DOI:10.32604/cmc.2022.022469

| Computers, Materials & Continua DOI:10.32604/cmc.2022.022469 |  |
| Article |
Intelligent Disease Diagnosis Model for Energy Aware Cluster Based IoT Healthcare Systems
1Department of Information Technology, Faculty of Computing and Information Technology, King Abdulaziz University, Jeddah, Saudi Arabia
2Department of Computer Science, Faculty of Computing and Information Technology, King Abdulaziz University, Jeddah, Saudi Arabia
3Department of Mathematics and Statistics, College of Science, Taif University, Taif, 21944, Saudi Arabia
4Department of Mathematics, Faculty of Science, New Valley University, El-Kharga, 72511, Egypt
*Corresponding Author: Wafaa Alsaggaf. Email: waalsaggaf@kau.edu.sa
Received: 08 August 2021; Accepted: 09 September 2021
Abstract: In recent days, advancements in the Internet of Things (IoT) and cloud computing (CC) technologies have emerged in different application areas, particularly healthcare. The use of IoT devices in healthcare sector often generates large amount of data and also spent maximum energy for data transmission to the cloud server. Therefore, energy efficient clustering mechanism is needed to effectively reduce the energy consumption of IoT devices. At the same time, the advent of deep learning (DL) models helps to analyze the healthcare data in the cloud server for decision making. With this motivation, this paper presents an intelligent disease diagnosis model for energy aware cluster based IoT healthcare systems, called IDDM-EAC technique. The proposed IDDM-EAC technique involves a 3-stage process namely data acquisition, clustering, and disease diagnosis. In addition, the IDDM-EAC technique derives a chicken swarm optimization based energy aware clustering (CSOEAC) technique to group the IoT devices into clusters and select cluster heads (CHs). Moreover, a new coyote optimization algorithm (COA) with deep belief network (DBN), called COA-DBN technique is employed for the disease diagnostic process. The COA-DBN technique involves the design of hyperparameter optimizer using COA to optimally adjust the parameters involved in the DBN model. In order to inspect the betterment of the IDDM-EAC technique, a wide range of experiments were carried out using real time data from IoT devices and benchmark data from UCI repository. The experimental results demonstrate the promising performance with the minimal total energy consumption of 63% whereas the EEPSOC, ABC, GWO, and ACO algorithms have showcased a higher total energy consumption of 69%, 78%, 83%, and 84% correspondingly.
Keywords: Intelligent models; healthcare systems; disease diagnosis; internet of things; cloud computing; clustering; deep learning
The Internet of Things (IoT) plays an important part in healthcare fields by fully altering the landscape of the entire world. Miniaturized devices are the paradigm shift and building blocks to reform healthcare, therefore sustainability and security are the essential parameters to construct smart IoT based medical healthcare [1]. Also, IoT method is the magic to determine the stronger connections among real-worlds and physical by gathering all the heterogeneous techniques at a single general environment in a cost-effective, prominent, secure dynamic, and flexible way. As well, developing and broadly utilized part of IoT created the everyone lives convenient and comfortable when posed the several problems viz., high energy drain, less sustainability, and less security and so on threatening the smart IoT enabled healthcare related application. IoT application is advanced to utilize this interconnected network, based on a digital platform. It provides a novel opportunity to accurate and fast replies by attaining appropriate data. This smart network could obtain data from various sources, locally process data by the reduced computing power or in a centralized way with high digital computing resources for making smart decisions [2]. From this, predictive analysis, pattern detection, or intelligent recommendations could be done.
Using these smart capabilities, IoT technique allows the enhancement of Quality of Service (QoS). The data interchange is providing a continual flow among doctors, patients, biomedical suppliers, pharmaceutical, etc. Regarding this, IoT utilizes innovative IT techniques for integrating different modules of a cooperative network to enhance the service capability, flexibility, and efficiency among smart devices. Such smart devices are capable of monitoring and sensing their environmental condition, and evaluate the functions/activities on the installed platform [3]. The collected data could be transferred to a decision support system or management unit for additional processing. Gathered sensory data could be utilized for understanding the system's present state by observing the state of all units in the network and the status of the whole system. Initially, data processing technology could be applied for transforming raw to input data [4]. Processed input data could be transformed into useful data with the help of data processing methods and lastly, this data could allow the system to offer self-action via knowledge processing methods with no human intervention. Specifically, IoT systems could generate autonomous systems through self-management and self-governance capabilities.
Presently, a big portion of data is being made with IoT devices, utilized as “big data” and input fed by deep learning (DL) algorithm for yielding useful data [5]. The DL method contains several implications and is nearly accessible in all aspects of their life. Healthcare and Medical utilization are amongst the more common ones and are yet developing. EHRs, incorporated digital images (histology, radiography, and mammography), medical and administrative databases, data obtained from medical devices IoT, genes data, data come from search engines and mobile applications, are the key resources of DL algorithm which could help decide clinically, predict, diagnose, and so on. Other people utilized in pharmaceutical and biomedical areas like pharmacogenomics, molecular diagnostics, DNA Sequencing, identification of pathogenic variants, personalized cancer care, drug discovery, and gene splicing [6]. Machine learning (ML) is utilized in different fields such as healthcare and education. With the development of technologies, the availability of datasets and better computing power on public domain sources have additionally improved the usage of ML [7].
ML is utilized in healthcare in massive regions. The healthcare sectors produce huge number of data based on patient data, images, etc. which assist to recognize patterns and create predictions. ML is utilized in healthcare for solving several challenges. Heart disease is depending upon the person, and the extent of heart disease could differ from one patient to another [8]. Therefore, creating an ML method, trained it on the dataset, and entering personal details could assist in predictions. The predictive results would be based on the data entered and therefore would be particular to that person.
This paper presents an intelligent disease diagnosis model for energy aware cluster based IoT healthcare systems, called IDDM-EAC technique. The proposed IDDM-EAC technique initially enables the IoT devices to perform the data acquisition process. Besides, a chicken swarm optimization based energy aware clustering (CSOEAC) technique is designed to group the IoT devices into clusters and select cluster heads (CHs). Furthermore, a new coyote optimization algorithm (COA) with deep belief network (DBN), called COA-DBN technique is employed for the disease diagnostic process. To assess the enhanced outcomes of the IDDM-EAC technique, a series of simulations take place using the real time data from IoT devices and benchmark data from UCI repository.
Bharathi et al. [9] introduce an EEPSOC method for the efficient election of CHs amongst different IoT devices. The IoT device utilized to sensitive healthcare information is gathered to a kind of clusters and a CH would be selected through EEPSOC. Then, an ANN based classification method is employed for diagnosing the healthcare information in the cloud servers for identifying the seriousness of the disease. In Mohammadi et al. [10], the patient's courtesy signal is recorded using a wearable sensor. Such signals are later transferred to a server in the network platform. Also, this study presents a novel hybrid decision making method for diagnoses. In this technique, feature sets of person signals are generated primarily. Later, this feature keeps a low profile based on a learning method. Then, a diagnosis is executed by a neural fuzzy method.
Phan et al. [11], proposed a smart LED therapy scheme for automated facial acne vulgaris diagnoses on the basis of DL and IoT applications. The primary objective of this work is to improve an LED therapy device using distinct LED grid control and power densities. Also, a DL method based on adapted ResNet50 & YOLOv2 for automated acne diagnoses is established. Lastly, smartphone applications are developed for LED therapy parameter configuration and facial photography image capture. Moreover, an H-IoT environment for the connectivity among LED therapy device, smartphone application, and the cloud servers are projected for improving efficacy of the treatment procedure.
