DOI:10.32604/cmc.2022.018736

| Computers, Materials & Continua DOI:10.32604/cmc.2022.018736 |  |
| Article |
Real-time Privacy Preserving Framework for Covid-19 Contact Tracing
1School of Computer Science, University of Petroleum & Energy Studies (UPES), Dehradun, 248007, India
2Department of Computer Science, College of Computer and Information Sciences, Majmaah University, Majmaah, 11952, Saudi Arabia
3Department of Information Technology, Faculty of Computer and Information, Assiut University, Assiut, 71515, Egypt
4Department of Information Technology, College of Computer and Information Sciences, Majmaah University, Majmaah, 11952, Saudi Arabia
5Department of Information System, College of Technological Innovation, Zayed University, Abu Dhabi, United Arab Emirates
*Corresponding Author: Ahmed A. Mohamed. Email: amohamed@mu.edu.sa
Received: 19 March 2021; Accepted: 14 May 2021
Abstract: The recent unprecedented threat from COVID-19 and past epidemics, such as SARS, AIDS, and Ebola, has affected millions of people in multiple countries. Countries have shut their borders, and their nationals have been advised to self-quarantine. The variety of responses to the pandemic has given rise to data privacy concerns. Infection prevention and control strategies as well as disease control measures, especially real-time contact tracing for COVID-19, require the identification of people exposed to COVID-19. Such tracing frameworks use mobile apps and geolocations to trace individuals. However, while the motive may be well intended, the limitations and security issues associated with using such a technology are a serious cause of concern. There are growing concerns regarding the privacy of an individual’s location and personal identifiable information (PII) being shared with governments and/or health agencies. This study presents a real-time, trust-based contact-tracing framework that operates without the use of an individual’s PII, location sensing, or gathering GPS logs. The focus of the proposed contact tracing framework is to ensure real-time privacy using the Bluetooth range of individuals to determine others within the range. The research validates the trust-based framework using Bluetooth as practical and privacy-aware. Using our proposed methodology, personal information, health logs, and location data will be secure and not abused. This research analyzes 100,000 tracing dataset records from 150 mobile devices to identify infected users and active users.
Keywords: Privacy; contact tracing; mobile apps; Bluetooth; Covid; epidemic
Epidemics such as H1N1, SARS, Ebola, and the recent coronavirus have impacted millions of people worldwide, resulting in a large death toll. The World Health Organization (WHO) has issued several advisories and courses for action to limit the spread of COVID-19 [1] infection by tracing infected individuals. The tracing process requires infected individuals to share information with governments and local medical agencies, which are tasked with tracking and quarantining individuals who may have been in close contact with infected victims, and the subsequent collection of further information about the infected victims. Tracking involves acquiring the personal information of each infected individual, including their travel history, locations visited, recent contacts, and their health details [2]. While most individuals may be comfortable with sharing this information for their own and the nation’s benefit, privacy-aware individuals may not be so willing. This can hinder the contact tracing process, even as the virus continues to spread at alarming rates [3]. Secure and privacy-aware contact tracing methods can inspire everyone, infected or not, of all ages to join the contact tracing, with an assurance of the data being processed confidentially and with no malicious intent. Globally, various contact tracing applications, such as mobile apps and global positioning systems (GPS), are being used. The infected individual is expected to self-test and self-report health details using mobile applications and location data [4]. However, the sharing of data depends on local infrastructure and networks, which rely on unsecured external technologies such as wireless access points, GPS, data networks, or even those involved in the deployment and maintenance of the application itself. The government of Singapore has launched a contact tracing app called “Trace Together.” The Indian government’s contact tracing app, which is called Aarogya Setu, performs real-time tracking, as illustrated in Fig. 1.
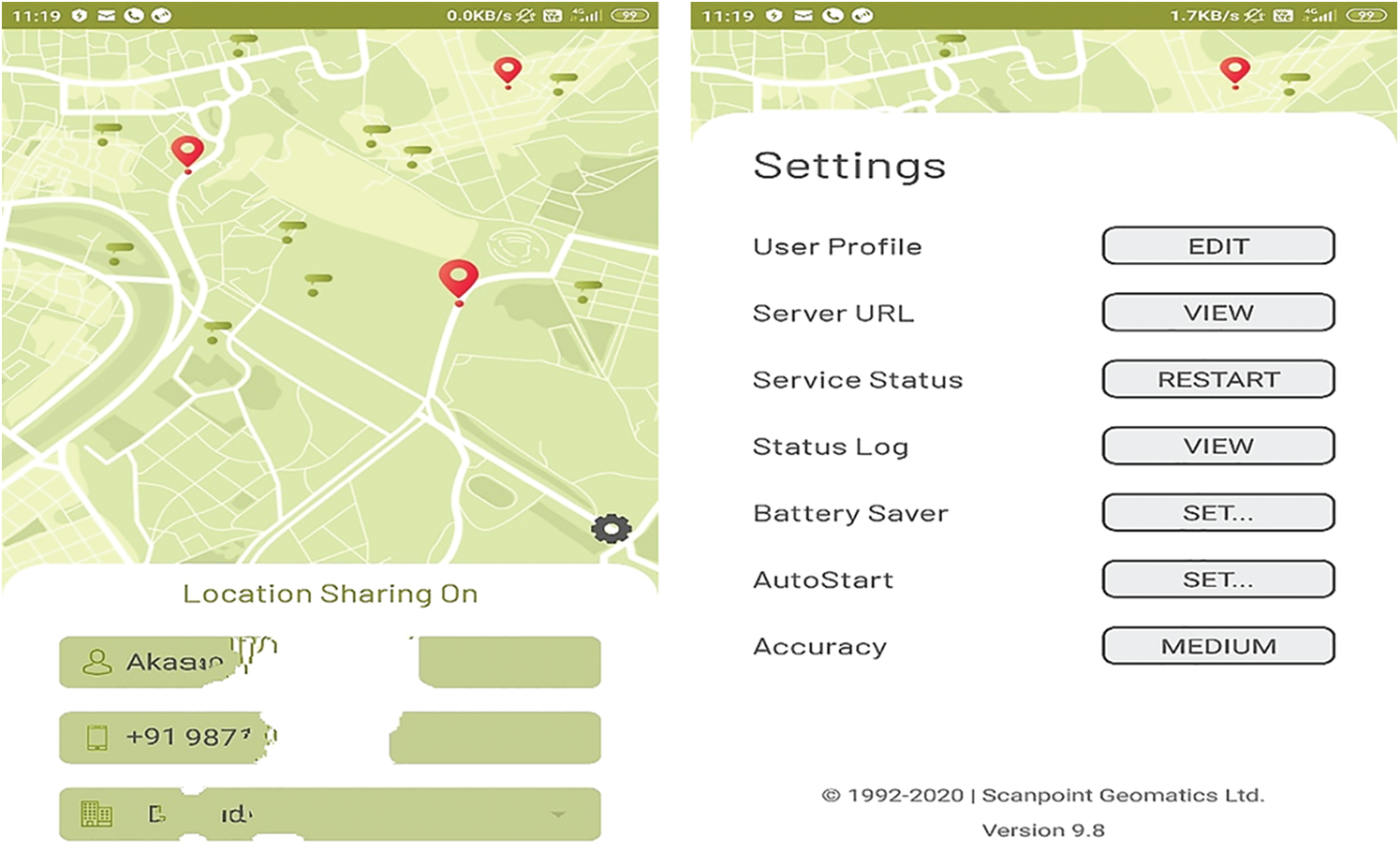
Figure 1: Interface of Aarogya Setu contact tracing app
This study proposes the use of a mobile application with Bluetooth connectivity to perform real-time contact tracing. The authors propose the use of mobile devices to send anonymous beacons of encrypted random code messages via Bluetooth. This allows for foolproof data privacy, and individuals remain anonymous. No collection of privacy-sensitive data is involved or dependent on external third-party IT infrastructure. The major highlights of this research are privacy-aware contact-tracing mobile applications with the following features.
