DOI:10.32604/cmc.2022.020585

| Computers, Materials & Continua DOI:10.32604/cmc.2022.020585 |  |
| Article |
Multi-Step Detection of Simplex and Duplex Wormhole Attacks over Wireless Sensor Networks
Self-Development Skills Department, Common First Year Deanship, King Saud University, Riyadh, KSA
*Corresponding Author: Abrar M. Alajlan. Email: aalajlan1@ksu.edu.sa
Received: 30 May 2021; Accepted: 20 July 2021
Abstract: Detection of the wormhole attacks is a cumbersome process, particularly simplex and duplex over the wireless sensor networks (WSNs). Wormhole attacks are characterized as distributed passive attacks that can destabilize or disable WSNs. The distributed passive nature of these attacks makes them enormously challenging to detect. The main objective is to find all the possible ways in which how the wireless sensor network’s broadcasting character and transmission medium allows the attacker to interrupt network within the distributed environment. And further to detect the serious routing-disruption attack “Wormhole Attack” step by step through the different network mechanisms. In this paper, a new multi-step detection (MSD) scheme is introduced that can effectively detect the wormhole attacks for WSN. The MSD consists of three algorithms to detect and prevent the simplex and duplex wormhole attacks. Furthermore, the proposed scheme integrated five detection modules to systematically detect, recover, and isolate wormhole attacks. Simulation results conducted in OMNET++ show that the proposed MSD has lower false detection and false toleration rates. Besides, MSD can effectively detect wormhole attacks in a completely distributed network environment, as suggested by the simulation results.
Keywords: Wireless sensor network; wormhole attack; node validation; multi-step detection
Many applications that use WSNs can be vulnerable to a wide range of security threats [1]. The sensors are strategically placed to monitor real-time events that may be utilized for a variety of business and domestic purposes. WSNs, on the other hand, have difficulties dealing with security risks [2]. Wormhole attacks, which have significant impacts on the network layer, are one of the biggest dangers. Wormhole attacks, according to research, can disrupt network routing, location-based wireless security, and data aggregation [3–6]. A wormhole attack can be launched by a single node or by a pair of cooperating nodes [7]. Because it may disrupt the network discretely, this attack is extremely difficult to detect [8]. Even if one does not understand the different cryptographic algorithms employed [9], it is usually caused by one or more nodes [10].
The consequences of a wormhole attack are quite severe [11]. For example, a wormhole-enabled node may conspire to falsify the routing configuration in order to obtain total control of the network traffic [12]. As a result, the nodes may disrupt processes that rely on topological proximity [13]. These attacks can also raise node power consumption by allocating various resources and transmitting excessive data [14]. Wormholes cannot be prevented using various cryptographic algorithms and cryptic keys since they just replay data packets that already exist in WSNs [15]. Because WSNs connected to IoT have various hardware flaws, solutions in range-free localization are more likely to seek cost-effective solutions [16,17]. The adoption of the DV-hop algorithm to avoid wormhole attacks is one example of a low-cost approach [18,19].
This paper presents a new scheme for the multi-detection of wormhole attacks to address these security concerns. The proposed scheme consists of the following three modules: neighbor node validation process (NNVP), fake link reduction process (FLRP), and wormhole isolation.
The NNVP determines whether or not the node is infected and whether or not it is a neighbor node. The links that originate from a wormhole are referred to as “false links”. These connections can be removed using the FLRP. Finally, the isolation module guarantees that the detection and recovery processes are carried out properly, isolating all traces and instances of the wormhole. This paper contributes as:
• The proposed MSD involves five detection methods, which can detect the successfully classified simplex and duplex wormhole attacks.
• MSD is supported with a valid locator detection feature, which can adjustably fine-tune a threshold value to make a sensor node easily to detect the valid locator(VL). Once VL is identified, then the detection process is used to determine the wormhole-enabled node for the WSN connected with IoT.
• MSD consists of a self-healing procedure that determines the wormhole attack and points to the positions of wormhole-enabled nodes.
• Secret key and signature generation processes are used to guarantee the secure communication process among the sensor node and adjacent sensor nodes or sensor node and base station.
This section explores into the key aspects of striking approaches. To detect and recover from wormhole attacks in multi-hop WSNs, the distributed self-healing method was suggested [20]. It also determines the locations of malicious nodes and separates them from the network. It is the first approach that carries out both routing organization recovery and wormhole node quarantine in response to wormhole attacks. However, it requires proper localization capabilities as well as time analysis. The proposed method relies solely on network connection in a distributed manner. The simulation results showed that the suggested technique detects all wormhole-enabled nodes with 100 percent accuracy and zero percent erroneous detection. In terms of power usage and overhead, the result also shows that the suggested technique outperforms other competing alternatives.
The cloned and wormhole node detection method is introduced in Maheswari et al. [21]. This method examines each node’s behavior to determine if it is a wormhole or not. If the node has not received authorization from the base, it is not permitted to participate in the communication. To solve the problem of wormhole and Grayhole attacks, the lightweight trust-driven approach was proposed [22]. The suggested method uses direct trust, which is determined based on the node's characteristics. It has also been utilized to establish indirect trust based on the perspectives of nearby sensor nodes. According to the authors, the suggested technique is energy efficient and would not add extra overhead to data flow.
The directional antennas are introduced to prevent wormhole attacks [23]. To avoid a wormhole, each node exchanges a secret key with its neighbors and maintains a current list of all neighbors. The direction in which a signal is heard from a neighbor is used to build all lists in a secure way, provided that all nodes antennas are aligned. However, it only mitigates the threat of wormhole attacks to a limited extent. It only protects against wormhole attacks, in which hostile nodes try to trick two nodes into thinking they are neighbors. In wireless sensor networks, the effects of wormhole attacks are widely examined utilizing IoT [24].
The authors proposed the label-based DV-hop localization method to defend against the possibility of wormhole attacks. Furthermore, the correctness of the approach is also proved using the simulation results.
DAWN: A Distributed detection algorithm is proposed for controlling the Wormhole in WSN [25]. The suggested method made an attempt to establish a lower constraint on efficient detection rate. The authors investigated the battle of DAWN against collusion and wormhole attacks. Furthermore, the suggested technique has no increased cost due to the use of additional testing messages. DAWN is supported by substantial experimental findings, as all existing wormhole detection techniques increase communication overhead and false negatives. The proposed technique, on the other hand, has a low communication overhead and a high accuracy rate.
3 Proposed Multi Detection Scheme
This section presents the proposed multi-detection scheme for detecting wormhole attacks. Thus, the data distribution process is of paramount vital before detecting the attacks. The Poisson distribution [26] has been used for the data distribution over the network. The data is available at different locations of a WSN. Each data location has a degree of self-sufficiency, is capable of handling local as well as global applications. Data distribution is shaped either by captivating a prevailing single location or excruciating it over different locations. The data uncertainty of data distribution can be computed as:
where
The proposed scheme consists of the three modules, which are discussed in the subsequent sections:
• Neighbor node validation process (NNVP),
• Fake link reduction process (FLRP),
• Wormhole isolation.
3.1 Neighbor Node Validation Process
For each type of wormhole attack detected, there are corresponding different identification protocols. They are as follows.
There are different types of wormhole attacks. They could be classified as either simplex or duplex wormhole attacks [27,28]. In this work, different detection processes have been applied to identify the wormhole attacks.
3.1.1 Duplex Wormhole Link Attack
To detect whether a network is experiencing the problem due to the duplex wormhole attack, the sensor node attempts to recognize all its Valid Locators (VLs) prior to the self-discovery process. Let us take
• The locator is within the range of transmission of the sensor node. Thus, the sensor node received three times message from
• The locator is not within the range of the sensor nodes’ transmission; then the sensor node receives the message twice from the as
• The locator is within the range of transmission of the sensor node, then the sensor node receives the message twice from the
The attacker node has a capability of changing the location in order to attack the legitimate node. Let us assume that distance between attacker and victim is symbolized as
where
When an attacker node knows that its position is exposed, then it attempts to update the position. However, the victim node can identify whenever an attacker moves away from there based on a random-change. Hence, if the random change is greater than 1 or less than −1 that provides the clue to the victim node. The moving process of the attacker node ‘
If the response time of victim node is faster then, it can identify the movement of an attacker node efficiently depicted in Fig. 1.
