DOI:10.32604/cmc.2022.027858

| Computers, Materials & Continua DOI:10.32604/cmc.2022.027858 |  |
| Article |
An Effective Signcryption with Optimization Algorithm for IoT-enabled Secure Data Transmission
Department of Computing Technologies, School of Computing, SRM Institute of Science and Technology, Kattankulathur, 603203, Tamilnadu, India
*Corresponding Author: A. Chinnappa. Email: ca5461@srmist.edu.in
Received: 27 January 2022; Accepted: 01 April 2022
Abstract: Internet of Things (IoT) allows several low resources and controlled devices to interconnect, calculate processes and make decisions in the communication network. In the heterogeneous environment for IoT devices, several challenging issues such as energy, storage, efficiency, and security. The design of encryption techniques enables the transmission of the data in the IoT environment in a secured way. The proper selection of optimal keys helps to boost the encryption performance. With this motivation, the study presents a signcryption with quantum chaotic krill herd algorithm for secured data transmission (SCQCKH-SDT) in IoT environment. The proposed SCQCKH-SDT technique aims to effectively encrypts the data by the use of optimal keys generated by the CQKH algorithm. The proposed SCQCKH-SDT technique initially employs the signcryption technique for the encryption of data. In order to optimize the secrecy, the optimal key generation process is carried out using Chaotic Krill Herd (CQKH) algorithm. The CQKH algorithm incorporates the concept of quantum computing and chaotic theory into the traditional KH algorithm. The performance validation of the SCQCKH-SDT technique is performed using benchmark dataset. An extensive comparative analysis reported the superior performance of the SCQCKH-SDT technique over the recent approaches.
Keywords: Security; Internet of Things; encryption; optimal key generation; metaheuristics
Recently, with the expansion of new network advancements and a constant updating of terminal devices [1], Internet of Things (IoT) has become widespread. It is estimated that IoT would attain fifty billion devices by 2020. IoT is the effect of tremendous growth, beginning with computerization of some processes, utilizing electronic gadgets, and the procedure is updated with transmission capacity [2]. Owing to the development in remote transmission, embedded framework, and sensor IoT system is widely utilized in some spaces. While the high accessibility of IoT systems is proportionate to increasing security and privacy risks [3]. Although efficiency of IoT systems must improve the lives of many people, customary digital attack on IoT framework is feasible [4]. The use of system privacy and security highlight to increase in worth issues, on the ground that IoT method has different elements: User Interface (UI) component, implanted gadget, device control, cloud computing for data processing, etc. [5]. Privacy-preserving is a security problem confronted by end-client when managing IoT-enabled applications. Cloud computing (CC) provides the basis and storing IoT data processing. Cryptographic-based methodology was presented as a standout amongst other methods to guarantee the privacy of IoT information. Cryptosystem supplies components to ensure data integrity and classification. When the information is continuously encrypted in the cloud, then the suspicions are evacuated, and control isn’t lost [6]. The security necessity for data and algorithms has become extremely challenging in the past few years. The different types of attacks in IoT environment is shown in Fig. 1.
Figure 1: Types of attacks in IoT security
In such scenarios, it is crucial to frame a powerful method for guarantying the trustworthiness and safety of the patient symptomatic information that is received and transmitted from IoT [7]. ‘Encryption cryptography’ is the method where the message is encrypted so that the programmer could not read it, yet that is permitted by the presented faculty. Rivest–Shamir–Adleman (RSA) and Advanced Encryption Standard (AES) approaches are employed for data encryption. Consequently, the IoT offer ascent to different restorative application includes remote healthcare monitoring [8]. For example, in light of the patient healthcare information, a social insurance specialist cooperative could enhance by examining the person's condition and could recommend the earlier intercession and optimal treatment. Traditional security systems won’t be capable of obliging IoT devices completely because a major part of this device has battery-restricted assets and limitations; in other cases, this component requires further resources [9]. Long key makes the figure hard to break, and also, it approves a systematic ‘scramble and decodes’ procedure. In general, RSA is an open key calculation that is widely used as a part of individual communication and business areas [10]. Jang et al. [11] presented an approach to partially encrypt secured data in images with FF1 and FF3-1. The presented approach encodes secured data without raising the data size, resolving the issue of unused memory space. Further, certain section of encrypted image is recognized and decrypted beforehand decryption of whole data, which address the problem of attacking image encryption and privacy masking approaches. Medileh et al. [12] introduced a scalable encryption method named Flexible encryption method (FlexenTech), to secure IoT data. The presented method is appropriate for resource-limited networks and devices. It provides a lower encryption time, protects against popular attacks namely replay attacks and determines configurable modes, whereas another amount of key sizes of rounds might be utilized. Jeong et al. [13] verified optimum lightweight cryptography for privacy improvement in an IoT based Environment Monitoring Scheme which controls and monitors the nearby humidity and temperature. Then, compared processing time and CPU usage while different lightweight cryptography has been employed. This assisted us to accomplish that the optimum lightweight cryptography for IoT based method is Lightweight Encryption Algorithm (LEA) that is block cipher. Chowdhury et al. [14] proposed Modified AES (MAES), a lightweight version of AES that meets the requirement. A One Dimensional (1D) Substitution Box is presented by creating a square matrix in affine transformation stage of MAES. The authors in [15] presented a hybridization of data encrypting method for sheltering the data diagnoses in healthcare images. The presented method is proposed by integrating 2-Dimensional (2D)-Discrete Wavelet Transform (DWT)-2 L or 2D-DWT-1 L steganography. The hybrid encryption is constructed by strategically using AES and RSA approaches to secure diagnoses data to be embedded with Red Green Blue (RGB) channel. The main novelty is the usage of Adoptive Genetic Algorithm with Optimum Pixel Adjustment Process (AGA-OPAP) improves data hiding capacity and imperceptibility feature.
This paper presents a signcryption with quantum chaotic krill herd algorithm for secured data transmission (SCQCKH-SDT) in IoT environment. The proposed SCQCKH-SDT technique initially employs the signcryption technique for the encryption of data and optimal key generation process using the CQKH algorithm. The CQKH algorithm incorporates the concept of quantum computing and chaotic theory into the traditional KH algorithm. The performance validation of the SCQCKH-SDT technique is performed using benchmark dataset and the results are examined under various aspects.
This paper has developed a novel SCQCKH-SDT to effectively encrypt the data by the use of optimal keys generated by the CQKH algorithm in the IoT environment. The workflow of proposed model is given in Fig. 2. The proposed SCQCKH-SDT technique follows a 2-stage process namely signcryption based encryption and CQKH based optimal key generation process. The CQKH algorithm incorporates the concept of quantum computing and chaotic theory into the traditional Kill Herd (KH) algorithm.
