DOI:10.32604/cmc.2022.019593

| Computers, Materials & Continua DOI:10.32604/cmc.2022.019593 |  |
| Article |
Hybrid Computational Modeling for Web Application Security Assessment
1Department of Information Technology, Babasaheb Bhimrao Ambedkar University, Lucknow, 226025, Uttar Pradesh, India
2Department of Information Technology, College of Computers and Information Technology, Taif University, Taif, 21944, Saudi Arabia
3Department of Computer Science, University College of Al Jamoum, Umm Al Qura University, Makkah, 21421, Saudi Arabia
4Department of Computer Applications, Shri Ramswaroop Memorial University, Barabanki, 225003, Uttar Pradesh, India
5Department of Computer Science, Aligarh Muslim University, Aligarh, 202002, Uttar Pradesh, India
*Corresponding Author: Rajeev Kumar. Email: rs0414@gmail.com
Received: 18 April 2021; Accepted: 19 May 2021
Abstract: Transformation from conventional business management systems to smart digital systems is a recurrent trend in the current era. This has led to digital revolution, and in this context, the hardwired technologies in the software industry play a significant role However, from the beginning, software security remains a serious issue for all levels of stakeholders. Software vulnerabilities lead to intrusions that cause data breaches and result in disclosure of sensitive data, compromising the organizations’ reputation that translates into, financial losses as well. Most of the data breaches are financially motivated, especially in the healthcare sector. The cyber invaders continuously penetrate the E-Health data because of the high cost of the data on the dark web. Therefore, security assessment of healthcare web-based applications demands immediate intervention mechanisms to weed out the threats of cyber-attacks. The aim of this work is to provide efficient and effective healthcare web application security assessment. The study has worked with the hybrid computational model of Multi-Criteria Decision Making (MCDM) based on Analytical Hierarchy Process (AHP) and Technique for Order of Preference by Similarity to Ideal-Solutions (TOPSIS) under the Hesitant Fuzzy (HF) environment. Hesitant fuzzy sets provide effective solutions to address decision making problems where experts counter hesitation to make a decision. The proposed research endeavor will support designers and developers in ide.pngying, selecting and prioritizing the best security attributes for web applications’ development. The empirical analysis concludes that Robustness got highest priority amongst the assessed security attributes set followed by Encryption, Authentication, Limit Access, Revoke Access, Data Validation, and Maintain Audit Trail. The results of this research endeavor depict that this proposed computational procedure would be the most conversant mechanism for determining the web application security. The study also establishes guidelines which the developers can refer for the documentation and arrangement of security factors to construct more secure and trustworthy web-based applications.
Keywords: Healthcare web application; security assessment; AHP-TOPSIS; hesitant fuzzy sets
The present day healthcare industry is one of the leading industries to adapt to the revolution of digitization. Switching from old paper-based system to digital data has made the health services accessible to everyone with the help of smart devices, internet connectivity and web-based applications. Digital healthcare services have led to enormous gains in the healthcare sector. Moreover, it is considered that e-health applications will reduce the healthcare service costs and minimize the extraneous consumptions [1]. In the same league, the healthcare web applications provide provides efficient and usable services to its customers. The most commonly used and famous healthcare web applications are Google Health, Microsoft HealthVault, and Dossia [2]. There are various Electronic Health Record (EHR) web based systems available at present. These are owned by different service providers in different countries. However, the security of these web applications is a serious concern, mostly for the customers who share their sensitive and valuable data with the healthcare service providers by using these web-based applications.
Web based application or web application is a type of software that is mostly stored on remote servers, accessed via internet and rendered on client's web browser. Fast growing use of smart electronic devices and internet connectivity has put a great impact on web-based software development. Software marketing studies cite that in 2017, software market was $57.6 billion and in 2022 it will be $89.3 billion; that is an increment of 55% throughout the world [3]. Thus, fulfilling this rapidly growing demand with efficient security mechanism is a challenging issue. Besides, building and designing secure software applications is in itself a difficult duty, however the mu.pngold increase in intruders’ attacks and vulnerabilities make this task even more difficult. Development of web applications and security are not two different things. The concept of software security is as old as software itself. Software security is an essential aspect of software development process. But addressing security issues of software with traditional and informal methods increases the software vulnerabilities. As observed in several reports, it is believed that a hacking attack is carried out in every 39 s [3]. Globally, it is reported that 54% of the business organizations faced at least one cyber-attack last year. Alarmingly, only 38% of these companies were able to resist the attacks [4–7]. Data sensitivity of the healthcare industry makes it more susceptible to cyber invasions. According to a report published by HIPAA, 510 healthcare data breaches were reported in 2019. 303 of these intrusions were carried out through hacking and other IT incidents that comprised 59.41% of the total. Moreover, 87.60% of the total breached records were exposed due to hacking/IT incidents in this year [4]. From January to April 2020, 145 healthcare data breaches have been stated and 82 of them are because of IT/hacking happenings; this accounts for 56.55% of the total [5]. One of the reasons for continuously targeting healthcare data is the cost of a breached health data. For instance, while, the average cost estimated for a data breach in 2019 was $3.92 million the cost of a data breach in the healthcare sector was estimated to be $6.45 million [6]. Such whopping costs and enormous profits are the lure factors for the hackers who are regularly devising new techniques to exploit the smallest of the vulnerabilities in the healthcare web applications. In this row, the healthcare data breach reports and other software vulnerability analysis studies point out the compelling need for improvised security assessment of healthcare web applications.
