DOI:10.32604/cmc.2022.025204

| Computers, Materials & Continua DOI:10.32604/cmc.2022.025204 |  |
| Article |
Artificial Intelligence Based Data Offloading Technique for Secure MEC Systems
1Department of Computer Sciences, College of Computer and Information Sciences, Princess Nourah bint Abdulrahman University, Riyadh, 11671, Saudi Arabia
2Department of Information Systems, College of Computer and Information Sciences, Prince Sultan University, Rafha Street, Riyadh, 11586, Saudi Arabia
3Department of Information Systems, College of Computer and Information Sciences, Princess Nourah bint Abdulrahman University, Riyadh, 11671, Saudi Arabia
4Department of Computer Science, College of Science & Arts at Mahayil, King Khalid University, Muhayel Aseer, 62529, Saudi Arabia
5Department of Information Systems, Faculty of Computer and Information Technology, Sana'a University, 61101, Yemen
6Department of Computer and Self Development, Preparatory Year Deanship, Prince Sattam bin Abdulaziz University, Al-Kharj, 16278, Saudi Arabia
*Corresponding Author: Anwer Mustafa Hilal. Email: a.hilal@psau.edu.sa
Received: 16 November 2021; Accepted: 06 January 2022
Abstract: Mobile edge computing (MEC) provides effective cloud services and functionality at the edge device, to improve the quality of service (QoS) of end users by offloading the high computation tasks. Currently, the introduction of deep learning (DL) and hardware technologies paves a method in detecting the current traffic status, data offloading, and cyberattacks in MEC. This study introduces an artificial intelligence with metaheuristic based data offloading technique for Secure MEC (AIMDO-SMEC) systems. The proposed AIMDO-SMEC technique incorporates an effective traffic prediction module using Siamese Neural Networks (SNN) to determine the traffic status in the MEC system. Also, an adaptive sampling cross entropy (ASCE) technique is utilized for data offloading in MEC systems. Moreover, the modified salp swarm algorithm (MSSA) with extreme gradient boosting (XGBoost) technique was implemented to identification and classification of cyberattack that exist in the MEC systems. For examining the enhanced outcomes of the AIMDO-SMEC technique, a comprehensive experimental analysis is carried out and the results demonstrated the enhanced outcomes of the AIMDO-SMEC technique with the minimal completion time of tasks (CTT) of 0.680.
Keywords: Data offloading; mobile edge computing; security; machine learning; artificial intelligence; XGBoost; salp swarm algorithm
Internet of Things (IoT) has heterogeneous resource-based environment which is applied for providing continuous service for fulfilling the end-user requirement. The idea of IoT varies from small sensor which comprises processing, and communication features with storage space. The intelligence of this human communicative behaviour and machines are used for assisting user requirements [1]. With the wide-ranging application of communication tools and several models, the IoT has been employed in the military services, medical sector, mobile communications, industrial fields, etc. The number of information responsible to IoT could not be determined particularly due to the density of a device, the random memory space, and request rate [2]. Mobile Edge Computing (MEC) is an alternative transmission method which provides service to devoted users in the transmitting network. The derived resource is extended to user for offering complex services. The facilities such as mobility, support transformation, elasticity, reliability, and adaptability features support different user device densities. Fig. 1 depicts the framework of MEC [3].
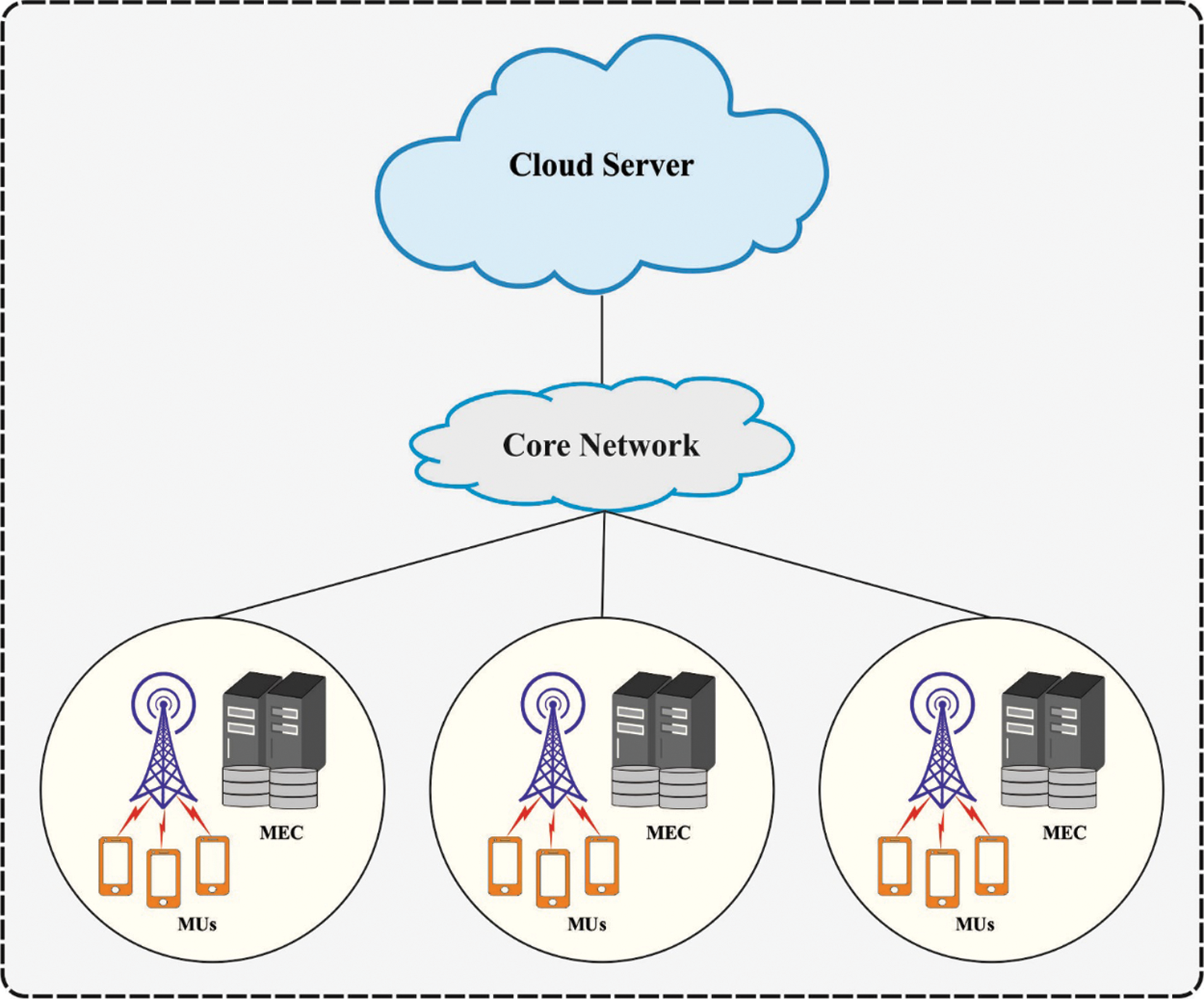
Figure 1: MEC structure