• The proposed contact tracing application does not involve any public wireless or network infrastructure.
• No personally identifiable sensitive information, geolocation, or logs is shared or gathered.
• Real-time tracking enables the rapid identification of locations corresponding to new infected cases.
• Focuses on complete privacy and the use of an individual's Bluetooth connection to determine others within a specific range.
• Around 100,000 contact tracing datasets were used, which involves 150 individual mobiles.
This technology process helps to monitor infected individuals as well as reduce the medical costs involved during quarantine measures. The focus is on testing a framework that ensures complete privacy. To evaluate the contact-tracing framework, T-test and regression analysis were used to validate datasets from real scenarios.
The remainder of this paper is organized as follows: Section 1 describes in detail contact tracing and privacy issues, and Section 2 presents the literature survey regarding the different contact-tracing methods employed by various researchers. The proposed Contact Tracking Framework (CTF) algorithm is illustrated in Section 3. Section 4 discusses the experimental results obtained and presents the T-test validation of the dataset reviewed.
1.1 Contact Tracing and Privacy Issues
Contact tracing involves the identification, assessment, and management of persons exposed to diseases to prevent any onward transmission. If scientifically applied, this can help break the transmission chain of infectious diseases and can be an effective health tool for managing outbreaks. With respect to COVID-19, contact tracing requires the identification of individuals who may have been exposed. Steps such as the quarantining of contacts and the isolation of cases need to be performed. The design and development involved in the contact tracing application system needed to consider various threat vectors in terms of privacy, as presented in Tab. 1.

Gathering personal mobility details for health application purposes presents challenges, even if privacy ethics and issues are upheld. The analysis of any individual’s mobility and health data can only be justified if the benefits are related to public health. Most existing contact-tracing solutions rely on wireless infrastructure for contact tracing to preserve privacy.
During the 2014 EBOLA outbreak, the WHO expounded on the significance of contact tracing and even proposed protocols for tracing infected individuals. However, no mobile application or data-gathering technologies were deployed. The WHO has proposed recommendations for medical staff and those on the front line to improve the safety of using contact tracing applications. With COVID-19, several countries have mandated the use of mobile-based contact tracing, thus gathering data and making use of data obtained from mobile applications. Monitoring and regulating interactions are vital for preventing the spread of this disease. Internet-and mobile-based technologies have aided in terms of surveillance, modeling of infection, remote sensing, etc., to predict and control the disease spread [5]. This tactic of using new-age technology to deal with global epidemics is classified as digital epidemiology under a new domain, as described by Chancay-García et al. [6]. Recently, several researchers have assessed the categorization of mobile call data records. Dede et al. [7] and Christak et al. [8] tracked user mobility patterns to model and evaluate epidemic sickness. Tizooni et al. [9] explored the use of proxy systems for individual users. The authors evaluated the mobility flow to predict the spread of epidemics. The accuracy of the predictive analysis, which was performed using mobility data sources, varied with the epidemic rate of propagation and timing of data results gathered.
Salathe et al. [10] discussed the use of wireless technologies, such as the ZigBee protocol and Bluetooth, to detect and trace infected people. The authors obtained detailed data on the social contacts of infected persons during the infection period. Then, the authors recreated the social networks of potentially infected users. To evaluate the spread, diffusion, and impact, the authors also proposed the SEIR model based on features such as susceptible, exposed, infectious, and recovered. Mastrandrea et al. [11] presented a prototype of wearable sensors for determining contacts amongst individuals and students. The authors matched the results with contacts from personal records, and associated the spread of an epidemic using sensors and diaries with a notable difference in dynamics. Interest in contact-tracing strategies has increased in recent times, and different methods have been used to estimate the impact and rate of spread before and during the plagues, as well as the efficiency of measures against contiguous epidemics. In many outbreaks, contact tracing is the only feasible option to identify infected individuals, as presented by Lima et al. [12], Rubrichi et al. [13], and Fraser et al. [14], who also tested reasons that aid in controlling an outbreak.
