DOI:10.32604/cmc.2022.028088

| Computers, Materials & Continua DOI:10.32604/cmc.2022.028088 |  |
| Article |
Statistical Analysis with Dingo Optimizer Enabled Routing for Wireless Sensor Networks
1Department of Mathematics, College of Science & Arts, King Abdulaziz University, Rabigh, 21911, Saudi Arabia
2Department Statistics, College of Science, University of Tabuk, Tabuk, Saudi Arabia
3Department of Computer Science, College of Computer, Qassim University, Buraydah, 51452, Saudi Arabia
4Department of Mathematics and Statistics, College of Science, Taif University, Taif, 21944, Saudi Arabia
5Mathematics Department, Faculty of Science, Sohag University, Sohag, 82524, Egypt
*Corresponding Author: Abdulaziz S. Alghamdi. Email: ashalghamedu@kau.edu.sa
Received: 02 February 2022; Accepted: 17 March 2022
Abstract: Security is a vital parameter to conserve energy in wireless sensor networks (WSN). Trust management in the WSN is a crucial process as trust is utilized when collaboration is important for accomplishing trustworthy data transmission. But the available routing techniques do not involve security in the design of routing techniques. This study develops a novel statistical analysis with dingo optimizer enabled reliable routing scheme (SADO-RRS) for WSN. The proposed SADO-RRS technique aims to detect the existence of attacks and optimal routes in WSN. In addition, the presented SADO-RRS technique derives a new statistics based linear discriminant analysis (LDA) for attack detection, Moreover, a trust based dingo optimizer (TBDO) algorithm is applied for optimal route selection in the WSN and accomplishes secure data transmission in WSN. Besides, the TBDO algorithm involves the derivation of the fitness function involving different input variables of WSN. For demonstrating the enhanced outcomes of the SADO-RRS technique, a wide range of simulations was carried out and the outcomes demonstrated the enhanced outcomes of the SADO-RRS technique.
Keywords: Statistical analysis; reliability; routing; wireless sensor networks; linear discriminant analysis; dingo optimizer; security
In recent times, WSN has extended the application range from early deployment for battlefield intelligence surveillance to fields like meteorological weather forecasting, emergency response support, factory automation security application, and so on. WSN consists of inexpensive and small sensors without a current architecture [1]. They are frequently utilized for sensing, processing, transmitting, and receiving data from the region they are positioned beforehand it is transported to a base station. A conventional WSN contains several sensors that are classified based on the environment and the structure (topology) where they are deployed. Basically, WSN is classified based on the deployment of the sensors in the environment [2]. This node is of equivalent capacity, while others have different capacities, based on the infrastructure. The three major kinds type WSN architecture are hierarchical, flat-based (tree), and cluster-based. Moreover, the environment where the sensors are positioned in a WSN is classified into five groups, such as mobile WSN, underground WSN, terrestrial WSN, underwater WSN, and multimedia WSN system [3]. The sensors in a WSN are frequently deployed in inaccessible, remote, and harsh regions and are frequently represented by resource constraints including limited storage, limited power, short communication range, and limited bandwidth [4]. They are integrated with the susceptibility of the wireless medium (that is open and shared) have generated sensors vulnerable to distinct security attacks namely the denial of service (DoS) [5]. Fig. 1 illustrates the WSN structure.
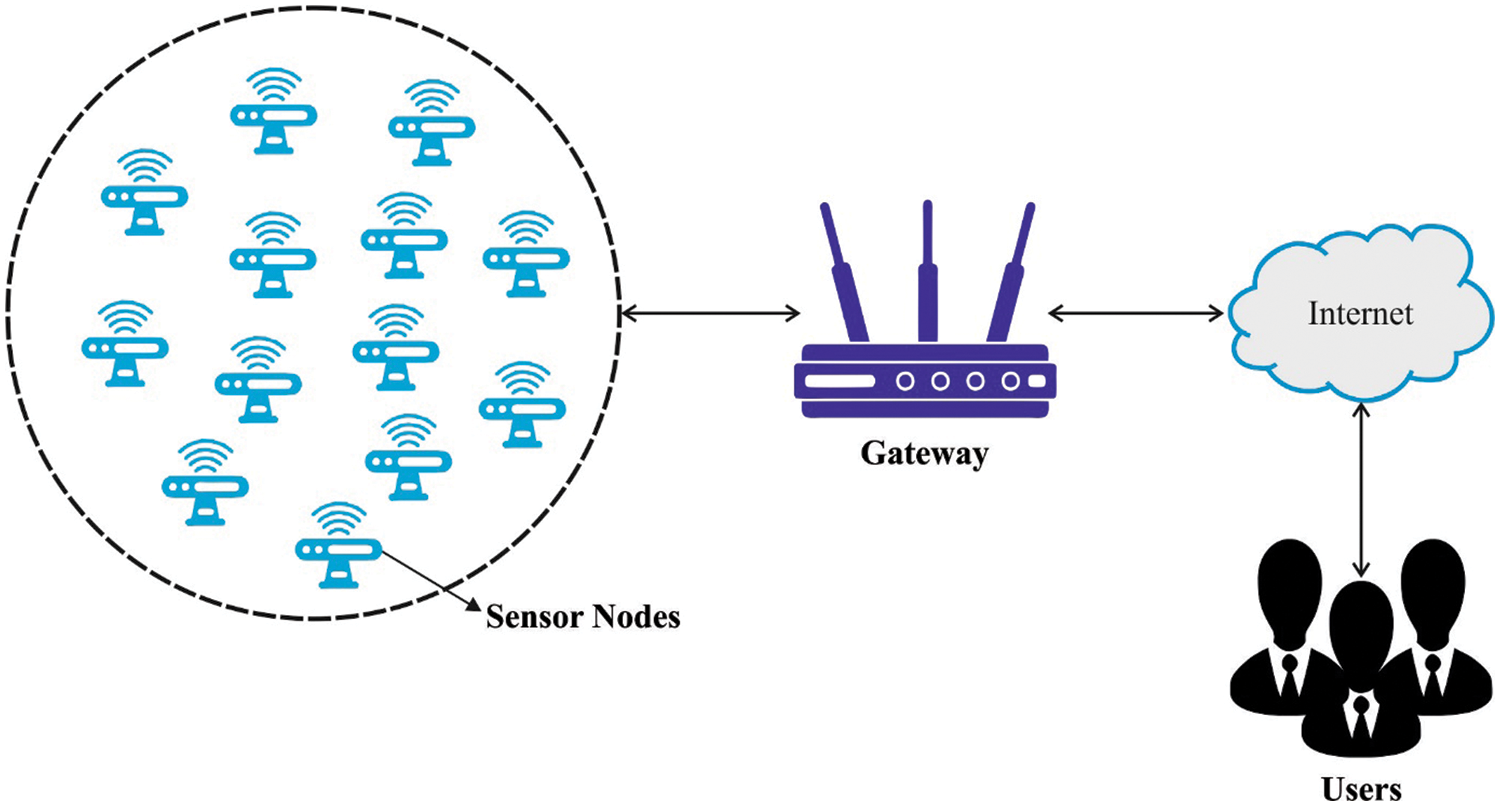
Figure 1: WSN structure
Even though conventional security approaches like authentication and cryptography could offer security at certain level, they alone could not handle compromised node attacks [6]. When the nodes are compromised, it launches attacks based on commands from the outside that could control or cripple the entire WSN system. For instance, malicious node could attract the information from another node via distinct method, and when it begins to receive the information, it could randomly receive or drop all information that considerably reduces the routing system efficiency [7]. To handle this type of node is to detect and monitor them. While there are no centralized authorities in WSN, nodes must detect and monitor malicious nodes in a distributed way. Several solutions are presented for securing WSN [8], together with routing. Since routing executes data distribution to BS, it is major protocol for WSN. Therefore, secured routing is strong against packet drop and disruption, and alteration act on routing process is vital [9,10]. To protect routing, particularly against compromised nodes, several solutions have been introduced. One of these solutions is trust establishment, utilized in several study areas. Trust establishment identifies untrustworthy and trustworthy nodes by estimating them according to past performance or behavior. It prevents untrustworthy nodes and only chooses trustworthy in routing process [11]. As trust method is efficient and simple in compromised node detection, a considerable study is performed for enhancing cooperation and improving security in the networks.
