DOI:10.32604/cmc.2022.019289

| Computers, Materials & Continua DOI:10.32604/cmc.2022.019289 |  |
| Article |
Security Threat and Vulnerability Assessment and Measurement in Secure Software Development
1Department of Information Systems, College of Computer and Information Sciences, Jouf University, Al-Jouf, KSA
2School of Computer Science and Engineering (SCE), Taylor's University, Selangor, Malaysia
3Department of Computer Science, Bahria University, Islamabad, Pakistan
*Corresponding Author: NZ Jhanjhi. Email: NoorZaman.Jhanjhi@taylors.edu.my
Received: 08 April 2021; Accepted: 10 May 2021
Abstract: Security is critical to the success of software, particularly in today's fast-paced, technology-driven environment. It ensures that data, code, and services maintain their CIA (Confidentiality, Integrity, and Availability). This is only possible if security is taken into account at all stages of the SDLC (Software Development Life Cycle). Various approaches to software quality have been developed, such as CMMI (Capability maturity model integration). However, there exists no explicit solution for incorporating security into all phases of SDLC. One of the major causes of pervasive vulnerabilities is a failure to prioritize security. Even the most proactive companies use the “patch and penetrate” strategy, in which security is accessed once the job is completed. Increased cost, time overrun, not integrating testing and input in SDLC, usage of third-party tools and components, and lack of knowledge are all reasons for not paying attention to the security angle during the SDLC, despite the fact that secure software development is essential for business continuity and survival in today's ICT world. There is a need to implement best practices in SDLC to address security at all levels. To fill this gap, we have provided a detailed overview of secure software development practices while taking care of project costs and deadlines. We proposed a secure SDLC framework based on the identified practices, which integrates the best security practices in various SDLC phases. A mathematical model is used to validate the proposed framework. A case study and findings show that the proposed system aids in the integration of security best practices into the overall SDLC, resulting in more secure applications.
Keywords: Security; secure software development; software development life cycle (SDLC); confidentiality; integrity; availability
Software security is a process that includes the design, development, and testing of software for security where vulnerabilities are detected and revealed by the software itself [1–3]. It fundamentally requires a proactive approach that takes place within the pre-deployment process. It's all about making the software development team do a great job to make it easier for operators. A simple error sometimes can end up causing millions of dollars of losses in today's business processes. But unfortunately, many software development companies do not follow best practices to incorporate security in SDLC [4,5]. This negligence includes lack of awareness, fear of time and cost overrun, use of third-party components and, lack of qualified professionals, etc. Due to the popularity and excessive usage of internet applications such as the internet of things, cloud computing, social media systems, etc., the number of security vulnerabilities is also overgrowing [6–9].
SDLC is a mechanism that generates the best quality and low-cost software in the shortest possible time. It offers a well-structured step flow that helps an enterprise easily produce high-quality, well-tested, and ready-to-use software. The common phases of SLDC include planning, analysis, design, implementation, testing & integration, and maintenance [10–12]. All these phases are dependent on each other and are of equal importance. If security is incorporated during all phases of SDLC then the resultant product will not be vulnerable to security threats. This is only possible if a secure SDLC process is followed, secure SDLC ensures that security-related activities are an integral part of the overall development effort [13–16].
Traditional security mechanisms mainly focus on network systems, and they spent a huge amount of money to make their network secure. These mechanisms include IDs (Intrusion detection system), firewalls, encryption, antivirus, and antispyware [17–19]. Further, security is considered an afterthought that is usually addressed after completing the development cycle using the approach of P&P (penetrate and patch), which means creating the patches for the available flaws. The drawback of the P&P technique is that the application users do not apply these patches. Further, attackers might plan and penetrate new vulnerabilities [20–23]. According to a report published by RiskIQ, security vulnerabilities alone cost as much as $25 per minute to the major companies while crypto companies face the loss of almost $2000 per minute due to cybercrimes [24]. Another report presented by positive technologies; 9 out of 10 web applications are vulnerable to security threats and about 39% of websites are vulnerable to unauthorized access, while data breach is a threat for about 64% of applications [25]. According to this report, 82 percent of vulnerabilities were due to flaws in code. This report has also published the severity of web application vulnerabilities in the past. This shows that security is one of the serious issues in the current era that need to be addressed carefully during SDLC. Further, the relative cost of addressing bugs and failure increase as the project progress as mentioned in the IBM system science institute report [26]. Therefore, handling security from the beginning of the project is necessary to save the software from future security breaches.
It is evident from the above discussion that secure software development is inevitable for improving project quality and reducing bug fixing cost, and there exists no explicit solution to this problem. As a contribution to research, we reviewed the current literature on vulnerability evaluation and assessment in SDLC and outlined the security best practices to evaluate and quantify security threats and vulnerabilities in SDLC. Based on the identified best practices, we have proposed a secure SDLC framework. The proposed framework tries to mitigate the security vulnerabilities in SDLC by addressing end-to-end security. The proposed framework is validated using a mathematical model and a case study. Fig. 1 illustrates the research process that was followed to carry out this research study.
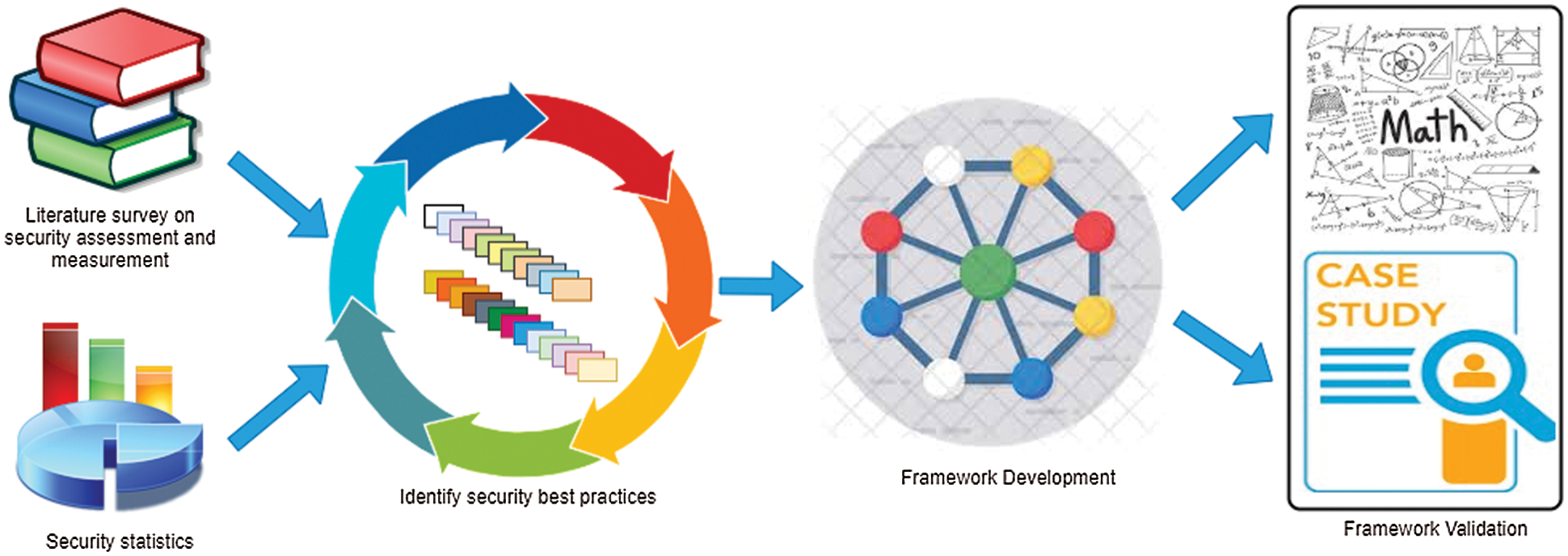
Figure 1: Research process
The results of the case study show that the proposed approach helps incorporate security in SDLC. The remaining paper is structured as; Section 2 describes the existing work to highlight the best practices and techniques available for the assessment and measurements of security threats and vulnerabilities. Section 3 presents our proposed framework that addresses security in SDLC. Sections 4 & 5 evaluate the proposed framework using mathematical modeling and case study. Section 6 discusses the findings of the study. Section 7 concludes this paper by providing directions for future work.
