DOI:10.32604/cmc.2022.021012

| Computers, Materials & Continua DOI:10.32604/cmc.2022.021012 |  |
| Article |
Network Quality Assessment in Heterogeneous Wireless Settings: An Optimization Approach
Computer Science Department, College of Computer and Information Science, Umm AlQura University, Makkah, Kingdom of Saudi Arabia
*Corresponding Author: Sultan H. Almotiri. Email: shmotiri@uqu.edu.sa
Received: 19 June 2021; Accepted: 30 July 2021
Abstract: The identification of an effective network which can efficiently meet the service requirements of the target, while maintaining ultimate performance at an increased level is significant and challenging in a fully interconnected wireless medium. The wrong selection can contribute to unwanted situations like frustrated users, slow service, traffic congestion issues, missed and/or interrupted calls, and wastefulness of precious network components. Conventional schemes estimate the handoff need and cause the network screening process by a single metric. The strategies are not effective enough because traffic characteristics, user expectations, network terminology and other essential device metrics are not taken into account. This article describes an intelligent computing technique based on Multiple-Criteria Decision-Making (MCDM) approach developed based on integrated Fuzzy AHP-TOPSIS which ensures flexible usability and maximizes the experience of end-users in miscellaneous wireless settings. In different components the handover need is assessed and the desired network is chosen. Further, fuzzy sets provide effective solutions to address decision making problems where experts counter uncertainty to make a decision. The proposed research endeavor will support designers and developers to identify, select and prioritize best attributes for ensuring flexible usability in miscellaneous wireless settings. The results of this research endeavor depict that this proposed computational procedure would be the most conversant mechanism for determining the usability and experience of end-users.
Keywords: Wireless sensor networks; fuzzy logic; AHP-TOPSIS; miscellaneous network; intelligent computing techniques
Wireless networks technology have made tremendous progress in recent years. Although, any specific type of current system equipped with wireless network like Wi-Fi, Bluetooth, UMTS, Worldwide Interoperability for Microwave Access (WiMAX) cannot offer any level of handling, for example broad coverage as well as high bandwidth. The unified diverse network of sustainable development calls for a combination of different form of network, such as bandwidth, time-limit communication distance, speed assistance, energy usage, protection, end-user cost, etc., [1–5].
Digital networking now provides diverse, flexible distribution and Quality of service wireless communications [6–9]. Among the key aspects for utilizing wireless communication technologies 4th generation (4G) systems are heterogeneous cellular networks. The miscellaneous network is a blend of diverse connectivity technologies to ensure the participant's integrated accessibility and excellent service, like high wireless communication distribution and wireless local area network (WLAN) bandwidth [10–15].
Wireless networks of the next generation require different wireless technology. Because of the limitation of network infrastructure, coverage issues and increasing needs of the customer, one channel may not always be capable and requires QoS to support the user during the session [16–21]. Consequently, switching between various wireless channels continues to be easy resolutions in modern miscellaneous networks settings due to the integration of several network connectivity systems [22–26]. With our growing dependence on technology, it has become extremely important to protect all aspects of digital information and data [27–29]. Privacy and Security is now one of the most critical issues for organizations to remember as the modern internet infrastructures have become larger [30–32]. Increased demand for wireless communication in the implementation of intelligent infrastructure, a huge rise in internet usage, growth in implementation of the internet of things (IoT), growing trends such as work from home as well as virtual learning leading to the COVID-19 pandemic, and growing demand for low-power wi-fi are the main reasons influencing the wireless communication industry growth.
The overall number of Internet consumers worldwide is expected to rise at a CAGR of 6% from 3.9 billion in 2018 to 5.3 billion by 2023. In terms of population, this accounts for 51% of the world's population in 2018 and 66% of worldwide population growth by 2023 [33,34]. The following Fig. 1 shows the Internet user growth worldwide.
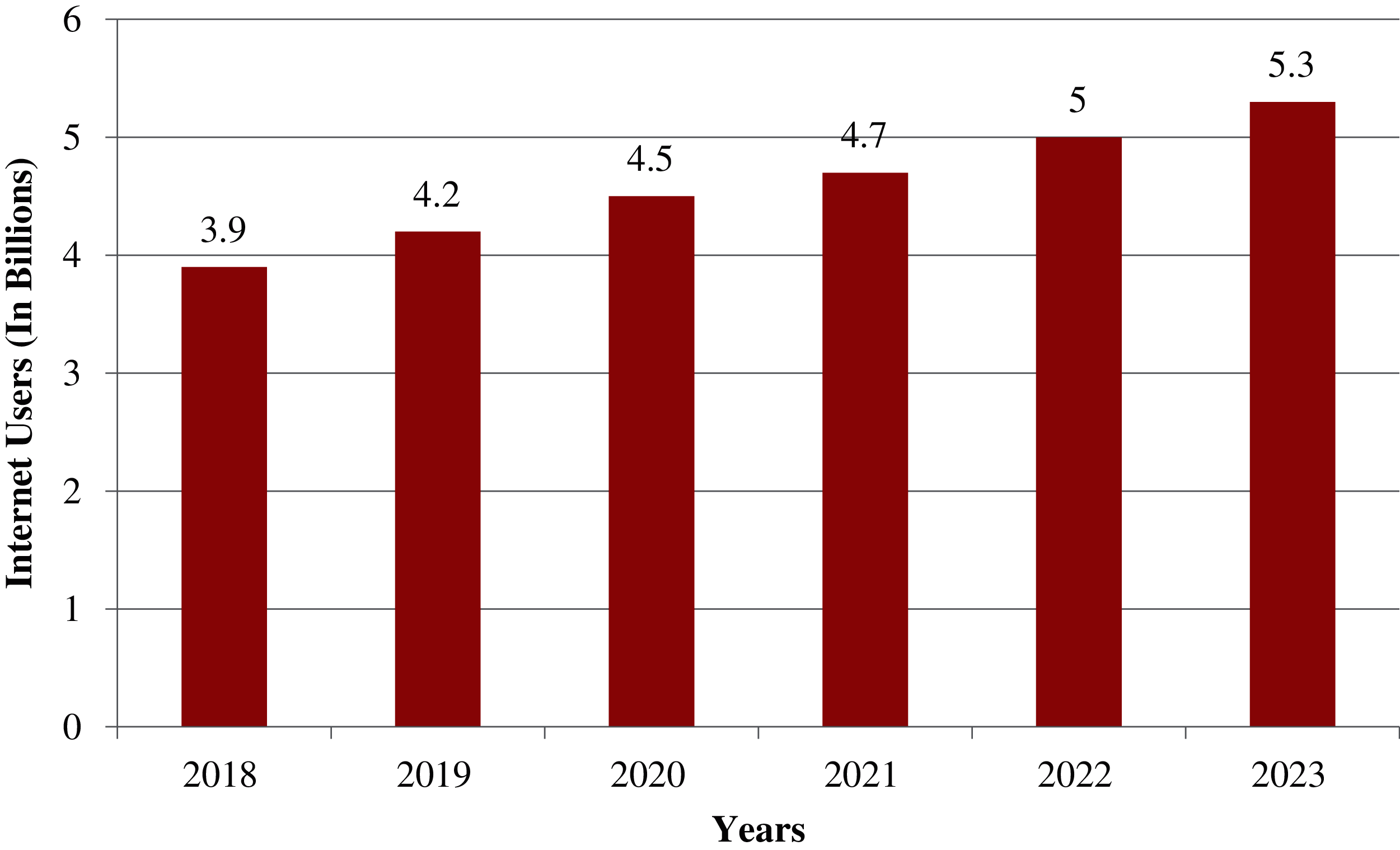
Figure 1: Global internet user growth (source: cisco annual internet report, 2018–2023)
In this article, we concentrate on the identification in expert based of the always appropriate linked network, preserving QoS for communication systems in a constrained environment. This is how we follow a Fuzzy approach to improve horizontal transfer decisions; it allows for a sensible and informed decision on the transfer, based on the network criteria. In order to justify the proposed objectives, deployment and analysis are presented.