Security assessment of web applications is an uninterrupted procedure that must be implemented periodically through the practitioners to verify the security of the software product. It comprises the ide.pngication of recommendations and vulnerabilities of software to prevent and resist beside upcoming threats and reduce the possibilities of risk [8]. Different security parameters are fixed by practitioner’s judgments to perform security assessment of web applications. Further, practitioners employ various MCMD approaches to evaluate security of software. As software security assessment is a decision-making problem [3]. For prioritizing the security factors according their impact on overall mechanism and ide.pngy the most relevant factors, MCDM method pay a crucial role [7]. Additional, prioritizing the security attributes and choosing the most relevant ones that must be focused on while designing and developing the web applications will support the practitioners to maintain and enhance the security from the start of the development process. Furthermore, this will correspondingly increase the duration of the web applications and decrease the total maintenance cost and time invested in the development [7]. With the help of AHP-TOPSIS and hesitant fuzzy sets, the proposed work purposes to estimate the healthcare web application security kept by Indian hospitals.
Analytical hierarchical process, an MCDM technique, has a significant potential in addressing decision making problems that are of hierarchical nature. The proposed technique was first devised by T. L. Saaty in 1970. Since then, the technique has seen several refinements. It provides an effective approach for criteria's (attribute) weight qua.pngication. It helps the experts to find out the decision that best suits their goal and their problem-understanding instead of providing a correct decision. Furthermore, integrating hesitant fuzzy with this technique, makes it more efficient and helps to elicit more accurate results [9,10]. Usually, professionals encounter an unwillingness during building a judgment in AHP and cannot agree on a specific significance because they might want to go beyond or beneath the values. However, these principles are not presented [11–15]. At this type of condition, hesitant fuzzy sets play a critical role and help in signifying decision-makers’ uncertain favorites. HF-logic can be used to remove hesitancies that might occur in the decision making process, particularly when it is challenging to define the membership of a component into a stable set. The normal fuzzy logic cannot address such of issues [16–21]. Thus, the hesitant Fuzzy collection has received considerable attention from scholars at home and abroad ever since it was put forward. Further, TOPSIS technique is also widely known for its characteristic of alternative ranking in the best possible way [3]. Thus, integration of hesitant fuzzy logic with AHP-TOPSIS approach makes this study more efficient and effective for the evaluation of usable-security.
AHP-TOPSIS method based on hesitant fuzzy has a noteworthy capability to address MCDM difficulties that occur due to imprecise and uncertain information [22–26]. During MCDM related problem solutions, hesitant fuzzy based AHP method produces extra truthful weight of the factors, thus generating additional actual outcomes [27–32]. TOPSIS method based on hesitant fuzzy is a more conversant approach for the ranking of alternatives in MCDM problem solving [13]. In this work, seven security attributes are considered as criteria and ten web-based applications of hospitals as alternatives. Ide.pngication and selection of attributes is based on the experts’ opinions and prominent research work.
The other sections of this work are structured as: Section 2 details the review of existing literature; Section 3 describes the security of healthcare web-based applications; Section 4 depicts the practiced methodology; Section 5 provides numerical calculations of the work, and Section 6 of the work enlists the conclusions of the study.
Literature review of the current pertinent works is a momentous figure for finding the authentic investigation gap, and in ide.pngying the ideas of the projected work. With the help of this literature review, it was established that a respectable figure of works have previously been finished on web applications’ security assessment through different techniques and tools. Furthermore, various MCDM approaches like F-AHP, TOPSIS and F-AHP with F-TOPSIS have been employed in various interested parts to ide.pngy the resolutions for difficulties related to MCDM. These are limited pertinent and eminent research works:-
Sahu et al. [28] (2020)—To assess the software durability of web-based applications, the work presented a decision-making model based on hesitant fuzzy sets [28]. They discovered that maintainability and trustworthiness are two basic fundamental criteria for preserving the durability of web applications.
Agarwal et al. [3] (2020)—Well known patterns commonly known as design tactics are practiced in this work to make an assessment of university's different software systems fuzzy based ANP-TOPSIS. A unique set of security attributes with respect to security tactics perspective is ide.pngied and selected to assess the university's software security.
Alenezi et al. [7] (2020)—The authors conducted a deep analytical study of security design tactics [7]. AHP-TOPSIS method based on combined multi-criteria fuzzy sets has been employed to measure design and prioritize the tactics of security factors.
Alharbe [11] (2020)—Proposed a combined tactic of fuzzy-Delphi and AHP to measure usable-security of hospital management system based on web applications [11]. It delivers strategies to practitioners for prioritizing and ide.pngying the factors of usable-security while building and designing software products.
Kaur et al. [15] (2020)—The recommended study uses adaptive neuro fuzzy inference system for the ide.pngication and evaluation of security risk-factors during web application development. This study provides guidelines to the practitioners for assessing and prioritizing security risks of healthcare web-apps at the early stages of web application development for building secure software products.