Satpathy et al. [12], proposed an IoT based analyses method that could be utilized for designing a user electronic device. These IoT based analyses method would alert the consumer while some of the variables associated with his/her health are below/above the standard range. The data gathered by this technique is transfer to the cloud via mobile applications and later transfer to the FPGA analyses scheme. The raw data is processed and computed using the FPGA scheme, and pathological condition is shown on the patients’ wearable IoT device. Juyal et al. [13] present a novel ‘Intelligent’ Skin Monitoring Device concept, which enables patients in rural regions for monitoring skin disease remotely. The presented method has AI and cloud based IoT, in which CNN is utilized for analyzing the disease predictions and medical images. Also, the impacts of the season are tackled in this study. The architecture provides a preventive and diagnostic method to address the problem confronted by the person with minimum or no skincare services in remote regions.
Sharma et al. [14], proposed a DL based Internet of Health Framework for the Assistance of Alzheimer's Patients. DeTrAs functions in 3 stages: (i) A RNN based Alzheimer predictive system is projected that utilizes sensory motion data, (ii) an ensemble method for tracing abnormalities of Alzheimer patients is developed that contains 2 portions: (a) CNN based emotion detection system and (b) time-stamp window based NLP system, and (iii) an IoT based assistance mechanisms for the Alzheimer patient are introduced. Praveen et al. [15] introduce a novel OGSO approach based clustering using DNN named OGSO-DNN method for dispersed healthcare system. The OGSO method was employed in this work for selecting the CH from the accessible IoT device. The elected CH transmits the data to cloud server, i.e., later performs DNN based classification procedure for healthcare diagnoses.
Tuli et al. [16] presented a new architecture named HealthFog for incorporating ensemble DL in Edge computing devices and placed for the real world applications of automated Heart Disease analyses. Akhbarifar et al. [17], presented a remote health monitoring method that employs a lightweight block encryption technique for providing security for health and medicinal data in cloud based IoT platforms. In this method, the patient's healthcare status is defined by forecasting crucial situations via data mining approaches for analyzing their biological data sensed with a smart medical IoT device where a lightweight secure block encryption system is utilized for ensuring the patient sensitive data becomes secured.
3 The Proposed IDDM-EAC Technique
Fig. 1 illustrates the overall block diagram of IDDM-EAC model. In this study, a new IDDM-EAC technique is derived for disease diagnosis in IoT enabled cluster-based healthcare system. The IDDM-EAC technique involves a 3-stage process namely data acquisition using IoT devices, CSOEAC based clustering, and COA-DBN technique disease diagnosis. The detailed working of three modules is discussed in the succeeding sections.
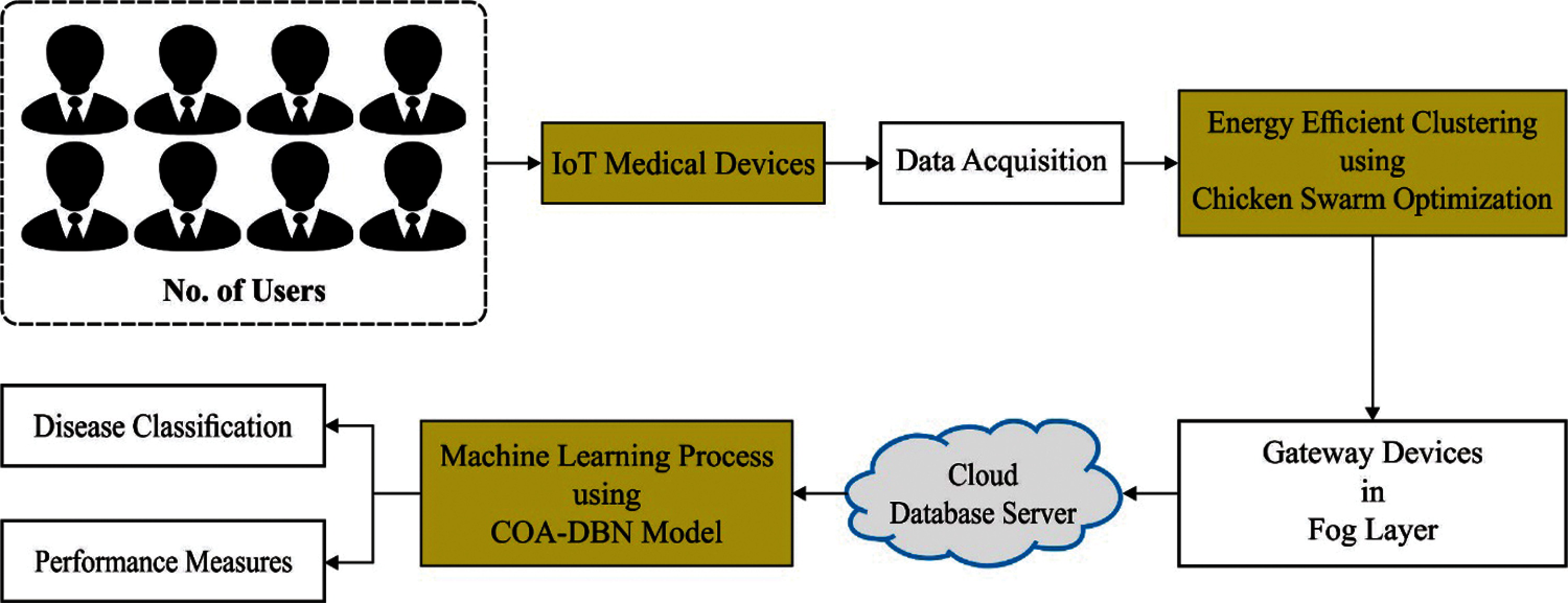
Figure 1: Overall process of IDDM-EAC model
In user, health facts are gathered utilizing data acquisition approach which enables a seamless combination of smart, low-power sensor, and alternate medical gadgets. As sensor node is combined in, and about the human body for resolve of observing the function of person. During this method, the user body sensor network was included with wearable and implanted sensor. The sensor is appropriate in collecting student physiological measure also structured/unstructured design and transmitting to coordinator. Also, time is most important parameter, and gateways are calculated to provide transient synchronization to varied dataset previous to performing broadcast tasks. For maintaining the data security at time of transferring, a channel is secure utilizing Secure Socket Layer (SSL) for offering security as well as privacy.
3.2 Design of CSOEAC Technique
At this stage, the CSOEAC technique is designed to elect an optimal set of CHs and organize clusters in the healthcare system. The conventional CSO algorithm mostly handles the optimization issues as the procedure of chicken exploring to food. The entire CS is separated into various chicken flocks, all of them have chicks, cock, and hens. There is competition among every CS, and the optimal cluster individual is attained via competition. The procedure of CSO algorithm is given below:
(1) In every CS, there are several sub-CSs, all of them involved with single cock, many chicks, and hens.
(2) The CS splits numerous sub-CSs and determines the fitness value of individuals were the chicks, cocks, and hens dependent. Many individuals with an optimal fitness value could act as cock. Every cock is a leader of a CS. The hen arbitrarily follows a cock, and the relationships among the hens and chicks are arbitrarily made.