The rest of the paper is organized accordingly. Section 2 summarizes associated work on network selection in miscellaneous wireless settings. Section 3 the presents the materials and methods used to achieve the objective of this study. Further, Section 3 also deals with and the implementation of integrated fuzzy AHP-TOPSIS approach and presents the statistical findings with sensitivity and comparative analysis. Finally the paper concludes in Section 4.
Quang et al. [1] designed MCDM based method has to an effective target network out of the available alternative networks to providing the best service and also to provide enough best wireless network service at all times. This article intends to provide a means by which a desired network system of the available channels can be chosen optimally. This way the best wireless network can be chosen for deployment target network between many alternate networks to optimize service quality.
Gazis et al. [2] suggested a model of two rating systems, one of which is network-specific as well as the other user-specific. Systems used fuzzy logic to rate various networks focused on their parameters. The distinction between the two rating systems lies in the dynamism that they delivered. The user-specific rating criteria were versatile, whereas the network-specific system uses defined criteria. The network-specific process can assist to provide a framework to visualize the overall output index of the networks.
Kaleem et al. [3] anticipated a novel multi-criteria VHO technique that selects a targeted NAT centered on many variables, like user expectations, device factors, and network traffic-types along with variable quality of service (QoS) specifications. They used two parameters i.e., the VHO Necessity Estimation (VHONE) system as well as the target NAT preference component. All components used a set of weighted application and device parameters. In order to boost the superiority of the suggested method, the weighting method is premised based on the idea of fuzzy oriented linguistic terms.
Charilas et al. [7] tackled such problem by implementing Multi-Attribute Decision Making (MADM) approaches. Fuzzy AHP (Analytical Hierarchy Process) the MADM system is originally used to decide the weights of many service quality measures that serve as parameters influencing the decision-making process. In the form of subjective assessments, the fuzzy extension of this approach and hence the use of fizzy numbers was implemented to integrate the presence of fuzziness. Subsequently, ELECTRE, MADM priority scoring system, is used to rate alternatives.
Alkhawlani et al. [9] presented a comprehensive model to fix the issue of network selection (ANS) within heterogeneous wireless networks (HWN). Their suggested technique was designed to introduce and model a specific multicriteria software assistant (SA) which could be considered by the user, the controller and/or the QoS point of view. Mixed fuzzy logic and genetic algorithms (GAs) were used to provide the proposed technique with the necessary optimization, versatility and usability. Their consequences have demonstrated that the suggested methodology and SA have stronger and more stable output over unsystematic assortment.
Drissi et al. [10] suggested a strategy to effective network assortment focused on the Fuzzy Analytical Hierarchy System (FAHP) used to assess the comparative weights of the assessment parameters. They used Simple Additive Weighting (SAW) to prioritize the accessible channels. Deployment and visualisation tests with the NS3 Network Simulator are provided to evaluate the anticipated methodology. Experiential findings showed that FAHP, relative to traditional AHP, produced substantial improvements of up to 10% in terms of delay and 25% in terms of packet failure.
Mehbodniya et al. [11] introduced a new multi-attribute vertical hand-off approach for heterogeneous wireless channels that maintains flexible accessibility while optimizing end-user experience. They utilized two parameters to predict the need for hand-off and also to choose the projected channels. Such components use simultaneous Fuzzy Logic Controllers (FLCs) with a decreased instruction set in association through a network rating methodology built focused on Fuzzy VIKOR (FVIKOR). The simulation findings were given and also contrasted to the standard.
3 Materials, Methods and Results
3.1 Design of Hierarchical Structure
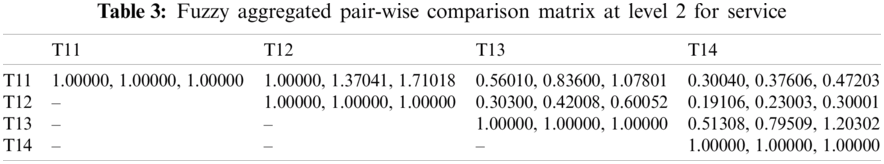
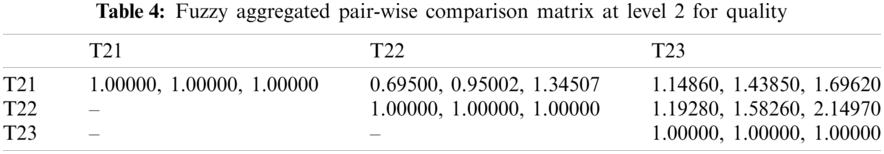
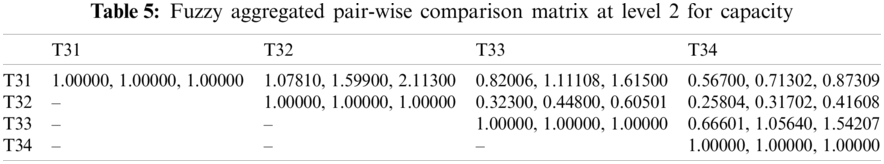
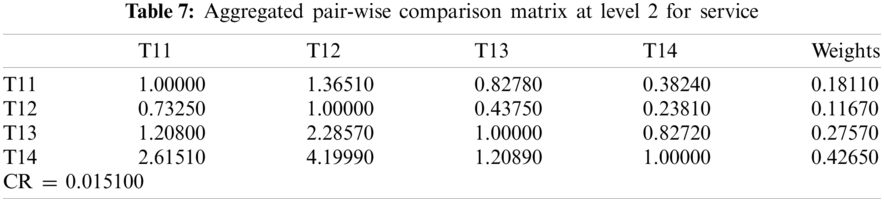
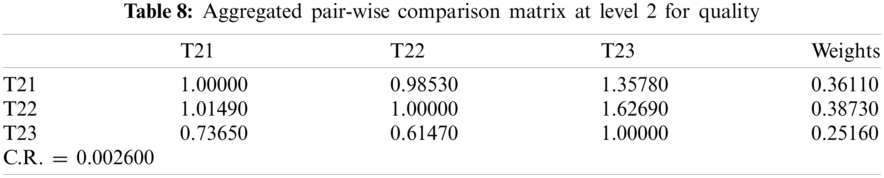
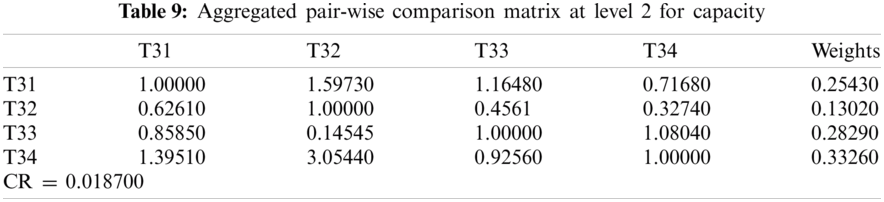
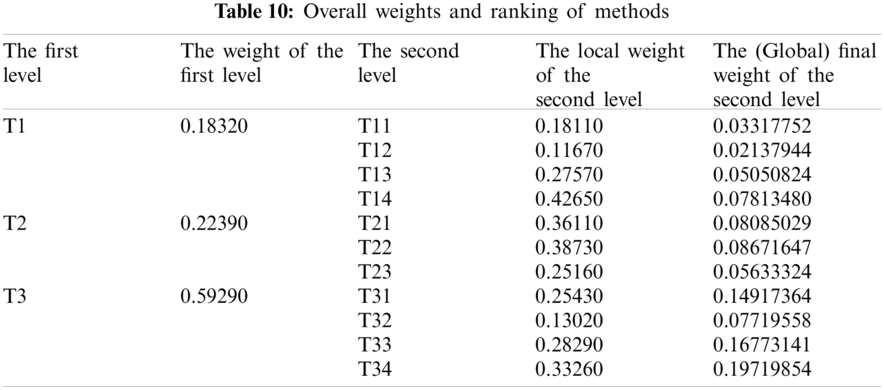
In this section, we aim to illustrate how and why the fuzzy AHP-TOPSIS approach should be used to overcome the issue of effective network selection in various wireless environments. The subsequent situation is taken into account: the client wants to share the data connection in a mobile for which four channels are accessible. All connections may support the client; although in order to optimize the Service (T1) [35], Quality (T2) [36] and Capability (T3) [37] criteria provided, the most effective network must be identified. The sub-criteria for the Service (T1) to be taken into account in the MCDM (Multiple-criteria decision-making) process are Delay (T11) [38,39], Jitter (T12) [40], Packet Loss Ratio (T13) [41,42] and Throughput (T14) [43,44]. Delay and Jitter are of higher importance relative to other Service criteria, whereas Throughput is of lower importance. The sub-criteria for Quality (T2) are Cost-effectiveness (T21) [45], Reliability (T22) [46,47] and Maintainability (T23) [48]. Moreover the sub-criteria for Capability (T3) are Security (T31) [49], Scalability (T32) [50], Data Support Rate (T33) [51] and Latency (T34) [49–51] yields an assortment of significance. Further, description of different types of wireless communication networks is given in Tab. 1.

