DOI:10.32604/cmc.2022.022817

| Computers, Materials & Continua DOI:10.32604/cmc.2022.022817 |  |
| Article |
Robust Watermarking Scheme for NIfTI Medical Images
1School of Computer Science and IT, JAIN (Deemed to be University), Bangalore, 560069, India
2Department of Computer Science and Information Engineering, National Cheng Kung University, Tainan, 701, Taiwan
3Department of Computer Science & Engineering, Panimalar Engineering College, Anna University, Chennai, 600123, India
4Patna Women's College, Patna, 800001, India
5Information Systems Department, College of Computer and Information Sciences, Imam Mohammad Ibn Saud Islamic University (IMSIU), Riyadh, 11432, Saudi Arabia
6Department of Computer Science and Engineering, Oakland University, Rochester, 48309, USA
*Corresponding Author: Abdul Khader Jilani Saudagar. Email: aksaudagar@imamu.edu.sa
Received: 19 August 2021; Accepted: 09 October 2021
Abstract: Computed Tomography (CT) scan and Magnetic Resonance Imaging (MRI) technologies are widely used in medical field. Within the last few months, due to the increased use of CT scans, millions of patients have had their CT scans done. So, as a result, images showing the Corona Virus for diagnostic purposes were digitally transmitted over the internet. The major problem for the world health care system is a multitude of attacks that affect copyright protection and other ethical issues as images are transmitted over the internet. As a result, it is important to apply a robust and secure watermarking technique to these images. Notably, watermarking schemes have been developed for various image formats, including .jpg, .bmp, and .png, but their impact on NIfTI (Neuroimaging Informatics Technology Initiative) images is not noteworthy. A watermarking scheme based on the Lifting Wavelet Transform (LWT) and QR factorization is presented in this paper. When LWT and QR are combined, the NIfTI image maintains its inherent sensitivity and mitigates the watermarking scheme's robustness. Multiple watermarks are added to the host image in this approach. Measuring the performance of the graphics card is done by using PSNR, SSIM, Q (a formula which measures image quality), SNR, and Normalized correlation. The watermarking scheme withstands a variety of noise attacks and conversions, including image compression and decompression.
Keywords: Watermarking; NIfTI; LWT; QR; image security
Today, the role of computers in a wide range of occupations is critical to success, because computer-assisted technologies provide rapid and accurate results in every industry. In addition to medical science and healthcare systems, these technologies were used to quickly transmit digital medical images around the world to aid in diagnosis. CT-scan, MRI, and Color Doppler Imaging have transformed modern medicine. As a result, doctors can acquire and interpret imaging results much faster and more accurately than with previous imaging methods such as x-rays. There are two major issues with film-based imaging. One is that print costs are high, and the other is that filmless imaging techniques must be used to solve this problem. Because multiple radiologists can view the same image at the same time, film-less imaging provides greater access and broader diagnostics than film-based imaging. Thus, a doctor who is too far away from the patient may provide a solution by using a film-less imaging system, which is beneficial to both the patient and the doctor. COVID-19 has recently spread throughout the world, and it is now a major concern for doctors. Researchers are working to find a cure for the corona pandemic, which is affecting billions of people, by using digital imaging technology to detect and assess COVID-19 [1]. However, it is critical to safeguard private electronic data from malicious intruders.
Hospitals now hold the majority of COVID-19 patient data due to the increased use of medical imaging (medical imaging of the patient) with patient personal information, diagnosis history, and other reports delivered over the network. It has become common practise to expose yourself to new risks in order to benefit from them for specific reasons such as diagnosis, treatment, medical consultation, distance learning, and training. Healthcare providers (doctors and imaging providers) have a difficult time taking security threats seriously. Images may be intentionally or unintentionally distorted during medical image generation and communication, which can have serious consequences for patient diagnosis [2]. For the researcher, this is the moment of truth: It is a difficult task to maintain the delicate medical image's integrity and authenticity in an unprotected network. Watermarking can ensure the image's integrity and authenticity. Digital watermarking is a process that embeds a digital watermark (a meaningful image) into an image carrier (an image that has not been altered in any way, such as size, format, or information) without changing anything else, including the image's characteristics (image size, format, and content). To verify the image's legitimacy, you must extract the watermark that has been embedded in the host image [3]. When a watermarking procedure affects a medical image in a clinical setting, trust in the image is undermined. Misdiagnosis caused by minor changes in the image could result in dangerous consequences and legal issues. Watermarking techniques that use transformation domains and spatial domains can be considered. To convert an image to the frequency domain, a transform domain strategy employs various wavelet transforms such as DCT, DFT, DWT, and watermark insertion. In contrast to spatial watermarking techniques, which embed the watermark's bits in the host image, image watermarking strategies embed the watermark's bits in a different location. Transformation domain schemes outperform spatial domain systems in terms of robustness [4]. The robustness of all digital watermarking techniques is a major issue. Many researchers have proposed watermarking proposals for. bmp and jpg medical photos. As of now, three DICOM watermarking systems have been proposed: The increasing use of advanced imaging technologies such as X-ray, ultrasound, MRI, and CAT scans necessitated the development of the NIfTI imaging technology rather than Windows-style BMP, JPEG, and DICOM-based CT scans. There is highly sensitive medical data in NIfTI photographs. To prevent counterfeiting, it is critical to use a strong watermarking method in the NIfTI images to provide the necessary medical diagnosis in the healthcare system [5].
A safe watermarking approach for NIfTI images is based on LWT and QR factorization, which we call NIfTI QR LWT. The image watermarking and grayscale watermarks that are used in this approach try to provide better robustness and reduced complexity for CT-Scan image watermarking (.nii format). start by applying the LWT on the image, which breaks the image down into four sub-bands LL (low-low), HL (high-low), LH (low-high) and HH (high-high). It permits every one of these steps to take place; then apply QR factorization on the watermark. As you can see, LL uses more of the image's energy in their factorized watermark, and so would be the best choice for that application.
This proposed system is extremely resilient to noise attacks and various formatting changes. Related work has been discussed in Section 2. Sections 3 and 4 go over the LWT and QR. Section 4 also introduces the proposed watermarking strategy. Section 5 includes experimental results as well as an examination of some proposed medical imaging work. Section 6 examines the results of the robustness analysis, and Section 7 provides the analysis’ conclusions.
The fact that telemedicine applications have advanced significantly [6] indicates that researchers are now interested in the application of digital medical imaging. The majority of medical images are classified as colour or grayscale. Furthermore, most medical equipment, such as CT scans, X-rays, and ultrasounds, generate images with varying shades of grey, such as bmp, jpg, DICOM, and so on. As a result, researchers are more aware of medical imaging, which has far-reaching applications beyond medical imaging. Several image watermarking techniques are reported in the literature, all of which are based on matrix decompositions.