This section will provide an overview of some latest research in secure software development to highlight the best practices that need to be followed for developing quality software. Further, it will pave the way for the proposed framework.
In paper [27], an integrated security framework is proposed for secure SDLC. Security test cases and guidelines were generated based on the security activities, and best practices followed in secure SDLC. Security testing tools were integrated for the automation of test case execution. A prototype was constructed to evaluate the proposed framework. The results of the experiment showed that the proposed approach provides stable service with enhanced quality and security. In Paper [20], a Multi-vocal literature review was conducted to identify the best practices for designing secure software. Based on identified best practices, a framework Secure Software Design Maturity Model (SSDMM) was developed. The framework was evaluated using case studies, and the results show that SSDMM helps measure the maturity level of an organization. Further, SSDMMM helps organizations in the evaluation and improvement of software design security practices.
In paper [28], a systematic literature review (SLR) was performed to pinpoint the required practices for developing secure software. This paper also amended Somerville's requirement engineering practices. After identifying best requirement practices, a framework for secure requirement engineering named as Requirements Engineering Security Maturity Model (RESMM) was developed. The proposed framework was tested using questionnaires and case studies. The results show that the proposed framework is useful and easily adaptable. According to [29], security is not considered in the overall SDLC due to which a lot of security breaches occur. This paper presents a secure paradigm that is an extension of security development practices in agile methodology to overcome this problem in web application development. The proposed paradigm consists of three phases namely, inception, construction, and transition. Further, this paper classifies security vulnerabilities and common risks and threats that occur during web application development. Based on identified gaps, a framework is proposed for secure web application development. The survey method was used for the evaluation of the proposed framework, and the results were satisfactory.
According to the paper [30], the use of best practices for risk management should be followed in overall SDLC for getting a quality software product. This paper discussed various practices of risk management and security in different phases of SDLC. It provides an insight to the researchers and practitioners about the existing best practices that need to be followed. According to [31], security is an important aspect of software systems. However, existing studies do not address it explicitly into SDLC, therefore, this study identified important security policies, practices, and tools within SDLC and proposed a model for incorporating these elements into SDLC. This research study used a case study-based approach for answering research questions. Further, an expert review was conducted for the validation of the proposed model.
Paper [32] concludes that understanding software and proper application methods results in a reliable and quality software product. This research identified the issues that occurred while incorporating security into SDLC along with suitable solutions. Further, it discussed some security-related issues in detail such as security testing, threat modeling, risk assessment, and other suitable techniques that help in developing secure software. Paper [33] investigates security aspects in various phases of SDLC and evaluates these aspects with the help of the research community and software engineers. The results obtained from this qualitative study were analyzed using the SPSS tool, some security rules were also proposed for various phases of SDLC.
According to [34], security has been considered an afterthought for a long time. However, this approach is not suitable in today's fast-paced economy. Security needs to be incorporated from the beginning of software till the end. This paper provides an overview of security plans in various phases of SDLC. Further, it emphasizes the importance of good governance for the success of the project. A systematic mapping study is performed in [35] to identify the existing security approaches, followed in SDLC. In this paper, 118 studies were selected as the primary studies, and 52 security practices were identified from the selected studies. According to study findings, most of the security practices are being followed in the coding stage of SDLC.
It is obvious from the above discussion that incorporating security in different phases of SDLC is inevitable for quality software. There exist various studies that discuss the importance of incorporating security in SDLC, however, still there exists space for further research in the area. As a contribution towards this research direction, first, we have highlighted the common reasons for security flaws in SDLC as shown in Fig. 2. by providing a taxonomy of SDLC [36–42]. Next, we have proposed an approach that will incorporate security best practices in various phases of SDLC as mentioned in the upcoming section. Further, we have proposed a secure SDLC framework in the next section that is evaluated using a mathematical model and case study.
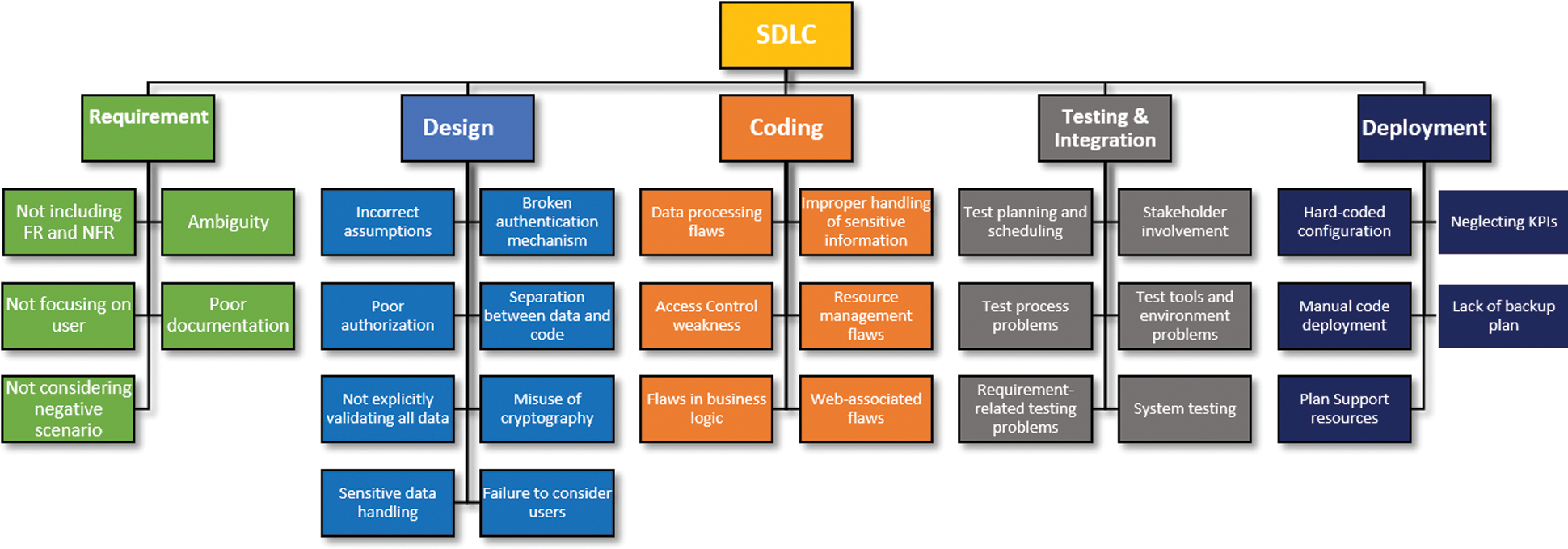
Figure 2: A taxonomy of security flaws reasons in SDLC
This section will discuss different phases of SDLC, the discussion of each phase will focus on three dimensions; the tasks performed in that phase, security issues involved, and mitigation strategies. It will not only provide a detailed overview of secure SDLC rather will also pave the way for our proposed solution. Below we discuss these phases briefly.