Solangi et al. [9] (2019)—Developed a framework for determining the utmost appropriate renewable energy resource for power generation [9]. To carry out this tryout, Delphi-AHP and fuzzy-based TOPSIS methods are used. Wind energy was shown to be the best alternative for generating electricity in Pakistan in this study.
Goutam et al. [16] (2019)—This paper presented a framework for estimating the vulnerability of online applications [16]. Penetration testing is a technique for determining software vulnerabilities. Financial web apps have been subjected to both automated and manual testing in order to determine their security. The outcomes of both vulnerability testing methodologies are practically symmetric throughout the study.
Sengul et al. [13] (2015)—Suggested a fuzzy-TOPSIS-based methodology for ranking Turkey’s renewable-energy supply systems [13]. The weights of properties were calculated using Shannon’s Entropy technique. The hydro-power station was discovered to be the finest renewable-energy supply system in this study.
Qian et al. [26] (2013)—The uses of hesitant fuzzy sets in decision-making systems were discovered by Qian et al., [26]. The study concludes that generalised HF sets are the best fit for circumstances in which decision makers are unsure which membership to choose due to a variety of possible memberships with unknown probabilities.
Buyukozkan et al. [12] (2012)—The authors did an analytical study on healthcare electronic-service quality by using combined AHP-TOPSIS technique based on fuzzy sets [12]. Interactivity, specialization, service reliability, accuracy, and responsiveness were ide.pngied to be the most important factors in providing effective and satisfactory healthcare web services, according to the study.
Sarfaraz et al. [14] (2012)—Applied AHP under fuzzy based environment for the selection of web development platform. In this study, LAMP, ASP.NET, and J2EE are evaluated as three web development platforms under the criteria set of security, compatibility, performance and licensing cost. LAMP platform has been found to be the best choice for web application development as compared to the two other platforms.
Lee et al. [8] (2000)—The authors employed ANP, a MCDM problem solving approach, for better selection in the context of information system projects. The study also applies goal programming to generate efficient results. Both the approaches are used because of multi-criteria and interdependency property.
Thus, it is clear that to address decision-making problems such as security attribute ide.pngication and assessment, AHP, TOPSIS and Fuzzy are reasonable assessment procedures. However, the shortcoming of fuzzy sets is that it doesn't go beyond its membership's value [27]. While according to literature studied in this context, hesitant fuzzy sets cover this limitation and give more precise results. In addition, analysis of the literature reveals that there are very few studies that approach computational fuzzy based AHP, ANP, and TOSIS methodology to assess software security. However, we didn't find any research study that assesses software security through integrated hesitant fuzzy based AHP-TOPSIS approach. Hence, our aim is to assess software security through the proposed computational approach for more fair and accurate results. Moreover, the method has been tested on real-time hospital software in Varanasi, India.
3 Healthcare Web Applications Security
Increasing use of internet, smart devices, and busy schedules of life has changed the priorities of both the individuals and organizations. Online digital services are highly recommended as well as practiced in different areas of life. Web based applications make these services easily accessible and serviceable. However, the security of these applications, carrying confidential data has become a critical issue and a persistent apprehension for both the stakeholders and developers [3]. Web based Electronic Health Record (EHR) systems have gained consistent popularity in healthcare sector [17,29]. The data repositories in the healthcare sector are highly sensitive and must not be breached upon [6]. Nonetheless, there are numerous security challenges and issues found in healthcare applications [18]. Fig. 1 provides the architectural structure of EHR web-based systems. Thus, considering security and prioritizing security attributes at the initial phases of healthcare web application development has become a challenging and fascinating issue for the designers and developers. Literally, security is defined as “protection from both the internal and external attacks and threats” [3]. Here, security mainly ensures availability, confidentiality, and integrity of web-based healthcare systems processing, and storing thoughtful healthcare data.

Figure 1: Web based EHR system
To prioritize the security factors of web applications based on healthcare, this work implemented a case study on ten web applications of Indian hospitals. The selection and ide.pngication of security factors for the estimation of web applications is a common judgment of specialists’ opinions and authors’ experiences. The literature review of the current pertinent works has a momentous role in this process. For this work, seven security attributes with 10 various alternatives for assessing security of web applications have been considered. Healthcare web applications of ten different hospitals in Varanasi have been selected as alternatives. They are signified as HWA-1, HWA-2, HWA-3, HWA-4, HWA-5, HWA-6, HWA-7, HWA-8, HWA-9, and HWA-10. Fig. 2 specified below denotes the selected security attributes and their interdependency on each other. The seven selected security factors of web application are defined as:

Figure 2: AHP structure of security attributes
Authentication: It guarantees that the claimed entity provides all info essential to establish his or her claim [3]. For instance, for successful login, enter the right username and password. Only authorised users have access to the system, thanks to a strong authentication process. Information and information systems are more secure as an outcome of this.
Encryption: It is the process of transforming the normal data (plan-text) into the encrypted form commonly known as cypher-text to protect data from illegitimate access and modification. Advanced encryption procedures ensure the improvement of overall security of a system but mainly focus on confidentiality and integrity of a system. Encrypted data is less susceptible to modification and disclosure.