Rathee et al. [12], proposed an ACO based QoS aware energy balancing secured routing (QEBSR) approach for WSN. Improved heuristics to calculate the end-to-end delay of communication and the trust factor of the node on the routing path are presented. The presented method has been related to 2 current approaches: energy efficient routing with node compromised resistance and distributed energy balanced routing. Haseeb et al. [13] developed an energy-effective and secured routing method (ESR) for avoiding intrusion from IoT based WSN to improve the data trustworthiness and network period. First, the presented method makes distinct energy-effective clusters based on the intrinsic qualify of nodes. Next, according to the (k,n) threshold-based Shamir secret sharing system, the security and reliability of the sensory data amongst the BS and CH are accomplished.
Haseeb et al. [14] presented an intrusion prevention architecture for mobile IoT devices using the incorporation of WSN for providing data security with enhanced network delivery ratio. The presented method is comprised of two sub-elements. First, autonomously organized and non-overlapping clusters are created and sustained the clusters stability according to the uncertainty principle. Next, end-to-end secured and multihop routing path is designed according to the blockchain architecture. In Selvi et al. [15], a secured routing method named energy aware trust based secured routing approach is presented whereby the trust score assessment is utilized for identifying the malevolent user efficiently in WSN and spatio-temporal constraint is utilized with DT approach to choosing optimal path.
This study develops a novel statistical analysis with dingo optimizer enabled reliable routing scheme (SADO-RRS) for WSN. The proposed SADO-RRS technique aims to detect the existence of attacks and optimal routes in WSN. In addition, the presented SADO-RRS technique derives a new statistics based linear discriminant analysis (LDA) for attack detection, Moreover, a trust based dingo optimizer (TBDO) algorithm is applied for optimal route selection in the WSN and accomplishes secure data transmission in WSN. Besides, the TBDO algorithm involves the derivation of the fitness function involving different input variables of WSN. In order to demonstrate the enhanced outcomes of the SADO-RRS technique, a wide range of simulations was carried out.
In this study, a novel SADO-RRS technique has been developed for reliable routing in WSN. The proposed SADO-RRS technique determines the presence of attacks and optimal routes in WSN. In addition, the presented SADO-RRS technique derives a new statistics based LDA for attack detection. Furthermore, a TBDO algorithm is applied for optimal route selection in the WSN and accomplishes secure data transmission in WSN.
2.1 LDA Based Attack Detection
Primarily, the LDA model is applied for the detection of intrusions in the network. The discriminant analysis concentrates on the connection amongst several independent variables and definite dependence variables by creating multiple independent variables. This kind of multivariate investigation defines the extents of the sum of composite variables discriminate amongst more than two existing sets of subjects and also could develop the classifier model to predict the group membership of novel observation. During this case, a linear discriminant function (LDF) which passed with the means of 2 groups (centroids) are utilized for discriminating subjects amongst 2 centroids. If there are further centroids, the amount of centroid minus one purpose has been required for classifying an observation amongst them. In order to all centroids, LDA considers as the explanatory variable that is usually distributed with equivalent covariance matrices. To all cases, the evaluated co-efficient to independent variables are multiplied by case’s score on that variables.
The LDF has been demonstrated as:
where
The rule by that the discriminant co-efficient (or weights) were chosen is that maximizing the distance amongst 2 centroid means (centroids)
2.2 TBDO Based Routing Technique
The dingoes are sufficient able for finding the place of prey. Afterward trace the place, the pack after that alpha surrounds the prey. For modeling dingo’s social hierarchy, it can be considered that the present optimum agent’s method is an objective or purpose prey that is same as the optimum as the quest region is not recognized a priori [17]. Meanwhile, another quest agency is until seek for refreshing its approaches on the following feasible method. This performance of dingoes is demonstrated as the subsequent mathematical Eqs. (3)–(7). Besides, a brief explanation of nomenclatures is utilized from the formula.
The place of neighborhood dingoes is signified utilizing a 2D place vector. Based on the place of prey
Conversely, during the searching space based on the model, agent does not usually have computation of place of the prey (optimally). Scheming the dingoes hunting plan mathematical, it is considered that each pack member containing alpha, beta, and others are optimum skill on the potential place of prey. The alpha dingo continuously commands the hunting. But, at times beta and other dingo’s can also be participating from hunting. Therefore, it is assumed the 1st two optimum values attained so far. According to place of optimum searching agents, other dingoes are also required for updating their place. Due to the discussion, Eqs. (8)–(16) are demonstrated this issue. In addition, a brief explanation of the nomenclatures utilized in the formula.