MEC has technologically advanced as a considerable solution for providing nearby distance to the mobile end-users and computing resource at the network edge [4]. The main advantage of MEC technology comprises: reduce the energy consumption of mobile gadgets by mitigating the problem of execution its computing task, giving location awareness, offering exact computing results in an appropriate way, improving the efficacy of the mobile applications, and it is possible to reduce the latency. However, the adoption of MEC method from the whole network architecture was developed for network congestion, MEC server computation capacity, and end-user QoS condition [5]. The challenges of data offloading in the end-users to MEC for further computing are extensively studied from present research while examining the computational and transmission limitations [6].
Various methods and techniques to computational off-loading in MEC were developed from the study with the purpose of assigning radio resources effectively, energy utilization, and decreasing the computational latency. Achieving the best possible offloading result in complex and dynamic multi-user wireless MEC systems are complex process. Additionally, the security threats confronted during data forwarding have not been addressed in each offloading method [7]. Moreover, insufficient data security checks might quickly exceed the advantage of MEC method. In order to counter the cyber threats in MCC, it is crucial to detect early cyber threats, therefore performing fast countermeasures to prevent the risks [8].
Currently, it has various techniques presented for preventing and detecting cyber risks in cloud platforms. The usual limitation of this technique is relatively minimal accuracy from detect cyber threat, and they could not work effectively in cloud system [9]. In this case, they presented a framework utilizing an advanced detecting methodology developed from the DL method that permits detection of various threats with high precision. The DL technique is a subdivision of ML method which emphasizes the approach inspired by the structure and function of NN. In recent times, DL method was performed efficiently in various domains.
Hilal et al. [10] develop a powerful DL based data offloading and cyberattack detection (DL-DOCAD) technology for MEC. The aim of the presented method is to improve the QoE in MEC system. The presented model contains attack detection, traffic prediction, data offloading and. This method employs a GRU based prediction methodology to traffic detection. Additionally, the BSA-FFNN technique is employed as a detector for cyber threats in MEC. Elgendy et al. [11], presented a DL methodology for detecting the best possible solution.
In Mitsis et al. [12], the combined problems of MEC server selection by end-user and the optimum price setting, and data offloading by the MEC are examined in several end-user environments and MEC servers. The programmability and flexibility provided by the SDN technique allow the real time execution of the presented architecture. At first, an SDN controller performs an RL architecture based stochastic learning automata to enable the end-users for selecting MEC servers for data offloading.
Alkatheiri [13] presents privacy-controlled offloading system to improve the data sharing security among the edge-IoT gadgets. In this system, harmonized trust validation with recursive decision making is implemented, afterward the data offloading method. Xu et al. [14], proposed a time-effective offloading technique (TEO) with privacy preservation to smart sensors in edge computing. In fact, the offloading and time utilization of secured information is examined in a formal manner. Next, an enhanced Strength Pareto Evolutionary Algorithm (SPEA2) is leveraged for jointly optimizing the average privacy entropy and time utilization. Eventually, various experiment assessments were performed for verifying the reliability and efficiency of this approach.
