DOI:10.32604/cmc.2022.023697

| Computers, Materials & Continua DOI:10.32604/cmc.2022.023697 |  |
| Article |
Robust Authentication and Session Key Agreement Protocol for Satellite Communications
1Department of Computer Engineering, Ferdowsi University of Mashhad, Mashhad, 9177948974, Iran
2Faculty of Mathematics and Science, Universitas Padjadjaran, Jatinangor, 45363, Indonesia
3Faculty of Computer Science, Universitas Mercu Buana, Jakarta, 11650, Indonesia
*Corresponding Author: Rahmat Budiarto. Email: rahmat.budiarto@mercubuana.ac.id
Received: 17 September 2021; Accepted: 08 December 2021
Abstract: Satellite networks are recognized as the most essential communication infrastructures in the world today, which complement land networks and provide valuable services for their users. Extensive coverage and service stability of these networks have increased their popularity. Since eavesdropping and active intrusion in satellite communications are much easier than in terrestrial networks, securing satellite communications is vital. So far, several protocols have been proposed for authentication and key exchange of satellite communications, but none of them fully meet the security requirements. In this paper, we examine one of these protocols and identify its security vulnerabilities. Moreover, we propose a robust and secure authentication and session key agreement protocol using the elliptic curve cryptography (ECC). We show that the proposed protocol meets common security requirements and is resistant to known security attacks. Moreover, we prove that the proposed scheme satisfies the security features using the Automated Validation of Internet Security Protocols and Applications (AVISPA) formal verification tool and On-the fly Model-Checker (OFMC) and ATtack SEarcher (ATSE) model checkers. We have also proved the security of the session key exchange of our protocol using the Real or Random (RoR) model. Finally, the comparison of our scheme with similar methods shows its superiority.
Keywords: Satellite communications; authentication; session key agreement; secure communication; security protocols; formal verification
Nowadays, mobile satellite networks are used to provide advanced personal communication services. These services complement terrestrial networks, providing benefits such as global coverage and increasing mobility and reliability for users. Satellite communications are valuable in an emergency and when other networks are unable to operate. Users can use satellite phones anytime and anywhere, including seas, islands, and high mountains, where land-based networks cannot provide services [1–3]. Furthermore, multicast applications delivery such as multimedia content distribution is perfectly performed by satellite systems [4,5].
While there are many different types of satellites, Low-Earth-Orbit (LEO) satellites are used more in mobile communications. These satellites are at shorter distances from Earth, so they have higher signal strength and lower latency [6,7]. However, unlike the Geosynchronous-Equatorial-Orbit (GEO) satellite, which alone covers the entire surface of the earth, several LEO satellites are required for this purpose [8].
The LEO satellite is a land-based satellite located less than 2000 km above the earth, which enables communication between mobile devices and the network control center through gateways [8,9]. Fig. 1 illustrates a general overview of satellite communications. The four basic components of these communications are mobile users, the network control center (NCC), LEOs, and gateways. Mobile users need to register with NCC to use the services. Gateways communicate between LEOs and the NCC.
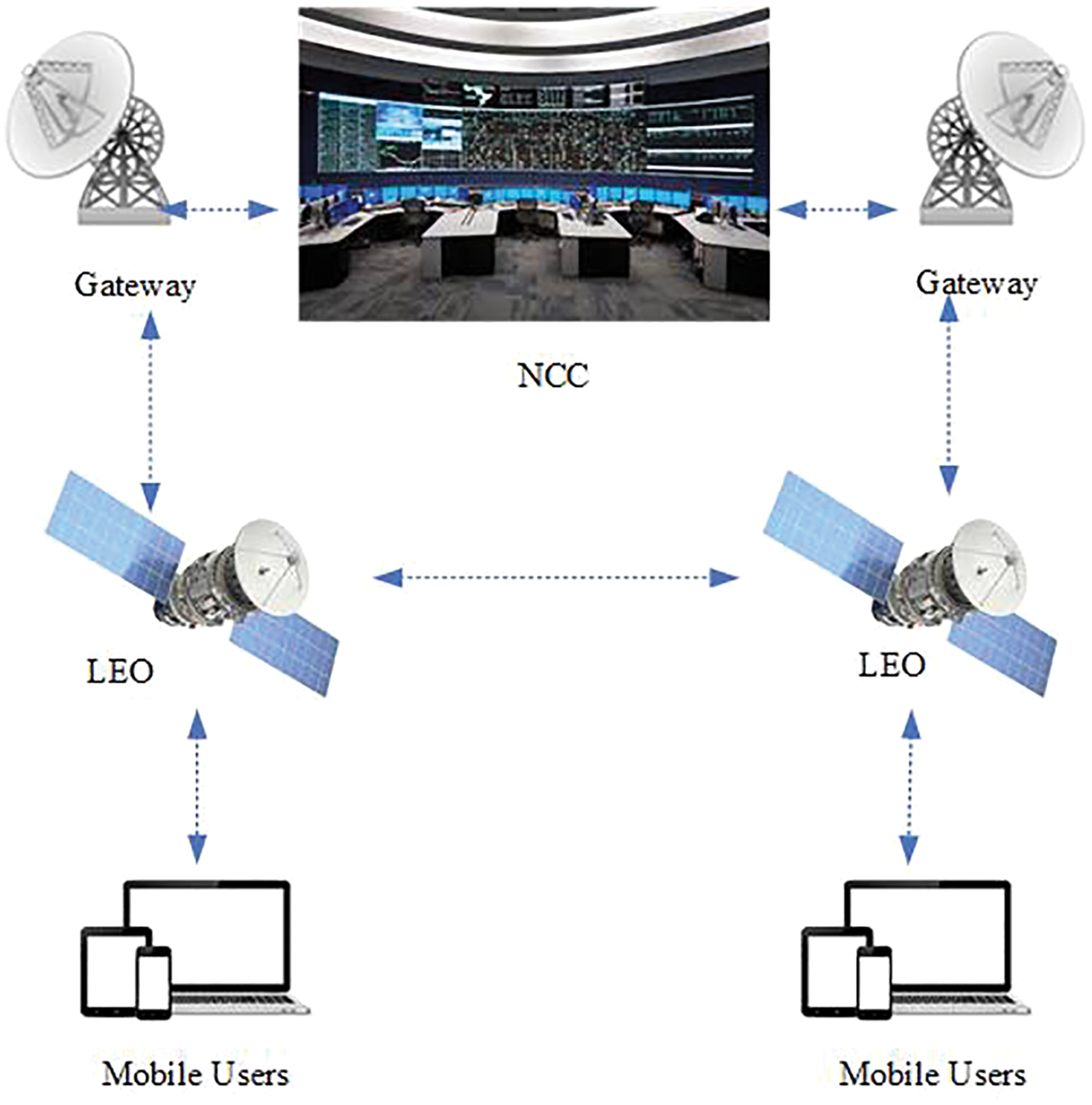
Figure 1: An overview of satellite communications
Because satellite communications are more susceptible to security attacks due to their broadcast nature, these communications need to be secure. Therefore, a session key is required for each communication session to encrypt the messages. There is also a need for strong authentication of both parties.