Although relative value cannot be precisely defined, we anticipate the utilization of fuzzy logic to be a beneficial option in our methodology. Ambiguity in correlations may be interpreted by fuzzy numbers, such that a range of potential results is obtained rather than just another single value. Correlating fuzzy numbers can be obtained from expert questionnaire survey or network measurements [13–17] in which the worst and best ratings may be the bottom and top limits of fuzzy numbers, accordingly. The following Fig. 2 shows the hierarchy for effective network selection.
The FAHP-TOPSIS strategy is a systematic mixture of the Fuzzy AHP method and the Fuzzy TOPSIS process. In the first point, Fuzzy AHP is being utilized to calculate the relative value of the parameters as contrasted to one another. These weighted parameters are used to allocate a rating to each individual for each assessment criterion. This step is characterized by the Fuzzy TOPSIS, in which the distance score of and individual to the ideal is determined on the basis of the given ratings, for respectively the positive ideal and for the negative ideal. The strongest alternatives must be as close to the positive standard as practicable and as far away as possible from the negative ideal. The succinct measures of the FAHP-TOPSIS are as shown in Fig. 3.
Fuzzy AHP Initially introduced by Thomas L. Saaty, AHP is among the powerful MCDM solutions to address complex, unorganized challenges by constructing a conceptual hierarchy [14]. The key principle of AHP is to establish a preference for the weighting for every alternative decision. Priorities may be defined using a natural linguistic or numeric data value to determine the statistical significance of each parameter. In order to evaluate the order, the first two parameters are contrasted with the help of a nine-point scale ranking for importance [15]. To add fuzziness, pairwise values are then used in a matrix with the help of Triangular Fuzzy Number (TFN) [16,34].
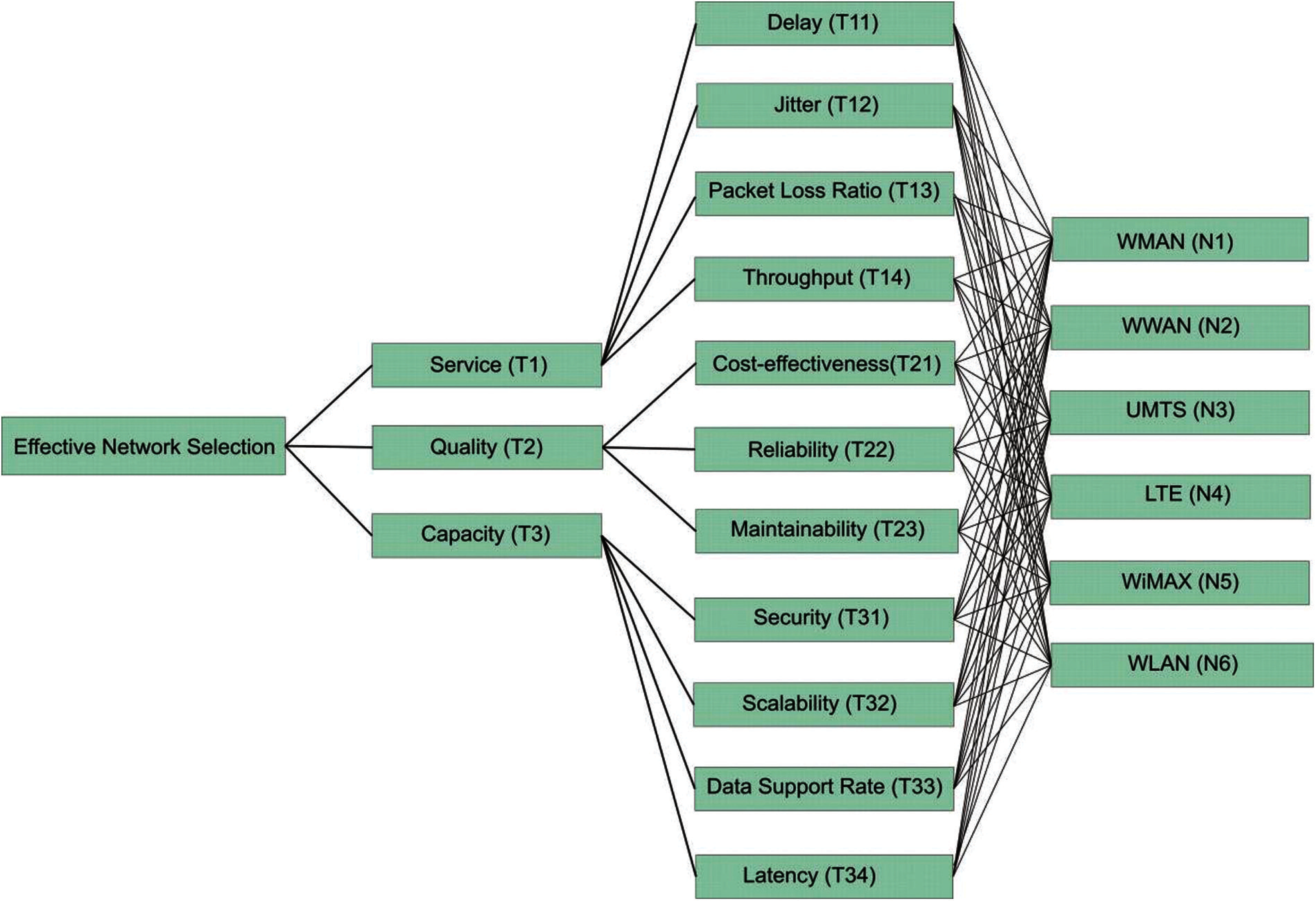
Figure 2: Hierarchy for effective network selection
Fuzzy Technique for Order of Preference by Similarity to Ideal Solution (FTOPSIS) is the MCDM method developed by Hwang and Yoon [17], in which the resolution is the ones having the Euclidean distance closest to the strongest assumption, the Positive Ideal Solution (PIS) as well as the farthest with the weakest assumption, the Negative Ideal Solution (NIS) [18–24]. Fuzzy TOPSIS requires details on the overall relevance of every other weighting criterion. In integrated Fuzzy AHP-TOPSIS, the weights have always been determined in the Fuzzy AHP step [25–29].
This section addresses numerous statistical results from the implementation of the integrated fuzzy AHP-TOPSIS model. Network experts typically perform behavioral assessments to examine the performance of different networks on the basis of identified criteria. To that end, the problematic actions of broad collections of indicators of implementation must be defined and characterized. Experts and researchers in wireless communication networks have a challenging task to quantify numerically the impact of different wireless networks in telecommunication organization. We have used a well-developed and validated decision maker technique, Integrated fuzzy AHP-TOPSIS, in order to achieve the goal in our research paper. This procedure is acquainted for prioritizing the different wireless networks based on their service, quality and capability evaluation in modern telecommunication situation.