Contact tracing methods adopt two primary models, namely, population-based and agent-based approaches. Klinkenberget et al. [15] proposed a population-based top-down approach for analyzing system research data from a macroscopic perspective. Then, Kwok et al. [16] and Müller et al. [17] presented an agent-based bottom-up approach, considering every individual as a self-regulating agent entity. Each agent is responsible for its own infection state, movement, and location to estimate unrelated and adaptive activities. The stochastic model introduced by Farrahiet et al. [18] and Keelinget et al. [19] involves grouping the associated measures and fundamental dynamics of epidemics using a deterministic approach. In previous years, contact-tracing models have focused on a generic network of contacts. To improve the precision of such network contact models, Huerta et al. [20] presented a similar model as part of the epidemic regulation tactics. This method helped to estimate the impact of contact tracing and the random tracing of complex contact networks. Yang et al. [21] proved that by tracing the contacts at a low additional cost, the spread of an outbreak may be considerably reduced, and even eradicated. The FluPhone project developed at Cambridge University [22] was one of the first attempts to use mobile apps to determine contacts. Using wireless Bluetooth as a proxy, the application was able to estimate physical contacts. The application promoted users to report symptoms to determine the rate and risk of infection. Similar contact tracing schemes focus on privacy issues, such as the pan-European privacy-preserving proximity tracing (PEPP-PT) [23] and the MIT project Safe Paths [24]. Corporate enterprises such as Apple, Facebook, and Google teamed up to integrate their web portals with handheld and sensor devices to provide similar solutions for Android and iOS mobiles. Isella et al. [25] claimed that the practice of contact tracing and isolation did not prevent the COVID-19 epidemic. The decreasing infection count is primarily due to asymptomatic infected individuals who are undetected, and who it is believed contribute to the spread of the COVID-19 outbreak. Using mobile apps to find previous contacts, we mathematically proved that such epidemic diseases can be checked even when no one uses the mobile application.
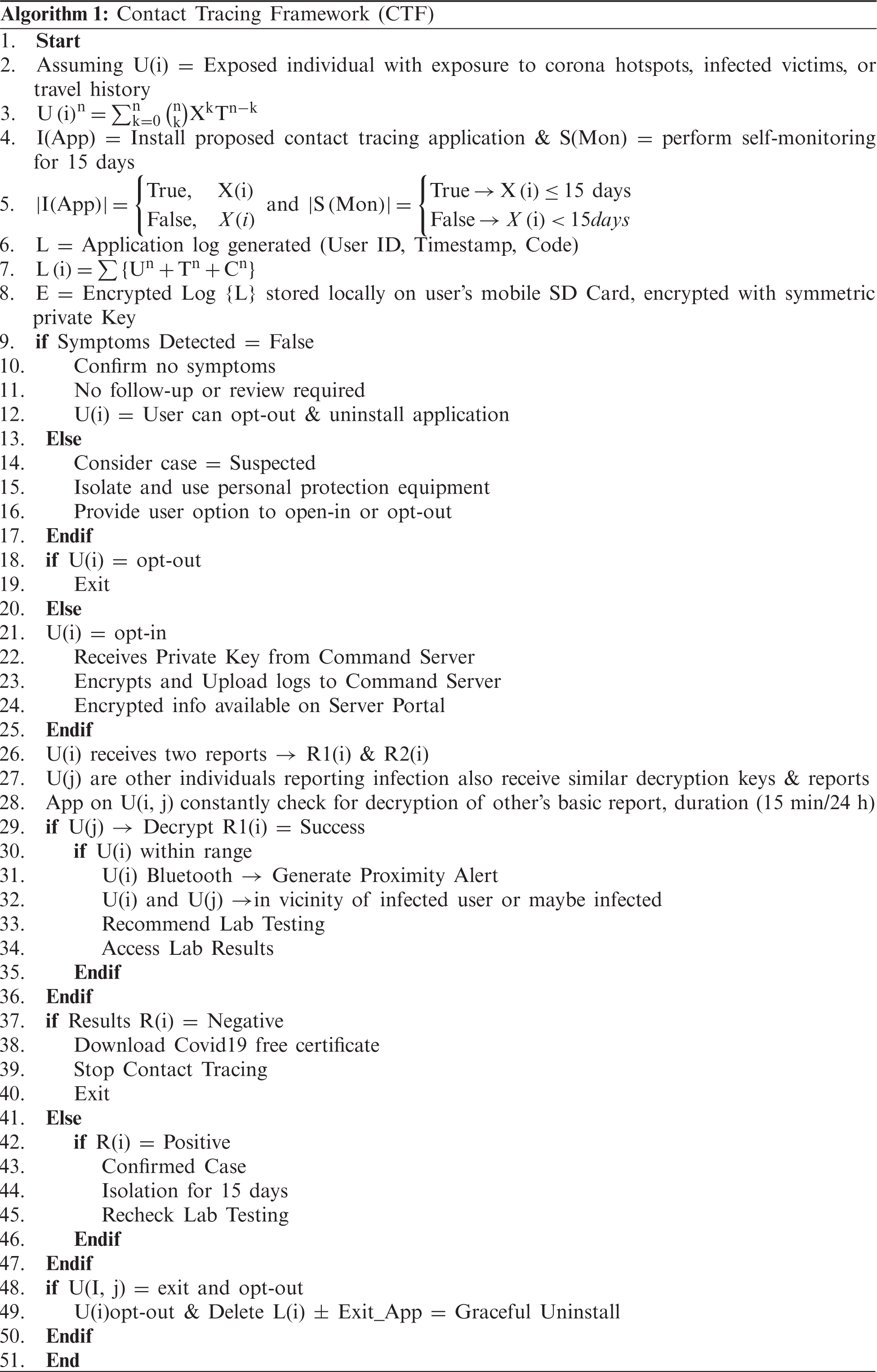
A real-time contact tracking framework (CTF) was designed and developed as a secure mobile application using the Android platform, SDK tools, and Java. Instead of using a data network or IT infrastructure such as wireless or office networks, the lightweight application uses Bluetooth with the need for limited computing resources of the individual’s mobile. However, there are unauthorized and malicious privacy impacts from threat vectors. The CTF process is trust-based; individuals own the process, and it is his/her prerogative to join or exit, and further perform regular 15 days self-assessment to determine any infection. The generated logs comprise a unique ID (user’s Bluetooth), timestamp (date and time), and health status code (random salted number) for each application user. The contract tracking framework follows five phases, as shown in Tab. 2.