In recent years, various protocols for securing satellite communications have been proposed, most of which have security flaws. In particular, some authentication and key management protocols have provided ECC-based solutions leveraging the elliptic curve discrete logarithm problem (ECDLP) [10–14]. In this paper, we examine Qi et al.'s work [12] and show its security vulnerabilities. We propose a secure and robust protocol for key exchange in satellite communications, which is resistant to known security attacks and satisfies the security requirements. Further, a thorough analysis of the proposed protocol shows that it performs better in terms of security than other ECC-based protocols.
The contributions of this paper are as follows:
• Analysis of key exchange protocol introduced by Qi et al. [12] and security vulnerabilities are revealed.
• A secure ECC-based authentication and key exchange protocol that resists common attacks and meets common security requirements.
• A thorough security analysis of the proposed protocol and its resistance to various types of attacks.
• Formal security verification of the proposed protocol on AVISPA tool, considering different model checking techniques that the proposed protocol meets different security requirements.
• The proof of security of the proposed key exchange protocol using the RoR model.
The rest of the paper is structured as follows: In Section 2, some essential related works are discussed. Section 3 provides background information on elliptic curve cryptography and the threat models. Section 4 describes Qi et al.'s protocol [12] and analyzes its security. Section 5 describes the proposed authentication and key exchange protocol for satellite communications. The security analysis of the proposed method is described in Section 6. In Section 7, the proposed protocol is compared with other similar protocols in terms of time complexity, communication cost, and security features. Finally, Section 8 is devoted to the conclusion.
To provide satellite communications over unsecured networks, Cruickshank [15] developed the first satellite communication protocol in 1996. Since then, many protocols were introduced to secure satellite communications, and later on, other researchers take turns finding out weaknesses and flaws in those protocols and propose improved protocols.
Chen et al. [16] proposed an authentication mechanism for mobile satellite communication systems. Later on, Lasc et al. [17] showed that Chen et al.'s protocol was not resistant to the Denial of Service (DoS) attack and then suggested an improvement. Next, Chang et al. [18] revealed that Lasc et al.'s protocol was susceptible to impersonation attack through a stolen smart card. Then they proposed an authentication protocol for satellite communications. The newly proposed protocol was claimed to be resistant to all kinds of attacks. However, Zhang et al. [19] showed that the protocol proposed by Chang et al. was not resistant against the DoS attack and the impersonation attack.
Lee et al. [20] introduced an authentication and key exchange protocol for mobile satellite communications systems and claimed that it is resistant to all kinds of attacks. Later, Zhang et al. [21] revealed that Lee et al.'s protocol was not resistant against replay attacks, DoS attacks, and attacks from a stolen smart card. Then they developed a new protocol for satellite communication authentication. In 2018, Qi et al. [10] stated that Zhang et al.’ protocol was insecure against the stolen-verifier attack and DoS attack. Then they proposed an ECC-based protocol for satellite communication authentication. In 2019, Ostad-sharif et al. [11] showed that Qi and Chen's protocol could not meet the security requirements of perfect forward secrecy and did not resist the ephemeral secret leakage attack.
Liu et al. [22] proposed a Lightweight protocol for satellite communications authentication. Later on, Qi et al. [12] showed that the protocol proposed by Liu et al. does not meet the perfect forward security requirement. Then they introduced an authentication protocol based on ECC. In this paper, we prove that the protocol of Qi et al. is not resistant to Known-session-specific temporary information attacks and insider attacks.
Altaf et al. [14] proposed an authentication and key agreement scheme which is based on the (ECDLP problem. Then, Chen and Chen [13] proved that Altaf et al.'s protocol does not provide perfect forward secrecy. Moreover, we found that their scheme is vulnerable to DoS attack. The attacker can resend the request message to the NCC many times and force it to do the time-expensive point multiplication operation many times and thus overwhelms the NCC. Furthermore, Hosseini-Seno et al. [23] have proposed an authentication and key management protocol to provide patient privacy in Tele-medical information system. The proposed protocol cautiously considers all aspects of security requirements including the perfect forward secrecy.
3.1 Elliptic Curve Cryptography (ECC)
ECC uses the elliptic curve
where
The ECC
The building block for elliptic curve cryptography is the elliptic curve discrete logarithm problem: Given two points R and S over
To select a suitable elliptic curve, in addition to determining the values of a, b, and p, we should also define the generator G. In some elliptic curves, all points on the curve (
The most popular threat model is the Dolev-Yao model [26], which is an abstract model of agents’ capabilities. The Dolev-Yao model strips away the extraneous details of communications and shows a simple view of exchanged messages. The Dolev-Yao model presents term of algebra and models the protocol messages as terms. It presents some term derivation rules which define how agents can build new terms from the old ones.
Suppose
The term syntax in Dolev-Yao model is defined in (5).
where
The intruder in the Dolev-Yao model is one of the agents and has access to the hash function, public keys of all agents, his private key, and his shared key with other entities. Moreover, the intruder has full control over all communication messages between agents. He can eavesdrop, intercept, or replay the messages [27]. However, in examining the strength of security protocols, a stricter threat model such as the Canetti–Krawczyk (CK) [28] model is usually used. The attacker in the CK model not only has complete control over communications but also has the ability to obtain secret data in the system's memories. Therefore, the adversary may access private keys of parties or session-specific temporary keys. We consider the CK treat model in the analysis of our protocol.
4 Review and Analysis of Qi et al. Protocol
This section analyzes the protocol introdued by Qi et al. [12]. The protocol consists of four phases, namely, 1) initialization, 2) user registration, 3) login and authentication with key agreement, and 4) password update. In the registration phase, each user firstly selects his ID and password (
When the message is received, the NCC checks that the selected
We demonstrate that the protocol proposed by Qi et al. is vulnerable against attacks, as follows.
