DOI:10.32604/cmc.2022.020146

| Computers, Materials & Continua DOI:10.32604/cmc.2022.020146 |  |
| Article |
Hesitant Fuzzy-Sets Based Decision-Making Model for Security Risk Assessment
1Department of Information Systems, Faculty of Computing and Information Technology, King Abdulaziz University, Jeddah, 21589, Saudi Arabia
2Department of Computer Science, Faculty of Computing and Information Technology, King Abdulaziz University, Jeddah, 21589, Saudi Arabia
3Department of Information Technology, Babasaheb Bhimrao Ambedkar University, Lucknow, 226025, Uttar Pradesh, India
4Department of Computer Applications, Shri Ramswaroop Memorial University, Lucknow-Deva Road, Barabanki, 225003, Uttar Pradesh, India
*Corresponding Author: Asif Irshad Khan. Email: aikhan@kau.edu.sa
Received: 10 May 2021; Accepted: 11 June 2021
Abstract: Security is an important component in the process of developing healthcare web applications. We need to ensure security maintenance; therefore the analysis of healthcare web application's security risk is of utmost importance. Properties must be considered to minimise the security risk. Additionally, security risk management activities are revised, prepared, implemented, tracked, and regularly set up efficiently to design the security of healthcare web applications. Managing the security risk of a healthcare web application must be considered as the key component. Security is, in specific, seen as an add-on during the development process of healthcare web applications, but not as the key problem. Researchers must ensure that security is taken into account right from the earlier developmental stages of the healthcare web application. In this row, the authors of this study have used the hesitant fuzzy-based AHP-TOPSIS technique to estimate the risks of various healthcare web applications for improving security-durability. This approach would help to design and incorporate security features in healthcare web applications that would be able to battle threats on their own, and not depend solely on the external security of healthcare web applications. Furthermore, in terms of healthcare web application's security-durability, the security risk variable is measured, and vice versa. Hence, the findings of our study will also be useful in improving the durability of several web applications in healthcare.
Keywords: Web applications; security risk; security durability; hesitant-based decision-making approach
The web application development team faces many challenges in improving the functionality of healthcare web application security. Moreover, tech businesses are also looking for a viable method for enhancing the security of healthcare web applications. To effectively contain the various security threats, especially for the healthcare web applications, the practitioners keep changing their strategies to manage the security of the web applications in use. . However, risk is a threat that has particular objectives and can interrupt well-defined methods [1–3]. The procedures that are used to manage and minimise the security risk protect the healthcare web application and also help in maximizing the efficacy as well as the functionality of the application. In this context, the Risk management technology helps in risk reduction practices in the healthcare web application development process [4–5]. This technology includes security monitoring, mitigating, and maintaining which are interconnected procedures, integrated into the security design during the healthcare web application development process.
Major research work has been carried out for managing security risk [6,7]. For implementing effective security risk management procedures, it is important to handle a variety of security risks during the healthcare web application's development process. To achieve better results, all processes must be modified. To identify and minimize risks for strategic risk management, the entire healthcare web application life cycle is used. In line with the policy and oversight included in the assessment of healthcare web application security, risk management mechanisms have varying prominence; for example, they are not the results of criteria such as costs and schedules but are important components of security risk management.
This point of view has not been taken into account in the past, but it is necessary today to use the concept of integrated security. A simpler and added modernized security performance monitoring approach is risk recognition and security management systems [8,9]. Combined risk management processes use strategies and practical approaches for enhancing the security performance. In this row, the practitioners have made efforts to address and analyse different methodologies of healthcare web application security. Such an analysis helps in identifying the existing research gaps in the quest to design more secure-durable healthcare web applications.
Notably, ‘compromise in designing’ has originated as one of the topmost severe security threats in several cases. It has been observed that the practitioners tend to speed up the design process to reduce “time-to-market”. This means that security is not designed into a healthcare web application but remains a mere external addition, thus weakening the security. The security risk can be well-defined as the potential for failure or harm if a threat compromises susceptibility. The development team usually relies on risk management expertise and skills without sufficient risk management frameworks.
Security must be the core focus of the designers while developing the healthcare web applications. In this row, as cited by Rodriguez et al. [10], three foundations of a secure healthcare web applications that need to be prioritised are: managing security risk framework, information, and touch points. Therefore, if one wishes to enhance healthcare web application's security, management procedures of security risk are one of the key issues to focus upon.
With previous methods, characteristics quantification is very difficult during the security risk management process. Sahu et al. [11] have indicated that to evaluate the real security of any healthcare web application, adequate assessment, which is itself a very complex procedure, is essential. Kaur et al. [12] have divided the fuzzy methods into two significant forms during security risk assessment: conceptual and traditional methods concerning fuzzy sets. For managing the security risk of the healthcare web application, many multi-criteria decision-making methods are generally addressed by practitioners because the security management process is a decision-making problem [13,14].
By using hesitant fuzzy sets, this article evaluated the healthcare web application security risks at the design phase. Schiefer [15] has employed fuzzy sets in the security risk management process. Kumar et al. [16] used the hierarchical analysis representation method of security risk to construct an empirical security risk assessment procedure. The term hesitant fuzzy has been used by some researchers to describe the procedure of ambiguity and analytical hierarchy process to determine the importance of different characteristics during healthcare web application development [17]. The security techniques, including hierarchical characterization and acceptance, were also investigated by some other researchers [8,12]. Nevertheless, with the aid of the hesitant fuzzy-based AHP-TOPSIS technique, the authors of the current research work have not found any study that emphasizes upon assessing the impact of security risk to enhance the security of healthcare web applications. That is why our research work assessed the impact of several security risk characteristics at the design phase through the hesitant fuzzy-based AHP-TOPSIS technique.
The remainder of this research work is structured as follows: The paper outlines the identification and evaluation of security risk of healthcare web applications in Section 2. Section 3 addresses the hesitant fuzzy-based AHP-TOPSIS technique and the effect of healthcare web application security risks has been assessed. Section 4 concludes this study.
2 Risk Scenario of Healthcare Web Application
The digitalization of the healthcare industry has created a huge platform for attackers who can attain valuable information from many sources and blackmail or sell this information to the buyers. In the context of the proposed paper on the durability and management of security in healthcare web applications, it is very significant to introduce the basic risks plots and situation of attacks in the healthcare domain for a better overview of a topic. A thorough understanding of the current attack trends would help in identifying effective solutions. The authors observed that the attack ratio of penetrators and hacking incidents in a healthcare organizations increased by 25% in 2020. 29 million medical records were breached in 2020 alone. Another study on attack source classification for healthcare organizations discloses that a total of 642 data breach incidents were reported in 2020 and 66.82% of breaches [18] were specifically caused by hacking and vulnerability exploitation in web platforms. A descriptive representation of incidents and their sources is discussed in the following Fig. 1.