Data Validation: It ensures the completeness, consistency, and accuracy of data shifted among legitimate entities of a associated network [20]. Thus, it implies that the integrity of data and can be estimated as proportion of valid data with respect to the available data.
Robustness: It defines the quality of error handling of a system during its execution process [21]. The International Organization for Standardization (ISO) defines resilience as the degree of smallness in the variability of a system’s function under varied noisy environments [22]. Thus, degree of robustness of a system will directly affect the timeliness of a system. More robust systems are less susceptible to attacks such as flooding, and distributed denial of services. Hence, the attribute improves the quality of availability that is one of main component of CIA Triad [23].
Maintain Audit Trail: A systematic tracking of detailed transactions of an item or record is referred to as an audit trail. In computing, however, an audit trail keeps track of system operations that have been saved to a file or database. As a result, the web application system based on healthcare should store an audit trail of user actions and system records, as well as their effects, for future use [3]. The users of the system will be held accountable if an audit trail is kept. As a result, the property will increase the system’s non-repudiation feature.
Limit Access: It guarantees that various users of a system are given varying rights based on their function and requirements. There should be a restricted access protocol for system resource allocation that allows users to access resources based on their needs. According to the structural needs of the company, this protocol can be implemented on both an individual and group level.
Revoke Access: Revoke access refers to a system user’s privileges being revoked. It ensures that anytime a potential risk or threat to the system resources is detected, system managers can severely limit or revoke access to thoughtful properties.
Thus, all the above discussed attributes are evidently vital for the healthcare web application security assessment. They provide enhanced security mechanism for designing and developing secure healthcare web application systems. Moreover, the selected attributes would also help the practitioners to improve the overall security mechanism of web applications if followed during the development process.
The trial on healthcare online apps is carried out using the accepted research methodology, which provides a structured step-by-step procedure. In order to perform this task, AHP and TOPSIS based on hesitant fuzzy were used. The computational integrated techniques AHP-TOPSIS are part of the MCDM problem-solving domain [17]. AHP-TOPSIS is used in this study in a hesitant fuzzy logic environment, which allows it to produce more accurate results. When membership degrees cannot be openly cleared or judgement-maker do not choose on membership selection, there are a few options. Torra et al. [30] represented hesitant fuzzy sets, which Rodriguez et al. [31] improved. As an advanced form of classical logic, hesitant fuzzy logic has gained a lot of traction in fields where the solution to a problem can be anything from absolutely true to absolutely untrue. It could be entirely true, somewhat true, entirely false, or entirely false. It originates with the capability to deal with information uncertainty [9]. The most appropriate technique for handling problems that might create many hierarchical solutions is the AHP, which is an MCDM problem solving technique. It does a hierarchical analysis of the problem. In comparison to other MCDM techniques, AHP delivers correct computations in the situation of the characteristics’ objective and subjective values [9,14,32]. It also assesses the strength and consistency of the qualities as established by expert judgement. TOPSIS is best recognised in the MCDM problem arena for alternative ranking. Its working concept is shown to be the best alternative among competitive alternatives when a set of performance scores is used to rate all accessible alternatives [8,10]. In this work, the weights of criteria (attributes/ characteristics) are determined using AHP technique based on hesitant fuzzy sets, and then TOPSIS is used to rank the alternatives. Fig. 3. Provides the step-wise working procedure undertaken for this research analysis. In the succeeding sub-section, arithmetical procedures are delivered that helped the researchers to make numerical analysis of this work [17].

Figure 3: Working diagram of AHP-TOPSIS based on hesitant fuzzy sets
In this research endeavor, we presented AHP method based on hesitant fuzzy sets to assess the importance of security features in web-based applications, and we later estimated their analysis and influence on choices for related features using the HF-TOPSIS approach. The following is a detailed step-by-step description of the methodology:
Step_1: The proposed methodology begins with the building of hierarchical models for various factors.
Step_2: Decision makers employed linguistic phrases and computed pair-wise comparisons between those factors with the help of Tab. 1.

Step_3: Applying fuzzy wrappers [33] on converted outcomes. In the provided linguistic scale, it is assumed that T0 has the lowest priority and Tg has the greatest, and that the evaluations are between Ti and Tj such that T0 ≤ Ti ≤ Tj ≤ Tg; factor ordered weighted average has been performed as in Eq. (1).
W denotes the weight of factors, while OWA describes the algorithm for ordered weighted averaging. Similarly, experts use Eq. (2) to determine the trapezoidal numbers
The 1st and 2nd type weights were deliberated with the help of Eqs. (6), (7). This is a number within the unit interval [0, 1], which experts obtain using Eqs. (6) and (7), respectively.
1st type weights
2nd type weights
s, and , where g is the highest rank number in assessments (as per Tab. 1 g = 10), and i and j are the low and high factor calculation ranks, respectively.
Step_4: Experts generate the pair-wise comparison matrix (
Step_5: Experts use Eq. (10) to ide.pngy comparison matrix experts utilise it for matrix defuzzification.