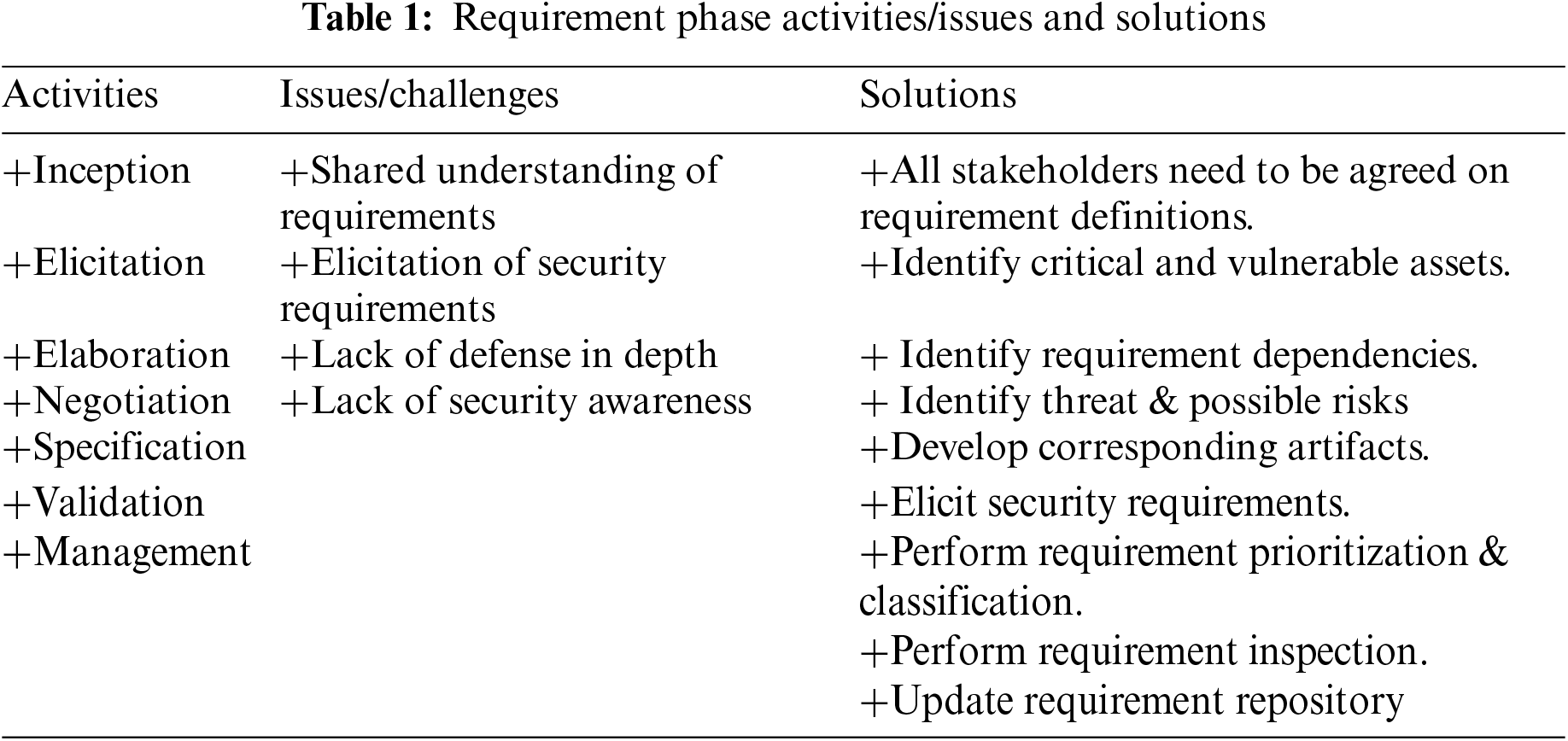
Requirement engineering is the first phase of SDLC, and the success of this phase leads towards a better software product. Further, handling security from the requirement phase help to save rework and additional cost. The tasks performed at this level are listed in Column 1 of Tab. 1 [43–45]. Existing literature on requirement security has highlighted different issues that might occur if security is not incorporated from the beginning. Some common security issues that might occur during the requirement phase of SDLC are listed in column 2 of Tab. 1 [30,33,46,47]. To accomplish this phase and to address security from the beginning, best practices need to be followed. Different researchers have proposed different practices that need to be followed. Column 3 of Tab. 1 list down the commonly used best practices for handling security during the requirement phase of SDLC [28,30,33,48–50]
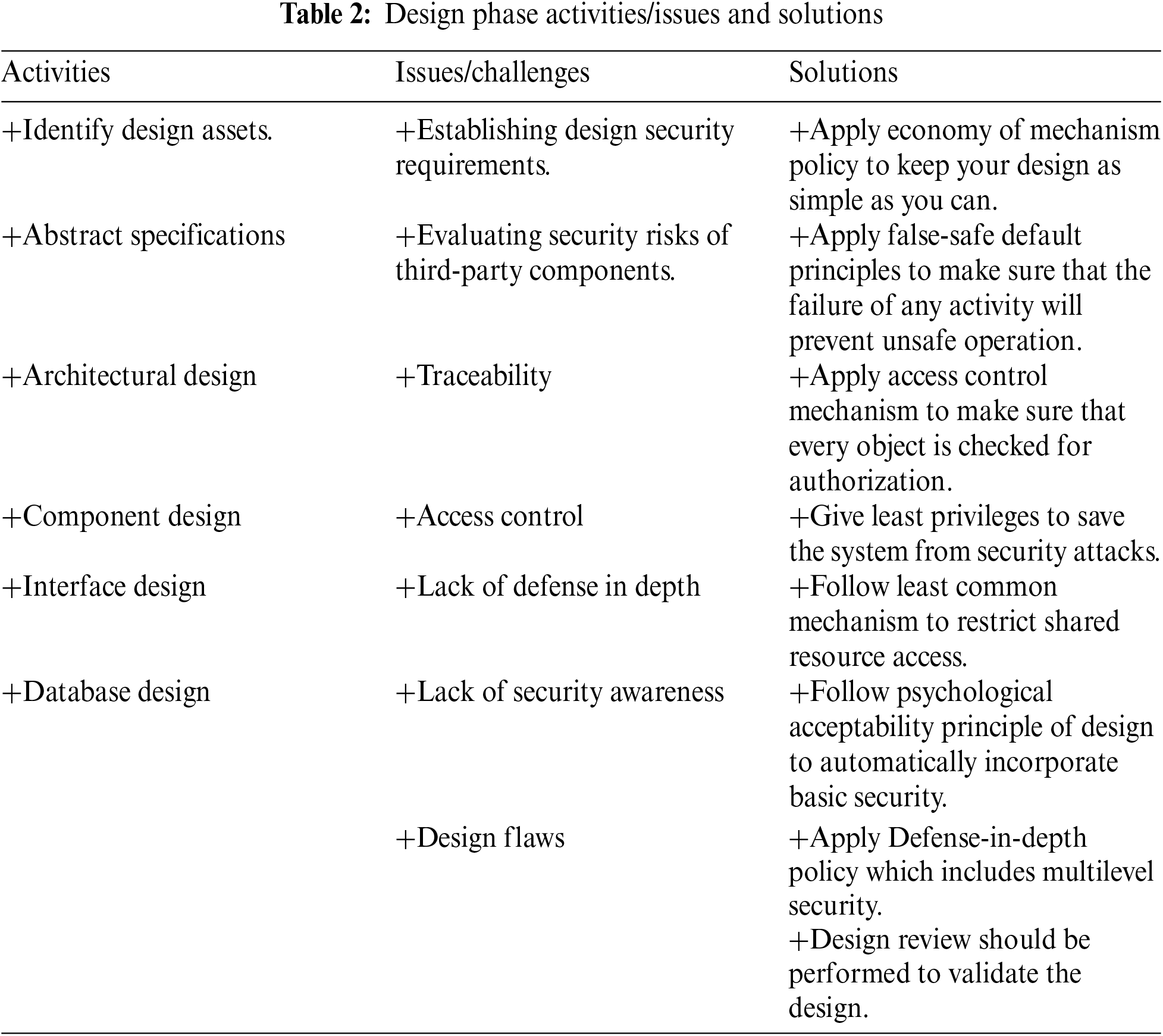
Design is an essential step of the SDLC because it determines the look and sound of the app. Furthermore, it offers a user-interactive platform, making it vulnerable to numerous security threats. The important tasks performed during this phase are listed in Column 1 of Tab. 2 [51–55]. Common security issues that are usually faced during software design are listed in Column 2 of Tab. 2 [20,53,56–59] while security best practices are listed in Column 3 of Tab. 2 [13,14,20,28,52,53,60,61]
The practice of secure coding is inevitable for safeguarding computer software against security vulnerabilities; therefore, the coding phase is among the critical phases of SDLC. Tasks performed during this phase are listed in Column 1 of Tab. 3 The selection of appropriate coding language and classification of modules is a challenging task. Further, the reusability of code also creates a challenge if security is not considered while coding. Column 2 of Tab. 3 list down the security issues that are usually faced during the coding phase while best practices of secure coding are listed in Column 3 of Tab. 3 [28,33,62–70]
3.4 Testing & Integration Phase
The testing & integration phase aims to make sure that all the system components provide their required functionality alone and as part of the whole system. The tasks involved in this phase are listed in colum1 of Tab. 4. This phase aims to find possible bugs and errors in the system and remove them. Some common security issues involved in this phase are listed in Column 2 of Tab. 4. This phase gives the final touch to the software before deployment therefore quality must be assured. Column 3 of Tab. 4 lists down the best practices that help to make this phase secure and successful [71–77].
