DOI:10.32604/cmc.2022.023685

| Computers, Materials & Continua DOI:10.32604/cmc.2022.023685 |  |
| Article |
Text Encryption Using Pell Sequence and Elliptic Curves with Provable Security
1Department of Mathematics, Quaid-i-Azam University, Islamabad, 45320, Pakistan
2Department of Applied Mathematics and Physics, Graduate School of Informatics, Kyoto University, Kyoto, 606-8501, Japan
*Corresponding Author: Naveed Ahmed Azam. Email: azam@amp.i.kyoto-u.ac.jp
Received: 17 September 2021; Accepted: 11 November 2021
Abstract: The demand for data security schemes has increased with the significant advancement in the field of computation and communication networks. We propose a novel three-step text encryption scheme that has provable security against computation attacks such as key attack and statistical attack. The proposed scheme is based on the Pell sequence and elliptic curves, where at the first step the plain text is diffused to get a meaningless plain text by applying a cyclic shift on the symbol set. In the second step, we hide the elements of the diffused plain text from the attackers. For this purpose, we use the Pell sequence, a weight function, and a binary sequence to encode each element of the diffused plain text into real numbers. The encoded diffused plain text is then confused by generating permutations over elliptic curves in the third step. We show that the proposed scheme has provable security against key sensitivity attack and statistical attacks. Furthermore, the proposed scheme is secure against key spacing attack, ciphertext only attack, and known-plaintext attack. Compared to some of the existing text encryption schemes, the proposed scheme is highly secure against modern cryptanalysis.
Keywords: Text encryption; pell numbers; elliptic curves; key sensitivity; statistical cryptanalysis
There is a high demand for data security schemes due to the recent advancement in the fields of computation and communication technologies. Cryptography and steganography are the two main branches of data security schemes. Cryptography is the study of data security schemes where secret data is transformed into an unreadable data [1]. Steganography is the study of data security schemes where secret data is embedded into host data so that the attackers cannot detect the existence of secret data [2].
Different data security schemes have been proposed based on different mathematical structures such as elliptic curves [3–9], algebraic structures [10–15], chaotic maps [16–21] and fuzzy set theory [22,23]. Security and privacy of the text messages are major concerns of the users while communicating on popular messaging platforms such as WhatsApp and Signal. So, the security of the text messages gained great attention now a days. We briefly review some of the recent text encryption schemes. Abdullah et al. [23] proposed a cryptosystem based on fuzzy logic where triangular fuzzy numbers are used to represent plain text and ciphertext. Gupta et al. [24] proposed a data security algorithm based on logical and shifting operations. Pattanayak et al. [25] used linear congruences and extended Euclidean algorithm to design a text encryption scheme. By utilizing 8-bit code values of alphabets, Agrawal et al. [26] proposed an efficient algorithm for text encryption. Ghrare et al. [27] designed a hidden encrypted symmetric key algorithm by hiding the secret key inside the ciphertext. Linear recurrences such as generalized Fibonacci numbers, Pell numbers and Pell-Lucas numbers have many applications in the field of mathematics and computer science [28–30]. The schemes in [31–33] used linear recurrences for cryptography purpose. Luma et al. [31] explored a relationship between Fibonacci and Lucas sequence and used it for encryption and decryption purpose. Overmars et al. [32] proposed an efficient method to compute the golden ratio to avoid cryptographic breaches. Agarwal et al. [33] proposed a data encryption scheme based on Fibonacci numbers. Recently, DNA sequences are also used to generate secret keys for data security [34–36]. Clelland et al. [34] combined a DNA based technique and the microdot to send messages secretly. Abbasy et al. [36] employed useful features of DNA sequences for data hiding. Chaotic maps are used to develop new security schemes due to their high sensitivity to the initial condition [37–42]. Murillo-Escobar et al. [37] proposed a new text encryption scheme based on a logistic map. Similarly, elliptic curves (ECs) received great attention in the field of cryptography for image encryption [43–47], text encryption [48–53] and signcryption [54–56] due to comparable security against modern cryptanalysis with low key size. Sunneetha et al. [48] proposed a secure algorithm using elliptic curves and algebraic operations to transmit messages. Naji et al. [49] proposed a novel text encryption scheme by representing characters of the plain text with the affine points on an EC. Agrawal et al. [50] designed a text encryption method using ECC and Hill cipher with better security and complexity. Keerthi et al. [51] proposed a novel text encryption scheme where the hexadecimal form of the ASCII values of plain text are mapped to affine points of an ECs. Kumar et al. [52] used paired ASCII values corresponding to the plain text as an input for the elliptic curve. Singh and Singh developed an algorithm that can be used for encryption and decryption of any size of text message with given ASCII values. Ullah et al. [54] provided a critical review of hyper elliptic curves based signcryption algorithms. A hyper elliptic curve based signcryption scheme more suitable for emerging resource constraints environment is proposed by Ullah et al. [56].