In the given Eq. (10), (l, m1, m2, h) represents four trapezoidal number components: lower bound, upper middle bound, lower middle bound, and higher bound. Defuzzification gives you accurate numbers.
Experts use Eqs. (11), (12) to determine the Consistency Ratio (CR) [4].
Where CI stands for consistency index and RI stands for random index, which is described by Saaty [32] and changes for different n numbers. If the value of CR n is less than 0.1, our determined matrix is consistent; otherwise, go back to step_2 and change your judgement.
Step_6: The geometric mean for row values is computed using Eq. (13) by domain experts.
Step_7: Experts examine the weight of the most essential traits using Eq. (14) to ide.pngy the most important criterion.
Step_8: Experts applied Eq. (15) to the defuzzified values and conducted an analysis.
Step 9: Experts in the domain defuzzified values and turned them into normalisation weights using Eq. (16).
Thereafter, The HF-TOPSIS algorithm is used to select the best option from a list of options. TOPSIS has proven to be one of the greatest strategies for selecting the best option and assisting experts in addressing real-world problems as a widely used MCDM technique [3]. The solutions developed by TOPSIS are the furthest from the negative ideal solution and the closest to the positive ideal solution [13]. The proposed method is based on using envelopes to measure distances between H1s and H2s, for example. The distance is defined as Eq. (17) with the envelopes envp (H1s) = [Tp, Tq].
Additional, the process can be well-defined as:
Step_10: Here we assume for the beginning step that the concerned problem has E alternatives
Here, ex represents the practitioners and k depicts the numeric count of experts in TOPSIS approach.
The HF-TOPSIS standard for evaluating criteria and the impact of outcomes is as follows, with a scale ranging from very terrible to extremely good:
The comparative fuzzy envelope has been calculated as follows for each linguistic expression as [30]:
envpF(EGH (btM&G)) = T (0.3300, 0.5000, 0.6700, 0.8300)
envpF(EGH (amM)) = T (0.0000, 0.0000, 0.3500, 0.6700)
envpF(EGH (alG)) = T (0.5000, 0.8500, 1.0000, 1.0000)
envpF(EGH (btVB&M)) = T (0.0000, 0.3000, 0.3700, 0.6700)
Step_11: The aggregated individual assessments of practitioners have been taken, and the building of a summarised decision matrix X = [xij] has been accomplished with the help of Eq. (18).
Step_12: In TOPSIS assessment, the effective factor is denoted by αb, whereas the most effective factor is denoted by Aj, and the cost characteristic is denoted by αc. Furthermore, the lowest relative options for cost-related preferences necessitate a high level of precision. These Eqs. (19)–(22) have been used to make cost assessments and effective features [33]:
Step_13: Experts take help from the Eqs. (23), (24) to calculate the positive and negative ideal matrixes (
Step_14: The relative closeness score for each alternative was calculated using Eqs. (25), (26).
where,
Step_15: Based on the associated relative proximity ratings, an ordered ranking of the options has been produced.
This work will use the above-mentioned systematic step-by-step technique to conduct a case study on healthcare online apps for security evaluation. The numerical computations for this investigation are detailed in the next section of this paper.
5 Results and Numerical Analysis
Measuring the quality factor of a web-based programme that also contains security is a difficult issue [3], since quantitative evaluation of a qualitative factor is a hard effort by rationale. This work’s numerical analysis will provide a quantitative assessment of healthcare online application security. For that, the authors of this study undertook a case study on 10 different web-based applications of healthcare for security assessment. AHP-TOPSIS method based on hesitant fuzzy sets, is approached to make this work more corroborative and efficient. To determine the security assessment of healthcare web applications, seven security attributes namely Authentication, Encryption, Data Validation, Robustness, Maintain Audit Trail, Limit Access, and Revoke Access were considered for this experiment. These attributes are symbolized as M1, M2, M3, M4, M5, M6, and M7, respectively, in the following tables. With the help of Eqs. (1)–(26) specified in Section 4 of this study, security assessment of healthcare web applications by applying AHP-TOPSIS under hesitant fuzzy environment has been examined as follows:
Firstly, taking help from the Eqs. (1)–(9) and considering Tab. 1 as a standard scale, the authors of this study converted the linguistic terms to numeric values and then into HF based crisp numeric values. After that, numerical calculations are performed to build a pair-wise comparison matrix, and the final findings are shown in Tab. 2. The use of Eq. (1) to create fuzzy wrappers; Eqs. (2)–(5) to calculate trapezoidal numbers C = (p, q, r, s); and Eqs. (6), (7) to determine first and second type weights with the involvement of, which represents a value between 0 and 1, are the intermediate processes used to acquire Tab. 2 results. Finally, the experts constructed the pair-wise comparison matrix using Eqs. (8), (9). They have not been represented here due to the word limit of this study and the lesser importance of the intermediately activities.