Known Session-Specific Temporary Information Attack
If the random parameters generated in a protocol are captured by the attacker, the session key should not be revealed. However, in the Qi et al.'s protocol, the session key
Insider Attack
It is assumed that the internal attacker (here NCC) tries to obtain the password of each user. Since the user sends the
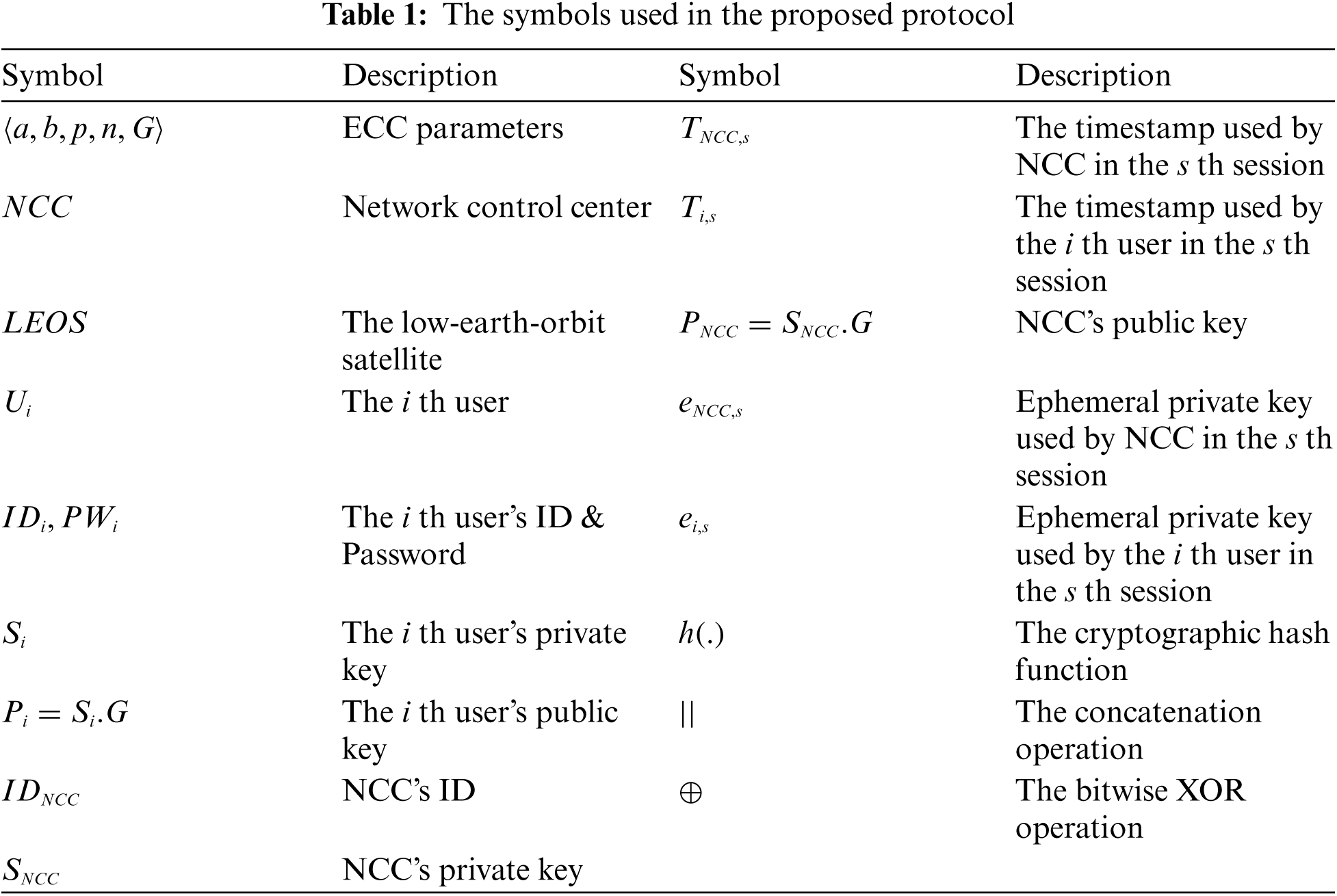
The proposed protocol uses elliptic curve encryption and consists of initialization, registration, and authentication and key agreement steps. Tab. 1 shows the symbols used in the proposed protocol.
In this phase, the NCC sets some parameters to be used in authentication and key management. As explained in the previous section, to use the ECC cryptosystem, the NCC needs to set the five-tuple
To use the NCC services, the user needs to register first. The steps of user registration are depicted in Fig. 2 and are as follows:
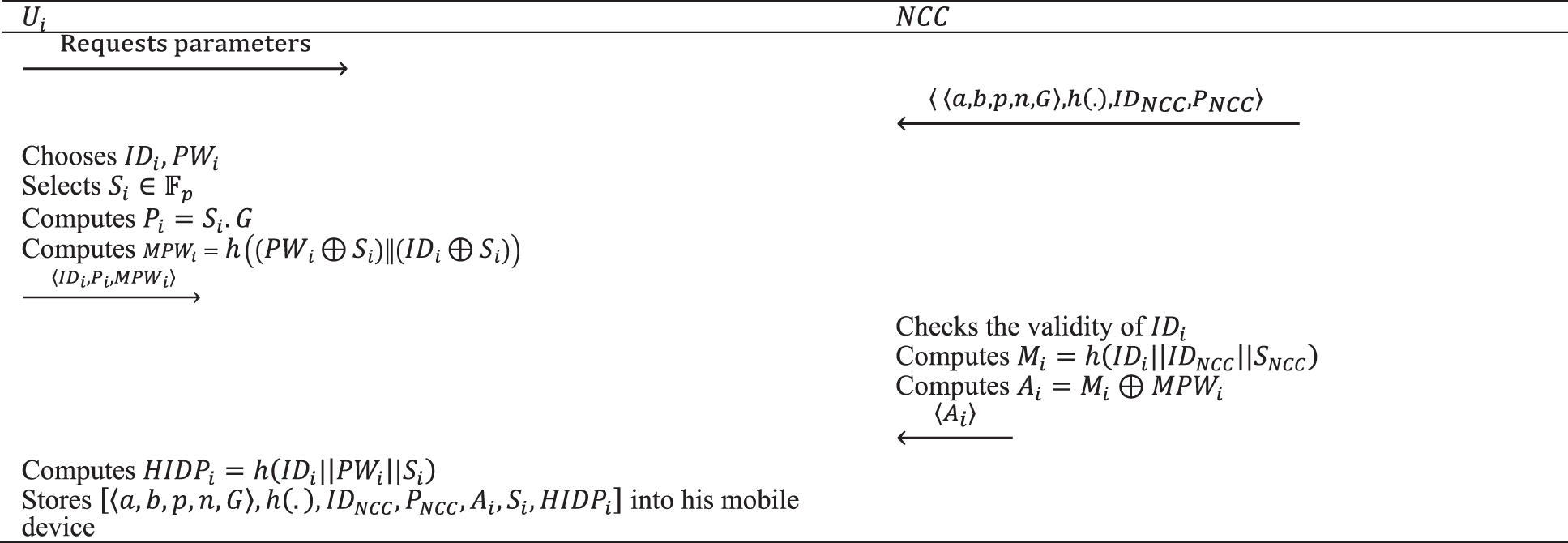
Figure 2: The registration phase of the proposed protocol
Step 1. The user
Step 2. After receiving the necessary parameters, the user chooses an ID and password. He also selects a random number
Finally, he sends the triple
Step 3. Upon receiving
Then, the NCC performs the XOR operation on
Finally, the NCC sends
Step 4. The user calculates the hash of his identity, his password, and his private key as defined in (9).