This is the last stage of SDLC which handles the release and change management. In this phase, the software is installed in its actual environment. It seems simple but pairing the software with the existing environment is sometimes complex. Patches are created to handle the flaws; this makes the software vulnerable to various security threats. Column 1 of Tab. 5 lists down the tasks that are performed in this stage. Some common security issues involved in this stage are listed in Column 2 of Tab. 5. Further, customer satisfaction is very important at this level therefore Column 3 of Tab. 5 list down the best practices that need to be considered for making this phase successful [78–83].

The above discussion has highlighted the brief details of SDLC phases along with security issues and mitigation strategies. Based on identified challenges and best practices for each phase of SDLC, we have developed a framework as shown in Fig. 3. This framework addresses security in overall SDLC by incorporating security best practices in different phases of SDLC. The framework is divided into two dimensions. The horizontal dimension of the framework shows SDLC phases while the vertical dimension of the framework list down the details of the tasks performed during each phase of SDLC, security issues involved in each phase, and corresponding mitigation strategies.
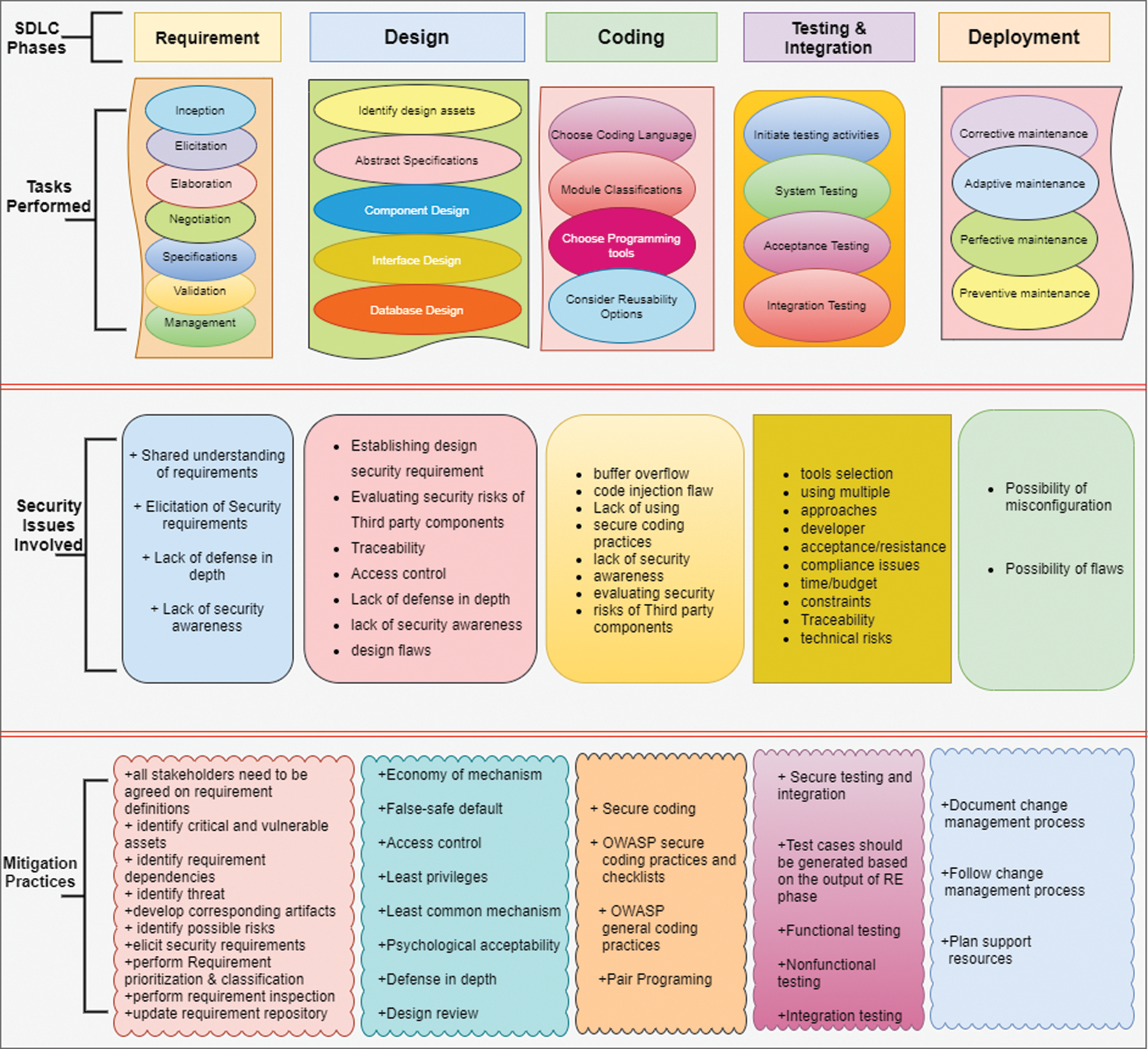
Figure 3: Proposed secure SDLC framework
According to the proposed framework, security best practices need to be incorporated from the beginning of the project until deployment to get secure and quality software. The practices mentioned in the above framework will not only make the software secure but will also not add much to the project budget and time. The detail of the framework is also presented in the form of an algorithm.

4 Framework Evaluation Using Mathematical Modeling
Before proceeding towards mathematical modeling, we first define notations used in the mathematical model for getting a better understanding. Tab. 6 lists down the notations of our mathematical model.
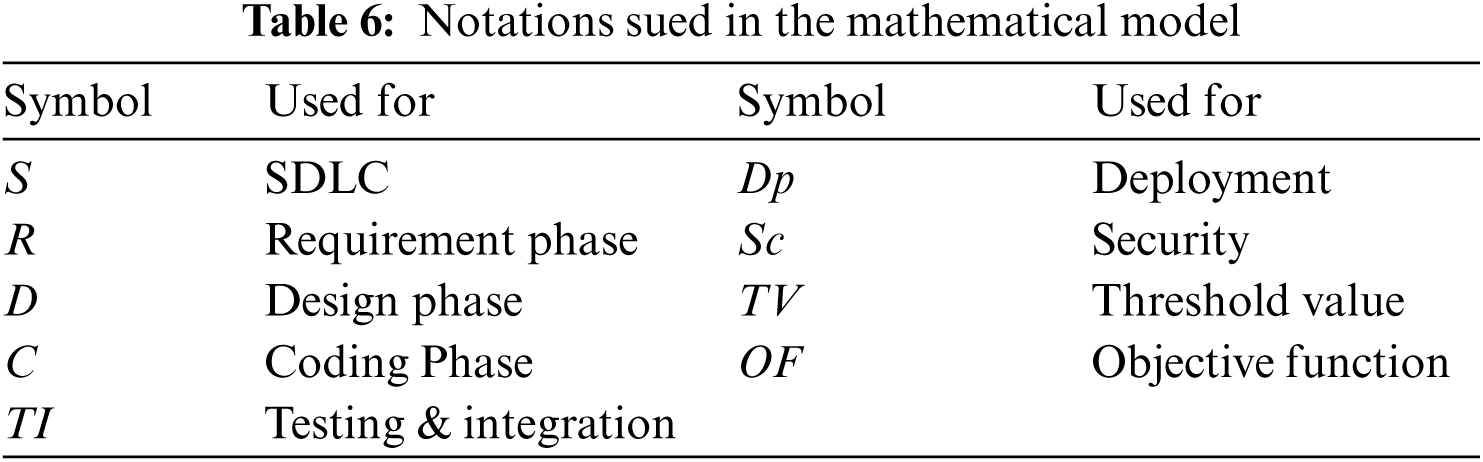
According to the proposed framework, secure SDLC need to incorporate security in overall SDLC as shown in Eq. (1)
The proposed framework aims to enhance security, therefore, the objective function in our case will be as shown in Eq. (2)
The Requirement phase of SDLC can be improved by following best practices as mentioned in the proposed framework. Hence the requirement phase can be modeled as
where
Eq. (4) must be true for secure completion of the requirement phase. The value of
where
Eq. (6) must be true for the completion of the secure software design phase. Once the requirement and design phase is complete, the organization moves towards the coding phase. Whatsoever the development model an organization is following, the basic activities/phases of SDLC remain almost the same. To make the coding process secure, organizations need to follow the best security practices during coding as mentioned in Eq. (7).
