DOI:10.32604/cmc.2022.017910

| Computers, Materials & Continua DOI:10.32604/cmc.2022.017910 |  |
| Article |
Energy Efficient Cluster-Based Optimal Resource Management in IoT Environment
1Department of Computer Science and Engineering, Velammal College of Engineering and Technology, Madurai, 625009, India
2Department of Electronics and Communication Engineering, University College of Engineering, BIT Campus, Anna University, Tiruchirappalli, 620024, India
3Department of Information Technology, SRM Institute of Science and Technology, Kattankulathur, 603203, Tamil Nadu, India
4Department of Medical Equipment Technology, College of Applied Medical Sciences, Majmaah University, Al Majmaah, 11952, Saudi Arabia
5Department of Mathematics, College of Science, King Khalid University, P.O. Box 9004, Abha, 61413, Saudi Arabia
6Department of Mathematics, Faculty of Science, Al-Azhar University, Assiut, 71524, Egypt
7College of Computer Information Technology, American University in the Emirates, Dubai, 503000, United Arab Emirates
8Department of Computer Applications, Alagappa University, Karaikudi, India
*Corresponding Author: T. Jayasankar. Email: jayasankar27681@gmail.com
Received: 17 February 2021; Accepted: 02 May 2021
Abstract: Internet of Things (IoT) is a technological revolution that redefined communication and computation of modern era. IoT generally refers to a network of gadgets linked via wireless network and communicates via internet. Resource management, especially energy management, is a critical issue when designing IoT devices. Several studies reported that clustering and routing are energy efficient solutions for optimal management of resources in IoT environment. In this point of view, the current study devises a new Energy-Efficient Clustering-based Routing technique for Resource Management i.e., EECBRM in IoT environment. The proposed EECBRM model has three stages namely, fuzzy logic-based clustering, Lion Whale Optimization with Tumbling (LWOT)-based routing and cluster maintenance phase. The proposed EECBRM model was validated through a series of experiments and the results were verified under several aspects. EECBRM model was compared with existing methods in terms of energy efficiency, delay, number of data transmission, and network lifetime. When simulated, in comparison with other methods, EECBRM model yielded excellent results in a significant manner. Thus, the efficiency of the proposed model is established.
Keywords: IoT environment; clustering; routing; resource management; energy efficiency
Internet of Things (IoT) and Information and Communication Technologies (ICT) can be best leveraged if integrated together. This combination can independently and incredibly reform different domains such as transportation, wearable tools, mobile phones and Personal Computers (PCs). IoT plays a vital role in making modern cities effective by connecting people with global users. This universal connection helps in the distribution of valid and extraordinary data such as video, audio, image, and text. The data exchange phenomenon has become a significant objective in developing a smart city. Smart city concept has evolved to accomplish sustainable and environment-friendly cities. Smart city concept has major frameworks that use key units such as IoT, Cloud Computing (CC), big data, remote sensing, and so on. Besides, various protective sensor networks namely, Wireless Sensor Networks (WSNs), Body Sensor Networks (BSN), Internet of Everything (IoE), Web of Things (WoT) and so on are engaged effectively in the production, collection, execution and transmission of data to enhance smart city approaches. A set of flawless and high value information can be obtained from smart cities using multimedia system.
On the other end, media-based sensors, its efficiency at peak conditions and volatile nature of data collection process stimulate the need for cloud computing model. It is primarily applied in the collection of big data at regular intervals. In this domain, IBM is the chief player among cloud computing service providers across the globe. According to industry reports, the quantity of data generated by and collected from sensor-centric IoT gadgets is set to drastically increase in the coming years than the past. In this scenario, high peak and inconsistent data collection, memory storage, visible data transmission, etc. are some of the complications that pose threat to CC model. Despite the innovation of new devices and models, it still remains ineffective alike classical approaches. Only a handful of developers [1] defined that WSN can collect a maximum amount of data. Among other components used in smart city development, sensor-relied methods such as IoT are predicted to be the main solution for tackling different challenges in corporates, education, agriculture, healthcare and so on. Outstanding growth in lightweight sensors has reformed the conventional firms in healthcare and business by revitalizing innovative objects and seeking the maximum attention of users.
International Data Corporation (IDC) conducted a survey in which it was stated that IoT trading is set to improve drastically to a remarkable volume [2]. Every tool represents the highest performance of IoT in future by realizing movements and models of smart city. From a scientific perspective, IoT examines the bewildering involvement of many applications. Furthermore, it fuses alternative tools and helps in enhancing the ability to reconstruct the universe using massive amounts of data. Thus, IoT is ought to be the main producer of big data and extensively involved in remote sensing, sensor networks, and so on.