Finally, he stores
5.3 Authentication and Key Agreement Phase
Upon completion of the registration, the user and the NCC start a two-way authentication and key exchange process to communicate with each other via an insecure channel. A complete description of this phase is given in Fig. 3 and is described in the following steps:
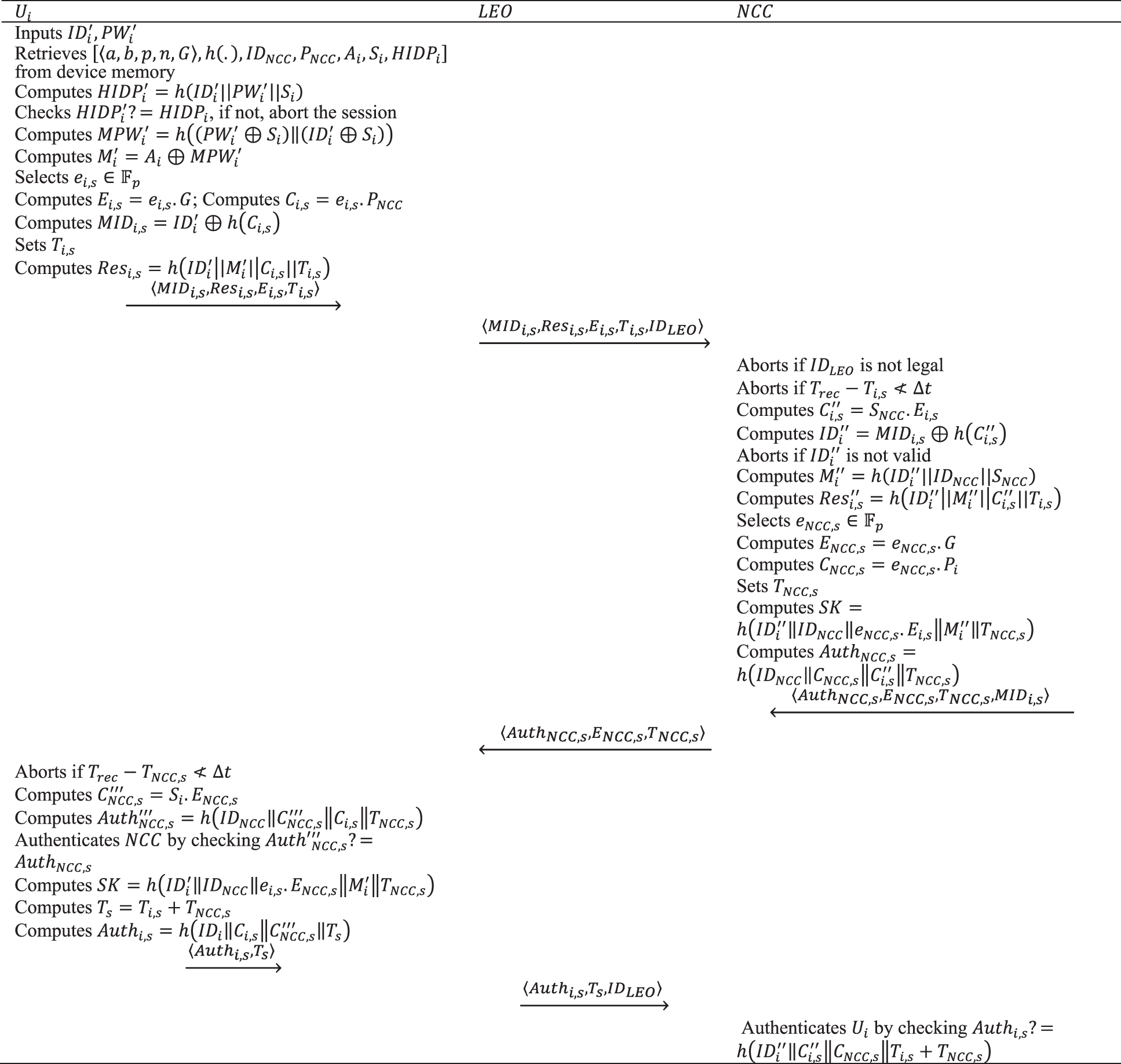
Figure 3: The authentication and key agreement phase of the proposed protocol
Step 1. The user enters his identity and password (
Then the mobile device calculates the masked identity of the user for this session as defined in (14).
The mobile device then sets the timestamp
Finally, the mobile device sends the four-tuple
Step 2. Upon receiving the message
Moreover, the NCC computes
Note that here we use the double prime symbol to indicate that the variables are calculated in a new step of the protocol.
Then the NCC calculates
Then the NCC selects the ephemeral private key of the session,
The NCC then sets the timestamp
Finally, the NCC sends the four-tuple
Step 3. The mobile device verifies the freshness of the received message by checking
Then, the mobile device checks whether
Next, the mobile device computes
Finally, it sends
Step 4. The NCC authenticates the user by checking whether the received
6 Security Analysis of the Proposed Protocol
In this section, we describe the security features, the robustness against several security attacks of the proposed protocol, and formally verify the correctness of the proposed protocol in terms of satisfying security features using AVISPA.
Key agreement protocols require the parties to authenticate each other. In our proposed method, the user selects the ephemeral private key
The session key generated in the proposed method is shared between the user and the NCC, and no other entity can access the session key. The session key on the server-side is calculated with
The perfect forward secrecy guarantees the security of the session key, even though the long-term secret keys of parties are compromised. The proposed method preserves this feature because the session key is built using both long-term private keys and temporary secret keys. Even if the adversary
The proposed method does not send the user identity in plain text over insecure channels, but the masked user identity,
Our proposed method is resistant against the replay attack because, in addition to sending the timestamp
6.2.2 Man-in-the-Middle Attack
If the adversary
The user does not send the password to NCC in the registration phase explicitly but sends it in hidden form,
If the adversary
6.2.5 Known-Session-Specific Temporary Information Attack
If the attacker accesses the temporary session parameters in any way, he should not be able to access the session key. Since the session key,
If the user's mobile device (or smart card) is stolen, the adversary
In our proposed method, NCC does not store any information about users other than their ID. Therefore, if the adversary accesses the NCC database, it will not receive any additional information.
Denial of Service attacks can be done on satellite communications entities, including the users and the NCC. By persuading the NCC to perform a large number of heavy-weight point multiplication operations on the elliptic curve, the attacker causes the NCC to crash and makes it impossible to provide services to authorized users. Our proposed protocol is resistant to this attack because if one of the users wants to carry out this attack against the NCC, he himself will suffer the same heavy-weight operations. Also, due to the resistance of the proposed method to replay attacks, the adversary is not able to resend the request message to the NCC. For the same reason, it is not possible to perform this attack on system users.
6.3 Formal Security Analysis with AVISPA
AVISPA is a role-based language that provides a formal language for specifying protocols and security properties and uses several back-ends to analyze them [29,30]. Each participant in the protocol is represented by a role, which communicates with other roles by channels. The HLPSL specification is translated to an intermediate format, which is then analyzed by some back-ends. The four back-ends used by AVISPA include Tree Automata-based Protocol Analyzer (TA4SP), OFMC [31], Constraint Logic-based Attack Searcher (CL-ATSE) [32], and satisfiability-based Model-Checker (SATMC) [33].
