DOI:10.32604/cmc.2022.023840

| Computers, Materials & Continua DOI:10.32604/cmc.2022.023840 |  |
| Article |
Optimizing Energy Conservation in V2X Communications for 5G Networks
1Department of Computer Science, COMSATS University Islamabad, Lahore Campus, Lahore, Punjab, Pakistan
2Department of Computer Science and Information Technology, Virtual University of Pakistan, Lahore, Punjab, Pakistan
3Computer Science Department, University of Tabuk, Tabuk, Saudi Arabia
*Corresponding Author: Abid Sohail. Email: abidbhutta@cuilahore.edu.pk
Received: 23 September 2021; Accepted: 25 October 2021
Abstract: The smart vehicles are one of critical enablers for automated services in smart cities to provide intelligent transportation means without human intervention. In order to fulfil requirements, Vehicle-to-Anything(V2X) communications aims to manage massive connectivity and high traffic load on base stations and extend the range over multiple hops in 5G networks. However, V2X networking faces several challenges from dynamic topology caused by high velocity of nodes and routing overhead that degrades the network performance and increases energy consumption. The existing routing scheme for V2X networking lacks energy efficiency and scalability for high velocity nodes with dense distribution. In order to handle the challenges, this article proposes a scalable and energy-efficient routing scheme called Dynamic proactive reactive routing for 5G (DPR5) for high mobility speed and dense environment. As compared to existing schemes it uses a single routing table and efficiently minimizes the energy consumption in dense environment, improves node ‘s lifetime upto 42%, and optimizes network performance by reducing the packet loss ratio upto 46% in a high velocity dense environment.
Keywords: Internet of vehicles; vehicle-to-any device; energy conservation
A The Internet of things (IoT) is changing the world with an aim to improve daily life by providing diverse applications for smart homes, health care, industrial automation, consumer market, Intelligent transportation system (ITS), security and environmental monitoring [1]. The Internet of vehicles (IoV) is basically an integration of the IoT and vehicular network, in which vehicles communicate with other vehicles and IoT enabled devices located in their close proximity [2]. Different types of communication needs will exist in IoV such as Vehicle to vehicle(V2V), Vehicle to internet(V2I), Vehicle to people(V2P), Vehicle to traffic controller(V2T), Vehicle to surveillance(V2S) and this list grows on. In short, vehicles will connect to anything and thus a term V2X communication is used as shown in Fig. 1. It is important to note that vehicles communicate to the Internet through regular Fifth generation (5G) connectivity and only the communications to nodes such as vehicles, traffic controllers and people present in the surrounding environment are through adhoc network. Thus, causing a significant reduction in the amount of traffic load on the 5G base station.
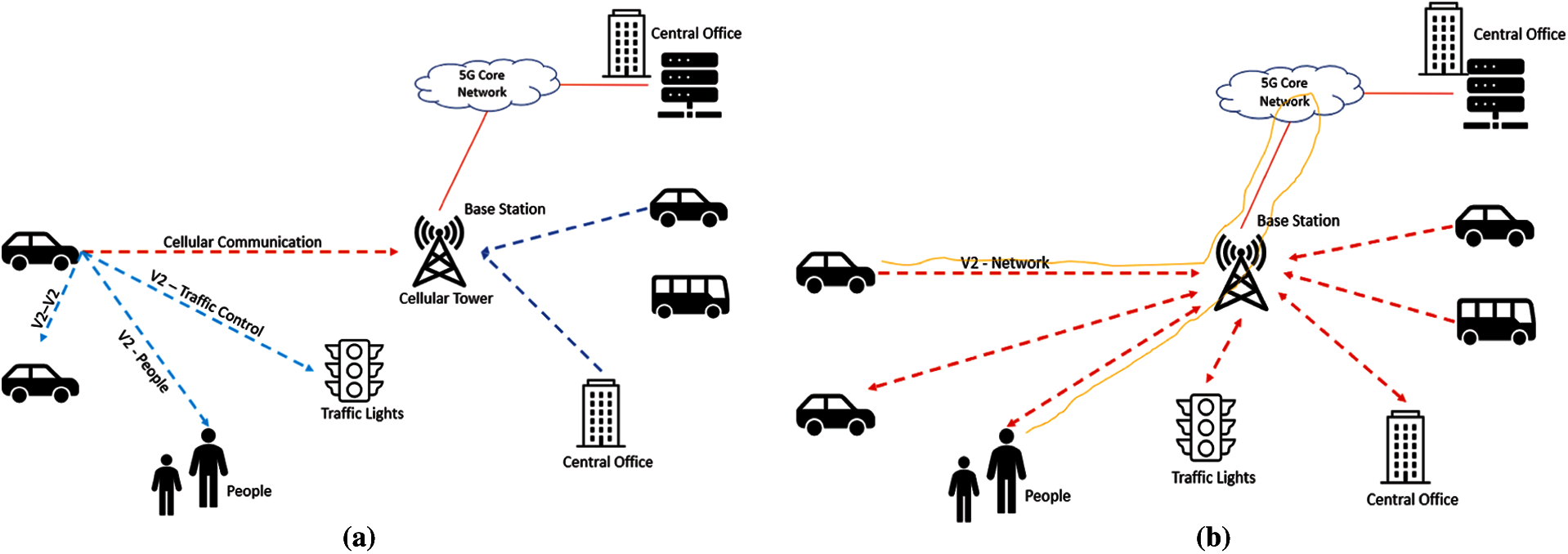
Figure 1: Types of communications (a) V2X communications (b) IoV communications
The IoV is an advanced concept of traditional Adhoc networks, and its basic implementation is similar to its predecessor technologies along with more specific requirements [3,4]. It has potential to support connectivity of a large number of devices and enables them to communicate over the Internet. It is expected that more than 20 billion devices will become part of the Internet by the end of this decade. In the absence of V2X communication support, the rapid growth in IoV and their connections will consequently bring a storm in the Internet traffic [5]. The huge boost in the Internet traffic will restrain it to achieve IoV objectives and hinder its wide applications [6]. The efficiency and effectiveness of IoV depends upon high network throughput, high availability of networks under diverse situations, ultra-low latency, energy efficiency, massive heterogeneous connectivity, and ubiquitous coverage [7]. However, current wireless technologies have limitations and are unable to fulfill the requirements, especially providing high network throughput in a dense network [8]. Vehicles in IoV form a distributed network in which all devices communicate with each other under different circumstances [9] and based on the category of devices, nodes form multiple communication models [10]. The 5G wireless technology has promised to meet deliverables set by IoTs [11]. It provides a very high data rate in an energy-efficient manner under dense network environments. It supports the architecture of an ultra-dense network (UDN) [12] where a macro cell is hierarchically split into manageable small cells according to coverage requirements, the quality of service, data rate, number of users, line of sight, and other application scenarios [13]. As the cell size becomes small, the number of base stations will increase up to 1000 cells/sq km [14]. The increase in density of base stations helps to handle massive network traffic, improve signal quality, and ultra-high-speed data rate for end-users. In addition to UDN, 5G allows direct communications across devices to reduce the dense network traffic [15] consequently in the context of IOV, the vehicle to any other devices (V2X) communications are desired. V2X communications are adhoc in nature and allow communication among vehicles, people, other vehicles, base stations, traffic, and surveillance control devices without the intervention of the base station. The direct communication across the devices is also beneficial in terms of spectrum reusability and interference mitigation [16].
Although V2X communication has many advantages, it suffers from multiple challenges as well, and must be resolved for the successful realization of V2X communications. IoV are a combination of heterogeneous devices. The mobility nature of vehicles and other devices that need to be connected is different [17]. Some devices are static like sensors or cameras which are installed at different locations while others have moderate mobility like human-centric devices. Some of them have an even higher degree of mobility, for instance, vehicular nodes in the Intelligent transport systems (ITS) are highly mobile and nodes can move at a speed of 40 m/s [18]. The mobile nature of nodes changes the network topology very frequently as various issues are associated such as increased frequency of update messages, higher flooding, and retransmissions. Thus, there is a higher probability of high packet loss and retransmission consuming more energy. The situation further aggravates with higher density and higher mobility velocities and lifetime of battery-operated devices significantly reduced.
The existing standalone proactive or reactive routing protocols are not suitable due to their inability to handle the high mobility of vehicles and higher node density. The scalability and energy efficiency in IoV are still a challenge and researchers have been adopting various approaches to address the issue [19–21].
