DOI:10.32604/cmc.2022.024932

| Computers, Materials & Continua DOI:10.32604/cmc.2022.024932 |  |
| Article |
A Drones Optimal Path Planning Based on Swarm Intelligence Algorithms
1Information Technology Department, Faculty of Computing and Information Technology, King Abdulaziz University, Jeddah 21589, Saudi Arabia
2Center of Artificial Intelligence for Precision Medicines, King Abdulaziz University, Jeddah 21589, Saudi Arabia
3Information Systems Department, Faculty of Computing and Information Technology, King Abdulaziz University, Jeddah 21589, Saudi Arabia
4Department of Mathematics, Faculty of Science, Al-Azhar University, Naser City 11884, Cairo, Egypt
5Department of Mathematics, Faculty of Science, Taif University, Taif, Saudi Arabia
6Department of Mathematics, Faculty of Science, Sohag University, Sohag, Egypt
7Department of Computer Engineering, College of Computers and Information Technology, Taif University, Taif, Saudi Arabia
*Corresponding Author: Mahmoud Ragab. Email: mragab@kau.edu.sa
Received: 05 November 2021; Accepted: 21 December 2021
Abstract: The smart city comprises various interlinked elements which communicate data and offers urban life to citizen. Unmanned Aerial Vehicles (UAV) or drones were commonly employed in different application areas like agriculture, logistics, and surveillance. For improving the drone flying safety and quality of services, a significant solution is for designing the Internet of Drones (IoD) where the drones are utilized to gather data and people communicate to the drones of a specific flying region using the mobile devices is for constructing the Internet-of-Drones, where the drones were utilized for collecting the data, and communicate with others. In addition, the SIRSS-CIoD technique derives a tuna swarm algorithm-based clustering (TSA-C) technique to choose cluster heads (CHs) and organize clusters in IoV networks. Besides, the SIRSS-CIoD technique involves the design of a biogeography-based optimization (BBO) technique to an optimum route selection (RS) process. The design of clustering and routing techniques for IoD networks in smart cities shows the novelty of the study. A wide range of experimental analyses is carried out and the comparative study highlighted the improved performance of the SIRSS-CIoD technique over the other approaches.
Keywords: Drones; smart city; swarm intelligence; route selection; internet of drones; networking
Recently, Smart cities have attracted growing interest in the field of institutions, transportation, home energy management, also providing facilities for the citizens, safety and security, and businesses in healthcare management. The smart city technology presented by National Institute of Standards and Technology (NIST) consists of 6 major elements that is smart people, smart mobility, smart environment, smart economy, smart governance, and smart living, with cloud computing as the environment for storing information, and the Internet-of-Things (IoT) as an enabling technique [1]. Furthermore, it is predicted that in 2020, the amount of smaller-scale drones attained 2.7 million, smartphone undertakes an important role in extending the use of smart city applications, since it allows the citizen to send and receive information as well as logging on to the application [2,3]. Unmanned Aerial vehicles (UAV), is also called drones, are considered smart city components which provide surveillance and smart mobility for the citizen. UAV includes various kinds of sensor nodes that assist many applications using cooperative form among themselves [4].
Especially, a drone has smart devices, like time-of-flight (ToF) sensor, magnetic-field change sensor, light-pulse distance sensor, thermal and chemical sensor orientation sensor, radio range, and detection sensor. It is remotely controlled and often moves autonomously with no human interference. Now, drones were utilized in a large number of civilian applications, namely package delivery, air traffic control, remote sensing, monitoring, firefighting, and an inspection of infrastructure. This drone would provide various services and occupy lower airspace. The concept of “Internet-of-Drones (IoD)” relates to technique where multiple drones, each containing flying zones, procedure an aerial mesh network for gathering data and communicate via sensors, i.e., subsequently transmitted to a control server. The sample structure of IoD in the smart city is shown in Fig. 1. External mobile users could access and monitor any drones via their mobile phones in a certain flying zone over a control server providing that she/he is allowed to access the drone. The communication could take place in-between the trusted control server, the user and the drone, and amongst the user or drones [5].

Figure 1: Structure of IoD in a smart city environment
Drones have limited computational power scarce and battery resources that could affect the entire transmission efficacy in IoD. To effectively employ this scarce resource, a transmission technique has been developed that yields higher throughput, guarantees lower computational complexity, and lower routing overhead could be a tedious process. The routing mechanism for an effective transmission is needed for the data transmission amongst drones. The ever-growing mobility and topology of the drones in IoD create the transmission amongst drones a challenging process [6]. The solution to this problem is hierarchal routing which is also called clustering. In clustering, the network forms into subgroups, a cluster includes cluster member (CM) and cluster head (CH). A CH is selected between each member in the cluster and it controls the performances of the cluster by handling it effectively and efficiently [7,8]. Therefore, the selection of CH is the most significant task of clustering and all the CMs could be a candidate for the selection of CH. Rather than a single-hop transmission network, a multihop cluster-based network leads to scalability and better performance.
