DOI:10.32604/cmc.2022.027496

| Computers, Materials & Continua DOI:10.32604/cmc.2022.027496 |  |
| Article |
Protected Fair Secret Sharing Based Bivariate Asymmetric Polynomials in Satellite Network
1Department of Electronics and Communication Engineering, Beijing Electronics Science and Technology Institute, Beijing, 100070, China
2State Key Laboratory of Integrated Services Networks, Xidian University, Xi’an, 710126, China
3Department of Cryptography and Technology, Beijing Electronics Science and Technology Institute, Beijing, 100070, China
4Department of Cyberspace Security, Beijing Electronic Science and Technology Institute, Beijing, 100070, China
5School of Communication Engineering, Xidian University, Xi’an, 710126, China
6Institute of Information Engineering, Chinese Academy of Sciences, Beijing, 100093, China
7University of Management Technology, Lahore-Pakistan, 55300, Pakistan
*Corresponding Author: Chao Guo. Email: guo99chao@163.com
Received: 19 January 2022; Accepted: 08 March 2022
Abstract: Verifiable secret sharing mainly solves the cheating behavior between malicious participants and the ground control center in the satellite network. The verification stage can verify the effectiveness of secret shares issued by the ground control center to each participant and verify the effectiveness of secret shares shown by participants. We use a lot of difficult assumptions based on mathematical problems in the verification stage, such as solving the difficult problem of the discrete logarithm, large integer prime factorization, and so on. Compared with other verifiable secret sharing schemes designed for difficult problems under the same security, the verifiable secret sharing scheme based on the Elliptic Curve Cryptography (ECC) system has the advantages of less computational overhead and shorter key. At present, the binary polynomial is a single secret scheme and cannot provide effective verification. Therefore, based on a Protected Verifiable Synchronous Multi Secret Sharing (PVS-MSS) scheme, this paper is designed based on bivariate asymmetric polynomials. The advanced verifiable attribute is introduced into the Protected Secret Sharing (PSS) scheme. This paper extends the protected synchronous multi-secret sharing scheme based on bivariate polynomial design. The ECC system constructs the security channel between the ground control center and participants and constructs the verification algorithm. Through the verification algorithm, any participant can verify the consistency and effectiveness of the secret shadow and secret share received from other participants or presented by the secret distribution center. Therefore, no additional key agreement protocol is required; participants do not need to negotiate the session key for encryption; the secret share polynomial can generate the session key between participants and speed up the secret reconstruction process. The verification stage has lower computational complexity than the verifiable scheme constructed by Rivest Shamir Adleman (RSA) and other encryption methods. Chinese Remainder Theorem (CRT) is used to update the secret shadow. The secret shadow does not need to be updated with the change of the scheme shared secret, and the public value update efficiency is higher. Reduce the complexity of sharing secret updates in a synchronous multi-secret sharing scheme.
Keywords: Multi-secret sharing; binary asymmetric; verifiable synchronization; protected; satellite network
A Satellite network is a comprehensive information system composed of different types of satellites in different orbits, ground control centers, and user terminals. It has the characteristics of wide coverage and flexible networking and is widely used in military, resource survey, meteorology, and other fields. However, Li et al. proposed a resource allocation scheme [1]. Md introduces a method to save satellite space [2]. However, due to the available deployment of satellites, limited onboard resources, transmission data is easy to be intercepted, and other security threats, the secret protection in the process of satellite transmission has also become particularly important.
In 1979, Shamir and Blakley proposed
Many secret sharing technologies exist in satellite network secret sharing schemes, such as literature [18]. We need to ensure the security of multiple nodes in the communication requirements of satellite networks. And the secret-sharing verification shall be distributed in the ground control center and each node satellite. We propose a verifiable secret sharing scheme based on binary asymmetric polynomials. At present, verifiable secret sharing schemes based on bivariate polynomial design are all single secret sharing schemes [19]; Secondly, the primary purpose of the design is to construct an efficient verifiable secret sharing protocol in the presence of different numbers of cheaters. Research status of secret sharing scheme based on bivariate polynomial design: PSS scheme lacks various additional attributes to resist separate spoofing attacks and is suitable for different scenarios [20]; Reference [21,22], a simple multi-secret sharing scheme, can’t resist the invasion of semi-honest people; The Verifiable Multi-Secret Sharing (VMSS) in reference [23] has no protected characteristics. The primary purpose of this scheme research is the verifiable attribute introduced into a secret sharing scheme with protected features like the PSS scheme. Secondly, it extends the similar design of [24] synchronous multi-secret sharing scheme to make it more widely used. The scheme has the following advantages:
■ There is no need for a secure channel between that secret distribution center and the participant.