Entities involved in the CTF process require privacy protection. These include individuals (mobile IMEI and number), location (IP address and geolocation), health data, and command server communication. The proposed CTF application ensures that the data collected is never shared with any of these entities, and keeps the individuals anonymous. The proposed workflow is shown in Fig. 2.
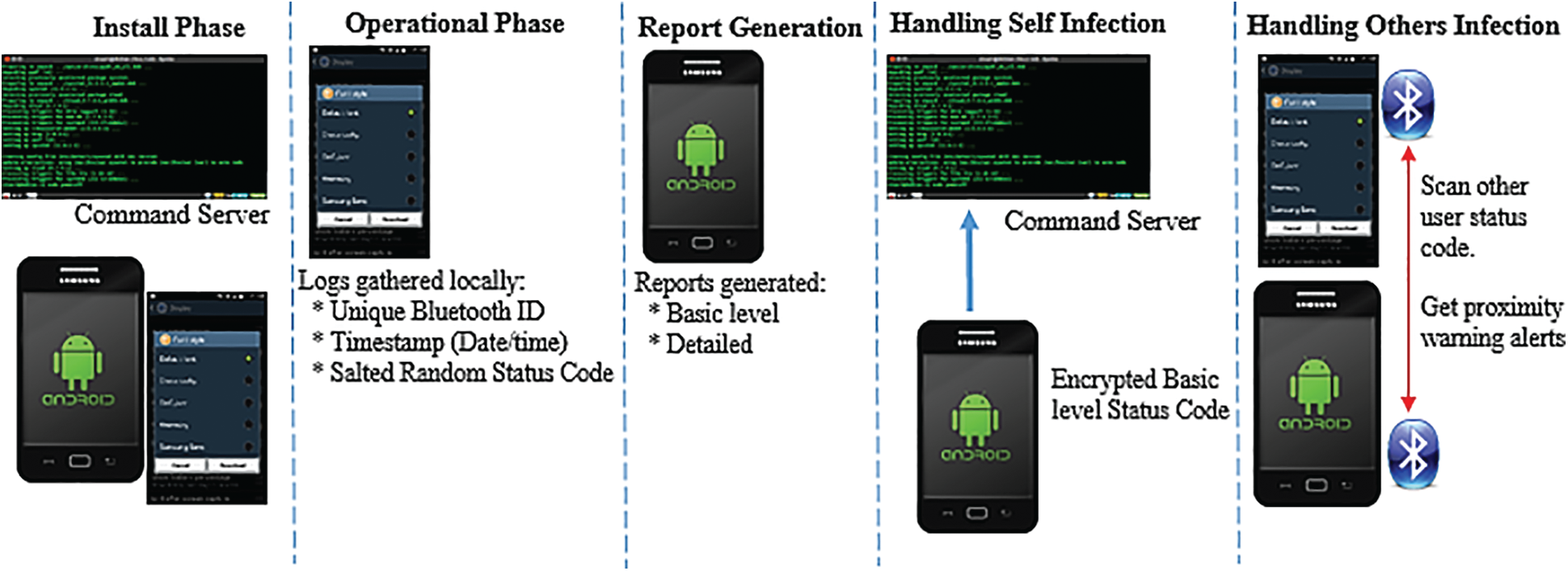
Figure 2: Process flow for secure contact tracing framework
This application was designed for Android mobile devices. The reports are saved locally on the mobile, and are encrypted with a private key in the form of two reports. The first report is a detailed description accessible only to individuals. If the individual is infected, he can share with the medical teams all of the details in full confidence using a private key in order to determine the treatment. The second report is a basic-level code encrypted with a public key and uploaded to the command server. Whenever an individual goes outside, the application scans other mobile devices using Bluetooth. This sends and receives anonymous encrypted beacons to and from other mobile devices. If the application can decrypt the basic report of other individuals, Bluetooth alerts are generated immediately.
• Should not reveal any personal information, location, reports, or other individual information.
• While scanning, any personally identifying information should not be revealed to other users.
• Should be arranged, encrypted with a symmetric key to prevent any log being revealed to any other user.
• Should be randomly generated every 24 h to prevent the identification of transmitted information.
These are individuals who were or are infected, and who are never:
• Mandated to upload their details on the command server.
• Notified by the command server to verify potential contact with other non-infected.
• Receive medical certificate encrypted with medical teams’ public key.
These are individuals who are infected:
• Are given the option to opt-in so that others can determine if they are near to any infected user.
• Can check if they are close to others or those who opted to join.
• Can stay anonymous even from the admin teams of the command server.