In this paper, we introduce a routing scheme with dynamic reactive and proactive routing process selection for V2X communications to efficiently manage mobility, reduce overhead, improve the energy conservation and performance in a dense environment. Our major contribution in this article is to design an efficient routing scheme to address high speed mobility and energy efficiency. Moreover, we evaluate the scheme using MATLAB and present an analysis of performance, node ‘s lifetime in terms of energy efficiency and packet loss. Rest of the paper is organized as follows: Section 2 discusses existing routing schemes and highlights their shortcomings. Section 3 describes the proposed DPR5 scheme in detail. Experiments and results are discussed in Section 4, and finally Section 5 concludes the findings.
V2X communications are similar to device-to-device communications and ad hoc in nature with specific characteristics like fast mobility and rapid changes in topology. Furthermore, the V2X communication falls under the critical services nature as any delays, information loss or corruption may result in life threatening conditions resulting from accidents and incorrectly calculated routes. Inefficient V2X communication not only degrades the network performance but also inhibits the achievement of the desired network goals such as collecting, evaluating, and sending data to the base station. Moreover, this wastes scarce network resources as well as energy and ultimately shortens the lifetime of devices [22].
In proactive routing schemes, every node is required to maintain information of neighbors and topology of the network and information requires regular updates [23]. A routing scheme called multi-hop cellular networks (MCN) has been proposed in the literature by Othmen et al. [24] to provide connectivity to single as well as for multi hops communication. It transmits a data packet multiple times for single and multiple hop nodes and causes wastage of energy and computation resources. Furthermore, as the node density increases, it floods more and more redundant packets often leading to congestion and degradation of the network performance. In contrast, the Base-centric routing (BCN) scheme proposed by Shaikh et al. [25] efficiently utilizes the network resources in a comparatively simpler way. However, it also transmits the data packets multiple times and cannot ensure the end-to-end delay in case of congestion caused by the increased node density due to which BCN is not a scalable solution for V2X communications. A similar scheme called Cellular based multi-hop network (CBMN) was proposed in [26] to address the scalability issues by using separate transceivers for data and control packet. However, the procedure to identify the data and control packets lead to complexity of the scheme and also wastes computing resources.
The reactive routing schemes do not maintain any routing tables; rather routes are discovered on demand. A route discovery process is used to flood route request messages and receive the route responses from other nodes. The best route is selected to transmit the data packet based on some metrics. In this category, a Spectrum sharing scheme (SSS) has been proposed for cellular users and device-to-device communications by Lin et al. [27] (2014). This scheme can manage the network interference by adjusting transmit power, however it causes some scalability issues. Furthermore, the frequency division used in this scheme is not feasible with higher densities of the nodes due to the difficulties faced in identifying cellular users and D2D users. The absence of clear demarcation methods between the cellular and D2D users results in load balancing issues in the network. A similar scheme called DSR has been proposed by [28]. In this scheme only nodes become active when required and can respond to route request messages, otherwise do not participate in the route discovery process. With sleep mode, it reduces the energy consumption on nodes and reduces the route discovery overhead. However, in networks with higher node density, overhead of the route discovery process increases the delay in communications, furthermore it performs well only on static and low density and low mobility velocities. In the reactive class of routing scheme an Interference-conscious routing (ICR) scheme has been studied by Shaikh et al. [29]. It calculates the optimal route based on the minimum signal to interference noise ratio. However, it calculates the SINR at a step and may select longer routes with several relay nodes thus requiring more energy for data packet transmission.
As compared to the proactive and reactive schemes, hybrid schemes of routing are used to improve the scalability of routing. Bello et al. [30] has presented a model of an adaptive routing scheme where a centralized reactive process is used for a certain number of hops. If the hop threshold increases a distributed proactive process is used for route discovery. The route calculation process involves both the nodes and Base station (BS) and hence reduces the load on BS and results in enhanced coverage, connectivity, and throughput. However, due to three different communication modes, the route discovery process becomes complex and energy consumption increases three-fold. Moreover, the wrong selection of hop thresholds badly affects the efficiency of the routing process. To minimize the complexity of the routing with improved coverage Han et al. [31] proposed the Light dark routing protocol (LDR) scheme. It classifies the single hop nodes as light nodes and multi hop nodes as dark nodes. For dark nodes it uses the reactive route discovery and for light nodes it uses the proactive process. This scheme has improved the coverage in a simpler way, but it uses two control packets for information exchanging continuously that consumes more energy. Furthermore, it has longer end to end delays in a network with high node density and efficiency of the route discovery is dependent on mobility. Another hybrid scheme called Centralized adaptive routing (CAR) has been proposed by Shaikh et al. [25]. It uses the same common frequency for both cellular and D2D users Communications and provides an efficient solution in terms of energy consumption and coverage only for low node density networks. This model shows better power utilization for all users under the coverage of BS.
In this section, we have discussed various existing schemes in the context of V2X communications and has seen that energy efficiency and scalability are still issues faced in V2X communications. We have discussed various reactive and proactive schemes and discussed their issues in terms of performance, energy efficiency and scalability. Moreover, the hybrid schemes based on fixed hop count criteria are also inefficient in an environment with high mobility speed and node density and results in a higher routing overhead and retransmissions. In the next section, we propose a DPR5 routing scheme dynamically select the reactive and proactive route discovery and substantially reduces the energy consumption and improves the scalability.
The proactive routing for V2X communications although can provide fast route discovery and reliability in the packet delivery but incurs large overhead and all nodes within the proximity transmit hello message periodically to find the changes. In contrast, the reactive or on-demand routing approach has lesser overhead and lesser resource consumption, but it results in high latency during the route calculation and involves excessive flooding and network clogging. DPR5 design is focused to avoid network clogging in V2X communications, reduce routing overhead and delay in the route discovery process. The scheme consists of two sub-processes, namely a Proactive routing process(PRP) and Reactive routing process (RRP). Both processes coordinate through four coordination points where control of route discovery is transferred from PRP to RRP or vice versa.
The PRP route discovery process is shown in Fig. 2, where each active node broadcasts an inquiry packet and builds a periodically updated Directly connected node ‘s list (DCL) that contains the addresses of Directly connected neighbors(DCN). The Data buffer status (BUFS) is continuously checked by waiting for the data (WFD) signal and updates the Data state status (DSS) flag. If DSS status is ready then PRP checks the routing table and if there is no rout existing in the table, the DCL list is checked otherwise the route entry is saved. If there is no matching entry in the DCL, the control of the route discovery is transferred to RRP process as indicated in Fig. 2 with coordination point A. Similarly, after the transmission of data packet, if the acknowledgement is not received during the specified threshold value, the control of route discovery is transferred to RRP as indicated with the coordination point D otherwise DSS is checked for next data packet transmission.