In clustering algorithms, CH election and cluster formation are essential tasks to effectively preserve cluster topology. Successive modifications in the relative location of CM change the entire cluster topology. Hence, it is necessary to design an effective clustering method for the effective use of energy resources and better scalability of rapidly developing topology [9]. The swarm intelligence (SI) based models are utilized to a near-optimum solution. In an Adhoc technique, there is no centralized control that leads to growing complexities in management and configuration [10]. Therefore, it is necessary to develop this network architecture which contains self-organizing abilities like self-optimization, self-configuring, self-healing, and adaptive to environments.
This study designs a novel Swarm Intelligence-based Route Selection Strategy for Clustered Internet of Drones Enabled Smart City Applications, called SIRSS-CIoD. In addition, the SIRSS-CIoD technique derives a tuna swarm algorithm-based clustering (TSA-C) technique to choose cluster heads (CHs) and organize clusters in IoV networks. Besides, the SIRSS-CIoD technique involves the design of a biogeography-based optimization (BBO) technique to a better route selection (RS) process. The design of clustering and routing techniques for IoD networks in smart cities shows the novelty of the study. A wide range of experimental analyses is carried out and the comparative study highlighted the improved performance of the SIRSS-CIoD technique over the other approaches.
The rest of the paper is organized as follows. Section 2 offers the related works, Section 3 provides the proposed method, Section 4 discusses the results, and Section 5 concludes the work.
In [11], the function of UAVs in the Adhoc network and their cooperation with vehicles in VANET is examined for assisting the method of detection and routing of malicious vehicles. The routing protocol called VRU is presented which consists of 2 distinctive methods of routing of data: (1) routing packets of information among UAVs with a protocol called VRU_u, and (2) delivering a packet of information among vehicles through UAVs with a protocol termed VRU_vu. In [12], a tight plane-based architecture is presented that uses the current public transportation like city trains, public buses, and their paths to offer time-sensitive monitoring. Then, proposed a loose hierarchical-based architecture. To assist seamless monitoring over wide-ranging, they utilize 2 kinds of UAVs, that enable replenishment amongst heterogeneous UAVs at distinct layers via airborne docking.
In [13], a UAV heterogeneous fleet routing problem is addressed, handling vehicles constrained autonomy with the consideration of respecting operational requirements and multiple charging stations. A green routing problem is developed to overcome problems that are present because of constrained vehicle driving range. As a result of the massive number of emerging drones in society, UAV efficacy and use need to be enhanced. In [14], a lower complex architecture is designed for determining the time plans shortest and trajectories for all the members of the fleet when considering the various limitations. A collision can be prevented by forcing several drones to statically hover to permit its peers to securely permit the path segments. Some scenarios were examined to display the efficacy of the scheduling and routing architecture.
The performances of UAVs flight (single/group flight) for the decision of distinct target tasks in the city using data air navigation methods [15] and technique of arithmetical modeling in artificial intelligence (AI) (methods of deciding risk graph theory, fuzzy logic (FL) model, dynamic programming, Expert Judgment Method and so on.). The optimization and configuration group flight paths for UAVs are based on the kinds of “target tasks”. The limitations of emergency response and traffic policing handling schemes are addressed in [16]. Besides, the authors presented a smart, independent UAV-assisted solution; and describes the structure in simulated setting. Some scenarios of policing system and traffic monitoring are taken into account in the simulation: mobile speeding trap and automatic notifications, accident detection and traffic light violation, vehicle tracing using UAV, traffic rerouting and congestion detection, autonomous emergency response handling system, and pending arrest warrants or flagged stolen vehicles [17].
A spatiotemporal scheduling architecture is developed for autonomous UAVs with the RL method. This architecture allows UAV to separately define their schedule to cover the maximal pre-scheduled event temporally and spatially dispersed over a pre-defined time horizon and provided geographical region. The proposed method can upgrade the planned schedule in the event of an unpredicted emergency. Huang et al. [18] proposed the Active Trust Verification Data Collection (ATVDC) system to the secure, efficient, and cheap gathering of information. In this system, a UAV is adapted for collecting basic information from the sensor to estimate the trust of mobile vehicle (MV), and a high-trust MV priority recruitment (HTMPR) approach is presented for recruiting credible MV at a lower cost. Additionally, a genetic-algorithm-based trajectory planning (GATP) strategy was developed for permitting the UAV for collecting further basic information at minimal flight costs.