Most of the text encryption schemes available in the literature such as the schemes presented in [23–27,33,34,36,37,48–51,53] are not secure against well know attacks including key spacing, key sensitivity, statistical attack, ciphertext only attack and known-plaintext attack. The aim of this paper is to propose a novel text encryption scheme that has high security against modern cryptanalysis including key spacing, key sensitivity, statistical attack, ciphertext only attack and known-plaintext attack as compared to the existing text encryption schemes [23–27,33,34,36,37,48–51,53]. The proposed scheme is based on the Pell sequence and elliptic curves and has three main steps, where we first diffuse the plain text. Then an encoding procedure is applied to the diffused plain text based on the Pell sequence instep 2. Finally, the encoded diffused plain text is confusedin step 3 based on ECs. The rest of the paper is organized as follows. Section 2 contains some preliminaries. We discuss a novel text encryption scheme in Section 3. Security analysis and a detailed comparison of the proposed scheme with the existing text encryption schemes [23–27,33,34,36,37,48–51,53] is discussed in Section 4. A conclusion is drawn in Section 5.
For initial values
The first six terms of the Pell sequence are 0, 1, 2, 5, 12, and 29. By [30] it is known that for
For a finite prime field
where
By [57], when
The key features of these orderings are: (i) they diffuse the y-coordinates of the ordered EC; and (ii) the ordered ECs generated by these orderings are highly uncorrelated. Furthermore, it can be observed from Fig. 1 that the three orderings are non-equivalent and are capable of generating randomness. Due to these properties, Azam et al. [4,5] showed that these orderings are cryptographically suitable for generating a large number of secure permutations over ECs.
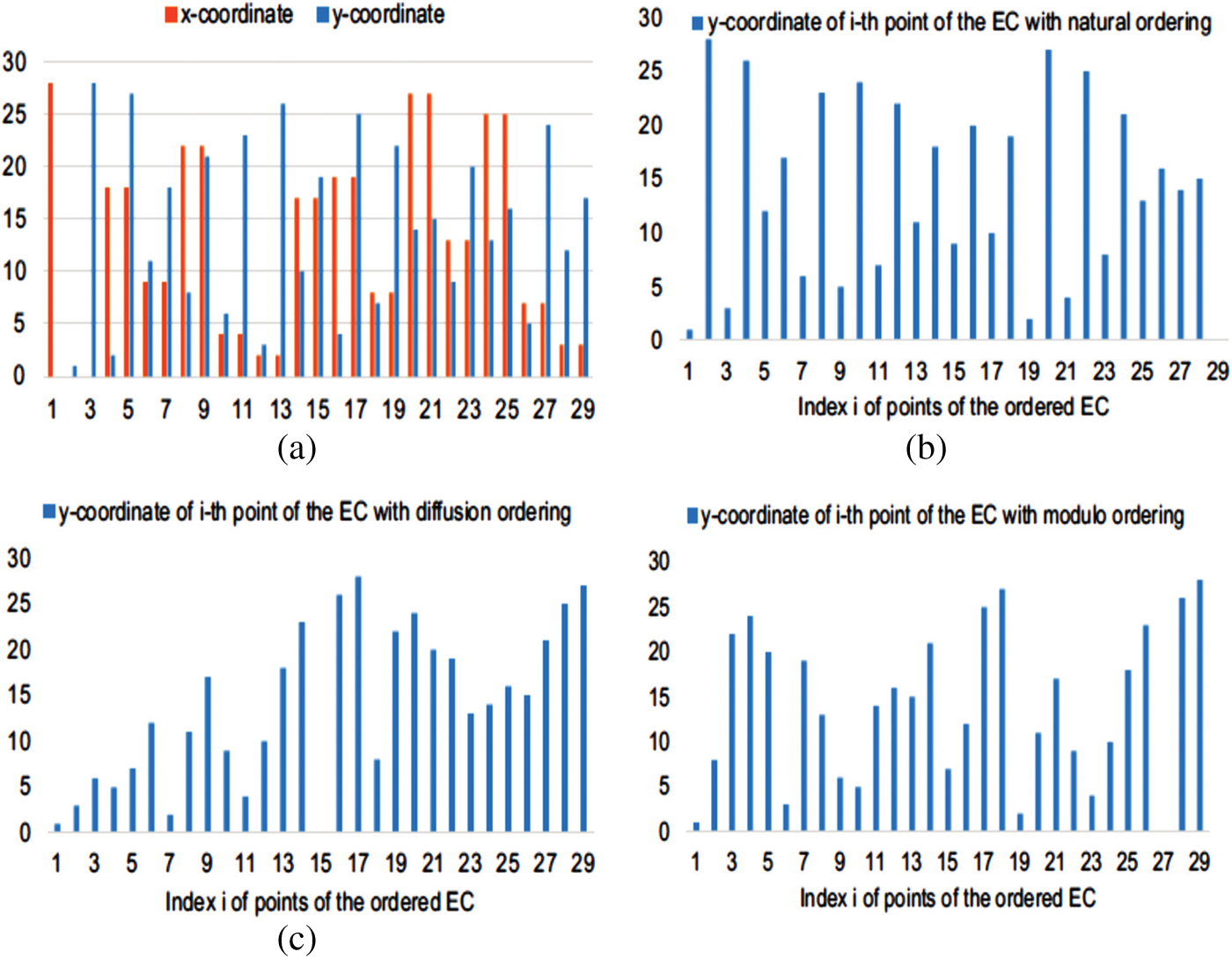