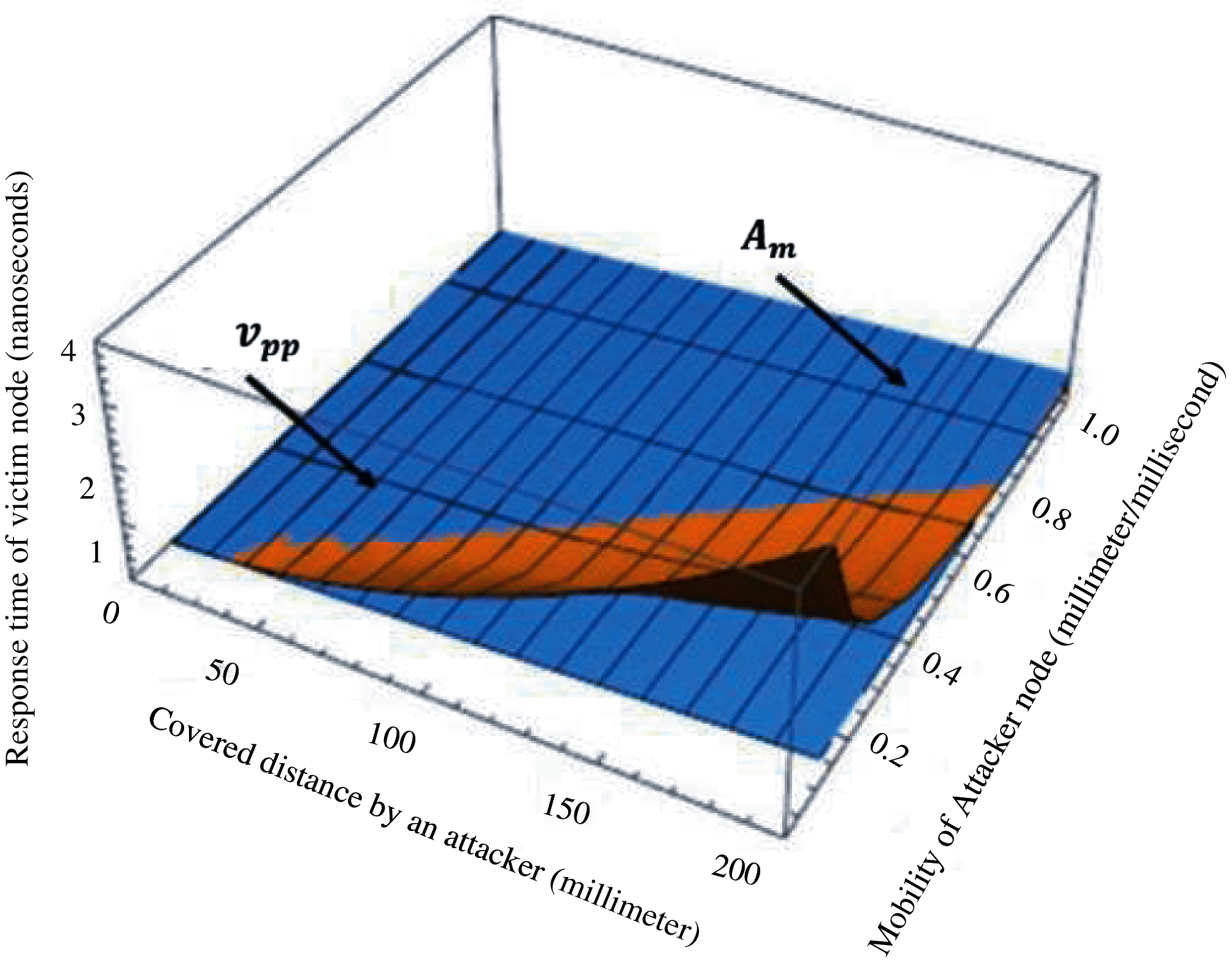
Figure 1: Response time of victim node
• Detection Process-1
In the first scenario, if the sensor node gets victim due to a wormhole attack and receives three times LAM of the Neighbor Locator (NL), then a bit of the LAM should be set to 1. Thus NL is declared as a VL that is shown as
In the second scenario, if the sensor node gets the LAM twice from the NL, then a bit of the LAM should be set to 1, and NL is considered as a Suspicious Locator (SL) such as
Definition 1: Data reiteration rate ‘
where
Definition 2: If the observation time for the sample-sending
where
In the third scenario, if the sensor node gets the LAM twice from the NL, then a bit of the LAM should be set to 0, and NL is regarded as the VL. Also, measured distance based on the LAM is considered as correct with the shorter response time as
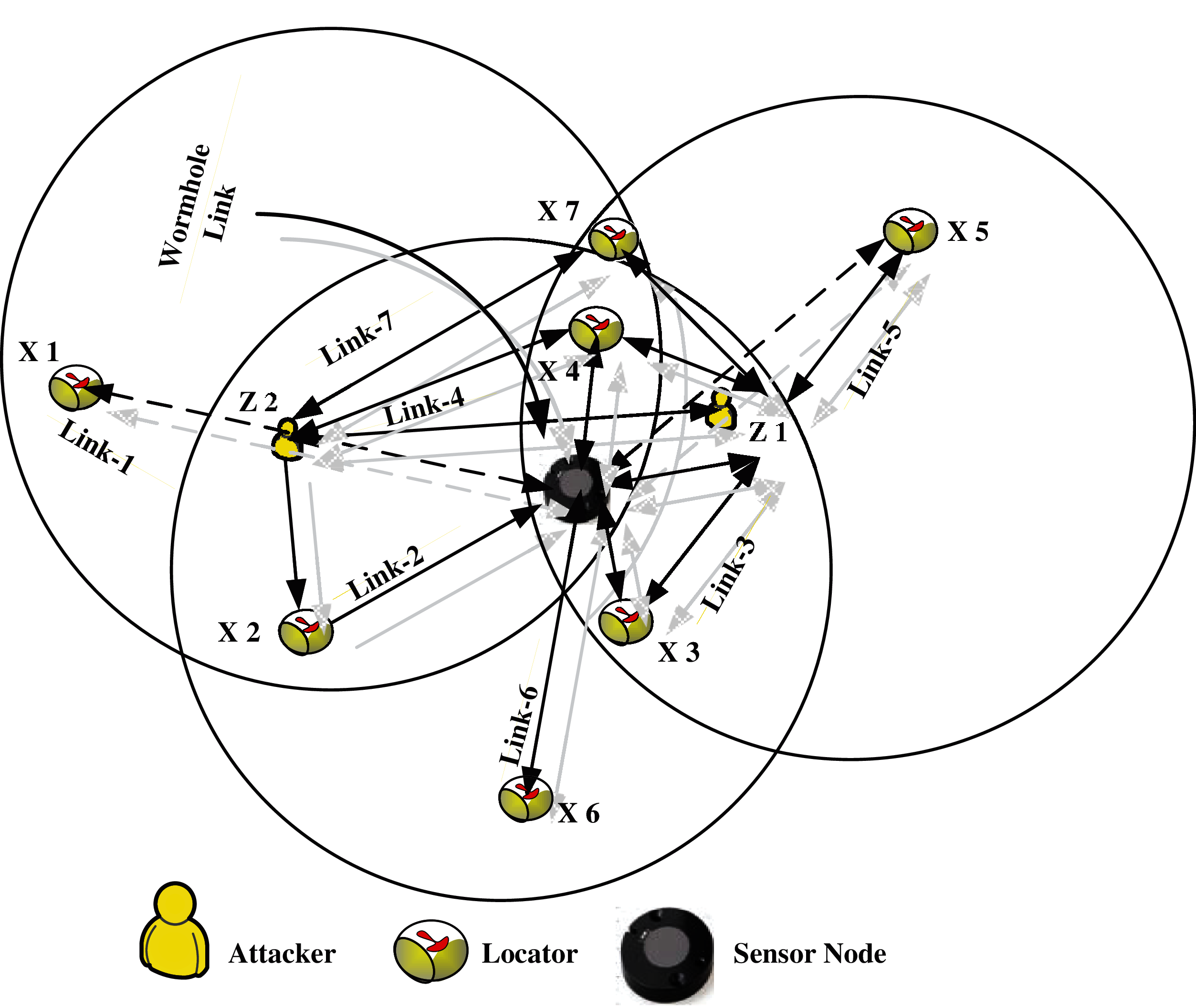
Figure 2: Showing Duplex wormhole attack process
Let us take a set of locators such that L = {(a1, b1), (a2, b2),…, (ap, bp)} and corresponding measured distances S = {l1, l2,…, Sp}, where (ai, bi) is the location ‘
The distance dependability property (DDP) of the legal locators demonstrates that the MSE of the estimated location is based on the exact distance that is smaller than a minimum threshold. On the other hand, the MSE of the estimated location is based on the distance that involves some inappropriate distance measurements that is not smaller than a threshold value. More VLs are detected using the DDP of the VLs.
