DOI:10.32604/cmc.2022.021338

| Computers, Materials & Continua DOI:10.32604/cmc.2022.021338 |  |
| Article |
Metaheuristic Resource Allocation Strategy for Cluster Based 6G Industrial Applications
1Department of Computer and Self Development, Preparatory Year Deanship, Prince Sattam bin Abdulaziz University, AlKharj, Saudi Arabia
2Department of Electrical Engineering, College of Engineering, Princess Nourah bint Abdulrahman University, Saudi Arabia
3Department of Computer Science, King Khalid University, Muhayel Aseer, Saudi Arabia
4Department of Natural and Applied Sciences, College of Community-Aflaj, Prince Sattam bin Abdulaziz University, Saudi Arabia
*Corresponding Author: Anwer Mustafa Hilal. Email: a.hilal@psau.edu.sa
Received: 30 June 2021; Accepted: 12 August 2021
Abstract: The emergence of Beyond 5G (B5G) and 6G networks translated personal and industrial operations highly effective, reliable, and gainful by speeding up the growth of next generation Internet of Things (IoT). Industrial equipment in 6G encompasses a huge number of wireless sensors, responsible for collecting massive quantities of data. At the same time, 6G network can take real-world intelligent decisions and implement automated equipment operations. But the inclusion of different technologies into the system increased its energy consumption for which appropriate measures need to be taken. This has become mandatory for optimal resource allocation in 6G-enabled industrial applications. In this scenario, the current research paper introduces a new metaheuristic resource allocation strategy for cluster-based 6G industrial applications, named MRAS-CBIA technique. MRAS-CBIA technique aims at accomplishing energy efficiency and optimal resource allocation in 6G-enabled industrial applications. The proposed MRAS-CBIR technique involves three major processes. Firstly, Weighted Clustering Technique (WCT) is employed to elect the optimal Cluster Heads (CHs) or coordinating agents with the help of three parameters namely, residual energy, distance, and node degree. Secondly, Decision Tree-based Location Prediction (DTLP) mechanism is applied to determine the exact location of Management Agent (MA). Finally, Fuzzy C-means with Tunicate Swarm Algorithm (FCM-TSA) is used for optimal resource allocation in 6G industrial applications. The performance of the proposed MRAS-CBIA technique was validated and the results were examined under different dimensions. The resultant experimental values highlighted the superior performance of MRAS-CBIR technique over existing state-of-the-art methods.
Keywords: 6G; industrial internet of things; energy efficiency; resource allocation; metaheuristics
With a strong motivation coming from highly-demanding upcoming IoT-enabled applications and constraints faced in fifth generation (5G) networks, sixth generation (6G) networks have evolved based on 5G in all aspects to revolutionize human life and society. At first, network efficiency of 6G is set to upgrade to new high levels, for instance, high data rate (upto Tbps), low latency (sub-ms), 3D ubiquitous coverage (in sea, undersea, and space), high precision localization (up to cm-level), extreme level security, privacy, etc. Next, 6G application areas are set to be highly complex and multi-faceted in nature, resulting in conflicting needs [1].
Consequently, 6G possesses the capability to connect millions of applications and devices seamlessly with a guarantee for performance. Therefore, 6G plays a significant role in enabling huge connectivity for IoT devices of completely different service needs. In order to enable huge IoT, 6G is set to follow a novel network framework with advanced technologies that can meet the future requirements. Fig. 1 shows the applications of 6G networks. From technological framework perceptions, some industrial 6G primarily consists of application layer, perception layer, network layer, and platform layer. Amongst them, perception layer gathers huge volumes of data through a number of sensor nodes. Data mining is a concept which practices the collection of huge volumes of data [2,3]. The network layer is primarily accounted for forwarding and transmission of data, whereas the application and platform layers exist in data centre. In spite of holding huge volumes of data, conventional data centre is highly ineffective in data processing. It has several wireless communication techniques. It cannot meet the transmission needs with the help of one kind of network communication technique during distinct situations. The sensor nodes in the network should execute cooperative transmission if it needs to achieve low delay, less network transmission cost and high efficiency [4]. But, due to network bandwidth constraints, when the requirement for low latency and collaborative work increases, the CC scheme could not meet the needs of users within the given response time. Now, the development of edge computing module certainly carries a solution to this efficacy problem. But there is certainly a low level of gradual reduction observed in the energy consumption of sensor nodes. Further, the edge computing module still faces the QoS needs of the scheme. In this scenario, it becomes inevitable to find a solution for the execution of moderate resource allocation to reduce node energy utilization and attain an effective collaboration among nodes [5].
In order to achieve the aforementioned requirement and increase the overall capacity of system, two distinct methods can be followed based on Shannon’s data concept i.e., improve the spectral performance or increase system bandwidth [6]. Though there exists few challenges, it is familiar that spectrum management is significant for effective spectrum consumption. Particularly, it is well-known that the main problem in mobile networks are fixed models for resource management and spectrum assignment. This becomes highly complex in 6G, owing to increasing number of subscribers and their demand for high number of data-hungry applications and intermittent connectivity [7]. In this scenario, several researches have displayed that though fixed spectrum allocation is not a difficult task, spectrum performance becomes low because the license owners of the specific spectrum do not use it continuously. Many methods have been projected to improve spectrum management, for instance, auction mechanisms/Opportunistic Spectrum Access (OSA). In spite of the benefits of this approach, there exists few challenges based on convergence, security, and high computing power. Mainly, when this protocol provides few collaborations at system level, the collaboration among the users is not deliberated since it hinders the efficiency of entire solution. Compared to the previous generation, 6G is anticipated to be highly supportive with novel techniques such as mobile edge computing, wireless power transfer, Device-to-Device (D2D) communications and IoE highly based on the cooperation among devices. In such case, there is no need of new methods based on resource management and central authority controlling spectrums like blockchain [8,9].
Figure 1: Applications of 6G networks
Liu et al. [10] proposed NOMA-based hybrid spectrum access system for 6G-enabled cognitive IoT (CIoT) in which CIoT might access the busy and idle spectrum through NOMA irrespective of PU states. Mukherjee et al. [11] tackled the energy utilization problem of a huge IoT system using dynamic network clustering/architecture with MAS for industrial 6G applications. Shukla et al. [12] proposed Block RAS, a blockchain-based RAS to manage the demand & supply of resources among RPC and users through a trusted and secured platform. Block RAS offers an optimum bandwidth transmission which is highly reliable and low latent among RPC and users with embedded 6G network structure. Sodhro et al. [13] emphasized on how energy-effective communication occurs and a user’s QoE level could be taken by UT device at the time of multimedia transmission. At last, a relation module is presented to integrate QoS parameters after evaluating the QoE perceptions. Deebak et al. [14] presented Dynamic Driven Congestion Control and Segment Re-routing (DD-CCSR) process with two basic objectives such as mitigation of signal congestion and flow rate and enhancement of path adjustment and monitoring procedure. Segment rerouting method, Deleroi Superimposed, and forward backward interface were configured and implemented in IMSCore framework to analyze the quality metrics like transmission delay and throughput rate.
