DOI:10.32604/cmc.2022.022759

| Computers, Materials & Continua DOI:10.32604/cmc.2022.022759 |  |
| Article |
A Provably Secure and Efficient Remote Password Authentication Scheme Using Smart Cards
1Department of Mathematical Sciences, Faculty of Science and Technology, Universiti Kebangsaan Malaysia, UKM Bangi, 43600, Selangor, Malaysia
2Department of Mathematics, Faculty of Computer and Mathematical Sciences, Universiti Teknologi MARA Pahang, Raub Campus, Raub, 27600, Pahang, Malaysia
*Corresponding Author: Eddie Shahril Ismail. Email: esbi@ukm.edu.my
Received: 18 August 2021; Accepted: 06 December 2021
Abstract: Communication technology has advanced dramatically amid the 21st century, increasing the security risk in safeguarding sensitive information. The remote password authentication (RPA) scheme is the simplest cryptosystem that serves as the first line of defence against unauthorised entity attacks. Although the literature contains numerous RPA schemes, to the best of the authors’ knowledge, only few schemes based on the integer factorisation problem (IFP) and the discrete logarithm problem (DLP) that provided a provision for session key agreement to ensure proper mutual authentication. Furthermore, none of the previous schemes provided formal security proof using the random oracle model. Therefore, this study proposed an improved RPA scheme with session key establishment between user and server. The design of the proposed RPA scheme is based on the widely established Dolev-Yao adversary model. Moreover, as the main contribution, a novel formal security analysis based on formal definitions of IFP and DLP under the random oracle model was presented. The proposed scheme's performance was compared to that of other similar competitive schemes in terms of the transmission/computational cost and time complexity. The findings revealed that the proposed scheme required higher memory storage costs in smart cards. Nonetheless, the proposed scheme is more efficient regarding the transmission cost of login and response messages and the total time complexity compared to other scheme of similar security attributes. Overall, the proposed scheme outperformed the other RPA schemes based on IFP and DLP. Finally, the potential application of converting the RPA scheme to a user identification (UI) scheme is considered for future work. Since RPA and UI schemes are similar, the proposed approach can be expanded to develop a provably secure and efficient UI scheme based on IFP and DLP.
Keywords: Authentication scheme; discrete logarithm; factorisation; password; provable security
In the 21st century, anything is possible on the internet by using applications and services, like operational networks, databases, banking services, and e-commerce, that are available to anyone, anywhere. Although users can enjoy access to the services remotely, the convenience offered is not without a cost. The communication between users and service providers often involves sensitive data dan messages being transmitted through insecure public channel. Furthermore, communication technology has progressed rapidly, thereby increasing the security risk security to protect private information. The remote password authentication (RPA) scheme is a cryptosystem that allows authorised users access to securely communicate with the service providers. Therefore, the RPA scheme serves as the first line of defence against dangerous security threats.
In 1999, Yang et al. [1] proposed two RPA schemes with smart cards, using timestamp and nonce (random number used once). The schemes adopted the concept of an ID-based signature scheme by Shamir [2] without the need to maintain a password verification table. Furthermore, the schemes enabled users to easily select their passwords and demonstrated resistance to replay and forged login attacks. The schemes’ security foundation was grounded on two cryptographic primitives: Integer Factorisation Problem (IFP) and Discrete Logarithm Problem (DLP). Nevertheless, some improved schemes [3–9] have been proposed to overcome the security concerns of Yang et al. [1] scheme while still maintaining the cryptographic primitives of IFP and DLP.
Fig. 1 presents the literature development of RPA schemes based on Yang et al. [1] scheme. The related works are defined as studies that have proposed improvements of RPA schemes and maintained the security foundation of IFP and DLP. These works are selected from the lists of citations and references of the previous studies. As an example, from Fig. 1, the enhancement scheme proposed by Shen et al. [4] was designed based on cryptanalysis of Yang et al. [1] scheme.
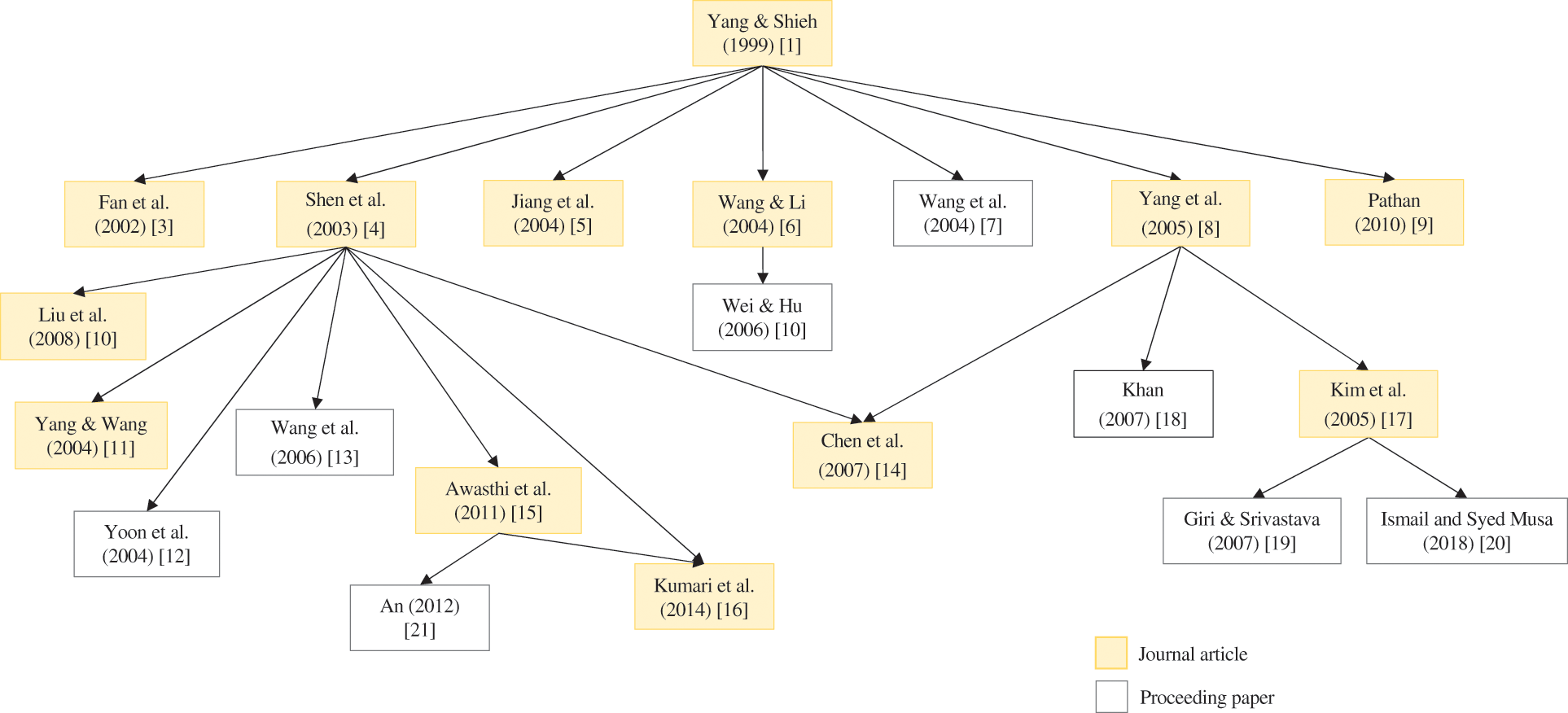
Figure 1: Development of RPA schemes based on Yang et al. [1] scheme using two cryptographic primitives (IFP and DLP)
Shen et al. [4] provided one of the most significant enhancements to scheme by Yang et al. [1], arguing that adversaries could exploit users’ sensitive data through fake servers. As a result, the problem was rectified by incorporating mutual authentication between user and server. Nevertheless, the scheme was shown to be vulnerable to existing and novel security attacks, such as replay, secret-key guessing, and forgery attacks [10–13]. From there, numerous modifications [10–16] have been proposed. These studies reported their schemes to be more practical and efficient than earlier comparable schemes while maintaining a security basis of similar cryptographic primitives (i.e., IFP and DLP) during mutual authentication. Notably, Liu et al. [10] developed a novel nonce-based RPA scheme that could prevent forged login without incurring additional computational cost on the smart card.