• Detection Process-2
If the sensor node has detected not less than two VLs using Detection Process 1; thus, it detects other VLs by examining whether an estimated distance is dependable. A predefined threshold ‘
where
When a new locator joins the network, then it is of paramount significance to calculate the distance of the new locator ‘
where
The objective function is used to analyze the nature of the link, whether wormhole or not.
The sensor node initiates the detection process one by one for the uncertain locators (ULs). For example, to examine whether
Theorem 1: When a sensor node becomes victim due to duplex wormhole link attack,
Proof: When a sensor node is a victim due to duplex wormhole link attack as depicted in Fig. 1. All of the locations in
For each
Thus, the message cannot be advanced to wormhole link, and there is no anomaly for the interchange of the message interchange between
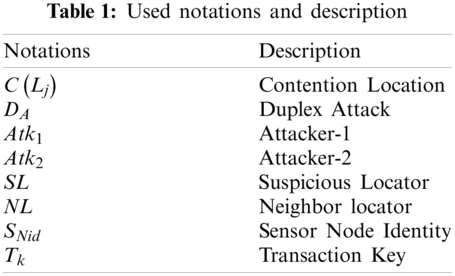
Tab. 1 shows the notations and their description.
3.1.2 Simplex Wormhole Link Attack
When the sensor node discovers the simplex wormhole attack, then it adopts the VLs’ detection processes.
• Detection Process-3
If the sensor node gets the victim due to simplex wormhole link attack as depicted in Fig. 2. If the sensor node receives the LAM of an NL twice, then that NL is considered as a VL. For example, if
Property 1: The sensor node is unable to get the messages from two NLs concurrently if the measured distance between these two NLs is larger than 2d.
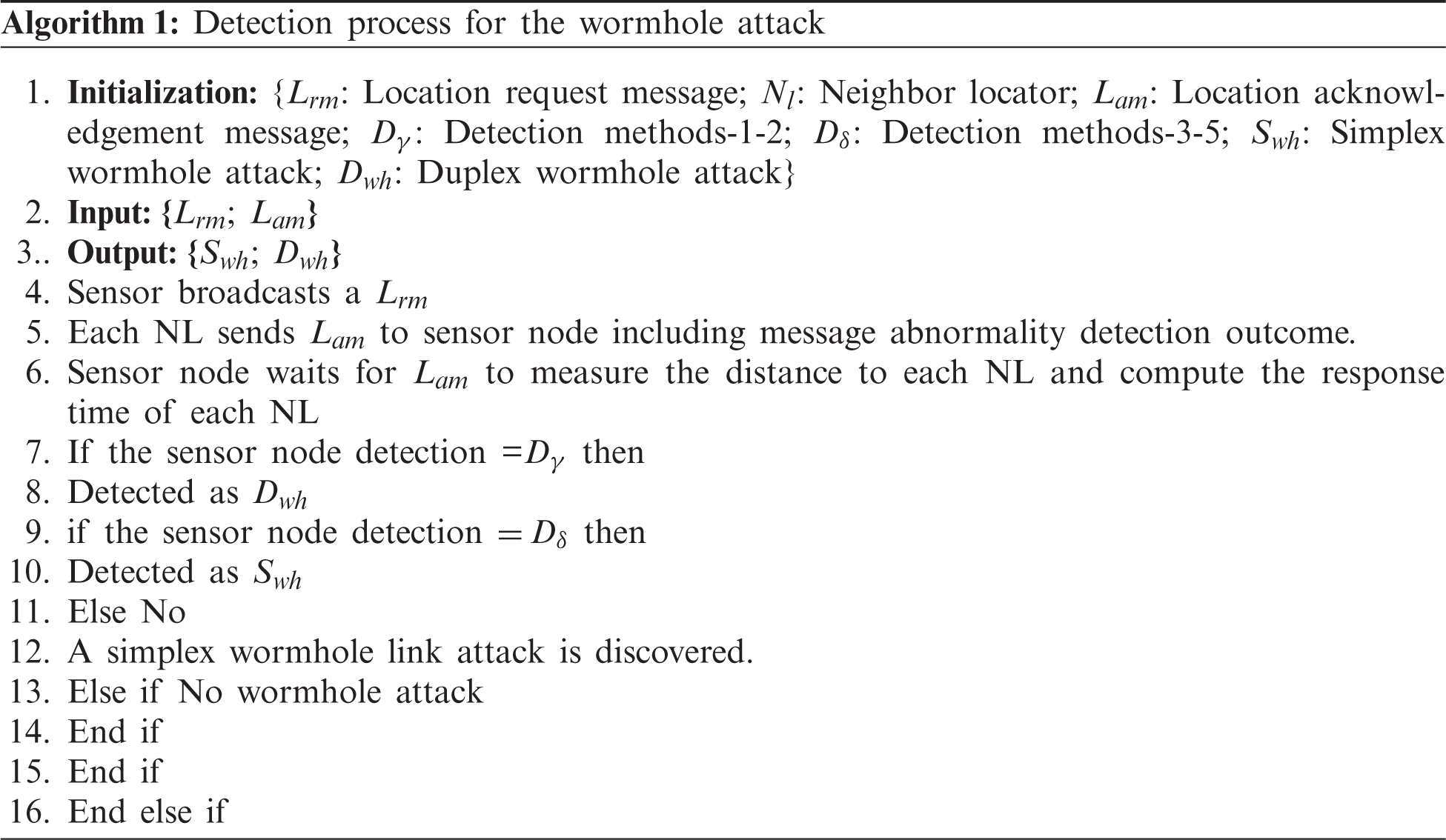
In Algorithm 1, the simplex and duplex detection processes are explained. In step-1, variables are initialized. Steps-2 provides the input. Step-3 gives the output. In step-4, the sensor node broadcasts the location request message. In step-5, each neighbor locator sends location acknowledgment message to the sensor node, including message irregularity detection result. In step-6, each neighbor locator sends the location acknowledgment message to measure the distance to each neighbor locator and computes the response time for each node locator. In step-7, if the sensor node detection methods fall within the category of dections: 1–2 methods, then the duplex wormhole method is observed. In step-8, if the sensor node detection methods fall within the category of detections; 3–5 methods, then the simplex wormhole method is observed. In step-9, if a sensor node is neither falling within the processes of
• Detection Process-4
When the sensor node becomes victim due to the simplex wormhole link attack as depicted in Fig. 2, if two NLs violate the spatial property, it is noticeable that one of them is a valid locator (VL) and explained in the Algorithm 2, and the other is a Suspicious Locator (SL). Let us take an example of
