packets. Because of the large-scale exploration of the search space, the simplicity of implementation, the wide range of applications and its potential development [10], the Whale Optimization Algorithm (WOA) is used to select the optimal set of features and to tune parameters of the classification Neural Network.
The WOA is an optimization algorithm that mimics the hunting mechanism of humpback whales in nature. Whales prefer to hunt in a group of whales, initially every whale searches globally for a prey in a random direction, this process is called exploration phase, the following mathematical model illustrates it.
where:
Since the optimum position of the prey in the search space is not known previously, the group of whales will communicate to identify the current best elected solution. The other whales will update their direction towards the current elected whale; this step is called exploitation phase, modeled as follows:
where:
where: p is a random number in [0,1].
In encircling prey, after defining the best search agent, the other search agents will try to update their positions towards the best search agent. This behavior is represented by the following equations:
where:
The pseudo of WOA is shown in Algorithm 1.

Fig. 4 represents the four stages deployed to determine the status of the received packet. The first two stages (searching the switch’s forwarding table and inquiring the controller to specify the packet forwarding path) are performed by any standard SDN environment. While the other two stages (search attack signature DB and a deep learning classification) are appended. Algorithm 2 and the logic diagram of the received packet flow status in Fig. 4 clarify the classification process in detail.

Figure 4: Received packet flow status

A hybrid classification algorithm composed of Whale Optimization Algorithm (WOA) in Tab. 1 and a tuned Neural Network (NN) in Tab. 2 is used in experiments. WOA is used to select the most effective set of features from the used datasets, whereas the tuned ANN is used to accurately classify the newly unknown suspicious packets, reducing the computation overhead and increasing the IDS classification accuracy.


The framework is evaluated using three datasets, NSL-KDD and CSE-CIC-IDS2018 are the most traditional network’s datasets commonly used, where the third is SDN specific dataset. First, NSL-KDD dataset contains 4,898,430 records each of 41 features. Feature no. 42 is the records’ labels, which may be Normal or attack; attack records are categorized into 4 types DoS, Probe, R2L or U2R.
Despite its simplicity, NSL-KDD dataset is not the ideal representation of the actual network model, so CIC-IDS2018 dataset is used to accurately evaluate any IDS since it represents real attacks. It has 83 features, of 2,830,540 distinct records, and categorized in the label field to 15 classes.
Although the characteristics of CIC-IDS2018 dataset have some weaknesses, first with this huge number of records (3,119,345) and 83 features each, enormous loading and processing overhead is required. Second, it contains some missing data. The last demerit is class imbalance problem [38], in which different attacking classes do not have equal number of instances, some are represented by a large number (BENIGN = 2,359,087 instances) others have few number (HeartBleed = 11 instances). So, when using this dataset for training classifiers or detectors it will make the classifiers biasing toward the majority class [38] degrading the classifier’s accuracy with a higher false ratio. Alleviating methods for these shortcomings will be introduced in the Data preprocessing subsection.
Since the architecture of traditional network differs from that of SDN, which results in a major difference in the feature sets of the data gathered from both. Mininet emulator [39] software has been used to create a realistic virtual network, 23 features in the designed SDN topology with the total number and different categories used in following experiments.
Network collected dataset may include some error values like duplicate, infinity, missing or categorical data, this may cause classification problems. These error values should be eliminated or mitigated before training and testing phase. Duplicate records should be removed, deleting records having outlier’s values. Techniques like one-hot encoder are used to convert categorical data into numeric values.
Feature scaling methods (Normalization and Standardization) [40]: features having values of varying degrees of magnitude, may hurdle the performance of some machine learning algorithms especially those types using gradient descent as optimization techniques. So, these scaling methods may be used to scale their values between 0 and 1, or +a and –a.
Data imbalance reduction [41]: where some features are highly underrepresented, causing the classifier to bias towards the majority features. Many techniques are designed to handle class imbalance problem, one of them deployed in this paper is class relabeling. By either splitting the majority classes into more classes or merging some minority classes to form one class.
Evaluating the trained model’s performance can be done using the confusion matrix and advanced evaluation metrics are shown in Fig. 5.

Figure 5: Confusion matrix and evaluation metrics
True Positive (TP): denotes the no. of positive class correctly judged as positive. False Negative (FN): denotes the no. of positive class mistakenly judged as negative. False Positive (FP): denotes the no. of negative class mistakenly judged as positive. True Negative (TN): denotes the no. of negative class correctly judged as negative.
Three experiments have been conducted to validate the performance of the (HDLIDP) framework.
Experiment 1: (NSL-KDD dataset): using a two hidden layers tuned ANN classifier.
Tab. 4 shows the advanced metrics obtained from the confusion matrix shown in Tab. 3. The average results of confusion matrix when utilizing two hidden layers are 97.903, 91.690, 98.271 and 94.798 for Accuracy, Precision, Recall and F1 Score, respectively.