In this study, an efficient SIRSS-CIoD technique is derived for grouping the drones in the cluster and enabling optimal data transmission in smart cities via shortest routes. The proposed SIRSS-CIoD technique involves the TSA-C technique to choose CHs and BBO algorithm for optimal RS. The detailed working of these modules is discussed in the following sections.
3.1 Phase I: Algorithmic Steps Involved in TSA-C Technique
Primarily, the TSA-C technique gets executed to pick an optimal set of CHs from the available drones in the network [19]. Tuna, scientifically called Thunnini, is a marine carnivorous fish. They utilize their intelligence to attack and find their prey. This creature has changed a huge amount of intelligent and effective foraging behaviors. The initial behavior was spiral foraging. Once tuna are feeding, it swim by making a spiral procedure for acquiring the prey as to shallow water where they are attacked more easily. The next behavior is parabolic foraging. Every tuna swim afterward the prior individuals, which form a parabolic formation for enclosing their prey. Tuna effectively forages by the above mentioned 2 strategies. In this work, a novel swarm based meta-heuristic optimized method, such as tuna swarm optimization, is presented dependent upon modeling this natural foraging behavior.
Initiation
Like other swarm-based metaheuristics method, TSA begin the procedure of optimization by making the first population at random uniformly in the searching space,
whereas
Spiral Foraging
Once sardines, herring, also other smaller school fish encounters predator, the whole schooling of fish forming a dense structure continuously changes the swimming direction, which makes it complex for the predator for locking the target. Now, the tuna group chases the prey by creating a tight spiral form. Even though many school fishes have a small sense of direction, as soon as a smaller group of fish swims firmly in specific direction, the neighboring fish would alter its direction consecutively and lastly create a larger group with similar goals and starts to hunt. Besides spiraling afterward their prey, the school of tuna exchanges data with one another. All the tuna following the prior fish, hence enabling data sharing between adjacent tuna. As mentioned above, the arithmetical equation for the spiral foraging behavior can be expressed in the following:
In which
whereas
Parabolic Foraging
Besides feeding by making a spiral form tuna forms a parabolic cooperative feeding. Tunas form a parabolic shape using food as a reference point. Additionally, tuna hunts to food by seeking everywhere. Both strategies are carried out concurrently, with the assumption that chosen probability is 50% for both. The arithmetical expression can be determined in the following:
In which
Usually, there are 4 objective functions in which it encompasses all the considerable factors essential for energy effective clusterings such as identifying present energy ratio, preserving the energy using the constrained number of CH, mitigation of intracluster distance, improved intercluster distance from CH, balancing the load between CHs, and reducing the distance among base station (BS) and CH. The newly developed TSA-C technique makes an optimal solution by acquiring a fitness function (FF) with distance to BS, distance to neighbors, network load, and energy. Consequently, FF is determined in the currently utilized technique by:
In which

Figure 2: Flowchart of TSA
The subsequent function determines the distance to neighbors that are determined as a Euclidean distance between the sensor nodes (SNs).
The 3rd function decreases the distance among CH & BS. In this technique was deliberated as
The ultimate operation is employed to accomplish the load in CH. Eq. (15) restraint the maximum load amongst CHs.
3.2 Phase II: Algorithmic Steps Involved in BBO-RS Technique
At this stage, the BBO-RS technique is employed to derive an optimal set of routes to the destination in the IoD network [20].
In BBO, every problem solution is regarded as a “habitat” with habitat survival index (HSI), i.e., the same as a fitness of EA to estimate an individual. Higher HSI habitat shares their feature with lower HSI habitat. The procedure of sharing better features amongst solutions are represented as migration. BBO adapts the migration behavior for sharing data between solutions. Better individuals’ data could be preserved at the time of the evolutionary procedure to guarantee population convergence. Mutation operators are utilized for generating various solutions to help the variety of the population. The complete processes are given in the following. Assume that the specific amount of all the individuals i represent
where as
Assume that species amount changes with species migrating;
Next, the mutation rate
where as
For detecting an optimum set of paths, the dimension of all the BBO-RS techniques can be determined to be equal to CH and the additional locations are situated in the BS. Consider,
The objective is for defining an optimum set of paths from CH to BS with an FF with 2 variables like distance and energy. At first, the RE of the following hop nodes can be determined and the nodes using the highest energy are processed as a relay node. For transmitting the information, the source node is transferred to the relay node which further moves to BS utilizing inter CH. So, the nodes using high RE are processed as the following hop nodes. The primary sub-objectives
As well, Euclidean distance is utilized to define the distance from CH to BSs. The minimalization of energy dissipation is dependent largely on the broadcast distance. If a lower distance occurs, the energy could be stored considerably. As soon as the distance gets increased, a massive quantity of energy could be expended. Henceforth, a node with less distance is chosen for relay nodes. Hence, the subsequent sub-objectives using distance is
As mentioned, sub-objective can be briefly described to FF as follows, while
This section investigates the performance validation of the proposed model under the distinct number of drones. Primarily, an extensive Network Lifetime (NLT) analysis of the SIRSS-CIoD technique is provided in Tab. 1 and Fig. 3. A comparative results analysis is made with glowworm swarm optimization based clustering with routing (GSOCR), grey wolf optimization based clustering with routing (GWOCR), improved particle swarm optimization based clustering with routing (IPSOCR), and particle swarm optimization based clustering with routing (PSOCR).