■ No additional key agreement protocol is needed: Participants do not need to negotiate extra session keys for encryption. The secret share polynomial can generate session keys among participants, thus accelerating the process of secret reconstruction.
■ Protected: The pairwise session key generated by a share polynomial can protect the information exchange between participants in the process of secret reconstruction and resist external attacks.
■ ECC realizes verifiable attributes. The verification phase has lower computational complexity than verifiable schemes constructed by RSA and other encryption methods.
■ Synchronous multi-secret sharing: the number of optional shared secrets in the secret distribution center is flexible. A single secret reconstruction process can reconstruct multiple shared secret values according to different situations.
Although literature [25] proposed placing some calculations below the ground or LEO, it does not introduce security issues. Therefore, to ensure security under the same premise, we achieve less computing cost, shorter key, and save system resources according to the characteristics of limited satellite resources and limited bandwidth. The ECC system constructs the safety channel between the ground control center and the node satellite. Using CRT to update the secret shadow, the ground control center only needs to publish part of the public value, which makes the public value update more efficient.
Let P be a prime number and k be the key
When there are t participants
Any two prime
Set up
Fig. 1 describes the process of participants receiving secrets. Participants’ environment is changeable, such as the ocean, wild, etc. Of course, there are various participants, such as individual participants on the ground, ground satellite stations, or satellites in orbit in the air. First, the ground control center distributes secret shares and sends broadcast parameters to Geostationary Earth Orbiting (GEO). Then, GEO sends it to each participant or Low Earth Orbiting (LEO) through the link to get the corresponding secret share. At this time, each participant will generate a unique session key and communicate with each other. The secret can be reconstructed under two different thresholds when ensuring that the participants are honest.
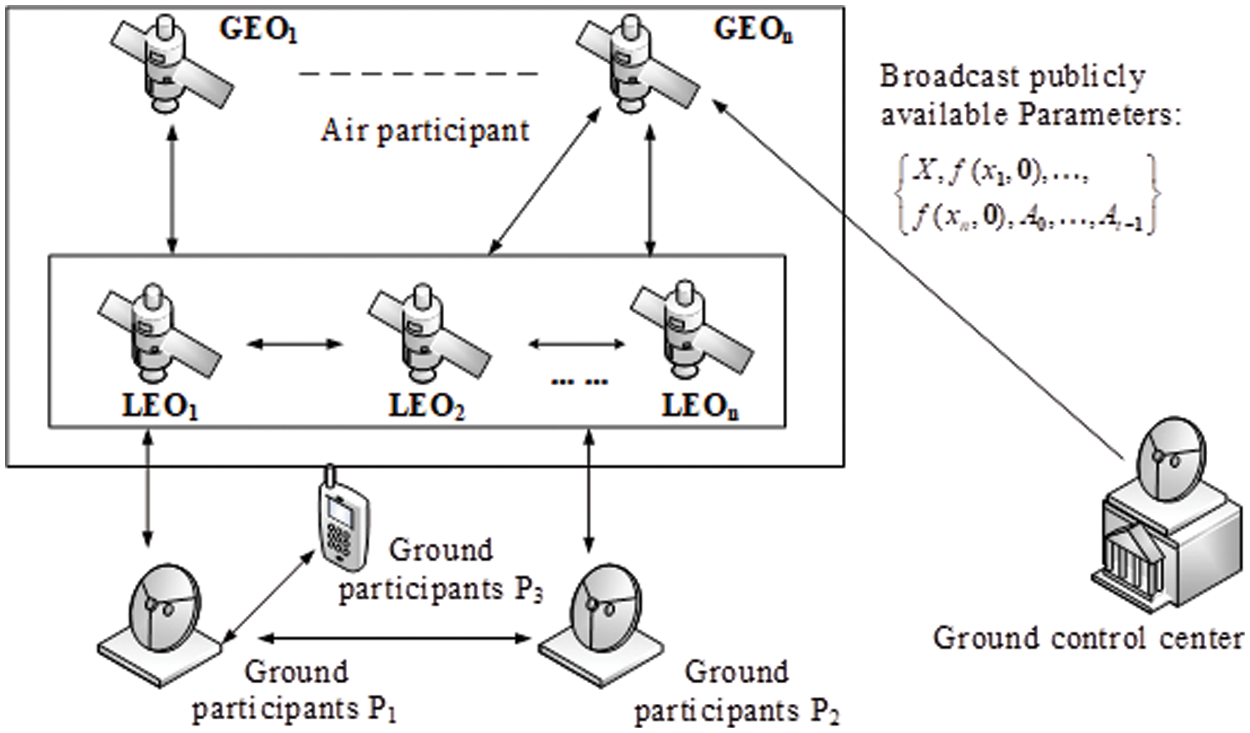
Figure 1: Satellite network secret sharing scheme model
Suppose there is a trusted ground control center D, a set of actors
■
■
Perform the following steps between D and
■ Step 1:
■ Step 2: Each participant
■ Step 3: Both D and
■ Step 4:
■ Step 5: When any participant
Finally, the ground control center D and participant
Suppose D wants to share k secrets
Case 1: When the number of secrets to be shared, k is less than or equal to the threshold value t.