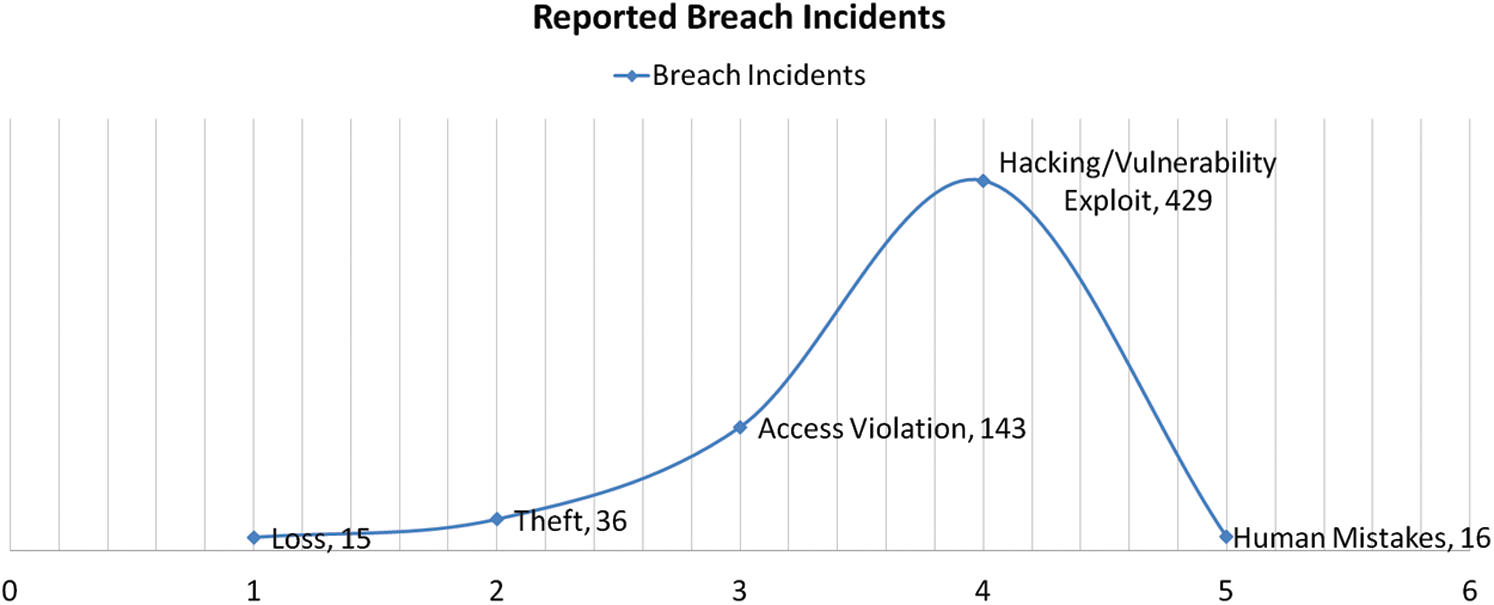
Figure 1: Healthcare reported breach incidents statistics along with their source
The above statistics portray that vulnerability exploitation is the major cause of breach incidents and issues in the healthcare organizations. This graphical representation of 2020 statistics portrays an immense need for a standardized mechanism or procedure for managing security in digital platforms of healthcare. Moreover, a report on cyber security concerns for healthcare industry discusses that approximately $125 billion are going to be spent on security services and hardware by 2025 [19]. This huge investment prediction shows the market concerns and security issues in the healthcare domain. Thus, the demand and the need for managing the security for functionality of digital platforms cannot be overstated. This can be done more corroboratively from the design phase itself. Addressing this possibility, the proposed article works on a simplified and feasible procedure which can be adapted by the researchers aiming at enhancing the security-durability of the web applications; the same has been discussed in following headings.
3 Healthcare Web Application Security Risks at Design Phase
The security designer is not inherently the best person to perform security risk estimation, because risk management itself requires technical expertise. Thorough risk estimation relies on awareness of financial impacts, including knowledge of laws, regulations, and the business model sustained by a healthcare web application. The practitioners develop certain assumptions about their systems’ risks and the security experts help to test those assumptions at a reasonable level. However, all the effective techniques of security risk analysis have different advantages and disadvantages. Inspite of their best efforts, the practitioners are often unable to address the constraints that arise due to any technique, thus compromising the security of the web application and also hampering its functionality. In this context, it is important to relate traditional security risk principles to the healthcare web application design. This would help in mapping clear mitigation requirements that separate a noteworthy risk assessment from a mere average assessment process of a healthcare web application. A high-level tactic to adaptive security risk analysis will be fully combined into the development process of healthcare web applications [4]. Risk management of information security has become a vital activity. Security engineering has become important for everybody from initial education to fundamental engineering to progress into the twenty-first century. Since threats are everywhere, the healthcare web application must be extremely secure due to huge investments and users’ reliance on the development process of healthcare web applications [11].
The developers of the healthcare web application should be well aware of the core of the security threats because the vulnerabilities and threats can have a momentous impact on time and costs entailed in the development process. Security threat recognition and their causes during the healthcare web application development process can also assist the practitioners in taking preliminary steps to counter these threats. It has been stated that the assessment of security risks by machine computing can considerably enhance the life span of the security of the healthcare web application. For a more effective and accurate procedure, our study identifies the key security threats that the designers must focus on and calculates the effect of these by using the hesitant fuzzy-based AHP-TOPSIS approach. The critical security risks that have been selected in this research work are based on the associated security characteristics. It has become a prerequisite for a secure healthcare web application development process to address security characteristics including access control, confidentiality, authentication, honesty, etc. Particularly, nowadays, when the users are mainly worried about the security of their data, the developers’ primary responsibility is to address this effectively. In this research study, therefore, the authors have filtered the healthcare web application security risks that may penetrate from the Common Vulnerabilities Enumeration (CWE) list into the program at the design stage [4,6]. CWE is a group that promotes the development of secure healthcare web applications by providing a list of all potential vulnerabilities in any web application. By offering a standard for detection and mitigation of different healthcare web application vulnerabilities, it acts as a security tool. As defined by the researchers, the key design-level security risks have been demonstrated in Tab. 1. Fig. 2 shows the security risks at the design phase. Further, Fig. 3 shows the relationship between security threats and security characteristics along with the concept of security risk.