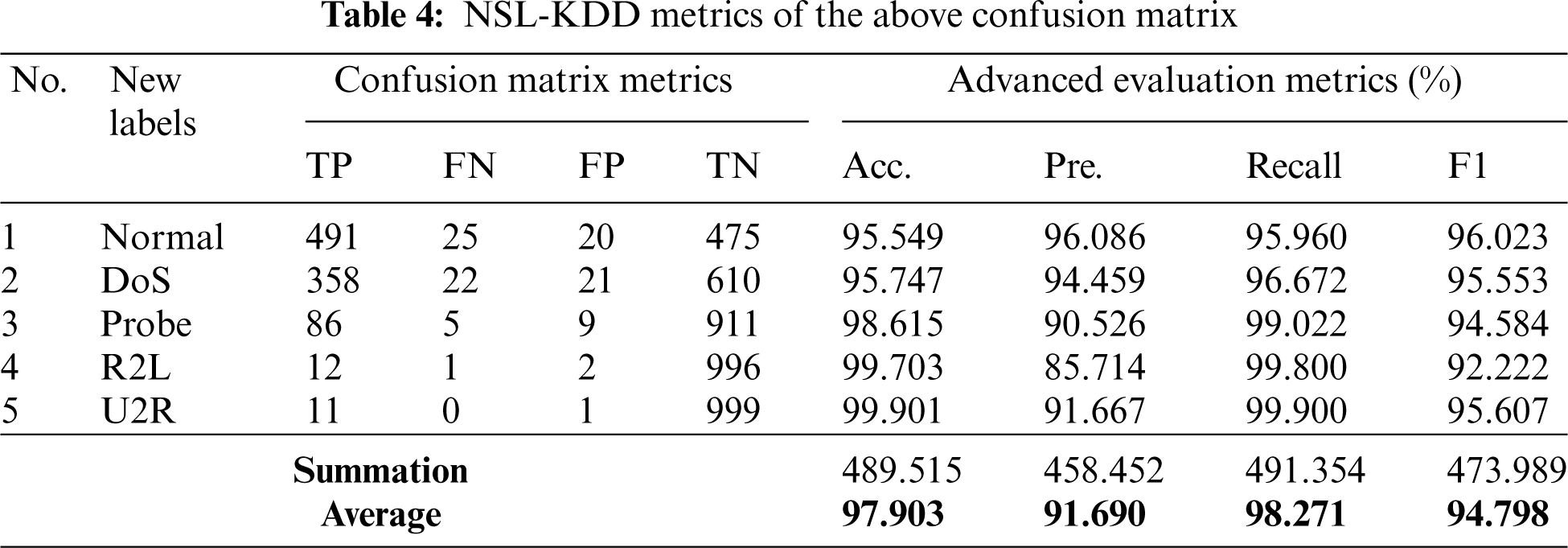
Tab. 5 and Figs. 6 and 7 show the parameters of the ANN classification in case of single, two and three hidden layers compared with the Genetic Algorithm (GA) and Difficult Set Sampling Technique (DSSTE) algorithm. The DSSTE algorithm employs both Edited Nearest Neighbor (ENN) and K-Means clustering algorithms to reduce the data set’s majority class for improving the classifier’s training stage consequently enhances performance. The results show, using two hidden layers NN each contains maximum of 10 neurons provides best performance and approximately good time.
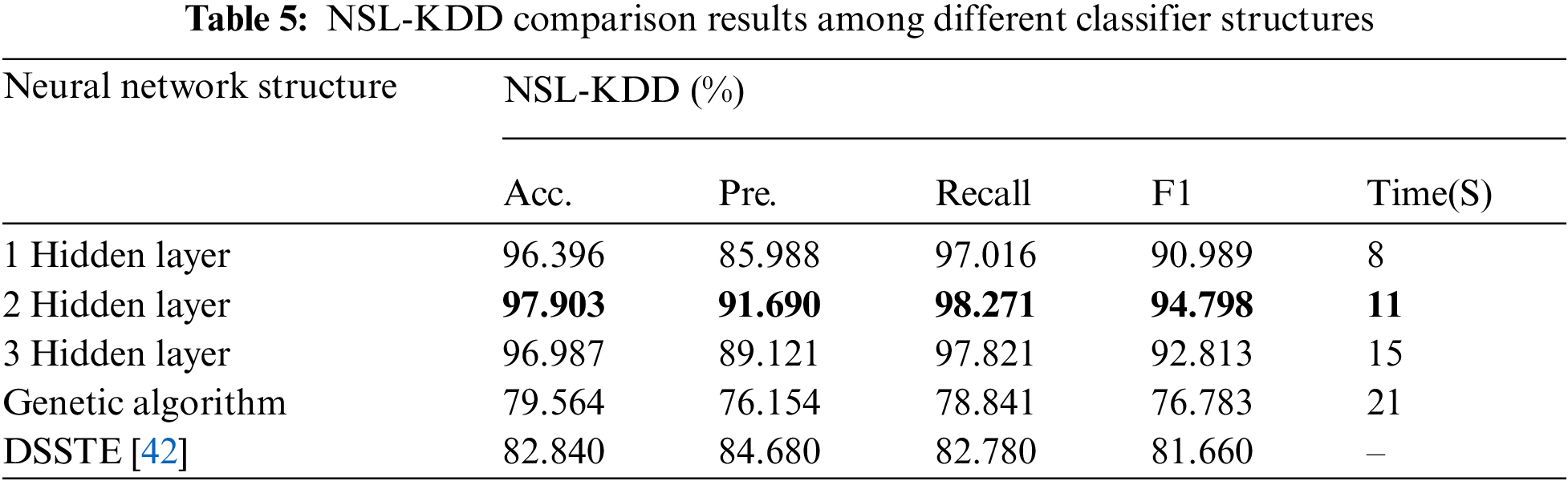

Figure 6: NSL-KDD comparison results among deep learning classifier with different hidden layers

Figure 7: NSL-KDD Time comparison results among DL classifier with different hidden layers
Experiment 2: (CIC-IDS2018 dataset): using a two hidden layers tuned ANN classifier.