Liu et al. [15], a new MD-IMA system was proposed to exploit disparate resource limitations between heterogeneous equipment for 5G & 6G networks. Using real-world QoS requirements, the resource availability and real-world data analyses of the interrelated equipment were established in the projected MD-IMA system. Based on this, MA system is smartly adopted for all the equipment in multidimensional resource areas so as to maximize the entire system requirements which had functional limitations. Hu et al. [16] proposed a blockchain and AI-empowered DRS framework. In this framework, the blockchain was utilized for achieving the functionalities in DRS with security and automation and enhanced distribution. Further, AI was executed to improve the efficiency of decision making and pattern recognition in DRS.
The current research paper introduces a new Metaheuristic Resource Allocation Strategy for Cluster-Based 6G Industrial Applications abbreviated as MRAS-CBIA technique. The proposed MRAS-CBIA technique aims at accomplishing energy efficiency and resource allocation in 6G industrial applications. The proposed MRAS-CBIR technique involves three major processes. Firstly, Weighted Clustering Technique (WCT) is employed to elect the optimal Cluster Heads (CHs) or coordinating agents using three parameters namely, residual energy, distance, and node degree. Secondly, Decision Tree-based Location Prediction (DTLP) mechanism is applied to determine the exact location of Management Agent (MA). Finally, Fuzzy C-Means with Tunicate Swarm Algorithm (FCM-TSA) is used for optimal resource allocation in 6G industrial applications. The performance of the proposed MRAS-CBIA technique was validated and the results were examined under different dimensions.
The authors proposed MRAS-CBIA-based 6G scheme in which a huge amount of sensor nodes is arbitrarily placed. In order to manage and decrease the continual process of redundant/related data, the authors introduced the idea of clustering. This method separates the sensor nodes into distinct clusters, i.e., separates the whole network into a number of autonomous and independent small networks. The task, assumed by the sensor nodes in every cluster, is distinct. A task’s Cluster Member node (CM) is the so-called Task Agent (TA). CH selection and clustering processes consume more amount energy. So, the goal is to decrease the energy utilization as much as possible while enhance the performance of the system. A dynamic MA is determined in the proposed MRAS-CBIA scheme to manage the entire node resources. It is important to attain a precise position data of MA for smart resource allocation. Hence, the study forecasted the position data of MA. Based on the memory and energy utilization of whole 6G system, moderate resource allocation is performed for every cluster. When a CH is assigned to the resource, it announces the CM in the cluster and request is to send the collected observation to themselves. In order to decrease the effect of redundant data, WCT is used for CH selection as it results in reduced energy utilization. Then, the CM meets the needs and dynamic alliance is created to complete the tasks of whole system. It defines the execution of complete resource allocation in succeeding sections.
The overall working principle, involved in the presented MRAS-CBIA technique, is shown in Fig. 2. Primarily, the network nodes are randomly placed in preferable industrial applications. Then, WCT is used to select the CHs (coordinate nodes) while rest of the nodes are termed as CMs (task nodes). Followed by, DTLP technique is used to estimate the location of nodes in the network. Lastly, FCM-TSA technique is utilized in proficient allocation of resources in 6G industrial application environment. The detailed working process of every module is discussed in the upcoming subsections.
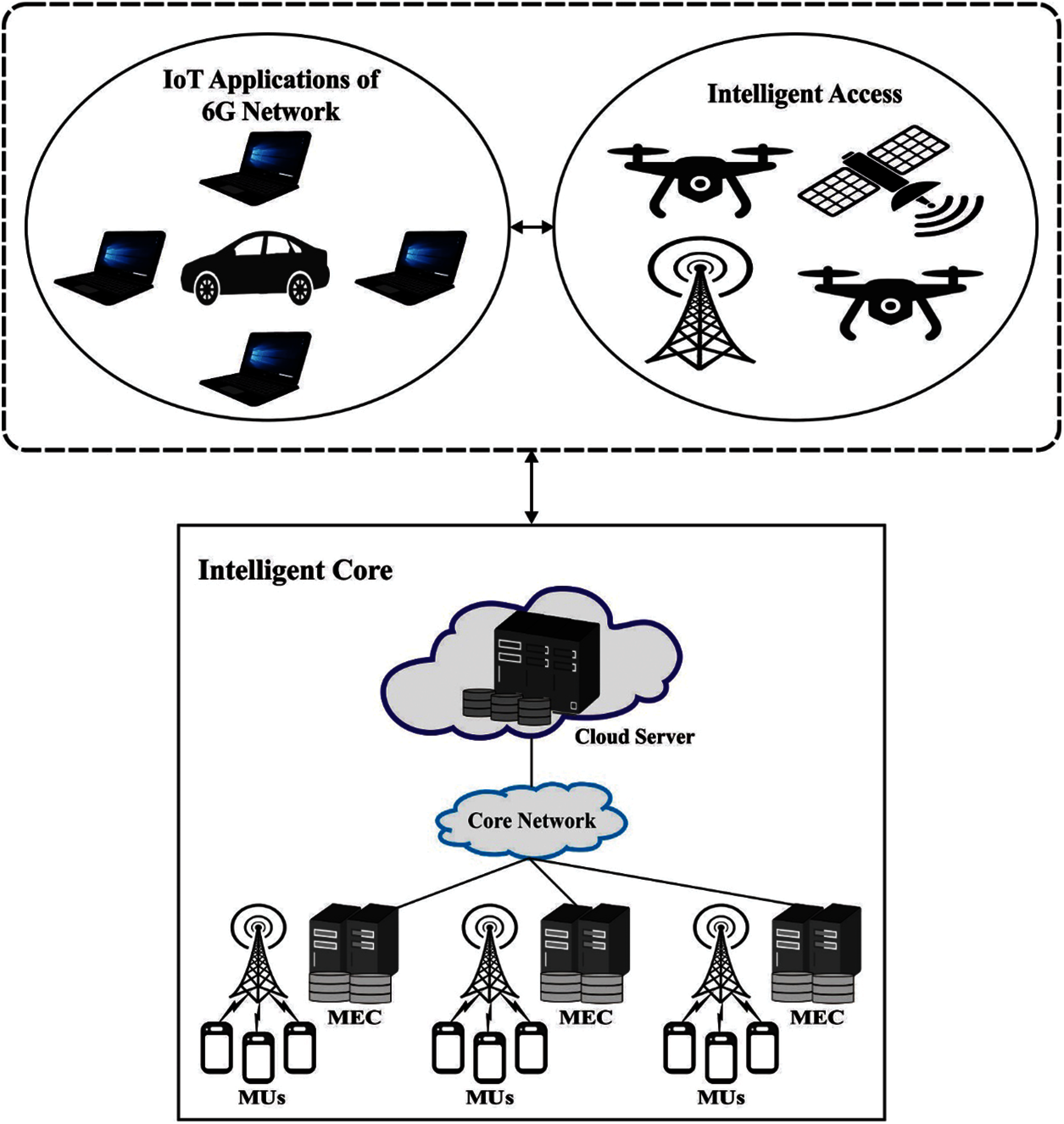
Figure 2: Proposed architecture for 6G networks
3.1 Weighted Clustering Technique
WCT is employed in determining the CHs and it creates clusters based on three variables such as node degree, residual energy, and distance.