This study introduces an artificial intelligence with metaheuristic based data offloading technique for Secure MEC (AIMDO-SMEC) systems. The proposed AIMDO-SMEC technique incorporates an effective traffic prediction module using Siamese Neural Networks (SNN) to determine the traffic status in the MEC system. Also, an adaptive sampling cross entropy (ASCE) technique is utilized for data offloading in MEC systems. Moreover, the modified salp swarm algorithm (MSSA) with extreme gradient boosting (XGBoost) technique is applied for the identification and classification of cyberattacks that exist in the MEC systems. For examining the enhanced outcomes of the AIMDO-SMEC technique, a comprehensive experimental analysis is carried out and the results demonstrated the enhanced outcomes of the AIMDO-SMEC technique interms of different measures.
The rest of the paper is organized as follows. Section 2 introduces the proposed AIMDO-SMEC technique. Then, Section 3 validates the proposed model and Section 4 concludes the study.
In this study, a novel AIMDO-SMEC technique has been developed to accomplish effective data offloading and security in MEC. The projected AIMDO-SMEC approach encompasses three major stages namely SNN based traffic flow prediction, ASCE based data offloading, and MSSA with XGBoost based cyberattack classification.
2.1 Design of SNN Based Traffic Prediction Model
Initially, the SNN model receives the input data and then effectively determines the traffic status in the MEC systems. SNN contains identical networks that accept dissimilar inputs however, they are combined with an energy function at the top. This process calculates few metrics among the high-level feature depiction on all the sides. The variables among the identical networks are tied. Weight tying guarantees that 2 absolutely equal images couldn't be mapped by their corresponding network to distinct positions in feature space since all the networks compute the same functionalities. As well, the network is symmetric, therefore we proposed 2 different images to the identical networks, and the topmost conjoining layers would evaluate the similar metrics since we propose the similar 2 images to the opposite twins. The conventional method is a Siamese convolution neural network with L layer with
The algorithm contains a series of convolution layers, all of which utilize an individual with a filter of differing size and a fixed stride of 1. The amount of convolution filters is stated as a multiple of 16 to enhance the performances. Therefore, the kth filter map in all the layers take the succeeding form:
whereas
2.2 Design of ASCE Based Data Offloading Process
During data offloading process, the ASCE manner was utilized to offload the data in the MEC systems. The CE is termed as probability concept as Kullback Leibler (KL) deviation, also it is simplified as measure of distance between 2 probability distributions. In the event of 2 distributions,
During the representation of CE, is used to cost function in ML, and solves the problem using probability learning. It is learn in
Whereas
Using (3) & (5) and encourage
In the projected algorithm, the CE interrelated measures are employed for extending the probability. In supposing the arbitrariness of sampling, count of instances is lesser, the
Whereas
2.3 Design of MSSA with XGBoost Based Cyberattack Detection Model
At the final stage, the XGBoost model is utilized to identify the occurrence of cyberattacks. XGBoost is an ensemble-based classification method and was developed by Chen et al. [17]. XGBoost employs boosted tree and is employed for regression and classification. XGBoost was extensively utilized for several predictive tasks and produce considerable results because of effective learning speed and capability. XGBoost is an improved form of the gradient boosting tree. The key objective is to decrease the computation resource consumption, loss, and model complexity. The difficulty can be decreased by regularization. Furthermore, the method normalization is employed for alleviating the over-fitting concept. The purpose of utilizing XGBoost for medical data is because of its innate ability to manage the data imbalance. This process operates by including the trees repeatedly by partitioning the feature. In each iteration, the loss decreases, and novel rules are further. The process repeats till the algorithm attained effective performance. Consider D represent the dataset consisting of n number of features:
Y signifies the class attribute; Yi denotes the actual value, whereas Yt characterizes the predictable value [18].
In which Tree_Ens implies a tree ensemble method. *e loss indicates loss function that is variance among the actual and predicted. N signifies the amount of trees. F characterizes the set of trees utilized from the training model. Ω indicates the regularization term.
The parameters involved in the XGBoost model are optimally chosen by the use of MSSA. SSA is newly developed population-based meta-heuristic approach [19]. The main concept was invented from scavenging and propulsion events of salp inside ocean. Salps belong to the salpaide family with transparent and barrel shaped bodies. Inside Deep Ocean individual salps related to one another and make a chain as structure named salp swarm/salp chain at the time of food search. The entire population in the salp swarm could be assumed as, supporters and front-runners. Supporter salp alters their corresponding locations according to each other. The front-runner led the sequence from the anterior to the target by changing its own position as per the nourishment parameter when examining searching space. Mathematical position of front-runner salps are changed as
Whereas
In which l indicates existing iteration and L represents maximal amount of iteration.
Let,
From the optimization perspective, SSA is considered as follows: the chain or swarm of salps is the searching agent and the deep salty ocean is the searching space. The leader salps discover and exploit the whole searching area by changing corresponding position as per the nourishment and save outcomes of all the iterations. Afterward accomplishment of each iteration global optimal solution has last optimal saved solution [20]. The SSA displays some benefits over other meta-heuristic approaches like (i) the method employs only one variable as controlling factor El i.e., linearly reduced (ii) it saves the optimum outcome observed in all iterations by utilizing the food source parameter for later work, once the population breaks down (i) the leader explores the searching area by changing the corresponding position by nourishment resource and the follower alters their corresponding position according to each other and move to the leader salps, that results in barring the model to fall in local optimal stagnation. Fig. 2 demonstrates the flowchart of SSA.