Figure 2: Healthcare web application security risks at the design phase
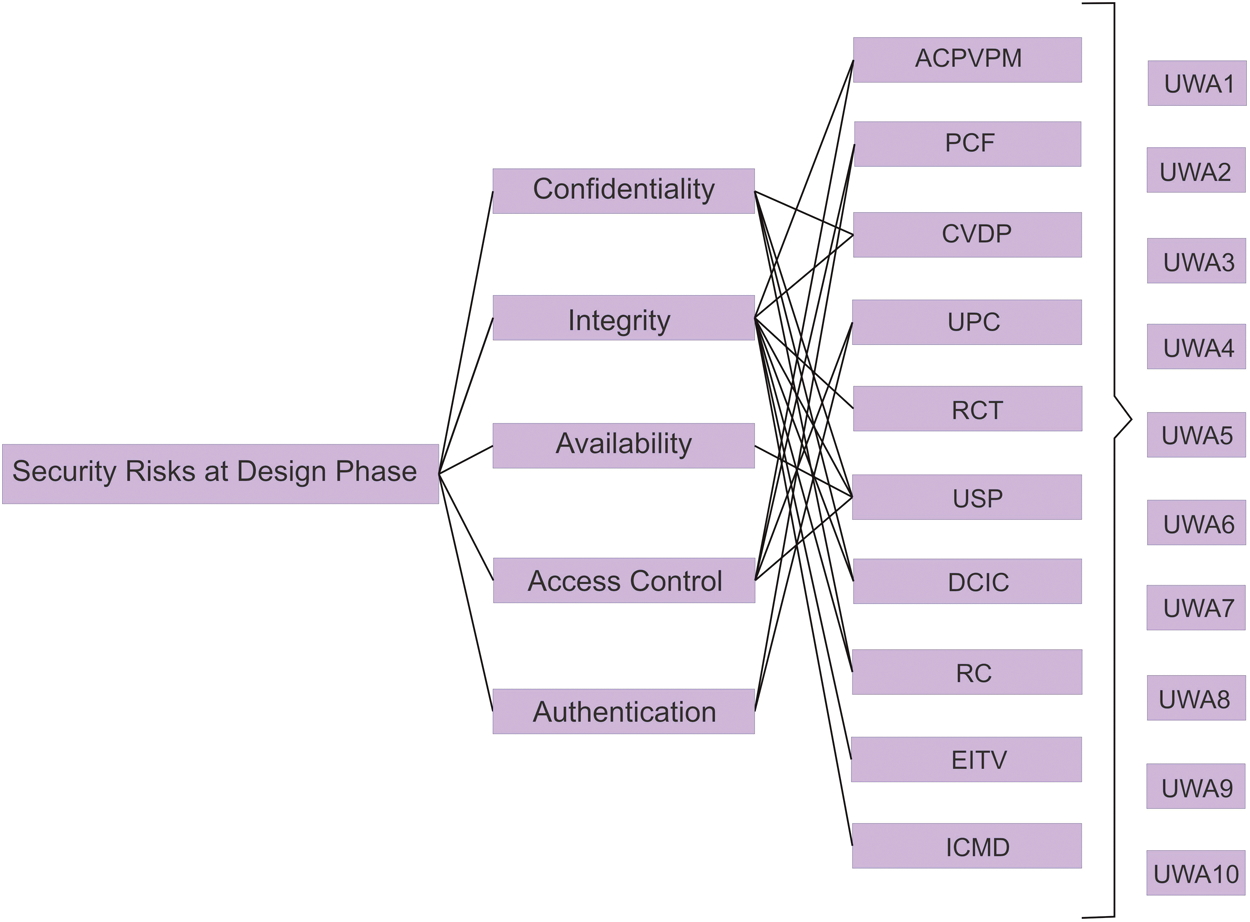
Figure 3: Healthcare web application security risk attributes concerning security durability
Some real-world issues demand unique or multi-choice-based solutions that are crucial for the users to choose the best from several options without any solid base. To tackle this situation and give an ideal quantitative solution to these issues, the adopted MCDM approaches are implemented by various researchers [12–14]. Specifically adopted AHP approach combined with a fuzzy set theory is more effective and simple in comparison of others. This is evident from various previous research initiatives [15–17]. If there is more than one option available for evaluation in the technique during the computation process, then this situation influences the calculated results even more strongly. In the context of the proposed article, the authors adopt a hesitant fuzzy set-based MCDM approach that gives an extra efficiency in results in the perspective of assessment. Besides, the TOPSIS approach has been used to assess the risk impact of healthcare web application security. Moreover, to get more productive and accurate results, this study adopts the hesitant fuzzy-based TOPSIS approach. For testing the evaluated results, the adopted methodology of TOPSIS is the most appropriate approach available among the MCDM approaches. The biggest advantage of this methodology is that it gives a positive impact as well as negative impact and deliberates it in the calculation.
In our research, HF-AHP methods were enlisted to assess the priority of the security risk factors, and then we tested their approach HF-TOPSIS on alternatives for similar factors [5]. A step-by-step procedure, in brief, is deliberated below:
Step 1: The first step in the implemented approach is the hierarchy development of factors.
Step 2: In Tab. 2, examiners use linguistic terminology to create accurate and beneficial assessment criteria for the decision-makers.
Step 3: The next step in technique evaluation is the adoption of fuzzy wrappers [8] from Eq. (1).
Same as experts evaluate the trapezoidal numbers
After imposing the Eqs. (3)–(5), the experts decide the first and second form of weights η, i.e., the number between [0, 1] and Eqs. (6) and (7) applied by the experts to obtain these numbers.
1st type weights
2nd type weights
The numerical form for the highest rank in the formula
Step 4: Eqs. (8) and (9) are used by the experts after evaluating the entire previous approach to satisfy the remaining comparison matrix attributes. Thereafter, the experts use Eq. (10) to defuzzify the matrix to determine the comparison matrix.
Step 5: The phase of defuzzification provides correct values. The experts examine the Consistency Ratio (CR) by applying the Eqs. (11) and (12) to analyse the CR of these values.
Step 6: In this step, by Eq. (13), the experts assess the geometrical mean of the values.
Step 7: The most significant criterion in the entire set is evaluated by experts by applying the Eq. (14).
Step 8: Examiners analyze the defuzzified values by Eq. (15).
Step 9: By applying the Eq. (16), experts transform the defuzzified values into normalized values or weights.
Now after identifying priority list for selected attributes the second adopted methodology of TOPSIS is used for testing the effectiveness of obtained results. TOPSIS is effective as a MADM technique in recommending the most preferred option for use. The definition of the TOPSIS approach was presented by Torra et al. [14]. The synthesis of positive and negative ideas is the TOPSIS methodology; the most accurate and effective option is the most precise and reliable factor. The worst option, on the other hand, is an irrelevant factor. The authors utilized the hesitant fuzzy AHP TOPSIS approach to test and assess the security risk of healthcare web application [15–17]. The TOPSIS method associates the distance between two linguistic values such as H1s and H2s and performs its computations. Below, the procedure has been clarified (Eq. (17)):
• Step 10: The following terms are described as the starting process:
The following written formulas are applied as
• Similarly, k is used to show the numeric count of experts in TOPSIS e_x d enotes the experts.