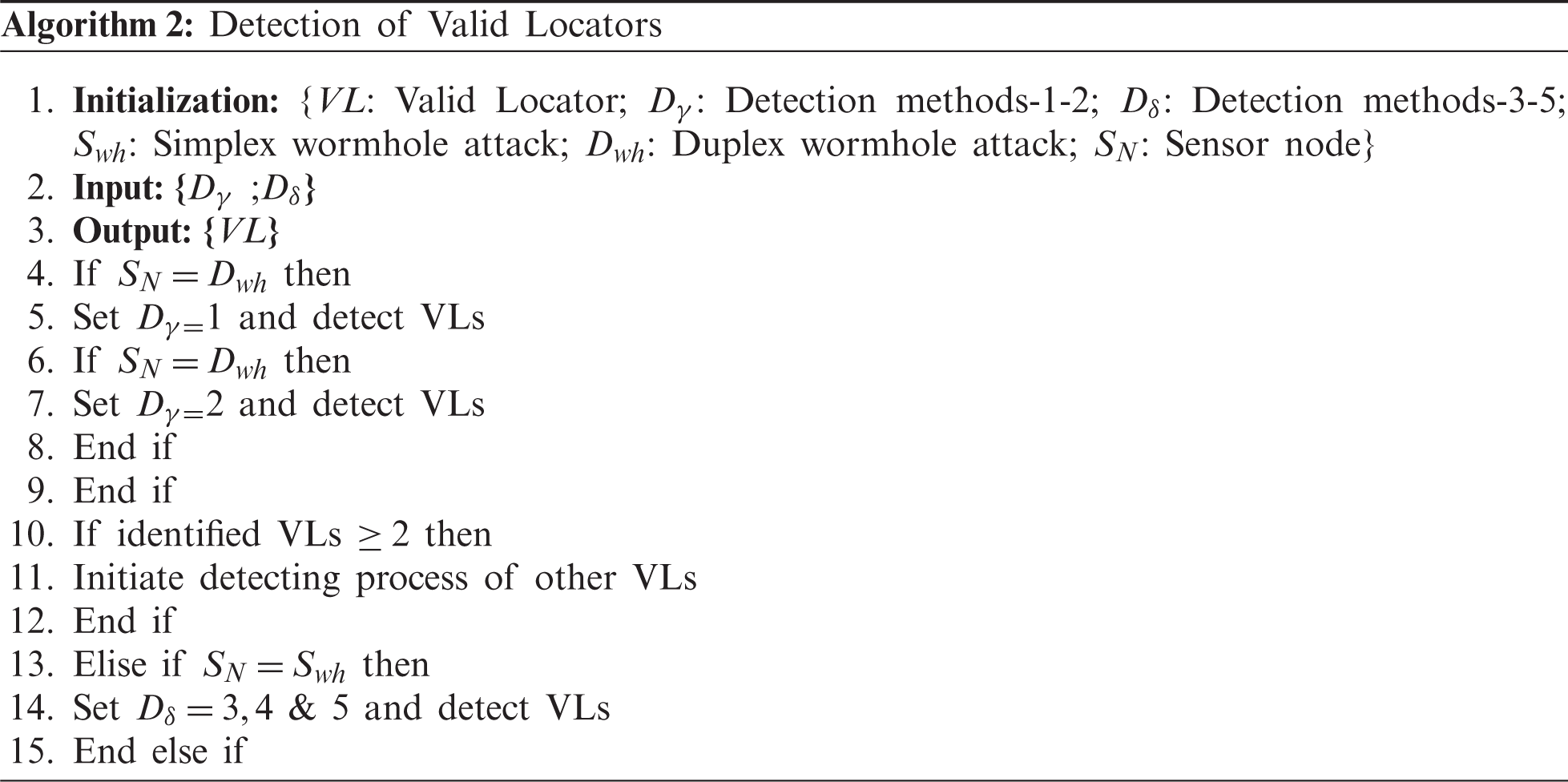
In Algorithm 2, the valid locators are identified. In step-1, variables are initialized. In steps-2–3, give the input and output. In steps-4–7, when the sensor node detects the duplex wormhole attack, then it initiates the ‘
Let us take a ‘
Let us take a ‘
For the data coming from each sensor node is evaluated for every event. As we get
• Detection Process-5
When the sensor node becomes the victim of the simplex wormhole attack, similar to Detection Process 2, if the sensor node uses detection processes 3–4 for detecting minimum two VLs, it can detect other VLs based on the Distance Consistency Property (DCP) of VLs. Considering the scenario of Fig. 3, the sensor node can detect
The procedure of the basic VLs detection approach is enumerated in Algorithm 2: When the sensor node gets a victim of the duplex wormhole link attack, then it needs to execute the detection Process 1 to determine the VLs. As the distance stability process requires at least three VLs, if the sensor node classifies no less than two VLs, it can use the detection process 2 to detect other VLs. In case if the sensor node becomes the victim due to simplex wormhole link attack, then it adopts the detection processes 3–4 to identify the VLs. After that, if at least two VLs are identified, the sensor node executes the detection process 5 to identify other VLs.
3.2 Prolonged Node Validation Process
In the basic VL detection process, if the sensor node detects less than three VLs, it terminates the self-localization. This occurs because the statistical method of maximum likelihood estimation (MLE) used in the self-localization needs at least three distance measurements. However, when using detection processes based on the distance consistency property of V-locators, many VLs cannot be determined due to the threshold of MSE,
A prolonged valid locators’ identification approach is used to handle the above problem. The proposed approach can adaptively adjust the threshold value of
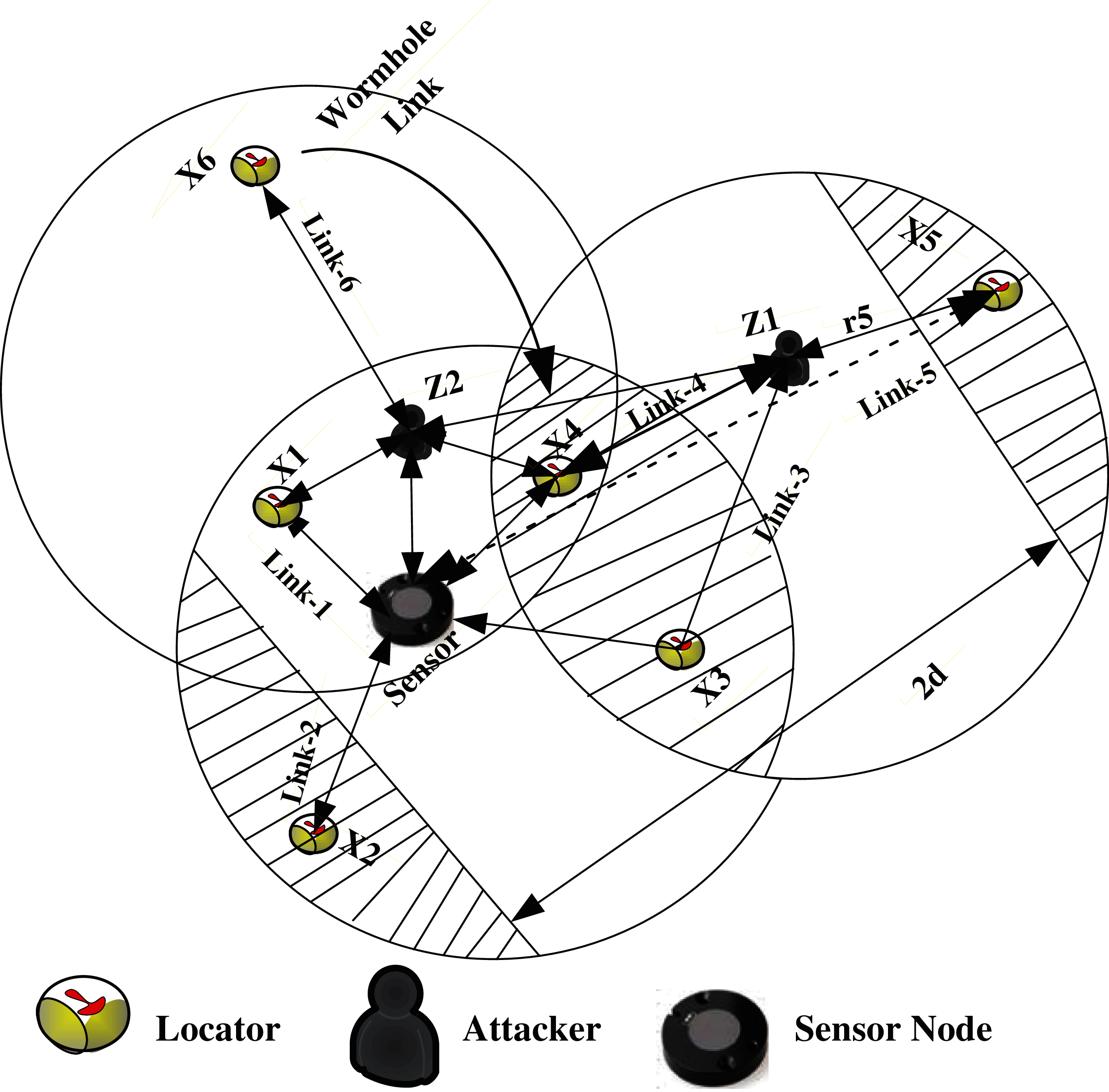
Figure 3: Showing Simplex wormhole attack process
After the wormhole link attack detection and VLs’ identification, the sensor node can detect VLs from its NLs. Furthermore, the sensor node can calculate the accurate distance for the VLs. If the sensor node gets minimum three correct measured distances to its NLs, it performs the Maximum Likelihood Estimation (MLE) localization process based on the locations and distances of the associated NLs.