The defuzzified values and normalised weights of the level 1 characteristics have been computed using Eqs. (10)–(16), and the final results are shown in Tab. 3. The entire process for calculating Tab. 3 includes the following intermediate operations: With the use of Eq. (10), the pair-wise comparison matrices were first turned into combined defuzzified values by defuzzification operations. To check matrix consistency, Eqs. (11), (12) were used to construct the consistency index and consistency ratio. Our determined consistency ratio, CR = 0.0712254, is less than 0.1, indicating that our estimated matrix is consistent. The geometric mean for row values, as well as the determination of the most important criterion, were then determined using Eqs. (13), (14). Further, Eqs. (15), (16) were used to analyse defuzzified values and convert them to normalised weights, accordingly.



This section gives a realistic assessment of the examined findings for highly sensitive healthcare online apps used by Indian institutions. After obtaining the defuzzified and normalised weights of each factor using the AHP technique based on hesitant fuzzy sets, the global ranking of competing alternatives was generated using TOPSIS method based on hesitant fuzzy sets. Authors acquired feedbacks on the scie.pngic data of 10 healthcare online applications using the regular scales in stage 10 and Eq. (17) established in the procedure portion, and the combined findings are shown in Tab. 4. The factor weights created by AHP method based on hesitant fuzzy sets are supplied to TOPSIS technique in a fuzzy environment to obtain alternative ranking. The normalised fuzzy decision-matrix for seven factors and ten competitive alternatives is presented and established in Tab. 5 with the help of step 10 (described in the procedure section) for intermediate actions and by applying Eq. (18) for normalised fuzzy decision-matrix for seven factors and ten competitive alternatives. Using Eqs. (19)–(22), the normalised fuzzy decision-matrix cell values (performance-values) are multiplied by each factor weight rate, resulting in a weighted fuzzy normalised decision-matrix, as shown in Tab. 6. The final findings are provided in Tab. 7 after applying Eqs. (22), (23) to determine negative and positive idealness of each alternative with regard to each factor. Following that, Eqs. (25), (26) were used to compute the comparative closeness score for each alternative, and the results are displayed in Tab. 8.


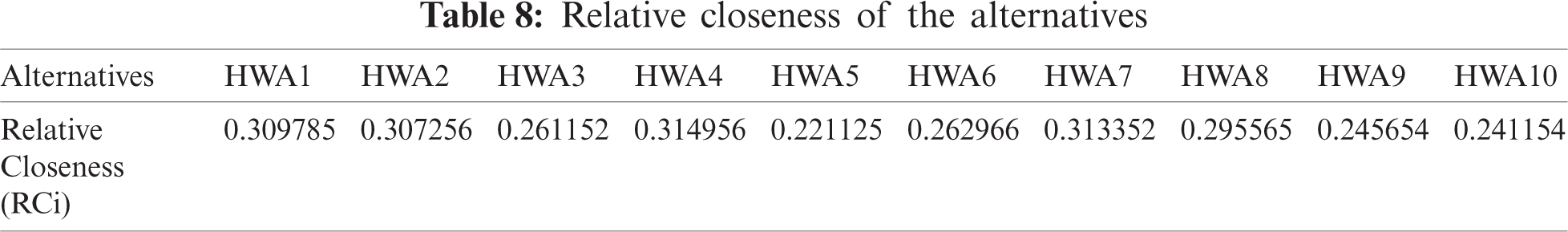
In terms of security assessment, the ranking of competitive alternatives (ten healthcare web apps) is generated as HWA-4, HWA-7, HWA-1, HWA-2, HWA-8, HWA-6, HWA-3, HWA-9, HWA-10, and HWA-5 based on preference scores or relative closeness scores. The security assessment performed on 10 distinct healthcare web apps revealed that HWA-4 provides a better security mechanism to solve primary security risks and challenges based on selected criteria, according to this report. Furthermore, using the hesitant fuzzy TOPSIS technique, the recognized factors for security assessment in this work were prioritised in the following order: Robustness, Encryption, Authentication, Limit Access, Revoke Access, Data Validation, and Maintain Audit Trail with the global normalized weights 0.2340, 0.1840, 0.1500, 0.1440, 0.1210, 0.0850, and 0.0820, respectively.
The main objective of this work is to assess security of healthcare web applications through a computational MCDM technique named as AHP-TOPSIS based on hesitant fuzzy sets. Ide.pngication and collection of security factors employed for assessment has been done on the basis of professionals’ views and current pertinent investigation consequences. Results of AHP method based on fuzzy sets displays that the Robustness attribute has got the highest priority followed by Encryption, Authentication, Limit Access, Revoke Access, Data Validation, and Maintain Audit Trail. TOPSIS method based on hesitant fuzzy sets generated ranking of alternatives (Healthcare web applications) depicts that HWA-4 has got the highest ranking, while the HWA-5 got the lowest ranking with performance score of 0.221125 tested with respect to the ide.pngied factors of security. Results show that HWA-4 provides comparatively more reliable and trustworthy security mechanism than the other nine available alternatives. This study will be helpful for healthcare web application security analysis and for the development of secure and trustworthy products.
From the results of the study, healthcare web application-4 (HWA-4) has optimally satisfied the security criteria that were employed in this work to estimate the security of HWAs. Thus, it was found to be the best in providing reliable and trustworthy security mechanism against threats and attacks with a performance score of 0.314956. The main observations and results of the study are concluded in the following points.