When a message is transmitted through
Where E: denotes the current energy of the node;
It is possible to have constraint node distance to enhance cluster consistency [17]. For each node
It displays the amount of
Whereas
whereas
3.2 Location Prediction Mechanism
A DT-based technique is adapted in the prediction of subsequent semantic place based on the extracted spatiotemporal features. Stay points, denoted through precise position of latitude and longitude, are nearly useless in describing the position. Hence, it is critical to annotate the stay points with location type which become semantic places when taking end as the prediction object. For endowing the stay points with individual data, a semantic place recognition process is proposed by POI dictionary and “check in” points. Consecutive semantic trajectories of all the individuals are created after the execution of semantic place recognition procedure. Based on the past motion paths, one can detect the behavioral patterns and individual activity routines with the help of DT technique, a common ML approach [18]. Generally, it takes two stages to build a DT such as pruning and developing decision tree. In this study, ID3 DT method was adapted as a key tool in the implementation of DT. This technique generates a multiway tree containing leaf node, root node, child node, and branches. The categorical feature present in every node should be found since it produce huge data for categorical targets. Data gain and entropy equations are given below.
Whereas
3.3 Resource Allocation Strategy
Tunicates are able to determine the position of food source in sea. But it cannot view the source of food in the provided searching area. TSA adapts two characteristics of tunicates in food source identification process namely jet propulsion and Swarm Intelligence (SI). In the mathematical modeling of jet propulsion nature, tunicates need to fulfill three criteria such as avoiding the conflict amongst Search Agents (SAs), motion in the course of place for the optimal SA, and staying closer to the optimal SA. Then, the swarming nature updates the position of SAs based on the optimum solution. In order to avoid the conflicts amongst SAs, vector
where
where
where
where
The processes involved in TSA are listed herewith. Fig. 3 illustrates the flowchart of TSA technique.
Step-1: Initialization of tunicate population,
Step-2: Select the initial parameters and maximum iteration count
Step-3: Determine the fitness value of all SAs
Step-4: Once the fitness values are computed, the optimal SA is identified in the provided searching area
Step-5: Upgrade the location of all SAs
Step-6: Modify the upgraded SA that exceeds the limit in the provided searching area
Step-7: Determine the fitness value of the upgraded SA. When improved solutions are obtained compared to earlier ones, then upgrade
Step-8: When the termination condition is fulfilled, then TSA is terminated. Or else, go to step 5
Step-9: Display the optimum solutions attained
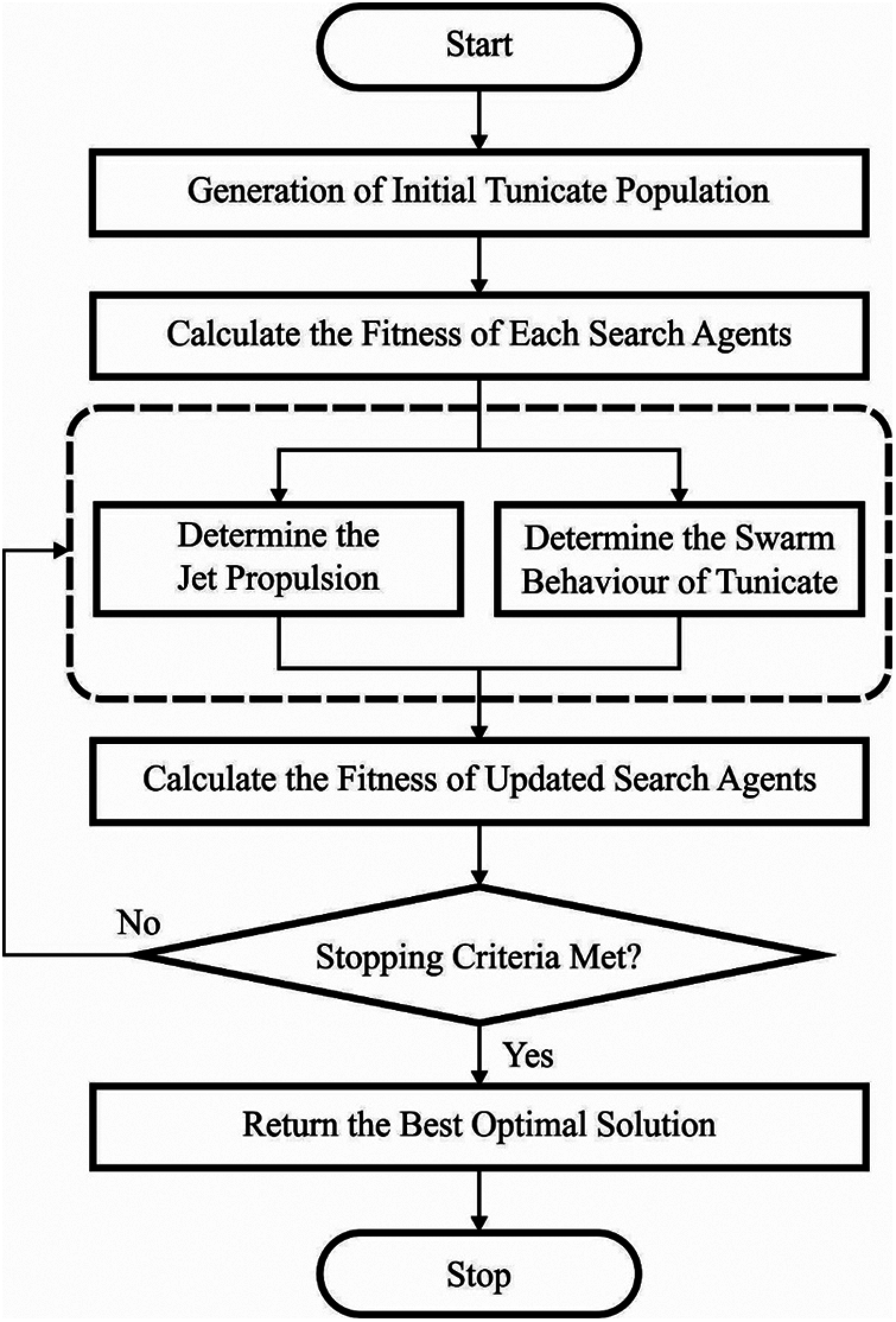
Figure 3: Flowchart of TSA
Generally, FCM is employed in grouping the instances, in which the FCM application depends upon the guarantee of participation incentive/opening bunch in order to focus the review features. It provides a method to assemble the ‘data focusses’ that populate few multidimensional spaces for a certain amount of distinct clusters. A fundamental perspective of fuzzy c represents that the clustering process provides approval to the repeated enrollment of data focuses on clusters, which are defined as degrees. The key objective of FCM and the determination of iterative bunching are to limit the weight inside clustering fully with a squared blunder target capability given below.