(3) The mother-child relationship, dominance relationship, and hierarchy in the CS aren't changed; chicken regroups and upgrades each G generation.
(4) Sub-CS looks for food using the cock, the chick looks for food everywhere, the hens, and individuals have a benefit in discovering food. The chicks, cocks, and hens in the CS perform distinct manners of optimizing.
Individuals in the CS move based on their individual rules till they discover an optimal location. Hence, the individual location in the CS corresponds to a solution to the optimization issue, and detecting an optimal solution is the best solution to the optimization issue [18]. In the entire CSO, the number of individuals in each flock is fixed to N, and the location of all CS individuals are denoted as
The location corresponds to the cock is upgraded by:
Whereas Rand
Whereas rand represents an arbitrary amount among zero & one, r1 represents the spouse cock of ith hen,
The position corresponds to the chick is upgraded by:
Whereas m signifies the hen corresponds to the ith chick and F indicates the follow-up coefficient that implies chick followup the hen for finding food. Fig. 2 demonstrates the flowchart of CSO.
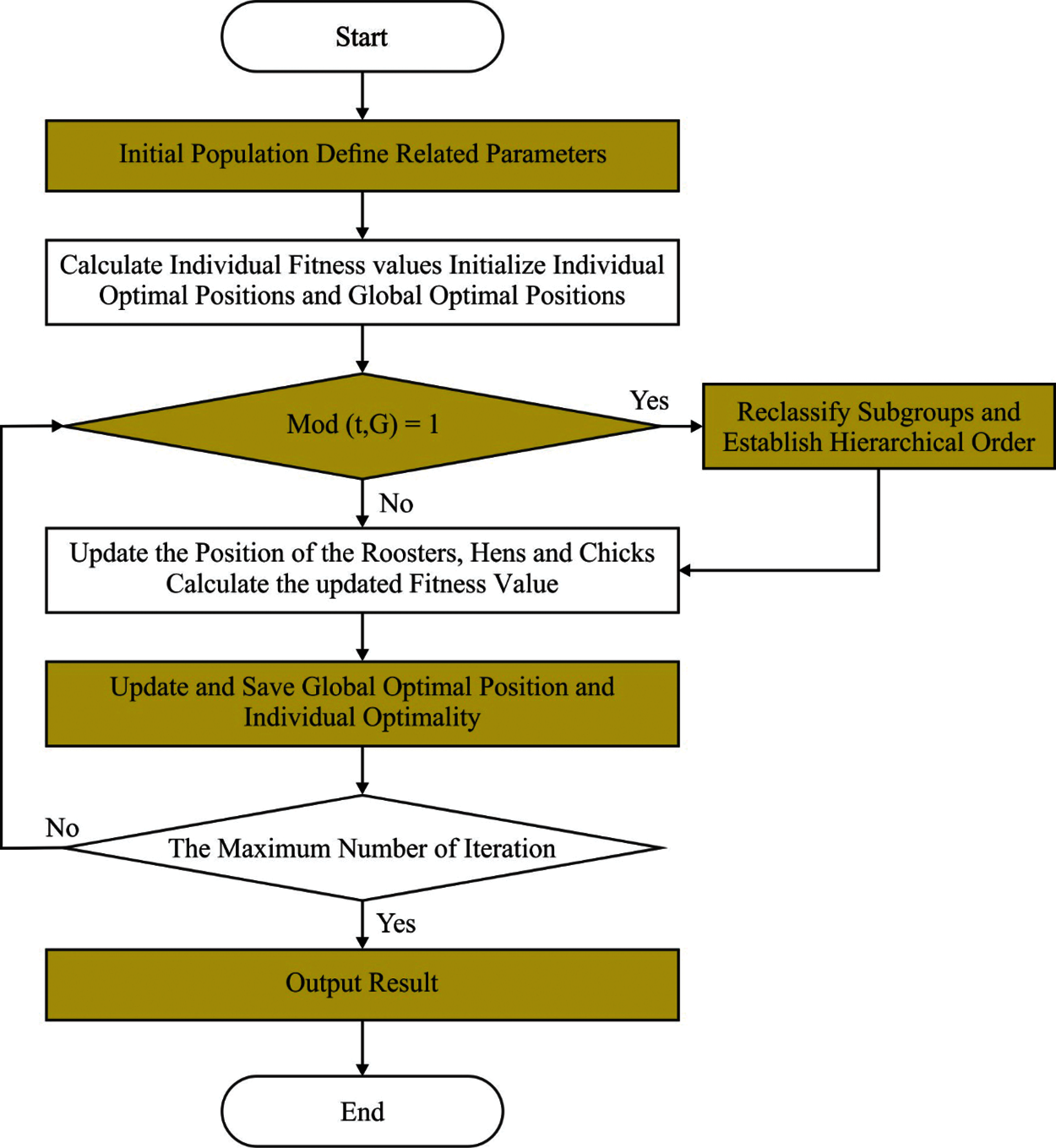
Figure 2: Flowchart of CSO
3.3 Design of COA-DBN Technique
The COA-DBN technique examines the healthcare data available at the cloud server and diagnoses the diseases proficiently. DBN is a probabilistic generative method that has a stacking of several layers of Restricted Boltzmann Machines (RBM) where it involves a layer of hidden visible and unit. The DBN method endures extraction of a deep hierarchical depiction of the input data using greedy layerwise process. When the layer of RBM endured training, the depiction of previously hidden layer is fed as input to the following hidden layer. The framework of DBN is represented in Fig. 3. The DBN method using l hidden layers involves l weight matrix:
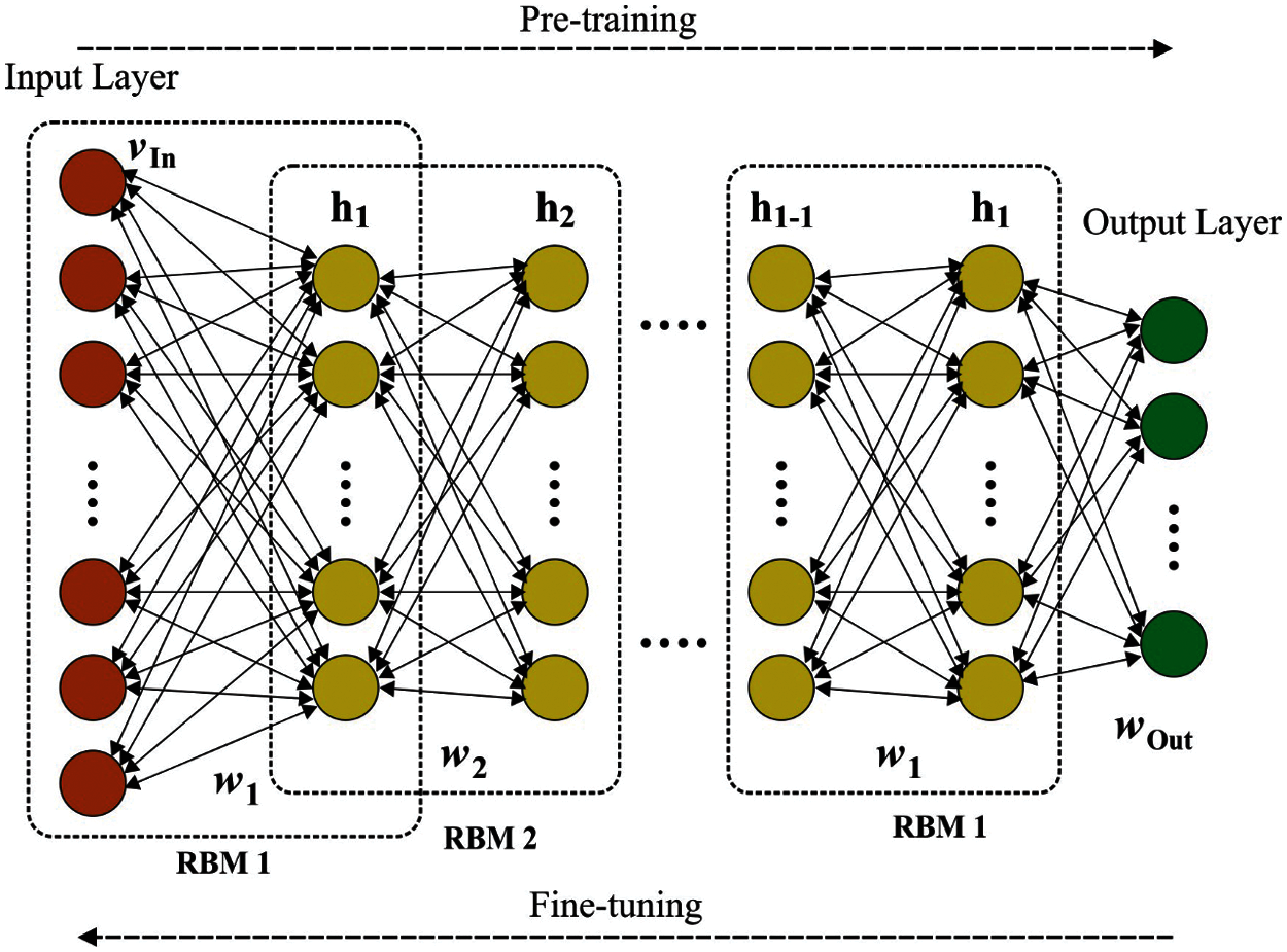
Figure 3: Structure of DBN
A 2-layer DBN arranged by 2 RBMs hold a group of visible units and 2 layers of hidden unit. Where
If the real valued visible units are occurred, employed
The weight from the trained DBN could be tuned optimally by the COA for enhancing the efficacy of the whole network.
COA is an advanced metaheuristic method i.e., depending on the adoptable features of the coyotes as well as they face swapping actions. It has an attractive method of balancing between exploitation and exploration. It starts with