For calculating the intensity of all the dingoes, subsequent formulas are being utilized:
The place upgrade from the
When there is no place upgrade, it refers the dingo done the hunting by attacking the prey. In order to mathematical formulate the approach, the value of
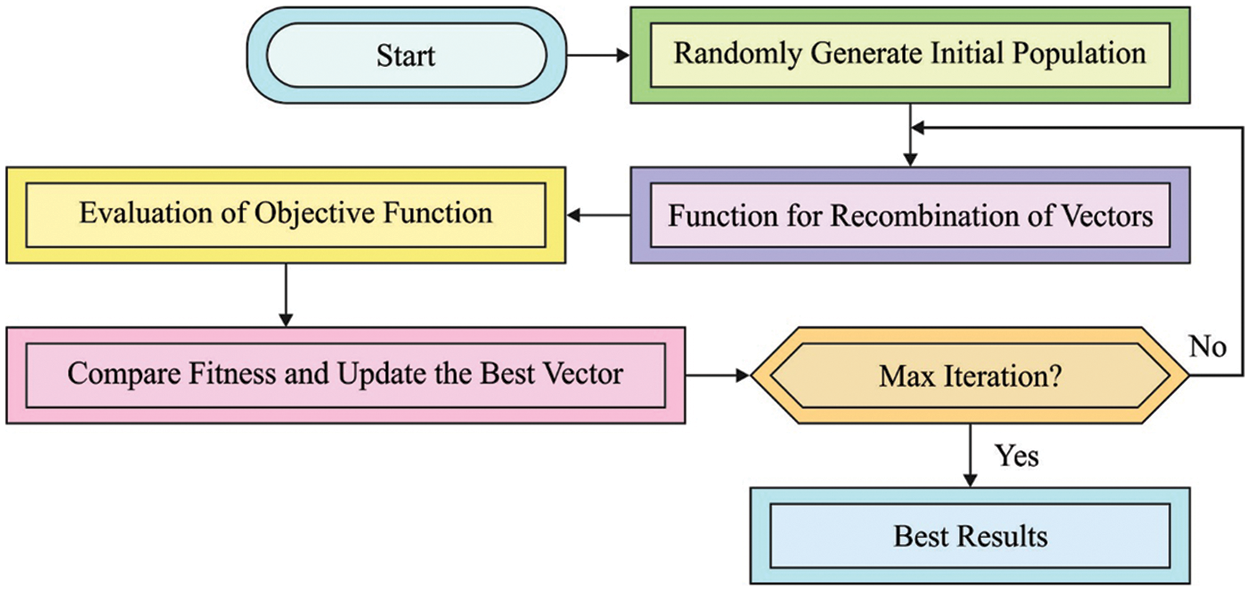
Figure 2: Flowchart of DO technique
The presented surrounding technique does certainly reveal exploration to any extent; but, for accentuating exploration, DOX needs further operation. The DOX supports their quest agent from changing its place dependent upon the locating of,
The dingoes hunt the prey frequently based on the pack’s place. It is continuously travel forwarded to hunt and strike predators. So,
It is optimum to search and avoidance of neighboring optimal. According to a dingo’s place, it can be arbitrarily agreed on prey value and create it essential for meeting dingo rigidly/beyond. Purposely, it is utilized
The presented approach develops a FF utilizing 3 input parameters such as trust level, distance to neighbors, and energy to optimum route selective.
Distance to neighbors: It is suitable to select route with lesser distance amongst neighbouring nodes. In the intra-cluster communication procedure, sensor node utilization power to data broadcast. When the neighbour node distance has been moderated, then the power of intra-cluster broadcast is also minimized.
Objective 1: Minimizing
Trust factor (TF): Initially, every node is declared that TF is one. The value of TF has been reduced by anomalous prediction method if the node processes the abnormal task and nodes are named as malicious nodes.
Objective 2: Maximizing