Another notable contribution is the improved scheme by Yang et al. [8], which could withstand forgery, password-guessing, smart card loss, and replay attacks. Subsequently, Kim et al. [17] demonstrated that Yang et al. [8] scheme could not withstand previous forgery attacks. Later, Khan [18] demonstrated the vulnerabilities in [8] and presented an enhanced scheme with mutual authentication to address the problem. Nevertheless, other studies [19], [20] have shown that Kim et al. [17] is vulnerable to forgery attacks. As a result, Giri et al. [19] proposed a new scheme to resist the forgery attacks, as well as other types of threats, such as password-guessing, smart card loss, and replay attacks. The most recent related study by Ismail et al. [20] presented a new attack and proposed modifications to address the new threats.
Awasthi et al. [15] demonstrated that the scheme by Shen et al. [4] is vulnerable to forged login attacks and presented additional security concerns about the scheme by Liu et al. [10]. Hence, Awasthi et al. [15] proposed an enhanced scheme for resisting forgery attacks with reduced smart card memory storage cost. Unfortunately, the scheme was shown to be vulnerable to impersonation, insider, and password-guessing attacks by An [21], which also suggested improvements to make the scheme more secure to resist all of the mentioned attacks while supporting mutual authentication. Furthermore, Kumari et al. [16] highlighted that scheme proposed by Awasthi et al. [15] could not resist the claimed attacks. Therefore, they recommended a three-factor scheme authentication improvement with the added security of the user's fingerprint.
Kumari et al. [16] proposed the latest RPA scheme construction based on IFP and DLP. The study was the first to introduce a scheme that included a shared session key between the user and the server to eliminate the man-in-the-middle attack, accompanied by the most comprehensive and informal security analysis. The proposed scheme was shown to be resistant to many security attacks, including the smart card loss, replay, impersonation, forgery, offline password-guessing, denial-of-service, insider, and stolen verifier attacks. Nevertheless, the scheme's computational and communication costs were the highest among all the schemes in Fig. 1.
1.2 Motivation and Contributions
Security analysis, like that of other cryptosystems, is imperative in developing new RPA schemes. Although numerous RPA schemes based on IFP and DLP have been proposed in the literature, none of them provides security proof under the random oracle model. The security proof requirement has been fulfilled by many schemes constructed based on other cryptographic primitives in the literature, such as IFP [22], Elliptic Curve Discrete Logarithm Problem (ECDLP) [23], and chaotic maps [24]. Although the study by Kumari et al. [16] featured many security attributes, no formal security proof of its scheme was presented. Consequently, despite being the most secure among similar works, the proposed scheme had to sacrifice its performance efficiency. Therefore, the purpose of this study is two-fold. First, the aim of this study is to propose an efficient RPA scheme with session key agreement based on two cryptographic primitives (IFP and DLP). Next, the main contribution of this study is to present a formal security analysis based on the formal definitions of IFP and DLP under the random oracle model to prove the security of the proposed scheme.
The remainder of this paper is organised as follows. Section 2 presents the mathematical and security preliminaries. Section 3 then explains the newly proposed scheme. Section 4 presents the proposed scheme's formal and informal security analyses. Section 5 provides a comparative study of the previous schemes of [4,15,16], and the present scheme. Section 6 discusses how the RPA scheme could be used to develop a user identification (UI) scheme. Finally, Section 7 presents the conclusion and recommendation.
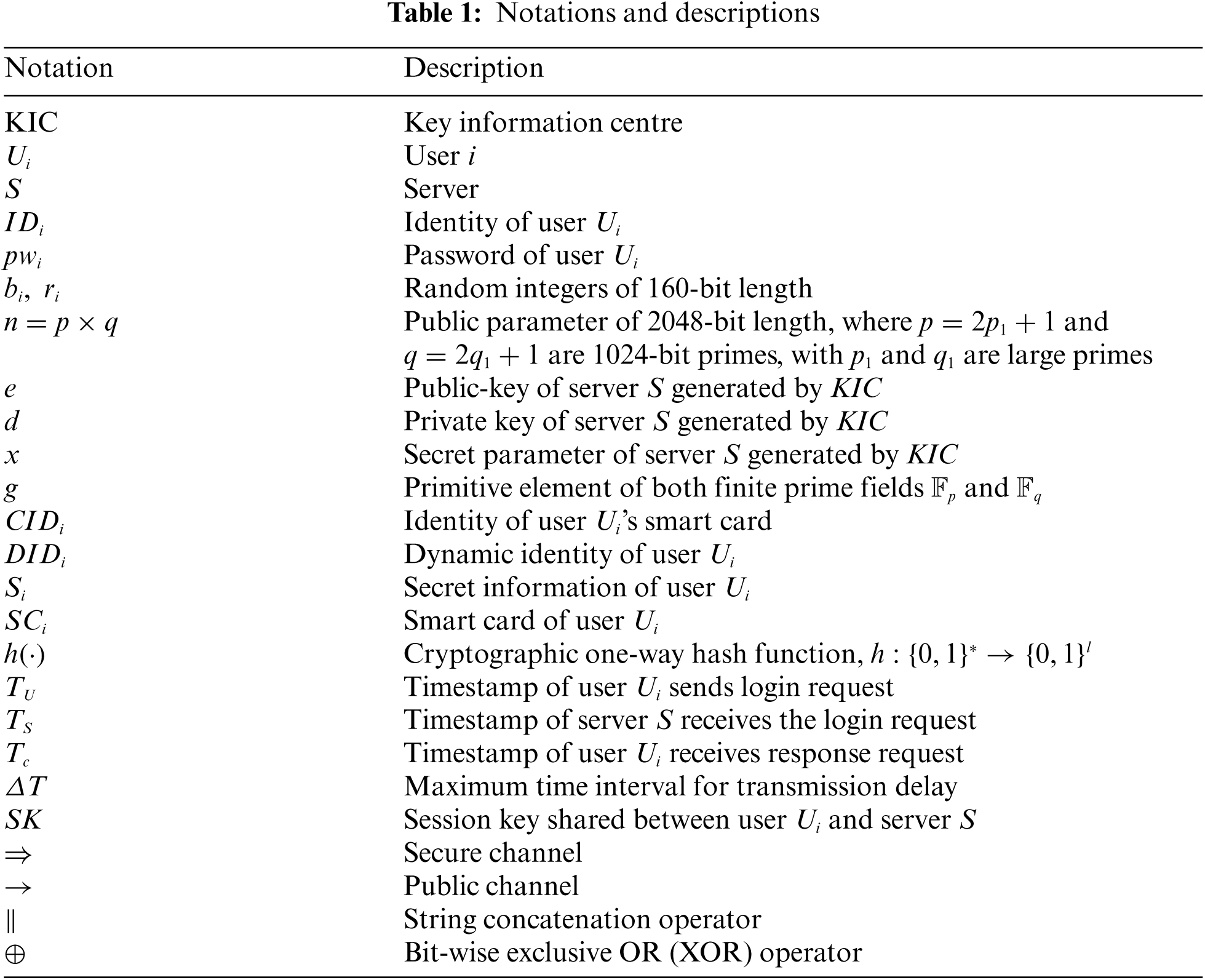
This section provides a brief overview of the mathematical concepts that served as the security foundation in the development of the proposed scheme in this study, including the definitions of IFP [25], DLP [26], and the one-way hash function (e.g., MD5 [27] or SHA-256 [28]). The adversary model and security goals were also considered. Tab. 1 shows the notations and descriptions used in this paper.