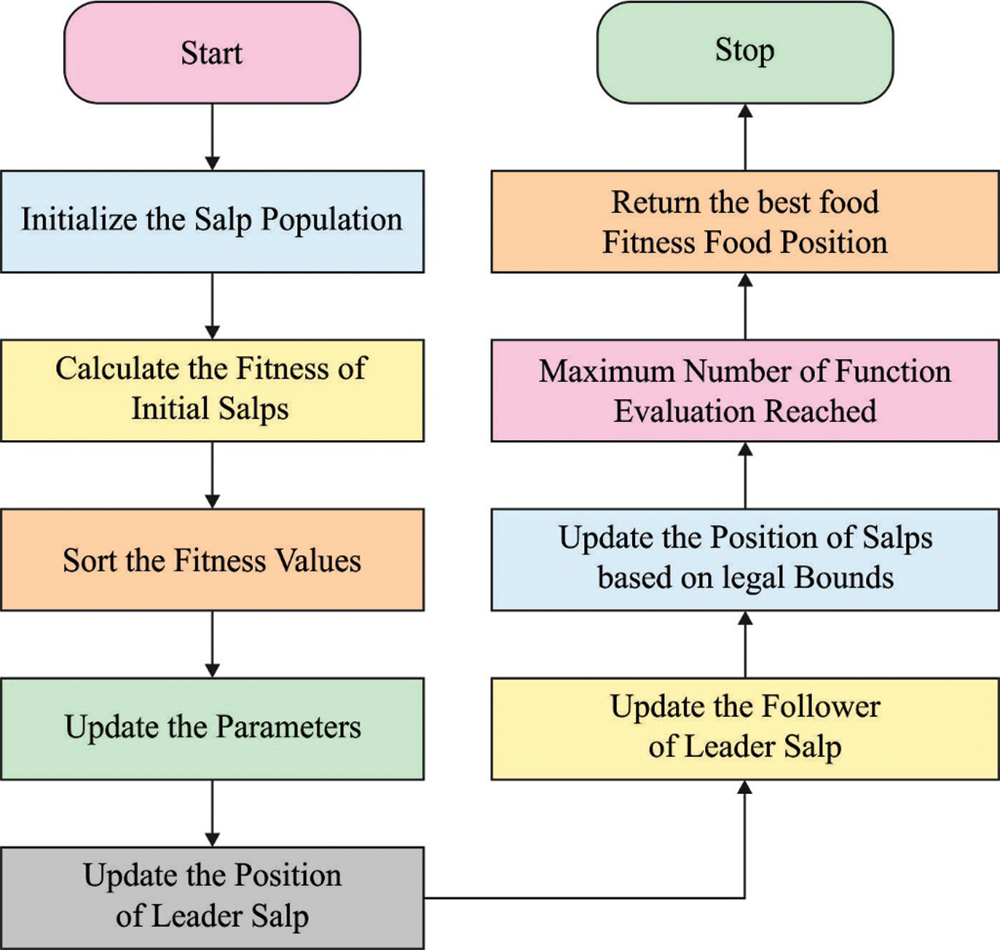
Figure 2: Flowchart of SSA
Every nature simulated meta-heuristic technique selects the primary parameter arbitrarily as the candidate solution. Usually, the arbitrary population elective procedure follows uniform distribution method. As the learning techniques follows black box manner and could not need some background data it begins enhancing the candidate solution for getting optimal result still existing conditions are not attained. The efficiency of such techniques has restricted the count of time utilized by validating all candidate solutions inside the explore space for reaching neighboring optimum solutions as global optimal. In order to obtain global optimal, all adjacent optimum solutions have that scrutinized. Therefore, detection of neighboring optimum solution as only continued with primary guess of parameter could not sufficient in the explore space. Besides, for increasing the exploration ability from the explore space, when it can be assumed that opposite case concurrently with primary guess, afterward the possibility of obtaining neighboring optimum solutions near global optimal improves. For enhancing the exploration ability as well as avoiding early convergence from local minimal, novel evolutionary approach appeared, planned as space transformation search (STS). Based on STS process the ongoing search area was reallocated to fresher area for evaluating candidate solutions for both spaces concurrently. An STS approach includes 4 methods amongst that OBL is among them. The OBL method is written as
where,
The fitness has computed then getting a novel place by utilizing OBL approach in the transmitted space. Afterward, the fitness has been related to the preceding observed fitness created in the primary population of SSA. Afterward, comparative further neighboring optimum solutions are assumed that next generation and continue the round still determined conditions not obtained.
In this section, the experimental results analysis of the AIMDO-SMEC technique takes place and the results are reviewed under several aspects.