Whereas, c denotes the number and p represents the group and t indicates the simulative time to design parameter. Initially, some arbitrary coyotes are generated as the solution candidate exists in the search field, as follows.
Whereas,
The COA updates the position of groups in an arbitrary manner. Additionally, the candidate could update the position when it is leaving from the group and the leaving procedure created on the basis of likelihood as follows.
Whereas
The common feature of coyotes for the traditional conversion is determined by [20]:
Whereas,
The COA treats the coyote's lifecycle i.e., incorporation of environmental factor as well as social characteristics of parent coyote. The coyotes’ lifecycle could be shown in Eq. (16):
whereas
In which, d represents the parameter dimension. The algorithm of balancing process of coyotes’ lifecycle is provided under.
Calculate i &
if
else if
else
End if Whereas i represents the coyote amount in the group,
Whereas,
Whereas
A main characteristic of this approach is the ability to escape from the local optimal.
This section investigates the performance of the proposed IDDM-EAC technique interms of different measures. Firstly, the disease diagnostic outcome of the IDDM-EAC technique is examined interms of sensitivity, specificity, accuracy, and F-score. The proposed model is executed on a PC Motherboard - MSI Z370 A-Pro, Processor - i5-8600k, Graphics Card - GeForce 1050Ti 4GB, RAM - 16GB, OS Storage - 250GB, and SSD File Storage - 1TB HDD.
A brief sensitivity analysis of the IDDM-EAC technique under varying instance count is demonstrated in Fig. 4. The results depicted that the IDDM-EAC technique has gained maximum sensitivity under all instance count. For instance, with 2000 instances, increased sensitivity of 95.89% is achieved by the IDDM-EAC technique whereas the K-NN, NB, SVM, DT, and EEPSOC-ANN techniques have offered a decreased sensitivity of 92.60%, 87.90%, 83.20%, 93.30%, and 94.78% respectively. Eventually, with 6000 instances, a higher sensitivity of 97.10% is realized by the IDDM-EAC technique whereas the K-NN, NB, SVM, DT, and EEPSOC-ANN techniques have obtained a lower sensitivity of 93.20%, 86.40%, 83.90%, 93.60%, and 95.63% respectively. In addition, with 10000 instances, a raised sensitivity of 98.68% is reached by the IDDM-EAC technique whereas the K-NN, NB, SVM, DT, and EEPSOC-ANN techniques have accomplished a decreased sensitivity of 93.60%, 89.10%, 84.20%, 96.00%, and 97.86% respectively.