Whereas
Based on traditional FCM clustering and TSA model, FCM-TSA technique is introduced to supply the resource in 6G industrial IoT platforms. The fundamental aim is to employ TSA module in FCM method. Consider the cluster sample set as
Thus,
This technique is called local optimization method since an optimum solution is provided with the help of hill climbing. The primary goal is to enhance the affinity between objects that are separated as same cluster and to reduce the comparison among different clusters. TSA method is a heuristic method with advantages of global optimization and fast convergence. Hence, it is combined with FCM technique to resolve the disadvantages and advantages of FCM method and is named after FCM-TSA module. In FCM-TSA method, the main aim of FCM tactic is to calculate the cluster center, and
In the event of 6G industrial IoT applications, the resource attribute contains bandwidth, computation, and storage. Different operations are included by various resources. However, only a few kinds of computation resources and computational tasks are highly efficient, while few bandwidth tasks and bandwidth resources are deliberated as important ones. Thus, to meet the requirements of distinct users, the resources are gathered into sets. Due to the heterogeneity and dynamicity of 6G industrial IoT resources, it is highly challenging to define the unique resources. So, it is employed with FCM-TSA module to cluster the resources based on multidimensional attributes. A group of 6G industrial IoT resources
Whereas maximal value of the resource in
whereas,
Based on TSA, the fuzzy clustering method is presented to cluster the calculated resource matrix data. The procedure included in TSA is discussed herewith. The initiation of population occurs when each individual contains a randomly-created cluster center that divides the resources under three categories, while the cooperative number of cluster centers are stated to be three. Next, the membership matrix
Then, global and local pollution are continuously updated. When it undergoes a large amount of iterations, then it can be ended to acquire a group of cluster centers. Next, the obtained simulation result is deliberated as a primary value for FCM module and is executed to achieve the global optimum solution. At last, when the clustering function gets completed, 6G industrial IoT resources are divided into three elements such as bandwidth, computing, and storage resources. When 6G industrial IoT resources are separated, then the resource scale of a provisioning procedure gets constrained. So, the user requirements must be categorized under different kinds. Appropriate resource classification is required in which the needs of users should be mapped with resources.
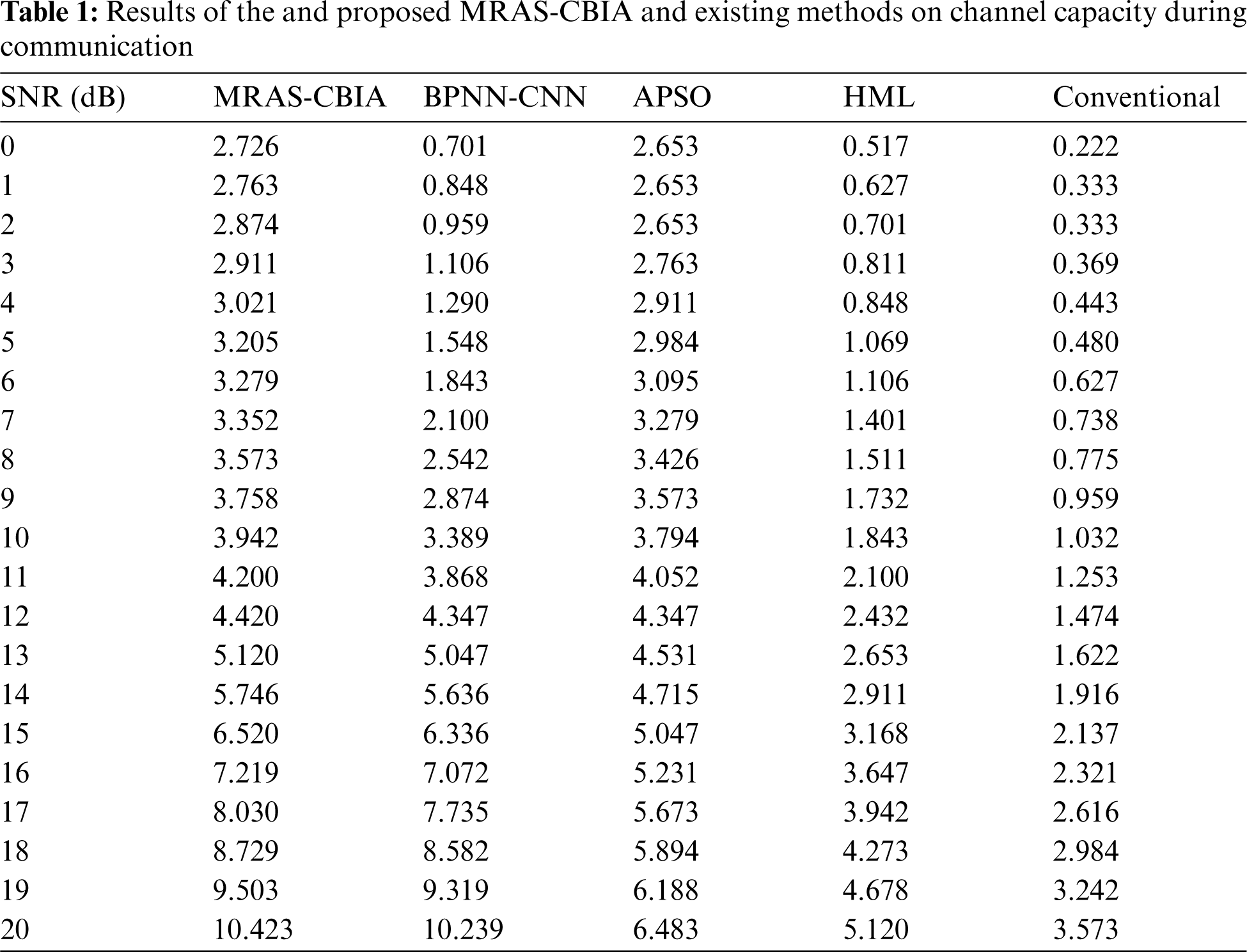
The current section validates the performance of the proposed MRAS-CBIR technique under different measures. Tab. 1 shows the results from channel capacity analysis of MRAS-CBIR technique against other techniques under varying Signal-to-Noise ratios (SNR). The experimental results highlight that the proposed MRAS-CBIR technique obtained an increased channel capacity with a rise in SNR level and is superior to all other techniques. For instance, with an SNR of 5 dB, MRAS-CBIR technique obtained a high channel capacity of 3.205 whereas BPNN-CNN, APSO, HML, and conventional models attained the least channel capacity values such as 1.548, 2.984, 1.069, and 0.480 respectively. Similarly, with an SNR of 10 dB, the proposed MRAS-CBIR technique accomplished an increased channel capacity of 3.942, whereas BPNN-CNN, APSO, HML, and conventional models accomplished the least channel capacity values such as 3.389, 3.794, 1.843, and 1.032 respectively. Likewise, with an SNR of 15 dB, MRAS-CBIR technique achieved an improved channel capacity of 6.520, whereas BPNN-CNN, APSO, HML, and conventional models demonstrated reduced channel capacity values such as 6.336, 5.047, 3.168, and 2.137 respectively. Eventually, with an SNR of 20 dB, MRAS-CBIR technique obtained an enhanced channel capacity of 10.423, whereas other models such as BPNN-CNN, APSO, HML, and conventional models attained the minimal channel capacity values such as 10.239, 6.483, 5.120, and 3.573 respectively.