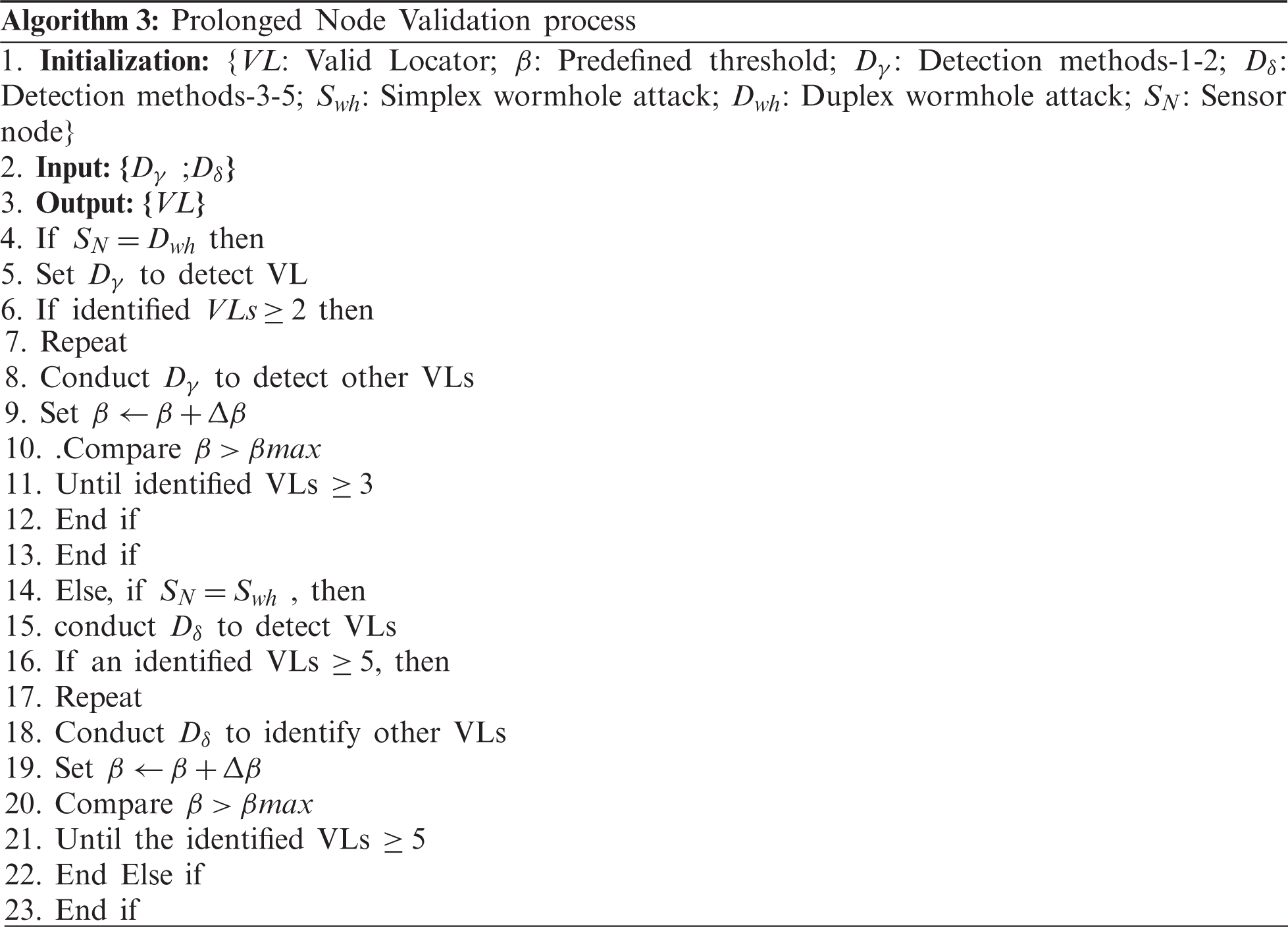
In Algorithm 3, the Prolonged node validation process is explained. In step-1, used variables are initialized. Steps-2–3 specify the input and output. Steps-4–5 shows the detection process of the duplex wormhole link attack conducted by the sensor node; then it initiates to conduct the detection process-1 to identify the VLs. In steps-6–7, the value of the identified VLs is compared; if identified VLs are greater than or equal to 2, then this process will be continued until determine for the rest of the detection methods. The steps-8–9 show the process of detecting other VLs; then the threshold value is set by adding the maximum threshold value and incremental of a predefined threshold value.
In steps-10–13, the predefined threshold value is compared with the maximum incremental predefined threshold value; this process continues until an identified VLs are greater than or equal to 3. In steps-14–20, the sensor node detects the simplex wormhole attack, then the detection process of valid locators is begun. By applying the detection methods 3–5, then other valid locators are determined. Finally, the threshold values are set in order to identify all the valid locators.
3.3 Secret Key and Signature Generation Process
The sensor nodes are tiny, and their data sending process is vulnerable. Thus, the proposed approach wants to secure the data communication process. Hence, the secret key is generated for sending the data confidentially. In addition, the signature is created to validate the sent message.
3.3.1 Secret Key Generation Process
When the sensor node interacts either with an adjacent sensor node or the base station, then it requires to generate the secret key for interacting and sending the data.
Let us assume that the sensor node ‘
For
where
3.3.2 Signature Generation Process
The signature must be calculated, and the sensor node obtains the received file ‘
where
The sensor node computes the pair of the signature
First, Calculating two hash value as:
Once two hash values are calculated, then start a file of secret sharing
Finally, compute the number of the random variables ‘
where
Therefore, the signature generation process is secure that also supports the sensor nodes to avoid impersonation and identity attacks.
To validate the effectiveness of the proposed MSD approach, the simulation is conducted using OMNET++ 5.6.2 simulator. Based on the simulation results, the performance of MSD approach has been analyzed and compared with existing state-of-the-art schemes: Hybrid Algorithm to Eliminate Wormhole Attack (HAW) [20], Dynamic Detection and Prevention (DDP) [21], and Wormhole and Gray attack (WGA) [22]. The sensor nodes are distributed randomly to serve the data sending process. The deployed sensor nodes are connected using the end-to-end reliable and bi-directional approach.
The main goal of the simulation is to balance the bandwidth usage and proper data exchange. Several scenarios (Malicious and Non-Malicious) are generated to conclude the realization of the proposed approach. The simulation scenarios resemble the tangible WSN situation. The given outcomes demonstrate alike to a realistic environment. The simulation network consists of
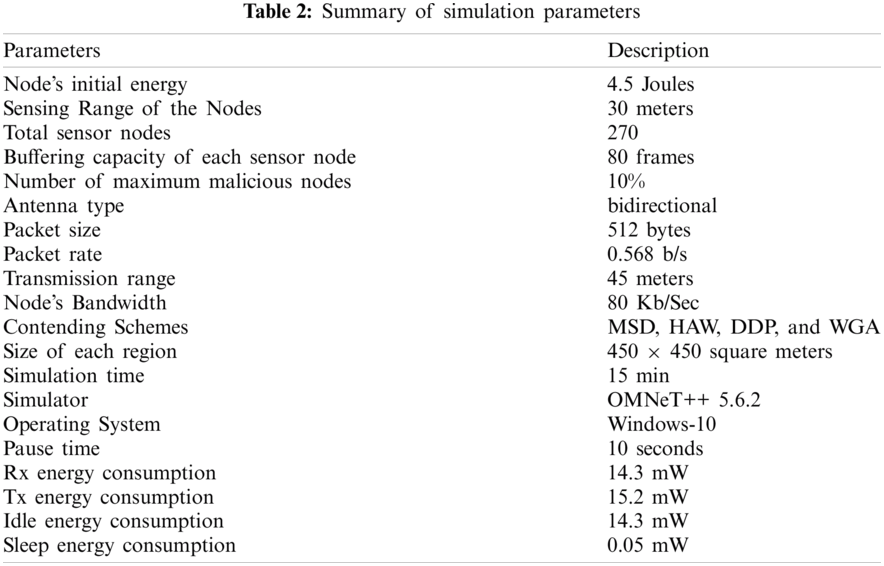
Based on simulation outcomes, the following metrics have been achieved.
• Accuracy
• Detection (false negative, true positive and false positive)
Accuracy requires both precision and authenticity. Fig. 4 shows the accuracy of the proposed MSD and other contending schemes (HAW, DDP, and WGA). The accuracy of the proposed approach and contending approaches has been measured using the variable number of valid sensor nodes up to maximum 180 with the 10% malicious sensor nodes. The result demonstrates that the MSD produced a maximum of 99.93% accuracy. Whereas other contending schemes produced 98.74%--99.47%.