The results revealed that the SIRSS-CIoD technique has accomplished improved NLT over the other techniques. For instance, with 10 drones, the SIRSS-CIoD methodology has accomplished an increased NLT of 6010 rounds while the GSOCR method, GWOCR model, IPSOCR approach, and PSOCR algorithms have attained lower NLT of 5880, 5850, 5650, and 5100 rounds respectively. Concurrently, with 20 drones, the SIRSS-CIoD technique has offered enhanced NLT of 6220 rounds but the GSOCR method, GWOCR model, IPSOCR approach, and PSOCR algorithms have attained decreased NLT of 5830, 5620, 5500, and 5070 rounds respectively. In addition, with 30 drones, the SIRSS-CIoD methodology has accomplished a superior NLT of 6070 rounds although the GSOCR method, GWOCR model, IPSOCR approach, and PSOCR algorithms have attained decreased NLT of 5610, 5320, 5170, and 4900 rounds respectively.


Figure 3: Comparative NLT analysis of SIRSS-CIoD with recent approaches
A comparative average delay (AD) analysis of the SIRSS-CIoD technique takes place in Tab. 2 and Fig. 4. The results showcased that the SIRSS-CIoD system has gained minimal AD over the other techniques. For instance, with 10 drones, the SIRSS-CIoD technique has obtained a lower AD of 1.59 s whereas the GSOCR method, GWOCR model, IPSOCR approach, and PSOCR algorithms have gotten maximum AD of 2.02, 2.09, 2.21, and 2.75 s respectively. Eventually, with 20 drones, the SIRSS-CIoD technique has reached the reduced AD of 2.36 s whereas the GSOCR method, GWOCR model, IPSOCR approach, and PSOCR algorithms have resulted in higher AD of 2.52, 2.82, 3.71, and 4.87 s respectively. Meanwhile, with 30 drones, the SIRSS-CIoD technique has provided decreased AD of 2.79 s whereas the GSOCR method, GWOCR model, IPSOCR approach, and PSOCR algorithms have reached increased AD of 3.25, 3.51, 4.77, and 6.01 s respectively.

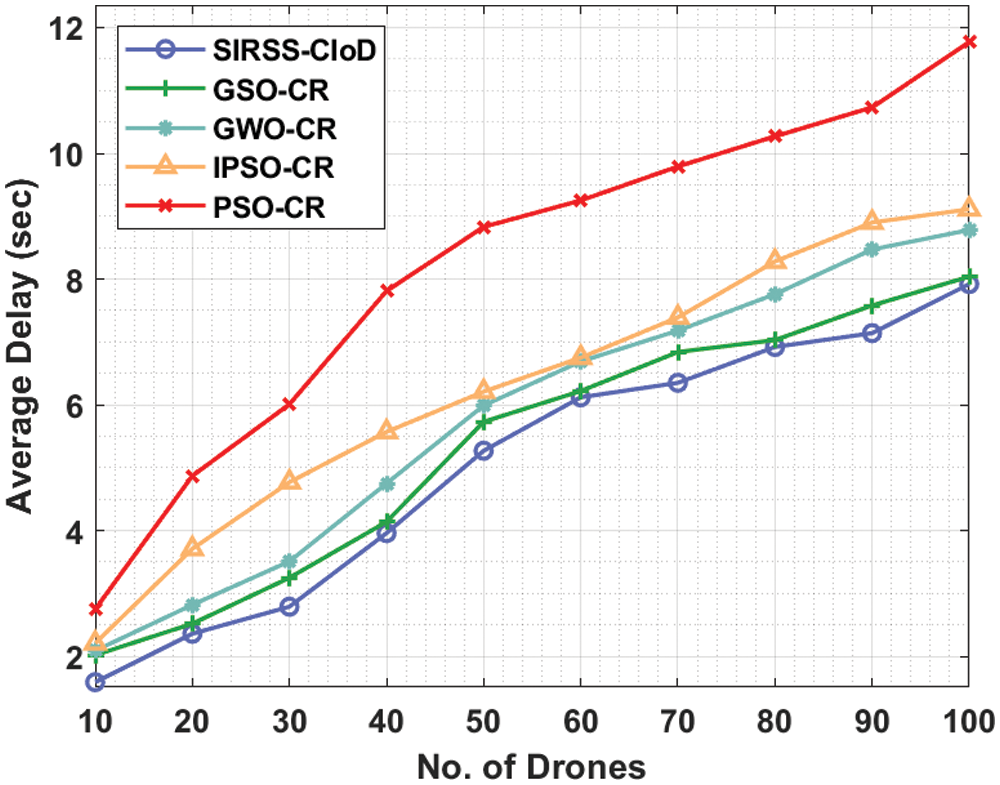
Figure 4: Comparative AD analysis of SIRSS-CIoD with recent approaches