• Can find an infected user and determine when or where the actual contact happened.
• Should be assured of their IMEI number or MAC address.
• Can use the TOR browser to upload or download their logs and reports, thus remaining anonymous.
These alerts warn about an infected person in an individual’s proximity. This indicates the presence of an infected individual within a range of 8–10 m. The flow of the secure contact tracing process is shown in Fig. 3. In this case, the user should then proceed to be tested. This process is anonymous, and no information about the individual is shared with the command server or other individuals. Individuals can opt-in or opt out as the process is trust-based. Only those who shared the reports on the command server and individual infections were verified using Bluetooth. The authors formally prove that the application guaranteed privacy-sensitive features and trust verification for the individuals observed correctly. The following features were considered when designing the framework.
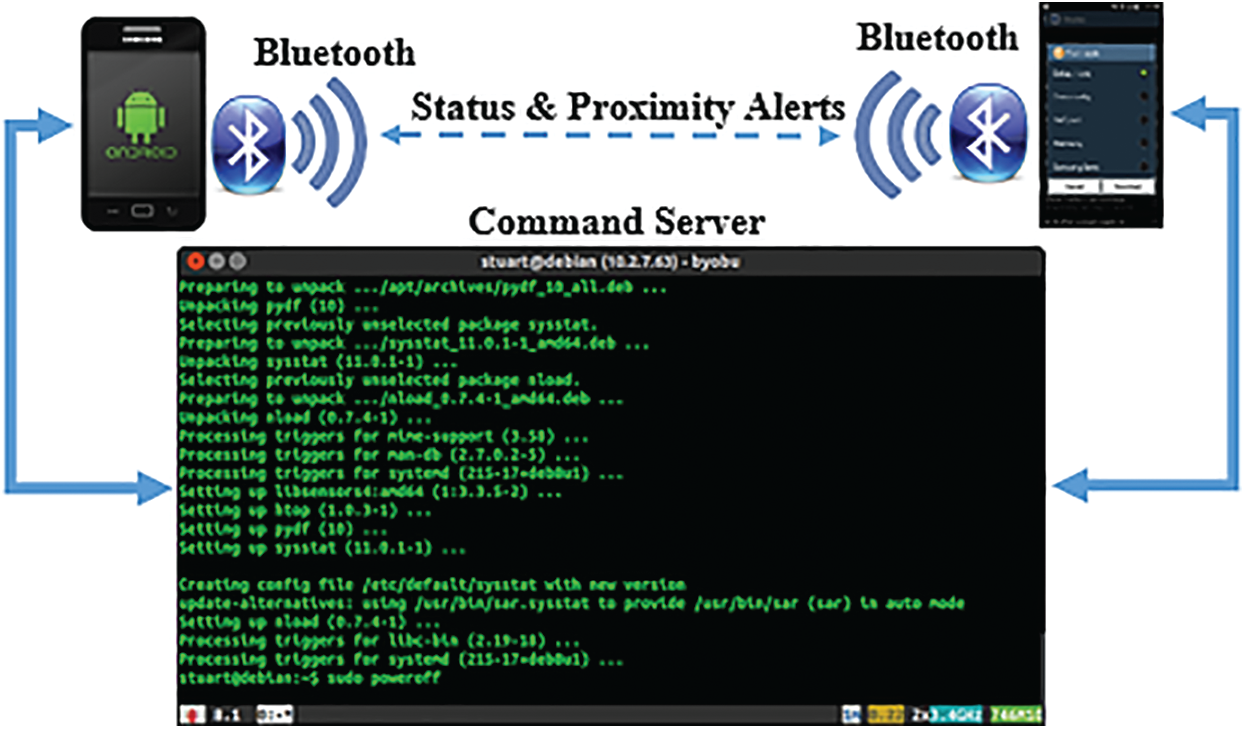
Figure 3: Bluetooth and command server communication
Algorithm 1 presents the proposed secure application workflow and the CTF process. Tab. 3 lists the notations used in the proposed algorithm.

The proposed contact detection runs as a service utilizing Bluetooth beaconing. This confirms the proximity detection of data exchange with nearby phones, even as the advertisements are non-connectable and undirected. Fig. 4 illustrates the flow of advertisements between the application and remote Bluetooth devices. Contact detection and advertisement services are run on devices with a Bluetooth 16-bit UUID 0 x FA5F to enable proximity sensing between devices. Devices advertise and scan using a 128-bit proximity identifier that is periodically modified. Each advertisement scan is timestamped, and the discoverable bit is initially set to 1 and captured. The scan interval window is 5 min, which is sufficient to provide the discovery of advertisers and coverage. The advertiser address and proximity are changed so that they cannot be linked in any way. The advertising intervals are changed every few hundred milliseconds. The scanning internal window performs periodic sampling for every few minutes.

Figure 4: Dataflow for advertisement between mobiles
Fig. 5 illustrates the dataflow process and behavior for the device scans, which ensure that privacy is maintained as the most critical specification while designing the application. This is utilized with the Bluetooth protocol, which is location independent, yet it uses the Bluetooth beacon to detect the device proximity. The user proximity ID correlates and obtains IDs of other devices every 15 min. This reset window reduces the loss from privacy advertisements and is processed exclusively on the local device. If any user is detected to have COVID-19 symptoms, the user can consent to the sharing of the diagnosis keys with the main server. Thus, users have control and transparency regarding their participation for contact tracing. These precautions are implemented in the framework design to ensure user privacy.

Figure 5: Dataflow and behavior of device scan process
The results varied between randomly selected individuals and those infected. Moreover, this research considered different time slots during which users turn ON their Bluetooth to evaluate the effectiveness of our protocols in different scenarios. The validations were repeated to capture the randomness of the simulations for 150 devices.