A comparative analysis of the proposed MRAS-CBIA technique against existing techniques was conducted in terms of Depletion Rate of Residual Energy (DRRE) and the results are shown in Tab. 2. For enhanced network performance, DRRE value should be high and tend to decrease with a rise in time response. The experimental values highlight that the proposed MRAS-CBIA technique accomplished an effectual outcome with a minimal DDRE value under distinct time responses. For instance, at a time response of 0.05 ms, MRAS-CBIA technique gained a DDRE of 16.331, whereas BPNN-CNN, LEACH-VD, and conventional techniques exhibited high DDRE values such as 23.207, 53.004, and 65.896 respectively. Meanwhile, at a time response of 0.20 ms, MRAS-CBIA technique accomplished a DDRE of 11.174, whereas BPNN-CNN, LEACH-VD, and conventional techniques demonstrated increased DDRE values such as 15.471, 37.532, and 89.104 respectively. Concurrently, at a time response of 0.30ms, MRAS-CBIA technique produced a DDRE of 9.168, whereas BPNN-CNN, LEACH-VD, and conventional techniques depicted the maximum increase in the DDRE value such as 14.039, 33.521, and 59.593 respectively. Lastly, at a time response of 0.50ms, the proposed MRAS-CBIA technique attained a DDRE of 6.303, whereas BPNN-CNN, LEACH-VD, and conventional techniques accomplished increased DDRE values such as 10.314, 27.505, and 51.571 respectively.
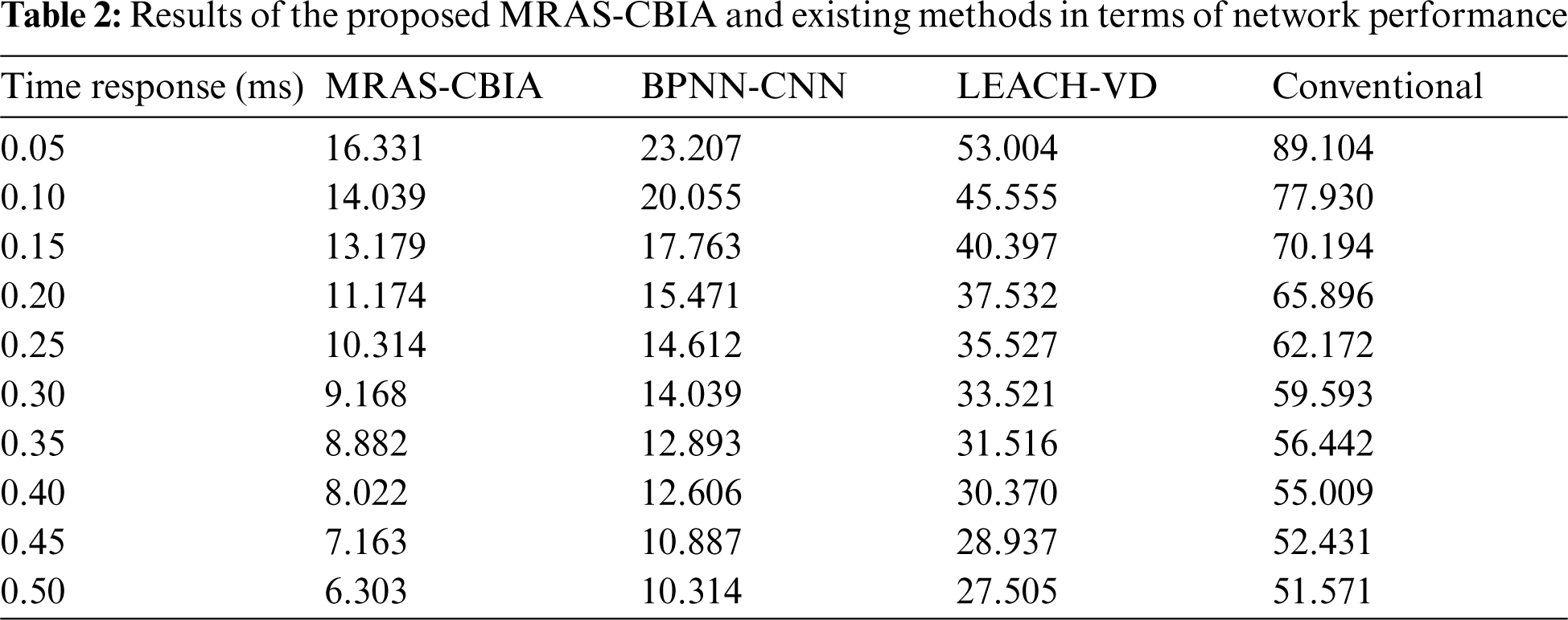
Fig. 4 shows the results achieved in the performance of MRAS-CBIA technique in terms of resource allocation under numerous rounds of simulation. From the figure, it is evident that the NN model is the least performer with low resource allocation outcome. Followed by, APSO-DNN model showcased a slightly increased performance over NN model. In line with this, BPNN-CNN model tried to portray a moderately considerable resource allocation performance. However, the proposed MRAS-CBIA technique accomplished superior performance over other techniques with maximum resource allocation performance.