Figure 1: EC E29,0,1 and the effect of the natural, diffusion and modulo ordering on the EC E29,0,1: (a) Points of the EC E29,0,1 are shown w.r.t. non-decreasing x-coordinate from left to right; (b) y-coordinates of the points of the ordered EC E29,0,1 with natural ordering; (c) y-coordinates of the points of the ordered EC E29,0,1 with diffusion ordering; (d) y-coordinates of the points of the ordered EC E29,0,1 with modulo ordering
For an encryption scheme, it is essential to diffuse and confuse the plain text up to a certain level [2]. Therefore, our scheme consists of three main steps where we first diffuse the plain text followed by an encoding procedure and then create confusion in the encoded diffused plain text. The diffusion step is performed by permuting the symbol set of the plain text. We use a restricted Pell sequence, a weight function, and a binary sequence to encode each element and its position in the diffused plain text with real numbers. Due to the sensitivity of the ECs over its parameters, we generate permutations over ECs to create confusion in the encoded diffused plain text. We discuss these three steps in detail below.
Let S be a finite symbol set of size m, and for
Step 1. Diffuse plain text: We select an integer
i.e.,
Step 2. Encode diffused plain text: To encode the elements of the diffused plain text
Select two positive integers h and
-
- all entries of
Observe that the entries of the restricted Pell sequence
Generate a weight function
Generate a binary sequence
Now, generate an encoded diffused plain text
where
Step 3. Confuse encoded plain text: In this step, we create confusion in the encoded plain text
Transmit the confused sequence
The integers
Note that for a given
Assume that the channel between sender and receiver is noiseless, and therefore the receiver receives the ciphertext
for some
of the permutation by using the secret key k. To get the plain text
By repeating the above procedure for each

Figure 2: Flowchart of the proposed encryption and decryption scheme
We demonstrate our proposed encryption and decryption procedures in detail in Example 1.