We have implemented our protocol in the HLPSL language. We have defined a role for the user, role_Ui, and a role for the NCC, role_NCC. We have also defined a session role that specifies a session of the protocol. In addition, we have considered an environment role and defined three sessions in it. The first session is between the user and the NCC. In the second session, the intruder impersonates the user, and in the third session, the intruder impersonates the NCC. In addition, we have defined the intruder's knowledge and the security goals.
The goal of secrecy_of sec_1 examines the confidentiality of
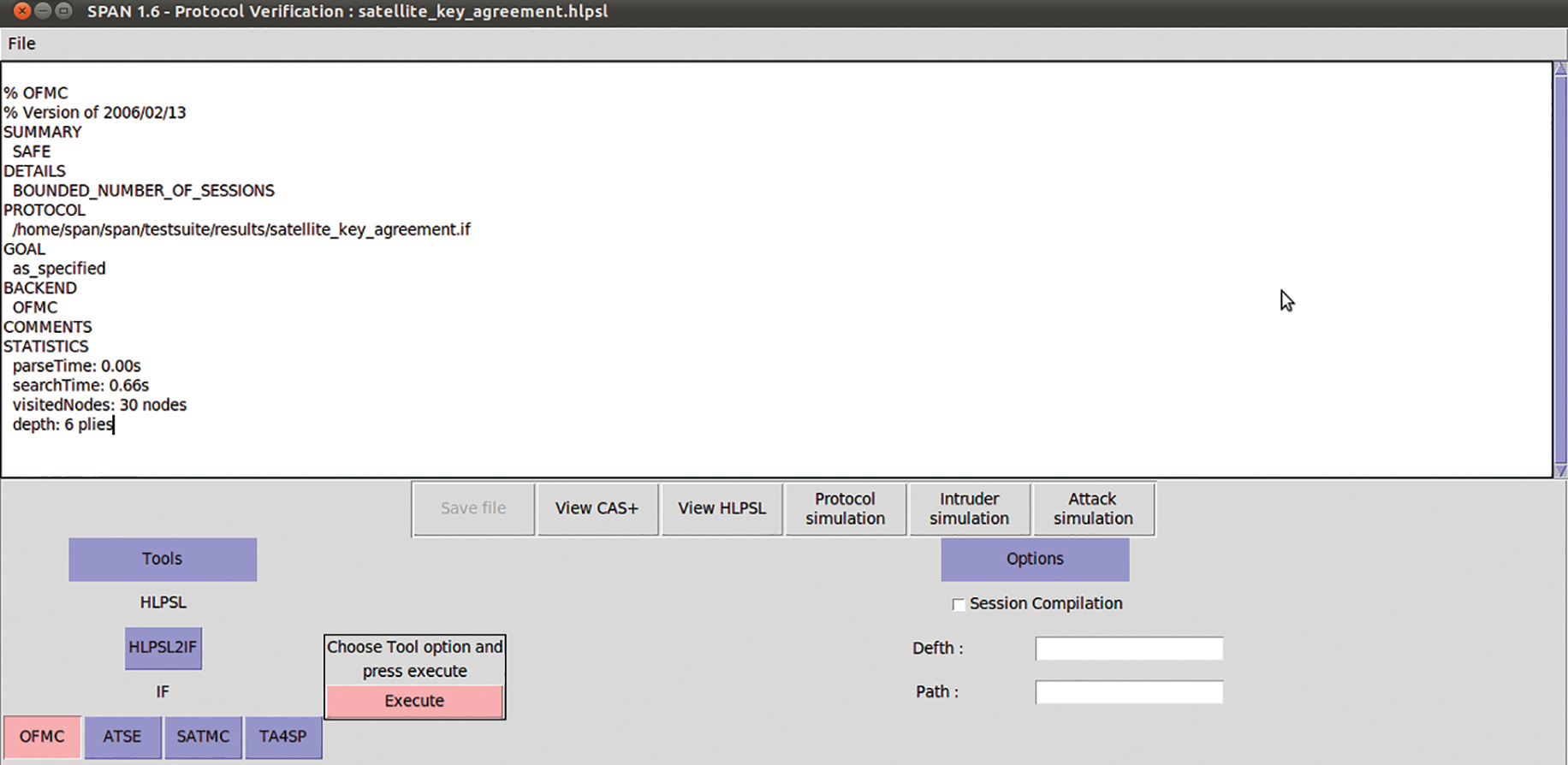
Figure 4: The results of OFMC model checker on the proposed protocol
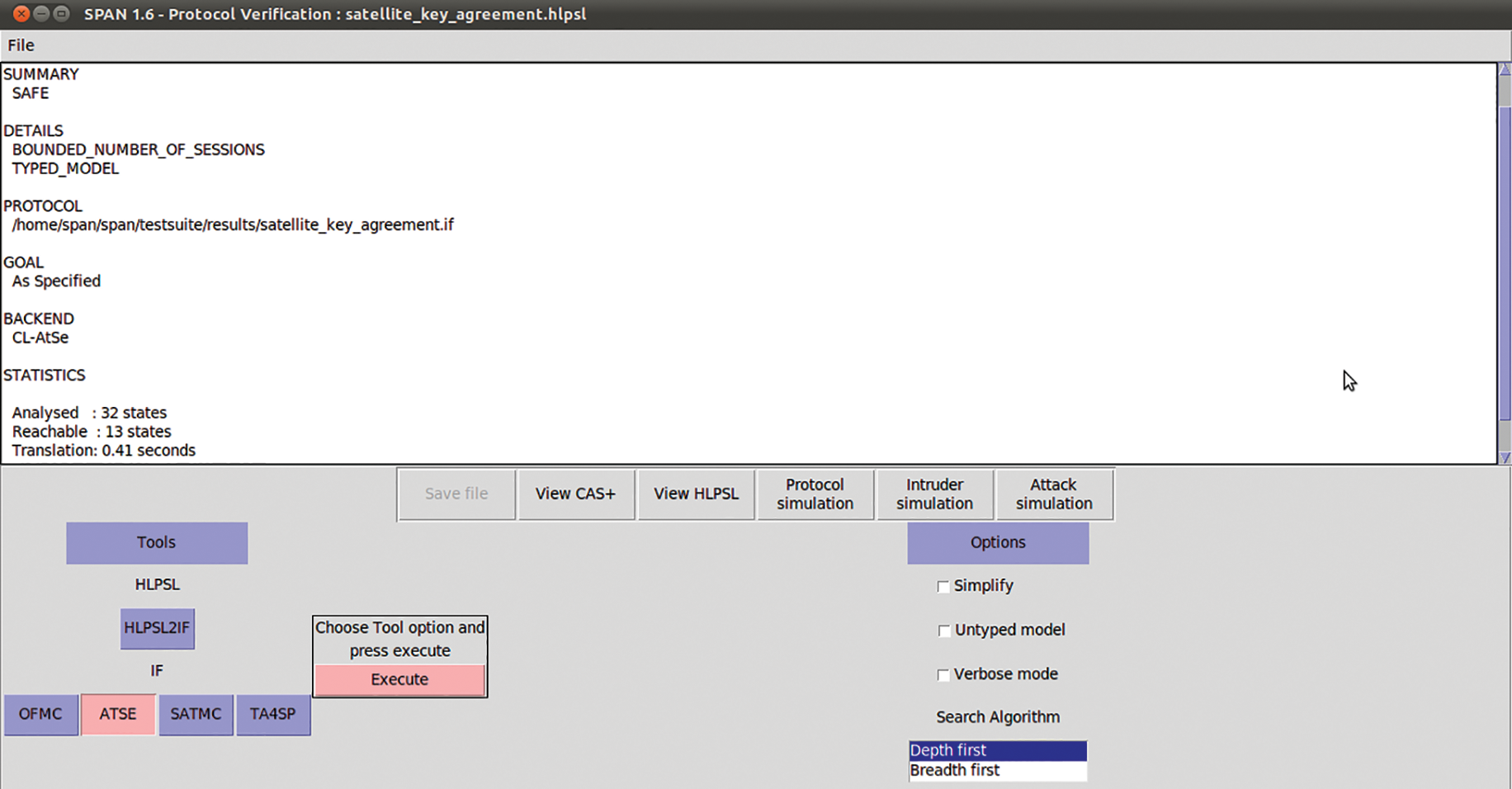
Figure 5: The results of ATSE model checker on the proposed protocol
6.4 Proving the Security of Proposed Key Exchange Protocol Using RoR Model
We examine semantic security of the session key of the proposed protocol using the Real-or-Random model [34,35]. In this model, adversary A obtains a session key or a random value by querying protocol participants. The adversary must guess whether the output returned to him is a real key or a random value. For this purpose, we introduce various concepts such as participants, participant instances, oracles available to A, queries to these oracles, and the concept of partnering.
