DOI:10.32604/cmc.2022.019534

| Computers, Materials & Continua DOI:10.32604/cmc.2022.019534 |  |
| Article |
Blockchain Based Secured Load Balanced Task Scheduling Approach for Fitness Service
1Big Data Research Center, Department of Computer Science and Statistics, Jeju National University, Korea, Jeju-si, 63243, Korea
2Department of Computer Engineering (and Advanced Technology Research Institute), Jeju National University, Jeju 63243, Korea
*Corresponding Author: DoHyeun Kim. Email: kimdh@jejunu.ac.kr
Received: 16 April 2021; Accepted: 19 July 2021
Abstract: In recent times, the evolution of blockchain technology has got huge attention from the research community due to its versatile applications and unique security features. The IoT has shown wide adoption in various applications including smart cities, healthcare, trade, business, etc. Among these applications, fitness applications have been widely considered for smart fitness systems. The users of the fitness system are increasing at a high rate thus the gym providers are constantly extending the fitness facilities. Thus, scheduling such a huge number of requests for fitness exercise is a big challenge. Secondly, the user fitness data is critical thus securing the user fitness data from unauthorized access is also challenging. To overcome these issues, this work proposed a blockchain-based load-balanced task scheduling approach. A thorough analysis has been performed to investigate the applications of IoT in the fitness industry and various scheduling approaches. The proposed scheduling approach aims to schedule the requests of the fitness users in a load-balanced way that maximize the acceptance rate of the users’ requests and improve resource utilization. The performance of the proposed task scheduling approach is compared with the state-of-the-art approaches concerning the average resource utilization and task rejection ratio. The obtained results confirm the efficiency of the proposed scheduling approach. For investigating the performance of the blockchain, various experiments are performed using the Hyperledger Caliper concerning latency, throughput, resource utilization. The Solo approach has shown an improvement of 32% and 26% in throughput as compared to Raft and Solo-Raft approaches respectively. The obtained results assert that the proposed architecture is applicable for resource-constrained IoT applications and is extensible for different IoT applications.
Keywords: Load balancing; resource scheduling; task scheduling; Internet of things; blockchain; fitness applications
For the last few years, the increase in various type of chronic and serious diseases has been witnessed due to tough and stressful routines, unhygienic food, which ultimately lead to various type of disabilities, mortality, and poor physical fitness [1]. Several studies have shown that majority of the people utilize their time in doing work or sitting, which resulted in negative health life. On the other hand, people who spend 30 min in various type of light exercises result in a long-life by approximately 13%. The unhealthy lifestyle and low-quality diet imply that one out of three adults cause obesity [2,3]. Moreover, various life anxieties are produced due to poor physical health [4–6]. Therefore, the doctors always recommend various exercises for maintaining a healthy life. Therefore, the individuals need to spare time for daily fitness activities and keep track of the appropriate diet plan to maintain healthy life. The fitness sports have shown potential growth in the last few years. Several fitness gyms in the world exists [7] where thousands of individuals join and perform exercises on daily basis. Thus, scheduling of the user requests for the exercises like scheduling of other applications is also a big challenge. Various task scheduling approaches [8,9] have been proposed to schedule the user requests on the available resources, improving various metrics like resource utilization, throughput, minimizing task rejections, throughput, and load balancing etc. The resources can be machines or other devices and the user request can be a task, activity or events.
In last few years, the espousal of Internet of Things (IoT) [10–12] in various domains of life has revolutionized the life of the individuals. In the case of IoT, thousands of small IoT devices monitor various environments, gather important sensory data and then forward the accumulated data to some Central location for further processing, helping in various decisions. Like other applications, the healthcare [13] is considered as one of the most important area. In most of the cases, the doctors always recommend various types of exercises to the patients for maintaining a healthy physique. Technological advancements have been seen in the fitness industry in the last few years. The IoT wearable devices are attached or implanted to the trainees in the fitness centers to keep track of their activities and visualize the impact of the exercises on the trainees. The information gathered from these sensing devices are used for various types of trainings conducted in the gyms. Moreover, IoT fitness sensors found to be useful in addressing various critical issues like muscle imbalance, injury, etc. [13]. Like other applications, the fitness IoT data can be used for various data analytics. Based on the data analytics, the trainer can guide the trainees about various types of exercises and improvement in trainee capabilities. In addition, their exists some IoT embedded devices that are useful in ensuring the trainee safety like better workout plan management and notifying the trainees about their stress level. Various approaches have been introduced by the research community relying on the Artificial Intelligence based approaches like DL (Deep Learning), RL (Reinforcement Learning) for various type of decision makings [14,15]. The DL-based approaches are powerful data analytic techniques concerning intelligent decision-making, accurate prediction, and classification in the context of IoT. These approaches extract important features from huge sensory data and perform various type of predictions and other decision-making tasks.