The watermarking scheme created by Wang et al. [7] was first used by the image's creator. HL and LH were chosen for watermark insertion, so LU factorization is also applied to those two sub-bands. To incorporate a watermark, it has first altered with the Arnold transformation and then the transformed watermark is applied to the bands that have been selected. Multiple image processing attacks, such as contrast adjustment, noise assault, JPEG compression, cropping, and Gaussian noise, are resistant to this methodology. Lin et al. [8] introduced a watermarking methodology in which the initially DWT is applied to the LL band, and the QR decomposition is subsequently employed on the R matrix to incorporate the encrypted watermark in the initial row. According to Su et al. [9], a blind watermarking method for QR decomposition is proposed. When the image was first divided into 4 X 4 blocks, QR decomposition was applied to each block and watermark is inserted in the initial row of R matrix of each blocks. While cropping, blurring, rotation, scaling, adding noise, and sharpening have no effect on the image, the technique is well protected against each of these effects. Ni et al. [10] suggested LWT-based watermarking technique. The watermark is added in LL sub bands after LWT has been applied to the host image. A chaotic sequence is used to estimate the location of spatial tempering. In this study, Gao et al. [11] proposed a reversible watermarking scheme using the LWT and chaotic system. To divide the host image into non-overlapping blocks, the author first applied LWT on every non-overlapping block. The subsequent LL band is used to insert the watermark on every block. To make shuffling of blocks even more chaotic, use the chaotic system. This is specifically meant to counter crop hacking, and it is very secure. Lizong et al. [12] suggested a watermarking approach based on LWT and a chaotic system. The black-and-white image is the watermark, while the color image is the host image. This approach survives image processing attacks such as cropping, sharpening, and JPEG compression. A new method devised by Zairi et al. [13] uses DWT, DCT, and QR decomposition in combination. Entropy values have been used to determine watermark embedding in this method, according to the images’ entropy. Researchers Ghaderi et al. [14] developed a method that utilized LWT and SVD. An author performs a 4-level LWT on the HL and LH sub bands before applying the SVD to the HL and LH sub bands. The watermark image has been transformed into a binary image, and afterwards the watermark is added by changing the values of the binary image's bands. It has built-in contrast and rotation, scaling, and cropping resistance for the JPEG compression and cropping. In a study done by Chamlawi et al. [15], a novel LWT semi-fragile watermarking approach is created. The first watermark is used for authentication, while the second watermark for image recovery and authenticity was implemented. Determines that the JPEG compression attack scheme is both efficient and secure. In a paper published in the Computational Molecular Biology journal, Mehta et al. [16] described a scheme that combines the Lagrangian Weibull (LWT), QR, and SVR models (LSVR). For the cover image, the author started with the LWT. After that, he broke the low-frequency sub bands into 4x4 blocks. Once QR decomposition has been applied to these blocks, watermarking is done to the first row of R matrix. This approach is completely resistant to cropping, scaling, noise, and JPEG compression attacks. Su et al. [17] devised a watermarking strategy that makes use of LWT and state coding. The LWT was first applied to the colour space YCrCb. A watermark is also added to the Y, Cr, and Cb frequencies in low-frequency bands. Sleit et al. [18] developed semi-blind hybrid watermarking in grayscale images by first using SVD and DWT and then adding a binary watermark. Golshan et al. [19] proposed a hybrid watermarking technique that incorporates SVD, DCT, and DWT. The image was first decomposed using the DCT, followed by the DWT, which was used to divide it into four sub-bands. Finally, a watermark is inserted into the singular values of each sub. S. introduced the technique of using LWT and SVD to create robust watermarking. K. and Sarkar. The transformation in this scheme was performed using Sarkar et al. [20], LWT. The image is divided into 2x2 blocks using LWT. The author then applied the SVD to these blocks, inserting a watermark in each individual value. According to Verma et al. [21], a recent LWT-based design scheme is planned in which three levels of LWT are used, after which LH bands are separated into blocks that are then randomly shuffled before being encoded using binary watermarking. One major disadvantage of this strategy is that it cannot withstand noise or rotation attacks.
Using image security enhancement, LWT (Lifting Wavelet Transform) is the most common watermarking method. The Wim Sweldens created it [22] The main feature of the lifting method is that all construction is done in the spatial domain. It cuts down the time and space complexity better than traditional wavelet transforms. There are fewer calculations to perform with the traditional wavelet transform, but with the lifting wavelet transform, fewer calculations are required, which means it is better as far as time and space complexity. Therefore, the quickest and most efficient approach to calculating the wavelet transform is to use the DWT. Neither the Fourier transform nor the lifting transform is required for lifting operations. After the wavelet transformation, the digital signal's sequence of integers becomes a sequence of floating-point numbers. The digital signal cannot be completely restructured, as a result of this. In order to have a reasonably reversible implementation, we need a transform algorithm that preserves the domain of signal after the transform. when converted to LWT, the scope of the transform stays the same This ensures that integer to integer transformations will always be applied. LWT always outperforms traditional wavelet transforms, as this explains why it is broadly utilized in image processing.
Now, we'll talk about LWT in image processing. LWT divides an image into four sub-bands: LL, LH, HL, and HH. The LL sub-band has low-frequency components that contain the majority of the image's energy, while the other sub-bands have high-frequency components that contain less of the image's energy. Because the LL band contains the majority of the energy in the raw image, the LWT can be applied several times on it to decompose it into sub-bands. The 2-level LWT is depicted in Fig. 1.
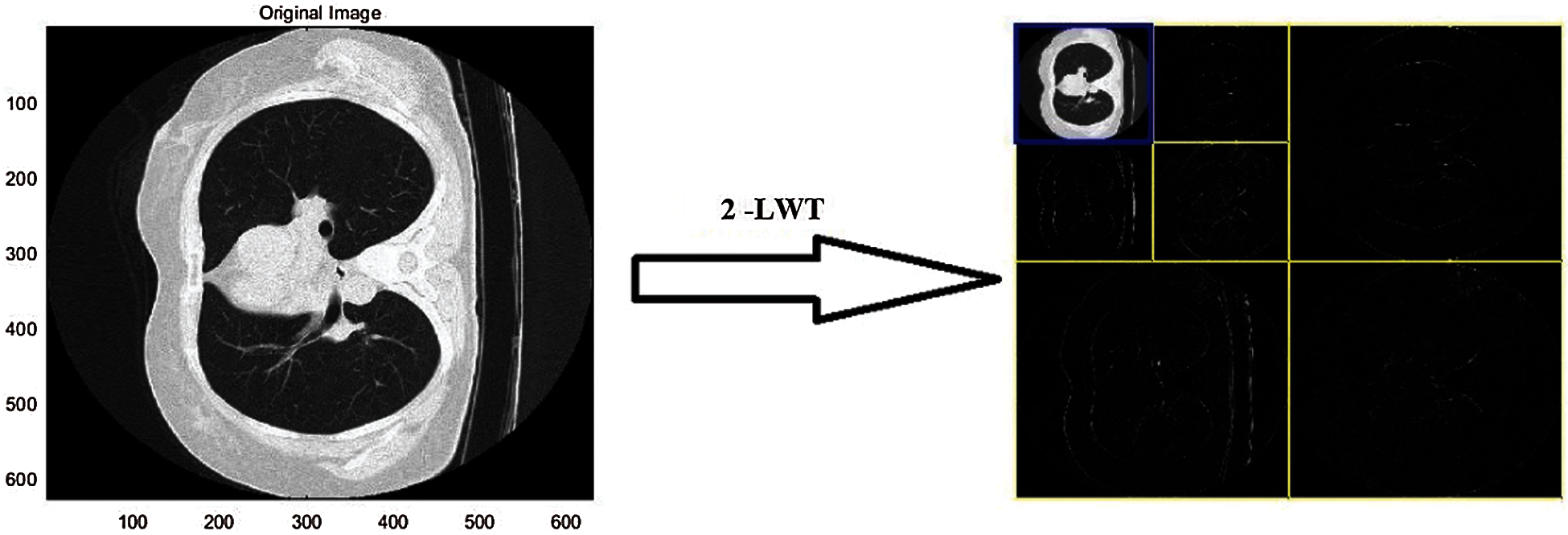
Figure 1: 2-Level LWT
QR Factorization Theorem: In QR decomposition [23], a non-singular matrix of size
where Q is an orthogonal matrix with size
First, the information needed for watermarking is securely stored, and then the information contained in the image data is processed to include watermarks. Grayscale is used for both the watermark and the background image. After selecting the first slice of the NIfTI image, perform LWT on it, resulting in the division of the image into four different frequency sub-bands as shown in Fig. 2. This sub-band transmits the information required for image processing. During the QR factorization process, the primary components of the watermark are transformed into a new vector, which is then transformed into a new vector through the QR factorization process.