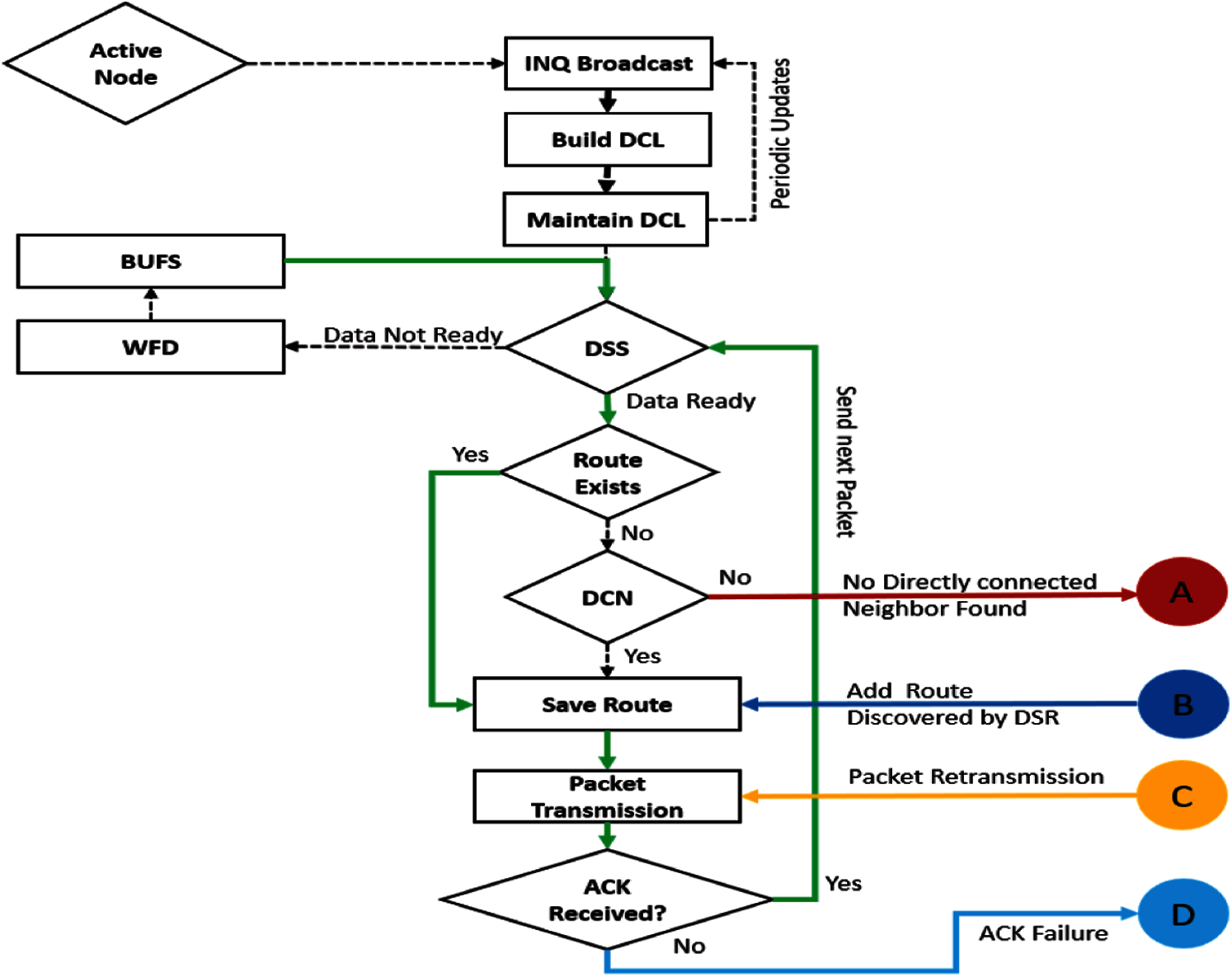
Figure 2: PRP routing subprocess
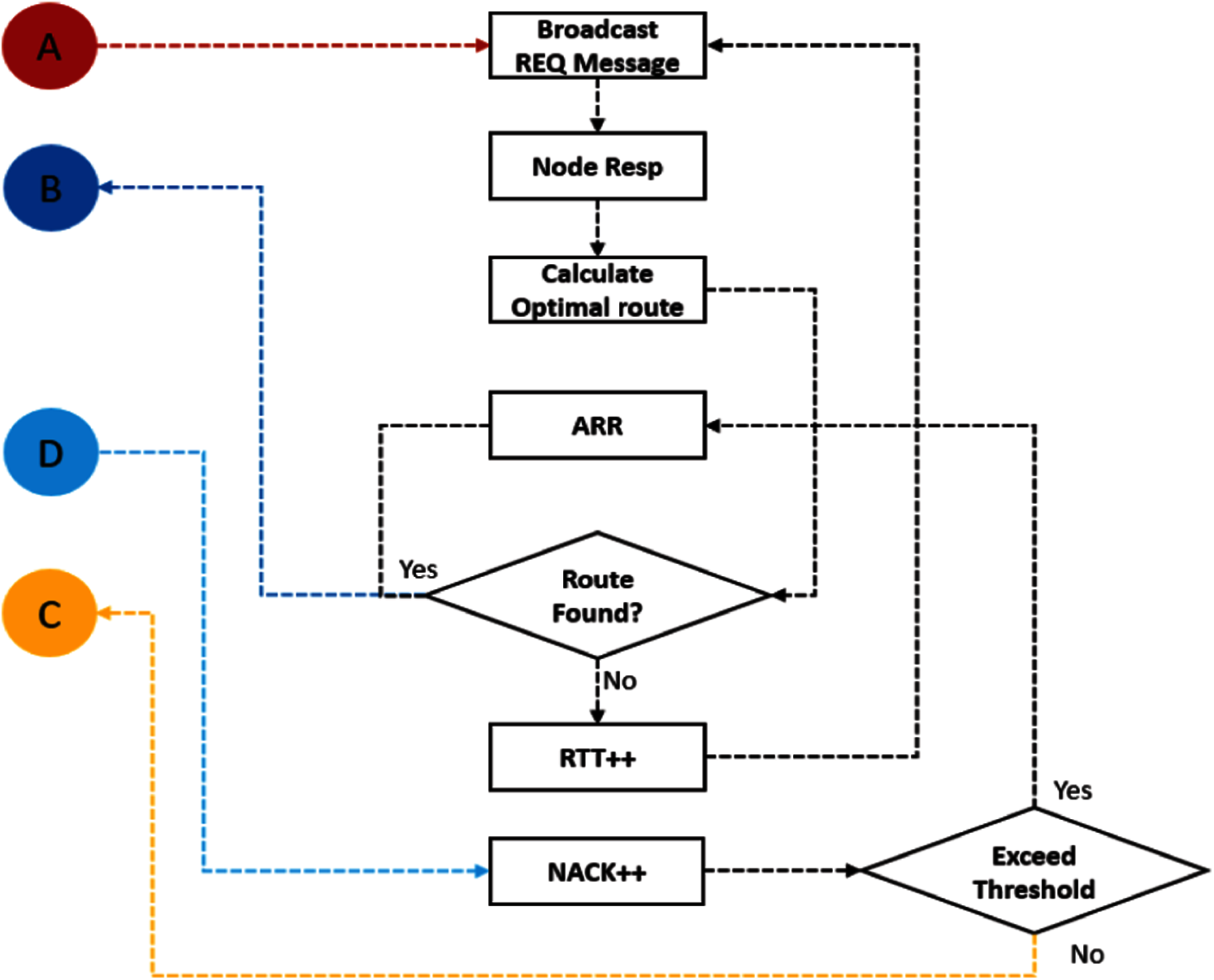
Figure 3: RRP routing subprocess
The RRP route discovery subprocess is shown in Fig. 3 which is initiated through the coordination point A, by broadcasting route requests where the node responses are used to calculate the optimal route.
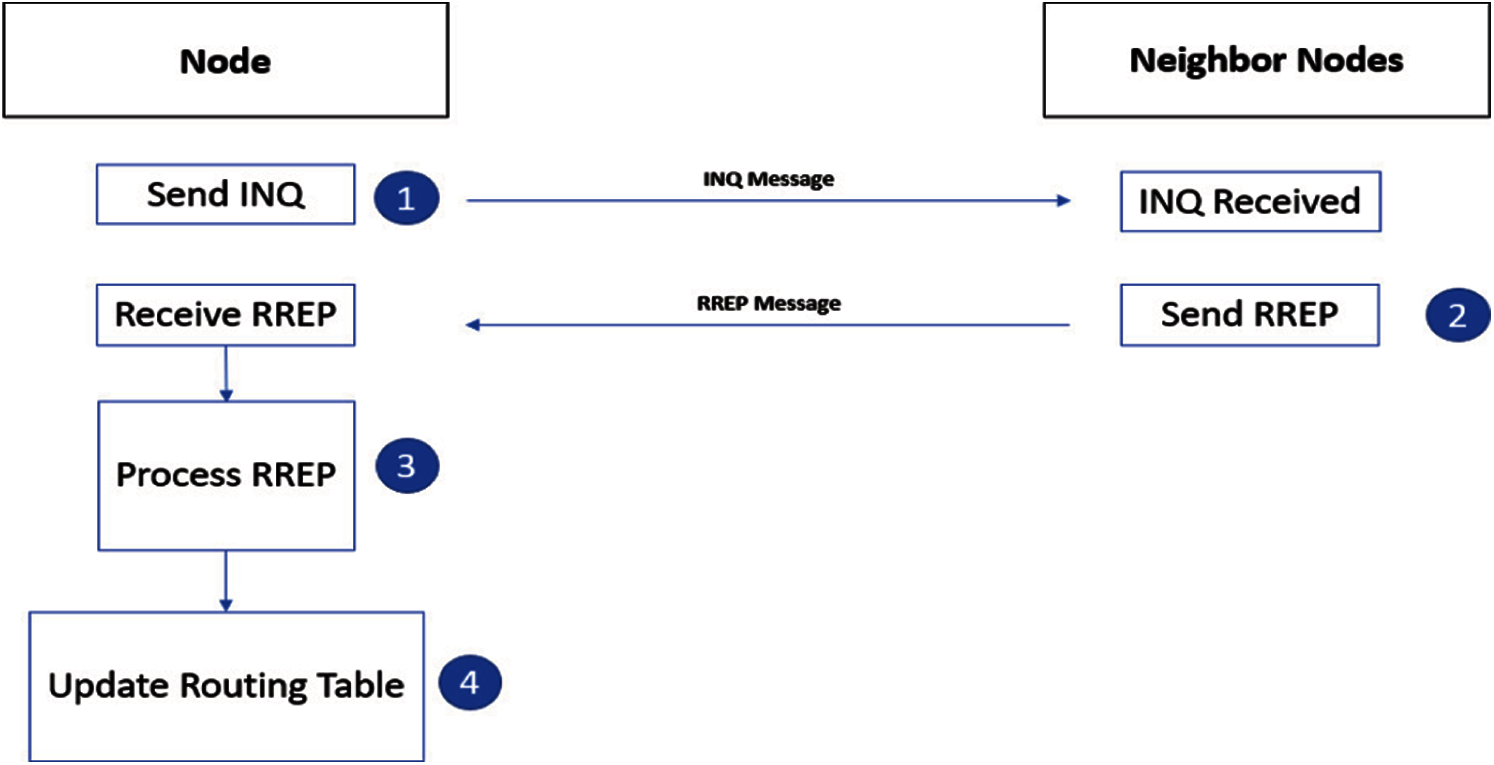
Figure 4: Procedure for routing table updates
If a suitable route is found it is propagated to PRP via coordination point B and after saving the route data packet is transmitted, otherwise Round trip time(RTT) is incremented, and the process is repeated till RTT threshold is reached. Similarly, if a Negative acknowledgement (NAK) is received from PRP, it is incremented till the NAK threshold. During this adoptive route recovery (ARR) is used to find an optimal route that is propagated back to PRP. The coordination point C is used to inform the PRP when no route exists to the destination. According to the spatial locality principle, the probability of communication with the neighbor's nodes is quite high as compared to the nodes which are located at a far distance from the target node.