Tabs. 6 and 7 show the average results of confusion matrix as 99.849, 93.333, 99.761 and 96.325 for Accuracy, Precision, Recall and F1 Score, respectively.
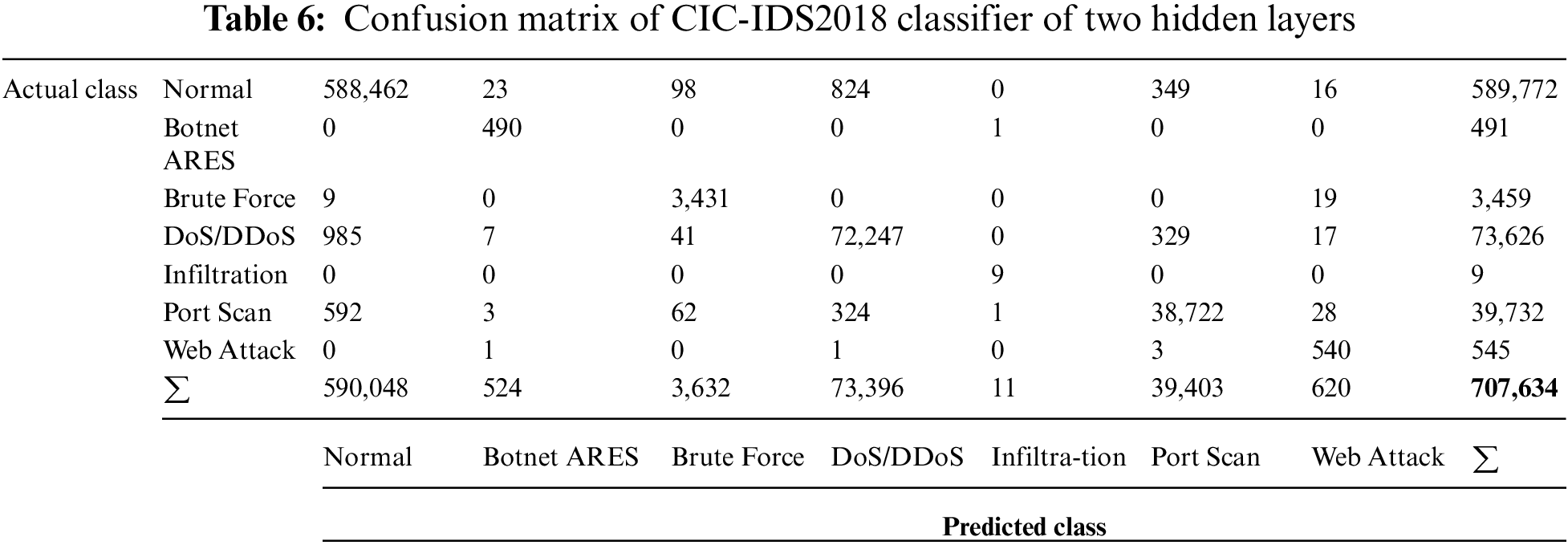
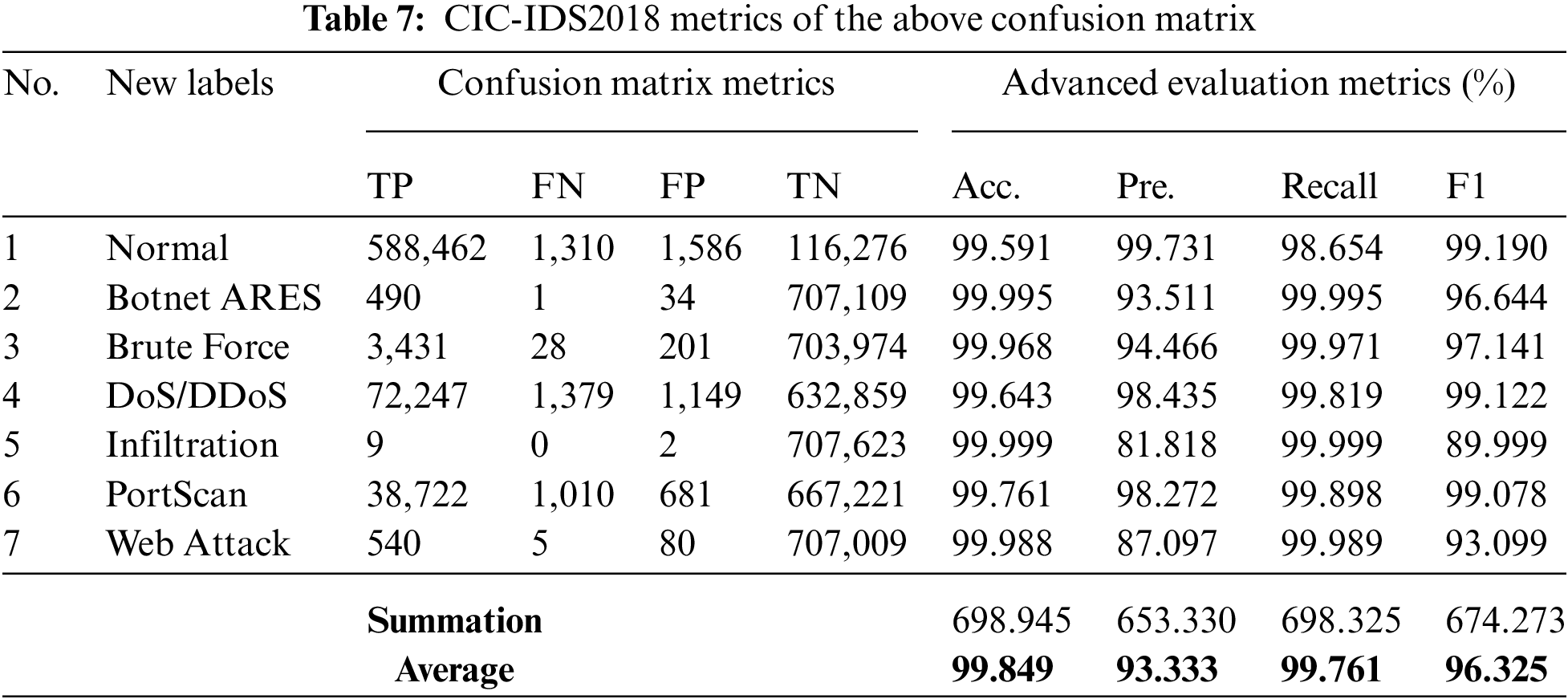
Since the framework has been designed to be deployed in real time world, so both performance accuracy and running time should be highly improved. From Tab. 8 and Figs. 8 and 9, show that the best accuracy is obtained