where
The weighted total of coding practices must be greater than the set threshold value for secure coding. Once the coding is done securely, the software team moves towards the testing and integration phase. This phase is critical as all the bugs and errors must be removed during this phase otherwise software will be handover to the customer after the completion of this phase. Customer acceptability is inevitable for business continuity and project acceptance therefore security of the testing and integration phase must be ensured. The organizations need to follow security best practices during this phase as shown in Eq. (9).
where
The weighted total of best testing and integration practices should result in more than the set threshold value for ensuring the security of this phase.
The last phase of SDLC is a deployment where software is installed in its working environment, any change requested by the user is accommodated at this stage. This phase should be planned carefully to avoid any inconsistency and dissatisfaction from the user. According to the proposed model, a set of best practices need to be followed during this phase to make it secure and satisfactory. Eq. (11) illustrates the best practices of the deployment phase.
where
The weighted total of the best practices incorporated in the deployment phase must be greater than the set value of the threshold for the secure execution of this phase.
Once all the phases of SDLC are done while considering security as a priority and incorporating security best practices in SDLC. The organizations need to check the overall security of the project against a threshold value that is set for the project based on its nature. The accumulative security can be calculated using the formula of Eq. (13)
where accumulative security must be greater than the set value of the accumulative threshold as shown in Eq. (14)
Once the organization achieves accumulative security for its developed software by incorporating the best practices mentioned in the proposed framework, the resultant software is resistant against security vulnerabilities and threats.
5 Framework Evaluation Using Case Study
Security is inevitable for all kinds of software projects; however, it varies from project to project. Some systems are security-critical as compared to others. The traditional security mechanism of P&P is sometimes more costly and complex. Therefore, security must be incorporated in the overall SDLC. There exist various approaches for integrating security into SDLC but still, the problem persists. To handle security in overall SDLC, we have proposed a secure SDLC framework. According to the proposed framework, Security must be incorporated from the beginning until the software is deployed in its working environment.
The organization XYZ follows the proposed framework, it set the values for different parameters according to the project's nature. The concept mapping technique is used to measure the actual values of best practices used in various phases of SDLC. In this technique, important concepts related to the practice are identified and a panel of a software team is asked to map these concepts based on their understanding. This technique is very useful for measuring qualitative attributes [84–86]. The last column of Tab. 7 shows the obtained value for each security best practice using the concept mapping technique. Column 3 of Tab. 7 shows the weight for each practice that was decided based on the nature of the project and the importance of that practice for the project's security.
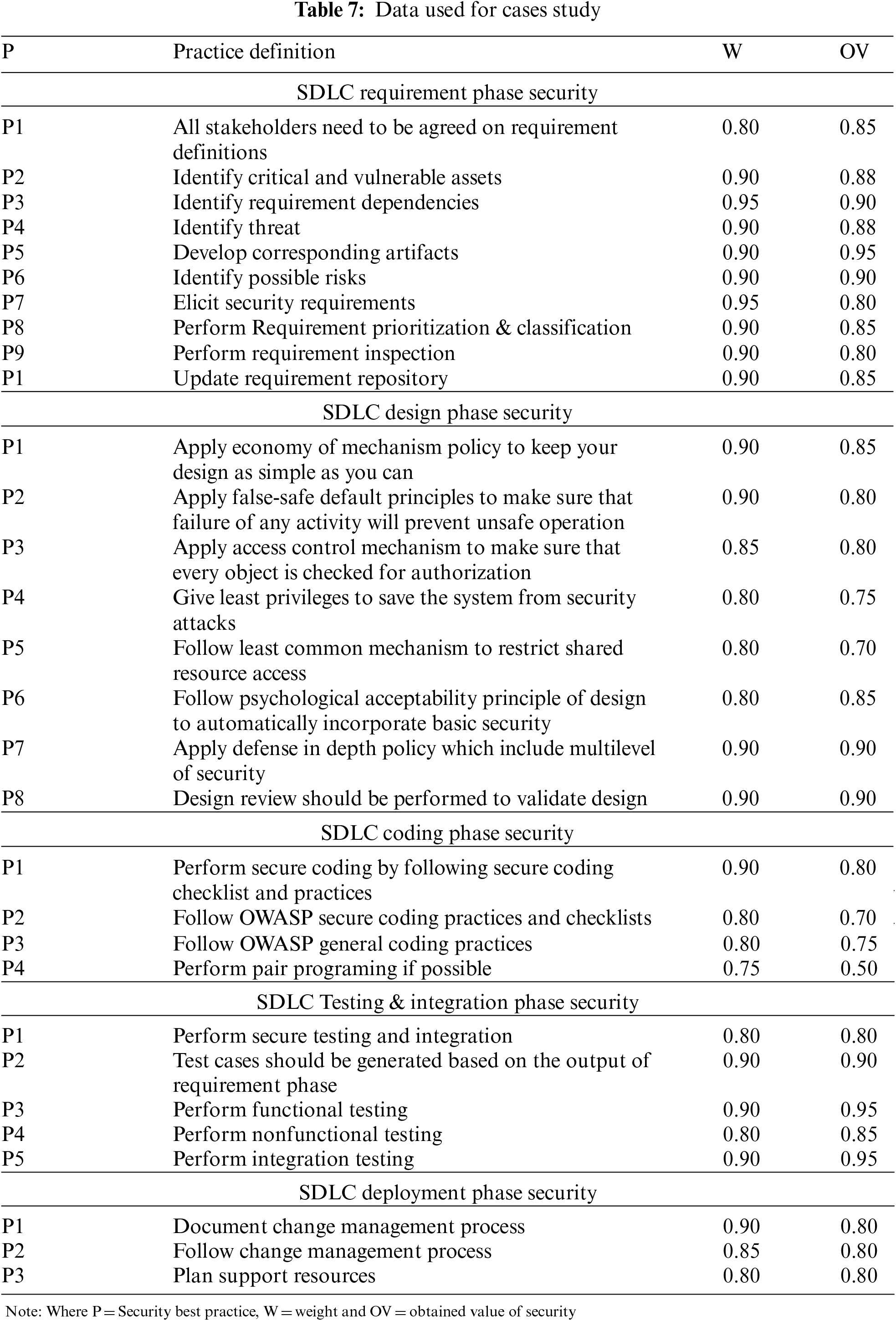
The total value of
Similarly,
The obtained security value of
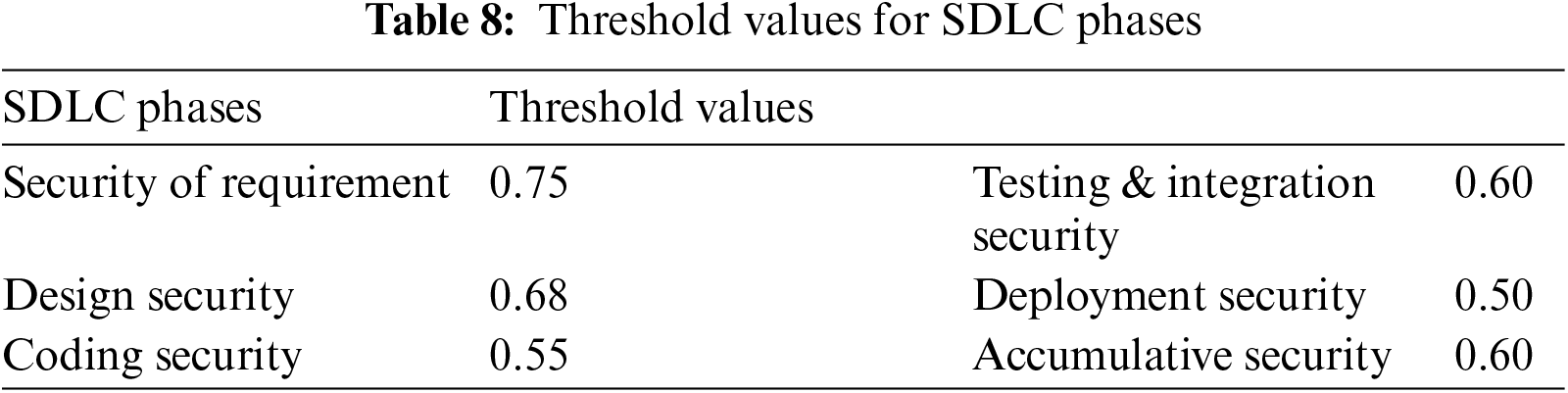
The obtained security value for the coding phase is 0.56 while the threshold value is 0.55. This shows that organizations need to incorporate security best practices during the SDLC coding phase as mentioned in the proposed framework.