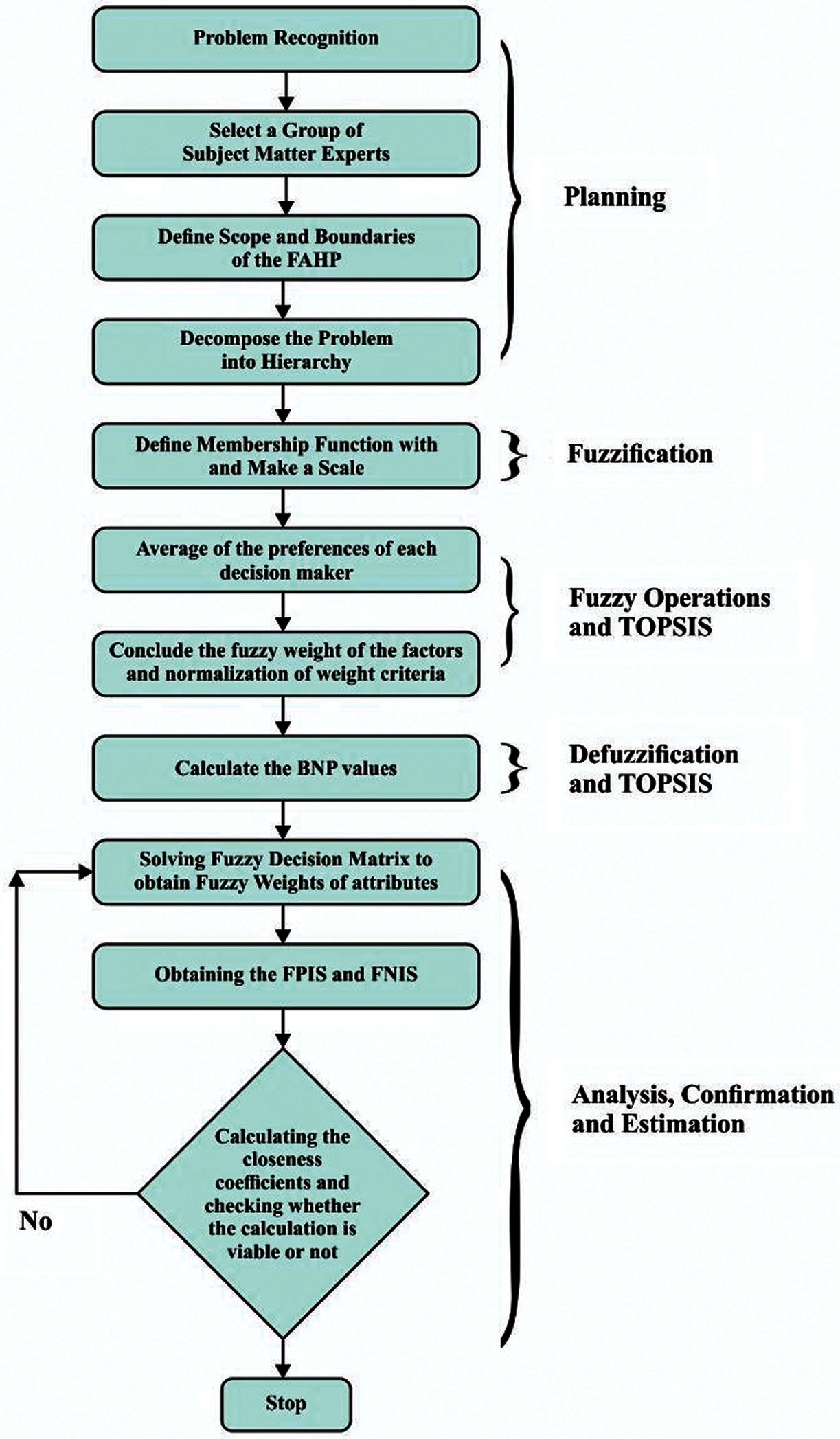
Figure 3: Flow chart of fuzzy AHP-TOPSIS method
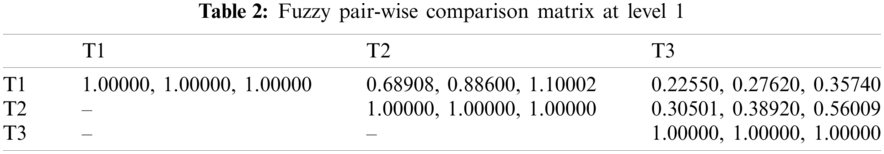
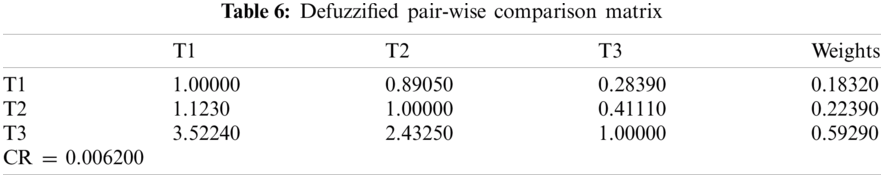
For producing a more substantial result, we took recommendations from 75 network experts who come from different telecommunication firms and academic professional. The information subcontracted from these experts was composed for our observed investigations. The different factors for the performance evaluation at implementation phase i.e., Service, Quality and Capability are represented by T1, T2 and T3 respectively. Systematic approach of fuzzy-AHP TOPSIS is used according to functional structure shown in Fig. 3 to determine the effective network among different alternatives such as WMAN, WWAN, UMTS, LTE, WiMAX and WLAN represented by N1, N2, N3, N4, N5 and N6 respectively. The following Tabs. 2–14 demonstrates the statistical findings of the present study and graphical representation of satisfaction degree of different alternatives is shown in Fig. 4.
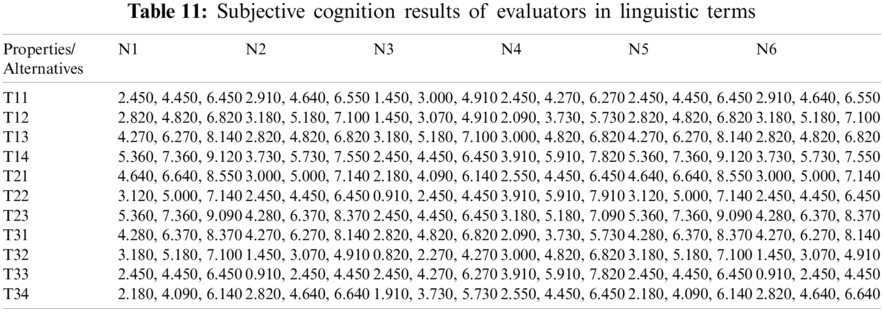
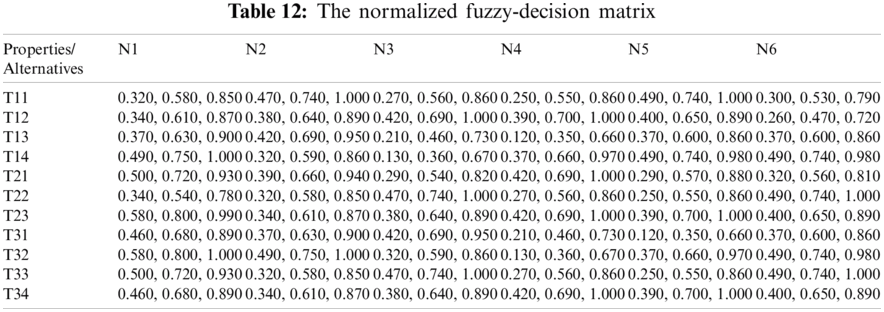
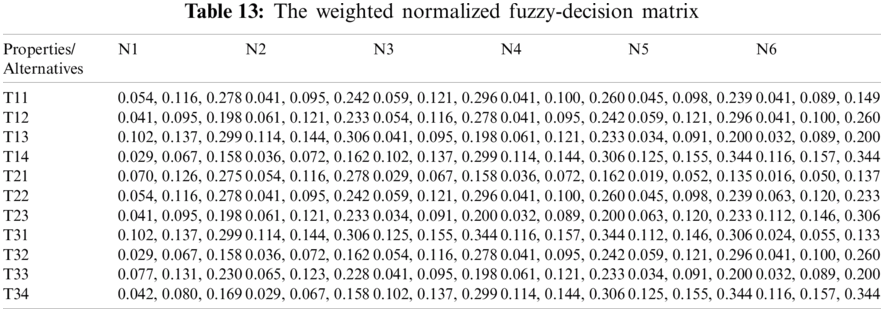
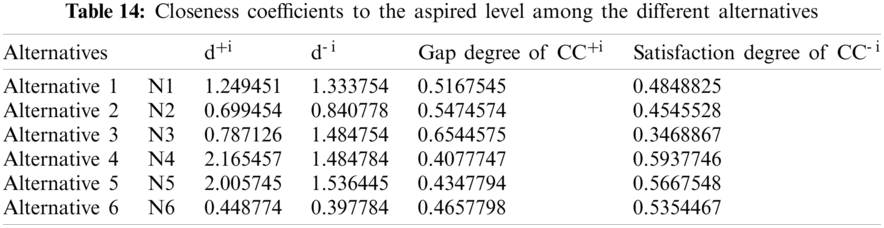
We discussed the issue of network selection in wireless telecommunication context which characterizes operational efficiency over a miscellaneous wireless access setting. The implementation of Fuzzy AHP with Fuzzy TOPSIS, i.e., two powerful MCDM approach, for the assessment of different wireless network alternatives were defined in this context. Although the relative value of each parameter over another could be clearly specified, fuzzy numbers have been introduced in order to incorporate the complexity of subjective judgments into the description of the issues. The anticipated technique was eventually checked by means of a numerical model, which showed how the most effective solution, in this case the most effective wireless channel, was chosen. The satisfaction degree (CC-i) of different alternatives is estimated as 0.4848825, 0.4545528, 0.3468867, 0.5937746, 0.5667548 and 0.5354467 for N1, N2, N3, N4, N5 and N6 respectively. As per the findings shown in Fig. 4 the fourth alternative (N4) is highly effective and proficient network channel among miscellaneous wireless settings in a telecommunication organization.