Tab. 1 and Fig. 3 showcases the
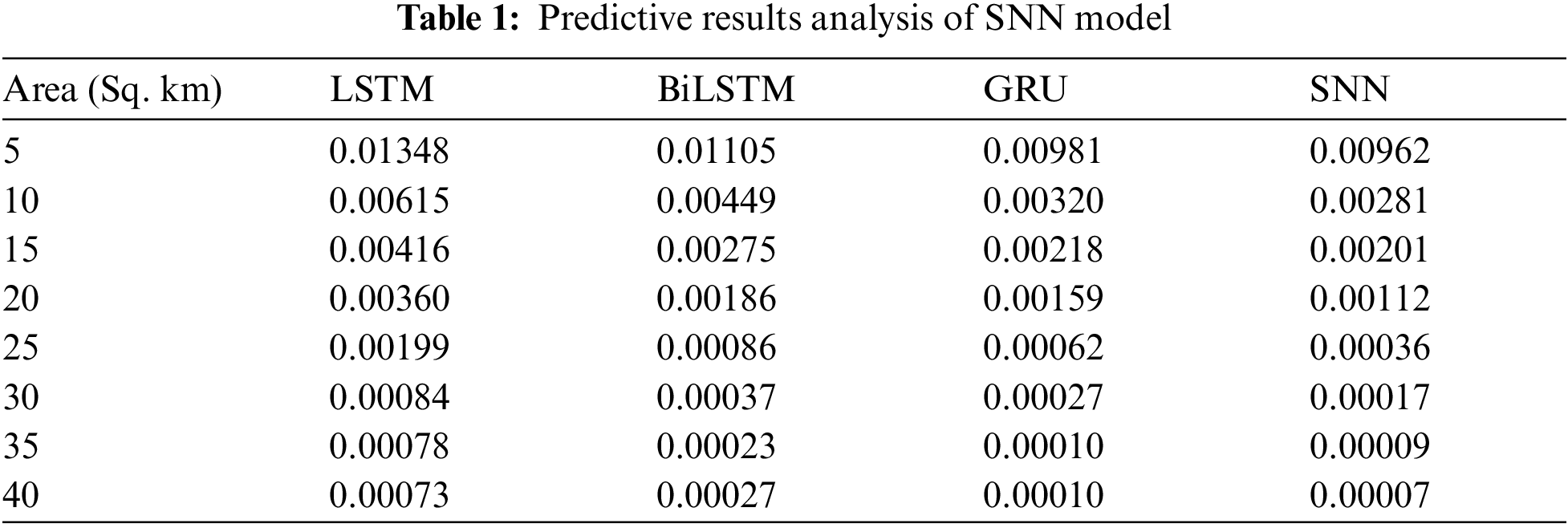
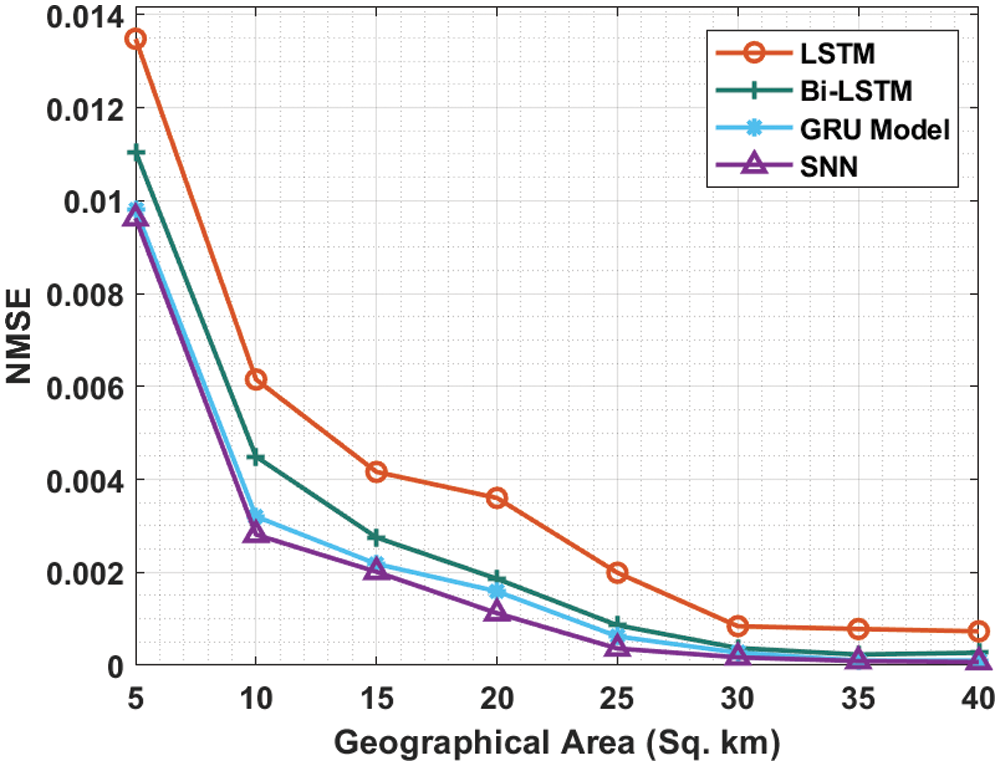
Figure 3: N_MSE analysis of SNN model
Tab. 2 and Fig. 4 depict the CTT analysis of the ASCE manner to study the traffic prediction outcomes. The results ensured that the ASCE method has reached increased prediction outcomes with lower values of CTT. For instance, with task count of 1, the ASCE system has obtained lower CTT of 0.424 but the Adaptive and fixed approaches have attained higher CTT of 0.675 and 0.651 correspondingly. Also, with task count of 5, the ASCE algorithm has obtained lower CTT of 0.513 while the Adaptive and fixed systems have obtained maximal CTT of 1.154 and 1.251 respectively. Similarly, with task count of 15, the ASCE approach has obtained lower CTT of 0.837 while the Adaptive and fixed systems have attained higher CTT of 2.176 and 2.436 correspondingly. At last, with task count of 20, the ASCE methodology has obtained minimal CTT of 0.983 but the Adaptive and fixed methodologies have achieved higher CTT of 2.971 and 3.198 respectively.