Step 1: D constructs the following binary asymmetric polynomials with the order x as
There are k coefficients about the x term in
Step 2: D select n random integers
Step 3: D calculate the secret share
Step 4: D calculates the unique integer
Step 5: D calculates the secret polynomials
Step 6: Open
Case 2: The number of secrets to be shared k is greater than the threshold value t.
Step 1: D constructs the following binary asymmetric polynomials with the order x as
There are k coefficients about the x term in
Step 2: D select n random integers
Step 3: D calculate the secret share
Step 4: D calculates the unique integer
Step 5: D calculates the secret polynomials
Step 6:
Step 7: Open
Because the PVS-MSS scheme has protected properties, resistance to reconstruct phase external attacks, but internal attackers, will reduce the schema’s safety. Because internal attackers can be arbitrary tamper with the secret shadow, whether conspired with the collusion attack, internal attackers benefit maximization (the remaining honest refactoring can’t get the Shared secret). Therefore, the scheme of PVS-MSS has two different secret numbers. Taking
■ Step 1: Any refactor
■ Step 2: The PVS-MSS scheme does not lose generality. Any reconstructor
In the secret reconstruction stage, if the set of reconstructors participating in the protocol is
Step 1: Any two reconstructors
Step 2: Any reconstructor
Step 3: When the reconstructor
Step 4: Each refactorer is divided into the following two cases to reconstruct the shared secret value:
■ Case 1: When the number of shared secrets k is less than or equal to the threshold value
■ Case 2: When the number of shared secrets k is greater than the threshold value
The coefficient set
When the PVS-MSS scheme shares a secret update, the polynomial constructed by the synchronous multi-secret sharing scheme also needs to be updated, and the public value of the scheme also needs to be updated. YCH and other schemes adopt a bivariate univariate function to ensure that the ground control center D does not need to re-issue secret shadow to each participant for the next new secret sharing [28]. The master secret shadow of the scheme is also multi-purpose without initialization. Only the ground control center D needs to update some public values. In particular, the new X is very high. According to the CRT theorem in Section 2.2 of this paper,
Theorem 4.1: The PVS-MSS scheme has any reconfigurable secret greater than or equal to t reconfigurator.
Prove: Suppose
Theorem 4.2: When
Prove: The secret share
Theorem 4.3: The main secret shadow
Prove: Suppose an attacker
Theorem 4.4: It is computationally difficult to calculate the secret
Prove:
Theorem 4.5: The scheme resists internal and external attacks in the reconstruction process.