Let the ordered symbol set S be the set of the capital English alphabet including blank-space and full-stop. This set is listed in the fourth column of Tab. 1. Let

Suppose the sender wants to send the plain text T = STAY SAFE with nine elements. For each integer

To permute the encoded diffused plain text, we generated the ordered ECs
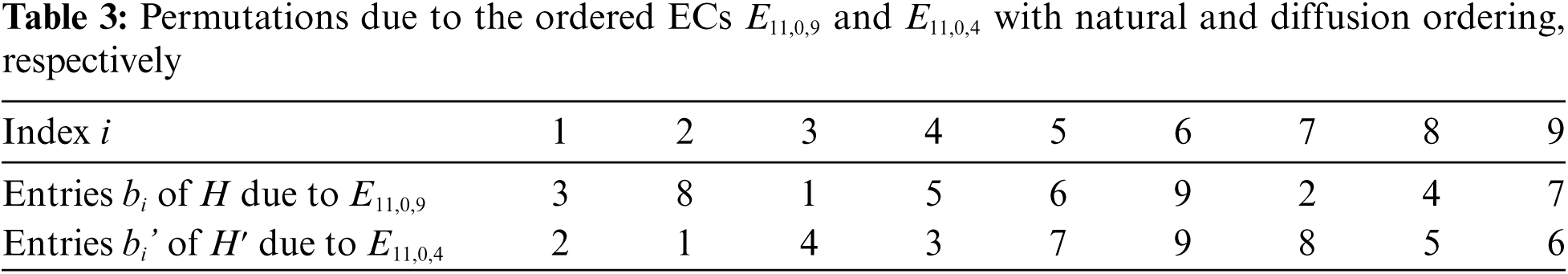
The confused encoded plain text

We demonstrate the decryption procedure for the 5-th element
4 Security Analysis and Comparison
To analyze the security of the proposed scheme, we apply some well-known security tests including key spacing analysis, key sensitivity analysis, histogram test, information entropy analysis, ciphertext only attack and known-plaintext attack. We briefly explain these tests and their results for the proposed scheme in Sections 4.1–4.5. Furthermore, we give a detailed comparison of the security of the proposed scheme and some of the existing text encryption schemes in Section 4.6.
Brute-force attack is commonly used by cryptanalysts to decrypt ciphertext. Key spacing analysis is used to analyze the security of an encryption scheme against brute-force attack. For an encryption scheme, key spacing is defined to be the number of distinct secret keys that it can generate. An encryption scheme is secure if its key spacing is at least
An encryption scheme is secure if it can generate a significantly different ciphertext for the same plaintext when the secret keys are slightly changed. In the next lemma, we show that for any plain text our scheme can generate a different ciphertext when any of the secret keys
Lemma 1. Let T be a plain text of size n over symbol set S of size m and
(i) The ciphertext
(ii) The ciphertext
(iii) If
Proof. Let
(i) The integer
(ii) For any integer
(iii) Since
By Lemma 1, our scheme is highly sensitive to the secret keys

An encryption scheme is highly secure against statistical attacks if it can generate a highly random ciphertext. Histogram analysis and entropy analysis are the two commonly used tests to analyze the security of a scheme against statistical attacks. A scheme is secure against statistical attacks if it can generate ciphertexts with uniform histogram and optimal entropy.
Let X be a data set over a symbol set
In the following result, we show that for each plain text, our scheme can generate a ciphertext with a uniform histogram and optimal entropy.
Lemma 2. For any plaint text, there exists at least one weight function
Proof. Let T be a plain text of size n over a symbol set S and
By Lemma 2, it follows that for each plain text, the proposed scheme can generate a ciphertext with uniform histogram and optimal entropy by using the weight function w constructed in Lemma 2 and

In ciphertext only attack, the cryptanalyst has access to some ciphertexts and try to get secret keys and hence the plain text. The cryptanalyst cannot reveal the plain text without the secret keys of the proposed scheme. Furthermore, there are at least
In this attack, the attacker knows a pair of plain text and ciphertext and tries to generate secret keys. In our scheme, the attacker tries to generate
The proposed scheme has five secret keys, the three integers
We compared the security strength of the proposed scheme when

The schemes in [49] and [53] do not have provable security against key sensitivity attack and statistical attack. By Sections 4.2 and 4.3, the proposed scheme has high security against key sensitivity and statistical attacks as compared to the security of the schemes in [49] and [53].