The security values of the testing & integration phase can be calculated by using the formula.
The security value for testing and integration phase obtained after applying security best practices as mentioned in the proposed framework is 0.768 which is higher than the threshold value of 0.60. This shows that the proposed framework helps improve the security of testing & integration phase of SDLC.
The obtained security value for the deployment phase is 0.68 which is greater than the threshold value of 0.50 which shows that security best practices need to be incorporated in the SDLC deployment phase.
Now we find the accumulative security by using the formula below.
The obtained value for accumulative security is 0.70 which is also greater than the threshold value for the cumulative security of 0.60. The results of the case study show that the proposed framework helps improve the security of SDLC.
Security is one of the important factors that need to be considered from the very beginning of the software development process. Bugs and errors which are detected in the early phases of development are easy and cheap to handle as compared to the ones which are captured during later phases. Therefore, incorporating security in overall SDLC is inevitable for secure software development as well as organizations’ business continuity and avoiding rework. Traditionally, security is considered an afterthought activity that is handled by creating patches for the flaws identified during testing of the project or after deployment. However, the P&P strategy is not easy to implement in today's software development environment where billions of devices are interconnected, and software has to work as an integral part of the overall system.
To incorporate security in the overall development cycle, we have done a detailed literature review and identified the best practices that help manage security in SDLC. Based on the identified security best practices, we have formulated a secure SDLC framework. The structure of the framework that has been suggested is two-dimensional. The phases of SDLC are represented on the horizontal axis, while the vertical axis is separated into three layers; layer 1 highlights the critical tasks performed in the corresponding SDLC process. Layer 2 describes the security issues involved in the SDLC phase while best practices for overcoming the listed security problems are discussed in layer 3. The proposed framework was modeled mathematically and was also evaluated using a case study. The case study results show that incorporating security best practices in different phases of SDLC improve software security.
One of the most critical things to be considered from the start of the software development process is security. When bugs and defects are discovered early in the production process, they are easier and less expensive to fix than those discovered later. In the past, many software failed due to negligence of the security factor. Testing the software for security after development is not only time-consuming and complex; rather, it increases the time and cost of the project. To avoid complexity and project failure at a later stage, it is necessary to consider security as an important attribute of the software from the beginning of the project until the deployment. To address this issue, we have provided a framework based on existing security best practices for different phases of SDLC. The proposed framework was evaluated using a mathematical model and a case study and results show that the proposed framework helps improve the security of SDLC.
In the future, we are planning to extend the proposed framework by incorporating more security best practices and evaluating it on a security-critical project.
Funding Statement: The authors received no specific funding for this study
Conflicts of Interest: The authors declare that they have no conflicts of interest to report regarding the present study.
1. S. F. Wen and B. Katt, “Learning software security in context: An evaluation in open source software development environment,” in Proc. ARES, Canterbury, UK, pp. 1–10, 2019. [Google Scholar]
2. M. Humayun, M. Niazi, N. Z. Jhanjhi, M. Alshayeb and S. Mahmood, “Cyber security threats and vulnerabilities: A systematic mapping study,” Arabian Journal for Science and Engineering, vol. 45, no. 4, pp. 1–19, 2020. [Google Scholar]
3. S. Dotcenko, A. Vladyko and I. Letenko, “A fuzzy logic-based information security management for software-defined networks,” in Proc ICACT, Phoenix Park, Pyeong Chang, Korea, pp. 167–171, 2014. [Google Scholar]
4. W. Khreich, S. S. Murtaza, A. H. Alhadj and C. Talhi, “Combining heterogeneous anomaly detectors for improved software security,” Journal of Systems and Software, vol. 137, no. 1, pp. 415–429, 2018. [Google Scholar]
5. S. Hosseinzadeh, S. Rauti, S. Lauren, J. M. Makela and J. Holvitie et al., “Diversification and obfuscation techniques for software security: A systematic literature review,” Information and Software Technology, vol. 104, no. 1, pp. 72–93, 2018. [Google Scholar]
6. D. K. Alferidah and N. Z. Jhanjhi, “A review on security and privacy issues and challenges in internet of things,” International Journal of Computer Science and Network Security, vol. 20, no. 4, pp. 263–286, 2020. [Google Scholar]
7. D. K. Alferidah and N. Jhanjhi, “Cybersecurity impact over big data and IoT growth, in Proc ICCI, Istanbul, Turkey, pp. 103–108, 2020. [Google Scholar]
8. O. L. Ben, G. Chehrazi, E. Bodden, P. Tsalovski and A. D. Brucker, “Time for addressing software security issues: Prediction models and impacting factors,” Data Science and Engineering, vol. 2, no. 2, pp. 107–124, 2017. [Google Scholar]
9. B. Kim, “Open source software security issues and applying a secure coding scheme,” KIISE Transactions on Computing Practices, vol. 23, no. 8, pp. 487–491, 2017. [Google Scholar]
10. S. Z. Hlaing and K. Ochimizu, “An integrated cost-effective security requirement engineering process in SDLC using FRAM,” in Proc CSCI, Las Vegas, Nevada, USA, pp. 852–857, 2018. [Google Scholar]
11. B. Sugiantoro, M. Anshari and D. Sudrajat, “Developing framework for web based e-commerce: Secure-SDLC, Journal of Physics: Conference Series, vol. 1566, no. 1, pp. 012020, 2020. [Google Scholar]
12. A. M. Fernandes, A. Pai and L. M. Colaco, “Secure SDLC for IoT based health monitor,” in Proc ICECA, Coimbatore, India, pp. 1236–1241, 2018. [Google Scholar]
13. R. Khaim, S. Naz, F. Abbas, N. Iqbal and M. Hamayun, “A review of security integration technique in agile software development,” International Journal of Software Engineering & Applications, vol. 7, no. 3, pp. 49–68, 2016. [Google Scholar]
14. D. A. Arrey, “Exploring the integration of security into Software Development Life Cycle (SDLC) methodology,” Ph.D. dissertation, Colorado Technical University, Colorado, 2019. [Google Scholar]
15. S. Kang and S. Kim, “CIA-Level driven secure SDLC framework for integrating security into SDLC process,” Journal of the Korea Institute of Information Security & Cryptology, vol. 30, no. 5, pp. 909–928, 2020. [Google Scholar]
16. T. Bhuvaneswari and S. Prabaharan, “A survey on software development life cycle models,” International Journal of Computer Science and Mobile Computing, vol. 2, no. 5, pp. 262–267, 2013. [Google Scholar]