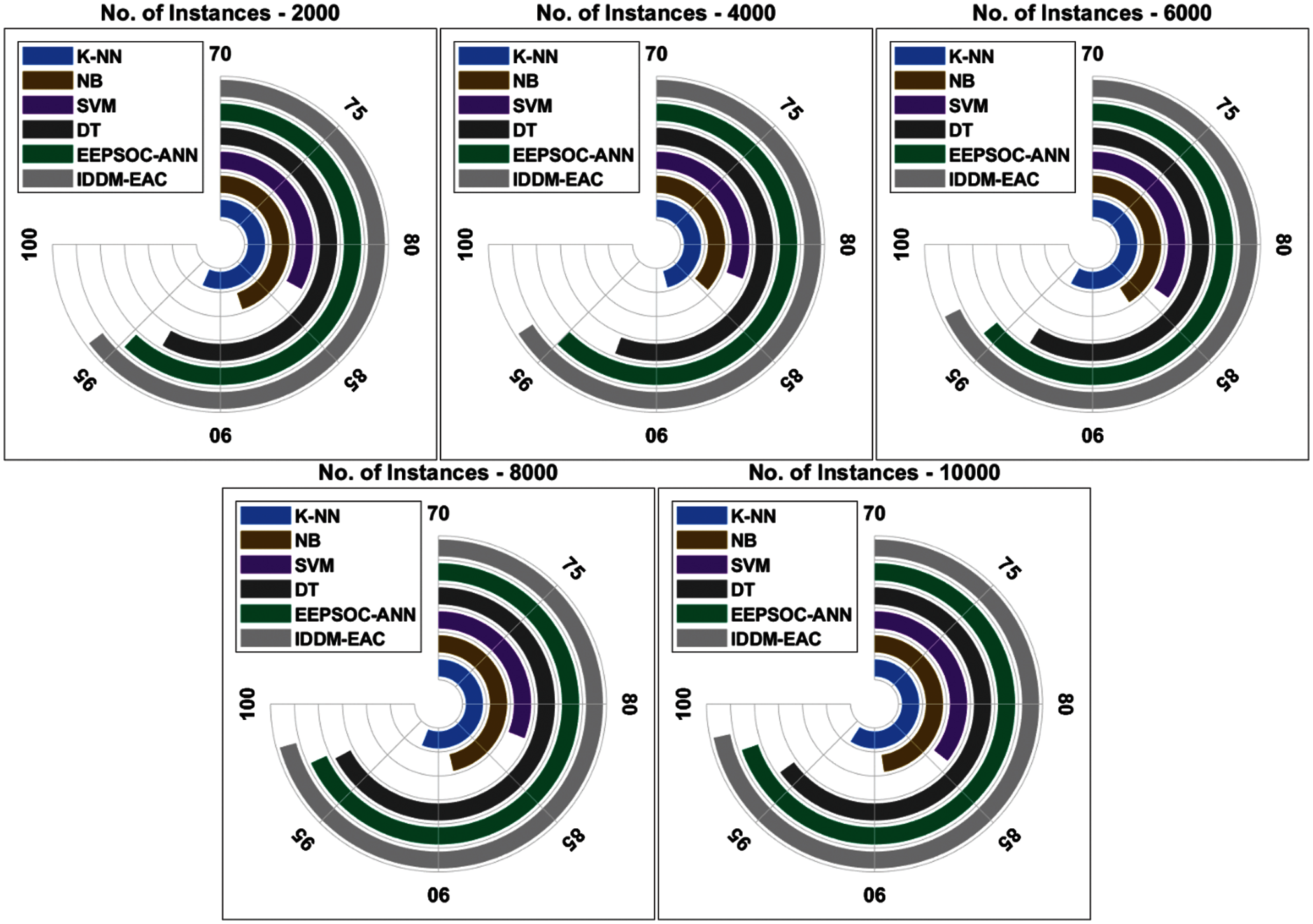
Figure 4: Sensitivity analysis of existing and proposed IDDM-EAC method
Detailed specificity analysis of the IDDM-EAC approach under distinct instance count is depicted in Fig. 5. The outcomes showcased that the IDDM-EAC technique has reached maximal specificity under all instance count. For sample, with 2000 instances, an increased specificity of 95.10% is attained by the IDDM-EAC manner whereas the K-NN, NB, SVM, DT, and EEPSOC-ANN algorithms have offered a decreased specificity of 84.20%, 83.40%, 80.20%, 92.60%, and 94.32% correspondingly. Similarly, with 6000 instances, a higher specificity of 96.08% is understood by the IDDM-EAC technique whereas the K-NN, NB, SVM, DT, and EEPSOC-ANN techniques have obtained a lower specificity of 87.30%, 86.90%, 83.40%, 92.40%, and 94.87% correspondingly. Eventually, with 10000 instances, a superior specificity of 94.21% is reached by the IDDM-EAC technique whereas the K-NN, NB, SVM, DT, and EEPSOC-ANN methods have accomplished a minimal specificity of 89.30%, 86.40%, 84.30%, 90.40%, and 92.38% correspondingly.
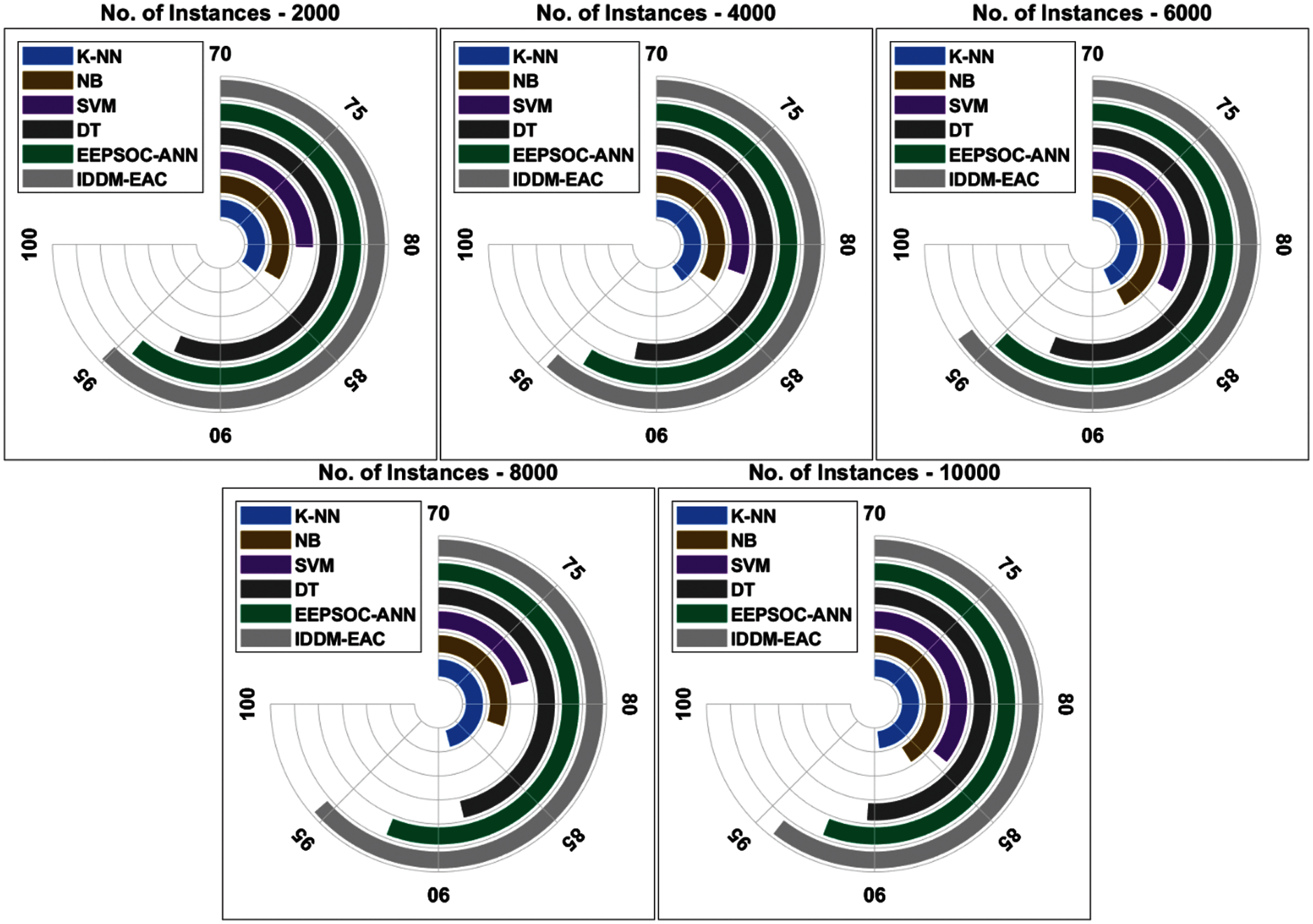
Figure 5: Specificity analysis of existing and proposed IDDM-EAC method
Comparative accuracy analysis of the IDDM-EAC approach under varying instance count is exhibited in Fig. 6. The results portrayed that the IDDM-EAC method has obtained higher accuracy under all instance count. For sample, with 2000 instances, improved accuracy of 94.60% is reached by the IDDM-EAC technique whereas the K-NN, NB, SVM, DT, and EEPSOC-ANN techniques have offered a decreased accuracy of 89.40%, 76.80%, 73.40%, 91.60%, and 93.49% correspondingly. At the same time, with 6000 instances, higher accuracy of 94.55% is realized by the IDDM-EAC technique whereas the K-NN, NB, SVM, DT, and EEPSOC-ANN techniques have obtained the least accuracy of 87.60%, 77.80%, 75.60%, 90.40%, and 93.48% correspondingly. Furthermore, with 10000 instances, a raised accuracy of 96.86% is reached by the IDDM-EAC technique whereas the K-NN, NB, SVM, DT, and EEPSOC-ANN methodologies have accomplished a lesser accuracy of 89.30%, 82.40%, 81.60%, 92.80%, and 94.20% correspondingly.