Data distribution, association, and supplementation might be regarded as key components in the activation of sustainable pervasive platforms such as smart cities. Periodical investigation of data, obtained from IoT-oriented sensors, allows rapid, apparent, highly-visible, supreme, consistent, and exact data replacement. At this point, multimedia mechanism should be incorporated to accomplish quick data exchange irrespective of the place and time. The main purpose of applying this model is to create a new technology that can achieve green and sustainable smart city by concentrating on IoT-based sensors. Besides, the rapid development of sensors transforms the lifestyle of people into a vibrant one. This further helps in attaining a clear video transmission. Due to ever-growing population, different problems emerge such as financial crisis, environmental issues, food stability and so on. Population growth is a never-ending issue and it paves the way for other problems as well that could not be handled through traditional methods. These problems can be solved with the help of resource-effective, modern, green, and sustainable models which can be leveraged to achieve smart cities.
Owing to dynamic and unpredictable nature of IoT applications, resource management is considered as an important issue to be addressed. In case of private and confidential details of the customer and IoT user, practical management of edge resources is essential to increase the efficiency of IoT network. In this scenario, the current research work presents a novel Energy-Efficient Cluster-based routing technique for Resource Management i.e., EECBRM in IoT environment.
The proposed EECBRM model has three levels such as clustering, routing and cluster maintenance. Initially, fuzzy logic-based clustering technique is applied in the clustering of IoT devices in the network for optimal management of energy resources. Then, Lion Whale Optimization with Tumbling (LWOT)-based routing process is followed which determines the optimal path between IoT devices and server. It is beneficial for further optimization of the resources. Finally, Cluster Maintenance Phase (CMP) is invoked to manage uniform energy distribution among all the IoT devices connected in the network. The presented EECBRM model was validated using a series of experiments and the authors considered a few parameters for this study such as energy efficiency, delay, number of data transmission and network lifetime.
The upcoming sections of the paper are as follows. Section 2 elaborates a few works related to EECBRM in IoT platform. Section 3 discusses the proposed EECBRM model while Section 4 validates the performance of the presented model. Section 5 concludes the study.
IoT-centric smart city has gained attention in the recent years across the globe under different perspectives. Alam et al. [3] proposed a big data sensor model based on the research gap that identified the crises found in smart cities. Traditional cities lack their concentration on energy saving, energy storage, green energy, sustainability and efficient energy supply. However, smart cities generate big data from massive number of network sensors during its day-to-day functions which is highly helpful in improving the lifestyle of people without compromising the environmental issues. Sodhro et al. [4] developed a brief study in data combination, chances, issues, and techniques for IoT-oriented smart cities; however, the study did not consider battery efficiency and reduction in energy exhaustion at the time of video transmission process. The integration of IoT and big data model has been investigated earlier too for smart cities. Such models identified different problems for which the solutions were proposed with the help of new & innovative approaches. However, such studies did not assume power-draining features of IoT-based sensors especially when computing video transmission in smart city model.
Enayet et al. [5] used alternate models and projected the functioning of smart cities in China that generate huge volumes of data. This study introduced a big data management model in cloud computing. The concept did not consider both energy and battery charging drains during video transmission process. Belchandan et al. [6] developed sensor-relied wearable tools for investigating the Electrocardiogram (ECG). The study deployed transmission-based power management devices to save energy in healthcare applications. However, this study too did not disclose information with regards to smart city, energy, and battery-effective paradigms.
Bernard et al. [7] proposed a common responsibility for IoT, communication methods and network classes, while the model did not concentrate on energy saving and battery consumption schemes for video transmission in smart cities. Followed by, Batalla et al. [8] presented a semantic approach that unifies IoT and Machine Learning (ML) approaches for smart cities. In this approach, data retrieval was performed from urban platform. So, it also met a similar challenging issue i.e., non-consideration of green and sustainable video transmission models. In the study [9] conducted earlier, the major responsibility of IoT is predicted to be the development of recent and future models.
On the other hand, a fault detection as well as error alteration model was published in the literature. In this study, delay tolerant technique was proposed for effective power data transmission and the model was also tested with considerable packet loss ratio. However, this method too did not consider power and battery-effective techniques for video transmission in smart cities. Diégue et al. [10] addressed the main function of smart city, its attributes and units in combination with IoT models. In this method, energy and battery-based solutions were not focused, when studying about media broadcasting requirement.