17. M. Droppa, B. Matej and M. Haraka, “Cyber threat assessment report in selected environment conducted by choosen technology of firewalls,” Science & Military Journal, vol. 12, no. 2, pp. 37–41, 2017. [Google Scholar]
18. S. S. Chakkaravarthy, D. Sangeetha and V. Vaidehi, “A survey on malware analysis and mitigation techniques,” Computer Science Review, vol. 32, no. 1, pp. 1–23, 2019. [Google Scholar]
19. H. Yang and F. Wang, “Wireless network intrusion detection based on improved convolutional neural network,” IEEE Access, vol. 7, no. 1, pp. 64366–64374, 2019. [Google Scholar]
20. A. M. Hassan, S. Mahmood, M. Alshayeb and M. Niazi, “A maturity model for secure software design: A multivocal study,” IEEE Access, vol. 8, no. 1, pp. 215758–215776, 2020. [Google Scholar]
21. M. A. Hamid, Y. Hafeez, B. Hamid, M. Humayun and N. Jhanjhi, “Towards an effective approach for architectural knowledge management considering global software development,” International Journal of Grid and Utility Computing, vol. 11, no. 6, pp. 780–791, 2020. [Google Scholar]
22. M. Haris, M. Alshayeb, S. Mahmood and M. Niazi, “An empirical study to improve software security through the application of code refactoring,” Information and Software Technology, vol. 96, no. 1, pp. 112–125, 2018. [Google Scholar]
23. H. Sandra, “Are software security issues a result off in software development methodologies,” Ph.D. dissertation, Utica College, New York, USA, 2020. [Google Scholar]
24. S. Hamza and M. Naveed, “Sok: Anatomy of data breaches,” Proceedings on Privacy Enhancing Technologies, vol. 4, no. 1, pp. 153–174, 2020. [Google Scholar]
25. Positive Technologies, Web Applications vulnerabilities and threats: Statistics for 2019, https://www.ptsecurity.com/ww-en/analytics/web-vulnerabilities-2020/, Accessed on March 2021. [Google Scholar]
26. M. Dawson, D. N. Burrell, E. Rahim and S. Brewster, “Integrating software assurance into the software development life cycle (SDLC),” Journal of Information Systems Technology and Planning, vol. 3, no. 6, pp. 49–53, 2010. [Google Scholar]
27. Y. H. Tung, S. C. Lo, J. F. Shih and H. F. Lin, “An integrated security testing framework for secure software development life cycle,” in Proc APNOMS, pp. 1–4, Kanazawa, Japan, 2018. [Google Scholar]
28. M. Niazi, A. M. Saeed, M. Alshayeb, S. Mahmood and S. Zafar, “A maturity model for secure requirements engineering,” Computers & Security, vol. 95, no. 1, pp. 101852, 2020. [Google Scholar]
29. B. Subedi, A. Alsadoon, P. W. C. Prasad and A. Elchouemi, “Secure paradigm for web application development,” in Proc RoEduNet, Bucharest, Romania, pp. 1–6, 2016. [Google Scholar]
30. M. Alenezi and S. Almuairfi, “Security risks in the software development lifecycle,” International Journal of Recent Technology and Engineering (IJRTE), vol. 8, no. 1, pp. 13, 2019. [Google Scholar]
31. A. N. Karim, A. Albuolayan, T. Saba and A. Rehman, “The practice of secure software development in SDLC: An investigation through existing model and a case study,” Security and Communication Networks, vol. 18, no. 9, pp. 5333–5345, 2016. [Google Scholar]
32. A. H. A. Kamal, C. C. Y. Yen, G. J. Hui and P. S. Ling, “Risk assessment, threat modeling and security testing in SDLC,” arXiv preprint arXiv: 2012.07226, pp. 1–13. [Google Scholar]
33. N. Nazir and M. K. Nazir, “A review of security issues in SDLC,” American Scientific Research Journal for Engineering, Technology, and Sciences (ASRJETS), vol. 46, no. 1, pp. 247–259, 2018. [Google Scholar]
34. J. Danahy, “The ‘phasing-in'of security governance in the SDLC,” Network Security, vol. 12, no. 1, pp. 15–17, 2008. [Google Scholar]
35. M. Nabil, M. Niazi, M. Alshayeb and S. Mahmood, “Exploring software security approaches in software development lifecycle: A systematic mapping study,” Computer Standards & Interfaces, vol. 50, no. 1, pp. 107–115, 2017. [Google Scholar]
36. M. Asadullah, R. K. Yadav and V. Namdeo, “A survey on security issues and challenges in cloud computing,” International Journal of Innovative Research in Technology and Management, vol. 4, no. 4, pp. 43–50, 2020. [Google Scholar]
37. Y. A. Bangash and Y. E. Salhi, “Security issues and challenges in wireless sensor networks: A survey,” IAENG International Journal of Computer Science, vol. 44, no. 2, pp. 94–108, 2017. [Google Scholar]
38. A. Yosef and Q. H. Mahmoud, “Cyber physical systems security: Analysis, challenges and solutions,” Computers & Security, vol. 68, no. 1, pp. 81–97, 2017. [Google Scholar]
39. F. A. Bukhsh, Z. A. Bukhsh and M. Daneva, “A systematic literature review on requirement prioritization techniques and their empirical evaluation,” Computer Standards & Interfaces, vol. 69, no. 1, pp. 103389, 2020. [Google Scholar]
40. A. Ishfaq, M. Asif, M. Shahbaz, A. Khalid and M. Rehman et al., “Text categorization approach for secure design pattern selection using software requirement specification,” IEEE Access, vol. 6, no. 1, pp. 73928–73939, 2018. [Google Scholar]
41. A. Yasemin, C. Stransky, D. Wermke, C. Weir and M. L. Mazurek et al., “Developers need support, too: A survey of security advice for software developers,” in Proc SecDev, Cambridge, MA, USA, pp. 22–26, 2017. [Google Scholar]
42. W. Brandon, S. Mengel and A. Ertas, “An evolutionary approach for the hierarchical scheduling of safety-and security-critical multicore architectures,” Computers, vol. 9, no. 3, pp. 71, 2020. [Google Scholar]
43. A. A. Adanna and O. F. Nonyelum, “Criteria for choosing the right software development life cycle method for the success of software project,” IUP Journal of Information Technology, vol. 16, no. 2, pp. 39–65, 2020. [Google Scholar]
44. M. K. Sharma, “A study of SDLC to develop well engineered software,” International Journal of Advanced Research in Computer Science, vol. 8, no. 3, pp. 520–523, 2017. [Google Scholar]
45. S. U. Rehman and V. Gruhn, “An effective security requirements engineering framework for cyber-physical systems,” Technologies, vol. 6, no. 3, pp. 65, 2018. [Google Scholar]
46. M. Humayun and N. Jhanjhi, “Exploring the relationship between GSD, knowledge management, trust and collaboration,” Journal of Engineering Science and Technology, vol. 14, no. 2, pp. 820–843, 2019. [Google Scholar]
47. S. Pukdesree, “The comparative study of collaborative learning and SDLC model to develop IT group projects,” TEM Journal, vol. 6, no. 4, pp. 800–809, 2017. [Google Scholar]
48. E. I. Tatli, “Developer-oriented web security by integrating secure SDLC into IDEs,” Sakarya University Journal of Computer and Information Sciences, vol. 1, no. 1, pp. 36–44, 2018. [Google Scholar]
49. S. Turpe, “The trouble with security requirements,” in Proc REW, Lisbon, Portugal, pp. 122–133, 2017. [Google Scholar]
50. M. Hamza, H. Hu, M. A. Akbar, F. Mehmood and Y. Hussain et al., “SIOT-RIMM: Towards secure IOT-requirement implementation maturity model,” in Proc EASE, Trondheim, Norway, pp. 463–468, 2020. [Google Scholar]
51. R. Scroggins, “SDLC and development methodologies,” Global Journal of Computer Science and Technology, vol. 7, no. 7, pp. 1–3, 2014. [Google Scholar]
52. S. Rani, “A detailed study of software development life cycle (SDLC) models,” International Journal of Engineering and Computer Science, vol. 6, no. 7, pp. 22097, 22100, 2017. [Google Scholar]