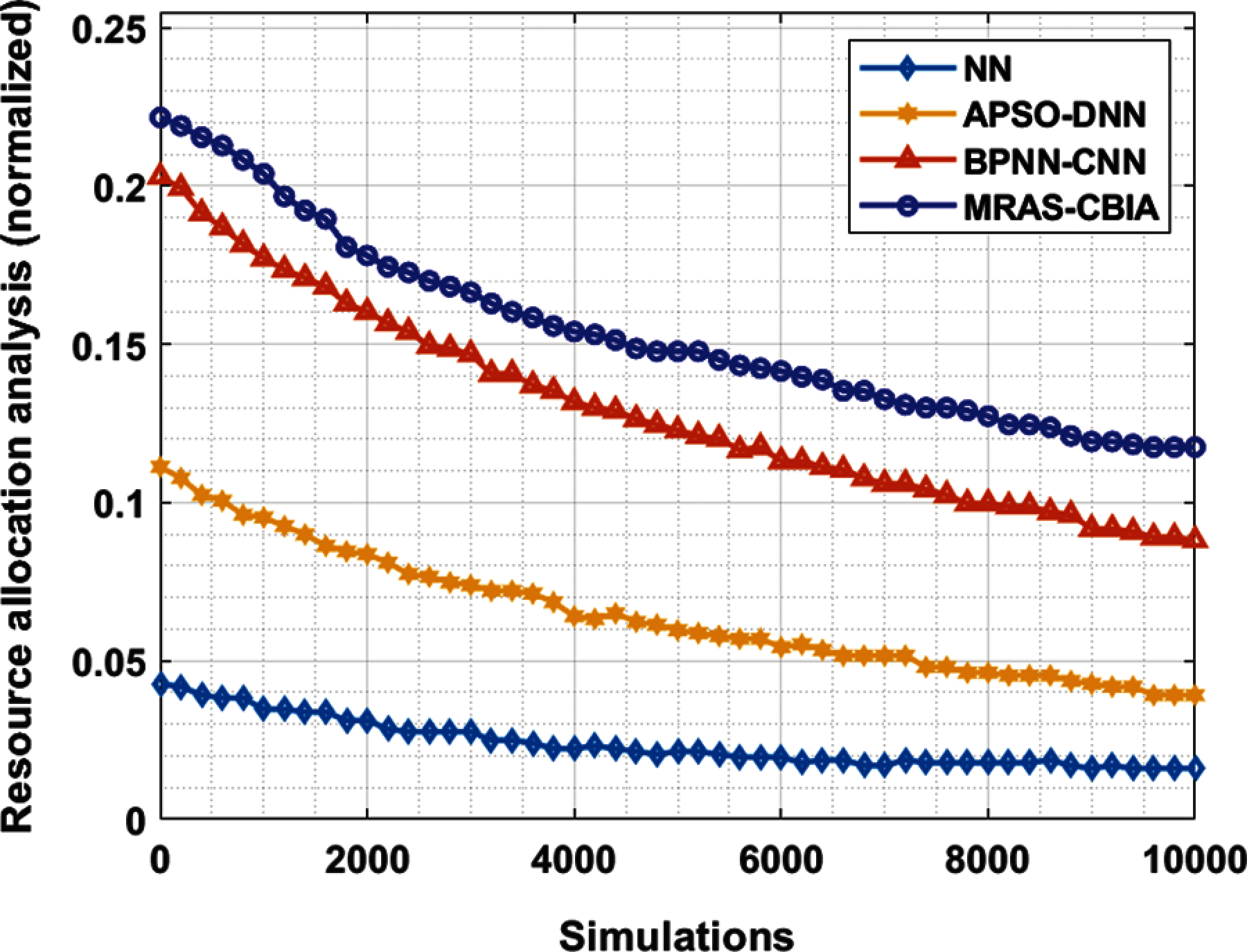
Figure 4: Analysis of optimal resource allocation
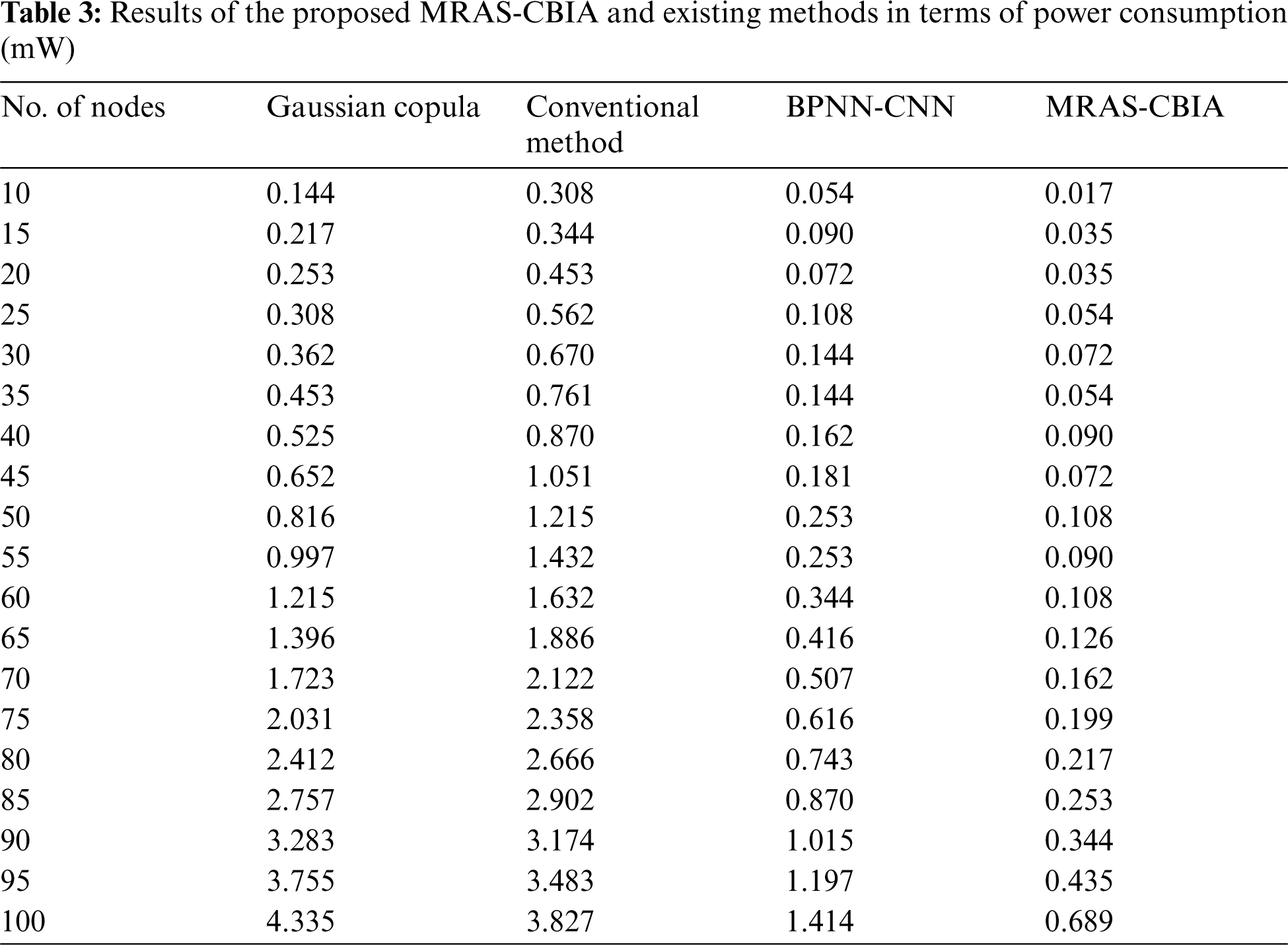
Finally, a detailed power consumption analysis of the proposed MRAS-CBIA technique against other techniques was performed and the results are shown in Tab. 3 and Fig. 5. The experimental values showcase that the proposed MRAS-CBIA technique gained an effectual outcome by consuming minimal power under distinct node counts. For instance, under 25 nodes, MRAS-CBIA technique reduced the power consumption to 0.017 mW, whereas Gaussian Copula, Conventional method, and BPNN-CNN techniques increased the power consumption up to 0.144, 0.308, and 0.054 mW respectively. Under 50 nodes, MRAS-CBIA technique reduced the power consumption to 0.816mW, whereas Gaussian Copula, Conventional method, and BPNN-CNN techniques accomplished high power consumption i.e., 0.816, 1.215, and 0.253 mW respectively. Moreover, under 75 nodes, MRAS-CBIA technique reduced the power consumption to 0.199 mW, whereas Gaussian Copula, Conventional method, and BPNN-CNN techniques increased their power consumption up to 2.031, 2.358, and 0.616 mW respectively. Finally, under 100 nodes, MRAS-CBIA technique reduced the power consumption to 4.335 mW, whereas Gaussian Copula, Conventional method, and BPNN-CNN techniques resulted in increased power consumption of 3.827, 1.414, and 0.689 mW respectively.