A detailed energy consumption (ECM) analysis of the SIRSS-CIoD technique takes place in Tab. 3 and Fig. 5. The results showcased that the SIRSS-CIoD technique has offered reduced ECM over the other techniques. For instance, with 10 drones, the SIRSS-CIoD technique has attained a lower ECM of 42 mJ whereas the GSOCR method, GWOCR model, IPSOCR approach, and PSOCR algorithms have obtained higher ECM of 0.19, 46, 51, 47, and 56 mJ respectively. Likewise, with 20 drones, the SIRSS-CIoD technique has reached to reduced ECM of 60 mJ whereas the GSOCR method, GWOCR model, IPSOCR approach, and PSOCR algorithms have obtianed increased ECM of 66, 72, 79, and 82 mJ respectively. Concurrently, with 30 drones, the SIRSS-CIoD technique has provided decreased ECM of 95 mJ whereas the GSOCR method, GWOCR model, IPSOCR approach, and PSOCR algorithms have obtained raised ECM of 100, 102, 112, and 118 mJ respectively.

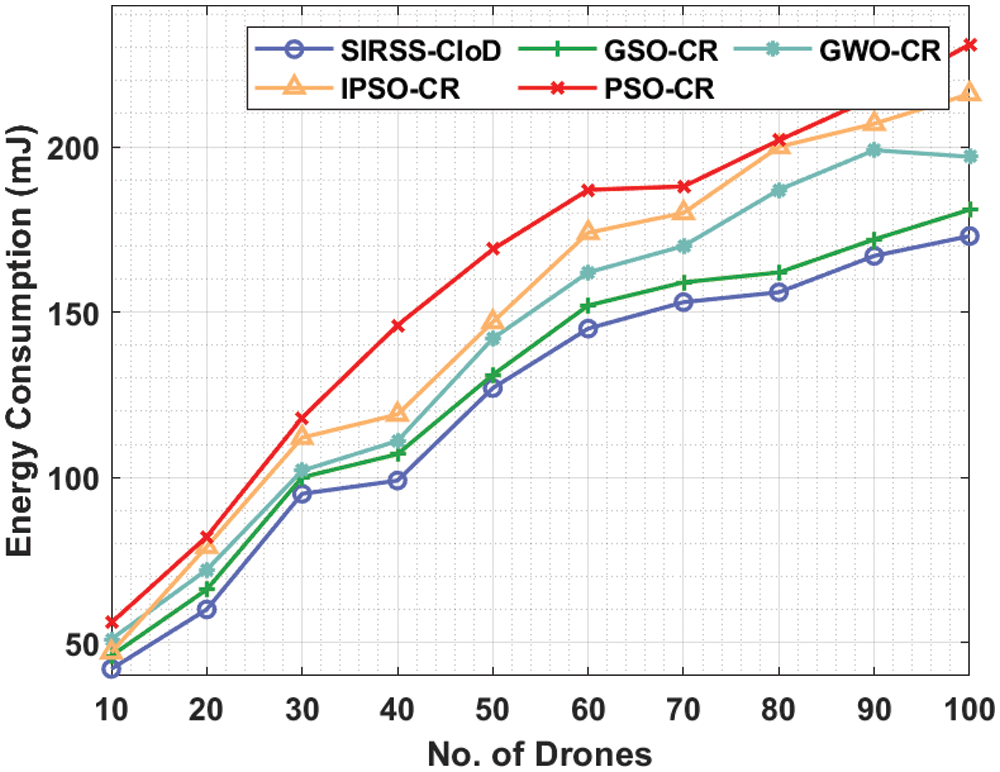
Figure 5: Comparative ECM analysis of SIRSS-CIoD with recent approaches
A comparative throughput (THR) analysis of the SIRSS-CIoD technique is provided in Tab. 4 and Fig. 6. The results exposed that the SIRSS-CIoD technique has accomplished improved THR over the other techniques. For instance, with 10 drones, the SIRSS-CIoD approach has accomplished a higher THR of 0.92 Mbps but the GSOCR method, GWOCR model, IPSOCR approach, and PSOCR algorithms have attained lower THR of 0.81, 0.79, 0.74, and 0.72 Mbps respectively. Concurrently, with 20 drones, the SIRSS-CIoD technique has offered enhanced THR of 0.86 Mbps although the GSOCR method, GWOCR model, IPSOCR approach, and PSOCR algorithms have attained decreased THR of 0.73, 0.75, 0.62, and 0.57 Mbps respectively. Simultaneously, with 30 drones, the SIRSS-CIoD technique has accomplished an increased THR of 0.83 Mbps while the GSOCR method, GWOCR model, IPSOCR approach, and PSOCR algorithms have attained decreased THR of 0.73, 0.59, 0.54, and 0.55 Mbps respectively.