• The security attributes’ assessment through AHP under hesitant fuzzy environment prioritizes the security attributes in the following order: Robustness, Encryption, Authentication, Limit Access, Revoke Access, Data Validation, and Maintain Audit Trail with the global normalized weights 0.2340, 0.1840, 0.1500, 0.1440, 0.1210, 0.0850, and 0.0820, respectively.
• The sequential order of other competitive alternatives according to their produced performance scores after HWA-4 is as: HWA-7, HWA-1, HWA-2, HWA-8, HWA-6, HWA-3, HWA-9, HWA-10, and HWA-5 with respect to recognized weighted security factors.
• Security of healthcare web applications is a serious issue and in this league, our work will provide adequate guidelines to the developers for building secure as well as reliable healthcare web applications.
• This work has been particularly completed with respect to healthcare web applications but it can also be practiced as a guideline for developing any type of secure web application.
• Research is a dynamic as well as a continuing procedure. So, our security evaluation cannot challenge for the optimality of results, though our results are also accurate. Yet another reckoner in this regard is that there are other MCDM techniques that can be used for producing more efficient results. Nevertheless, our empirical estimations prove that we have also chosen a better technique for this assessment.
Acknowledgement: This research was supported by Taif University Researchers Supporting Project Number (TURSP-2020/211), Taif University, Taif, Saudi Arabia.
Funding Statement: This Project was funded by the Taif University Researchers Supporting Projects at Taif University, Kingdom of Saudi Arabia, under Grant Number: TURSP-2020/211.
Conflicts of Interest: The authors declare that they have no conflicts of interest to report regarding the present study.
1. W. J. M. Stevens, R. V. D. Sande, L. Beijer, M. G. M. Gerritsen and W. J. J. Assendelft, “E-health apps replacing or complementing health care contacts: Scoping review on adverse effects,” Journal of Medical Internet Research, vol. 21, no. 3, pp. 1–11, 2019. [Google Scholar]
2. J. Williams, “Social networking applications in health care: Threats to the privacy and security of health information,” in Proc. ICSE Workshop on Software Engineering in Health Care, Cape Town, South Africa, pp. 39–49, 2010. [Google Scholar]
3. A. Agarwal, A. H. Seh, A. Baz, H. Alhakami, M. Baz et al., “Software security estimation using the hybrid fuzzy ANP-tOPSIS approach: Design tactics perspective,” Symmetry, vol. 12, no. 4, pp. 1–21, 2020. [Google Scholar]
4. S. Alder, “2019 Healthcare Data Breach Report,” HIPAA Journal. [Online]. Available: https://www.hipaajournal.com/2019-healthcare-data-breach-report/. [Google Scholar]
5. S. Alder, “2020 Healthcare Data Breach Report,” HIPAA Journal. [Online]. Available: https://www.hipaajournal.com/april-2020-healthcare-data-breach-report/. [Google Scholar]
6. A. H. Seh, M. Zarour, M. Alenzi, A. K. Sarkar, A. Agrawal et al., “Healthcare data breaches: Insights and implications,” Healthcare, vol. 8, no. 2, pp. 1–18, 2020. [Google Scholar]
7. M. Alenezi, A. Agrawal, R. Kumar and R. A. Khan, “Evaluating performance of web application security through a fuzzy based hybrid multi-criteria decision-making approach: Design tactics perspective,” IEEE Access, vol. 8, no. 8, pp. 25543–25556, 2020. [Google Scholar]
8. J. W. Lee and S. H. Kim, “Using analytic network process and goal programming for interdependent information system project selection,” Computers and Operations Research, vol. 27, no. 8, pp. 367–382, 2000. [Google Scholar]
9. Y. A. Solangi, Q. Tan, N. H. Mirjat, G. D. Valasai, M. W. A. Khan et al., “An integrated delphi-aHP and fuzzy TOPSIS approach toward ranking and selection of renewable energy resources in Pakistan,” Processes, vol. 7, no. 2, pp. 118–131, 2019. [Google Scholar]
10. Y. J. Lai, T. Y. Liu and C. Hwang, “TOPSIS for MODM,” European Journal of Operational Research, vol. 76, no. 3, pp. 486–500, 1994. [Google Scholar]
11. N. Alharbe, “A fuzzy-delphi based decision-making process for measuring usable-security of web based smart hospital management system,” ICIC Express Letters, vol. 14, no. 1, pp. 1–19, 2020. [Google Scholar]
12. G. Buyukozkan and G. Cifici, “A combined fuzzy AHP and fuzzy TOPSIS based strategic analysis of electronic service quality in healthcare industry,” Expert Systems with Applications, vol. 39, no. 3, pp. 2341–2354, 2012. [Google Scholar]
13. U. Sengul, M. Eren, S. Eslamian, V. Gezder and A. B. Send, “Fuzzy TOPSIS method for ranking renewable energy supply systems in Turkey,” Renewable Energy, vol. 75, no. 9, pp. 617–625, 2015. [Google Scholar]