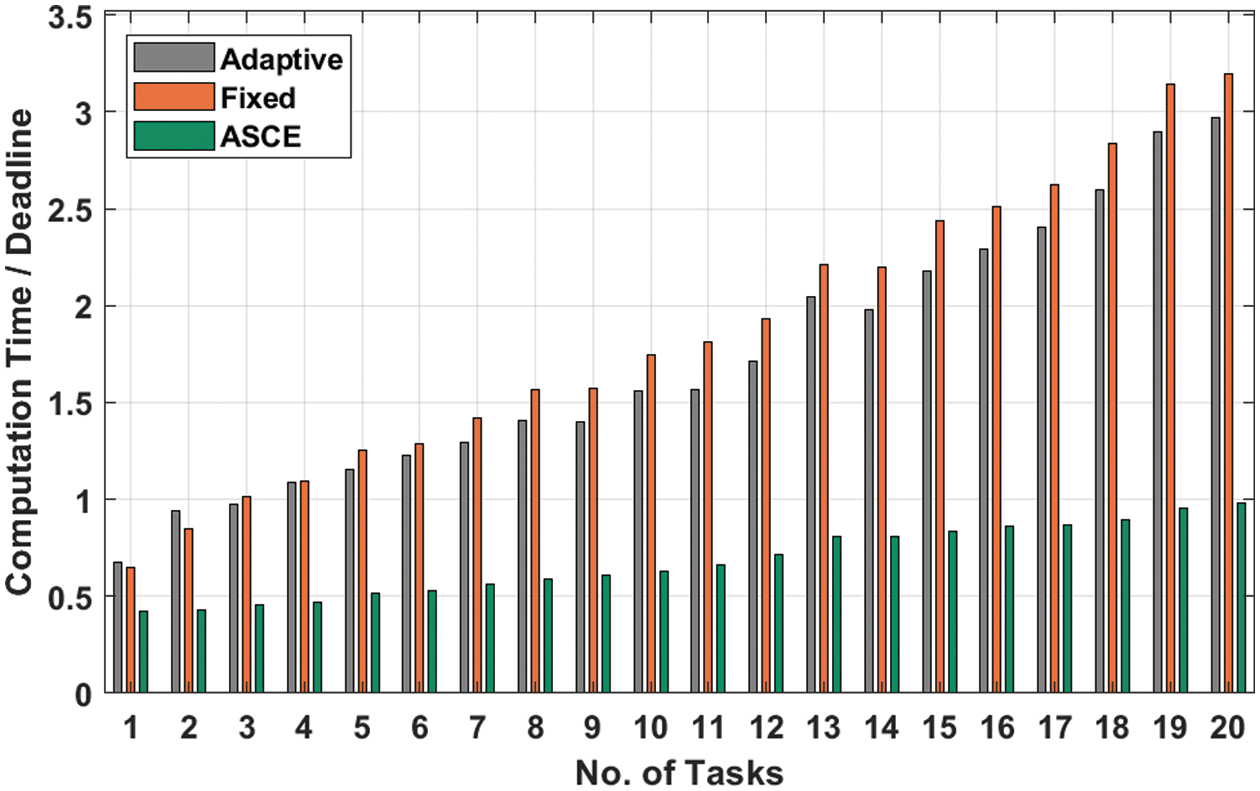
Figure 4: CTT analysis of ASCE technique with different count of tasks
A comprehensive results analysis of the MSSA-XBoost technique takes place under TS of 60% in Fig. 5. The results show that the RF technique has accomplished least performance with the
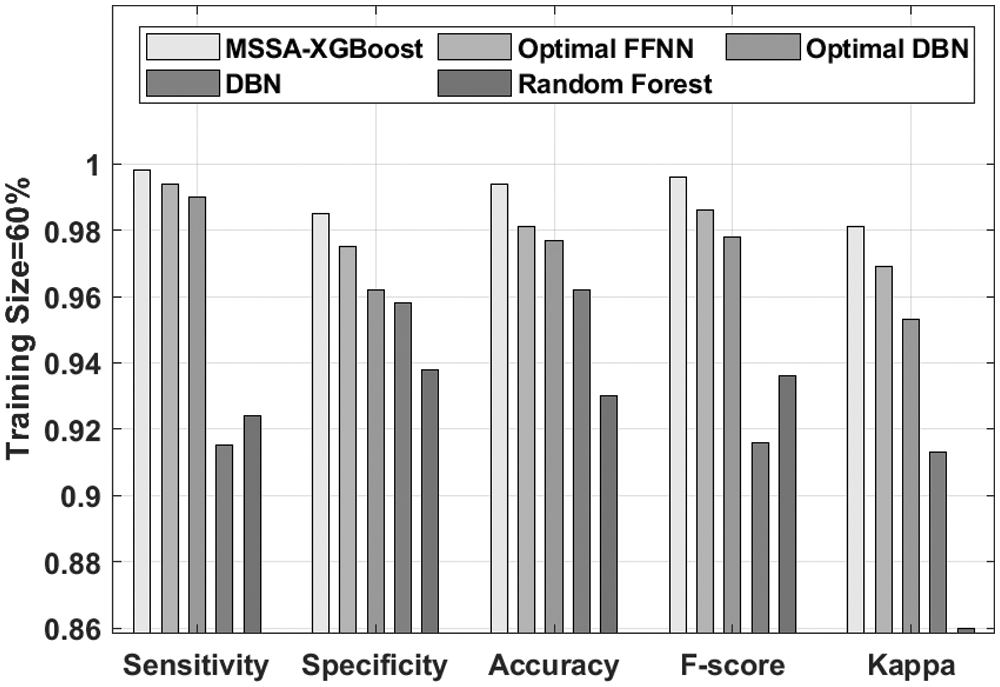
Figure 5: Comparative analysis of MSSA-XBoost technique under TS = 60%
A brief results analysis of the MSSA-XBoost approach take place under TS of 70% in Fig. 6. The outcomes demonstrated that the RF manner has accomplished worse performance with the

Figure 6: Comparative analysis of MSSA-XBoost technique under TS = 70%
A detailed results analysis of the MSSA-XBoost manner takes place under TS of 80% in Fig. 7. The outcomes exhibited that the RF system has accomplished worse performance with the
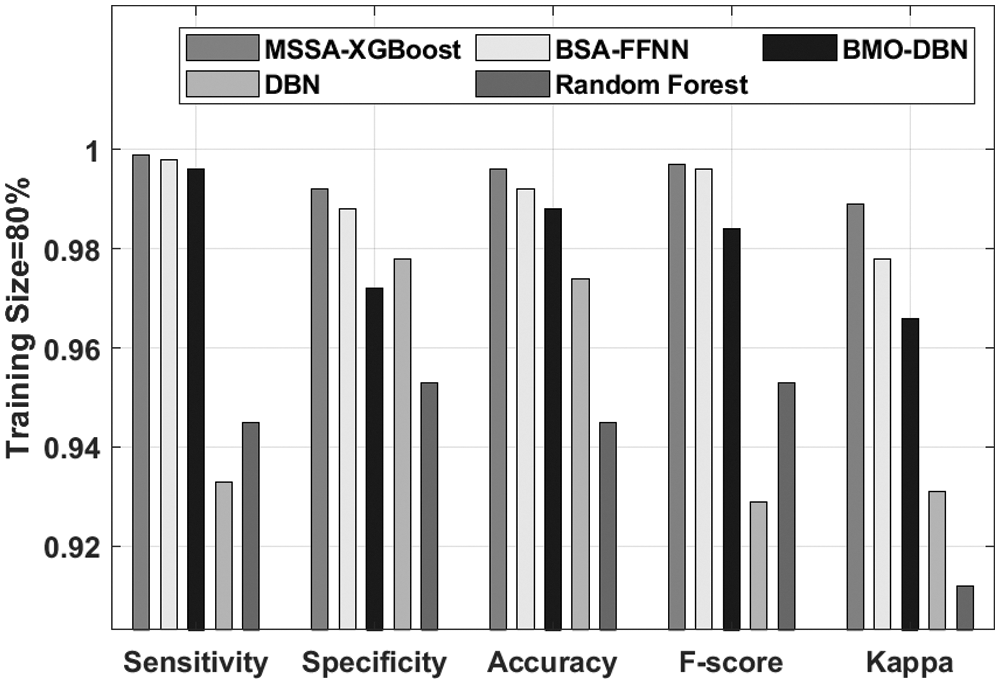
Figure 7: Comparative analysis of MSSA-XBoost technique under TS = 80%
The above mentioned results analysis demonstrated that the proposed manner is found to be an effective tool for data offloading and cyberattacks identification in MEC systems.