Energy: When the node intake minimal power utilized as sensing, process, and transmission process also with maximal RE has gathered of minimal energy ratio. So, the low as energy ratio, the CH selective develop more possible.
Objective 3: Minimizing
In the proposed technique, it could be vital to decrease the linear group of main functions. So, the potential energy function of presented approach was implemented as:
where
This section inspects the performance validation of the SADO-RRS technique with existing techniques. The results are inspected interms of distinct aspects.
Tab. 1 provides detailed intrusion detection results of the SADO-RRS technique with recent methods. Fig. 3 inspects the
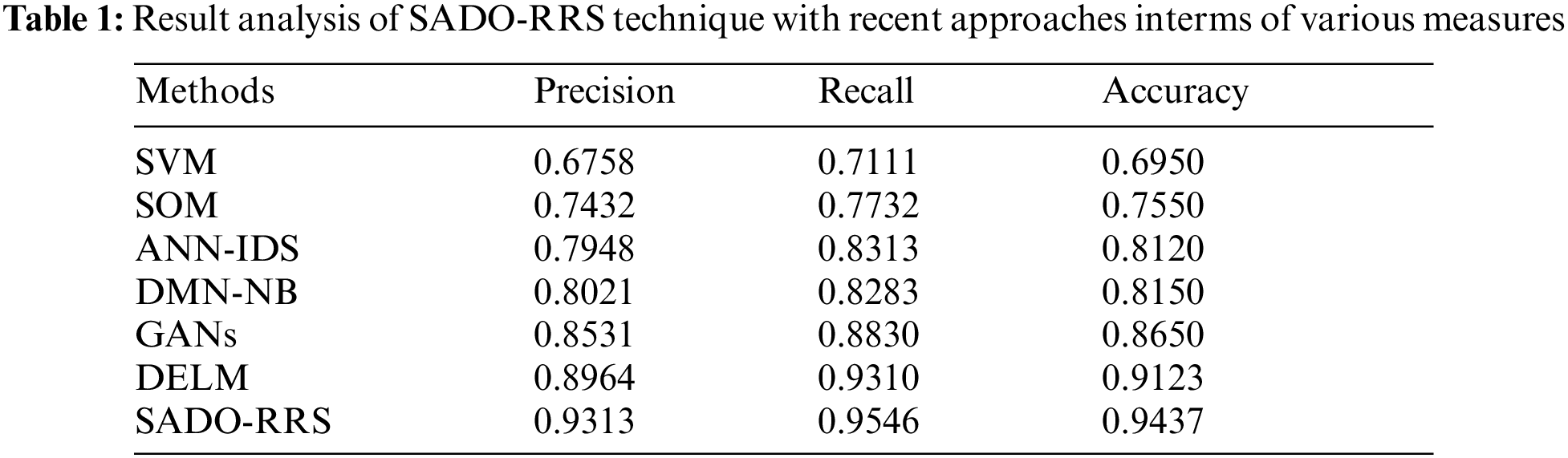
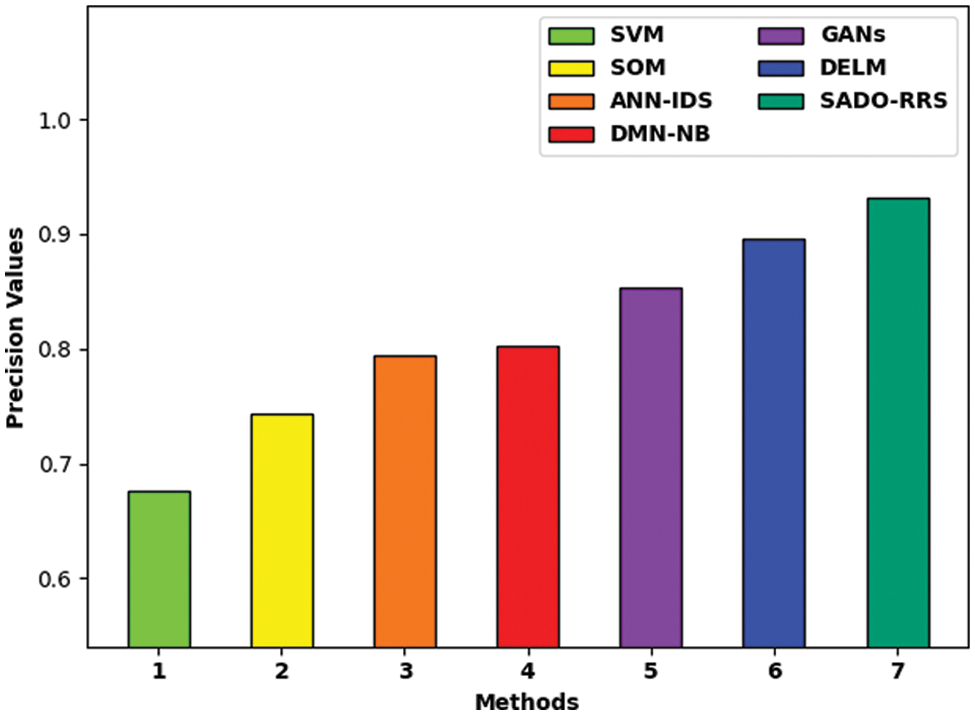
Figure 3:
Fig. 4 examines the
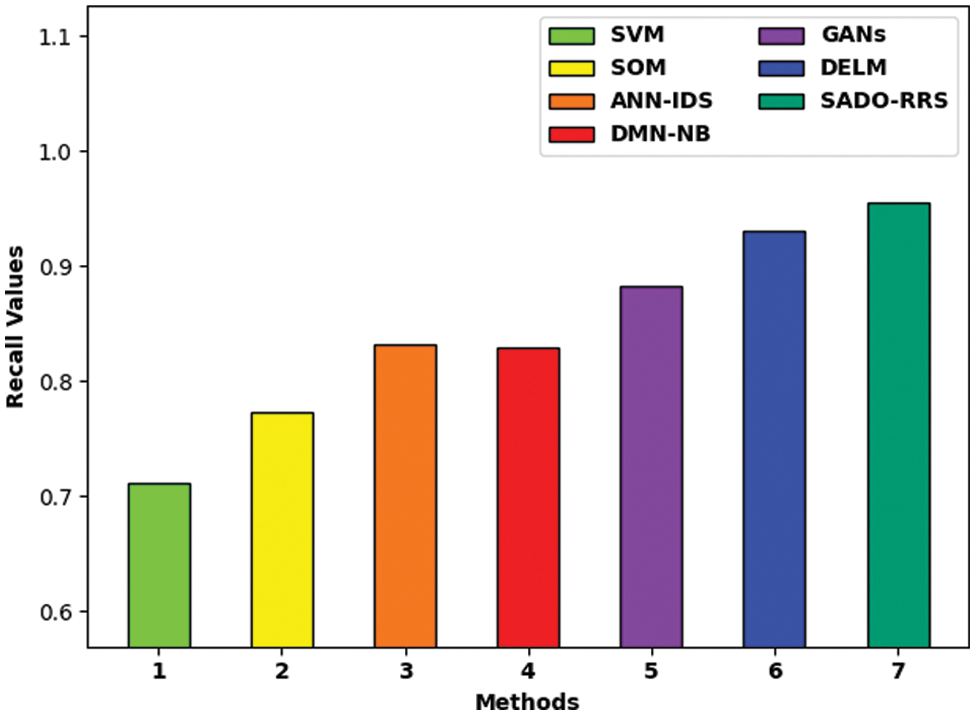
Figure 4:
Fig. 5 demonstrates the
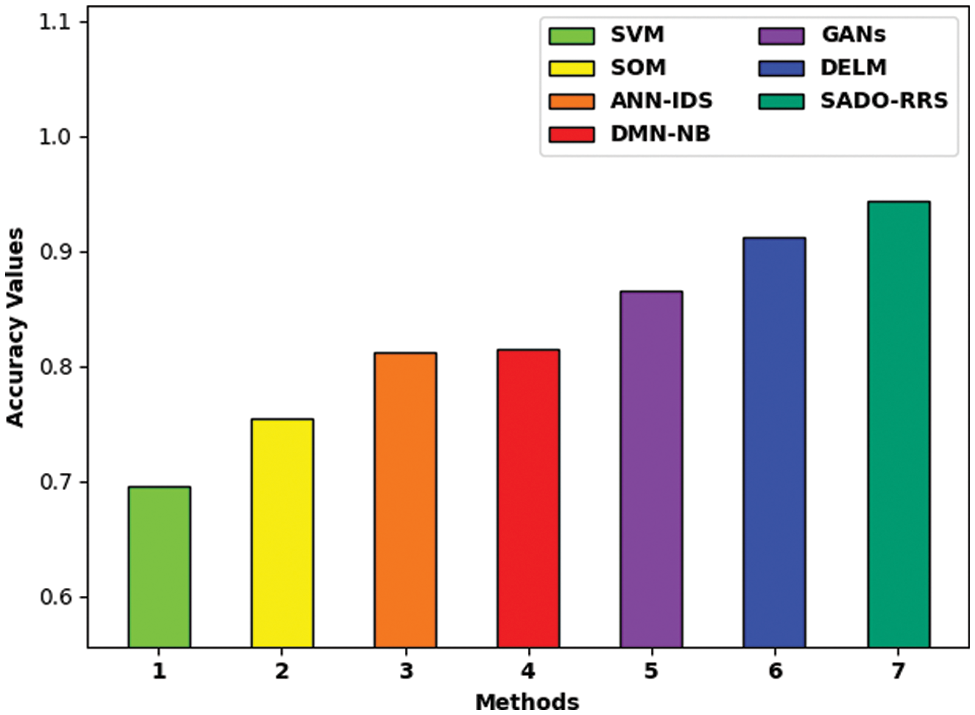
Figure 5:
Tab. 2 and Fig. 6 illustrate the network lifetime (NLFT) examination of the SADO-RRS technique with existing ones under distinct number of compromised nodes. The results indicated that the SADO-RRS technique has resulted in increased NLFT over the other methods under all compromised nodes. For instance, with 5% of compromised nodes, the SADO-RRS technique has offered higher NLFT of 961 rounds whereas the DEBR, EENC, and QEBSR techniques have attained lower 793, 878, and 927 rounds respectively. Similarly, with 30% of compromised nodes, the SADO-RRS approach has obtainable maximal NLFT of 919 rounds whereas the DEBR, EENC, and QEBSR methodologies have attained lower 615, 766, and 868 rounds correspondingly.