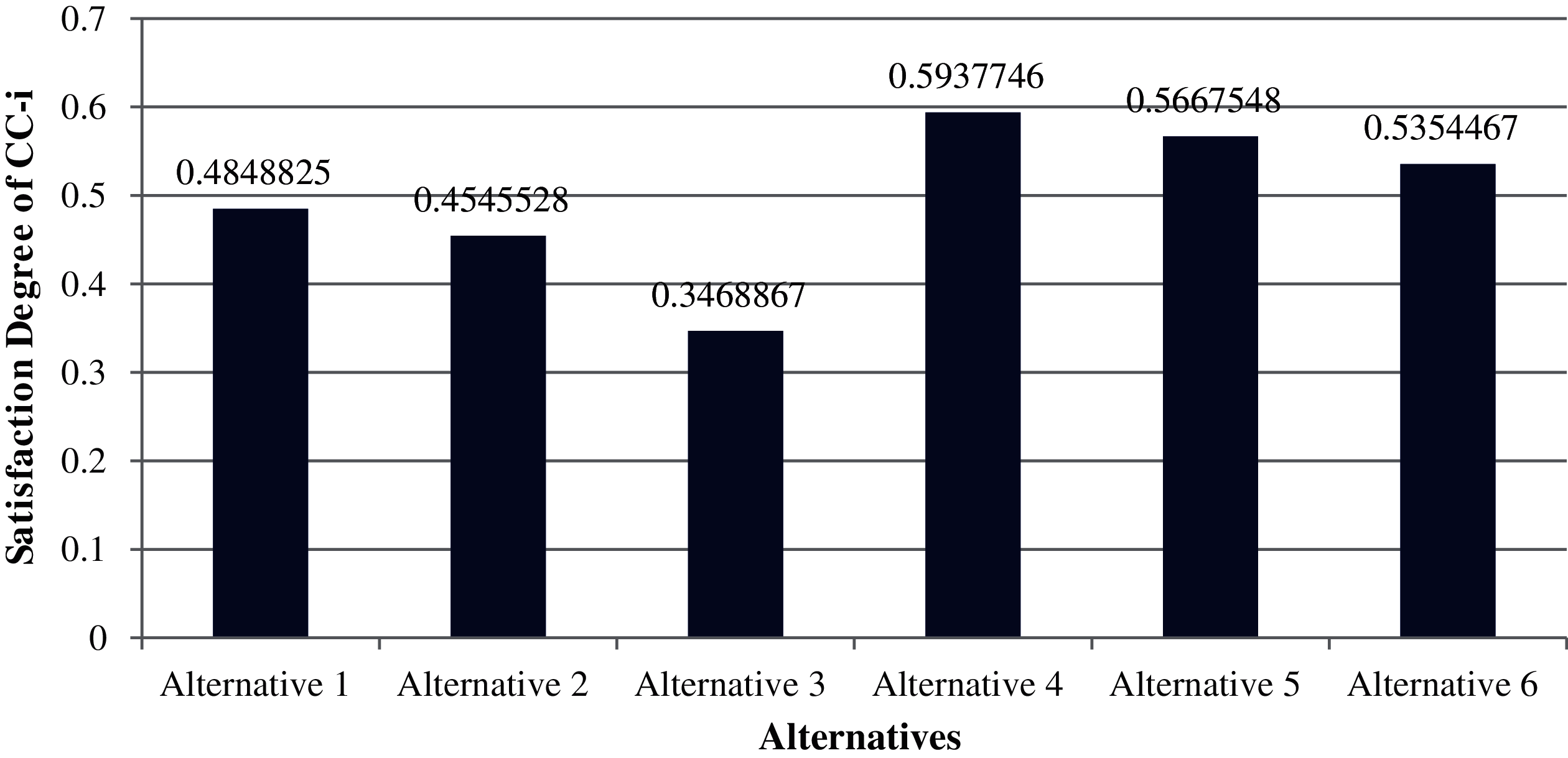
Figure 4: Graphical representation of satisfaction degree of different alternatives
In this section we present the findings of sensitive analysis performed with the help of different experiments. Sensitive analysis is a significant approach used to analyses how the numbers of independent factors would affect a specific dependent factor under a certain set of expectations. Its application will be determined by one or many input parameters within the specified parameters. Any action or system can benefit from sensitivity analysis. Ultimately, the decision maker has a good notion of how sensitive his optimal solution is to variations in the input values of one or more variables. Tab. 15 and Fig. 5 shows the sensitivity analysis of the final results.