14. A. Sarfaraz, P. Mukherjee and K. Jenab, “Using fuzzy analytical hierarchy process (AHP) to evaluate web development platform,” Management Science Letters, vol. 2, no. 1, pp. 253–262, 2012. [Google Scholar]
15. J. Kaur, A. I. Khan, Y. B. Abushark, M. Alam, S. A. Khan et al., “Security risk assessment of healthcare web application through adaptive neuro-fuzzy inference system: A design perspective,” Risk Management and Healthcare Policy, vol. 13, no. 7, pp. 355–371, 2020. [Google Scholar]
16. A. Goutam and V. Tiwari, “Vulnerability assessment and penetratin testing to enhance the security of web application,” in 2019 4th Int. Conf. on Information Systems and Computer Networks, Mathura, India, pp. 601–605, 2019. [Google Scholar]
17. M. Zarour, M. T. J. Ansari, M. Alenezi, A. K. Sarkar, M. Faizan et al., “Evaluating the impact of blockchain models for secure and trustworthy electronic healthcare records,” IEEE Access, vol. 8, no. 8, pp. 25574–25586, 2020. [Google Scholar]
18. M. T. J. Ansari and D. Pandey, “Risks, security, and privacy for HIV/AIDS data: Big data perspective,” Big Data Analytics in HIV/AIDS Research, vol. 2, no. 1, pp. 117–139, 2018. [Google Scholar]
19. J. M. França, J. D. S. Lima and M. Soares, “Development of an electronic health record application using a multiple view service oriented architecture,” Science and Technology Publications, vol. 2, no. 1, pp. 308–315, 2017. [Google Scholar]
20. A. Alhogail, “Design and validation of information security culture framework,” Computers in Human Behavior, vol. 49, no. 6, pp. 567–575, 2015. [Google Scholar]
21. A. Shahrokni and R. Feldt, “A systematic review of software robustness,” Information and Software Technology, vol. 55, no. 1, pp. 1–17, 2013. [Google Scholar]
22. W. Alosaimi, R. Kumar, A. Alharbi, H. Alyami, A. Agrawal et al., “Computational technique for effectiveness of treatments used in curing sars-cov-2,” Intelligent Automation & Soft Computing, vol. 28, no. 3, pp. 617–628, 2021. [Google Scholar]
23. A. Agarwal, M. Alenezi, S. A. Khan, R. Kumar and R. A. Khan, “Multi-level fuzzy system for usable-security assessment,” Journal of King Saud University–Computer and Information Sciences, Article in press, pp. 1–16, 2019. https://doi.org/10.1016/j.jksuci.2019.04.007. [Google Scholar]
24. R. Kuo, C. W. Hsu and Y. Chen, “Integration of fuzzy ANP and fuzzy TOPSIS for evaluating carbon performance of suppliers,” International Journal of Environmental Science and Technology, vol. 12, no. 5, pp. 3863–3876, 2015. [Google Scholar]
25. R. Kumar, M. Zarour, M. Alenezi, A. Agrawal and R. A. Khan, “Measuring security durability of software through fuzzy-based decision-making process,” International Journal of Computational Intelligence Systems, vol. 12, no. 2, pp. 627–642, 2019. [Google Scholar]
26. G. Qian, H. Wang and X. Feng, “Generalized hesitant fuzzy sets and their application in decision support system,” Knowledge-Based Systems, vol. 37, no. 9, pp. 357–365, 2013. [Google Scholar]
27. W. Yu, Z. Zhang and Q. Zhong, “Consensus reaching for MAGDM with multi-granular hesitant fuzzy linguistic term sets: A minimum adjustment-based approach,” Annals of Operations Research, vol. 25, no. 9, pp. 1–24, 2019. [Google Scholar]
28. K. Sahu, F. A. Alzahrani, R. K. Srivastava and R. Kumar, “Hesitant fuzzy sets based symmetrical model of decision-making for estimating the durability of web application,” Symmetry, vol. 12, no. 11, pp. 1–20, 2020. [Google Scholar]
29. A. F. Subahi, “Edge-based IoT medical record system: Requirements, recommendations and conceptual design,” IEEE Access, vol. 7, no. 8, pp. 94150–94159, 2019. [Google Scholar]
30. V. Torra and Y. Narukawa, “On hesitant fuzzy sets and decision,” in Proc. 2009 IEEE Int. Conf. on Fuzzy Systems, Jeju, South Korea, pp. 1378–1382, 2009. [Google Scholar]
31. R. M. Rodríguez, L. Martínez, V. Torra, Z. S. Xu and F. Herrera, “Hesitant fuzzy sets: State of the art and future directions,” International Journal of Intelligent Systems, vol. 29, no. 6, pp. 495–524, 2019. [Google Scholar]
32. T. L. Saaty, “The analytic network process,” Operations Research and Management Science, vol. 10, no. 7, pp. 637–652, 2001. [Google Scholar]
33. K. Sahu, F. A. Alzahrani, R. K. Srivastava and R. Kumar, “Evaluating the impact of prediction techniques: Software reliability perspective,” Computers, Materials & Continua, vol. 67, no. 2, pp. 1471–1488, 2021. [Google Scholar]
 | This work is licensed under a Creative Commons Attribution 4.0 International License, which permits unrestricted use, distribution, and reproduction in any medium, provided the original work is properly cited. |