The IoT fitness data of the trainee and trainers are of utmost significance and ensuring the security and integrity of such data is most important requirement. In storing the fitness data outside the user premises on some external storage location including fog, edge, or Cloud computing, the big challenge is to ensure the integrity and unauthorized access of the users’ fitness data. It is therefore important to verify that fitness data has not been tampered or altered. In recent times, the blockchain-based approaches are proposed for different security services [11,15]. Like other applications, the Blockchain also offer solutions to verify the trustworthiness of information as well. The Blockchain approaches are scalable in nature and have the ability to ensure the security of various transactions in a decentralized manner by providing authority to each participant for transactions verification. Every transaction in the blockchain network is signed and ultimately verified by each legitimate network participant. The cryptographic hash algorithms are used to ensure the integrity of the transactions and the mining nodes are responsible for signing and verifying transactions and maintaining the blockchain ledger consisting of chained blocks of transactions [13,15,16]. All these features of the blockchain lead to the transactions that are immutable and altering any transactions is not possible.
The task scheduling problem is NP-hard in nature thus it is difficult to propose and develop a complete optimal scheduling solution. The first part of this work proposes a load balanced device scheduling approach based on the fuzzy logic that schedule the user requests (also called tasks in this work) over the available fitness devices in a load balanced way. The user fitness data is critical and needs to be secured from unauthorized access. To overcome the security issue, a blockchain-based secured architecture for fitness data security management is proposed.
The rest of the paper is organized as follows: In Section 2, the discussion about existing work concerning the task scheduling, Machine learning algorithms, and blockchain based solutions is presented. The proposed approach is delineated in Section 3, followed by experimental setup and performance evaluation section. The conclusions and future directions are discussed in Section 5.
The related section is divided into three subsections. In first part of this section, the related work concerning the state-of-the-art task scheduling approaches is discussed. The second subsection delineates the existing machine learning approaches concerning the fitness data management and intelligent decision making. The last part of the related work shed light on the available blockchain based approaches used for the security of fitness data.
Task scheduling has been a widely considered research topic in various domains including industry, processing, distributed computing, Cloud computing, user request scheduling over the available resources, etc. The resources in any system are precious thus, efficiently utilizing the resources is always the main focus. The task scheduling approaches are adopted to cope with various challenges including resource utilization, minimizing average response time, execution time, throughput, minimizing SLA violation, and load balancing, etc. The Fist-In-First-Out (FIFO) approach assigns the tasks to the available resources according to their arrival order [17]. The FIFO approach is simple to implement and involves less computation overhead. However, the smaller size tasks will face long time wait if larger size task arrived earlier. This will lead to a bad user experience and also the response time is increased for smaller tasks. The Min-Min [18] heuristic picks the task with a smaller size from the available task list and then assigns the task to the resource which completes its execution in the minimum time on the available resources. The Min-Min-based approach is complex and involves high computation overhead as compared to the FIFO approach. This approach penalizes the large-size tasks concerning waiting time and prefers smaller-size tasks. On the other hand, the Max-Min [19] task scheduling approach picks the largest task and then maps it to the device that completes its execution in the minimum possible time. The inputs to this approach are tasks and device lists and it select the large size task and computes the expected finish time on all the devices one by one. The Max-Min assigns the task to the resource having the least expected finish time. This approach favors large-size tasks and the small-size tasks are penalized concerning response time. Thus, the Max-Min approach results in inefficient resource utilization. Authors in [20] have proposed a Dynamic Max-Min approach that is based on the Max-Min heuristic. The dynamic Max-Min approach is provided a list of tasks that selects the largest task from the received task list and assigns it to the device with the least finish time. This approach can update the device status and task status table at different intervals of time. The Dynamic Max-Min approach leads to resources under-utilization and load imbalance.