In this article, an effective AIMDO-SMEC technique has been developed to accomplish effective data offloading and security in MEC. The presented AIMDO-SMEC manner encompasses three major stages namely SNN based traffic flow prediction, ASCE based data offloading, and MSSA with XGBoost based cyberattack classification. The use of MSSA technique helps to properly adjust the parameters involved in the XGBoost technique and it results in improved detection outcomes. For examining the enhanced outcomes of the AIMDO-SMEC technique, a comprehensive experimental analysis is carried out and the results demonstrated the enhanced outcomes of the AIMDO-SMEC technique interms of different measures. The experimental results confirmed the supremacy of the AIMDO-SMEC technique over the recent approaches. In future, energy aware task scheduling and resource allocation models can be introduced for MEC systems.
Funding Statement: The authors extend their appreciation to the Deanship of Scientific Research at King Khalid University for funding this work under Grant Number (RGP 2/209/42). Princess Nourah bint Abdulrahman University Researchers Supporting Project Number (PNURSP2022R77), Princess Nourah bint Abdulrahman University, Riyadh, Saudi Arabia. The authors would like to acknowledge the support of Prince Sultan University for paying the Article Processing Charges (APC) of this publication.
Conflicts of Interest: The authors declare that they have no conflicts of interest to report regarding the present study.