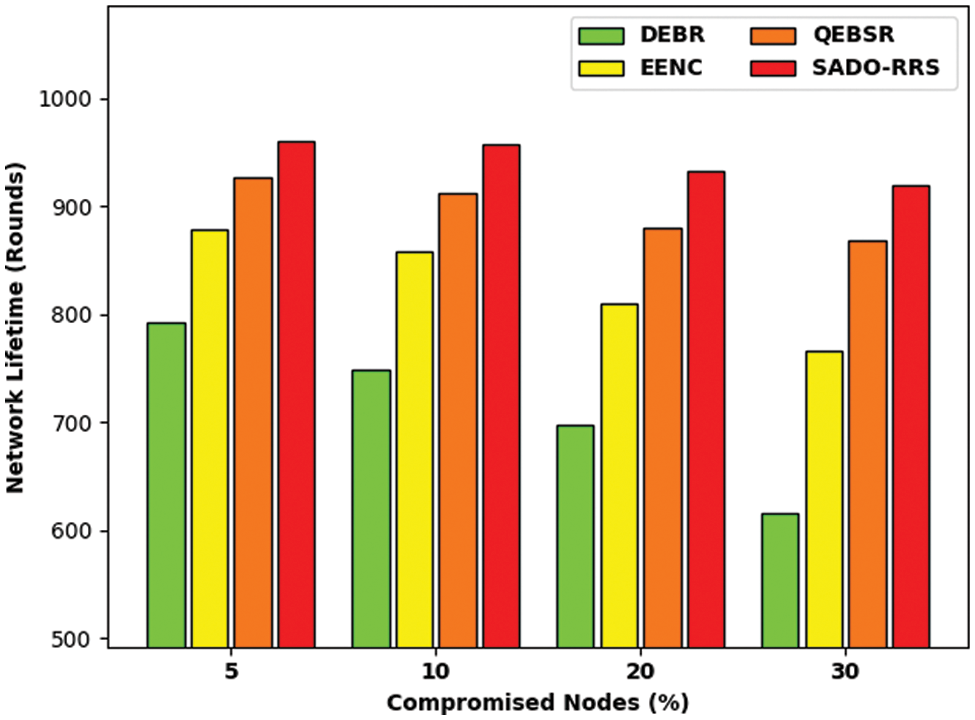
Figure 6: NLFT analysis of SADO-RRS technique under distinct compromised nodes
Tab. 3 and Fig. 7 depict the NLFT examination of the SADO-RRS approach with existing ones under distinct number of nodes. The outcomes referred that the SADO-RRS methodology has resulted in increased NLFT over the other methods under all nodes. For instance, with 100 nodes, the SADO-RRS approach has accessible maximal NLFT of 1040 rounds whereas the DEBR, EENC, and QEBSR systems have obtained minimal 693, 827, and 888 rounds correspondingly. At the same time, with 400 nodes, the SADO-RRS approach has obtainable superior NLFT of 2439 rounds whereas the DEBR, EENC, and QEBSR methodologies have reached minimal 1976, 2098, and 2360 rounds correspondingly.