2.2 Machine Learning Approaches for Fitness Technology
Like other applications of IoT, the advancement in IoT technology for fitness applications has shown tremendous progress in the last few years [14]. Various fitness devices are implanted or attached to the human body to get an insight into various fitness indexes and health status of the sports fitness players in a ubiquitous way, thus helping in health assessment of the humans and fitness maintenance of the sports players [21]. The individuals as well as the trainers in the fitness gyms can monitor and evaluate the trainee fitness progress using the gathered sensor fitness data. The current research on the fitness applications has shown deep insights into how various fitness exercises impact the human body, helping in controlled exercises and diet plans accordingly. The authors in [22] presented the idea of utilizing Mobile sensors and wearable devices for monitoring the athlete muscles and fitness conditions. The authors proposed an approach utilizing the K-Nearest Neighbor approach for monitoring the sports players’ fitness during the training and then providing them the feedback based on the analyzed data. The authors proposed an IoT and blockchain integrated approach to create a healthy connection between the IoT applications and human beings to provide insights into the usefulness of IoT for fitnes [23]. The proposed architecture is composed of three layers that are; perception, transmission, and application. The IoT sensors continuously monitor and acquire sports and fitness information, aggregate the acquired data and then disseminate it to the system for further analytic processing for useful insights. In Atlam et al. [24] presented the details concerning the applicability of IoT in AI-based applications for various intelligent decision making and analysis. This work also sheds light on some of the challenges associated with the integration of IoT with AI applications.
Fig. 1 depicts a generic blockchain based IoT and AI integrated model for fitness applications. The IoT devices capture human body postures and store in the blockchain for further analytical processing. The data is then used for data analytics by various machine learning models to provide useful insights about the trainees which can be exploited by the trainers in the fitness center or by healthcare professionals for various decision making.
2.3 Blockchain for Fitness Data Security
In the last few years, fitness centers utilize various electronic IoT devices to capture, share, digitize, and process fitness data. In this section, we investigated some state-of-the-art blockchain-based fitness applications. In [25], the authors proposed and discussed fitness applications that allow trainee users to perform physical activities and are paid for that based on a pre-defined incentives-based strategy. This work provides an insight into the changes in the user's physical activities, such as counting daily steps. Th author in [26] discussed and presented a sweatcoin strategy considered as a digital currency that is provided as an incentive to the users for their physical activities. The users are required to gather personal physical information like step counts and are provided sweatcoin as an incentive. In [27], an application called Run2Play is developed for monitoring the user's physical exercise activities and incentives are provided to the users for each physical activity. In 2017, Martin designed Ethereum based Movement app that incentives the users for physical exercises, such as running, treadmill, jogging, and any other physical activity [28]. They also build a marketplace where the users can use their tokens for purchasing fitness devices and also register for online yoga courses. In addition, the users can exchange their tokens with another cryptocurrency. In 2016, a fitness application called Truegymis is developed for educating people about exercise management. This application exploits machine learning-based techniques to analyze the acquired data of the trainee and then recommend a training plan for the user [28]. Drake designed an Ethereum based blockchain fitness application called ‘The Hustle’ for promoting health, wellness, and user fitness data. The Ethereum token is provided as a reward to the user who participates in the fitness exercises. The HUSL token is exchangeable with other currencies, such as BTC, ETH, or USD [29]. Most of the existing blockchain-based applications for fitness applications, utilize the crypto-currency that has some computations overhead.

Figure 1: Generic blockchain based IoT and AI integrated model for fitness applications
In the light of the aforementioned issues, this work contributed Blockchain based User-Device Scheduling Mechanism. The work is divided into two different parts. In the first part, fuzzy-based device scheduling (also called tasks) is proposed that schedules the request of the fitness users on the available fitness devices in a load-balanced way. The second contribution of this work is related to the security assurance of the fitness data using the blockchain-based approach.
In this work, we have proposed Enhanced User-Device Scheduling Mechanism using Fuzzy Logic based on Blockchain for secure smart fitness service. The discussion about the proposed work is presented as follows.

Figure 2: System architecture of proposed task scheduling fitness service
3.1 Blockchain Based Secure Fitness Scheduling Service
This section discusses the system architecture of the proposed fitness scheduling service. As the task scheduling is NP-hard in nature thus optimally scheduling the tasks is always challenging. In large-scale Gyms, thousands of users request the gym at various times and need various fitness devices for exercise. The increase in the number of users and requests for devices leads to the complexity of the scheduling problem. In most of the gyms, the exercise sessions are divided into three shifts (sessions) i.e., morning, evening, and night. Each shift will have different number of slots, each of one hour. Moreover, the users can be either members (who have a membership and frequently join the exercises) or non-member who join the exercise less frequently. Thus, maximizing the user request acceptance and increased resource utilization is ultimately required. Various approaches are in place to improve the resource utilization of the available resources. In this research, a priority-aware, load-balanced device scheduling scheme is proposed. The load-balanced scheduling has two benefits, firstly, to entertain maximum user requests and secondly, to maximize resource (fitness devices) utilization. The proposed approach is comprised of several components as shown in Fig. 2. Initially, the user requests for fitness device for exercise and each user request is stored in Task repository. The information about the available fitness devices is stored in device repository. The user requests (Tasks) and the fitness devices are provided as an input to the priority mapping module. The priority mapping module provides user information like age, gender, weight and height to the fuzzy inference controller. Based on the user information, the BMI is calculated to find the health level of the user as given in Eq. (1).