Initial research focused on the infection rate among individuals depending on the initial infection and contagiousness probability. These datasets were obtained from infections reported by individuals who had installed the contact tracing application, and who were using it.
Subsequent research focused on three scenarios (i1–i3) as follows:
• i1: Individuals who randomly turn ON/OFF their Bluetooth anytime
• i2: Individuals who turn ON Bluetooth when outside their homes, in a market, or in crowded places
• i3: Individuals who turn ON their Bluetooth only at specific hours and for set durations.
The authors conducted a parametric statistical t-test and regression analysis to ensure that the datasets had no violations of the information presented in random samples from 100,000 records. The use of regression validated the prediction of continuous dependent variables from independent variables in the datasets. The deviations from the linear point line are the errors. The distribution of the sample mean is normal, and the variances of the different parameters are similar. The null hypothesis assumes that if the data violate these assumptions, then it can be safely assumed that the results obtained have committed a Type I error, which is more or less than the alpha probability, and the T-Test validation parameters are interpreted as presented in Tab. 4.
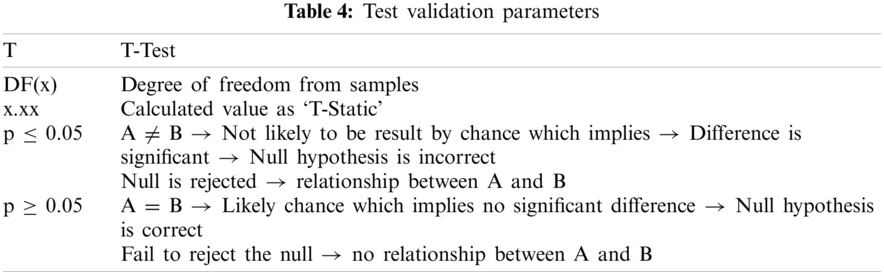
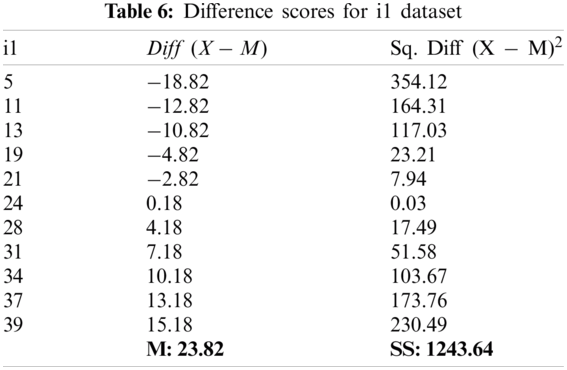
The requirement for performing the T-Test is the use of two independent samples with normally distributed data and samples with the same variance. The authors take the null hypothesis, H0: H1 − H2 = 0, where H1 and H2 are the means for the two datasets. The null hypothesis is that there is no difference between the means of the two datasets, or more formally, that the difference is zero. Tab. 5 presents the T-test validation of the CTF dataset sample.
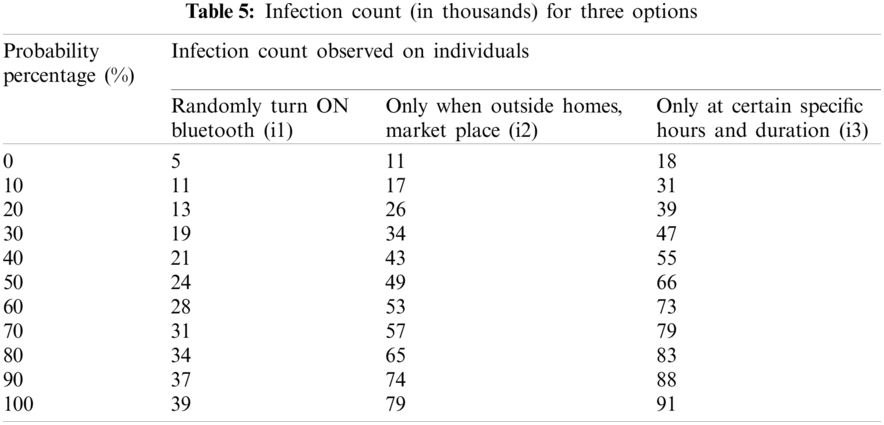
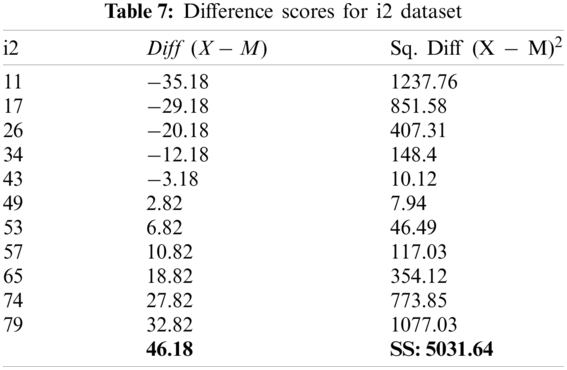
Considering the datasets for i1 and i2, the authors used a significance level of 0.05 with a two-tailed hypothesis. The difference scores that were calculated are presented in Tabs. 6 and 7 below.
T-Test calculations are performed for validation on datasets, and are presented in Tabs. 8 and 9.