when using two hidden layers NN, while the best running time obtained with a single hidden layer NN. According to the results obtained, it is advised to deploy the framework with two hidden layers NN as it has best accuracy and approximately good running time.

In the next experiment, the proposed framework is evaluated using SDN dataset collected from the Mininet emulator and comparing its results with those of the framework introduced in [43].

Figure 8: CIC-IDS2018 comparison results among DL classifier with different hidden layers

Figure 9: CIC-IDS time comparison results among DL classifier with different hidden layers
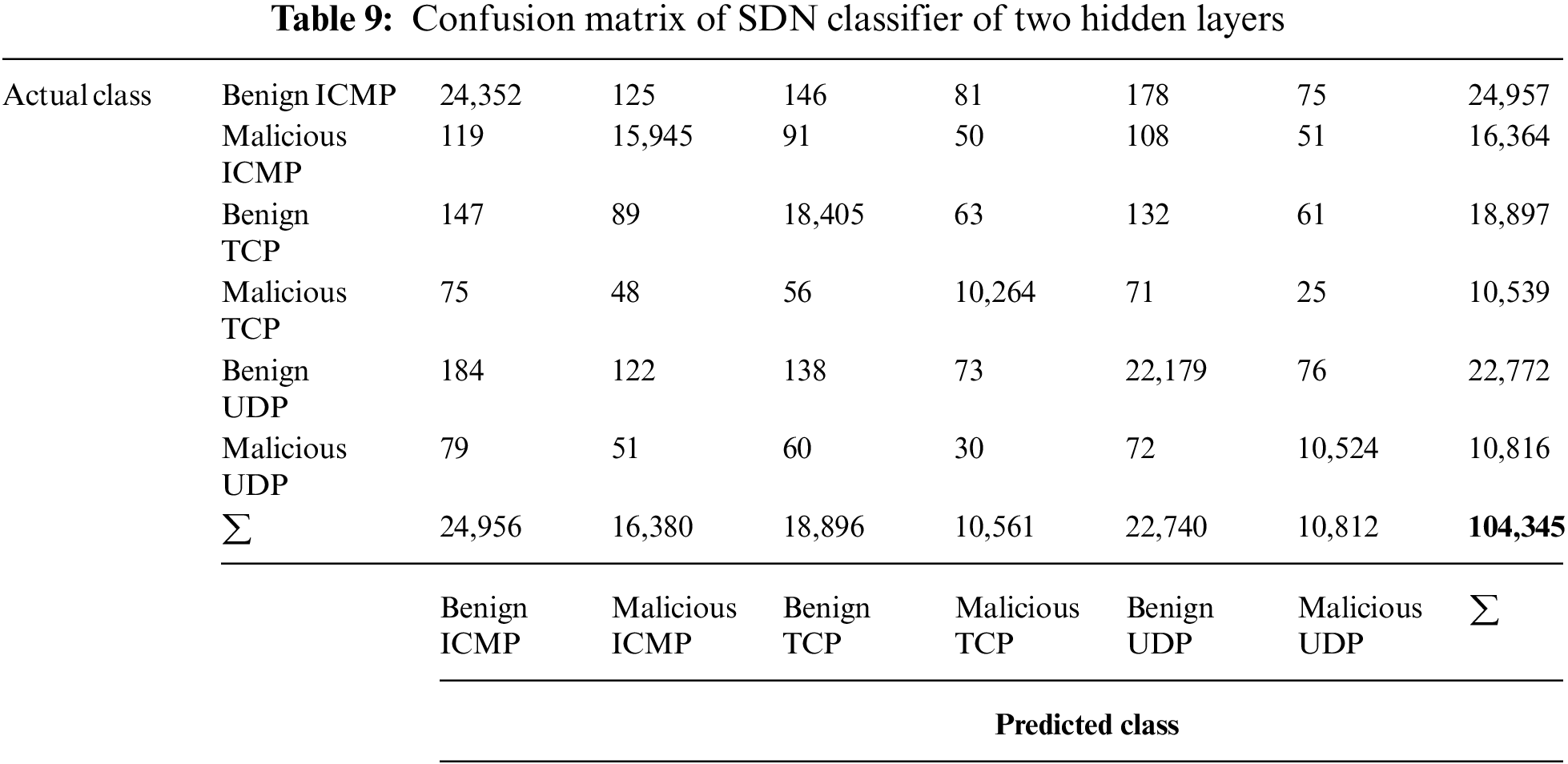
Experiment 3: (SDN dataset): the experiment has been done on a two hidden layers ANN classifier.
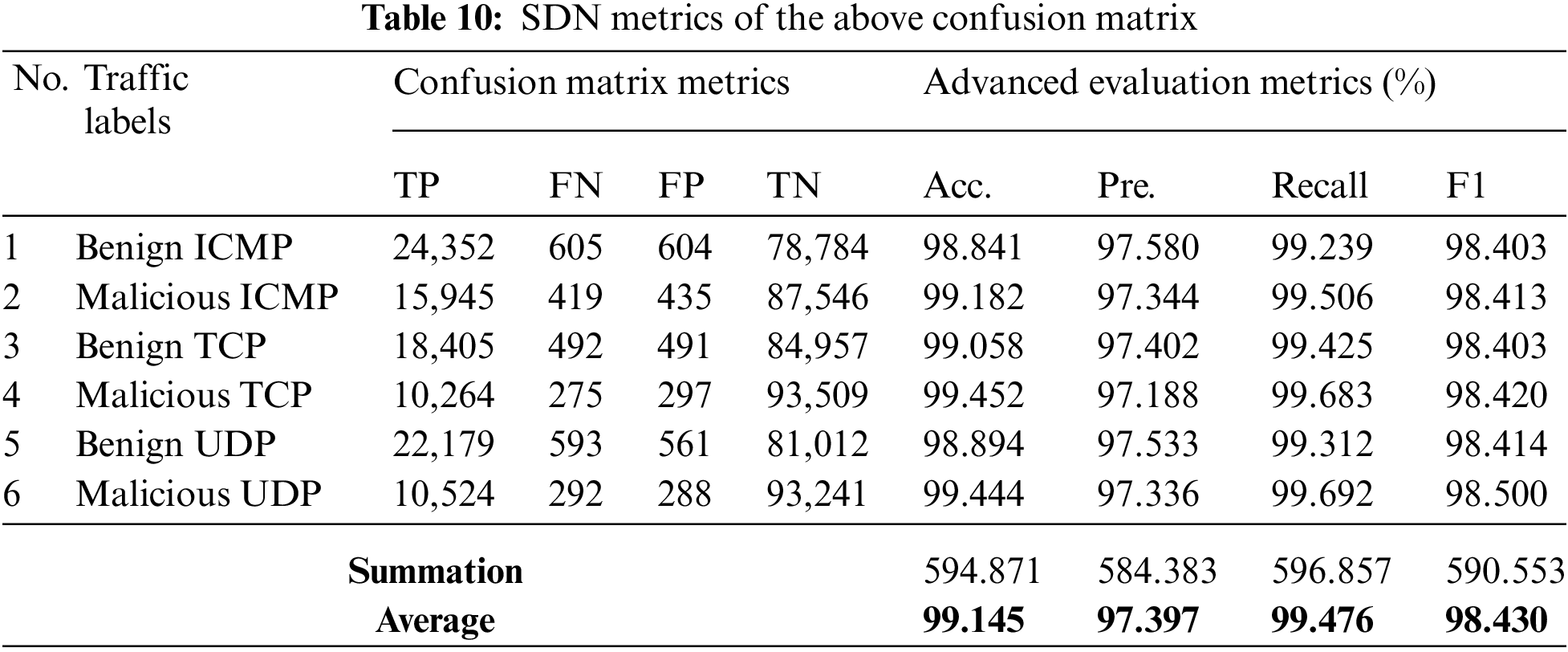
Tabs. 9 and 10 shows the average values of Accuracy, Precision, Recall and F1 Score.