Given a 2048-bit integer
Assume that g is a primitive element of a finite field
Given g,
DLP is defined over a multiplicative group
If the factorisation of order
A cryptographic one-way hash function
■ The function h takes an arbitrary length input
■ The function h is one-way; that is, given the input x, computing
■ The function h is collision-resistant, which means that finding two inputs
The SHA-256 hash function was adopted for the proposed scheme. Other secure hash algorithms, such as SHA-1, SHA-224, SHA-384, SHA-512, and SHA-512/256 [28], can also be implemented.
For communications over an insecure public channel, the Dolev et al. [31] adversary model was considered. Accordingly, the following assumptions were made.
■ Assumption A1: An adversary
■ Assumption A2: An adversary
■ Assumption A3: An adversary
According to this adversary model, the following two cases as per [35] were also taken into account.
■ Case 1: An adversary
■ Case 2: An adversary
The following are the security goals of an ideal RPA scheme defined in this study that should be achieved, as listed in [36].
■ Mutual authentication: Both the server and the user can verify the legitimacy of each other. Furthermore, no illegal users or servers can impersonate a legal user or server.
■ Session key agreement: A session key should be created at the end of a successful mutual authentication process. Subsequently, the data transmitted between both entities should be encrypted to ensure confidentiality and secrecy.
■ User anonymity: During data transmission over a public channel, a user's valid identity should be concealed. Even if adversary
This section presents the proposed RPA scheme based on the security of IFP and DLP and consisted of five phases: (1) initialisation phase, (2) registration phase, (3) login phase, (4) authentication phase, and (5) password change phase. Furthermore, three entities were also considered: KIC, user
The KIC sets up the server's public and secret parameters during the initialisation phase.
1. Generate two large primes
2. Compute
3. Find a prime number e and integer d such that
4. Find an integer g, which is a primitive element for both finite prime fields
5. Decide on a secret parameter
6.
The private key d, secret parameter x, and format of a user's
In the registration phase, a new user
1. Choose the identity
2. Generate a random integer
3. Compute
4.
The KIC then performs the following steps.
5. Generate
6. Compute
7. Compute
8. Compute
9. KIC
After receiving the smart card
10. Compute
11. Update the smart card
Fig. 2 depicts an overview of the proposed RPA scheme's phases.
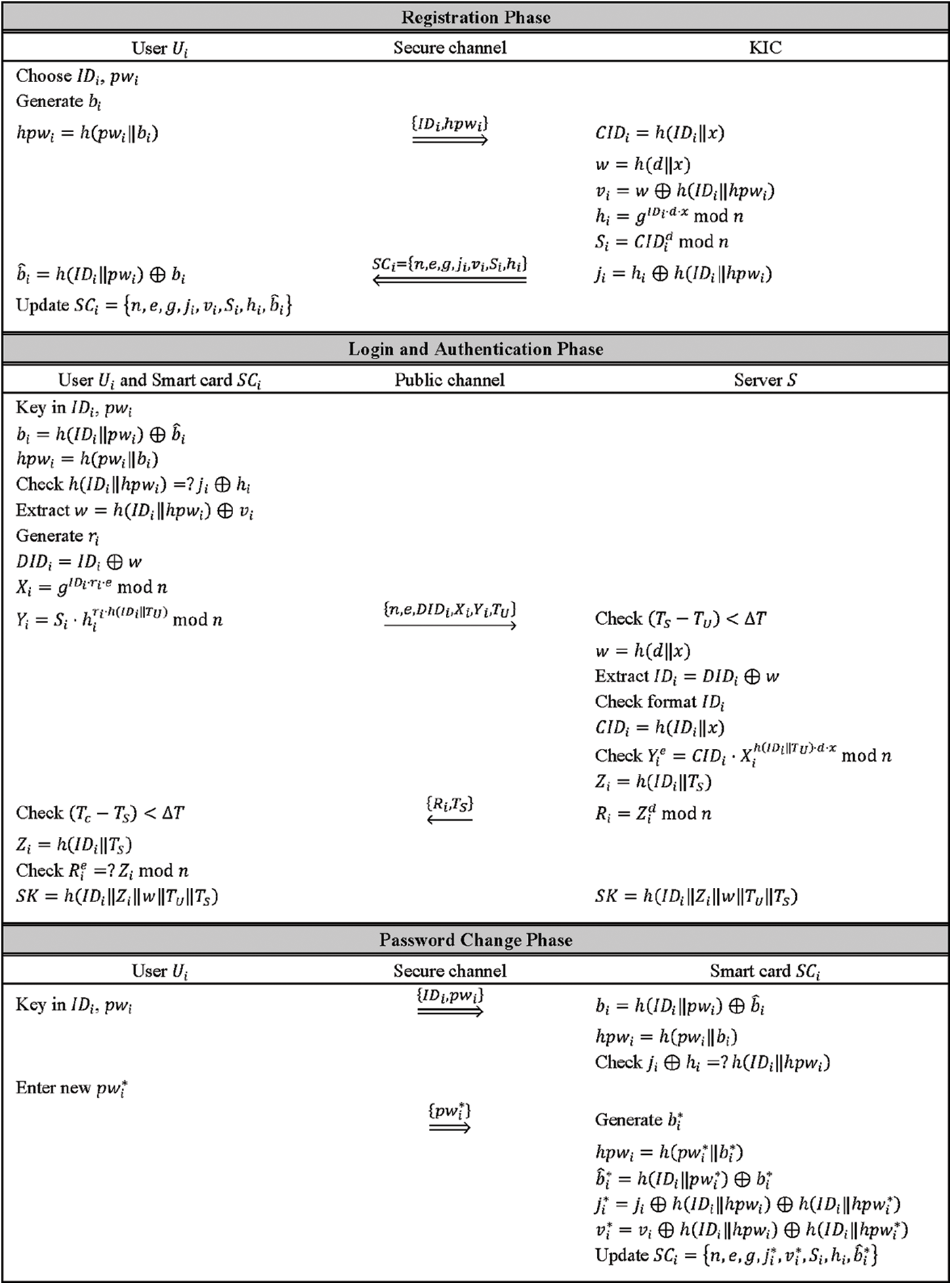
Figure 2: Overview of the proposed RPA scheme
When a registered user
1. Extract
2. Compute
3. Check
4. Extract w by computing
5. Generate a random integer
6. Compute dynamic identity of
7. Compute
8.