Participants. The two disjoint sets of our proposed protocol participants are U and
Participant Instances. During the execution of the protocol by the adversary, several instances of each participant may be executed. The instance i of the participant
Long-Lived Keys. Each participant
Ephemeral Keys. Each participant
Acceptance. To simulate the protocol, first, a user instance,
Partnering. Two oracles
Protocol Execution. A protocol indicates how participant instances behave in response to signals received from the environment [36]. Intending to break the protocol security, the adversary sends signals to the instances of the participants (oracles) and receives a response according to the rules of the protocol. In fact, the adversary sends queries to oracles, and these queries model the attacker's ability in a real attack. Types of queries include:
• Execute(
• Send(
• Reveal(
• Corrupt(
• Test(
Freshness. An oracle
Semantic Security of A Key Exchange Protocol. Suppose adversary
Theorem 1. Suppose adversary
where
Proof. To prove Theorem 1, we define a six-step game: G0 to G5.
G0. Game 0 is the real attack of
G1. In this game, we simulate passive attacks by the adversary. The adversary eavesdrops on messages between oracles
G2. In this game, in addition to simulating eavesdropping attacks, active attacks are also simulated with the Send query. Active attacks by the adversary can be one of three attacks: replay attack, man-in-the-middle, or impersonation attack. As stated in sections 6.2.1, 6.2.2, and 6.2.4, the proposed method is immune to these attacks. Therefore, the advantage of
G3. In this game, the adversary queries the Hash oracle
G4. This game simulates the smart card loss attack. If the mobile device (or smart card) of the user is stolen,
G5. In this game, the adversary asks the Corrupt query and gets the oracle's long-lived key in response. Of course, to get the session key,
Given that
7 Performance Analysis and Comparison
In this section, we examine the computational complexity of the proposed method. The messages in the proposed protocol are obtained by combining xor, hash, and scalar multiplication on the elliptic curve. In calculating time complexity, we ignore the xor time execution, and we calculate the time required for hash and scalar multiplication based on the time reported in [37]. The computation times of various cryptographic operations, reported by Xu et al. [37], are as follows:
•
•
•
•
The time complexity of our protocol includes the time spent by the user's mobile device and the time spent by the NCC. The time spent by the mobile device is
To measure the communication cost of the proposed method, we need to measure the size of the messages exchanged between the different entities of the protocol. Messages consist of a combination of IDs, hash values, timestamps, and points on the elliptic curve. To calculate the communication cost, suppose each identifier is 64 bits long, the hash size is 256 bits, the timestamp is 64 bits, and the point size on the elliptic curve is 192 bits (due to secp192r1 selection).
To exchange the session key between the user and the NCC, it is necessary to send messages
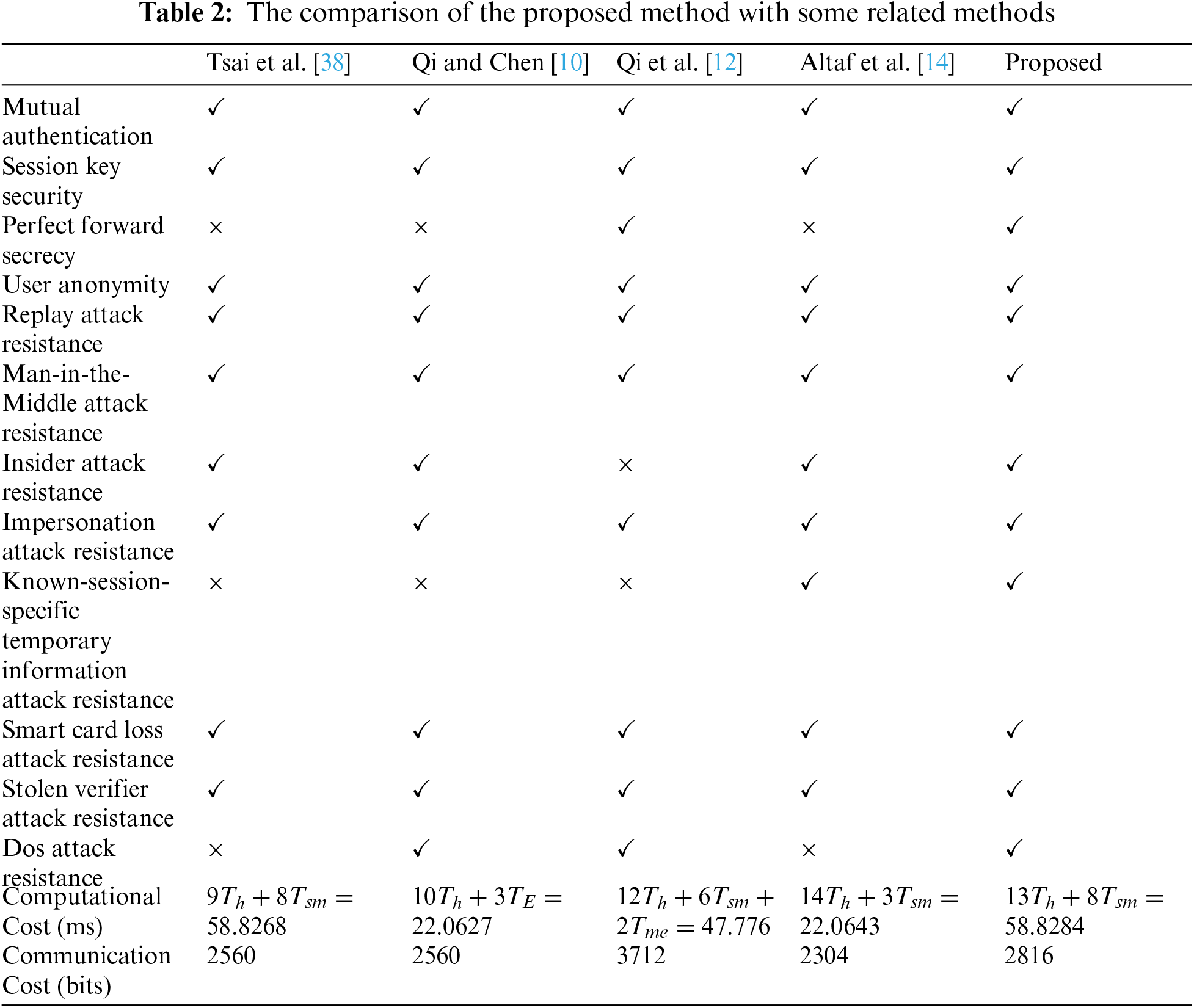
At the end of this section, we compare the proposed method with several similar methods, which are all based on the ECDLP problem, in terms of security features and computational cost. As shown in Tab. 2, Tsai et al.'s protocol [38] does not satisfy perfect forward secrecy. Moreover, it is vulnerable to the known-session-specific temporary information attack and DoS attack. The protocol of Qi and Chen [10] does not meet the perfect forward secrecy and is not resistant against the known-session-specific temporary information attack. The protocol of Qi et al. [12] is vulnerable to insider attack and the known-session-specific temporary information attack. Finally, Altaf et al.'s protocol [14] is vulnerable to DoS attack and does not meet perfect forward secrecy. We see that our method, by spending a little more time, is resistant to the known attacks and meets security requirements. We also see that the communication cost of the proposed method is almost similar to other methods except [12] in which modular exponentiation are used.
This paper contributes towards the widespread deployment of satellite applications by tackling one of the main challenges, i.e., security issues. This paper first analyzed the authentication protocol for satellite communications proposed by Qi et al. and proved its vulnerability to two kinds of security attacks. Then this paper presented a robust secure authentication and key agreement protocol based on elliptic curve cryptography for secure satellite communications. Moreover, a thorough security analysis of the proposed protocol was performed. The security analysis showed that it is resistant to all known attacks. Besides, the formal verification of the proposed method proved that it satisfies the security requirements.