The fuzzy logic considers BMI (Body Mass Index) parameter for assigning the priority. The task priority is calculated based on the following rules:
R1. If BMI < 18.5 then Health level is Underweight and priority is Low
R1. If 18.5 < BMI ≤ 24.9 then health level is Normal and priority is Medium.
R1. If 24.9 < BMI ≤ 29.9 then Health level is Overweight and priority is High
R1. If BMI ≥ 30 then Health level is Obese and priority is High
The tasks are first prioritized using the fuzzy rules and then passed to the task scheduling layer as an input. The task scheduler then considers the tasks priority and map the user requests using the proposed task scheduling approach. Algorithm 1 prioritizes the user requests using fuzzy rules that considers the user health level based on the BMI metric. The health level is categorized into four types that are Underweight, Normal, Overweight, and Obesity. Based on the input of the health status, the priority is calculated using fuzzy rules discussed previously. The available slots are in morning, evening, and night. In Algorithm 1, the priority list is populated using fuzzy logic.
The next step is to map the user requests to the available fitness devices. Each user request is compared whether in the priority list. If the task is having high priority, then user request is mapped to the requested time in the requested time slot. In case, the priority is low or medium, the requests are mapped into a temporary list. Following are nine inference rules used for mapping the user tasks to the available fitness devices:
R1. If (task priority is high and arrival time is short then task will be mapped)
R2. If (task priority is Medium and arrival time is short then task will be mapped)
R3. If (task priority is Low and arrival time is short then task will wait, and mapped)
R4. If (task priority is high and arrival time is Medium then task will be wait and mapped)
R5. If(task priority is Medium and arrival time is Medium then task will wait and mapped)
R6. If (task priority is Low and arrival time is Medium then task will suspend, wait, and mapped)
R7. If (task priority is high and arrival time is High then task will be wait and mapped)
R8. If (task priority is Medium and arrival time is High then task will suspend, wait, and mapped)
R9. If (task priority is Low and arrival time is High then task will suspend, wait, and mapped)

In the last step, the tasks are scheduled on the available devices in a load-balanced way. The scheduling information is forwarded to some central location like Cloud or edge computing platform.
Moreover, the fitness users perform various exercises and physical activities during the fitness in the gym. This data of the users is of prime importance thus integrity and privacy is of much concern. The IoT wearables collect physical activity information of the user steps and transfer it to the IoT server. The collected information is then forwarded to the blockchain network. Every node in the blockchain carries a replica of the ledger and any alteration in a copy will result in the updation of other copies of the ledger across the blockchain within seconds to minutes. For security insurance, an identity certificate is issued and approved by the network member across the smart contract-based blockchain network. The identity certificate is used by each peer node to store each transaction securely in the blockchain network. In the smart contract-based blockchain network, the inference engine is used to discover useful knowledge, patterns and perceive latent insights from the users' fitness data. The users are provided front-end interfaces to work with secure fitness services and visualize various useful fitness information.

Fig. 3 contemplates the flowchart of the proposed task scheduling fitness service. The system user is allowed to connect and access fitness services. The inputs to the fitness service are the user requests for the devices and the fitness devices. Initially, the user requests and device list are provided as an input to the system. The next step is to execute scheduling of the user requests for the fitness devices based on the priority assigned to various user requests. The user requests are prioritized based on BMI. The previous subsection discussed how priority is assigned to the user request and then scheduled. The fuzzy logic inference controller exploits 4 rules to assign the priority. Once the priorities are assigned, the next step is to map the users to the respected fitness devices. For this purpose, the Scheduling module requests the fitness resource manager for reserving the fitness device. The resources are then assigned and the scheduling is then performed in a load-balanced way. The detailed steps about scheduling are provided and discussed in Algorithm 2. The fitness scheduling information is then collected and stored in the blockchain network in a secured way.