When the number of sensor nodes increase then, accuracy is marginally affected with 10% malicious nodes. The results demonstrate that proposed MSD obtain 99.904% accuracy with 270 sensor nodes. Whereas, the contending approaches obtain the accuracy 97.9%--98.6% with 270 sensor nodes. HAW produced less accuracy with 270 sensor nodes as shown in Fig. 5. The testing procedure involves true negative, and true positive. Thus, the accuracy is given by:
where
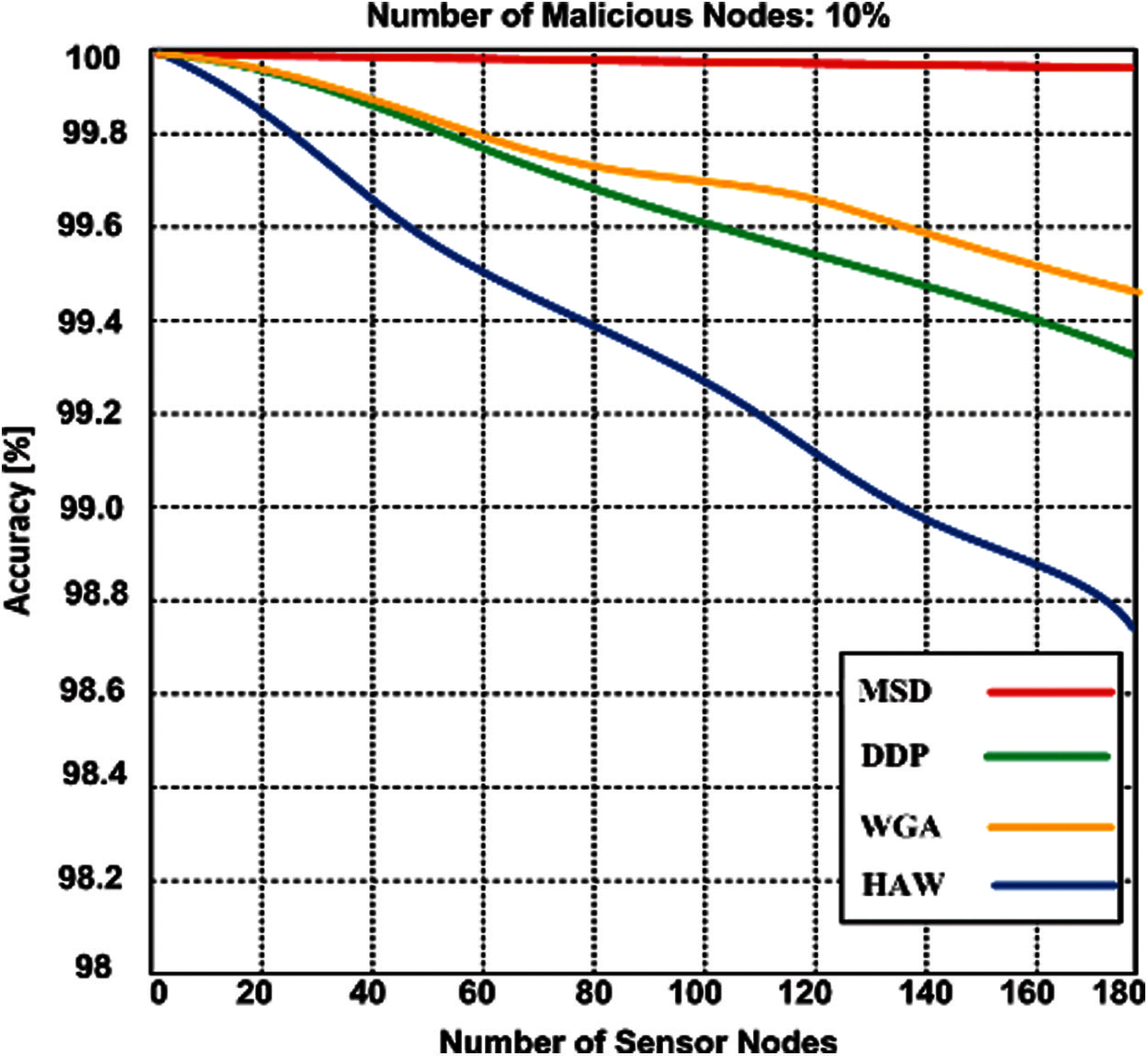
Figure 4: Accuracy of proposed MSD and contending with 180 nodes
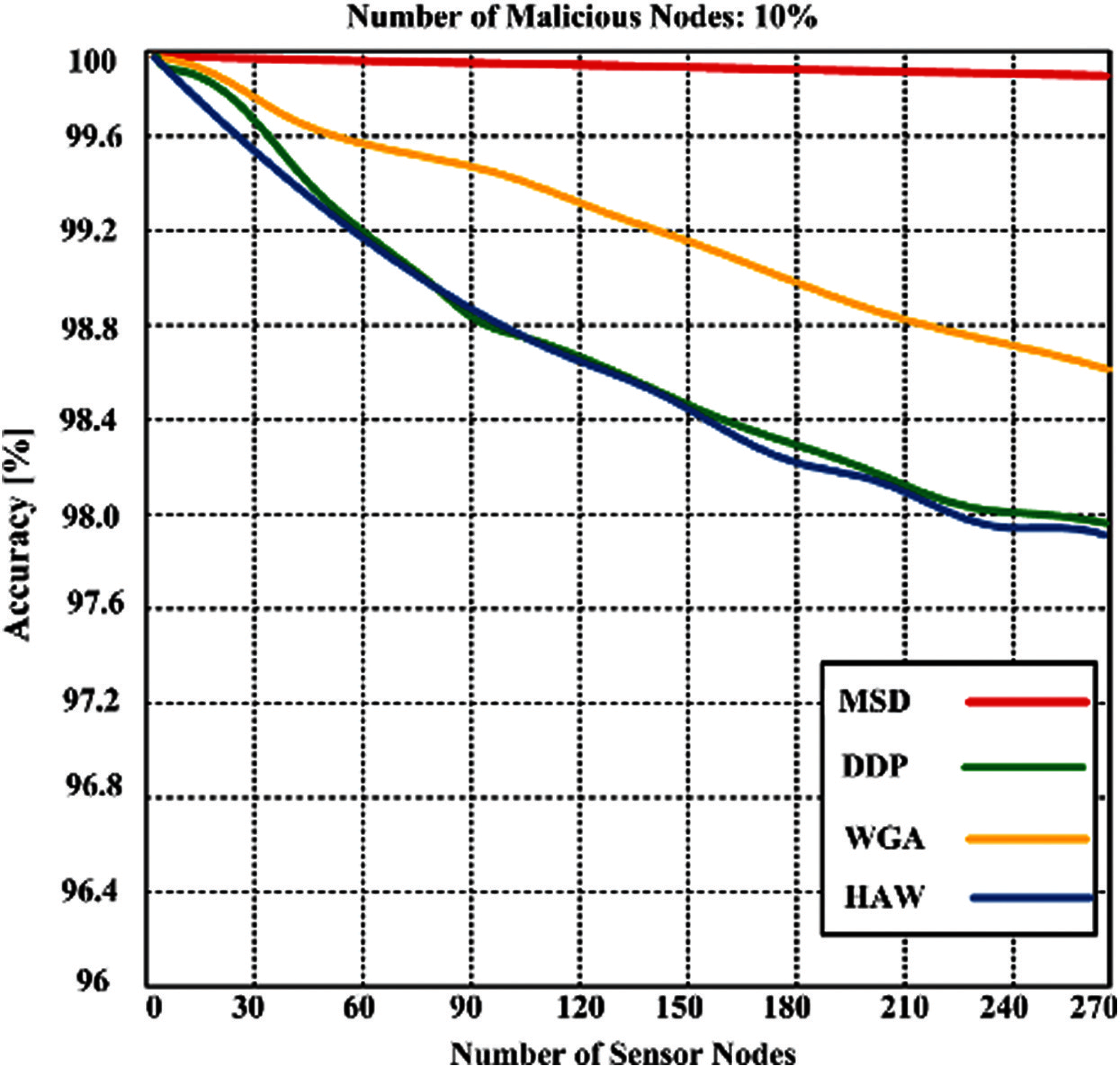
Figure 5: Accuracy of proposed MSD and contending HAW, DDP, and WGA with 270 sensor nodes
The reason behind better accuracy for the proposed approach is to use five detection methods and secret key and signature generation processes that determine the precise true negative and true positive successfully.