Once the server S receives the login message request at the time
1. Check
2. Compute
3. Extract
4. Check the validity of the format for
5. Compute
6. Check
7. Otherwise, compute
8.
Once the user
9. Check
10. Compute
11. Check
12. If mutual authentication is successful, the session key
Once the session key
This phase enables the user
1. Extract
2. Compute
3. Check
Once the user
4. Generate a random integer
5. Compute
6. Compute
7. Replace
8. Update the smart card
If user
The propositions and proofs of correctness are presented below for the sake of completeness of the proposed scheme.
Proposition 1. If user
Proposition 2. If all the login phase steps and Steps 1–5 of the authentication phase run well, and the login message
Proposition 3. If all the steps in the authentication phase (Steps 1–10) run well and the response message
4 Security Analysis of the Proposed Scheme
This section presents the formal security proof that the proposed scheme is provably secure against an adversary
The formal security analysis of the proposed scheme, which is based on the random oracle model, is explained below. Specifically, the proposed scheme's formal security proof adopted the approach taken by [22,37–39]. To begin, the formal definitions of the collision-resistant cryptographic one-way hash function [39], IFP [22] and DLP [40,41] are given.
Definition 1. A secure collision-resistant one-way hash function
is a deterministic algorithm that takes an arbitrary length input
An adversary
where
Definition 2. Assume that
For any adversary
The integer factorisation assumption states that
Definition 3. Let G be an order n cyclic group, g be a generator of G, and A be an algorithm that returns an integer in

The DLP advantage of algorithm A with execution time t is defined as
If the DLP advantage of any adversary
For this security proof, the adversary
■
■
■
The three theorems and proof of formal security analysis are then presented as follows.
Theorem 1. If the cryptographic one-way hash function
Proof. Initially, an adversary

The success probability of
According to
Theorem 2. If the cryptographic one-way hash function
Proof. An adversary
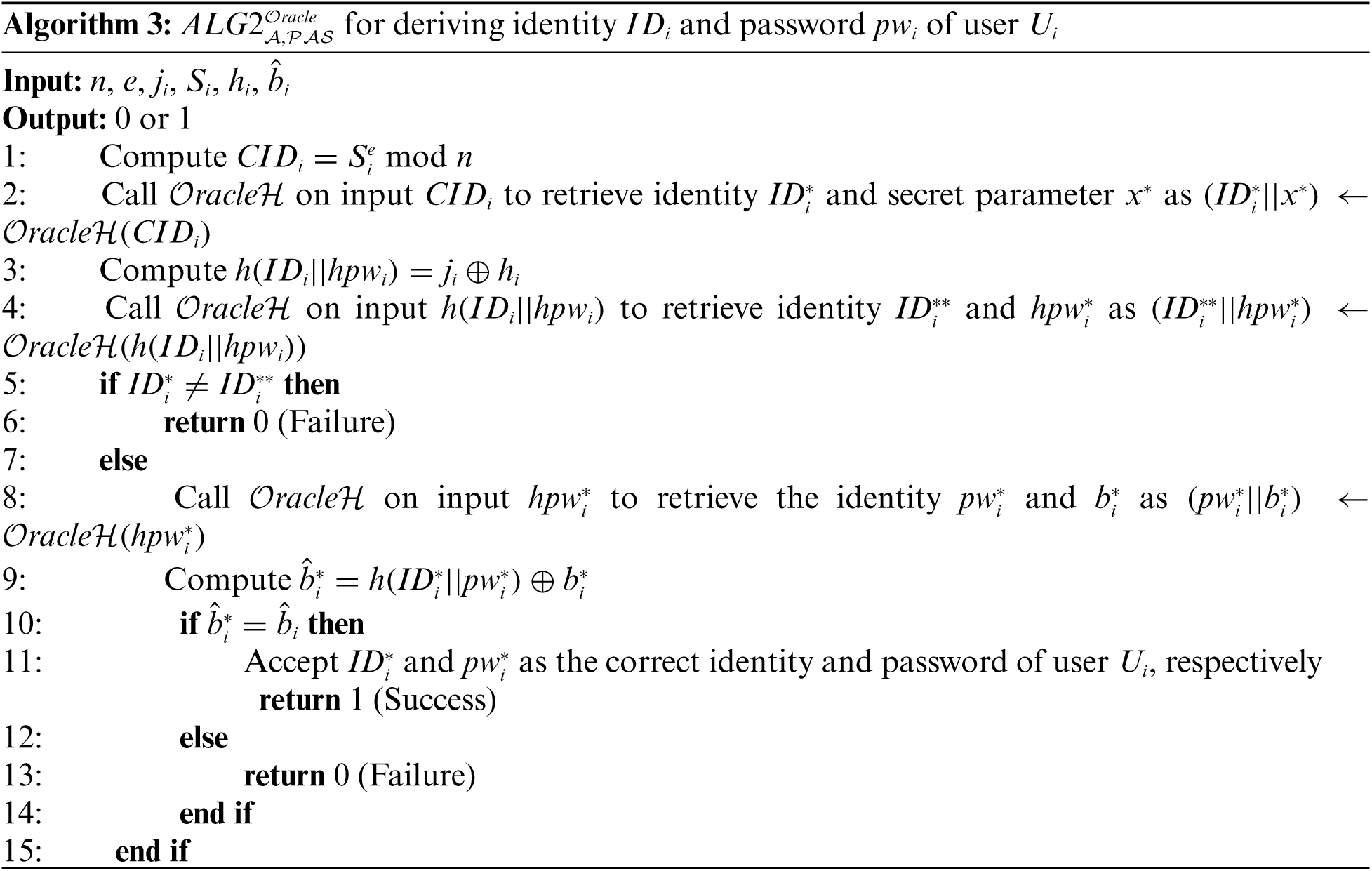
The success probability of
Consider
Theorem 3. If the cryptographic one-way hash function
Proof. Suppose that an adversary can derive the shared session key
Given the success probability of
Based on
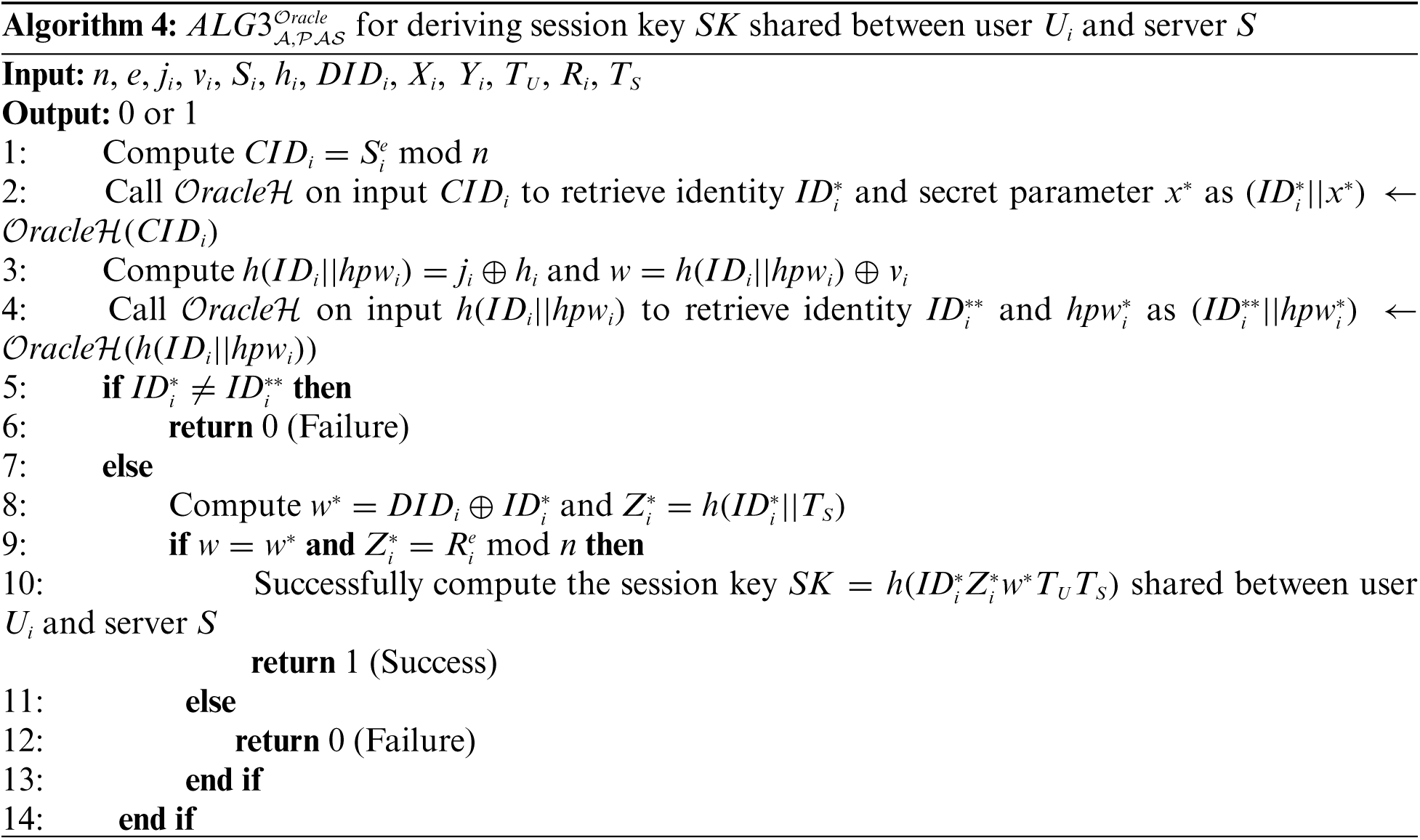