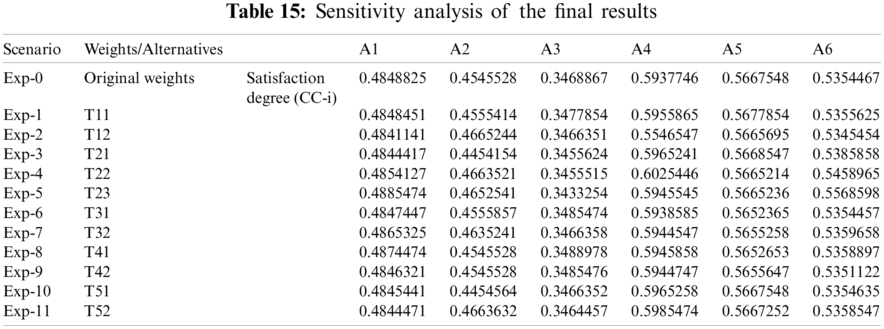
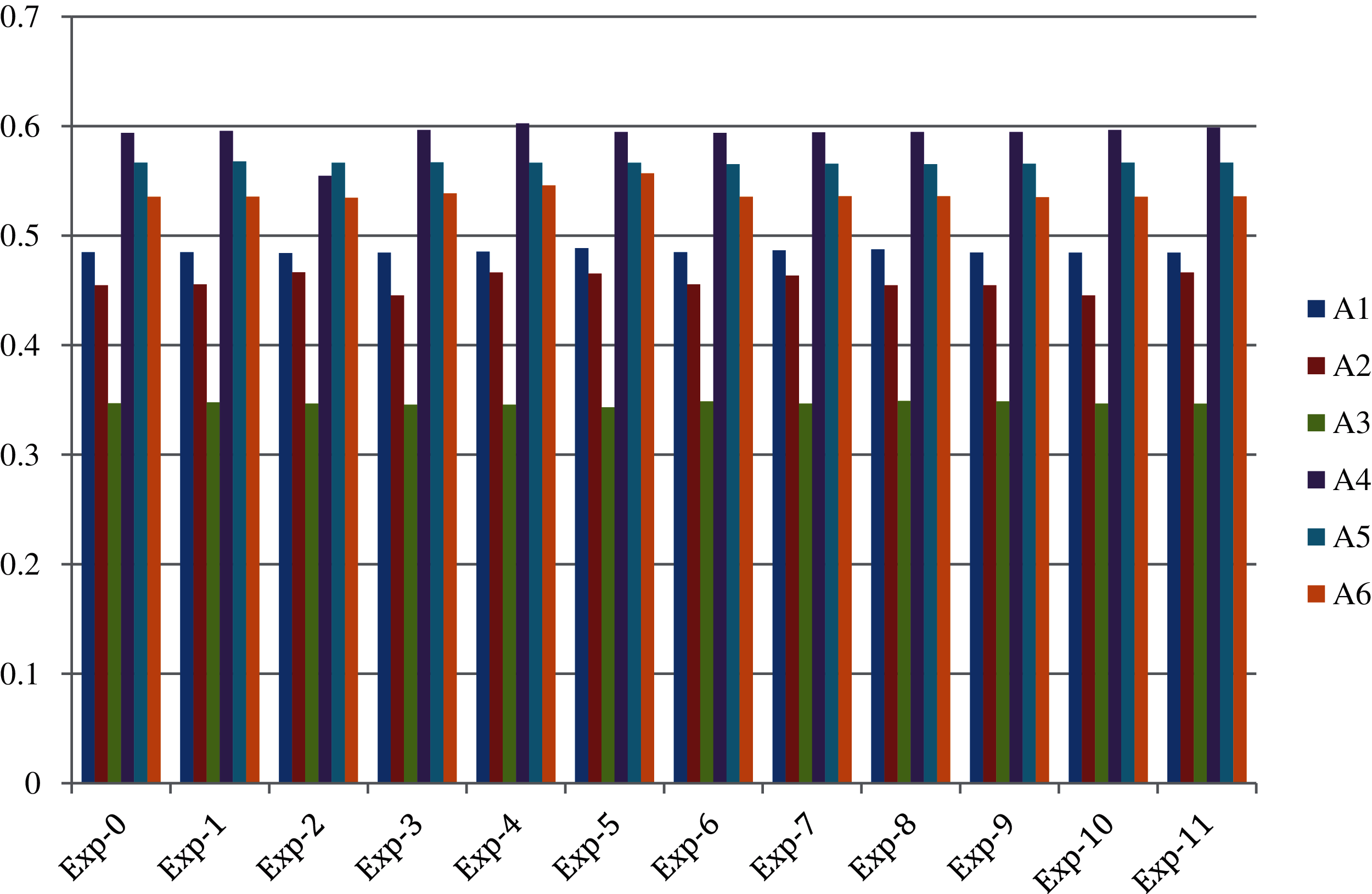
Figure 5: Graphical representation of sensitivity analysis
Comparing the results of many alternative approaches and displaying the accuracy of the results is a regular process in multi criterion decision making. Models are frequently tested using cross-validation approaches and directly compared. Although straightforward, this strategy can be deceptive because it is difficult to determine if the difference in average performance ratings is true or the product of a statistical anomaly. Here we compare findings from Fuzzy-AHP-TOPSIS Method with findings of four other MCDM approach such as Fuzzy-ANP-TOPSIS Method, Fuzzy Weighted Average Method, Classical-AHP-TOPSIS Method, Classical-AHP-TOPSIS Method. The following Tab. 16 and Fig. 6 shows the comparison of the outcomes from different MCDM methodology.
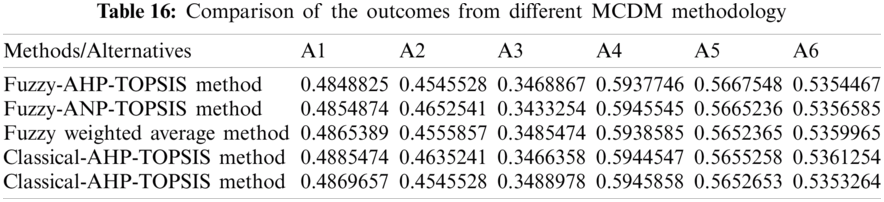
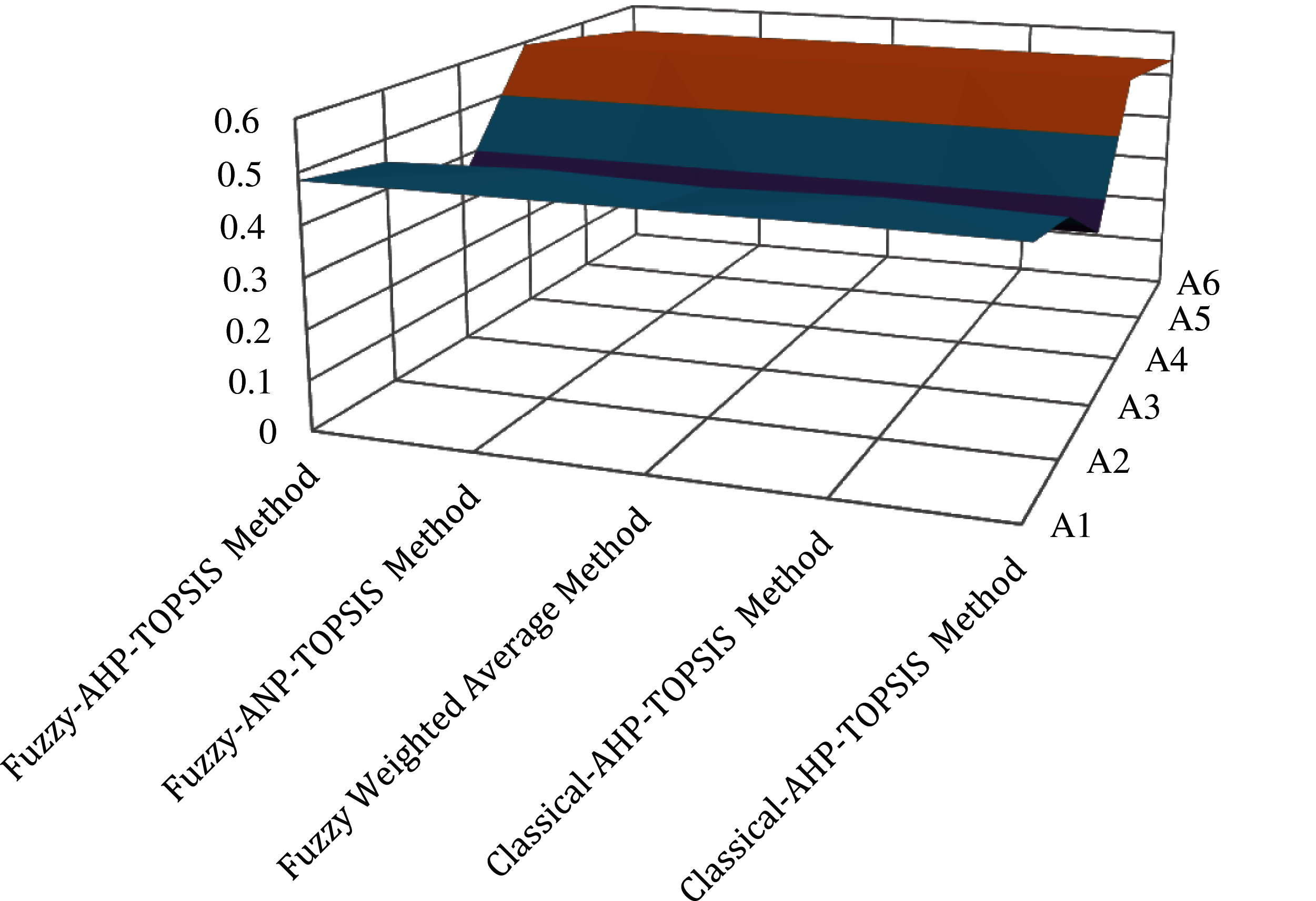
Figure 6: Graphical representation of different outcomes
We have demonstrated through the findings that in particular, the goals for effective network selection for the telecommunications organization are very consistent from one observer to another. This represents the presence of a group of standards which are considered to be crucial for the organization in choosing its network for assured functions. FAHP-TOPSIS has successfully captured this by consistently determining the effective access network which currently holds the better service, quality and capability. Although there are, areas in which the preferences provided the value of the determining factor have seemed to vary from the standard operation, causing in a failure of the FAHP-TOPSIS. Consequently, it should be assumed that the FAHP-TOPSIS is generally effective when implemented in the effective access network selection process. Although the drawback is that the experts whose viewpoint is being used as feedback must have an outstanding understanding or principles similar to those of the implementation of the smart for the evaluation process. Additionally, FAHP-TOPSIS may help as a significant method to provide feedback to an evaluation process that is supposed to conform with some kind of group of standards, because it is more impartial when associated to participants.
