DOI:10.32604/cmc.2022.025828

| Computers, Materials & Continua DOI:10.32604/cmc.2022.025828 |  |
| Article |
A Blockchain-Based Architecture for Enabling Cybersecurity in the Internet-of-Critical Infrastructures
1Information Technology Department, Faculty of Computing and Information Technology, King Abdulaziz University, Jeddah, 21589, Saudi Arabia
2Center of Artificial Intelligence for Precision Medicines, King Abdulaziz University, Jeddah, 21589, Saudi Arabia
3Mathematics Department, Faculty of Science, Al-Azhar University, Naser City, 11884, Cairo, Egypt
*Corresponding Author: Mahmoud Ragab. Email: mragab@kau.edu.sa
Received: 06 December 2021; Accepted: 12 January 2022
Abstract: Due to the drastic increase in the number of critical infrastructures like nuclear plants, industrial control systems (ICS), transportation, it becomes highly vulnerable to several attacks. They become the major targets of cyberattacks due to the increase in number of interconnections with other networks. Several research works have focused on the design of intrusion detection systems (IDS) using machine learning (ML) and deep learning (DL) models. At the same time, Blockchain (BC) technology can be applied to improve the security level. In order to resolve the security issues that exist in the critical infrastructures and ICS, this study designs a novel BC with deep learning empowered cyber-attack detection (BDLE-CAD) in critical infrastructures and ICS. The proposed BDLE-CAD technique aims to identify the existence of intrusions in the network. In addition, the presented enhanced chimp optimization based feature selection (ECOA-FS) technique is applied for the selection of optimal subset of features. Moreover, the optimal deep neural network (DNN) with search and rescue (SAR) optimizer is applied for the detection and classification of intrusions. Furthermore, a BC enabled integrity checking scheme (BEICS) has been presented to defend against the misrouting attacks. The experimental result analysis of the BDLE-CAD technique takes place and the results are inspected under varying aspects. The simulation analysis pointed out the supremacy of the BDLE-CAD technique over the recent state of art techniques with the
Keywords: BC; internet of critical infrastructure; ids; deep learning; security; deep neural network; machine learning
Critical infrastructure system has been utilized for underpinning the functions of an economy and society. Also, it ranges from conventionally-defined physical assets to a broader description of current assets in the fields of agriculture, gas, transportation, water supply, electricity, telecommunication, public health, security services, and so on [1]. Such transformation is mainly because of the extensive utilization of Internet of Things (IoT) and their considerable aid for critical infrastructure systems in industry 4.0 [2]. The IoT system has become essential part of critical infrastructure in industry 4.0, which creates smart services like smart grids and offers numerous benefits for efficiencies and cost savings. The international data corporation (IDC) have predicted that there would be an estimation of 41.6 billion interconnected IoT device, which generate 79.4 zettabytes (ZB) by 2025 [3].
The industrial control system (ICS) is the core of critical infrastructure system [4]. It is largely accountable for supervisory control and data collection (SCADA), which monitors the control flows and processes of data in industry. The possible application areas of critical infrastructure with IoT are shown in Fig. 1 [5]. The wider adaption of Internet connected IoT devices have offered different challenges to critical infrastructure. Initially, ICS was mainly developed for a closed infrastructure and proprietary without taking care of security problems into account, since conventional critical infrastructure is kind of isolated and is invulnerable to cyber-attacks. With this infrastructure being interconnected to the Internet via IoT system, a wide-ranging of cyberattacks, including malware, Man-in-the-middle attack, distributed denial-of service (DDoS), Brute force, breach, and phishing attacks are threatening the process of ICS [6,7]. The compromised ICS by cyber attackers might generate possible risk for the loss of information [8]. Next, scalability is another challenge where ICS wasn't initially developed to resolve. Assuming the dramatic growth in the volume of data and the number of IoT devices they are analyzing and collecting, the centralized method for data analysis and collection has become a bottleneck of ICS. A decentralized method is crucially needed to satisfy the evolving needs of ICS.
Figure 1: Application areas of critical infrastructures with IoT
Blockchain (BC) and Artificial intelligence (AI) have their own benefits, but, all of them have relative drawbacks. BC has problems relating to scalability, security, energy consumption, efficiency, and privacy, whereas AI systems face problems like effectiveness and interpretability. As two distinct directions of research, they could be associated with one another and have the benefits of natural integration. Both techniques have shared requirements for data trust, analysis, and security, and they could empower one another [9]. For example, AI technique based on three most important components: computing power, data, and algorithms, and the BC could break the island of data and realize the flow of data resources, algorithms, and computing power, according to its specific features, involving immutability, anonymization, and decentralization. Additionally, BC could ensure the audit traceability and credibility of AI and the credibility of the original data. Furthermore, BC could record the decision-making of AI that assists in analyzing and understanding the behaviour of AI and eventually promote the decision-making of AI, which makes it more explainable, trustworthy, and transparent. The AI technique could improve the BC construction for making it more efficient, secure, and energy-saving [10].
Gumaei et al. [11] presented an architecture which integrates a BC with a deep recurrent neural network (DRNN) and edge computing for 5G-enabled assisted mode detection and drone identification. In the presented approach, raw RF signals of dissimilar drones under various flight modes are collected and sensed remotely on a cloud framework for training a DRNN method and allocate the training models on edge devices to detect their flight modes and drones. BC is utilized in this architecture for securing data transmission and integrity. Alkadi et al. [12] presented a DBF to provide security-based privacy-based BC and distributed IDS with smart contracts in IoT networks. The IDS is applied by a BiLSTM-DL method for handling sequential network data and is measured by the data sets. The smart contract and privacy-based BC methodologies are designed by utilizing the Ethereum library to offer security to the distributed IDS engine.
Singh et al. [13] introduced a DL-based IoT-based framework for a secured smart city in which BC provides a distributed platform at the transmission stage of software defined networks (SDN) and cyber-physical systems (CPS) established the protocol for forwarding information. A DL based cloud is employed at the application layer for resolving transmission scalability, centralization, and latency. Zhang et al. [14] presented an edge intelligence and BC enabled industrial IoT architecture that attains secure and flexible edge service management. Next, developed a credit-differentiated edge transaction approval method and present a cross-domain sharing inspired edge resource scheduling system.