Dasgupta et al. [11] deployed a new model for Hyper-Text Transfer Protocol (HTTP) compliant media streaming, a key supplement for modern domains like entertainment and tourism. This study applied a radio access system to designate the bandwidth among devices for combined streaming within IoT environment. However, the issues such as power and battery charge exhaustion in IoT sensors were not considered for video telecasting.
Aloi et al. [12] conducted a study in IoT atmosphere in which the authors worked on healthcare data transmission using sensor-based tools. This study defined the problems in video transmission and provided solutions using IoT system. In Fortino et al. [13], wearable ECG textile fiber nodes and projection of heart-rate-difference models were applied in medical sector. This method too did not consider green and sustainable principles for video transmission in smart cities. Arasteh et al. [14] developed a smart city approach in line with major data communication methods. Power and battery draining issues that arise due to IoT sensors were not assumed in media transmission.
Haghi et al. [15] created a power and energy-effective solution during media transmission and physiological signals in BSN. A comparative review was conducted upon innovative energy conservation systems in medical applications. However, video transmission was not assumed in smart city models. Lin et al. [16] conducted a wider review regarding dynamic augmented reality-oriented solutions for data collection and resources assignment, since the former facilitates sustainable smart city and IoT platform.
Fig. 1 shows the overall working process of the proposed model. As shown in the figure, energy efficient resource management process, in IoT network, has three major phases such as fuzzy logic-based clustering phase, secure routing phase and cluster maintenance phase.
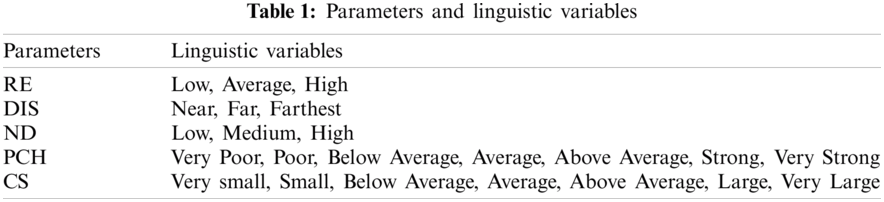
In clustering phase of the projected EECBRM model, two sub-stages exist such as CH election and cluster development. Initially, BS runs the developed model to select both better CHs and proper CS in order to perform uniform load distribution. Next, the selected CHs form different clusters with nearby IoT devices. For CH and CS election, three input variables such as RE, DIS and ND are employed in FL. The resultant attributes are Probability of being CH (PCH) and CS. The initial input i.e., RE implies the overall quantity of energy retained in IoT devices. The second variable i.e., DIS shows the overall distance between IoT devices and servers.
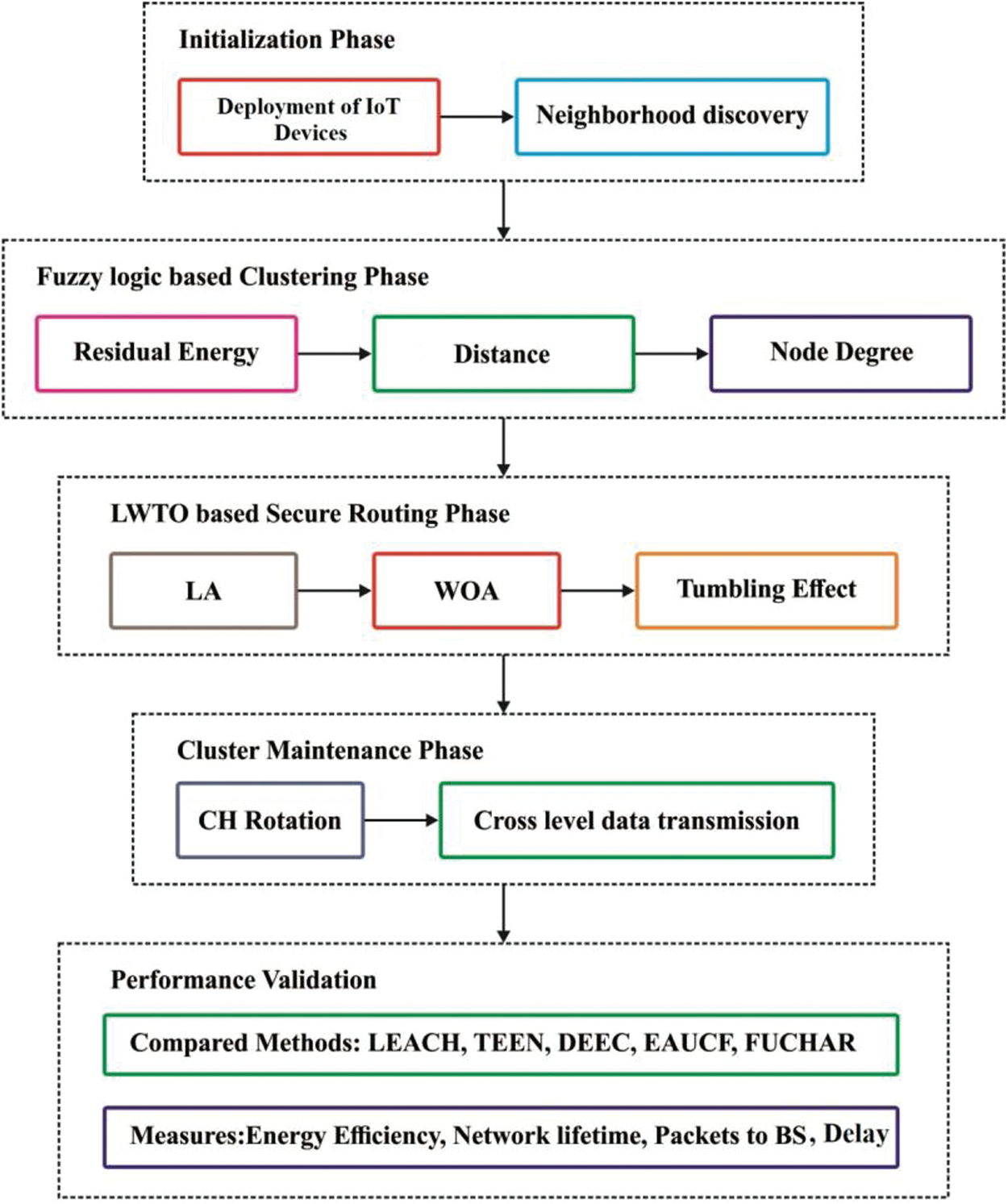
Figure 1: Workflow of the proposed method
Third parameter ND denotes the overall number of adjacent IoT devices in competing radius. The resultant parameter PCH offers a rate that shows the Probability of being CH (PCH). An IoT device, with maximum PCH, has the viability of becoming CH whereas the IoT device with minimum PCH has the least opportunity to become a CH. The output parameter i.e., CS provides the competition radius of each IoT device.
Fig. 2 shows the clustering process in the projected EECBRM which is comprised of four phases.
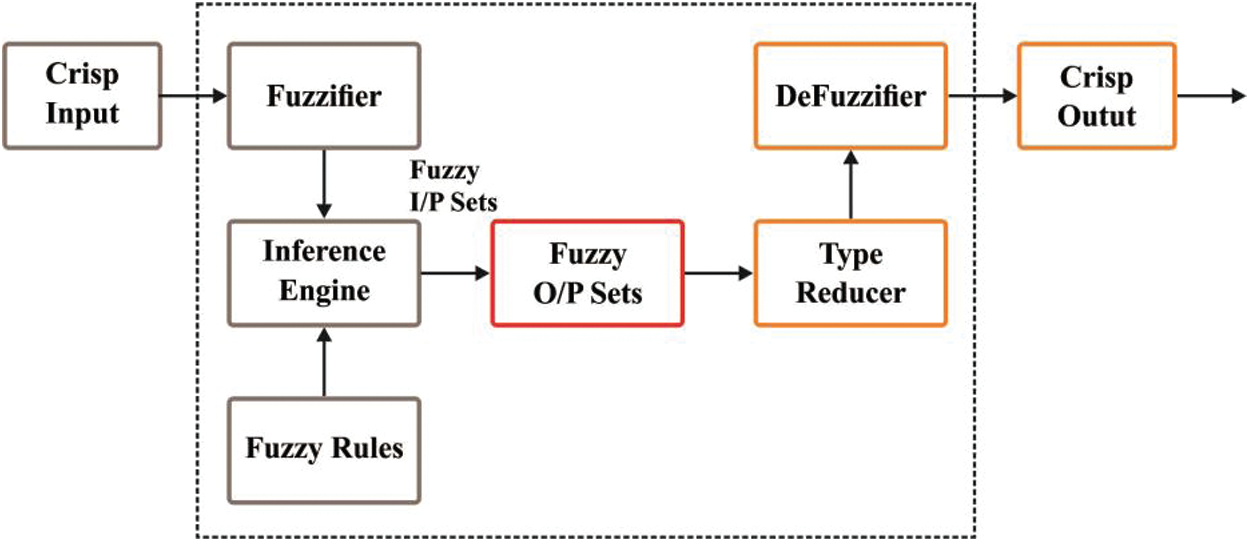
Figure 2: The T2FL model
It transfers the actual input to fuzzified rates. The input parameters for CH election as well as CS determination are formulated in Tab. 1.