In Eq. (1) N is the total number of nodes into the network,
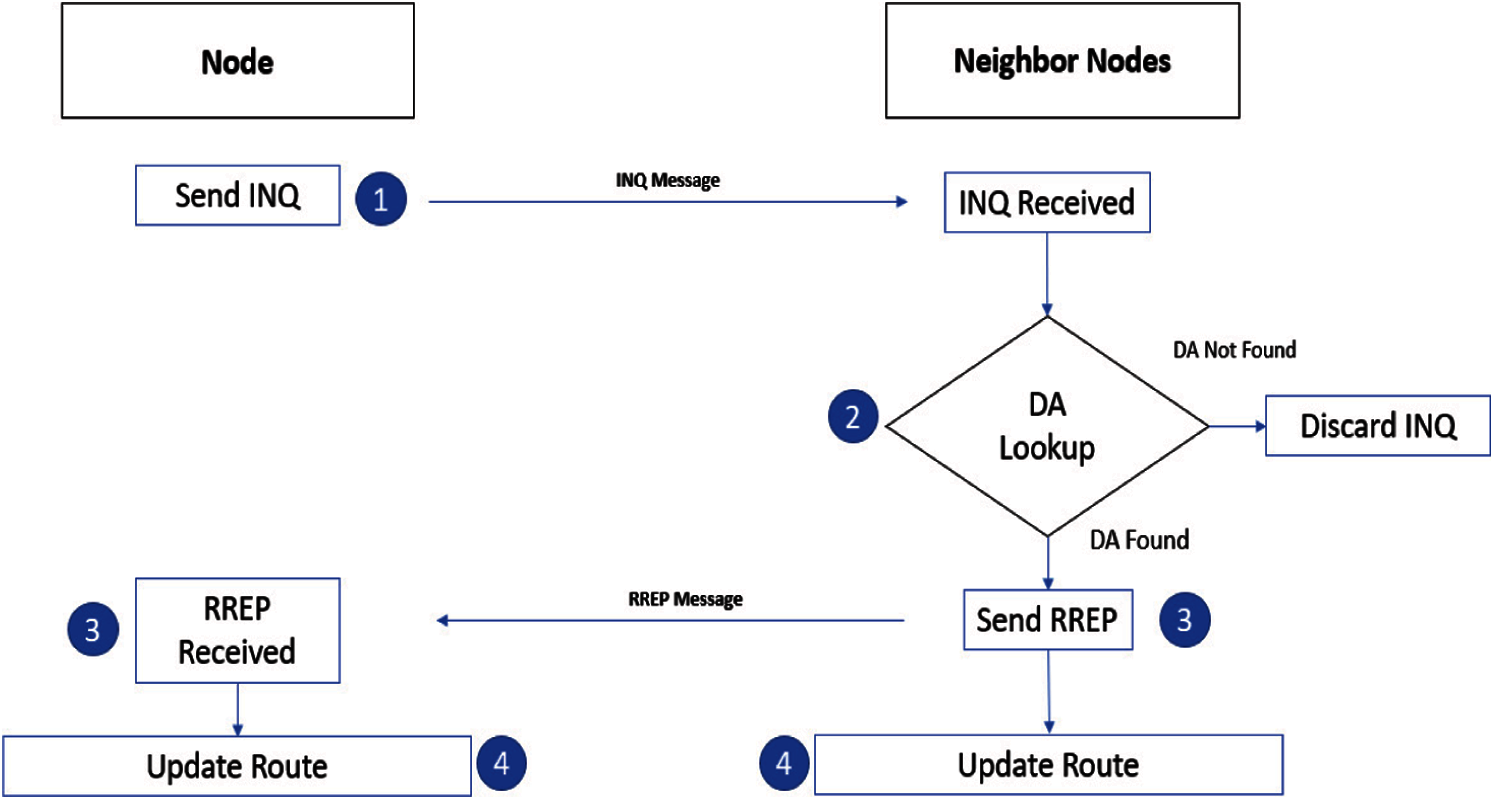
Figure 5: Inquiry message broadcast in RRP
The PRP starts with an INQ message for updating the routing table. During INQ broadcast, the nodes that sent INQ message for their neighboring nodes are included in the routing table and all other nodes are filtered out as shown in Fig. 5.
All the nodes that are under direct coverage of the initiator node receive and extract the INQ message packet, however receiving nodes do not rebroadcast the message. Based on INQ massage each node generates a routing table that includes source and destination address. If the source node does not exist in the neighbor table, an entry into the table is created for that source node. The update of routing table is required when topological change found in the INQ message, and the routing table is updated accordingly. Whenever a node is required to send data, it checks the routing table. If a routing entry is found then start sending data to its destination, otherwise destination may exist at multi hops or doesn't present in the network. We used a DSR reactive approach for multi-hop communication.
The RRP is similar to the DSR, and it is a combination of two mechanisms, which work together to allow on-demand route discovery and maintenance for routes. The route discovery process is triggered when a source node wants to send data packets to any destination node route required from a source to destination. This is an on-demand process in which no periodic INQ message is broadcast into the network and the route discovery process is triggered only if there are some data packets to be sent. When a source node wants to send data packets, it generates a Route request (RREQ) inquiry message and places the source and destination address into it. The broadcast INQ massage consists of source ID, destination ID, residual energy, and source location information. All nodes that are under BS coverage receive INQ messages, extract it, and check the destination address. If the receiving node is the intended destination itself or has a destination route into its routing table, then respond otherwise discard it. Only those nodes that have destination address, or it is required destination, will respond to RREQ and disregard INQ message otherwise. In the responding message format, they embedded destination address, energy level, hop count up to the destination and relay nodes address. Based on responding RREQ messages, BS establishes a route from source to destination. BS share the route information with the initiator and check whether they are ready to send data. When all nodes such as a source, destination, and relay nodes become ready, the BS informs the source to send data through delay nodes up to the destination node. With the established route, source nodes continue to send data and receive acknowledgment (ACK) signals from the recipient nodes. In the route maintenance process route are ensured to be maintained by sending and receiving ACK messages to its respective nodes. If due to some reasons ACK messages are not received by sending nodes up to some threshold number, then an error message is broadcast into the network which indicates that route does not exist, so the route discovery process again originated. Each node has limited storage capacity for data packets. When any nodes want to send data, it places packets into its data buffer. Nodes periodically check the buffer and if data is found then find the route through a proactive or reactive routing process and send it to its destination node. If there is no data to send in its data buffer, wait for the arrival of data packets to send.
The process of discovering a route is comparatively a complex and critical procedure, especially in the case of the reactive approach. Without saving the route information, the routes are searched again and again before sending multiple packets to the same destination. Route information is saved in a Routing buffer (RB) and before sending data to a destination instead of directly initiating the route discovery process, RB is checked for the existence of any matching route. The RB is a fast but limited capacity cache that saves only one entry into its buffer space. As the density of the network is increased, the probability of the indirect communications decreases as per Eq. (1), thus the load on route buffer is also reduced. When a route is found whether it's through a proactive or reactive routing process, it is saved into it's the RB. An entry in the RB contains information such as the last route or the current route from the source to destination. The RB use can potentially reduce the route discovery time, energy consumption, and other computational resources. The route establishment process is confirmed with an acknowledgment mechanism. On receipt of a packet, the receiving node must acknowledge the initiator through the same route. If the initiator receives the ACK message, it sends the next data packet, otherwise it increments the NAK counter, which indicates the ACK message is not received. The receipt of an ACK message is the only way to check the status of a route and confirm that a data packet is received and its ACK was sent. However, during this process a route may get disturbed and results in failure of receipt of ACK message.