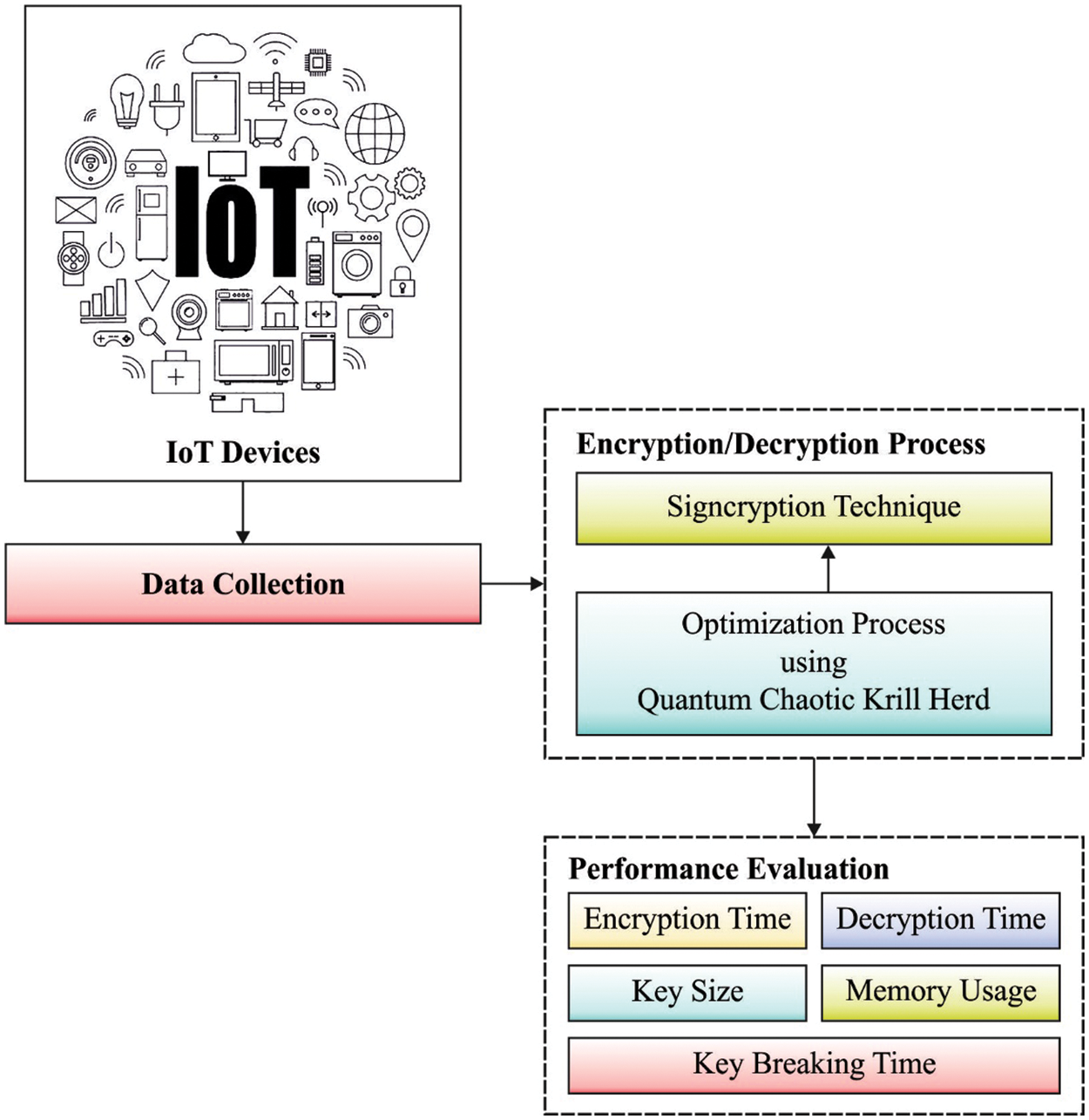
Figure 2: Workflow of SCQCKH-SDT technique
2.1 Stage 1: Encryption Process
At the initial stage, the signcryption technique can be employed to encrypt the data before transmission process. It is a public key cryptographic technique that concurrently fulfills the digital signature and opens key encryption with minimal complexity. It involves several subprocesses as defined in the following section [16]:
The key generating method: The probabilistic approach takes 2 prime numbers
Key generating method
Data encrypting method (DEM): The probabilistic approach takes the symmetric key
Key generating method
Key derivative key: The probabilistic approach take input as length of integer
Key derivative
Encryption: The probabilistic approach takes input as receivers public key
Key derivative function: The probabilistic approach (hash function – Message Digest(MD5)) takes length of key encryption key
Key derivative function
Wrapped function: The probabilistic approach (Wrapping) takes input as key encrypting key
Wrapped function
Concatenation: The probabilistic approach takes input ciphertext
Signcryption: The probabilistic approach takes senders private key
Signcryption
Unsigncryption procedure
Signature authentication: The probabilistic approach takes input senders public key
Detach: The probabilistic approach takes input
Decryption: The probabilistic approach takes input ciphertext
Key derivative function: The probabilistic approach (hash function (MD5)) take input random integer
Unwrapped function: The probabilistic approach (Wrapping) takes input as key encrypting key
Wrapped function
Data encrypting method (DEM): The probabilistic approach (AES) takes ciphertext
Key generating method
2.2 Stage 2: Optimal Key Generation Process
During the encryption process, the choice of keys plays a vital role and can be optimally generated by the use of CQKH algorithm. Krill herd (KH) is a metaheuristic optimization approach to resolve optimization issues that is depending on the stimulation of the KH swarm regarding environmental and biological methods [17]. The time- based location of an individual krill in two-dimensional surface is given below:
• Motion influenced by krill individual;
• Foraging movement
• Random or Physical diffusion
The Lagrangian method is generalized to
In which
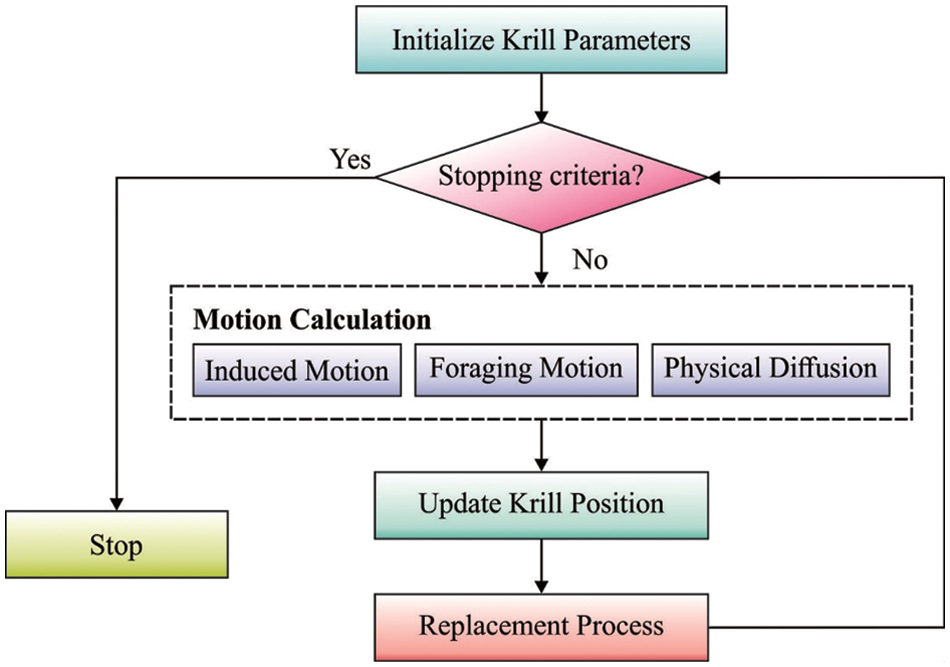
Figure 3: Flowchart of KH algorithm
Let
whereas
whereas
where
In which
The QCKH algorithm is derived by the use of QC, which is a current domain in computer science that is concerned in quantum computer with the phenomena of quantum mechanism namely entanglement, quantum gate, and state superposition [20]. The basic data unit in quantum computation is
whereas
The amplitude
The state of
This section inspects the security analysis of the SCQCKH-SDT technique under various dimensions [21–24]. The results are investigated under distinct file sizes [25–27]. Tab. 1 offers the overall encryption result analysis of the SCQCKH-SDT technique under distinct file sizes. The results denoted that the SCQCKH-SDT technique has accomplished effective security in the IoT environment. Fig. 4 demonstrates the encryption time (ET) and decryption time (DT) analysis [28] of the SCQCKH-SDT technique under various file sizes. The figure reported that the SCQCKH-SDT technique has resulted to effectual outcome with least ET and DT. For instance, with 10kb file size, the SCQCKH-SDT technique has attained ET and DT of 550.943 and 86.548 s respectively. Simultaneously, with 30 kb file size, the SCQCKH-SDT technique has obtained ET and DT of 581.053 and 88.371 s respectively. Concurrently, with 50 kb file size, the SCQCKH-SDT technique has achieved ET and DT of 597.168 and 101.130 s respectively.