Prove: Suppose there is an internal attacker
In the reconstruction process, The encryption of the session key
5 Scheme Comparison and Performance Analysis
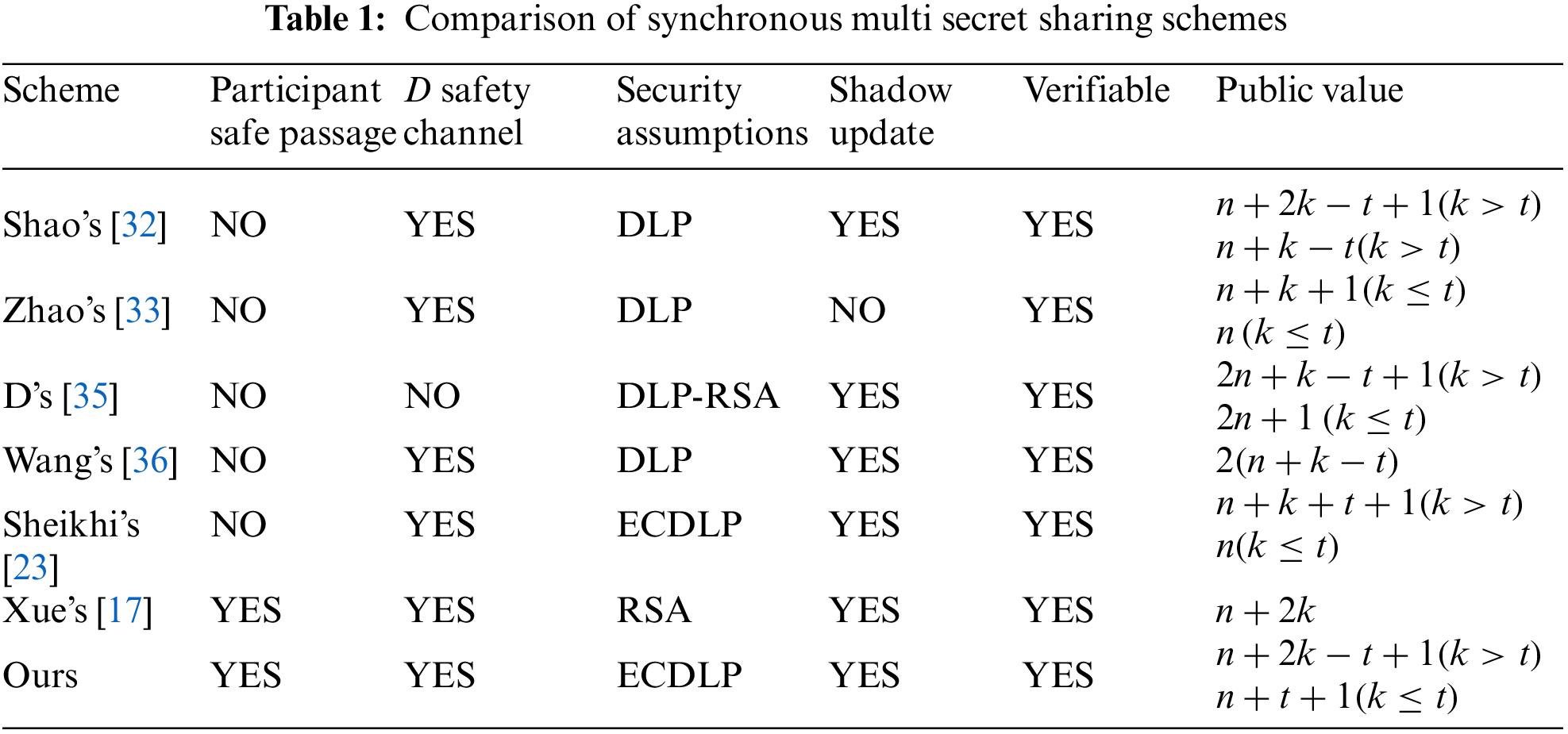
The PVS-MSS scheme’s main parameters, characteristics, and cost are compared with existing schemes. Compared with synchronous multi-secret sharing schemes such as [21,28–31], the PVS-MSS scheme introduces verifiability. There is no need to maintain an additional secure channel between the ground control center and participants. Compared with the verifiable multi-secret sharing schemes in [23,32–35], PVS-MSS scheme participants do not need additional key negotiation mechanisms, which reduces the actual operating cost of the scheme. In the PVS-MSS scheme, the security of the safety channel between the ground control center and participants is based on the Discrete Logarithm Problem of Elliptic Curve (ECDLP). In [32], security is based on the Discrete Logarithm Problem (DLP). Under the same security level, the required parameter bit length is smaller. The amount of calculation is smaller. For example, under the security of 256 bits of the symmetric key, the minimum bit length of the parameter