The infrastructures of T1FL and T2FL are homogeneous. Here, a collection of 27 rules is applied. The set of fuzzy rules used in the estimation of CHs and CS is represented in (1).
where i denotes the ith rule in fuzzy rule, whereas A1, A2 and A3 denote the corresponding fuzzy sets of x1, x2 and x3 respectively. Rule base inference engine is comprised of 27 rules which are framed on the basis of Mamdani Inference system. In T2FLS, the inference engines combine the rules and match the input T2FS to output T2FS.
3.1.3 Membership Functions (MF)
The MF of the input variable is illustrated in Figs. 3–5. T2FL is implied by a qualified MF and a poor MF. Such functions are represented by T1FL MF. The range of these two functions denote the Footprint Of Uncertainty (FOU) that is applied to define a T2FL set. Assume that FOU is represented by f. While f ∈ [0, 1], and f → 0, then MF is assumed to be T1FL, whereas f → 0 to 1. T2FL is comprised of extensive FOU range between 0 and 1. Therefore, the distribution of rules in T2FL logic is the same as T1FL and is expressed as follows
3.1.4 Type Reducer/Defuzzifier
Type Reducer or Defuzzifer yields the T1FL result which is then converted into mathematical output after the execution of defuzzifier. Afterwards, the IoT devices receive both PCH and CS. Then, a broadcasting message is transmitted to adjacent IoT devices. The message includes Device_ID as well as the measure of PCH. IoT devices, with maximum possibility, are elected as CH and it forwards the CH_WON message to corresponding IoT devices. At this point, it forwards CH_JOIN message and combines it with nearby CH. While receiving CH_JOIN message, the validation of the accessible CS by nearby CH occurs quickly than the approval of novel CM. Since the overall number of recent CMs is not higher than the estimated CS, it confirms the new CM by swapping CM_ACCEPT message or else, CH_REJECT message is forwarded.
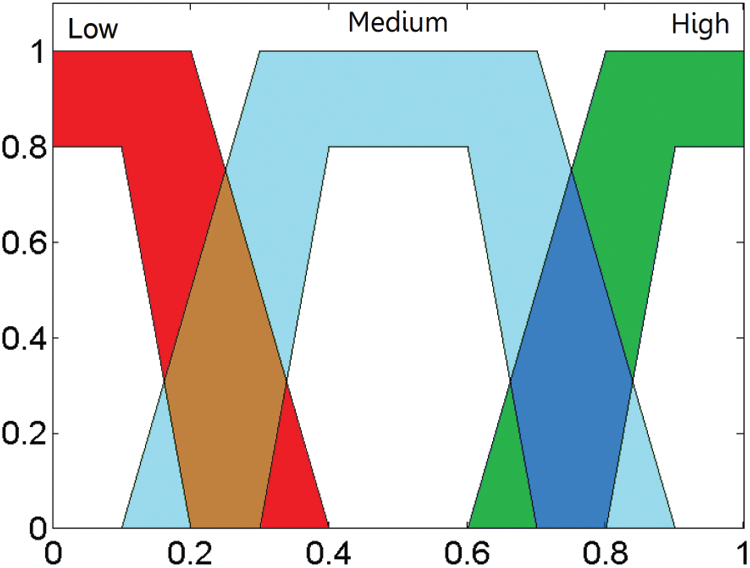
Figure 3: The MF of RE

Figure 4: The MF of DIS

Figure 5: The MF of ND
If CM_REJECT message is accepted, then it re-transmits CM_JOIN message to consecutive CH without the inclusion of CH removal. This process is repeated, until a novel CH is found. If an IoT device does not merge with alternate CH inside the region ‘R’, then it is decided as CH. As a result, every cluster has an IoT device without any division in WSN. If RE of CH exceeds the threshold value, then it results in CH rotation, whereas novel CH would be elected with the help of PCH. By repeating a similar process, early expiry of CH can be decreased and network duration can be enhanced.
3.2 LWTO-Based Secure Routing Scheme
The newly-developed method integrates LA and WOA-T approaches to select the optimal path for secured communication. It considers different QoS parameters such as energy, security, distance, etc. While determining QoS and security attributes, a collection of
LWTO model begins at the initial stage in which the population of whales
where
where
where
where
where
where
where
where
The above procedure is repeated until the termination condition is reached. It is capable of selecting a termination criterion based on the given scenarios.