As future work, the protocol performance can be improved in terms of time execution by reducing the number of scalar multipliers while preserving the security requirements. Implementation on application in blockchain [39] and software defined network [40] are also considered as future works.
Funding Statement: The authors received no specific funding for this study.
Conflicts of Interest: The authors declare that they have no conflicts of interest to report regarding the present study.
1. P. Chini, G. Giambene and S. Kota, “A survey on mobile satellite systems,” International Journal of Satellite Communications and Networking, vol. 28, no. 1, pp. 29–57, 2010. [Google Scholar]
2. J. P. Choi and C. Joo, “Challenges for efficient and seamless space-terrestrial heterogeneous networks,” IEEE Communications Magazine, vol. 53, no. 5, pp. 156–162, 2015. [Google Scholar]
3. H. Yao, L. Wang, X. Wang, Z. Lu and Y. Liu, “The space-terrestrial integrated network: an overview,” IEEE Communications Magazine, vol. 56, no. 9, pp. 178–185, 2018. [Google Scholar]
4. X. Zhu, C. Jiang, L. Kuang, N. Ge, S. Guo et al., “Cooperative transmission in integrated terrestrial-satellite networks,” IEEE Network, vol. 33, no. 3, pp. 204–210, 2019. [Google Scholar]
5. K. Shi, X. Zhang, S. Zhang and H. Li, “Time-expanded graph based energy-efficient delay-bounded multicast over satellite networks,” IEEE Transactions on Vehicular Technology, vol. 69, no. 9, pp. 10380–10384, 2020. [Google Scholar]
6. T. T. Reid, P. Walter, D. Enge, H. S. Lawrence, G. Cobb et al., “Navigation from Low earth orbit: Part 1: concept, current capability, and future promise,” Position, Navigation, and Timing Technologies in the 21st Century: Integrated Satellite Navigation, Sensor Systems, and Civil Applications, vol. 2, pp. 1359–1379, 2020. [Google Scholar]
7. J. E. Oros, J. Trejo and A. Salcedo, “Identification, location, and reception of low earth orbit satellites (LEO) signals,” in Proc. of 2015 Int. Conf. on Mechatronics, Electronics and Automotive Engineering (ICMEAE), Cuernavaca, Mexico, pp. 246–250, 2015. [Google Scholar]
8. Z. Katona, M. Gräßlin, A. Donner, N. Kranich, H. Brandt et al., “A flexible LEO satellite modem with Ka-band RF frontend for a data relay satellite system,” International Journal of Satellite Communications and Networking, vol. 38, no. 3, pp. 301–313, 2020. [Google Scholar]
9. I. Altaf, M. A. Saleem, K. Mahmood, S. Kumari, P. Chaudhary et al., “A lightweight key agreement and authentication scheme for satellite-communication systems,” IEEE Access, vol. 8, pp. 46278–46287, 2020. [Google Scholar]
10. M. Qi and J. Chen, “An enhanced authentication with key agreement scheme for satellite communication systems,” International Journal of Satellite Communications and Networking, vol. 36, no. 3, pp. 296–304, 2018. [Google Scholar]
11. A. Ostad-Sharif, D. Abbasinezhad-Mood and M. Nikooghadam, “Efficient utilization of elliptic curve cryptography in design of a three-factor authentication protocol for satellite communications,” Computer Communications, vol. 147, pp. 85–97, 2019. [Google Scholar]
12. M. Qi, J. Chen and Y. Chen, “A secure authentication with key agreement scheme using ECC for satellite communication systems,” International Journal of Satellite Communications and Networking, vol. 37, no. 3, pp. 234–244, 2019. [Google Scholar]
13. Y. Chen and J. Chen, “An enhanced dynamic authentication scheme for mobile satellite communication systems,” International Journal of Satellite Communications and Networking, vol. 39, no. 3, pp. 250–262, 2021. [Google Scholar]
14. I. Altaf, M. Arslan Akram, K. Mahmood, S. Kumari, H. Xiong et al., “A novel authentication and key-agreement scheme for satellite communication network,” Transactions on Emerging Telecommunications Technologies, vol. 32, no. 7, pp. e3894, 2020. [Google Scholar]
15. H. Cruickshank, “A security system for satellite networks,” in Proc. of the 5th Int. Conf. on Satellite Systems for Mobile Communications and Navigation, London, UK, pp. 187–190, 1996. [Google Scholar]
16. T. -H. Chen, W. -B. Lee and H. -B. Chen, “A Self-verification authentication mechanism for mobile satellite communication systems,” Computers & Electrical Engineering, vol. 35, no. 1, pp. 41–48, 2009. [Google Scholar]
17. I. Lasc, R. Dojen and T. Coffey, “Countering jamming attacks against an authentication and key agreement protocol for mobile satellite communications,” Computers & Electrical Engineering, vol. 37, no. 2, pp. 160–168, 2011. [Google Scholar]
18. C. C. Chang, T. F. Cheng and H. L. Wu, “An authentication and key agreement protocol for satellite communications,” International Journal of Communication Systems, vol. 27, no. 10, pp. 1994–2006, 2014. [Google Scholar]
19. Y. Zhang, J. Chen and B. Huang, “Security analysis of an authentication and key agreement protocol for satellite communications,” International Journal of Communication Systems, vol. 27, no. 12, pp. 4300–4306, 2014. [Google Scholar]