This issue generally occurs in multi hops communication. If an ACK message is not received, the NAK counter is incremented. The NAK counter has a threshold of 5 that means if the NAK counter reaches its limit, a signal is broadcasted into the network that the current route is no more valid, and the route discovery process needs to be started. Before sending every data packet, the first of all the NAK buffer threshold is checked if it exceeds its threshold limit then route the route is again discovered otherwise continue to send data packets. When a route is not found through a proactive or reactive approach, an error message is broadcast into the network. It shows that the destination node does not exist in the network.
4 Measurements and Experimental Results
The proposed routing scheme was evaluated in MATLAB, and various parameters selected for experiments are shown in Tab. 1.
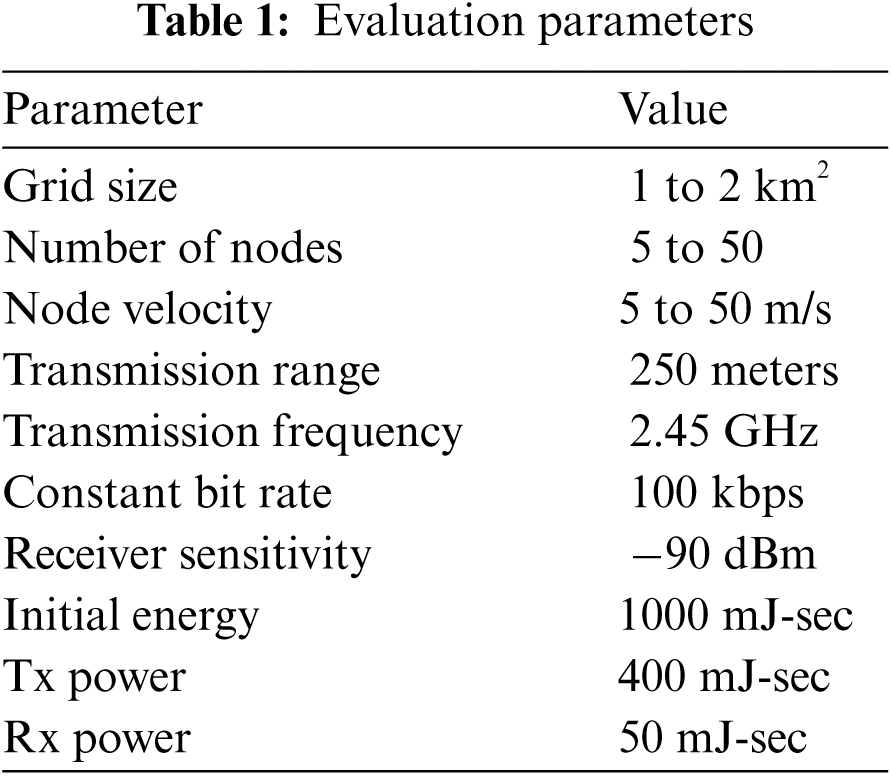
In the experimental scenario, the initial network is farmed in a two-dimensional free space where the position and direction of nodes are set randomly. The transmission power of nodes is selected at 250 meters. Those nodes participate in network formations which have energy levels above the threshold level. Nodes are allowed to freely move in the operational area. The experiments are conducted by varying the number of nodes from 20 to 50. The node movement is confined to a grid area of 1 km × 1 km and 2 km × 2 km with velocity varying between 10 m/s to 20 m/s. For the sake of fair comparison, values of different parameters are kept the same for all of the algorithms. We conducted multiple experiments for each algorithm with each setup and computed their average results. The performance is conducted in terms of PLR and energy consumption. The nodes are generally equipped with a full form GPS and transceivers having a transmission range of almost 250 meters. Other sensors provide required information, especially energy level of node and data buffer having limited storage capacity. The nodes leave or join the network following Poisson distribution.
Consider
In Eq. (2),
According to above Eq. (3), the energy consumption increases over time due to the fact that initially the node consumes fewer amperes, but after consuming half of the battery it consumes more power, and battery time declines at a faster rate. From the Peukert equation [32], we can find the residual energy as,
The
Similarly, if
As we have discussed in earlier sections, that energy conservation, coverage and scalability are major issues faced with V2X routing, we have evaluated the Packet loss ratio (PLR) and energy consumption by varying node density, coverage, and mobility speed with the proposed model. The results have been compared with adaptive routing and LDR scheme. The reason behind choosing these algorithms for comparison is that the architecture and implementation of these two algorithms are closely related to our model.
The general performance of the PDR5 has been evaluated by measuring throughput, end-to-end delay, and jitter in the network. During these measurements we have excluded the propagation delay in order to analyze the routing process. Fig. 6a shows the results of instantaneous throughput achieved during the experiment. The maximum throughput achieved is 2 Kilo packets per second (KPPS) with the average rate at 0.75 KPPS in a dense environment of 1x1 km grid size and a total of ten high speed nodes. Fig. 6b shows the end-to-end delay increases with more nodes starting transmission, however, the maximum delay observed is below 3ps without including the propagation delay. Similarly, the jitter is also within a reasonable limit of 0.6ps and average to 0.12ps as shown in Fig. 6c. The major outstanding issues for the V2X communications are scalability, energy efficiency and mobility as discussed in earlier sections, we have compared the PDR5 with other approaches in the next subsection only for these aspects.