4.2 Detection (True Positive, False Negative and False Positive)
The proposed MSD and contending schemes (HAW, DDP, and WGA) have been measured using False-positive ‘
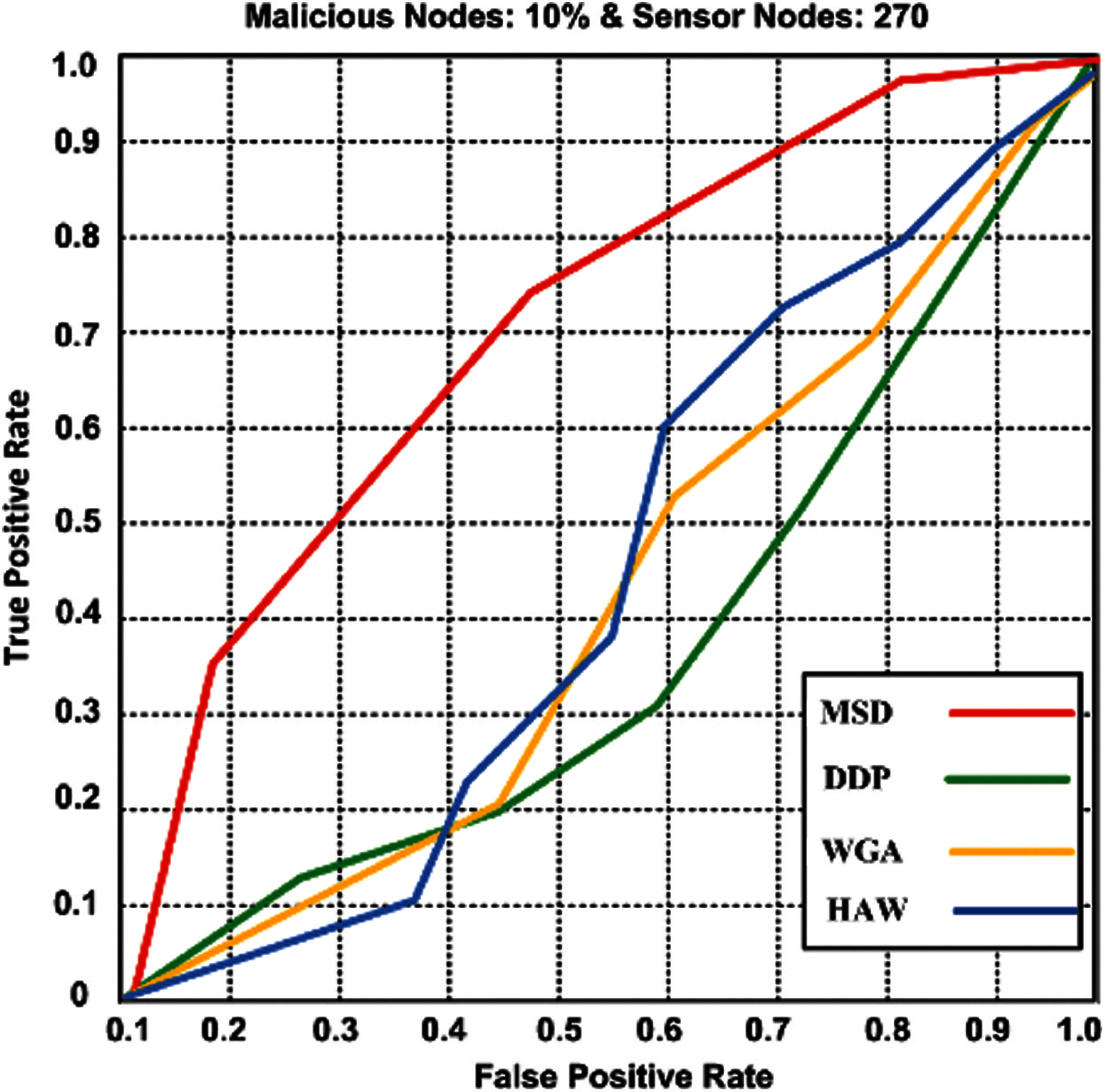
Figure 6: False positive rate and true positive rate for proposed MSD and competing schemes (HAW, DDP, and WGA)
The trend of the result in the graph demonstrates that the proposed MSD gets a higher true positive rate, and only 0.015 false-negative rates are detected, while contending schemes show the higher false-negative rate that is counted as 0.023–0.072. MSD gains the higher false-negative rage that is measured to be 0.072. Based on the outcomes, it has been confirmed that the proposed scheme attains the true higher positive and gains lower false-negative rates. Thus, true positive, false positive and false negative rates can be calculated using Eqs. (17)–(19).
where
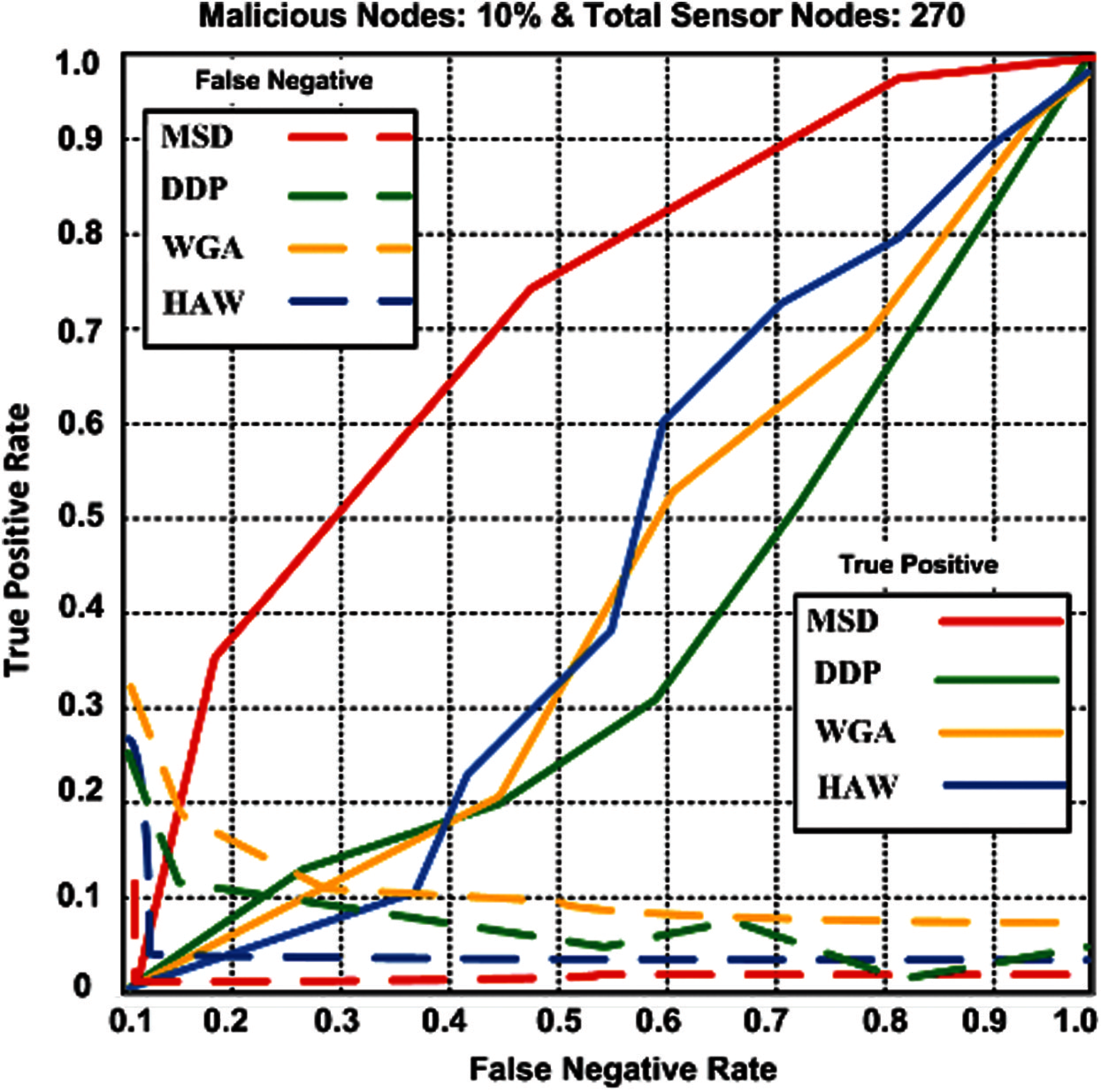
Figure 7: False negative rate and true positive rate for proposed MSD and competing schemes (HAW, DDP, and WGA)
A new multi-detection scheme has been executed for detecting the wormhole attacks in WSNs over the distributed environment. In the proposed scheme, different integrated detection modules implemented to systematically detect, recover, and isolate wormhole attacks. In this multi-step detection (MSD) scheme, the neighbor node validation process plays a crucial role in identifying the infected nodes and the false neighbors. In addition, the proposed MSD can be used to eliminate all fake links (i.e., the links which originate from a wormhole). Finally, the performance of isolation module ensured that detection and recovery are highly effective and thereby isolates the wormhole completely from the network. To support the proposed scheme, different algorithms were executed that provide specific details of how exactly each component (e.g., Wormhole attack detection scheme and Extended Node Validation process) of the proposed scheme was effectively detected and successfully recovered the network inside the distributed environment. Current limitations on assessing after the rerouting and rescheduling in real time traffic management for the detection model should be taken into consideration towards further research. In future, attacks in integrated network scenarios around the distributed environment will be evaluated through non-traditional algorithms for optimum desirability to detect and recover the WSN from the wormhole attacks.