• Based on the selection of best solution
• Result should not be modified
• Attainment of the desired count
To improve the performance of LWO algorithm, tumbling effect is included, which in turn identifies the parameters that exist in it. Here, the motions of whales are chosen by fitness function. The whales move in an identical path as the chemotactic motion of bacteria which is given herewith.
Once the whales move in the direction of fitness function, the process is referred to as swimming. Otherwise, the motion of whales is carried out based on the movement of bacteria.
3.3 Cluster Maintenance Phase (CMP)
This is an important phase to control the clusters from going overhead. After numerous iterations, the clusters nearby the server are heavily loaded with maximum inter-cluster traffic due to which it releases the energy rapidly. At this point, it is applied in cases such as even load distribution, avoidance of HSP and enhancement of existing models. This phase has two stages such as CH rotation in cluster and cross-level data transmission. Initially, CH rotation is carried out while RE of the CH undergoes iteration until the threshold value. When RE exceeds the threshold value, a novel CH is selected according to PCH of the CH. When a partial number of IoT devices is treated as CHs in a cluster, the knowledge server with minimum count of IoT devices is retained to become a CH. Data transmission is performed by telecasting the message to a consecutive CH. As a result, uniform power distribution is carried out to enhance the network duration.
This section presents the information on the performance of the presented EECBRM model, how it was validated using several types of performance measures and the results attained for the evaluation parameters. To examine the efficiency of EECBRM, some of the parameters given herewith were applied.
• Power utilization: It is applied in the estimation of quantity of energy exhausted by every IoT device at the time of simulation.
• First Node Die (FND): It denotes the number of iterations, when the first IoT device expires. It is applicable in learning time duration, when every IoT device is completely available.
• Half Node Die (HND): It defines the count of iterations for which the IoT device dies in the network. Further, it is an apt value to know the time duration, when half of the IoT devices are dead and remaining them are active.
• Last Node Die (LND): It implies the number of iterations and the count of IoT devices that got expired in the system. This value is used to predict the time, when system may go inactive.
• No. of active nodes per iteration: It mimics the overall number of IoT devices with complete energy.
• Delay: It denotes the total time taken for transmitting data from an IoT device to the destination device.
The efficiency of the projected model was calculated by comparing the performance with popular clustering protocols:
• LEACH is an conventional and familiar model
• TEEN implies the 1st reactive protocol applied in hostile domains
• DEEC is a hybrid clustering protocol that combines the characteristics of TEEN
• EAUCF is said to be fuzzy-relied clustering protocol and is applied for comparison
• FUCHAR is a newly-developed fuzzy centric and routing protocol
4.1 Average Energy Consumption
Fig. 6 shows the results attained for power efficiency of the protocols. Power utilization is measured in terms of maximum energy expended by each sensor under 2500 rounds. EECBRM accomplished the maximum energy efficiency in comparison with other models. The energy conservation in EECBRM approach was high alike fuzzy-based CH election, CS with higher RE, massive number of neighboring IoT devices, higher IoT device centrality and minimum DIS. Followed by, the energy required for intra-cluster communication got reduced. LEACH attained an inferior function owing to following reasons: CHs were elected arbitrarily and it remained independent of reputed measures like RE, distance, and so on. Also, single hop data transmission resulted in maximum power distribution.
Besides, TEEN accomplished minimum power utilization in comparison with LEACH; however, it could not attain the optimal results against EAUCF and the presented technique. Since TEEN is a reactive protocol, it forwards the data in case of a certain action. It minimizes the data transmission and results in low power utilization. Therefore, arbitrary CH election pulls back the performance of TEEN behind EAUCF, FUCHAR and EECBRM methodologies. Even though EAUCF employed FL for CH election, tentative CHs are chosen under the application of probabilistic model. Hence, an IoT device with least RE has less chance of becoming CHs.

Figure 6: Average energy consumption of EECBRM model
Fig. 7 shows the delay analysis of EECBRM model and other methods under different buffer sizes. The figure portrays that the EECBRM model incurred minimal delay compared to other methods. It is also shown that the delay got significantly increased in other methods, when the buffer size increased. However, the EECBRM model attained minimum delay even after an increase in buffer size.