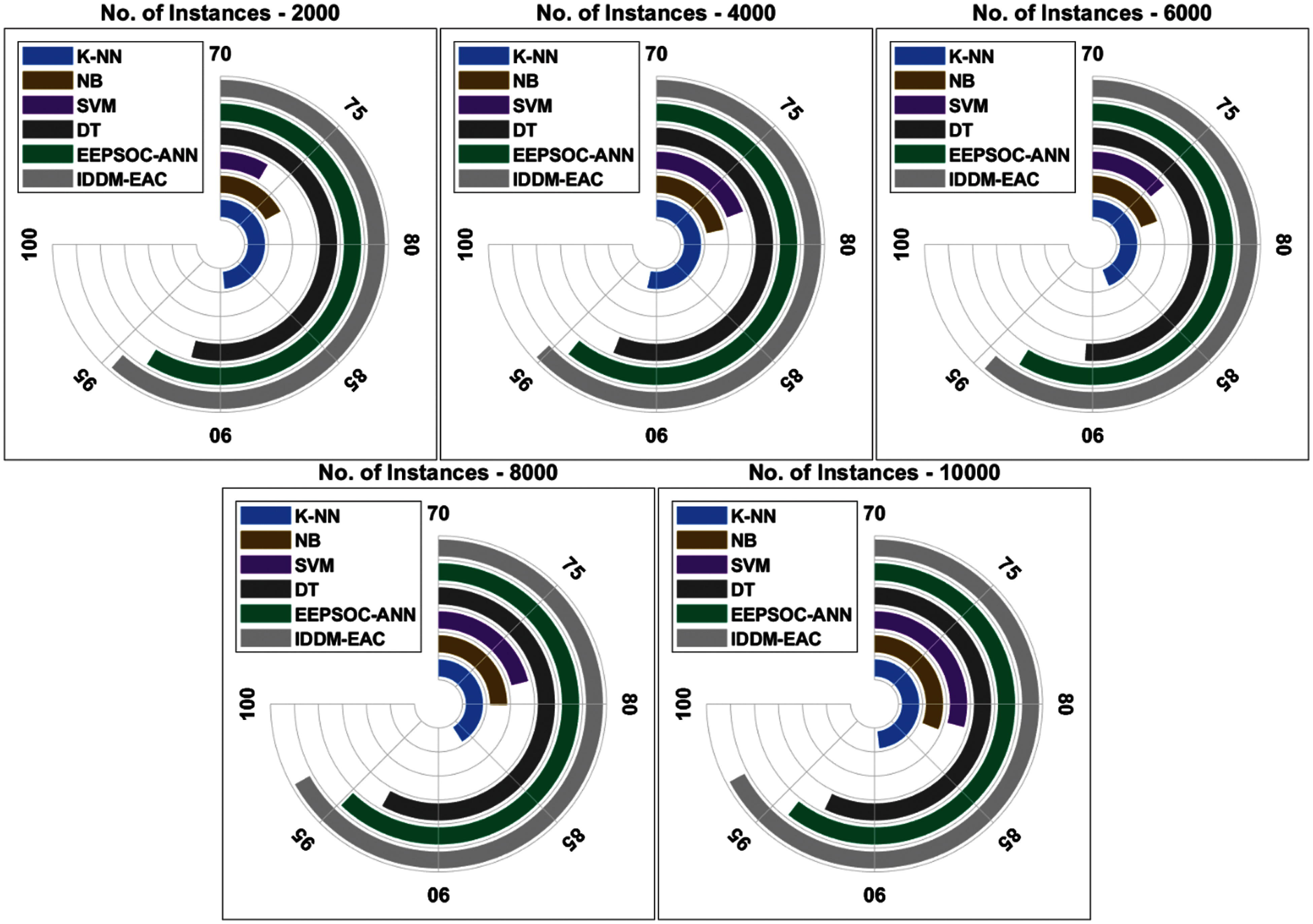
Figure 6: Accuracy analysis of existing and proposed IDDM-EAC method
A detailed F-score analysis of the IDDM-EAC approach under different instance count is outperformed Fig. 7. The results depicted that the IDDM-EAC technique has reached maximal F-score under all instance count. For instance, with 2000 instances, an increased F-score of 98.68% is achieved by the IDDM-EAC technique whereas the K-NN, NB, SVM, DT, and EEPSOC-ANN techniques have offered a decreased F-score of 92.40%, 85.60%, 81.20%, 97.60%, and 98.14% correspondingly. Followed by, with 6000 instances, a higher F-score of 96.56% is realized by the IDDM-EAC technique whereas the K-NN, NB, SVM, DT, and EEPSOC-ANN techniques have obtained a lower F-score of 92.40%, 87.20%, 86.40%, 93.20%, and 94.67% correspondingly. Also, with 10000 instances, a raised F-score of 96.17% is attained by the IDDM-EAC algorithm whereas the K-NN, NB, SVM, DT, and EEPSOC-ANN techniques have accomplished a minimal F-score of 90.90%, 83.70%, 81.90%, 93.30%, and 95.21% correspondingly.
Finally, a total energy consumption analysis of IDDM-EAC technique with recent techniques is Fig. 8 [9]. The results depicted that the IDDM-EAC technique has required minimal total energy consumption under distinct number of IoT sensors. For instance, with 100 IoT sensor nodes, the IDDM-EAC technique consumed lower total energy of 42% whereas the EEPSOC, ABC, GWO, and ACO algorithms have demonstrated a higher total energy consumption of 46%, 58%, 61%, and 67% respectively. Also, with 300 IoT sensor nodes, the IDDM-EAC manner consumed lesser total energy of 54% whereas the EEPSOC, ABC, GWO, and ACO techniques have outperformed an increased total energy consumption of 59%, 67%, 73%, and 77% correspondingly. Finally, with 500 IoT sensor nodes, the IDDM-EAC method consumed lower total energy of 63% whereas the EEPSOC, ABC, GWO, and ACO algorithms have showcased a higher total energy consumption of 69%, 78%, 83%, and 84% correspondingly.