We proposed a secure text encryption scheme. The scheme has three main steps, where we first diffuse the plain text by permuting the symbol set to convert the plain text into a meaningless message. In the second step, the diffused plain text is encoded with real numbers based on the Pell sequence, a weight function, and a binary sequence to hide the diffused plain text. In the third step, the scheme creates confusion in the encoded diffused plain text by generating permutations over ECs. We analyzed the security of the proposed scheme against several modern attacks including key spacing attack, key sensitivity attack, statistical attacks, ciphertext only attack and known-plaintext attack. From the analysis it is clear that the proposed scheme has high resistance against modern attacks. Furthermore, we compared the security strength of the proposed scheme with the existing text encryption schemes in [23–27,33,34,36,37,48–51,53]. It is evident from the comparison that the proposed scheme is more secure as compared to the existing scheme against modern cryptanalysis.
By this scheme, we gave an application of the Pell sequence and ordered ECs in cryptography. In this scheme, we used binary sequence and weight function, which can be generated by any available method.
An interesting future direction would be to generate binary sequence and weight function by using ordered EC and propose an encryption scheme that can provide provable confidentiality and integrity.
Funding Statement: This research is funded through JSPS KAKENHI Grant Number 18J23484, QAU- URF 2015 and HEC project NRPU-7433.
Conflicts of Interest: The authors declare that they have no conflicts of interest to report regarding the present study.
1. C. G. Kessler, An Overview of Cryptography, 2010. [Online]. Available: http://www.garykessler.net/library/crypto.html. [Google Scholar]
2. C. E. Shannon, “Communication theory of secrecy systems,” The Bell System Technical Journal, vol. 28, no. 4, pp. 656–715, 1949. [Google Scholar]
3. U. Hayat and N. A. Azam, “A novel image encryption scheme based on an elliptic curve,” Signal Processing, vol. 155, pp. 391–402, 2019. [Google Scholar]
4. N. A. Azam, U. Hayat and I. Ullah, “Efficient construction of a substitution box based on a Mordell elliptic curve over a finite field,” Frontiers of Information Technology and Electronic Engineering, vol. 20, no. 10, pp. 1378–1389, 2019. [Google Scholar]
5. N. A. Azam, U. Hayat and I. Ullah, “An injective S-box design scheme over an ordered isomorphic elliptic curve and its characterization,” Security and Communication Networks, vol. 2018, Article ID 3421725, 9 pages, 2018. [Google Scholar]
6. U. Hayat, N. A. Azam and M. Asif, “A method of generating 8 x 8 substitution boxes based on elliptic curves,” Wireless Personal Communications, vol. 101, no. 1, pp. 439–451, 2018. [Google Scholar]
7. A. A. Khan, V. Kumar and M. Ahmad, “An elliptic curve cryptography based mutual authentication scheme for smart grid communications using biometric approach,” Journal of King Saud University-Computer and Information Sciences, 2019. https://doi.org/10.1016/j.jksuci.2019.04.013. [Google Scholar]
8. V. Kumar, M. Ahmad, A. Kumari, S. Kumari and M. K. Khan, “SEBAP: A secure and efficient biometric-assisted authentication protocol using ECC for vehicular cloud computing,” International Journal of Communication Systems, vol. 34, no. 2, pp. 4103, 2019. [Google Scholar]
9. Z. E. Dawahdeh, S. N. Yaakob and R. R. B. Othman, “A new image encryption technique combining elliptic curve cryptosystem with hill cipher,” Journal of King Saud University-Computer and Information Sciences, vol. 30, no. 3, pp. 349355, 2018. [Google Scholar]