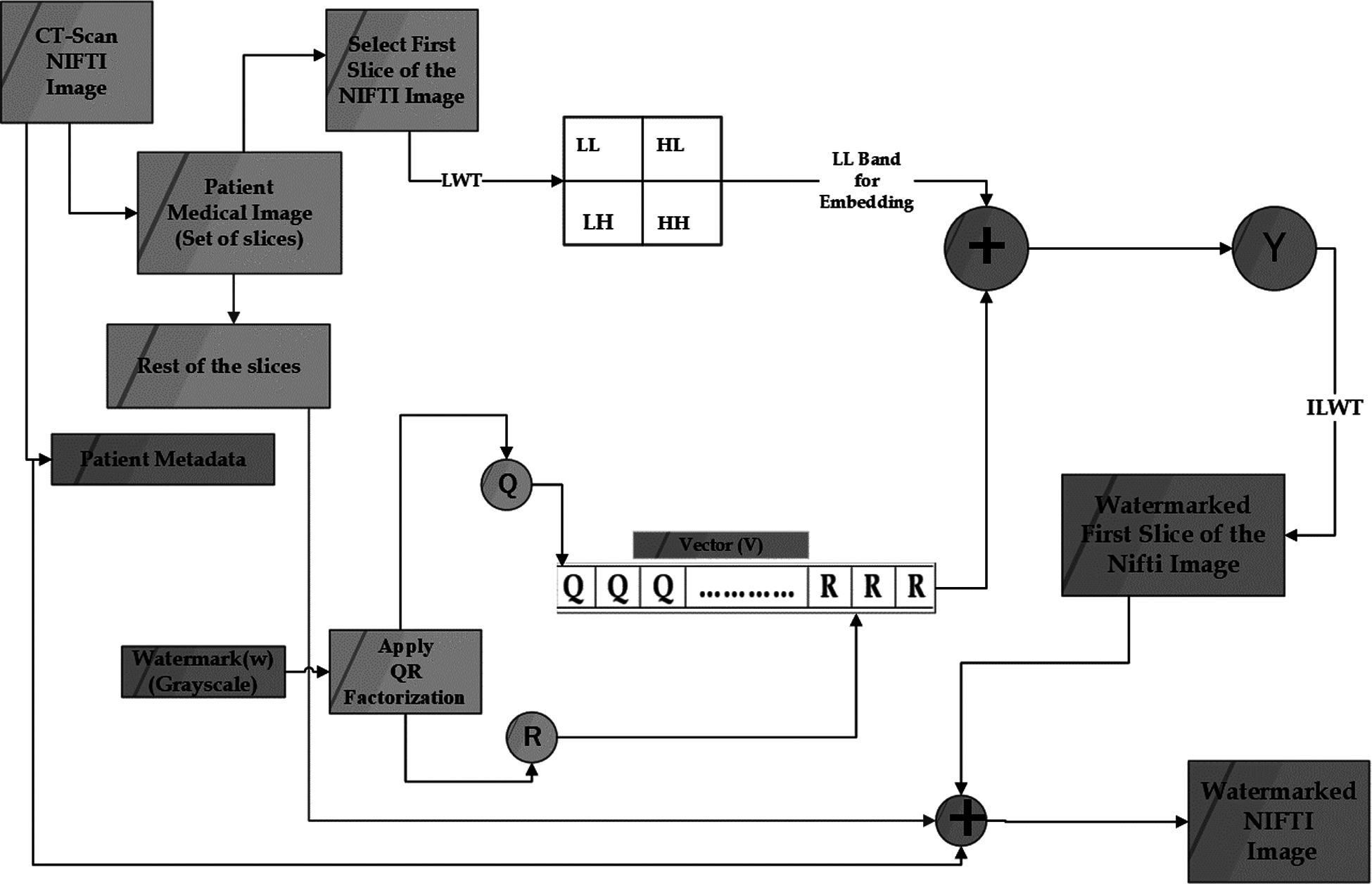
Figure 2: Block diagram of hybrid method for digital watermarking process
Embedded in the first slice of the NIfTI image's LL frequency sub-band, the new watermark vector can be seen as an LL frequency sub-band watermark. It is necessary to control the augmentation of the host watermark by using a scaling factor (alpha). LL frequency sub-bands are overlaid on the composite image, which is then inverse transformed to achieve this result. After that, the patient's EPR metadata (which includes their medical image information) is added to the original dataset, which results in the generation of the watermarked NIfTI image. A representation of the algorithm is shown in Fig. 2, which can be found further down on this page.
Input: CT-Scan NIfTI image Size (630 × 630)
Grayscale Watermark Size (32 × 32)
Output: Watermarked NIfTI image
Step 1 Extract patient metadata from the image.
Step 2 Apply the QR Factorization using Eq. (1) on the watermark.
Step 3 Perform two level LWT on first slice of the NIfTI image which decompose the slice into
LH, HL, LL, and HH sub bands.
Step 4 The factorized watermark components are embedded into transformed components of the
host slice by selecting the LL band. Watermark is embedded in the slice as shown in Eq. (2).
where
The transformed component of the watermark slice is denoted by x’.
The factorized watermark component is denoted by y.
x is the host slice's transform slice.
And,
Step 5 Apply the final watermarked slice to an Inverse Lifting Wavelet Transformation.
Step 6 Embedded the patient's metadata in watermarked image.
After performing the watermark embedding process as shown in Fig. 2, the watermark extraction process is the next critical step. The proposed watermark extraction process is depicted in Fig. 3. The original NIfTI image is required to extract the watermark from the watermarked NIfTI image, as can be seen. EPR is initially separated from both the actual and watermarked NIfTI image and select the first slice of the NIfTI image. Next, we apply the LWT to both the actual and watermarked slice, decomposing them into four different frequency sub-bands, namely LL, LH, HL, and HH. Furthermore, we isolated the noisy components from the watermarked slice using the LL sub-bands of both slices, and then used the Inverse QR factorization on these noisy components to generate the watermarks. The proposed method's extraction process is depicted in Fig. 3 and explained below.
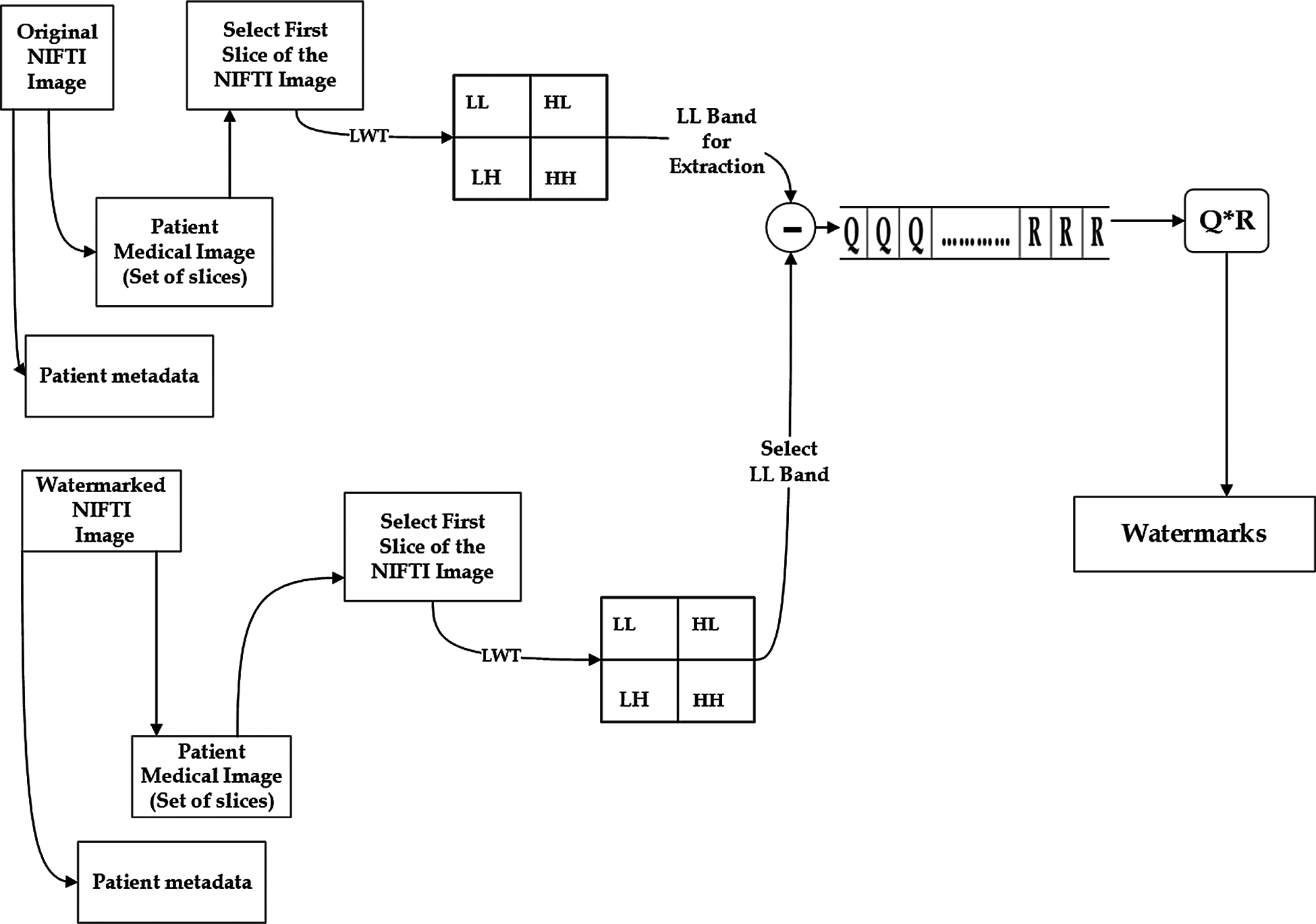
Figure 3: Block diagram of hybrid method for watermark extraction
Input: M x N NIfTI image I; and M x N NIfTI watermarked image I+.