This section further analyses the security attributes offered by the proposed RPA scheme.
4.2.1 No Data Storage in Server
The proposed scheme preserves the “no data storage” feature of Kumari et al. [16] scheme. By using the information provided by the login message request, private key d, and secret parameter x, the server S can perform all the calculations to authenticate the validity of the user
The proposed scheme includes mutual authentication steps for verifying the legitimacy of the user
Next, the user
After completing the mutual authentication process, both the user
According to Assumption A2, the adversary
4.2.5 Local Password Verification
The proposed scheme offers an incorrect input detection feature. Before logging into the server S, the smart card
The extra “password change” phase in the proposed scheme grants users the convenience to change or update their passwords locally. This phase can be done without interacting with the KIC or the server S.
The proposed scheme permits the user
5 Performance Comparison and Analysis
The endorsement of a new RPA scheme should be supported by careful analysis of its performance. For this purpose, the proposed scheme was compared with similar RPA schemes [4,15,16]. These schemes are chosen according to the security attributes offered, which are mutual authentication and no data storage in the server. Furthermore, since the aim of this study is to propose an efficient RPA scheme, it is considerable to compare its performance to the most recent scheme by Kumari et al. [16] that is found in the literature. The security attributes and efficiency of all schemes considered are investigated in this section.
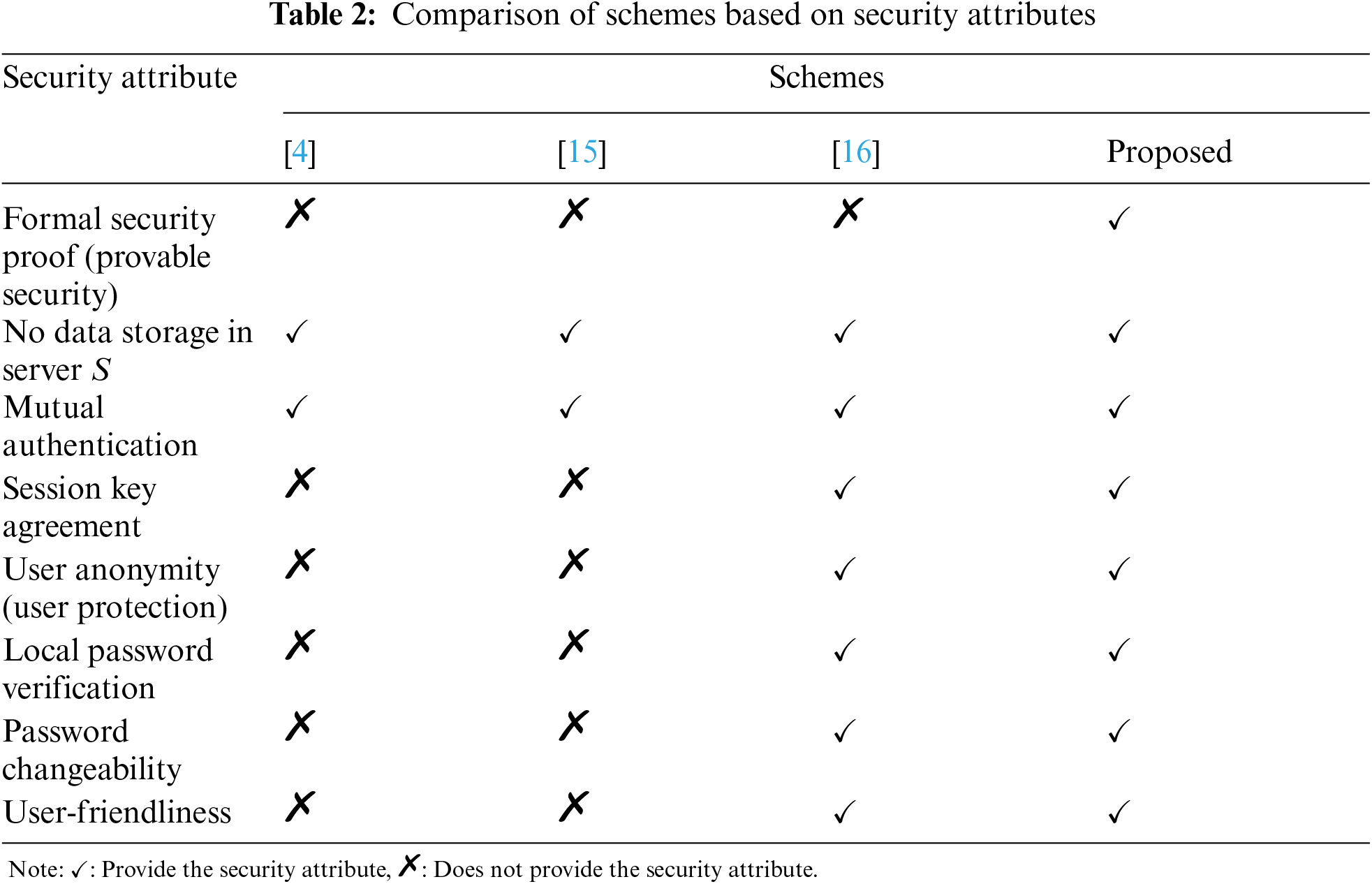
Tab. 2 compares all schemes based on the security attributes discussed in Section 4. According to Tab. 2, the proposed scheme and the scheme by Kumari et al. [16] outperformed the schemes by Shen et al. [4] and Awasthi et al. [15]. All of the security attributes of [16] were retained in the proposed scheme, including no storage of data in server S, mutual authentication, session key agreement, user anonymity, local password verification, password changeability, and user-friendliness. Furthermore, unlike the other schemes, the proposed scheme includes a formal security analysis. As a result, the proposed RPA scheme outperformed other considered schemes in terms of security attributes.