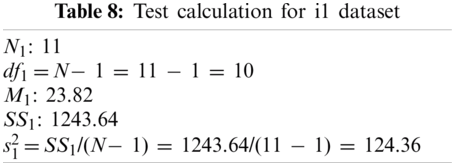
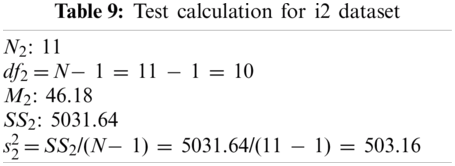
For T-Value Calculation:
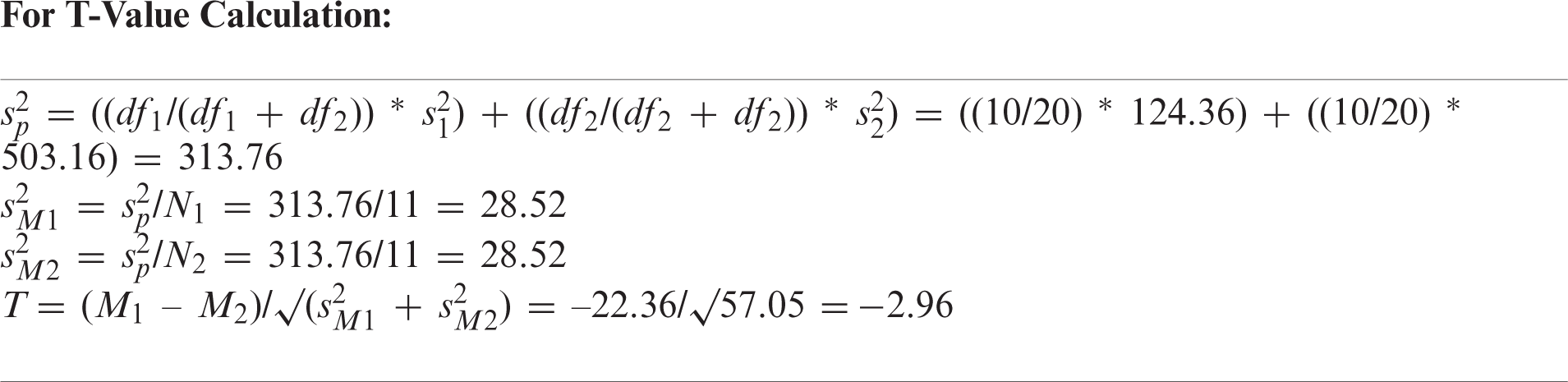
T-value is −2.96089 and the P-value is 0.007726 → Result is significant at p < 0.05.
Because the P-value is less than the significance level, alpha 0.05 → Null Hypo (H0) is rejected and the Alternative Hypo (Ha) is accepted.
Further, validating with regression analysis:

Regression Equation = ŷ = bX + a
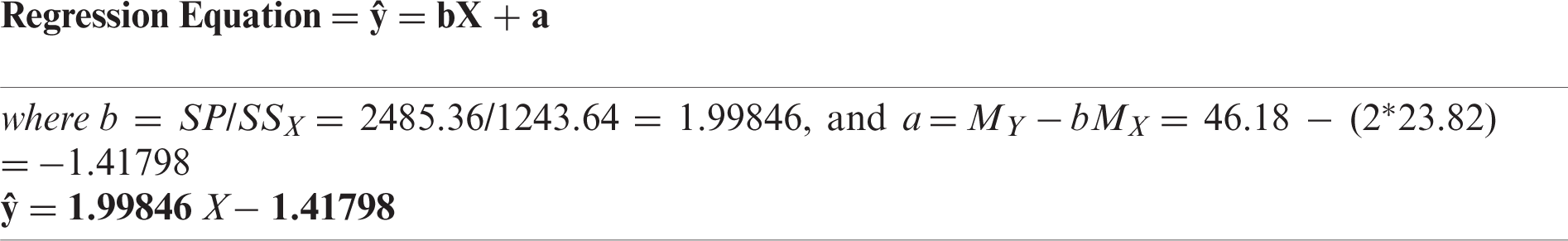
From the graph shown in Fig. 6 below, individuals who randomly turn on their Bluetooth when going out or in crowded places display better performance and contagiousness probability than those who turn on Bluetooth only when outside their homes or only at certain specific hours of for a set duration.

Figure 6: Infected users vs. contagiousness probability
The presented research work successfully demonstrates the real-time, trust-based contact tracing framework (CTF) as a feasible privacy-aware solution. Nation-states need not use methods or applications that pose privacy-related risks or face issues when an individual’s personal information or health logs can be misused. This study considers the features and entities that are related to protecting the privacy of an individual. The focus is to build a trust-based framework with a lightweight Bluetooth-based mobile application. Using sample datasets, the authors have shown how contact tracing with three options can mitigate the spread of COVID-19. Existing contact tracing applications do not provide open-source software for research or experimentation purposes. In the future, the authors plan to release this research as an open-source software implementation for both Android and iOS devices.
Funding Statement: The author would like to thank the Deanship of Scientific Research at Majmaah University for supporting this work under Project No. R-2021-131.
Conflicts of Interest: The authors declare that they have no conflicts of interest to report regarding the present study.