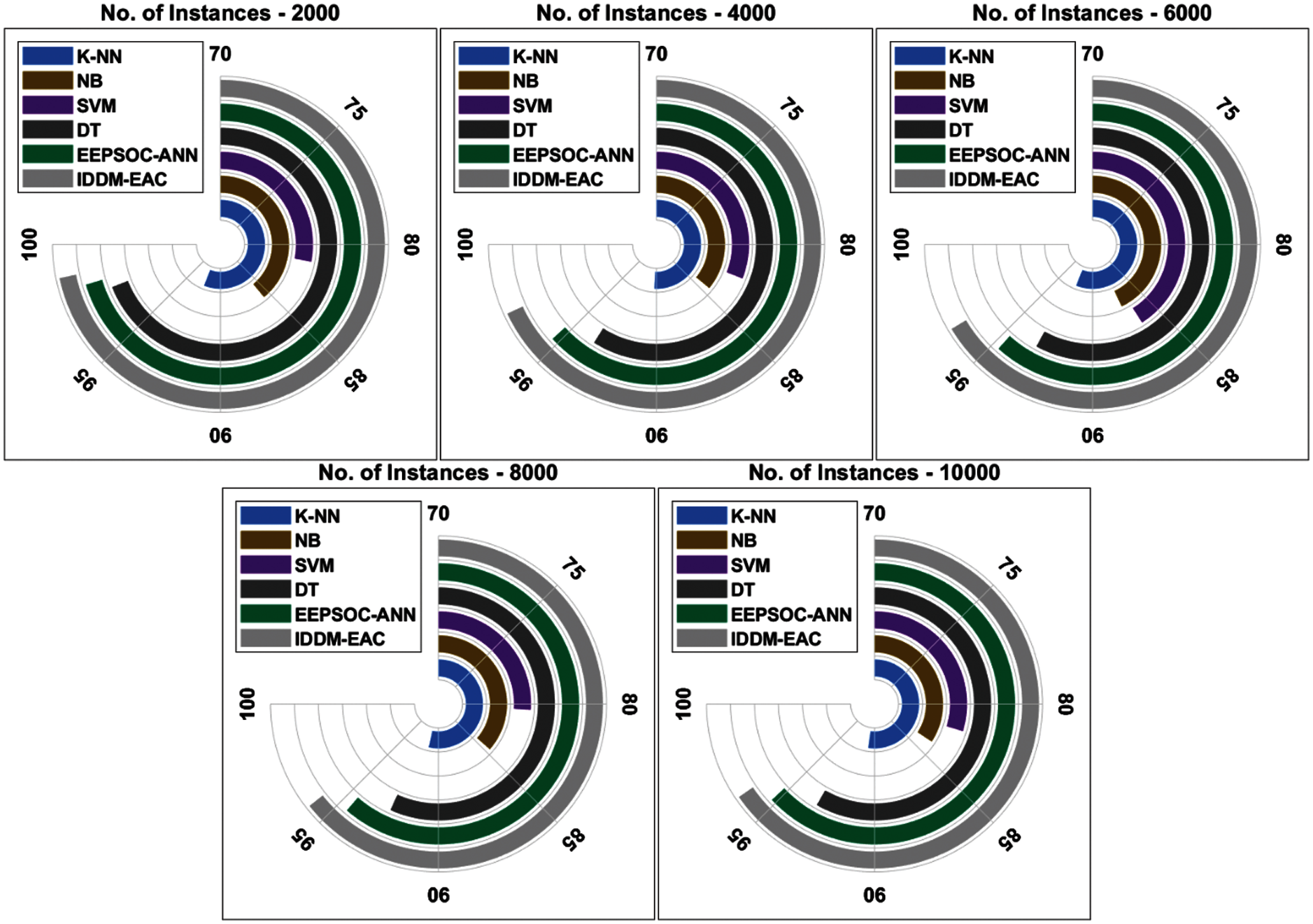
Figure 7: F-score analysis of existing and proposed IDDM-EAC method
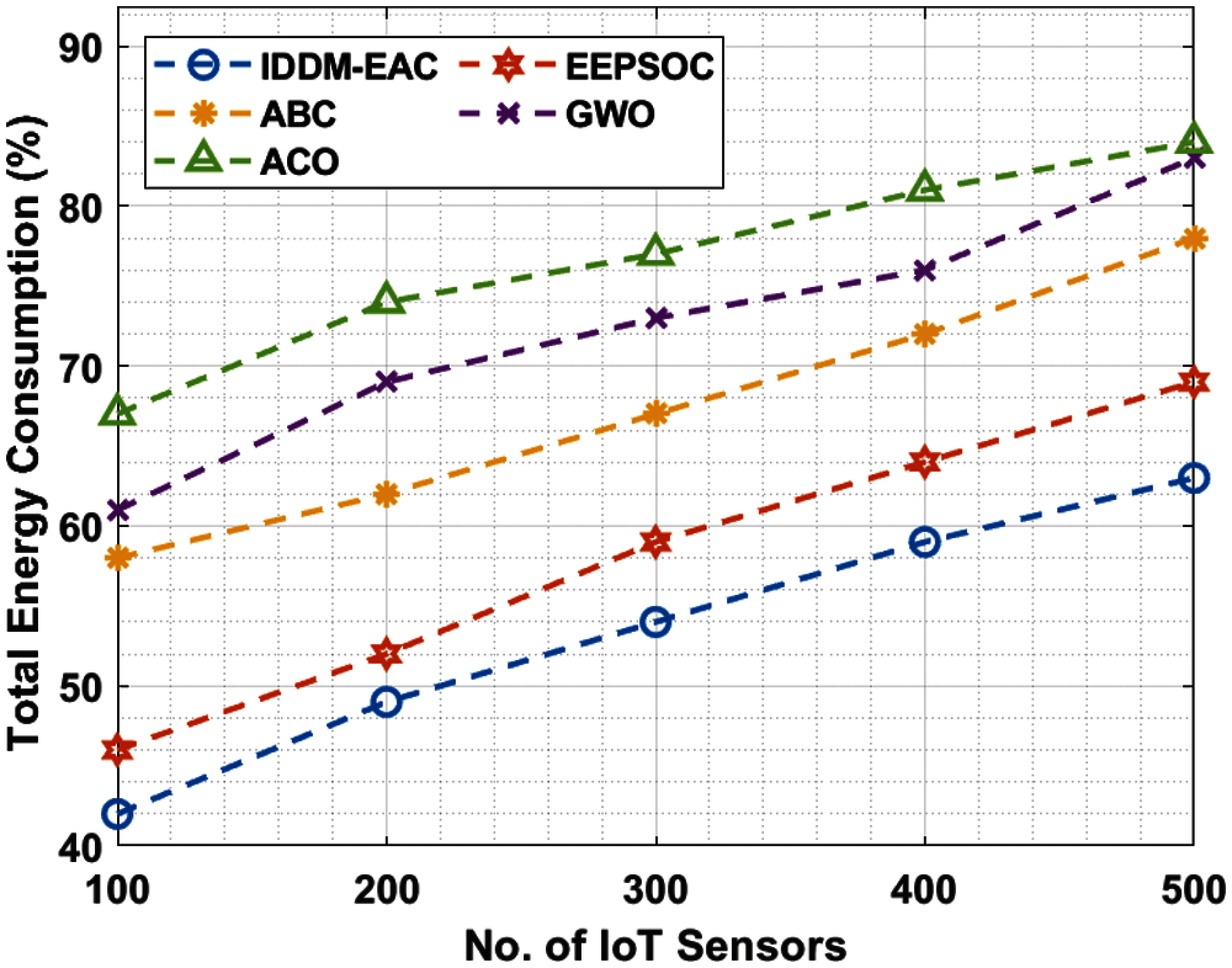
Figure 8: Total energy consumption analysis of IDDM-EAC technique
In this study, a new IDDM-EAC technique is derived for disease diagnosis in IoT enabled cluster based healthcare system. The IDDM-EAC technique involves a 3-stage process namely data acquisition using IoT devices, CSOEAC based clustering, and COA-DBN technique disease diagnosis. The COA-DBN technique examines the healthcare data available at the cloud server and diagnoses the diseases proficiently. In the COA-DBN technique, a hyperparameter optimizer using COA is applied to optimally adjust the parameters involved in the DBN model. To assess the enhanced outcomes of the IDDM-EAC technique, a series of simulations take place using the real time data from IoT devices and benchmark data from UCI repository. The experimental results demonstrate the promising performance of the IDDM-EAC technique with the minimal total energy consumption of 63% whereas the EEPSOC, ABC, GWO, and ACO algorithms have showcased a higher total energy consumption of 69%, 78%, 83%, and 84% correspondingly. In future, energy aware route planning and data aggregation techniques can be designed to boost the overall efficiency of the complete network.