Tab. 11 and Fig. 10 show a comparison in case of one, two and three hidden layers with the GA and Automated DDoS attack detection in SDN [43] framework.
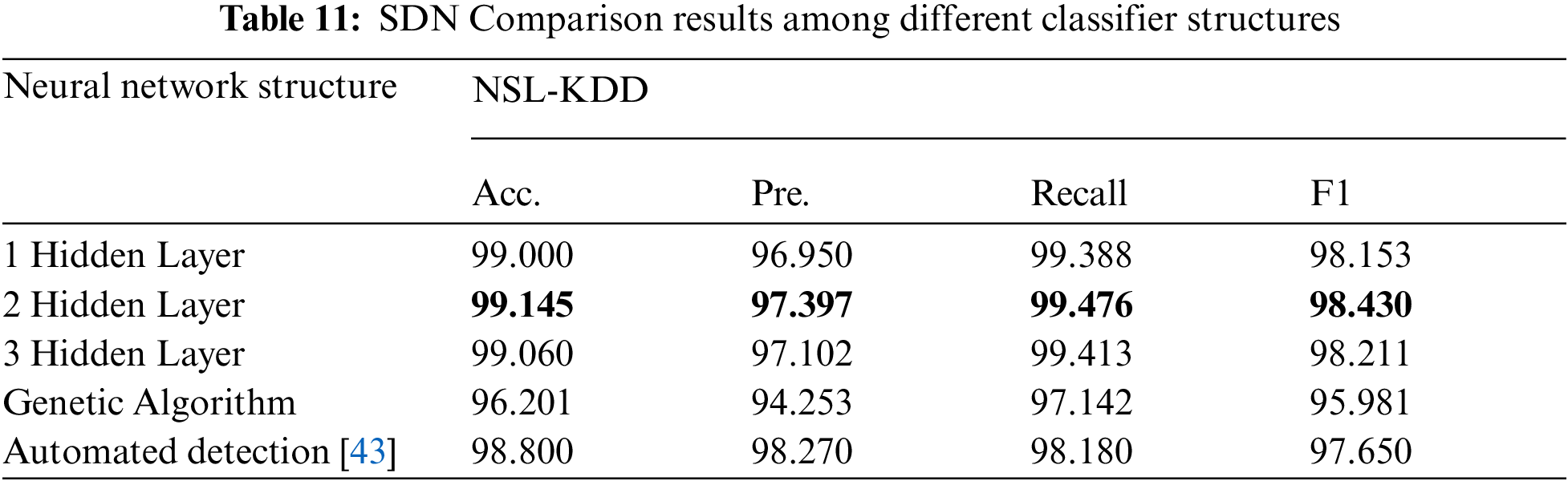

Figure 10: SDN comparison results among DL classifier with different hidden layers
Despite the importance of computer networks and its different services, it is difficult to manage and secure a huge number of distributed devices. A Hybrid Deep Learning Intrusion Detection and Prevention framework (HDLIDP) that is suitable for use with SDN networks has been proposed in this paper. Signature-based and deep learning detection techniques have been deployed to improve framework performance. A signature based technique ensure that a packet is an attack, but not that it is legitimate, while deep learning technique classifies packets based on their type, if it is an attacker or not, successfully taking the needed action. Both techniques may improve attack detection accuracy and speed. The outcomes are determined by important factors such as classification accuracy and system responsiveness. A comprehensive study has been conducted using three datasets that have been applied to single, two, and three layers NN classifiers. Additionally, we cannot ignore the role played by using the WOA optimizer in selecting the effective set of dataset’s features for improving the classification process. Results revealed the superiority of the proposed framework, especially in cases of double NN hidden layers. In future, the proposed framework could be improved by deploying different optimization algorithms and evaluated by using more SDN environment datasets.
Funding Statement: The authors received no specific funding for this study.
Conflicts of Interest: The authors declare that they have no conflicts of interest to report regarding the present study.