From the aforementioned tables and figures, it is clear that the proposed MRAS-CBIA technique is an effectual performer compared to all other methods.
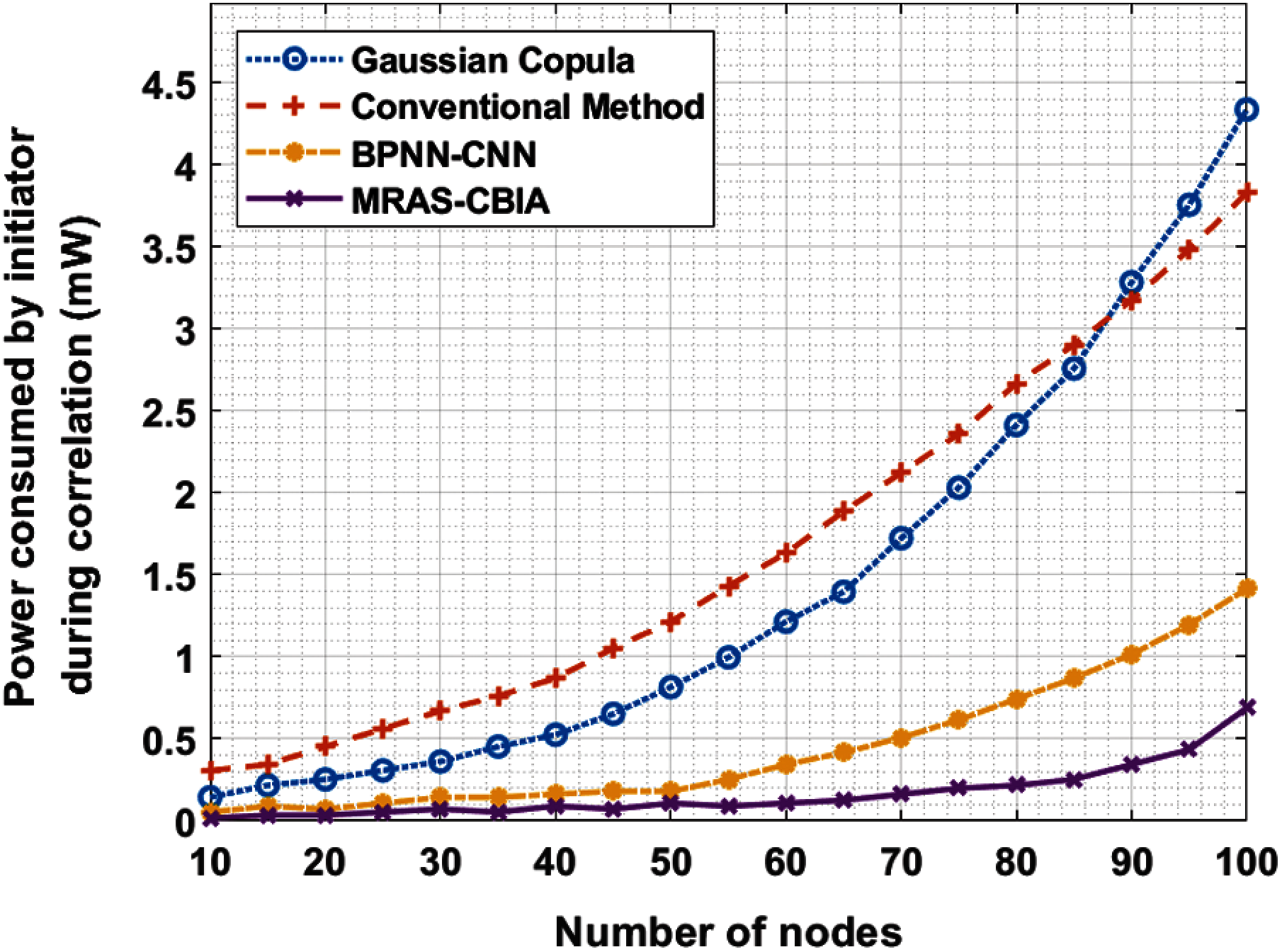
Figure 5: Comparative Analysis of MRAS-CBIA Model in terms of Power Consumption
The current study designed a new MRAS-CBIA technique to achieve energy efficiency and optimal resource allocation in 6G Industrial applications. The proposed MRAS-CBIA technique derives a new WCT to elect an optimal set of coordination nodes in 6G networks while rest of them are labeled as task nodes. Followed by, DTLP technique is executed to determine the location of nodes in the network. Finally, FCM-TSA technique effectually allocates the resources and accomplishes energy efficiency. Besides, FCM-TSA technique partitioned the resource while the scalability of resource searching process gets minimized. In order to validate the enhanced performance of the presented MRAS-CBIA technique, an extensive range of simulations was conducted. The experimental values confirmed that the proposed MRAS-CBIA technique achieved high energy efficiency and optimal resource allocation in 6G industrial applications. In future, the design of MRAS-CBIA technique can be extended to include task scheduling and MAC scheduling approaches.