This study designs a novel BC with deep learning empowered cyber-attack detection (BDLE-CAD) in critical infrastructures and ICS. The proposed BDLE-CAD technique aims to identify the existence of intrusions in the network. In addition, the presented enhanced chimp optimization based feature selection (ECOA-FS) technique is applied for the selection of optimal subset of features. Moreover, the optimal deep neural network (DNN) with search and rescue (SAR) optimizer is applied for the detection and classification of intrusions. Furthermore, a BC enabled integrity checking scheme (BEICS) has been presented to defend the misrouting attacks. The experimental result analysis of the BDLE-CAD technique takes place and the results are inspected under varying aspects.
In this study, a new BDLE-CAD technique has been developed to identify the existence of intrusions in critical infrastructures. The proposed BDLE-CAD technique encompasses ECOA-FS technique for the selection of optimal subset of features. Moreover, the DNN with SAR optimizer is can be used as a classifier and the BEICS has been presented to defend over the misrouting attacks. The experimental result analysis of the BDLE-CAD technique takes place and the results are inspected under varying aspects.
2.1 ECOA Based Feature Selection
Primarily, the ECOA-FS technique is executed to choose the optimal subset of features. The chimp optimization algorithm (COA) is a mathematical method that is dependent upon intelligent diversity [15]. Drive, chase, block, and attack are capable of 4 distinct kinds of chimps that are realized by attacker, obstacle, chaser, and driver. The 4 hunting stages are finalized in 2 phases. In primary stage is the exploration step, and the second step is the exploitation phase. The exploration phase contains driving, blocking, and chasing the prey. Since the exploitation step, it has attacked the prey. Where the drive and chase are demonstrated as in Eqs. (1) and (2).
where
where f implies the non-linearly declined in 2.5 to
In ECOA, the extremely disruptive polynomial mutation is increased version of polynomial mutation technique [16]. It could resolve the limitation that polynomial mutation technique is fall as to local optimal once the variable is nearby boundary. In Eqs. (9)–(12) illustrate the procedure of HDPM modifies the
where
In contrast to the classical ECOA, in which the update of solutions takes place in the search area in the direction of continuous value location. However, in the BECOA, the searching area can be defined by n dimension Boolean lattice. In addition, the solutions get updated using the corner of a hypercube. Moreover, for selecting the features, 1 represents the selection of features, otherwise 0. In addition, the BECOA derived a fitness function in determining the solutions for maintaining a tradeoff between a pair of objectives, as given in Eq. (13):
2.2 Optimal DNN Based Intrusion Detection and Classification
At this stage, the chosen features are passed into the DNN model for intrusion classification. The DNN is an ANN that consists of input, hidden, and output layers. The hidden layer applies a group of non-linear functions and it can be demonstrated as follows [17]:
where x refers the input of all nodes, W and bias signifies the weight as well as bias vectors correspondingly and
The 2 steps of human search are demonstrated as follows. i) Social step: The search way has provided by
At this point
ii) Individual step: According to the present place humans identify its novel place and novel place of
Every solution is placed from the solution spaces, once the novel place is outer the solution space then it can be enhanced utilizing the formula
where
where
Once the USN value is superior to the maximal unsuccessful searching number, the human becomes an arbitrary place from the searching space utilized in Eq. (21), and the value of
where
The BC [19] is a major component of the integrity verification system. The primary concept is to offer a solution in which that every flow produced from the controller is saved in a verifiable and immutable dataset. The BC includes a series of blocks interconnected to one another via hash values. At the BC network, the users contain a pair of keys namely private key for signing the BC transaction and public key for representing the irreplaceable address. The client signed a transaction by the use of private key and transmit it to the other ones in the network for verification. Once the broadcasting block gets verified, it is added to the BC. If it is saved, the data in the provided blocks could not be modified with no changes of all succeeding blocks. Besides, the data is present in many hosts concurrently, therefore, the modifications can be discarded by the peer hosts. Here, a private BC has been presented in contrast to a public BC. The private BC decides who can get participated in the network and represented actions as well as permissions allotted identifiable applicants. Therefore, it limits the need for consensus mechanisms like Proof of Work. Fig. 2 shows the structure of BC.
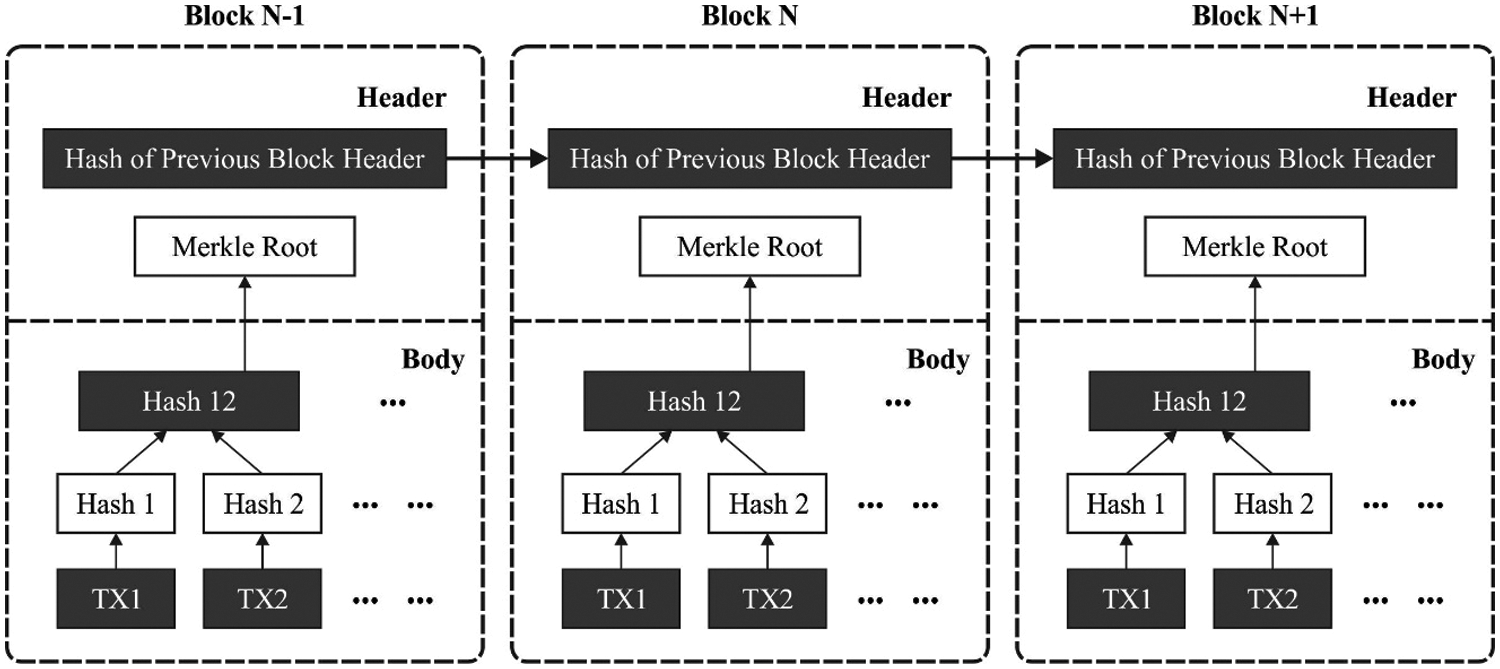
Figure 2: Structure of BC
In this section, the performance validation of the BDLE-CDE technique takes place using benchmark dataset [20], which comprises 1000's different classes of events. The dataset contains binary (Natural and Attack) and multiclass (No event, Natural, and Attack) labels. Tab. 1 provides a detailed result analysis of the BDLE-CDE technique on the binary class dataset.