Funding Statement: This research work was funded by Institutional Fund Projects under grant no (IFPHI-050-611-2020). Therefore, authors gratefully acknowledge technical and financial support from the Ministry of Education and King Abdulaziz University, Jeddah, Saudi Arabia.
Conflicts of Interest: The authors declare that they have no conflicts of interest to report regarding the present study.
1. T. Khan, K. Singh, M. H. Hasan, K. Ahmad, G. T. Reddyet al., “ETERS: A comprehensive energy aware trust-based efficient routing scheme for adversarial WSNs,” Future Generation Computer Systems, vol. 125, pp. 921–943, 2021. [Google Scholar]
2. P. N. Srinivasu, A. K. Bhoi, R. H. Jhaveri, G. T. Reddy and M. Bilal, “Probabilistic deep Q network for real-time path planning in censorious robotic procedures using force sensors,” Journal of Real-Time Image Processing, 2021. https://doi.org/10.1007/s11554-021-01122-x. [Google Scholar]
3. D. N. Le, V. S. Parvathy, D. Gupta, A. Khanna, J. J. P. C. Rodrigueset al., “IoT enabled depthwise separable convolution neural network with deep support vector machine for COVID-19 diagnosis and classification,” International Journal of Machine Learning and Cybernetics, 2021. https://doi.org/10.1007/s13042-020-01248-7. [Google Scholar]
4. A. Naeem, A. R. Javed, M. Rizwan, S. Abbas, J. C. W. Linet al., “DARE-SEP: A hybrid approach of distance aware residual energy-efficient sep for wsn,” IEEE Transactions on Green Communications and Networking, vol. 5, no. 2, pp. 611–621, 2021. [Google Scholar]
5. K. K. Patro, S. P. R. Reddi, S. K. E. Khalelulla, P. Rajesh Kumar and K. Shankar, “ECG data optimization for biometric human recognition using statistical distributed machine learning algorithm,” The Journal of Supercomputing, vol. 76, no. 2, pp. 858–875, 2020. [Google Scholar]
6. K. Shankar, “IoT with cloud based end to end secured disease diagnosis model using light weight cryptography and gradient boosting tree,” Recent Advances in Computer Science and Communications, vol. 13, no. 1, pp. 1–8, 2020. [Google Scholar]
7. S. Tyagi, A. Agarwal and P. Maheshwari, “A conceptual framework for IoT-based healthcare system using cloud computing,” in 2016 6th Int. Conf.-Cloud System and Big Data Engineering (ConfluenceNoida, India, pp. 503–507, 2016. [Google Scholar]
8. T. Vaiyapuri, V. S. Parvathy, V. Manikandan, N. Krishnaraj, D. Guptaet al., “A novel hybrid optimization for cluster-based routing protocol in information-centric wireless sensor networks for iot based mobile edge computing,” Wireless Personal Communications, 2021. https://doi.org/10.1007/s11277-021-08088-w. [Google Scholar]
9. R. Bharathi, T. Abirami, S. Dhanasekaran, D. Gupta, A. Khannaet al., “Energy efficient clustering with disease diagnosis model for IoT based sustainable healthcare systems,” Sustainable Computing: Informatics and Systems, vol. 28, pp. 100453, 2020. [Google Scholar]
10. F. A. Mohammadi, M. N. Meqdad and S. Kadry, “Development of an IoT-based and cloud-based disease prediction and diagnosis system for healthcare using machine learning algorithms,” IAES International Journal of Artificial Intelligence (IJ-AI), vol. 9, no. 4, pp. 766, 2020. [Google Scholar]
11. D. T. Phan, Q. B. Ta, T. C. Huynh, T. H. Vo, C. H. Nguyenet al., “A smart LED therapy device with an automatic facial acne vulgaris diagnosis based on deep learning and internet of things application,” Computers in Biology and Medicine, vol. 136, pp. 104610, 2021. [Google Scholar]
12. S. Satpathy, P. Mohan, S. Das and S. Debbarma, “A new healthcare diagnosis system using an IoT-based fuzzy classifier with FPGA,” The Journal of Supercomputing, vol. 76, no. 8, pp. 5849–5861, 2020. [Google Scholar]
13. S. Juyal, S. Sharma and A. S. Shukla, “Smart skin health monitoring using AI-enabled cloud-based IoT,” Materials Today: Proceedings, 2021. https://doi.org/10.1016/j.matpr.2021.01.074. [Google Scholar]
14. S. Sharma, R. K. Dudeja, G. S. Aujla, R. S. Bali and N. Kumar, “DeTrAs: Deep learning-based healthcare framework for IoT-based assistance of Alzheimer patients,” Neural Computing and Applications, 2020. https://doi.org/10.1007/s00521-020-05327-2. [Google Scholar]
15. K. V. Praveen, P. M. J. Prathap, S. Dhanasekaran, I. S. H. Punithavathi, P. Duraipandyet al., “Deep learning based intelligent and sustainable smart healthcare application in cloud-centric iot,” Computers, Materials & Continua, vol. 66, no. 2, pp. 1987–2003, 2021. [Google Scholar]
16. S. Tuli, N. Basumatary, S. S. Gill, M. Kahani, R. C. Aryaet al., “Healthfog: An ensemble deep learning based smart healthcare system for automatic diagnosis of heart diseases in integrated IoT and fog computing environments,” Future Generation Computer Systems, vol. 104, pp. 187–200, 2020. [Google Scholar]
17. S. Akhbarifar, H. H. S. Javadi, A. M. Rahmani and M. Hosseinzadeh, “A secure remote health monitoring model for early disease diagnosis in cloud-based IoT environment,” Personal and Ubiquitous Computing, 2020. https://doi.org/10.1007/s00779-020-01475-3. [Google Scholar]
18. Y. Li, S. Wang and M. Han, “Truss structure optimization based on improved chicken swarm optimization algorithm,” Advances in Civil Engineering, vol. 2019, pp. 1–16, 2019. [Google Scholar]
19. J. Li, X. Shao and R. Sun, “A dbn-based deep neural network model with multitask learning for online air quality prediction,” Journal of Control Science and Engineering, vol. 2019, pp. 1–9, 2019. [Google Scholar]
20. Z. Yuan, W. Wang, H. Wang and A. Yildizbasi, “Developed coyote optimization algorithm and its application to optimal parameters estimation of pemfc model,” Energy Reports, vol. 6, pp. 1106–1117, 2020. [Google Scholar]
 | This work is licensed under a Creative Commons Attribution 4.0 International License, which permits unrestricted use, distribution, and reproduction in any medium, provided the original work is properly cited. |