Funding Statement: The authors extend their appreciation to the Deanship of Scientific Research at King Khalid University for funding this work under Grant Number (RGP2/209/42), https://www.kku.edu.sa. This research was funded by the Deanship of Scientific Research at Princess Nourah bint Abdulrahman University through the Fast-Track Path of Research Funding Program.
Conflicts of Interest: The authors declare that they have no conflicts of interest to report regarding the present study.
1. M. Hnatiuc, O. Geman, A. G. Avram, D. Gupta and K. Shankar, “Human signature identification using IoT technology and gait recognition,” Electronics, vol. 10, no. 7, pp. 1–17, 2021. [Google Scholar]
2. F. Marozzo, D. Talia and P. Trunfio, “A Workflow management system for scalable data mining on clouds,” IEEE Transactions on Services Computing, vol. 11, no. 3, pp. 480–492, 2018. [Google Scholar]
3. T. Vaiyapuri, V. S. Parvathy, V. Manikandan, N. Krishnaraj, D. Gupta et al., “A novel hybrid optimization for cluster-based routing protocol in information-centric wireless sensor networks for IoT based mobile edge computing,” Wireless Personal Communications, vol. 49, pp. 145, 2021. [Google Scholar]
4. D. M. S. Velandia, N. Kaur, W. G. Whittow, P. P. Conway and A. A. West, “Towards industrial internet of things: Crankshaft monitoring, traceability and tracking using RFID,” Robotics and Computer-Integrated Manufacturing, vol. 41, pp. 66–77, 2016. [Google Scholar]
5. R. Bharathi, T. Abirami, S. Dhanasekaran, D. Gupta, A. Khanna et al., “Energy efficient clustering with disease diagnosis model for IoT based sustainable healthcare systems, Sustainable Computing,” Informatics and Systems, vol. 28, pp. 1–8, 2020. [Google Scholar]
6. H. Xu, P. V. Klaine, O. Onireti, B. Cao and M. Imran, “Blockchain-enabled resource management and sharing for 6G communications,” Digital Communications and Networks, vol. 6, no. 3, pp. 261–269, 2020. [Google Scholar]
7. P. S. Raman, K. Shankar and M. Ilayaraja, “Securing cluster based routing against cooperative black hole attack in mobile ad hoc network,” International Journal of Engineering & Technology, vol. 7, no. 1.9, pp. 1–6, 2018. [Google Scholar]
8. W. Saad, M. Bennis and M. Chen, “A vision of 6G wireless systems: Applications, trends, technologies, and open research problems,” IEEE Network, vol. 34, no. 3, pp. 134–142, 2020. [Google Scholar]
9. K. Shankar, E. Perumal, M. Elhoseny and P. T. Nguyen, “An IoT-cloud based intelligent computer-aided diagnosis of diabetic retinopathy stage classification using deep learning approach,” Computers, Materials & Continua, vol. 66, no. 2, pp. 1665–1680, 2021. [Google Scholar]
10. X. Liu, H. Ding and S. Hu, “Uplink resource allocation for NOMA-based hybrid spectrum access in 6G-enabled cognitive internet of things,” IEEE Internet Things Journal, vol. 99, pp. 1–1, 2020. [Google Scholar]
11. A. Mukherjee, P. Goswami, M. A. Khan, L. Manman, L. Yang et al., “Energy-efficient resource allocation strategy in massive IoT for industrial 6G applications,” IEEE Internet Things Journal, vol. 8, no. 7, pp. 5194–5201, 2021. [Google Scholar]
12. A. Shukla, R. Gupta, S. Tanwar, N. Kumar and J. J. P. C. Rodrigues, “Block-RAS: A p2p resource allocation scheme in 6G environment with public blockchains,” in GLOBECOM, 2020 - 2020 IEEE Global Communications Conference, Taipei, Taiwan, pp. 1–6, 2020. [Google Scholar]
13. A. H. Sodhro, S. Pirbhulal, Z. Luo, K. Muhammad and N. Z. Zahid, “Toward 6G architecture for energy-efficient communication in IoT-enabled smart automation systems,” IEEE Internet Things Journal, vol. 8, no. 7, pp. 5141–5148, 2021. [Google Scholar]
14. B. D. Deebak, F. Al-Turjman and M. Alazab, “Dynamic-driven congestion control and segment re-routing in the 6G-enabled data networks,” IEEE Transactions on Industrial Informatics, vol. 17, no. 10, pp. 1, 2020. [Google Scholar]
15. Y. Liu, X. Wang, G. Boudreau, A. B. Sediq and H. Abou-Zeid, “A multi-dimensional intelligent multiple access technique for 5G beyond and 6G wireless networks,” IEEE Transactions on Wireless Communications, vol. 20, no. 2, pp. 1308–1320, 2021. [Google Scholar]
16. S. Hu, Y. -C. Liang, Z. Xiong and D. Niyato, “Blockchain and artificial intelligence for dynamic resource sharing in 6G and beyond,” IEEE Transactions on Wireless Communications, vol. 28, no. 4, pp. 1–7, 2021. [Google Scholar]
17. R. Pal, S. Yadav, R. Karnwal and K. Aarti, “EEWC: Energy-efficient weighted clustering method based on genetic algorithm for HWSNs,” Complex & Intelligent Systems, vol. 6, no. 2, pp. 391–400, 2020. [Google Scholar]
18. L. Xia, Q. Huang and D. Wu, “Decision tree-based contextual location prediction from mobile device logs,” Mobile Information Systems, vol. 2018, no. 5, pp. 1–11, 2018. [Google Scholar]
19. S. Kaur, L. K. Awasthi, A. L. Sangal and G. Dhiman, “Tunicate swarm algorithm: A new bio-inspired based metaheuristic paradigm for global optimization,” Engineering Applications of Artificial Intelligence, vol. 90, no. 2, pp. 1–29, 2020. [Google Scholar]
20. V. Porkodi, A. R. Singh, A. R. W. Sait, K. Shankar, E. Yang et al., “Resource provisioning for cyber-physical–social system in cloud-fog-edge computing using optimal flower pollination algorithm,” IEEE Access, vol. 8, pp. 105311–105319, 2020. [Google Scholar]
 | This work is licensed under a Creative Commons Attribution 4.0 International License, which permits unrestricted use, distribution, and reproduction in any medium, provided the original work is properly cited. |