Figure 7: Delay analysis of EECBRM model
4.3 Number of Data Transmissions
The performance of resource management in IoT applications was investigated according to the number of data transmissions that was suitably carried out from CHs to server. The information collected from CHs identifies a partial number of IoT devices. The presented model delayed HND through novel routing principles as well as CMP. Data transmission by different protocols is demonstrated in Fig. 8. The projected approaches produced high number of data transmissions in comparison with LEACH and EAUCF. Fig. 8 conveys that LEACH achieved the worst efficiency under diverse cases in comparison with alternate protocols. In general, LEACH is not capable of managing numerous CMs and it reduced the transmission of data from all sensors to BS. TEEN forwards the sensing data after it reaches a threshold value. However, the newly deployed model sent the data in a hybrid manner, and the data transmission got enhanced in TEEN, but lower than the compared protocols. Additionally, the presented approach insisted that CHs limit the CM on the basis of size of resultant fuzzy.

Figure 8: Number of data transmissions
IoT devices, which are present nearby, tend to get expired quickly. Though it does not affect the functioning of whole system, the data supremacy gets destructed. If HND dies in a network, then the data loses its superiority and becomes poor. When LND dies in a network, it becomes inactive.
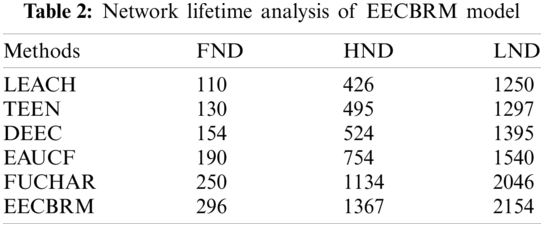
In order to determine the lifespan of IoT network, FND, HND and LND were determined, and are given in Tab. 2 and Fig. 9. It is evident that the presented model reduced the expiry of first IoT device compared to LEACH, TEEN and EAUCF.

Figure 9: Network lifetime analysis of IoT devices
The newly developed model improved the lifespan of the system because of (i) Optimal CH election and CS based on three variables (ii) data transmission using LWOT algorithm and (iii) CMP which in turn made other CHs to use the same quantity of power. The FND of EECBRM model occurred at 296 rounds, whereas the FND of LEACH, TEEN, DEEC, EAUCF and FUCHAR models occurred at 110, 130, 154, 190 and 250 rounds respectively.
Similarly, the HND of the EECBRM model occurred at 1367 rounds, whereas the HND of LEACH, TEEN, DEEC, EAUCF and FUCHAR models occurred at 426, 495, 524, 754 and 1134 rounds respectively. Further, the LND of EECBRM model appeared at 2154 rounds, whereas the LND of LEACH, TEEN, DEEC, EAUCF and FUCHAR models occurred at 1250, 1297, 1395, 1540 and 2046 rounds respectively. Fig. 10 shows the dead node analysis of EECBRM model over simulation time. As shown in the figure, there was a considerable decline in the number of active nodes in EECBRM model, due to optimal allocation of resources in the network. From the figures illustrated above, it is apparent that the EECBRM model ensured optimal allocation of resources among IoT devices in the network and resulted in maximum energy efficiency.

Figure 10: Number of dead node analysis
The current research article introduced a novel EECBRM model for optimal allocation of resources in IoT platform. The proposed EECBRM model has three levels namely, clustering, routing and cluster maintenance. Energy-efficient resource management process, in IoT network, generally has three major phases such as fuzzy logic-based clustering phase, LWOT-based secure routing phase and CMP. The application of CMP helped in uniform energy management among IoT devices in the network. EECBRM model was validated using a series of experiments in terms of energy efficiency, delay, number of data transmissions and network lifetime. The simulation outcome infers that the EECBRM model outperformed other models considerably. Therefore, the current study established EECBRM model as an effective tool for optimal resource allocation in IoT devices. In future, the performance of the EECBRM model can be enhanced using intrusion detection techniques.
Acknowledgement: The authors extend their appreciation to the Deanship of Scientific Research at King Khalid University for funding this work through Research Group Program under Grant Number RGP. 1/58/42.
Funding Statement: This research received the support from the Deanship of Scientific Research at King Khalid University for funding this work through Research Group Program under Grant Number RGP. 1/58/42.
Conflicts of Interest: The authors declare that they have no conflicts of interest to report regarding the present study.