• The equation
• The standards are written for TOPSIS to determine the criteria and effect of outcomes:
The standard for TOPSIS evaluation lies in between very poor and very good scale,
For HF matrix, the following formulas are used [9]:
Step 11: By applying the Eq. (18) formula, the associated combined matrix is created:
Step 12: The effective factor where most effective factor is indicated by Aj, is shown by alpha in the TOPSIS evaluation, and alpha shows the cost-related preferences. In addition, the latest efficient alternatives need high precision for cost related preferences. The following Eqs. (19)–(22) are used to define and compare cost as well as effective factors:
Step 13: Experts evaluate TOPISIS +ve and -ve concepts components by applying following Eqs. (23), (24).
Step 14: Experts build and assess the closeness of positive and negative factors evaluated by Eqs. (25) and (26).
where
Step 15: The ranks are allocated to conclude the process, and the tabular form of options are focused on their assessment of effectiveness.
In further parts of this study, a highly detailed and evaluated numerical assessment of security risk has been conducted for improving the life span of healthcare web application security.
This sub-section addresses numerous statistical results from the implementation of the integrated hesitant fuzzy-based AHP-TOPSIS method [8]. To evaluate the impact of security risk, the experts generally conduct behavior-based risk research. It is essential to recognize and characterize uncertain behaviors from large sets of signs of execution to accomplish this. The security practitioners face a daunting challenge of numerically analyzing the impact of risk. For a more simplified approach, we have used a recognized and authenticated decision-making tactic, the hesitant fuzzy-based combined methodology of AHP-TOPSIS, to achieve the goals. In the current cybersecurity environment, this hybrid method is suitable for prioritizing malware analysis techniques based on their impact assessment.
The authors of the present research work acquired opinions from 110 security practitioners from numerous sectors of education and development industries to generate a more comprehensive result. For our empirical investigations, the data outsourced from these specialists were gathered. T1, T2, T3, T4, and T5, respectively, reflect the different characteristics for assessing the security risk at the early stage of the healthcare web application development process including access control, availability, authentication, confidentiality, and integrity. To evaluate the impact of the