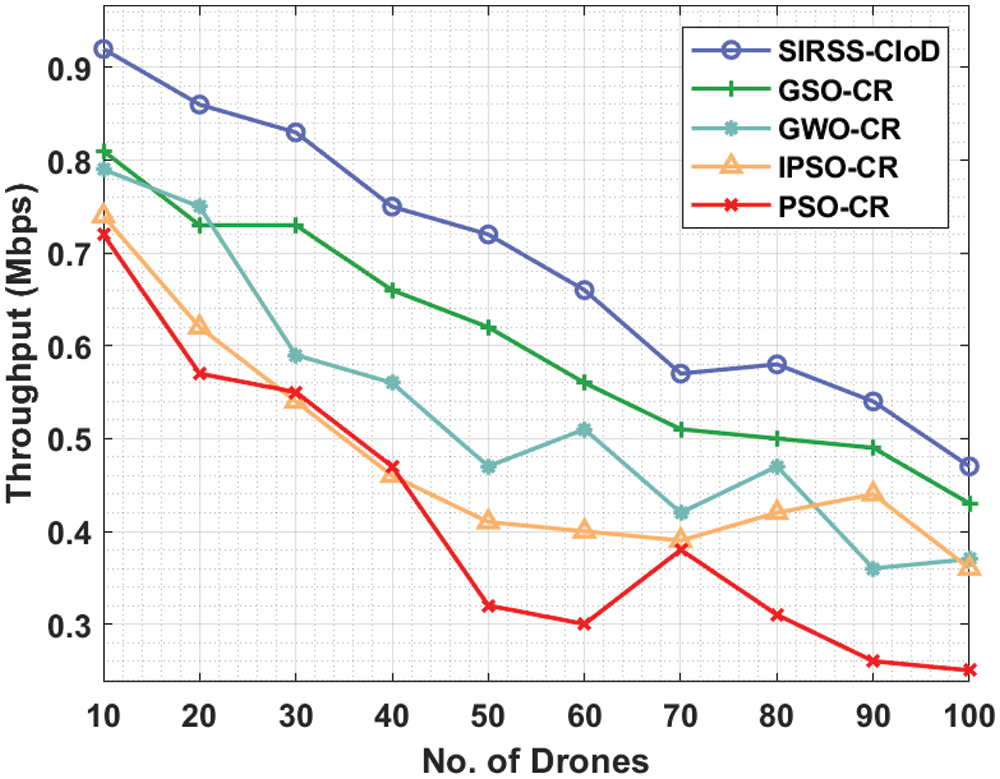
Figure 6: Comparative THR analysis of SIRSS-CIoD with recent approaches
Finally, a brief packet loss rate (PLR) analysis of the SIRSS-CIoD technique takes place in Tab. 5 and Fig. 7. The results reported that the SIRSS-CIoD technique has resulted in reduced PLR over the other techniques.
For instance, with 10 drones, the SIRSS-CIoD technique has attained a lower PLR of 0.08 Mbps whereas the GSOCR method, GWOCR approach, IPSOCR algorithm, and PSOCR system have obtained higher PLR of 0.19, 0.21, 0.26, and 0.28 Mbps respectively. Likewise, with 20 drones, the SIRSS-CIoD technique has reached to reduced PLR of 0.14 Mbps whereas the GSOCR method, GWOCR approach, IPSOCR algorithm, and PSOCR technique have gained increased PLR of 0.27, 0.25, 0.38, and 0.43 Mbps respectively. Concurrently, with 30 drones, the SIRSS-CIoD technique has provided decreased PLR of 0.17 Mbps whereas the GSOCR method, GWOCR approach, IPSOCR algorithm, and PSOCR technique have obtained raised PLR of 0.27, 0.41, 0.46, and 0.45 Mbps respectively.