20. C. C. Lee, C. T. Li and R. X. Chang, “A simple and efficient authentication scheme for mobile satellite communication systems,” International Journal of Satellite Communications and Networking, vol. 30, no. 1, pp. 29–38, 2012. [Google Scholar]
21. Y. Zhang, J. Chen and B. Huang, “An improved authentication scheme for mobile satellite communication systems,” International Journal of Satellite Communications and Networking, vol. 33, no. 2, pp. 135–146, 2015. [Google Scholar]
22. Y. Liu, A. Zhang, S. Li, J. Tang and J. Li, “A lightweight authentication scheme based on self-updating strategy for space information network,” International Journal of Satellite Communications and Networking, vol. 35, no. 3, pp. 231–248, 2017. [Google Scholar]
23. S. A. Hosseini Seno, M. Nikooghadam and R. Budiarto, “An efficient lightweight authentication and key agreement protocol for patient privacy,” Computer Materials & Continua (CMC), vol. 69, no. 3, pp. 3495–3512, 2021. [Google Scholar]
24. Y. Chen and J. -S. Chou, “ECC-Based untraceable authentication for large-scale active-tag RFID systems,” Electronic Commerce Research, vol. 15, no. 1, pp. 97–120, 2015. [Google Scholar]
25. N. Gura, A. Patel, A. Wander, H. Eberle and S. C. Shantz, “Comparing elliptic curve cryptography and RSA on 8-bit CPUs,” in Proc. of the 6th Int. Workshop Cambridge, Massachusetts, USA, pp. 119–132, 2004. [Google Scholar]
26. D. Dolev and A. Yao, “On the security of public key protocols,” IEEE Transactions on Information Theory, vol. 29, no. 2, pp. 198–208, 1983. [Google Scholar]
27. R. Ramanujam, V. Sundararajan and S. Suresh, “Extending dolev-yao with assertions,” in Proc. of the tenth Int. Conf. on Information Systems Security, Hyderabad, India, pp. 50–68, 2014. [Google Scholar]
28. R. Canetti and H. Krawczyk, “Analysis of key-exchange protocols and their use for building secure channels,” in Proc. of Int. Conf. on the Theory and Applications of Cryptographic Techniques, Innsbruck, Austria, pp. 453–474, 2001. [Google Scholar]
29. A. Armando, D. Basin, Y. Boichut, Y. Chevalier, L. Compagna et al., “The AVISPA tool for the automated validation of internet security protocols and applications,” in Proc. of the 17th Int. Conf. on Computer Aided Verification, Edinburgh, Scotland, UK, pp. 281–285, 2005. [Google Scholar]
30. D. Von Oheimb, “The high-level protocol specification language HLPSL developed in the EU project AVISPA,” in Proc. of the 3rd Int. Workshop on Applied Semantics (APPSEM 2005), Frauenchiemsee, Germany, pp. 1–17, 2005. [Google Scholar]
31. D. Basin, S. Mödersheim and L. Vigano, “OFMC: A symbolic model checker for security protocols,” International Journal of Information Security, vol. 4, no. 3, pp. 181–208, 2005. [Google Scholar]
32. M. Turuani, “The CL-atse protocol analyser,” in Proc. of the 17th Int. Conf. on Rewriting Techniques and Applications, Seattle, WA, USA, pp. 277–286, 2006. [Google Scholar]
33. A. Armando and L. Compagna, “SATMC: A SAT-based model checker for security protocols,” in Proc. of the 9th European Workshop on Logics in Artificial Intelligence, Lisbon, Portugal, pp. 730–733, 2004. [Google Scholar]
34. M. Bellare, D. Pointcheval and P. Rogaway, “Authenticated key exchange secure against dictionary attacks,” in Proc. of Int. Conf. on the Theory and Applications of Cryptographic Techniques, Bruges, Belgium, pp. 139–155, 2000. [Google Scholar]
35. M. Abdalla, E. Bresson, O. Chevassut and D. Pointcheval, “Password-based group key exchange in a constant number of rounds,” in Proc. of the 9th Int. Workshop on Public Key Cryptography, New York, USA, pp. 427–442, 2006. [Google Scholar]
36. C. -C. Chang and H. -D. Le, “A provably secure, efficient, and flexible authentication scheme for ad hoc wireless sensor networks,” IEEE Transactions on Wireless Communications, vol. 15, no. 1, pp. 357–366, 2015. [Google Scholar]
37. L. Xu and F. Wu, “Cryptanalysis and improvement of a user authentication scheme preserving uniqueness and anonymity for connected health care,” Journal of Medical Systems, vol. 39, no. 2, pp. 1–9, 2015. [Google Scholar]
38. J. L. Tsai, N. W. Lo and T. C. Wu, “Secure anonymous authentication scheme without verification table for mobile satellite communication systems,” International Journal of Satellite Communications and Networking, vol. 32, no. 5, pp. 443–452, 2014. [Google Scholar]
39. F. A. Susilo and Y. S. Triana, “Digital supply chain development in blockchain technology using rijndael algorithm 256,” in Int. Conf. on Design, Engineering and Computer Sciences, IOP Conf. Series: Materials Science and Engineering, vol. 453 pp. 012075–012080, 2018. [Google Scholar]
40. A. A. Seyedkolaei, S. A. Hosseini-Seno, A. Moradi and R. Budiarto, “Cost-effective survivable controller placement in software-defined networks,” IEEE Access, vol. 9, pp. 129130–129140, 2021. [Google Scholar]
 | This work is licensed under a Creative Commons Attribution 4.0 International License, which permits unrestricted use, distribution, and reproduction in any medium, provided the original work is properly cited. |