1. S. Azizi, N. Hashemi and A. Khonsari, “A flexible and high-performance data center network topology,” Supercomputing, vol. 73, no. 4, pp. 1484–1503, 2017. [Google Scholar]
2. M. Birje, P. Challagidad, R. H. Goudar and M. T. Tapale, “Cloud computing review: Concepts, technology, challenges and security,” International Journal of Cloud Computing, vol. 6, no. 1, pp. 32–57, 2017. [Google Scholar]
3. D. S. Rana, S. A. Dhondiyaland and S. K. Chamoli, “Software defined networking (SDN) challenges, issues and solution,” International Journal of Computer Science and Engineering, vol. 7, no. 1, pp. 884–889, 2019. [Google Scholar]
4. S. H. Haji, S. R. M. Zeebaree, R. H. Saeed, S. Y. Ameen, H. Shukur et al., “Comparison of software defined networking with traditional networking,” Asian Journal of Computer Science and Information Technology, vol. 9, no. 2, pp. 1–18, 2021. [Google Scholar]
5. M. M. Fadel, A. I. El-Desoky, A. Y. Haikel and L. M. Labib, “A low-storage precise IP traceback technique based on packet marking and logging,” Oxford University Press, The Computer Journal, vol. 59, no. 11, pp. 1581–1592, 2016. [Google Scholar]
6. M. M. Fadel, M. Areed and A. I. El-Desoky, “A hybrid approach for detecting, preventing, and traceback DDoS attacks,” WSEAS Transactions on Computers, vol. 11, no. 7, pp. 191–196, 2014. [Google Scholar]
7. J. Singh and S. Behal, “Detection and mitigation of DDoS attacks in SDN: A comprehensive review, research challenges and future directions,” ElSevier Computer Science Review, vol. 37, no. 2, pp. 1–25, 2020. [Google Scholar]
8. S. Katoch, S. S. Chauhan and V. Kumar, “A review on genetic algorithm: Past, present, and future,” Multimedia Tools and Applications, vol. 80, no. 17, pp. 8091–8126, 2021. [Google Scholar]
9. W. A. Khan, N. N. Hamadneh, S. L. Tilahun and J. M. T. Ngnotchouye, “A review and comparative study of Firefly algorithm and its modified versions,” in Optimization Algorithms-Methods and Applications, First ed., vol. 1. London, United Kingdom: IntechOpen Press, pp. 281–313, 2016. [Google Scholar]
10. Z. Li, R. Tan and B. Ren, “Research on particle swarm optimization of variable parameter,” in Proc. Int, Conf. Advances on P2P, Parallel, Grid, Cloud and Internet Computing (3PGCIC 2016), Lecture Notes on Data Engineering and Communications Technologies, Springer, Cham, Germany, vol. 1, pp. 25–33, 2016. [Google Scholar]
11. S. Mirjalili and A. Lewis, “The whale optimization algorithm,” Advances in Engineering Software, vol. 95, no. 12, pp. 51–67, 2016. [Google Scholar]
12. P. Kaur, M. Kumar and A. Bhandari, “A review of detection approaches for distributed denial of service attacks,” Systems Science & Control Engineering, vol. 5, no. 1, pp. 301–320, 2017. [Google Scholar]
13. J. Xie, F. R. Yu, T. Huang, R. Xie, J. Liu et al., “A survey of machine learning techniques applied to software defined networking (SDNResearch issues and challenges,” IEEE Communications Surveys & Tutorials, vol. 21, no. 1, pp. 393–430, 2019. [Google Scholar]
14. W. Sun, G. Z. Dai, X. R. Zhang, X. Z. He and X. Chen, “TBE-Net: A three-branch embedding network with part-aware ability and feature complementary learning for vehicle re-identification,” IEEE Transactions on Intelligent Transportation Systems, vol. 99, pp. 1–13, 2021. [Google Scholar]
15. W. Sun, L. Dai, X. R. Zhang, P. S. Chang and X. Z. He, “RSOD: Real-time small object detection algorithm in UAV-based traffic monitoring,” Applied Intelligence, vol. 92, no. 6, pp. 1–16, 2021. [Google Scholar]
16. M. M. Fadel, “HDSL: A hybrid distributed single-packet low-storage IP traceback framework,” Mansoura Engineering Journal (MEJ), vol. 46, no. 4, pp. 75–89, 2021. [Google Scholar]
17. A. Khraisat, I. Gondal, P. Vamplew and J. Kamruzzaman, “Survey of intrusion detection systems: Techniques, datasets and challenges,” Cybersecurity, vol. 2, no. 20, pp. 1–22, 2019. [Google Scholar]
18. P. J. Criscuolo, “Distributed denial of service, tribe flood network 2000, and stacheldraht, CIAC-2319,” Department of Energy Computer Incident Advisory Capability (CIACUCRLID-136939, Rev. 1, vol. 1, pp. 1–18, 2000. [Google Scholar]
19. P. D. Bojovic, I. Basicevic, S. Ocovaj and M. Popovic, “A practical approach to detection of distributed denial-of-service attacks using a hybrid detection method,” Computers and Electrical Engineering, vol. 73, pp. 84–96, 2019. [Google Scholar]
20. K. Kalkan, L. Altay, G. Gur and F. Alagoz, “JESS: Joint entropy-based DDoS defense scheme in SDN,” IEEE Journal on Selected Areas in Communications, vol. 36, no. 10, pp. 2358–2372, 2018. [Google Scholar]
21. N. A. S. Lima and M. P. Fernandez, “Towards an efficient DDoS detection scheme for software-defined networks,” IEEE Latin America Transactions, vol. 16, no. 8, pp. 2296–2301, 2018. [Google Scholar]