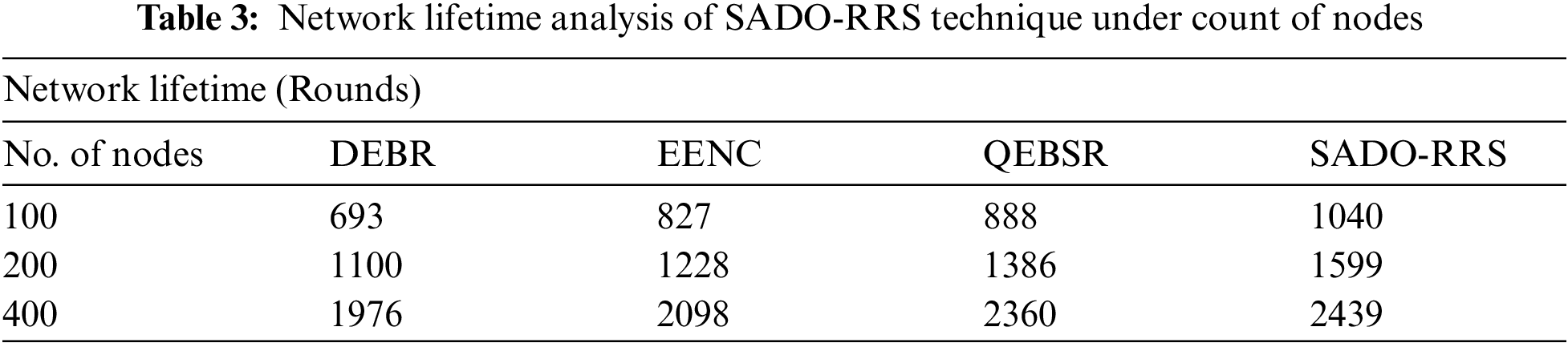
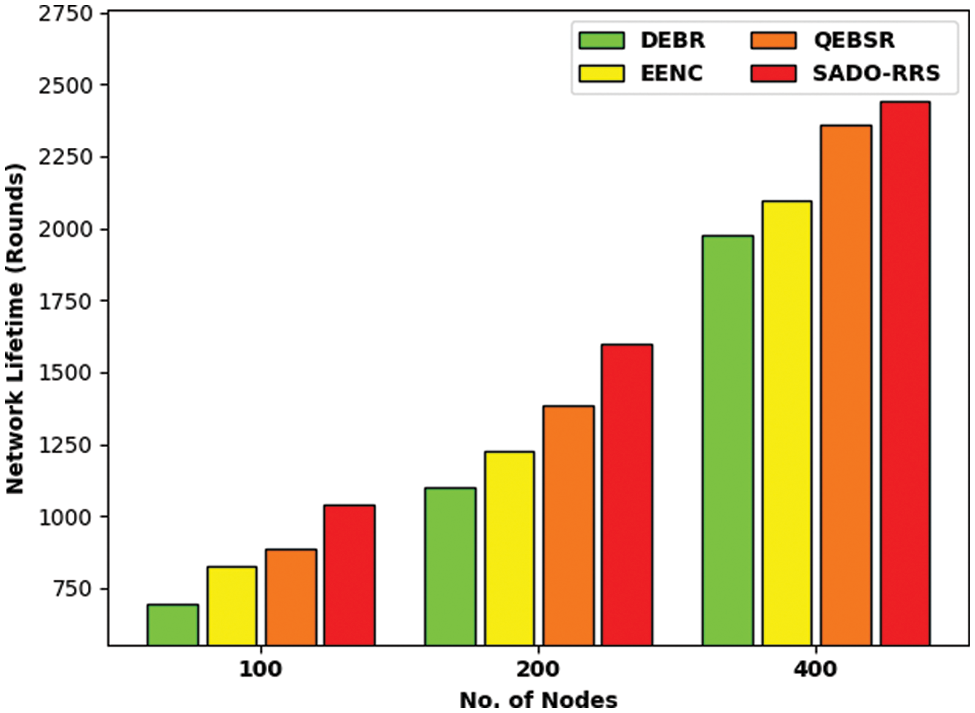
Figure 7: NLFT analysis of SADO-RRS technique under count of nodes
Tab. 4 and Fig. 8 depict the PDR examination of the SADO-RRS technique with existing ones under distinct count of compromised nodes. The results referred that the SADO-RRS technique has resulted in maximum PDR over the other methods under all compromised nodes. For instance, with 5% of compromised nodes, the SADO-RRS system has offered increased PDR of 0.9670 rounds whereas the DEBR, EENC, and QEBSR systems have reached lesser of 0.9363, 0.9617, and 0.9649 rounds correspondingly. Also, with 30% of compromised nodes, the SADO-RRS approach has obtainable increased PDR of 0.9572 rounds whereas the DEBR, EENC, and QEBSR approaches have achieved reduced 0.9369, 0.9418, and 0.9480 rounds correspondingly.
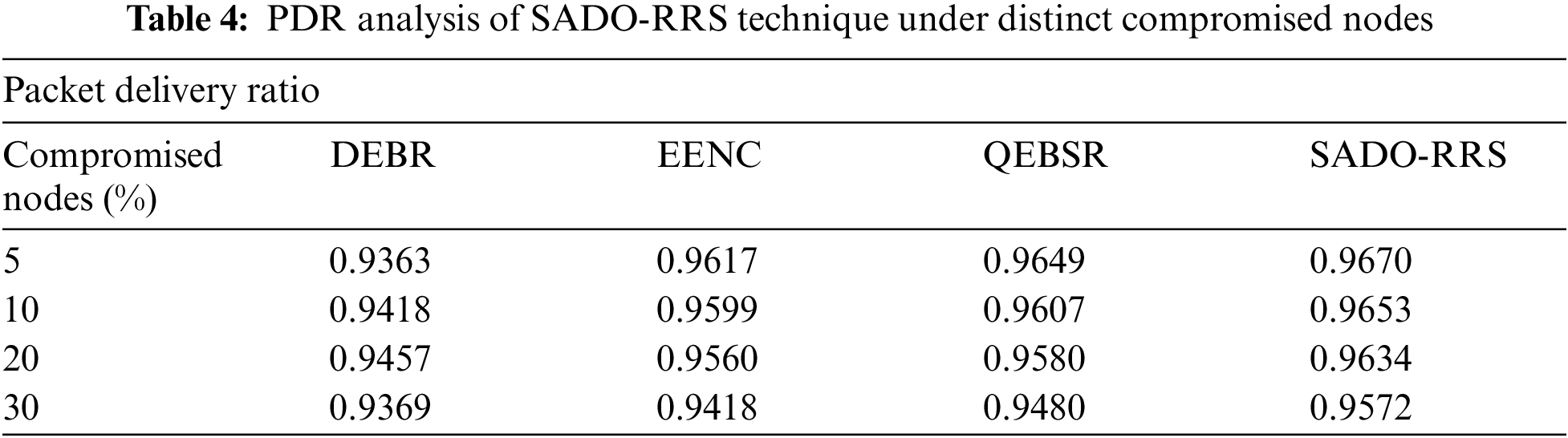
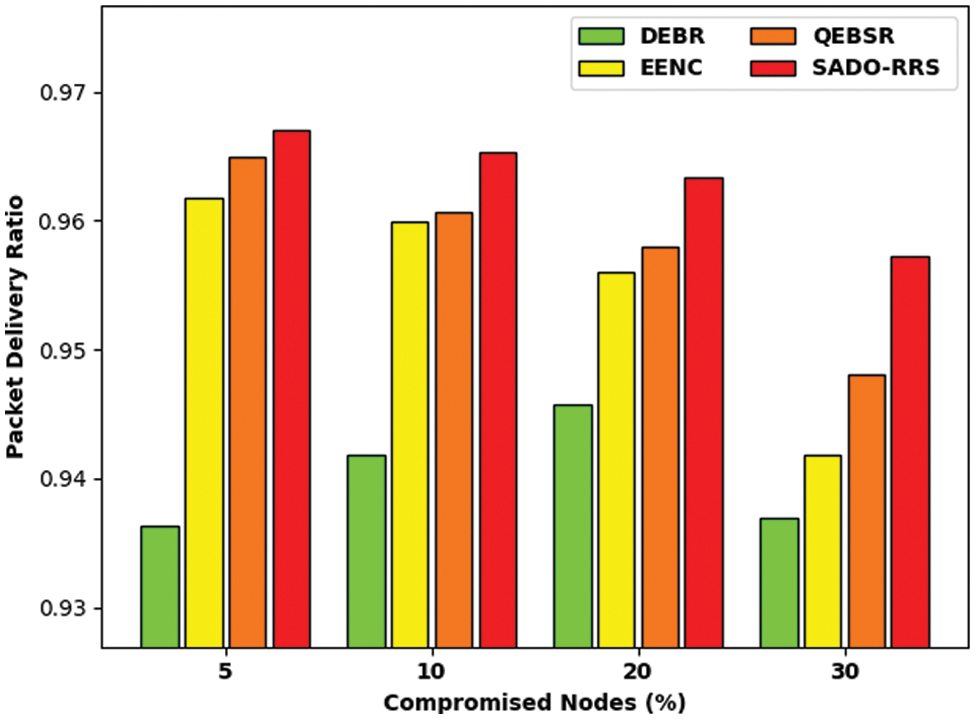
Figure 8: PDR analysis of SADO-RRS technique under distinct compromised nodes
A detailed PLR examination of the SADO-RRS technique with recent models in Tab. 5 and Fig. 9. The outcomes indicated the betterment of the SADO-RRS technique over the other methods under distinct number of compromised nodes. For instance, with 5% of compromised nodes, the SADO-RRS technique has attained reduced PLR of 0.0330 whereas the DEBR, EENC, and QEBSR techniques have obtained least PLR of 0.0637, 0.0383, and 0.0351 respectively. Also, with 30% of compromised nodes, the SADO-RRS approach has reached lower PLR of 0.0428 whereas the DEBR, EENC, and QEBSR approaches have attained minimal PLR of 0.0631, 0.0582, and 0.0520 correspondingly.