In the initialization stage of the PVS-MSS scheme, the ground control center and participant calculate
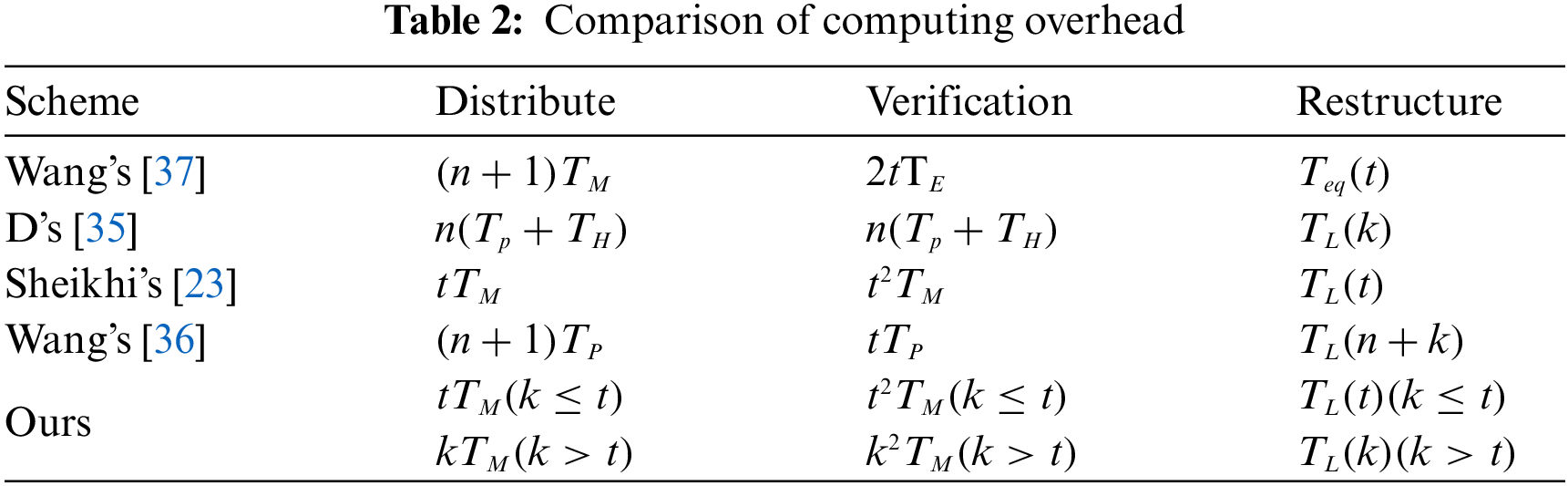
6.1 Secret Share Leakage Probability of Satellite Nodes
Reference [38] shows that the probability of secret share leakage of a single satellite is an exponential function, expressed by
We can see from Fig. 2 that the abscissa shown in the figure below is time, and the ordinate is leakage probability. With the increase of time X, the leakage probability also increases, and the lower the leakage rate
Figure 2: Secret failure rate
6.2 Satellite Network Security Quality
Reference [39] shows that the key of each satellite network node is different. Hence, the attack on a satellite nodes is a a Bernoulli process, and the probability that the secret share obtained by the attacker is less than t in one cycle:
When
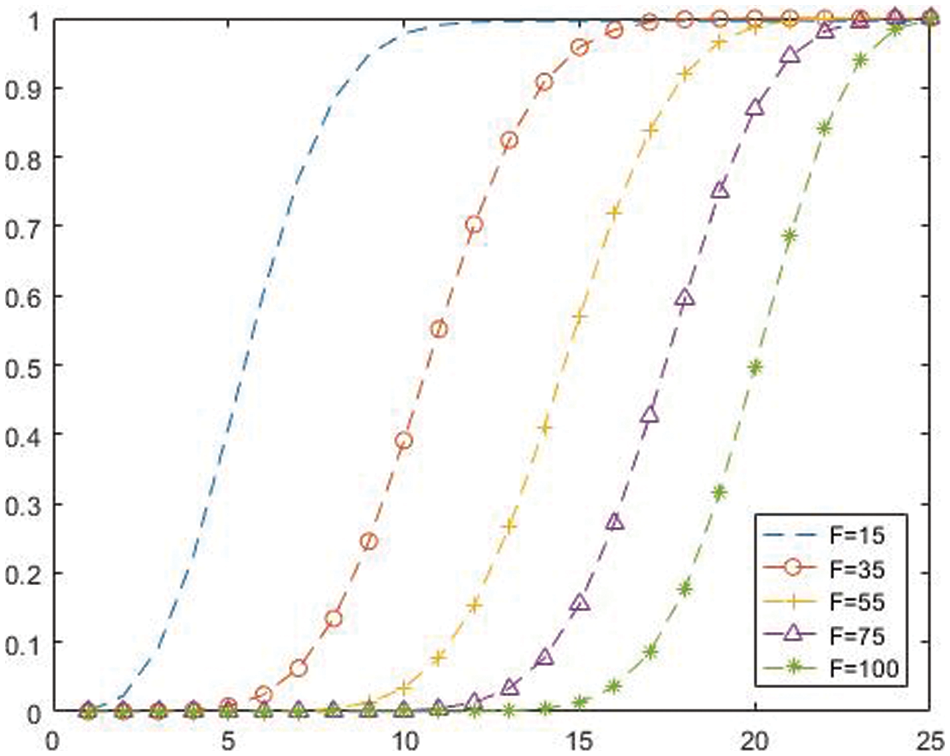
Figure 3: Satellite network security quality
It is advanced to propose a protected synchronous multi-secret sharing scheme based on binary asymmetric polynomials. It is very advanced to introduce verifiable attributes into the PSS scheme. This scheme extends the protected synchronous multi-secret sharing scheme based on binary polynomial design. This scheme is suitable for the secret sharing of satellite networks. The ECC system is used to interact with the main secret shadow safely, and a verification algorithm is constructed. Through the verification algorithm, any participant can verify the consistency and effectiveness of the secret shadow received from other participants or the secret share presented by the ground control center. We discuss the correctness of the algorithm in Section 4.1 of this paper. Whether the number of shared secrets is greater than or less than the threshold, we can get the unique polynomial from the Lagrange difference formula and the additive homomorphism of secret sharing
Acknowledgement: We gratefully acknowledge anonymous reviewers who read drafts and made many helpful suggestions.
Funding Statement: This work is supported by The State Key Laboratory of Integrated Services Networks, Xidian University (ISN22-13).
Conflicts of Interest: The authors declare that they have no conflicts of interest to report regarding the present study.