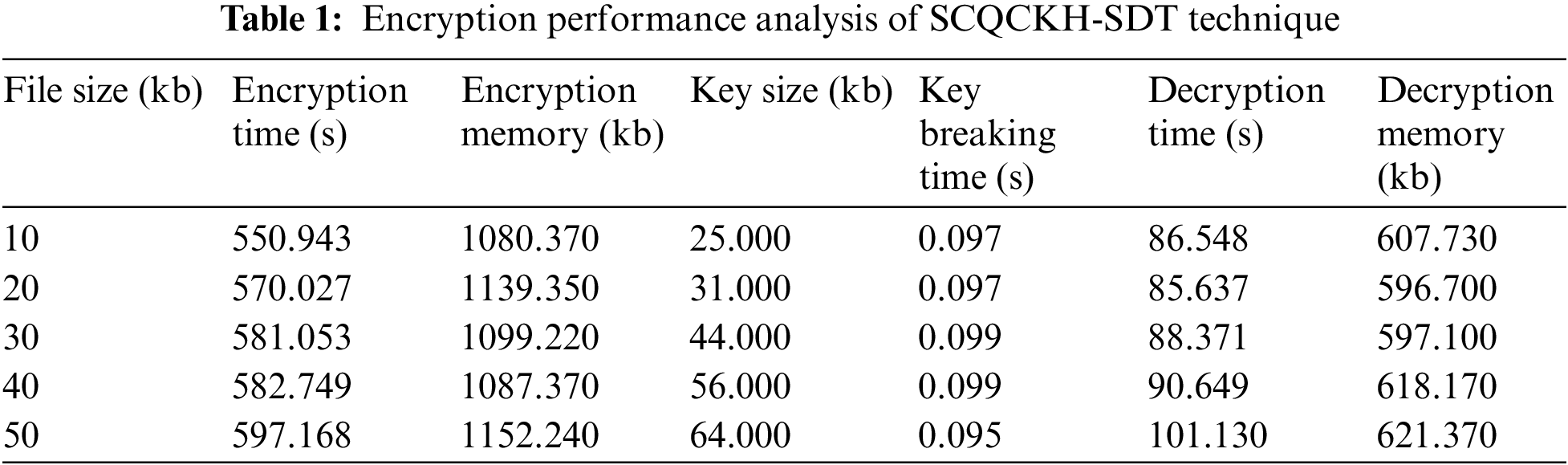
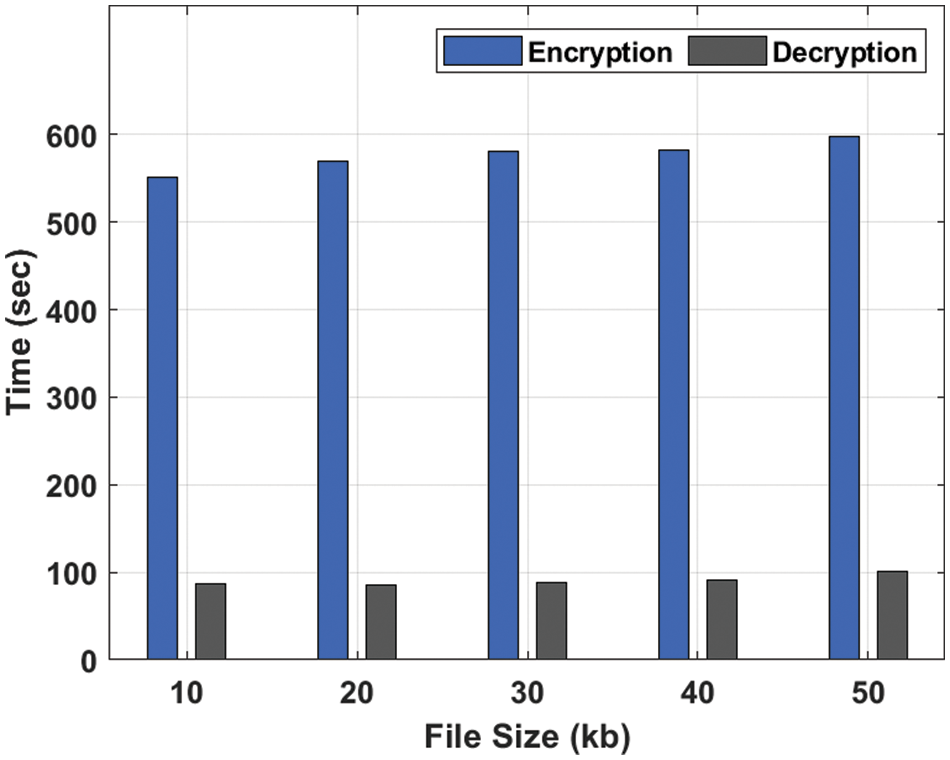
Figure 4: ET and DT analysis of SCQCKH-SDT technique
A brief encryption memory (EM) and decryption memory (DM) analysis [29] of the SCQCKH-SDT technique takes place under varying file sizes in Fig. 5. The results indicated that the SCQCKH-SDT technique has required minimal EM and DM under all files. For instance, with 10kb file size, the SCQCKH-SDT technique has needed EM and DM of 1080.370 and 607.730 kB respectively. Along with that, with 30 kb file size, the SCQCKH-SDT technique has offered EM and DM of 1099.220 and 597.100 kB respectively. In line with, with 50 kb file size, the SCQCKH-SDT technique has resulted to ET and DT of 1152.240 and 621.370 kb respectively.
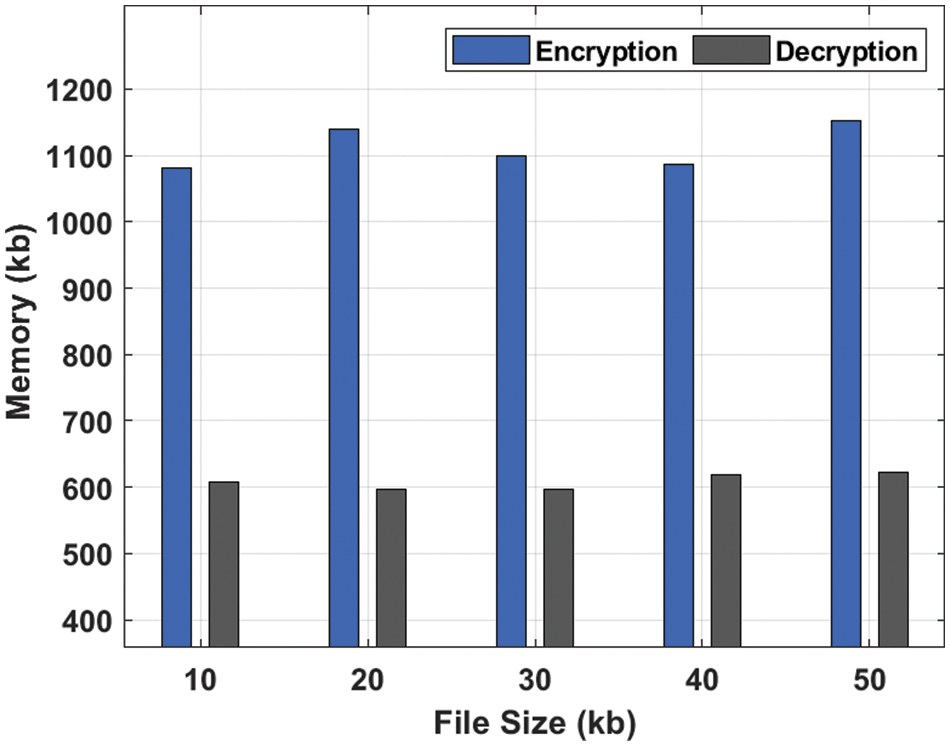
Figure 5: EM and DM analysis of SCQCKH-SDT technique
An extensive comparative result analysis of the SCQCKH-SDT technique with other techniques take place in Tab. 2 and Fig. 6. The table values implied that the SCQCKH-SDT technique has reached lower ET over the other methods under all file sizes. For instance, with 10 kb file size, the SCQCKH-SDT technique has provided least ET of 550.943 s whereas the ECC, HE, and OHE techniques have offered increased ET of 589.958, 574.692 and 561.121 s respectively. Moreover, with 30kb file size, the SCQCKH-SDT technique has gained reduced ET of 581.053 s whereas the ECC, HE, and OHE techniques have obtained increased ET of 626.005, 606.073 and 598.864 s respectively. Furthermore, with 50 kb file size, the SCQCKH-SDT technique has resulted to lower ET of 597.168 s whereas the ECC, HE, and OHE techniques have reached higher ET of 648.481, 636.183 and 611.586 s respectively.