The assessment assumptions for the efficiency analysis were based on [17,29]. Assuming that each value of

In the proposed scheme, the parameters
Based on Tab. 3, the total computational costs (
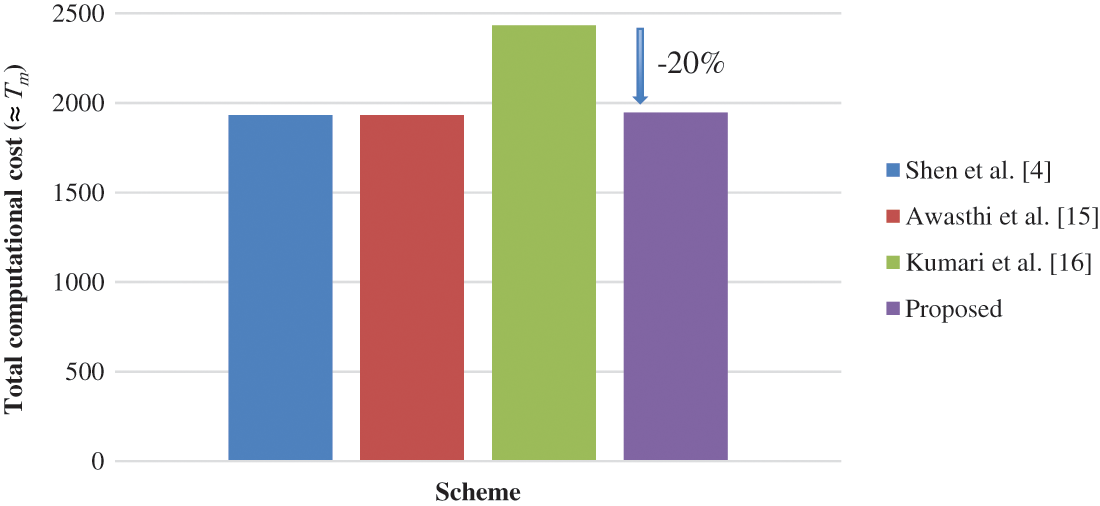
Figure 3: Comparison of schemes based on total computational cost (
As provided in Tab. 2, both the proposed scheme and Kumari et al. [16] require extra steps for session key agreement, which explains the higher computational cost when compared to the schemes by Shen et al. [4] and Awasthi et al. [15] in Tab. 3. It is worth noting that, as shown in Tab. 3, the proposed scheme requires larger smart card memory storage, particularly 3480-bit more than Kumari et al. [16]. However, this is justified because the proposed RPA scheme significantly reduced the transmission cost by 1024-bit as compared to Kumari et al. [16]. Additionally, the total computational cost improved to 1945
This section discusses the proposed approach's potential applicability in developing a UI scheme. The UI scheme can be considered a simpler algorithm used to distinguish unique users prior to the authentication process. Most RPA schemes require two or more factors (e.g., password, smart card, and fingerprint), whereas UI schemes just need the user's identity. Figs. 4a and 4b show the flowcharts for the RPA and UI schemes, respectively. At a glance, the phases in the RPA and UI schemes appear similar, except that the UI scheme does not require a login phase. Some parameters can be removed while retaining the cryptographic primitives of IFP and DLP, depending on the security goals and purposes. Therefore, it would be interesting to investigate the prospect of converting the proposed RPA scheme into an improved UI scheme with provable security.