The trainee user then starts exercises according to their defined schedule. The IoT wearable collects physical activity information of the user steps and transferred it to the IoT server. The collected information is then forwarded to the smart contract-based blockchain network. Then, the consensus algorithm is executed and then collected real-time information is archived in the blockchain state database, and every peer in the blockchain network affix the physical activity transactions. Furthermore, the smart contract executes machine learning approach to infer knowledge from the gathered data and perform various decisions. The obtained results and inferred knowledge are then shown to the trainees and trainers through the client application. All successful transactions are then stored and updated by every peer in the blockchain network ledger state.

Figure 3: Proposed secured fitness system workflow
4 Experimental Setup and Performance Evaluation
This section contemplates the details concerning the experimental setup configuration details and the performance analysis of the proposed approach against the contemporary approaches. This section is divided into the following subsections.
The performance evaluation can be performed in three different ways that are experimental, analytical, or simulation approaches. The experimental setup is costly and difficult to configure due to the complexities involved in setup and execution. However, experimental approaches provide more real performance evaluation of the underlying approaches. The analytical approaches are easy to deploy; however, they are unable to grasp some of the important characteristics for the performance evaluation. The simulation-based approaches are widely used techniques for an in-depth evaluation of various types of networks.
In this paper, we have considered the experimental approach for some of the experiments and for other experiments, we have utilized the simulation approach. The objectives of this paper are two folds that are; task scheduling of the user request for fitness devices and security of the user fitness data by using blockchain based network. For the first objective, the simulation experiments are performed by using implementation in the python language. To validate the second objective, the implementation is performed using the hyper-ledger fabric and the result evaluation using hyper-ledger caliper tool. The experiments are executed on a system equipped with 20 GB of RAM and a processing speed of 3.00 GHz core I5.
Several experiments have been performed to evaluate the performance of the proposed task scheduling approach and evaluating the performance of the blockchain network implemented in this work. The details concerning experiment 1 for evaluating the performance evaluation against the compared approaches is presented in Tab. 1.
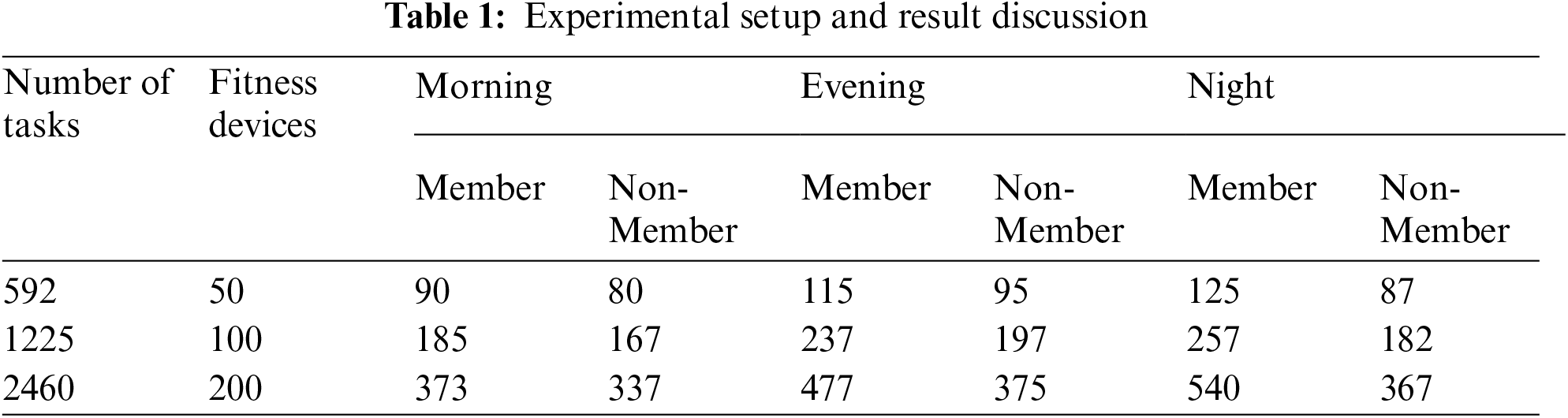
The experiments are executed multiple times with three different configurations i.e., the number of available fitness devices are 50, 100, and 200 whereas the number of user requests (Tasks) are 592, 1225, and 2460 respectively. The availability of the devices for exercise are divided into three shifts; morning, evening, and night. The time slots are divided into a time of one hour and each of the shift is comprised of 4 slots. Thus, the total number of slots available are 12 and each of the device is available for these 12 hours. The total number of slots available can be calculated using the Eq. (2).