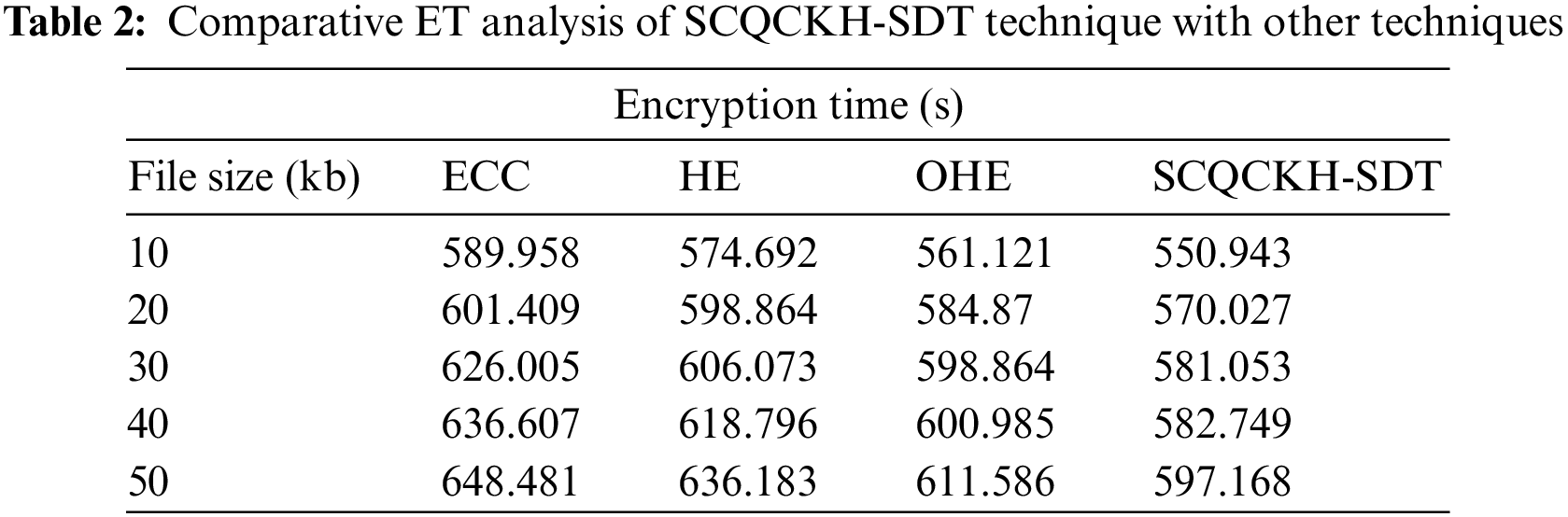
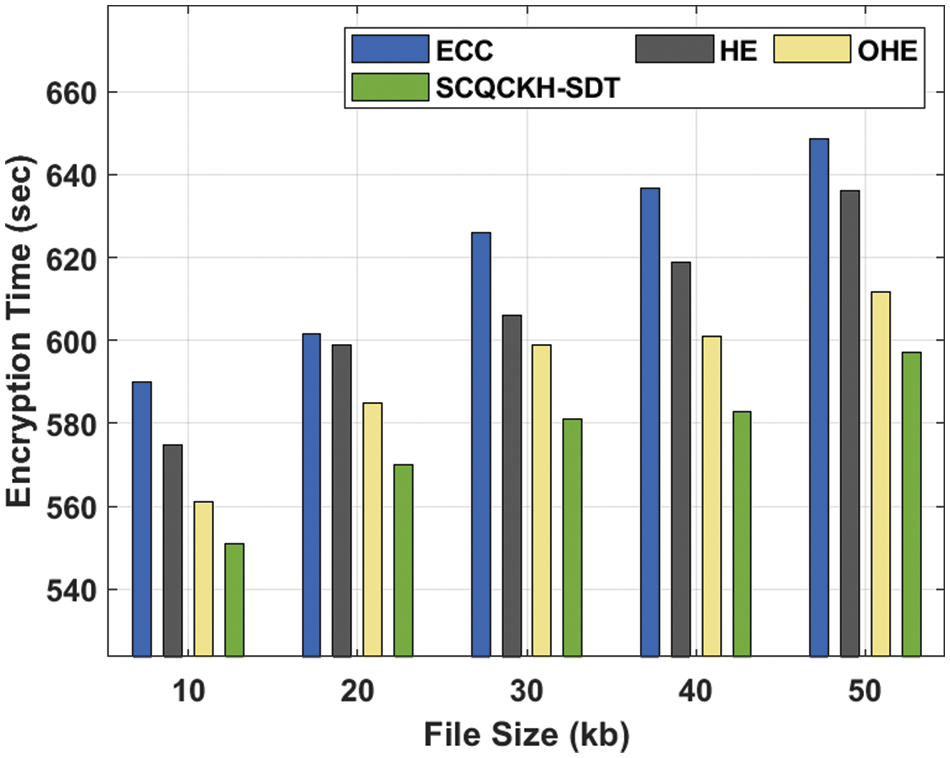
Figure 6: ET Analysis of SCQCKH-SDT technique under distinct file sizes
A comparison study of the SCQCKH-SDT technique in terms of DT is offered in Tab. 3 and Fig. 7. The experimental results reported that the SCQCKH-SDT technique has accomplished minimal DT over the other methods under all file sizes.