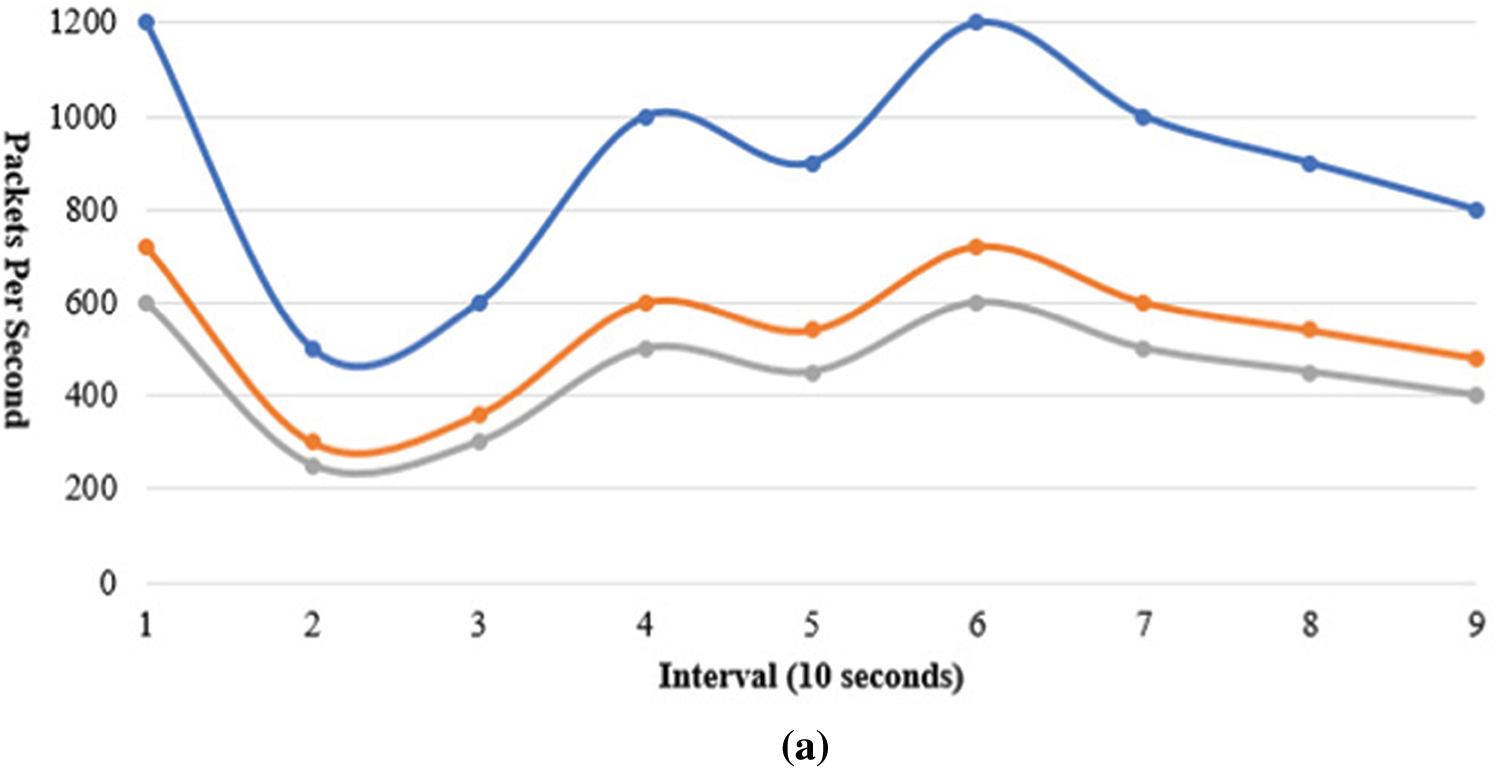
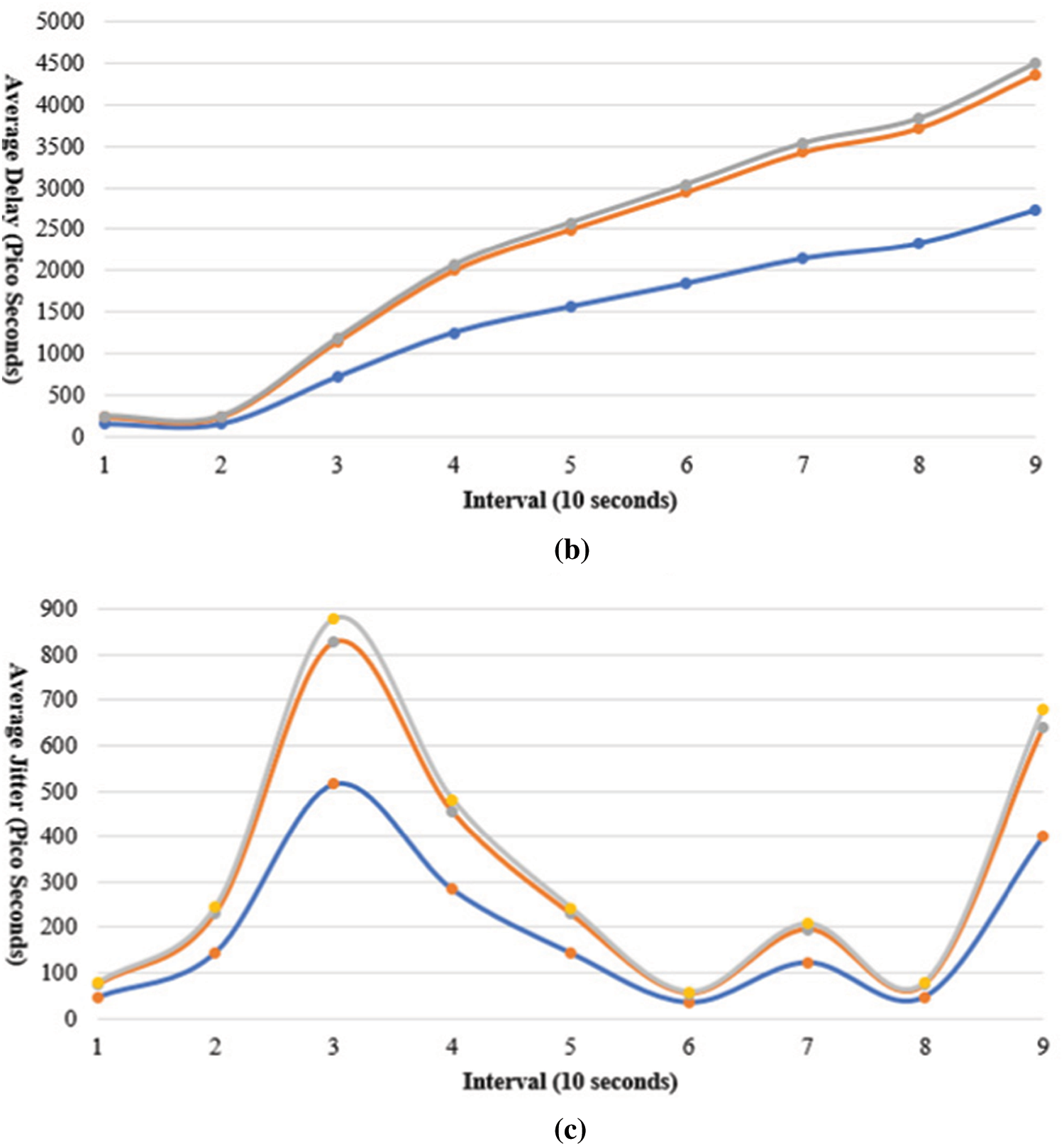
Figure 6: Delay and jitter analysis (a) Throughput of DPR5 (b) End to End Delay (c) End to End Jitter
In this section, we compare the aspects of mobility, scalability, the packet loss ratio, and energy consumption with other state-of-the-art schemes namely the adaptive routing and LDR. The delay(d) and jitter(j) calculations are performed as per the following system of Eqs. (7)–(11) [33] where i and
PLR is a measure of the number of packets dropped as compared to the number of packets transmitted. It has an inverse relationship with performance; high PLR means low network performance and vice versa. We measured the PLR while varying node density and velocity.
a) PLR vs. Node Density Measurement
In a grid area of 1 km × 1 km, the formation of the number of nodes is varied from 20 to 50 and checks the PLR of the network. Fig. 7a shows the comparison of PLR results with DPR5, LDR and adaptive routing.
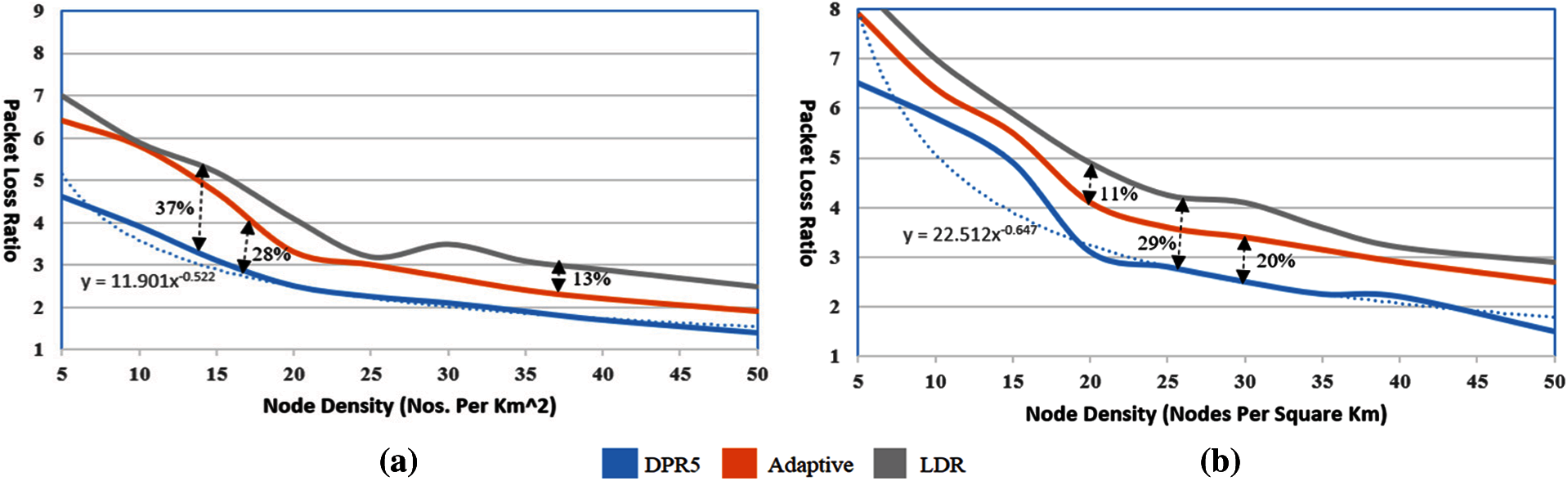
Figure 7: PLR vs. node density measurement results (a) Grid size 1 x 1 km (b) Grid size 2 x 2 km
Increasing the number of nodes causes a decrease in the PLR. With 50 nodes, PLR of the proposed hybrid model reaches 1.3%. While in the case of the other two algorithms PLR also decreased, but not at the same rate as in the proposed model. The drop in PLR is due to the fact that as the number of nodes increase in the limited geographical region, the degree of neighborhood, probability of route-finding and route establishment increases. But in the case of adaptive routing, increasing the number of nodes increases the broadcast message three times, which congests the network. Moreover, finding the hops threshold in a dense network is a complex task which affects the PLR of the network. In the case of LDR, finding a proxy node in a dense network consumes much time which affects the throughput of the network. Another affecting metric is INQ messages, when the number of nodes increases it doubles the number of broadcast messages in the network. Fig. 7b shows PLR measurements results and node density for a grid size of 2 × 2 km. As the grid size increases, the node deploys at a far distance. The probability of neighborhood, route establishment, route find decreased. However, as compared to 1 km × 1 km grid size, this network has more PLR at all levels. In this case, the minimum PLR of the network is approximately 4 at 50 nodes in the proposed model. Grid size highly affects the PLR of Adaptive and LDR, because in LDR selection of proxy nodes for remote nodes is not fusible or even consumes much time.
b) Speed vs. PLR of Network
Mobility speed is also an important factor to check the performance of a mobile network. It disturbs the routes and routing processes spend more time in route discovery and maintenance process, that directly affects the PLR of the network. We vary the speed of nodes from 10 m/s to 20 m/s while the number of nodes is set at 50. Fig. 8a shows the results of mobility speeds and PLR of the network for all three algorithms in a grid area of 1 km × 1 km.