Output: Watermark W
Step 1: Extract patient information from both the NIfTI images i.e., I and I+.
Step 2: Select the first slice of both images I and I+.
Step 3: Perform single level LWT on both slice S and S+ to obtain LL, LH, HL and HH sub bands.
Step 4: By reversing the embedding steps; Eq. (3) extract the watermark from the watermarked
image
where
The watermarked slice is
The factorized watermark component is denoted by y.
The original slice is S.
Step 5: Perform inverse QR factorization on extracted components to get the extracted watermark.
The proposed watermarking method is tested over NIfTI images generated by the CT-Scan of COVID patient taken from https://zenodo.org/record/3757476#.X0pwCnkzZPZ [24] under ethical medical practices, without revealing the patient's identity and only for the experimental purpose. On the MATLAB platform, the proposed watermarking method was tested on an Intel core TM i7-5500U CPU 2.5 GHz Windows10 machine with 8 GB RAM. Various NIfTI images with a resolution of 630 × 630 pixels and a png watermark with a resolution of 32 × 32 pixels and a bit depth of 8 bits.
The proposed watermarking method's imperceptibility is evaluated using six different NIfTI images. As described in Eqs. (4)–(9) respectively with MSE, PSNR, SNR, NC, Q and SSIM are the image quality measurements that are examined. PSNR, NC, and SSIM are used to assess perceptual imperceptibility. For the watermark perceptibility estimation, PSNR is employed, which is outlined as follows [25].
To assess the quality of the watermarking method, NC are calculated as the difference between the actual slice and the watermarked slice as defined below [26].
Universal IQI (image quality index) Q [27] is defined as follows.
where,
and
The original and test image signals are represented by w and z, respectively.
Index of universal image quality Q can be defined as the product of three components:
SSIM (Structural Similarity Index Measure), It is used to determine how similar the actual slice and the watermarked slice. The SSIM value ranges from −1 to + 1; if SSIM = 1, the actual image and watermark image are identical as described in Eq. (9).
where
σ2p: the variance of original cover and σ2q: the variance of watermarked image with covariance σpq. Where, k1and k2 are free parameters.
5.2 Analysis of Proposed Method
The proposed method has been tested on six different NIfTI images which are Img1, Img2, Img3, Img4, Img5 and Img6 to determine the imperceptibility and robustness. The test results are depicted in Figs. 4 and 5. The metadata containing COVID-19 affected person's information is also preserved within the watermarked NIfTI image.

Figure 4: First slice of NIfTI images used for experiment and watermark image in BMP format

Figure 5: Extracted watermarks from six medical images
Tab. 1 shows the performance metrics for watermarked images ranging from Img1 to Img6. Fig. 7 shows a graphical representation of the MSE between the original slice of NIfTI image and the watermarked slice of image. Fig. 6 shows the difference in Q and NC between the original NIfTI image and the watermarked image. Fig. 8 depicts the graphical interpretation of the method's PSNR and SNR metrics. Fig. 9 depicts the proposed SSIM, which is closer to one.
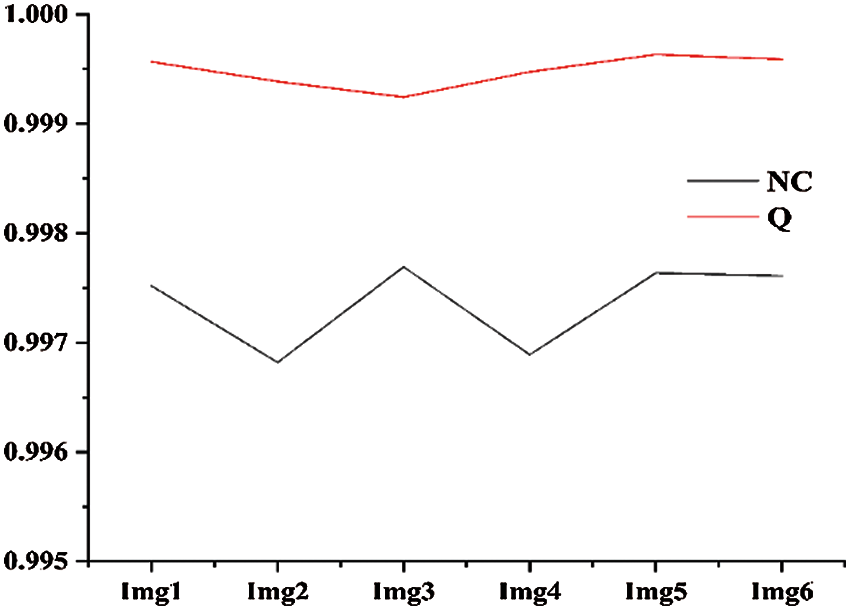
Figure 6: NC and Q of all six images
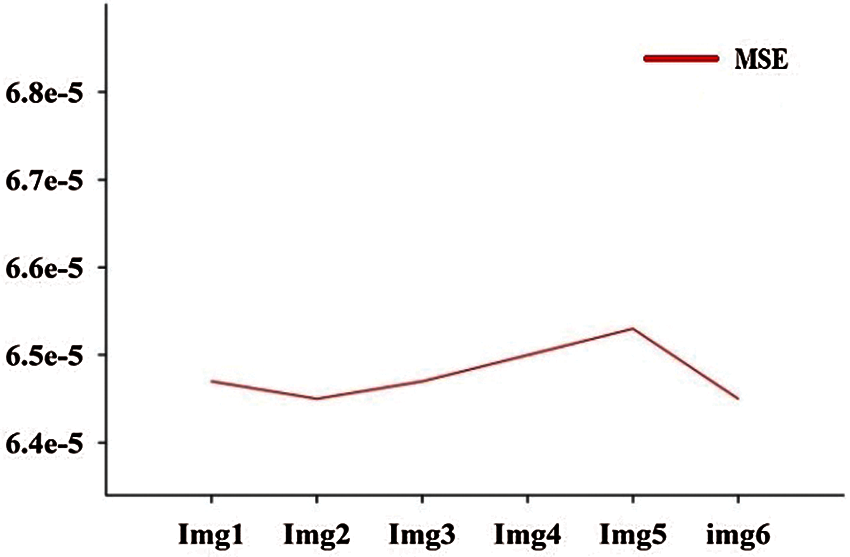
Figure 7: MSE of all six images
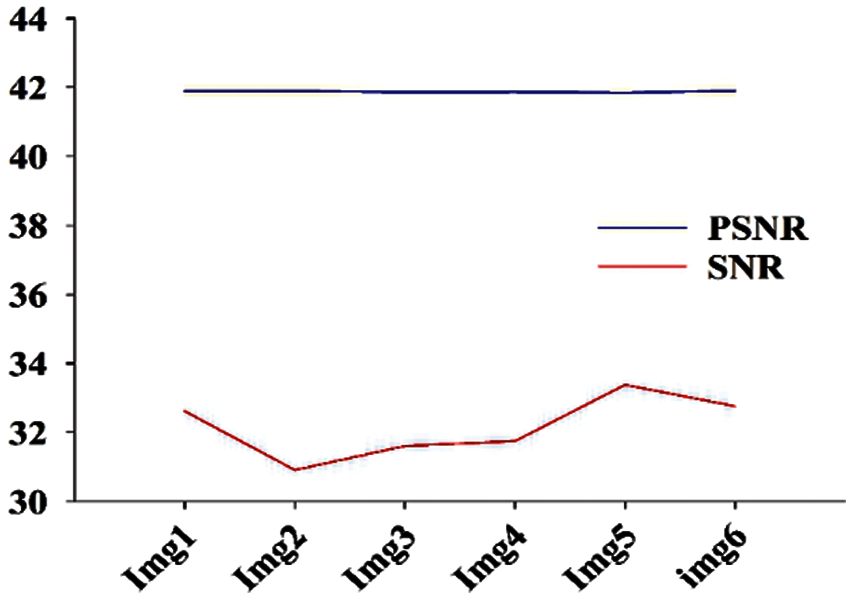
Figure 8: PSNR and SNR matrices of all six images
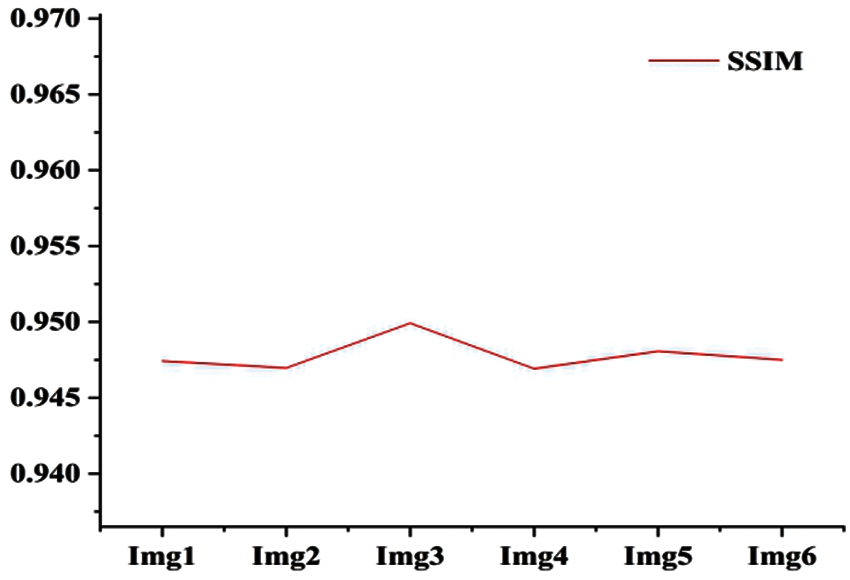
Figure 9: SSIM of all six images
Image quality parameters NC, SSIM and Q are having values approximately close to one; indicating virtually excellent correlation between the initial and watermarked images. PSNR of the watermarked image is over 41.5 db, which suggests that the watermarked image quality is extremely considerable.