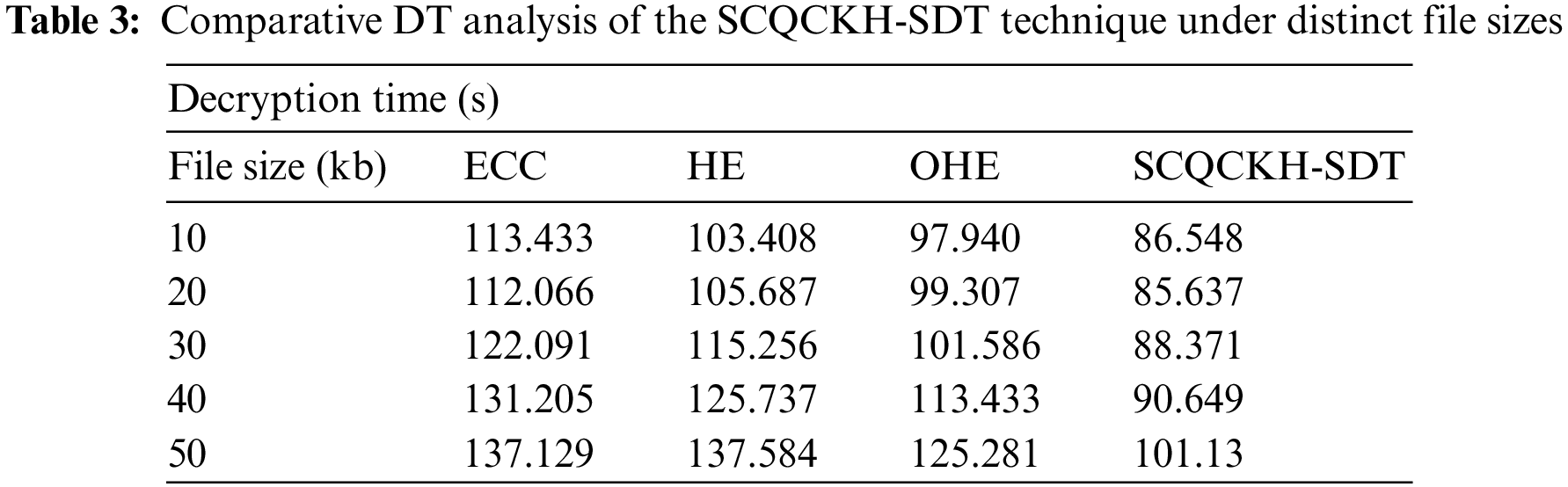
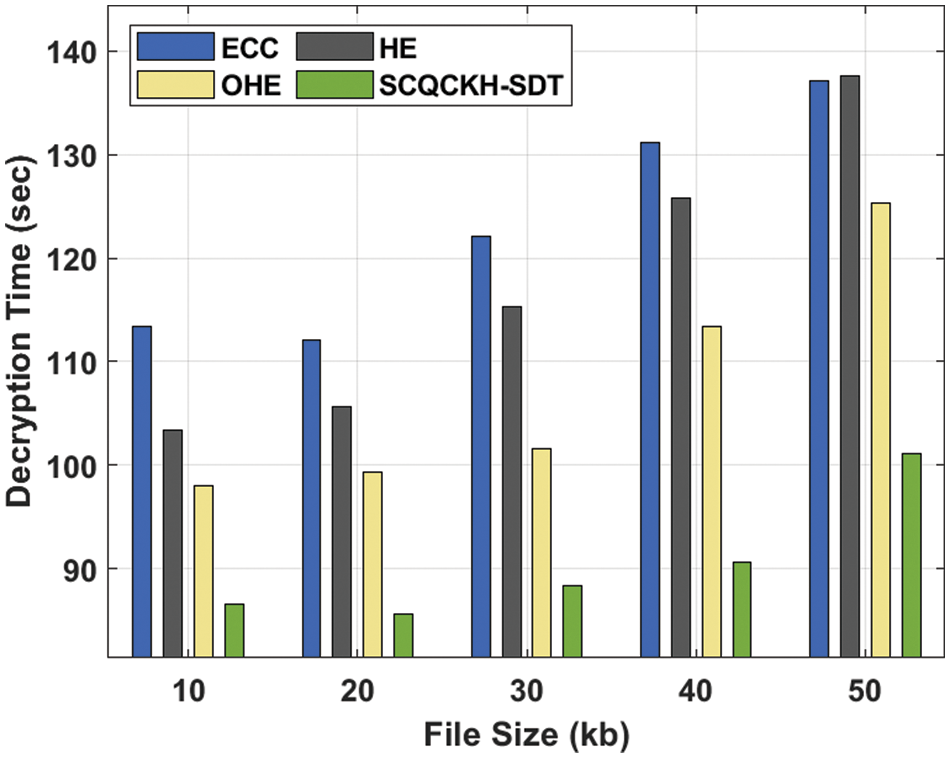
Figure 7: DT analysis of the SCQCKH-SDT with existing techniques
For instance, with 10 kb file size, the SCQCKH-SDT technique has accomplished lower DT of 86.548 s whereas the ECC, HE, and OHE techniques have attained higher DT of 113.433, 103.408 and 97.940 s respectively. Concurrently, with 30 kb file size, the SCQCKH-SDT technique has depicted minimum DT of 88.371 s whereas the ECC, HE, and OHE techniques have exhibited maximum DT of 122.091, 115.256 and 101.586 s respectively. Eventually, with 50 kb file size, the SCQCKH-SDT technique has resulted to lower DT of 101.13 s whereas the ECC, HE, and OHE techniques have demonstrated higher DT of 137.129, 137.584 and 125.281 s respectively.
Tab. 4 and Fig. 8 inspects the key breaking time (KBT) analysis [30] of the SCQCKH-SDT technique with the recent methods. The results demonstrated that the SCQCKH-SDT technique has demonstrated better KBT under all files. For instance, with 10 s file size, the SCQCKH-SDT technique has offered raised KBT of 0.097 s whereas the ECC, HE, and OHE techniques have obtained reduced KBTs of 0.090, 0.094 and 0.096 s respectively. Similarly, with 30 s file size, the SCQCKH-SDT technique has resulted to better KBT of 0.099 s whereas the ECC, HE, and OHE techniques have accomplished decreased KBTs of 0.090, 0.094 and 0.097 s respectively. Likewise, with 50 s file size, the SCQCKH-SDT technique has provided increased KBT of 0.095 s whereas the ECC, HE, and OHE techniques have obtained reduced KBTs of 0.090, 0.092, and 0.094 respectively.