1. Y. Li, J. Xie, M. Xia, Q. Li, M. Li et al., “Dynamic resource pricing and allocation in multilayer satellite network,” Computers, Materials & Continua, vol. 69, no. 3, pp. 3619–3628, 2021. [Google Scholar]
2. M. A. Ullah, T. Alam, A. F. Almutairi and M. T. Islam, “Low profile uhf antenna design for low earth-observation cubesats,” Computers, Materials & Continua, vol. 71, no. 2, pp. 2533–2542, 2022. [Google Scholar]
3. A. Shamir, “How to share a secret,” Communications of the ACM, vol. 22, no. 11, pp. 612–613, 1979. [Google Scholar]
4. G. R. Blakley, “Safeguarding cryptographic keys,” in Int. Workshop on Managing Requirements Knowledge (MARK), New York, NY, USA, pp. 313–318, 1979. [Google Scholar]
5. H. Ghodosi, “Comments on Harn–Lin’s cheating detection scheme,” Designs Codes and Cryptography, vol. 60, no. 1, pp. 63–66, 2011. [Google Scholar]
6. L. Harn and C. Lin, “Detection and identification of cheaters in (t, n) secret sharing scheme,” Designs Codes and Cryptography, vol. 52, no. 1, pp. 15–24, 2009. [Google Scholar]
7. Y. Liu, C. Yang, Y. Wang, Z. Lei and W. Ji, “Cheating identifiable secret sharing scheme using symmetric bivariate polynomial,” Information Sciences, vol. 453, no. 1, pp. 21–29, 2018. [Google Scholar]
8. H. Y. Lin, L. Harn, “Fair reconstruction of a secret,” Information Processing Letters, vol. 55, no. 1, pp. 45–47, 1995. [Google Scholar]
9. L. Harn, “Comments on ‘fair (t, n) threshold secret sharing scheme’,” IET Information Security, vol. 8, no. 6, pp. 303–304, 2014. [Google Scholar]
10. Y. Tian, J. Ma, C. Peng and J. Qi, “Fair (t, n) threshold secret sharing scheme,” IET Information Security, vol. 7, no. 2, pp. 106–112, 2013. [Google Scholar]
11. L. Harn, C. Lin and Y. Li, “Fair secret reconstruction in (t, n) secret sharing,” Journal of Information Security and Applications, vol. 23, pp. 1–7, 2015. [Google Scholar]
12. L. Harn, “Secure secret reconstruction and multi-secret sharing schemes with unconditional security,” Security and Communication Networks, vol. 7, no. 3, pp. 567–573, 2014. [Google Scholar]
13. W. Y. Gu, F. Y. Miao and X. T. He, “Fair secret sharing scheme based on bivariate symmetric polynomials,” Computer Engineering and Applications, vol. 52, no. 13, pp. 38–42+109, 2016. [Google Scholar]
14. L. Mei, C. Xu, L. Xu, X. Yu and C. Zuo, “Verifiable identity-based encryption with keyword search for IoT from lattice,” Computers, Materials & Continua, vol. 68, no. 2, pp. 2299–2314, 2021. [Google Scholar]
15. X. Jin, L. Su and J. Huang, “A reversible data hiding algorithm based on secret sharing,” Journal of Information Hiding and Privacy Protection, vol. 3, no. 2, pp. 69–82, 2021. [Google Scholar]
16. K. Javeed, X. Wang and M. Scott, “High performance hardware support for elliptic curve cryptography over general prime field,” Microprocessors and Microsystems, vol. 51, no. 6, pp. 331–42, 2017. [Google Scholar]
17. K. Xue, W. Meng, H. Zhou, D. S. L. Wei and M. Guizani, “A lightweight and secure group Key based handover authentication protocol for the software-defined space information network,” IEEE Transactions on Wireless Communications, vol. 19, no. 6, pp. 3673–3684, 2020. [Google Scholar]
18. L. Zhang, Y. Wang and H. Zhu, “Safeguarding UAV-enabled wireless power transfer against aerial eavesdropper: A colonel blotto game,” IEEE Wireless Communications Letters, vol. 11, no. 3, pp. 503--507, 2021. [Google Scholar]
19. L. L. Yu and W. Z. Du, “Secret sharing scheme based on symmetric bivariate polynomial,” Computer Engineering and Applications, vol. 56, no. 13, pp. 120–123, 2020. [Google Scholar]
20. L. Harn, C. F. Hsu, Z. Xia and J. W. Zhou, “How to share secret efficiently over networks,” Security and Communication Networks, vol. 2017, pp. 1–6, 2017. [Google Scholar]
21. T. Zhang, X. H. Ke and Y. X. Liu, “(t, n) multi-secret sharing scheme extended from Harn-Hsu’s scheme,” Eurasip Journal on Wireless Communications and Networking, vol. 2018, no. 1, pp. 71, 2018. [Google Scholar]