5.3 Analysis of Proposed Method for Different Number of Watermarks Insertion
Proposed watermarking method inserted the multiple number of watermarks across the image. The maximum watermark insertions in the NIfTI image without hampering the diagnosis of watermarked NIfTI image, demonstrated in Tab. 1. These images contain sensitive patient's medical information too. Thus, it is much essential that the quality of these image must not be degraded after the watermarking. Tab. 2 shows that the image quality metrics are directly proportional to the number of watermarks inserted, with no discernible change. Figs. 10–13 show the PSNR, NC, Q, and SNR, respectively. In Fig. 10, we can see that decreasing the number of inserted watermarks raises the PSNR value. If we evaluate the PSNR and SNR of img1 at 24 watermark insertions and 2 watermark insertions, we find that there is a significant variation in PSNR from 44.9879 DB to 55.86161 DB and SNR from 35.71489 DB to 46.58859 DB, but no significant variation in NC and Q. In Tab. 3, the proposed method's results are compared to those of the other existing methods, and it is discovered that the proposed method's results are more significant [2–3,28].
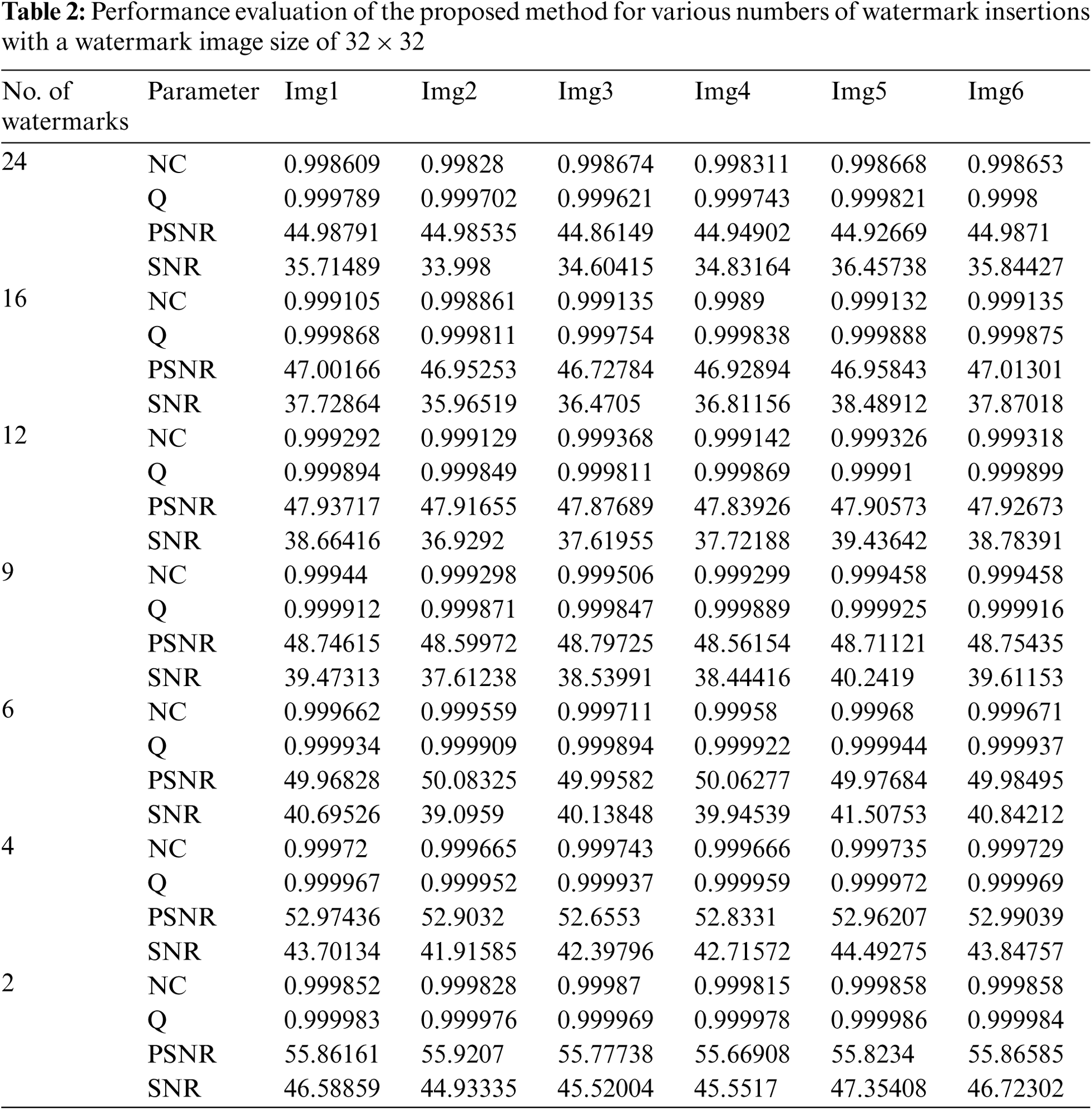
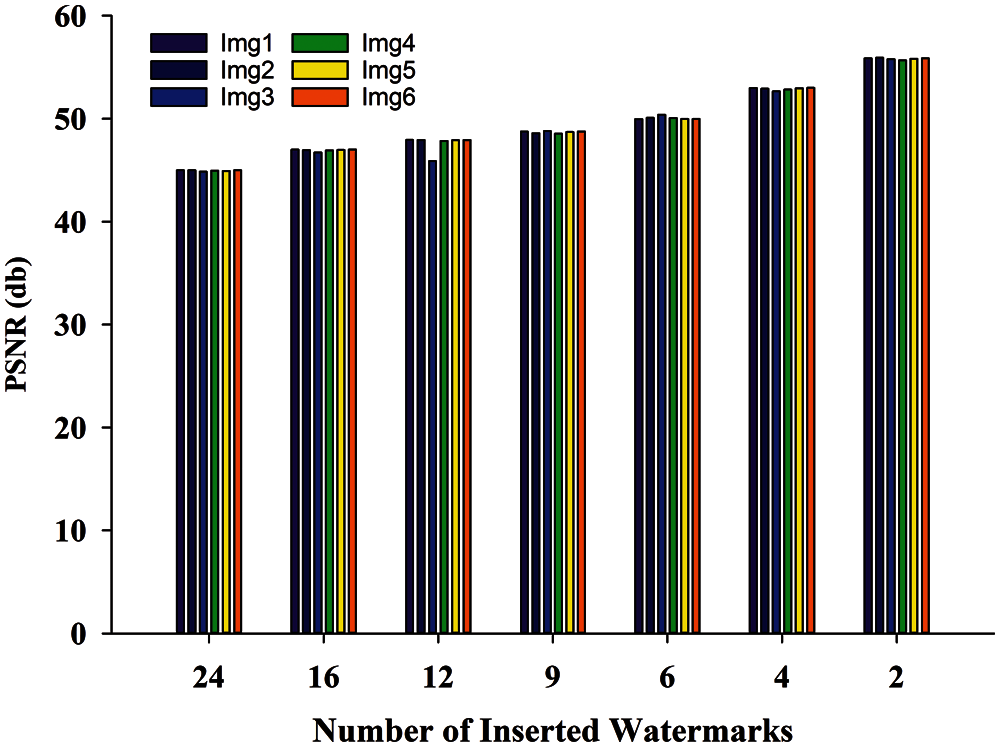
Figure 10: PSNR comparison at different number of inserted watermarks
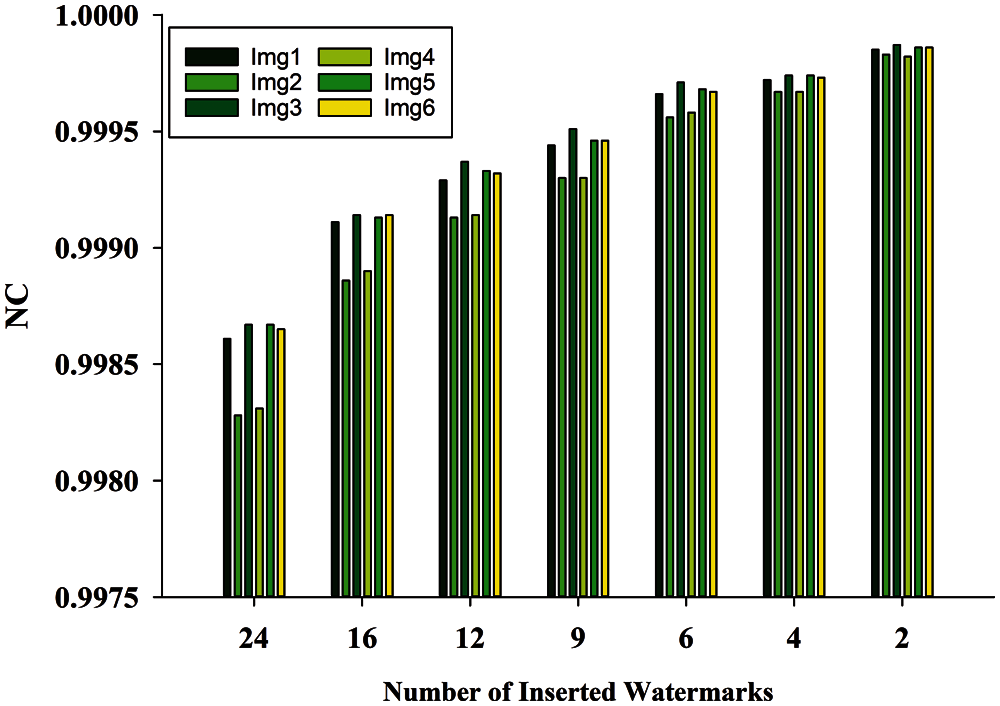
Figure 11: Normalized correlation comparison at different number of watermark insertion
Figure 12: Image quality comparison at different number of watermark insertion