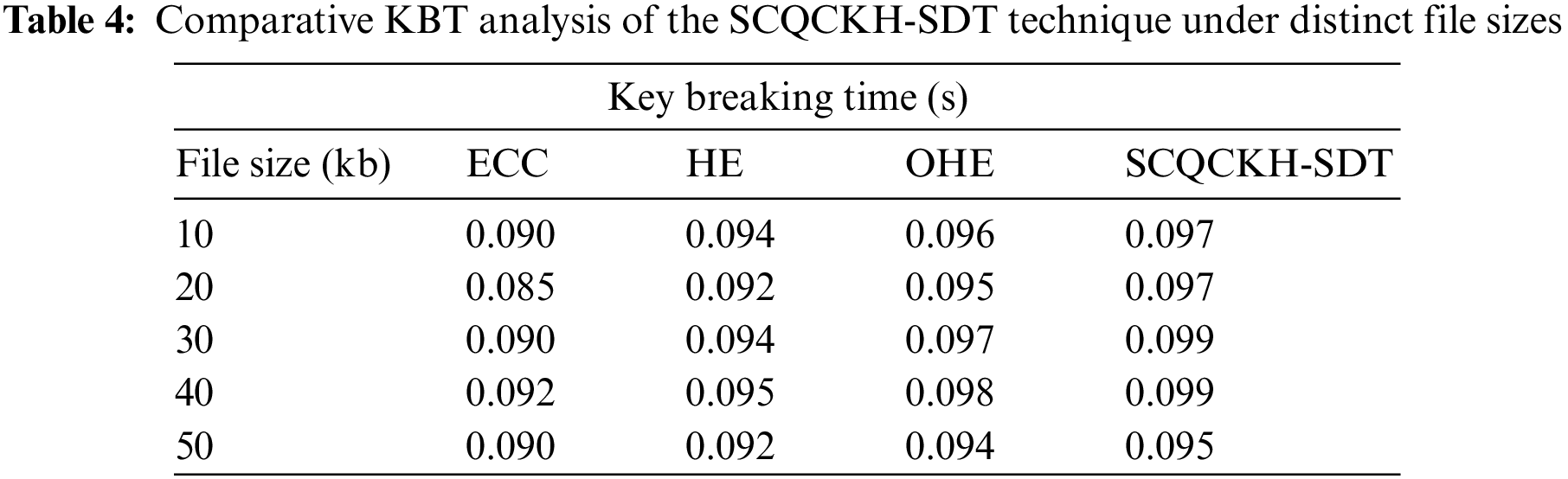
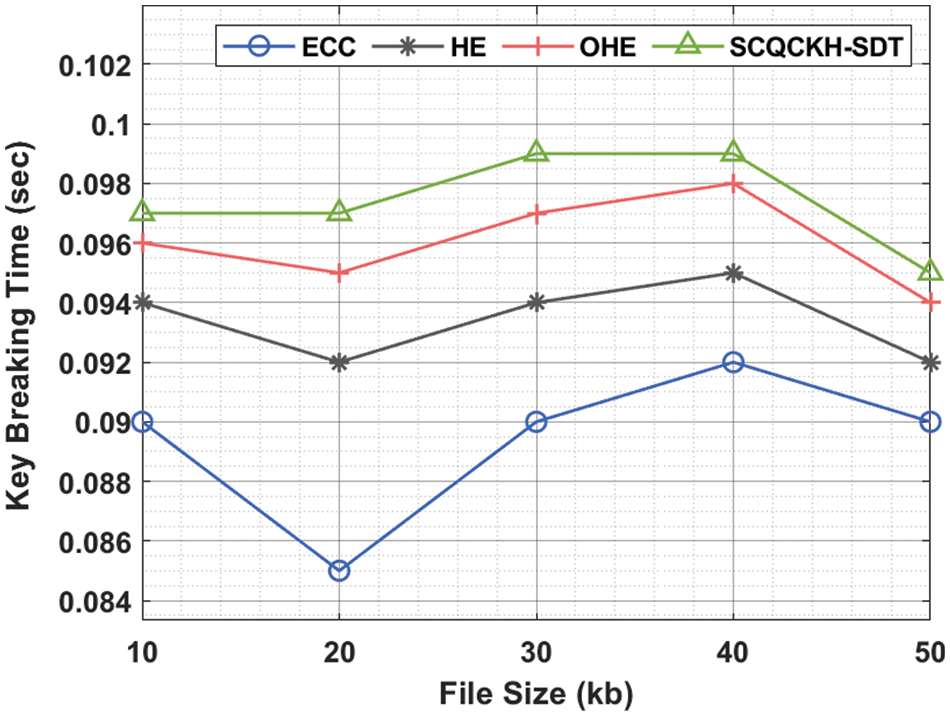
Figure 8: KBT analysis of the SCQCKH-SDT with existing techniques
The key size analysis of the SCQCKH-SDT technique is compared with the recent methods in Tab. 5 and Fig. 9. The experimental results indicated that the SCQCKH-SDT technique has accomplished increased key size under all files. For instance, with 10 kb file size, the SCQCKH-SDT technique has provided increased key size of 25 kb whereas the ECC, HE, and OHE techniques have obtained reduced key sizes of 20, 21 and 22 kb respectively. Along with that, with 30 kb file size, the SCQCKH-SDT technique has resulted to better key size of 44 kb whereas the ECC, HE, and OHE techniques have accomplished decreased key sizes of 36, 40 and 42 kb respectively. In line with, with 50 kb file size, the SCQCKH-SDT technique has provided increased key size of 64 kb whereas the ECC, HE, and OHE techniques have obtained reduced key sizes of 58, 60 and 62 kb respectively.
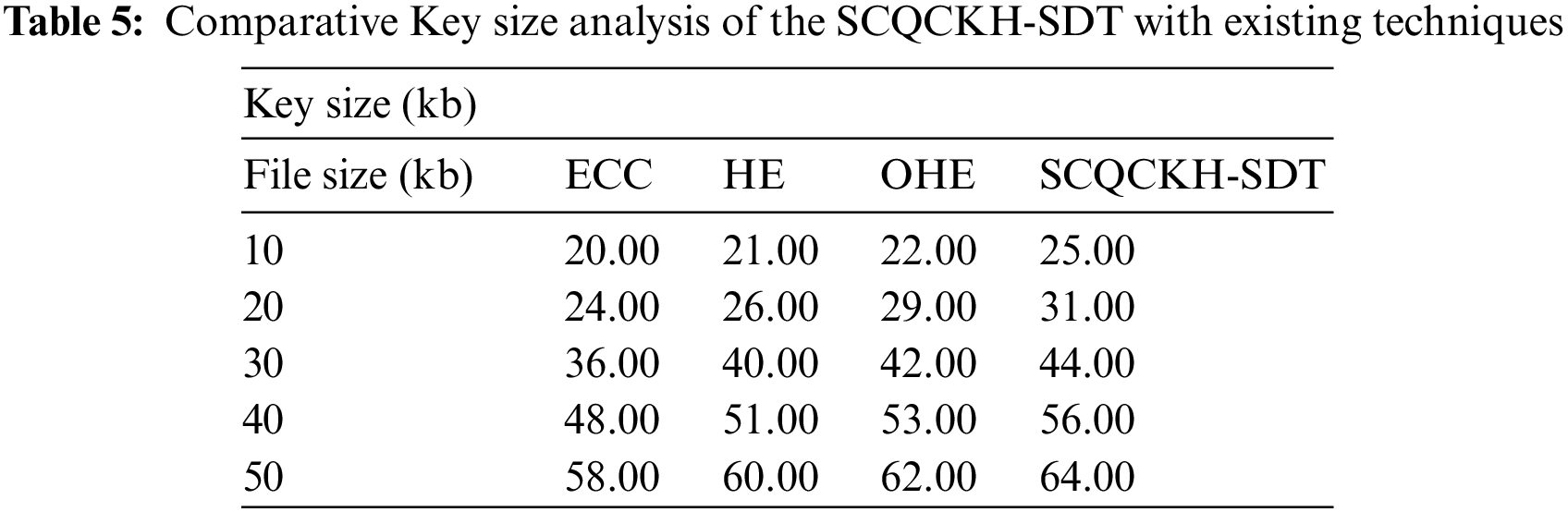
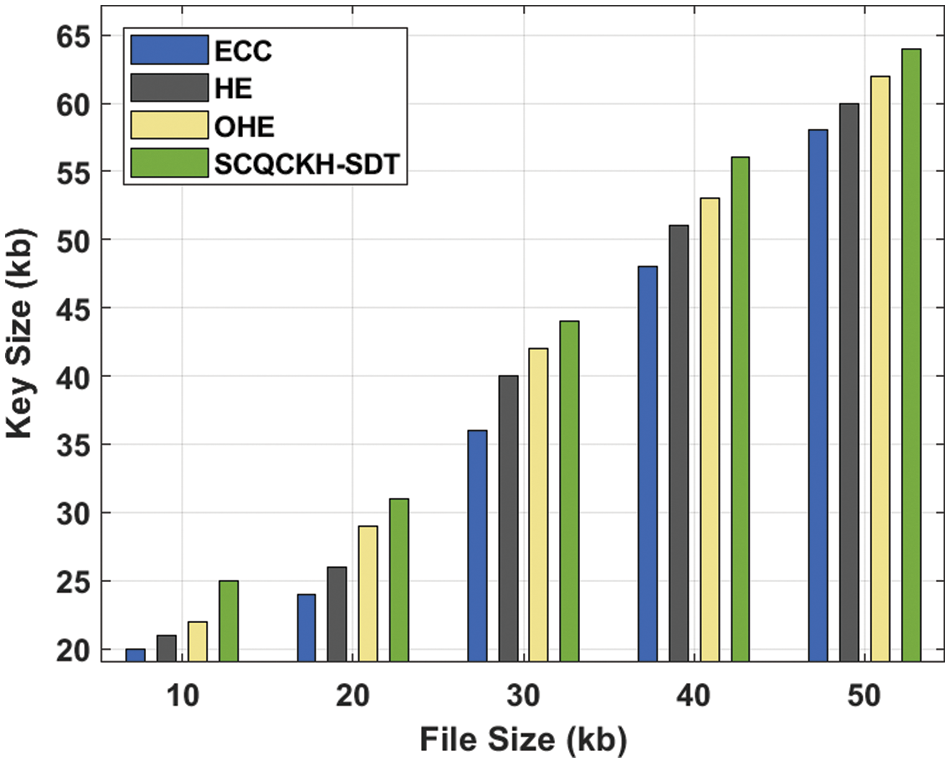
Figure 9: Key size analysis of the SCQCKH-SDT with existing techniques
Finally, a brief EM and DM analysis of the SCQCKH-SDT technique with existing methods take place in Tab. 6 and Fig. 10. The results shown that the ECC algorithm has shown worse outcome with the EM and DM of 1022.26 and 510.294 kb respectively. Followed by, the HE and OHE techniques have obtained slightly increased values of EM and DM. However, the SCQCKH-SDT technique has accomplished effective performance with the higher EM and DM of 1152.24 and 621.37 kb respectively.