10. A. Razaq, H. Alolaiyan, M. Ahmad, M. A. Yousaf, U. Shuaib et al., “A novel method for generation of strong substitution-boxes based on coset graphs and symmetric groups,” in IEEE Access, vol. 8, pp. 75473–75490, 2020. [Google Scholar]
11. M. A. Yousaf, H. Alolaiyan, M. Ahmad, M. Dilbar and A. Razaq, “Comparison of pre and post-action of a finite abelian group over certain nonlinear schemes,” IEEE Access, vol. 8, pp. 39781–39792, 2020. [Google Scholar]
12. M. Khan and N. A. Azam, “Right translated AES gray S-boxes,” Security and Communication Networks, vol. 8, no. 9, pp. 1627–1635, 2015. [Google Scholar]
13. M. Khan and N. A. Azam, “S-boxes based on affine mapping and orbit of power function,” 3D Research, vol. 6, no. 2, pp. 12, 2015. [Google Scholar]
14. Ö. Koruoğlu and R. Sahin, “Generalized fibonacci sequences related to the extended hecke groups and an application to the extended modular group,” Turkish Journal of Mathematics, vol. 34, no. 3, pp. 325–332, 2010. [Google Scholar]
15. S. Ullah, L. Zhang, M. W. Sardar and M. T. Hussain, “Τ-Access policy: Attribute-based encryption scheme for social network based data trading,” China Communications, vol. 18, no. 8, pp. 183–198, 2021. [Google Scholar]
16. Z. Hua, S. Yi and Y. Zhou, “Medical image encryption using high-speed scrambling and pixel adaptive diffusion,” Signal Processing, vol. 144, pp. 134–144, 2018. [Google Scholar]
17. O. Vilardy, M. Juan, J. Barba, M. Torres and O. Cesar, “Image encryption and decryption systems using the jigsaw transform and the iterative finite field cosine transform,” Photonics, vol. 6, no. 4, pp. 121, 2019. [Google Scholar]
18. D. Lambić, A. Janković and M. Ahmad, “Security analysis of the efficient chaos pseudo-random number generator applied to video encryption,” Journal of Electronic Testing, vol. 36, no. 4, pp. 709–715, 2018. [Google Scholar]
19. H. A. Ahmed, M. F. Zolkipli and M. Ahmad, “A novel efficient substitution-box design based on firefly algorithm and discrete chaotic map,” Neural Computing and Applications, vol. 31, no. 11, pp. 7201–7210, 2019. [Google Scholar]
20. M. Ahmad, S. Khurana, S. Singh and H. D. AlSharari, “A simple secure hash function scheme using multiple chaotic maps,” 3D Research, vol. 8, no. 28, pp. 13, 2017. [Google Scholar]
21. M. Ahmad, M. N. Doja and M. M. S. Beg, “Security analysis and enhancements of an image cryptosystem based on hyperchaotic system,” Journal of King Saud University-Computer and Information Sciences, vol. 33, no. 1, pp. 77–85, 2021. [Google Scholar]
22. N. A. Azam, “A novel fuzzy encryption technique based on multiple right translated AES Gray S-boxes and phase embedding,” Security and Communication Networks, vol. 2017, Article ID 5790189, 9 pages, 2017. [Google Scholar]
23. K. Abdullah, S. A. Bakar, N. H. Kamis and H. Aliamis, “RSA cryptosystem with fuzzy set theory for encryption and decryption,” in AIP Conference Proceedings, vol. 1905, no. 1, pp. 030001, 2017. [Google Scholar]
24. V. Gupta, G. Singh and R. Gupta, “Advance cryptography algorithm for improving data security,” International Journal of Advanced Research in Computer Science and Software Engineering, vol. 2, no. 1, pp. 1–6, 2012. [Google Scholar]
25. S. Pattanayak and D. Dey, “Text encryption and decryption with extended Euclidean algorithm and combining the features of linear congruence generator,” International Journal of Development Research, vol. 6, no. 7, pp. 8753–8756, 2016. [Google Scholar]