Fig. 4 contemplates the results concerning the average resource utilization (ARUR) for all of the task scheduling approaches. On x-axis, the number of tasks is shown for three different experiments and the y-axis represents the average resource utilization. The highest resource utilization of 95% has been observed for the proposed approach when the number of tasks is 2460 with 200 available devices. The FIFO approach has also shown improved performance and achieved second highest resource utilization of the three compared approaches. The proposed outperformed the other two approaches with an improvement of 20 to 35% in the resource utilization. The obtained results asserts that the proposed approach is suitable for the scheduling of user requests on the available devices.
Another important metric to evaluate the performance of scheduling approaches is task rejection ratio (TRR) that satisfies the user quality of experience. The results concerning the task rejection ratio for the proposed approach and compared approaches are delineated in Fig. 5. When the number of user requests are 585, the proposed approach has been able to reduce the TRC by 25 to 30% against the compared contemporary approaches. With the increase in number of users further, a dramatic decrease in TRR has been observed for the proposed approach while the other two approaches experienced poor performance concerning task rejection ratio. With further increase in the number of user requests, the proposed approach has shown consistent performance while the other two approaches have led to a rejection ratio of 14 to 18%. The obtained results asserts that the proposed approach is best choice for the user requests while considering huge number of user requests for the fitness devices.
To evaluate the performance of the blockchain network, the Hyperledger fabric is utilized for the implementation and deployment. The experiments are performed several times using Hyperledger caliper and the obtained results are discussed as below.
In our work, we performed several experiments with a varying number of users, executing queries for data retrieval from the blockchain network to see the impact of the number of users on the query transaction latency. The results concerning the query transaction latency are contemplated in Fig. 6. The results are obtained and plotted for minimum, maximum, and average latency with varying numbers of users. A steady behavior is observed in the latency when the number of users is increased from 100 to 1000. When the number of users is increased from 100 to 1000 a total of 29.4% is observed whereas when the users are increased from 1000 to 1200 the latency is increased by 32.3%. Further increase in the number of users leads to an increased query transaction latency. However, the results show scalable behavior of the blockchain network at the cost of approximately 4% increase in latency.

Figure 4: Average resource utilization comparison

Figure 5: Task rejection ratio comparison

Figure 6: Impact of varying number of users on query transaction latency
The Hyperledger Fabric also provides ordering services that order the transactions by using nodes called ordering nodes. To evaluate the performance of the blockchain network, three types of ordering service (i.e., solo, raft, and solo-raft) with varying transaction rates, such as 50, 100, …, 300 TPS are considered as given in Fig. 7a. The latency for the Raft is higher for 50 TPS and continues to increase to 300 TPS against the other two approaches. The obtained results show that the latency of solo is much lower as compared to the Raft and Solo Raft due to the overhead of transport layer security utilized for peer nodes authentication. The results in Fig. 7b. contemplates the throughput for solo, raft, and solo-raft ordering approaches with varying transaction send rates. All three approaches have shown similar behavior when the transaction send rate is 50. An increase in the send rate in transaction leads to a higher increase in the throughput for the Solo approach with an improvement of 32% and 26% against the Raft and Solo-Raft approaches respectively. This behavior is persistent for all the other tested experiments with a further increase in transaction send rate. It can be seen from the obtained results that higher throughput is achieved by the solo order service as compared to the other two ordering services.
The proposed approach has been evaluated concerning the task rejection ratio and resource utilization and compared against two state-of-the-art baseline scheduling approaches. Concerning the task rejection ratio, the proposed approach has dominated the other two approaches by 25% and then reaching to an improvement of 70%. This improvement is due to the reason that proposed approach accept most of the user requests and then employ load balanced approach to satisfy the QoS requirements of the users and distribute the requests in a load balanced way. The other two approaches are simple in nature; however, are unable to deal with quality-of-service requirements of the users and also lead to an imbalance distribution of user requests over the available devices. As the proposed approach keeps the load balanced over the available fitness devices, the resource utilization is also improved while maximizing the user quality of experience.

Figure 7: (a) Influence of changing orderer nodes with different send rates on Latency; (b) Influence of changing orderer nodes with different send rates on throughput
The users of fitness are increasing at an immense rate and the gymmers are constantly extending the fitness facilities. Thus, handling such a huge number of requests for fitness devices and scheduling these requests is a big challenge. Secondly, the user fitness data is critical and needs to be secured from unauthorized access. This work addressed these issues concerning the fitness data management that are the scheduling of user requests over the available fitness devices in a load-balanced way and then provisioning of security service by implementing and deploying the blockchain-based solution. For this purpose, an in-depth analysis has been performed to investigate the applications of IoT in the fitness industry and various scheduling approaches. The proposed outperformed the other two approaches with an improvement of 20 to 35% in resource utilization. The obtained results assert that the proposed approach is suitable for the scheduling of user requests on the available devices. The security of fitness data is a big concern thus in this work we proposed and employed smart contract enabled blockchain network. The obtained results imply that the proposed blockchain network provides the required security and is extensible for other IoT applications.