22. R. Wang, Z. Jia and L. Ju, “An entropy-based distributed DDoS detection mechanism in software-defined networking,” in Proc. IEEE Int. Conf. on Trust, Security and Privacy in Computing and Communications (TrustCom), Helsinki, Finland, pp. 310–317, 2015. [Google Scholar]
23. M. E. Ahmed, S. Ullah and H. Kim, “Statistical application fingerprinting for DDoS attack mitigation,” IEEE Transactions on Information Forensics and Security, vol. 14, no. 6, pp. 1471–1484, 2019. [Google Scholar]
24. E. Min, J. Long, Q. Liu, J. Cui and W. Chen, “TR-IDS: Anomaly-based intrusion detection through text-convolutional neural network and random forest,” Security and Communication Networks, vol. 2018, no. 1, pp. 1–9, 2018. [Google Scholar]
25. A. L. Buczak and E. Guven, “A survey of data mining and machine learning methods for cyber security intrusion detection,” IEEE Communications Surveys & Tutorials, vol. 18, no. 2, pp. 1153–1176, 2016. [Google Scholar]
26. Z. He, T. Zhang and R. B. Lee, “Machine learning based DDoS attack detection from source side in csloud,” in Proc. IEEE 4th Int. Conf. on Cyber Security and Cloud Computing (CSCloud), New York, NY, USA, pp. 114–120, 2017. [Google Scholar]
27. K. S. Hoon, K. C. Yeo, S. Azam, B. Shunmugam and F. D. Boer, “Critical review of machine learning approaches to apply big data analytics in DDoS forensics,” in Proc. Int. Conf. on Computer Communication and Informatics (ICCCI), Coimbatore, India, pp. 1–5, 2018. [Google Scholar]
28. A. Koay, A. Chen, I. Welch and W. K. G. Seah, “A new multi classifier system using entropy-based features in DDoS attack detection,” in Proc. IEEE Int. Conf. on Information Networking (ICOIN), Chiang Mai, Thailand, pp. 162–167, 2018. [Google Scholar]
29. C. Yin, Y. Zhu, J. Fei and X. He, “A deep learning approach for intrusion detection using recurrent neural networks,” IEEE Access, vol. 5, pp. 21954–21961, 2017. [Google Scholar]
30. K. Wu, Z. Chen and W. Li, “A novel intrusion detection model for a massive network using convolutional neural networks,” IEEE Access, vol. 6, pp. 50850–50859, 2018. [Google Scholar]
31. D. Kwon, K. Natarajan, S. C. Suh, H. Kim and J. Kim, “An empirical study on network anomaly detection using convolutional neural networks,” in Proc. IEEE 38th Int. Conf. on Distributed Computing Systems (ICDCS), Vienna, Austria, pp. 1595–1598, 2018. [Google Scholar]
32. University of New Brunswick benchmark dataset, [Accessed: 28-Dec-2021]. Available: https://www.unb.ca/cic/datasets/nsl.html. [Google Scholar]
33. MAWILab dataset, [Accessed: 3-Jan-2022]. Available: http://www.fukuda-lab.org/mawilab/data.html. [Google Scholar]
34. X. Yuan, C. Li and X. Li, “Deep defense: Identifying DDoS attack via deep learning,” in Proc. IEEE Int. Conf. on Smart Computing (SMARTCOMP), Hong Kong, China, pp. 1–8, 2017. [Google Scholar]
35. Intrusion detection evaluation dataset (ISCXIDS2012[Accessed: 23-Dec.-2021]. Available: https://www.unb.ca/cic/datasets/ids.html. [Google Scholar]
36. S. Suresh and N. S. Ram, “A review on various DPM traceback schemes to detect DDoS attacks,” Indian Journal of Science and Technology, vol. 9, no. 47, pp. 1–8, 2016. [Google Scholar]
37. Y. Bhavani, V. Janaki and R. Sridevi, “Survey on packet marking algorithms for IP traceback,” Oriental Journal of Computer Science & Technology, vol. 10, no. 2, pp. 507–512, 2017. [Google Scholar]
38. S. Wang, L. L. Minku and X. Yao, “A systematic study of online class imbalance learning with concept drift,” IEEE Transactions on Neural Networks and Learning Systems, vol. 29, no. 10, pp. 4802–4821, 2018. [Google Scholar]
39. Mininet emulator software, [Accessed: 11-Jan.-2022]. Available: https://mininet.org. [Google Scholar]
40. M. M. Ahsan, M. A. P. Mahmud, P. K. Saha, K. D. Gupta and Z. Siddique, “Effect of data scaling methods on machine learning algorithms and model performance,” Technologies, vol. 9, no. 52, pp. 1–17, 2021. [Google Scholar]
41. D. Zhao, X. Wang, Y. Mu and L. Wang, “Experimental study and comparison of imbalance ensemble classifiers with dynamic selection strategy,” Entropy, vol. 23, no. 7, pp. 1–22, 2021. [Google Scholar]
42. L. Liu, P. Wang, J. Lin and L. Liu, “Intrusion detection of imbalanced network traffic based on machine learning and deep learning,” IEEE Access, vol. 9, pp. 7550–7563, 2021. [Google Scholar]
43. N. Ahuja, G. Singal, D. Mukhopadhyay and N. Kumar, “Automated DDOS attack detection in software defined networking,” Journal of Network and Computer Applications, vol. 187, no. 6, pp. 1–42, 2021. [Google Scholar]
 | This work is licensed under a Creative Commons Attribution 4.0 International License, which permits unrestricted use, distribution, and reproduction in any medium, provided the original work is properly cited. |