1. J. B. Wang, H. Yang, M. Cheng, J. Y. Wang, M. Lin et al., “Joint optimization of offloading and resources allocation in secure mobile edge computing systems,” IEEE Transactions on Vehicular Technology, vol. 69, no. 8, pp. 8843–8854, 2020. [Google Scholar]
2. Y. Zhou, P. L. Yeoh, C. Pan, K. Wang, M. Elkashlan et al., “Offloading optimization for low-latency secure mobile edge computing systems,” IEEE Wireless Communications Letters, vol. 9, no. 4, pp. 480–484, 2020. [Google Scholar]
3. I. A. Elgendy, W. Zhang, Y. C. Tian and K. Li, “Resource allocation and computation offloading with data security for mobile edge computing,” Future Generation Computer Systems, vol. 100, pp. 531–541, 2019. [Google Scholar]
4. A. Rahman, E. Hassanain and M. S. Hossain, “Towards a secure mobile edge computing framework for hajj,” IEEE Access, vol. 5, pp. 11768–11781, 2017. [Google Scholar]
5. Y. Chen, Y. Zhang, S. Maharjan, M. Alam and T. Wu, “Deep learning for secure mobile edge computing in cyber-physical transportation systems,” IEEE Network, vol. 33, no. 4, pp. 36–41, 2019. [Google Scholar]
6. H. Yang, J. B. Wang, M. Cheng, C. Chang, J. Y. Wang et al., “Secure resource allocation in mobile edge computing systems,” in 2019 IEEE Global Communications Conf. (GLOBECOM), Waikoloa, HI, USA, pp. 1–6, 2019. [Google Scholar]
7. T. Bai, J. Wang, Y. Ren and L. Hanzo, “Energy-efficient computation offloading for secure uav-edge-computing systems,” IEEE Transactions on Vehicular Technology, vol. 68, no. 6, pp. 6074–6087, 2019. [Google Scholar]
8. X. Lai, L. Fan, X. Lei, Y. Deng, G. K. Karagiannidis et al., “Secure mobile edge computing networks in the presence of multiple eavesdroppers,” IEEE Transactions on Communications, vol. 70, pp. 1–1, 2021, https://doi.org/10.1109/TCOMM.2021.3119075. [Google Scholar]
9. S. Lai, R. Zhao, S. Tang, J. Xia, F. Zhou et al., “Intelligent secure mobile edge computing for beyond 5G wireless networks,” Physical Communication, vol. 45, pp. 101283, 2021. [Google Scholar]
10. A. M. Hilal, M. A. Alohali, F. N. A. Wesabi, N. Nemri, H. J. Alyamani et al., “Enhancing quality of experience in mobile edge computing using deep learning based data offloading and cyberattack detection technique,” Cluster Computing, 2021, https://doi.org/10.1007/s10586-021-03401-5. [Google Scholar]
11. I. A. Elgendy, A. Muthanna, M. Hammoudeh, H. Shaiba, D. Unal et al., “Advanced deep learning for resource allocation and security aware data offloading in industrial mobile edge computing,” Big Data, vol. 9, no. 4, pp. 265–278, 2021. [Google Scholar]
12. G. Mitsis, P. A. Apostolopoulos, E. E. Tsiropoulou and S. Papavassiliou, “Intelligent dynamic data offloading in a competitive mobile edge computing market,” Future Internet, vol. 11, no. 5, pp. 118, 2019. [Google Scholar]
13. M. S. Alkatheiri, “PCOS—Privacy-controlled offloading scheme for secure service data offloading in edge-internet of things-cloud scenario,” Arabian Journal for Science and Engineering, 2021. [Google Scholar]
14. Z. Xu, X. Liu, G. Jiang and B. Tang, “A Time-efficient data offloading method with privacy preservation for intelligent sensors in edge computing,” EURASIP Journal on Wireless Communications and Networking, vol. 2019, no. 1, pp. 236, 2019. [Google Scholar]
15. M. V. Arisoy, “Signature verification using siamese neural network one-shot learning,” International Journal of Engineering and Innovative Research, 2021, https://doi.org/10.47933/ijeir.972796. [Google Scholar]
16. T. Gopalakrishnan, D. Ruby, F. A. Turjman, D. Gupta, I. V. Pustokhina et al., “Deep learning enabled data offloading with cyber attack detection model in mobile edge computing systems,” IEEE Access, vol. 8, pp. 185938–185949, 2020. [Google Scholar]
17. T. Chen and C. Guestrin, “XGBoost: A scalable tree boosting system,” in Proc. of the 22nd ACM SIGKDD Int. Conf. on Knowledge Discovery and Data Mining, San Francisco California USA, pp. 785–794, 2016. [Google Scholar]
18. I. U. Khan, N. Aslam, T. Anwar, S. S. Aljameel, M. Ullah et al., “Remote diagnosis and triaging model for skin cancer using efficientnet and extreme gradient boosting,” Complexity, vol. 2021, pp. 1–13, 2021. [Google Scholar]
19. S. Mirjalili, A. H. Gandomi, S. Z. Mirjalili, S. Saremi, H. Faris et al., “Salp swarm algorithm: A bio-inspired optimizer for engineering design problems,” Advances in Engineering Software, vol. 114, pp. 163–191, 2017. [Google Scholar]
20. N. Panda and S. K. Majhi, “Oppositional salp swarm algorithm with mutation operator for global optimization and application in training higher order neural networks,” Multimedia Tools and Application, vol. 80, 2021, https://doi.org/10.1007/s11042-020-10304-x. [Google Scholar]
 | This work is licensed under a Creative Commons Attribution 4.0 International License, which permits unrestricted use, distribution, and reproduction in any medium, provided the original work is properly cited. |