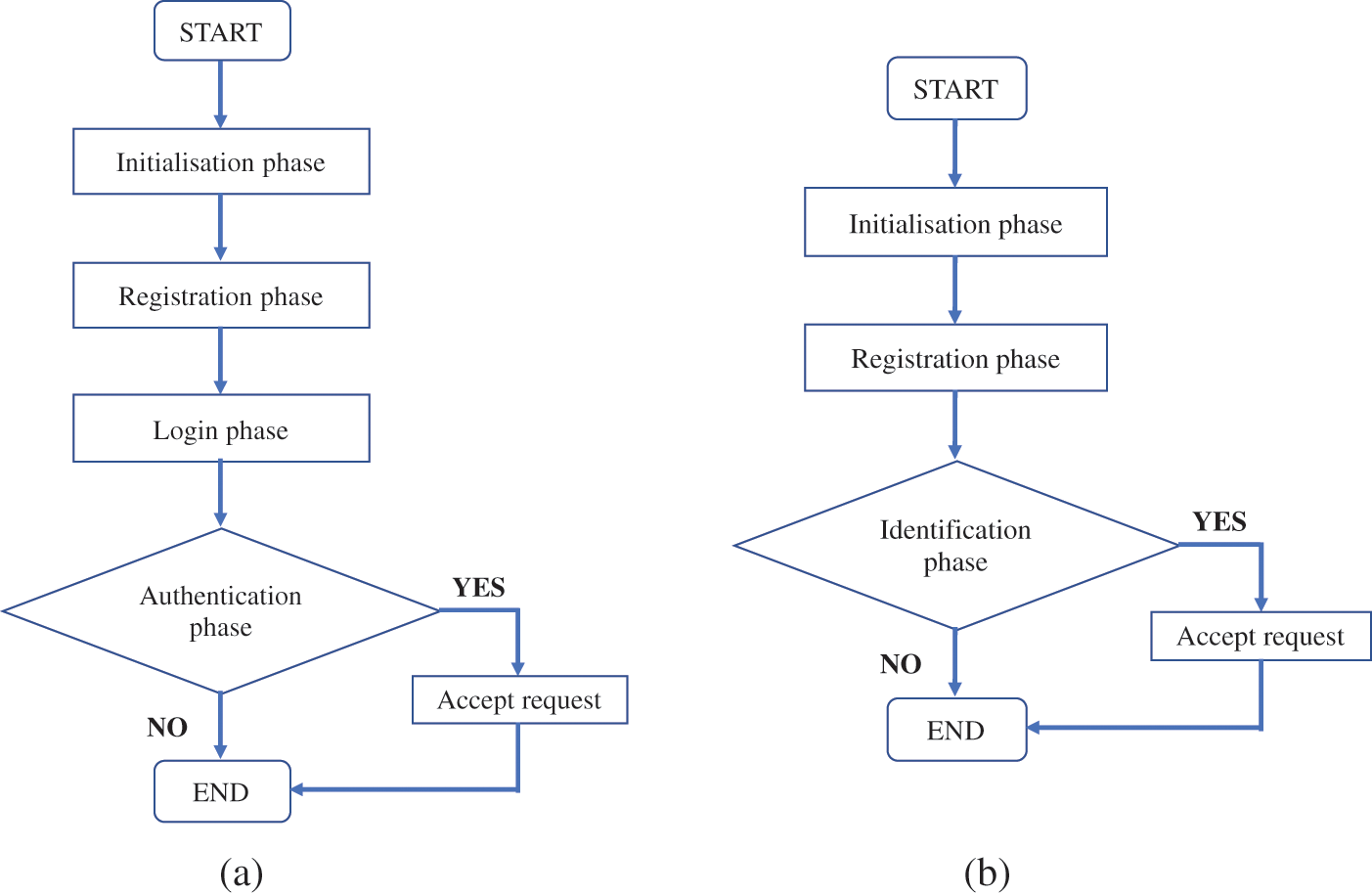
Figure 4: Process flowchart for RPA and UI schemes (a) RPA scheme (b) UI scheme
The aim of this study is to primarily propose an efficient RPA scheme that offers session key establishment between user and server. The widely established Dolev-Yao adversary model was considered in the development of the proposed scheme, which attained the desired security attributes of Kumari et al., such as no data storage in server S, user anonymity, local password verification, password changeability, and user-friendliness. Furthermore, as the main contribution, a formal security proof of the proposed scheme was presented based on the random oracle model using formal definitions of IFP and DLP. Although the proposed scheme required higher smart card memory than other similar schemes by Shen et al., Awasthi et al. and Kumari et al., this was acceptable owing to its much-reduced transmission/computation cost and time complexity than Kumari et al.'s scheme. The performance analysis proved that the proposed RPA scheme is noticeably better than Kumari et al., given that it can provide the same security attributes. Future work will investigate the use of two cryptographic primitives (IFP and DLP) in the development of UI schemes. Since the phases in RPA and UI schemes are similar, it would be interesting to examine the potential application, particularly in terms of security and performance. Expectantly, this should aid in the design of an efficient and provably secure UI scheme.
Acknowledgement: Authors are grateful for the support from Universiti Teknologi MARA (UiTM) and Universiti Kebangsaan Malaysia (UKM) for providing the facilities and resources, and UiTM/KPT-SLAB scholarship from the Ministry of Higher Education Malaysia (MOHE). In addition, the authors would like to thank anonymous reviewers for their comments and suggestions to improve this manuscript.
Funding Statement: This research is funded by UKM under Grant No. GUP-2020-029.
Conflicts of Interest: The authors declare that they have no conflicts of interest to report regarding the present study.
1. W. H. Yang and S. P. Shieh, “Password authentication schemes with smart cards,” Computers & Security, vol. 18, no. 8, pp. 727–733, 1999. [Google Scholar]
2. A. Shamir, “Identity-based cryptosystems and signature schemes,” in Lecture Notes Computer Sciences (Including Subseries Lect. Notes Artificial Intelligence Lecture Notes Bioinformatics), vol. 196 LNCS, Berlin, Heidelberg: Springer, pp. 47–53, 1985. [Google Scholar]
3. L. Fan, J. H. Li and H. W. Zhu, “An enhancement of timestamp-based password authentication scheme,” Computers & Security, vol. 21, no. 7, pp. 665–667, 2002. [Google Scholar]
4. J. J. Shen, C. W. Lin and M. S. Hwang, “Security enhancement for the timestamp-based password authentication scheme using smart cards,” Computers & Security, vol. 22, no. 7, pp. 591–595, 2003. [Google Scholar]
5. R. Jiang, L. Pan and J. H. Li, “Further analysis of password authentication schemes based on authentication tests,” Computers & Security, vol. 23, no. 6, pp. 469–477, 2004. [Google Scholar]
6. Y. Wang and J. Li, “Security improvement on a timestamp-based password authentication scheme,” IEEE Transactions on Consumer Electronics, vol. 50, no. 2, pp. 580–582, 2004. [Google Scholar]
7. Y. Wang, J. Li and L. Tie, “Security improvement on Yang-Shieh's authentication scheme,” in 2004 Int. Conf. on Communications, Circuits and Systems, Chengdu, China, vol. 1, pp. 4–5, 2004. [Google Scholar]
8. C. C. Yang, R. C. Wang and T. Y. Chang, “An improvement of the Yang-Shieh password authentication schemes,” Applied Mathematics and Computation, vol. 162, no. 3, pp. 1391–1396, 2005. [Google Scholar]
9. A. S. K. Pathan, “A review and cryptanalysis of similar timestamp-based password authentication schemes using smart cards,” International Journal of Communication Networks and Information Security, vol. 2, no. 1, pp. 15–20, 2010. [Google Scholar]
10. J. Y. Liu, A. M. Zhou and M. X. Gao, “A new mutual authentication scheme based on nonce and smart cards,” Computer Communications, vol. 31, no. 10, pp. 2205–2209, 2008. [Google Scholar]
11. C. C. Yang and R. C. Wang, “An improvement of security enhancement for the timestamp-based password authentication scheme using smart cards,” ACM SIGOPS Operation Systems Review, vol. 38, no. 3, pp. 91–96, 2004. [Google Scholar]
12. E. J. Yoon, E. K. Ryu and K. Y. Yoo, “Security of Shen et al.'s timestamp-based password authentication scheme,” in Lecture Notes in Computer Science (Including Subseries Lecture Notes in Artificial Intelligence and Lecture Notes in Bioinformatics), vol. 3046 LNCS, Berlin, Heidelberg: Springer, pp. 665–671, 2004. [Google Scholar]
13. X. Wang, J. Zhang, W. Zhang and M. K. Khan, “Security improvement on the timestamp-based password authentication scheme using smart cards,” in 2006 IEEE Int. Conf. on Engineering of Intelligent Systems, Islamabad, Pakistan, pp. 1–3, 2006. [Google Scholar]
14. T. H. Chen, G. Horng and K. C. Wu, “A secure YS-like user authentication scheme,” Informatica, vol. 18, no. 1, pp. 27–36, 2007. [Google Scholar]
15. A. K. Awasthi, K. Srivastava and R. C. Mittal, “An improved timestamp-based remote user authentication scheme,” Computers and Electrical Engineering, vol. 37, no. 6, pp. 869–874, 2011. [Google Scholar]
16. S. Kumari, M. K. Gupta, M. K. Khan and X. Li, “An improved timestamp-based password authentication scheme: Comments, cryptanalysis, and improvement,” Security and Communication Networks, vol. 7, no. 11, pp. 1921–1932, 2014. [Google Scholar]