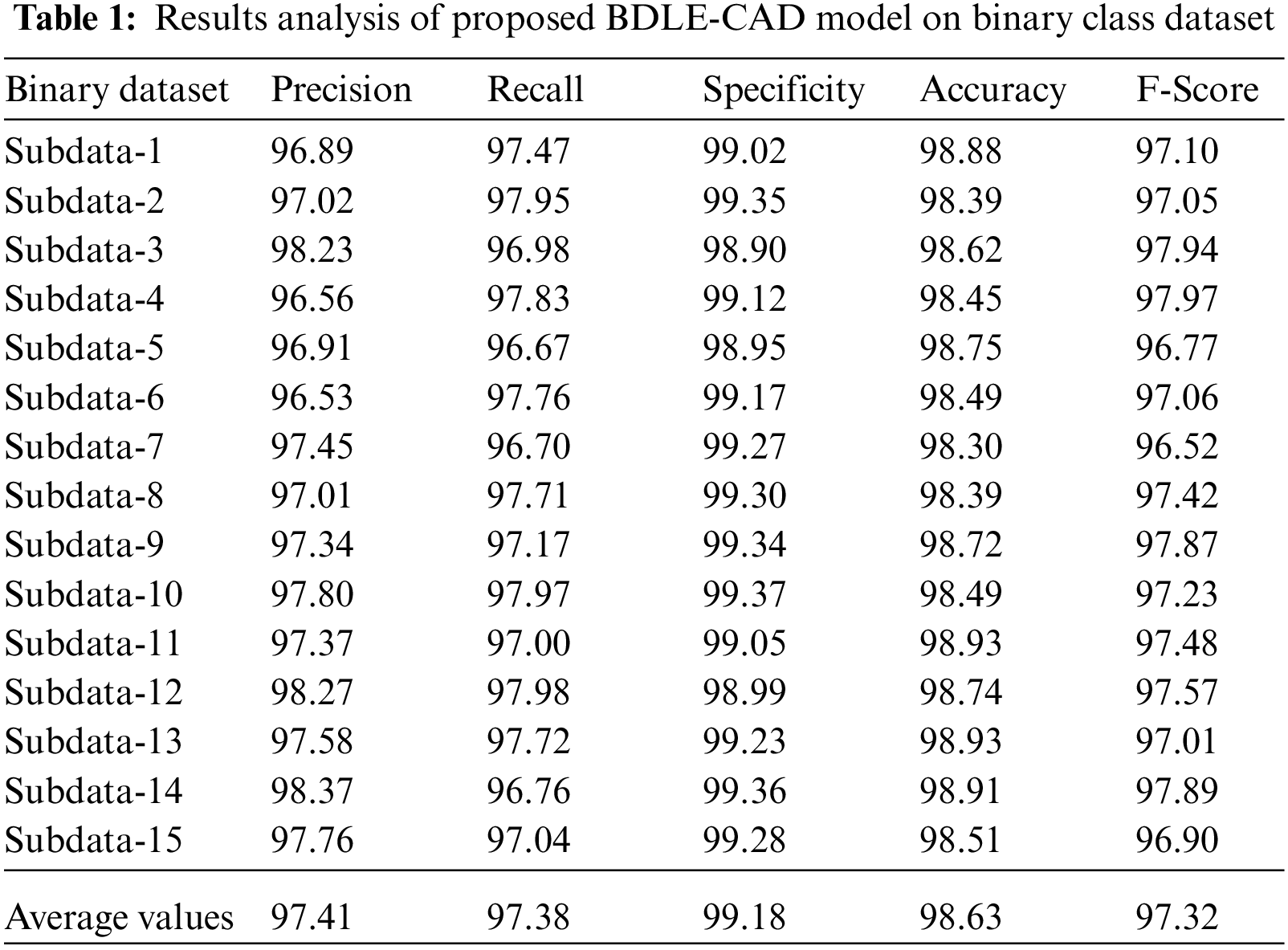
Fig. 3 offers a brief
Figure 3:
Fig. 4 exhibits a detailed
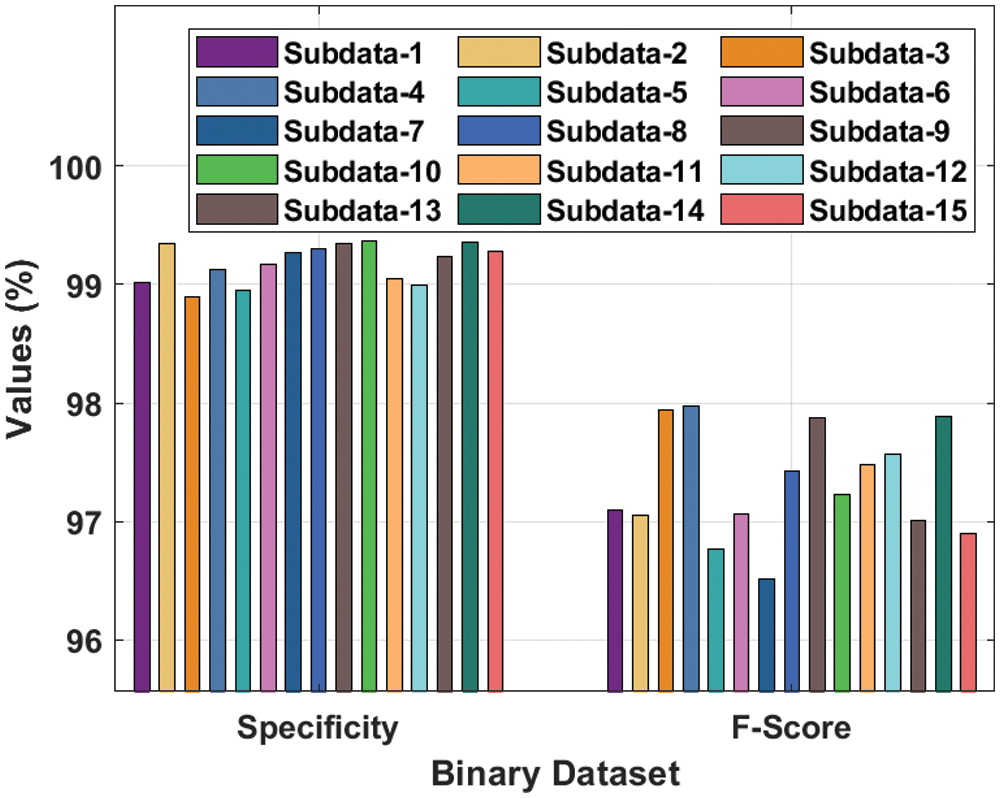
Figure 4:
Fig. 5 portrays the