1. E. K. Jeong, O. Park and Y. J. Park, “COVID-19 national emergency response center, epidemiology and case management team, Korea centers for disease control and prevention. Coronavirus disease-19: The first 7,755 cases in the Republic of Korea,” Osong Public Health and Research Perspectives, vol. 11, pp. 85–90, 2020. [Google Scholar]
2. R. Li, S. Pei, B. Chen, Y. Song, T. Zhang et al., “Substantial undocumented infection facilitates the rapid dissemination of novel coronavirus (SARS-CoV-2),” Science, vol. 368, no. 6490, pp. 489–493, 2020. [Google Scholar]
3. B. C. de Jong, B. M. Gaye, J. Luyten, B. van Buitenen, E. André, et al., “Ethical considerations for movement mapping to identify disease transmission hotspots,” Emerging Infectious Diseases, vol. 25, no. 7, 2019. https://doi.org/10.3201/eid2507.181421. [Google Scholar]
4. B. C. de Jong, B. M. Gaye, J. Luyten, B. van Buitenen, E. André et al., “Ethical considerations for movement mapping to identify disease transmission hotspots,” Emerging Infectious Diseases, vol. 25, no. 7, pp. E1–E6, 2019. [Google Scholar]
5. A. L. Barabási, “Network science,” Philosophical Transactions of the Royal Society A: Mathematical, Physical and Engineering Sciences, vol. 371, no. 1987, pp. 20120375, 2013. [Google Scholar]
6. L. Chancay-Garcia, E. Hernandez-Orallo, P. Manzoni, C. T. Calafate and J. C. Cano, “Evaluating and enhancing information dissemination in urban areas of interest using opportunistic networks,” IEEE Access, vol. 6, pp. 32514–32531, 2018. [Google Scholar]
7. J. Dede, A. Förster, E. Hernández-Orallo, J. Herrera-Tapia, K. Kuladinithi et al., “Simulating opportunistic networks: Survey and future directions,” IEEE Communications Surveys & Tutorials, vol. 20, no. 2, pp. 1547–1573, 2018. [Google Scholar]
8. E. Christaki, “New technologies in predicting, preventing and controlling emerging infectious diseases,” Virulence, vol. 6, no. 6, pp. 558–565, 2015. [Google Scholar]
9. M. Tizzoni, P. Bajardi, A. Decuyper, G. K. K. King, C. M. Schneider et al., “On the use of human mobility proxies for modeling epidemics,” PLOS Computational Biology, vol. 10, no. 7, pp. e1003716, 2014. [Google Scholar]
10. M. Salathé, M. Kazandjieva, J. W. Lee, P. Levis, M. W. Feldman et al., “A high-resolution human contact network for infectious disease transmission,” Proceedings of the National Academy of Sciences of the United States of America, vol. 107, no. 51, pp. 22020–22025, 2010. [Google Scholar]
11. R. Mastrandrea and A. Barrat, “How to estimate epidemic risk from incomplete contact diaries data?,” PLOS Computational Biology, vol. 12, no. 6, pp. e1005002, 2016. [Google Scholar]
12. A. Lima, V. Pejovic, L. Rossi, M. Musolesi and M. Gonzalez, “Progmosis: Evaluating risky individual behavior during epidemics using mobile network data,” arxiv.org, 2015. [Google Scholar]
13. S. Rubrichi, Z. Smoreda and M. Musolesi, “A comparison of spatial-based targeted disease mitigation strategies using mobile phone data,” EPJ Data Science, vol. 7, no. 1, pp. 17, 2018. [Google Scholar]
14. C. Fraser, S. Riley, R. M. Anderson and N. M. Ferguson, “Factors that make an infectious disease outbreak controllable,” Proceedings of the National Academy of Sciences of the United States of America, vol. 101, no. 16, pp. 6146–6151, 2004. [Google Scholar]
15. D. Klinkenberg, C. Fraser and H. Heesterbeek, “The effectiveness of contact tracing in emerging epidemics,” PLOS One, vol. 1, no. 1, pp. e12, 2006. [Google Scholar]
16. K. O. Kwok, A. Tang, V. W. I. Wei, W. H. Park, E. K. Yeoh et al., “Epidemic models of contact tracing: Systematic review of transmission studies of severe acute respiratory syndrome and middle east respiratory syndrome,” Computational and Structural Biotechnology Journal, vol. 17, no. 1, pp. 186–194, 2019. [Google Scholar]
17. J. Müller, M. Kretzschmar and K. Dietz, “Contact tracing in stochastic and deterministic epidemic models,” Mathematical Biosciences, vol. 164, no. 1, pp. 39–64, 2000. [Google Scholar]
18. K. Farrahi, R. Emonet and M. Cebrian, “Epidemic contact tracing via communication traces,” PLOS One, vol. 9, no. 5, pp. e95133, 2014. [Google Scholar]
19. M. J. Keeling, P. Rohani and B. Pourbohloul, “Modeling infectious diseases in humans and animals: Modeling infectious diseases in humans and animals,” Clinical Infectious Diseases, vol. 47, no. 6, pp. 864–865, 2008. [Google Scholar]
20. R. Huerta and L. S. Tsimring, “Contact tracing and epidemics control in social networks,” Physical Review E, vol. 66, no. 5, pp. 4, 2002. [Google Scholar]
21. H. X. Yang, W. X. Wang, Y. C. Lai and B. H. Wang, “Traffic-driven epidemic spreading on networks of mobile agents,” Europhysics Letters, vol. 98, no. 6, pp. 68003, 2012. [Google Scholar]
22. R. Raskar, “Apps gone rogue: Maintaining personal privacy in an epidemic,” [Online]. Available: https://montrealethics.ai/research-summary-apps-gone-rogue-maintaining-personal-privacy-in-an-epidemic/, Retrieved January 12, 2021. [Google Scholar]
23. E. Yoneki, Computer Laboratory Systems Research Group, 2019. [Online]. Available: https://www.cl.cam.ac.uk/research/srg/netos/projects/archive/fluphone2/, Retrieved January 4, 2021. [Google Scholar]
24. PEPP-PT, “Pan-european privacy-preserving proximity tracing,” Pepp-Pt, 2020. [Online]. Available: https://scholar.google.com/scholar?hl=en&as_sdt=0%2C5&q=Pan-European+Privacy-Preserving+Proximity+Tracing&btnG=. [Google Scholar]
25. R. Raskar and K. Esvelt, “Private kit: Safe paths; privacy-by-design,” 2020. [Online]. Available: https://safepaths.mit.edu/, Retrieved February 16, 2021. [Google Scholar]
 | This work is licensed under a Creative Commons Attribution 4.0 International License, which permits unrestricted use, distribution, and reproduction in any medium, provided the original work is properly cited. |