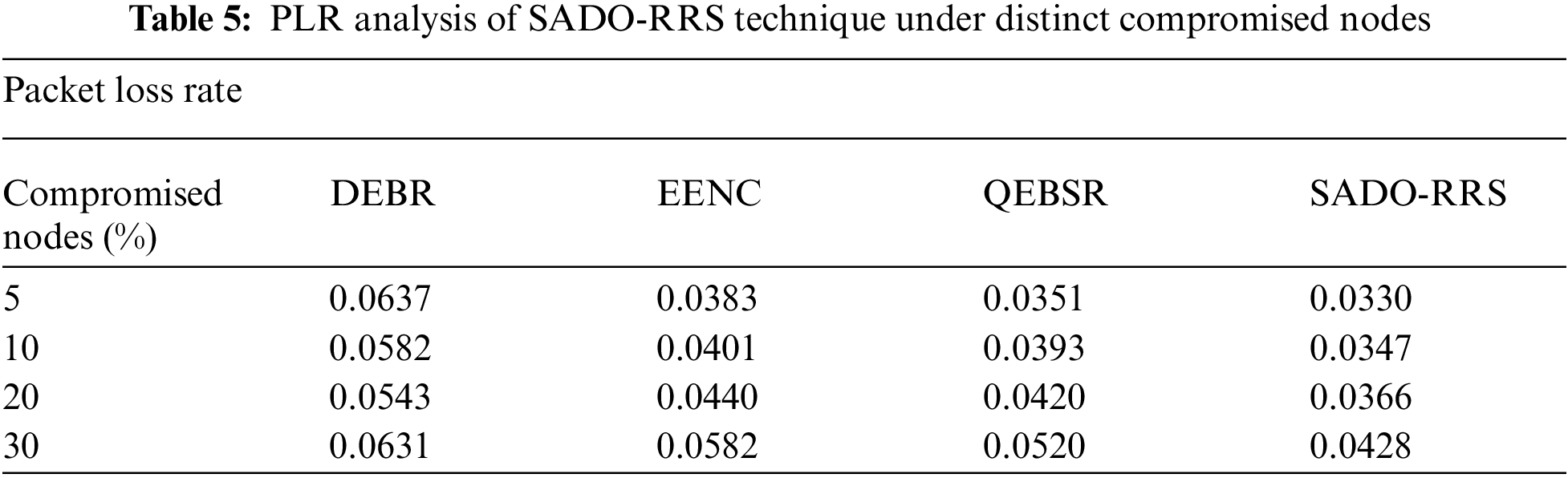
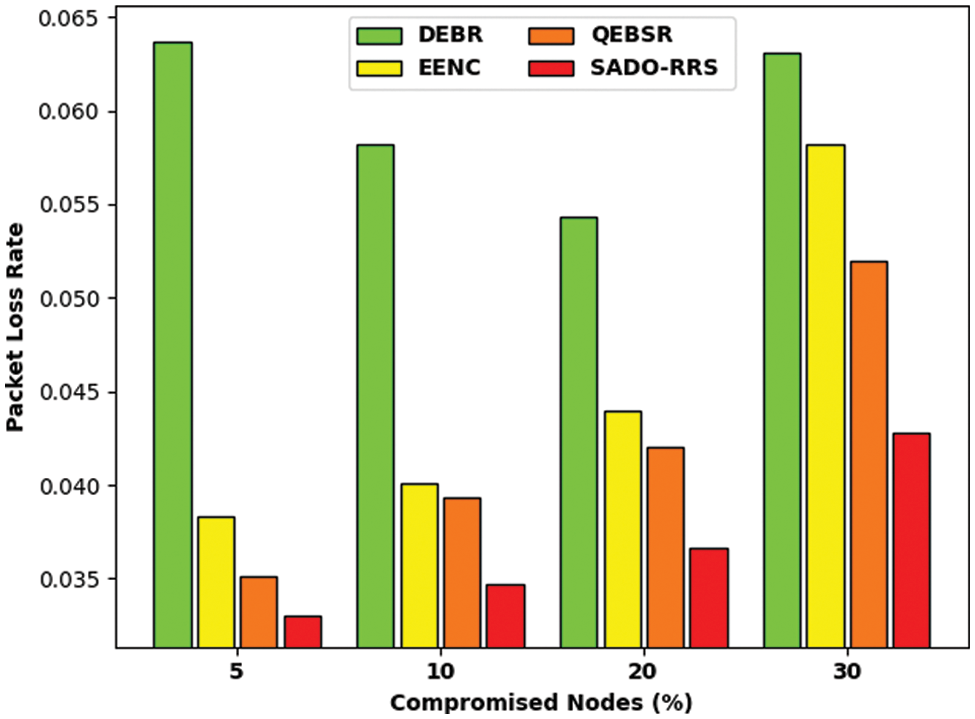
Figure 9: PLR analysis of SADO-RRS technique under distinct compromised nodes
In this study, a novel SADO-RRS technique has been developed for reliable routing in WSN. The proposed SADO-RRS technique determines the presence of attacks and optimal routes in WSN. In addition, the presented SADO-RRS technique derives a new statistics based LDA for attack detection. The presented approach develops a FF utilizing 3 input parameters such as trust level, distance to neighbors, and energy to optimum route selective. In the proposed technique, it could be vital to decrease the linear group of main functions. The experimental result analysis of the SADO-RRS technique highlighted the enhanced outcomes. In future, data aggregation approaches can be integrated into the SADO-RRS technique for enhanced performance in WSN.