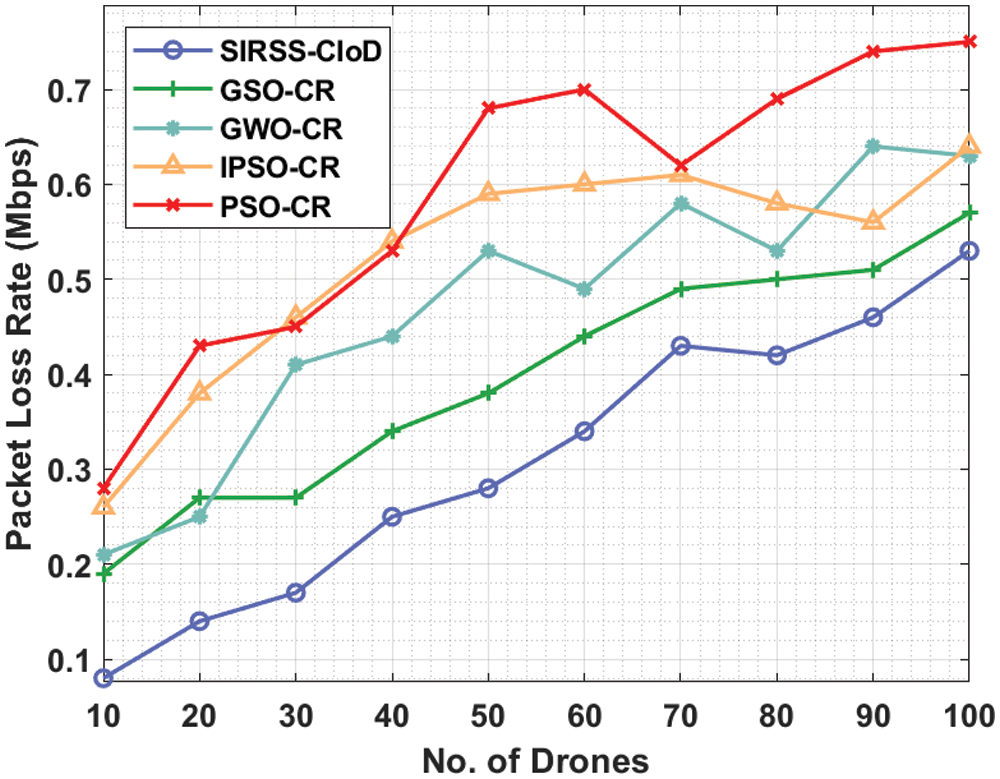
Figure 7: Comparative PLR analysis of SIRSS-CIoD with recent approaches
From the aforementioned tables and figures, it can be evident that the SIRSS-CIoD system is an effective tool for data collection and routing in the smart cities’ environment.
In this study, an efficient SIRSS-CIoD technique is derived for grouping the drones in the cluster and enabling optimal data transmission in smart cities via shortest routes. The proposed SIRSS-CIoD technique involves the TSA-C technique to choose CHs and BBO algorithm for optimal RS. Primarily, the TSA-C technique gets executed to pick an optimum group of CHs from the available drones in the network. Followed by, the BBO-RS approach was employed for deriving an optimal group of routes to the destination in the IoD network. A wide range of experimental analyses is carried out and the comparative study highlighted the improved performance of the SIRSS-CIoD technique over the other approaches. Therefore, the proposed SIRSS-CIoD technique can be applied as a proficient approach for data collection and routing in IoD-enabled smart city applications. In future, data aggregation and scheduling methods are developed to improve the network performance.
Acknowledgement: The authors extend their appreciation to the Deputyship for Research & Innovation, Ministry of Education in Saudi Arabia for funding this research work through the project number (IFPIP-1266-611-1442) and King Abdulaziz University, DSR, Jeddah, Saudi Arabia.
Funding Statement: This project was supported financially by Institution Fund projects under Grant No. (IFPIP-1266-611-1442).
Conflicts of Interest: The authors declare that they have no conflicts of interest to report regarding the present study.