1. A. H. Sodhro, S. P. Irbhulal, Z. Luo and V. H. C. de Albuquerque, “Towards an optimal resource management for IoT based green and sustainable smart cities,” Journal of Cleaner Production, vol. 220, no. 1, pp. 1167–1179, 2019. [Google Scholar]
2. A. H. Sodhro, Z. Luo, G. H. Sodhro, M. Muzamal, J. J. P. C. Rodrigues et al., “Artificial intelligence based QoS optimization for multimedia communication in IoV systems,” Future Generation Computer Systems, vol. 95, no. 1, pp. 667–680, 2019. [Google Scholar]
3. F. Alam, R. Mehmood, I. Katib, N. N. Albogami and A. Albeshri, “Data fusion and IoT for smart ubiquitous environments: A survey,” IEEE Access, vol. 5, pp. 9533–9554, 2017. [Google Scholar]
4. A. H. Sodhro, A. K. Sangaiah, S. Pirphulal, A. Sekhari and Y. Ouzrout, “Green media-aware medical IoT system,” Multimedia Tools and Applications, vol. 78, no. 3, pp. 3045–3064, 2019. [Google Scholar]
5. A. Enayet, M. A. Razzaque, M. M. Hassan, A. Alamri and G. Fortino, “A mobility-aware optimal resource allocation architecture for big data task execution on mobile cloud in smart cities,” IEEE Communications Magazine, vol. 56, no. 2, pp. 110– 117, 2018. [Google Scholar]
6. A. K. Belchandan, K. Deshmukh and J. Kumar, “Removal of noises in ECG signal by using digital FIR-IIR filter in VHDL,” Digital Signal Processing, vol. 8, no. 5, pp. 135–139, 2016. [Google Scholar]
7. T. Bernard and A. Nakib, “Adaptive ECG signal filtering using Bayesian based evolutionary algorithm,” Metaheuristics for Medicine and Biology, Studies in Computational Intelligence Book Series, vol. 704, pp. 187–211, 2017. [Google Scholar]
8. J. M. Batalla, P. Krawiec, C. X. Mavromoustakis, G. Mastorakis, N. Chilamkurti et al., “Efficient media streaming with collaborative terminals for the smart city environment,” IEEE Communications Magazine, vol. 55, no. 1, pp. 98–104, 2017. [Google Scholar]
9. C. Mahapatra, Z. Sheng, V. C. M. Leung and T. Stouraitis, “A reliable and energy efficient IoT data transmission scheme for smart cities based on redundant residue based error correction coding,” in 2015 12th Annual IEEE Int. Conf. on Sensing, Communication, and Networking - Workshops (SECON WorkshopsSeattle, WA, USA, pp. 1–6, 2015. [Google Scholar]
10. D. C. Diégue, A. P. Rivero, D. G. Coego, F. J. G. Castaño, P. S. R. Hernández et al., “Providing IoT services in smart cities through dynamic augmented reality markers,” Sensors, vol. 15, no. 7, pp. 16083–16104, 2015. [Google Scholar]
11. A. Dasgupta, S. Chakraborty and A. Routray, “A two-stage framework for denoising electrooculography signals,” Biomedical Signal Processing and Control, vol. 31, no. 3, pp. 231–237, 2017. [Google Scholar]
12. G. Aloi, G. Caliciuri, G. Fortino, R. Gravina, P. Pace et al., “Enabling IoT interoperability through opportunistic smartphone-based mobile gateways,” Journal of Network and Computer Applications, vol. 81, no. 7, pp. 74–84, 2017. [Google Scholar]
13. G. Fortino, R. Gravina, W. Russo and C. Savaglio, “Modeling and simulating internet-of-things systems: A hybrid agent-oriented approach,” Computing in Science & Engineering, vol. 19, no. 5, pp. 68– 76, 2017. [Google Scholar]
14. H. Arasteh, V. Hosseinnezhad, V. Loia, A. Tommasetti, O. Troisi et al., “IoT-based smart cities: A survey,” in 2016 IEEE 16th Int. Conf. on Environment and Electrical Engineering, Florence, Italy, pp. 1–6, 2016. [Google Scholar]
15. M. Haghi, K. Thurow, I. Habil, R. Stoll and M. Habil, “Wearable devices in medical internet of things: Scientific research and commercially available devices,” Healthcare Informatics Research, vol. 23, no. 1, pp. 4–15, 2017. [Google Scholar]
16. K. Lin, M. Chen, J. Deng, M. M. Hassan and G. Fortino, “Enhanced fingerprinting and trajectory prediction for IoT localization in smart buildings,” IEEE Transactions on Automation Science and Engineering, vol. 13, no. 3, pp. 1294–1307, 2016. [Google Scholar]
17. R. M. Chintalapalli and V. R. Ananthula, “M-LionWhale: Multi-objective optimisation model for secure routing in mobile ad-hoc network,” IET Communications, vol. 12, no. 12, pp. 1406–1415, 2018. [Google Scholar]
 | This work is licensed under a Creative Commons Attribution 4.0 International License, which permits unrestricted use, distribution, and reproduction in any medium, provided the original work is properly cited. |