above-mentioned security risks on various healthcare web applications signified by UWA1, UWA2, UWA3, UWA4, UWA5, UWA6, UWA7, UWA8, UWA9, and UWA10.0, the systemic tactic of hesitant fuzzy-based AHP-TOPSIS is employed.
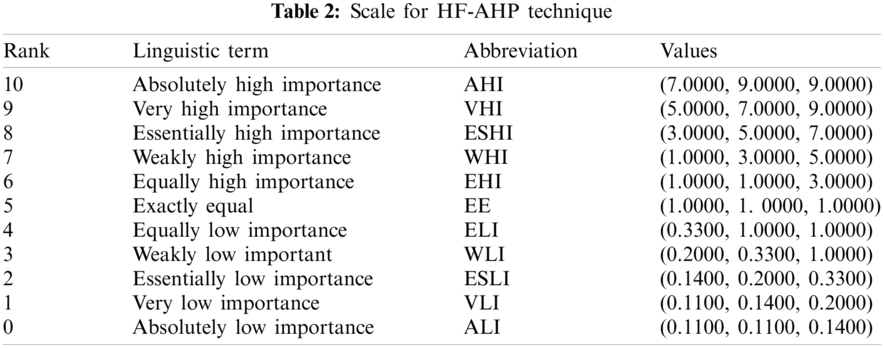
As shown in Tab. 3, the pair-wise comparative matrix of the characteristics at level 1 is built with the help of [8]. Likewise, with the help of [9], as displayed in Tabs. 4–7, the composite pair-wise comparative matrix for level 2 has been gathered. In this research work, the authors adopted the alpha cut method for defuzzification process and Tabs. 8–12 show the calculations and local weights of the characteristics. Further, final weights of the characteristics through the hierarchy are shown in Tab. 13. In addition, Tabs. 14 and 15 displays the description of the observations, the normalised fuzzy-decision matrix and weighted normalised fuzzy-decision matrix, respectively, with the help of terminology [16]. A combination to calculate the weight of the characteristic of each point is carried out to be more detailed. In addition, Tab. 16 and Fig. 4 show, with the aid of the hierarchy, the closeness coefficients at the desired level among the various alternatives and [9].
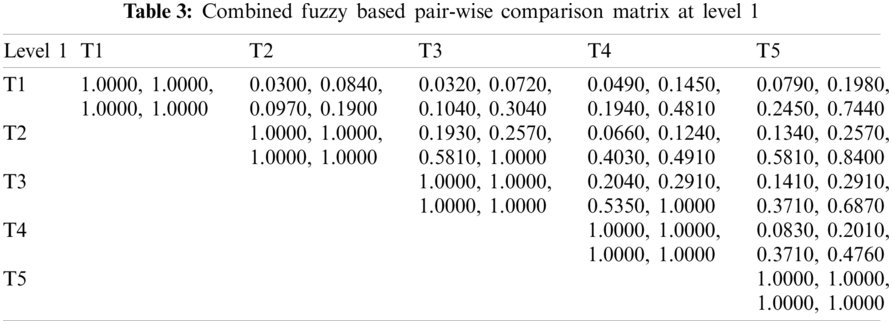
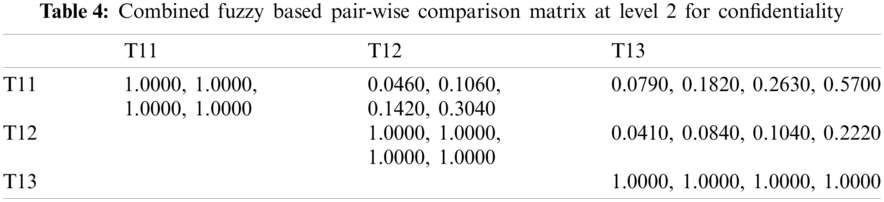