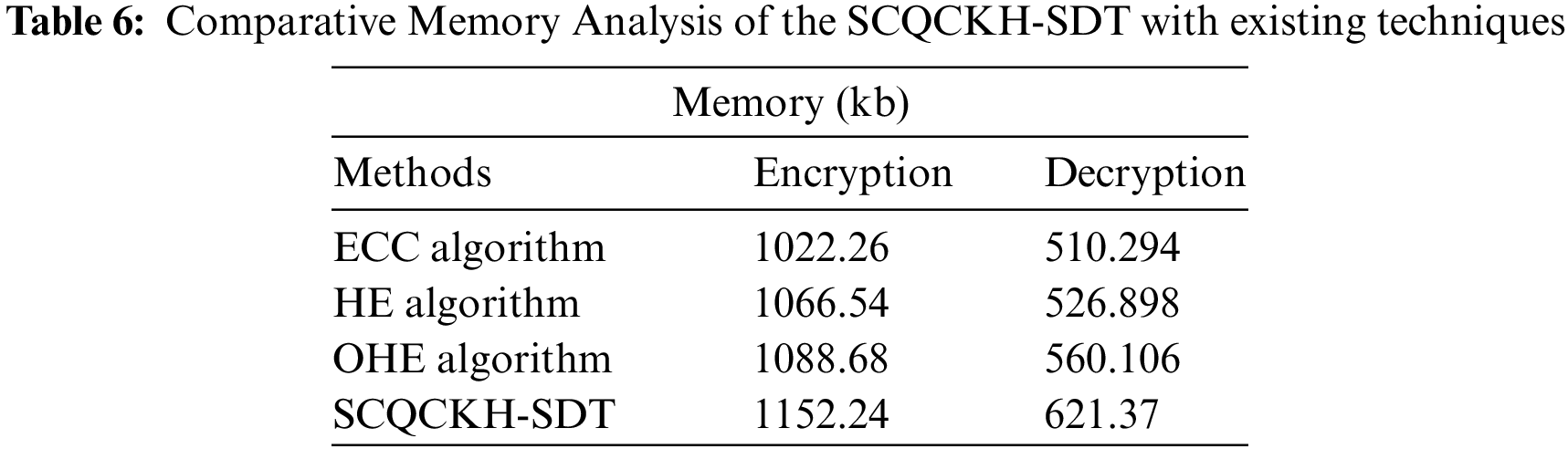
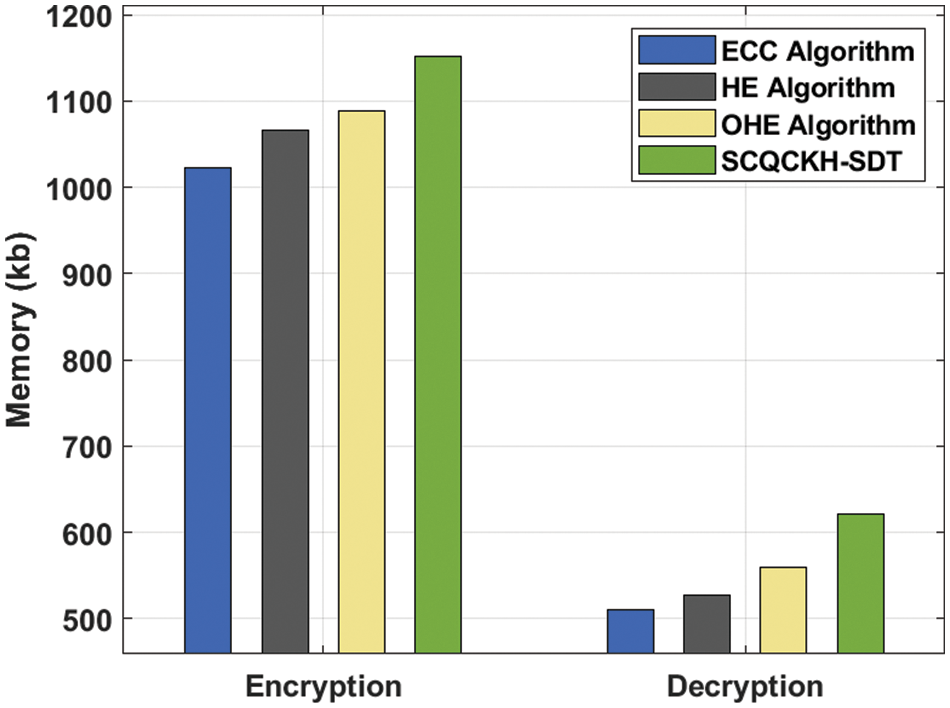
Figure 10: Comparative EM and DM analysis of the SCQCKH-SDT with existing techniques
From the detailed results and discussion, it is obvious that the SCQCKH-SDT technique has outperformed the other techniques under diverse aspects. Therefore, the SCQCKH-SDT technique can be utilized as an effective tool for accomplishing security in the IoT environment.
This paper has developed a SCQCKH-SDT to effectively encrypted the data by the use of optimal keys generated by the CQKH algorithm in the IoT environment. The proposed SCQCKH-SDT technique follows a 2-stage process namely signcryption based encryption and CQKH based optimal key generation process. The CQKH algorithm incorporates the concept of quantum computing and chaotic theory into the traditional KH algorithm. The performance validation of the SCQCKH-SDT technique is performed using benchmark dataset and the results are examined under various aspects. An extensive comparative analysis reported the superior performance of the SCQCKH-SDT technique over the recent approaches. In future, lightweight cryptographic techniques with classification models can be designed.
Funding Statement: The authors received no specific funding for this study.
Conflicts of Interest: The authors declare that they have no conflicts of interest to report regarding the present study.