The fitness IoT application involves huge sensory data concerning the user fitness data. This data needs to be stored and evaluated in a timely manner (keeping in view the delay requirements) to obtain useful insights. TAs a future work, we will propose a deadline aware task scheduling approach for edge computing to handle delay constrained fitness data.
Funding Statement: This research was supported by Energy Cloud R&D Program through the National Research Foundation of Korea (NRF) funded by the Ministry of Science, ICT (2019M3F2A1073387), and this research was supported by Institute for Information & communications Technology Planning & Evaluation (IITP) grant funded by the Korea government (MSIT) (No. 2018-0-01456, AutoMaTa: Autonomous Management framework based on artificial intelligent Technology for adaptive and disposable IoT). Any correspondence related to this paper should be addressed to Do-hyeun Kim.
Conflicts of Interest: The authors declare that they have no conflicts of interest to report regarding the present study.
1. J. F. Sallis, E. Cerin, J. Kerr, M. A. Adams, T. Sugiyama et al., “Built environment, physical activity, and obesity: Findings from the international physical activity and environment network (IPEN) adult study,” Annual Review of Public Health, vol. 41, no. 1, pp. 119–139, 2020. [Google Scholar]
2. B. Belza, J. Walwick, S. Schwartz, J. LoGerfo, S. Shiu-Thornton et al., “Older adult perspectives on physical activity and exercise: Voices from multiple cultures,” Preventing Chronic Disease, vol. 1, no. 4, pp. A09, 2004. [Google Scholar]
3. C. Bouchard, S. N. Blair and W. L. Haskell, “Physical activity and fitness with age, sex, and ethnic differences,” in Physical Activity and Health, 2nd ed., United Kingdom: Human Kinetics, pp. 72–110, 2012. [Google Scholar]
4. J. Borgman, “Design of a personalized e-coaching module on physical activity and nutrition for people with chronic diseases and low health literacy,” Bachelor’s thesis, University of Twente, Netherlands, 2020. [Google Scholar]
5. F. Mallamaci, A. Pisano and G. Tripepi, “Physical activity in chronic kidney disease and the exercise introduction to enhance trial,” Nephrology Dialysis Transplantation, vol. 35, pp. ii18–ii22, 2020. [Google Scholar]
6. G. Maugeri, P. Castrogiovanni, G. Battaglia, R. Pippim, V. D. Agata et al., “The impact of physical activity on psychological health during Covid-19 pandemic in Italy,” Heliyon, vol. 6, no. 6, pp. e04315, 2020. [Google Scholar]
7. Town of Cary, Fitness Dataset, 2017. [Online]. Available: https://data.world/townofcary/open-gym/workspace/file?filename=open-gym_3.csv. [Google Scholar]
8. S. Ahmad, L. Hang and D. Kim, “Design and implementation of cloud-centric configuration repository for DIY IoT applications,” Sensors, vol. 18, no. 2, pp. 474–494, 2018. [Google Scholar]
9. S. Ahmad, I. Hussain, M. Fayaz and D. Kim, “A distributed approach towards improved dissemination protocol for smooth handover in MediaSense IoT platform,” Processes, vol. 6, no. 5, pp. 46–61, 2018. [Google Scholar]
10. S. Ahmad, S. Malik, I. Ullah, M. Fayaz, D. H. Park et al., “An Adaptive approach based on resource-awareness towards power-efficient real-time periodic task modeling on embedded IoT devices,” Processes, vol. 6, no. 7, pp. 90–116, 2018. [Google Scholar]
11. A. Ferrag, L. Maglaras and H. Janicke, “Blockchain and its role in the Internet of things,” in Strategic Innovative Marketing and Tourism. Cham: Springer, pp. 1029–1038, 2019. [Google Scholar]
12. S. Ahmad, S. Malik, I. Ullah, D. H. Park, K. Kim et al., “Towards the design of a formal verification and evaluation tool of real-time tasks scheduling of IoT applications,” Sustainability, vol. 11, no. 1, pp. 204–226, 2019. [Google Scholar]