Figure 8: Speed vs. PLR measurement results (a) Grid Size 1 x 1 km (b) Grid Size 2 x 2 km
It can be noted from the graph that increasing the node's velocity increases the PLR. With the increase in speed, the PLR of the proposed model does not increase at the same rate as the other algorithms. The reason behind is that, on increasing the speed, nodes move under restricted geographical area and remain in close vicinity to each other. In this way route finding and establishment probability remains high without affecting the PLR in the network. In case of adaptive routing the calculation of hop count threshold is performed repeatedly which decreases PLR in the network. As in the case of LDR, it uses the control message which makes the route maintenance process quite slow, which results in route disturbance frequently. Therefore, the PLR of the network is badly affected due to the mobility of nodes. In the formation when the grid size increased, PLR also increased because the probability of route disturbance increased even more. Nodes may move at the outer region or at far distance from each other, which decreases the probability of route finding. Fig. 8b shows the PLR of the network. It shows that the PLR of the DPR5 scheme is not much affected as in adaptive and LDR routing algorithms.
Energy is another key parameter to check the network performance. It is highly important for such types of the network which operate under battery backup and have a limited lifetime. To improve the life of the network it's more important that we efficiently handle the energy of the network. Nodes’ used energy for multiple purposes during transmission, reception, and processing. We monitor the energy consumption while varying node density and velocity.
a) Node Density vs. Energy Consumption
We measured the scalability of the proposed model in terms of a relationship between nodes density, mobility speed and energy consumption. A network with a small number of nodes consumes less energy since they transmit, receive, and process fewer data and INQ packets. Similarly, when the number of nodes is increased, total energy consumption of the network also increases. In a dense network, every node receives multiple INQ messages, irrespective of whether they are related to it or not. Another reason for this high consumption is that a greater number of nodes will rely on the message. Since the proposed algorithm consumes less computation resources and performs efficient routing, it consumes less energy as compared to Adaptive and LDR. The proposed model just uses two types of INQ massages (RREQ, RREP) which consume less energy. Whereas adaptive routing algorithms use the three times more message broadcast into the network while finding a route, which causes it to deplete more energy. In the case of LDR, finding a proxy node in a dense network consumes much energy which affects the energy consumption of the network. As the grid size increases, the node deploys at a far distance. The neighborhood probability of route establishment decreased which triggered the routing process frequently. This results in more control and INQ packets, which is the wastage of energy. Fig. 9 shows the energy consumption as compared to node density (a and b) and the energy consumption with respect to the mobility speed (c and d) with grid size of 1x1 and 2 km x 2 km respectively.

Figure 9: Node's speed and density vs. energy consumption (a) Grid Size 1 x 1 km (b) Grid Size 2 × 2 km (c) Grid Size 1 × 1 km (d) Grid Size 2 × 2 km
In adaptive routing calculation of hop count threshold is performed repeatedly that results in broadcasting more INQ messages increased the energy consumption of nodes. In the case of LDR, the location of the proxy node changes at the same rate as speed which disturbs the route. Selection of proxy nodes, again and again, requires energy consumption activity. Energy consumption of the proposed model does not have much effect as in adaptive and LDR routing algorithms. Another important finding of DPR5 is shown in Fig. 10 where PLR is compared with ratio of node Density to node mobility (DMR).
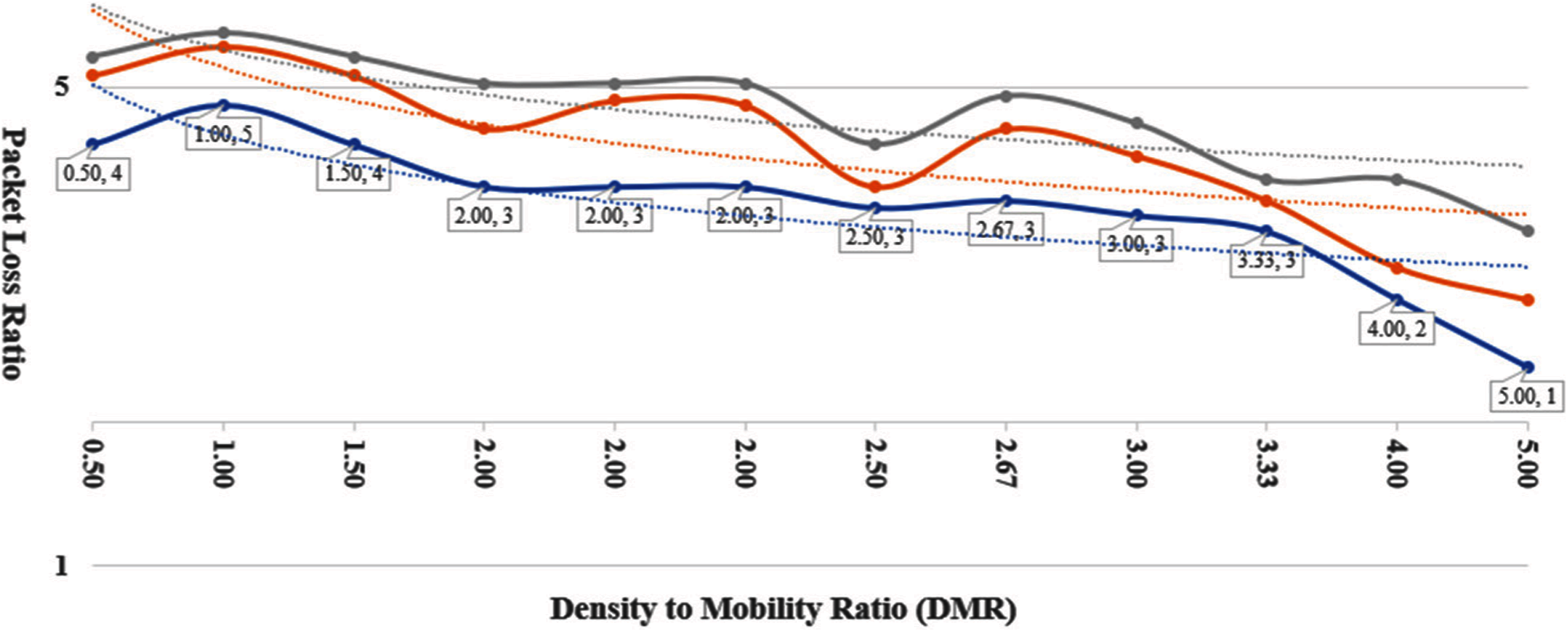
Figure 10: PLR vs. DMR comparison
The PLR of all the other schemes reduces as the DMR is increased, however with PDR5 the PLR remains minimum as compared to other routing schemes. The adoptive routing schemes PLR is twice as of the DPR5, and hybrid scheme has four times more PLR.
We have proposed an improved scheme for energy efficient and scalable routing in V2X communications for 5G. We have shown that it reduces energy consumption and the PLR in a high-speed dense environment as compared to the adaptive and LDR schemes. The PLR cumulative reduction is observed between
Funding Statement: The authors received no specific funding for this study.
Conflicts of Interest: The authors declare that they have no conflicts of interest to report regarding the present study.