1. S. Rajesh, V. Paul, V. G. Menon and M. R. Khosravi, “A secure and efficient lightweight symmetric encryption scheme for transfer of text files between embedded IoT devices,” Symmetry, vol. 11, no. 2, pp. 293– 312, 2019. [Google Scholar]
2. S. Kim and I. Lee, “IoT device security based on proxy re-encryption,” Journal of Ambient Intelligence and Humanized Computing, vol. 9, no. 4, pp. 1267–1273, 2018. [Google Scholar]
3. A. Hameed and A. Alomary, “Security issues in IoT: A survey,” in Proc. Int. Conf. on Innovation and Intelligence for Informatics, Computing, and Technologies (3ICT), Bahrain, pp. 1–5, 2019. [Google Scholar]
4. N. Pakniat, D. Shiraly and Z. Eslami, “Certificateless authenticated encryption with keyword search: Enhanced security model and a concrete construction for industrial IoT,” Journal of Information Security and Applications, vol. 53, no. 5, pp. 102525–102540, 2020. [Google Scholar]
5. B. Y. Sung, K. B. Kim and K. W. Shin, “An AES-GCM authenticated encryption crypto-core for IoT security,” in Proc. Int. Conf. on Electronics, Information, and Communication (ICEIC, Hawaii, USA, pp. 1–3, 2018. [Google Scholar]
6. H. Yan, Y. Wang, C. Jia, J. Li, Y. Xiang et al., “IoT-FBAC: Function-based access control scheme using identity-based encryption in IoT,” Future Generation Computer Systems, vol. 95, no. 7, pp. 344–353, 2019. [Google Scholar]
7. D. A. T. Toledo, O. R. L. Bonilla, E. E. G. Guerrero, E. T. Cuautle, D. L. Mancilla et al., “Real-time RGB image encryption for IoT applications using enhanced sequences from chaotic maps,” Chaos, Solitons & Fractals, vol. 153, no. 3, pp. 111506–111520, 2021. [Google Scholar]
8. M. A. F. Al-Husainy, B. Al-Shargabi and S. Aljawarneh, “Lightweight cryptography system for IoT devices using DNA,” Computers & Electrical Engineering, vol. 95, pp. 107418, 2021. [Google Scholar]
9. M. sarac, N. Pavlovic, N. Bacanin, F. Al-Turjman and S. Adamovic, “Increasing privacy and security by integrating a blockchain secure interface into an IoT device security gateway architecture,” Energy Reports, vol. 7, no. 18, pp. 8075–8082, 2021. [Google Scholar]
10. M. S. Kang, “Design of AES-based encryption chip for IoT security,” The Journal of the Institute of Internet, Broadcasting and Communication, vol. 21, no. 1, pp. 1–6, 2021. [Google Scholar]
11. W. Jang and S. Y. Lee, “Partial image encryption using format-preserving encryption in image processing systems for Internet of things environment,” International Journal of Distributed Sensor Networks, vol. 16, no. 3, pp. 1–16, 2021. [Google Scholar]
12. S. Medileh, A. Laouid, R. Euler, A. Bounceur, M. Hammoudeh et al., “A flexible encryption technique for the Internet of Things environment,” Ad Hoc Networks, vol. 106, no. 1, pp. 102240–102258, 2020. [Google Scholar]
13. J. Jeong, L. Bajracharya and M. Hwang, “Optimal lightweight cryptography algorithm for environmental monitoring service based on IoT,” in Proc. Int. Conf. on Information Science and Applications, Singapore, pp. 361–367, 2018. [Google Scholar]
14. A. R. Chowdhury, J. Mahmud, A. R. M. Kamal and M. A. Hamid, “MAES: Modified advanced encryption standard for resource constraint environments,” in Proc. IEEE Sensors Applications Symp. (SAS), Seoul, Korea, pp. 1–6, 2018. [Google Scholar]
15. R. Denis and P. Madhubala, “Hybrid data encryption model integrating multi-objective adaptive genetic algorithm for secure medical data communication over cloud-based healthcare systems,” Multimedia Tools and Applications, vol. 80, no. 14, pp. 21165–21202, 2021. [Google Scholar]
16. R. B. Nishanth, B. Ramakrishnan and M. Selvi, “Improved signcryption algorithm for information security in networks,” International Journal of Computer Networks and Applications (IJCNA), vol. 2, no. 3, pp. 151–157, 2015. [Google Scholar]
17. G. G. Wang, L. Guo, A. H. Gandomi, G. S. Hao, H. Wang et al., “Chaotic krill herd algorithm,” Information Sciences, vol. 274, no. 2, pp. 17–34, 2014. [Google Scholar]
18. P. Niveditha, M. S. Sujatha and M. Vijaya Kumar, “Implementation of krill herd algorithm for optimal sizing and placing of DG in radial distribution system,” International Journal of Grid and Distributed Computing, vol. 11, no. 9, pp. 51–64, 2018. [Google Scholar]
19. S. Li and Y. Tian, “Krill herd algorithm with chaotic time interval and elitism scheme,” Systems Science & Control Engineering, vol. 7, no. 2, pp. 71–84, 2019. [Google Scholar]
20. R. K. Agrawal, B. Kaur and S. Sharma, “Quantum based whale optimization algorithm for wrapper feature selection,” Applied Soft Computing, vol. 89, no. 1, pp. 106092–106106, 2020. [Google Scholar]
21. G. Kalyani and S. Chaudhari, “An efficient approach for enhancing security in Internet of Things using the optimum authentication key,” International Journal of Computers and Applications, vol. 42, no. 3, pp. 306–314, 2020. [Google Scholar]
22. N. Krishnaraj, M. Elhoseny, E. L. Lydia, K. Shankar and O. ALDabbas, “An efficient radix trie-based semantic visual indexing model for large-scale image retrieval in cloud environment,” Software: Practice and Experience, vol. 51, no. 3, pp. 489–502, 2021. [Google Scholar]
23. J. Yan, L. Wang, L. Wang, Y. Yang and W. Yao, “Efficient lattice-based signcryption in standard model,” Mathematical Problems in Engineering, vol. 2013, no. 702539, pp. 1–19, 2013. [Google Scholar]
24. K. Tamilarasi and A. Jawahar, “Medical data security for healthcare applications using hybrid lightweight encryption and swarm optimization algorithm,” Wireless Personal Communications, vol. 114, no. 3, pp. 1–16, 2020. [Google Scholar]
25. M. Fotouhi, M. Bayat, A. K. Das, H. A. N. Far, S. M. Pournaghi et al., “A lightweight and secure two-factor authentication scheme for wireless body area networks in health-care IoT,” Computer Networks, vol. 177, no. 1, pp. 107333–107347, 2020. [Google Scholar]
26. R. K. Mahendran and P. Velusamy, “A secure fuzzy extractor based biometric key authentication scheme for body sensor network in Internet of Medical Things,” Computer Communications, vol. 153, no. 1, pp. 545–552, 2020. [Google Scholar]
27. C. Vijayakumaran, B. Muthusenthil and B. Manickavasagam, “A reliable next generation cyber security architecture for industrial Internet of Things environment,” International Journal of Electrical and Computer Engineering, vol. 10, no. 1, pp. 387–395, 2020. [Google Scholar]
28. B. Muthusenthil, C. Vijayakumaran and H. Kim, “Security and privacy framework for academic monitoring system,” in Proc. 8th Int. Conf. on Security Technology (SecTech), Jeju Island, South Korea, pp. 5–8, 2015. [Google Scholar]
29. X. R. Zhang, X. Sun, X. M. Sun, W. Sun and S. K. Jha, “Robust reversible audio watermarking scheme for telemedicine and privacy protection,” Computers, Materials & Continua, vol. 71, no. 2, pp. 3035–3050, 2022. [Google Scholar]
30. X. R. Zhang, W. F. Zhang, W. Sun, X. M. Sun and S. K. Jha, “A robust 3-D medical watermarking based on wavelet transform for data protection,” Computer Systems Science & Engineering, vol. 41, no. 3, pp. 1043–1056, 2022. [Google Scholar]
 | This work is licensed under a Creative Commons Attribution 4.0 International License, which permits unrestricted use, distribution, and reproduction in any medium, provided the original work is properly cited. |