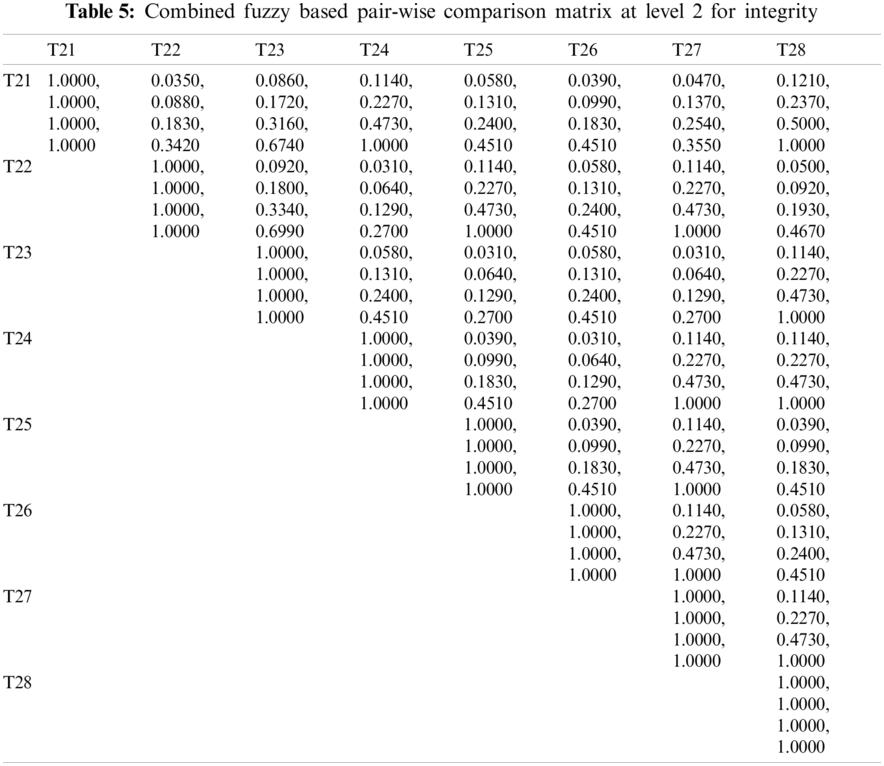
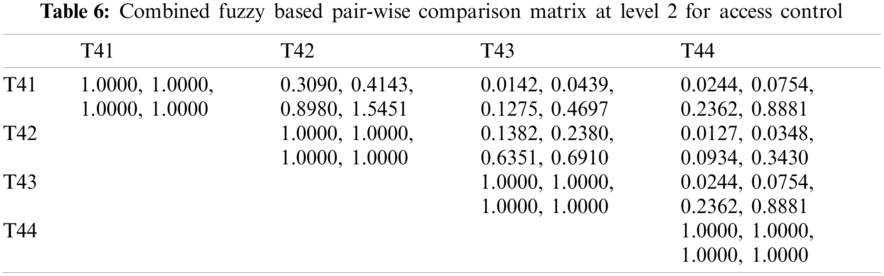
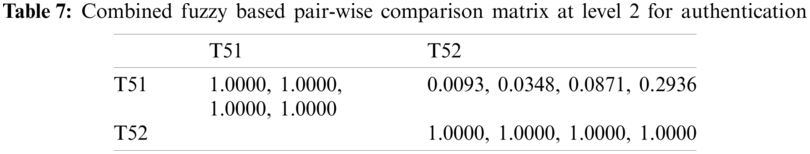
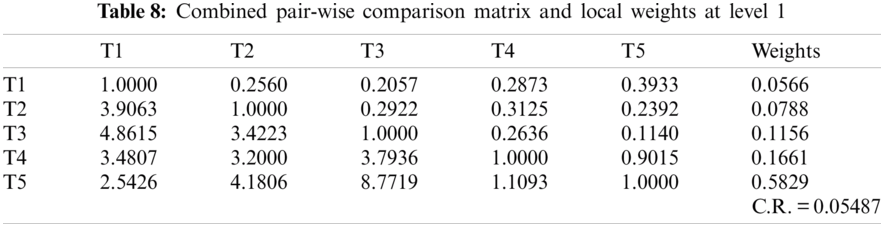

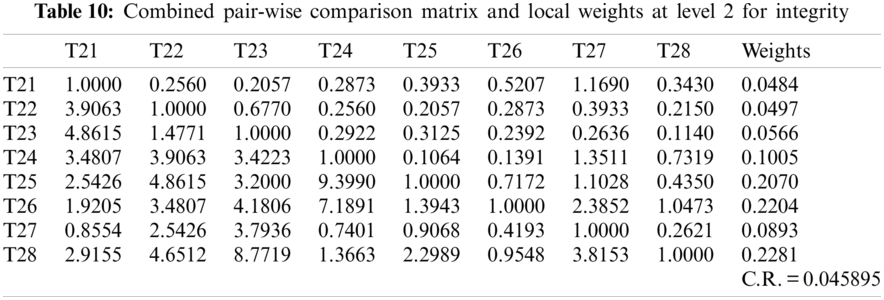
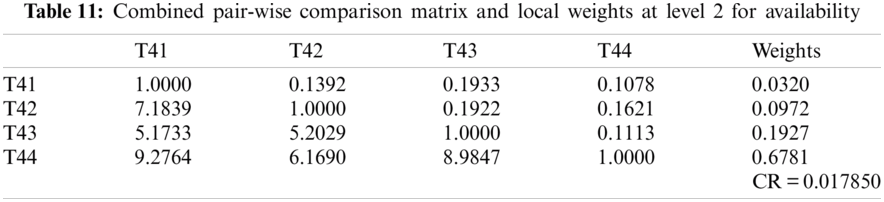
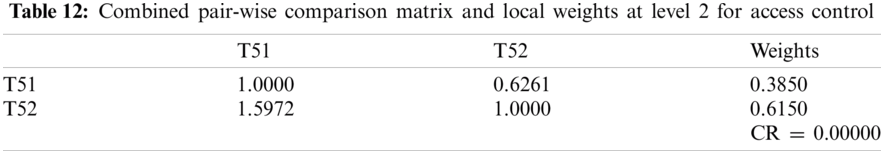
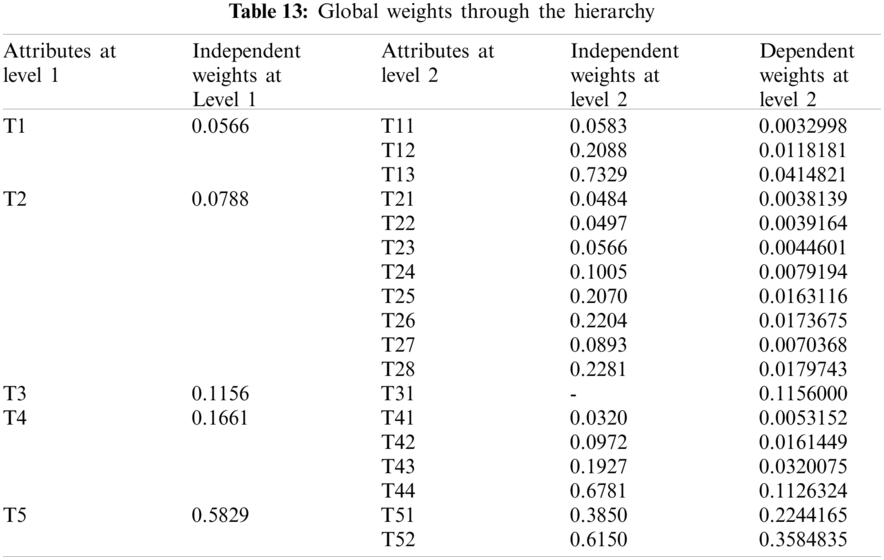
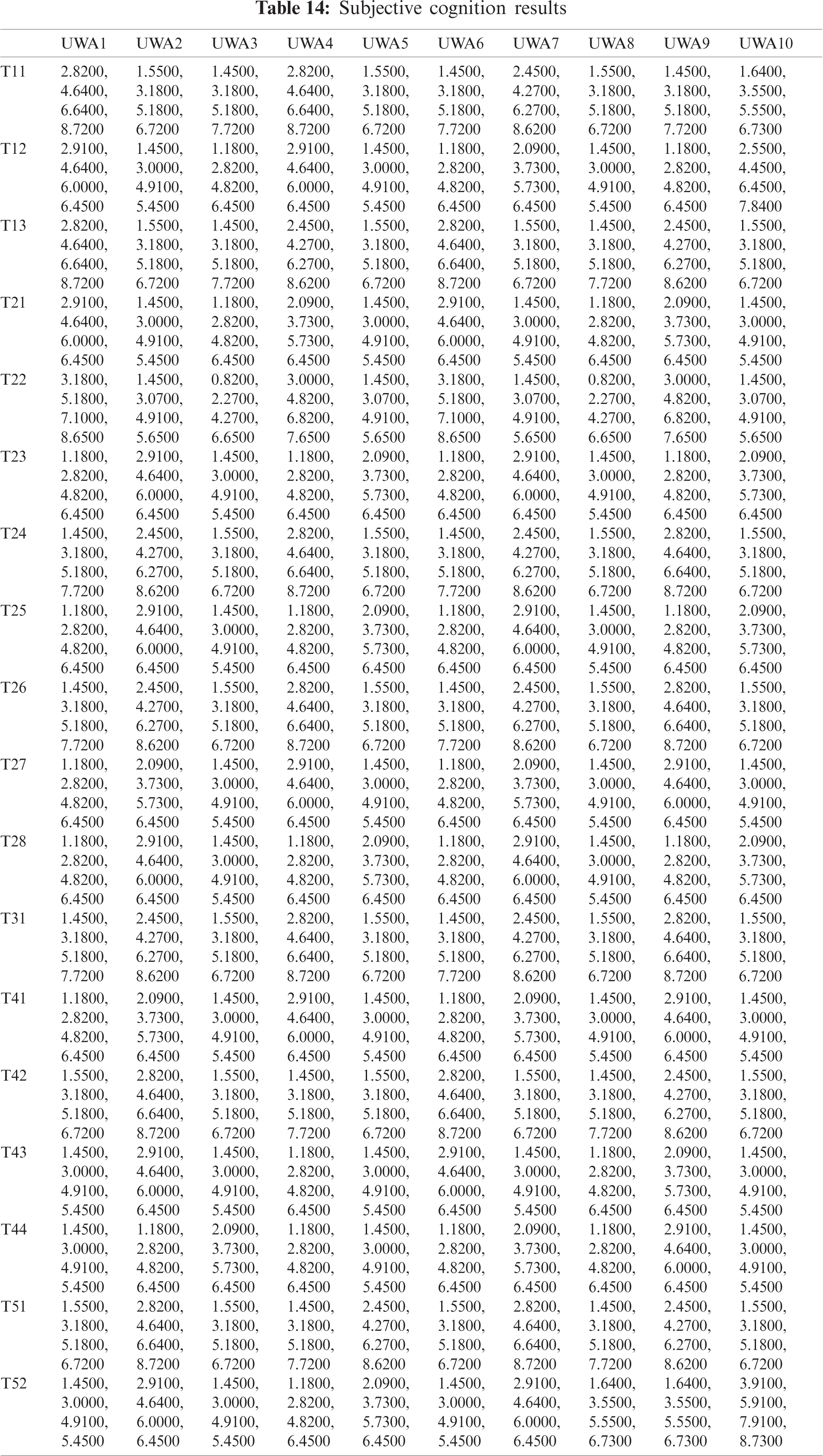
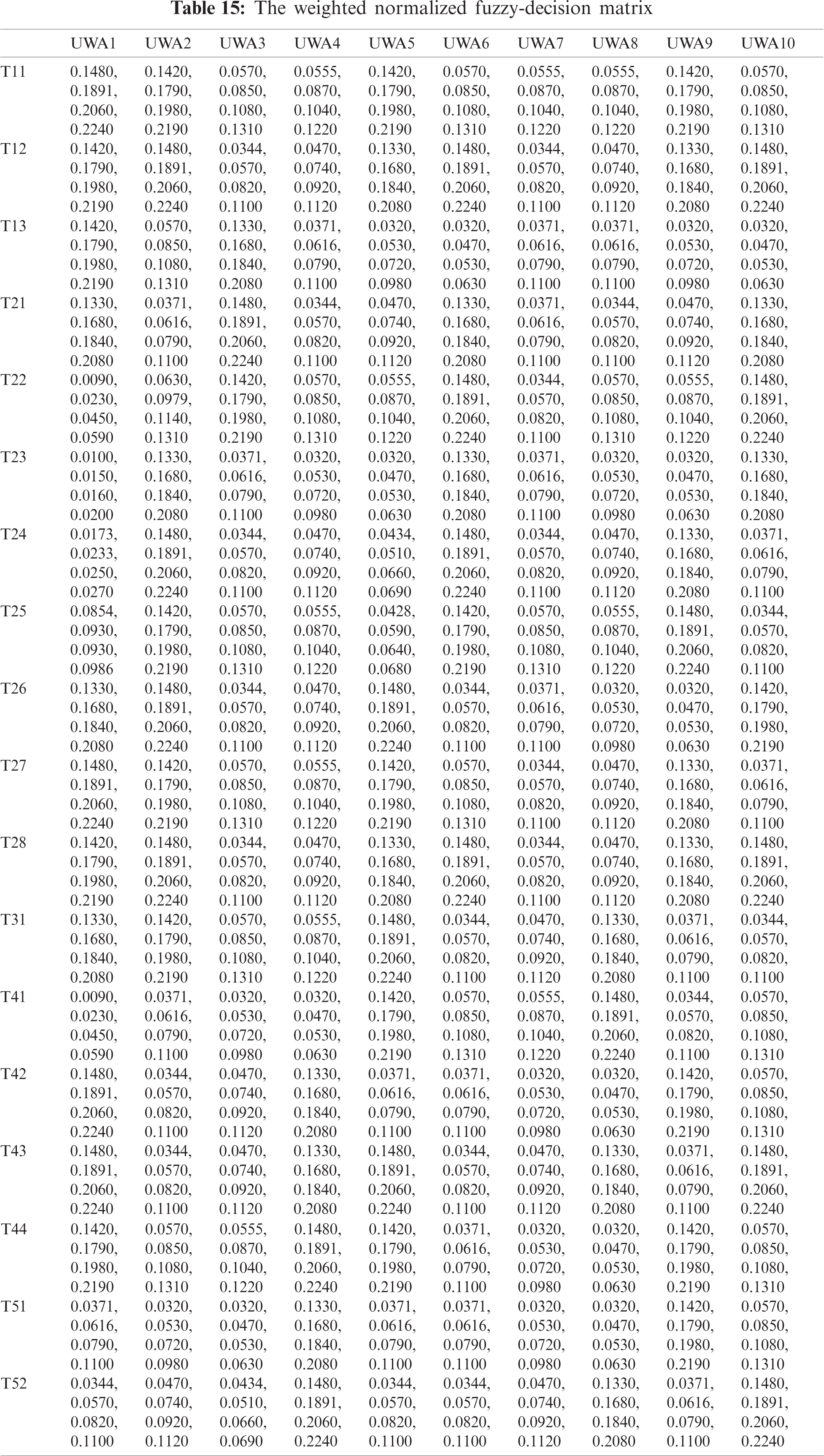
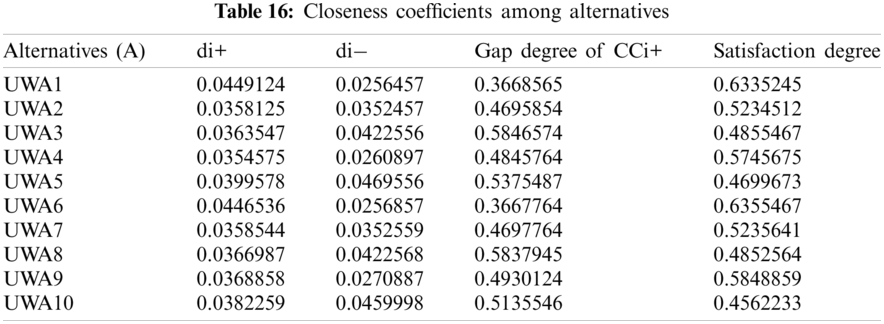
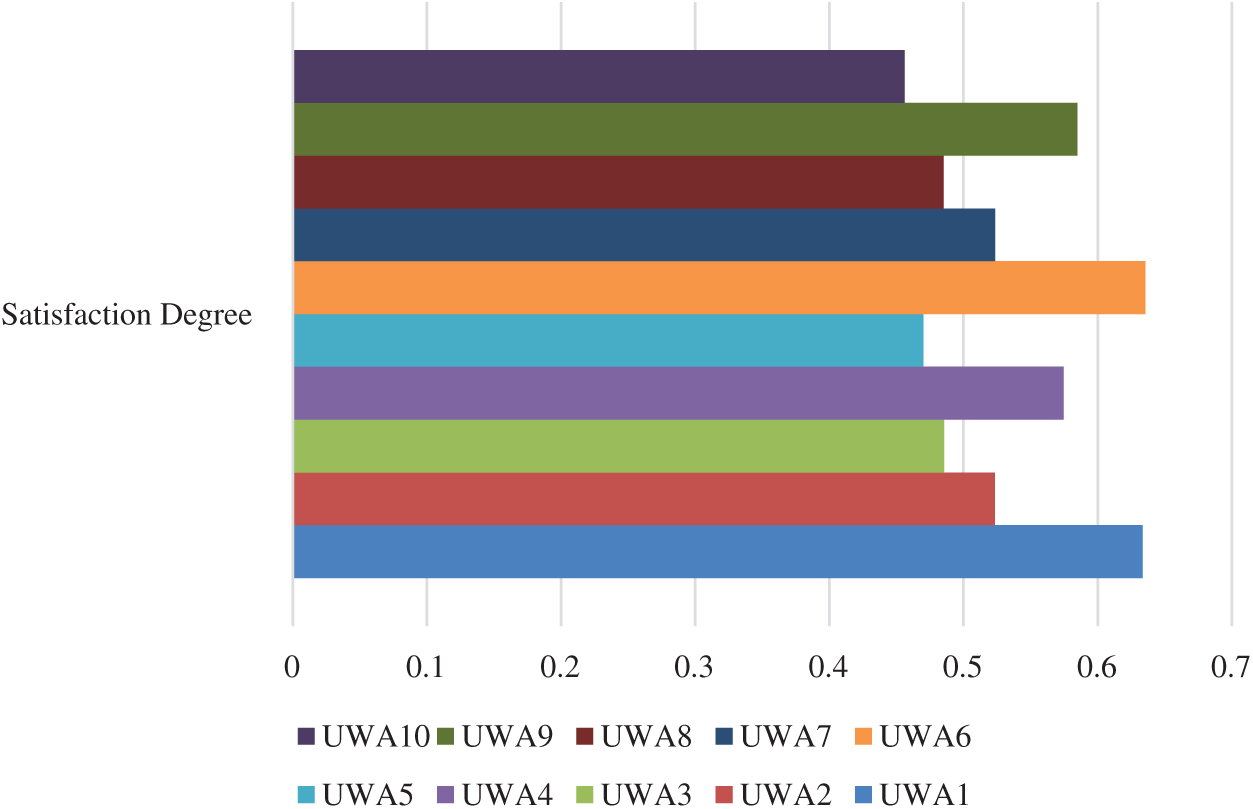
Figure 4: Graphical representation of satisfaction degrees
Security breaches can be minimized to a great extent if the issues pertaining to security-durability of web applications are resolved in their emerging phases itself. Thus, the analysis and management of security risks should be given the top priority while developing a healthcare web application. Adopting such an approach would result in more productive and reliable implementations. Nowadays, where almost everything is done digitally, the use of object-oriented technology continues to grow naturally. The security characteristic is hard to ignore at the same time. Therefore, if these security risks are linked to object-focused design properties, it could be very useful for secure healthcare web application development in the future.