1. V. Sharma, F. Song, I. You and M. Atiquzzaman, “Energy efficient device discovery for reliable communication in 5G-based IoT and BSNs using unmanned aerial vehicles,” Journal of Network and Computer Applications, vol. 97, pp. 79–95, 2017. [Google Scholar]
2. Y. J. Chen and L. C. Wang, “Privacy protection for internet of drones: A network coding approach,” IEEE Internet Things Journal, vol. 6, no. 2, pp. 1719–1730, 2019. [Google Scholar]
3. S. Aggarwal and N. Kumar, “Path planning techniques for unmanned aerial vehicles: A review, solutions, and challenges,” Computer Communications, vol. 149, pp. 270–299, 2020. [Google Scholar]
4. Y. K. Ever, “A secure authentication scheme framework for mobile-sinks used in the Internet of Drones applications,” Computer Communications, vol. 155, pp. 143–149, 2020. [Google Scholar]
5. M. Nikooghadam, H. Amintoosi, S. H. Islam and M. F. Moghadam, “A provably secure and lightweight authentication scheme for Internet of Drones for smart city surveillance,” Journal of Systems Architecture, vol. 115, pp. 101955, 2021. [Google Scholar]
6. S. A. R. Naqvi, S. A. Hassan, H. Pervaiz and Q. Ni, “Drone-aided communication as a key enabler for 5g and resilient public safety networks,” IEEE Communications Magazine, vol. 56, no. 1, pp. 36–42, 2018. [Google Scholar]
7. H. Menouar, I. Guvenc, K. Akkaya, A. S. Uluagac, A. Kadri et al., “UAV-enabled intelligent transportation systems for the smart city: Applications and challenges,” IEEE Communications Magazine, vol. 55, no. 3, pp. 22–28, 2017. [Google Scholar]
8. D. Schneider, “Air traffic control for delivery drones [Top Tech 2017],” IEEE Spectrum, vol. 54, no. 1, pp. 32–33, 2017. [Google Scholar]
9. W. Fawaz, C. A. Rjeily and C. Assi, “UAV-aided cooperation for fso communication systems,” IEEE Communications Magazine, vol. 56, no. 1, pp. 70–75, 2018. [Google Scholar]
10. F. Aftab, A. Khan and Z. Zhang, “Bio-inspired clustering scheme for Internet of Drones application in industrial wireless sensor network,” International Journal of Distributed Sensor Networks, vol. 15, no. 11, pp. 155014771988990, 2019. [Google Scholar]
11. H. Fatemidokht, M. K. Rafsanjani, B. B. Gupta and C. H. Hsu, “Efficient and secure routing protocol based on artificial intelligence algorithms with uav-assisted for vehicular ad hoc networks in intelligent transportation systems,” IEEE Transactions on Intelligent Transportation Systems, vol. 22, no. 7, pp. 4757–4769, 2021. [Google Scholar]
12. H. Kim, L. Mokdad and J. Ben-Othman, “Designing UAV surveillance frameworks for smart city and extensive ocean with differential perspectives,” IEEE Communications Magazine, vol. 56, no. 4, pp. 98–104, 2018. [Google Scholar]
13. B. N. Coelho, V. N. Coelho, I. M. Coelho, L. S. Ochi, R. H. Koochaksaraei et al., “A multi-objective green UAV routing problem,” Computers & Operations Research, vol. 88, pp. 306–315, 2017. [Google Scholar]
14. A. Bahabry, X. Wan, H. Ghazzai, G. Vesonder and Y. Massoud, “Collision-free navigation and efficient scheduling for fleet of multi-rotor drones in smart city,” in 2019 IEEE 62nd Int. Midwest Symp. on Circuits and Systems (MWSCAS), Dallas, TX, USA, pp. 552–555, 2019. [Google Scholar]
15. G. Hartwigsen, “Flexible redistribution in cognitive networks,” Trends in Cognitive Sciences, vol. 22, no. 8, pp. 687–698, 2018. [Google Scholar]
16. A. Beg, A. R. Qureshi, T. Sheltami and A. Yasar, “UAV-enabled intelligent traffic policing and emergency response handling system for the smart city,” Personal and Ubiquitous Computing, vol. 25, no. 1, pp. 33–50, 2021. [Google Scholar]
17. O. Bouhamed, H. Ghazzai, H. Besbes and Y. Massoud, “A generic spatiotemporal scheduling for autonomous uavs: A reinforcement learning-based approach,” IEEE Open Journal of Vehicular Technology, vol. 1, pp. 93–106, 2020. [Google Scholar]
18. S. Huang, J. Gui, T. Wang and X. Li, “Joint mobile vehicle–UAV scheme for secure data collection in a smart city,” Annals of Telecommunications, vol. 76, no. 9–10, pp. 559–580, 2021. [Google Scholar]
19. L. Xie, T. Han, H. Zhou, Z. R. Zhang, B. Han et al., “Tuna swarm optimization: A novel swarm-based metaheuristic algorithm for global optimization,” Computational Intelligence and Neuroscience, vol. 2021, pp. 1–22, 2021. [Google Scholar]
20. H. Mo, Z. Xu, L. Xu, Z. Wu and H. Ma, “Constrained multiobjective biogeography optimization algorithm,” The Scientific World Journal, vol. 2014, pp. 1–12, 2014. [Google Scholar]
 | This work is licensed under a Creative Commons Attribution 4.0 International License, which permits unrestricted use, distribution, and reproduction in any medium, provided the original work is properly cited. |