26. E. Agrawal and P. R. Pal, “A secure and fast approach for encryption and decryption of message communication,” International Journal of Engineering Science, vol. 7, no. 5, pp. 11481, 2017. [Google Scholar]
27. S. E. Ghrare, H. A. Barghi and N. R. Madi, “New text encryption method based on hidden encrypted symmetric key,” in Int. Conf., Advanced Computer Information Technologies, Ceske Budejovice, Czech Republic, 2018. [Google Scholar]
28. Q. Mushtaq and U. Hayat, “Horadam generalized Fibonacci numbers and the modular group,” Indian Journal of Pure and Applied Mathematics, vol. 38, no. 5, pp. 345, 2007. [Google Scholar]
29. Q. Mushtaq and U. Hayat, “Pell numbers, Pell-Lucas numbers and modular group,” Algebra Colloquium, Academy of Mathematics and Systems Science, Chinese Academy of Sciences, and Suzhou University, vol. 14, no. 1, pp. 97–102, 2007. [Google Scholar]
30. T. Koshy, Pell and Pell-Lucas Numbers with Applications, New York: Springer, 2014. [Google Scholar]
31. A. Luma and B. Raufi, “Relationship between fibonacci and lucas sequences and their application in symmetric cryptosystems,” in Proc. of the 4th Int. Conf. on Circuits, Systems and Signals, World Scientific and Engineering Academy and Society (WSEAS), Corfu Island, Greece, pp. 146–150, 2010. [Google Scholar]
32. A. Overmars and S. Venkatraman, “An efficient golden ratio method for secure cryptographic applications,” Mathematical and Computational Applications, vol. 23, no. 4, pp. 58, 2018. [Google Scholar]
33. P. Agarwal, N. Agarwal and R. Saxena, “Data encryption through fibonacci sequence and unicode characters,” MIT International Journal of Computer Science and Information Technology, vol. 5, no. 2, pp. 79–82, 2015. [Google Scholar]
34. T. Clelland, V. Risca and C. Bancroft, “Hiding messages in DNA microdots,” Nature, vol. 399, no. 6736, pp. 533–534, 1999. [Google Scholar]
35. M. Borda and O. Tornea, “DNA secret writing techniques,” in 2010 8th Int. Conf. on Communications IEEE, Bucharest, Romania, pp. 451–456, 2010. [Google Scholar]
36. M. R. Abbasy, A. A. Manaf and M. A. Shahidan, “Data hiding method based on DNA basic characteristics,” in Int. Conf. on Digital Enterprise and Information Systems, Springer, Berlin, Heidelberg, pp. 53–62, 2011. [Google Scholar]
37. M. A. Murillo-Escobar, F. Abundiz-Prez, C. Cruz-Hernndez and R. M. Lpez-Gutirrez, “A novel symmetric text encryption algorithm based on logistic map,” in Proc. of the Int. Conf. on Communications, Signal Processing and Computers, Honolulu, Hawaii, USA, vol. 4953, 2014. [Google Scholar]
38. H. Perez-Meana, E. Hernandez-Diaz and V. Silva-Garcia, “Encryption of RGB images by means of a novel cryptosystem using elliptic curves and chaos,” IEEE Latin America Transactions, vol. 18, no. 8, pp. 1407–1415, 2020. [Google Scholar]
39. I. Hussain, N. A. Azam and T. Shah, “Stego optical encryption based on chaotic S-box transformation,” Optics and Laser Technology, vol. 61, pp. 50–56, 2014. [Google Scholar]
40. M. Ahmad and M. S. Alam, “A new algorithm of encryption and decryption of images using chaotic mapping,” International Journal on Computer Science and Engineering, vol. 2, no. 1, pp. 46–50, 2009. [Google Scholar]
41. X. Zhang, Y. Mao and Z. Zhao, “An efficient chaotic image encryption based on alternate circular S-boxes,” Nonlinear Dynamics, vol. 78, no. 1, pp. 359–369, 2014. [Google Scholar]
42. M. Ahmad, M. N. Doja and M. M. S. Beg, “Security analysis and enhancements of an image cryptosystem based on hyperchaotic system,” Journal of King Saud University-Computer and Information Sciences, vol. 33, no. 1, pp. 77–85, 2021. [Google Scholar]