22. L. Harn, C. F. Hsu, “(t, n) multi-secret sharing scheme based on bivariate polynomial,” Wireless Personal Communications, vol. 95, pp. 1495–1504, 2017. [Google Scholar]
23. Maryam, G. S., Mojtaba, B., Christophe et al., “Threshold verifiable multi-secret sharing based on elliptic curves and Chinese remainder theorem,” IET Information Security, vol. 13, no. 3, pp. 278–284, 2019. [Google Scholar]
24. D. Tang and H. P. Shu,“Bivariate polynomial based secret sharing technology study,” Computer Applications and Software, vol. 29, no. 7, pp. 112–114, 2012. [Google Scholar]
25. L. Zhang, L. Hong, C. Guo, H. T. Xu, L. Y. Song et al., “Satellite-aerial integrated computing in disasters: User association and offloading decision,” in Proc. IEEE Int. Conf. on Communications (ICC), Dublin, Ireland, pp. 554–559, 2020. [Google Scholar]
26. R. L. Rivest, A. Shamir and L. Adleman, “A method for obtaining digital signatures and public-key cryptosystems,” Communications of the ACM, vol. 21, no. 2, pp. 120–126, 1978. [Google Scholar]
27. T. Elgamal, “A public key cryptosystem and a signature scheme based on discrete logarithms,” IEEE Transactions on Information Theory, vol. 31, no. 4, pp. 469–472, 1985. [Google Scholar]
28. C. C. Yang, T. Y. Chang and M. S. Hwang, “A (t, n) multi-secret sharing scheme,” Applied Mathematics and Computation, vol. 151, no. 2, pp. 483–490, 2004. [Google Scholar]
29. C. W. Chan and C. C. Chang, “A scheme for threshold multi-secret sharing,” Applied Mathematics and Computation, vol. 166, no. 1, pp. 1–14, 2005. [Google Scholar]
30. L. J. Pang, Y. Liu and Y. M. Wang, “An efficient. Threshold multi-secret sharing scheme,” Chinese Journal of Electronics, vol. 34, no. 4, pp. 587–589, 2006. [Google Scholar]
31. X. W. Zhong, L. Z. Xiong and Z. H. Xia, “A secure visual secret sharing scheme with authentication based on QR code,” Journal on Big Data, vol. 3, no. 2, pp. 85–95, 2021. [Google Scholar]
32. J. Shao and Z. Cao, “A new efficient (t, n) verifiable multi-secret sharing (VMSS) based on YCH scheme,” Applied Mathematics and Computation, vol. 168, no. 1, pp. 135–140, 2005. [Google Scholar]
33. J. Zhao, J. Zhang and R. Zhao, “A practical verifiable multi-secret sharing scheme,” Computer Standards & Interfaces, vol. 29, no. 1, pp. 138–141, 2007. [Google Scholar]
34. J. Shao, “Efficient verifiable multi-secret sharing scheme based on hash function,” Information Sciences, vol. 278, no. 1, pp. 104–109, 2014. [Google Scholar]
35. M. H. Dehkordi and S. Mashhadi, “An efficient threshold verifiable multi-secret sharing,” Computer Standards & Interfaces, vol. 30, no. 3, pp. 187–190, 2008. [Google Scholar]
36. N. Wang, Y. Y. Cai, J. Fu and X. Q. Chen, “Information privacy protection based on verifiable (t, n)-Threshold multi-secret sharing scheme,” IEEE Access, vol. 8, pp. 20799–20804, 2020. [Google Scholar]
37. S. J. Wang, Y. R. Tsai and C. C. Shen, “Verifiable threshold scheme in multi-secret sharing distributions upon extensions of ECC,” Wireless Personal Communications, vol. 56, no. 1, pp. 173–182, 2011. [Google Scholar]
38. H. F. Chen, W. D. Zhao and G. B. Xi, “Security analysis for proactive secret sharing system,” Zhejiang Daxue Xuebao (Gongxue Ban)/Journal of Zhejiang University, vol. 40, no. 8, pp. 1358–1357, 2006. [Google Scholar]
39. C. Y. Luo, W. Li, H. L. Li and B. Jian, “Measurement method for space networks authenticated key security under distributed CA,” Dianzi Yu Xinxi Xuebao/Journal of Electronics and Information Technology, vol. 31, no. 10, pp. 2316–2320, 2009. [Google Scholar]
 | This work is licensed under a Creative Commons Attribution 4.0 International License, which permits unrestricted use, distribution, and reproduction in any medium, provided the original work is properly cited. |