Acknowledgement: This research was supported by the Deanship of Scientific Research, King Saud University, Kingdom of Saudi Arabia.
Funding Statement: The author received no specific funding for this study.
Conflicts of Interest: The author declares that she has no conflicts of interest to report regarding the present study.
1. P. P. Devi and B. Jaison, “Protection on wireless sensor network from clone attack using the SDN-enabled hybrid clone node detection mechanisms,” Computer Communications, vol. 152, pp. 316–322, 2020. [Google Scholar]
2. Bharat Bhushan and Gadadhar Sahoo, “Requirements, protocols, and security challenges in wireless sensor networks: An industrial perspective,” in Handbook of computer networks and cyber security. Cham: Springer, pp. 683–713, 2020. [Google Scholar]
3. O. R. Ahutu and H. El-Ocla, “Centralized routing protocol for detecting wormhole attacks in wireless sensor networks,” IEEE Access, vol. 8, pp. 63270–63282, 2020. [Google Scholar]
4. R. Bhatt, P. Maheshwary, P. Shukla, P. Shukla, M. Shrivastava et al., “Implementation of fruit fly optimization algorithm (FFOA) to escalate the attacking efficiency of node capture attack in wireless sensor networks (WSN),” Computer Communications, vol. 149, no. 2, pp. 134–145, 2020. [Google Scholar]
5. H. Kalkha, H. Satori and K. Satori, “Preventing black hole attack in wireless sensor network using HMM,” Procedia Computer Science, vol. 148, no. 1, pp. 552–561, 2019. [Google Scholar]
6. K. Spurthy and T. N. Shankar, “An efficient cluster-based approach to thwart wormhole attack in adhoc networks,” Int. Journal of Advanced Computer Science and Applications, vol. 11, no. 9, pp. 312–316, 2020. [Google Scholar]
7. S. Deshmukh-Bhosale and S. S. Sonavane, “A real-time intrusion detection system for wormhole attack in the RPL based internet of things,” Procedia Manufacturing, vol. 32, pp. 840–847, 2019. [Google Scholar]
8. P. Kaliyar, W. Ben Jaballah, M. Conti and C. Lal, “LiDL: Localization with early detection of sybil and wormhole attacks in IoT Networks,” Computers & Security, vol. 94, 2020. [Google Scholar]
9. X. Li, J. Zheng, S. Liu and T. Zhu, “A novel wormhole-like mesoporous hybrid MnCoOx catalyst for improved ethanol catalytic oxidation,” Journal of Colloid and Interface Science, vol. 555, pp. 667–675, 2019. [Google Scholar]
10. J. Govindasamy and S. Punniakody, “A comparative study of reactive, proactive and hybrid routing protocol in wireless sensor network under wormhole attack,” Journal of Electrical Systems and Information Technology, vol. 5, no. 3, pp. 735–744, 2018. [Google Scholar]
11. G. Kumar, M. Kumar Rai and R. Saha, “Securing range free localization against wormhole attack using distance estimation and maximum likelihood estimation in wireless sensor networks,” Journal of Network and Computer Applications, vol. 99, pp. 10–16, 2017. [Google Scholar]
12. M. Panic, C. Hernandez, E. Quinones, J. Abella and F. J. Cazorla, “Modeling high-performance wormhole NoCs for critical real-time embedded systems,” in Proc. RTAS, Vienna, Austria, pp. 1–12, 2016. [Google Scholar]
13. C. Lee and J. Suzuki, “SWAT: A decentralized self-healing mechanism for wormhole attacks in wireless sensor networks,” in Handbook on Sensor Networks, Hackensack, NJ, USA: World Scientific, pp. 511–532, 2010. [Google Scholar]
14. K. Dong, D. Zhu and A. Daniel Hill, “Mechanism of wormholing and its optimal conditions: A fundamental explanation,” Journal of Petroleum Science and Engineering, vol. 169, no. 1, pp. 126–134, 2018. [Google Scholar]
15. Panwar Pratyush, Rohan Verma, M. M. S. Rauthan and Varun Barthwal, “An overview on security issues, attacks, challenges and protocols in WSN,” in Proc. of Integrated Intelligence Enable Networks and Computing, Gopeshwar, India, pp. 269–278, 2021. [Google Scholar]
16. N. Labraoui, M. Gueroui and M. Aliouat, “Secure DV-Hop localization scheme against wormhole attacks in wireless sensor networks,” Transactions on Emerging Telecommunications Technologies, vol. 23, no. 4, pp. 303–316, 2012. [Google Scholar]
17. P. Shukla, “ML-IDS: A machine learning approach to detect wormhole attacks in internet of things,” in Proc. IntelliSys, London, UK, pp. 234–240, 2017. [Google Scholar]
18. M. S. Ahsan, M. N. M. Bhutta and M. Maqsood, “Wormhole attack detection in routing protocol for low power lossy networks,” in Proc. ICICT, Karachi, Pakistan, pp. 58–67, 2017. [Google Scholar]
19. X. Wang, F. Hu, C. Zhai, Y. Zhang, X. Su et al., “Research on improved DV-HOP algorithm against wormhole attacks in WSN,” in Proc. ITA, Les Ulis, France, vol.7, 2016. [Google Scholar]
20. Asmita Singh, Atul Kumar Sah, Arun Singh, Bhavnesh Jaint and S. Indu, “Wormhole Attack Detection in Wireless Sensor Network Using SVM and Delay Per-hop Indication,” in Data Engineering and Communication Technology. Singapore: Springer, pp. 39–47, 2021. [Google Scholar]
21. P. U. Maheswari and P. G. Kumar, “Dynamic detection and prevention of clone attack in wireless sensor networks,” Wireless Personal Communications, vol. 94, no. 4, pp. 2043–2054, 2017. [Google Scholar]
22. R. Mehta and M. M. Parmar, “Trust based mechanism for securing IoT routing protocol RPL against wormhole & grayhole attacks,” in Proc. I2CT, Pune, India, pp. 1–6, 2018. [Google Scholar]
23. L. Hu and D. Evans, “Using Directional Antennas to Prevent Wormhole attacks,” in Proc. NDSS, San Diego, CA, USA, pp. 1–11, 2004. [Google Scholar]
24. H. Chen, W. Lou, Z. Wang, J. Wu, Z. Wang et al., “Securing DV-Hop localization against wormhole attacks in wireless sensor networks,” Pervasive and Mobile Computing, vol. 16, no. 2, pp. 22–35, 2015. [Google Scholar]
25. S. Ji, T. Chen, S. Zhong and S. Kak, “DAWN: Defending against wormhole attacks in wireless network coding systems,” in Proc. INFOCOM, Toronto, ON, Canada, pp. 664–672, 2014. [Google Scholar]
26. L. Dümbgen and J. A. Wellner, “The density ratio of poisson binomial versus poisson distributions,” Statistics & Probability Letters, vol. 165, 2020. [Google Scholar]
27. Patel Manish, Akshai Aggarwal and Nirbhay Chaubey, “Analysis of wormhole attacks in wireless sensor networks,” in Recent Findings in Intelligent Computing Techniques. Singapore: Springer, pp. 33–42, 2018. [Google Scholar]
28. M. Patel, A. Aggarwal and N. Chaubey, “Analysis of wormhole attacks in wireless sensor networks,” in Recent Findings in Intelligent Computing Techniques, vol. 708. Singapore: Springer, pp. 33–42, 2018. [Google Scholar]
 | This work is licensed under a Creative Commons Attribution 4.0 International License, which permits unrestricted use, distribution, and reproduction in any medium, provided the original work is properly cited. |