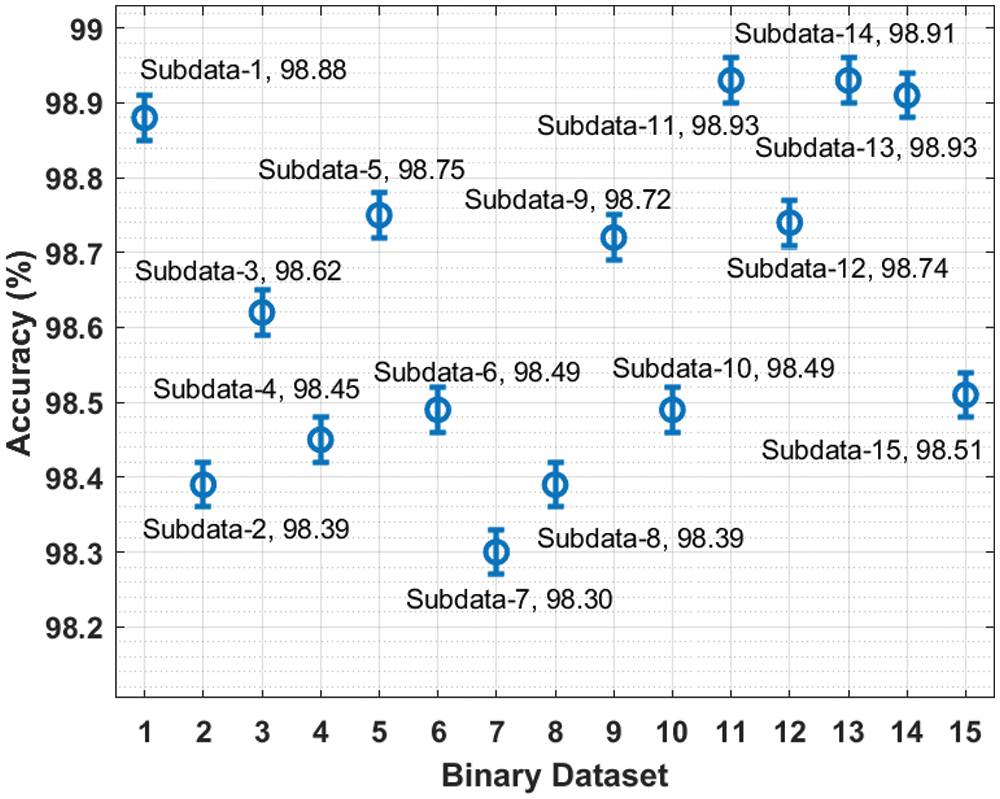
Figure 5:
Tab. 2 offers a comprehensive comparison study of the BDLE-CDE technique on the multi class dataset.