Acknowledgement: This work was supported by the King Abdul Aziz City for Science and Technology (KACST), under Grant No. (14-INF727-10).
Funding Statement: This project is funded by the King Abdul Aziz City for Science and Technology, under Grant Number: 14-INF727-10.
Conflicts of Interest: The authors declare that they have no conflicts of interest to report regarding the present study.
1. B. V. Quang, R. V. Prasad and I. Niemegeers, “A survey on handoffs lessons for 60 GHz based wireless systems,” IEEE Communications Surveys & Tutorials, vol. 14, no. 1, pp. 64–86, 2010. [Google Scholar]
2. V. Gazis, N. Alonistioti and L. Merakos, “Toward a generic always best connected capability in integrated WLAN/UMTS cellular mobile networks (and beyond),” IEEE Wireless Communications, vol. 12, no. 3, pp. 20–29, 2005. [Google Scholar]
3. F. Kaleem, Mehbodniya, A. Islam, K. K. Yen and F. Adachi, “Dynamic target wireless network selection technique using fuzzy linguistic variables,” China Communications, vol. 10, no. 1, pp. 1–16, 2013. [Google Scholar]
4. A. Dutta, S. Das, D. Famolari, Y. Ohba, K. Taniuchi et al., “Seamless proactive handover across heterogeneous access networks,” Wireless Personal Communications, vol. 43, no. 3, pp. 837–855, 2007. [Google Scholar]
5. M. T. J. Ansari, D. Pandey and M. Alenezi, “STORE: Security threat oriented requirements engineering methodology,” Journal of King Saud University-Computer and Information Sciences, Article in Press, pp. 1–18, 2018. https://doi.org/10.1016/j.jksuci.2018.12.005. [Google Scholar]
6. J. Madaan, S. Gupta and P. Manihas, “A new method for handoff target network selection,” IAES International Journal of Robotics and Automation, vol. 8, no. 1, pp. 36–43, 2019. [Google Scholar]
7. D. E. Charilas, O. I. Markaki, J. Psarras and P. Constantinou, “Application of fuzzy AHP and ELECTRE to network selection,” Lecture Notes of the Institute for Computer Sciences, Social Informatics and Telecommunications Engineering, vol. 13, no. 5, pp. 15–25, 2009. [Google Scholar]
8. K. Sahu, F. A. Alzahrani, R. K. Srivastava and R. Kumar, “Hesitant fuzzy sets based symmetrical model of decision-making for estimating the durability of web application,” Symmetry, vol. 12, no. 6, pp. 1770–1792, 2020. [Google Scholar]
9. M. Alkhawlani and A. Ayesh, “Access network selection based on fuzzy logic and genetic algorithms,” Advances in Artificial Intelligence, vol. 8, no. 12, pp. 152–160, 2008. [Google Scholar]
10. M. Drissi, M. Oumsis and D. Aboutajdine, “A fuzzy AHP approach to network selection improvement in heterogeneous cyberspace,” in Proc. of the Int. Conf. on Networked Systems, Rabat, Sale, Morocco, pp. 169–182, 2016. [Google Scholar]
11. A. Mehbodniya, F. Kaleem, K. K. Yen and F. Adachi, “A fuzzy extension of VIKOR for target network selection in heterogeneous wireless environments,” Physical Communication, vol. 7, no. 8, pp. 145–155, 2013. [Google Scholar]
12. A. Agrawal, M. Alenezi, S. A. Khan, R. Kumar and R. A. Khan, “Multi-level fuzzy system for usable-security assessment,” Journal of King Saud University-Computer and Information Sciences, article in press, pp. 1–9, 2019. https://doi.org/10.1016/j.jksuci.2019.04.007. [Google Scholar]
13. M. Alenezi, R. Kumar, A. Agrawal and R. A. Khan, “Usable-security attribute evaluation using fuzzy analytic hierarchy process,” ICIC Express Letters, vol. 13, no. 6, pp. 453–460, 2019. [Google Scholar]
14. T. L. Saaty, In Decision Making with Dependence and Feedback: the Analytic Network Process, New York Public Library, USA: RWS Publications, 1996. [Online]. Available: https://books.google.co.in/books/about/Decision_Making_with_Dependence_and_Feed.html?id=MGpaAAAAYAAJ. [Google Scholar]
15. R. Kumar, M. Alenezi, M. T. J. Ansari, B. Gupta, A. Agrawal et al., “Evaluating the impact of malware analysis techniques for securing web applications through a decision-making framework under fuzzy environment,” International Journal of Intelligent Engineering and Systems, vol. 13, no. 6, pp. 94–109, 2020. [Google Scholar]
16. R. Kumar, A. I. Khan, Y. B. Abushark, M. M. Alam, A. Agrawal et al., “An integrated approach of fuzzy logic, AHP and TOPSIS for estimating usable-security of web applications,” IEEE Access, vol. 8, no. 8, pp. 50944–50957, 2020. [Google Scholar]
17. C. L. Hwang and K. Yoon, “Methods for multiple attribute decision making,” Lecture Notes in Economics and Mathematical Systems, Springer, vol. 186, no. 5, pp. 58–191, 1981. [Google Scholar]
18. M. T. J. Ansari, F. A. Alzahrani, D. Pandey and A. Agrawal, “A fuzzy TOPSIS based analysis toward selection of effective security requirements engineering approach for trustworthy healthcare software development,” BMC Medical Informatics and Decision Making, vol. 20, no. 1, pp. 1–13, 2020. [Google Scholar]
19. D. S. Kumar, S. Radhika and K. N. S. Suman, “MADM methods for finding the right personnel in academic institutions,” International Journal of u- and -e Service, vol. 6, no. 5, pp. 133–144, 2013. [Google Scholar]
20. M. Zarour, M. T. J. Ansari, M. Alenezi, A. K. Sarkar, M. Faizan et al., “Evaluating the impact of blockchain models for secure and trustworthy electronic healthcare records,” IEEE Access, vol. 8, no. 8, pp. 157959–157973, 2020. [Google Scholar]
21. K. Sahu and R. Shree, “Stability: Abstract roadmap of security,” American International Journal of Research in Science, Engineering & Mathematics, vol. 2, no. 9, pp. 183–186, 2015. [Google Scholar]
22. S. A. Khan, M. Alenezi, A. Agrawal, R. Kumar and R. A. Khan, “Evaluating performance of software durability through an integrated fuzzy-based symmetrical method of ANP and TOPSIS,” Symmetry, vol. 12, no. 4, pp. 1–15, 2020. [Google Scholar]
23. K. Sahu and R. K. Srivastava, “Revisiting software reliability,” Advances in Intelligent Systems and Computing, vol. 802, pp. 221–235, 2019. [Google Scholar]
24. R. Kumar, S. A. Khan and R. A. Khan, “Durability challenges in software engineering,” Crosstalk, vol. 29, no. 5, pp. 29–31, 2016. [Google Scholar]
25. K. Sahu and R. K. Srivastava, “Soft computing approach for prediction of software reliability,” ICIC Express Letters, vol. 12, no. 12, pp. 1213–1222, 2018. [Google Scholar]