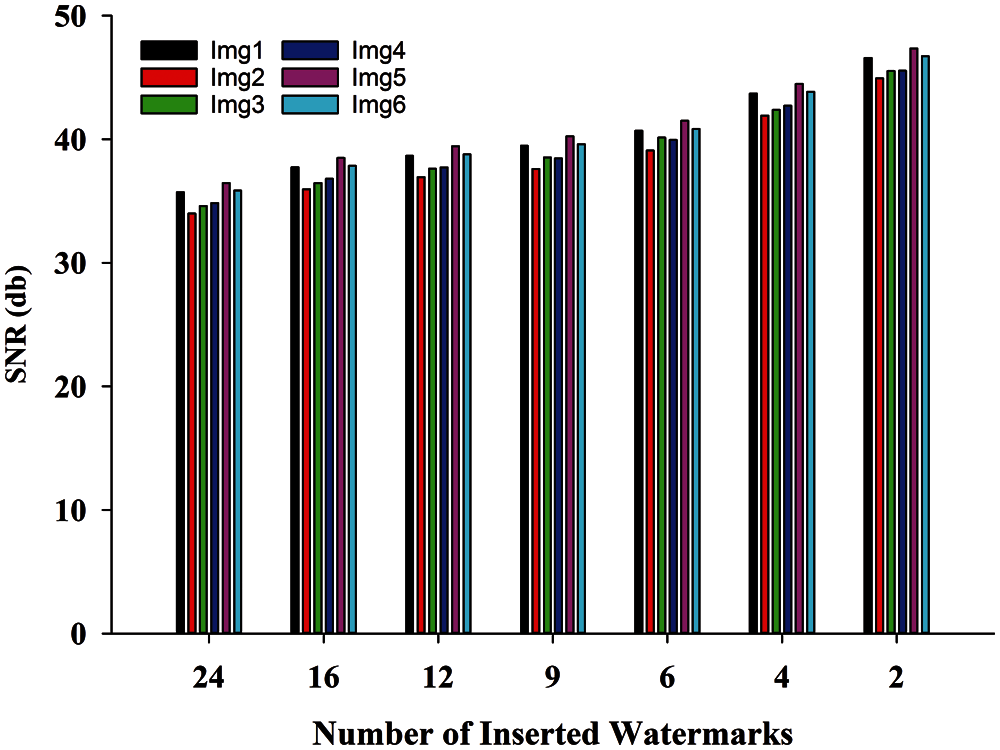
Figure 13: SNR comparison at different number of watermark insertion
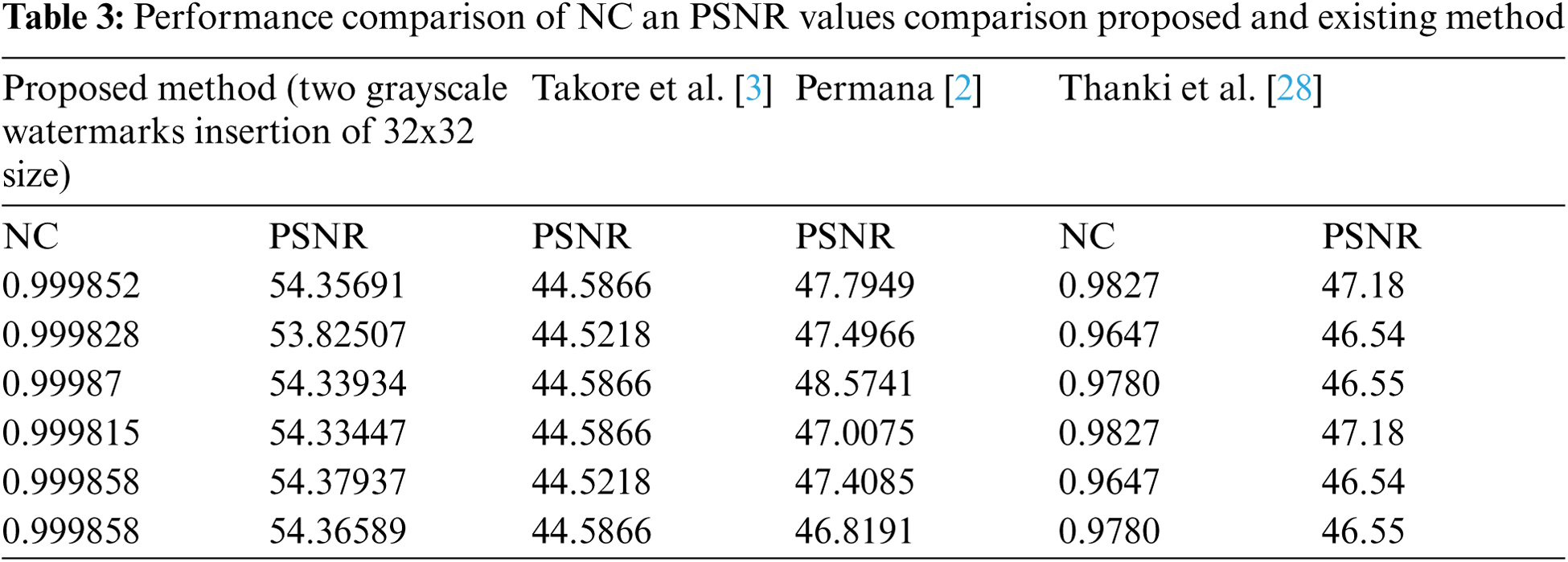
This method is tested with various number of watermark insertion and found that the results are promising. Watermarked images are subjected to various image processing attacks such as Salt & Pepper, Gaussian noise, Poisson, Speckle, which may result in the removal of watermarks. Sustenance of method against these attacks is a critical requirement of any significant watermarking method. The quality of the watermarked image and the robustness of the method are inversely proportional to each other, but a trade-off must be considered if necessary. As a result, this method is tested with the maximum number of watermarks insertion, which increases robustness, and the minimum number of watermarks insertion, which increases image watermark image quality. To test the method's robustness, attacks were performed on the watermarked image with the fewest number of watermark inclusions. The proposed watermarking method is for CT-Scan medical images; after watermarking, a watermarked NIfTI image is generated, and then diagnosis is framed on this watermarked NIFTI image. As a result, any significant degradation in the watermarked image quality is unacceptable because it may result in the patient's death. As a result, the method is tested with various noise attacks and parameters until the quality metrics indicate that the attacked watermarked image is of high quality.