43. A. A. A. El-Latif and X. Niu, “A hybrid chaotic system and cyclic elliptic curve for image encryption,” AEU-International Journal of Electronics and Communications, vol. 67, no. 2, pp. 136–143, 2013. [Google Scholar]
44. R. I. Abdelfatah, “Secure image transmission using chaotic-enhanced elliptic curve cryptography,” IEEE Access, vol. 8, pp. 3875–3890, 2019. [Google Scholar]
45. I. Ullah, U. Hayat and M. D. Bustamante, “Image encryption using elliptic curves and Rossby/drift wave triads,” Entropy, vol. 22, no. 4, pp. 454, 2020. [Google Scholar]
46. S. Toughi, M. H. Fathi and Y. A. Sekhavat, “An image encryption scheme based on elliptic curve pseudo random and advanced encryption system,” Signal Processing, vol. 141, pp. 217–227, 2017. [Google Scholar]
47. L. D. Singh and K. M. Singh, “Image encryption using elliptic curve cryptography,” Procedia Computer Science, vol. 54, pp. 472–481, 2015. [Google Scholar]
48. C. H. Suneetha, T. Surendra and C. H. Neelima, “Implementation of double fold text encryption based on elliptic curve cryptography (ECC) with digital signature,” International Journal of Recent Technology and Engineering (IJRTE), vol. 8, no. 5, pp. 3840–3846, 2020. [Google Scholar]
49. M. A. Naji, D. A. Hammood, H. A. Atee, R. S. Jebur, H. A. Rahim et al., “Cryptanalysis cipher text using new modeling: text encryption using elliptic curve cryptography,” in AIP Conf. Proc., Putrajaya, Malaysia, vol. 2203, no. 1, pp. 020003, 2020. [Google Scholar]
50. K. Agrawal and A. Gera, “Elliptic curve cryptography with hill cipher generation for secure text cryptosystem,” International Journal of Computer Applications, vol. 106, no. 1, pp. 18–24, 2014. [Google Scholar]
51. K. Keerthi and B. Surendiran, “Elliptic curve cryptography for secured text encryption,” in Int. Conf. on Circuit, Power and Computing Technologies (ICCPCT), Kollam, India, IEEE, pp. 1–5, 2017. [Google Scholar]
52. A. Kumar, S. S. Tyagi, M. Rana, N. Aggarwal and P. Bhadana, “A comparative study of public key cryptosystem based on ECC and RSA,” International Journal on Computer Science and Engineering, vol. 3, no. 5, pp. 1904–1909, 2011. [Google Scholar]
53. L. D. Singh and K. M. Singh, “Implementation of text encryption using elliptic curve cryptography,” Procedia Computer Science, vol. 54, pp. 73–82, 2015. [Google Scholar]
54. S. Ullah, X. Li and L. Zhang, “A review of signcryption schemes based on hyper elliptic curve,” in 3rd Int. Conf. on Big Data Computing and Communications (BIGCOM), Chengdu, China, pp. 51–58, 2017. [Google Scholar]
55. S. Ullah, X. Y. Li and Z. Lan, “A novel trusted third party based signcryption scheme,” Multimedia Tools and Applications, vol. 79, pp. 22749–22769, 2020. [Google Scholar]
56. S. Ullah and N. Din, “Blind signcryption scheme based on hyper elliptic curves cryptosystem,” Peer-to-Peer Networking and Applications, vol. 14, no. 2, pp. 917–932, 2021. [Google Scholar]
57. L. C. Washington, Elliptic Curves: Number Theory and Cryptography, New York: CRC Press, 2008. [Online]. Available: https://https://doi.org/10.1201/9781420071474. [Google Scholar]
58. Keith M. Martin, Everyday Cryptography: Fundamental Principles and Applications, Oxford University Press, 2012. [Google Scholar]
59. S. M. Seyedzadeh, B. Norouzi, M. R. Mosavi and S. Mirzakuchaki, “A novel color image encryption algorithm based on spatial permutation and quantum chaotic map,” Nonlinear Dynamics, vol. 81, no. 1–2, pp. 511–529, 2015. [Google Scholar]
 | This work is licensed under a Creative Commons Attribution 4.0 International License, which permits unrestricted use, distribution, and reproduction in any medium, provided the original work is properly cited. |