1. T. S. J. Darwish and K. Abu Bakar, “Fog based intelligent transportation big data analytics in the internet of vehicles environment: Motivations, architecture, challenges, and critical issues,” IEEE Access, vol. 6, pp. 15679–15701, 2018. [Google Scholar]
2. J. Contreras-Castillo, S. Zeadally and J. A. Guerrero-Ibañez, “Internet of vehicles: Architecture, protocols, and security,” IEEE Internet of Things Journal, vol. 5, no. 5, pp. 3701–3709, 2018. [Google Scholar]
3. H. Wei, G. Zheng, V. Gayah and Z. Li, “Recent advances in reinforcement learning for traffic signal control: A survey of models and evaluation,” ACM Special Interest Group on Knowledge Discovery and Data Mining Exploration Newsletters, vol. 22, no. 2, pp. 12–18, 2021. [Google Scholar]
4. S. Chavhan, D. Gupta, B. N. Chandana, A. Khanna and J. J. P. C. Rodrigues, “IoT-based context-aware intelligent public transport system in a metropolitan area,” IEEE Internet of Things Journal, vol. 7, no. 7, pp. 6023–6034, 2020. [Google Scholar]
5. W. Xu, H. Zhou, N. Cheng, F. Lyu, W. Shi et al., “Internet of vehicles in big data era,” IEEE/CAA Journal of Automatica Sinica, vol. 5, no. 1, pp. 19–35, 2018. [Google Scholar]
6. A. Singh, A. Payal and S. Bharti, “A walkthrough of the emerging IoT paradigm: Visualizing inside functionalities, key features, and open issues,” Journal of Network and Computer Applications, vol. 143, pp. 111–151, 2019. [Google Scholar]
7. M. Agiwal, A. Roy and N. Saxena, “Next generation 5G wireless networks: A comprehensive survey,” IEEE Communications Surveys Tutorials, vol. 18, no. 3, pp. 1617–1655, 2016. [Google Scholar]
8. G. A. Akpakwu, B. J. Silva, G. P. Hancke and A. M. Abu-Mahfouz, “A survey on 5G networks for the internet of things: Communication technologies and challenges,” IEEE Access, vol. 6, pp. 3619–3647, 2018. [Google Scholar]
9. R. Gasmi and M. Aliouat, “Vehicular ad hoc networks versus internet of vehicles - a comparative view,” in Proc. of Int. Conf. on Networking and Advanced Systems, Annaba, Algeria, pp. 1–6, 2019. [Google Scholar]
10. H. Vasudev and D. Das, “An efficient authentication and secure vehicle-to-vehicle communications in an IoV,” in Proc. of IEEE 89th Vehicular Technology Conf., Kuala Lumpur, Malaysia, pp. 1–5, 2019. [Google Scholar]
11. S. Talwar, D. Choudhury, K. Dimou, E. Aryafar, B. Bangerter et al., “Enabling technologies and architectures for 5G wireless,” in Proc. of IEEE MTT-S Int. Microwave Symposium, Tampa, FL, USA, pp. 1–4, 2014. [Google Scholar]
12. H. Zhang, N. Liu, X. Chu, K. Long, A. H. Aghvami et al., “Network slicing based 5G and future mobile networks: Mobility, resource management, and challenges,” IEEE Communications Magazine, vol. 55, no. 8, pp. 138–145, 2017. [Google Scholar]
13. W. Kim, “Dual connectivity in heterogeneous small cell networks with mmWave backhauls,” Mobile Information Systems, vol. 2016, p. e3983467, 2016. [Google Scholar]
14. S. Xu, M. Hou, K. Niu, Z. He and W. Wu, “Coverage and capacity optimization in LTE network based on non-cooperative games,” The Journal of China Universities of Posts and Telecommunications, vol. 19, no. 4, pp. 14–42, 2012. [Google Scholar]
15. H. Zhang, L. Song and Y. J. Zhang, “Load balancing for 5G ultra-dense networks using device-to-device communications,” IEEE Transactions on Wireless Communications, vol. 17, no. 6, pp. 4039–4050, 2018. [Google Scholar]
16. J. Gui and J. Deng, “Multi-hop relay-aided underlay D2D communications for improving cellular coverage quality,” IEEE Access, vol. 6, pp. 14318–14338, 2018. [Google Scholar]
17. R. Mahmoud, T. Yousuf, F. Aloul and I. Zualkernan, “Internet of things (IoT) security: Current status, challenges and prospective measures,” in Proc. of 10th Int. Conf. for Internet Technology and Secured Transactions, London, UK, pp. 336–341, 2015. [Google Scholar]
18. S. Din, A. Paul and A. Rehman, “5G-enabled hierarchical architecture for software-defined intelligent transportation system,” Computer Networks, vol. 150, pp. 81–89, 2019. [Google Scholar]
19. E. T. Michailidis, N. I. Miridakis, A. Michalas, E. Skondras and D. J. Vergados, “Energy optimization in Dual-RIS UAV-aided MEC-enabled internet of vehicles,” Sensors, vol. 21, no. 13, Art. no. 4392, 2021. [Google Scholar]
20. J. Gu, G. Zhang, H. Lv and W. Duan, “Research on cluster overlap and non-overlap region for 5G-IoV networks with NOMA,” EURASIP Journal on Wireless Communications and Networking, vol. 2021, no. 1, p. 63, 2021. [Google Scholar]
21. S. Abbasi, A. M. Rahmani, A. Balador and A. Sahafi, “Internet of vehicles: Architecture, services, and applications,” International Journal of Communication Systems, vol. 34, no. 10, p. e4793, 2021. [Google Scholar]
22. H. Zhang, S. Huang, C. Jiang, K. Long, V. C. M. Leung et al., “Energy efficient user association and power allocation in millimeter-wave-based ultra dense networks with energy harvesting base stations,” IEEE Journal on Selected Areas in Communications, vol. 35, no. 9, pp. 1936–1947, 2017. [Google Scholar]
23. S. A. Ahmad and M. Shcherbakov, “A survey on routing protocols in vehicular adhoc networks,” in Proc. 9th Int. Conf. on Information, Intelligence, Systems and Applications, Coimbatore, India, pp. 1–8, 2018. [Google Scholar]
24. S. Othmen, F. Zarai, A. Belghith and L. Kamoun, “Anonymous and secure on-demand routing protocol for multi-hop cellular networks,” in Proc. of Int. Symposium on Networks, Computers and Communications, Yasmine Hammamet, Tunisia, pp. 1–6, 2016. [Google Scholar]
25. F. S. Shaikh and R. Wismuller, “Centralized adaptive routing in multihop cellular D2D communications,” in Proc. of 2nd Int. Conf. on Computer and Communication Systems, Krakow, Poland, pp. 158–162, 2017. [Google Scholar]
26. Y. Cao, T. Jiang and C. Wang, “Cooperative device-to-device communications in cellular networks,” IEEE Wireless Communications, vol. 22, no. 3, pp. 124–129, 2015. [Google Scholar]
27. X. Lin, J. G. Andrews and A. Ghosh, “Spectrum sharing for device-to-device communication in cellular networks,” IEEE Transactions on Wireless Communications, vol. 13, no. 12, pp. 6727–6740, 2014. [Google Scholar]
28. M. Matis, L. Doboš and J. Papaj, “An enhanced hybrid social based routing algorithm for MANET-DTN,” Mobile Information Systems, vol. 2016, p. e4803242, 2016. [Google Scholar]
29. F. S. Shaikh and R. Wismuller, “Interference-conscious routing in multihop D2D communications,” in Proc. of 2nd Int. Conf. on Computer and Communication Systems, Krakow, Poland, pp. 146–151, 2017. [Google Scholar]
30. O. Bello, S. Zeadally and M. Badra, “Network layer inter-operation of device-to-device communication technologies in internet of things (IoT),” Ad Hoc Networks, vol. 57, pp. 52–62, 2017. [Google Scholar]
31. X. Han, H. Wang, M. Pan, Y. Ji and P. Zhang, “WSNp1–2: Light dark routing protocol: An innovative infrastructure-assisted ad hoc routing protocol,” in Proc. of IEEE Globecom, San Francisco, CA, USA, pp. 1–5, 2006. [Google Scholar]
32. D. Doerffel and S. A. Sharkh, “A critical review of using the Peukert equation for determining the remaining capacity of lead-acid and lithium-ion batteries,” Journal of Power Sources, vol. 155, no. 2, pp. 395–400, 2006. [Google Scholar]
33. A. H. Rashid and S. Shah Muhammad, “Traffic intensity based efficient packet schedualing,” in Proc. of Int. Conf. on Communication Technologies, Rawalpindi, Pakistan, pp. 88–101, 2019. [Google Scholar]
 | This work is licensed under a Creative Commons Attribution 4.0 International License, which permits unrestricted use, distribution, and reproduction in any medium, provided the original work is properly cited. |