6.1 Salt & Pepper Noise Attack
The salt and pepper noise attack are used on the watermarked NIfTI image with noise densities of 0.001 and 0.003 and the watermark is successfully extracted using the suggested watermarking method. Tab. 4 shows that this attack for NIfTI healthcare images is tabulated, and the results show that the efficiency of the suggested technique for NIfTI images is promising.
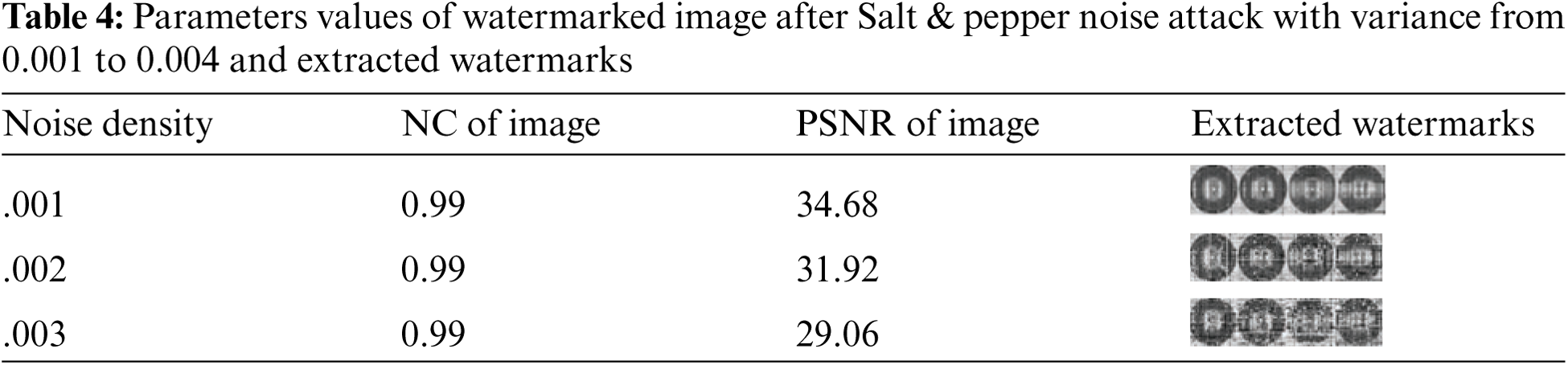
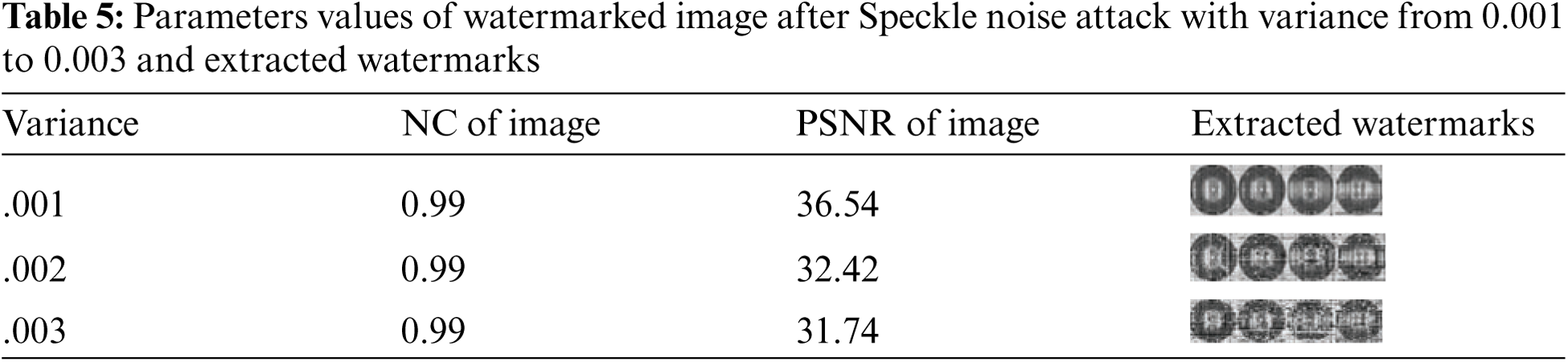
The watermark is successfully extracted by the proposed watermarking method after a speckle noise attack with a variance of 0.001 to 0.003 is applied to the watermarked NIfTI image. Tab. 5 shows the results of the evaluation of the NIfTI medical image attack, and the findings show that the proposed technique for NIfTI image is effective.
The Poisson noise attack is applied to the watermarked NIfTI image, and the watermark is successfully extracted using the proposed watermarking method. Tab. 6 tabulates the attack analysis for NIfTI medical images, and the results show that the proposed method for NIfTI images performs well for watermark extraction.
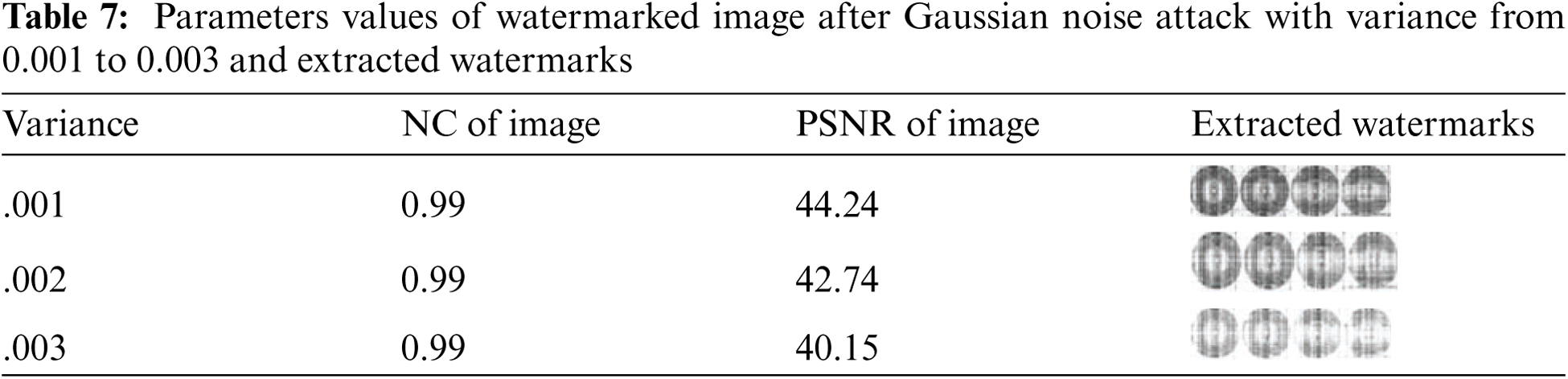
The proposed watermarking method successfully extracts the watermark from the watermarked NIfTI image using a Gaussian noise attack with variance 0.001 and varying it from 0.001 to 0.004. The results of the analysis of the attack for the NIfTI medical images are tabulated in Tab. 7, and the results show that the proposed method for NIfTI images performs well.

The digital image watermarking commonly used in the medical imaging in the field of teleradiology for the medical image authentication purpose while also preserving the integrity of the medical data. Indeed, in this Covid situation it may play an importance in remote diagnosis of the medical images, proposed watermarking scheme can contribute to the security of medical images which are transmitted over the Internet. These images are very sensitive so extreme precautions must be must needed. A seemingly minor image degradation is frequently not tolerated in this discipline since it could result in an inaccurate diagnosis. In this paper we have proposed a watermarking scheme for NIfTI images which ensure the integrity of the medical image while maintaining efficient imperceptibility and robustness.