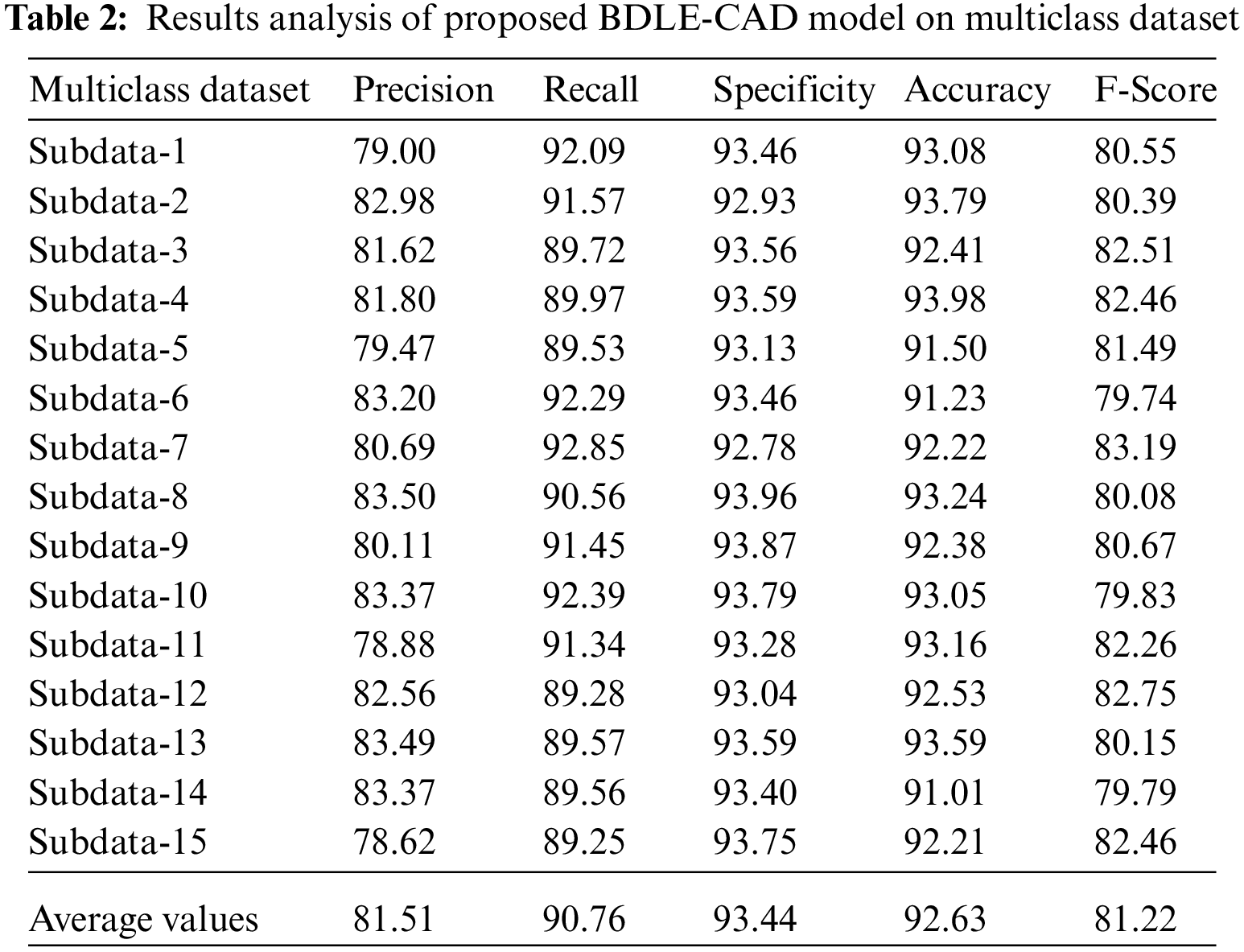
Fig. 6 showcases a brief
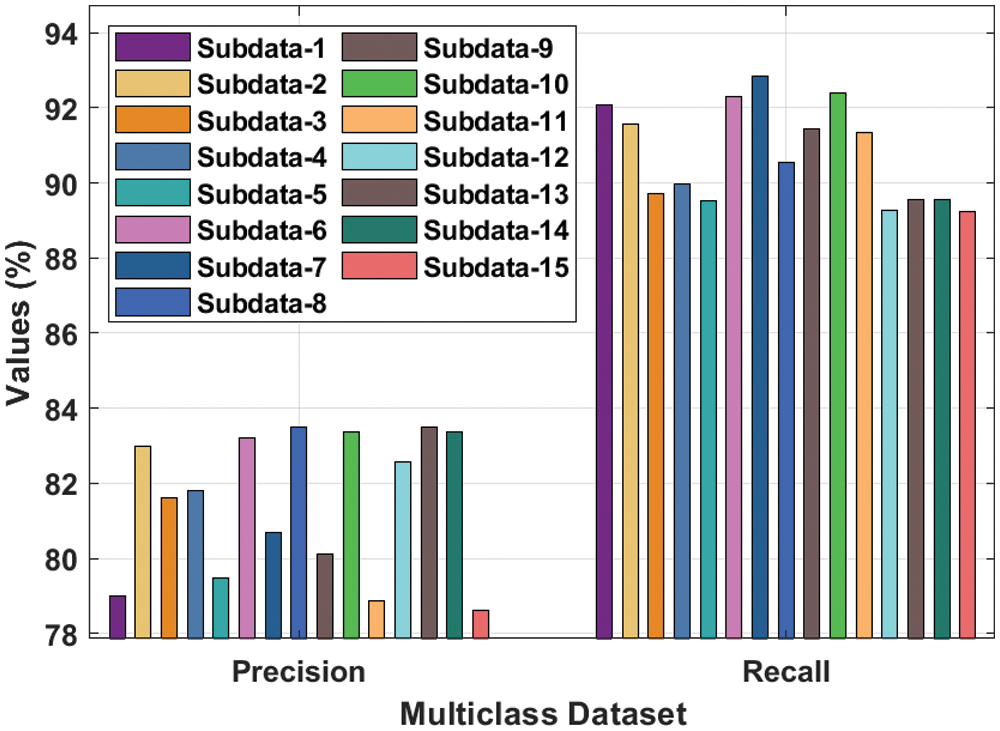
Figure 6:
Fig. 7 reveals a detailed
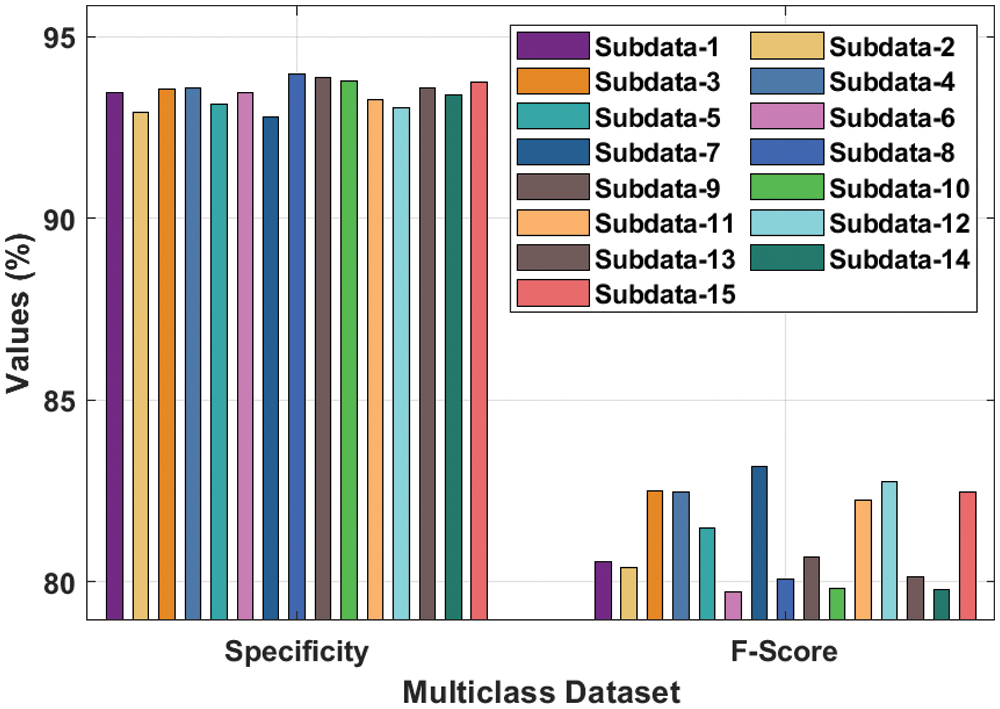
Figure 7:
Fig. 8 shows the
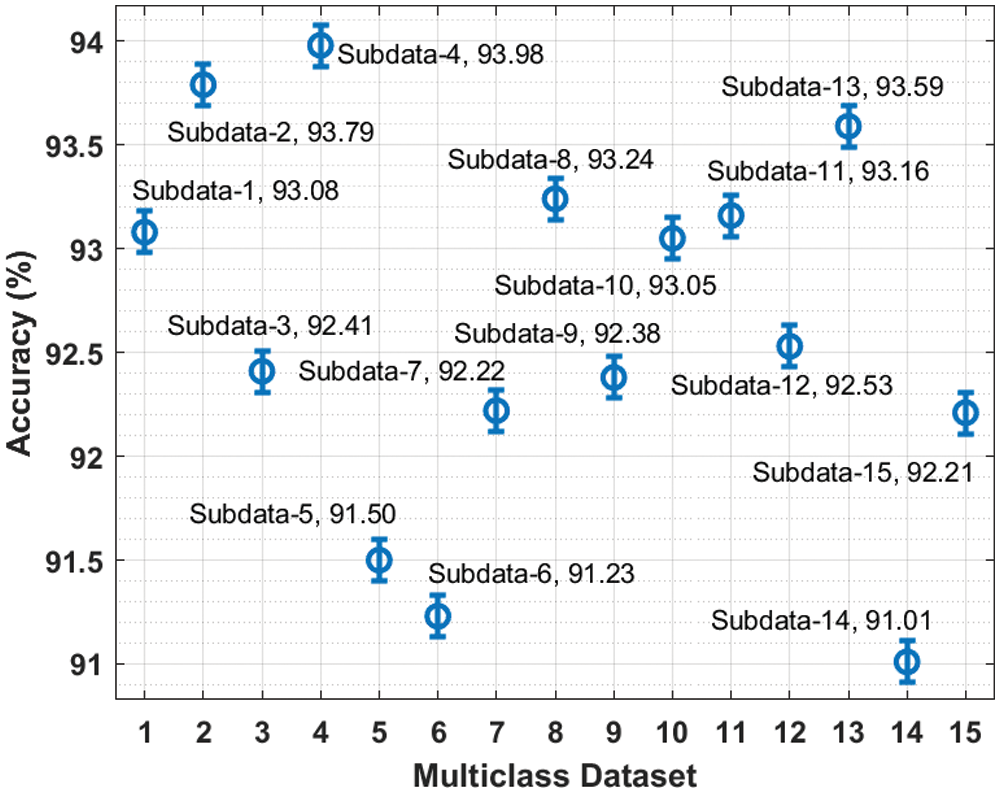
Figure 8:
Tab. 3 offers a detailed comparative study of the BDLE-CDE technique with recent methods [21]. A comparative classification result analysis of the BDLE-CDE technique on the binary class dataset is depicted in Fig. 9. The results exposed that the Nearest Neighbor (NN), random forest (RF), and SVM models have obtained lower
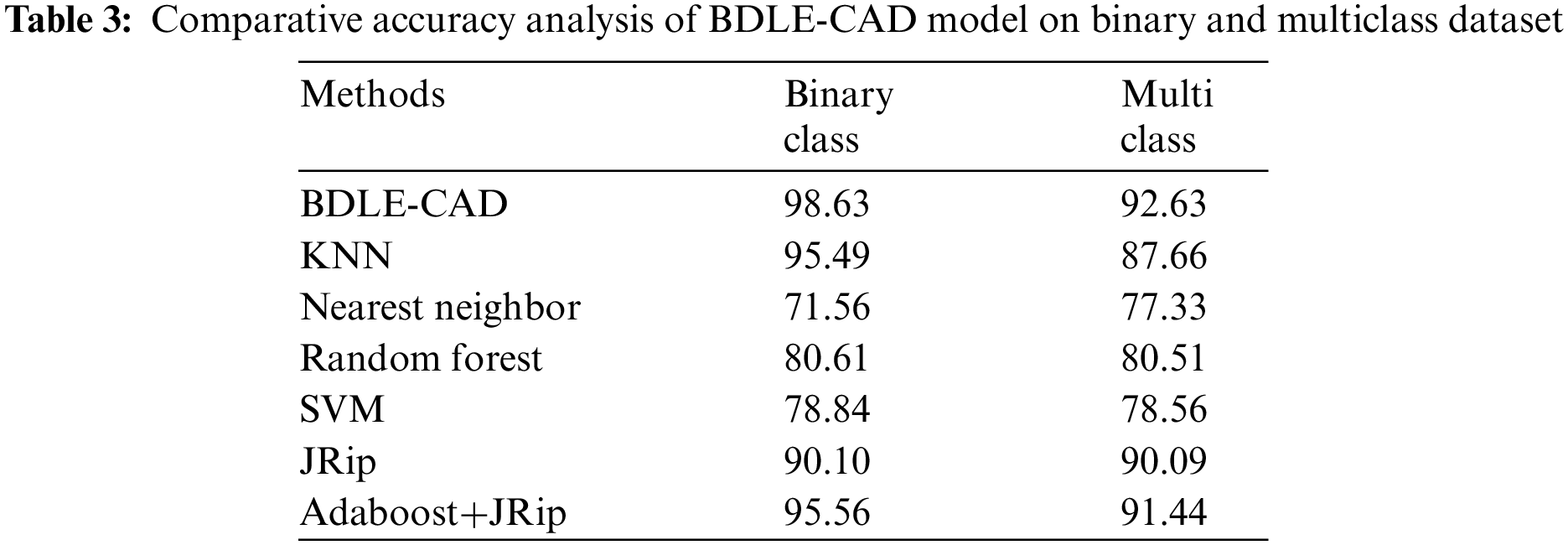