13. F. Jamil, S. Ahmad, N. Iqbal and D. H. Kim, “Towards a remote monitoring of patient vital signs based on IoT-based blockchain integrity management platforms in smart hospitals,” Sensors, vol. 20, no. 8, pp. 2195, 2020. [Google Scholar]
14. A. Farrokhi, R. Farahbakhsh, J. Rezazadeh and R. Minerva, “Application of Internet of Things and artificial intelligence for smart fitness: A survey,” Computer Networks, vol. 189, no. 107859, pp. 1–21, 2021. [Google Scholar]
15. A. H. Lone and R. Naaz, “Applicability of Blockchain smart contracts in securing Internet and IoT: A systematic literature review,” Computer Science Review, vol. 39, no. 100360, pp. 1–13, 2021. [Google Scholar]
16. F. Jamil, S. Ahmad, N. Iqbal and D. H. Kim, “Towards a remote monitoring of patient vital signs based on IoT-based blockchain integrity management platforms in smart hospitals,” Sensors, vol. 20, no. 8, pp. 2195, 2020. [Google Scholar]
17. P. Y. Zhang and M. C. Zhou, “Dynamic cloud task scheduling based on a two-stage strategy,” IEEE Transactions on Automation Science and Engineering, vol. 15, no. 2, pp. 772–783, 2018. [Google Scholar]
18. M. Ibrahim, S. Nabi, A. Baz, H. Alhakami, M. S. Raza et al., “An in-depth empirical investigation of state-of-the-art scheduling approaches for cloud computing,” IEEE Access, vol. 8, pp. 128282–128294, 2020. [Google Scholar]
19. M. Ibrahim, S. Nabi, R. Hussain, M. S. Raza, M. Imran et al., “A comparative analysis of task scheduling approaches in cloud computing,” in 20th IEEE/ACM Int. Sym. on Cluster, Cloud and Internet Computing (CCGRIDIEEE, pp. 681–684. [Google Scholar]
20. Y. Mao, X. Chen and X. Li, “Max-Min task scheduling algorithm for load balance in cloud computing,” in Proc. of Int. Conf. on Computer Science and Information Technology, Advances in Intelligent Systems and Computing, Kunming, China, vol. 255, pp. 457–465, 2014. [Google Scholar]
21. Y. Qiu, X. Zhu and J. Lu, “Fitness monitoring system based on Internet of things and big data analysis,” IEEE Access, vol. 9, pp. 8054–8068, 2021. [Google Scholar]
22. S. Liu, “Mobile sensor network and wearable devices application in athlete muscle and physical fitness image monitoring,” Microprocessors and Microsystems, vol. 82, pp. 1–5, 2021. [Google Scholar]
23. H. J. Pula, C. E. Trenzado, S. García-Mesa, C. Fallola and A. Sanz, “Effects of different culture systems on growth, immune status, and other physiological parameters of tench (Tinca tinca),” Aquaculture, vol. 485, no. 5, pp. 101–110, 2018. [Google Scholar]
24. H. F. Atlam, R. J. Walters and G. B. Wills, “Intelligence of things: Opportunities challenges,” in 3rd Cloudification of the Internet of Things (CIoT). Paris: USA, pp. 1–6, 2018. [Google Scholar]
25. M. Elliott, F. Eck, E. Khmelev, A. Derlyatka and O. Fomenko, “Physical activity behavior change driven by engagement with an incentive-based app: Evaluating the impact of Sweatcoin,” JMIR mHealth and uHealth, vol. 7, no. 7, pp. e12445, 2019. [Google Scholar]
26. A. Derlyatka, O. Fomenko, F. Eck, E. Khmelev and M. Elliott, “Bright spots, physical activity investments that work: Sweatcoin: A steps generated virtual currency for sustained physical activity behavior change,” British Journal of Sports Medicine, vol. 53, no. 18, pp. 1195–1196, 2019. [Google Scholar]
27. J. Anthony, run2play, 2018. [Online]. Available: https://www.run2play.com/wp-content/uploads/2018/06/Run2Play_Whitepaper_June-12-2018.pdf. [Google Scholar]
28. M. Holt, “Movement App,” 2021. [Online]. Available: https://icobench.com/ico/movement-app. [Google Scholar]
29. J. Štreit and M. D. Haladi, True-Gym, 2016. [Online]. Available: https://truegym.io/wp-content/uploads/2018/08/True-Gym-Whitepaper-EN-v2.pdf. [Google Scholar]
 | This work is licensed under a Creative Commons Attribution 4.0 International License, which permits unrestricted use, distribution, and reproduction in any medium, provided the original work is properly cited. |