The proposed watermarking method combines LWT and QR factorization to watermark NIfTI images that contain sensitive medical image data as well as patient information. The proposed method has been tested on various NIfTI images (630 x 630) sourced from CT-Scan and watermarked with grayscale watermarks (32 x 32). The parameters NC, Q, SNR, PSNR, and SSIM serve as the foundation for analyzing watermarked image quality. The tradeoff between image quality and watermark insertion ensures that significant results are obtained. The proposed watermarking method is resistant to image processing attacks such as Salt & Pepper, Poisson, Speckle, and Gaussian noise. After image processing attacks the watermarks are extracted successfully from the watermarked slice of the NIFTI image. The method's results are compared to other existing methods, which shows that the proposed method's results are extremely significant. In the future, the embedded watermark logo can be encrypted using the best encryption algorithm before embedding that provides the maximum efficiency. Furthermore, to increase the robustness of the watermarking scheme, chaotic systems with matrix factorizations can be used.
Acknowledgement: The authors extend their appreciation to the Deputyship for Research & Innovation, Ministry of Education in Saudi Arabia for funding this research work through the project number 959.
Funding Statement: This work was supported by Deputyship for Research & Innovation, Ministry of Education in Saudi Arabia for funding this research work through the project number 959.
Conflicts of Interest: The authors declare that they have no conflicts of interest to report regarding the present study.
1. R. Chamlawi and A. Khan, “Digital image authentication and recovery: Employing integer transform based information embedding and extraction,” Information Sciences, vol. 180, pp. 4909–4928, 2010. [Google Scholar]
2. TABW, Adiwijaya and F. P. Permana, “Medical image watermarking with tamper detection and recovery using reversible watermarking with LSB modification and run length encoding (RLE) compression,” in 2012 IEEE Int. Conf. on Communication, Networks and Satellite (ComNetSatBali, pp. 167–171, 2012. [Google Scholar]
3. T. Takore Tagesse, P. R. Kumar and G. L. Devi, “A modified blind image watermarking scheme based on DWT, DCT and SVD domain using GA to optimize robustness,” in 2016 Int. Conf. on Electrical, Electronics, and Optimization Techniques (ICEEOTChennai, pp. 2725–2729, 2016. [Google Scholar]
4. D. Wang, F. Yang and H. Zhang, “Blind color image watermarking based on DWT and LU decomposition,” Journal of Information Processing Systems, vol. 12, no. 4, pp. 765–778, 2016. [Google Scholar]
5. B. Nigam, A. Nigam, R. Jain, S. Dodia and N. Arora, “COVID-19: Automatic detection from X-ray images by utilizing deep learning methods,” Expert Systems with Applications, vol. 176, pp. 114883, 2021. [Google Scholar]
6. A. Saudagar and O. AlShathry, “Neural network-based image compression approach to improve the quality of biomedical image for telemedicine,” British Journal of Applied Science & Technology, 4, pp. 510–524, 2014. [Google Scholar]
7. D. Wang, F. Yang and H. Zhang, “Blind color image watermarking based on DWT and LU decomposition,” Journal of Information Processing Systems, vol. 12, no. 4, pp. 765–778, 2016. [Google Scholar]
8. N. Lin, J. Shen, X. Guo and J. Zhou, “A robust image watermarking based on DWT-qR decomposition,” in 2011 IEEE 3rd Int. Conf. on Communication Software and Networks, Xi'an, pp. 684–688, 2011. [Google Scholar]
9. Q. Su, Y. Niu, G. Wang, S. Jia and J. Yue, “Color image blind watermarking scheme based on QR decomposition,” Signal Processing, vol. 94, pp. 219–235, 2014. [Google Scholar]
10. R. Ni, Q. Ruan and J. Liu, “Tampering estimation watermarking based on lifting wavelet and chaotic sequence,” in 2006 8th Int. Conf. on Signal Processing, Beijing, 2006. [Google Scholar]
11. T. Gao and Q. Gu, “Reversible watermarking algorithm based on wavelet lifting scheme,” in Int. Conf. on Wavelet Analysis and Pattern Recognition, Beijing, pp. 1771–1775, 2007. [Google Scholar]
12. L. Lizong, G. Tiegang, G. Qiaolun and B. Lei, “A verifiable copyright-proving scheme based on lifting wavelet transformation,” in 2010 Third Int. Symposium on Intelligent Information Technology and Security Informatics, Jinggangshan, pp. 68–72, 2010. [Google Scholar]
13. M. Zairi, T. Boujiha and O. Abdelhaq, “An algorithm for digital image watermarking using 2-level DWT, DCT and QR decomposition based on optimal blocks selection,” in Proc. of the 3rd Int. Conf. on Networking, Information Systems & Security, Marrakech, pp. 1–4, 2020. [Google Scholar]
14. K. Ghaderi, F. Akhlaghianand and P. Moradi, “A new robust semi-blind digital image watermarking approach based on LWT-sVD and fractal images,” in 21st Iranian Conf. on Electrical Engineering (ICEEMashhad, pp. 1–5, 2013. [Google Scholar]
15. R. Chamlawi and A. Khan, “Digital image authentication and recovery: Employing integer transform based information embedding and extraction,” Information Sciences, vol. 180, pp. 4909–4928, 2010. [Google Scholar]
16. R. Mehta, N. Rajpal and V. P. Vishwakarma, “LWT- QR decomposition based robust and efficient image watermarking using lagrangian SVR,” Multimedia Tools and Applications, vol. 75, pp. 4129–4150, 2016. [Google Scholar]
17. Q. Su, Y. Niu, X. Liu and Y. Zhu, “A blind dual color images watermarking based on IWT and state coding,” Optics Communications, vol. 285, no. 7, pp. 1717–1724, 2012. [Google Scholar]
18. A. Sleit, S. Abusharkh, R. Etoom and Y. Khero, “An enhanced semi-blind DWT-sVD-based watermarking technique for digital images,” the Imaging Science Journal, vol. 60, no. 1, pp. 29–38, 2012. [Google Scholar]
19. F. Golshan and K. Mohammadi, “A hybrid intelligent SVD-based perceptual shaping of a digital image watermark in DCT and DWT domain,” Imaging Science Journal, vol. 61, no. 1, pp. 35–46, 2013. [Google Scholar]
20. S. Sarkar and K. Senthilkumar, “A highly secured digital watermarking algorithm for binary watermark using lifting wavelet transform and singular value decomposition,” in IET Chennai 3rd Int. on Sustainable Energy and Intelligent Systems (SEISCON 2012Tiruchengode, pp. 1–5, 2012. [Google Scholar]
21. V. S. Verma, R. K. Jha and A. Ojha, “Significant region based robust watermarking scheme in lifting wavelet transform domain,” Expert Systems with Applications, vol. 42, no. 21, pp. 8184–8197, 2015. [Google Scholar]
22. I. Daubechies and W. Sweldens, “Factoring wavelet transforms into lifting steps,” Journal of Fourier Analysis and Applications, vol. 4, no. 3, pp. 247–269, 1998. [Google Scholar]
23. C. J. Ahn, “Parallel detection algorithm using multiple QR decompositions with permuted channel matrix for SDM/OFDM,” IEEE Transactions on Vehicular Technology, vol. 57, no. 4, pp. 2578–2582, 2008. [Google Scholar]
24. M. Jun, G. Cheng, W. Yixin, A. Xingle, G. Jiantao et al., “COVID-19 CT lung and infection segmentation dataset,” Zenodo Data, 2020. [Online]. Available: https://zenodo.org/record/3757476#.YR4liIgzY2w. [Google Scholar]
25. Y. Chen, Z. Jia, Y. Peng, Y. Peng and D. Zhang, “A new structure-preserving quaternion QR decomposition method for color image blind watermarking,” Signal Processing, vol. 185, pp. 108088, 2021. [Google Scholar]
26. T. Salehnia and A. Fathi, “Fault tolerance in LWT-sVD based image watermarking systems using three module redundancy technique,” Expert Systems with Applications, vol. 179, pp. 115058, 2021. [Google Scholar]
27. Z. Wang and A. C. Bovik, “A universal image quality index,” IEEE Signal Processing Letters, vol. 9, no. 3, pp. 81–84, 2002. [Google Scholar]
28. R. Thanki, S. Borra, V. Dwivedi and K. Borisagarc, “An efficient medical image watermarking scheme based on FDCuT–DCT,” Engineering Science And Technology, An International Journal, vol. 20, no. 4, pp. 1366–1379, 2017. [Google Scholar]
 | This work is licensed under a Creative Commons Attribution 4.0 International License, which permits unrestricted use, distribution, and reproduction in any medium, provided the original work is properly cited. |