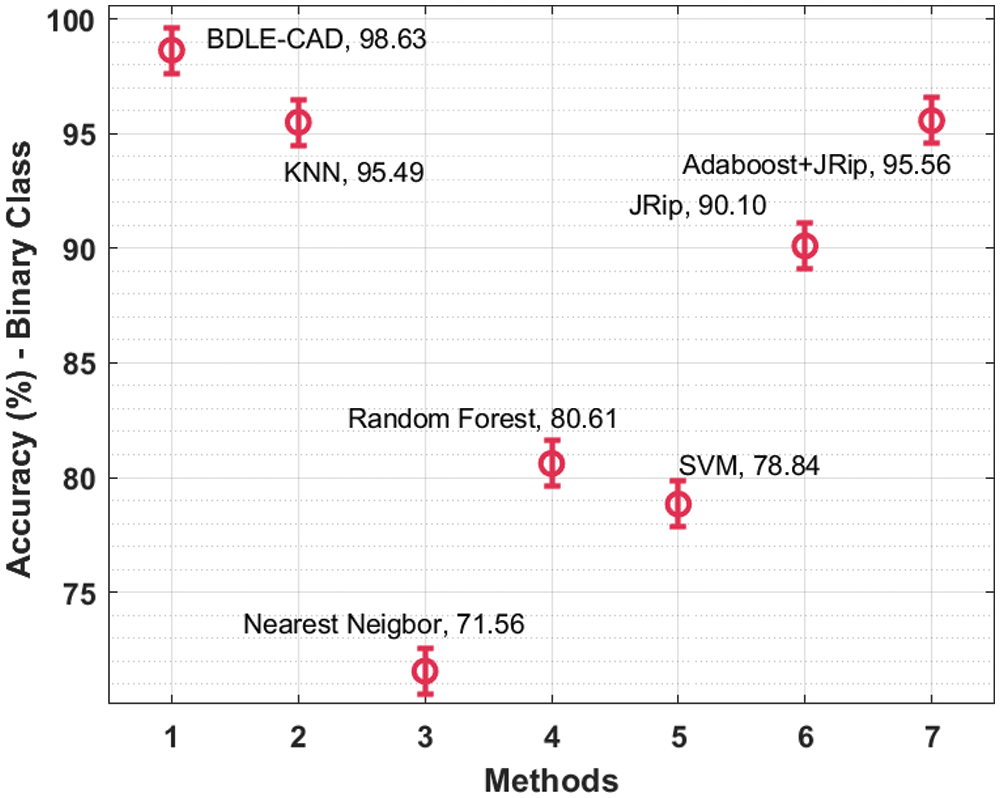
Figure 9: Comparative
Detailed multiclass performance analysis of the BDLE-CDE technique on the multi class dataset is offered in Fig. 10. The experimental values illustrated that the Nearest Neighbor (NN), random forest (RF), and SVM models have gained reduced
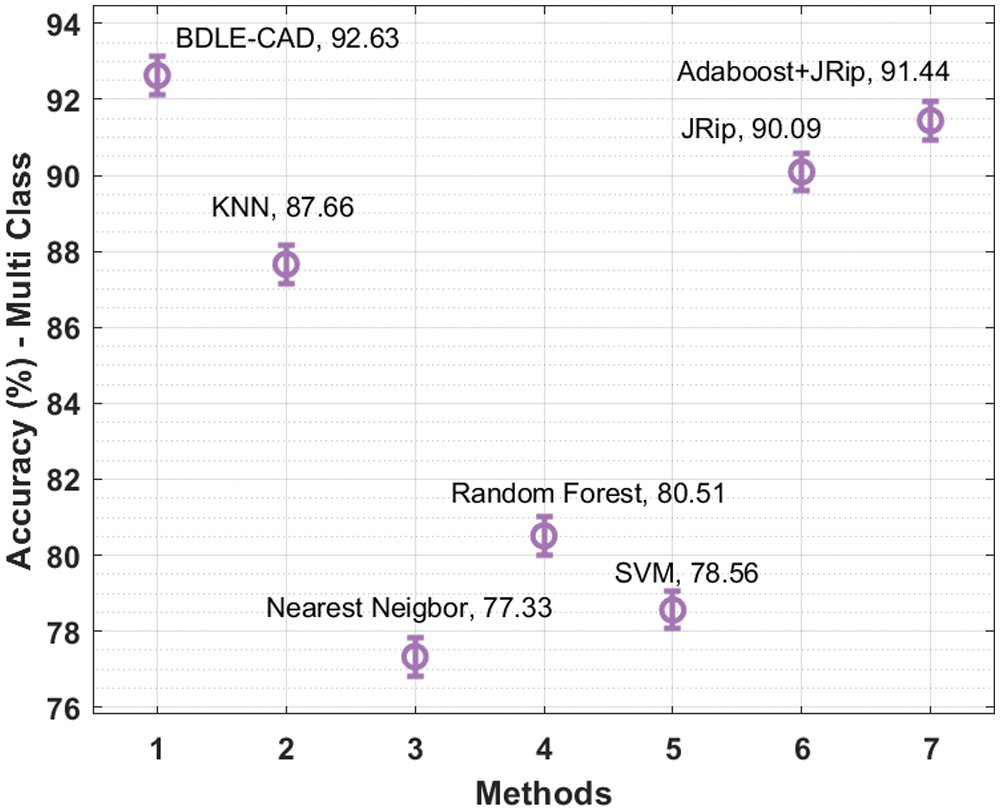
Figure 10: Comparative
In this study, a new BDLE-CAD technique has been developed to identify the existence of intrusions in critical infrastructures. The proposed BDLE-CAD technique encompasses ECOA-FS technique for the selection of optimal subset of features. Moreover, the DNN with SAR optimizer is can be used as a classifier and the BEICS has been presented to defend over the misrouting attacks. The experimental result analysis of the BDLE-CAD technique takes place and the results are inspected under varying aspects. The simulation analysis pointed out the supremacy of the BDLE-CAD technique over the recent state of art techniques with the accomplished superior
Acknowledgement: The authors extend their appreciation to the Deputyship for Research & Innovation, Ministry of Education in Saudi Arabia for funding this research work through the Project Number (IFPIP-145-351-1442) and King Abdulaziz University, DSR, Jeddah, Saudi Arabia.