17. K. W. Kim, J. C. Jeon and K. Y. Yoo, “An improvement on yang et al.'s password authentication schemes,” Applied Mathematics and Computation, vol. 170, no. 1, pp. 207–215, 2005. [Google Scholar]
18. M. K. Khan, “Cryptanalysis and security enhancement of two password authentication schemes with smart cards,” in INMIC2007-11th IEEE Int. Multitopic Conf., Lahore, Pakistan, pp. 1–4, 2007. [Google Scholar]
19. D. Giri and P. D. Srivastava, “Cryptanalysis and the improvement of Kim et al.'s password authentication schemes,” in Lecture Notes in Computer Science (Including Subseries Lecture Notes in Artificial Intelligence and Lecture Notes in Bioinformatics), vol. 4812 LNCS, Berlin, Heidelberg: Springer, pp. 156–166, 2007. [Google Scholar]
20. E. S. Ismail and S. M. S. Syed-Musa, “Timestamp-based password authentication scheme,” AIP Conference Proceedings, vol. 1974, pp. 1–5, 2018. [Google Scholar]
21. Y. An, “Security enhancements of an improved timestamp-based remote user authentication scheme,” in Communications in Computer and Information Science, vol. 339 CCIS, pp. 54–61, 2012. [Google Scholar]
22. N. Radhakrishnan and M. Karuppiah, “An efficient and secure remote user mutual authentication scheme using smart cards for telecare medical information systems,” Informatics in Medicine Unlocked, vol. 16, pp. 100092, 2018. [Google Scholar]
23. A. K. Das, S. Chatterjee and J. K. Sing, “A novel efficient access control scheme for large-scale distributed wireless sensor networks,” International Journal of Foundations of Computer Science, vol. 24, no. 5, pp. 625–653, 2013. [Google Scholar]
24. S. H. Islam, “Provably secure dynamic identity-based three-factor password authentication scheme using extended chaotic maps,” Nonlinear Dynamics, vol. 78, no. 3, pp. 2261–2276, 2014. [Google Scholar]
25. R. Amin, T. Maitra, D. Giri and P. D. Srivastava, “Cryptanalysis and improvement of an RSA based remote user authentication scheme scheme using using smart card,” Wireless Personal Communications, vol. 96, no. 3, pp. 4629–4659, 2017. [Google Scholar]
26. W. Diffie and M. Hellman, “New directions in cryptography,” IEEE Transactions on Information Theory, vol. 22, no. 6, pp. 644–654, 1976. [Google Scholar]
27. R. Rivest, “The MD5 message-digest algorithm,” RFC 1321, April 1992. https://ftp://ftp.rfc-editor.org/in-notes/rfc1321.txt. [Google Scholar]
28. NIST, “FIPS PUB 180-4 secure hash standard (SHS),” 2012. [Google Scholar]
29. S. C. Pohlig and M. E. Hellman, “An improved algorithm for computing logarithms over GF(p) and its cryptographic significance,” IEEE Transactions on Information Theory, vol. 24, no. 1, pp. 106–110, 1978. [Google Scholar]
30. J. Katz and Y. Lindell, Introduction to Modern Cryptography, 3rd edition. Boca Raton, USA: CRC Press, 2021. [Google Scholar]
31. D. Dolev and A. C. Yao, “On the security of public key protocols,” IEEE Transactions on Information Theory, vol. 29, no. 2, pp. 198–208, 1983. [Google Scholar]
32. P. Kocher, J. Jaffe and B. Jun, “Differential power analysis,” In: M. Wiener (Ed.) Advances in Cryptology, Berlin, Heidelberg: Springer, pp. 388–397, 1999. [Google Scholar]
33. T. S. Messerges, E. A. Dabbish and R. H. Sloan, “Examining smart-card security under the threat of power analysis attacks,” IEEE Transactions on Computers, vol. 51, no. 5, pp. 541–552, 2002. [Google Scholar]
34. S. K. Sood, A. K. Sarje and K. Singh, “Cryptanalysis of password authentication schemes: Current status and key issues,” in Proc. of Int. Conf. on Methods and Models in Computer Science, ICM2CS09, Delhi, India, 2009. [Google Scholar]
35. T. Maitra, M. S. Obaidat, S. H. Islam, D. Giri and R. Amin, “Security analysis and design of an efficient ECC-based two-factor password authentication scheme,” Security and Communication Networks, vol. 9, no. 17, pp. 4166–4181, 2016. [Google Scholar]
36. F. Wu, L. Xu, S. Kumari, X. Li and A. Alelaiwi, “A new authenticated key agreement scheme based on smart cards providing user anonymity with formal proof,” Security and Communication Networks, vol. 8, no. 18, pp. 3847–3863, 2015. [Google Scholar]
37. A. K. Das, N. R. Paul and L. Tripathy, “Cryptanalysis and improvement of an access control in user hierarchy based on elliptic curve cryptosystem,” Information Sciences, vol. 209, pp. 80–92, 2012. [Google Scholar]
38. A. K. Das, “A secure and effective user authentication and privacy preserving protocol with smart cards for wireless communications,” Networking Science, vol. 2, no. 1–2, pp. 12–27, 2013. [Google Scholar]
39. V. Odelu, A. K. Das and A. Goswami, “An efficient ECC-based privacy-preserving client authentication protocol with key agreement using smart card,” Journal of Information Security Applications, vol. 21, pp. 1–19, 2015. [Google Scholar]
40. M. Bellare and P. Rogaway, Introduction to Modern Cryptography, California, USA, University of California at Davis, 2005. [Online]. https://web.cs.ucdavis.edu/~rogaway/classes/227/spring05/book/main.pdf. [Google Scholar]
41. M. Karuppiah, A. K. Das, X. Li, S. Kumari, F. Fan et al., “Secure remote user mutual authentication scheme with key agreement for cloud environment,” Mobile Networks and Applications, vol. 24, no. 3, pp. 1046–1062, 2018. [Google Scholar]
42. C. H. Tsai and P. C. Su, “Multi-document threshold signcryption scheme,” Security and Communication Networks, vol. 8, no. 13, pp. 2244–2256, 2015. [Google Scholar]
 | This work is licensed under a Creative Commons Attribution 4.0 International License, which permits unrestricted use, distribution, and reproduction in any medium, provided the original work is properly cited. |