26. A. Agrawal, M. Zaroor, M. Alenezi, R. Kumar and R. A. Khan, “Security durability assessment through fuzzy analytic hierarchy process,” PeerJ Computer Science, pp. 1–43, 2019. https://doi.org/10.7717/peerj-cs.215. [Google Scholar]
27. K. Sahu and R. K. Srivastava, “Needs and importance of reliability prediction: An industrial perspective,” Information Sciences Letters, vol. 9, no. 1, pp. 33–37, 2020. [Google Scholar]
28. R. Kumar, S. A. Khan, A. Agrawal and R. A. Khan, “Security assessment through fuzzy Delphi analytic hierarchy process,” ICIC Express Letters, vol. 12, no. 10, pp. 1053–1060, 2018. [Google Scholar]
29. R. Kumar, S. A. Khan, A. Agrawal and R. A. Khan, “Measuring the security attributes through fuzzy analytic hierarchy process: Durability perspective,” ICIC Express Letters, vol. 12, no. 6, pp. 615–620, 2018. [Google Scholar]
30. M. T. J. Ansari, A. Baz, H. Alhakami, W. Alhakami, R. Kumar et al., “P-STORE: Extension of store methodology to elicit privacy requirements,” Arabian Journal for Science and Engineering, Article in Press, pp. 1–24, 2021. https://doi.org/10.1007/s13369-021-05476-z. [Google Scholar]
31. M. T. J. Ansari and D. Pandey, “An integration of threat modeling with attack pattern and misuse case for effective security requirement elicitation,” International Journal of Advanced Research in Computer Science, vol. 8, no. 3, pp. 1–21, 2017. [Google Scholar]
32. M. Zarour, M. Alenezi, M. T. J. Ansari, A. K. Pandey, M. Ahmad et al., “Ensuring data integrity of healthcare information in the era of digital health,” Healthcare Technology Letters, vol. 12, no. 6, pp. 615–620, 2021. [Google Scholar]
33. Cisco Team, “Cisco Annual Internet Report (2018–2023) White Paper,” Cisco, 2020. [Online]. Available: https://www.cisco.com/c/en/us/solutions/collateral/executive-perspectives/annual-internet-report/white-paper-c11-741490.html. [Google Scholar]
34. H. M. Lyu, W. H. Zhou, S. L. Shen and A. N. Zhou, “Inundation risk assessment of metro system using AHP and TFN-aHP in shenzhen,” Sustainable Cities and Society, vol. 56, no. 9, pp. 102–108, 2020. [Google Scholar]
35. R. Kumar, M. Zarour, M. Alenezi, A. Agrawal and R. A. Khan, “Measuring security durability of software through fuzzy-based decision-making process,” International Journal of Computational Intelligence Systems, vol. 12, no. 2, pp. 627–642, 2019. [Google Scholar]
36. A. Attaallah, M. Ahmad, M. Tarique, A. K. Pandey, R. Kumar et al., “Device security assessment of internet of healthcare things,” Intelligent Automation & Soft Computing, vol. 27, no. 2, pp. 593–603, 2021. [Google Scholar]
37. R. Kumar, A. I. Khan, Y. B. Abushark, M. M. Alam, A. Agrawal et al., “A knowledge-based integrated system of hesitant fuzzy set, AHP and TOPSIS for evaluating security-durability of web applications,” IEEE Access, vol. 8, no. 8, pp. 48870–48885, 2020. [Google Scholar]
38. R. Kumar, A. Baz, H. Alhakami, W. Alhakami, A. Agrawal et al., “A hybrid fuzzy rule-based multi-criteria framework for sustainable-security assessment of web application,” Ain Shams Engineering Journal, Article in Press, pp. 1–21, 2021. https://doi.org/10.1016/j.asej.2021.01.003. [Google Scholar]
39. F. A. Alzahrani, M. Ahmad, M. Nadeem, R. Kumar and R. A. Khan, “Integrity assessment of medical devices for improving hospital services,” Computers, Materials & Continua, vol. 67, no. 3, pp. 3619–3633, 2021. [Google Scholar]
40. R. Kumar, S. A. Khan and R. A. Khan, “Durable security in software development: Needs and importance,” CSI Communications, vol. 10, no. 10, pp. 34–36, 2015. [Google Scholar]
41. R. Kumar, S. A. Khan and R. A. Khan, “Revisiting software security risks,” Journal of Advances in Mathematics and Computer Science, vol. 11, no. 6, pp. 1–10, 2015. [Google Scholar]
42. W. Alosaimi, R. Kumar, A. Alharbi, H. Alyami, A. Agrawal et al., “Computational technique for effectiveness of treatments used in curing sars-cov-2,” Intelligent Automation & Soft Computing, vol. 28, no. 3, pp. 617–628, 2021. [Google Scholar]
43. R. Kumar, M. Zarour, M. Alenezi, A. Agrawal and R. A. Khan, “Measuring security durability of software through fuzzy-based decision-making process,” International Journal of Computational Intelligence Systems, vol. 12, no. 2, pp. 627–642, 2019. [Google Scholar]
44. K. Sahu, F. A. Alzahrani, R. K. Srivastava and R. Kumar, “Evaluating the impact of prediction techniques: Software reliability perspective,” Computers, Materials & Continua, vol. 67, no. 2, pp. 1471–1488, 2021. [Google Scholar]
45. R. Kumar, S. A. Khan and R. A. Khan, “Fuzzy analytic hierarchy process for software durability: Security risks perspective,” Advances in Intelligent Systems and Computing, vol. 508, pp. 469–478, 2017. [Google Scholar]
46. R. Kumar, M. T. J. Ansari, A. Baz, H. Alhakami, A. Agrawal et al., “A multi-perspective benchmarking framework for estimating usable-security of hospital management system software based on fuzzy logic, ANP and TOPSIS methods,” KSII Transactions on Internet and Information Systems, vol. 15, no. 1, pp. 240–263, 2021. [Google Scholar]
47. R. Kumar, S. A. Khan and R. A. Khan, “Revisiting software security: Durability perspective,” International Journal of Hybrid Information Technology, vol. 8, no. 2, pp. 311–322, 2015. [Google Scholar]
48. R. Kumar, S. A. Khan and R. A. Khan, “Analytical network process for software security: A design perspective,” CSI Transactions on ICT, vol. 4, no. 2, pp. 255–258, 2016. [Google Scholar]
49. R. Kumar, S. A. Khan and R. A. Khan, “Software security testing: A pertinent framework,” Journal of Global Research in Computer Science, vol. 5, no. 3, pp. 23–27, 2014. [Google Scholar]
50. K. Sahu and R. K. Srivastava, “Predicting software bugs of newly and large datasets through a unified neuro-fuzzy approach: Reliability perspective,” Advances in Mathematics: Scientific Journal, vol. 10, no. 1, pp. 543–555, 2021. [Google Scholar]
51. S. H. Almotiri, “Integrated fuzzy based computational mechanism for the selection of effective malicious traffic detection approach,” IEEE Access, vol. 9, no. 8, pp. 10751–10764, 2021. [Google Scholar]
 | This work is licensed under a Creative Commons Attribution 4.0 International License, which permits unrestricted use, distribution, and reproduction in any medium, provided the original work is properly cited. |