53. E. Aruna, “Design of non-functional requirement (security) using security design patterns in architecture phase to develop secure SDLC,” International Journal of Engineering Research & Technology (IJERT), vol. 4, no. 11, pp. 1–5, 2015. [Google Scholar]
54. J. C. Santos, K. Tarrit and M. Mirakhorli, “A catalog of security architecture weaknesses,” in Proc ICSAW, Gothenburg, Sweden, pp. 220–223, 2017. [Google Scholar]
55. N. Hernan, J. Antonio and M. Villavicencio., “Systematic mapping of the literature on secure software development,” IEEE Access, vol. 9, no. 1, pp. 36852–36867, 2021. [Google Scholar]
56. V. Mohino, J. B. Higuera, J. R. Higuera and J. A. S. Montalvo, “The application of a new secure software development life cycle (S-SDLC) with agile methodologies,” Electronics, vol. 8, no. 11, pp. 1218–1246, 2019. [Google Scholar]
57. F. Amalia, M. Kurniawan and D. T. Setiawan, “The design of traceability information system of smart packaging-based product supply chain to improve a competitiveness of apple processed agro-industry,” Journal of Information Technology and Computer Science, vol. 5, no. 3, pp. 247–254, 2020. [Google Scholar]
58. A. Imeri and D. Khadraoui, “The security and traceability of shared information in the process of transportation of dangerous goods,” in Proc NTMS, Paris, France, pp. 1–5, 2018. [Google Scholar]
59. X. Xu, Q. Lu, Y. Liu, L. Zhu and H. Yao et al., “Designing blockchain-based applications a case study for imported product traceability,” Future Generation Computer Systems, vol. 92, no. 1, pp. 399–406, 2019. [Google Scholar]
60. K. Cheung and J. Misic, “On virtual private networks security design issues,” Computer Networks, vol. 38, no. 2, pp. 165–179, 2002. [Google Scholar]
61. Y. Ali, Y. Xia, M. Linag and A. Hammad., “Secure design for cloud control system against distributed denial of service attack,” Control Theory and Technology, vol. 16, no. 1, pp. 14–24, 2018. [Google Scholar]
62. A. Z. Henley, K. Muclu, M. Christakis, S. D. Fleming and C. Bird, “Cfar: A tool to increase communication, productivity, and review quality in collaborative code reviews,” in Proc CHI, Montreal, Canada, pp. 1–13, 2018. [Google Scholar]
63. S. Georgiou, S. Rizou and D. Spinellis, “Software development lifecycle for energy efficiency: Techniques and tools,” ACM Computing Surveys (CSUR), vol. 52, no. 4, pp. 1–33, 2019. [Google Scholar]
64. B. C. Zapata, J. L. Aleman, A. Toval and A. Idri, “Reusable software usability specifications for mHealth applications,” Journal of Medical Systems, vol. 42, no. 3, pp. 1–9, 2018. [Google Scholar]
65. B. P. Miller and E. Heymann, “Tutorial: Secure coding practices, automated assessment tools and the SWAMP,” in Proc SecDev, Cambridge, MA, USA, pp. 124–125, 2018. [Google Scholar]
66. B. Hoisl, S. Sobernig and M. Strembeck, “Reusable and generic design decisions for developing UML-based domain-specific languages,” Information and Software Technology, vol. 92, no. 1, pp. 49–74, 2017. [Google Scholar]
67. H. Assal and S. Chiasson, “Think secure from the beginning a survey with software developers,” in Proc CHI, Glasgow, UK, pp. 1–13, 2019. [Google Scholar]
68. A. Hala and S. Chiasson, “Security in the software development lifecycle,” in Proc SOUPS, Baltimore, USA, pp. 281–296, 2018. [Google Scholar]
69. A. Papageorgiou, M. Strigkos, E. Politou, E. Alepis and A. Solanas et al., “Security and privacy analysis of mobile health applications: The alarming state of practice,” IEEE Access, vol. 6, no. 1, pp. 9390–9403, 2018. [Google Scholar]
70. N. Meng, S. Nagy, D. Yao, W. Zhuang and A. A. Gustawo, “Secure coding practices in java: Challenges and vulnerabilities,” in Proc ICSE, Gothenburg, Sweden, pp. 372–383, 2018. [Google Scholar]
71. D. R. Lakshmi and S. S. Mallika, “A review on web application testing and its current research directions,” International Journal of Electrical and Computer Engineering, vol. 7, no. 4, pp. 2132, 2017. [Google Scholar]
72. K. Sneha and G. M. Malle, “Research on software testing techniques and software automation testing tools,” in Proc ICECDS, Chennai, Tamil Nadu, India, pp. 77–81, 2017. [Google Scholar]
73. J. Choliz, J. Vilas and J. Moreira, “Independent security testing on agile software development: A case study in a software company,” in Proc ARES, Toulouse, France, pp. 522–531, 2015. [Google Scholar]
74. T. Rangnau, R. Buijtenen, F. Fransen and F. Turkmen, “Continuous security testing: A case study on integrating dynamic security testing tools in CI/CD pipelines,” in Proc EDOC, Eindhoven, Netherlands, pp. 145–154, 2020. [Google Scholar]
75. P. P. Kumar, “Development of software testing techniques for early fault detection,” Journal of Advancement in Parallel Computing, vol. 3, no. 3, pp. 15–23, 2021. [Google Scholar]
76. A. K. Alvi, M. Zulkernine, “A security pattern detection framework for building more secure software,” Journal of Systems and Software, vol. 171, no. 1, pp. 110838–110860, 2021. [Google Scholar]
77. S. Malik, “Software testing: Essential phase of SDLC and a comparative study of software testing techniques,” International Journal of System & Software Engineering, vol. 5, no. 2, pp. 38–45, 2017. [Google Scholar]
78. P. Dehraj, A. Sharma and P. Grover, “Maintenance assessment guidelines for autonomic system using ANP approach,” Journal of Statistics and Management Systems, vol. 22, no. 2, pp. 289–300, 2019. [Google Scholar]
79. A. Wang, H. Wang, B. Jiang and W. K. Chan, “Artemis: An improved smart contract verification tool for vulnerability detection,” in Proc DSA, Xi'an, China, pp. 173–181, 2020. [Google Scholar]
80. S. M. Rahaman and A. Kumari, “A model for corrective software maintenance effort estimation after privacy leak detection in social network,” in Proc AISP, Amaravati, India, pp. 1–10, 2020. [Google Scholar]
81. M. Bellare, J. A. GAray, R. Hauser, A. Herzberg and H. krawczyk et al., “Design, implementation, and deployment of the iKP secure electronic payment system,” IEEE Journal on Selected Areas in Communications, vol. 18, no. 4, pp. 611–627, 2000. [Google Scholar]
82. P. Frijns, R. Bierwolf and T. Zijderhand, “Reframing security in contemporary software development life cycle,” in Proc ICTMOD, Marrakech, Morocco, pp. 230–236, 2018. [Google Scholar]
83. R. A.Khan, S. U. Khan, H. U. Khan and M. Ilyas, “Systematic mapping study on security approaches in secure software engineering,” IEEE Access, vol. 9, pp. 19139–19160, 2021. [Google Scholar]
84. J. P. Donnelly, “A systematic review of concept mapping dissertations,” Evaluation and Program Planning, vol. 60, no. 1, pp. 186–193, 2017. [Google Scholar]
85. A. J. Canas, P. Reiska and A. Mollits, “Developing higher-order thinking skills with concept mapping: A case of pedagogic frailty,” Knowledge Management & E-Learning: An International Journal, vol. 9, no. 3, pp. 348–365, 2017. [Google Scholar]
86. R. D. Mauricio, L. Veado, R. T. Moreira, E. Figueiredo and H. Costa, “A systematic mapping study on game-related methods for software engineering education,” Information and Software Technology, vol. 95, no. 1, pp. 201–218, 2018. [Google Scholar]
 | This work is licensed under a Creative Commons Attribution 4.0 International License, which permits unrestricted use, distribution, and reproduction in any medium, provided the original work is properly cited. |