Funding Statement: This project was supported financially by Institution Fund projects under Grant No. (IFPIP-145-351-1442).
Conflicts of Interest: The authors declare that they have no conflicts of interest to report regarding the present study.
1. S. Otoum, I. A. Ridhawi and H. Mouftah, “Securing critical IoT infrastructures with blockchain-supported federated learning,” IEEE Internet Things Journal, pp. 1–1, 2021, https://doi.org/10.1109/JIOT.2021.3088056. [Google Scholar]
2. Y. Qi, L. Tian, Y. Zhou and J. Yuan, “Mobile edge computing-assisted admission control in vehicular networks: The convergence of communication and computation,” IEEE Vehicular Technology Magazine, vol. 14, no. 1, pp. 37–44, 2019. [Google Scholar]
3. D. Feng, C. She, K. Ying, L. Lai, Z. Hou et al., “Toward ultrareliable low-latency communications: Typical scenarios, possible solutions, and open issues,” IEEE Vehicular Technology Magazine, vol. 14, no. 2, pp. 94–102, 2019. [Google Scholar]
4. I. A. Ridhawi, S. Otoum, M. Aloqaily, Y. Jararweh and T. Baker, “Providing secure and reliable communication for next generation networks in smart cities,” Sustainable Cities and Society, vol. 56, pp. 102080, 2020. [Google Scholar]
5. Y. Wu, H. Dai and H. Wang, “Convergence of blockchain and edge computing for secure and scalable iiot critical infrastructures in industry 4.0,” IEEE Internet of Things Journal, vol. 8, no. 4, pp. 2300–2317, 2021. [Google Scholar]
6. K. Yu, L. Tan, X. Shang, J. Huang, G. Srivastava et al., “Efficient and privacy-preserving medical research support platform against covid-19: A blockchain-based approach,” IEEE Consumer Electronics Magazine, vol. 10, no. 2, pp. 111–120, 2021. [Google Scholar]
7. M. Chen, Y. Jiang, N. Guizani, J. Zhou, G. Tao et al., “Living with I-fabric: Smart living powered by intelligent fabric and deep analytics,” IEEE Network, vol. 34, no. 5, pp. 156–163, 2020. [Google Scholar]
8. K. Yu, L. Tan, M. Aloqaily, H. Yang and Y. Jararweh, “Blockchain-enhanced data sharing with traceable and direct revocation in IIoT,” IEEE Transactions on Industrial Informatics, vol. 17, no. 11, pp. 7669–7678, 2021. [Google Scholar]
9. J. M. Mcginthy and A. J. Michaels, “Secure industrial internet of things critical infrastructure node design,” IEEE Internet Things Journal, vol. 6, no. 5, pp. 8021–8037, 2019. [Google Scholar]
10. I. Stellios, P. Kotzanikolaou, M. Psarakis, C. Alcaraz and J. Lopez, “A survey of IoT-enabled cyberattacks: Assessing attack paths to critical infrastructures and services,” IEEE Communications Surveys and Tutorials, vol. 20, no. 4, pp. 3453–3495, 2018. [Google Scholar]
11. A. Gumaei, M. A. Rakhami, M. M. Hassan, P. Pace, G. Alai et al., “Deep learning and blockchain with edge computing for 5g-enabled drone identification and flight mode detection,” IEEE Network, vol. 35, no. 1, pp. 94–100, 2021. [Google Scholar]
12. O. Alkadi, N. Moustafa, B. Turnbull and K. K. R. Choo, “A deep blockchain framework-enabled collaborative intrusion detection for protecting iot and cloud networks,” IEEE Internet Things Journal, vol. 8, no. 12, pp. 9463–9472, 2021. [Google Scholar]
13. S. K. Singh, Y. S. Jeong and J. H. Park, “A deep learning-based IoT-oriented infrastructure for secure smart City,” Sustainable Cities and Society, vol. 60, pp. 102252, 2020. [Google Scholar]
14. K. Zhang, Y. Zhu, S. Maharjan and Y. Zhang, “Edge intelligence and blockchain empowered 5g beyond for the industrial internet of things,” IEEE Network, vol. 33, no. 5, pp. 12–19, 2019. [Google Scholar]
15. M. Khishe, M. Nezhadshahbodaghi, M. R. Mosavi and D. Martin, “A weighted chimp optimization algorithm,” IEEE Access, pp. 1–1, 2021, http://dx.doi.org/10.1109/ACCESS.2021.3130933. [Google Scholar]
16. D. Wu, W. Zhang, H. Jia and X. Leng, “Simultaneous feature selection and support vector machine optimization using an enhanced chimp optimization algorithm,” Algorithms, vol. 14, no. 10, pp. 282, 2021. [Google Scholar]
17. C. Muppala and V. Guruviah, “Detection of leaf folder and yellow stemborer moths in the paddy field using deep neural network with search and rescue optimization,” Information Processing in Agriculture, vol. 8, no. 2, pp. 350–358, 2021. [Google Scholar]
18. A. Shabani, B. Asgarian, S. A. Gharebaghi, M. A. Salido and A. Giret, “A new optimization algorithm based on search and rescue operations,” Mathematical Problems in Engineering, vol. 2019, pp. 1–23, 2019. [Google Scholar]
19. A. Derhab, M. Guerroumi, A. Gumaei, L. Maglaras, M. A. Ferrag et al., “Blockchain and random subspace learning-based ids for sdn-enabled industrial IoT security,” Sensors, vol. 19, no. 14, pp. 3119, 2019. [Google Scholar]
20. S. Abe, Y. Uchida, M. Hori, Y. Hiraoka and S. Horata, “Cyber threat information sharing system for industrial control system (ICS),” in 2018 57th Annual Conf. of the Society of Instrument and Control Engineers of Japan (SICE), Nara, pp. 374–379, 2018. [Google Scholar]
21. R. C. B. Hink, J. M. Beaver, M. A. Buckner, T. Morris, U. Adhikari et al., “Machine learning for power system disturbance and cyber-attack discrimination,” in 2014 7th Int. Symp. on Resilient Control Systems (ISRCS), Denver, CO, USA, pp. 1–8, 2014. [Google Scholar]
 | This work is licensed under a Creative Commons Attribution 4.0 International License, which permits unrestricted use, distribution, and reproduction in any medium, provided the original work is properly cited. |