The researchers may also measure the connection between these threats and object-oriented design properties of healthcare web applications through hesitant fuzzy-based AHP-TOPSIS for accurate interdependence. To establish the exact mutual reliability, an effective, powerful, and secure healthcare web application can be used. In this analysis, the Alternative (UWA6) delivered the utmost efficient and durable security system among all the 10 competing options. The evaluation of information security in the University's web application security strategies would be a useful aid in improving the quality of healthcare web applications that can offer secure and reliable mechanisms for protection against both internal and external attacks and threats. The key conclusions of this work are:
• The security risk characteristic outcomes affecting the healthcare web applications security from a design perspective delivers an efficient and perfect priority list.
• The most prioritized alternative is the UWA6.The results drawn from the analysis will be very useful for the researchers and developers who can refer to the present study's tabulations in their efforts to choose the most secure design approach for modeling effective healthcare web applications.
• The study has found four characteristics that affect healthcare web applications. By taking the assessment procedure of this research work, the weights of the healthcare web application security risks can be elicited.
Acknowledgement: This research work was funded by Institutional Fund Projects under Grant No. (IFPHI-286-611-2020). Therefore, the authors gratefully acknowledge technical and financial support from the Ministry of Education and King Abdulaziz University, DSR, Jeddah, Saudi Arabia.
Funding Statement: Funding for this study was received from the Ministry of Education and Deanship of Scientific Research at King Abdulaziz University, Kingdom of Saudi Arabia under Grant No. IFPHI-286-611-2020.
Conflicts of Interest: The authors declare that they have no conflicts of interest to report regarding the present study.
1. S. A. Khan, M. Alenezi, A. Agrawal, R. Kumar and R. A. Khan, “Evaluating performance of software durability through an integrated fuzzy-based symmetrical method of ANP and TOPSIS,” Symmetry, vol. 12, no. 4, pp. 1–15, 2020. [Google Scholar]
2. A. Agrawal, M. Zarour, M. Alenezi, R. Kumar and R. A. Khan, “Security durability assessment through fuzzy analytic hierarchy process,” PeerJ Computer Science, vol. 5, no. 9, pp. 1–43, 2019. [Google Scholar]
3. R. Kumar, M. Zarour, M. Alenezi, A. Agrawal and R. A. Khan, “Measuring security-durability through fuzzy based decision-making process,” International Journal of Computational Intelligence Systems, vol. 12, no. 2, pp. 627–642, 2019. [Google Scholar]
4. CWE-260: Password in configuration file, “Common weakness enumeration,” 2009. [Online]. Available: https://cwe.mitre.org/data/definitions/260.html. [Google Scholar]
5. R. Kumar, A. I. Khan, Y. B. Abushark, M. M. Alam, A. Agrawal et al., “A knowledge based integrated system of hesitant fuzzy set, AHP and TOPSIS for evaluating security-durability of web applications,” IEEE Access, vol. 8, no. 2, pp. 48870–48885, 2020. [Google Scholar]
6. CWE-494: Download of code without integrity check, “Common weakness enumeration,” 2013. [Online]. Available: https://cwe.mitre.org/data/definitions/494.html. [Google Scholar]
7. M. Xia and Z. Xu, “Hesitant fuzzy information aggregation in decision making,” International Journal of Approximation Reason, vol. 52, no. 5, pp. 395–407, 2011. [Google Scholar]
8. K. Sahu, F. A. Alzahrani, R. K. Srivastava and R. Kumar, “Hesitant fuzzy sets based symmetrical model of decision-making for estimating the durability of web application,” Symmetry, vol. 12, no. 6, pp. 1770–1792, 2020. [Google Scholar]
9. A. Attaallah, A. Algarni and R. A. Khan, “Managing security-risks for improving security-durability of institutional web-applications: Design perspective,” Computers, Materials & Continua, vol. 66, no. 2, pp. 1849–1865, 2021. [Google Scholar]
10. R. M. Rodriguez, L. Martinez and F. Herrera, “Hesitant fuzzy linguistic term sets for decision making,” IEEE Transaction Fuzzy System, vol. 20, no. 7, pp. 109–119, 2011. [Google Scholar]
11. K. Sahu and R. K. Srivastava, “Soft computing approach for prediction of software reliability,” ICIC Express Letters, vol. 12, no. 12, pp. 1213–1222, 2018. [Google Scholar]
12. J. Kaur, A. I. Khan, Y. B. Abushark, M. M. Alam, S. A. Khan et al., “Security risk assessment of healthcare web application through adaptive neuro-fuzzy inference system: A design perspective,” Risk Management and Healthcare Policy, vol. 13, no. 5, pp. 355–371, 2020. [Google Scholar]
13. K. Sahu and R. K. Srivastava, “Needs and importance of reliability prediction: An industrial perspective,” Information Sciences Letters, vol. 9, no. 1, pp. 33–37, 2020. [Google Scholar]
14. V. Torra, and Y. Narukawa, “On hesitant fuzzy sets and decision,” in Proc. of the 2009 IEEE Int. Conf. on Fuzzy Systems, Jeju Island, South Korea, pp. 1378–1382, 2009. [Google Scholar]
15. M. Schiefer, Internet of Things: Security Evaluation of Nine Fitness Trackers, Magdeburg, Germany, AV TEST, The Independent IT Security Institute, 2015. [Online]. Available: https://www.av-test.org/filead-min/pdf/publications/avtest_2015-06_fitness_tracker_english-1.pdf. [Google Scholar]
16. R. Kumar, A. K. Pandey, A. Baz, H. Alhakami, W. Alhakami et al., “Fuzzy-based symmetrical multi-criteria decision-making procedure for evaluating the impact of harmful factors of healthcare information security,” Symmetry, vol. 12, no. 664, pp. 1–23, 2020. [Google Scholar]
17. K. Sahu and R. K. Srivastava, “‘‘Revisiting software reliability,” Advances in Intelligent Systems and Computing, vol. 808, pp. 221–235, 2019. [Google Scholar]
18. S. Alder, “Healthcare data breach report,” HIPPA Journal, vol. 1, pp. 1–10, 2020. [Online]. Available: https://www.hipaajournal.com/2020-healthcare-data-breach-report-us/. [Google Scholar]
19. The 2020-2021 Healthcare Cybersecurity Report, “A special report from the editors at cybersecurity ventures,” Herjavec Group, 2021. [Online]. Available: https://1c7fab3im83f5gqiow2qqs2k-wpengine.net-dna-ssl.com/wp-content/uploads/2020/09/HG-Healthcare-Cybersecurity-Report-2021.pdf. [Google Scholar]
 | This work is licensed under a Creative Commons Attribution 4.0 International License, which permits unrestricted use, distribution, and reproduction in any medium, provided the original work is properly cited. |