Funding Statement: This project was funded by the Deanship of Scientific Research (DSR), King Abdulaziz University, Jeddah, Saudi Arabia under Grant No. (KEP-81–130-42). The authors, therefore acknowledge with thanks DSR technical and financial support.
Conflicts of Interest: The authors declare that they have no conflicts of interest to report regarding the present study.
1. H. Alwan and A. Agarwal, “Multi-objective Reliable multipath routing for wireless sensor networks,” in 2010 IEEE Globecom Workshops, Miami, FL, USA, pp. 1227–1231, 2010. [Google Scholar]
2. M. Tariq, Y. P. Kim, J. H. Kim, Y. J. Park and E. H. Jung, “Energy efficient and reliable routing scheme for wireless sensor networks,” in 2009 Int. Conf. on Communication Software and Networks, Chengdu, China, pp. 181–185, 2009. [Google Scholar]
3. X. R. Zhang, W. F. Zhang, W. Sun, X. M. Sun and S. K. Jha, “A robust 3-D medical watermarking based on wavelet transform for data protection,” Computer Systems Science & Engineering, vol. 41, no. 3, pp. 1043–1056, 2022. [Google Scholar]
4. X. R. Zhang, X. Sun, X. M. Sun, W. Sun and S. K. Jha, “Robust reversible audio watermarking scheme for telemedicine and privacy protection,” Computers Materials & Continua, vol. 71, no. 2, pp. 3035–3050, 2022. [Google Scholar]
5. C. H. Liu and Y. F. Chung, “Secure user authentication scheme for wireless healthcare sensor networks,” Computers & Electrical Engineering, vol. 59, no. 2, pp. 250–261, 2017. [Google Scholar]
6. S. Okdem and D. Karaboga, “Routing in wireless sensor networks using ant colony optimization,” in First NASA/ESA Conf. on Adaptive Hardware and Systems (AHS'06), Istanbul, Turkey, pp. 401–404, 2006. [Google Scholar]
7. K. Daabaj, M. Dixon, T. Koziniec and P. Cole, “Reliable routing scheme for indoor sensor networks,” in 21st Annual IEEE Int. Symp. on Personal, Indoor and Mobile Radio Communications, Istanbul, Turkey, pp. 1614–1619, 2010. [Google Scholar]
8. R. Srinivasan and E. Kannan, “Energy harvesting based efficient routing scheme for wireless sensor network,” Wireless Personal Communications, vol. 101, no. 3, pp. 1457–1468, 2018. [Google Scholar]
9. F. Zabin, S. Misra, I. Woungang, H. F. Rashvand, N.-W. Ma et al., “REEP: Data-centric, energy-efficient and reliable routing protocol for wireless sensor networks,” IET Communications, vol. 2, no. 8, pp. 995, 2008. [Google Scholar]
10. X. Li, W. Liu, M. Xie, A. Liu, M. Zhao et al., “Differentiated data aggregation routing scheme for energy conserving and delay sensitive wireless sensor networks,” Sensors, vol. 18, no. 7, pp. 2349, 2018. [Google Scholar]
11. I. Banerjee, P. Chanak, H. Rahaman and T. Samanta, “Effective fault detection and routing scheme for wireless sensor networks,” Computers & Electrical Engineering, vol. 40, no. 2, pp. 291–306, 2014. [Google Scholar]
12. M. Rathee, S. Kumar, A. H. Gandomi, K. Dilip, B. Balusamy et al., “Ant colony optimization based quality of service aware energy balancing secure routing algorithm for wireless sensor networks,” IEEE Transactions on Engineering Management, vol. 68, no. 1, pp. 170–182, 2021. [Google Scholar]
13. K. Haseeb, A. Almogren, N. Islam, I. U. Din and Z. Jan, “An energy-efficient and secure routing protocol for intrusion avoidance in iot-based WSN,” Energies, vol. 12, no. 21, pp. 4174, 2019. [Google Scholar]
14. K. Haseeb, N. Islam, A. Almogren and I. Ud Din, “Intrusion prevention framework for secure routing in wsn-based mobile internet of things,” IEEE Access, vol. 7, pp. 185496–185505, 2019. [Google Scholar]
15. M. Selvi, K. Thangaramya, S. Ganapathy, K. Kulothungan, H. K. Nehemiah et al., “An energy aware trust based secure routing algorithm for effective communication in wireless sensor networks,” Wireless Personal Communications, vol. 105, no. 4, pp. 1475–1490, 2019. [Google Scholar]
16. G. Antonogeorgos, D. Panagiotakos, K. Priftis and A. Tzonou, “Logistic regression and linear discriminant analyses in evaluating factors associated with asthma prevalence among 10- to 12-years-old children: Divergence and similarity of the two statistical methods,” International Journal of Pediatrics, vol. 2009, no. 1, pp. 1–6, 2009. [Google Scholar]
17. A. K. Bairwa, S. Joshi and D. Singh, “Dingo optimizer: A nature-inspired metaheuristic approach for engineering problems,” Mathematical Problems in Engineering, vol. 2021, no. 1, pp. 1–12, 2021. [Google Scholar]
18. J. H. A. Covarrubias, H. P. Vázquez, A. F. P. Delgado and P. M. G. Vite, “An improved dingo optimization algorithm applied to SHE-PWM modulation strategy,” Applied Sciences, vol. 12, no. 3, pp. 992, 2022. [Google Scholar]
 | This work is licensed under a Creative Commons Attribution 4.0 International License, which permits unrestricted use, distribution, and reproduction in any medium, provided the original work is properly cited. |